SAMPLE
|
Site Name |
Start Time |
End Time |
Total Time |
Status |
|---|---|---|---|---|
|
plesk |
October 10, 2010 11:49, EDT |
October 10, 2010 12:25, EDT |
36 minutes |
Success |
The audit was performed on one system which was found to be active and was scanned.
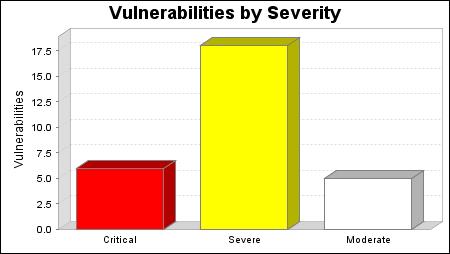 |
There were 29 vulnerabilities found during this scan. Of these, 6 were critical vulnerabilities. Critical vulnerabilities require immediate attention. They are relatively easy for attackers to exploit and may provide them with full control of the affected systems. 18 vulnerabilities were severe. Severe vulnerabilities are often harder to exploit and may not provide the same access to affected systems. There were 5 moderate vulnerabilities discovered. These often provide information to attackers that may assist them in mounting subsequent attacks on your network. These should also be fixed in a timely manner, but are not as urgent as the other vulnerabilities.
 |
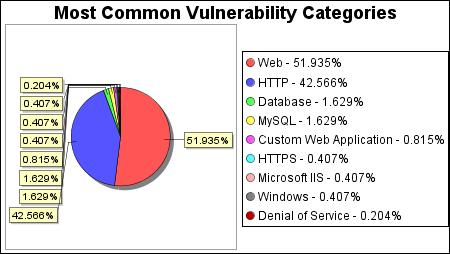 |
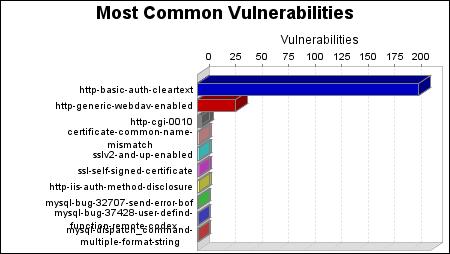
There were 209 occurrences of the http-basic-auth-cleartext vulnerability, making it the most common vulnerability. There were 255 vulnerabilities in the Web category, making it the most common vulnerability category.
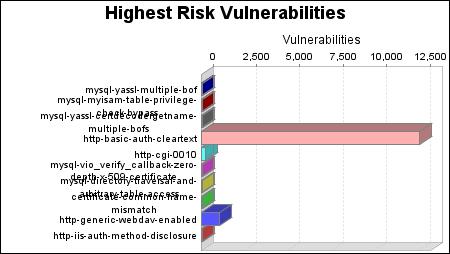 |
The mysql-yassl-multiple-bof, mysql-myisam-table-privilege-check-bypass and mysql-yassl-certdecodergetname-multiple-bofs vulnerabilities pose the highest risk to the organization with a risk score of 90. Vulnerability risk scores are calculated by looking at the likelihood of attack and impact, based upon CVSS metrics. The impact and likelihood are then multiplied by the number of instances of the vulnerability to come up with the final risk score.
One operating system was identified during this scan.
There were 9 services found to be running during this scan.
 |
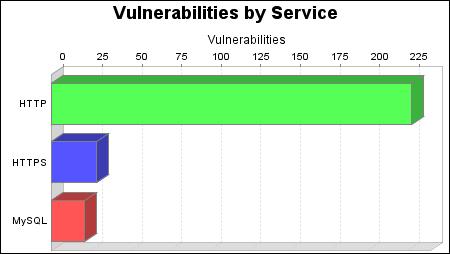 |
The DNS, DNS-TCP, FTP, HTTP, HTTPS, IMAP, Microsoft Remote Display Protocol, MySQL and POP services were found on 1 systems, making them the most common services. The HTTP service was found to have the most vulnerabilities during this scan with 228 vulnerabilities.