CVE-2013-6853: Stored XSS via Code Injection in Y! Toolbar DOM for FireFox on MAC Version 3.1.0.20130813024103 and Windows Version 2.5.9.2013418100420.
Published January 14, 2014 on XSS.Cx by Hoyt LLC
![]()
Date: November 11, 2013 Author: Hoyt LLC http://xss.cx/
A local Stored XSS via Code Injection in Y! Toolbar DOM for FireFox on MAC Version 3.1.0.20130813024103 and Windows Version 2.5.9.2013418100420 allows remote attackers to inject arbitrary Javascript into the Yahoo Toolbar for Firefox via AddBMToolbar : function(domBuilder).
CVE-2013-6853 , Stored XSS, Reflected XSS, DOM XSS, Y! ToolBar DOM, function(domBuilder), clickstream.js, Code Injection, CWE-79, CWE-94, CAPEC-86
This Article provides details with respect to a Vulnerability our Researchers identified in the Yahoo Toolbars for Windows and Mac during Q4/2013 (CVE-2013-6853). The Reader is expected to know how to abuse Firefox Extensions.
The Yahoo Toolbar is a FireFox Plugin which is Downloadable from either Yahoo or Mozilla. The stated purpose of the Y! Toolbar is "Web at your fingertips".. "Get Facebook, email, news, weather and more - right from your toolbar".
Tools Used
Burp Suite Pro - Must Have
JS Prime - Static Javascript Analysis - jQuery + YUI!
DOM XSS Wiki - RTFM for your Brain
Safari Developer Tools - Web Inspector
FireBug - Element Inspection, CLI
SpiderMonkey - JS Testing
JSBeautify - JS Helper
Selenium - Recon, Session Replay
User Agents - IE 8-11, Chrome, Safari/WebKit, Mozilla
