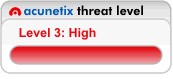
CDT 2012 in: 364 days
A TLS1 server is running on TCP port 443.
SSL server information:
Version: SSL2,SSL3,TLS1
Ciphers suported:
- TLS1_CK_RSA_EXPORT_WITH_RC4_40_MD5(OpenSSL ciphername: EXP-RC4-MD5, Protocol version: TLSv1, Key Exchange: RSA(512), Autentication: RSA, Symmetric encryption method: RC4(40), Message authentication code: MD5, export) - Low strength
- TLS1_CK_RSA_WITH_RC4_128_MD5(OpenSSL ciphername: RC4-MD5, Protocol version: TLSv1, Key Exchange: RSA, Autentication: RSA, Symmetric encryption method: RC4(128), Message authentication code: MD5) - High strength
- TLS1_CK_RSA_WITH_RC4_128_SHA(OpenSSL ciphername: RC4-SHA, Protocol version: TLSv1, Key Exchange: RSA, Autentication: RSA, Symmetric encryption method: RC4(128), Message authentication code: SHA1) - High strength
- TLS1_CK_RSA_EXPORT_WITH_RC2_CBC_40_MD5(OpenSSL ciphername: EXP-RC2-CBC-MD5, Protocol version: TLSv1, Key Exchange: RSA(512), Autentication: RSA, Symmetric encryption method: RC2(40), Message authentication code: MD5, export) - Low strength
- TLS1_CK_RSA_EXPORT_WITH_DES40_CBC_SHA(OpenSSL ciphername: EXP-DES-CBC-SHA, Protocol version: TLSv1, Key Exchange: RSA(512), Autentication: RSA, Symmetric encryption method: DES(40), Message authentication code: SHA1, export) - Low strength
- TLS1_CK_RSA_WITH_DES_CBC_SHA(OpenSSL ciphername: DES-CBC-SHA, Protocol version: TLSv1, Key Exchange: RSA, Autentication: RSA, Symmetric encryption method: DES(56), Message authentication code: SHA1) - Low strength
- TLS1_CK_RSA_WITH_3DES_EDE_CBC_SHA(OpenSSL ciphername: DES-CBC3-SHA, Protocol version: TLSv1, Key Exchange: RSA, Autentication: RSA, Symmetric encryption method: 3DES(168), Message authentication code: SHA1) - High strength
- TLS1_CK_DHE_RSA_EXPORT_WITH_DES40_CBC_SHA(OpenSSL ciphername: EXP-EDH-RSA-DES-CBC-SHA, Protocol version: TLSv1, Key Exchange: DH(512), Autentication: RSA, Symmetric encryption method: DES(40), Message authentication code: SHA1, export) - Low strength
- TLS1_CK_DHE_RSA_WITH_DES_CBC_SHA(OpenSSL ciphername: EDH-RSA-DES-CBC-SHA, Protocol version: TLSv1, Key Exchange: DH, Autentication: RSA, Symmetric encryption method: DES(56), Message authentication code: SHA1) - Low strength
- TLS1_CK_DHE_RSA_WITH_3DES_EDE_CBC_SHA(OpenSSL ciphername: EDH-RSA-DES-CBC3-SHA, Protocol version: TLSv1, Key Exchange: DH, Autentication: RSA, Symmetric encryption method: 3DES(168), Message authentication code: SHA1) - High strength
- TLS1_CK_RSA_WITH_AES_128_CBC_SHA(OpenSSL ciphername: AES128-SHA, Protocol version: TLSv1, Key Exchange: RSA, Autentication: RSA, Symmetric encryption method: AES(128), Message authentication code: SHA1) - High strength
- TLS1_CK_DHE_RSA_WITH_AES_128_CBC_SHA(OpenSSL ciphername: DHE-RSA-AES128-SHA, Protocol version: TLSv1, Key Exchange: DH, Autentication: RSA, Symmetric encryption method: AES(128), Message authentication code: SHA1) - High strength
- TLS1_CK_RSA_WITH_AES_256_CBC_SHA(OpenSSL ciphername: AES256-SHA, Protocol version: TLSv1, Key Exchange: RSA, Autentication: RSA, Symmetric encryption method: AES(256), Message authentication code: SHA1) - High strength
- TLS1_CK_DHE_RSA_WITH_AES_256_CBC_SHA(OpenSSL ciphername: DHE-RSA-AES256-SHA, Protocol version: TLSv1, Key Exchange: DH, Autentication: RSA, Symmetric encryption method: AES(256), Message authentication code: SHA1) - High strength
- TLS1_CK_RSA_WITH_CAMELLIA_128_CBC_SHA(OpenSSL ciphername: n/a, Protocol version: TLSv1, Key Exchange: RSA, Autentication: RSA, Symmetric encryption method: Camellia(128), Message authentication code: SHA1) - High strength
- TLS1_CK_DHE_RSA_WITH_CAMELLIA_128_CBC_SHA(OpenSSL ciphername: n/a, Protocol version: TLSv1, Key Exchange: DH, Autentication: RSA, Symmetric encryption method: Camellia(128), Message authentication code: SHA1) - High strength
- TLS1_CK_RSA_WITH_CAMELLIA_256_CBC_SHA(OpenSSL ciphername: n/a, Protocol version: TLSv1, Key Exchange: RSA, Autentication: RSA, Symmetric encryption method: Camellia(256), Message authentication code: SHA1) - High strength
- TLS1_CK_DHE_RSA_WITH_CAMELLIA_256_CBC_SHA(OpenSSL ciphername: n/a, Protocol version: TLSv1, Key Exchange: DH, Autentication: RSA, Symmetric encryption method: Camellia(256), Message authentication code: SHA1) - |