DOMinator - Useless for YUI3 debugging, use Safari
CVE-2013-6853 - Stored DOM XSS via Code Injection in Y! Toolbar DOM - REPRO
1. Using Firefox, open URL http://beta.data.toolbar.yahoo.com/
2. Install the Y! Toolbar
3. Open a new Tab in FireFox, Click this PoC:
4. ADD (store) the URL (XSS) in the Y! Toolbar Version 3.1.0.20130813024103 by Clicking on the + "Add to Yahoo Toolbar" Icon at Right on Toolbar.
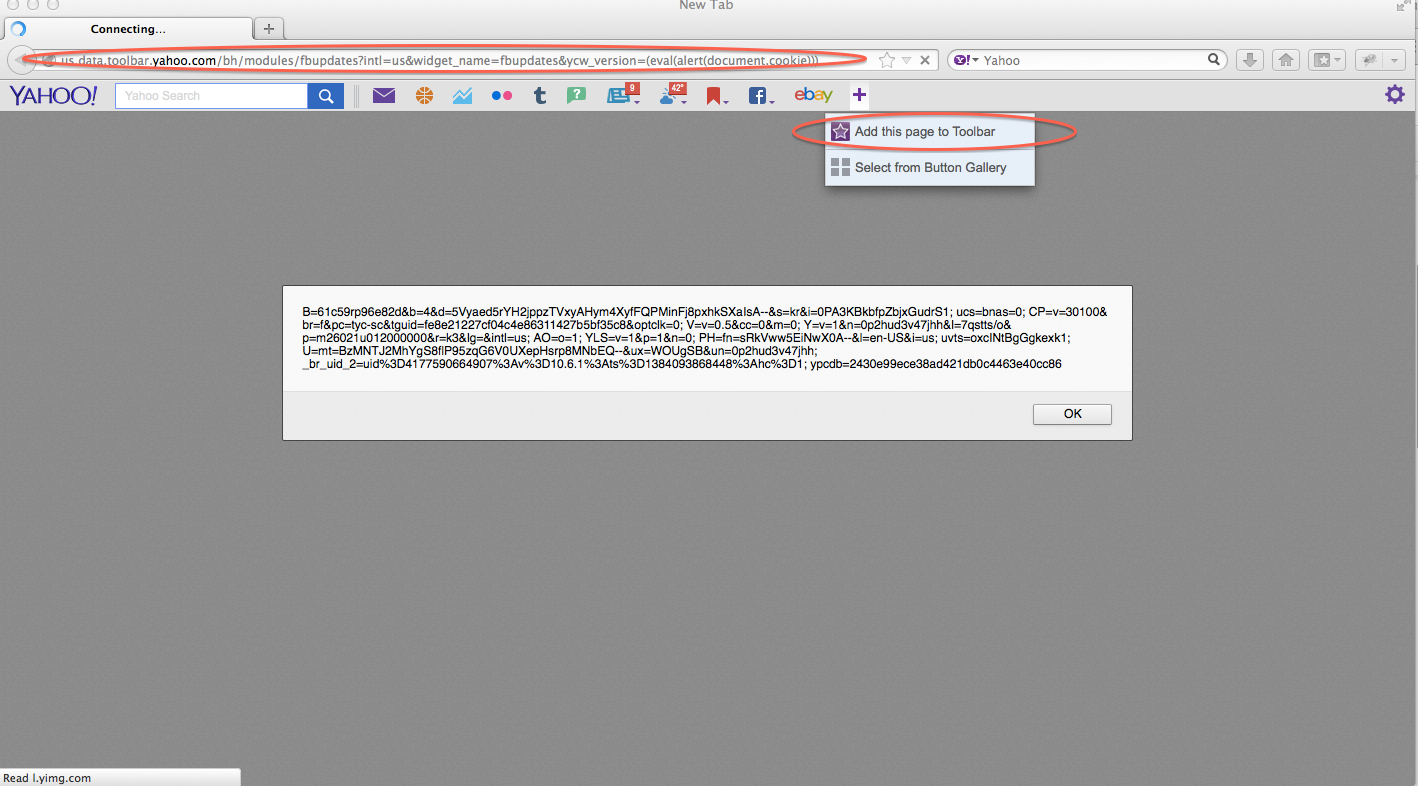
5. Click on the Y! Icon reproducing the XSS.
6. On a MAC, verify the STORED XSS written to File:
~/Library/Application Support/Firefox/Profiles/xxxxxxxxxxx
$ more lb_us_data_toolbar_yahoo_com_*
{"title":"","icon":"http://us.data.toolbar.yahoo.com/favicon.ico","url":"http://us.data.toolbar.yahoo.com/bh/modules/fbupdates?intl=us&widget_name=fbupdates&ycw_version=(eval(alert(document.cookie)))"}
The Y! Toolbar Config File contents with the complete javascript injection, unsanitized: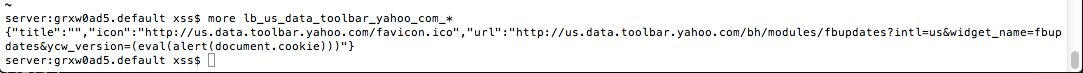
The above Code executes the Stored XSS in the Y! Toolbar DOM.
Additional Functionality of the Y! Toolbar for MAC Version 3.1.0.20130813024103 allows for accessing the Saved URL Feature (Stored XSS PoC) from any Computer (Windows included) as seen below:
CVE-2013-6853 has been assigned for Stored DOM XSS via Code Injection in Y! Toolbar DOM for FireFox on MAC Version 3.1.0.20130813024103 and Windows Version 2.5.9.2013418100420.
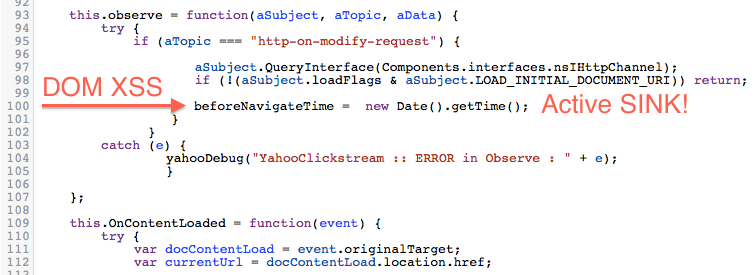
Line 100: beforeNavigateTime = new Date().getTime();